Assignment 5: Software Defined Networking CS640 Spring 2015
|
|
|
- Lynn Jordan
- 5 years ago
- Views:
Transcription
1 Assignment 5: Software Defined Networking CS640 Spring 2015 Due: Thursday, May 7 at 11pm Overview For this project you will implement two control application for a software defined network (SDN). A layer 3 routing application will install rules in SDN switches to forward traffic to hosts using the shortest, valid path through the network. A distributed load balancer application will redirect new TCP connections to hosts in a round robin order. Part 1: Getting Started Part 2: Layer 3 Routing Application Part 3: Distributed Load Balancer Application Submission Instructions Learning Objectives After completing this programming assignment, students should be able to: Contrast SDN applications and traditional network control planes Create SDN applications that use proactive or reactive flow installation Clarifications Access to next table id from LoadBalancer.java You should make the following changes to the L3Routing.java file we provided: 1) Change the qualifiers for the table variable in the L3Routing class to be public static (rather than private) 2) Remove "this." from the front of the assignment to the table variable in the init method in the L3Routing class You should then be able to use L3Routing.table from within the LoadBalancer class to specify the next table id for the OFInstructionGotoTable action you specify for some of the rules installed by your load balancer application. Part 1: Getting Started Your SDN applications will be written in Java and run atop the Floodlight OpenFlow controller. You will use Mininet to emulate a variety of network topologies consisting of OpenFlow switches and hosts. You should continue to use your assigned Mininet virtual machine (VM) for this project. 1/11
2 Preparing Your Environment Before beginning this project, there are some additional steps you need to complete to prepare your VM: 1. Install required packages sudo apt get update sudo apt get install y curl traceroute ant openjdk 7 jdk git iputils arping 2. Download Floodlight: cd ~ git clone plus.git 3. Download the starter code: cd ~ wget tar xzvf assign5.tgz 4. Symlink Floodlight cd ~/assign5/ ln s../floodlight plus 5. Patch Floodlight cd ~/assign5/floodlight plus patch p1 < ~/assign5/floodlight.patch 6. Install new version of Mininet and patch it cd ~/assign5./fixmininet.sh If you want to use Eclipse (on a machine other than your VM) for development, you should do the following: 1. cd floodlight plus ant eclipse 2. Open Eclipse and create a new workspace. Do not choose the floodlightplus or assign5 folders as the location for your workspace. 3. Select File Import General Existing Projects into Workspace. Click Next. 4. From Select root directory click Browse. Select the parent folder containing your floodlight plus and assign5 folders. 5. Check the boxes for floodlight plus and assign5. Click Finish. 6. Exclude the src/test/java folder from the build path: a. Right click on this folder in the Project Explorer pane. b. Select Build Path Remove from Build Path. 7. Add the floodlight plus project to the build path of assign5: a. Right click assign5 in the Project Explorer pane. b. Select Build Path Configure Build Path. c. Under the Projects tab; click Add. d. Check the floodlight plus project; click OK. Running Your Control Applications 1. Compile Floodlight and your applications: cd ~/assign5/ ant This will produce a jar file FloodlightWithApps.jar that includes the compiled code for Floodlight and your SDN applications. 2/11
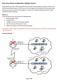
3 2. Start Floodlight and your SDN applications: java jar FloodlightWithApps.jar cf l3routing.prop The above command will start Floodlight and only your layer 3 routing application. You can start both your layer 3 routing and load balancer applications by using loadbalancer.prop for the cf (configuration file) argument. When Floodlight starts, you should see output like the following: 19:15: INFO [n.f.c.m.floodlightmoduleloader:main] Loading modules from file l3routing.prop 19:15: INFO [n.f.c.i.controller:main] Controller role set to MASTER 19:15: INFO [n.f.c.i.controller:main] Flush switches on reconnect Disabled 19:15: INFO [ArpServer:main] Initializing ArpServer... 19:15: INFO [L3Routing:main] Initializing L3Routing... 19:15: INFO [n.f.l.i.linkdiscoverymanager:main] Setting autoportfast feature to OFF 19:15: INFO [ArpServer:main] Starting ArpServer... 19:15: INFO [L3Routing:main] Starting L3Routing... 19:15: INFO [o.s.s.i.c.fallbackccprovider:main] Cluster not yet configured; using fallback local configuration 19:15: INFO [o.s.s.i.syncmanager:main] [32767] Updating sync configuration ClusterConfig [allnodes={32767=node [hostname=localhost, port=6642, nodeid=32767, domainid=32767]}, authscheme=no_auth, keystorepath=null, keystorepassword is unset] 19:15: INFO [o.s.s.i.r.rpcservice:main] Listening for internal floodlight RPC on localhost/ : :15: INFO [n.f.c.i.controller:main] Listening for switch connections on / :6633 Keep the terminal with Floodlight open, as you will need to see the output for debugging. Use another terminal for the next step. Now is a time to use screen. You can install screen in your VM by running: sudo apt get install screen. 3. Start Mininet: sudo./run_mininet.py single,3 The above command will create a topology with a single SDN switch (s1) and three hosts (h1 h3) directly connected to the switch: You can change the number of hosts by changing the numeric value included in the arguments to the run_mininet.py script. You can also start Mininet with six other topologies: linear,n: a chain of n switches with one host connected to each switch; for example, linear,3 produces the following topology: tree,n: a tree of depth n with a single root switch (s1) and two hosts connected to each leaf switch; for example tree,2 produces the following 3/11
4 topology: assign1: creates the topology from Part 3 of Assignment 1: triangle: creates a topology like the triangle_rt topology from Assignment 3: mesh,n: a complete graph with n switches and one host attached to each switch; for example, mesh,5 produces the following topology: someloops: creates the following topology: 4/11
5 Once mininet has started, you should see Floodlight produce output like the following: 11:04: INFO [n.f.c.i.ofchannelhandler:new I/O server worker #2 1] New switch connection from / : :04: INFO [n.f.c.i.ofchannelhandler:new I/O server worker #2 1] Disconnected switch [/ :50921 DPID[?]] 11:04: INFO [n.f.c.i.ofchannelhandler:new I/O server worker #2 2] New switch connection from / : :04: INFO [n.f.c.i.ofchannelhandler:new I/O server worker #2 2] Switch OFSwitchBase [/ :50922 DPID[00:00:00:00:00:00:00:01]] bound to class class net.floodlightcontroller.core.internal.ofswitchimpl, writethrottle=false, description OFDescriptionStatistics [Vendor: Nicira, Inc., Model: Open vswitch, Make: None, Version: 2.0.1, S/N: None] 11:04: INFO [n.f.c.ofswitchbase:new I/O server worker #2 2] Clearing all flows on switch OFSwitchBase [/ :50922 DPID[00:00:00:00:00:00:00:01]] 11:04: WARN [n.f.c.i.c.s.notification:main] Switch 00:00:00:00:00:00:00:01 connected. 11:04: INFO [L3Routing:main] Switch s1 added 11:04: INFO [L3Routing:Topology Updates] Link s1:0 > host updated 11:04: INFO [L3Routing:Topology Updates] Link s1:2 > host updated 11:04: WARN [n.f.c.i.c.s.notification:main] Switch 00:00:00:00:00:00:00:01 port s1 eth1 changed: UP 11:04: INFO [L3Routing:Topology Updates] Link s1:1 > host updated 4. You can now run commands (e.g., ping) in mininet like you did for the previous assignments. However, until you complete Part 2, no packets will be forwarded. You should always start Floodlight and your SDN applications before starting mininet. Also, we recommend that you restart Floodlight and your SDN applications whenever you restart mininet. Resources If you have questions about SDN, OpenFlow, or Floodlight you may want to consult: OpenFlow 1.3 Standard sections 2, 3, and are likely to be the most useful Floodlight plus Javadoc Part 2: Layer 3 Routing Application Background In Assignment 3, you wrote a router control plane that used RIP to construct a route table. The route table was then used by your router s data plane to determine where (i.e., out which interface) a packet should be forwarded. 5/11
6 Your first SDN application will also construct route tables. However, rather than exchanging RIP messages between routers, your application will construct route tables based on a global view of the network topology. The appropriate route table will be installed in each SDN switch by your application, and each SDN switch will forward packets according to the installed route table. It is important to note that SDN switches do not directly support the route table structure used in the last programming assignment. Rather, SDN switches use a more general flow table structure, which can accommodate route tables (used in traditional layer 3 routers), MAC learning tables (used in traditional layer 2 switches), and many other constructs. Each entry, or rule, in a flow table has match criteria that defines (on the basis of fields in Ethernet, IP, TCP, UDP, and other headers) which packets the rule applies to. Each entry also has one or more instructions/actions which should be taken for each packet that matches the rule. Your layer 3 routing application will install entries that match packets based on their destination IP address (and Ethernet type), and execute an output action to send the packet out a specific port on the SDN switch. (You ll use other match criteria and additional instructions/actions for the other SDN application you write, which is described in Part 3.) The match criteria serves the same purpose as the destination and mask fields in a traditional route table, and the output action servers the same purpose as the interface field in a traditional route table. There is no concept of a gateway in SDN flow tables, but that s okay your router only used the gateway to determine how to rewrite a packet s destination MAC address to ensure correct layer 2 forwarding, and we aren t using traditional layer 2 forwarding in SDN. Code Overview The code for your layer 3 routing application will reside in L3Routing.java in the edu.wisc.cs.sdn.apps.l3routing package. The file we provided already contains code to: Access host and topology information from other modules (or applications) included with Floodlight see the gethosts(), getswitches(), and getlinks() methods Receive notifications about changes in the network deviceadded(...), deviceremoved(...), devicemoved(...), switchadded(...), switchremoved(...), and linkdiscoveryupdate(...) We have also provided code in the edu.wisc.cs.sdn.apps.utils package for: An SDN application that responds to ARP requests from hosts see ArpServer.java Telling a switch to install a rule in the flow table, remove rules from the flow table, and send a packet see SwitchCommands.java TODOs You need to complete the TODOs in L3Routing.java to install and remove flow table entries from SDN switches such that traffic is forwarded to a host using the shortest path. Note that Floodlight creates only one instance (i.e., object) of the L3Routing class; this instances handles all switches. Computing Shortest Paths 6/11
7 You should use the Bellman Ford algorithm to compute the shortest paths to reach a host h from every other host h H, h h (H is the set of all hosts). You can use the gethosts(), getswitches(), and getlinks() methods to get the topology information that you need to provide as input to the Bellman Ford algorithm. There will be two link objects between pairs of switches, one in each direction. Due to the way links are discovered, there may be a short period of time (tens of milliseconds) where the controller has a link object only in one direction. If you have a link object in one direction, you can assume the physical link is bidirectional. When a host joins the network, both the deviceadded(...) and linkdiscoveryupdate(...) event handlers will be called. There are no guarantees on which order these event handlers are called. Thus, a host may be added but we may not yet know which switch it is linked to. The isattachedtoswitch() method in the Host class will return true if we know the switch to which a host is connected, otherwise it will return false. If the method returns false, then you do not need to install any rules to route traffic to this host. You can assume the following will always hold true in the network: The network is a connected graph. In other words, there will always be at least one possible path between every pair of switches. There is only one physical link between a pair of switches. Links are undirected. However, be aware that Floodlight maintains a Link object for each direction (i.e., there are two Link objects for each physical link). Installing Rules Once you have determined the shortest path to reach host h from h, you must install a rule in the flow table in every switch in the path. The rule should match IP packets (i.e., Ethernet type is IPv4) whose destination IP is the IP address assigned to host h. You can specify this in Floodlight by creating a new OFMatch object and calling the set methods for the appropriate fields; you must set the Ethernet Type before you set the destination IP. The rule s action should be to output packets on the appropriate port in order to reach the next switch in the path. You can specify this in Floodlight by creating an OFInstructionApplyActions object whose set of actions consists of a single OFActionOutput object with the appropriate port number. SDN switches have multiple flow tables we discuss this more in Part 3. For now, you should install rules in the table specified in the table class variable in the L3Routing class. Also, your rules should never timeout and have a default priority (both defined as constants in the SwitchCommands class). Testing and Debugging You should test your code by sending traffic between various hosts in the network topology mininet s built in pingall command is very useful for this. To help you debug, you can view the contents of an SDN switch s flow tables by running the following command in your mininet VM (not in mininet itself): sudo ovs ofctl O OpenFlow13 dump flows s1 This will output the contents of s1 s flow tables. Change the last argument to output the flow tables from a different switch. 7/11
8 Triggering Event Handlers You can trigger the linkdiscoveryupdate(...) event handler by running any of the following commands in mininet (substituting switch and host names as desired): link s1 s2 down takes down the link between s1 and s2; you can assume the network is a connected graph, so you should never take down a link that would result in a disconnected graph link s1 s2 up brings up the link between s1 and s2 link s1 h1 down takes down the link between s1 and h1; this will also result in a deviceremoved(...) event and the isattachedtoswitch() method for the Host object for h1 will now return false link s1 h1 up brings up the link between s1 and h1; this will also result in a devicemoved(...) event and the isattachedtoswitch() method for the Host object for h1 will now return true You can trigger the deviceremoved(...) event handler by taking down a link between a switch and a host, as described above You can trigger the devicemoved(...) event handler by bringing up a link between a switch and a host, as described above You can trigger the switchremoved(...) event handler by running the following command in a regular terminal window (not in mininet): sudo ovs vsctl del br s1 Note that once a switch is removed, you cannot easily add it back without restarting mininet. You can assume the network is a connected graph, so you should never remove a switch that would result in a disconnected graph. Part 3: Distributed Load Balancer Application Background Networks employ load balancing to distribute client requests among a collection of hosts running a specific service (e.g., a web server). In class, we discussed how DNS could be used to implement load balancing. Load balancing is also commonly implemented using a special piece of hardware. A hardware load balancer is placed in the network and configured with an IP address (e.g., ) and a set of hosts among which it should distribute requests (e.g., and ). Clients wanting to communicate with a service (e.g., a web server) running on those hosts are provided with the IP address of the load balancer, not the IP address of a specific host. Clients initiate a TCP connection to the IP address of the load balancer ( ) and the TCP port associated with the service (e.g., port 80). For each new TCP connection, the load balancer selects one of the specified hosts (usually in round robin order). The load balancer maintains a mapping of active connections identified by the client s IP and TCP port to the assigned hosts. For all packets sent from clients to the load balancer, the load balancer rewrites the destination IP and MAC addresses to the IP and MAC addresses of the selected host. The mapping information stored by the load balancer is used to determine the appropriate host 8/11
9 IP and MAC addresses that should be written into a packet arriving from a client. For all packets sent from servers to clients, the load balancer rewrites the source IP and MAC addresses to the IP and MAC addresses of the load balancer. Your second SDN application will implement the same functionality as a set of hardware load balancers. Your application will be provided with a list of virtual IPs and a set of hosts among which connections to the virtual IPs should be load balanced. (We use the term virtual IP because the IP address is not actually assigned to any node in the network.) When clients initiate TCP connections with a specific virtual IP, SDN switches will send the TCP SYN packet to the SDN controller. Your SDN application will select a host from a predefined set, and install rules in an SDN switch to rewrite the IP and MAC addresses of packets associated with the connection. You will also instruct the SDN switch to match the modified packets against the flow rules installed by your layer 3 routing application and apply the appropriate actions (i.e., send the packets out the appropriate ports). Code Overview The code for your load balancer application will reside in LoadBalancer.java in the edu.wisc.cs.sdn.apps.loadbalancer package. The file we provided already contains code to: Receive a notification when a switch joins the network switchadded(...) Receive a packet from a switch when the packet did not match any entries in the switch s flow table receive(...) The LoadBalancerInstance class represents a single distributed load balancer. (We use the term distributed because the load balancing is performed at many switches, rather than at a single hardware load balancer.) Each load balancer instance has a virtual IP address, virtual MAC address, and set of hosts among which TCP connections should be distributed. The instances class variable in the LoadBalancer class maps a virtual IP address to a specific load balancer instance. TODOs You need to complete the TODOs in LoadBalancer.java to: Install rules in every switch (when it joins the network) to: Notify the controller when a client initiates a TCP connection with a virtual IP we cannot specify TCP flags in match criteria, so the SDN switch will notify the controller of each TCP packet sent to a virtual IP which did not match a connection specific rule (described below) Notify the controller when a client issues an ARP request for the MAC address associated with a virtual IP Match all other packets against the rules in the next table in the switch (described below) Install connection specific rules for each new connection to a virtual IP to: Rewrite the destination IP and MAC address of TCP packets sent from a client to the virtual IP Rewrite the source IP and MAC address of TCP packets sent from server to client Connection specific rules should match packets on the basis of Ethernet type, source IP address, destination IP address, protocol, TCP source port, and TCP destination port. Connection specific rules should take precedence over the rules that send TCP packets to the controller, otherwise every TCP packet would be sent to the controller. Therefore, these rules should have a higher priority than the rules installed when a switch joins the network. Also, we want connection specific rules 9/11
10 to be removed when a TCP connection ends, so connection specific rules should have an idle timeout of 20 seconds. Construct and send an ARP reply packet when a client requests the MAC address associated with a virtual IP Multiple Tables Your load balancer application should work in tandem with your layer 3 routing application. To achieve this, you will need to leverage the multiple tables feature of OpenFlow switches. When packets first arrive at an OpenFlow switch, they are matched against the rules in table 0. The actions for these rules can specify that the packets be modified, output, sent to the controller, and/or matched against the rules in a different table. Your load balancer application should install rules in the table specified in the table class variable in the LoadBalancer class set to table 0 in the loadbalancer.prop configuration file. The connection specific rules that modify IP and MAC addresses should include an instruction to match the modified packets against the rules installed by your layer 3 routing application. Since your layer 3 routing application will install rules in the table class variable in the L3Routing class, this instruction should direct packets to the table defined in this class variable. The modified packet will then be matched against these rules and forwarded out the appropriate port. All packets which are not TCP packets destined for a virtual IP, or packets associated with a connection that has already been assigned to a specific host, should be send directly the table used by your layer 3 routing application. Sending ARP Packets When a client wants to initiate a connection with the virtual IP, it will need to determine the MAC address associated with the virtual IP using ARP. The client does not know the IP is virtual, and since it s not actually assigned to any host, your SDN application must take responsibility for replying to these requests. You can construct an ARP reply packet using the classes in the net.floodlightcontroller.packet package. You can use the sendpacket(...) method in the SwitchCommands class to send the packet. Rule Instructions/Actions When a rule should send a packet to the controller, the rule should include an OFInstructionApplyActions whose set of actions consists of a single OFActionOutput with OFPort.OFPP_CONTROLLER as the port number. When a rule should rewrite the destination IP and MAC addresses of a packet, the rule should include an OFInstructionApplyActions whose set of actions consists of: An OFActionSetField with a field type of OFOXMFieldType.ETH_DST and the desired MAC address as the value An OFActionSetField with a field type of OFOXMFieldType.IPV4_DST and the desired IP address as the value The actions for rewriting the source IP and MAC addresses of a packet are similar. When a packet should be processed by the SDN switch based on the rules installed by your layer 3 routing application, a rule should include an OFInstructionGotoTable whose table number is the value specified in the table class 10/11
11 variable in the L3Routing class. You should make the following changes to the L3Routing.java file we provided: 1) Change the qualifiers for the table variable in the L3Routing class to be public static (rather than private) 2) Remove "this." from the front of the assignment to the table variable in the init method in the L3Routing class You should then be able to use L3Routing.table from within the LoadBalancer class to specify the next table id for the OFInstructionGotoTable action you specify for some of the rules installed by your load balancer application. Testing and Debugging You should test your code by issuing web requests (using curl) from a client host to the virtual IPs. You can add or remove virtual IPs and hosts by modifying the loadbalancer.prop file. To see which packets a host is sending/recieving run: tcpdump v n i hn eth0 replacing N with the host s number. Submission Instructions You must submit a single tar file of the src directory containing the Java source files for your SDN applications. Please submit the entire src directory; do not submit any other files or directories. To create the tar file, run the following command, replacing username1 and username2 with the CS username of each group member: tar czvf username1_username2.tgz src Upload the tar file to the Assignment 5 dropbox on UW. Please submit only one tar file per group. 11/11
Project 4: SDNs Due: 11:59 PM, Dec 12, 2018
 CS168 Computer Networks Fonseca Project 4: SDNs Due: 11:59 PM, Dec 12, 2018 Contents 1 Introduction 2 2 Overview 2 2.1 Architecture......................................... 3 3 Shortest-path Switching
CS168 Computer Networks Fonseca Project 4: SDNs Due: 11:59 PM, Dec 12, 2018 Contents 1 Introduction 2 2 Overview 2 2.1 Architecture......................................... 3 3 Shortest-path Switching
Intro to OpenFlow Tutorial
 GENIExperimenter/Tutorials/OpenFlowOVS-Floodlight GENI: geni Intro to OpenFlow Tutorial Overview: This is a simple OpenFlow tutorial that will guide you how to use the Floodlight Controller in conjunction
GENIExperimenter/Tutorials/OpenFlowOVS-Floodlight GENI: geni Intro to OpenFlow Tutorial Overview: This is a simple OpenFlow tutorial that will guide you how to use the Floodlight Controller in conjunction
How to Work with Fast-Failover OpenFlow Groups
 How to Work with Fast-Failover OpenFlow Groups Background Redundant links are frequently used in network topology design in order to reduce the risk of end-to-end connectivity failure due to a single link
How to Work with Fast-Failover OpenFlow Groups Background Redundant links are frequently used in network topology design in order to reduce the risk of end-to-end connectivity failure due to a single link
Denial-of-Service (DoS) Attacks in an SDN Environment
 Denial-of-Service (DoS) Attacks in an SDN Environment Contents Experiment Task Design:... 3 Submission:... 3 Start the Experiment... 3 Conduct the Experiment... 6 Section 1.1: Installing Dependencies...
Denial-of-Service (DoS) Attacks in an SDN Environment Contents Experiment Task Design:... 3 Submission:... 3 Start the Experiment... 3 Conduct the Experiment... 6 Section 1.1: Installing Dependencies...
Design and development of the reactive BGP peering in softwaredefined routing exchanges
 Design and development of the reactive BGP peering in softwaredefined routing exchanges LECTURER: HAO-PING LIU ADVISOR: CHU-SING YANG (Email: alen6516@gmail.com) 1 Introduction Traditional network devices
Design and development of the reactive BGP peering in softwaredefined routing exchanges LECTURER: HAO-PING LIU ADVISOR: CHU-SING YANG (Email: alen6516@gmail.com) 1 Introduction Traditional network devices
Software-Defined Networking (Continued)
 Software-Defined Networking (Continued) CS640, 2015-04-23 Announcements Assign #5 released due Thursday, May 7 at 11pm Outline Recap SDN Stack Layer 2 Learning Switch Control Application Design Considerations
Software-Defined Networking (Continued) CS640, 2015-04-23 Announcements Assign #5 released due Thursday, May 7 at 11pm Outline Recap SDN Stack Layer 2 Learning Switch Control Application Design Considerations
ADVANCED COMPUTER NETWORKS Assignment 9: Introduction to OpenFlow
 Spring Term 2015 ADVANCED COMPUTER NETWORKS Assignment 9: Introduction to OpenFlow Assigned on: 7 May 2015 Due by: 20 May 2015, 23:59 1 Introduction The goal of this assignment is to give an introduction
Spring Term 2015 ADVANCED COMPUTER NETWORKS Assignment 9: Introduction to OpenFlow Assigned on: 7 May 2015 Due by: 20 May 2015, 23:59 1 Introduction The goal of this assignment is to give an introduction
Lab 3: Simple Firewall using OpenFlow
 Lab 3: Simple Firewall using OpenFlow This lab builds on the knowledge acquired through Lab 1 where you were first introduced to the Mininet environment. It will also help you prepare for the class project.
Lab 3: Simple Firewall using OpenFlow This lab builds on the knowledge acquired through Lab 1 where you were first introduced to the Mininet environment. It will also help you prepare for the class project.
ADVANCED COMPUTER NETWORKS Assignment 9: Introduction to OpenFlow
 Spring Term 2014 ADVANCED COMPUTER NETWORKS Assignment 9: Introduction to OpenFlow Assigned on: 8 May 2014 Due by: 21 May 2014, 23:59 1 Introduction The goal of this assignment is to give an introduction
Spring Term 2014 ADVANCED COMPUTER NETWORKS Assignment 9: Introduction to OpenFlow Assigned on: 8 May 2014 Due by: 21 May 2014, 23:59 1 Introduction The goal of this assignment is to give an introduction
Outline. SDN Overview Mininet and Ryu Overview Mininet VM Setup Ryu Setup OpenFlow Protocol and Open vswitch Reference
 1 Mininet and Ryu 2 Outline SDN Overview Mininet and Ryu Overview Mininet VM Setup Ryu Setup OpenFlow Protocol and Open vswitch Reference 3 SDN Overview Decoupling of control and data planes Directly Programmable
1 Mininet and Ryu 2 Outline SDN Overview Mininet and Ryu Overview Mininet VM Setup Ryu Setup OpenFlow Protocol and Open vswitch Reference 3 SDN Overview Decoupling of control and data planes Directly Programmable
Experiment Task Design:
 Experiment Task Design: In this task, students should demonstrate how the DOS attack on data-plane works, and describe the observed consequence. The following sections give stepby-step instructions to
Experiment Task Design: In this task, students should demonstrate how the DOS attack on data-plane works, and describe the observed consequence. The following sections give stepby-step instructions to
Network softwarization Lab session 2: OS Virtualization Networking
 Network softwarization Lab session 2: OS Virtualization Networking Nicolas Herbaut David Bourasseau Daniel Negru December 16, 2015 1 Introduction 1.1 Discovering docker 1.1.1 Installation Please launch
Network softwarization Lab session 2: OS Virtualization Networking Nicolas Herbaut David Bourasseau Daniel Negru December 16, 2015 1 Introduction 1.1 Discovering docker 1.1.1 Installation Please launch
Intro to OpenFlow Tutorial
 5/24/2015 GENIExperimenter/Tutorials/OpenFlowOVS GENI: geni Intro to OpenFlow Tutorial Overview: This is a simple OpenFlow tutorial that will guide you through the writing of simple OpenFlow controllers
5/24/2015 GENIExperimenter/Tutorials/OpenFlowOVS GENI: geni Intro to OpenFlow Tutorial Overview: This is a simple OpenFlow tutorial that will guide you through the writing of simple OpenFlow controllers
VPN-against-Firewall Lab: Bypassing Firewalls using VPN
 SEED Labs 1 VPN-against-Firewall Lab: Bypassing Firewalls using VPN Copyright c 2016 Wenliang Du, Syracuse University. The development of this document was partially funded by the National Science Foundation
SEED Labs 1 VPN-against-Firewall Lab: Bypassing Firewalls using VPN Copyright c 2016 Wenliang Du, Syracuse University. The development of this document was partially funded by the National Science Foundation
LAB THREE STATIC ROUTING
 LAB THREE STATIC ROUTING In this lab you will work with four different network topologies. The topology for Parts 1-4 is shown in Figure 3.1. These parts address router configuration on Linux PCs and a
LAB THREE STATIC ROUTING In this lab you will work with four different network topologies. The topology for Parts 1-4 is shown in Figure 3.1. These parts address router configuration on Linux PCs and a
Internet Technology. 15. Things we didn t get to talk about. Paul Krzyzanowski. Rutgers University. Spring Paul Krzyzanowski
 Internet Technology 15. Things we didn t get to talk about Paul Krzyzanowski Rutgers University Spring 2016 May 6, 2016 352 2013-2016 Paul Krzyzanowski 1 Load Balancers Load Balancer External network NAT
Internet Technology 15. Things we didn t get to talk about Paul Krzyzanowski Rutgers University Spring 2016 May 6, 2016 352 2013-2016 Paul Krzyzanowski 1 Load Balancers Load Balancer External network NAT
Open SDN Controller Applications
 The following topics describe the five applications that Open SDN Controller provides to facilitate the day-to-day administration of your network: BGPLS Manager, page 1 Inventory Manager, page 3 Model
The following topics describe the five applications that Open SDN Controller provides to facilitate the day-to-day administration of your network: BGPLS Manager, page 1 Inventory Manager, page 3 Model
Putting it all together
 Putting it all together What happens when a user shows up to a new network and wants to access a web site? (These are new slides. Please stop and ask questions if anything is unclear!) Scenario Scenario
Putting it all together What happens when a user shows up to a new network and wants to access a web site? (These are new slides. Please stop and ask questions if anything is unclear!) Scenario Scenario
Programming Assignment
 Overview Programming Assignment In this assignment, you will program the OpenFlow controller POX and use it to implement two applications. Task 1: Firewall In this part, your task is to implement a layer-2
Overview Programming Assignment In this assignment, you will program the OpenFlow controller POX and use it to implement two applications. Task 1: Firewall In this part, your task is to implement a layer-2
vrealize Operations Management Pack for NSX for vsphere 3.5.0
 vrealize Operations Management Pack for NSX for vsphere 3.5.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
vrealize Operations Management Pack for NSX for vsphere 3.5.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
HP 5920 & 5900 Switch Series
 HP 5920 & 5900 Switch Series OpenFlow Command Reference Part number: 5998-4679a Software version: Release 23xx Document version: 6W101-20150320 Legal and notice information Copyright 2015 Hewlett-Packard
HP 5920 & 5900 Switch Series OpenFlow Command Reference Part number: 5998-4679a Software version: Release 23xx Document version: 6W101-20150320 Legal and notice information Copyright 2015 Hewlett-Packard
Configuring OpenFlow 1
 Contents Configuring OpenFlow 1 Overview 1 OpenFlow switch 1 OpenFlow port 1 OpenFlow instance 2 OpenFlow flow table 3 Group table 5 Meter table 5 OpenFlow channel 6 Protocols and standards 7 Configuration
Contents Configuring OpenFlow 1 Overview 1 OpenFlow switch 1 OpenFlow port 1 OpenFlow instance 2 OpenFlow flow table 3 Group table 5 Meter table 5 OpenFlow channel 6 Protocols and standards 7 Configuration
Configuration and Management of Networks
 Final Laboratory Configuration and Management of Networks The final Lab consists in configuring a series of case study routing topologies to configure without instructions. Each scenario has a small description
Final Laboratory Configuration and Management of Networks The final Lab consists in configuring a series of case study routing topologies to configure without instructions. Each scenario has a small description
F5 BIG-IQ Centralized Management: Local Traffic & Network. Version 5.2
 F5 BIG-IQ Centralized Management: Local Traffic & Network Version 5.2 Table of Contents Table of Contents BIG-IQ Local Traffic & Network: Overview... 5 What is Local Traffic & Network?... 5 Understanding
F5 BIG-IQ Centralized Management: Local Traffic & Network Version 5.2 Table of Contents Table of Contents BIG-IQ Local Traffic & Network: Overview... 5 What is Local Traffic & Network?... 5 Understanding
OpenFlow. Finding Feature Information. Prerequisites for OpenFlow
 Finding Feature Information, page 1 Prerequisites for, page 1 Restrictions for, page 2 Information About Open Flow, page 3 Configuring, page 8 Monitoring, page 12 Configuration Examples for, page 12 Finding
Finding Feature Information, page 1 Prerequisites for, page 1 Restrictions for, page 2 Information About Open Flow, page 3 Configuring, page 8 Monitoring, page 12 Configuration Examples for, page 12 Finding
OpenFlow. Finding Feature Information. Prerequisites for OpenFlow
 Finding Feature Information, page 1 Prerequisites for, page 1 Restrictions for, page 2 Information About Open Flow, page 3 Configuring, page 8 Monitoring, page 12 Configuration Examples for, page 12 Finding
Finding Feature Information, page 1 Prerequisites for, page 1 Restrictions for, page 2 Information About Open Flow, page 3 Configuring, page 8 Monitoring, page 12 Configuration Examples for, page 12 Finding
Web-Based User Interface for the Floodlight SDN Controller
 3175 Web-Based User Interface for the Floodlight SDN Controller Hakan Akcay Department of Computer Engineering, Istanbul University, Istanbul Email: hknakcay@gmail.com Derya Yiltas-Kaplan Department of
3175 Web-Based User Interface for the Floodlight SDN Controller Hakan Akcay Department of Computer Engineering, Istanbul University, Istanbul Email: hknakcay@gmail.com Derya Yiltas-Kaplan Department of
Software Defined Networking
 Software Defined Networking Daniel Zappala CS 460 Computer Networking Brigham Young University Proliferation of Middleboxes 2/16 a router that manipulatees traffic rather than just forwarding it NAT rewrite
Software Defined Networking Daniel Zappala CS 460 Computer Networking Brigham Young University Proliferation of Middleboxes 2/16 a router that manipulatees traffic rather than just forwarding it NAT rewrite
vrealize Operations Management Pack for NSX for vsphere 3.0
 vrealize Operations Management Pack for NSX for vsphere 3.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
vrealize Operations Management Pack for NSX for vsphere 3.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
Cisco Unified Operating System Administration Web Interface
 Cisco Unified Operating System Administration Web Interface ServerGroup, page 1 Hardware, page 2 Network Configuration, page 3 Software Packages, page 4 System, page 5 IP Preferences, page 6 Ethernet Configuration,
Cisco Unified Operating System Administration Web Interface ServerGroup, page 1 Hardware, page 2 Network Configuration, page 3 Software Packages, page 4 System, page 5 IP Preferences, page 6 Ethernet Configuration,
Cisco Unified Operating System Administration Web Interface for Cisco Emergency Responder
 Cisco Unified Operating System Administration Web Interface for Cisco Emergency Responder These topics describe the Cisco Unified Operating System (OS) Administration web interface for Cisco Emergency
Cisco Unified Operating System Administration Web Interface for Cisco Emergency Responder These topics describe the Cisco Unified Operating System (OS) Administration web interface for Cisco Emergency
WhatsConfigured v3.1 User Guide
 WhatsConfigured v3.1 User Guide Contents Table of Contents Welcome to WhatsConfigured v3.1 Finding more information and updates... 1 Sending feedback... 2 Deploying WhatsConfigured STEP 1: Prepare the
WhatsConfigured v3.1 User Guide Contents Table of Contents Welcome to WhatsConfigured v3.1 Finding more information and updates... 1 Sending feedback... 2 Deploying WhatsConfigured STEP 1: Prepare the
Lab Using Wireshark to Examine Ethernet Frames
 Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
Firewall Evasion Lab: Bypassing Firewalls using VPN
 SEED Labs Firewall Evasion Lab 1 Firewall Evasion Lab: Bypassing Firewalls using Copyright 2018 Wenliang Du, Syracuse University. The development of this document was partially funded by the National Science
SEED Labs Firewall Evasion Lab 1 Firewall Evasion Lab: Bypassing Firewalls using Copyright 2018 Wenliang Du, Syracuse University. The development of this document was partially funded by the National Science
vrealize Operations Management Pack for NSX for vsphere 2.0
 vrealize Operations Management Pack for NSX for vsphere 2.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
vrealize Operations Management Pack for NSX for vsphere 2.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition.
Loadbalancer.org Virtual Appliance quick start guide v6.3
 Loadbalancer.org Virtual Appliance quick start guide v6.3 What are your objectives?...2 What is the difference between a one-arm and a two-arm configuration?...2 What are the different load balancing methods
Loadbalancer.org Virtual Appliance quick start guide v6.3 What are your objectives?...2 What is the difference between a one-arm and a two-arm configuration?...2 What are the different load balancing methods
OPENSDNCORE RELEASE 4. Use cases
 OPENSDNCORE RELEASE 4 Use cases AGENDA q Service Function Chaining q Tunneling with OpenSDNCore q Queues and Metering for QoS q Full Mesh Routing q Adaptive Flow Placement q Labeling q LoadBalancing 2
OPENSDNCORE RELEASE 4 Use cases AGENDA q Service Function Chaining q Tunneling with OpenSDNCore q Queues and Metering for QoS q Full Mesh Routing q Adaptive Flow Placement q Labeling q LoadBalancing 2
vrealize Operations Management Pack for NSX for Multi-Hypervisor
 vrealize Operations Management Pack for This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more
vrealize Operations Management Pack for This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more
Mininet/Openflow. Objectives. Network Topology. You will need a Number
 Mininet/Openflow Objectives In this lab, you will start by learning the basics of running Mininet in a virtual machine. Mininet facilitates creating and manipulating Software Defined Networking components.
Mininet/Openflow Objectives In this lab, you will start by learning the basics of running Mininet in a virtual machine. Mininet facilitates creating and manipulating Software Defined Networking components.
Assignment 5. 2 Assignment: Emulate a Data Center and Manage it via a Cloud Network Controller
 University of Crete Computer Science Department Lecturer: Prof. Dr. X. Dimitropoulos TAs: Dimitrios Gkounis, George Nomikos Manos Lakiotakis, George Vardakis HY436 - Software Defined Networks Tasks of
University of Crete Computer Science Department Lecturer: Prof. Dr. X. Dimitropoulos TAs: Dimitrios Gkounis, George Nomikos Manos Lakiotakis, George Vardakis HY436 - Software Defined Networks Tasks of
CIS 632 / EEC 687 Mobile Computing
 CIS 63 / EEC 687 Mobile Computing IP Software: Routing Prof. Chansu Yu Network Protocols for Wired Network: Ethernet Ethernet address 48-bit, also called hardware/physical/mac/layer address Globally unique:
CIS 63 / EEC 687 Mobile Computing IP Software: Routing Prof. Chansu Yu Network Protocols for Wired Network: Ethernet Ethernet address 48-bit, also called hardware/physical/mac/layer address Globally unique:
Using Diagnostic Tools
 Using Diagnostic Tools The Tools System Diagnostics page on the INVESTIGATE view provides several diagnostic tools that help troubleshoot various kinds of network problems and process monitors. Tech Support
Using Diagnostic Tools The Tools System Diagnostics page on the INVESTIGATE view provides several diagnostic tools that help troubleshoot various kinds of network problems and process monitors. Tech Support
Dropping Packets in Ubuntu Linux using tc and iptables
 Dropping Packets in Ubuntu Linux using tc and... 1 Dropping Packets in Ubuntu Linux using tc and iptables By Steven Gordon on Tue, 18/01/2011-8:13pm There are two simple ways to randomly drop packets on
Dropping Packets in Ubuntu Linux using tc and... 1 Dropping Packets in Ubuntu Linux using tc and iptables By Steven Gordon on Tue, 18/01/2011-8:13pm There are two simple ways to randomly drop packets on
H3C S9800 Switch Series
 H3C S9800 Switch Series OpenFlow Configuration Guide Hangzhou H3C Technologies Co., Ltd. http://www.h3c.com Software version: Release 213x Document version: 6W101-20151130 Copyright 2015, Hangzhou H3C
H3C S9800 Switch Series OpenFlow Configuration Guide Hangzhou H3C Technologies Co., Ltd. http://www.h3c.com Software version: Release 213x Document version: 6W101-20151130 Copyright 2015, Hangzhou H3C
Basic Cisco Router Configuration: Multiple Routers
 Basic Cisco Router Configuration: Multiple Routers Routers rarely exist alone. Most organizations have several to several dozens of routers. In this Lab, we will study two different ways in which routers
Basic Cisco Router Configuration: Multiple Routers Routers rarely exist alone. Most organizations have several to several dozens of routers. In this Lab, we will study two different ways in which routers
ENDEAVOUR: Towards a flexible software-defined network ecosystem
 ENDEAVOUR: Towards a flexible software-defined network ecosystem Project name ENDEAVOUR Project ID H2020-ICT-2014-1 Project No. 644960 Working Package Number 2 Deliverable Number 2.3 Document title Implementation
ENDEAVOUR: Towards a flexible software-defined network ecosystem Project name ENDEAVOUR Project ID H2020-ICT-2014-1 Project No. 644960 Working Package Number 2 Deliverable Number 2.3 Document title Implementation
Lab Using Wireshark to Examine Ethernet Frames
 Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
Topology Objectives Part 1: Examine the Header Fields in an Ethernet II Frame Part 2: Use Wireshark to Capture and Analyze Ethernet Frames Background / Scenario When upper layer protocols communicate with
Configuration and Management of Networks 2014 / 2015
 ! Departamento de Engenharia Electrotécnica Configuration and Management of Networks 2014 / 2015 Mestrado Integrado em Engenharia Electrotécnica e de Computadores 4º ano 8º semestre Final Lab part II:
! Departamento de Engenharia Electrotécnica Configuration and Management of Networks 2014 / 2015 Mestrado Integrado em Engenharia Electrotécnica e de Computadores 4º ano 8º semestre Final Lab part II:
Command Manual Network Protocol. Table of Contents
 Table of Contents Table of Contents Chapter 1 IP Address Configuration Commands... 1-1 1.1 IP Address Configuration Commands... 1-1 1.1.1 display ip host... 1-1 1.1.2 display ip interface... 1-1 1.1.3
Table of Contents Table of Contents Chapter 1 IP Address Configuration Commands... 1-1 1.1 IP Address Configuration Commands... 1-1 1.1.1 display ip host... 1-1 1.1.2 display ip interface... 1-1 1.1.3
Xen*, SDN and Apache Cloudstack. Sebastien Goasguen, Apache CloudStack Citrix EMEA August 28 th 2012 Xen Summit
 Xen*, SDN and Apache Cloudstack Sebastien Goasguen, Apache CloudStack Citrix EMEA August 28 th 2012 Xen Summit Outline A bit about CloudStack A bit about SDN A bit about OpenVswitch Some bits about SDN
Xen*, SDN and Apache Cloudstack Sebastien Goasguen, Apache CloudStack Citrix EMEA August 28 th 2012 Xen Summit Outline A bit about CloudStack A bit about SDN A bit about OpenVswitch Some bits about SDN
I Commands. iping, page 2 iping6, page 4 itraceroute, page 5 itraceroute6 vrf, page 6. itraceroute vrf encap vxlan, page 12
 iping, page 2 iping6, page 4 itraceroute, page 5 itraceroute6 vrf, page 6 itraceroute6 vrf encap vlan, page 7 itraceroute6 vrf encap vxlan dst-mac, page 8 itraceroute vrf, page 9 itraceroute vrf encap
iping, page 2 iping6, page 4 itraceroute, page 5 itraceroute6 vrf, page 6 itraceroute6 vrf encap vlan, page 7 itraceroute6 vrf encap vxlan dst-mac, page 8 itraceroute vrf, page 9 itraceroute vrf encap
Addressing and Routing
 Addressing and Routing Andrew Scott a.scott@lancaster.ac.uk Physical/ Hardware Addresses Aka MAC* or link(-layer) address Can only talk to things on same link Unique ID given to every network interface
Addressing and Routing Andrew Scott a.scott@lancaster.ac.uk Physical/ Hardware Addresses Aka MAC* or link(-layer) address Can only talk to things on same link Unique ID given to every network interface
BIG-IQ Centralized Management: ADC. Version 5.0
 BIG-IQ Centralized Management: ADC Version 5.0 Table of Contents Table of Contents BIG-IQ Application Delivery Controller: Overview...5 What is Application Delivery Controller?...5 Managing Device Resources...7
BIG-IQ Centralized Management: ADC Version 5.0 Table of Contents Table of Contents BIG-IQ Application Delivery Controller: Overview...5 What is Application Delivery Controller?...5 Managing Device Resources...7
CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists
 CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists Name: In this lab you will learn: PartA Cisco 2600 Router Configuration Static Routing PartB 20 min Dynamic
CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists Name: In this lab you will learn: PartA Cisco 2600 Router Configuration Static Routing PartB 20 min Dynamic
A short walk-through of Mininet and POX
 A short walk-through of Mininet and POX This tutorial has three parts. The first part covers the basics of the Mininet network emulation environment under which your programming assignment will be carried
A short walk-through of Mininet and POX This tutorial has three parts. The first part covers the basics of the Mininet network emulation environment under which your programming assignment will be carried
CS 344/444 Spring 2008 Project 2 A simple P2P file sharing system April 3, 2008 V0.2
 CS 344/444 Spring 2008 Project 2 A simple P2P file sharing system April 3, 2008 V0.2 1 Introduction For this project you will write a P2P file sharing application named HiP2P running on the N800 Tablet.
CS 344/444 Spring 2008 Project 2 A simple P2P file sharing system April 3, 2008 V0.2 1 Introduction For this project you will write a P2P file sharing application named HiP2P running on the N800 Tablet.
Introduction to Computer Networks. CS 166: Introduction to Computer Systems Security
 Introduction to Computer Networks CS 166: Introduction to Computer Systems Security Network Communication Communication in modern networks is characterized by the following fundamental principles Packet
Introduction to Computer Networks CS 166: Introduction to Computer Systems Security Network Communication Communication in modern networks is characterized by the following fundamental principles Packet
Cisco Nexus Data Broker for Network Traffic Monitoring and Visibility
 Guide Cisco Nexus Data Broker for Network Traffic Monitoring and Visibility Solution Implementation Guide 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information.
Guide Cisco Nexus Data Broker for Network Traffic Monitoring and Visibility Solution Implementation Guide 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information.
Vendor: Cisco. Exam Code: Exam Name: Developing with Cisco Network Programmability (NPDEV) Version: Demo
 Vendor: Cisco Exam Code: 600-502 Exam Name: Developing with Cisco Network Programmability (NPDEV) Version: Demo Question Set 1 QUESTION 1 A stock brokerage firm requires that all trades are executed quickly
Vendor: Cisco Exam Code: 600-502 Exam Name: Developing with Cisco Network Programmability (NPDEV) Version: Demo Question Set 1 QUESTION 1 A stock brokerage firm requires that all trades are executed quickly
First Exam for ECE671 Spring /22/18
 ECE67: First Exam First Exam for ECE67 Spring 208 02/22/8 Instructions: Put your name and student number on each sheet of paper! The exam is closed book. You have 75 minutes to complete the exam. Be a
ECE67: First Exam First Exam for ECE67 Spring 208 02/22/8 Instructions: Put your name and student number on each sheet of paper! The exam is closed book. You have 75 minutes to complete the exam. Be a
K2289: Using advanced tcpdump filters
 K2289: Using advanced tcpdump filters Non-Diagnostic Original Publication Date: May 17, 2007 Update Date: Sep 21, 2017 Topic Introduction Filtering for packets using specific TCP flags headers Filtering
K2289: Using advanced tcpdump filters Non-Diagnostic Original Publication Date: May 17, 2007 Update Date: Sep 21, 2017 Topic Introduction Filtering for packets using specific TCP flags headers Filtering
COMPUTER NETWORKS. CPSC 441, Winter 2016 Prof. Mea Wang Department of Computer Science University of Calgary
 COMPUTER NETWORKS CPSC 441, Winter 2016 Prof. Mea Wang Department of Computer Science University of Calgary Introduction: Wireshark and tshark Running tshark Running Wireshark Exercise: Analyze HTTP traffic
COMPUTER NETWORKS CPSC 441, Winter 2016 Prof. Mea Wang Department of Computer Science University of Calgary Introduction: Wireshark and tshark Running tshark Running Wireshark Exercise: Analyze HTTP traffic
Identity Firewall. About the Identity Firewall
 This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
Operation Manual DHCP H3C S3600 Series Ethernet Switches-Release Table of Contents
 Table of Contents Table of Contents Chapter 1 DHCP Overview... 1-1 1.1 Introduction to DHCP... 1-1 1.2 DHCP IP Address Assignment... 1-1 1.2.1 IP Address Assignment Policy... 1-1 1.2.2 Obtaining IP Addresses
Table of Contents Table of Contents Chapter 1 DHCP Overview... 1-1 1.1 Introduction to DHCP... 1-1 1.2 DHCP IP Address Assignment... 1-1 1.2.1 IP Address Assignment Policy... 1-1 1.2.2 Obtaining IP Addresses
Instituto Superior Técnico, Universidade de Lisboa Network and Computer Security. Lab guide: Traffic analysis and TCP/IP Vulnerabilities
 Instituto Superior Técnico, Universidade de Lisboa Network and Computer Security Lab guide: Traffic analysis and TCP/IP Vulnerabilities Revised on 2016-10-18 Alpha version: This is an early version and
Instituto Superior Técnico, Universidade de Lisboa Network and Computer Security Lab guide: Traffic analysis and TCP/IP Vulnerabilities Revised on 2016-10-18 Alpha version: This is an early version and
History Page. Barracuda NextGen Firewall F
 The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
VIRTUAL GPU LICENSE SERVER VERSION AND 5.1.0
 VIRTUAL GPU LICENSE SERVER VERSION 2018.06 AND 5.1.0 DU-07754-001 _v6.0 through 6.2 July 2018 User Guide TABLE OF CONTENTS Chapter 1. Introduction to the NVIDIA vgpu Software License Server... 1 1.1. Overview
VIRTUAL GPU LICENSE SERVER VERSION 2018.06 AND 5.1.0 DU-07754-001 _v6.0 through 6.2 July 2018 User Guide TABLE OF CONTENTS Chapter 1. Introduction to the NVIDIA vgpu Software License Server... 1 1.1. Overview
Host Identity Sources
 The following topics provide information on host identity sources: Overview: Host Data Collection, on page 1 Determining Which Host Operating Systems the System Can Detect, on page 2 Identifying Host Operating
The following topics provide information on host identity sources: Overview: Host Data Collection, on page 1 Determining Which Host Operating Systems the System Can Detect, on page 2 Identifying Host Operating
Installing Cisco VTS on a VMware Environment, page 6 Installing the Virtual Topology Forwarder, page 9 Verifying VTS Installation, page 14
 The following sections provide details about installing VTS on a Linux-OpenStack environment or a VMware-based environment. Ensure that you review the Prerequisites chapter, before you begin installing
The following sections provide details about installing VTS on a Linux-OpenStack environment or a VMware-based environment. Ensure that you review the Prerequisites chapter, before you begin installing
CS155: Computer Security Spring Project #1
 CS155: Computer Security Spring 2018 Project #1 Due: Part 1: Thursday, April 12-11:59pm, Parts 2 and 3: Thursday, April 19-11:59pm. The goal of this assignment is to gain hands-on experience finding vulnerabilities
CS155: Computer Security Spring 2018 Project #1 Due: Part 1: Thursday, April 12-11:59pm, Parts 2 and 3: Thursday, April 19-11:59pm. The goal of this assignment is to gain hands-on experience finding vulnerabilities
INF3190 Mandatory Assignment:
 INF3190 Mandatory Assignment: Formally: This assignment must be completed individually. The submission must be approved prior to submission of the Home Exam 1. To pass the submission must meet the requirements
INF3190 Mandatory Assignment: Formally: This assignment must be completed individually. The submission must be approved prior to submission of the Home Exam 1. To pass the submission must meet the requirements
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Typhoon: An SDN Enhanced Real-Time Big Data Streaming Framework
 Typhoon: An SDN Enhanced Real-Time Big Data Streaming Framework Junguk Cho, Hyunseok Chang, Sarit Mukherjee, T.V. Lakshman, and Jacobus Van der Merwe 1 Big Data Era Big data analysis is increasingly common
Typhoon: An SDN Enhanced Real-Time Big Data Streaming Framework Junguk Cho, Hyunseok Chang, Sarit Mukherjee, T.V. Lakshman, and Jacobus Van der Merwe 1 Big Data Era Big data analysis is increasingly common
Configuration Manager
 CHAPTER 7 This chapter describes how to perform routine Cisco VXC Manager configuration management tasks using the Administrator Console. It provides information on managing the configuration settings
CHAPTER 7 This chapter describes how to perform routine Cisco VXC Manager configuration management tasks using the Administrator Console. It provides information on managing the configuration settings
Configuring IP SLAs TCP Connect Operations
 This module describes how to configure an IP Service Level Agreements (SLAs) TCP Connect operation to measure the response time taken to perform a TCP Connect operation between a Cisco router and devices
This module describes how to configure an IP Service Level Agreements (SLAs) TCP Connect operation to measure the response time taken to perform a TCP Connect operation between a Cisco router and devices
SDN Controller Test. Network Emulator. Version 1.4. User Guide. Part Number: T / UG PKTBLASTER-SDN-CTR-EMU /1.1
 SDN Controller Test Network Emulator Version 1.4 User Guide Part Number: T / UG PKTBLASTER-SDN-CTR-EMU-1.4 1115/1.1 Copyright Veryx Technologies Pvt. Ltd. All rights reserved. Veryx and PktBlaster are
SDN Controller Test Network Emulator Version 1.4 User Guide Part Number: T / UG PKTBLASTER-SDN-CTR-EMU-1.4 1115/1.1 Copyright Veryx Technologies Pvt. Ltd. All rights reserved. Veryx and PktBlaster are
Configuring Commonly Used IP ACLs
 Configuring Commonly Used IP ACLs Document ID: 26448 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration Examples Allow a Select Host to Access the Network Deny a
Configuring Commonly Used IP ACLs Document ID: 26448 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration Examples Allow a Select Host to Access the Network Deny a
Chapter 4: network layer. Network service model. Two key network-layer functions. Network layer. Input port functions. Router architecture overview
 Chapter 4: chapter goals: understand principles behind services service models forwarding versus routing how a router works generalized forwarding instantiation, implementation in the Internet 4- Network
Chapter 4: chapter goals: understand principles behind services service models forwarding versus routing how a router works generalized forwarding instantiation, implementation in the Internet 4- Network
Configuring attack detection and prevention 1
 Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Contents Configuring attack detection and prevention 1 Overview 1 Attacks that the device can prevent 1 Single-packet attacks 1 Scanning attacks 2 Flood attacks 3 TCP fragment attack 4 Login DoS attack
Chapter 11. High Availability
 Chapter 11. High Availability This chapter describes the high availability fault-tolerance feature in D-Link Firewalls. Overview, page 289 High Availability Mechanisms, page 291 High Availability Setup,
Chapter 11. High Availability This chapter describes the high availability fault-tolerance feature in D-Link Firewalls. Overview, page 289 High Availability Mechanisms, page 291 High Availability Setup,
LAN Setup Reflection
 LAN Setup Reflection After the LAN setup, ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other
LAN Setup Reflection After the LAN setup, ask yourself some questions: o Does your VM have the correct IP? o Are you able to ping some locations, internal and external? o Are you able to log into other
HP Load Balancing Module
 HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-4218 Software version: Feature 3221 Document version: 6PW100-20130326 Legal and notice information Copyright 2013 Hewlett-Packard
HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-4218 Software version: Feature 3221 Document version: 6PW100-20130326 Legal and notice information Copyright 2013 Hewlett-Packard
Packet Tracer - Investigating the TCP/IP and OSI Models in Action (Instructor Version Optional Packet Tracer)
 (Instructor Version Optional Packet Tracer) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding
(Instructor Version Optional Packet Tracer) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding
Configuring IP SLAs LSP Health Monitor Operations
 Configuring IP SLAs LSP Health Monitor Operations This module describes how to configure an IP Service Level Agreements (SLAs) label switched path (LSP) Health Monitor. LSP health monitors enable you to
Configuring IP SLAs LSP Health Monitor Operations This module describes how to configure an IP Service Level Agreements (SLAs) label switched path (LSP) Health Monitor. LSP health monitors enable you to
Running Kmeans Spark on EC2 Documentation
 Running Kmeans Spark on EC2 Documentation Pseudo code Input: Dataset D, Number of clusters k Output: Data points with cluster memberships Step1: Read D from HDFS as RDD Step 2: Initialize first k data
Running Kmeans Spark on EC2 Documentation Pseudo code Input: Dataset D, Number of clusters k Output: Data points with cluster memberships Step1: Read D from HDFS as RDD Step 2: Initialize first k data
OpenFlow Firewall and NAT Devices
 OpenFlow Firewall and NAT Devices OpenFlow Firewall and NAT Devices Step by step Instructions Overview: This is a very simple tutorial with two topologies demonstrating an OpenFlow Firewall and an OpenFlow
OpenFlow Firewall and NAT Devices OpenFlow Firewall and NAT Devices Step by step Instructions Overview: This is a very simple tutorial with two topologies demonstrating an OpenFlow Firewall and an OpenFlow
The instructions in this document are applicable to personal computers running the following Operating Systems:
 Preliminary Notes The instructions in this document are applicable to personal computers running the following Operating Systems: Microsoft Windows from version 7 up to 10 Apple Mac OS X from versions
Preliminary Notes The instructions in this document are applicable to personal computers running the following Operating Systems: Microsoft Windows from version 7 up to 10 Apple Mac OS X from versions
Assignment 1: Getting to know Click and D-ITG
 ECEN 5023/CSCI 7000-0005: Advanced Networking Spring 2013 Assignment 1: Getting to know Click and D-ITG Due 2/10/2013 11:59pm (i.e., Sunday night) In this assignment, you will be using Click and D-ITG.
ECEN 5023/CSCI 7000-0005: Advanced Networking Spring 2013 Assignment 1: Getting to know Click and D-ITG Due 2/10/2013 11:59pm (i.e., Sunday night) In this assignment, you will be using Click and D-ITG.
H3C S5130-EI Switch Series
 H3C S5130-EI Switch Series OpenFlow Command Reference New H3C Technologies Co., Ltd. http://www.h3c.com Software version: Release 311x Document version: 6W102-20180323 Copyright 2016-2018, New H3C Technologies
H3C S5130-EI Switch Series OpenFlow Command Reference New H3C Technologies Co., Ltd. http://www.h3c.com Software version: Release 311x Document version: 6W102-20180323 Copyright 2016-2018, New H3C Technologies
Palo Alto Networks Cybersecurity Gateway
 Palo Alto Networks Cybersecurity Gateway Installation and Configuration Guide Document Version: 2018-08-07 Installation of Palo Alto Networks Cybersecurity Gateway virtual pods as described in this guide
Palo Alto Networks Cybersecurity Gateway Installation and Configuration Guide Document Version: 2018-08-07 Installation of Palo Alto Networks Cybersecurity Gateway virtual pods as described in this guide
IP NAT Troubleshooting. Solutions. Luke Bibby, CCIE #45527
 IP NAT Troubleshooting Solutions Luke Bibby, CCIE #45527 Quick Overview of Scenario Solutions Scenario #1 R2 s E0/0 should be NAT inside not NAT outside ACL 100 is configured incorrectly NAT policy missing
IP NAT Troubleshooting Solutions Luke Bibby, CCIE #45527 Quick Overview of Scenario Solutions Scenario #1 R2 s E0/0 should be NAT inside not NAT outside ACL 100 is configured incorrectly NAT policy missing
Configuration Guide TL-ER5120/TL-ER6020/TL-ER REV3.0.0
 Configuration Guide TL-ER5120/TL-ER6020/TL-ER6120 1910012186 REV3.0.0 June 2017 CONTENTS About This Guide Intended Readers... 1 Conventions... 1 More Information... 1 Viewing Status Information... 2 System
Configuration Guide TL-ER5120/TL-ER6020/TL-ER6120 1910012186 REV3.0.0 June 2017 CONTENTS About This Guide Intended Readers... 1 Conventions... 1 More Information... 1 Viewing Status Information... 2 System
Actual4Test. Actual4test - actual test exam dumps-pass for IT exams
 Actual4Test http://www.actual4test.com Actual4test - actual test exam dumps-pass for IT exams Exam : 200-125 Title : CCNA Cisco Certified Network Associate CCNA (v3.0) Vendor : Cisco Version : DEMO Get
Actual4Test http://www.actual4test.com Actual4test - actual test exam dumps-pass for IT exams Exam : 200-125 Title : CCNA Cisco Certified Network Associate CCNA (v3.0) Vendor : Cisco Version : DEMO Get
Observing Bufferbloat using mininet
 Observing Bufferbloat using mininet In this assignment the objective is to study the dynamics of TCP in a typical home networking setting to observe the bufferbloat problem. Take a look at the figure below,
Observing Bufferbloat using mininet In this assignment the objective is to study the dynamics of TCP in a typical home networking setting to observe the bufferbloat problem. Take a look at the figure below,
COMPUTER NETWORKING LAB EXERCISES (TP) 4
 Name 1: Name 2: Group number: COMPUTER NETWORKING LAB EXERCISES (TP) 4 IPV6 December 14, 2009 Abstract In this TP you will revisit some of the basic networking tools that were introduced in TP1, only this
Name 1: Name 2: Group number: COMPUTER NETWORKING LAB EXERCISES (TP) 4 IPV6 December 14, 2009 Abstract In this TP you will revisit some of the basic networking tools that were introduced in TP1, only this
Configuring the Oracle Network Environment. Copyright 2009, Oracle. All rights reserved.
 Configuring the Oracle Network Environment Objectives After completing this lesson, you should be able to: Use Enterprise Manager to: Create additional listeners Create Oracle Net Service aliases Configure
Configuring the Oracle Network Environment Objectives After completing this lesson, you should be able to: Use Enterprise Manager to: Create additional listeners Create Oracle Net Service aliases Configure
Chapter 09 Network Protocols
 Chapter 09 Network Protocols Copyright 2011, Dr. Dharma P. Agrawal and Dr. Qing-An Zeng. All rights reserved. 1 Outline Protocol: Set of defined rules to allow communication between entities Open Systems
Chapter 09 Network Protocols Copyright 2011, Dr. Dharma P. Agrawal and Dr. Qing-An Zeng. All rights reserved. 1 Outline Protocol: Set of defined rules to allow communication between entities Open Systems
Configuring CWMP Service
 CHAPTER 12 This chapter describes how to configure the CWMP service in Cisco Broadband Access Center (BAC). Topics covered are:, page 12-1 Configuring Service Ports on the DPE, page 12-2 Disabling Connection
CHAPTER 12 This chapter describes how to configure the CWMP service in Cisco Broadband Access Center (BAC). Topics covered are:, page 12-1 Configuring Service Ports on the DPE, page 12-2 Disabling Connection
Lab 1: Introduction to Linux Networking
 CMPE 150: Introduction to Computer Networks Fall 2011 http://courses.soe.ucsc.edu/courses/cmpe150/fall11/01/ Lab 1: Introduction to Linux Networking Materials: Please bring a USB drive to each lab section.
CMPE 150: Introduction to Computer Networks Fall 2011 http://courses.soe.ucsc.edu/courses/cmpe150/fall11/01/ Lab 1: Introduction to Linux Networking Materials: Please bring a USB drive to each lab section.
Packet Tracer - Explore a Network
 Topology Objectives Part 1: Examine Internetwork Traffic at Branch Part 2: Examine Internetwork Traffic to Central Part 3: Examine Internet Traffic from Branch Background This simulation activity is intended
Topology Objectives Part 1: Examine Internetwork Traffic at Branch Part 2: Examine Internetwork Traffic to Central Part 3: Examine Internet Traffic from Branch Background This simulation activity is intended
