Security Guide Zoom Video Communications Inc.
|
|
|
- Regina Watkins
- 6 years ago
- Views:
Transcription
1 Zoom unifies cloud video conferencing, simple online meetings, group messaging, and a softwaredefined conference room solution into one easy-to-use platform. Zoom offers the best video, audio, and wireless screen-sharing experience across Windows, Mac, Linux, ios, Android, Blackberry, Zoom Rooms, and H.323/SIP room systems. Zoom places security as the highest priority in the lifecycle operations of its public and hybrid cloud networks. Zoom strives to continually provide a robust set of security features to meet the requirements of businesses for safe and secure collaboration. The purpose of this document is to provide information on the security features and functions that are available with Zoom. The reader of this document is assumed to be familiar with Zoom functionalities related to meetings, webinars, and group messaging. Unless otherwise noted, the security features in this document apply across the product suite of Zoom Video Conferencing, Zoom Video Webinars, and Zoom Rooms, and across supported mobile, tablet, desktop, laptop, and H.323/SIP room system endpoints. Infrastructure The Zoom Cloud is a proprietary global network that has been built from the ground up to provide quality communication experiences. Zoom operates in a scalable hybrid mode; web services are hosted in the cloud and real time media is hosted out of tier-1 data centers. A distributed network of low-latency multimedia routers (software) resides on Zoom s communications infrastructure. With these low-latency multimedia routers, all session data originating from the host s device and arriving at the participants devices is dynamically switched never stored persistently through the Zoom communications infrastructure.
2 Zoom s communications infrastructure for real-time video, audio, and data communications resides on Zoom dedicated servers, which are housed in SSAE 16 SOC2 compliant datacenters on opposite sides of the US. Zoom sessions are completely temporary and operate analogously to the popular mobile conversation over the public mobile network. In addition to unique security benefits, Zoom s communications infrastructure also enables an extremely scalable and highly available meeting infrastructure unrestricted by the limitations of physical data centers. Firewall Compatibility The Zoom client communicates with the multimedia router to establish a reliable and secure connection. At the time of instantiation, the Zoom client will determine the best method for communication, attempting to connect automatically using udp and tcp port 8801, 8802 and 8804 or HTTPS (port 443/TLS). Client Application Role-based user security The following pre-meeting security capabilities are available to the meeting host: Enable end-to-end encrypted meeting Secure log-in using standard username and password or SAML Single Sign On Start a secured meeting with password Schedule secured meetings with password Selective meeting invitation: The host can selectively invite participants via , IM or SMS. This provides greater control over the distribution of the meeting access information. The host can also create the meeting to only allow members from a certain domain to join. Meeting Details Security: Zoom retains event details pertaining to a session for billing and reporting purposes. The event details are stored at the Zoom secured database and are available to customers for review on the customer portal page once they have securely logged-on. Application security: Zoom can encrypt all presentation content at the application layer using the Advanced Encryption Standard (AES) 256-bit algorithm. E2E Chat Encryption Zoom end-to-end (E2E) chat encryption allows for a secured communication where only the intended recipient can read the secured message. Zoom use public and private key to encrypt the chat session with Advance Encryption Standard (AES256). Session keys are generated with device unique hardware ID to avoid data being read from other devices. This ensures that the session can not be eavesdropped or tampered with. Meeting Security Role-based user security The following in-meeting security capabilities are available to the meeting host:
3 Secure a meeting with end-to-end encryption (E2E) Enable wait for host to join Expel a participant or all participants End a meeting Lock a meeting Chat with a participant or all participants Mute/Unmute a participant or all participants Enable/Disable a participant or all participants to record Temporary pause screen-sharing when a new window is opened The following in-meeting security capabilities are available to the meeting participants: Mute/Unmute audio Turn On/Off video Host and Client authenticated meeting: A host is required to authenticate (via https) to the Zoom site with their user credentials (ID and password) to start a meeting. Client authentication process uses a unique per-client, per-session token to confirm the identity of each participant attempting to join a meeting. Each session has a unique set of session parameters that are generated by Zoom. Each authenticated participant must have access to these session parameters in conjunction with the unique session token in order to successfully join the meeting. Open or password protected meeting: The host can require the participants to enter a password before joining the meeting. This provides greater access control and prevent uninvited guests from joining a meeting. Edit or delete meeting: The host can edit or delete an upcoming or previous meeting. This provides greater control over availability of meetings. Host controlled joining meeting: For greater control of meeting, the host can require participants to only join the meeting after the host has started it. For greater flexibility, the host can allow participants to join before the host. When joining before host, participants are restricted to a 30-minute meeting. In-meeting security: During the meeting, Zoom delivers real-time, rich-media content securely to each participant within a Zoom meeting. All content is shared with the participants in a meeting is only a representation of the original data. This content is encoded and optimized for sharing using a secured implementation as follows: Is the only means possible to join a Zoom meeting Is entirely dependent upon connections established on a session-by-session basis Performs a proprietary encoding process that encodes all shared data Can encrypt all screen sharing content using the AES 256 encryption standard Can encrypt the network connection to Zoom using 256-bit TLS encryption standard Provides a visual identification of every participant in the meeting
4 Secured Communications Zoom can secure all session content by encrypting the communications channel between the Zoom client and the multimedia router using a 256-bit Transport Layer Security (TLS) encryption tunnel. Host controlled joining meeting Authentication methods include Single Sign-on (SSO) with SAML or OAuth With SSO, a user logs-in once and gains access to multiple applications without being prompted to log-in again at each of them. Zoom supports SAML 2.0 which enables web-based authentication and authorization including single sign-on (SSO). SAML 2.0 is an XML-based protocol that uses security tokens containing assertions to pass information about a user between a SAML authority (an identity provider) and a web service (Zoom). Zoom works with Exchange ADFS 2.0 as well as Enterprise Identify Management such as PingOne, Okta, Centrify, Shibboleth, Gluu, OneLogin, Fugen, Symplified and many others. Zoom can map attributes to provision a user to different group with feature controls. Oauth based provisioning works with Google or Facebook OAuth for instant provisioning. Zoom also offers an API call to pre-provision user from any database backend. Additionally, your company/university can add users to your account automatically with Managed Domains. Once your Managed Domain application is approved, all existing and new users with your address domain will be added to your account. Administrative Controls The following security capabilities are available to the administrator: Secure login options using standard username and password or SAML Single Sign On. Add user and admin to account Upgrade or downgrade user subscription level Delete user from account Review billing and reports Manage account dashboard and cloud recordings Special Security Features/Options API A set of APIs is available for admins that are approved for use by Zoom. Each customer account managed by the admin will be given a pair of API key and passcode. The API calls are transmitted securely over secure web services and API authentication is required. Meeting Connector Zoom Meeting Connector is a hybrid cloud deployment method, which allows a customer to deploy Zoom multimedia router (software) within the company s internal network. User and meeting metadata are managed in Zoom communications infrastructure, but the meeting itself is hosted in customer s internal network. All real-time meeting traffic including audio, video and data sharing go through the company s internal network. This leverages your existing network
5 security setup to protect your meeting traffic. When customers choose a hybrid deployment, they have the option to segment by type of user where PRO and FREE (Basic) user type will use the cloud, and CORP user type will use the on-premise. If on-premise is offline, the meeting will automatically revert to use the cloud. Both our cloud and on-premise solutions are designed with failover and load balancing mechanisms when deployed. Zoom Rooms Zoom Rooms combines video conferencing, wireless content sharing, and integrated audio into one easy to use platform designed to work with Mac and ipad devices. Communications are established over secured network using 256-bits TLS encryption standard and all shared contents are encrypted using AES256 encryption standard. Zoom Rooms app is secured with App Lock Code. App Lock Code for Zoom Rooms is a required 1-16 digit numeric lock code that is use to secure your Zoom Room application. This prevents unauthorized changes to your Zoom Room application and settings on your ipad or Mac mini devices. Webinar Zoom webinar allows you to broadcast a Zoom meeting to up to 3000 view-only attendee and invite up to 25 panelists. Panelists are full participants in the meeting. They can view and send video, screen share, annotate, etc. Panelist invitation are sent separately from the Webinar attendee. Zoom Webinar contents and screensharing are secured using AES256 and communicate over secured network using 256-bit encryption standard. Registration Webinar Manually Approve Registration - The host of the Webinar will manually approve or decline whether a registrant receives the information to join the Webinar. Automatically Approve Registrants - All registrants to the Webinar will automatically receive information on how to join the Webinar Registration-less Webinar One-Time - Attendees will join the webinar only once. After the webinar ends, attendees will not be able to use the same information to join the Webinar Recurring - Attendees will be able to repeatedly join the same Webinar with the information provided. Recording Storage Zoom offers our customers the ability to record and share their meetings. Recordings can be stored on the local device with local recording option or on Zoom s cloud with Cloud Recording option. Cloud recordings are processed and securely stored in Zoom s cloud once the meeting has ended. The recordings are stored in both video/audio format and audio only format. Recording originator can manage their recordings through the secured web interface. Recordings can be download, share or deleted. Local recordings are stored locally on the recording originator s hard drive.
6 Privacy Zoom only stores basic information under user account profile information. address User password - salted hashed First Name Last Name Company Name Company Phone Number Profile Picture For more information about our privacy policy, visit Billing Details Zoom leverage a third-party, PCI compliant partner to process payment and handle all aspect of billing. We do not store any user credit card information or billing information in our database. Conclusion A growing number of businesses, small and large, use Zoom meeting services everyday. It is a high quality service for team meetings, sales interactions, marketing events, group mediation, product training, educational environments, and customer support. Zoom places privacy and security as the highest priority in the lifecycle operations of its communications infrastructure and meeting connector networks. In addition, Zoom strives to continually provide a robust set of security features to achieve its goal of providing the most efficient and secure real-time HD meeting service.
The Cloud Meeting Company
 The Cloud Meeting Company Cloud Meetings 2015 Cloud Meetings 1980 s 1990 s 2000 s Cloud Video Conferencing Telephone Conferencing Hardware Video Conferencing Online Meetings Group Messaging Simple Online
The Cloud Meeting Company Cloud Meetings 2015 Cloud Meetings 1980 s 1990 s 2000 s Cloud Video Conferencing Telephone Conferencing Hardware Video Conferencing Online Meetings Group Messaging Simple Online
Unleash the Power of Secure, Real-Time Collaboration
 White Paper Unleash the Power of Secure, Real-Time Collaboration This paper includes security information for Cisco WebEx Meeting Center, Cisco WebEx Training Center, Cisco WebEx Support Center and Cisco
White Paper Unleash the Power of Secure, Real-Time Collaboration This paper includes security information for Cisco WebEx Meeting Center, Cisco WebEx Training Center, Cisco WebEx Support Center and Cisco
2. Zoom Video Webinar runs on Windows, macos, Linux, Chrome OS, ios, Android, and
 Date: August 24, 2018 Name of Product: Zoom Plug-in for Microsoft Outlook v4.4 (Windows) Contact for more Information: access@zoom.us Zoom's video communications product suite runs on mobile, desktop,
Date: August 24, 2018 Name of Product: Zoom Plug-in for Microsoft Outlook v4.4 (Windows) Contact for more Information: access@zoom.us Zoom's video communications product suite runs on mobile, desktop,
2. Zoom Video Webinar runs on Windows, macos, Linux, Chrome OS, ios, Android, and
 Date: August 24, 2018 Name of Product: Zoom Product Web Pages Contact for more Information: access@zoom.us Zoom's video communications product suite runs on mobile, desktop, and conference room systems.
Date: August 24, 2018 Name of Product: Zoom Product Web Pages Contact for more Information: access@zoom.us Zoom's video communications product suite runs on mobile, desktop, and conference room systems.
Enterprise-ready Unified communications platform
 Enterprise-ready Unified communications platform Video gallery HD video or high resolution photos of attendees Consistent and familiar clients Immersive experience optimized for touch Single identity
Enterprise-ready Unified communications platform Video gallery HD video or high resolution photos of attendees Consistent and familiar clients Immersive experience optimized for touch Single identity
About This Document 3. Overview 3. System Requirements 3. Installation & Setup 4
 About This Document 3 Overview 3 System Requirements 3 Installation & Setup 4 Step By Step Instructions 5 1. Login to Admin Console 6 2. Show Node Structure 7 3. Create SSO Node 8 4. Create SAML IdP 10
About This Document 3 Overview 3 System Requirements 3 Installation & Setup 4 Step By Step Instructions 5 1. Login to Admin Console 6 2. Show Node Structure 7 3. Create SSO Node 8 4. Create SAML IdP 10
RingCentral Meetings QuickStart Guide
 RingCentral Meetings QuickStart Guide RingCentral Meetings empowers your workforce to collaborate from any location with face-toface online meetings in high definition. Share your screen, websites, documents,
RingCentral Meetings QuickStart Guide RingCentral Meetings empowers your workforce to collaborate from any location with face-toface online meetings in high definition. Share your screen, websites, documents,
2. Zoom Video Webinar runs on Windows, macos, Linux, Chrome OS, ios, Android, and
 Date: August 24, 2018 Name of Product: Zoom Video Conferencing and Webinar v4.1 (ios) Contact for more Information: access@zoom.us Zoom's video communications product suite runs on mobile, desktop, and
Date: August 24, 2018 Name of Product: Zoom Video Conferencing and Webinar v4.1 (ios) Contact for more Information: access@zoom.us Zoom's video communications product suite runs on mobile, desktop, and
2. Zoom Video Webinar runs on Windows, macos, Linux, Chrome OS, ios, Android, and
 Date: August 24, 2018 Name of Product: Zoom Video Conferencing and Webinar v4.1 (macos) Contact for more Information: access@zoom.us Zoom's video communications product suite runs on mobile, desktop, and
Date: August 24, 2018 Name of Product: Zoom Video Conferencing and Webinar v4.1 (macos) Contact for more Information: access@zoom.us Zoom's video communications product suite runs on mobile, desktop, and
Cisco Webex Control Hub
 Data Sheet Cisco Webex Control Hub (Management and Analytics) 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 1 of 12 Management and analytics overview
Data Sheet Cisco Webex Control Hub (Management and Analytics) 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 1 of 12 Management and analytics overview
2. Zoom Video Webinar runs on Windows, macos, Linux, Chrome OS, ios, Android, and
 Date: August 24, 2018 Name of Product: Zoom Extensions for browsers v1.4 (Google Chrome and Mozilla Firefox) Contact for more Information: access@zoom.us Zoom's video communications product suite runs
Date: August 24, 2018 Name of Product: Zoom Extensions for browsers v1.4 (Google Chrome and Mozilla Firefox) Contact for more Information: access@zoom.us Zoom's video communications product suite runs
2. Zoom Video Webinar runs on Windows, macos, Linux, Chrome OS, ios, Android, and
 Date: Jan 23, 2019 Name of Product: Zoom Plug-in for Microsoft Outlook v4.5 (macos) Contact for more Information: access@zoom.us Zoom's video communications product suite runs on mobile, desktop, and conference
Date: Jan 23, 2019 Name of Product: Zoom Plug-in for Microsoft Outlook v4.5 (macos) Contact for more Information: access@zoom.us Zoom's video communications product suite runs on mobile, desktop, and conference
2. Zoom Video Webinar runs on Windows, macos, Linux, Chrome OS, ios, Android, and
 Date: Jan 23, 2019 Name of Product: Zoom Rooms Controller v4.3.6 (ipad) Contact for more Information: access@zoom.us Zoom's video communications product suite runs on mobile, desktop, and conference room
Date: Jan 23, 2019 Name of Product: Zoom Rooms Controller v4.3.6 (ipad) Contact for more Information: access@zoom.us Zoom's video communications product suite runs on mobile, desktop, and conference room
Administrator s Guide. June 15, 2018
 Administrator s Guide June 15, 2018 Contents Administrators have control of their Enterprise Group. Provision and edit service for employees, and, view and manage billing and meeting history. One or more
Administrator s Guide June 15, 2018 Contents Administrators have control of their Enterprise Group. Provision and edit service for employees, and, view and manage billing and meeting history. One or more
Team Advanced VC Services. Cisco WebEx Services
 Team Advanced VC Services Cisco WebEx Services People Want to Collaborate Their Way More Technology Choices Are Available Than Ever Before They want mobility. They want applications that make them more
Team Advanced VC Services Cisco WebEx Services People Want to Collaborate Their Way More Technology Choices Are Available Than Ever Before They want mobility. They want applications that make them more
Exam Name: PASCERSE - Cisco SaaS Conferencing and EIM Resale ATP for the SE Exam
 Vendor: Cisco Exam Code: 650-303 Exam Name: PASCERSE - Cisco SaaS Conferencing and EIM Resale ATP for the SE Exam Version: Demo QUESTION 1 Which two steps describe best practices for placing a product
Vendor: Cisco Exam Code: 650-303 Exam Name: PASCERSE - Cisco SaaS Conferencing and EIM Resale ATP for the SE Exam Version: Demo QUESTION 1 Which two steps describe best practices for placing a product
Edge Foundational Training
 Edge Foundational Training Give your team the tools to get up and running with Edge Edge Foundational Training provides the tools and information needed to start using Edge whether in the cloud or on premises.
Edge Foundational Training Give your team the tools to get up and running with Edge Edge Foundational Training provides the tools and information needed to start using Edge whether in the cloud or on premises.
Getting Started with Zoom
 Getting Started with Zoom The Institute of Agriculture has recently purchased a site license for a new cloud-based video conferencing service known as Zoom. If you have ever connected to a GoToMeeting,
Getting Started with Zoom The Institute of Agriculture has recently purchased a site license for a new cloud-based video conferencing service known as Zoom. If you have ever connected to a GoToMeeting,
2. Zoom Video Webinar runs on Windows, macos, Linux, Chrome OS, ios, Android, and
 Date: Jan 23, 2019 Name of Product: Zoom Rooms v4.3 (Windows) Contact for more Information: access@zoom.us Zoom's video communications product suite runs on mobile, desktop, and conference room systems.
Date: Jan 23, 2019 Name of Product: Zoom Rooms v4.3 (Windows) Contact for more Information: access@zoom.us Zoom's video communications product suite runs on mobile, desktop, and conference room systems.
Dolby Conference Phone 3.1 configuration guide for West
 Dolby Conference Phone 3.1 configuration guide for West 17 January 2017 Copyright 2017 Dolby Laboratories. All rights reserved. For information, contact: Dolby Laboratories, Inc. 1275 Market Street San
Dolby Conference Phone 3.1 configuration guide for West 17 January 2017 Copyright 2017 Dolby Laboratories. All rights reserved. For information, contact: Dolby Laboratories, Inc. 1275 Market Street San
The office for the anywhere worker!!! Your LCB SOFTPHONE: A powerful new take on the all-in-one for a more immersive experience.
 The office for the anywhere worker!!! Your LCB SOFTPHONE: A powerful new take on the all-in-one for a more immersive experience. LCB SOFTPHONE FOR SALESFORCE Combine real-time communications and tracking
The office for the anywhere worker!!! Your LCB SOFTPHONE: A powerful new take on the all-in-one for a more immersive experience. LCB SOFTPHONE FOR SALESFORCE Combine real-time communications and tracking
ArcGIS Online A Security, Privacy, and Compliance Overview. Andrea Rosso Michael Young
 ArcGIS Online A Security, Privacy, and Compliance Overview Andrea Rosso Michael Young ArcGIS Online A Multi-Tenant System Portal Portal Portal ArcGIS Online Agenda Online Platform Security Deployment Architecture
ArcGIS Online A Security, Privacy, and Compliance Overview Andrea Rosso Michael Young ArcGIS Online A Multi-Tenant System Portal Portal Portal ArcGIS Online Agenda Online Platform Security Deployment Architecture
Sentinet for Microsoft Azure SENTINET
 Sentinet for Microsoft Azure SENTINET Sentinet for Microsoft Azure 1 Contents Introduction... 2 Customer Benefits... 2 Deployment Topologies... 3 Cloud Deployment Model... 3 Hybrid Deployment Model...
Sentinet for Microsoft Azure SENTINET Sentinet for Microsoft Azure 1 Contents Introduction... 2 Customer Benefits... 2 Deployment Topologies... 3 Cloud Deployment Model... 3 Hybrid Deployment Model...
ZOOM Video Conferencing: Quick Start Guide
 ZOOM Video Conferencing: Quick Start Guide Welcome to Zoom at James Cook University (JCU), a video conferencing system designed to enhance your communication and collaboration with colleagues, students
ZOOM Video Conferencing: Quick Start Guide Welcome to Zoom at James Cook University (JCU), a video conferencing system designed to enhance your communication and collaboration with colleagues, students
Quickstart Guide to Setup your Zoom Account To start, visit the USF Zoom site:
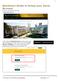 1 Quickstart Guide to Setup your Zoom Account To start, visit the USF Zoom site: http://usfca.zoom.us Click on the link Download Zoom on the upper right side of the page and then click on the link for
1 Quickstart Guide to Setup your Zoom Account To start, visit the USF Zoom site: http://usfca.zoom.us Click on the link Download Zoom on the upper right side of the page and then click on the link for
Level 1 Technical. Microsoft Lync Basics. Contents
 Level 1 Technical Microsoft Lync Basics Contents 1 Glossary... 2 2 Introduction... 3 3 Integration... 4 4 Architecture... 6 Lync Server Editions... 6 Lync Server Roles... 6 Server Pools... 6 Front End
Level 1 Technical Microsoft Lync Basics Contents 1 Glossary... 2 2 Introduction... 3 3 Integration... 4 4 Architecture... 6 Lync Server Editions... 6 Lync Server Roles... 6 Server Pools... 6 Front End
Sentinet for BizTalk Server SENTINET
 Sentinet for BizTalk Server SENTINET Sentinet for BizTalk Server 1 Contents Introduction... 2 Sentinet Benefits... 3 SOA and API Repository... 4 Security... 4 Mediation and Virtualization... 5 Authentication
Sentinet for BizTalk Server SENTINET Sentinet for BizTalk Server 1 Contents Introduction... 2 Sentinet Benefits... 3 SOA and API Repository... 4 Security... 4 Mediation and Virtualization... 5 Authentication
Cisco Jabber IM for iphone
 Data Sheet Cisco Jabber IM for iphone Cisco Collaboration Solutions improve team and customer experiences to help organizations encourage innovation and improve decision making while building trust and
Data Sheet Cisco Jabber IM for iphone Cisco Collaboration Solutions improve team and customer experiences to help organizations encourage innovation and improve decision making while building trust and
Welcome! Securely Sync, Store & Share with Citrix ShareFile
 Welcome! Securely Sync, Store & Share with Citrix ShareFile Chris Riley System Source criley@syssrc.com Dennis Kloster System Source dkloster@syssrc.com Charlie Brinson Citrix charlie.brinson@citrix.com
Welcome! Securely Sync, Store & Share with Citrix ShareFile Chris Riley System Source criley@syssrc.com Dennis Kloster System Source dkloster@syssrc.com Charlie Brinson Citrix charlie.brinson@citrix.com
Centrify for Dropbox Deployment Guide
 CENTRIFY DEPLOYMENT GUIDE Centrify for Dropbox Deployment Guide Abstract Centrify provides mobile device management and single sign-on services that you can trust and count on as a critical component of
CENTRIFY DEPLOYMENT GUIDE Centrify for Dropbox Deployment Guide Abstract Centrify provides mobile device management and single sign-on services that you can trust and count on as a critical component of
DreamFactory Security Guide
 DreamFactory Security Guide This white paper is designed to provide security information about DreamFactory. The sections below discuss the inherently secure characteristics of the platform and the explicit
DreamFactory Security Guide This white paper is designed to provide security information about DreamFactory. The sections below discuss the inherently secure characteristics of the platform and the explicit
The Nasuni Security Model
 White Paper Nasuni enterprise file services ensures unstructured data security and privacy, enabling IT organizations to safely leverage cloud storage while meeting stringent governance and compliance
White Paper Nasuni enterprise file services ensures unstructured data security and privacy, enabling IT organizations to safely leverage cloud storage while meeting stringent governance and compliance
Cloud FastPath: Highly Secure Data Transfer
 Cloud FastPath: Highly Secure Data Transfer Tervela helps companies move large volumes of sensitive data safely and securely over network distances great and small. Tervela has been creating high performance
Cloud FastPath: Highly Secure Data Transfer Tervela helps companies move large volumes of sensitive data safely and securely over network distances great and small. Tervela has been creating high performance
Designing Workspace of the Future for the Mobile Worker
 Designing Workspace of the Future for the Mobile Worker Paulo Jorge Correia Technical Solutions Architect Building Business Value Enable mobile workers and BYOD Locate and access remote experts Collaborate
Designing Workspace of the Future for the Mobile Worker Paulo Jorge Correia Technical Solutions Architect Building Business Value Enable mobile workers and BYOD Locate and access remote experts Collaborate
SAP Security in a Hybrid World. Kiran Kola
 SAP Security in a Hybrid World Kiran Kola Agenda Cybersecurity SAP Cloud Platform Identity Provisioning service SAP Cloud Platform Identity Authentication service SAP Cloud Connector & how to achieve Principal
SAP Security in a Hybrid World Kiran Kola Agenda Cybersecurity SAP Cloud Platform Identity Provisioning service SAP Cloud Platform Identity Authentication service SAP Cloud Connector & how to achieve Principal
Configure Mobile and Remote Access
 Mobile and Remote Access Overview, on page 1 Mobile and Remote Access Prerequisites, on page 3 Mobile and Remote Access Configuration Task Flow, on page 4 Mobile and Remote Access Overview Cisco Unified
Mobile and Remote Access Overview, on page 1 Mobile and Remote Access Prerequisites, on page 3 Mobile and Remote Access Configuration Task Flow, on page 4 Mobile and Remote Access Overview Cisco Unified
Services Description for VidyoCloud Services
 Services Description for VidyoCloud Services March 2017 Vidyo, Inc. 433 Hackensack Ave Hackensack, NJ 07601 Table of Contents DESCRIPTION FOR VIDYOCLOUD SERVICES 3 SUBSCRIPTIONS 3 TEAM PLAN & ENTERPRISE
Services Description for VidyoCloud Services March 2017 Vidyo, Inc. 433 Hackensack Ave Hackensack, NJ 07601 Table of Contents DESCRIPTION FOR VIDYOCLOUD SERVICES 3 SUBSCRIPTIONS 3 TEAM PLAN & ENTERPRISE
Security and Compliance at Mavenlink
 Security and Compliance at Mavenlink Table of Contents Introduction....3 Application Security....4....4....5 Infrastructure Security....8....8....8....9 Data Security.... 10....10....10 Infrastructure
Security and Compliance at Mavenlink Table of Contents Introduction....3 Application Security....4....4....5 Infrastructure Security....8....8....8....9 Data Security.... 10....10....10 Infrastructure
ForeScout Extended Module for VMware AirWatch MDM
 ForeScout Extended Module for VMware AirWatch MDM Version 1.7.2 Table of Contents About the AirWatch MDM Integration... 4 Additional AirWatch Documentation... 4 About this Module... 4 How it Works... 5
ForeScout Extended Module for VMware AirWatch MDM Version 1.7.2 Table of Contents About the AirWatch MDM Integration... 4 Additional AirWatch Documentation... 4 About this Module... 4 How it Works... 5
Architecture Overview
 Architecture Overview For organizations that need high quality video conferencing and want to avoid burdening their IT staff and resources, VidyoCloud is a hosted video collaboration solution that provides
Architecture Overview For organizations that need high quality video conferencing and want to avoid burdening their IT staff and resources, VidyoCloud is a hosted video collaboration solution that provides
RingCentral Office Premium Edition
 RingCentral Datasheet RingCentral Office Premium Edition RingCentral Office Premium Edition Empower your business to communicate, collaborate, and connect via voice, team messaging and collaboration, audio
RingCentral Datasheet RingCentral Office Premium Edition RingCentral Office Premium Edition Empower your business to communicate, collaborate, and connect via voice, team messaging and collaboration, audio
Configuration Tab. Cisco WebEx Messenger Administration Guide 1
 Overview, page 2 Organization Information, page 2 Domain Information, page 3 Resource Management Information, page 4 URL Configuration, page 5 Security Settings, page 6 Directory Settings, page 8 Password
Overview, page 2 Organization Information, page 2 Domain Information, page 3 Resource Management Information, page 4 URL Configuration, page 5 Security Settings, page 6 Directory Settings, page 8 Password
Breaking News CloudAXIS Suite 1.0
 August 2013 Level 2 Breaking News CloudAXIS Suite 1.0 Product Release Date: October, 2012 Disclaimer 2013 Polycom, Inc. All rights reserved. Polycom, Inc. 6001 America Center Dr San Jose, CA 95002 USA
August 2013 Level 2 Breaking News CloudAXIS Suite 1.0 Product Release Date: October, 2012 Disclaimer 2013 Polycom, Inc. All rights reserved. Polycom, Inc. 6001 America Center Dr San Jose, CA 95002 USA
ForeScout Extended Module for MaaS360
 Version 1.8 Table of Contents About MaaS360 Integration... 4 Additional ForeScout MDM Documentation... 4 About this Module... 4 How it Works... 5 Continuous Query Refresh... 5 Offsite Device Management...
Version 1.8 Table of Contents About MaaS360 Integration... 4 Additional ForeScout MDM Documentation... 4 About this Module... 4 How it Works... 5 Continuous Query Refresh... 5 Offsite Device Management...
Spontania User Setup Guide
 Spontania User Setup Guide ClearOne 5225 Wiley Post Way Suite 500 Salt Lake City, UT 84116 Telephone 1.800.945.7730 1.801.975.7200 Spontania Support 1.801.974.3612 TechSales 1.800.705.2103 FAX 1.801.977.0087
Spontania User Setup Guide ClearOne 5225 Wiley Post Way Suite 500 Salt Lake City, UT 84116 Telephone 1.800.945.7730 1.801.975.7200 Spontania Support 1.801.974.3612 TechSales 1.800.705.2103 FAX 1.801.977.0087
Frequently Asked Questions
 General Where can I find a user guide? When logged in, a user guide can be downloaded from within the client. Help is located in the options tab at the bottom right hand corner of the desktop client and
General Where can I find a user guide? When logged in, a user guide can be downloaded from within the client. Help is located in the options tab at the bottom right hand corner of the desktop client and
 Web Conference - InstaVC WebRTC-based Clientless VC Make the Right Impression Collaborate with your team like never before. With InstaVC, give presentations, have productive discussions, and come up with
Web Conference - InstaVC WebRTC-based Clientless VC Make the Right Impression Collaborate with your team like never before. With InstaVC, give presentations, have productive discussions, and come up with
Administrator s Guide. September 27, 2017
 Administrator s Guide September 27, 2017 Contents Administrators have control of their Enterprise Group. Provision and edit service for employees, and, view and manage billing and meeting history. One
Administrator s Guide September 27, 2017 Contents Administrators have control of their Enterprise Group. Provision and edit service for employees, and, view and manage billing and meeting history. One
Single Sign-On. Introduction
 Introduction DeliverySlip seamlessly integrates into your enterprise SSO to give your users total email security and an extra set of robust communications tools. Single sign-on (SSO) systems create a single
Introduction DeliverySlip seamlessly integrates into your enterprise SSO to give your users total email security and an extra set of robust communications tools. Single sign-on (SSO) systems create a single
Hosts have the top level of webinar control and can grant and revoke various privileges for participants.
 Introduction ClickMeeting is an easy-to-use SaaS webinar platform used worldwide. It was built using highend technology, with data security as the highest priority. The platform meets stringent security
Introduction ClickMeeting is an easy-to-use SaaS webinar platform used worldwide. It was built using highend technology, with data security as the highest priority. The platform meets stringent security
Quickstart Guide to Setup your Zoom Account To start, visit the USF Zoom site:
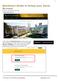 1 Quickstart Guide to Setup your Zoom Account To start, visit the USF Zoom site: http://usfca.zoom.us Click on the link Download Zoom on the upper right side of the page and then click on the link for
1 Quickstart Guide to Setup your Zoom Account To start, visit the USF Zoom site: http://usfca.zoom.us Click on the link Download Zoom on the upper right side of the page and then click on the link for
Cloud Video Conferencing. A Comprehensive Guide
 Cloud Video Conferencing Reference Paper May 2016 How we communicate in the business world is changing. Businesses increasingly have more remote workers. Whether working remote fulltime, part-time or just
Cloud Video Conferencing Reference Paper May 2016 How we communicate in the business world is changing. Businesses increasingly have more remote workers. Whether working remote fulltime, part-time or just
Cisco Spark Tech Ops and Security Frequently Asked Questions (FAQs)
 Cisco Spark Tech Ops and Security Frequently Asked Questions (FAQs) First Published: November 3, 2017 Last Updated: November 3, 2017 Question: Can Cisco provide a detailed Cisco Spark architecture diagram?
Cisco Spark Tech Ops and Security Frequently Asked Questions (FAQs) First Published: November 3, 2017 Last Updated: November 3, 2017 Question: Can Cisco provide a detailed Cisco Spark architecture diagram?
Security in Bomgar Remote Support
 Security in Bomgar Remote Support 2018 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of their
Security in Bomgar Remote Support 2018 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of their
Thank you for joining our Webinar, if you are having a problem logging in, please refer to the guide for more information.
 Webinar Guide Thank you for joining our Webinar, if you are having a problem logging in, please refer to the guide for more information. If you are unable to find the answer, please email the GRB team
Webinar Guide Thank you for joining our Webinar, if you are having a problem logging in, please refer to the guide for more information. If you are unable to find the answer, please email the GRB team
ForeScout Extended Module for MobileIron
 Version 1.8 Table of Contents About MobileIron Integration... 4 Additional MobileIron Documentation... 4 About this Module... 4 How it Works... 5 Continuous Query Refresh... 5 Offsite Device Management...
Version 1.8 Table of Contents About MobileIron Integration... 4 Additional MobileIron Documentation... 4 About this Module... 4 How it Works... 5 Continuous Query Refresh... 5 Offsite Device Management...
How to use Video Conferencing & Desktop Sharing on Magnet Voice
 How to use Video Conferencing & Desktop Sharing on Magnet Voice Video Conferencing and Collaboration CONTENTS User Guide... 1 1. How to set up a video session... 2. Running a video conference... 4 3. Screen
How to use Video Conferencing & Desktop Sharing on Magnet Voice Video Conferencing and Collaboration CONTENTS User Guide... 1 1. How to set up a video session... 2. Running a video conference... 4 3. Screen
Security and Certificates
 Encryption, page 1 Voice and Video Encryption, page 6 Federal Information Processing Standards, page 6 Certificate Validation, page 6 Required Certificates for On-Premises Servers, page 7 Certificate Requirements
Encryption, page 1 Voice and Video Encryption, page 6 Federal Information Processing Standards, page 6 Certificate Validation, page 6 Required Certificates for On-Premises Servers, page 7 Certificate Requirements
Setting Up Resources in VMware Identity Manager (On Premises) Modified on 30 AUG 2017 VMware AirWatch 9.1.1
 Setting Up Resources in VMware Identity Manager (On Premises) Modified on 30 AUG 2017 VMware AirWatch 9.1.1 Setting Up Resources in VMware Identity Manager (On Premises) You can find the most up-to-date
Setting Up Resources in VMware Identity Manager (On Premises) Modified on 30 AUG 2017 VMware AirWatch 9.1.1 Setting Up Resources in VMware Identity Manager (On Premises) You can find the most up-to-date
Vidyo Hosted Services Description for VidyoCloud Services
 Vidyo Hosted Services Description for VidyoCloud Services June 2016 Vidyo, Inc. 433 Hackensack Ave Hackensack, NJ 07601 Table of Contents VIDYO HOSTED SERVICES DESCRIPTION FOR VIDYOCLOUD SERVICES 3 SUBSCRIPTIONS
Vidyo Hosted Services Description for VidyoCloud Services June 2016 Vidyo, Inc. 433 Hackensack Ave Hackensack, NJ 07601 Table of Contents VIDYO HOSTED SERVICES DESCRIPTION FOR VIDYOCLOUD SERVICES 3 SUBSCRIPTIONS
USER MANUAL. VIA IT Deployment Guide for Firmware 2.3 MODEL: P/N: Rev 7.
 USER MANUAL MODEL: VIA IT Deployment Guide for Firmware 2.3 P/N: 2900-300631 Rev 7 www.kramerav.com Contents 1 Introduction 1 1.1 User Experience 2 1.2 Pre-Deployment Planning 2 2 Connectivity 3 2.1 Network
USER MANUAL MODEL: VIA IT Deployment Guide for Firmware 2.3 P/N: 2900-300631 Rev 7 www.kramerav.com Contents 1 Introduction 1 1.1 User Experience 2 1.2 Pre-Deployment Planning 2 2 Connectivity 3 2.1 Network
AXIAD IDS CLOUD SOLUTION. Trusted User PKI, Trusted User Flexible Authentication & Trusted Infrastructure
 AXIAD IDS CLOUD SOLUTION Trusted User PKI, Trusted User Flexible Authentication & Trusted Infrastructure Logical Access Use Cases ONE BADGE FOR CONVERGED PHYSICAL AND IT ACCESS Corporate ID badge for physical
AXIAD IDS CLOUD SOLUTION Trusted User PKI, Trusted User Flexible Authentication & Trusted Infrastructure Logical Access Use Cases ONE BADGE FOR CONVERGED PHYSICAL AND IT ACCESS Corporate ID badge for physical
Vodafone One Net app Quick Start Guide For PC
 Vodafone One Net app Quick Start Guide For PC Contents What is the One Net app? 1 Installing the One Net app 2 Logging in and out 2 Logging in for the first time 2 Starting the One Net app when you turn
Vodafone One Net app Quick Start Guide For PC Contents What is the One Net app? 1 Installing the One Net app 2 Logging in and out 2 Logging in for the first time 2 Starting the One Net app when you turn
App Gateway Deployment Guide
 C E N T R I F Y D E P L O Y M E N T G U I D E App Gateway Deployment Guide Abstract Centrify provides mobile device management and single sign-on services that you can trust and count on as a critical
C E N T R I F Y D E P L O Y M E N T G U I D E App Gateway Deployment Guide Abstract Centrify provides mobile device management and single sign-on services that you can trust and count on as a critical
Administrator s Guide
 Administrator s Guide (January 2017) Welcome! You have been invited to manage the subscriber community who will be using this videoconferencing service within your organization. This guide will provide
Administrator s Guide (January 2017) Welcome! You have been invited to manage the subscriber community who will be using this videoconferencing service within your organization. This guide will provide
Datasheet. Only Workspaces delivers the features users want and the control that IT needs.
 Datasheet Secure SECURE Enterprise ENTERPRISE File FILE Sync, SYNC, Sharing SHARING and AND Content CONTENT Collaboration COLLABORATION BlackBerry Workspaces makes enterprises more mobile and collaborative,
Datasheet Secure SECURE Enterprise ENTERPRISE File FILE Sync, SYNC, Sharing SHARING and AND Content CONTENT Collaboration COLLABORATION BlackBerry Workspaces makes enterprises more mobile and collaborative,
Known Issues, Limitations, and Important Notes
 Known Issues, page 1 Performance and Behavior Notes, page 1 Important Notes, page 4 Known Issues Microsoft Outlook Local Contacts and Presence Users' presence is unknown when the contact is manually added
Known Issues, page 1 Performance and Behavior Notes, page 1 Important Notes, page 4 Known Issues Microsoft Outlook Local Contacts and Presence Users' presence is unknown when the contact is manually added
Top. Reasons Legal Teams Select kiteworks by Accellion
 Top 10 Reasons Legal Teams Select kiteworks by Accellion Accellion Legal Customers Include: Top 10 Reasons Legal Teams Select kiteworks kiteworks by Accellion enables legal teams to manage their increasing
Top 10 Reasons Legal Teams Select kiteworks by Accellion Accellion Legal Customers Include: Top 10 Reasons Legal Teams Select kiteworks kiteworks by Accellion enables legal teams to manage their increasing
One-to-Many (Interactive Broadcast)
 Creating a 360 IP Video Strategy t John Shaw COO VBrick Systems Feb 1, 2011 IP Video Defined IP Video VC/ Telepresence Streaming Surveillance Desktop Roombased Consumer Corp, Edu, Gov t Media Building/
Creating a 360 IP Video Strategy t John Shaw COO VBrick Systems Feb 1, 2011 IP Video Defined IP Video VC/ Telepresence Streaming Surveillance Desktop Roombased Consumer Corp, Edu, Gov t Media Building/
LEVEL 3 SM WEB MEETING
 LEVEL 3 SM WEB MEETING REAL-TIME, INTUITIVE, ROBUST COLLABORATION AT YOUR FINGERTIPS JANUARY 2017 Today, organizations are finding that rudimentary web conferencing applications are inadequate and frustrating
LEVEL 3 SM WEB MEETING REAL-TIME, INTUITIVE, ROBUST COLLABORATION AT YOUR FINGERTIPS JANUARY 2017 Today, organizations are finding that rudimentary web conferencing applications are inadequate and frustrating
Account Management Settings section. Service Request Settings section
 WebEx Site Configuration Audit Log The following settings are included in the CSV export of changes to the Configuration > Common Site Settings > Options page of WebEx Site Administration. Account Management
WebEx Site Configuration Audit Log The following settings are included in the CSV export of changes to the Configuration > Common Site Settings > Options page of WebEx Site Administration. Account Management
MEMBER & HOST GUIDE. Additional support and feature-use documentation is available on our website home page. 10/27/2017 Page 1 of 9
 MEMBER & HOST GUIDE Welcome to ConferZoom, a service provided for the California Community Colleges. Use a web camera, text chat, and share desktop screens in collaboration or instruction. Get started
MEMBER & HOST GUIDE Welcome to ConferZoom, a service provided for the California Community Colleges. Use a web camera, text chat, and share desktop screens in collaboration or instruction. Get started
PCI DSS Compliance. White Paper Parallels Remote Application Server
 PCI DSS Compliance White Paper Parallels Remote Application Server Table of Contents Introduction... 3 What Is PCI DSS?... 3 Why Businesses Need to Be PCI DSS Compliant... 3 What Is Parallels RAS?... 3
PCI DSS Compliance White Paper Parallels Remote Application Server Table of Contents Introduction... 3 What Is PCI DSS?... 3 Why Businesses Need to Be PCI DSS Compliant... 3 What Is Parallels RAS?... 3
Sentinet for Windows Azure VERSION 2.2
 Sentinet for Windows Azure VERSION 2.2 Sentinet for Windows Azure 1 Contents Introduction... 2 Customer Benefits... 2 Deployment Topologies... 3 Isolated Deployment Model... 3 Collocated Deployment Model...
Sentinet for Windows Azure VERSION 2.2 Sentinet for Windows Azure 1 Contents Introduction... 2 Customer Benefits... 2 Deployment Topologies... 3 Isolated Deployment Model... 3 Collocated Deployment Model...
Google Identity Services for work
 INTRODUCING Google Identity Services for work One account. All of Google Enter your email Next Online safety made easy We all care about keeping our data safe and private. Google Identity brings a new
INTRODUCING Google Identity Services for work One account. All of Google Enter your email Next Online safety made easy We all care about keeping our data safe and private. Google Identity brings a new
Deploying, Configuring and Using Cisco Spark (SPARK) v2
 6210 Central Ave, Portage, IN. 46368 Phone: 219.764.3800 Fax: 219.764.3805 Web: http://www.ctclc.com Deploying, Configuring and Using Cisco Spark (SPARK) v2 This is a three day instructor-led course where
6210 Central Ave, Portage, IN. 46368 Phone: 219.764.3800 Fax: 219.764.3805 Web: http://www.ctclc.com Deploying, Configuring and Using Cisco Spark (SPARK) v2 This is a three day instructor-led course where
What is Zoom Web? Sign-in to Zoom Web
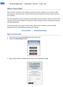 1 What is Zoom Web? Zoom is Clarion University s video conferencing solution for online meetings. You can host up to 100 participants for unlimited duration. Students and external participants do not need
1 What is Zoom Web? Zoom is Clarion University s video conferencing solution for online meetings. You can host up to 100 participants for unlimited duration. Students and external participants do not need
OpenIAM Identity and Access Manager Technical Architecture Overview
 OpenIAM Identity and Access Manager Technical Architecture Overview Overview... 3 Architecture... 3 Common Use Case Description... 3 Identity and Access Middleware... 5 Enterprise Service Bus (ESB)...
OpenIAM Identity and Access Manager Technical Architecture Overview Overview... 3 Architecture... 3 Common Use Case Description... 3 Identity and Access Middleware... 5 Enterprise Service Bus (ESB)...
LEVEL 3 SM WEB MEETING SECURITY GUIDE
 LEVEL 3 SM WEB MEETING SECURITY GUIDE DEDICATED TO SECURITY Meet with confidence with the Level 3 Web Meeting audio and web conferencing services, which are highly reliable and intuitive to use. The Web
LEVEL 3 SM WEB MEETING SECURITY GUIDE DEDICATED TO SECURITY Meet with confidence with the Level 3 Web Meeting audio and web conferencing services, which are highly reliable and intuitive to use. The Web
How to Access Protected Health Information from Anywhere and Stay Compliant
 How to Access Protected Health Information from Anywhere and Stay Compliant Secure, HIPAA-compliant file sharing & data storage with mobile data access Safeguard protected health information (PHI), support
How to Access Protected Health Information from Anywhere and Stay Compliant Secure, HIPAA-compliant file sharing & data storage with mobile data access Safeguard protected health information (PHI), support
Salesforce1 Mobile Security White Paper. Revised: April 2014
 Salesforce1 Mobile Security White Paper Revised: April 2014 Table of Contents Introduction Salesforce1 Architecture Overview Authorization and Permissions Communication Security Authentication OAuth Pairing
Salesforce1 Mobile Security White Paper Revised: April 2014 Table of Contents Introduction Salesforce1 Architecture Overview Authorization and Permissions Communication Security Authentication OAuth Pairing
Mozy. Implementing with Federated Identity
 Mozy Implementing with Federated Identity Preface 2017 Mozy, Inc. All rights reserved. Information in this document is subject to change without notice. The software described in this document is furnished
Mozy Implementing with Federated Identity Preface 2017 Mozy, Inc. All rights reserved. Information in this document is subject to change without notice. The software described in this document is furnished
Security Information & Policies
 Security Information & Policies 01 Table of Contents OVERVIEW CHAPTER 1 : CHAPTER 2: CHAPTER 3: CHAPTER 4: CHAPTER 5: CHAPTER 6: CHAPTER 7: CHAPTER 8: CHAPTER 9: CHAPTER 10: CHAPTER 11: CHAPTER 12: CHAPTER
Security Information & Policies 01 Table of Contents OVERVIEW CHAPTER 1 : CHAPTER 2: CHAPTER 3: CHAPTER 4: CHAPTER 5: CHAPTER 6: CHAPTER 7: CHAPTER 8: CHAPTER 9: CHAPTER 10: CHAPTER 11: CHAPTER 12: CHAPTER
LiveEngage Messaging Platform: Security Overview Document Version: 2.0 July 2017
 LiveEngage Messaging Platform: Security Overview Document Version: 2.0 July 2017 Contents Introduction... 3 Supported Platforms... 3 Protecting Data in Transit... 3 Protecting Data at Rest... 3 Encryption...
LiveEngage Messaging Platform: Security Overview Document Version: 2.0 July 2017 Contents Introduction... 3 Supported Platforms... 3 Protecting Data in Transit... 3 Protecting Data at Rest... 3 Encryption...
This paper introduces the security policies, practices, and procedures of Lucidchart.
 Lucidchart Security Abstract This paper introduces the security policies, practices, and procedures of Lucidchart. The paper lays out the architecture security of this software-as-a-service product. It
Lucidchart Security Abstract This paper introduces the security policies, practices, and procedures of Lucidchart. The paper lays out the architecture security of this software-as-a-service product. It
ExamTorrent. Best exam torrent, excellent test torrent, valid exam dumps are here waiting for you
 ExamTorrent http://www.examtorrent.com Best exam torrent, excellent test torrent, valid exam dumps are here waiting for you Exam : 400-251 Title : CCIE Security Written Exam (v5.0) Vendor : Cisco Version
ExamTorrent http://www.examtorrent.com Best exam torrent, excellent test torrent, valid exam dumps are here waiting for you Exam : 400-251 Title : CCIE Security Written Exam (v5.0) Vendor : Cisco Version
Course Catalog: Webex Teams + Webex Meetings + Jabber
 Course Catalog: Webex Teams + Webex Meetings + Jabber Webex Meetings, Webex Teams, and Jabber End User and Administrator Training Meet Me In The Cloud, Inc. https://meetmeinthecloud.com San Francisco Bay
Course Catalog: Webex Teams + Webex Meetings + Jabber Webex Meetings, Webex Teams, and Jabber End User and Administrator Training Meet Me In The Cloud, Inc. https://meetmeinthecloud.com San Francisco Bay
Microsoft 365. A complete, intelligent, secure solution to empower employees. Integrated for simplicity. Built for teamwork. Unlocks creativity
 2x 50% 5x Microsoft 365 A complete, intelligent, secure solution to empower employees Unlocks creativity Built for teamwork Integrated for simplicity Intelligent security Inner Loop Files Sites Content
2x 50% 5x Microsoft 365 A complete, intelligent, secure solution to empower employees Unlocks creativity Built for teamwork Integrated for simplicity Intelligent security Inner Loop Files Sites Content
Single Sign-On. Introduction. Feature Sheet
 Feature Sheet Single Sign-On Introduction CipherPost Pro seamlessly integrates into your enterprise single sign-on (SSO) to give your users total email security and an extra set of robust communications
Feature Sheet Single Sign-On Introduction CipherPost Pro seamlessly integrates into your enterprise single sign-on (SSO) to give your users total email security and an extra set of robust communications
<Partner Name> <Partner Product> RSA SECURID ACCESS. VMware Horizon View 7.2 Clients. Standard Agent Client Implementation Guide
 RSA SECURID ACCESS Standard Agent Client Implementation Guide VMware Horizon View 7.2 Clients Daniel R. Pintal, RSA Partner Engineering Last Modified: September 14, 2017
RSA SECURID ACCESS Standard Agent Client Implementation Guide VMware Horizon View 7.2 Clients Daniel R. Pintal, RSA Partner Engineering Last Modified: September 14, 2017
MB Microsoft Dynamics CRM 2016 Online Deployment.
 MB2-710 Microsoft Dynamics CRM 2016 Online Deployment Getting Started Overview CRM Online is a cloud-based offering of Microsoft Dynamics CRM The licensing is a subscription-based model with a monthly
MB2-710 Microsoft Dynamics CRM 2016 Online Deployment Getting Started Overview CRM Online is a cloud-based offering of Microsoft Dynamics CRM The licensing is a subscription-based model with a monthly
What s New with VMware vcloud Director 8.0
 Feature Overview TECHNICAL WHITE PAPER Table of Contents What s New with VMware....3 Support for vsphere 6.0 and NSX 6.1.4....4 VMware vsphere 6.0 Support...4 VMware NSX 6.1.4 Support....4 Organization
Feature Overview TECHNICAL WHITE PAPER Table of Contents What s New with VMware....3 Support for vsphere 6.0 and NSX 6.1.4....4 VMware vsphere 6.0 Support...4 VMware NSX 6.1.4 Support....4 Organization
Why is Office 365 the right choice?
 Why is Office 365 the right choice? People today want to be productive wherever they go. They want to work faster and smarter across their favorite devices, while staying current and connected. Simply
Why is Office 365 the right choice? People today want to be productive wherever they go. They want to work faster and smarter across their favorite devices, while staying current and connected. Simply
Core Solutions of Microsoft Skype for Business 2015
 Course 20334: Core Solutions of Microsoft Skype for Business 2015 Course Outline Module 1: Installing and Implementing Skype for Business Server 2015 This module helps you to identify the external dependencies
Course 20334: Core Solutions of Microsoft Skype for Business 2015 Course Outline Module 1: Installing and Implementing Skype for Business Server 2015 This module helps you to identify the external dependencies
Single Sign-On for PCF. User's Guide
 Single Sign-On for PCF Version 1.2 User's Guide 2018 Pivotal Software, Inc. Table of Contents Table of Contents Single Sign-On Overview Installation Getting Started with Single Sign-On Manage Service Plans
Single Sign-On for PCF Version 1.2 User's Guide 2018 Pivotal Software, Inc. Table of Contents Table of Contents Single Sign-On Overview Installation Getting Started with Single Sign-On Manage Service Plans
BOMGAR.COM BOMGAR VS. WEBEX UPDATED: 2/28/2017
 .COM VS. WEBEX UPDATED: 2/28/2017 Bomgar VS. Support Center LICENSING & DEPLOYMENT The proliferation of solutions has undoubtedly provided certain advantages for organizations seeking alternatives to traditional
.COM VS. WEBEX UPDATED: 2/28/2017 Bomgar VS. Support Center LICENSING & DEPLOYMENT The proliferation of solutions has undoubtedly provided certain advantages for organizations seeking alternatives to traditional
Cirius Secure Messaging Single Sign-On
 Cirius Secure Messaging seamlessly integrates into your enterprise SSO to give your users total email security and an extra set of robust communications tools. Single sign-on (SSO) systems create a single
Cirius Secure Messaging seamlessly integrates into your enterprise SSO to give your users total email security and an extra set of robust communications tools. Single sign-on (SSO) systems create a single
RingCentral Meetings QuickStart Guide
 RingCentral Meetings QuickStart Guide RingCentral Meetings empowers your workforce to collaborate from any location with face-to-face online meetings in high definition. Share your screen, websites, documents,
RingCentral Meetings QuickStart Guide RingCentral Meetings empowers your workforce to collaborate from any location with face-to-face online meetings in high definition. Share your screen, websites, documents,
Deploy Webex Video Mesh
 Video Mesh Deployment Task Flow, on page 1 Install Webex Video Mesh Node Software, on page 2 Log in to the Webex Video Mesh Node Console, on page 4 Set the Network Configuration of the Webex Video Mesh
Video Mesh Deployment Task Flow, on page 1 Install Webex Video Mesh Node Software, on page 2 Log in to the Webex Video Mesh Node Console, on page 4 Set the Network Configuration of the Webex Video Mesh
What desktop integrations are available using Productivity Tools?
 General Questions, page 1 Installation and Configuration, page 2 Scheduling Meetings using, page 4 Instant Meetings using, page 5 Site Administration, page 8 General Questions What are WebEx? What desktop
General Questions, page 1 Installation and Configuration, page 2 Scheduling Meetings using, page 4 Instant Meetings using, page 5 Site Administration, page 8 General Questions What are WebEx? What desktop
