GIOTTO. Design and Architecture
|
|
|
- Jeffery Robbins
- 5 years ago
- Views:
Transcription
1 GIOTTO Buildings form an essential part of our lives, and provide many services that make our indoor environment comfortable, productive and enjoyable. With advances in communication and computing, buildings are increasingly embedded with sensors and networked devices that enable a wide variety of services contextual services to occupants, monitoring of building infrastructure, and energy efficient operation. We have created Giotto as a successful IoT ecology. This includes a core building management middleware, an easy to use protocol agnostic API, robust security and privacy protectins, intergration of machine learning at multiple levels, to engage users with varying levels of experience. Our vision is to provide building users with a holistic view of the building across various different subsystems, such as lighting, water, air conditioning, and enable applications that work seamlessly across the underlying infrastructure. Giotto uses BuildingDepot, a prior building management system, as its core middleware and adds a number of other services. The following are the primary objectives of Giotto: Integration of data from a wide variety of building systems and communication protocols Provide an easy to use API that is protocol agnostic Provide a search interface to query building data and metadata Provide an access control system that facilitates security and privacy Provide support for actuation of building control systems Provide a middleware that scales with big data across multiple buildings Support for standardization to enable portable building applications Design and Architecture We have designed Giotto to incorporate a web service to support an easy to use RESTful API and leverage standard web service tools for scalability, modularity, maintainability and security. Giotto contains two types of web services: Central Service and Data Service. The Central Service hosts the building metadata information while the Data Service hosts the timeseries data. As an example, measurements from a building power meter will be stored in Data Service, and associated metadata such as location of meter and unit of measurement is hosted in Central Service. The Central Service also hosts user information, access control lists and structural information such as rooms and floors. A Giotto instance has only one Central Service that provides a uniform view of all the different systems across multiple buildings. The metadata in the Central Service provides the mapping between points and the corresponding Data Services where their timeseries is hosted. There
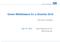
2 are no limits on the number of Data Services that can be associated with a Giotto instance. There could be one Data Service for each building, and even one Data Service per subsystem in a single building. Figure 1 shows the architecture of the core middleware of Giotto, BuildingDeport. Figure 1: Giotto MiddleWare System Architecture Giotto also contains a Machine Learning layer which allows for supervised machine learning. The machine learning layer communicates with the CentralService and appropriate DataService to train a classifier then can classify new input sensor data. This is all done without any manual feature extraction, training, or model tuning, allowing a novice end user to create example driven machine learning classifiers. Central Service We define any entity to which a timeseries can be associated with as a Point. A Point can be measurements from sensors, or commands to turn a light on/off, or a configuration parameter such as cycle type in a washing machine or even a fault indicator. This includes both real world sensors/actuators, as well as virtual sensors/actuators created in the Central Service as abstractions of RealWorld sensors/actuators (such as a building average temperature sensor ). Virtual and RealWorld points are treated identically within the CentralService, with differences occurring at the level of connectors (see Connectors document for interfacing between the
3 CentralService and sensors). In Giotto, each point is given a UUID (universally unique ID) and metadata is associated with it using tags. Tags are key value pairs associated with a point. For example, an office temperature sensor would be associated with tags like Room = 300, Type = Temperature Sensor, Unit = Fahrenheit and so on. Tags themselves can refer to complex entities and be associated with other tags. For example, Room 300 can be associated with its metadata such as area and 1 usage type. Tags form the core of Giotto metadata, and are used for searching and defining permissions. Giotto supports pre defined tag types that acts as a template for a user to start tagging entities in a building. These templates are provided to support standard naming convention, such as the 2 tags defined by Project Haystack. These tags are also used as the key search mechanism within Giotto. Using REST APIs, users can query for individual entities based on single tag (such as a Room = 300) or based on more complex combinations of tags (Room = 300 and Type = Occupancy and Building = Example_Building). All entities which meet the requirements of the search are returned as JSON objects which contain their UUID, tags, and Metadata. In addition to tags on entities, Giotto also utilizes context based tags for Users. Depending on how a user logs in (e.g. with or without admin privileges) they will have a context tag added to determine the privileges that they enjoy (user credentials). Users groups are created by assigning a user group tag to each user which is part of the group. This is of particular importance later when determining permissions. In addition to User Groups, Sensor groups are as the name suggests a set of points that have been grouped together on the basis of the tags that the user selected while creating the group. While creating a Sensor group each individual points that the user wants to put in the group do not have to be manually added. Simply selecting the tag will automatically add at the backend all the points containing that tag into this group. Sensor groups and User groups come together to form the access control lists. Access control lists are a key element in GioTTO to facilitate both privacy and security. For pairs of User Groups and Sensor Groups, we choose a permission value with which we want to associate. There are four levels of permission defined in Giotto which are d/r (deny read), r (read), r/w (read write) and r/w/p (read write permission). If there are multiple permission mappings between a user and a point then the one that is most restrictive is chosen. The deny read permission level, in particular, is important for maintaining privacy of data for various groups simultaneously using Giotto for a building. Levels permission access are as given below : 1 This feature is under development 2 Project Haystack. haystack.org/
4 d/r r r/w Deny read Will deny any access to the points Read Will give read only access to the points Read Write Will give read and write access to the points (such as changing values of actuators) r/w/p Read Write Permission Highest level of permission that can be assigned. Will give read and write access to the points. Permission additionally allows users to alter permissions for the points (see above). Ownership Defined at point creation. Has all privileges of r/w/p. Additionally, cannot be revoked or changed under any circumstances. Super or permanent R/W/P. When a r/w/p permission link is created between the UserGroup Home_usergroup and Sensor Group Home. All users in UserGroup get r/w/p access to points in SensorGroup. Any user can create any permission link that they want but the set of points that the users in the UserGroup get access to in the SensorGroup that they have been given permission to will depend on the user that has created the permission. Only the points that the creator of this permission has r/w/p access to will be the points that the users will gain access to based on this permission link. Data Service DataService stores point time series data points from the underlying point networks. The DataService manages the points and time series data points of points allocated to it. A DataService may belong to any single administrative group that requires sole control over who can access the underlying point data. Different buildings on a campus might desire their own DataService. Thus it is up to an institution to determine how many DataServices are needed depending on the specific groups that exist and their needs. DataService needs to query CentralService for user accounts, building tags and permission information. The communication is immensely frequent as almost every request to DataService needs user authentication and permission check. Therefore, only keeping a single CentralService would be a performance bottleneck. To resolve this issue, we set up the CentralService in a master slave mode. The master CentralService only accepts write requests and each of its replicas undertakes read requests from a single DataService. In this way, the request traffic load can be balanced on all replicas. Machine Learning The Machine Learning layer allows for supervised machine learning. A GIoTTO administrator or end user can provide a label to apply to all of the sensor time series available in a particular
5 location, for a particular segment in time. The machine learning layer communicates with the CentralService and appropriate DataService to train a classifier using these labels, and then can classify new input sensor data. This is all done without any manual feature extraction, training, or model tuning, allowing a novice end user to create example driven machine learning classifiers. Security Oauth: In order to access the GioTTO all users will first have to generate an OAuth Token using the Client ID and secret Client Key that they obtain from their account at the CentralService on GioTTO. Once logged into the CentralService users can go to the OAuth tab and generate a Client ID and Key that should never be shared with any other users. Once the Client ID and Key have been generated the user can request GioTTO for the access token. The access token will be valid for the next 24 hours after which another access token will have to be generated.the OAuth token should also never be shared publicly. HTTPS: HTTPS Ensures that communication with all Giotto services happens over encrypted connections.we Suggest using LetsEncrypt to generate the SSL Certificates,although we do provide option for using Self Signed Certificates. Access Control Layer Level of access granted to each user for a certain sensor is restricted through this layer based on permissions defined within Giotto middleware BuildingDepot. This is basically the permission levels that we discussed above. Performance: The performance of Giotto was benchmarked under the following conditions: Two Versions of Giotto using a uwsgi and nginx on a 1core/ 2GB VM 1000 clients were simulated to simultaneously send 1,000,000 requests to the service using apache benchmark
6 Example Applications Building Genie, a software thermostat, directly integrated with a building s HVAC system, is a recent example of an application using Giotto as its backend. Genie displays essential information required from a modern thermostat in a web app and supports features such as (i) the ability for occupants to send thermal feedback to building managers, (ii) an expanded level of temperature control, (iii) the ability to turn On/Off HVAC as needed, and (iv) estimates and displays the energy used by each thermal zone to building occupants. We deployed Genie in a 5 floor university building to study its real world usage by 220 users for 21 months. A paper on this application Genie: A Longitudinal Study Comparing Physical and Software Thermostats in Office Buildings was recently accepted to UBICOMP 2016 for more details. We also developed BuildingSherlock (BDSherlock), which is a web service based fault management framework that exposes building information to automatically detect faults using Giotto as its backend. Building faults can lead to large and unnecessary building operation costs (such as over heating or over cooling), and it is estimated that 5 20% of building energy costs are due to faults. We deployed BDSherlock in a sqft building at UC San Diego, successfully demonstrate faults using data driven analysis Getting Started with Giotto: We provide two additional documents with guidelines for how to set up and use Giotto. As mentioned previously, Giotto is a superset of BuildingDepot. Giotto uses BuildingDepot at its core and adds a number of other services. Our getting started guide applies towards getting the core BuildingDepot functionality running, as well as writing connectors to Giotto. For getting started with Giotto/BuildingDepot (Download/install/config): Uoopa _t0ynx6uo d2ibzglyk/edit?
7 usp=sharing For an example connector to Giotto/BuildingDepot See: Aqw5G361TXwSX 9gHA_bDsN9TV 1YlbctUJeFS2AjM/e dit?usp=sharing
Document Sub Title. Yotpo. Technical Overview 07/18/ Yotpo
 Document Sub Title Yotpo Technical Overview 07/18/2016 2015 Yotpo Contents Introduction... 3 Yotpo Architecture... 4 Yotpo Back Office (or B2B)... 4 Yotpo On-Site Presence... 4 Technologies... 5 Real-Time
Document Sub Title Yotpo Technical Overview 07/18/2016 2015 Yotpo Contents Introduction... 3 Yotpo Architecture... 4 Yotpo Back Office (or B2B)... 4 Yotpo On-Site Presence... 4 Technologies... 5 Real-Time
BuildingSherlock: Fault Management Framework for HVAC Systems in Commercial Buildings
 BuildingSherlock: Fault Management Framework for HVAC Systems in Commercial Buildings Hidetoshi Teraoka, Bharathan Balaji, Rizhen Zhang, Anthony Nwokafor, Balakrishnan Narayanaswamy, Yuvraj Agarwal University
BuildingSherlock: Fault Management Framework for HVAC Systems in Commercial Buildings Hidetoshi Teraoka, Bharathan Balaji, Rizhen Zhang, Anthony Nwokafor, Balakrishnan Narayanaswamy, Yuvraj Agarwal University
Virginia Tech Research Center Arlington, Virginia, USA
 SMART BUILDINGS AS BUILDING BLOCKS OF A SMART CITY Professor Saifur Rahman Virginia Tech Advanced Research Institute Electrical & Computer Engg Department University of Sarajevo Bosnia, 06 October, 2016
SMART BUILDINGS AS BUILDING BLOCKS OF A SMART CITY Professor Saifur Rahman Virginia Tech Advanced Research Institute Electrical & Computer Engg Department University of Sarajevo Bosnia, 06 October, 2016
Gmail Integration for Salesforce and Dynamics 365
 Gmail Integration for Salesforce and Dynamics 365 PRIVACY POLICY LAST MODIFIED: MARCH 12, 2019 2019 Introduction Welcome to Gmail Integration for Salesforce and Dynamics 365, a service provided by Akvelon,
Gmail Integration for Salesforce and Dynamics 365 PRIVACY POLICY LAST MODIFIED: MARCH 12, 2019 2019 Introduction Welcome to Gmail Integration for Salesforce and Dynamics 365, a service provided by Akvelon,
Alteryx Technical Overview
 Alteryx Technical Overview v 1.5, March 2017 2017 Alteryx, Inc. v1.5, March 2017 Page 1 Contents System Overview... 3 Alteryx Designer... 3 Alteryx Engine... 3 Alteryx Service... 5 Alteryx Scheduler...
Alteryx Technical Overview v 1.5, March 2017 2017 Alteryx, Inc. v1.5, March 2017 Page 1 Contents System Overview... 3 Alteryx Designer... 3 Alteryx Engine... 3 Alteryx Service... 5 Alteryx Scheduler...
Cloud FastPath: Highly Secure Data Transfer
 Cloud FastPath: Highly Secure Data Transfer Tervela helps companies move large volumes of sensitive data safely and securely over network distances great and small. Tervela has been creating high performance
Cloud FastPath: Highly Secure Data Transfer Tervela helps companies move large volumes of sensitive data safely and securely over network distances great and small. Tervela has been creating high performance
Libelium Cloud Hive. Technical Guide
 Libelium Cloud Hive Technical Guide Index Document version: v7.0-12/2018 Libelium Comunicaciones Distribuidas S.L. INDEX 1. General and information... 4 1.1. Introduction...4 1.1.1. Overview...4 1.2. Data
Libelium Cloud Hive Technical Guide Index Document version: v7.0-12/2018 Libelium Comunicaciones Distribuidas S.L. INDEX 1. General and information... 4 1.1. Introduction...4 1.1.1. Overview...4 1.2. Data
FUJITSU Cloud Service K5 - API Management Service Description
 FUJITSU Cloud Service K5 - API Management Service Description August 8, 2018 1. API Management Service Overview API Management Service is built on Apigee Edge, an integrated API platform product provided
FUJITSU Cloud Service K5 - API Management Service Description August 8, 2018 1. API Management Service Overview API Management Service is built on Apigee Edge, an integrated API platform product provided
FUJITSU Cloud Service K5 - API Management Service Description
 FUJITSU Cloud Service K5 - API Management Service Description March 22, 2018 1. API Management Service Overview API Management Service is built on Apigee Edge, an integrated API platform product provided
FUJITSU Cloud Service K5 - API Management Service Description March 22, 2018 1. API Management Service Overview API Management Service is built on Apigee Edge, an integrated API platform product provided
MarkLogic Server. MarkLogic Server on Microsoft Azure Guide. MarkLogic 9 January, 2018
 MarkLogic Server on Microsoft Azure Guide 1 MarkLogic 9 January, 2018 Last Revised: 9.0-4, January, 2018 2018 MarkLogic Corporation. MarkLogic and the MarkLogic logo are trademarks or registered trademarks
MarkLogic Server on Microsoft Azure Guide 1 MarkLogic 9 January, 2018 Last Revised: 9.0-4, January, 2018 2018 MarkLogic Corporation. MarkLogic and the MarkLogic logo are trademarks or registered trademarks
Security Overview of the BGI Online Platform
 WHITEPAPER 2015 BGI Online All rights reserved Version: Draft v3, April 2015 Security Overview of the BGI Online Platform Data security is, in general, a very important aspect in computing. We put extra
WHITEPAPER 2015 BGI Online All rights reserved Version: Draft v3, April 2015 Security Overview of the BGI Online Platform Data security is, in general, a very important aspect in computing. We put extra
A Survey of Context-Aware Mobile Computing Research
 A Survey of Context-Aware Mobile Computing Research Guanling Chen and David Kotz 2005.11. 14 Cho Jaekyu jkcho@mmlab.snu.ac.kr Contents 1 2 3 4 5 6 7 8 Introduction Definition of Context Context-Aware Computing
A Survey of Context-Aware Mobile Computing Research Guanling Chen and David Kotz 2005.11. 14 Cho Jaekyu jkcho@mmlab.snu.ac.kr Contents 1 2 3 4 5 6 7 8 Introduction Definition of Context Context-Aware Computing
Policy Manager for IBM WebSphere DataPower 8.0: Installation Guide
 Policy Manager for IBM WebSphere DataPower 8.0: Installation Guide Policy Manager for IBM WebSphere DataPower Install Guide AKANA_PMDP_Install_8.0 Copyright Copyright 2016 Akana, Inc. All rights reserved.
Policy Manager for IBM WebSphere DataPower 8.0: Installation Guide Policy Manager for IBM WebSphere DataPower Install Guide AKANA_PMDP_Install_8.0 Copyright Copyright 2016 Akana, Inc. All rights reserved.
RSA SecurID Implementation
 Partner Information Partner Name Website Product Name Barracuda Networks Version & Platform x60 Series Product Description Product Category Solution Summary www.barracudanetworks.com Product Information
Partner Information Partner Name Website Product Name Barracuda Networks Version & Platform x60 Series Product Description Product Category Solution Summary www.barracudanetworks.com Product Information
Simplifying Device and System Integration Specifications for Building Automation Systems
 Simplifying Device and System Integration Specifications for Building Automation Systems Ron Bernstein LonMark Chief Ambassador ron@lonmark.org LONMARK The Next Generation Greater system integration going
Simplifying Device and System Integration Specifications for Building Automation Systems Ron Bernstein LonMark Chief Ambassador ron@lonmark.org LONMARK The Next Generation Greater system integration going
Tutorial: Building the Services Ecosystem
 Tutorial: Building the Services Ecosystem GlobusWorld 2018 Steve Tuecke tuecke@globus.org What is a services ecosystem? Anybody can build services with secure REST APIs App Globus Transfer Your Service
Tutorial: Building the Services Ecosystem GlobusWorld 2018 Steve Tuecke tuecke@globus.org What is a services ecosystem? Anybody can build services with secure REST APIs App Globus Transfer Your Service
RELEASE NOTES. Sippo WebRTC Application Controller. Version December Last updated: September 2017
 RELEASE NOTES Sippo WebRTC Application Controller Last updated: September 2017 Version 3.1 - December 2017 It is been over a year, but Sippo is now a complete matured RTC framework. Not only is able to
RELEASE NOTES Sippo WebRTC Application Controller Last updated: September 2017 Version 3.1 - December 2017 It is been over a year, but Sippo is now a complete matured RTC framework. Not only is able to
VMware AirWatch Content Gateway Guide for Windows
 VMware AirWatch Content Gateway Guide for Windows AirWatch v9.1 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com. This product
VMware AirWatch Content Gateway Guide for Windows AirWatch v9.1 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com. This product
Integration Note OVERVIEW AND SUPPORTED FEATURES
 Manufacturer: Model Number(s): KNX Climate (Various) Minimum Core Module g! 5.4 Version: g! 6.2 Minimum for Fan Coil Climate Modes Document Revision Date: 10/8/2015 OVERVIEW AND SUPPORTED FEATURES Integration
Manufacturer: Model Number(s): KNX Climate (Various) Minimum Core Module g! 5.4 Version: g! 6.2 Minimum for Fan Coil Climate Modes Document Revision Date: 10/8/2015 OVERVIEW AND SUPPORTED FEATURES Integration
VMware AirWatch Content Gateway for Windows. VMware Workspace ONE UEM 1811 Unified Access Gateway
 VMware AirWatch Content Gateway for Windows VMware Workspace ONE UEM 1811 Unified Access Gateway You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware AirWatch Content Gateway for Windows VMware Workspace ONE UEM 1811 Unified Access Gateway You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Powerful Insights with Every Click. FixStream. Agentless Infrastructure Auto-Discovery for Modern IT Operations
 Powerful Insights with Every Click FixStream Agentless Infrastructure Auto-Discovery for Modern IT Operations The Challenge AIOps is a big shift from traditional ITOA platforms. ITOA was focused on data
Powerful Insights with Every Click FixStream Agentless Infrastructure Auto-Discovery for Modern IT Operations The Challenge AIOps is a big shift from traditional ITOA platforms. ITOA was focused on data
Echidna Concepts Guide
 Salt Group Concepts Guide Version 15.1 May 2015 2015 Salt Group Proprietary Limited. All rights reserved. Information in this document is subject to change without notice. The software described in this
Salt Group Concepts Guide Version 15.1 May 2015 2015 Salt Group Proprietary Limited. All rights reserved. Information in this document is subject to change without notice. The software described in this
What s New with VMware vcloud Director 8.0
 Feature Overview TECHNICAL WHITE PAPER Table of Contents What s New with VMware....3 Support for vsphere 6.0 and NSX 6.1.4....4 VMware vsphere 6.0 Support...4 VMware NSX 6.1.4 Support....4 Organization
Feature Overview TECHNICAL WHITE PAPER Table of Contents What s New with VMware....3 Support for vsphere 6.0 and NSX 6.1.4....4 VMware vsphere 6.0 Support...4 VMware NSX 6.1.4 Support....4 Organization
IBM Campaign Version-independent Integration with IBM Engage Version 1 Release 3.1 April 07, Integration Guide IBM
 IBM Campaign Version-independent Integration with IBM Engage Version 1 Release 3.1 April 07, 2017 Integration Guide IBM Note Before using this information and the product it supports, read the information
IBM Campaign Version-independent Integration with IBM Engage Version 1 Release 3.1 April 07, 2017 Integration Guide IBM Note Before using this information and the product it supports, read the information
Security Guide Zoom Video Communications Inc.
 Zoom unifies cloud video conferencing, simple online meetings, group messaging, and a softwaredefined conference room solution into one easy-to-use platform. Zoom offers the best video, audio, and wireless
Zoom unifies cloud video conferencing, simple online meetings, group messaging, and a softwaredefined conference room solution into one easy-to-use platform. Zoom offers the best video, audio, and wireless
Sentinet for Microsoft Azure SENTINET
 Sentinet for Microsoft Azure SENTINET Sentinet for Microsoft Azure 1 Contents Introduction... 2 Customer Benefits... 2 Deployment Topologies... 3 Cloud Deployment Model... 3 Hybrid Deployment Model...
Sentinet for Microsoft Azure SENTINET Sentinet for Microsoft Azure 1 Contents Introduction... 2 Customer Benefits... 2 Deployment Topologies... 3 Cloud Deployment Model... 3 Hybrid Deployment Model...
uick Start Guide 1. Install Oracle Java SE Development Kit (JDK) version or later or 1.7.* and set the JAVA_HOME environment variable.
 API Manager uick Start Guide WSO2 API Manager is a complete solution for publishing APIs, creating and managing a developer community, and for routing API traffic in a scalable manner. It leverages the
API Manager uick Start Guide WSO2 API Manager is a complete solution for publishing APIs, creating and managing a developer community, and for routing API traffic in a scalable manner. It leverages the
CPM. Quick Start Guide V2.4.0
 CPM Quick Start Guide V2.4.0 1 Content 1 Introduction... 3 Launching the instance... 3 CloudFormation... 3 CPM Server Instance Connectivity... 3 2 CPM Server Instance Configuration... 4 CPM Server Configuration...
CPM Quick Start Guide V2.4.0 1 Content 1 Introduction... 3 Launching the instance... 3 CloudFormation... 3 CPM Server Instance Connectivity... 3 2 CPM Server Instance Configuration... 4 CPM Server Configuration...
VMware AirWatch Content Gateway Guide for Windows
 VMware AirWatch Content Gateway Guide for Windows AirWatch v9.2 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com. This product
VMware AirWatch Content Gateway Guide for Windows AirWatch v9.2 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com. This product
Launch Smart Products With End-to-End Solutions You & Your Customers Can Trust
 Solution Brief: Launch Smart Products With End-to-End Solutions You & Your Customers Can Trust DeviceTone, our ready to run "connect, manage and enable" solution for product companies, makes secure connectivity,
Solution Brief: Launch Smart Products With End-to-End Solutions You & Your Customers Can Trust DeviceTone, our ready to run "connect, manage and enable" solution for product companies, makes secure connectivity,
Securing ArcGIS Server Services An Introduction
 2013 Esri International User Conference July 8 12, 2013 San Diego, California Technical Workshop Securing ArcGIS Server Services An Introduction David Cordes & Derek Law Esri - Redlands, CA Agenda Security
2013 Esri International User Conference July 8 12, 2013 San Diego, California Technical Workshop Securing ArcGIS Server Services An Introduction David Cordes & Derek Law Esri - Redlands, CA Agenda Security
Best Practices in Designing Cloud Storage based Archival solution Sreenidhi Iyangar & Jim Rice EMC Corporation
 Best Practices in Designing Cloud Storage based Archival solution Sreenidhi Iyangar & Jim Rice EMC Corporation Abstract Cloud storage facilitates the use case of digital archiving for long periods of time
Best Practices in Designing Cloud Storage based Archival solution Sreenidhi Iyangar & Jim Rice EMC Corporation Abstract Cloud storage facilitates the use case of digital archiving for long periods of time
Data Insight Feature Briefing Box Cloud Storage Support
 Data Insight Feature Briefing Box Cloud Storage Support This document is about the new Box Cloud Storage Support feature in Symantec Data Insight 5.0. If you have any feedback or questions about this document
Data Insight Feature Briefing Box Cloud Storage Support This document is about the new Box Cloud Storage Support feature in Symantec Data Insight 5.0. If you have any feedback or questions about this document
WHITE PAPER AIRWATCH SUPPORT FOR OFFICE 365
 WHITE PAPER AIRWATCH SUPPORT FOR OFFICE 365 Airwatch Support for Office 365 One of the most common questions being asked by many customers recently is How does AirWatch support Office 365? Customers often
WHITE PAPER AIRWATCH SUPPORT FOR OFFICE 365 Airwatch Support for Office 365 One of the most common questions being asked by many customers recently is How does AirWatch support Office 365? Customers often
Deploying OAuth with Cisco Collaboration Solution Release 12.0
 White Paper Deploying OAuth with Cisco Collaboration Solution Release 12.0 Authors: Bryan Morris, Kevin Roarty (Collaboration Technical Marketing) Last Updated: December 2017 This document describes the
White Paper Deploying OAuth with Cisco Collaboration Solution Release 12.0 Authors: Bryan Morris, Kevin Roarty (Collaboration Technical Marketing) Last Updated: December 2017 This document describes the
BIG-IP Access Policy Manager : Secure Web Gateway. Version 13.0
 BIG-IP Access Policy Manager : Secure Web Gateway Version 13.0 Table of Contents Table of Contents BIG-IP APM Secure Web Gateway Overview...9 About APM Secure Web Gateway... 9 About APM benefits for web
BIG-IP Access Policy Manager : Secure Web Gateway Version 13.0 Table of Contents Table of Contents BIG-IP APM Secure Web Gateway Overview...9 About APM Secure Web Gateway... 9 About APM benefits for web
Orchestrating an OpenStack* based IoT Smart Home
 Orchestrating an OpenStack* based IoT Smart Home Michael Kadera, John Geier, Dr. Yih Leong Sun Intel Open Source Technology Center 26th October, Wednesday, 17:55-18:35 *Other names and brands may be claimed
Orchestrating an OpenStack* based IoT Smart Home Michael Kadera, John Geier, Dr. Yih Leong Sun Intel Open Source Technology Center 26th October, Wednesday, 17:55-18:35 *Other names and brands may be claimed
VMware AirWatch Content Gateway Guide for Windows
 VMware AirWatch Content Gateway Guide for Windows AirWatch v9.3 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com. This product
VMware AirWatch Content Gateway Guide for Windows AirWatch v9.3 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com. This product
Solutions Business Manager Web Application Security Assessment
 White Paper Solutions Business Manager Solutions Business Manager 11.3.1 Web Application Security Assessment Table of Contents Micro Focus Takes Security Seriously... 1 Solutions Business Manager Security
White Paper Solutions Business Manager Solutions Business Manager 11.3.1 Web Application Security Assessment Table of Contents Micro Focus Takes Security Seriously... 1 Solutions Business Manager Security
FIREFLY ARCHITECTURE: CO-BROWSING AT SCALE FOR THE ENTERPRISE
 FIREFLY ARCHITECTURE: CO-BROWSING AT SCALE FOR THE ENTERPRISE Table of Contents Introduction... 2 Architecture Overview... 2 Supported Browser Versions and Technologies... 3 Firewalls and Login Sessions...
FIREFLY ARCHITECTURE: CO-BROWSING AT SCALE FOR THE ENTERPRISE Table of Contents Introduction... 2 Architecture Overview... 2 Supported Browser Versions and Technologies... 3 Firewalls and Login Sessions...
This paper introduces the security policies, practices, and procedures of Lucidchart.
 Lucidchart Security Abstract This paper introduces the security policies, practices, and procedures of Lucidchart. The paper lays out the architecture security of this software-as-a-service product. It
Lucidchart Security Abstract This paper introduces the security policies, practices, and procedures of Lucidchart. The paper lays out the architecture security of this software-as-a-service product. It
Data Governance Overview
 3 Data Governance Overview Date of Publish: 2018-04-01 http://docs.hortonworks.com Contents Apache Atlas Overview...3 Apache Atlas features...3...4 Apache Atlas Overview Apache Atlas Overview Apache Atlas
3 Data Governance Overview Date of Publish: 2018-04-01 http://docs.hortonworks.com Contents Apache Atlas Overview...3 Apache Atlas features...3...4 Apache Atlas Overview Apache Atlas Overview Apache Atlas
VMware AirWatch Content Gateway Guide for Windows
 VMware AirWatch Content Gateway Guide for Windows Workspace ONE UEM v1810 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
VMware AirWatch Content Gateway Guide for Windows Workspace ONE UEM v1810 Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
Microsoft Architecting Microsoft Azure Solutions.
 Microsoft 70-535 Architecting Microsoft Azure Solutions https://killexams.com/pass4sure/exam-detail/70-535 QUESTION: 106 Your organization has developed and deployed several Azure App Service Web and API
Microsoft 70-535 Architecting Microsoft Azure Solutions https://killexams.com/pass4sure/exam-detail/70-535 QUESTION: 106 Your organization has developed and deployed several Azure App Service Web and API
VMware Integrated OpenStack Quick Start Guide
 VMware Integrated OpenStack Quick Start Guide VMware Integrated OpenStack 1.0.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
VMware Integrated OpenStack Quick Start Guide VMware Integrated OpenStack 1.0.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
Boundary control : Access Controls: An access control mechanism processes users request for resources in three steps: Identification:
 Application control : Boundary control : Access Controls: These controls restrict use of computer system resources to authorized users, limit the actions authorized users can taker with these resources,
Application control : Boundary control : Access Controls: These controls restrict use of computer system resources to authorized users, limit the actions authorized users can taker with these resources,
O365 Solutions. Three Phase Approach. Page 1 34
 O365 Solutions Three Phase Approach msfttechteam@f5.com Page 1 34 Contents Use Cases... 2 Use Case One Advanced Traffic Management for WAP and ADFS farms... 2 Use Case Two BIG-IP with ADFS-PIP... 3 Phase
O365 Solutions Three Phase Approach msfttechteam@f5.com Page 1 34 Contents Use Cases... 2 Use Case One Advanced Traffic Management for WAP and ADFS farms... 2 Use Case Two BIG-IP with ADFS-PIP... 3 Phase
Partner Center: Secure application model
 Partner Center: Secure application model The information provided in this document is provided "as is" without warranty of any kind. Microsoft disclaims all warranties, either express or implied, including
Partner Center: Secure application model The information provided in this document is provided "as is" without warranty of any kind. Microsoft disclaims all warranties, either express or implied, including
OpenIAM Identity and Access Manager Technical Architecture Overview
 OpenIAM Identity and Access Manager Technical Architecture Overview Overview... 3 Architecture... 3 Common Use Case Description... 3 Identity and Access Middleware... 5 Enterprise Service Bus (ESB)...
OpenIAM Identity and Access Manager Technical Architecture Overview Overview... 3 Architecture... 3 Common Use Case Description... 3 Identity and Access Middleware... 5 Enterprise Service Bus (ESB)...
OCCUPANCY TRACKING: Your Secret Source of Savings
 OCCUPANCY TRACKING: Your Secret Source of Savings Drivers of Smart Building Transformation Energy Mandates Efficiency Cost Savings 30% ($60B of $200B) US Energy wastage on C&I Buildings LED Transition,
OCCUPANCY TRACKING: Your Secret Source of Savings Drivers of Smart Building Transformation Energy Mandates Efficiency Cost Savings 30% ($60B of $200B) US Energy wastage on C&I Buildings LED Transition,
Developing with the Cloud
 Developing with the Cloud Aben Kovoor Developer & Platform Group Microsoft Corporation Middle East & Africa Developer & Platform Group SESSION GOALS A brief overview of the history and our customer challenges
Developing with the Cloud Aben Kovoor Developer & Platform Group Microsoft Corporation Middle East & Africa Developer & Platform Group SESSION GOALS A brief overview of the history and our customer challenges
Introduction. Overview of HCM. HCM Dashboard CHAPTER
 CHAPTER 1 This chapter describes the Hosted Collaboration Mediation (HCM) software. It includes: Overview of HCM, page 1-1 Terminology Used in HCM, page 1-2 HCM Dashboard Architecture, page 1-3 Starting
CHAPTER 1 This chapter describes the Hosted Collaboration Mediation (HCM) software. It includes: Overview of HCM, page 1-1 Terminology Used in HCM, page 1-2 HCM Dashboard Architecture, page 1-3 Starting
70-487: Developing Windows Azure and Web Services
 70-487: Developing Windows Azure and Web Services Candidates for this certification are professional developers that use Visual Studio 2015112017 11 and the Microsoft.NET Core Framework 4.5 to design and
70-487: Developing Windows Azure and Web Services Candidates for this certification are professional developers that use Visual Studio 2015112017 11 and the Microsoft.NET Core Framework 4.5 to design and
DIGIPASS Authentication for Cisco ASA 5500 Series
 DIGIPASS Authentication for Cisco ASA 5500 Series With Vasco VACMAN Middleware 3.0 2008 VASCO Data Security. All rights reserved. Page 1 of 35 Integration Guideline Disclaimer Disclaimer of Warranties
DIGIPASS Authentication for Cisco ASA 5500 Series With Vasco VACMAN Middleware 3.0 2008 VASCO Data Security. All rights reserved. Page 1 of 35 Integration Guideline Disclaimer Disclaimer of Warranties
DreamFactory Security Guide
 DreamFactory Security Guide This white paper is designed to provide security information about DreamFactory. The sections below discuss the inherently secure characteristics of the platform and the explicit
DreamFactory Security Guide This white paper is designed to provide security information about DreamFactory. The sections below discuss the inherently secure characteristics of the platform and the explicit
Coveo Platform 7.0. Yammer Connector Guide
 Coveo Platform 7.0 Yammer Connector Guide Notice The content in this document represents the current view of Coveo as of the date of publication. Because Coveo continually responds to changing market conditions,
Coveo Platform 7.0 Yammer Connector Guide Notice The content in this document represents the current view of Coveo as of the date of publication. Because Coveo continually responds to changing market conditions,
VMware Identity Manager Connector Installation and Configuration (Legacy Mode)
 VMware Identity Manager Connector Installation and Configuration (Legacy Mode) VMware Identity Manager This document supports the version of each product listed and supports all subsequent versions until
VMware Identity Manager Connector Installation and Configuration (Legacy Mode) VMware Identity Manager This document supports the version of each product listed and supports all subsequent versions until
Oracle Mission Critical Support Platform. General. Installation. Troubleshooting. Inventory and Discovery. Frequently Asked Questions Release 2.
 Oracle Mission Critical Support Platform Frequently Asked Questions Release 2.3 E23199-01 May 2011 General What is Oracle Mission Critical Support Platform? Is Oracle Mission Critical Support Platform
Oracle Mission Critical Support Platform Frequently Asked Questions Release 2.3 E23199-01 May 2011 General What is Oracle Mission Critical Support Platform? Is Oracle Mission Critical Support Platform
PowerExchange for Facebook: How to Configure Open Authentication using the OAuth Utility
 PowerExchange for Facebook: How to Configure Open Authentication using the OAuth Utility 2013 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means
PowerExchange for Facebook: How to Configure Open Authentication using the OAuth Utility 2013 Informatica Corporation. No part of this document may be reproduced or transmitted in any form, by any means
Single Sign-On for PCF. User's Guide
 Single Sign-On for PCF Version 1.2 User's Guide 2018 Pivotal Software, Inc. Table of Contents Table of Contents Single Sign-On Overview Installation Getting Started with Single Sign-On Manage Service Plans
Single Sign-On for PCF Version 1.2 User's Guide 2018 Pivotal Software, Inc. Table of Contents Table of Contents Single Sign-On Overview Installation Getting Started with Single Sign-On Manage Service Plans
Smart Buildings and Connected Lighting: The Perfect Partnership. February, 2018
 Smart Buildings and Connected Lighting: The Perfect Partnership February, 2018 1 Who I Am John O Connell Director of End User Systems & Services Office & Industry 2 2 Businesses in North America could
Smart Buildings and Connected Lighting: The Perfect Partnership February, 2018 1 Who I Am John O Connell Director of End User Systems & Services Office & Industry 2 2 Businesses in North America could
WHAT IS THE DIGI-RTU South 59 th Street Omaha, NE bes-tech.net
 WHAT IS THE DIGI-RTU The Digi-RTU is a Heating, Ventilation, and Air Conditioning (HVAC) rooftop unit control kit that is both a demand management and energy usage device. It is designed to improve the
WHAT IS THE DIGI-RTU The Digi-RTU is a Heating, Ventilation, and Air Conditioning (HVAC) rooftop unit control kit that is both a demand management and energy usage device. It is designed to improve the
DIGIPASS Authentication for Check Point VPN-1
 DIGIPASS Authentication for Check Point VPN-1 With Vasco VACMAN Middleware 3.0 2007 Integration VASCO Data Security. Guideline All rights reserved. Page 1 of 51 Disclaimer Disclaimer of Warranties and
DIGIPASS Authentication for Check Point VPN-1 With Vasco VACMAN Middleware 3.0 2007 Integration VASCO Data Security. Guideline All rights reserved. Page 1 of 51 Disclaimer Disclaimer of Warranties and
Mobility best practice. Tiered Access at Google
 Mobility best practice Tiered Access at Google How can IT leaders enable the productivity of employees while also protecting and securing corporate data? IT environments today pose many challenges - more
Mobility best practice Tiered Access at Google How can IT leaders enable the productivity of employees while also protecting and securing corporate data? IT environments today pose many challenges - more
RESTful API Design APIs your consumers will love
 RESTful API Design APIs your consumers will love Matthias Biehl RESTful API Design Copyright 2016 by Matthias Biehl All rights reserved, including the right to reproduce this book or portions thereof in
RESTful API Design APIs your consumers will love Matthias Biehl RESTful API Design Copyright 2016 by Matthias Biehl All rights reserved, including the right to reproduce this book or portions thereof in
20489: Developing Microsoft SharePoint Server 2013 Advanced Solutions
 20489: Developing Microsoft SharePoint Server 2013 Advanced Solutions Length: 5 days Audience: Developers Level: 300 OVERVIEW This course provides SharePoint developers the information needed to implement
20489: Developing Microsoft SharePoint Server 2013 Advanced Solutions Length: 5 days Audience: Developers Level: 300 OVERVIEW This course provides SharePoint developers the information needed to implement
Green Middleware for a Smarter Grid
 Green Middleware for a Smarter Grid Hans-Arno Jacobsen July 13 th, 2012 https://msrg.in.tum.de http://msrg.org Our Smart Grid System Vision Smart grid storage: multiple big data repositories for specifications,
Green Middleware for a Smarter Grid Hans-Arno Jacobsen July 13 th, 2012 https://msrg.in.tum.de http://msrg.org Our Smart Grid System Vision Smart grid storage: multiple big data repositories for specifications,
2.4. Target Audience This document is intended to be read by technical staff involved in the procurement of externally hosted solutions for Diageo.
 Diageo Third Party Hosting Standard 1. Purpose This document is for technical staff involved in the provision of externally hosted solutions for Diageo. This document defines the requirements that third
Diageo Third Party Hosting Standard 1. Purpose This document is for technical staff involved in the provision of externally hosted solutions for Diageo. This document defines the requirements that third
VMware AirWatch Content Gateway for Linux. VMware Workspace ONE UEM 1811 Unified Access Gateway
 VMware AirWatch Content Gateway for Linux VMware Workspace ONE UEM 1811 Unified Access Gateway You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
VMware AirWatch Content Gateway for Linux VMware Workspace ONE UEM 1811 Unified Access Gateway You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
WHITEPAPER. Security overview. podio.com
 WHITEPAPER Security overview Podio security White Paper 2 Podio, a cloud service brought to you by Citrix, provides a secure collaborative work platform for team and project management. Podio features
WHITEPAPER Security overview Podio security White Paper 2 Podio, a cloud service brought to you by Citrix, provides a secure collaborative work platform for team and project management. Podio features
ARCHITECTURE GUIDE. Campaign Manager 6.0
 ARCHITECTURE GUIDE Campaign Manager 6.0 VERSION CONTROL Version Date Author Changes 1.0 28 April 2017 D Cooper Release RELATED DOCUMENTS The related documents are located in the Alterian product help.
ARCHITECTURE GUIDE Campaign Manager 6.0 VERSION CONTROL Version Date Author Changes 1.0 28 April 2017 D Cooper Release RELATED DOCUMENTS The related documents are located in the Alterian product help.
Flex Tenancy :48:27 UTC Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement
 Flex Tenancy 2015-04-28 17:48:27 UTC 2015 Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement Contents Flex Tenancy... 3 Flex Tenancy... 4 Understanding the Flex Tenancy
Flex Tenancy 2015-04-28 17:48:27 UTC 2015 Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement Contents Flex Tenancy... 3 Flex Tenancy... 4 Understanding the Flex Tenancy
Remote power and console management in large datacenters
 Remote power and console management in large datacenters A Horváth IT department, CERN, CH-1211 Genève 23, Switzerland E-mail: Andras.Horvath@cern.ch Abstract. Today s datacenters are often built of a
Remote power and console management in large datacenters A Horváth IT department, CERN, CH-1211 Genève 23, Switzerland E-mail: Andras.Horvath@cern.ch Abstract. Today s datacenters are often built of a
Axway Validation Authority Suite
 Axway Validation Authority Suite PKI safeguards for secure applications Around the world, banks, healthcare organizations, governments, and defense agencies rely on public key infrastructures (PKIs) to
Axway Validation Authority Suite PKI safeguards for secure applications Around the world, banks, healthcare organizations, governments, and defense agencies rely on public key infrastructures (PKIs) to
Installing and Configuring vcenter Support Assistant
 Installing and Configuring vcenter Support Assistant vcenter Support Assistant 6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
Installing and Configuring vcenter Support Assistant vcenter Support Assistant 6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced
Red Hat OpenStack Platform 10 Product Guide
 Red Hat OpenStack Platform 10 Product Guide Overview of Red Hat OpenStack Platform OpenStack Team Red Hat OpenStack Platform 10 Product Guide Overview of Red Hat OpenStack Platform OpenStack Team rhos-docs@redhat.com
Red Hat OpenStack Platform 10 Product Guide Overview of Red Hat OpenStack Platform OpenStack Team Red Hat OpenStack Platform 10 Product Guide Overview of Red Hat OpenStack Platform OpenStack Team rhos-docs@redhat.com
ThoughtSpot on AWS Quick Start Guide
 ThoughtSpot on AWS Quick Start Guide Version 4.2 February 2017 Table of Contents Contents Chapter 1: Welcome to ThoughtSpot...3 Contact ThoughtSpot... 4 Chapter 2: Introduction... 6 About AWS...7 Chapter
ThoughtSpot on AWS Quick Start Guide Version 4.2 February 2017 Table of Contents Contents Chapter 1: Welcome to ThoughtSpot...3 Contact ThoughtSpot... 4 Chapter 2: Introduction... 6 About AWS...7 Chapter
Yanzi IoT for Smart Buildings From Sensor to Cloud. Marie Lassborn, VP Cloud Operations Jfokus 2018
 Yanzi IoT for Smart Buildings From Sensor to Cloud Marie Lassborn, VP Cloud Operations Jfokus 2018 1 WHAT IS YANZI? Analytics Conversions Storage Cloud Visualizations An IoT Solution for Smart Office Headquarter
Yanzi IoT for Smart Buildings From Sensor to Cloud Marie Lassborn, VP Cloud Operations Jfokus 2018 1 WHAT IS YANZI? Analytics Conversions Storage Cloud Visualizations An IoT Solution for Smart Office Headquarter
IMPLEMENTATION POLICY AND PROCEDURES FOR SECURING NETWORKED DEVICES
 UNIVERSITY OF CALIFORNIA, BERKELEY BERKELEY DAVIS IRVINE LOS ANGELES RIVERSIDE SAN DIEGO SAN FRANCISCO SANTA BARBARA SANTA CRUZ ECONOMETRICS LABORATORY Institute of Business and Economic Research ECONOMETRICS
UNIVERSITY OF CALIFORNIA, BERKELEY BERKELEY DAVIS IRVINE LOS ANGELES RIVERSIDE SAN DIEGO SAN FRANCISCO SANTA BARBARA SANTA CRUZ ECONOMETRICS LABORATORY Institute of Business and Economic Research ECONOMETRICS
Top 7 Data API Headaches (and How to Handle Them) Jeff Reser Data Connectivity & Integration Progress Software
 Top 7 Data API Headaches (and How to Handle Them) Jeff Reser Data Connectivity & Integration Progress Software jreser@progress.com Agenda Data Variety (Cloud and Enterprise) ABL ODBC Bridge Using Progress
Top 7 Data API Headaches (and How to Handle Them) Jeff Reser Data Connectivity & Integration Progress Software jreser@progress.com Agenda Data Variety (Cloud and Enterprise) ABL ODBC Bridge Using Progress
Inland Revenue. Build Pack. Identity and Access Services. Date: 04/09/2017 Version: 1.5 IN CONFIDENCE
 Inland Revenue Build Pack Identity and Access Services Date: 04/09/2017 Version: 1.5 IN CONFIDENCE About this Document This document is intended to provide Service Providers with the technical detail required
Inland Revenue Build Pack Identity and Access Services Date: 04/09/2017 Version: 1.5 IN CONFIDENCE About this Document This document is intended to provide Service Providers with the technical detail required
Vblock Infrastructure Packages: Accelerating Deployment of the Private Cloud
 Vblock Infrastructure Packages: Accelerating Deployment of the Private Cloud Roberto Missana - Channel Product Sales Specialist Data Center, Cisco 1 IT is undergoing a transformation Enterprise IT solutions
Vblock Infrastructure Packages: Accelerating Deployment of the Private Cloud Roberto Missana - Channel Product Sales Specialist Data Center, Cisco 1 IT is undergoing a transformation Enterprise IT solutions
Energy Action Plan 2015
 Energy Action Plan 2015 Purpose: In support of the Texas A&M University Vision 2020: Creating a Culture of Excellence and Action 2015: Education First Strategic Plan, the Energy Action Plan (EAP) 2015
Energy Action Plan 2015 Purpose: In support of the Texas A&M University Vision 2020: Creating a Culture of Excellence and Action 2015: Education First Strategic Plan, the Energy Action Plan (EAP) 2015
CA IT Client Manager / CA Unicenter Desktop and Server Management
 CA GREEN BOOKS CA IT Client Manager / CA Unicenter Desktop and Server Management Object Level Security Best Practices LEGAL NOTICE This publication is based on current information and resource allocations
CA GREEN BOOKS CA IT Client Manager / CA Unicenter Desktop and Server Management Object Level Security Best Practices LEGAL NOTICE This publication is based on current information and resource allocations
Deploying Liferay Digital Experience Platform in Amazon Web Services
 Deploying Liferay Digital Experience Platform in Amazon Web Services Table of Contents Introduction................................. 1 Reference Architecture........................ 1 Overview..................................
Deploying Liferay Digital Experience Platform in Amazon Web Services Table of Contents Introduction................................. 1 Reference Architecture........................ 1 Overview..................................
OpenNebula on VMware: Cloud Reference Architecture
 OpenNebula on VMware: Cloud Reference Architecture Version 1.2, October 2016 Abstract The OpenNebula Cloud Reference Architecture is a blueprint to guide IT architects, consultants, administrators and
OpenNebula on VMware: Cloud Reference Architecture Version 1.2, October 2016 Abstract The OpenNebula Cloud Reference Architecture is a blueprint to guide IT architects, consultants, administrators and
How Big Data Analytics Helps Hotels Improve Maintenance and Comfort, and Save Energy
 How Big Data Analytics Helps Hotels Improve Maintenance and Comfort, and Save Energy Critical facility management drivers are impacting all industries Sustainability Big Data/Cloud Open Building Systems
How Big Data Analytics Helps Hotels Improve Maintenance and Comfort, and Save Energy Critical facility management drivers are impacting all industries Sustainability Big Data/Cloud Open Building Systems
On the Creation & Discovery of Topics in Distributed Publish/Subscribe systems
 On the Creation & Discovery of Topics in Distributed Publish/Subscribe systems Shrideep Pallickara, Geoffrey Fox & Harshawardhan Gadgil Community Grids Lab, Indiana University 1 Messaging Systems Messaging
On the Creation & Discovery of Topics in Distributed Publish/Subscribe systems Shrideep Pallickara, Geoffrey Fox & Harshawardhan Gadgil Community Grids Lab, Indiana University 1 Messaging Systems Messaging
ClarityNow Best Practices Guide
 ClarityNow Best Practices Guide Abstract A guide containing ClarityNow best practices and recommendations for common deployment to help avoid difficulties. Document includes descriptions of some default
ClarityNow Best Practices Guide Abstract A guide containing ClarityNow best practices and recommendations for common deployment to help avoid difficulties. Document includes descriptions of some default
August 2017 Welcome Design Topic Product Focus
 EngineeringAdvantage Newsletter August 2017 In This Issue: Welcome Design Topic Smart Buildings Product Focus Siemens Total Room Automation Welcome to Siemens EngineeringAdvantage Newsletter We hope you
EngineeringAdvantage Newsletter August 2017 In This Issue: Welcome Design Topic Smart Buildings Product Focus Siemens Total Room Automation Welcome to Siemens EngineeringAdvantage Newsletter We hope you
Implementing Project Haystack
 Implementing Project Haystack Applying Haystack Tagging for a sample building Introduction 1 Document Goals 1 Project Haystack Data Model 1 Background Reading 1 Core Data Model Concepts 2 Entities and
Implementing Project Haystack Applying Haystack Tagging for a sample building Introduction 1 Document Goals 1 Project Haystack Data Model 1 Background Reading 1 Core Data Model Concepts 2 Entities and
DIGIPASS Authentication for F5 BIG-IP
 DIGIPASS Authentication for F5 BIG-IP With VASCO VACMAN Middleware 3.0 2008 VASCO Data Security. All rights reserved. Page 1 of 37 Integration Guideline Disclaimer Disclaimer of Warranties and Limitations
DIGIPASS Authentication for F5 BIG-IP With VASCO VACMAN Middleware 3.0 2008 VASCO Data Security. All rights reserved. Page 1 of 37 Integration Guideline Disclaimer Disclaimer of Warranties and Limitations
vcloud Director Administrator's Guide vcloud Director 9.0
 vcloud Director 9.0 You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/ The VMware Web site also provides the latest product updates. If you have
vcloud Director 9.0 You can find the most up-to-date technical documentation on the VMware Web site at: https://docs.vmware.com/ The VMware Web site also provides the latest product updates. If you have
Zombie Apocalypse Workshop
 Zombie Apocalypse Workshop Building Serverless Microservices Danilo Poccia @danilop Paolo Latella @LatellaPaolo September 22 nd, 2016 2015, Amazon Web Services, Inc. or its Affiliates. All rights reserved.
Zombie Apocalypse Workshop Building Serverless Microservices Danilo Poccia @danilop Paolo Latella @LatellaPaolo September 22 nd, 2016 2015, Amazon Web Services, Inc. or its Affiliates. All rights reserved.
Technical Overview. Version March 2018 Author: Vittorio Bertola
 Technical Overview Version 1.2.3 26 March 2018 Author: Vittorio Bertola vittorio.bertola@open-xchange.com This document is copyrighted by its authors and is released under a CC-BY-ND-3.0 license, which
Technical Overview Version 1.2.3 26 March 2018 Author: Vittorio Bertola vittorio.bertola@open-xchange.com This document is copyrighted by its authors and is released under a CC-BY-ND-3.0 license, which
WORKSHARE HYBRID STORAGE INSTALLATION GUIDE
 WORKSHARE HYBRID STORAGE INSTALLATION GUIDE June 2017 COMPANY INFORMATION Workshare Hybrid Storage Installation Guide Workshare Ltd. (UK) 20 Fashion Street London E1 6PX UK Workshare Inc. (USA) 625 Market
WORKSHARE HYBRID STORAGE INSTALLATION GUIDE June 2017 COMPANY INFORMATION Workshare Hybrid Storage Installation Guide Workshare Ltd. (UK) 20 Fashion Street London E1 6PX UK Workshare Inc. (USA) 625 Market
X100 ARCHITECTURE REFERENCES:
 UNION SYSTEMS GLOBAL This guide is designed to provide you with an highlevel overview of some of the key points of the Oracle Fusion Middleware Forms Services architecture, a component of the Oracle Fusion
UNION SYSTEMS GLOBAL This guide is designed to provide you with an highlevel overview of some of the key points of the Oracle Fusion Middleware Forms Services architecture, a component of the Oracle Fusion
LiveEngage Messaging Platform: Security Overview Document Version: 2.0 July 2017
 LiveEngage Messaging Platform: Security Overview Document Version: 2.0 July 2017 Contents Introduction... 3 Supported Platforms... 3 Protecting Data in Transit... 3 Protecting Data at Rest... 3 Encryption...
LiveEngage Messaging Platform: Security Overview Document Version: 2.0 July 2017 Contents Introduction... 3 Supported Platforms... 3 Protecting Data in Transit... 3 Protecting Data at Rest... 3 Encryption...
SignalFx Platform: Security and Compliance MARZENA FULLER. Chief Security Officer
 SignalFx Platform: Security and Compliance MARZENA FULLER Chief Security Officer SignalFx Platform: Security and Compliance INTRODUCTION COMPLIANCE PROGRAM GENERAL DATA PROTECTION DATA SECURITY Data types
SignalFx Platform: Security and Compliance MARZENA FULLER Chief Security Officer SignalFx Platform: Security and Compliance INTRODUCTION COMPLIANCE PROGRAM GENERAL DATA PROTECTION DATA SECURITY Data types
Managing NCS User Accounts
 7 CHAPTER The Administration enables you to schedule tasks, administer accounts, and configure local and external authentication and authorization. Also, set logging options, configure mail servers, and
7 CHAPTER The Administration enables you to schedule tasks, administer accounts, and configure local and external authentication and authorization. Also, set logging options, configure mail servers, and
