CYBEX SECURE DESKTOP KVM SWITCHING SOLUTIONS. Achieve New Levels of Desktop Security, Control and Productivity
|
|
|
- Brett Underwood
- 5 years ago
- Views:
Transcription
1 CYBEX SECURE DESKTOP KVM SWITCHING SOLUTIONS Achieve New Levels of Desktop Security, Control and Productivity
2 CYBEX SECURE DESKTOP KVM SWITCHING SOLUTIONS Every day, news headlines report another cyber security breach. Military and government agencies, financial institutions, national health plans, large media companies and multi-national retail chains none have been immune to major security events. While the importance of security at the network level has long been recognized, security management at the desktop has sometimes been overlooked. But each desktop computer or device offers a potential point of entry into your network. Laptops, PCs, smartphones, tablets all of these can be the catalyst for malicious attack or intellectual property theft. Whether you are running a company with limited IT resources or managing a department within a large company, protecting the desktop environment is critical to reducing risk and abiding by privacy and security regulations. The Vertiv Cybex secure desktop KVM portfolio offers a proven solution for guarding against cyber intrusion at the desktop. These KVMs are designed to meet the stringent specifications of the U.S. government and are certified to the latest NAIP / Common Criteria protection profile for peripheral sharing switches version 3.0. With more Cybex KVM switches deployed in military and intelligence agencies than any other brand, Vertiv continues to be the most trusted product for securing the desktop environment. Cybex KVM switches deliver strong, effective security management designed to: yprevent unauthorized access by and to peripheral devices ydeliver transparent security that does not impede user productivity CAC Reader SC845 Series 4-port KVM Switch The Vertiv Cybex SC 800 and SC 900 Series Switches provide outstanding security, streamlined connectivity and advanced control of desktop resources. 2
3 The Industry s Most Extensive Desktop Security Capabilities The Vertiv Cybex SC KVM series delivers outstanding control through an extensive suite of security capabilities: ysupport for USB authentication devices. A CAC port provides secure connection to common access cards for authenticating users. An optional dedicated peripheral port supports additional types of authentication devices, such as facial recognition and fingerprint readers. Only Vertiv offers a dedicated peripheral port certified to the latest National Information Assurance Partnership (NIAP) Protection Profile V3.0 for peripheral-sharing switches. yunique NUM Lock, CAPS Lock and Scroll Lock indicators. While the Vertiv Cybex series maintains unidirectional data flow, it also provides indicators that alert users when the NUM Lock, CAPS Lock or Scroll Lock is on to improve ease of use. yperipheral isolation. A unidirectional optical data diode for each channel assures data can flow from the USB device to the host computer only, providing complete isolation. yalways-on anti-tampering system. The active anti-tampering system and holographic tampering-evident labels alert the user if someone has attempted to physically penetrate the KVM switch. In addition, locked memory prevents attempts to alter the switch by reprogramming the firmware. yeavesdropping prevention. Patented emulation technology prevents Display Data Channel (DDC) signal leakage and guards against signal attacks. yautomated access prevention. The Cybex KVM switch monitors all the devices attached to it, ignoring any access attempts by unauthorized USB devices. ydiscrete processing paths. Isolated ports on the switch provide discrete processing paths to each system, preventing data leakage, transfer or crosstalk between adjacent ports. With these discrete paths, a single KVM switch can support a mix of secure and unsecured systems. yno keyboard buffering. Hardware-based peripheral isolation loads all firmware on ROM with no keyboard buffering or memory. When data is transmitted to or from the desktop, the Vertiv Cybex KVM switch will automatically clear the buffer immediately after the transmission, ensuring no data is ever left in the buffer where it could be compromised. 3
4 CYBEX SECURE DESKTOP KVM SWITCHING SOLUTIONS A PROVEN SOLUTION FOR SECURING THE DESKTOP yover 800,000 switches deployed yhighest security with several models designed to NIAP Peripheral Sharing Switch protection profile 3.0 y27 years of experience in the KVM market High Security with Greater Flexibility and Lower Costs With Vertiv, there s no need to sacrifice productivity and lower costs for greater security. The Cybex Secure KVM series combines its extensive security capabilities with outstanding ease of use. You can easily provide access to multiple systems through a single monitor, keyboard and mouse. Reduce costs A user can access multiple systems with just a single keyboard, monitor and mouse, eliminating the cost of purchasing multiple sets of peripherals for each desktop. Fewer peripherals means lower energy consumption, less workstation space needed per user, and less validation and inspection costs per user. Gain true image reproduction and display flexibility Cybex KVM switches offer the industry s broadest range of video connections including DVI-I, HDMI and DP; and support for resolutions up to UHD 4K to make sure image quality is highly accurate and video plays at the highest definition possible. 4
5 Choose the Cybex Secure KVM Switch That Best Meets Your Needs Vertiv uses the most sophisticated technology and manufacturing process to ensure the highest performance and reliability in its secure desktop KVM switches. The Vertiv portfolio of secure desktop KVM solutions includes the industry leading Avocent SwitchView SC and Vertiv Cybex SC family of offerings. Vertiv Cybex SC800 Series Vertiv Cybex SC900 Series Four secure, isolated channels Ultra HD/4K Resolution Support for DVI-I, HDMI or DP CAC/DPP option available Single monitor support NIAP Protection Profile for Peripheral Switching Switches v. 3.0 Four secure, isolated channels Ultra HD/4K Resolution Support for DVI-I, HDMI or DP CAC/DPP option available Dual monitor support NIAP Protection Profile for Peripheral Switching Switches v. 3.0 Avocent SwitchView SC600 Series Avocent SwitchView SC700 Series Two, four or eight secure, isolated channels High resolution DVI-I CAC option available Single monitor support EAL2+ Four or eight secure, isolated channels High resolution DVI-I CAC option available Dual monitor support EAL2+ Cables sold separately. The Avocent SwitchView SC secure switches are compatible with most keyboards, mice, monitors and smart card readers. For specific configuration questions, contact an Avocent customer representative. All Avocent SwitchView SC switches listed are NIAP Common Criteria validated GSA Schedule: GS-35F-0264K 5
6 VertivCo.com Vertiv Headquarters, 1050 Dearborn Drive, Columbus, OH, 43085, USA 2016 Vertiv Co. All rights reserved. Vertiv and the Vertiv logo are trademarks or registered trademarks of Vertiv Co. All other names and logos referred to are trade names, trademarks or registered trademarks of their respective owners. While every precaution has been taken to ensure accuracy and completeness herein, Vertiv Co. assumes no responsibility, and disclaims all liability, for damages resulting from use of this information or for any errors or omissions. Specifications are subject to change without notice. AV (R11/15)
Achieve New Levels of Desktop Security, Control and Productivity. Emerson Cybex Secure Desktop KVM Switching Solutions
 Achieve New Levels of Desktop Security, Control and Productivity Emerson Cybex Secure Desktop KVM Switching Solutions Every day, news headlines report another cyber security breach. Military and government
Achieve New Levels of Desktop Security, Control and Productivity Emerson Cybex Secure Desktop KVM Switching Solutions Every day, news headlines report another cyber security breach. Military and government
DESKTOP KM SWITCHES Critical Decisions Require Real-time Access to Information
 DESKTOP KM SWITCHES Critical Decisions Require Real-time Access to Information VERTIV DESKTOP KM SWITCHES In demanding, fast-paced environments, such as emergency and utility control centers, professionals
DESKTOP KM SWITCHES Critical Decisions Require Real-time Access to Information VERTIV DESKTOP KM SWITCHES In demanding, fast-paced environments, such as emergency and utility control centers, professionals
The Ultimate Secure KVM Solution. Product Highlights. K248E 8-Port Dual-Head Secure KVM Switch
 Product Highlights Dual-head support Support four computers each one two displays. Support any resolution. Can drive VGA, HDMI single-link and dual-link DVI. Unidirectional optical data diodes Assuring
Product Highlights Dual-head support Support four computers each one two displays. Support any resolution. Can drive VGA, HDMI single-link and dual-link DVI. Unidirectional optical data diodes Assuring
The Ultimate Secure KVM Solution. Product Highlights. K244/E 4-Ports Dual-Head DVI Secure KVM Switch
 Product Highlights Dual-head support Support four computers each one two displays. Support any resolution. Can drive VGA, HDMI single-link and dual-link DVI. Unidirectional optical data diodes Assuring
Product Highlights Dual-head support Support four computers each one two displays. Support any resolution. Can drive VGA, HDMI single-link and dual-link DVI. Unidirectional optical data diodes Assuring
What is a Secure KVM Matrix? Product Highlights. The Ultimate Secure KVM Solution. K224/E 4-Ports Dual Display Secure KVM Matrix
 Product Highlights Dual displays support Support two independent user displays at any resolution. Any input can be switched to any output. Support HDMI and dual-link DVI. Unidirectional optical data diodes
Product Highlights Dual displays support Support two independent user displays at any resolution. Any input can be switched to any output. Support HDMI and dual-link DVI. Unidirectional optical data diodes
THE HSL SECURE KVM COMBINERS. Simultaneously interact with multiple computers on the same screen
 THE HSL SECURE KVM COMBINERS Simultaneously interact with multiple computers on the same screen THE NEED 1 Demanding environments require real-time presentation of information from isolated computers on
THE HSL SECURE KVM COMBINERS Simultaneously interact with multiple computers on the same screen THE NEED 1 Demanding environments require real-time presentation of information from isolated computers on
SECURE KVM SWITCHES SOLUTIONS BROCHURE BLACKBOX.COM/SECUREKVM
 SECURE KVM SWITCHES SOLUTIONS BROCHURE 1.877.877.2269 BLACKBOX.COM/SECUREKVM COMBAT THE VARIETY OF SECURITY THREATS THAT ARISE WHEN SHARING PERIPHERALS BETWEEN COMPUTER NETWORKS WITH DIFFERENT SECURITY
SECURE KVM SWITCHES SOLUTIONS BROCHURE 1.877.877.2269 BLACKBOX.COM/SECUREKVM COMBAT THE VARIETY OF SECURITY THREATS THAT ARISE WHEN SHARING PERIPHERALS BETWEEN COMPUTER NETWORKS WITH DIFFERENT SECURITY
Product Highlights. What is a Secure KVM Combiner? Why K40x? K402/E K404/E 2/4-Ports Secure KVM Combiner
 Product Highlights Works simultaneously with 2 / 4 isolated networks User can work in a single display while accessing 2 / 4 isolated networks having different security levels through windows. Highest
Product Highlights Works simultaneously with 2 / 4 isolated networks User can work in a single display while accessing 2 / 4 isolated networks having different security levels through windows. Highest
SECURING ENERGY COMPANY DESKTOPS from Cyber Threats with the Latest KVM Technology
 SECURING ENERGY COMPANY DESKTOPS from Cyber Threats with the Latest KVM Technology The threat of debilitating cyber-attacks is at an alltime high. It seems as if cyber criminals are now more sophisticated,
SECURING ENERGY COMPANY DESKTOPS from Cyber Threats with the Latest KVM Technology The threat of debilitating cyber-attacks is at an alltime high. It seems as if cyber criminals are now more sophisticated,
AVOCENT SOLUTIONS FOR THE BROADCAST CONTROL ROOM Driving Innovation in Omni-Platform Broadcasting
 AVOCENT SOLUTIONS FOR THE BROADCAST CONTROL ROOM Driving Innovation in Omni-Platform Broadcasting AVOCENT SOLUTIONS FOR THE BROADCAST CONTROL ROOM The Control Room Challenge in an Omni-platform World The
AVOCENT SOLUTIONS FOR THE BROADCAST CONTROL ROOM Driving Innovation in Omni-Platform Broadcasting AVOCENT SOLUTIONS FOR THE BROADCAST CONTROL ROOM The Control Room Challenge in an Omni-platform World The
Advanced Secure 2-port Flip KM and KVM Switches
 Advanced Secure 2-port Flip KM and KVM Switches This Belkin product is certified by NIAP to the latest Common Criteria Protection Profile PSS Ver 3.0, which exceeds EAL4 and PP PSS Ver. 2.1. The Need Many
Advanced Secure 2-port Flip KM and KVM Switches This Belkin product is certified by NIAP to the latest Common Criteria Protection Profile PSS Ver 3.0, which exceeds EAL4 and PP PSS Ver. 2.1. The Need Many
Secure Desktop KVM Switch Update. Keep classified information classified.
 Secure Desktop KVM Switch Update Keep classified information classified. Introduction Until recently, the National Information Assurance Partnership (NIAP) used Common Criteria Evaluation & Validation
Secure Desktop KVM Switch Update Keep classified information classified. Introduction Until recently, the National Information Assurance Partnership (NIAP) used Common Criteria Evaluation & Validation
ARE YOUR RACK PDUS KEEPING YOU FROM OPTIMIZING POWER MANAGEMENT?
 ARE YOUR RACK PDUS KEEPING YOU FROM OPTIMIZING POWER MANAGEMENT? 1 ARE YOU ENSURING A HIGHLY AVAILABLE, GRID-TO-CHIP POWER CHAIN? As your data processing needs increase, you re experiencing rising power
ARE YOUR RACK PDUS KEEPING YOU FROM OPTIMIZING POWER MANAGEMENT? 1 ARE YOU ENSURING A HIGHLY AVAILABLE, GRID-TO-CHIP POWER CHAIN? As your data processing needs increase, you re experiencing rising power
AVOCENT LONGVIEW 3000 SERIES
 AVOCENT LONGVIEW 3000 SERIES HIGH PERFORMANCE KVM EXTENDER SYSTEMS LongView Extender Single-user Configuration Up to 300 meters separation Transmitter Extender Additional CAT x link Receiver Extender Additional
AVOCENT LONGVIEW 3000 SERIES HIGH PERFORMANCE KVM EXTENDER SYSTEMS LongView Extender Single-user Configuration Up to 300 meters separation Transmitter Extender Additional CAT x link Receiver Extender Additional
The Belkin Advanced Secure windowing kvm
 Validated EAL 4+ The Belkin Advanced Secure windowing kvm The Current Situation There are many cases where analysts and operators need to work simultaneously with multiple computers and limited desktop
Validated EAL 4+ The Belkin Advanced Secure windowing kvm The Current Situation There are many cases where analysts and operators need to work simultaneously with multiple computers and limited desktop
REMOTE ACCESS AND CONTROL SOLUTIONS
 REMOTE ACCESS AND CONTROL SOLUTIONS What is a KVM switch? KVM switches enable users to access and control multiple computer devices from a single keyboard, video and mouse (KVM) console. This includes
REMOTE ACCESS AND CONTROL SOLUTIONS What is a KVM switch? KVM switches enable users to access and control multiple computer devices from a single keyboard, video and mouse (KVM) console. This includes
Vertiv Cybex SC Switching System. Installer/User Guide
 Vertiv Cybex SC Switching System Installer/User Guide Technical Support Site If you encounter any installation or operational issues with your product, check the pertinent section of this manual to see
Vertiv Cybex SC Switching System Installer/User Guide Technical Support Site If you encounter any installation or operational issues with your product, check the pertinent section of this manual to see
ADVANCED 4/8 PORT DVI-D MATRIX SECURE KVM SWITCH
 ADVANCED 4/8 PORT DVI-D MATRIX SECURE KVM SWITCH USM-2S0-3M1 REV: 1.00 DATE: 04/03/2018 CONSOLE 3 CONSOLE 4 SS8P-DVI-8X4-U 8 PORT DVI-D W/ AUDIO AND MODELS: SS4P-DVI-4X2-U SS4P-DVI-4X4-U SS8P-DVI-8X2-U
ADVANCED 4/8 PORT DVI-D MATRIX SECURE KVM SWITCH USM-2S0-3M1 REV: 1.00 DATE: 04/03/2018 CONSOLE 3 CONSOLE 4 SS8P-DVI-8X4-U 8 PORT DVI-D W/ AUDIO AND MODELS: SS4P-DVI-4X2-U SS4P-DVI-4X4-U SS8P-DVI-8X2-U
K202B & K202D Secure KVM Switch: 2-Port, DVI Video. User Manual
 K202B & K202D Secure KVM Switch: 2-Port, DVI Video User Manual Models: K202B Secure 2-port DVI-I KVM Switch w/audio K202D Secure 2-port DVI-D KVM Switch w/audio Rev: 2. Doc No.: HDC06143 Table of Content
K202B & K202D Secure KVM Switch: 2-Port, DVI Video User Manual Models: K202B Secure 2-port DVI-I KVM Switch w/audio K202D Secure 2-port DVI-D KVM Switch w/audio Rev: 2. Doc No.: HDC06143 Table of Content
THE BELKIN ADVANCED SECURE KM SWITCH
 NIAP PP PSS 3.0 CERTIFIED C O M M O N C R I A I T E R This Belkin product is certified by NIAP to the latest Common Criteria Protection Profile PSS Ver 3.0, which exceeds EAL4 and PP PSS Ver. 2.. THE BELKIN
NIAP PP PSS 3.0 CERTIFIED C O M M O N C R I A I T E R This Belkin product is certified by NIAP to the latest Common Criteria Protection Profile PSS Ver 3.0, which exceeds EAL4 and PP PSS Ver. 2.. THE BELKIN
Advanced 2/4-Port DisplayPort Secure KVM Switch
 Document ID: DOC-IPG-2008 Revision: 1.10 Release Date: December 13, 2016 Advanced 2/4-Port DisplayPort Secure KVM Switch USER MANUAL SDPN-2S SDPN-2D SDPN-2S-P SDPN-2D-P SDPN-4S SDPN-4D SDPN-4S-P SDPN-4D-P
Document ID: DOC-IPG-2008 Revision: 1.10 Release Date: December 13, 2016 Advanced 2/4-Port DisplayPort Secure KVM Switch USER MANUAL SDPN-2S SDPN-2D SDPN-2S-P SDPN-2D-P SDPN-4S SDPN-4D SDPN-4S-P SDPN-4D-P
Avocent Switchview Dvi 4-port Kvm Switch Manual
 Avocent Switchview Dvi 4-port Kvm Switch Manual Avocent SwitchView DVI: Compare Avocent SwitchView DVI 2 Port & competing KVM Switch technologies from leading KVM manufacturers. shutdown a pc in lan avocent
Avocent Switchview Dvi 4-port Kvm Switch Manual Avocent SwitchView DVI: Compare Avocent SwitchView DVI 2 Port & competing KVM Switch technologies from leading KVM manufacturers. shutdown a pc in lan avocent
Document ID: DOC-IPG-2004 Revision: 1.10 Release Date: December 13th, Advanced 2/4-Port DVI-I Secure KVM Switch
 Document ID: DOC-IPG-2004 Revision: 1.10 Release Date: December 13th, 2016 Advanced 2/4-Port DVI-I Secure KVM Switch USER MANUAL SDVN-2S SDVN-2D SDVN-2S-P SDVN-2D-P SDVN-4S SDVN-4D SDVN-4S-P SDVN-4D-P
Document ID: DOC-IPG-2004 Revision: 1.10 Release Date: December 13th, 2016 Advanced 2/4-Port DVI-I Secure KVM Switch USER MANUAL SDVN-2S SDVN-2D SDVN-2S-P SDVN-2D-P SDVN-4S SDVN-4D SDVN-4S-P SDVN-4D-P
Advanced 8-Port DisplayPort Secure KVM Switch
 Document ID: DOC-IPG-2022 Revision: 1.10 Release Date: January 4, 2018 USER MANUAL SDPN-8S SDPN-2S-P 8-Port Secure DisplayPort KVM with Audio 2-Port Secure DisplayPort KVM with Audio and CAC Support Made
Document ID: DOC-IPG-2022 Revision: 1.10 Release Date: January 4, 2018 USER MANUAL SDPN-8S SDPN-2S-P 8-Port Secure DisplayPort KVM with Audio 2-Port Secure DisplayPort KVM with Audio and CAC Support Made
User Manual. User Manual: K244E Secure KVM Switch: 4-Port, Dual Head, DVI Video, DPP port
 User Manual: K244E Secure KVM Switch: 4-Port, Dual Head, DVI Video, DPP port User Manual Model covered in this user manual: K244E Secure 4-port Dual-Head DVI-I KVM Switch w/audio and DPP Rev: 2.4 Doc No:
User Manual: K244E Secure KVM Switch: 4-Port, Dual Head, DVI Video, DPP port User Manual Model covered in this user manual: K244E Secure 4-port Dual-Head DVI-I KVM Switch w/audio and DPP Rev: 2.4 Doc No:
Advanced 2/4 Port DisplayPort to HDMI Secure KVM
 Document ID: USM-0S0-1M4 Revision: 1.11 Release Date: July 3rd, 2018 Advanced 2/4 Port DisplayPort to HDMI Secure KVM USER MANUAL SDHN-2S-P SDHN-2D-P SDHN-4S-P SDHN-4D-P SDHN-4Q-P 2 Port Secure Single-Head
Document ID: USM-0S0-1M4 Revision: 1.11 Release Date: July 3rd, 2018 Advanced 2/4 Port DisplayPort to HDMI Secure KVM USER MANUAL SDHN-2S-P SDHN-2D-P SDHN-4S-P SDHN-4D-P SDHN-4Q-P 2 Port Secure Single-Head
Certification Report
 Certification Report Avocent Cybex SwitchView SC Series Switches Issued by: Communications Security Establishment Certification Body Canadian Common Criteria Evaluation and Certification Scheme Government
Certification Report Avocent Cybex SwitchView SC Series Switches Issued by: Communications Security Establishment Certification Body Canadian Common Criteria Evaluation and Certification Scheme Government
Advanced 4/8-Port DVI-D Matrix KVM
 Document ID: USM-0S0-3M1 Revision: 2.10 Release Date: July 3rd, 2018 CONSOLE 3 CONSOLE 4 SDVN-44-X OR OR OR OR Advanced 4/8-Port DVI-D Matrix KVM USER MANUAL SDVN-42-X SDVN-44-X SDVN-82-X SDVN-84-X 4-Port
Document ID: USM-0S0-3M1 Revision: 2.10 Release Date: July 3rd, 2018 CONSOLE 3 CONSOLE 4 SDVN-44-X OR OR OR OR Advanced 4/8-Port DVI-D Matrix KVM USER MANUAL SDVN-42-X SDVN-44-X SDVN-82-X SDVN-84-X 4-Port
Advanced 2/4/8-Port DisplayPort Secure KVM Switch
 Document ID: USM-0S0-MM3 Revision: 1.11 Release Date: July 3rd, 2018 USER MANUAL SDPN-2S SDPN-2D SDPN-2S-P SDPN-2D-P SDPN-4S SDPN-4D SDPN-4S-P SDPN-4D-P SDPN-4Q-P SDPN-8S SDPN-8S-P 2-Port Secure DisplayPort
Document ID: USM-0S0-MM3 Revision: 1.11 Release Date: July 3rd, 2018 USER MANUAL SDPN-2S SDPN-2D SDPN-2S-P SDPN-2D-P SDPN-4S SDPN-4D SDPN-4S-P SDPN-4D-P SDPN-4Q-P SDPN-8S SDPN-8S-P 2-Port Secure DisplayPort
K208E/248E/2016E Secure Large KVM Switches w/dpp. User Manual
 K208E/248E/2016E Secure Large KVM Switches w/dpp User Manual Model covered in this user manual: K208E - Secure 8-port Single-Head DVI-I KVM Switch w/ DPP K248E - Secure 8-port Dual-Head DVI-I KVM Switch
K208E/248E/2016E Secure Large KVM Switches w/dpp User Manual Model covered in this user manual: K208E - Secure 8-port Single-Head DVI-I KVM Switch w/ DPP K248E - Secure 8-port Dual-Head DVI-I KVM Switch
Advanced 2/4/8/16-Port DVI-I Secure KVM
 Document ID: USM-0S0-MM1 Revision: 2.10 Release Date: July 3rd, 2018 Advanced 2/4/8/16-Port DVI-I Secure KVM USER MANUAL SDVN-2S SDVN-2D SDVN-2S-P SDVN-2D-P SDVN-4S SDVN-4D SDVN-4S-P SDVN-4D-P SDVN-4Q-P
Document ID: USM-0S0-MM1 Revision: 2.10 Release Date: July 3rd, 2018 Advanced 2/4/8/16-Port DVI-I Secure KVM USER MANUAL SDVN-2S SDVN-2D SDVN-2S-P SDVN-2D-P SDVN-4S SDVN-4D SDVN-4S-P SDVN-4D-P SDVN-4Q-P
Advanced 4-Port DVI-I Secure KVM Switch
 Document ID: USM-0S0-421 Revision: 1.20 Release Date: July 3rd, 2018 SDMN-4S-P 1 2 3 4 Full PIP QuadT QuadQ Select Preview Advanced 4-Port DVI-I Secure KVM Switch USER MANUAL SDMN-4S-P 4-port Secure DVI-I
Document ID: USM-0S0-421 Revision: 1.20 Release Date: July 3rd, 2018 SDMN-4S-P 1 2 3 4 Full PIP QuadT QuadQ Select Preview Advanced 4-Port DVI-I Secure KVM Switch USER MANUAL SDMN-4S-P 4-port Secure DVI-I
National Information Assurance Partnership. Common Criteria Evaluation and Validation Scheme. Validation Report. Tripp Lite Secure KVM Switch Series
 National Information Assurance Partnership Common Criteria Evaluation and Validation Scheme TM Validation Report Report Number: CCEVS-VR-VID10481-2011 Dated: October 31, 2011 Version: 2.0 National Institute
National Information Assurance Partnership Common Criteria Evaluation and Validation Scheme TM Validation Report Report Number: CCEVS-VR-VID10481-2011 Dated: October 31, 2011 Version: 2.0 National Institute
APPLYING DATA CENTER INFRASTRUCTURE MANAGEMENT IN COLOCATION DATA CENTERS
 APPLYING DATA CENTER INFRASTRUCTURE MANAGEMENT IN COLOCATION DATA CENTERS Table of Contents Executive Summary 3 The Colocation Market 4 An Introduction to DCIM 5 The Value of DCIM for Colocation Providers
APPLYING DATA CENTER INFRASTRUCTURE MANAGEMENT IN COLOCATION DATA CENTERS Table of Contents Executive Summary 3 The Colocation Market 4 An Introduction to DCIM 5 The Value of DCIM for Colocation Providers
National Information Assurance Partnership. Common Criteria Evaluation and Validation Scheme. Validation Report. for
 National Information Assurance Partnership Common Criteria Evaluation and Validation Scheme TM Validation Report for of Peripheral Sharing Switches Report Number: CCEVS-VR-10822-2018 Dated: January 29,
National Information Assurance Partnership Common Criteria Evaluation and Validation Scheme TM Validation Report for of Peripheral Sharing Switches Report Number: CCEVS-VR-10822-2018 Dated: January 29,
ADVANCED 1/2/4-PORT DVI-I SECURE KVM SWITCH
 ADVANCED 1/2/4-PORT DVI-I SECURE KVM SWITCH USM-2S0-MM1 REV: 1.1 DATE: 08/11/2017 1 2 3 4 SS4P-SH-DVI-U SECURE KVM SWITCH 4 PORT DVI-I W/ AUDIO AND MODELS: SI1P-SH-DVI-U SS2P-SH-DVI-U SS2P-DH-DVI-U SS2P-SH-DVI-U
ADVANCED 1/2/4-PORT DVI-I SECURE KVM SWITCH USM-2S0-MM1 REV: 1.1 DATE: 08/11/2017 1 2 3 4 SS4P-SH-DVI-U SECURE KVM SWITCH 4 PORT DVI-I W/ AUDIO AND MODELS: SI1P-SH-DVI-U SS2P-SH-DVI-U SS2P-DH-DVI-U SS2P-SH-DVI-U
National Information Assurance Partnership. Common Criteria Evaluation and Validation Scheme
 National Information Assurance Partnership Common Criteria Evaluation and Validation Scheme TM Validation Report Report Number: CCEVS-VR-10446-2011 Dated: July 1, 2011 Version: 1.0 National Institute of
National Information Assurance Partnership Common Criteria Evaluation and Validation Scheme TM Validation Report Report Number: CCEVS-VR-10446-2011 Dated: July 1, 2011 Version: 1.0 National Institute of
USER GUIDE TABLE OF CONTENTS TECHNICAL SPECIFICATIONS WHAT S IN THE BOX? SECURITY FEATURES SECURE KVM SWITCH FRONT AND REAR INSTALLATION
 ADVANCED 2/4/8-PORT DISPLAYPORT SECURE KVM SWITCH USM-2S0-MM3 REV: 1.1A DATE: 07/03/2018 1 2 3 4 SS4P-SH-DP-U SECURE KVM SWITCH 4 PORT DP W/ AUDIO AND MODELS: SS2P-SH-DP-U SS2P-SH-DP-U SS2P-DH-DP-U SS2P-DH-DP-U
ADVANCED 2/4/8-PORT DISPLAYPORT SECURE KVM SWITCH USM-2S0-MM3 REV: 1.1A DATE: 07/03/2018 1 2 3 4 SS4P-SH-DP-U SECURE KVM SWITCH 4 PORT DP W/ AUDIO AND MODELS: SS2P-SH-DP-U SS2P-SH-DP-U SS2P-DH-DP-U SS2P-DH-DP-U
Secure KVM switching Assured separation with easy access
 Secure KVM switching Assured separation with easy access As specialists in computer switching since 1984, the engineers at Adder Technology have designed many products that transfer data between systems
Secure KVM switching Assured separation with easy access As specialists in computer switching since 1984, the engineers at Adder Technology have designed many products that transfer data between systems
ADVANCED 4/8-PORT SECURE KM SWITCH
 ADVANCED 4/8-PORT SECURE KM SWITCH USM-2S0-1M0 REV: 1.1 DATE: 09/11/2017 1 2 3 4 SS4P-KM-U SECURE KM SWITCH 4 PORT W/ AUDIO MODELS: SS4P-KM-U SS4P-KM-UCAC SS8P-KM-U SS8P-KM-UCAC 4-Port Secure KM Switch
ADVANCED 4/8-PORT SECURE KM SWITCH USM-2S0-1M0 REV: 1.1 DATE: 09/11/2017 1 2 3 4 SS4P-KM-U SECURE KM SWITCH 4 PORT W/ AUDIO MODELS: SS4P-KM-U SS4P-KM-UCAC SS8P-KM-U SS8P-KM-UCAC 4-Port Secure KM Switch
Performance and Compliance Made Easy
 Performance and Compliance Made Easy Why Belkin? As a proven technology leader for more than 25 years, Belkin International, Inc., has provided public and private sector organizations with high-quality,
Performance and Compliance Made Easy Why Belkin? As a proven technology leader for more than 25 years, Belkin International, Inc., has provided public and private sector organizations with high-quality,
THE CHALLENGES WITH A COLOCATION ROLL-OUT: And how to simplify the deployment and maintenance of IT equipment at the colocation facility
 THE CHALLENGES WITH A COLOCATION ROLL-OUT: And how to simplify the deployment and maintenance of IT equipment at the colocation facility TWO STAGE POWER DISTRIBUTION Executive Summary Colocation services
THE CHALLENGES WITH A COLOCATION ROLL-OUT: And how to simplify the deployment and maintenance of IT equipment at the colocation facility TWO STAGE POWER DISTRIBUTION Executive Summary Colocation services
The Ultimate Secure KVM Solution. Product Highlights. What is a KVM Combiner? Why modular? K600 Modular KVM Combiner
 Product Highlights Operates between Highest Security Level Gaps Designed for safe isolation between national security and the internet. Mouse controlled windowing Highly-intuitive and easy operation. Superior
Product Highlights Operates between Highest Security Level Gaps Designed for safe isolation between national security and the internet. Mouse controlled windowing Highly-intuitive and easy operation. Superior
Assurance Activity Report for Belkin Secure F1 DP/HDMI to DP/HDMI KVMs w/ CAC v33303-c6c6
 Belkin Secure F1 DP/HDMI to DP/HDMI KVMs w/ CAC Version: 1.3 6 November 2018 Prepared by: EWA-Canada, An Intertek Company 1223 Michael Street North, Suite 200 Ottawa, Ontario, Canada K1J 7T2 Prepared for:
Belkin Secure F1 DP/HDMI to DP/HDMI KVMs w/ CAC Version: 1.3 6 November 2018 Prepared by: EWA-Canada, An Intertek Company 1223 Michael Street North, Suite 200 Ottawa, Ontario, Canada K1J 7T2 Prepared for:
4-Port Single-head Secure Pro DVI-D KVM Switch with KB/Mouse USB emulation, CAC and Preview Screen
 4-Port Single-head Secure Pro DVI-D KVM Switch with KB/Mouse USB emulation, and Preview Screen USM-2S0-M21 REV: 1.1 DATE: 08/11/2017 1 2 3 4 Quad TQuad PIP Full Select Preview SECURE KVM SWITCH 4 PORT
4-Port Single-head Secure Pro DVI-D KVM Switch with KB/Mouse USB emulation, and Preview Screen USM-2S0-M21 REV: 1.1 DATE: 08/11/2017 1 2 3 4 Quad TQuad PIP Full Select Preview SECURE KVM SWITCH 4 PORT
Data Sheet Fujitsu Port Replicators Components Accessories
 Data Sheet Fujitsu Port Replicators Components Accessories Get connected to your peripherals in no time Flexibility, expandability, desktop replacement and investment protection are just few benefits of
Data Sheet Fujitsu Port Replicators Components Accessories Get connected to your peripherals in no time Flexibility, expandability, desktop replacement and investment protection are just few benefits of
Administrative Guide. Intended Audience This document is intended for the following professionals: System Administrators/IT Managers.
 Administrative Guide Introduction This Administrator Guide provides all the details you ll need to receive log and audit data from your new product. This Administrator Guide provides all the details required
Administrative Guide Introduction This Administrator Guide provides all the details you ll need to receive log and audit data from your new product. This Administrator Guide provides all the details required
National Information Assurance Partnership. Common Criteria Evaluation and Validation Scheme. Validation Report. for
 National Information Assurance Partnership Common Criteria Evaluation and Validation Scheme TM Validation Report for of Peripheral Sharing Switches Report Number: CCEVS-VR-10865-2018 Dated: February 13,
National Information Assurance Partnership Common Criteria Evaluation and Validation Scheme TM Validation Report for of Peripheral Sharing Switches Report Number: CCEVS-VR-10865-2018 Dated: February 13,
Solution. Imagine... a New World of Authentication.
 A Solution Imagine... a New World of Authentication. Imagine a World Where Passwords can t be hacked People can t share credentials Users can t pretend to be someone else Where authentication is more Secure
A Solution Imagine... a New World of Authentication. Imagine a World Where Passwords can t be hacked People can t share credentials Users can t pretend to be someone else Where authentication is more Secure
THE BELKIN ADVANCED SECURE WINDOWING KVM
 THE BELKIN ADVANCED SECURE WINDOWING KVM THE CURRENT SITUATION There are many cases where analysts and operators need to work simultaneously with multiple computers and limited desktop space. THE BELKIN
THE BELKIN ADVANCED SECURE WINDOWING KVM THE CURRENT SITUATION There are many cases where analysts and operators need to work simultaneously with multiple computers and limited desktop space. THE BELKIN
Vertiv Secure KM Switch Security Target
 Vertiv Secure KM Switch Security Target Release Date: Mar 28, 2017 Document ID: HDC11603 Revision: 4.1 Prepared By: Rick Holloway, Vertiv Page 1 Contents 1 Introduction... 7 1.1 ST and TOE Identification...
Vertiv Secure KM Switch Security Target Release Date: Mar 28, 2017 Document ID: HDC11603 Revision: 4.1 Prepared By: Rick Holloway, Vertiv Page 1 Contents 1 Introduction... 7 1.1 ST and TOE Identification...
2016 COOLING THE EDGE SURVEY. Conducted by Vertiv Publication Date: August 30, 2016
 2016 COOLING THE EDGE SURVEY Conducted by Vertiv Publication Date: August 30, 2016 TWO STAGE POWER DISTRIBUTION Table of Contents Section I: Methodology Section II: Key Findings 1. Strategic Importance
2016 COOLING THE EDGE SURVEY Conducted by Vertiv Publication Date: August 30, 2016 TWO STAGE POWER DISTRIBUTION Table of Contents Section I: Methodology Section II: Key Findings 1. Strategic Importance
2-Port Dual Monitor DVI KVM Switch, TAA, GSA with Audio and USB 2.0 Hub, Cables included
 2-Port Dual Monitor DVI KVM Switch, TAA, GSA with Audio and USB 2.0 Hub, Cables included MODEL NUMBER: B004-2DUA2-K Description Tripp Lite's B004-2DUA2-K 2-Port Dual Monitor DVI KVM Switch, TAA, GSA allows
2-Port Dual Monitor DVI KVM Switch, TAA, GSA with Audio and USB 2.0 Hub, Cables included MODEL NUMBER: B004-2DUA2-K Description Tripp Lite's B004-2DUA2-K 2-Port Dual Monitor DVI KVM Switch, TAA, GSA allows
VERTIV RACK PDUS. Power Perfectly Configured for Your IT Application
 VERTIV RACK PDUS Power Perfectly Configured for Your IT Application VERTIV RACK PDUS Enhanced Performance and Management of Dynamic IT Spaces Enhance Business Agility, Efficiency and Availability with
VERTIV RACK PDUS Power Perfectly Configured for Your IT Application VERTIV RACK PDUS Enhanced Performance and Management of Dynamic IT Spaces Enhance Business Agility, Efficiency and Availability with
Liebert. PDX and PCW Compact Perimeter Cooling Solutions
 PDX and PCW Perimeter Cooling Solutions LIEBERT PDX AND LIEBERT PCW Perimeter Cooling Solutions Introducing thermal management solutions that efficiently lower your operating costs and pack a lot of capacity
PDX and PCW Perimeter Cooling Solutions LIEBERT PDX AND LIEBERT PCW Perimeter Cooling Solutions Introducing thermal management solutions that efficiently lower your operating costs and pack a lot of capacity
1U Rack-Mount Console with 19" LCD, DVI or VGA
 1U Rack-Mount Console with 19" LCD, DVI or VGA MODEL NUMBER: B021-000-19-HD Description Need to add convenient rack-side access to securely manage and control your critical network systems? Tripp Lite's
1U Rack-Mount Console with 19" LCD, DVI or VGA MODEL NUMBER: B021-000-19-HD Description Need to add convenient rack-side access to securely manage and control your critical network systems? Tripp Lite's
Security Enhancements
 OVERVIEW Security Enhancements February 9, 2009 Abstract This paper provides an introduction to the security enhancements in Microsoft Windows 7. Built upon the security foundations of Windows Vista, Windows
OVERVIEW Security Enhancements February 9, 2009 Abstract This paper provides an introduction to the security enhancements in Microsoft Windows 7. Built upon the security foundations of Windows Vista, Windows
Liebert icom CMS Administration Portal. Installer/User Guide
 Liebert icom CMS Administration Portal Installer/User Guide Technical Support Site If you encounter any installation or operational issues with your product, check the pertinent section of this manual
Liebert icom CMS Administration Portal Installer/User Guide Technical Support Site If you encounter any installation or operational issues with your product, check the pertinent section of this manual
Assurance Activity Report for Belkin Secure 2 Ports Flip KVM Switch v33303-c6c6
 Belkin Secure 2 Ports Flip KVM Switch v33303-c6c6 Version: 1.2 6 November 2018 Prepared by: EWA-Canada 1223 Michael Street North, Suite 200 Ottawa, Ontario, Canada K1J 7T2 Prepared for: Communications
Belkin Secure 2 Ports Flip KVM Switch v33303-c6c6 Version: 1.2 6 November 2018 Prepared by: EWA-Canada 1223 Michael Street North, Suite 200 Ottawa, Ontario, Canada K1J 7T2 Prepared for: Communications
Assurance Activities Report for IOGEAR Secure KVM Switch
 Assurance Activities Report for IOGEAR Secure KVM Switch Version 1.1 01/19/2018 Prepared by: Leidos Inc. https://www.leidos.com/civil/commercial-cyber/product-compliance Common Criteria Testing Laboratory
Assurance Activities Report for IOGEAR Secure KVM Switch Version 1.1 01/19/2018 Prepared by: Leidos Inc. https://www.leidos.com/civil/commercial-cyber/product-compliance Common Criteria Testing Laboratory
Belkin Secure 2 port Flip DVI-D/VGA/DP KVM Switch User Manual
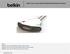 Models: F1DN102V Secure 2-port VGA KVM w/ audio and remote controller F1DN102F - Secure 2-port DVI-D single-link KVM w/ audio and remote controller F1DN102N - Secure 2-port DP KVM w/ audio and remote controller
Models: F1DN102V Secure 2-port VGA KVM w/ audio and remote controller F1DN102F - Secure 2-port DVI-D single-link KVM w/ audio and remote controller F1DN102N - Secure 2-port DP KVM w/ audio and remote controller
In today s business environment, data creates value so it s more important than ever to protect it as a vital business asset
 In today s business environment, data creates value so it s more important than ever to protect it as a vital business asset Seagate Secure Reliable Data Protection Solutions Always-on Data Protection
In today s business environment, data creates value so it s more important than ever to protect it as a vital business asset Seagate Secure Reliable Data Protection Solutions Always-on Data Protection
The Power of Being There. SwitchView Control your entire desktop with SwitchView Desktop KVM Switches
 The Power of Being There SwitchView Control your entire desktop with SwitchView KVM switches SwitchView Desktop KVM Switches THE EASE OF KVM Switching Avocent SwitchView desktop KVM switches offer the
The Power of Being There SwitchView Control your entire desktop with SwitchView KVM switches SwitchView Desktop KVM Switches THE EASE OF KVM Switching Avocent SwitchView desktop KVM switches offer the
Secure KVM Combiner SC21H-3 SC42DU/DHU/PHU-3 QUICK SETUP GUIDE. Models:
 SCH-3 SCDU/DHU/PHU-3 QUICK SETUP GUIDE Secure KVM Combiner Models: SCH-3 Secure -Port HDMI Video KVM Combiner, PP 3.0 SCDU-3 Secure P to P DVI Video KVM Combiner w/fusb SCDHU-3 Secure P DVI to P HDMI Video
SCH-3 SCDU/DHU/PHU-3 QUICK SETUP GUIDE Secure KVM Combiner Models: SCH-3 Secure -Port HDMI Video KVM Combiner, PP 3.0 SCDU-3 Secure P to P DVI Video KVM Combiner w/fusb SCDHU-3 Secure P DVI to P HDMI Video
Advanced 4/8 Port Secure KM Switch
 Document ID: DOC-IPG-2007 Revision: 1.10 Release Date: February 17th, 2017 Advanced 4/8 Port Secure KM Switch USER MANUAL SKMN-4S SKMN-4S-P SKMN-8S SKMN-8S-P 4-Port Secure KM with Audio 4-Port Secure KM
Document ID: DOC-IPG-2007 Revision: 1.10 Release Date: February 17th, 2017 Advanced 4/8 Port Secure KM Switch USER MANUAL SKMN-4S SKMN-4S-P SKMN-8S SKMN-8S-P 4-Port Secure KM with Audio 4-Port Secure KM
DATA CENTER TRANSFORMATION: THE IMPACT OF EMERGING POWER ARCHITECTURES ON TODAY S DATA CENTERS
 DATA CENTER TRANSFORMATION: THE IMPACT OF EMERIN POWER ARCHITECTRES ON TODAY S DATA CENTERS TWO STAE POWER DISTRIBTION Entering the Cloud eneration The unprecedented capacity requirements of large social
DATA CENTER TRANSFORMATION: THE IMPACT OF EMERIN POWER ARCHITECTRES ON TODAY S DATA CENTERS TWO STAE POWER DISTRIBTION Entering the Cloud eneration The unprecedented capacity requirements of large social
Raritan Secure Switch Administrator Guide
 Raritan Secure Switch Administrator Guide Release 1.0 Copyright 2018 Raritan, Inc. SecureSwitch_admin-0A-v1.0-E January 2018 255-80-0052-00 RoHS Raritan Secure Switch Series Administrator Guide version
Raritan Secure Switch Administrator Guide Release 1.0 Copyright 2018 Raritan, Inc. SecureSwitch_admin-0A-v1.0-E January 2018 255-80-0052-00 RoHS Raritan Secure Switch Series Administrator Guide version
User Manual. Secure Ultra High Def DP/HDMI to DP/HDMI KVM Switch
 NIAP PP PSS 3.0 CERTIFIED Secure Ultra High Def DP/HDMI to DP/HDMI KVM Switch C O M M O N C R I A I T E R This Belkin product is compliant with latest NIAP Protection Profile PSS Ver. 3.0, which exceeds
NIAP PP PSS 3.0 CERTIFIED Secure Ultra High Def DP/HDMI to DP/HDMI KVM Switch C O M M O N C R I A I T E R This Belkin product is compliant with latest NIAP Protection Profile PSS Ver. 3.0, which exceeds
Overview. Premium Data Sheet. DigitalPersona. DigitalPersona s Composite Authentication transforms the way IT
 DigitalPersona Premium Data Sheet Overview DigitalPersona s Composite Authentication transforms the way IT executives protect the integrity of the digital organization by going beyond traditional two-factor
DigitalPersona Premium Data Sheet Overview DigitalPersona s Composite Authentication transforms the way IT executives protect the integrity of the digital organization by going beyond traditional two-factor
Overview. DigitalPersona Logon for Windows Data Sheet. DigitalPersona s Composite Authentication transforms
 DigitalPersona Logon for Windows Data Sheet Overview DigitalPersona s Composite Authentication transforms the way IT executives protect the integrity of the digital organization by going beyond two-factor
DigitalPersona Logon for Windows Data Sheet Overview DigitalPersona s Composite Authentication transforms the way IT executives protect the integrity of the digital organization by going beyond two-factor
PROTECTION FOR WORKSTATIONS, SERVERS, AND TERMINAL DEVICES ENDPOINT SECURITY NETWORK SECURITY I ENDPOINT SECURITY I DATA SECURITY
 PROTECTION FOR WORKSTATIONS, SERVERS, AND TERMINAL DEVICES ENDPOINT SECURITY NETWORK SECURITY I ENDPOINT SECURITY I DATA SECURITY OUR MISSION Make the digital world a sustainable and trustworthy environment
PROTECTION FOR WORKSTATIONS, SERVERS, AND TERMINAL DEVICES ENDPOINT SECURITY NETWORK SECURITY I ENDPOINT SECURITY I DATA SECURITY OUR MISSION Make the digital world a sustainable and trustworthy environment
REMOTE IT MANAGEMENT SOLUTIONS: MANAGE REMOTE OFFICES WITHOUT LEAVING YOURS
 REMOTE IT MANAGEMENT SOLUTIONS: MANAGE REMOTE OFFICES WITHOUT LEAVING YOURS IT Challenges AT THE REMOTE OFFICE Compared to data centers, remote offices and facilities pose unique hardware and IT management
REMOTE IT MANAGEMENT SOLUTIONS: MANAGE REMOTE OFFICES WITHOUT LEAVING YOURS IT Challenges AT THE REMOTE OFFICE Compared to data centers, remote offices and facilities pose unique hardware and IT management
National Information Assurance Partnership. Common Criteria Evaluation and Validation Scheme. Validation Report. for
 National Information Assurance Partnership Common Criteria Evaluation and Validation Scheme TM Validation Report for Report Number: CCEVS-VR-10772-2017 Dated: March 9, 2017 Version: 1.0 National Institute
National Information Assurance Partnership Common Criteria Evaluation and Validation Scheme TM Validation Report for Report Number: CCEVS-VR-10772-2017 Dated: March 9, 2017 Version: 1.0 National Institute
VERTIV LIFE SERVICES. Remote Diagnostic and Preventive Monitoring
 VERTIV LIFE SERVICES Remote Diagnostic and Preventive Monitoring VERTIV LIFE SERVICES REMOTE DIAGNOSTIC AND PREVENTIVE MONITORING Vertiv LIFE Services, provides Remote Diagnostics and Preventive Monitoring
VERTIV LIFE SERVICES Remote Diagnostic and Preventive Monitoring VERTIV LIFE SERVICES REMOTE DIAGNOSTIC AND PREVENTIVE MONITORING Vertiv LIFE Services, provides Remote Diagnostics and Preventive Monitoring
Custom Monitor Configuration Guide
 F1DN104K-3 F1DN108K-3 Custom Monitor Configuration Guide May, 2018 LNKPG-00559 Rev. A00 Introduction The Secure KM Switch Viewing and Interacting with Multiple Systems Simultaneously The Secure KM Switch
F1DN104K-3 F1DN108K-3 Custom Monitor Configuration Guide May, 2018 LNKPG-00559 Rev. A00 Introduction The Secure KM Switch Viewing and Interacting with Multiple Systems Simultaneously The Secure KM Switch
Owner s Manual. Secure KVM Switches, NIAP Protection Profile Version 3.0
 Owner s Manual Secure KVM Switches, NIAP Protection Profile Version 3.0 DisplayPort Models: B002-DP1A4, B002-DP2A4, B002-DP2AC4 DVI Models: B002-DV1A2, B002-DV1A4, B002-DV1AC4, B002-DV1AC8, B002-DV2A4,
Owner s Manual Secure KVM Switches, NIAP Protection Profile Version 3.0 DisplayPort Models: B002-DP1A4, B002-DP2A4, B002-DP2AC4 DVI Models: B002-DV1A2, B002-DV1A4, B002-DV1AC4, B002-DV1AC8, B002-DV2A4,
... Amazing Performance.
 ... Amazing Performance. DEAR BUSINESS PARTNERS, AND CUSTOMERS. USB 3.1 SuperSpeed+ is the connection of the future. It is fast becoming the new universal connection standard and is already supported by
... Amazing Performance. DEAR BUSINESS PARTNERS, AND CUSTOMERS. USB 3.1 SuperSpeed+ is the connection of the future. It is fast becoming the new universal connection standard and is already supported by
Certification Report
 Certification Report EAL 4+ Evaluation of High Security Labs Secure DVI KVM Switch, Secure KM Switch and Secure KVM Combiner Issued by: Communications Security Establishment Canada Certification Body Canadian
Certification Report EAL 4+ Evaluation of High Security Labs Secure DVI KVM Switch, Secure KM Switch and Secure KVM Combiner Issued by: Communications Security Establishment Canada Certification Body Canadian
CyberFence Protection for DNP3
 CyberFence Protection for DNP3 August 2015 Ultra Electronics, 3eTI 2015 DNP3 Issues and Vulnerabilities DNP3 is one of the most widely used communications protocols within the utility space for the purpose
CyberFence Protection for DNP3 August 2015 Ultra Electronics, 3eTI 2015 DNP3 Issues and Vulnerabilities DNP3 is one of the most widely used communications protocols within the utility space for the purpose
Secure Government Computing Initiatives & SecureZIP
 Secure Government Computing Initiatives & SecureZIP T E C H N I C A L W H I T E P A P E R WP 700.xxxx Table of Contents Introduction FIPS 140 and SecureZIP Ensuring Software is FIPS 140 Compliant FIPS
Secure Government Computing Initiatives & SecureZIP T E C H N I C A L W H I T E P A P E R WP 700.xxxx Table of Contents Introduction FIPS 140 and SecureZIP Ensuring Software is FIPS 140 Compliant FIPS
SECURE KVM SWITCHES EDID CONFIGURATION GUIDE SS2P, SS4P, SS8P, SS16P SERIES 24/7 TECHNICAL SUPPORT AT OR VISIT BLACKBOX.
 EDID CONFIGURATION GUIDE SS2P, SS4P, SS8P, SS16P SERIES SECURE KVM SWITCHES 24/7 AT OR VISIT BLACKBOX.COM CONSOLE IN-4 IN-3 DP OUT DP DP IN-2 DP IN-1 DP IN-4 IN-3 IN-2 IN-1 12VDC2.0A DP OUT DP DP DP 12VDC2.0A
EDID CONFIGURATION GUIDE SS2P, SS4P, SS8P, SS16P SERIES SECURE KVM SWITCHES 24/7 AT OR VISIT BLACKBOX.COM CONSOLE IN-4 IN-3 DP OUT DP DP IN-2 DP IN-1 DP IN-4 IN-3 IN-2 IN-1 12VDC2.0A DP OUT DP DP DP 12VDC2.0A
Make security part of your client systems refresh
 Make security part of your client systems refresh Safeguard your information with Dell Data Security Solutions while boosting productivity and reducing costs Your organization might have many reasons for
Make security part of your client systems refresh Safeguard your information with Dell Data Security Solutions while boosting productivity and reducing costs Your organization might have many reasons for
Data Loss Prevention Whitepaper. When Mobile Device Management Isn t Enough. Your Device Here. Good supports hundreds of devices.
 Data Loss Prevention Whitepaper When Mobile Device Management Isn t Enough Your Device Here. Good supports hundreds of devices. Contents Shifting Security Landscapes 3 Security Challenges to Enterprise
Data Loss Prevention Whitepaper When Mobile Device Management Isn t Enough Your Device Here. Good supports hundreds of devices. Contents Shifting Security Landscapes 3 Security Challenges to Enterprise
GUIDANCE ON ELECTRONIC VOTING SYSTEM PREPARATION AND SECURITY
 September, 2016 GUIDANCE ON ELECTRONIC VOTING SYSTEM PREPARATION AND SECURITY As a reminder for counties, and refresher on good cyber hygiene practices, DOS recommends the following procedures in the preparation
September, 2016 GUIDANCE ON ELECTRONIC VOTING SYSTEM PREPARATION AND SECURITY As a reminder for counties, and refresher on good cyber hygiene practices, DOS recommends the following procedures in the preparation
Data Leak Prevention
 Data Leak Prevention Key advantages Full suite DLP solution Short time-to-benefit High level of tamperresistance All speciality functions covered against leakage Agnostic approach Clearly defined data
Data Leak Prevention Key advantages Full suite DLP solution Short time-to-benefit High level of tamperresistance All speciality functions covered against leakage Agnostic approach Clearly defined data
SwitchView Desktop Switches at a Glance
 SwitchView Desktop Switches at a Glance Users Computers Platforms Resolution Key Features Single 2 PC 2048 x 1536 Multiple PS/2 Computers Single 4 PC 2048 x 1536 Multiple PS/2 Computers SwitchView Multimedia
SwitchView Desktop Switches at a Glance Users Computers Platforms Resolution Key Features Single 2 PC 2048 x 1536 Multiple PS/2 Computers Single 4 PC 2048 x 1536 Multiple PS/2 Computers SwitchView Multimedia
Vertiv Local Rack Access 18.5" LED LCD Console
 Vertiv Local Rack Access 18.5" LED LCD Console With Integrated Keyboard, Touchpad and Dual USB 2.0 Ports Installer/User Guide Technical Support Site If you encounter any installation or operational issues
Vertiv Local Rack Access 18.5" LED LCD Console With Integrated Keyboard, Touchpad and Dual USB 2.0 Ports Installer/User Guide Technical Support Site If you encounter any installation or operational issues
SECURING DEVICES IN THE INTERNET OF THINGS
 SECURING DEVICES IN THE INTERNET OF THINGS EXECUTIVE SUMMARY Security breaches at the device level in the Internet of Things (IoT) can have severe consequences, including steep financial losses, damage
SECURING DEVICES IN THE INTERNET OF THINGS EXECUTIVE SUMMARY Security breaches at the device level in the Internet of Things (IoT) can have severe consequences, including steep financial losses, damage
Trellis Real-Time Infrastructure Optimization Platform Release Notes
 VERTIV Trellis Real-Time Infrastructure Optimization Platform Release Notes VERSION 5.0.1.1, APRIL 13, 2018 Release Notes Section Outline 1 New Features Overview 2 General Features Overview 3 Notes and
VERTIV Trellis Real-Time Infrastructure Optimization Platform Release Notes VERSION 5.0.1.1, APRIL 13, 2018 Release Notes Section Outline 1 New Features Overview 2 General Features Overview 3 Notes and
National Information Assurance Partnership. Common Criteria Evaluation and Validation Scheme Validation Report
 National Information Assurance Partnership TM Common Criteria Evaluation and Validation Scheme Validation Report Cybex SwitchView SC Series Switches for Models without [EXP_TMP] Report Number: CCEVS-VR-VID10250-2008
National Information Assurance Partnership TM Common Criteria Evaluation and Validation Scheme Validation Report Cybex SwitchView SC Series Switches for Models without [EXP_TMP] Report Number: CCEVS-VR-VID10250-2008
SECURING DEVICES IN THE INTERNET OF THINGS
 SECURING DEVICES IN THE INTERNET OF THINGS WHEN IT MATTERS, IT RUNS ON WIND RIVER EXECUTIVE SUMMARY Security breaches at the device level in the Internet of Things (IoT) can have severe consequences, including
SECURING DEVICES IN THE INTERNET OF THINGS WHEN IT MATTERS, IT RUNS ON WIND RIVER EXECUTIVE SUMMARY Security breaches at the device level in the Internet of Things (IoT) can have severe consequences, including
User Manual. Advanced Secure 2-port Flip KVM Switches
 Advanced Secure 2-port Flip KVM Switches User Manual F1DN102F-3 Secure 2-port Flip DVI-D KVM with Audio, PP 3.0 F1DN102N-3 Secure 2-port Flip DP KVM with Audio, PP 3.0 F1DN102V-3 Secure 2-port Flip VGA
Advanced Secure 2-port Flip KVM Switches User Manual F1DN102F-3 Secure 2-port Flip DVI-D KVM with Audio, PP 3.0 F1DN102N-3 Secure 2-port Flip DP KVM with Audio, PP 3.0 F1DN102V-3 Secure 2-port Flip VGA
Port Replicator User s Guide
 Fujitsu Computer Systems Corporation Port Replicator User s Guide I N S T R U C T I O N S The port replicator extends the functionality of your LifeBook T Series Tablet PC by providing ports to connect
Fujitsu Computer Systems Corporation Port Replicator User s Guide I N S T R U C T I O N S The port replicator extends the functionality of your LifeBook T Series Tablet PC by providing ports to connect
A HOLISTIC APPROACH TO IDENTITY AND AUTHENTICATION. Establish Create Use Manage
 A HOLISTIC APPROACH TO IDENTITY AND AUTHENTICATION Establish Create Use Manage SIMPLE. SECURE. SMART. ALL FROM A SINGLE SOURCE. As the ways to access your organization and its sensitive data increase,
A HOLISTIC APPROACH TO IDENTITY AND AUTHENTICATION Establish Create Use Manage SIMPLE. SECURE. SMART. ALL FROM A SINGLE SOURCE. As the ways to access your organization and its sensitive data increase,
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS
 10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
10 KEY WAYS THE FINANCIAL SERVICES INDUSTRY CAN COMBAT CYBER THREATS WHITE PAPER INTRODUCTION BANKS ARE A COMMON TARGET FOR CYBER CRIMINALS AND OVER THE LAST YEAR, FIREEYE HAS BEEN HELPING CUSTOMERS RESPOND
IBM 1735 Rack-Based Local Console Switches (Withdrawn) Product Guide
 IBM 1735 Rack-Based Local Console Switches (Withdrawn) Product Guide The family of IBM rack-based local console switches is designed to provide exceptional scalability and flexibility in managing data
IBM 1735 Rack-Based Local Console Switches (Withdrawn) Product Guide The family of IBM rack-based local console switches is designed to provide exceptional scalability and flexibility in managing data
CATx and Fiber DVI and USB Extenders
 ACX310-R2 ACX310S-R2 ACX310F-R2 ACX310FIA-R2 Product Data Sheet CATx and Fiber DVI and USB Extenders ACX310F-R2 OVERVIEW CATx or Fiber DVI/HDMI + USB Extenders are optimized for state-of-the-art signals
ACX310-R2 ACX310S-R2 ACX310F-R2 ACX310FIA-R2 Product Data Sheet CATx and Fiber DVI and USB Extenders ACX310F-R2 OVERVIEW CATx or Fiber DVI/HDMI + USB Extenders are optimized for state-of-the-art signals
Mobile Data Security Essentials for Your Changing, Growing Workforce
 Mobile Data Security Essentials for Your Changing, Growing Workforce White Paper February 2007 CREDANT Technologies Security Solutions White Paper YOUR DYNAMIC MOBILE ENVIRONMENT As the number and diversity
Mobile Data Security Essentials for Your Changing, Growing Workforce White Paper February 2007 CREDANT Technologies Security Solutions White Paper YOUR DYNAMIC MOBILE ENVIRONMENT As the number and diversity
IOGEAR Secure KVM Switch Series. Security Target
 IOGEAR Secure KVM Switch Series Security Target Version 1.0 January 19, 2018 Prepared for: 15365 Barranca Pkwy, Irvine, CA 92618 Prepared by: Common Criteria Testing Laboratory 6841 Benjamin Franklin Drive,
IOGEAR Secure KVM Switch Series Security Target Version 1.0 January 19, 2018 Prepared for: 15365 Barranca Pkwy, Irvine, CA 92618 Prepared by: Common Criteria Testing Laboratory 6841 Benjamin Franklin Drive,
The Shortcut Guide To. Protecting Against Web Application Threats Using SSL. Dan Sullivan
 tm The Shortcut Guide To Protecting Against Web Application Threats Using SSL Chapter 3: Planning, Deploying, and Maintaining SSL Certificates to Protect Against Inf ormation Loss and Build Customer Trust...
tm The Shortcut Guide To Protecting Against Web Application Threats Using SSL Chapter 3: Planning, Deploying, and Maintaining SSL Certificates to Protect Against Inf ormation Loss and Build Customer Trust...
