The Mis-entropists: New Approaches to Measures in Tor
|
|
|
- Agatha Atkins
- 5 years ago
- Views:
Transcription
1 The Mis-entropists: New Approaches to Measures in Tor Angèle M. Hamel Dept. of Physics and Computer Science, Wilfrid Laurier University Waterloo, ON Canada Jean-Charles Grégoire INRS Montréal, QC Canada Ian Goldberg Cheriton School of Computer Science, University of Waterloo Waterloo, ON Canada ABSTRACT Measuring path compromise in the anonymity system Tor is a problem of important and immediate interest. We discuss the drawbacks to the traditional anonymity network measure entropy and explore the advantages of an attackbased measure. Our perspective is that of an adversary with a bandwidth budget (a fixed amount of bandwidth he or she can compromise), and we derive theoretical and numerical results that illustrate path compromise under these conditions. 1. INTRODUCTION We need a better understanding of how much anonymity the Tor network provides against a partial network adversary who observes and/or operates some of the network.... The simplistic metric also gets misused in academic research papers to produce misleading results like I can sign up 2% of the Tor relays and capture 50% of the paths, when what they mean is I can provide half the capacity in the Tor network and capture half the paths.... The goal here isn t to come up with the one true metric for summarizing Tor s safety. Rather, we need to recognize that there are many threat models to consider at once, so we need many different views into what types of safety the network can offer. [6] This Tor Blog entry highlights both the need for effective measures of the risks of using Tor in certain circumstances, and the difficulty of providing such measures. It also calls for different views on safety. Here we provide one such different view based on the capability of the adversary and the resulting probability of path compromise. Messages sent through Tor are typically routed through a path consisting of three nodes: entry, middle, and exit. Of particular interest to the user is, how vulnerable is my path to compromise? That is, how likely is it that a nonglobal passive adversary can tell which services I am accessing? Path compromise is generally acknowledged to be a problem chiefly when the adversary controls the entry and exit nodes. Thus the question, how likely is it that my path is compromised? can be interpreted as, how likely is it that the adversary controls the entry and exit nodes on my path? This approach has already been advocated by various authors [11, 12]. Here we use the concept of adversarial bandwidth fraction or ABWF. In this model, the adversary has a bandwidth budget; that is, the adversary can afford to compromise a fixed percentage of bandwidth, say n%. Of importance, too, is the choice of nodes made by the adversary within that budget. This bandwidth budget idea is related to the approach in Murdoch and Watson [11] in which they consider path construction where an adversary can control not just a given number of nodes, but also nodes of a given total bandwidth capacity. Assuming the adversary optimizes their bandwidth budget, i.e. he or she chooses the set of nodes that allows them the highest probability of compromising paths, what is the level of danger inherent in the system? There is already a standard measure for anonymity: entropy. Why then pose this question at all? As we will discuss below, entropy has a number of shortcomings. In particular, it is based on holistic properties of the system, rather than the actions of the attacker. We have coined the term misentropist, as a play on misanthropist, to be one who distrusts entropy. It is time for a fresh look, to strip down to the bare wood, to question assumptions, and to see what properties we can obtain. As the Tor Blog reminds us, the perfect measure still eludes us. Our contributions: We discuss entropy, summarizing a number of issues that have been advanced by other authors, and we propose that an attack-based measure would be superior. To this end, we calculate the probability of path compromise given various bandwidth budgets available to the adversary, and propose ways to use this information. The paper is structured as follows: Section 2 looks at the classical measure of entropy and discusses some of its drawbacks. Section 3 explores the path selection algorithm for Tor and the primary ingredients to it: nodes and bandwidth. Section 4 discusses several different ways of calculating path probability depending on how bandwidth is taken into account and to what extent. It also explores the probability of picking a compromised pair of nodes, given an adversarial bandwidth fraction. Section 5 delivers our results. Sections 6 and 7 round out the paper and address related work and conclusions. 2. ENTROPY The classical measure for anonymity is (Shannon) entropy. It is defined as K i=1 Pi log 2 P i, where there are K sep- 1
2 arate events and P i is the probability of the ith event occurring. Entropy was proposed as a measure for anonymity networks by Serjantov and Danezis [14] and Diaz et al. [5], both at PET Although it was introduced to measure the anonymity in a mix network, it has been co-opted for use in measuring uncertainty in other aspects of anonymity networks in particular, the randomness in path selection in Tor [1, 12]. Entropy has a lot of good statistical properties and is commonly used in a number of disciplines. Furthermore, it is relatively easy to compute. While this measure has been widely used, there are some drawbacks to it. Exact measures of probability can be challenging. Further, estimates of probability are just that: estimates, and the entropy formula is only as good as the probabilities it uses. As pointed out by Toth et al. [20], the entropy measure is a measure of the entire system (global anonymity) rather than a measure of the anonymity for a particular user (local anonymity). Shmatikov and Wang [16] advocate minentropy instead of Shannon entropy, pointing out [Shannon] Entropy does not always capture the right anonymity property. Consider a distribution of 100 potential destinations, in which all but one are equally likely with probability 0.009, and a single destination has probability [Shannon] Entropy of this distribution is 6.40, close to the theoretical maximum of Clauß and Schiffner [4] also make the same point that the influence of outliers is strong, i.e. if one element is very likely the entropy can be very high, even though the elements are not evenly distributed. Syverson [18] takes issue with the entire concept of indistinguishability as the basis for a measure. He introduces the idea of trust in anonymity network and advocates for security measures that reflect the difficulty an adversary has in overcoming them, and measures that do not depend on the value of variables that are difficult to predict or determine. Furthermore, entropy is good for comparative measures Mine is bigger than yours! but it is less valuable in absolute terms. What to make of entropy values? Consider three cases, each involving about alternatives, but spread in three different ways: uniform, where all cases are equally likely; chosen few, where a handful are 100 times more likely than others, and exponential, where frequency of occurrence is in inverse proportion with the likelihood. We can calculate the entropy in each of these sitations as: uniform: chosen few: exponential: Those numbers are quite distinct, yet essentially meaningless. The more heterogeneous the model, the lower the number, yet the impact of a compromised node depends strongly on the probability of its being chosen in a path, which entropy in its multiple variants does not reflect. The authors mentioned above have taken issue with entropy as a measure of anonymity. But it also fails to measure the effect of an attack. It makes the assumption that more diversity/inequality/disorder/randomness in paths leads to better safety. But, as Murdoch and Watson [11] suggest, any measure based on uniformity of path selection misses key information: The link between these metrics and practical security depends on the assumption that cost of injecting nodes is independent of the path selection algorithm and node parameters. In the case of Tor, where path selection probability depends strongly on bandwidth, this is analogous to assuming that an attacker has unlimited bandwidth, but is constrained by IP addresses. Thus we take the view that the attacker and his or her capabilities are key particularly with reference to bandwidth and derive results that indicate the direct effects of attack. To summarize, entropy measures diversity and answers questions such as how disordered is the system? However, when the focus is on the attacker, and on compromised paths, the question to be answered is more properly what is the danger a path is compromised? and entropy does not speak to such questions. 3. PATH SELECTION 3.1 Nodes The nodes in a Tor path, and their capabilities and limitations, are of fundamental interest. Exit nodes are special in that they connect directly to a server (e.g. web server) and thus may have exit policies restricting the types of traffic exiting from them. If traffic requires a certain port, the user will have to pick an exit node which supports the service they require. The entry node position is occupied by a type of node called a guard node. Guard nodes were first proposed by Wright et al. [22] (where they are called helper nodes ). As stated above, the problem occurs when an adversary controls both the entry and exit nodes. Since in Tor the path is changed every 10 minutes, a user connected for n minutes is exposed to n/10 different paths and thus n/10 possibilities for compromise. In general the issue is not so much the amount of traffic observed by the adversary, but the fact the adversary has observed any traffic at all. It is generally considered better to pick a few the usual recommendation is three possibilities for entry nodes and stick with those. These possibilities are called guard nodes. Our analysis considers the situation before a user selects guard nodes. If all the guard nodes turn out to be honest, then there is no possibility of path compromise. The user does not know this a priori, of course. According to the Tor specification [19], we thus have four kinds of nodes to select from in forming paths: guard nodes, exit nodes, guard+exit nodes (suitable for either the guard or the exit position), and non-flagged (i.e. middle) nodes. In our analysis we will treat these nodes differently. 2
3 Note, however, that all four kinds of nodes can occupy the middle position. Allowing such an occurrence can seem a bit wasteful of scarce resources, but does permit more randomness in path construction. However, Tor does impose a penalty in the form of weights. Depending on the position and scarcity of types of nodes they will be weighted by an additional factor during path selection. This weighting algorithm will be explained in more detail below. In addition to being designated as guard, exit, or guard+exit nodes, nodes can also be fast or stable or both; see Figure 1. The Tor Directory Protocol [19] defines a node as fast if it is active, and its bandwidth is either in the top 7/8ths for known active routers or at least 20 KB/s. It defines a node as stable if it is active, and either its Weighted MTBF [Mean Time Between Failure] is at least the median for known active routers or its Weighted MTBF corresponds to at least 7 days. To calculate weighted MTBF, compute the weighted mean of the lengths of all intervals when the router was observed to be up, weighting intervals by α n, where n is the amount of time that has passed since the interval ended, and α is chosen so that measurements over approximately one month old no longer influence the weighted MTBF much. A fast path contains only fast nodes; a stable path contains only stable nodes. 3.2 Bandwidth The bandwidth available is the lifeblood of the Tor network. More bandwidth means better efficiency and a greater number of users, and may contribute to a reduction in latency. However, there is a complex, and not completely understood, relationship between bandwidth and anonymity. Does more bandwidth in the system mean greater anonymity? Can bandwidth in the wrong places actually reduce anonymity (e.g. by routing too much traffic through a handful of nodes)? What influence does the bandwidth at individual nodes have on anonymity? Bandwidth is one factor in the path selection algorithm in Tor. Initially, this was self-reported bandwidth; however, recognizing that malicious nodes can lie, this was changed to a consensus bandwidth [13]. The bandwidth used in the path selection calculation is capped at 10 MB/s to prevent too much influence from nodes that may be lying. See Figure 2 for an indication of how bandwidth has grown in Tor. 3.3 Path Selection Algorithm The path selection algorithm first selects an exit node, then the guard node (from a list of guard nodes that the user has already selected), then the middle node. There is an additional list of constraints, such as no two nodes can belong to the same family, available in the Tor Path Specification [7]. Murdoch and Watson [11] identify three different random selection algorithms for node selection in Tor, which include catering to weights, as described above: Simple random selection (SRS), in which the node is selected from a set of candidate nodes with uniform probability. Bandwidth-weighted random selection (BWRS), in which the node is selected from a set of candidate nodes with probability proportional to their individual capped bandwidths. Adjusted bandwidth-weighted random selection (AB- WRS), where weights specified in the Tor Directory Specification [19] are applied to the bandwidths, and nodes are selected with probability proportional to those weighted bandwidths. These weights are discussed below. The additional weighting factors are multiplied by the bandwidths of the exit nodes and guard nodes. The purpose of the weighting factor is to discourage the use of scarce resources in times of shortage, i.e. if the system is short of exit nodes, it makes it more likely an exit node will be used as an exit than as a middle node. The weights are of the form W xy where x is the position (guard (g), middle (m), exit (e)) of the node, and y is the type of node (guard nodes are denoted by g, exit nodes by e, and guard+exit nodes by d). Let G be the total bandwidth for Guard-flagged nodes, M be the total bandwidth for non-flagged nodes, E be the total bandwidth for Exit-flagged nodes, and D be the total bandwidth for Guard+Exit-flagged nodes. Full details are in the Tor Directory Protocol [19]. The weights are understood to satisfy balancing constraints (e.g. bandwidth of the guard nodes must equal the bandwidth of the middle nodes and the bandwidth of the exit nodes). For example, if the guard and exit nodes are not scarce, we have W gd = 1/3 W ed = 1/3 W md = 1/3 W ee = (E + G + M)/(3 E) W me = 1 W ee W mg = (2 G E M)/(3 G) W gg = 1 W mg 4. PROBABILITY OF PATH COMPROMISE Next, given a set of compromised nodes, we calculate the probability of path compromise (i.e. the probability that both the guard and exit node are compromised) under each of the three path selection algorithms described above. Calculating the probability of picking a compromised pair in a uniform situation, as in SRS, where each node is equally likely to be chosen, is straightforward. Suppose that c pairs of nodes are compromised. Then we can ask the question, what is the probability that a particular pair is one of these c? If the pairs are chosen with uniform probability for the paths then each one has an equal chance. For example, given two possible entry nodes A 1 and A 2 and three possible exit nodes B 1, B 2, and B 3, then there are six possible pairs. If we know two pairs are compromised, then there is a 1/3 chance of having a compromised pair. However, if the pairs are not chosen with uniform probability, i.e. if they are chosen with a bandwidth dependent 3
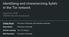
4 Figure 1: Graph showing growth in number of nodes in Tor from January 1, 2009 to May 31, As can be seen in the graph, almost all nodes are fast; a solid, but significantly smaller proportion, are stable. Figure 2: Graph showing the growth of total bandwidth available in Tor from January 1, 2009 to May 31,
5 probability as they are in the BWRS and ABWRS cases, then given that c pairs are compromised, it is challenging to calculate the probability of picking a compromised pair. For example, now suppose A 1 has 9/10 of the bandwidth and A 2 has 1/10. Further suppose that B 1 has 1/2 the bandwidth and B 2 and B 3 each have 1/4. Then the pairs have probabilities 18/40, 2/40, 9/40, 9/40, 1/40, 1/40, and the chance that you pick a compromised pair is no longer 1/3. For example, the pair A 2B 3 is rarely picked, so even if it is compromised, it hardly matters; the issue becomes to calculate this probability. In the following subsections we derive equations for each of these situations. 4.1 SRS If we ignore bandwidth then the probability of a specific pair of entry and exit nodes appearing can be calculated using the number of nodes of each type. The user re-uses guard nodes, but this calculation is performed before the user selects them. Define the following: g =number of guard nodes e =number of exit nodes m =number of non-flagged nodes (i.e. only good for middle) d = number of guard+exit nodes Corollary The probability that a path will start from a given node from the set of guard nodes is (e + d) (ge + gd + de + d(d 1)). (2) 2. The probability that a path will start from a given node from the set of guard+exit nodes is (e+d 1) (ge+gd+de+d(d 1)). 3. The probability that a path will end with a given node from the set of exit nodes is (g+d) (ge+gd+de+d(d 1)). 4. The probability that a path will end with a given node from the set of guard+exit nodes is Table 1: set. (g+d 1) (ge+gd+de+d(d 1)). General Statistics for Consensus Sample Total number of routers 2328 Total number of Authority routers 10 Total number of Bad directory routers 0 Total number of Bad exit routers 7 Total number of Exit routers 997 Total number of Fast routers 2273 Total number of Guard routers 810 Total number of Named routers 1686 Total number of Stable routers 1410 Total number of Running routers 2328 Total number of Valid routers 2328 Total number of V2Dir routers 1126 Total number of Hidden Service routers 851 Thus the formula for number of paths can easily be calculated as: Theorem 4.1. Let g be the number of guard nodes, e be the number of exit nodes, m be the number of non-flagged nodes, and d be the number of guard+exit nodes. Then the number of possible paths is (ge + gd + de + d(d 1)) (g + d + e + m 2) (1) Proof: There are two choices for the entry node: either it is from the set of guard nodes or from the set of guard+exit nodes. If it is from the set of guard nodes there are g choices. Then we have free choice on the final node to be from the set of exit nodes or from the set of guard+exit nodes. So there are g(e+d) choices for the two nodes. Now the middle could be any node except the two already picked, and there are g + d + e + m 2 choices for the middle node. If instead the entry node is from the guard+exit nodes there are d choices. Then the final node could be from the exit nodes or from the guard+exit nodes (except the one already chosen). So the number of choices for the two nodes is d(e + d 1). Again, the middle nodes can be chosen from g + d + e + m 2 choices. Putting it all together we have (ge + gd + de + d(d 1)) (g + d + e + m 2) paths. The following corollary is immediate: Example. We downloaded a consensus of Tor on April 22, 2011 (see summary in Table 1, while the full distribution of bandwidths is shown in Figure 3). From this consensus we determined there were 2328 valid nodes altogether, of which e = 721 were pure exit nodes, g = 541 were pure guard nodes, d = 269 were guard+exit nodes, and m = 797 were non-flagged nodes. Then we could calculate the probabilities in the corollary as: The probability that a path will start from a given (990) node from the set of guard nodes is = (801631) The probability that a path will start from a given 989 node from the set of guard+exit nodes is = The probability that a path will end with a given node 810 from the set of exit nodes is = The probability that a path will end with a given node 809 from the set of guard+exit nodes is = We can also examine this from a path compromise perspective. Recall that a path is compromised if the guard and exit nodes are compromised. Thus we can use the principle of inclusion exclusion to conclude that the number of possible pairs of entry exit nodes is (g + d)(e + d) d (3) 5
6 (Capped) Contribution to bandwidth Contribution to bandwidth, capped, from high to low (KBps) Cumulative fraction of total bandwidth Cumulative bandwidth (fraction) Number of nodes Figure 3: Capped Bandwidth distribution from April 22, 2011 Tor consensus data. Reasoning: There are g + d choices for the entry node and e + d choices for the exit node. The total choices are (g + d)(e + d) = ge + gd + ed + d 2 ; however, some of the node pairs counted by d 2 are those that use the same guard+exit node for entry and exit, which is not allowed in Tor, thus we need to subtract those duplicate instances, of which there are d. If we know that some of these are compromised say, g C guard nodes, e C exit nodes, and d C guard+exit nodes then the probability of picking a pair of compromised nodes is (g C + d C)(e C + d C) d C (4) (g + d)(e + d) d by reasoning similar to the above. 4.2 BWRS Recall there are four types of nodes: guard, exit, guard+exit, and non-flagged (only good for the middle position). Let B i be the bandwidth of node x i. Let Sg be the set of guard nodes, Se the set of exit nodes, Sd the set of guard+exit nodes, and Sm the set of non-flagged nodes. In all cases the contribution of the middle node is essentially irrelevant. From a calculation point of view, once the guard and exit nodes are chosen, the middle node is chosen from what remains, so we must subtract the bandwidth used up by the other nodes. The probability of a given middle node m being in a path is B m ( i Se Bi + i Sg Bi + i Sd Bi + i Sm Bi) Bg Be. (5) For conciseness, we let B = ( i Se Bi+ i Sg Bi+ i Sd Bi+ Bi) Bg Be and write Bm/B. However, if we want i Sm the probability of compromise, we sum the probability for all given nodes, which is ( i Se Bi + i Sg Bi + i Sd Bi + i Sm Bi) Bg Be ( i Se Bi + i Sg Bi + i Sd Bi + i Sm Bi) Bg Be (6) which is B/B = 1. Of course, the fact that the contribution of the middle nodes is just 1 can be seen intuitively as the probability of path compromise is simply the probability of guard node compromise multiplied by the probability of exit node compromise; whether the middle node is compromised is actually not relevant. Now we consider the choice of guard and exit nodes. The probability of x g being chosen as the first node is B g i Sg Bi + i Sd Bi (7) because the guard node could come from either Sg or Sd. This follows from a direct counting argument, and Bauer et al. [2] has the same declaration the available bandwidth for that node is the numerator and the total available bandwidth of all nodes is the denominator, so this indicates what fraction of the total bandwidth the node controls. The probability of x e being chosen as the exit node is B e i Se Bi + i Sd Bi (8) again because it could come from either Se or Sd. It is tempting to say that the probability that a path contains x g as the entry node, x m as the middle node, and x e as the exit node is: 6
7 ( B g i Sg Bi + i Sd Bi ) ( B e i Se Bi + i Sd Bi ) ( ) Bm. B However, this is not quite right for example, if g is from Sd then e could be chosen from (Se Sd)\g and not from Se Sd. To take care of this we could partition the consideration into cases; however, since we need the sum over all possibilities, this can be accomplished using a counting argument. More formally, suppose the set of compromised nodes C = G C E C D C is partitioned into a set of G C guard nodes, a set E C of exit nodes, and a set D C of guard+exit nodes. An elementary counting argument can be used to establish: Theorem 4.3. The probability that a path constructed according to BWRS will start with a compromised node and end with a compromised node is ( i GC Bi + i DC Bi ) ( i EC Bi + i DC Bi ) S ( i DC B2 i ) where S = ( i Sg Bi + i Sd Bi ) ( i Se Bi + i Sd Bi ) ( i Sd B2 i ). Proof: Given a set of compromised nodes, the probability of a compromised node being chosen for a path is the sum of the probabilities of each given node being chosen, i.e. for the guard and guard+exit nodes being chosen for entry position, the probability is ( i G C B i + ) i D C B i i Sg Bi +, i Sd Bi and for exit and guard+exit nodes it is ( i E C B i + ) i D C B i i Se Bi +. i Sd Bi For the middle nodes, from the analysis before equations (5) and (6), we know the contribution from the middle nodes is just 1. We cannot simply multiply these probabilities together, however, if we need to consider the probabilities of pairs of nodes. This is because such a product would imply the counting is with replacement, meaning it allows the same node to be used as guard node and as exit node, which is not allowed in Tor. Thus, using the same sort of analysis as in (4), we derive the ratio in the statement of the theorem. 4.3 ABWRS An analysis parallel to that of the previous section provides the following weighted theorem: S (9) Theorem 4.4. The probability that a path constructed according to ABWRS will start with a compromised node and end with a compromised node is where G C = E C = D C = G = E = D = W gg W ee G C E C D C G E D i G C B i + W gd W gd W ed ( ( ( i E C B i + W ed i D C B 2 i i D C B i i D C B i ) W gg B i + W gd B i i Sg i Sd ) W ee B i + W ed B i i Se W gd W ed i Sd B 2 i ) i Sd (10) 5. RESULTS In Section 2 we have discussed the drawbacks to entropy and how entropy is not suitable as an attack-based measure. Instead we propose the probability of path compromise given an adversarial bandwidth budget. In Section 4 we derived formulas for such probabilities under different bandwidth and weighting conditions. Here we calculate these probabilities using consensus data for Tor from April 22, To explore an attack-based measure we want to explore from the perspective of the adversary: what is best for him or her? Note, again, that a measure like entropy does not take such perspectives into account, so does not consider what might be a realistic attack or probability of compromise. We consider the adversary bandwidth fraction (ABWF) situation. We assume the adversary has a fixed bandwidth budget, n%. That is, he or she can control up to n% of the entire bandwidth. Of course, many sets of nodes could give that n%. Of interest, then, is which of these sets gives the highest probability of compromise, and, further, what that probability is. Recall that a path is compromised if the adversary controls the entry node and exit node of the path. Figure 4 represents this value, taken over all sets. The x-axis is labelled by the fraction of bandwidth controlled by the adversary, while the y-axis is labelled with the percentage of guard-exit pairs that are compromised. The point (b, p) on the graph means that p is the highest probability of choosing a compromised pair, chosen over all sets of compromised nodes with total bandwidth at most b. These numbers were derived from the same dataset used above and illustrated in Figure 3. As can be seen from the graph, the chance of compromise starts to increase rapidly when the fraction of compromised nodes is more than 25%. 7
8 To find the best combination of nodes to compromise the maximum number of paths with a given bandwidth, we explore all combinations of guard and exit nodes, starting with the smallest bandwidth offered. This obviously leads to combinatorial exploration of all possibilities, so we stop after a reasonable amount of time has elapsed since the last discovery. In all cases, the best case (in that sense) was discovered within one hour of computation, sometimes after several minutes. This leads us to believe that the solution found, understandably made from a large number of nodes of each category, is optimal because using such nodes allows us to get the closest to the allocated bandwidth budget. We can observe that our results are not far from a rough approximation to the probability of picking a compromised path in Tor by f 2, where f is the proportion of bandwidth controlled by the adversary, assuming those nodes could play either guard or exit roles. In practice we may not achieve exactly f 2 because nodes come in fixed, predetermined amounts (or denominations, if you will) and it maybe not be possible to find a set of nodes whose bandwidth sum exactly equals the bandwidth budget (cf. the knapsack problem). In comparing these results to that of Murdoch and Watson [11], we find a lower expectation of path compromise. However, our points of view are different. One difference between our work and theirs is that their results flow from a simulation of a small number of paths and we are working from bandwidth compromised. Our approach satisfies the criterion given by the quotation from Murdoch and Watson in Section 2 it reflects the limited bandwidth available to an attacker. Entropy misses this key information and, in a sense, measures the crowd and how easy it is to get lost in it, rather than how likely it is that members of that crowd are malicious. 5.1 Example We ran a number of calculations on the consensus dataset from April 22, 2011 and produced the following results. The associated weights, as discussed in Section 3.3 are: W gd = , W ed = , W md = , W ee = 1, W me = 0, W mg = , W gg = (11) The nodes and their bandwidths were divided into categories as follows: Node type Number of Nodes Total Bandwidth (KB/s) Guard 540 1,246,537 Exit ,093 Guard+Exit ,524 Non-flagged ,255 We then gave the adversary various budgets of (capped) bandwidth and computed optimal solutions, as described above. The types of nodes the adversary would be choosing from are either guard nodes, exit nodes or guard+exit nodes. The table below shows, for a given bandwidth budget, the total bandwidth of each type of node that is in the computed optimal solution: Bw % G bw (KB/s) E bw (KB/s) G+E bw (KB/s) 5% 40,031 20,935 62,339 10% 77,005 34, ,169 15% 113,795 50, ,699 20% 158,155 51, ,699 25% 186,845 61, ,229 Using equation (10) we can derive the probability of node compromise for each of these bandwidth budgets as: Bandwidth % Probability of compromise 5% % % % % RELATED WORK As mentioned in Section 2, entropy was introduced as a measure for anonymity by Serjantov and Danezis [14] and Diaz et al. [5]. There have been several alternative measures proposed for mix networks. As already mentioned, Shmatikov and Wang [16] explore min entropy. Clauß and Schiffner [4] advocate Rényi entropy. Edman et al. propose a combinatorial measure [9], later improved [21] by Gierlichs et al. However, to the best of our knowledge, none of these have been applied to Tor paths. Snader and Borisov [17] introduce an inequality measure, the Gini coefficient, to measure the inequality in their Tor path selection algorithm, but they consider this measure only. Syverson [18] asserts that a metric should reflect the difficulty an adversary has in compromising the system. Finally, Murdoch and Watson [11] and Panchenko and Renner [12] also look at measures when the adversary controls the entry and exit nodes. Murdoch and Watson [11] further discuss the idea of a bandwidth budget available to the adversary and perform simulations using several path selection techniques. They calculate percentage of compromised paths in these simulations. 7. CONCLUSION AND FUTURE WORK We exposed a number of critiques of entropy and discussed in particular how it fails to consider an attack-based approach. We calculated the probability of path compromise under three different Tor path selection algorithms, and combined this with the idea of adversarial bandwidth fraction to determine the likelihood of path compromise under different bandwidth budget conditions. Additional constraints. Broadening the range of situations in which we measure compromise would also be an interesting avenue. Compromise is more likely in some situations than others. For example, what if your guard node is controlled by an adversary? Dingledine and Murdoch [8] said one of the problems was that guard nodes were hanging around too long. That is, once chosen, they were held onto by the user for months at a time, and were thus overloaded. 8
9 Figure 4: Worst-case probability of path compromise given an adversary s bandwidth budget They suggest that they should be retained for a few weeks instead. But the frequency of change of guard nodes has implications for the likelihood of path compromise. Another issue is that when the nodes operate under the same administration they are more vulnerable to compromise if the administration is corrupt. There are further cases to consider, e.g. are they managed by the same operator, a different branch of the same operator, or operators running under the same jurisdiction (country). While it is clear that coordination becomes harder as we get further away from network operations, higher risks remain. Ideally a measure would allow for consideration of these types of constraints as well. In our investigations we found that the top 10 countries in bandwidth offered (in MB/s) were the following: Country Bandwidth Germany DE 240 Unites States US Holland NL Sweden SE France FR 36 Austria AT 25.7 Great Britain GB 22 Romania RO 19.9 Switzerland CH 19.3 Luxembourg LU 8.8 Thus the amount of bandwidth for substantial compromise is clearly beyond what any single country offers at this point (for the April 22, 2011 data set). It would be interesting to investigate whether the country information could be used to decide on a reasonable level of compromise: a country could not reasonably be entirely under the control of an unique entity (speaking of the countries at the top of our list), nor could such an entity control but a small proportion of nodes in most (key) jurisdictions. For example, we see that approximately 5% of the bandwidth is in the country with the highest amount of bandwidth Germany so it may be reasonable to assume that no adversary would control more than that. We also assumed a passive adversary. it would be interesting to examine this work under the assumption of an active attacker, as in Borisov et al. [3]. Policy. The probability of path compromise clearly depends on a number of quantitative factors such as total number of nodes, number of compromised nodes, bandwidth of nodes, and how often paths change. However, in addition to these factors are a number of qualitative factors we call policy. These are factors set by the user and include things like countries to avoid (e.g. most users may be happy to connect through Sweden, but Julian Assange may be less content!), how long a user connects for, and how often a user connects. As the user sets policies, the set of nodes from which it is choosing will shrink, and a graph representing the probability of detection vs. number of paths will change. Policy is individual and hard to quantify, but is there a way of incorporating it into a measure? Alternate designs. We consider the default path selection algorithm in Tor. But we could have looked at others such as Snader and Borisov [17], Panchenko and Renner [12], Sherr et al. [15], Edman and Syverson [10], Zhang et al. [23]. This would also be interesting future work. 9
10 8. ACKNOWLEDGEMENTS The authors thank Kevin Bauer, Tariq Elahi, Ryan Henry, Rob Smits, and Tao Wang for helpful comments on the manuscript. This work was supported by NSERC, MITACS and The Tor Project. 9. REFERENCES [1] Kevin Bauer, Damon McCoy, Dirk Grunwald, Tadayoshi Kohno, and Douglas Sicker. Low-resource routing attacks against anonymous systems. Technical report, University of Colorado at Boulder, CU-CS , [2] Kevin Bauer, Damon McCoy, Dirk Grunwald, Tadayoshi Kohno, and Douglas Sicker. Low-resource routing attacks against Tor. In Proceedings of the Workshop on Privacy in the Electronic Society (WPES 2007), pages 11 20, Washington, DC, USA, October [3] Nikita Borisov, George Danezis, Prateek Mittal, and Parisa Tabriz. Denial of service or denial of security? How attacks on reliability can compromise anonymity. In Proceedings of CCS 2007, pages , October [4] S. Clauß and S. Schiffner. Structuring anonymity metrics. In DIM, pages 55 62, November [5] Claudia Diaz, Stefaan Seys, Joris Claessens, and Bart Preneel. Towards measuring anonymity. In Roger Dingledine and Paul Syverson, editors, Proceedings of Privacy Enhancing Technologies Workshop (PET 2002). Springer-Verlag, LNCS 2482, April [6] R. Dingledine. The Tor Blog, Research Problem: measuring the safety of the Tor network, February 5, Accessed April [7] R. Dingledine and N. Mathewson. Tor path specification. plain; hb=head;f=path-spec.txt. Accessed April [8] R. Dingledine and S. Murdoch. Performance improvements on Tor or, why Tor is slow and what we re going to do about it. Tor Technical Report performance.pdf. Accessed April [9] M. Edman, F. Sivrikaya, and B. Yener. A combinatorial approach to measuring anonymity. Intelligence and Security Informatics, 2007 IEEE, pages , May [10] Matthew Edman and Paul F. Syverson. AS-awareness in Tor path selection. In Ehab Al-Shaer, Somesh Jha, and Angelos D. Keromytis, editors, Proceedings of the 2009 ACM Conference on Computer and Communications Security, CCS 2009, Chicago, Illinois, USA, November 9-13, 2009, pages ACM, [11] Steven J. Murdoch and Robert N. M. Watson. Metrics for security and performance in low-latency anonymity networks. In Nikita Borisov and Ian Goldberg, editors, Proceedings of the Eighth International Symposium on Privacy Enhancing Technologies (PETS 2008), pages , Leuven, Belgium, July Springer. [12] A. Panchenko and J. Renner. Path selection metrics for performance-improved onion routing. In SAINT, pages , July [13] M. Perry. TorFlow: Tor network analysis. In HotPETS, [14] Andrei Serjantov and George Danezis. Towards an information theoretic metric for anonymity. In Roger Dingledine and Paul Syverson, editors, Proceedings of Privacy Enhancing Technologies Workshop (PET 2002). Springer-Verlag, LNCS 2482, April [15] M. Sherr, B.T. Loo, and M. Blaze. Towards application-aware anonymous routing. In USENIX Workshop on Hot Topics in Security, Article 4, [16] Vitaly Shmatikov and Ming-Hsiu Wang. Measuring relationship anonymity in mix networks. In Proceedings of the Workshop on Privacy in the Electronic Society (WPES 2006), October [17] Robin Snader and Nikita Borisov. A tune-up for Tor: Improving security and performance in the Tor network. In Proceedings of the Network and Distributed Security Symposium - NDSS 08. Internet Society, February [18] P. Syverson. Why I m not an entropist. In 17th Security Protocols Workshop, Cambridge, UK, [19] Tor Directory Protocol. plain; hb=head;f=dir-spec.txt. Accessed April [20] Gergely Tóth, Zoltán Hornák, and Ferenc Vajda. Measuring anonymity revisited. In Sanna Liimatainen and Teemupekka Virtanen, editors, Proceedings of the Ninth Nordic Workshop on Secure IT Systems, pages 85 90, Espoo, Finland, November [21] Carmela Troncoso, Benedikt Gierlichs, Bart Preneel, and Ingrid Verbauwhede. Perfect matching statistical disclosure attacks. In Nikita Borisov and Ian Goldberg, editors, Proceedings of the Eighth International Symposium on Privacy Enhancing Technologies (PETS 2008), pages 2 23, Leuven, Belgium, July Springer. [22] Matthew Wright, Micah Adler, Brian Neil Levine, and Clay Shields. Defending anonymous communication against passive logging attacks. In Proceedings of the 2003 IEEE Symposium on Security and Privacy, pages 28 43, May [23] N. Zhang, W. Yu, X. Fu, and S.K. Das. gpath: A game-theoretic path selection algorithm to protect Tor s anonymity. In GameSec, pages 58 71, November
Metrics for Security and Performance in Low-Latency Anonymity Systems
 Metrics for Security and Performance in Low-Latency Anonymity Systems Tor user Entry node Tor Network Middle node Exit node Bandwidth per node (kb/s) (log scale) 1e+01 1e+03 1e+05 Encrypted tunnel Web
Metrics for Security and Performance in Low-Latency Anonymity Systems Tor user Entry node Tor Network Middle node Exit node Bandwidth per node (kb/s) (log scale) 1e+01 1e+03 1e+05 Encrypted tunnel Web
CE Advanced Network Security Anonymity II
 CE 817 - Advanced Network Security Anonymity II Lecture 19 Mehdi Kharrazi Department of Computer Engineering Sharif University of Technology Acknowledgments: Some of the slides are fully or partially obtained
CE 817 - Advanced Network Security Anonymity II Lecture 19 Mehdi Kharrazi Department of Computer Engineering Sharif University of Technology Acknowledgments: Some of the slides are fully or partially obtained
One Fast Guard for Life (or 9 months)
 One Fast Guard for Life (or 9 months) Roger Dingledine 1, Nicholas Hopper 2, George Kadianakis 1, and Nick Mathewson 1 1 The Tor Project, https://torproject.org {arma,asn,nickm}@torproject.org 2 University
One Fast Guard for Life (or 9 months) Roger Dingledine 1, Nicholas Hopper 2, George Kadianakis 1, and Nick Mathewson 1 1 The Tor Project, https://torproject.org {arma,asn,nickm}@torproject.org 2 University
Tor Experimentation Tools
 Tor Experimentation Tools Fatemeh Shirazi TU Darmstadt / KU Leuven Darmstadt, Germany fshirazi@cdc.informatik.tu-darmstadt.de Matthias Göhring TU Darmstadt Darmstadt, Germany de.m.goehring@ieee.org Claudia
Tor Experimentation Tools Fatemeh Shirazi TU Darmstadt / KU Leuven Darmstadt, Germany fshirazi@cdc.informatik.tu-darmstadt.de Matthias Göhring TU Darmstadt Darmstadt, Germany de.m.goehring@ieee.org Claudia
Toward Improving Path Selection in Tor
 Toward Improving Path Selection in Tor Fallon Chen Department of Computer Science and Engineering University of California, San Diego La Jolla, CA 203-00 Email: ftchen@cs.ucsd.edu Joseph Pasquale Department
Toward Improving Path Selection in Tor Fallon Chen Department of Computer Science and Engineering University of California, San Diego La Jolla, CA 203-00 Email: ftchen@cs.ucsd.edu Joseph Pasquale Department
Towards measuring anonymity
 Towards measuring anonymity Claudia Díaz, Stefaan Seys, Joris Claessens, and Bart Preneel K.U.Leuven ESAT-COSIC Kasteelpark Arenberg 0, B-300 Leuven-Heverlee, Belgium claudia.diaz@esat.kuleuven.ac.be http://www.esat.kuleuven.ac.be/cosic/
Towards measuring anonymity Claudia Díaz, Stefaan Seys, Joris Claessens, and Bart Preneel K.U.Leuven ESAT-COSIC Kasteelpark Arenberg 0, B-300 Leuven-Heverlee, Belgium claudia.diaz@esat.kuleuven.ac.be http://www.esat.kuleuven.ac.be/cosic/
Avoiding The Man on the Wire: Improving Tor s Security with Trust-Aware Path Selection
 Avoiding The Man on the Wire: Improving Tor s Security with Trust-Aware Path Selection Aaron Johnson Rob Jansen Aaron D. Jaggard Joan Feigenbaum Paul Syverson (U.S. Naval Research Laboratory) (U.S. Naval
Avoiding The Man on the Wire: Improving Tor s Security with Trust-Aware Path Selection Aaron Johnson Rob Jansen Aaron D. Jaggard Joan Feigenbaum Paul Syverson (U.S. Naval Research Laboratory) (U.S. Naval
Adaptive throttling of Tor clients by entry guards
 Adaptive throttling of Tor clients by entry guards Roger Dingledine arma@torproject.org Tor Tech Report 2010-09-001 September 19, 2010 Abstract Looking for a paper topic (or a thesis topic)? Here s a Tor
Adaptive throttling of Tor clients by entry guards Roger Dingledine arma@torproject.org Tor Tech Report 2010-09-001 September 19, 2010 Abstract Looking for a paper topic (or a thesis topic)? Here s a Tor
Message Splitting Against the Partial Adversary
 Message Splitting Against the Partial Adversary Andrei Serjantov and Steven J. Murdoch The Free Haven Project, UK schnur@gmail.com University of Cambridge Computer Laboratory, 5 JJ Thomson Ave, Cambridge,
Message Splitting Against the Partial Adversary Andrei Serjantov and Steven J. Murdoch The Free Haven Project, UK schnur@gmail.com University of Cambridge Computer Laboratory, 5 JJ Thomson Ave, Cambridge,
Safely Measuring Tor. Rob Jansen U.S. Naval Research Laboratory Center for High Assurance Computer Systems
 Safely Measuring Tor Safely Measuring Tor, Rob Jansen and Aaron Johnson, In the Proceedings of the 23rd ACM Conference on Computer and Communication Security (CCS 2016). Rob Jansen Center for High Assurance
Safely Measuring Tor Safely Measuring Tor, Rob Jansen and Aaron Johnson, In the Proceedings of the 23rd ACM Conference on Computer and Communication Security (CCS 2016). Rob Jansen Center for High Assurance
Measuring the Tor Network Evaluation of Relays from Public Directory Data
 Measuring the Tor Network Evaluation of Relays from Public Directory Data Karsten Loesing karsten@torproject.org Tor Tech Report 2009-06-001 June 22, 2009 Abstract This document contains the results of
Measuring the Tor Network Evaluation of Relays from Public Directory Data Karsten Loesing karsten@torproject.org Tor Tech Report 2009-06-001 June 22, 2009 Abstract This document contains the results of
Counting daily bridge users
 Counting daily bridge users Karsten Loesing karsten@torproject.org Tor Tech Report 212-1-1 October 24, 212 Abstract As part of the Tor Metrics Project, we want to learn how many people use the Tor network
Counting daily bridge users Karsten Loesing karsten@torproject.org Tor Tech Report 212-1-1 October 24, 212 Abstract As part of the Tor Metrics Project, we want to learn how many people use the Tor network
Safely Measuring Tor. Rob Jansen U.S. Naval Research Laboratory Center for High Assurance Computer Systems
 Safely Measuring Tor Safely Measuring Tor, Rob Jansen and Aaron Johnson, In the Proceedings of the 23rd ACM Conference on Computer and Communication Security (CCS 2016). Rob Jansen Center for High Assurance
Safely Measuring Tor Safely Measuring Tor, Rob Jansen and Aaron Johnson, In the Proceedings of the 23rd ACM Conference on Computer and Communication Security (CCS 2016). Rob Jansen Center for High Assurance
Analysis on End-to-End Node Selection Probability in Tor Network
 Analysis on End-to-End Node Selection Probability in Tor Network Saurav Dahal 1, Junghee Lee 2, Jungmin Kang 2 and Seokjoo Shin 1 1 Department of Computer Engineering, Chosun University, Gwangju, South
Analysis on End-to-End Node Selection Probability in Tor Network Saurav Dahal 1, Junghee Lee 2, Jungmin Kang 2 and Seokjoo Shin 1 1 Department of Computer Engineering, Chosun University, Gwangju, South
ANONYMOUS CONNECTIONS AND ONION ROUTING
 I J C I T A E Serials Publications 6(1) 2012 : 31-37 ANONYMOUS CONNECTIONS AND ONION ROUTING NILESH MADHUKAR PATIL 1 AND CHELPA LINGAM 2 1 Lecturer, I. T. Dept., Rajiv Gandhi Institute of Technology, Mumbai
I J C I T A E Serials Publications 6(1) 2012 : 31-37 ANONYMOUS CONNECTIONS AND ONION ROUTING NILESH MADHUKAR PATIL 1 AND CHELPA LINGAM 2 1 Lecturer, I. T. Dept., Rajiv Gandhi Institute of Technology, Mumbai
Cryptanalysis of a fair anonymity for the tor network
 Cryptanalysis of a fair anonymity for the tor network Amadou Moctar Kane KSecurity, BP 47136, Dakar, Senegal amadou1@gmailcom April 16, 2015 Abstract The aim of this paper is to present an attack upon
Cryptanalysis of a fair anonymity for the tor network Amadou Moctar Kane KSecurity, BP 47136, Dakar, Senegal amadou1@gmailcom April 16, 2015 Abstract The aim of this paper is to present an attack upon
Low-Resource Routing Attacks Against Tor
 Low-Resource Routing Attacks Against Tor Kevin Bauer Damon McCoy Dirk Grunwald Tadayoshi Kohno Douglas Sicker Department of Computer Science University of Colorado Boulder, CO 80309-0430 USA {bauerk, mccoyd,
Low-Resource Routing Attacks Against Tor Kevin Bauer Damon McCoy Dirk Grunwald Tadayoshi Kohno Douglas Sicker Department of Computer Science University of Colorado Boulder, CO 80309-0430 USA {bauerk, mccoyd,
Social Networking for Anonymous Communication Systems: A Survey
 Social Networking for Anonymous Communication Systems: A Survey Rodolphe Marques Instituto de Telecomunicações Aveiro, Portugal rmarques@av.it.pt André Zúquete Universidade de Aveiro/IEETA Aveiro, Portugal
Social Networking for Anonymous Communication Systems: A Survey Rodolphe Marques Instituto de Telecomunicações Aveiro, Portugal rmarques@av.it.pt André Zúquete Universidade de Aveiro/IEETA Aveiro, Portugal
A New Replay Attack Against Anonymous Communication Networks
 1 A New Replay Attack Against Anonymous Communication Networks Ryan Pries, Wei Yu, Xinwen Fu and Wei Zhao Abstract Tor is a real-world, circuit-based low-latency anonymous communication network, supporting
1 A New Replay Attack Against Anonymous Communication Networks Ryan Pries, Wei Yu, Xinwen Fu and Wei Zhao Abstract Tor is a real-world, circuit-based low-latency anonymous communication network, supporting
DynaFlow: An Efficient Website Fingerprinting Defense Based on Dynamically-Adjusting Flows
 DynaFlow: An Efficient Website Fingerprinting Defense Based on Dynamically-Adjusting Flows ABSTRACT David Lu MIT PRIMES davidboxboro@gmail.com Albert Kwon MIT kwonal@mit.edu Website fingerprinting attacks
DynaFlow: An Efficient Website Fingerprinting Defense Based on Dynamically-Adjusting Flows ABSTRACT David Lu MIT PRIMES davidboxboro@gmail.com Albert Kwon MIT kwonal@mit.edu Website fingerprinting attacks
Moving Tor Circuits Towards Multiple-Path: Anonymity and Performance Considerations
 Moving Tor Circuits Towards Multiple-Path: Anonymity and Performance Considerations F. Rochet Universite Catholique de Louvain ICTEAM Crypto Group Louvain-la-Neuve, Belgium O. Pereira Universite Catholique
Moving Tor Circuits Towards Multiple-Path: Anonymity and Performance Considerations F. Rochet Universite Catholique de Louvain ICTEAM Crypto Group Louvain-la-Neuve, Belgium O. Pereira Universite Catholique
AnoA: A Differential Anonymity Framework
 AnoA: A Differential Anonymity Framework Michael Backes, Aniket Kate, Praveen Manoharan, Sebastian Meiser, Esfandiar Mohammadi CISPA, Saarland University Abstract Protecting individuals privacy in online
AnoA: A Differential Anonymity Framework Michael Backes, Aniket Kate, Praveen Manoharan, Sebastian Meiser, Esfandiar Mohammadi CISPA, Saarland University Abstract Protecting individuals privacy in online
Improving stream correlation attacks on anonymous networks
 Improving stream correlation attacks on anonymous networks Gavin O Gorman Dublin City University Glasnevin, D9 Dublin, Ireland gavin.ogorman@computing.dcu.ie Stephen Blott Dublin City University Glasnevin,
Improving stream correlation attacks on anonymous networks Gavin O Gorman Dublin City University Glasnevin, D9 Dublin, Ireland gavin.ogorman@computing.dcu.ie Stephen Blott Dublin City University Glasnevin,
Low Latency Anonymity with Mix Rings
 Low Latency Anonymity with Mix Rings Matthew Burnside and Angelos D. Keromytis Department of Computer Science, Columbia University {mb,angelos}@cs.columbia.edu Abstract. We introduce mix rings, a novel
Low Latency Anonymity with Mix Rings Matthew Burnside and Angelos D. Keromytis Department of Computer Science, Columbia University {mb,angelos}@cs.columbia.edu Abstract. We introduce mix rings, a novel
Sleeping dogs lie on a bed of onions but wake when mixed
 Sleeping dogs lie on a bed of onions but wake when mixed Paul Syverson Naval Research Laboratory, USA. Abstract. We introduce and investigate sleeper attacks and explore them in the context of anonymous
Sleeping dogs lie on a bed of onions but wake when mixed Paul Syverson Naval Research Laboratory, USA. Abstract. We introduce and investigate sleeper attacks and explore them in the context of anonymous
Preventing Active Timing Attacks in Low-Latency Anonymous Communication
 Preventing Active Timing Attacks in Low-Latency Anonymous Communication [Extended Abstract] Joan Feigenbaum 1, Aaron Johnson 2, and Paul Syverson 3 1 Yale University Joan.Feigenbaum@yale.edu 2 The University
Preventing Active Timing Attacks in Low-Latency Anonymous Communication [Extended Abstract] Joan Feigenbaum 1, Aaron Johnson 2, and Paul Syverson 3 1 Yale University Joan.Feigenbaum@yale.edu 2 The University
Bridging and Fingerprinting: Epistemic Attacks on Route Selection
 Bridging and Fingerprinting: Epistemic Attacks on Route Selection George Danezis 1 and Paul Syverson 2 1 Microsoft Research, Cambridge, UK. 2 Naval Research Laboratory, USA. Abstract. Users building routes
Bridging and Fingerprinting: Epistemic Attacks on Route Selection George Danezis 1 and Paul Syverson 2 1 Microsoft Research, Cambridge, UK. 2 Naval Research Laboratory, USA. Abstract. Users building routes
Design and Analysis of Efficient Anonymous Communication Protocols
 Design and Analysis of Efficient Anonymous Communication Protocols Thesis Defense Aaron Johnson Department of Computer Science Yale University 7/1/2009 1 Acknowledgements Joan Feigenbaum Paul Syverson
Design and Analysis of Efficient Anonymous Communication Protocols Thesis Defense Aaron Johnson Department of Computer Science Yale University 7/1/2009 1 Acknowledgements Joan Feigenbaum Paul Syverson
Impact of Network Topology on Anonymity and Overhead in Low-Latency Anonymity Networks
 Impact of Network Topology on Anonymity and Overhead in Low-Latency Anonymity Networks Claudia Diaz 1, Steven J. Murdoch 2, Carmela Troncoso 1 1 K.U.Leuven, ESAT/COSIC 2 University of Cambridge / The Tor
Impact of Network Topology on Anonymity and Overhead in Low-Latency Anonymity Networks Claudia Diaz 1, Steven J. Murdoch 2, Carmela Troncoso 1 1 K.U.Leuven, ESAT/COSIC 2 University of Cambridge / The Tor
Internet Privacy. Markus Klein, Joshua Juen University of Illinois Fall 2011
 Internet Privacy Markus Klein, Joshua Juen University of Illinois Fall 2011 I have nothing to hide!...they accept the premise that privacy is about hiding a wrong. It's not." Rather, privacy is most ohen
Internet Privacy Markus Klein, Joshua Juen University of Illinois Fall 2011 I have nothing to hide!...they accept the premise that privacy is about hiding a wrong. It's not." Rather, privacy is most ohen
communication Claudia Díaz Katholieke Universiteit Leuven Dept. Electrical Engineering g ESAT/COSIC October 9, 2007 Claudia Diaz (K.U.
 Introduction to anonymous communication Claudia Díaz Katholieke Universiteit Leuven Dept. Electrical Engineering g ESAT/COSIC October 9, 2007 Claudia Diaz (K.U.Leuven) 1 a few words on the scope of the
Introduction to anonymous communication Claudia Díaz Katholieke Universiteit Leuven Dept. Electrical Engineering g ESAT/COSIC October 9, 2007 Claudia Diaz (K.U.Leuven) 1 a few words on the scope of the
PrivCount: A Distributed System for Safely Measuring Tor
 PrivCount: A Distributed System for Safely Measuring Tor Rob Jansen Center for High Assurance Computer Systems Invited Talk, October 4 th, 2016 University of Oregon Department of Computer and Information
PrivCount: A Distributed System for Safely Measuring Tor Rob Jansen Center for High Assurance Computer Systems Invited Talk, October 4 th, 2016 University of Oregon Department of Computer and Information
The New Cell-Counting-Based Against Anonymous Proxy
 The New Cell-Counting-Based Against Anonymous Proxy Yadarthugalla Raju M.Tech Student, Department of CSE, Dr.K.V.S.R.I.T, Kurnool. K. Pavan Kumar Assistant Professor, Department of IT, Dr.K.V.S.R.I.T,
The New Cell-Counting-Based Against Anonymous Proxy Yadarthugalla Raju M.Tech Student, Department of CSE, Dr.K.V.S.R.I.T, Kurnool. K. Pavan Kumar Assistant Professor, Department of IT, Dr.K.V.S.R.I.T,
Revisiting Circuit Clogging Attacks on Tor
 Revisiting Circuit Clogging Attacks on Tor Eric Chan-Tin, Jiyoung Shin and Jiangmin Yu Department of Computer Science Oklahoma State University {chantin, jiyoung, jiangmy}@cs.okstate.edu Abstract Tor is
Revisiting Circuit Clogging Attacks on Tor Eric Chan-Tin, Jiyoung Shin and Jiangmin Yu Department of Computer Science Oklahoma State University {chantin, jiyoung, jiangmy}@cs.okstate.edu Abstract Tor is
Torchestra: Reducing Interactive Traffic Delays over Tor
 Torchestra: Reducing Interactive Traffic Delays over Tor Deepika Gopal UC San Diego drgopal@cs.ucsd.edu Nadia Heninger UC San Diego nadiah@cs.princeton.edu ABSTRACT Tor is an onion routing network that
Torchestra: Reducing Interactive Traffic Delays over Tor Deepika Gopal UC San Diego drgopal@cs.ucsd.edu Nadia Heninger UC San Diego nadiah@cs.princeton.edu ABSTRACT Tor is an onion routing network that
LINKING TOR CIRCUITS
 LINKING TOR CIRCUITS MSc Information Security, 2014 University College London Otto Huhta Supervisor: Dr George Danezis This report is submitted as part requirement for the MSc in Information Security at
LINKING TOR CIRCUITS MSc Information Security, 2014 University College London Otto Huhta Supervisor: Dr George Danezis This report is submitted as part requirement for the MSc in Information Security at
D-Optimal Designs. Chapter 888. Introduction. D-Optimal Design Overview
 Chapter 888 Introduction This procedure generates D-optimal designs for multi-factor experiments with both quantitative and qualitative factors. The factors can have a mixed number of levels. For example,
Chapter 888 Introduction This procedure generates D-optimal designs for multi-factor experiments with both quantitative and qualitative factors. The factors can have a mixed number of levels. For example,
The Onion Routing Performance using Shadowplugin-TOR
 The Onion Routing Performance using Shadowplugin-TOR Hartanto Kusuma Wardana, Liauw Frediczen Handianto, Banu Wirawan Yohanes * Faculty of Electronic and Computer Engineering Universitas Kristen Satya
The Onion Routing Performance using Shadowplugin-TOR Hartanto Kusuma Wardana, Liauw Frediczen Handianto, Banu Wirawan Yohanes * Faculty of Electronic and Computer Engineering Universitas Kristen Satya
Shining Light in Dark Places: Understanding the Tor Network
 Shining Light in Dark Places: Understanding the Tor Network Damon McCoy 1,KevinBauer 1,DirkGrunwald 1, Tadayoshi Kohno 2, and Douglas Sicker 1 1 Department of Computer Science, University of Colorado,
Shining Light in Dark Places: Understanding the Tor Network Damon McCoy 1,KevinBauer 1,DirkGrunwald 1, Tadayoshi Kohno 2, and Douglas Sicker 1 1 Department of Computer Science, University of Colorado,
Traffic Optimization in Anonymous Networks
 Traffic Optimization in Anonymous Networks Patrik Kristel patrik.kristel@onedata.sk Ján Lučanský jan.lucansky@stuba.sk Ivan Kotuliak ivan.kotuliak@stuba.sk Abstract Anonymous communication networks, such
Traffic Optimization in Anonymous Networks Patrik Kristel patrik.kristel@onedata.sk Ján Lučanský jan.lucansky@stuba.sk Ivan Kotuliak ivan.kotuliak@stuba.sk Abstract Anonymous communication networks, such
A Composite-Metric Based Path Selection Technique for the Tor Anonymity Network
 REPRINTED FROM: 1 A Composite-Metric Based Path Selection Technique for the Tor Anonymity Network Sadegh Momeni Milajerdi, and Mehdi Kharrazi Tor relays. On one side, and from the performance aspect, a
REPRINTED FROM: 1 A Composite-Metric Based Path Selection Technique for the Tor Anonymity Network Sadegh Momeni Milajerdi, and Mehdi Kharrazi Tor relays. On one side, and from the performance aspect, a
COST TO DEFEAT THE N-1 ATTACK. Neil Chettiar
 COST TO DEFEAT THE -1 ATTAC eil Chettiar The -1 Attack MIX Different Variations: Threshold Mixes Timed Mixes Pool Mixes Attacks are Exact and Certain. Basic idea: Attacker should be able to account for
COST TO DEFEAT THE -1 ATTAC eil Chettiar The -1 Attack MIX Different Variations: Threshold Mixes Timed Mixes Pool Mixes Attacks are Exact and Certain. Basic idea: Attacker should be able to account for
Onion services. Philipp Winter Nov 30, 2015
 Onion services Philipp Winter pwinter@cs.princeton.edu Nov 30, 2015 Quick introduction to Tor An overview of Tor Tor is a low-latency anonymity network Based on Syverson's onion routing......which is based
Onion services Philipp Winter pwinter@cs.princeton.edu Nov 30, 2015 Quick introduction to Tor An overview of Tor Tor is a low-latency anonymity network Based on Syverson's onion routing......which is based
Guard Sets in Tor using AS Relationships
 Proceedings on Privacy Enhancing Technologies ; 218 (1):145 165 Mohsen Imani*, Armon Barton, and Matthew Wright Guard Sets in Tor using AS Relationships Abstract: The mechanism for picking guards in Tor
Proceedings on Privacy Enhancing Technologies ; 218 (1):145 165 Mohsen Imani*, Armon Barton, and Matthew Wright Guard Sets in Tor using AS Relationships Abstract: The mechanism for picking guards in Tor
Practical Anonymity for the Masses with MorphMix
 Practical Anonymity for the Masses with MorphMix Marc Rennhard, Bernhard Plattner () Financial Cryptography 2004 12 th February 2004 http://www.tik.ee.ethz.ch/~morphmix Overview Circuit-based mix networks
Practical Anonymity for the Masses with MorphMix Marc Rennhard, Bernhard Plattner () Financial Cryptography 2004 12 th February 2004 http://www.tik.ee.ethz.ch/~morphmix Overview Circuit-based mix networks
More Anonymity Through Trust Degree in Trust-based Onion Routing
 More Anonymity Through Trust Degree in Trust-based Onion Routing Peng Zhou, Xiapu Luo, and Rocky K. C. Chang Department of Computing, The Hong Kong Polytechnic University, Hunghom, Hong Kong {cspzhouroc,csxluo,csrchang}@comp.polyu.edu.hk
More Anonymity Through Trust Degree in Trust-based Onion Routing Peng Zhou, Xiapu Luo, and Rocky K. C. Chang Department of Computing, The Hong Kong Polytechnic University, Hunghom, Hong Kong {cspzhouroc,csxluo,csrchang}@comp.polyu.edu.hk
Low-Cost Traffic Analysis of Tor
 Low-Cost Traffic Analysis of Tor Steven J. Murdoch, George Danezis University of Cambridge, Computer Laboratory Review of Tor Support anonymous transport of TCP streams over the Internet Support anonymous
Low-Cost Traffic Analysis of Tor Steven J. Murdoch, George Danezis University of Cambridge, Computer Laboratory Review of Tor Support anonymous transport of TCP streams over the Internet Support anonymous
Automated Website Fingerprinting through Deep Learning
 Automated Website Fingerprinting through Deep Learning Vera Rimmer 1, Davy Preuveneers 1, Marc Juarez 2, Tom Van Goethem 1 and Wouter Joosen 1 NDSS 2018 Feb 19th (San Diego, USA) 1 2 Website Fingerprinting
Automated Website Fingerprinting through Deep Learning Vera Rimmer 1, Davy Preuveneers 1, Marc Juarez 2, Tom Van Goethem 1 and Wouter Joosen 1 NDSS 2018 Feb 19th (San Diego, USA) 1 2 Website Fingerprinting
Theorem 2.9: nearest addition algorithm
 There are severe limits on our ability to compute near-optimal tours It is NP-complete to decide whether a given undirected =(,)has a Hamiltonian cycle An approximation algorithm for the TSP can be used
There are severe limits on our ability to compute near-optimal tours It is NP-complete to decide whether a given undirected =(,)has a Hamiltonian cycle An approximation algorithm for the TSP can be used
CSE 484 / CSE M 584: Computer Security and Privacy. Anonymity Mobile. Autumn Tadayoshi (Yoshi) Kohno
 CSE 484 / CSE M 584: Computer Security and Privacy Anonymity Mobile Autumn 2018 Tadayoshi (Yoshi) Kohno yoshi@cs.washington.edu Thanks to Dan Boneh, Dieter Gollmann, Dan Halperin, Ada Lerner, John Manferdelli,
CSE 484 / CSE M 584: Computer Security and Privacy Anonymity Mobile Autumn 2018 Tadayoshi (Yoshi) Kohno yoshi@cs.washington.edu Thanks to Dan Boneh, Dieter Gollmann, Dan Halperin, Ada Lerner, John Manferdelli,
RAPTOR: Routing Attacks on Privacy in Tor. Yixin Sun. Princeton University. Acknowledgment for Slides. Joint work with
 RAPTOR: Routing Attacks on Privacy in Tor Yixin Sun Princeton University Joint work with Annie Edmundson, Laurent Vanbever, Oscar Li, Jennifer Rexford, Mung Chiang, Prateek Mittal Acknowledgment for Slides
RAPTOR: Routing Attacks on Privacy in Tor Yixin Sun Princeton University Joint work with Annie Edmundson, Laurent Vanbever, Oscar Li, Jennifer Rexford, Mung Chiang, Prateek Mittal Acknowledgment for Slides
Veracity: Practical Secure Network Coordinates via Vote-Based Agreements
 Veracity: Practical Secure Network Coordinates via Vote-Based Agreements Micah Sherr, Matt Blaze, and Boon Thau Loo University of Pennsylvania USENIX Technical June 18th, 2009 1 Network Coordinate Systems
Veracity: Practical Secure Network Coordinates via Vote-Based Agreements Micah Sherr, Matt Blaze, and Boon Thau Loo University of Pennsylvania USENIX Technical June 18th, 2009 1 Network Coordinate Systems
Heartbeat Traffic to Counter (n-1) Attacks
 Heartbeat Traffic to Counter (n-1) Attacks Red-Green-Black Mixes George Danezis University of Cambridge, Computer Laboratory, William Gates Building, 15 JJ Thomson Avenue, Cambridge CB3 0FD, United Kingdom.
Heartbeat Traffic to Counter (n-1) Attacks Red-Green-Black Mixes George Danezis University of Cambridge, Computer Laboratory, William Gates Building, 15 JJ Thomson Avenue, Cambridge CB3 0FD, United Kingdom.
For our example, we will look at the following factors and factor levels.
 In order to review the calculations that are used to generate the Analysis of Variance, we will use the statapult example. By adjusting various settings on the statapult, you are able to throw the ball
In order to review the calculations that are used to generate the Analysis of Variance, we will use the statapult example. By adjusting various settings on the statapult, you are able to throw the ball
0x1A Great Papers in Computer Security
 CS 380S 0x1A Great Papers in Computer Security Vitaly Shmatikov http://www.cs.utexas.edu/~shmat/courses/cs380s/ Privacy on Public Networks Internet is designed as a public network Wi-Fi access points,
CS 380S 0x1A Great Papers in Computer Security Vitaly Shmatikov http://www.cs.utexas.edu/~shmat/courses/cs380s/ Privacy on Public Networks Internet is designed as a public network Wi-Fi access points,
Challenges in Mobile Ad Hoc Network
 American Journal of Engineering Research (AJER) e-issn: 2320-0847 p-issn : 2320-0936 Volume-5, Issue-5, pp-210-216 www.ajer.org Research Paper Challenges in Mobile Ad Hoc Network Reshma S. Patil 1, Dr.
American Journal of Engineering Research (AJER) e-issn: 2320-0847 p-issn : 2320-0936 Volume-5, Issue-5, pp-210-216 www.ajer.org Research Paper Challenges in Mobile Ad Hoc Network Reshma S. Patil 1, Dr.
Congestion-aware Path Selection for Tor
 Congestion-aware Path Selection for Tor Tao Wang, Kevin Bauer, Clara Forero, and Ian Goldberg Cheriton School of Computer Science University of Waterloo {t55wang,k4bauer,ciforero,iang}@cs.uwaterloo.ca
Congestion-aware Path Selection for Tor Tao Wang, Kevin Bauer, Clara Forero, and Ian Goldberg Cheriton School of Computer Science University of Waterloo {t55wang,k4bauer,ciforero,iang}@cs.uwaterloo.ca
Blending different latency traffic with alpha-mixing
 Blending different latency traffic with alpha-mixing Roger Dingledine 1, Andrei Serjantov 2, and Paul Syverson 3 1 The Free Haven Project (arma@freehaven.net) 2 The Free Haven Project (aas23@freehaven.net)
Blending different latency traffic with alpha-mixing Roger Dingledine 1, Andrei Serjantov 2, and Paul Syverson 3 1 The Free Haven Project (arma@freehaven.net) 2 The Free Haven Project (aas23@freehaven.net)
2. On classification and related tasks
 2. On classification and related tasks In this part of the course we take a concise bird s-eye view of different central tasks and concepts involved in machine learning and classification particularly.
2. On classification and related tasks In this part of the course we take a concise bird s-eye view of different central tasks and concepts involved in machine learning and classification particularly.
7. Decision or classification trees
 7. Decision or classification trees Next we are going to consider a rather different approach from those presented so far to machine learning that use one of the most common and important data structure,
7. Decision or classification trees Next we are going to consider a rather different approach from those presented so far to machine learning that use one of the most common and important data structure,
An Improved Algorithm for Tor Circuit Scheduling
 An Improved Algorithm for Tor Circuit Scheduling Can Tang Cheriton School of Computer Science University of Waterloo Waterloo, ON, Canada c24tang@cs.uwaterloo.ca Ian Goldberg Cheriton School of Computer
An Improved Algorithm for Tor Circuit Scheduling Can Tang Cheriton School of Computer Science University of Waterloo Waterloo, ON, Canada c24tang@cs.uwaterloo.ca Ian Goldberg Cheriton School of Computer
ARELAY network consists of a pair of source and destination
 158 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL 55, NO 1, JANUARY 2009 Parity Forwarding for Multiple-Relay Networks Peyman Razaghi, Student Member, IEEE, Wei Yu, Senior Member, IEEE Abstract This paper
158 IEEE TRANSACTIONS ON INFORMATION THEORY, VOL 55, NO 1, JANUARY 2009 Parity Forwarding for Multiple-Relay Networks Peyman Razaghi, Student Member, IEEE, Wei Yu, Senior Member, IEEE Abstract This paper
General properties of staircase and convex dual feasible functions
 General properties of staircase and convex dual feasible functions JÜRGEN RIETZ, CLÁUDIO ALVES, J. M. VALÉRIO de CARVALHO Centro de Investigação Algoritmi da Universidade do Minho, Escola de Engenharia
General properties of staircase and convex dual feasible functions JÜRGEN RIETZ, CLÁUDIO ALVES, J. M. VALÉRIO de CARVALHO Centro de Investigação Algoritmi da Universidade do Minho, Escola de Engenharia
Identifying and characterizing Sybils in the Tor network
 Identifying and characterizing Sybils in the Tor network August 12, 2016 USENIX Security Symposium Philipp Winter Princeton University and Karlstad University Roya Ensafi Princeton University Karsten Loesing
Identifying and characterizing Sybils in the Tor network August 12, 2016 USENIX Security Symposium Philipp Winter Princeton University and Karlstad University Roya Ensafi Princeton University Karsten Loesing
CPSC 320: Intermediate Algorithm Design and Analysis. Tutorial: Week 3
 CPSC 320: Intermediate Algorithm Design and Analysis Author: Susanne Bradley Tutorial: Week 3 At the time of this week s tutorial, we were approaching the end of our stable matching unit and about to start
CPSC 320: Intermediate Algorithm Design and Analysis Author: Susanne Bradley Tutorial: Week 3 At the time of this week s tutorial, we were approaching the end of our stable matching unit and about to start
Towards Measuring Resilience in Anonymous Communication Networks
 Towards Measuring Resilience in Anonymous Communication Networks Fatemeh Shirazi KU Leuven, ESAT/COSIC and iminds, Leuven, Belgium fshirazi@esat.kuleuven.be Claudia Diaz KU Leuven ESAT/COSIC, iminds, Leuven,
Towards Measuring Resilience in Anonymous Communication Networks Fatemeh Shirazi KU Leuven, ESAT/COSIC and iminds, Leuven, Belgium fshirazi@esat.kuleuven.be Claudia Diaz KU Leuven ESAT/COSIC, iminds, Leuven,
Towards Predicting Efficient and Anonymous Tor Circuits
 Towards Predicting Efficient and Anonymous Tor Circuits Armon Barton, Mohsen Imani, and Jiang Ming, University of Texas at Arlington; Matthew Wright, Rochester Institute of Technology https://www.usenix.org/conference/usenixsecurity8/presentation/barton
Towards Predicting Efficient and Anonymous Tor Circuits Armon Barton, Mohsen Imani, and Jiang Ming, University of Texas at Arlington; Matthew Wright, Rochester Institute of Technology https://www.usenix.org/conference/usenixsecurity8/presentation/barton
Vocabulary: Data Distributions
 Vocabulary: Data Distributions Concept Two Types of Data. I. Categorical data: is data that has been collected and recorded about some non-numerical attribute. For example: color is an attribute or variable
Vocabulary: Data Distributions Concept Two Types of Data. I. Categorical data: is data that has been collected and recorded about some non-numerical attribute. For example: color is an attribute or variable
Vida: How to use Bayesian inference to de-anonymize persistent communications
 Vida: How to use Bayesian inference to de-anonymize persistent communications George Danezis 1 and Carmela Troncoso 2 1 Microsoft Research Cambridge gdane@microsoft.com 2 K.U. Leuven/IBBT, ESAT/SCD-COSIC
Vida: How to use Bayesian inference to de-anonymize persistent communications George Danezis 1 and Carmela Troncoso 2 1 Microsoft Research Cambridge gdane@microsoft.com 2 K.U. Leuven/IBBT, ESAT/SCD-COSIC
On the Origins of a Thesis
 STM 2008 On the Origins of a Thesis Steven J. Murdoch 1 University of Cambridge Computer Laboratory Cambridge, United Kingdom Abstract A PhD thesis typically reads as an idealised narrative: how would
STM 2008 On the Origins of a Thesis Steven J. Murdoch 1 University of Cambridge Computer Laboratory Cambridge, United Kingdom Abstract A PhD thesis typically reads as an idealised narrative: how would
Middle School Math Course 2
 Middle School Math Course 2 Correlation of the ALEKS course Middle School Math Course 2 to the Indiana Academic Standards for Mathematics Grade 7 (2014) 1: NUMBER SENSE = ALEKS course topic that addresses
Middle School Math Course 2 Correlation of the ALEKS course Middle School Math Course 2 to the Indiana Academic Standards for Mathematics Grade 7 (2014) 1: NUMBER SENSE = ALEKS course topic that addresses
Peer-to-Peer Systems and Security
 Peer-to-Peer Systems and Security Attacks! Christian Grothoff Technische Universität München April 13, 2013 Salsa & AP3 Goal: eliminate trusted blender server Idea: Use DHT (AP3: Pastry, Salsa: custom
Peer-to-Peer Systems and Security Attacks! Christian Grothoff Technische Universität München April 13, 2013 Salsa & AP3 Goal: eliminate trusted blender server Idea: Use DHT (AP3: Pastry, Salsa: custom
Introduction. Jamie Hayes and George Danezis Guard Sets for Onion Routing
 Proceedings on Privacy Enhancing Technologies 215; 215 (2):65 8 Jamie Hayes and George Danezis Guard Sets for Onion Routing Abstract: Entry guards protect the Tor onion routing system from variants of
Proceedings on Privacy Enhancing Technologies 215; 215 (2):65 8 Jamie Hayes and George Danezis Guard Sets for Onion Routing Abstract: Entry guards protect the Tor onion routing system from variants of
Perfect Matching Disclosure Attacks
 Perfect Matching Disclosure Attacks Carmela Troncoso, Benedikt Gierlichs, Bart Preneel, and Ingrid Verbauwhede K.U. Leuven, ESAT/SCD-COSIC, IBBT Kasteelpark Arenberg 10, B-3001 Leuven-Heverlee, Belgium
Perfect Matching Disclosure Attacks Carmela Troncoso, Benedikt Gierlichs, Bart Preneel, and Ingrid Verbauwhede K.U. Leuven, ESAT/SCD-COSIC, IBBT Kasteelpark Arenberg 10, B-3001 Leuven-Heverlee, Belgium
6.001 Notes: Section 4.1
 6.001 Notes: Section 4.1 Slide 4.1.1 In this lecture, we are going to take a careful look at the kinds of procedures we can build. We will first go back to look very carefully at the substitution model,
6.001 Notes: Section 4.1 Slide 4.1.1 In this lecture, we are going to take a careful look at the kinds of procedures we can build. We will first go back to look very carefully at the substitution model,
CPSC 467b: Cryptography and Computer Security
 CPSC 467b: Cryptography and Computer Security Michael J. Fischer Lecture 7 January 30, 2012 CPSC 467b, Lecture 7 1/44 Public-key cryptography RSA Factoring Assumption Computing with Big Numbers Fast Exponentiation
CPSC 467b: Cryptography and Computer Security Michael J. Fischer Lecture 7 January 30, 2012 CPSC 467b, Lecture 7 1/44 Public-key cryptography RSA Factoring Assumption Computing with Big Numbers Fast Exponentiation
Section 1.2 Fractions
 Objectives Section 1.2 Fractions Factor and prime factor natural numbers Recognize special fraction forms Multiply and divide fractions Build equivalent fractions Simplify fractions Add and subtract fractions
Objectives Section 1.2 Fractions Factor and prime factor natural numbers Recognize special fraction forms Multiply and divide fractions Build equivalent fractions Simplify fractions Add and subtract fractions
Midterm 2 Solutions. CS70 Discrete Mathematics for Computer Science, Fall 2007
 CS70 Discrete Mathematics for Computer Science, Fall 007 Midterm Solutions Note: These solutions are not necessarily model answers Rather, they are designed to be tutorial in nature, and sometimes contain
CS70 Discrete Mathematics for Computer Science, Fall 007 Midterm Solutions Note: These solutions are not necessarily model answers Rather, they are designed to be tutorial in nature, and sometimes contain
NodeId Verification Method against Routing Table Poisoning Attack in Chord DHT
 NodeId Verification Method against Routing Table Poisoning Attack in Chord DHT 1 Avinash Chaudhari, 2 Pradeep Gamit 1 L.D. College of Engineering, Information Technology, Ahmedabad India 1 Chaudhari.avi4u@gmail.com,
NodeId Verification Method against Routing Table Poisoning Attack in Chord DHT 1 Avinash Chaudhari, 2 Pradeep Gamit 1 L.D. College of Engineering, Information Technology, Ahmedabad India 1 Chaudhari.avi4u@gmail.com,
Introduction to Machine Learning
 Introduction to Machine Learning Decision Tree Example Three variables: Attribute 1: Hair = {blond, dark} Attribute 2: Height = {tall, short} Class: Country = {Gromland, Polvia} CS4375 --- Fall 2018 a
Introduction to Machine Learning Decision Tree Example Three variables: Attribute 1: Hair = {blond, dark} Attribute 2: Height = {tall, short} Class: Country = {Gromland, Polvia} CS4375 --- Fall 2018 a
Enhancing Forecasting Performance of Naïve-Bayes Classifiers with Discretization Techniques
 24 Enhancing Forecasting Performance of Naïve-Bayes Classifiers with Discretization Techniques Enhancing Forecasting Performance of Naïve-Bayes Classifiers with Discretization Techniques Ruxandra PETRE
24 Enhancing Forecasting Performance of Naïve-Bayes Classifiers with Discretization Techniques Enhancing Forecasting Performance of Naïve-Bayes Classifiers with Discretization Techniques Ruxandra PETRE
Rank Measures for Ordering
 Rank Measures for Ordering Jin Huang and Charles X. Ling Department of Computer Science The University of Western Ontario London, Ontario, Canada N6A 5B7 email: fjhuang33, clingg@csd.uwo.ca Abstract. Many
Rank Measures for Ordering Jin Huang and Charles X. Ling Department of Computer Science The University of Western Ontario London, Ontario, Canada N6A 5B7 email: fjhuang33, clingg@csd.uwo.ca Abstract. Many
THE SECOND GENERATION ONION ROUTER. Roger Dingledine Nick Mathewson Paul Syverson. -Presented by Arindam Paul
 THE SECOND GENERATION ONION ROUTER Roger Dingledine Nick Mathewson Paul Syverson 1 -Presented by Arindam Paul Menu Motivation: Why do we need Onion Routing? Introduction : What is TOR? Basic TOR Design
THE SECOND GENERATION ONION ROUTER Roger Dingledine Nick Mathewson Paul Syverson 1 -Presented by Arindam Paul Menu Motivation: Why do we need Onion Routing? Introduction : What is TOR? Basic TOR Design
Numerical & Proportional Reasoning: Place Value Patterns & Equivalent Forms Kindergarten Grade 2 Grades 3-5
 Numerical & Proportional Reasoning: Place Value Patterns & Equivalent Forms 2.1 Numbers and words can be used to count and represent quantities or position. The position of a digit in any number determines
Numerical & Proportional Reasoning: Place Value Patterns & Equivalent Forms 2.1 Numbers and words can be used to count and represent quantities or position. The position of a digit in any number determines
From Passages into Elements in XML Retrieval
 From Passages into Elements in XML Retrieval Kelly Y. Itakura David R. Cheriton School of Computer Science, University of Waterloo 200 Univ. Ave. W. Waterloo, ON, Canada yitakura@cs.uwaterloo.ca Charles
From Passages into Elements in XML Retrieval Kelly Y. Itakura David R. Cheriton School of Computer Science, University of Waterloo 200 Univ. Ave. W. Waterloo, ON, Canada yitakura@cs.uwaterloo.ca Charles
Efficiency Optimisation Of Tor Using Diffie-Hellman Chain
 Efficiency Optimisation Of Tor Using Diffie-Hellman Chain Kun Peng Institute for Infocomm Research, Singapore dr.kun.peng@gmail.com Abstract Onion routing is the most common anonymous communication channel.
Efficiency Optimisation Of Tor Using Diffie-Hellman Chain Kun Peng Institute for Infocomm Research, Singapore dr.kun.peng@gmail.com Abstract Onion routing is the most common anonymous communication channel.
ExperimenTor: A Testbed for Safe and Realistic Tor Experimentation
 ExperimenTor: A Testbed for Safe and Realistic Tor Experimentation Kevin Bauer University of Waterloo k4bauer@cs.uwaterloo.ca Damon McCoy University of California, San Diego dlmccoy@cs.ucsd.edu Micah Sherr
ExperimenTor: A Testbed for Safe and Realistic Tor Experimentation Kevin Bauer University of Waterloo k4bauer@cs.uwaterloo.ca Damon McCoy University of California, San Diego dlmccoy@cs.ucsd.edu Micah Sherr
Lecture 1: Perfect Security
 CS 290G (Fall 2014) Introduction to Cryptography Oct 2nd, 2014 Instructor: Rachel Lin 1 Recap Lecture 1: Perfect Security Scribe: John Retterer-Moore Last class, we introduced modern cryptography and gave
CS 290G (Fall 2014) Introduction to Cryptography Oct 2nd, 2014 Instructor: Rachel Lin 1 Recap Lecture 1: Perfect Security Scribe: John Retterer-Moore Last class, we introduced modern cryptography and gave
Analyzing the Dual-Path Peer-to-Peer Anonymous Approach
 Analyzing the Dual-Path Peer-to-Peer Anonymous Approach Ehsan Saboori K.N Toosi University of Technology Tehran, Iran Majid Rafigh Shahid Beheshti University (Former National University) Tehran, Iran Alireza
Analyzing the Dual-Path Peer-to-Peer Anonymous Approach Ehsan Saboori K.N Toosi University of Technology Tehran, Iran Majid Rafigh Shahid Beheshti University (Former National University) Tehran, Iran Alireza
Two-dimensional Totalistic Code 52
 Two-dimensional Totalistic Code 52 Todd Rowland Senior Research Associate, Wolfram Research, Inc. 100 Trade Center Drive, Champaign, IL The totalistic two-dimensional cellular automaton code 52 is capable
Two-dimensional Totalistic Code 52 Todd Rowland Senior Research Associate, Wolfram Research, Inc. 100 Trade Center Drive, Champaign, IL The totalistic two-dimensional cellular automaton code 52 is capable
Location Traceability of Users in Location-based Services
 Location Traceability of Users in Location-based Services Yutaka Yanagisawa Hidetoshi Kido Tetsuji Satoh, NTT Communication Science Laboratories, NTT Corporation Graduate School of Information Science
Location Traceability of Users in Location-based Services Yutaka Yanagisawa Hidetoshi Kido Tetsuji Satoh, NTT Communication Science Laboratories, NTT Corporation Graduate School of Information Science
gpath: A Game-Theoretic Path Selection Algorithm to Protect Tor s Anonymity
 gpath: A Game-Theoretic Path Selection Algorithm to Protect Tor s Anonymity Nan Zhang 1,WeiYu 2,XinwenFu 3,andSajalK.Das 4 1 George Washington University nzhang10@gwu.edu 2 Towson University wyu@towson.edu
gpath: A Game-Theoretic Path Selection Algorithm to Protect Tor s Anonymity Nan Zhang 1,WeiYu 2,XinwenFu 3,andSajalK.Das 4 1 George Washington University nzhang10@gwu.edu 2 Towson University wyu@towson.edu
CS268: Beyond TCP Congestion Control
 TCP Problems CS68: Beyond TCP Congestion Control Ion Stoica February 9, 004 When TCP congestion control was originally designed in 1988: - Key applications: FTP, E-mail - Maximum link bandwidth: 10Mb/s
TCP Problems CS68: Beyond TCP Congestion Control Ion Stoica February 9, 004 When TCP congestion control was originally designed in 1988: - Key applications: FTP, E-mail - Maximum link bandwidth: 10Mb/s
Introduction to Traffic Analysis. George Danezis University of Cambridge, Computer Laboratory
 Introduction to Traffic Analysis George Danezis University of Cambridge, Computer Laboratory Outline Introduction to anonymous communications Macro-level Traffic Analysis Micro-level Traffic Analysis P2P
Introduction to Traffic Analysis George Danezis University of Cambridge, Computer Laboratory Outline Introduction to anonymous communications Macro-level Traffic Analysis Micro-level Traffic Analysis P2P
Anonymity. Assumption: If we know IP address, we know identity
 03--4 Anonymity Some degree of anonymity from using pseudonyms However, anonymity is always limited by address TCP will reveal your address address together with ISP cooperation Anonymity is broken We
03--4 Anonymity Some degree of anonymity from using pseudonyms However, anonymity is always limited by address TCP will reveal your address address together with ISP cooperation Anonymity is broken We
Passive-Logging Attacks Against Anonymous Communications Systems
 Passive-Logging Attacks Against Anonymous Communications Systems MATTHEW K. WRIGHT University of Texas at Arlington and MICAH ADLER and BRIAN NEIL LEVINE University of Massachusetts Amherst and CLAY SHIELDS
Passive-Logging Attacks Against Anonymous Communications Systems MATTHEW K. WRIGHT University of Texas at Arlington and MICAH ADLER and BRIAN NEIL LEVINE University of Massachusetts Amherst and CLAY SHIELDS
Anonymity With Tor. The Onion Router. July 21, Technische Universität München
 The Onion Router Nathan S. Evans Christian Grothoff Technische Universität München July 21, 2011 Overview What is Tor? Motivation Background Material How Tor Works Hidden Services Attacks Specific Attack
The Onion Router Nathan S. Evans Christian Grothoff Technische Universität München July 21, 2011 Overview What is Tor? Motivation Background Material How Tor Works Hidden Services Attacks Specific Attack
Measuring anonymity: a few thoughts and a differentially private bound
 Measuring anonymity: a few thoughts and a differentially private bound George Danezis 15 May 2013 1 Early Measures Measuring the quality of protection offered by security mechanisms, including anonymous
Measuring anonymity: a few thoughts and a differentially private bound George Danezis 15 May 2013 1 Early Measures Measuring the quality of protection offered by security mechanisms, including anonymous
Survey on Traffic Pattern Discovery System For MANETs
 Survey on Traffic Pattern Discovery System For MANETs Sanchali S. Pandhare 1 PG student, Department of Computer Science & engineering, Pankaj Laddhad Institute of Technology & Management Studies, Buldana.
Survey on Traffic Pattern Discovery System For MANETs Sanchali S. Pandhare 1 PG student, Department of Computer Science & engineering, Pankaj Laddhad Institute of Technology & Management Studies, Buldana.
3 No-Wait Job Shops with Variable Processing Times
 3 No-Wait Job Shops with Variable Processing Times In this chapter we assume that, on top of the classical no-wait job shop setting, we are given a set of processing times for each operation. We may select
3 No-Wait Job Shops with Variable Processing Times In this chapter we assume that, on top of the classical no-wait job shop setting, we are given a set of processing times for each operation. We may select
