Ten steps to make your DCIM implementation a success
|
|
|
- Joella Marsh
- 6 years ago
- Views:
Transcription
1 WHITE PAPER OCTOBER 2014 Ten steps to make your DCIM implementation a success Dhesikan Ananchaperumal Distinguished Engineer and SVP, Engineering, Infrastructure Management Solutions, CA Technologies Hervé Tardy Vice President and General Manager, Distributed Power Quality Division, Eaton Corporation
2 2 WHITE PAPER: TEN STEPS TO MAKE YOUR DCIM IMPLEMENTATION A SUCCESS ca.com Table of Contents Executive Summary 3 Achieve maximum value with minimum effort 3 Best practice steps for implementation success 4 Conclusions 10 About the Authors 10
3 3 WHITE PAPER: TEN STEPS TO MAKE YOUR DCIM IMPLEMENTATION A SUCCESS ca.com Executive Summary As demands on the data center increase, IT and facilities departments need to be able to increase and sustain high availability, maximize efficiency and minimize costs. Data Center Infrastructure Management (DCIM) provides an integrated platform for monitoring and measuring consumption, capacity and performance of both IT and facilities resources in the data center. For many organizations, 2014 will be the year they implement DCIM. This practical white paper will also ensure that 2014 is the year they realize their return on investment from DCIM. From defining business needs and setting operational thresholds to enabling integrations and ensuring scalability, we have taken the combined expertise of CA Technologies and Eaton, based on lessons learned from our customers, to provide this best practice implementation guide to DCIM. Achieve maximum value with minimum effort DCIM has crossed the chasm from IT buzzword to business enabler, with more than half of data center managers recognizing the value of using an integrated DCIM system. Yet only a third of organizations have so far deployed a DCIM solution, with cost and integration issues being cited as the main adoption barriers 2. However, with the right planning, a DCIM deployment need not be a costly or a complex undertaking. For example, a Fortune 500 bank implemented CA DCIM in just six weeks in its double tier IV certified data center. It is important to remember that DCIM is not a one-off project; it s an ongoing program. As such, an implementation can be phased with future investment being funded by the savings achieved from the initial stages. This practical guide helps organizations determine where to start their DCIM implementation and how to achieve the best outcomes.
4 4 WHITE PAPER: TEN STEPS TO MAKE YOUR DCIM IMPLEMENTATION A SUCCESS ca.com Best practice steps for implementation success 1) Validate what you want to achieve The success of any DCIM implementation will be determined by the specification of the initial requirements. As one of the major goals of most DCIM implementations is to provide a unified and granular view of numerous data center information sources, it is important to first understand the current state of the environment. This is particularly key when assessing existing management systems. Typically, organizations have around 10 to 40 systems for managing their data centers. DCIM should not become another addition to this long list. A DCIM implementation presents organizations with an opportunity to amalgamate and/or retire existing management tools. To identify optimization opportunities, IT and facilities departments need to go back to basics and establish: Who is using the system and for what purpose? How much does it cost to maintain the system? What value is the system adding? Can I leverage this existing investment as a data feed into DCIM (for example a Building Management System (BMS) or Electrical Power Management System (EPMS)? Functionality overlaps will help determine those tools that can be phased out or integrated, with the end goal being just one or two centralized data center management systems. 2) Stay aligned to the business From capacity and consumption to availability and recoverability, DCIM solutions can generate an abundance of performance metrics across the data center. However, a wealth of information doesn t necessarily mean a wealth of knowledge. To ensure a DCIM implementation remains aligned to business goals and priorities, IT and facilities departments need to take time to identify the metrics that matter: the metrics that will help them make the data center leaner and greener. This mapping process, which should happen prior to implementation, will differ between each organization and each data center. For example, for a managed service provider with a new data center, the priority might be tracking power consumption to individual devices. For a bank with a portfolio of facilities, safeguarding availability might represent the primary business metric. The results of the requirements study will be key to identifying the right performance metrics of which there are now plenty. For example, while PUE was once the stalwart for measuring data center efficiency, it only provides a mere snapshot of the full picture. To maximize performance and minimize costs in the data center, organizations now need much broader and deeper metrics and analytics that span power availability, IT asset utilization, carbon emissions and even water consumption.
5 5 WHITE PAPER: TEN STEPS TO MAKE YOUR DCIM IMPLEMENTATION A SUCCESS ca.com A best-of-breed DCIM solution will be able to generate metrics across this broad spectrum, and adapt to new industry measures as they emerge. It will also enable IT and facilities departments to implement their own customized metrics as their implementation matures. Metric mapping: customer scenario By taking a business centric approach to its DCIM metrics, a large shipping company has been able to correlate the costs of data center operations and power consumption to each container that it transports. With better visibility of its operational costs, the company can prioritize investments, continuously improve operations and safeguard profitability. 3) Maintain data quality and consistency Multiple streams of data are the foundation of every DCIM metric. For metrics to be meaningful, data must be collected in real-time and on a regular or even continuous basis. Data capture intervals will not be the same for every device and will be influenced by the business needs established in the initial requirements study. Smart polling not only overcomes the issue of the frequency of data collection but also the diversity of data formats. IT and facilities systems use a wide range of protocols such as Modbus, BACnet and SNMP and DCIM solutions need to integrate with all of them. Without this interoperability, data gaps will start to emerge and metrics will no longer be completely accurate. The disparity between naming conventions for different variables can also have a major impact on data accuracy especially when polling facilities systems. For example, a CRAC unit manufactured by Vendor A might use the term Inlet Temperature while the same device from Vendor B refers to Temp_In. DCIM solutions need to detect that these are in fact the same variables and process the data accordingly. Without this built-in intelligence, organizations will end up with inconsistent data that demands considerable manual aggregation and is not suitable for granular back-end analytics. It is also common for facilities equipment to use a scaling factor. DCIM solutions need to recognize the different scaling factors being used for different variables and take this into account when calculating metrics. By implementing a DCIM solution with such broad functionality and compatibility, organizations can avoid the need for protocol converters and additional monitoring tools, thereby avoiding unnecessary cost and complexity. Smart polling: customer scenario A major insurance company has been able to safeguard service quality by using its DCIM solution to control polling frequency across different workloads. With polling throttled for less critical workloads, it is able to focus on capturing granular data only from core systems. As a result, the data center operations team can see analytics in real time in the NOC via a DCIM dashboard.
6 6 WHITE PAPER: TEN STEPS TO MAKE YOUR DCIM IMPLEMENTATION A SUCCESS ca.com 4) Avoid alert overload More management systems in the data center means more alerts. DCIM solutions can help cut through this noise but only if alarms are classified and configured correctly during implementation. Event correlation is key to suppressing the volume of alerts. Unlike many of today s disparate data center management tools, DCIM can aggregate alerts from IT and facilities devices to prevent one event from being logged as multiple incidents. By using advanced alerting features, such as time over threshold and deviation from normal, organizations can prevent every change in operational conditions from raising a false alarm and waking the data center manager in the middle of the night. Defining alert profiles based on use cases is key to establishing this intelligent approach and averting alarm overload. When a genuine alert is raised, organizations need to ensure that their DCIM solutions communicate the event in terms that are relevant to both IT and facilities. For example, for an alert related to a power surge, the DCIM solution should communicate the impact on dependent IT systems and business services/sites. This will enable IT and facilities to collaborate swiftly and effectively to minimize disruption to end users. Some DCIM solutions will even go one step further by learning the normal behavior of different devices and thermal conditions in the data center. Given the evolving nature of today s data centers, thresholds can rapidly change as new devices are added and cooling and power supplies put under greater strain. Intelligent alerting: customer scenario By deploying DCIM, an MSP has been able to resolve a recurring problem with alarms related to power spikes in its data center. The alerts, which were raised by a building management system, did not provide sufficient context to pinpoint the problem. The MSP has used its DCIM solution to set up intelligent thresholds that prevent the false alarms from being issued. 5) Establish effective integrations With the average organization using dozens of different tools to manage their data center operations, integration is a major consideration for any DCIM implementation. BMS are the most obvious candidates, but this is just the tip of the integration iceberg: service desk ticketing platforms, fire detection systems, physical security systems and user authentication controls can all be linked to DCIM. The integrations can be phased-in as different DCIM use cases come into scope. As well as being the most obvious, DCIM/BMS integration is the most important. When integrating with a BMS, organizations need to: Identify the various protocols used for communicating with the BMS and evaluate how they can be leveraged. For example, there may be web services that can be utilized. Establish a secure link for those BMS hosted on an isolated network to facilitate data importing into the DCIM solution. Create a list of key data points and polling frequency based on the use cases defined during the requirements study.
7 7 WHITE PAPER: TEN STEPS TO MAKE YOUR DCIM IMPLEMENTATION A SUCCESS ca.com Effective integration will also enable the use of automated workflows, for example for incident and problem management, which will accelerate response times and free up resources. Systems integration: customer scenario When a power strip to a production system failed, it went unnoticed except by the company s DCIM solution. Thanks to the integrations established with other IT management tools, a service desk ticket was automatically raised and an alert routed to the monitoring team s console. As a result, the team was able to take immediate action to minimize business impact. 6) Protect data and system integrity Safeguarding the data stored in IT systems is of growing importance and DCIM is no exception. Device and facility information could expose unforeseen vulnerabilities to hackers, putting the entire data center operation at risk. To ensure IT and facility data stays secure on the network, DCIM systems must be subjected to the same security measures as other enterprise-level solutions. For example, access should be governed by user authentication particularly if DCIM data is being viewed on mobile devices where authentication, authorization and access control should be handled by an efficient Mobile Device Management solution. To support robust identity and access management, organizations should ensure their DCIM solution integrates with LDAP and Active Directory. Support for secure communication protocols, such as SNMP v3 and IP v6, plus the ability to encrypt data between integrated systems and polled devices are also key security considerations. The DCIM solution s own alerting functionality can also be used to issue alarms when unusual data flow patterns or requests are observed. Security is not a tick-in-the-box activity and therefore needs to routinely reviewed. In addition to undertaking vulnerability testing as part of the implementation, organizations should carry out similar tests at regular intervals throughout the lifecycle of the DCIM system to ensure emerging threats are addressed. Information security: customer scenario A high-security public organization needed to isolate certain data center processes and information to minimize risk and meet its regulatory obligations. Using its DCIM solution, the organization has set up rigorous security controls that segregate user management rights for different infrastructure assets, such as cabling and cooling, while still enabling collaboration on a single system.
8 8 WHITE PAPER: TEN STEPS TO MAKE YOUR DCIM IMPLEMENTATION A SUCCESS ca.com 7) Take it one step at a time A DCIM implementation can spiral out of control if too much is attempted at once. By taking a phased approach, organizations can achieve small successes and avoid big messes. The initial requirements study will help organizations plot their implementation roadmap by identifying the main pain points and the potential for rapid gains. If an organization has multiple data centers around the world, then the geography of each facility may impact the implementation. An incremental approach will enable IT and facilities departments to incorporate lessons learned from the first stage into future phases, creating a repeatable process that enables rapid and lower-risk deployment. A phased implementation will also minimize any potential disruption to business processes and simplify the migration and duplication of often large volumes of historical data. Communicating the successes that have been accomplished with the initial implementation of the solution will help drive ongoing support and investment. 8) Accelerate user adoption As DCIM solutions span both IT and facilities, organizations need to ensure they provide role-focused training to ensure adoption. User training should not be delivered in isolation but in context with other integrated systems, so users can see how DCIM enhances existing processes. Demonstrating value is key to gaining rapid user buy-in. By linking training back to the initial requirements study, IT and facilities stakeholders can be made of aware of expected efficiency gains in their department. The following functionality will be core to enabling users to deliver quick wins from the initial DCIM implementation, and should therefore be high on the training priority list: Setting data collection parameters Generating custom reports Configuring alert rules Establishing event workflows Providing primary users with a sandbox installation of the DCIM solution following the initial training period will help continue the familiarization process and identify any remaining bugs. Simplifying access with single sign-on will also help to smooth the initial adoption. 9) Safeguard performance levels DCIM solutions have to be built to scale. As the implementation matures, organizations could soon find themselves polling thousands and possibly millions of devices and sensors. That is a lot of data. And if the DCIM architecture can t support it, performance will soon be impacted cancelling out many of the initial benefits. Scalability and performance are not just factors during implementation; they also need to be considered when selecting a DCIM solution. The ability to store huge amounts of data for a reasonable period of time without impacting performance is a must for a DCIM solution. This includes having the right architecture, database and schema, optimized query engines, high availability, distributed deployment. For example,
9 9 WHITE PAPER: TEN STEPS TO MAKE YOUR DCIM IMPLEMENTATION A SUCCESS ca.com multiple data collectors can be deployed across several data centers around the world, but only a rolled up data set may be uploaded to the master DCIM server with the ability to drill down to the time series data from the local data collector itself. The performance of a DCIM solution will also be influenced by how metrics and data are handled. For example, metrics can be calculated from polled data points in different ways. These include: 1. A user initiates the calculation from a DCIM dashboard 2. Automated workflows process the calculation at a pre-defined time 3. The calculation is done in real-time during the polling process and is stored alongside the raw data As part of the implementation, organizations need to consider what represents an optimal balance between granular data and ongoing system performance. A pilot with a simulated data set will help determine this balance and ongoing scalability requirements. Scalability: customer scenario A large global bank is using its DCIM solution to poll data from 80,000 components across 11 different data centers and 6,000 racks. By selecting a highly scalable solution, the company is able to capture data every five minutes without any performance degradation. This data has provided the bank with real-time power management capabilities that will reduce consumption and costs. 10) Enable continuous improvement To unlock the full value of DCIM, organizations must consider what happens after the initial implementation. DCIM is not a discrete project; it is a constantly evolving discipline. As organizations become exposed to more actionable information, the more opportunities will arise for optimizing the data center. To capture continuous improvement opportunities, organizations should look to task specific individuals with gathering ongoing requirements from IT and facilities teams as well as other business stakeholders. Metric and analytics requirements, in particular, will evolve over time. The very nature of DCIM means that it is the perfect partner for continuous improvement in the data center itself: historical trending, scenario planning and advanced analytics are just some of the features that will help organizations drive an optimization roadmap. Continuous improvement: customer scenario By using its DCIM solution to baseline power consumption and data center performance, has been able to identify when legacy assets need to be replaced. Once the new equipment is installed, the DCIM solution enables the company to validate that the expected ROI has been achieved by recording improvement in energy efficiency and operational performance.
10 10 WHITE PAPER: TEN STEPS TO MAKE YOUR DCIM IMPLEMENTATION A SUCCESS ca.com Conclusions When implemented effectively, DCIM can deliver value and deliver it quickly. As IDC cites: DCIM not only enables improved operations, greater agility, and lower risk but also can rapidly accelerate such tasks as data collection and routine calculations and analysis, enabling staff to focus on higher-level activities such as strategizing, engineering, and implementing improved data center systems and approaches. To unlock these benefits, organizations need to ensure they establish the right integrations and configurations at the outset and safeguard ongoing scalability and performance. Working with an experienced DCIM partner will help organizations realize the full value of DCIM and prevent them from having to reinvent the implementation wheel. By taking the time to get DCIM right today, organizations will achieve better outcomes tomorrow. About the Authors Dhesikan Ananchaperumal is a member of the CA Council for Technical Excellence. He is responsible for leading and overseeing the day-to-day activities of the engineering team of Infrastructure Management Solutions business unit - products include: CA Performance Management, CA Mediation Manager, CA Spectrum, CA DCIM and CA Capacity Manager, CA ehealth. Dhesi was awarded the designation of Distinguished Engineer (DE), in this role he provides guidance to executive leadership on the introduction of new technologies and mentorship to engineering community and counsel in driving the implementation of new architectures, products and solutions to ensure innovation, integration and customer value. An industry veteran with an expertise in IT Infrastructure and Energy Management, Dhesi has published numerous white papers and articles and is a frequent speaker at Data Center and IT conferences. Prior to his current role, Dhesi was involved with Emerging Technologies, Business Relationship Management and M&A activities for CA. Prior to joining CA, Dhesi held various management and technology positions at Netegrity, Affinnova, AMS and Infosys Technologies. Dhesi holds a Bachelor s degree in Electronics Engineering, a Master s degree in Computer Science and a Master s degree in Electronics Design Technology from the Center for Electronics Design Technology, India. Dhesi also has ISC2-CISSP, Six Sigma and ITIL certifications. Hervé Tardy is Vice President and General Manager of Eaton s Distributed Power Solutions business unit. In this role since 2007, Hervé manages the Americas product roadmap for single-phase UPSs, software and connectivity products to reinforce the technology leadership of Eaton. He also has responsibility for the Eaton IT channel. Tardy is based in Raleigh, North Carolina. Hervé graduated from ESSEC Business School in Paris, France and Stanford Executive Program. He is a 28-year veteran in the UPS industry and held multiple positions in sales, channel marketing, marketing communications, product marketing and product development. His focus has always been to position the UPS as an IT peripheral more than a simple power device, and he turned out to become an expert in power management and software communication solutions.
11 11 WHITE PAPER: TEN STEPS TO MAKE YOUR DCIM IMPLEMENTATION A SUCCESS Connect with CA Technologies at ca.com CA Technologies (NASDAQ: CA) creates software that fuels transformation for companies and enables them to seize the opportunities of the application economy. Software is at the heart of every business, in every industry. From planning to development to management and security, CA is working with companies worldwide to change the way we live, transact and communicate across mobile, private and public cloud, distributed and mainframe environments. Learn more at ca.com. Some information in this publication is based upon CA or customer experiences with the referenced software product in a variety of development and customer environments. Past performance of the software product in such development and customer environments is not indicative of the future performance of such software product in identical, similar or different environments. CA does not warrant that the software product can operate as specifically set forth in this publication. CA will support the referenced product only in accordance with (i) the documentation and specifications provided with the referenced product, and (ii) CA s then-current maintenance and support policy for the referenced product. Copyright 2014 CA. All rights reserved. All trademarks, trade names, service marks, and logos referenced herein belong to their respective companies. This document is for your informational purposes only. CA assumes no responsibility for the accuracy or completeness of the information. To the extent permitted by applicable law, CA provides this document as is without warranty of any kind, including, without limitation, any implied warranties of merchantability, fitness for a particular purpose, or non-infringement. In no event can CA be liable for any loss or damage, direct or indirect, from the use of this document, including, without limitation, lost profits, business interruption, good will, or lost data, even if CA is expressly advised in advance of the possibility of such damages. CA does not provide legal advice. Neither this document nor any CA software product referenced herein shall serve as a substitute for your compliance with any laws (including but not limited to any act, statute, regulation, rule, directive, policy, standard, guideline, measure, requirement, administrative order, executive order, etc. (collectively, Laws )) referenced in this document. You should consult with competent legal counsel regarding any Laws referenced herein. CS200_87417_1014
Overview. Business value
 PRODUCT SHEET CA Top Secret for z/vse CA Top Secret for z/vse CA Top Secret for z/vse provides innovative and comprehensive security for business transaction environments which enable your business to
PRODUCT SHEET CA Top Secret for z/vse CA Top Secret for z/vse CA Top Secret for z/vse provides innovative and comprehensive security for business transaction environments which enable your business to
CA ecometer. Overview. Benefits. agility made possible. Improve data center uptime and availability through better energy management
 PRODUCT SHEET: CA ecometer CA ecometer Improve data center uptime and availability through better energy management agility made possible CA ecometer helps you to visualize, monitor, and better manage
PRODUCT SHEET: CA ecometer CA ecometer Improve data center uptime and availability through better energy management agility made possible CA ecometer helps you to visualize, monitor, and better manage
Moving From Reactive to Proactive Storage Management with an On-demand Cloud Solution
 Moving From Reactive to Proactive Storage Management with an On-demand Cloud Solution The Ever-Present Storage Management Conundrum In the modern IT landscape, the storage management conundrum is as familiar
Moving From Reactive to Proactive Storage Management with an On-demand Cloud Solution The Ever-Present Storage Management Conundrum In the modern IT landscape, the storage management conundrum is as familiar
CA ERwin Data Profiler
 PRODUCT BRIEF: CA ERWIN DATA PROFILER CA ERwin Data Profiler CA ERWIN DATA PROFILER HELPS ORGANIZATIONS LOWER THE COSTS AND RISK ASSOCIATED WITH DATA INTEGRATION BY PROVIDING REUSABLE, AUTOMATED, CROSS-DATA-SOURCE
PRODUCT BRIEF: CA ERWIN DATA PROFILER CA ERwin Data Profiler CA ERWIN DATA PROFILER HELPS ORGANIZATIONS LOWER THE COSTS AND RISK ASSOCIATED WITH DATA INTEGRATION BY PROVIDING REUSABLE, AUTOMATED, CROSS-DATA-SOURCE
SOLUTION BRIEF NETWORK OPERATIONS AND ANALYTICS. How Can I Predict Network Behavior to Provide for an Exceptional Customer Experience?
 SOLUTION BRIEF NETWORK OPERATIONS AND ANALYTICS How Can I Predict Network Behavior to Provide for an Exceptional Customer Experience? SOLUTION BRIEF CA DATABASE MANAGEMENT FOR DB2 FOR z/os DRAFT When used
SOLUTION BRIEF NETWORK OPERATIONS AND ANALYTICS How Can I Predict Network Behavior to Provide for an Exceptional Customer Experience? SOLUTION BRIEF CA DATABASE MANAGEMENT FOR DB2 FOR z/os DRAFT When used
WHITE PAPER MARCH Automating Data Masking and Reduction for SAP System Copy
 WHITE PAPER MARCH 2018 Automating Data Masking and Reduction for SAP System Copy 2 WHITE PAPER AUTOMATING DATA MASKING AND REDUCTION FOR SAP SYSTEM COPY ca.com Table of Contents Executive Summary 3 Section
WHITE PAPER MARCH 2018 Automating Data Masking and Reduction for SAP System Copy 2 WHITE PAPER AUTOMATING DATA MASKING AND REDUCTION FOR SAP SYSTEM COPY ca.com Table of Contents Executive Summary 3 Section
RSA Solution Brief. Managing Risk Within Advanced Security Operations. RSA Solution Brief
 RSA Solution Brief Managing Risk Within Advanced Security Operations RSA Solution Brief How do you advance your security operations function? Increasingly sophisticated security threats and the growing
RSA Solution Brief Managing Risk Within Advanced Security Operations RSA Solution Brief How do you advance your security operations function? Increasingly sophisticated security threats and the growing
Accelerate Your Enterprise Private Cloud Initiative
 Cisco Cloud Comprehensive, enterprise cloud enablement services help you realize a secure, agile, and highly automated infrastructure-as-a-service (IaaS) environment for cost-effective, rapid IT service
Cisco Cloud Comprehensive, enterprise cloud enablement services help you realize a secure, agile, and highly automated infrastructure-as-a-service (IaaS) environment for cost-effective, rapid IT service
PREPARE FOR TAKE OFF. Accelerate your organisation s journey to the Cloud.
 PREPARE FOR TAKE OFF Accelerate your organisation s journey to the Cloud. cloud. Contents Introduction Program & Governance BJSS Cloud Readiness Assessment: Intro Platforms & Development BJSS Cloud Readiness
PREPARE FOR TAKE OFF Accelerate your organisation s journey to the Cloud. cloud. Contents Introduction Program & Governance BJSS Cloud Readiness Assessment: Intro Platforms & Development BJSS Cloud Readiness
Protect Your Data the Way Banks Protect Your Money
 Protect Your Data the Way Banks Protect Your Money A New Security Model Worth Understanding and Emulating Enterprise security traditionally relied on a fortress strategy that locked down user endpoints
Protect Your Data the Way Banks Protect Your Money A New Security Model Worth Understanding and Emulating Enterprise security traditionally relied on a fortress strategy that locked down user endpoints
VMware Cloud Operations Management Technology Consulting Services
 VMware Cloud Operations Management Technology Consulting Services VMware Technology Consulting Services for Cloud Operations Management The biggest hurdle [that CIOs face as they move infrastructure and
VMware Cloud Operations Management Technology Consulting Services VMware Technology Consulting Services for Cloud Operations Management The biggest hurdle [that CIOs face as they move infrastructure and
Comune della Spezia protects service continuity with integrated backup and replication from CA Technologies
 CUSTOMER SUCCESS STORY Comune della Spezia protects service continuity with integrated backup and replication from CA Technologies CLIENT PROFILE Industry: Local government Company: Municipality of La
CUSTOMER SUCCESS STORY Comune della Spezia protects service continuity with integrated backup and replication from CA Technologies CLIENT PROFILE Industry: Local government Company: Municipality of La
Symantec Data Center Transformation
 Symantec Data Center Transformation A holistic framework for IT evolution As enterprises become increasingly dependent on information technology, the complexity, cost, and performance of IT environments
Symantec Data Center Transformation A holistic framework for IT evolution As enterprises become increasingly dependent on information technology, the complexity, cost, and performance of IT environments
Smart Data Center Solutions
 Smart Data Center Solutions New Data Center Challenges Require New Solutions Data Center Architecture. Inside and Out. Data centers are mission-critical facilities. A silo-based approach to designing,
Smart Data Center Solutions New Data Center Challenges Require New Solutions Data Center Architecture. Inside and Out. Data centers are mission-critical facilities. A silo-based approach to designing,
DATACENTER SERVICES DATACENTER
 SERVICES SOLUTION SUMMARY ALL CHANGE React, grow and innovate faster with Computacenter s agile infrastructure services Customers expect an always-on, superfast response. Businesses need to release new
SERVICES SOLUTION SUMMARY ALL CHANGE React, grow and innovate faster with Computacenter s agile infrastructure services Customers expect an always-on, superfast response. Businesses need to release new
Using Threat Analytics to Protect Privileged Access and Prevent Breaches
 Using Threat Analytics to Protect Privileged Access and Prevent Breaches Under Attack Protecting privileged access and preventing breaches remains an urgent concern for companies of all sizes. Attackers
Using Threat Analytics to Protect Privileged Access and Prevent Breaches Under Attack Protecting privileged access and preventing breaches remains an urgent concern for companies of all sizes. Attackers
How can we gain the insights and control we need to optimize the performance of applications running on our network?
 SOLUTION BRIEF CA Network Flow Analysis and Cisco Application Visibility and Control How can we gain the insights and control we need to optimize the performance of applications running on our network?
SOLUTION BRIEF CA Network Flow Analysis and Cisco Application Visibility and Control How can we gain the insights and control we need to optimize the performance of applications running on our network?
THE JOURNEY OVERVIEW THREE PHASES TO A SUCCESSFUL MIGRATION ADOPTION ACCENTURE IS 80% IN THE CLOUD
 OVERVIEW Accenture is in the process of transforming itself into a digital-first enterprise. Today, Accenture is 80 percent in a public cloud. As the journey continues, Accenture shares its key learnings
OVERVIEW Accenture is in the process of transforming itself into a digital-first enterprise. Today, Accenture is 80 percent in a public cloud. As the journey continues, Accenture shares its key learnings
SYMANTEC: SECURITY ADVISORY SERVICES. Symantec Security Advisory Services The World Leader in Information Security
 SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
SYMANTEC: SECURITY ADVISORY SERVICES Symantec Security Advisory Services The World Leader in Information Security Knowledge, as the saying goes, is power. At Symantec we couldn t agree more. And when it
SIEM: Five Requirements that Solve the Bigger Business Issues
 SIEM: Five Requirements that Solve the Bigger Business Issues After more than a decade functioning in production environments, security information and event management (SIEM) solutions are now considered
SIEM: Five Requirements that Solve the Bigger Business Issues After more than a decade functioning in production environments, security information and event management (SIEM) solutions are now considered
5 OAuth Essentials for API Access Control
 5 OAuth Essentials for API Access Control Introduction: How a Web Standard Enters the Enterprise OAuth s Roots in the Social Web OAuth puts the user in control of delegating access to an API. This allows
5 OAuth Essentials for API Access Control Introduction: How a Web Standard Enters the Enterprise OAuth s Roots in the Social Web OAuth puts the user in control of delegating access to an API. This allows
Information Infrastructure and Security. The value of smart manufacturing begins with a secure and reliable infrastructure
 Information Infrastructure and Security The value of smart manufacturing begins with a secure and reliable infrastructure The Case for Connection To be competitive, you must be connected. That is why industrial
Information Infrastructure and Security The value of smart manufacturing begins with a secure and reliable infrastructure The Case for Connection To be competitive, you must be connected. That is why industrial
CA Security Management
 CA Security CA Security CA Security In today s business environment, security remains one of the most pressing IT concerns. Most organizations are struggling to protect an increasing amount of disparate
CA Security CA Security CA Security In today s business environment, security remains one of the most pressing IT concerns. Most organizations are struggling to protect an increasing amount of disparate
ROI CASE STUDY MAY Logicalis Achieves 159% ROI* with CA DCIM Solution
 ROI CASE STUDY MAY 2015 Logicalis Achieves 159% ROI* with CA DCIM Solution 2 ROI CASE STUDY: LOGICALIS MAY 2015 Logicalis increases efficiency and maximizes availability with CA DCIM UK service provider
ROI CASE STUDY MAY 2015 Logicalis Achieves 159% ROI* with CA DCIM Solution 2 ROI CASE STUDY: LOGICALIS MAY 2015 Logicalis increases efficiency and maximizes availability with CA DCIM UK service provider
Implementing ITIL v3 Service Lifecycle
 Implementing ITIL v3 Lifecycle WHITE PAPER introduction GSS INFOTECH IT services have become an integral means for conducting business for all sizes of businesses, private and public organizations, educational
Implementing ITIL v3 Lifecycle WHITE PAPER introduction GSS INFOTECH IT services have become an integral means for conducting business for all sizes of businesses, private and public organizations, educational
DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE
 DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE EXECUTIVE SUMMARY ALIGNING CYBERSECURITY WITH RISK The agility and cost efficiencies
DATA SHEET RISK & CYBERSECURITY PRACTICE EMPOWERING CUSTOMERS TO TAKE COMMAND OF THEIR EVOLVING RISK & CYBERSECURITY POSTURE EXECUTIVE SUMMARY ALIGNING CYBERSECURITY WITH RISK The agility and cost efficiencies
SIMPLIFY IT. Transform IT with VCE and Vblock TM Infrastructure Platforms. Copyright 2011 VCE Company LLC, All rights reserved.
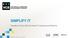 SIMPLIFY IT Transform IT with VCE and Vblock TM Infrastructure Platforms I.T. BUDGET DILEMMA 73% Maintain 27% Invest Source: Forrester Research, Inc., IT Budget Allocations: Planning For 2011, December
SIMPLIFY IT Transform IT with VCE and Vblock TM Infrastructure Platforms I.T. BUDGET DILEMMA 73% Maintain 27% Invest Source: Forrester Research, Inc., IT Budget Allocations: Planning For 2011, December
Dell helps you simplify IT
 Dell helps you simplify IT Workshops the first step. Reduce desktop and data center complexity. Improve productivity. Innovate. Dell IT Consulting Services New Edition 2011 Introduction Are you spending
Dell helps you simplify IT Workshops the first step. Reduce desktop and data center complexity. Improve productivity. Innovate. Dell IT Consulting Services New Edition 2011 Introduction Are you spending
Optimize Your Databases Using Foglight for Oracle s Performance Investigator
 Optimize Your Databases Using Foglight for Oracle s Performance Investigator Solve performance issues faster with deep SQL workload visibility and lock analytics Abstract Get all the information you need
Optimize Your Databases Using Foglight for Oracle s Performance Investigator Solve performance issues faster with deep SQL workload visibility and lock analytics Abstract Get all the information you need
SOLUTION BRIEF RSA ARCHER IT & SECURITY RISK MANAGEMENT
 RSA ARCHER IT & SECURITY RISK MANAGEMENT INTRODUCTION Organizations battle growing security challenges by building layer upon layer of defenses: firewalls, antivirus, intrusion prevention systems, intrusion
RSA ARCHER IT & SECURITY RISK MANAGEMENT INTRODUCTION Organizations battle growing security challenges by building layer upon layer of defenses: firewalls, antivirus, intrusion prevention systems, intrusion
RSA Solution Brief. The RSA Solution for VMware. Key Manager RSA. RSA Solution Brief
 RSA Solution Brief The RSA Solution for VMware View: Managing Securing the the Lifecycle Virtual of Desktop Encryption Environment Keys with RSA Key Manager RSA Solution Brief 1 According to the Open Security
RSA Solution Brief The RSA Solution for VMware View: Managing Securing the the Lifecycle Virtual of Desktop Encryption Environment Keys with RSA Key Manager RSA Solution Brief 1 According to the Open Security
CA Test Data Manager Key Scenarios
 WHITE PAPER APRIL 2016 CA Test Data Manager Key Scenarios Generate and secure all the data needed for rigorous testing, and provision it to highly distributed teams on demand. Muhammad Arif Application
WHITE PAPER APRIL 2016 CA Test Data Manager Key Scenarios Generate and secure all the data needed for rigorous testing, and provision it to highly distributed teams on demand. Muhammad Arif Application
Networking for a smarter data center: Getting it right
 IBM Global Technology Services October 2011 Networking for a smarter data center: Getting it right Planning the network needed for a dynamic infrastructure 2 Networking for a smarter data center: Getting
IBM Global Technology Services October 2011 Networking for a smarter data center: Getting it right Planning the network needed for a dynamic infrastructure 2 Networking for a smarter data center: Getting
How Cisco IT Improved Development Processes with a New Operating Model
 How Cisco IT Improved Development Processes with a New Operating Model New way to manage IT investments supports innovation, improved architecture, and stronger process standards for Cisco IT By Patrick
How Cisco IT Improved Development Processes with a New Operating Model New way to manage IT investments supports innovation, improved architecture, and stronger process standards for Cisco IT By Patrick
Keep the Door Open for Users and Closed to Hackers
 Keep the Door Open for Users and Closed to Hackers A Shift in Criminal Your Web site serves as the front door to your enterprise for many customers, but it has also become a back door for fraudsters. According
Keep the Door Open for Users and Closed to Hackers A Shift in Criminal Your Web site serves as the front door to your enterprise for many customers, but it has also become a back door for fraudsters. According
Solutions Technology, Inc. (STI) Corporate Capability Brief
 Solutions Technology, Inc. (STI) Corporate Capability Brief STI CORPORATE OVERVIEW Located in the metropolitan area of Washington, District of Columbia (D.C.), Solutions Technology Inc. (STI), women owned
Solutions Technology, Inc. (STI) Corporate Capability Brief STI CORPORATE OVERVIEW Located in the metropolitan area of Washington, District of Columbia (D.C.), Solutions Technology Inc. (STI), women owned
Cisco Director Class SAN Planning and Design Service
 Cisco Director Class SAN Planning and Design Service Rapidly Plan and Deploy a Cisco Director Class MDS Solution for More Efficient Storage Networking Service Overview Cisco s intelligent storage networking
Cisco Director Class SAN Planning and Design Service Rapidly Plan and Deploy a Cisco Director Class MDS Solution for More Efficient Storage Networking Service Overview Cisco s intelligent storage networking
RED HAT ENTERPRISE LINUX. STANDARDIZE & SAVE.
 RED HAT ENTERPRISE LINUX. STANDARDIZE & SAVE. Is putting Contact us INTRODUCTION You know the headaches of managing an infrastructure that is stretched to its limit. Too little staff. Too many users. Not
RED HAT ENTERPRISE LINUX. STANDARDIZE & SAVE. Is putting Contact us INTRODUCTION You know the headaches of managing an infrastructure that is stretched to its limit. Too little staff. Too many users. Not
CA Cloud Service Delivery Platform
 CA Cloud Service Delivery Platform Service Problems and Faults Release 1.1 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as
CA Cloud Service Delivery Platform Service Problems and Faults Release 1.1 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as
Six Sigma in the datacenter drives a zero-defects culture
 Six Sigma in the datacenter drives a zero-defects culture Situation Like many IT organizations, Microsoft IT wants to keep its global infrastructure available at all times. Scope, scale, and an environment
Six Sigma in the datacenter drives a zero-defects culture Situation Like many IT organizations, Microsoft IT wants to keep its global infrastructure available at all times. Scope, scale, and an environment
New Zealand Government IBM Infrastructure as a Service
 New Zealand Government IBM Infrastructure as a Service A world class agile cloud infrastructure designed to provide quick access to a security-rich, enterprise-class virtual server environment. 2 New Zealand
New Zealand Government IBM Infrastructure as a Service A world class agile cloud infrastructure designed to provide quick access to a security-rich, enterprise-class virtual server environment. 2 New Zealand
WEB-APIs DRIVING DIGITAL INNOVATION
 WEB-APIs DRIVING DIGITAL INNOVATION Importance of Web-APIs Simply put, Web-APIs are the medium to make a company s digital assets consumable to any channel, which has a current or latent need. It helps
WEB-APIs DRIVING DIGITAL INNOVATION Importance of Web-APIs Simply put, Web-APIs are the medium to make a company s digital assets consumable to any channel, which has a current or latent need. It helps
Demystifying GRC. Abstract
 White Paper Demystifying GRC Abstract Executives globally are highly focused on initiatives around Governance, Risk and Compliance (GRC), to improve upon risk management and regulatory compliances. Over
White Paper Demystifying GRC Abstract Executives globally are highly focused on initiatives around Governance, Risk and Compliance (GRC), to improve upon risk management and regulatory compliances. Over
DATA SHEET RSA NETWITNESS PLATFORM PROFESSIONAL SERVICES ACCELERATE TIME-TO-VALUE & MAXIMIZE ROI
 DATA SHEET RSA NETWITNESS PLATFORM PROFESSIONAL SERVICES ACCELERATE TIME-TO-VALUE & MAXIMIZE ROI EXECUTIVE SUMMARY The shortage of cybersecurity skills Organizations continue to face a shortage of IT skill
DATA SHEET RSA NETWITNESS PLATFORM PROFESSIONAL SERVICES ACCELERATE TIME-TO-VALUE & MAXIMIZE ROI EXECUTIVE SUMMARY The shortage of cybersecurity skills Organizations continue to face a shortage of IT skill
The SD-WAN implementation handbook
 The SD-WAN implementation handbook Your practical guide to a pain-free deployment This is the future of your business Moving to SD-WAN makes plenty of sense, solving a lot of technical headaches and enabling
The SD-WAN implementation handbook Your practical guide to a pain-free deployment This is the future of your business Moving to SD-WAN makes plenty of sense, solving a lot of technical headaches and enabling
CA Performance Management Data Aggregator
 CA Performance Management Data Aggregator Basic Self-Certification Guide 2.4.1 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to
CA Performance Management Data Aggregator Basic Self-Certification Guide 2.4.1 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to
INTELLIGENCE DRIVEN GRC FOR SECURITY
 INTELLIGENCE DRIVEN GRC FOR SECURITY OVERVIEW Organizations today strive to keep their business and technology infrastructure organized, controllable, and understandable, not only to have the ability to
INTELLIGENCE DRIVEN GRC FOR SECURITY OVERVIEW Organizations today strive to keep their business and technology infrastructure organized, controllable, and understandable, not only to have the ability to
Smart Data Center From Hitachi Vantara: Transform to an Agile, Learning Data Center
 Smart Data Center From Hitachi Vantara: Transform to an Agile, Learning Data Center Leverage Analytics To Protect and Optimize Your Business Infrastructure SOLUTION PROFILE Managing a data center and the
Smart Data Center From Hitachi Vantara: Transform to an Agile, Learning Data Center Leverage Analytics To Protect and Optimize Your Business Infrastructure SOLUTION PROFILE Managing a data center and the
Services for Smart Solutions: Delivering Innovations & Efficiency Surendran Vangadasalam
 Services for Smart Solutions: Delivering Innovations & Efficiency Surendran Vangadasalam Practice Leader : Borderless Network Architecture APJC Services Agenda Priorities & Smart Solutions Innovation and
Services for Smart Solutions: Delivering Innovations & Efficiency Surendran Vangadasalam Practice Leader : Borderless Network Architecture APJC Services Agenda Priorities & Smart Solutions Innovation and
NC Education Cloud Feasibility Report
 1 NC Education Cloud Feasibility Report 1. Problem Definition and rationale North Carolina districts are generally ill-equipped to manage production server infrastructure. Server infrastructure is most
1 NC Education Cloud Feasibility Report 1. Problem Definition and rationale North Carolina districts are generally ill-equipped to manage production server infrastructure. Server infrastructure is most
Improve Service Quality: CA Insight DPM Integration with CA Spectrum Service Assurance. Walter Guerrero, Sr Software Engineer
 Improve Service Quality: CA Insight DPM Integration with CA Spectrum Service Assurance Walter Guerrero, Sr Software Engineer Terms of This Presentation This presentation was based on current information
Improve Service Quality: CA Insight DPM Integration with CA Spectrum Service Assurance Walter Guerrero, Sr Software Engineer Terms of This Presentation This presentation was based on current information
CA Automation Capabilities A Technical Look at Process and Runbook Automation. Tom Kouhsari and AJ Dennis
 CA Automation Capabilities A Technical Look at Process and Runbook Automation Tom Kouhsari and AJ Dennis Terms of This Presentation This presentation was based on current information and resource allocations
CA Automation Capabilities A Technical Look at Process and Runbook Automation Tom Kouhsari and AJ Dennis Terms of This Presentation This presentation was based on current information and resource allocations
A Better Approach to Leveraging an OpenStack Private Cloud. David Linthicum
 A Better Approach to Leveraging an OpenStack Private Cloud David Linthicum A Better Approach to Leveraging an OpenStack Private Cloud 1 Executive Summary The latest bi-annual survey data of OpenStack users
A Better Approach to Leveraging an OpenStack Private Cloud David Linthicum A Better Approach to Leveraging an OpenStack Private Cloud 1 Executive Summary The latest bi-annual survey data of OpenStack users
HPE IT Operations Management (ITOM) Thought Leadership Series
 haroldk@theedison.com 89 Fifth Avenue, 7th Floor New York, NY 10003 www.theedison.com HPE IT Operations Management (ITOM) Thought Leadership Series Supporting Transformation from Traditional IT to a Digital
haroldk@theedison.com 89 Fifth Avenue, 7th Floor New York, NY 10003 www.theedison.com HPE IT Operations Management (ITOM) Thought Leadership Series Supporting Transformation from Traditional IT to a Digital
Data Management and Security in the GDPR Era
 Data Management and Security in the GDPR Era Franck Hourdin; Vice President, EMEA Security Russ Lowenthal; Director, Database Security Product Management Mike Turner; Chief Operating Officer, Capgemini
Data Management and Security in the GDPR Era Franck Hourdin; Vice President, EMEA Security Russ Lowenthal; Director, Database Security Product Management Mike Turner; Chief Operating Officer, Capgemini
WITH ACTIVEWATCH EXPERT BACKED, DETECTION AND THREAT RESPONSE BENEFITS HOW THREAT MANAGER WORKS SOLUTION OVERVIEW:
 SOLUTION OVERVIEW: ALERT LOGIC THREAT MANAGER WITH ACTIVEWATCH EXPERT BACKED, DETECTION AND THREAT RESPONSE Protecting your business assets and sensitive data requires regular vulnerability assessment,
SOLUTION OVERVIEW: ALERT LOGIC THREAT MANAGER WITH ACTIVEWATCH EXPERT BACKED, DETECTION AND THREAT RESPONSE Protecting your business assets and sensitive data requires regular vulnerability assessment,
APPLYING DATA CENTER INFRASTRUCTURE MANAGEMENT IN COLOCATION DATA CENTERS
 APPLYING DATA CENTER INFRASTRUCTURE MANAGEMENT IN COLOCATION DATA CENTERS Table of Contents Executive Summary 3 The Colocation Market 4 An Introduction to DCIM 5 The Value of DCIM for Colocation Providers
APPLYING DATA CENTER INFRASTRUCTURE MANAGEMENT IN COLOCATION DATA CENTERS Table of Contents Executive Summary 3 The Colocation Market 4 An Introduction to DCIM 5 The Value of DCIM for Colocation Providers
Get your business Skype d up. Lessons learned from Skype for Business adoption
 Get your business Skype d up Lessons learned from Skype for Business adoption On the rise with Skype for Business Recent figures from Microsoft found that 90% of Fortune 500 companies and over 100 million
Get your business Skype d up Lessons learned from Skype for Business adoption On the rise with Skype for Business Recent figures from Microsoft found that 90% of Fortune 500 companies and over 100 million
Security Monitoring Engineer / (NY or NC) Director, Information Security. New York, NY or Winston-Salem, NC. Location:
 Position: Reports to: Location: Security Monitoring Engineer / (NY or NC) Director, Information Security New York, NY or Winston-Salem, NC Position Summary: The Clearing House (TCH) Information Security
Position: Reports to: Location: Security Monitoring Engineer / (NY or NC) Director, Information Security New York, NY or Winston-Salem, NC Position Summary: The Clearing House (TCH) Information Security
PPM Essentials Accelerator Product Guide - On Premise. Service Pack
 PPM Essentials Accelerator Product Guide - On Premise Service Pack 02.0.02 This Documentation, which includes embedded help systems and electronically distributed materials (hereinafter referred to as
PPM Essentials Accelerator Product Guide - On Premise Service Pack 02.0.02 This Documentation, which includes embedded help systems and electronically distributed materials (hereinafter referred to as
HP BladeSystem Matrix
 HP BladeSystem Matrix Industry s first Converged Infrastructure platform that delivers IT services in minutes Solution brief Get the benefits of shared services today A better approach for productivity
HP BladeSystem Matrix Industry s first Converged Infrastructure platform that delivers IT services in minutes Solution brief Get the benefits of shared services today A better approach for productivity
IT Consulting and Implementation Services
 PORTFOLIO OVERVIEW IT Consulting and Implementation Services Helping IT Transform the Way Business Innovates and Operates 1 2 PORTFOLIO OVERVIEW IT Consulting and Implementation Services IT is moving from
PORTFOLIO OVERVIEW IT Consulting and Implementation Services Helping IT Transform the Way Business Innovates and Operates 1 2 PORTFOLIO OVERVIEW IT Consulting and Implementation Services IT is moving from
JBoss Enterprise Middleware
 JBoss Enterprise Middleware Making software from the open source community ready for the enterprise DLT Solutions 2411 Dulles Corner Park, Suite 800 Herndon, VA 20171 Web: www.dlt.com Phone: 703-709-7172
JBoss Enterprise Middleware Making software from the open source community ready for the enterprise DLT Solutions 2411 Dulles Corner Park, Suite 800 Herndon, VA 20171 Web: www.dlt.com Phone: 703-709-7172
IBM Software IBM InfoSphere Information Server for Data Quality
 IBM InfoSphere Information Server for Data Quality A component index Table of contents 3 6 9 9 InfoSphere QualityStage 10 InfoSphere Information Analyzer 12 InfoSphere Discovery 13 14 2 Do you have confidence
IBM InfoSphere Information Server for Data Quality A component index Table of contents 3 6 9 9 InfoSphere QualityStage 10 InfoSphere Information Analyzer 12 InfoSphere Discovery 13 14 2 Do you have confidence
Closing the Biggest Security Hole in Web Application Delivery
 WHITE PAPER JANUARY 2014 Closing the Biggest Security Hole in Web Application Delivery Addressing Session Hijacking with CA SiteMinder Enhanced Session Assurance with DeviceDNA Martin Yam CA Security Management
WHITE PAPER JANUARY 2014 Closing the Biggest Security Hole in Web Application Delivery Addressing Session Hijacking with CA SiteMinder Enhanced Session Assurance with DeviceDNA Martin Yam CA Security Management
Dynamic What? I m Dynamic, Aren t You? Andrew Chapman & Sam Knutson VP Product Management CA Technologies
 Dynamic What? I m Dynamic, Aren t You? Andrew Chapman & Sam Knutson VP Product Management CA Technologies March 13, 2014 Dynamic Data Center: Business Solutions on Demand Continuous Delivery Bring Your
Dynamic What? I m Dynamic, Aren t You? Andrew Chapman & Sam Knutson VP Product Management CA Technologies March 13, 2014 Dynamic Data Center: Business Solutions on Demand Continuous Delivery Bring Your
Networking for a dynamic infrastructure: getting it right.
 IBM Global Technology Services Networking for a dynamic infrastructure: getting it right. A guide for realizing the full potential of virtualization June 2009 Executive summary June 2009 Networking for
IBM Global Technology Services Networking for a dynamic infrastructure: getting it right. A guide for realizing the full potential of virtualization June 2009 Executive summary June 2009 Networking for
Comprehensive Data Center Energy Management Solutions
 FROM INSIGHT TO EFFICIENCY: Comprehensive Data Center Energy Management Solutions Since 1995, facility managers and BAS professionals have relied on the Niagara framework to provide full convergence of
FROM INSIGHT TO EFFICIENCY: Comprehensive Data Center Energy Management Solutions Since 1995, facility managers and BAS professionals have relied on the Niagara framework to provide full convergence of
IBM Internet Security Systems Proventia Management SiteProtector
 Supporting compliance and mitigating risk through centralized management of enterprise security devices IBM Internet Security Systems Proventia Management SiteProtector Highlights Reduces the costs and
Supporting compliance and mitigating risk through centralized management of enterprise security devices IBM Internet Security Systems Proventia Management SiteProtector Highlights Reduces the costs and
SIEMLESS THREAT MANAGEMENT
 SOLUTION BRIEF: SIEMLESS THREAT MANAGEMENT SECURITY AND COMPLIANCE COVERAGE FOR APPLICATIONS IN ANY ENVIRONMENT Evolving threats, expanding compliance risks, and resource constraints require a new approach.
SOLUTION BRIEF: SIEMLESS THREAT MANAGEMENT SECURITY AND COMPLIANCE COVERAGE FOR APPLICATIONS IN ANY ENVIRONMENT Evolving threats, expanding compliance risks, and resource constraints require a new approach.
ALIENVAULT USM FOR AWS SOLUTION GUIDE
 ALIENVAULT USM FOR AWS SOLUTION GUIDE Summary AlienVault Unified Security Management (USM) for AWS is a unified security platform providing threat detection, incident response, and compliance management
ALIENVAULT USM FOR AWS SOLUTION GUIDE Summary AlienVault Unified Security Management (USM) for AWS is a unified security platform providing threat detection, incident response, and compliance management
Proven Integration Strategies for Government
 Opening Slide Proven Integration Strategies for Government Larry Singer, Vice President, US State and Local Government and Education Sales Technology for better business outcomes 2007 Hewlett-Packard Development
Opening Slide Proven Integration Strategies for Government Larry Singer, Vice President, US State and Local Government and Education Sales Technology for better business outcomes 2007 Hewlett-Packard Development
SIEM Solutions from McAfee
 SIEM Solutions from McAfee Monitor. Prioritize. Investigate. Respond. Today s security information and event management (SIEM) solutions need to be able to identify and defend against attacks within an
SIEM Solutions from McAfee Monitor. Prioritize. Investigate. Respond. Today s security information and event management (SIEM) solutions need to be able to identify and defend against attacks within an
agility made possible
 SOLUTION BRIEF CA Mainframe Suite for IBM Rational Developer for System z Unit Test do you want to run your mainframe software from CA Technologies on IBM Rational Developer for System z Unit Test? agility
SOLUTION BRIEF CA Mainframe Suite for IBM Rational Developer for System z Unit Test do you want to run your mainframe software from CA Technologies on IBM Rational Developer for System z Unit Test? agility
Making the most of DCIM. Get to know your data center inside out
 Making the most of DCIM Get to know your data center inside out What is DCIM? Data Center Infrastructure Management (DCIM) is the discipline of managing the physical infrastructure of a data center and
Making the most of DCIM Get to know your data center inside out What is DCIM? Data Center Infrastructure Management (DCIM) is the discipline of managing the physical infrastructure of a data center and
Raytheon s Strategic IT Energy and Resource Management Program
 Raytheon s Strategic IT Energy and Resource Management Program 2degrees Champion Award Application February 2015. Copyright 2014 Raytheon Company. All rights reserved. Customer Success Is Our Mission is
Raytheon s Strategic IT Energy and Resource Management Program 2degrees Champion Award Application February 2015. Copyright 2014 Raytheon Company. All rights reserved. Customer Success Is Our Mission is
CenturyLink for Microsoft
 Strategic Partner Alliances CenturyLink for Microsoft EMPOWER REACH AGILITY 2017 CenturyLink. All Rights Reserved. The CenturyLink mark, pathways logo and certain CenturyLink product names are the property
Strategic Partner Alliances CenturyLink for Microsoft EMPOWER REACH AGILITY 2017 CenturyLink. All Rights Reserved. The CenturyLink mark, pathways logo and certain CenturyLink product names are the property
TECHNOLOGY BRIEF: CA ERWIN DATA PROFILER. Combining Data Profiling and Data Modeling for Better Data Quality
 TECHNOLOGY BRIEF: CA ERWIN DATA PROFILER Combining Data Profiling and Data Modeling for Better Data Quality Table of Contents Executive Summary SECTION 1: CHALLENGE 2 Reducing the Cost and Risk of Data
TECHNOLOGY BRIEF: CA ERWIN DATA PROFILER Combining Data Profiling and Data Modeling for Better Data Quality Table of Contents Executive Summary SECTION 1: CHALLENGE 2 Reducing the Cost and Risk of Data
Information Security and Service Management. Security and Risk Management ISSM and ITIL/ITSM Interrelationship
 Information Security and Service Management for Management better business for State outcomes & Local Governments Security and Risk Management ISSM and ITIL/ITSM Interrelationship Introduction Over the
Information Security and Service Management for Management better business for State outcomes & Local Governments Security and Risk Management ISSM and ITIL/ITSM Interrelationship Introduction Over the
Hybrid WAN Operations: Extend Network Monitoring Across SD-WAN and Legacy WAN Infrastructure
 Hybrid WAN Operations: Extend Network Monitoring Across SD-WAN and Legacy WAN Infrastructure An ENTERPRISE MANAGEMENT ASSOCIATES (EMA ) White Paper Prepared for SevOne May 2017 IT & DATA MANAGEMENT RESEARCH,
Hybrid WAN Operations: Extend Network Monitoring Across SD-WAN and Legacy WAN Infrastructure An ENTERPRISE MANAGEMENT ASSOCIATES (EMA ) White Paper Prepared for SevOne May 2017 IT & DATA MANAGEMENT RESEARCH,
Getting Hybrid IT Right. A Softchoice Guide to Hybrid Cloud Adoption
 Getting Hybrid IT Right A Softchoice Guide to Hybrid Cloud Adoption Your Path to an Effective Hybrid Cloud The hybrid cloud is on the radar for business and IT leaders everywhere. IDC estimates 1 that
Getting Hybrid IT Right A Softchoice Guide to Hybrid Cloud Adoption Your Path to an Effective Hybrid Cloud The hybrid cloud is on the radar for business and IT leaders everywhere. IDC estimates 1 that
Turning Strategic Insight Into Business Impact
 Turning Strategic Insight Into Business Impact VMware Accelerate Advisory Services Identify Opportunities and Create Strategies for the Journey to IT as a Service No longer relegated to simply keeping
Turning Strategic Insight Into Business Impact VMware Accelerate Advisory Services Identify Opportunities and Create Strategies for the Journey to IT as a Service No longer relegated to simply keeping
Network Visibility and Segmentation
 Network Visibility and Segmentation 2019 Cisco and/ or its affiliates. All rights reserved. Contents Network Segmentation A Services Approach 3 The Process of Segmentation 3 Segmentation Solution Components
Network Visibility and Segmentation 2019 Cisco and/ or its affiliates. All rights reserved. Contents Network Segmentation A Services Approach 3 The Process of Segmentation 3 Segmentation Solution Components
RSA Solution Brief. The RSA Solution for Cloud Security and Compliance
 The RSA Solution for Cloud Security and Compliance The RSA Solution for Cloud Security and Compliance enables enduser organizations and service providers to orchestrate and visualize the security of their
The RSA Solution for Cloud Security and Compliance The RSA Solution for Cloud Security and Compliance enables enduser organizations and service providers to orchestrate and visualize the security of their
Best Practices in Securing a Multicloud World
 Best Practices in Securing a Multicloud World Actions to take now to protect data, applications, and workloads We live in a multicloud world. A world where a multitude of offerings from Cloud Service Providers
Best Practices in Securing a Multicloud World Actions to take now to protect data, applications, and workloads We live in a multicloud world. A world where a multitude of offerings from Cloud Service Providers
CA Cloud Service Delivery Platform
 CA Cloud Service Delivery Platform Problem Manager Release 1.1 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation
CA Cloud Service Delivery Platform Problem Manager Release 1.1 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation
White Paper. View cyber and mission-critical data in one dashboard
 View cyber and mission-critical data in one dashboard Table of contents Rising cyber events 2 Mitigating threats 2 Heighten awareness 3 Evolving the solution 5 One of the direct benefits of the Homeland
View cyber and mission-critical data in one dashboard Table of contents Rising cyber events 2 Mitigating threats 2 Heighten awareness 3 Evolving the solution 5 One of the direct benefits of the Homeland
CA Cloud Service Delivery Platform
 CA Cloud Service Delivery Platform Incident Manager Release 1.1 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation
CA Cloud Service Delivery Platform Incident Manager Release 1.1 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation
Unlock a Second Wave of Energy Savings with Automated Measurement and Verification
 WHITE PAPER January 2013 Unlock a Second Wave of Energy Savings with Automated Measurement and Verification Lara Greden, PhD Senior Principal / Energy & Sustainability CA Technologies Table of Contents
WHITE PAPER January 2013 Unlock a Second Wave of Energy Savings with Automated Measurement and Verification Lara Greden, PhD Senior Principal / Energy & Sustainability CA Technologies Table of Contents
21ST century enterprise. HCL Technologies Presents. Roadmap for Data Center Transformation
 21ST century enterprise HCL Technologies Presents Roadmap for Data Center Transformation june 2016 21st Century Impact on Data Centers The rising wave of digitalization has changed the way IT impacts business.
21ST century enterprise HCL Technologies Presents Roadmap for Data Center Transformation june 2016 21st Century Impact on Data Centers The rising wave of digitalization has changed the way IT impacts business.
ORACLE SERVICES FOR APPLICATION MIGRATIONS TO ORACLE HARDWARE INFRASTRUCTURES
 ORACLE SERVICES FOR APPLICATION MIGRATIONS TO ORACLE HARDWARE INFRASTRUCTURES SERVICE, SUPPORT AND EXPERT GUIDANCE FOR THE MIGRATION AND IMPLEMENTATION OF YOUR ORACLE APPLICATIONS ON ORACLE INFRASTRUCTURE
ORACLE SERVICES FOR APPLICATION MIGRATIONS TO ORACLE HARDWARE INFRASTRUCTURES SERVICE, SUPPORT AND EXPERT GUIDANCE FOR THE MIGRATION AND IMPLEMENTATION OF YOUR ORACLE APPLICATIONS ON ORACLE INFRASTRUCTURE
The Value of Data Modeling for the Data-Driven Enterprise
 Solution Brief: erwin Data Modeler (DM) The Value of Data Modeling for the Data-Driven Enterprise Designing, documenting, standardizing and aligning any data from anywhere produces an enterprise data model
Solution Brief: erwin Data Modeler (DM) The Value of Data Modeling for the Data-Driven Enterprise Designing, documenting, standardizing and aligning any data from anywhere produces an enterprise data model
THE INSIDE-OUT APPROACH. Enabling an Open, Scalable Data Center IoT
 THE INSIDE-OUT APPROACH Enabling an Open, Scalable Data Center IoT TWO STAGE POWER DISTRIBUTION The Next Wave of Disruption With an impact that extends from transportation to healthcare to manufacturing
THE INSIDE-OUT APPROACH Enabling an Open, Scalable Data Center IoT TWO STAGE POWER DISTRIBUTION The Next Wave of Disruption With an impact that extends from transportation to healthcare to manufacturing
AN APPLICATION-CENTRIC APPROACH TO DATA CENTER MIGRATION
 WHITE PAPER AN APPLICATION-CENTRIC APPROACH TO DATA CENTER MIGRATION Five key success factors Abstract IT organizations today are under constant business pressure to transform their infrastructure to reduce
WHITE PAPER AN APPLICATION-CENTRIC APPROACH TO DATA CENTER MIGRATION Five key success factors Abstract IT organizations today are under constant business pressure to transform their infrastructure to reduce
Building a power monitoring and management strategy Selecting the software and services needed to keep critical power systems continuously available
 White Paper Markets Served Data center & IT By Arthur Mulligan Product Line Manager, Eaton U.S. Power Quality Jim Tessier Product Manager, Eaton IT Hardware and Software Building a power monitoring and
White Paper Markets Served Data center & IT By Arthur Mulligan Product Line Manager, Eaton U.S. Power Quality Jim Tessier Product Manager, Eaton IT Hardware and Software Building a power monitoring and
OUTSMART ADVANCED CYBER ATTACKS WITH AN INTELLIGENCE-DRIVEN SECURITY OPERATIONS CENTER
 OUTSMART ADVANCED CYBER ATTACKS WITH AN INTELLIGENCE-DRIVEN SECURITY OPERATIONS CENTER HOW TO ADDRESS GARTNER S FIVE CHARACTERISTICS OF AN INTELLIGENCE-DRIVEN SECURITY OPERATIONS CENTER 1 POWERING ACTIONABLE
OUTSMART ADVANCED CYBER ATTACKS WITH AN INTELLIGENCE-DRIVEN SECURITY OPERATIONS CENTER HOW TO ADDRESS GARTNER S FIVE CHARACTERISTICS OF AN INTELLIGENCE-DRIVEN SECURITY OPERATIONS CENTER 1 POWERING ACTIONABLE
Securing Your Digital Transformation
 Securing Your Digital Transformation Security Consulting Managed Security Leveraging experienced, senior experts to help define and communicate risk and security program strategy using real-world data,
Securing Your Digital Transformation Security Consulting Managed Security Leveraging experienced, senior experts to help define and communicate risk and security program strategy using real-world data,
BUILDING the VIRtUAL enterprise
 BUILDING the VIRTUAL ENTERPRISE A Red Hat WHITEPAPER www.redhat.com As an IT shop or business owner, your ability to meet the fluctuating needs of your business while balancing changing priorities, schedules,
BUILDING the VIRTUAL ENTERPRISE A Red Hat WHITEPAPER www.redhat.com As an IT shop or business owner, your ability to meet the fluctuating needs of your business while balancing changing priorities, schedules,
Professional Services for Cloud Management Solutions
 Professional Services for Cloud Management Solutions Accelerating Your Cloud Management Capabilities CEOs need people both internal staff and thirdparty providers who can help them think through their
Professional Services for Cloud Management Solutions Accelerating Your Cloud Management Capabilities CEOs need people both internal staff and thirdparty providers who can help them think through their
Italy s Interior Ministry Assures Electoral Data Collection with CA Technologies Solutions
 CUSTOMER SUCCESS STORY Italy s Interior Ministry Assures Electoral Data Collection with CA Technologies Solutions CUSTOMER PROFILE Organization: Italy s Interior Ministry Department for Internal and Territorial
CUSTOMER SUCCESS STORY Italy s Interior Ministry Assures Electoral Data Collection with CA Technologies Solutions CUSTOMER PROFILE Organization: Italy s Interior Ministry Department for Internal and Territorial
