A Measurement-Based Model for Parallel Real-Time Tasks
|
|
|
- Isabella Fields
- 5 years ago
- Views:
Transcription
1 A Measureent-Based Model for Parallel Real-Tie Tasks Kunal Agrawal 1 Washington University in St. Louis St. Louis, MO, USA kunal@wustl.edu Sanjoy Baruah 2 Washington University in St. Louis St. Louis, MO, USA baruah@wustl.edu Abstract Under the federated paradig of ultiprocessor scheduling, a set of processors is reserved for the exclusive use of each real-tie task. If tasks are characterized very conservatively as is typical in safety-critical systes, it is likely that ost invocations of the task will have coputational deand far below the worst-case characterization, and could have been scheduled correctly upon far fewer processors than were assigned to it assuing the worst-case characterization of its runtie behavior. Provided we could safely deterine during run-tie when all the processors are going to be needed, for the rest of the tie the unneeded processors could be idled in low-energy sleep ode, or used for executing non-real tie work in the background. In this paper we propose a odel for representing parallelizable real-tie tasks in a anner that perits us to do so. Our odel does not require us to have fine-grained knowledge of the internal structure of the code represented by the task; rather, it characterizes each task by a few paraeters that are obtained by repeatedly executing the code under different conditions and easuring the run-ties ACM Subject Classification Coputer systes organization Real-tie systes, Software and its engineering Real-tie schedulability, Theory of coputation Parallel coputing odels Keywords and phrases ultiprocessor federated scheduling, parallel tasks, work and span, ixed criticality Digital Object Identifier /LIPIcs.ECRTS Introduction Scheduling theory is concerned with the analysis of real-tie systes. As ultiprocessor and ulticore ipleentations of real-tie systes becoe prevalent, it is desirable that the odels used in scheduling theory for representing real-tie workloads be capable of exposing the parallelis that ay exist within these workloads. This need has given rise to foral task odels such as the fork-join odel [1, 2], the sporadic DAG tasks odel [3] see [4, Chapter 21] for a text-book description, the ulti-dag odel [5], the conditional DAG 1 Supported in part by SF grants CCF and CCF Supported in part by SF Grants CS , CPS , and CS Kunal Agrawal and Sanjoy Baruah; licensed under Creative Coons License CC-BY 30th Euroicro Conference on Real-Tie Systes ECRTS Editor: Sebastian Alteyer; Article o. 5; pp. 5:1 5:19 Leibniz International Proceedings in Inforatics Schloss Dagstuhl Leibniz-Zentru für Inforatik, Dagstuhl Publishing, Gerany
2 5:2 A Measureent-Based Model for Parallel Real-Tie Tasks tasks odel [6, 7] etc. Each of these odels represents the internal structure of the piece of code being odeled at a relatively fine level of granularity, with the parallelis in the code typically odeled as a directed acyclic graph DAG. Each vertex in such a DAG represents a segent of sequential code, and edges represent precedence constraints between such code segents: the segent of sequential code represented by the vertex at the tail of an edge uch coplete execution before the segent of sequential code represented by the vertex at the head of the edge ay begin to execute. Such DAG-based odels for representing parallel real-tie code have proved popular in the real-tie scheduling theory counity, and uch iportant and interesting research has been accoplished that is based upon representing systes using these odels. This body of research has indeed provided us with a deeper insight into the issues that arise in exploiting parallelis in ultiprocessor real-tie systes; however due to a variety of reasons soe of which are enuerated and discussed in soe detail in Section 2 there are soe classes of real-tie applications for which such DAG-based representations ay not be appropriate for the purposes of schedulability analysis; alternative representations are needed. In this paper we propose one such possible alternative representation that ay be suitable under certain circustances. In this odel we do not attept to explicitly represent the internal parallel structure of the code. Instead, we seek to identify a few iportant paraeters of parallalizable code that are ost useful for scheduling algoriths that seek to schedule such code upon ultiprocessor platfors, and propose that the code be looked upon as a black box that is characterized by just these paraeters. Furtherore, we do not require that the internal structure of the code be exained in order to obtain these paraeter values. Rather, we propose that values for these paraeters be estiated via extensive siulation experients: repeatedly executing the code in a controlled laboratory environent in order to be able to copute bounds on the paraeter values. Such an approach is inspired by the large and growing body of current research [8] on probabilistic worst-case execution tie pwcet analysis. Since easureent-based approaches are typically not able to provide paraeter values that are guaranteed correct with absolute certainty, we incorporate, fro the ixed-criticality scheduling literature [9], Vestal s idea [10] of characterizing a single task with two sets of paraeters: one set very conservative and hence trusted to a very high level of assurance and the other, far less conservative but ore representative of typical behavior. Organization. The reainder of this paper is organized as follows. In Section 2 we otivate the new odel by identifying relevant characteristics of parallelizable real-tie code that current odels are not well-suited to represent, and forally define the workload and syste odel that we are proposing. In Section 3 we briefly discuss soe prior research that provides the foundations upon which our proposed odel is built. In Section 4 we derive, and prove the correctness and other relevant properties of, an algorith for scheduling systes represented using the proposed odel. Our overall objective is to be able to obtain ore resource-efficient ipleentations of systes, while ensuring correctness; in Section 5 we explore soe possible eans of further enhancing the efficiency of the algorith presented in Section 4. We conclude in Section 6 with a discussion on the relevance, significance, and liitations of our proposed odel, and an enueration of possible directions for continued research.
3 K. Agrawal and S. Baruah 5:3 2 Syste odel: Motivation and Definition In this section we flesh out the details of the odel we are proposing for representing parallelizable real-tie code that is not conveniently represented using previously-proposed DAG-based task odels. We will first otivate the odel inforally, and seek to explain aspects of the odel via illustrative exaples. A foral definition of the odel is then provided in Section 2.1; our proposed algorith for scheduling tasks represented using this odel is described in Section 2.2. Why a new odel? As stated in Section 1 above, several excellent DAG-based odels for representing parallel real-tie code have been developed in the real-tie scheduling theory counity; however there are soe classes of real-tie applications for which such odels have proved unsuitable. This ay be for one or ore of the following reasons: 1. The internal structure of the parallel code ay be very coplex, with ultiple conditional dependencies as ay be represented in e.g., the conditional DAG tasks odel [6, 7] and bounded loops. Explicit enueration of all possible paths through such code in order to identify worst-case behavior ay be coputationally infeasible If soe parts of the code are procured fro outside the application-developers organization, the provider of this code ay seek to protect their intellectual property IP by not revealing the internal structure of the code and instead only providing executables this ay be the case if, e.g., coercial vision algoriths are used in a real-tie application. Although reverse-engineering of the executable code in order to deterine its internal structure ay be possible in principle, such reverse engineering tends to be tedious and error-prone. 3. Algoriths for the analysis of systes represented using DAG-based odels tend to have run-tie pseudo-polynoial or exponential in the size of the DAG. Such run-ties have traditionally been considered acceptably sall enough to allow the algoriths to be practical in practice; however, this state of affairs ay not continue in the future. For any cyber-physical real-tie systes, constraints such as deadlines are typically dictated by physical factors. As the processors upon which we ipleent such cyber-physical realtie systes becoe increasingly ore powerful, it becoes possible to incorporate far ore coplex processing that would be represented as larger DAGs than was previously the case. As this trend towards ore coplex processing and the consequent larger DAGs continues, run-ties pseudo-polynoial in the size of these larger DAGs ay becoe too large be used in practice during syste design and analysis. 4. Further exacerbating the situation, explicitly representing the internal structure of soe pieces of parallel code in DAG for results in DAGs that ay be of size exponential in the size of the code. Consider, for exaple, the following code snippet written in OpenMP an application prograing interface API that supports ulti-platfor shared eory ultiprocessing prograing: #praga op parallel #praga op for for i=0; i<10; i++ { //do_soething } 3 We point out that techniques for approxiating the worst-case behavior of coplex conditional parallelizable code have been proposed with regards to specific scheduling algoriths such as global fixed-priority [6], global EDF [7] or federated [11]. E C R T S
4 5:4 A Measureent-Based Model for Parallel Real-Tie Tasks This code snippet would translate to a DAG with = 12 nodes. If we were to replace the 10 in the upper bound of the for loop with a 100, however, the resulting DAG would have 102 nodes; replacing it with 1000 would yield 1002 nodes, etc. increasing the size of the progra by one ASCII character results in an alost ten-fold increase in the size of the DAG. 5. Particularly for conditional code, it ay be the case that the true worst-case behavior of the code is very infrequently expressed during run-tie. 4. Traditional odels based on conditional DAGs ay not be suitable for representing such code although ixedcriticality [10, 12, 13, 14] extensions of such conditional DAG odels are a possibility to our knowledge, such odels have not yet been proposed, let alone studied. For pieces of parallel real-tie code possessing one or ore of the characteristics discussed above, DAG-based representations ay not be appropriate for the purposes of schedulability analysis; alternative representations are needed. Let us now discuss what such a representation should provide. Identifying relevant characteristics of parallelizable real-tie code. In odeling parallelizable real-tie code that is to be executed upon a ultiprocessor platfor, a prie objective is to enable the exploitation of the parallelis that ay be present in the code by scheduling algoriths, in order to enhance the likelihood that we will be able to eet tiing constraints. We are interested here in developing predictable real-tie systes systes that can have their tiing and other correctness verified prior to run-tie. For the purposes of enabling a priori tiing verification, decades of research in the parallel coputing counity suggests the following two tiing paraeters of a piece of parallelizable code are particularly significant: 1. The work paraeter denotes the cuulative worst-case execution tie of all the parallel branches that are executed across all processors. ote that for non-conditional parallelizable code this is equal to the worst case execution tie of the code on a single processor ignoring counication overhead fro synchronizing processors. 2. The span paraeter denotes the axiu cuulative worst-case execution tie of any sequence of precedence-constrained pieces of code. It represents a lower bound on the duration of tie the code would take to execute, regardless of the nuber of processors available. The span of a coputation is also called the critical path length of the coputation, and a sequence of precedence-constrained pieces of code with cuulative worst-case execution tie equal to the span, a critical path through the coputation. The relevance of these two paraeters arises fro well-known results in scheduling theory concerning the ultiprocessor scheduling of precedence-constrained jobs i.e., DAGs to iniize akespan this is the widely-studied P prec S ax proble in the classic 3- field α β γ notation that is coonly used in scheduling theory [15]. This proble has long been known to be P-hard in the strong sense [16]; i.e., coputationally highly intractable. However, Graha s list scheduling algorith [17], which constructs a workconserving schedule by executing at each instant in tie an available job, if any are present, upon any available processor, perfors fairly well in practice. It was shown [17] that list 4 Consider, for exaple, a real-tie application that periodically onitors a sensor for anoalous input. Most of the tie the sought-for anoolous input is not detected, and not uch coputation needs to be perfored. But on the rare occasions when anoalous input is detected, considerable additional processing of such input is necessary.
5 K. Agrawal and S. Baruah 5:5 scheduling akes the following guarantee: if S ax denotes the iniu akespan with which a particular DAG can be scheduled upon processors, then the schedule generated by list scheduling this DAG upon processors will have a akespan no greater than 2 1 S ax. This result, in conjunction with a hardness result in [18] showing that deterining a schedule for this DAG of akespan 4 3 S ax reains P-hard in the strong sense 5, suggests that list scheduling is a reasonable algorith to use in practice, and in fact ost run-tie scheduling algoriths that are used for scheduling DAGs upon ultiprocessors use soe variant or the other of list scheduling. We will do so in this paper as well. An upper bound on the akespan of a schedule generated by list scheduling is easily stated. Letting work and span denote the work and span paraeters of the DAG being scheduled, it has been proved in [17] that the akespan of the schedule for a given DAG is guaranteed to be no larger than work span + span 1 Thus a good upper bound on the akespan of the list-scheduling generated schedule for a DAG ay be stated in ters of only its work and span paraeters. Equivalently if the DAG represents a real-tie piece of code characterized by a relative deadline paraeter D, work span + span D is a sufficient test for deterining whether the code will coplete by its deadline upon an -processor platfor. We therefore identify the work and span paraeters of a piece of parallel real-tie code as being particularly relevant fro the perspective of schedulability analysis. A easureent-based approach to paraeter estiation. The work and span paraeters of tasks that are represented using DAG-based odels are quite straightforward to copute in tie linear in the representation of the DAGs algoriths for doing so are described in [3, 7]. As we have discussed above, however, our interest is in characterizing parallel code that is typically not conveniently represented using DAG-based odels. We propose that for the purposes of representing pieces of such code for schedulability analysis, we ignore their internal structure and instead seek to characterize the solely via their work and span paraeters. And since we cannot in general deterine the precise values of the work and span paraeters of a piece of code without knowing its internal structure, we advocate here that easureent-based approaches be used to estiate these paraeters. Measureentbased approaches have been developed for estiating probabilistic worst-case execution tie pwcet [20, 21, 22] distributions of individual pieces of code, and ipleented in pwcet tools such as RapiTie fro Rapita Systes. We now briefly discuss how easureent-based approaches ay be adapted to estiate the work and span paraeters of parallel code. Ignoring overhead associated with ipleenting global scheduling, observe that the work paraeter of a piece of code is equal to the tie needed to coplete its execution upon a single processor, while its span paraeter is equal to the tie needed to coplete its execution upon an unbounded nuber of processors. Hence one can estiate the probability distribution of the work paraeter of a piece of code by using pwcet techniques to estiate its WCET distribution upon a single processor. One can siilarly estiate the probability distribution of the span paraeter by 5 In fact, assuing a reasonable coplexity-theoretic conjecture that is soewhat stronger than P P, a result of Svensson [19] iplies that a polynoial-tie algorith for deterining a schedule of akespan 2S ax for all is ruled out. E C R T S
6 5:6 A Measureent-Based Model for Parallel Real-Tie Tasks 1. first adapting the easureent-based techniques underpinning pwcet-estiation to deterine the akespan probability distribution upon a given nuber of processors rather than the copletion-tie upon a single processor; and then 2. estiating the akespan distribution of the parallel code upon platfors in which the nuber of processors is repeatedly increased, until further increases do not result in significant changes to the estiated distribution. The proposed odel: ultiple work and span estiates. As discussed above, it is possible, by suitable adaptation and application of pwcet techniques, to estiate probability distributions for the work and span paraeters of pieces of parallel real-tie code. It is understood in the pwcet counity that pwcet-based techniques cannot in general deterine bounds that are guaranteed to be correct with absolute certainty; rather, they provide bounds that are guaranteed correct to specified probabilistic degrees of confidence/ levels of assurance Davis et al. [8] provide a thoughtful and considered discussion as to how the concept of probabilities should be interpreted when used in such a anner. In the odel we propose for representing parallel real-tie code, we suggest that each such piece of code be characterized by two pairs of work, span paraeter values, each pair corresponding to a different probability threshold in the work and span distributions and therefore valid at different levels of assurance. Specifically, one pair of values should be very conservative and therefore trusted to a very high level of assurance and the other, while still relatively safe, should be ore representative of typical behavior, not attepting to cover scenarios that are highly unlikely to occur. We illustrate via an exaple. Exaple 1. Suppose that we were able to deterine for a piece of code that Its work paraeter is > 120 with soe sall probability p, but > 900 with a far saller probability p p. Its span paraeter is > 40 with probability p; however the probability that it is > 600 is p. We could characterize this piece of code with two ordered pairs of work,span values a 1 p probability of being 120, 40, and a far greater 1 p probability of being 900, 600. We require that correctness criteria hold under the ore conservative estiate. Suppose for instance that it were specified that this code should execute within a relative deadline of D; we require that the akespan by D provided work 900 and span 600. The proposed run-tie scheduling approach. Since correctness is defined with respect to the ore conservative estiates for work and span, in order to satisfy correctness requireents we ust provision coputing resources to a task assuing these ore conservative estiates. However, it is our expectation that the task s run-tie behavior is very likely to be bounded by the less conservative paraeter estiates, and hence statically provisioning adequate resources for it under the ore conservative assuptions is likely to result in significant wastage of coputing resources during run-tie. One anner of aeliorating such wastage is by keeping soe of the provisioned resource in reserve, perhaps by placing soe processors in sleep ode or having the execute background non real-tie work, with the option of switching the to work upon executing the task if we deterine, during run-tie, that the task s run-tie behavior is in fact not likely to be bounded by the less conservative paraeter estiates. The following exaple illustrates.
7 K. Agrawal and S. Baruah 5:7 Exaple 2. Suppose the code in Exaple 1 to be scheduled with a relative deadline equal to 690, upon a 10-processor platfor. According to Expression 1, the akespan of the schedule upon 10 processors is no ore than = = 630 assuing the ore conservative work and span estiates hold. Hence, correctness is guaranteed. In fact, ten processors are not necessary for correctness: if we were executing this piece of code upon just four processors, the corresponding akespan bound according to Expression 1 would be = 675. Our run-tie algorith could therefore realize soe energy savings by siply switching off six of the ten provided processors, and executing the task on the reaining four. Could we switch off seven processors? The reader ay verify that with three processors Expression 1would yield a akespan bound of = 700. Since 700 exceeds the specified relative deadline of 690, we conclude that we ay iss the deadline if we were to switch off seven processors and the syste behaved worse than anticipated by its less conservative paraeters although not its ore conservative paraeters. We therefore conclude that we need at least 4 processors to not be in sleep ode, in order to ensure correctness. The run-tie algorith we will derive in this paper is designed for systes in which the less conservative paraeters are very likely to hold ost of the tie ; i.e., the value of p is itself very sall. Provided such is the case for this exaple our run-tie scheduling algorith starts out scheduling the syste on just three processors, leaving the reaining seven processors in sleep ode. If execution has not copleted by soe tie-instant whose value is precoputed, it wakes up the sleeping processors and akes all ten processors available for this task to execute upon. We will prove later that with this algorith, the task copletes by the specified deadline of 690 provided the ore conservative task paraeters hold; correctness is thus established. Additionally, there is a p probability that it will not coplete by the pre-coputed tie-instant and hence need to awaken the reaining seven processors. To evaluate the efficiency, suppose, for this exaple, that p = 0.05, indicating that the less conservative paraeters hold with 95% probability. There is therefore a 5% probability that the task will not coplete by the specified tie-instant, 6 and the expected nuber of processors that would be needed is no larger than = = 3.35 in contrast to the four that would be needed if our run-tie scheduling algorith were to not be used. Exaples 1 and 2 above have illustrated the task odel, and the associated run-tie strategy for scheduling tasks that are so odeled, that we are proposing in this paper. We now forally define the task odel in Section 2.1, and the run-tie scheduler in Section 2.2, below. 6 In fact, since the work and span paraeters will not in general be perfectly correlated, the expected probability of this happening is likely to be far less than 5%. This issue is revisited in Section 5. E C R T S
8 5:8 A Measureent-Based Model for Parallel Real-Tie Tasks 2.1 Syste Model We now provide a foral definition of our odel, by describing in detail the workload odel we assue. The workload we seek to odel coprises a single piece of parallelizable real-tie code that is characterized by the following list of paraeters: work O, span O, work, span, D, with the following interpretation: 1. work O, span O. These represent very conservative estiates of the true worst-case values of the work and span paraeters; as discussed above, we expect that these estiates will be obtained using the kinds of easureent-based techniques that have been developed for estiating probabilistic worst-case execution tie pwcet distributions. 2. D denotes the relative deadline paraeter: for correct execution it is required that the job be scheduled with akespan no greater than D. We highlight here that tiing correctness is specified assuing that the work O, span O paraeter estiates are correct: the code is required to coplete execution within the specified relative deadline D provided its work and span paraeters are no larger than work O and span O respectively. 3. work, span. These are less conservative estiates on the values of the work and span paraeters: it is expected that the actual values of the work and span paraeters are very likely to be no larger than work and span respectively. The subscript in work and span stand for noinal [23]. These paraeter estiates play no role in defining correctness; rather as we have seen in Exaples 1 and 2, their values ay be used for the purposes of devising ore resourceefficient scheduling strategies. It is hence not as critical that their values be assigned correctly as it is for the work O and span O paraeters: while incorrectly estiated values for work O and span O ay coproise tiing correctness in the sense that we ay end up issing deadlines, incorrectly estiated values for work and span siply result in less efficient ipleentations. We assue that work work O and span span O. Although our results are readily extended to situations where these assuptions do not hold, we do not see a rationale for relaxing these assuptions, since by very definition the work, span paraeters represent less conservative estiates than the work O, span O paraeters. In this paper, we consider the scheduling of a single such task upon a dedicated bank of identical processors. We point out that our results are directly applicable to the scheduling of recurrent periodic or sporadic real-tie DAGs under the federated paradig [24] of ultiprocessor scheduling, provided each periodic/ sporadic task satisfies the additional constraint that its relative deadline paraeter is no larger than its period paraeter i.e., they are constrained-deadline tasks. We believe our approach is particularly appropriate for scheduling systes of recurrent tasks: for such tasks, we anticipate that the work, span paraeters will bound the behavior of ost invocations dag-jobs [3] of the task, with an occasional rare dag-job exceeding these bounds. Hence any of the allocated processors will reain in sleep ode ost of the tie, with the occasional dag-job requiring that the sleeping processors be awakened until that dag-job copletes execution, after which they can be returned to sleep ode.
9 K. Agrawal and S. Baruah 5:9 2.2 The Scheduling Algorith Given a task as specified above: work O, span O, work, span, D, that is to be executed upon a platfor coprising identical processors, we first perfor soe pre-run-tie schedulability analysis that deterines whether we are able to schedule the task upon the processors in a anner that ensures correctness. Recall that correctness is specified as requiring that the task eet its deadline provided its work paraeter is work O and its span paraeter is span O : by Expression 1, this is guaranteed provided worko span O + span O D; 2 If Condition 2 does not hold, our scheduling algorith declares failure: it is unable to schedule this instance in a anner that guarantees tiing correctness. Otherwise, it coputes a pair of values and S the anner in which these values are coputed will be derived in Section 4.2. These coputed paraeters have the following intended interpretation: provided the less conservative work and span paraeter estiates are correct i.e., work is work and span is span for the task, list scheduling can schedule the task upon processors to have a akespan no greater then S. Run-tie scheduling. Suppose that the piece of parallelizable real-tie code represented by this task is activated at soe tie-instant t o during run-tie. 1. The scheduler sets a tier to go off at tie-instant t o + S, and begins executing the task upon processors using the list-scheduling algorith [17]. The reaining processors assigned to this task are placed/ reain in sleep ode. 2. If the task has not copleted execution by tie-instant t o + S, then the scheduler awakens the sleeping processors, and uses list-scheduling to execute the reainder of the task upon the entire bank of processors. 3. As entioned in Section 2.1 above, in the case of recurrent tasks these awakened processors are returned to sleep ode upon copletion of execution of the current dag-job of the task. In Section 4 we will derive the anner in which the values of and S are to be coputed in order to guarantee correctness: the algorith copletes execution of the task within D tie units of its arrival, provided its work paraeter is work O and its span paraeter is span O. We close this section with an exaple illustrating the operation of our run-tie scheduler. Exaple 3. Consider once again the instance discussed in Exaples 1 and 2. In the notation of Section 2, this task is represented by the following paraeters: work O, span O, work, span, D = 900, 600, 120, 40, 690. It is to be scheduled upon = 10 processors. In Exaple 4 we will show that the algorith of Section 4 assigns the paraeter the value 3, and the paraeter S, a value Hence our run-tie scheduler starts out scheduling this task on 3 processors. If the task E C R T S
10 5:10 A Measureent-Based Model for Parallel Real-Tie Tasks behaves as specified by its work, span paraeters, then by Expression 1 the akespan is no ore than = = and hence the additional seven processors are not needed. If it does not coplete by tieinstant , all ten processors becoe available for this task to execute upon, and results in Section 4 allow us to conclude that the task does execute correctly, copleting by the specified deadline at tie-instant Related Work The approach to the odeling and run-tie scheduling of parallelizable tasks that we are proposing here draws inspiration fro research in the areas of parallel coputing, ixedcriticality scheduling, and probabilistic WCET. As stated in Section 2 above, the proble of scheduling DAGs to iniize akespan the P prec S ax proble in 3-field notation [15] has been very widely studied in traditional scheduling theory. Given the inherent intractability of this proble [16] and the existence of a good approxiation as represented by List Scheduling [17] with its associated akespan bound Inequality 1, the parallel coputing counity soon began to focus upon the work and span paraeters as reasonable proxies for parallelizable coputational workloads; this is one of the fundaental ideas that underpins our proposed approach. The concept of specifying ultiple values, which are considered trustworthy to different levels of assurance, to a task s paraeters was proposed by Vestal [10] and fors the basis of ixed-criticality scheduling theory. There is a large body of research exploring the Vestal odel see [14] for a survey. In studying the scheduling of ixed-criticality parallel tasks, Li et al. [23] first proposed a odel in which each task is characterized by different work and span paraeters at low and high criticality levels it is this odel that we are studying in depth here. The overall context of the research in [23] is quite different fro ours: while we are, in the terinology of [23], considering the scheduling of a single parallelizable real-tie task with the objective of iniizing the nuber of processors used in the noinal case while concurrently guaranteeing to eet deadlines in the overloaded case, [23] was concerned with devising ixed-criticality scheduling algoriths with good capacity augentation bounds. Our approach also draws upon ideas fro the considerable body of prior research e.g., [20, 21, 22] on easureent-based techniques for estiating probabilistic worstcase execution tie distributions pwcet. The correctness of our scheduling fraework very strongly depends upon the validity and accuracy of pwcet-estiation techniques, since we are in effect guaranteeing correct tiing behavior eeting deadlines under the assuption that the ore conservative estiations work O and span O are correct upper bounds. In contrast, incorrect estiations of work and span do not coproise correctness, although they could have an adverse ipact on efficiency. Rather than being considered as estiations of worst-case paraeter values, these paraeters are perhaps closer in spirit to what Chishol et al [25] have called provisioned paraeter values and Li et al. [23], noinal paraeter values values that represent typical or coon-case behavior and ay be obtained by, e.g., soewhat inflating average-case paraeter values.
11 K. Agrawal and S. Baruah 5:11 D S tie 0 S D Figure 1 The parallel task begins execution at tie-instant 0 with a deadline at tie-instant D. It executes upon processors over the interval [0, S, and upon processors over the interval [S, D. The x-axis thus denotes tie, and the y-axis, the processors. 4 Scheduling Algorith Derivation and Analysis Given a task characterized, as described in Section 2.1, by the paraeters work O, span O, work, span, D and processors upon which to execute it, we discuss in this section how we should copute values of and S in order to ensure that the run-tie scheduling algorith described in Section 2.2 above copletes execution of the task within D tie units of its arrival. We will start out in Section 4.1 assuing that values for and S are already known, and derive sufficient conditions for ensuring tiing correctness given these values of and S. We will then describe, in Sections 4.2, how values ay be assigned to and S in a anner that ensures that these sufficient conditions are satisfied. 4.1 Sufficient Schedulability Conditions Suppose that we are given values of and S with 0 < and 0 S D, and the run-tie algorith schedules the task on processors using list scheduling. If the task copletes execution within S tie units, correctness is preserved since S D. It reains to deterine sufficient conditions for correctness when the task does not coplete by tie-instant S ; this we do in the reainder of this section. Figure 1 depicts the processors that are available for this task if it does not coplete execution within S tie units, thereby resulting in the run-tie scheduler awakening the processors that had been in sleep ode over [0, S. We will now derive conditions for ensuring that the task copletes execution by its deadline at tie-instant D when executing upon these available processors, given that its work paraeter ay be as large as work O and its span paraeter, span O. Let work and span denote the work and span paraeters of the aount of coputation of the parallel task that reains at tie-instant S these are > 0, since the task is assued to not have copleted execution by tie-instant S. This reaining coputation executes upon processors; By Expression 1 the overall akespan is therefore bounded fro above by work span S + + span 3 E C R T S
12 5:12 A Measureent-Based Model for Parallel Real-Tie Tasks Since the reaining span at tie-instant S is span, an aount span O span of the critical path of the task has executed during [0, S ]. At each instant when the critical path is not executing, it ust be the case that all processors are busy executing tasks not on the critical path. Hence the total aount of execution occurring over [0, S is at least S span O span + span O span, fro which it follows that work work O S + span O span span O span = work O S + span O span 1 = work O S + span O 1 span 1 4 Substituting Inequality 4 into the Expression 3, we obtain the following upper bound on the overall akespan: worko S + span S + O 1 span 1 span + span worko S + span = S + O 1 span + span worko S + span = S + O 1 span + span worko S + span = S + O 1 + span 1 5 Since, Expression 5 is axiized when span is large as possible; i.e., span = span O the physical interpretation is that the worst case occurs when no job on the critical path is executed prior to tie-instant S : instead the entire critical path executes after S. Substituting span span O into Expression 5, we get the following upper bound on the overall akespan: worko S + span S + O 1 + span O 1 = S + work O S span O + span O Correctness is guaranteed by having this upper bound on the akespan be D: S + work O S span O + span O D S S D work O span O span O S 1 D work O span O span O Expression 6 above is thus the sufficient schedulability condition we seek: values of and S satisfying Expression 6 guarantee tiing correctness Coputing and S We saw in Section 4.1 above that in order to ensure correctness, our scheduling algorith should choose the paraeters and S such that Condition 6 above is satisfied. Recall that an additional goal is efficiency: the saller the value of, the better, since the reaining processors can be placed in sleep ode. In this section we describe how our algorith coputes such a value.
13 K. Agrawal and S. Baruah 5:13 One reasonable approach for assigning a value to the paraeter is by using the task s noinal work and span paraeters work and span. Assuing that these paraeters bound the work and span values of a typical invocation of the task, it is guaranteed by Inequality 1 that upon processors a typical invocation will have a akespan no greater than work span / + span. We ay hence assign S a value as follows: work span S + span 7 Substituting this value for S into Expression 6, we get work span + span 1 D work O span O span O 8 as a sufficient schedulability condition. Since every ter other than is a constant in this expression, the expression can be algebraically siplified to a for that is a quadratic expression in ; solving this quadratic expression, and taking the ceiling since the nuber of processors ust be integral yields the desired value. Once is so coputed, the value of S ay be obtained fro Expression 7. We illustrate via an exaple; the algorith for coputing and S is provided in pseudo-code for after the exaple. Exaple 4. Consider once again the instance discussed in Exaples 1 and 2: work O, span O, work, span, D to be scheduled upon = 10 processors. Substituting these values into Expression 8, we get work span + span fro which we obtain = 900, 600, 120, 40, 690 D work O span O span O Since the nuber of processors ust be integral, we conclude that 3. The corresponding value for S is equal to work span span = = = E C R T S
14 5:14 A Measureent-Based Model for Parallel Real-Tie Tasks Algorith 1: Coputing values for, S. worko Input:, span O, work, span, D, Output: failure, or values for, S 1 begin 2 if < work O span O /D span O then 3 return failure /* The test of Inequality 1 cannot guarantee that the deadline will be et on processors */ 4 end 5 A span 6 B D span O + span work O span O + work span 7 C 1 work span 8 1 B + B 2 4 A C/2 A 9 S span + work span / 10 return, S 11 end Pseudo-code representation. of the for It ay be verified that Expression 8 can be rewritten to be A 2 + B + C 0 with A, B, and C assigned the following values: A span B D span O + span work O span O + work span C 1 work span The pseudo-code in Algorith listing 1 finds the positive root of this quadratic inequality; the ceiling of which denotes the nuber of processors needed this coputation occurs in Line 8. In Line 9 the value coputed for is used to deterine the value to be assigned to S. Run-tie coplexity. Algorith 1 coprises straight-line code with no loops or recursive calls. Hence given as input the paraeters specifying a task, it is evident that Algorith 1 has constant Θ1 run-tie. 5 Achieving Greater Efficiency: A More Aggressive Approach In an attept to achieve efficiency reducing the nuber of processors used in the coon case while aintaining correctness guaranteeing to eet deadlines provided task behavior does not exceed the worst-case bounds of work O and span O, the approach derived in Section 4.2 above uses the noinal paraeter values work and span to assign values to and S. In this section, we propose a ore aggressive approach to achieving perhaps greater efficiency without coproising correctness in any anner. This ore aggressive approach is based upon exploiting insights regardingi the probabilistic characterization of the run-tie behavior of the syste; and ii the typical behavior of List Scheduling.
15 K. Agrawal and S. Baruah 5:15 The probabilistic characterization of run-tie behavior. As discussed in Section 2 and illustrated in Exaples 1 and 2, we ay have a probability associated with the likelihood that the work and span paraeter values are correct. We ay, for exaple be able to assert that there is a 0.05 probability that the actual work will exceed work, and a 0.05 probability that the actual span will exceed span. ow this threshold probability of 0.05 ay have been selected because we desire that the probability that the sleeping processors will need to be awakened be If so, the ethod for coputing S and described in Section 4.2 above ay be overly conservative since the work and span distributions ay not be perfectly correlated if they are not, the probability that both the work would exceed work and the span exceed span, during a particular execution of the task is saller than In the extree if the two distributions are ore or less independent, the probability is closer to which equals.0025, a value that is is far saller than the sought-for threshold probability of Soe observations on List Scheduling. Assuing that the actual work and span paraeters of the coputation do not exceed work and span respectively, in Section 4.2 we used Expression 1 to assign values to and S in a anner guaranteeing that the coputation will coplete execution within an interval of duration S upon processors. ote that Expression 1 is an upper bound on the akespan of a List Scheduling generated schedule of a DAG; this upper bound is tight only for DAGs possessing a very specific structural for and/ or List Scheduling aking a particular sequence of scheduling decisions and then only if each node of the DAG executes for its entire WCET. Siulation experients using randoly-generated graphs see to indicate that these structures and scheduling decisions are relatively rare; for randoly-generated graphs, the akespans of actual list-scheduling generated schedules tend to cluster closer towards the lower end of the interval between the upper bound of Expression 1 and the obvious lower bound of work ax, span, 9 even if each node of the DAG does actually execute for its entire WCET. To illustrate this, we randoly generated 1000-node DAGs with varying nubers of edges in the anner described in Section 5.1 below; for each, we coputed the lower bound of Expression 9, the actual akespan using a list scheduling ipleentation, and the upper bound of Expression 1, for scheduling the DAG upon a 10-processor platfor. The results are listed in Table 1. The right-ost colun the one titled Ratio denotes the fraction of the interval between the lower bound and the upper bound upon which the actual akespan encroaches. More aggressive coputation of and S. We highlight the fact that being too optiistic in assigning values to S and does not coproise correctness: the sole effect is upon efficiency in ters of the nuber of processors we are able to aintain in sleep ode, and the likelihood that these processors will need to be switched on during soe run of the syste. Hence one possible ore aggressive approach towards achieving greater resource efficiency during run-tie would be to assign S a value between the lower and upper bounds of Expressions 9 and 1 as follows rather than according to Expression 7: work [ work span S ax, span +α work ] +span ax, span with α, 0 α 1 a tuning paraeter: the saller the value of α, the ore aggressive the choice of S. An intuitive interpretation of the tradeoff here is that the saller the 10 E C R T S
16 5:16 A Measureent-Based Model for Parallel Real-Tie Tasks Table 1 Actual akespan, and lower and upper bounds, of randoly-generated DAGs upon a 10-processor platfor. Each graph has 1000 vertices; each row corresponds to 1000-vertex DAGs with the nuber of edges specified in the first colun. The last colun denotes the ratio actual akespan - lower bound upper bound - lower bound sall values denote that the actual akespan is close to the lower bound. The experients used to generate this table are detailed in Section 5.1. M A K E S P A # edges Lower Exp. 9 Actual Upper Exp. 1 Ratio value of α, the greater the nuber of processors we can switch off, but the greater the likelihood that they will need to be awakened during soe execution of the task. For the randoly-generated DAGs of Table 1, a value of α would have been safe: during run-tie the sleeping processors are not awakened as long as the task s run-tie behavior does not violate its noinal paraeters work and span. If S is assigned a value according to Expression 10 rather than Expression 7, it is no longer the case that solving Expression 8 yields the desired value of. We have not attepted to derive a closed-for solution for when Expression 10 is used in place of Expression 7; rather, we iterate through candidate values for over the range [1,, stopping at the first such value for which this value for, and the resulting value for S coputed according to Expression 10, causes Condition 6 to evaluate to true. This ore aggressive approach to coputing and S therefore has run-tie coplexity Θ where denotes the nuber of processors available; a straightforward application of the idea of binary search reduces this to Θlog. 5.1 The Experients Reported in Table 1 We now briefly describe the experiental procedure used to generate the data populating Table 1. Graphs were synthesized using a DAG-generating variant of the well-known Erdös- Rényi ethod [26] for generating rando graphs. The Erdös-Rényi ethod, given paraeters n, p, yields a graph on n vertices in which each edge has an independent probability p of existence. We odified this ethod to generated directed acyclic graphs with a target nuber of edges. Specifically, The nuber of vertices in the DAG, n, the axiu WCET paraeter for a vertex w, and the desired nuber of edges e, are specified. The nuber of processors upon which the DAG is to be scheduled is also specified. Each vertex is assigned a WCET paraeter that is a randoly and uniforly drawn integer over the range 1, w.
17 K. Agrawal and S. Baruah 5:17 The paraeter p, denoting the probability of existence of each edge, is coputed as follows: p 2e n n 1. The idea is that since a DAG with n vertices has a axiu of n/ n 1/2 edges, if we were to create each such edge independently with probability p, on average the desired nuber e of edges would be created. All edges are assued to be directed fro the lower-indexed vertex to the higher-indexed vertex hence a topological sorting of the DAG could yield the vertices in order of increasing index. Each such edge is created with probability p, as follows: for i := 1 to n for j := i+1 to n create edge i,j with probability p The work and span paraeter of the generated DAG are coputed, assuing that each vertex executes for exactly its WCET paraeter value i.e., WCET paraeters are taken to represent the actual execution duration, rather than an upper bound on the execution duration. Using these values, a lower bound on akespan as given by Expression 9, and an upper bound as given by Expression 1, for the DAG upon the specified nuber of processors are coputed. A schedule of the DAG upon processors using a standard ipleentation of list scheduling is generated once again assuing that each vertex executes for exactly its WCET paraeter value. The akespan of the resulting schedule is recorded. Each data-point reported in Table 1 was obtained by generating one hundred such graphs, coputing the reported paraeters upon each, and taking their averages. 6 Suary and Conclusions Although DAG-based odels for representing parallelizable real-tie code have proved very popular in the real-tie scheduling theory counity, they suffer fro several shortcoings that restrict their usefulness in representing soe kinds of real-tie code. In this paper, we have explored an alternative odel, one that is based upon characterizing a task by just two paraeters work and span with two estiates on upper bounds on the value of each paraeter one that ay be very large but is trust-worthy to a very high level of assurance, and a second that is saller and is ore reflective of typical or noinal behavior. We have developed an algorith for scheduling tasks that are so odeled upon a dedicated cluster of processors in a anner guaranteeing correctness deadlines are always et provided run-tie behavior does not violate the high-assurance bounds while striving for efficiency any processors can reain in sleep ode uch of the tie, only being switched on in rare circustances when run-tie behavior exceeds the noral bounds. The odel for representing parallelizable code that is being proposed in this paper, and the associated run-tie scheduling algorith, is particularly suitable for a certain kind of real-tie application: one that repeatedly i.e., periodically or sporadically onitors the external environent seeking to detect soe particular kind of anoalous sensory input. Most of the tie the sought-for input is not detected, and not uch coputation needs to be perfored. But on the rare occasions when the anoalous input is detected, considerable additional processing of such input is necessary; furtherore, such processing is highly parallel in nature. Exaple applications of this kind include real-tie intrusion detection, E C R T S
Scheduling Parallel Real-Time Recurrent Tasks on Multicore Platforms
 IEEE TRANSACTIONS ON PARALLEL AND DISTRIBUTED SYSTEMS, VOL., NO., NOV 27 Scheduling Parallel Real-Tie Recurrent Tasks on Multicore Platfors Risat Pathan, Petros Voudouris, and Per Stenströ Abstract We
IEEE TRANSACTIONS ON PARALLEL AND DISTRIBUTED SYSTEMS, VOL., NO., NOV 27 Scheduling Parallel Real-Tie Recurrent Tasks on Multicore Platfors Risat Pathan, Petros Voudouris, and Per Stenströ Abstract We
Energy-Efficient Disk Replacement and File Placement Techniques for Mobile Systems with Hard Disks
 Energy-Efficient Disk Replaceent and File Placeent Techniques for Mobile Systes with Hard Disks Young-Jin Ki School of Coputer Science & Engineering Seoul National University Seoul 151-742, KOREA youngjk@davinci.snu.ac.kr
Energy-Efficient Disk Replaceent and File Placeent Techniques for Mobile Systes with Hard Disks Young-Jin Ki School of Coputer Science & Engineering Seoul National University Seoul 151-742, KOREA youngjk@davinci.snu.ac.kr
Clustering. Cluster Analysis of Microarray Data. Microarray Data for Clustering. Data for Clustering
 Clustering Cluster Analysis of Microarray Data 4/3/009 Copyright 009 Dan Nettleton Group obects that are siilar to one another together in a cluster. Separate obects that are dissiilar fro each other into
Clustering Cluster Analysis of Microarray Data 4/3/009 Copyright 009 Dan Nettleton Group obects that are siilar to one another together in a cluster. Separate obects that are dissiilar fro each other into
Fair Energy-Efficient Sensing Task Allocation in Participatory Sensing with Smartphones
 Advance Access publication on 24 February 2017 The British Coputer Society 2017. All rights reserved. For Perissions, please eail: journals.perissions@oup.co doi:10.1093/cojnl/bxx015 Fair Energy-Efficient
Advance Access publication on 24 February 2017 The British Coputer Society 2017. All rights reserved. For Perissions, please eail: journals.perissions@oup.co doi:10.1093/cojnl/bxx015 Fair Energy-Efficient
Identifying Converging Pairs of Nodes on a Budget
 Identifying Converging Pairs of Nodes on a Budget Konstantina Lazaridou Departent of Inforatics Aristotle University, Thessaloniki, Greece konlaznik@csd.auth.gr Evaggelia Pitoura Coputer Science and Engineering
Identifying Converging Pairs of Nodes on a Budget Konstantina Lazaridou Departent of Inforatics Aristotle University, Thessaloniki, Greece konlaznik@csd.auth.gr Evaggelia Pitoura Coputer Science and Engineering
Utility-Based Resource Allocation for Mixed Traffic in Wireless Networks
 IEEE IFOCO 2 International Workshop on Future edia etworks and IP-based TV Utility-Based Resource Allocation for ixed Traffic in Wireless etworks Li Chen, Bin Wang, Xiaohang Chen, Xin Zhang, and Dacheng
IEEE IFOCO 2 International Workshop on Future edia etworks and IP-based TV Utility-Based Resource Allocation for ixed Traffic in Wireless etworks Li Chen, Bin Wang, Xiaohang Chen, Xin Zhang, and Dacheng
Survivability Function A Measure of Disaster-Based Routing Performance
 Survivability Function A Measure of Disaster-Based Routing Perforance Journal Club Presentation on W. Molisz. Survivability function-a easure of disaster-based routing perforance. IEEE Journal on Selected
Survivability Function A Measure of Disaster-Based Routing Perforance Journal Club Presentation on W. Molisz. Survivability function-a easure of disaster-based routing perforance. IEEE Journal on Selected
Analysing Real-Time Communications: Controller Area Network (CAN) *
 Analysing Real-Tie Counications: Controller Area Network (CAN) * Abstract The increasing use of counication networks in tie critical applications presents engineers with fundaental probles with the deterination
Analysing Real-Tie Counications: Controller Area Network (CAN) * Abstract The increasing use of counication networks in tie critical applications presents engineers with fundaental probles with the deterination
OPTIMAL COMPLEX SERVICES COMPOSITION IN SOA SYSTEMS
 Key words SOA, optial, coplex service, coposition, Quality of Service Piotr RYGIELSKI*, Paweł ŚWIĄTEK* OPTIMAL COMPLEX SERVICES COMPOSITION IN SOA SYSTEMS One of the ost iportant tasks in service oriented
Key words SOA, optial, coplex service, coposition, Quality of Service Piotr RYGIELSKI*, Paweł ŚWIĄTEK* OPTIMAL COMPLEX SERVICES COMPOSITION IN SOA SYSTEMS One of the ost iportant tasks in service oriented
Investigation of The Time-Offset-Based QoS Support with Optical Burst Switching in WDM Networks
 Investigation of The Tie-Offset-Based QoS Support with Optical Burst Switching in WDM Networks Pingyi Fan, Chongxi Feng,Yichao Wang, Ning Ge State Key Laboratory on Microwave and Digital Counications,
Investigation of The Tie-Offset-Based QoS Support with Optical Burst Switching in WDM Networks Pingyi Fan, Chongxi Feng,Yichao Wang, Ning Ge State Key Laboratory on Microwave and Digital Counications,
Oblivious Routing for Fat-Tree Based System Area Networks with Uncertain Traffic Demands
 Oblivious Routing for Fat-Tree Based Syste Area Networks with Uncertain Traffic Deands Xin Yuan Wickus Nienaber Zhenhai Duan Departent of Coputer Science Florida State University Tallahassee, FL 3306 {xyuan,nienaber,duan}@cs.fsu.edu
Oblivious Routing for Fat-Tree Based Syste Area Networks with Uncertain Traffic Deands Xin Yuan Wickus Nienaber Zhenhai Duan Departent of Coputer Science Florida State University Tallahassee, FL 3306 {xyuan,nienaber,duan}@cs.fsu.edu
Mapping Data in Peer-to-Peer Systems: Semantics and Algorithmic Issues
 Mapping Data in Peer-to-Peer Systes: Seantics and Algorithic Issues Anastasios Keentsietsidis Marcelo Arenas Renée J. Miller Departent of Coputer Science University of Toronto {tasos,arenas,iller}@cs.toronto.edu
Mapping Data in Peer-to-Peer Systes: Seantics and Algorithic Issues Anastasios Keentsietsidis Marcelo Arenas Renée J. Miller Departent of Coputer Science University of Toronto {tasos,arenas,iller}@cs.toronto.edu
Collaborative Web Caching Based on Proxy Affinities
 Collaborative Web Caching Based on Proxy Affinities Jiong Yang T J Watson Research Center IBM jiyang@usibco Wei Wang T J Watson Research Center IBM ww1@usibco Richard Muntz Coputer Science Departent UCLA
Collaborative Web Caching Based on Proxy Affinities Jiong Yang T J Watson Research Center IBM jiyang@usibco Wei Wang T J Watson Research Center IBM ww1@usibco Richard Muntz Coputer Science Departent UCLA
Solving the Damage Localization Problem in Structural Health Monitoring Using Techniques in Pattern Classification
 Solving the Daage Localization Proble in Structural Health Monitoring Using Techniques in Pattern Classification CS 9 Final Project Due Dec. 4, 007 Hae Young Noh, Allen Cheung, Daxia Ge Introduction Structural
Solving the Daage Localization Proble in Structural Health Monitoring Using Techniques in Pattern Classification CS 9 Final Project Due Dec. 4, 007 Hae Young Noh, Allen Cheung, Daxia Ge Introduction Structural
Fair Resource Allocation for Heterogeneous Tasks
 Fair Resource Allocation for Heterogeneous Tasks Koyel Mukherjee, Partha utta, Gurulingesh Raravi, Thangaraj Balasubraania, Koustuv asgupta, Atul Singh Xerox Research Center India, Bangalore, India 560105
Fair Resource Allocation for Heterogeneous Tasks Koyel Mukherjee, Partha utta, Gurulingesh Raravi, Thangaraj Balasubraania, Koustuv asgupta, Atul Singh Xerox Research Center India, Bangalore, India 560105
Design and Implementation of Business Logic Layer Object-Oriented Design versus Relational Design
 Design and Ipleentation of Business Logic Layer Object-Oriented Design versus Relational Design Ali Alharthy Faculty of Engineering and IT University of Technology, Sydney Sydney, Australia Eail: Ali.a.alharthy@student.uts.edu.au
Design and Ipleentation of Business Logic Layer Object-Oriented Design versus Relational Design Ali Alharthy Faculty of Engineering and IT University of Technology, Sydney Sydney, Australia Eail: Ali.a.alharthy@student.uts.edu.au
Scheduling Parallel Task Graphs on (Almost) Homogeneous Multi-cluster Platforms
 1 Scheduling Parallel Task Graphs on (Alost) Hoogeneous Multi-cluster Platfors Pierre-François Dutot, Tchiou N Takpé, Frédéric Suter and Henri Casanova Abstract Applications structured as parallel task
1 Scheduling Parallel Task Graphs on (Alost) Hoogeneous Multi-cluster Platfors Pierre-François Dutot, Tchiou N Takpé, Frédéric Suter and Henri Casanova Abstract Applications structured as parallel task
Performance Analysis of RAID in Different Workload
 Send Orders for Reprints to reprints@benthascience.ae 324 The Open Cybernetics & Systeics Journal, 2015, 9, 324-328 Perforance Analysis of RAID in Different Workload Open Access Zhang Dule *, Ji Xiaoyun,
Send Orders for Reprints to reprints@benthascience.ae 324 The Open Cybernetics & Systeics Journal, 2015, 9, 324-328 Perforance Analysis of RAID in Different Workload Open Access Zhang Dule *, Ji Xiaoyun,
Theoretical Analysis of Local Search and Simple Evolutionary Algorithms for the Generalized Travelling Salesperson Problem
 Theoretical Analysis of Local Search and Siple Evolutionary Algoriths for the Generalized Travelling Salesperson Proble Mojgan Pourhassan ojgan.pourhassan@adelaide.edu.au Optiisation and Logistics, The
Theoretical Analysis of Local Search and Siple Evolutionary Algoriths for the Generalized Travelling Salesperson Proble Mojgan Pourhassan ojgan.pourhassan@adelaide.edu.au Optiisation and Logistics, The
Compiling an Honest but Curious Protocol
 6.876/18.46: Advanced Cryptography May 7, 003 Lecture 1: Copiling an Honest but Curious Protocol Scribed by: Jonathan Derryberry 1 Review In previous lectures, the notion of secure ultiparty coputing was
6.876/18.46: Advanced Cryptography May 7, 003 Lecture 1: Copiling an Honest but Curious Protocol Scribed by: Jonathan Derryberry 1 Review In previous lectures, the notion of secure ultiparty coputing was
Computer Aided Drafting, Design and Manufacturing Volume 26, Number 2, June 2016, Page 13
 Coputer Aided Drafting, Design and Manufacturing Volue 26, uber 2, June 2016, Page 13 CADDM 3D reconstruction of coplex curved objects fro line drawings Sun Yanling, Dong Lijun Institute of Mechanical
Coputer Aided Drafting, Design and Manufacturing Volue 26, uber 2, June 2016, Page 13 CADDM 3D reconstruction of coplex curved objects fro line drawings Sun Yanling, Dong Lijun Institute of Mechanical
Geo-activity Recommendations by using Improved Feature Combination
 Geo-activity Recoendations by using Iproved Feature Cobination Masoud Sattari Middle East Technical University Ankara, Turkey e76326@ceng.etu.edu.tr Murat Manguoglu Middle East Technical University Ankara,
Geo-activity Recoendations by using Iproved Feature Cobination Masoud Sattari Middle East Technical University Ankara, Turkey e76326@ceng.etu.edu.tr Murat Manguoglu Middle East Technical University Ankara,
A Trajectory Splitting Model for Efficient Spatio-Temporal Indexing
 A Trajectory Splitting Model for Efficient Spatio-Teporal Indexing Slobodan Rasetic Jörg Sander Jaes Elding Mario A. Nasciento Departent of Coputing Science University of Alberta Edonton, Alberta, Canada
A Trajectory Splitting Model for Efficient Spatio-Teporal Indexing Slobodan Rasetic Jörg Sander Jaes Elding Mario A. Nasciento Departent of Coputing Science University of Alberta Edonton, Alberta, Canada
λ-harmonious Graph Colouring Lauren DeDieu
 λ-haronious Graph Colouring Lauren DeDieu June 12, 2012 ABSTRACT In 198, Hopcroft and Krishnaoorthy defined a new type of graph colouring called haronious colouring. Haronious colouring is a proper vertex
λ-haronious Graph Colouring Lauren DeDieu June 12, 2012 ABSTRACT In 198, Hopcroft and Krishnaoorthy defined a new type of graph colouring called haronious colouring. Haronious colouring is a proper vertex
Detection of Outliers and Reduction of their Undesirable Effects for Improving the Accuracy of K-means Clustering Algorithm
 Detection of Outliers and Reduction of their Undesirable Effects for Iproving the Accuracy of K-eans Clustering Algorith Bahan Askari Departent of Coputer Science and Research Branch, Islaic Azad University,
Detection of Outliers and Reduction of their Undesirable Effects for Iproving the Accuracy of K-eans Clustering Algorith Bahan Askari Departent of Coputer Science and Research Branch, Islaic Azad University,
Modeling Parallel Applications Performance on Heterogeneous Systems
 Modeling Parallel Applications Perforance on Heterogeneous Systes Jaeela Al-Jaroodi, Nader Mohaed, Hong Jiang and David Swanson Departent of Coputer Science and Engineering University of Nebraska Lincoln
Modeling Parallel Applications Perforance on Heterogeneous Systes Jaeela Al-Jaroodi, Nader Mohaed, Hong Jiang and David Swanson Departent of Coputer Science and Engineering University of Nebraska Lincoln
Enhancing Real-Time CAN Communications by the Prioritization of Urgent Messages at the Outgoing Queue
 Enhancing Real-Tie CAN Counications by the Prioritization of Urgent Messages at the Outgoing Queue ANTÓNIO J. PIRES (1), JOÃO P. SOUSA (), FRANCISCO VASQUES (3) 1,,3 Faculdade de Engenharia da Universidade
Enhancing Real-Tie CAN Counications by the Prioritization of Urgent Messages at the Outgoing Queue ANTÓNIO J. PIRES (1), JOÃO P. SOUSA (), FRANCISCO VASQUES (3) 1,,3 Faculdade de Engenharia da Universidade
Defining and Surveying Wireless Link Virtualization and Wireless Network Virtualization
 1 Defining and Surveying Wireless Link Virtualization and Wireless Network Virtualization Jonathan van de Belt, Haed Ahadi, and Linda E. Doyle The Centre for Future Networks and Counications - CONNECT,
1 Defining and Surveying Wireless Link Virtualization and Wireless Network Virtualization Jonathan van de Belt, Haed Ahadi, and Linda E. Doyle The Centre for Future Networks and Counications - CONNECT,
Real-Time Detection of Invisible Spreaders
 Real-Tie Detection of Invisible Spreaders MyungKeun Yoon Shigang Chen Departent of Coputer & Inforation Science & Engineering University of Florida, Gainesville, FL 3, USA {yoon, sgchen}@cise.ufl.edu Abstract
Real-Tie Detection of Invisible Spreaders MyungKeun Yoon Shigang Chen Departent of Coputer & Inforation Science & Engineering University of Florida, Gainesville, FL 3, USA {yoon, sgchen}@cise.ufl.edu Abstract
I ve Seen Enough : Incrementally Improving Visualizations to Support Rapid Decision Making
 I ve Seen Enough : Increentally Iproving Visualizations to Support Rapid Decision Making Sajjadur Rahan Marya Aliakbarpour 2 Ha Kyung Kong Eric Blais 3 Karrie Karahalios,4 Aditya Paraeswaran Ronitt Rubinfield
I ve Seen Enough : Increentally Iproving Visualizations to Support Rapid Decision Making Sajjadur Rahan Marya Aliakbarpour 2 Ha Kyung Kong Eric Blais 3 Karrie Karahalios,4 Aditya Paraeswaran Ronitt Rubinfield
TensorFlow and Keras-based Convolutional Neural Network in CAT Image Recognition Ang LI 1,*, Yi-xiang LI 2 and Xue-hui LI 3
 2017 2nd International Conference on Coputational Modeling, Siulation and Applied Matheatics (CMSAM 2017) ISBN: 978-1-60595-499-8 TensorFlow and Keras-based Convolutional Neural Network in CAT Iage Recognition
2017 2nd International Conference on Coputational Modeling, Siulation and Applied Matheatics (CMSAM 2017) ISBN: 978-1-60595-499-8 TensorFlow and Keras-based Convolutional Neural Network in CAT Iage Recognition
The Boundary Between Privacy and Utility in Data Publishing
 The Boundary Between Privacy and Utility in Data Publishing Vibhor Rastogi Dan Suciu Sungho Hong ABSTRACT We consider the privacy proble in data publishing: given a database instance containing sensitive
The Boundary Between Privacy and Utility in Data Publishing Vibhor Rastogi Dan Suciu Sungho Hong ABSTRACT We consider the privacy proble in data publishing: given a database instance containing sensitive
Evaluation of a multi-frame blind deconvolution algorithm using Cramér-Rao bounds
 Evaluation of a ulti-frae blind deconvolution algorith using Craér-Rao bounds Charles C. Beckner, Jr. Air Force Research Laboratory, 3550 Aberdeen Ave SE, Kirtland AFB, New Mexico, USA 87117-5776 Charles
Evaluation of a ulti-frae blind deconvolution algorith using Craér-Rao bounds Charles C. Beckner, Jr. Air Force Research Laboratory, 3550 Aberdeen Ave SE, Kirtland AFB, New Mexico, USA 87117-5776 Charles
Geometry. The Method of the Center of Mass (mass points): Solving problems using the Law of Lever (mass points). Menelaus theorem. Pappus theorem.
 Noveber 13, 2016 Geoetry. The Method of the enter of Mass (ass points): Solving probles using the Law of Lever (ass points). Menelaus theore. Pappus theore. M d Theore (Law of Lever). Masses (weights)
Noveber 13, 2016 Geoetry. The Method of the enter of Mass (ass points): Solving probles using the Law of Lever (ass points). Menelaus theore. Pappus theore. M d Theore (Law of Lever). Masses (weights)
Brian Noguchi CS 229 (Fall 05) Project Final Writeup A Hierarchical Application of ICA-based Feature Extraction to Image Classification Brian Noguchi
 A Hierarchical Application of ICA-based Feature Etraction to Iage Classification Introduction Iage classification poses one of the greatest challenges in the achine vision and achine learning counities.
A Hierarchical Application of ICA-based Feature Etraction to Iage Classification Introduction Iage classification poses one of the greatest challenges in the achine vision and achine learning counities.
A Hybrid Network Architecture for File Transfers
 JOURNAL OF IEEE TRANSACTIONS ON PARALLEL AND DISTRIBUTED SYSTEMS, VOL. 6, NO., JANUARY 9 A Hybrid Network Architecture for File Transfers Xiuduan Fang, Meber, IEEE, Malathi Veeraraghavan, Senior Meber,
JOURNAL OF IEEE TRANSACTIONS ON PARALLEL AND DISTRIBUTED SYSTEMS, VOL. 6, NO., JANUARY 9 A Hybrid Network Architecture for File Transfers Xiuduan Fang, Meber, IEEE, Malathi Veeraraghavan, Senior Meber,
Structural Balance in Networks. An Optimizational Approach. Andrej Mrvar. Faculty of Social Sciences. University of Ljubljana. Kardeljeva pl.
 Structural Balance in Networks An Optiizational Approach Andrej Mrvar Faculty of Social Sciences University of Ljubljana Kardeljeva pl. 5 61109 Ljubljana March 23 1994 Contents 1 Balanced and clusterable
Structural Balance in Networks An Optiizational Approach Andrej Mrvar Faculty of Social Sciences University of Ljubljana Kardeljeva pl. 5 61109 Ljubljana March 23 1994 Contents 1 Balanced and clusterable
Planet Scale Software Updates
 Planet Scale Software Updates Christos Gkantsidis 1, Thoas Karagiannis 2, Pablo Rodriguez 1, and Milan Vojnović 1 1 Microsoft Research 2 UC Riverside Cabridge, UK Riverside, CA, USA {chrisgk,pablo,ilanv}@icrosoft.co
Planet Scale Software Updates Christos Gkantsidis 1, Thoas Karagiannis 2, Pablo Rodriguez 1, and Milan Vojnović 1 1 Microsoft Research 2 UC Riverside Cabridge, UK Riverside, CA, USA {chrisgk,pablo,ilanv}@icrosoft.co
The optimization design of microphone array layout for wideband noise sources
 PROCEEDINGS of the 22 nd International Congress on Acoustics Acoustic Array Systes: Paper ICA2016-903 The optiization design of icrophone array layout for wideband noise sources Pengxiao Teng (a), Jun
PROCEEDINGS of the 22 nd International Congress on Acoustics Acoustic Array Systes: Paper ICA2016-903 The optiization design of icrophone array layout for wideband noise sources Pengxiao Teng (a), Jun
An Efficient Approach for Content Delivery in Overlay Networks
 An Efficient Approach for Content Delivery in Overlay Networks Mohaad Malli, Chadi Barakat, Walid Dabbous Projet Planète, INRIA-Sophia Antipolis, France E-ail:{alli, cbarakat, dabbous}@sophia.inria.fr
An Efficient Approach for Content Delivery in Overlay Networks Mohaad Malli, Chadi Barakat, Walid Dabbous Projet Planète, INRIA-Sophia Antipolis, France E-ail:{alli, cbarakat, dabbous}@sophia.inria.fr
Leveraging Relevance Cues for Improved Spoken Document Retrieval
 Leveraging Relevance Cues for Iproved Spoken Docuent Retrieval Pei-Ning Chen 1, Kuan-Yu Chen 2 and Berlin Chen 1 National Taiwan Noral University, Taiwan 1 Institute of Inforation Science, Acadeia Sinica,
Leveraging Relevance Cues for Iproved Spoken Docuent Retrieval Pei-Ning Chen 1, Kuan-Yu Chen 2 and Berlin Chen 1 National Taiwan Noral University, Taiwan 1 Institute of Inforation Science, Acadeia Sinica,
Smarter Balanced Assessment Consortium Claims, Targets, and Standard Alignment for Math
 Sarter Balanced Assessent Consortiu s, s, Stard Alignent for Math The Sarter Balanced Assessent Consortiu (SBAC) has created a hierarchy coprised of clais targets that together can be used to ake stateents
Sarter Balanced Assessent Consortiu s, s, Stard Alignent for Math The Sarter Balanced Assessent Consortiu (SBAC) has created a hierarchy coprised of clais targets that together can be used to ake stateents
NON-RIGID OBJECT TRACKING: A PREDICTIVE VECTORIAL MODEL APPROACH
 NON-RIGID OBJECT TRACKING: A PREDICTIVE VECTORIAL MODEL APPROACH V. Atienza; J.M. Valiente and G. Andreu Departaento de Ingeniería de Sisteas, Coputadores y Autoática Universidad Politécnica de Valencia.
NON-RIGID OBJECT TRACKING: A PREDICTIVE VECTORIAL MODEL APPROACH V. Atienza; J.M. Valiente and G. Andreu Departaento de Ingeniería de Sisteas, Coputadores y Autoática Universidad Politécnica de Valencia.
Designing High Performance Web-Based Computing Services to Promote Telemedicine Database Management System
 Designing High Perforance Web-Based Coputing Services to Proote Teleedicine Database Manageent Syste Isail Hababeh 1, Issa Khalil 2, and Abdallah Khreishah 3 1: Coputer Engineering & Inforation Technology,
Designing High Perforance Web-Based Coputing Services to Proote Teleedicine Database Manageent Syste Isail Hababeh 1, Issa Khalil 2, and Abdallah Khreishah 3 1: Coputer Engineering & Inforation Technology,
Response-Time Analysis of Synchronous Parallel Tasks in Multiprocessor Systems Claudio Maia* Marko Bertogna Luis Miguel Nogueira* Luis Miguel Pinho*
 Technical Report Response-Tie Analysis of Synchronous Parallel Tasks in Multiprocessor Systes Claudio Maia* Marko Bertogna Luis Miguel Nogueira* Luis Miguel Pinho* *CISTER Research Center CISTER-TR-141001
Technical Report Response-Tie Analysis of Synchronous Parallel Tasks in Multiprocessor Systes Claudio Maia* Marko Bertogna Luis Miguel Nogueira* Luis Miguel Pinho* *CISTER Research Center CISTER-TR-141001
THE rapid growth and continuous change of the real
 IEEE TRANSACTIONS ON SERVICES COMPUTING, VOL. 8, NO. 1, JANUARY/FEBRUARY 2015 47 Designing High Perforance Web-Based Coputing Services to Proote Teleedicine Database Manageent Syste Isail Hababeh, Issa
IEEE TRANSACTIONS ON SERVICES COMPUTING, VOL. 8, NO. 1, JANUARY/FEBRUARY 2015 47 Designing High Perforance Web-Based Coputing Services to Proote Teleedicine Database Manageent Syste Isail Hababeh, Issa
A Comparative Study of Two-phase Heuristic Approaches to General Job Shop Scheduling Problem
 IE Vol. 7, No. 2, pp. 84-92, Septeber 2008. A Coparative Study of Two-phase Heuristic Approaches to General Job Shop Scheduling Proble Ji Ung Sun School of Industrial and Managent Engineering Hankuk University
IE Vol. 7, No. 2, pp. 84-92, Septeber 2008. A Coparative Study of Two-phase Heuristic Approaches to General Job Shop Scheduling Proble Ji Ung Sun School of Industrial and Managent Engineering Hankuk University
A Novel Fast Constructive Algorithm for Neural Classifier
 A Novel Fast Constructive Algorith for Neural Classifier Xudong Jiang Centre for Signal Processing, School of Electrical and Electronic Engineering Nanyang Technological University Nanyang Avenue, Singapore
A Novel Fast Constructive Algorith for Neural Classifier Xudong Jiang Centre for Signal Processing, School of Electrical and Electronic Engineering Nanyang Technological University Nanyang Avenue, Singapore
Design Optimization of Mixed Time/Event-Triggered Distributed Embedded Systems
 Design Optiization of Mixed Tie/Event-Triggered Distributed Ebedded Systes Traian Pop, Petru Eles, Zebo Peng Dept. of Coputer and Inforation Science, Linköping University {trapo, petel, zebpe}@ida.liu.se
Design Optiization of Mixed Tie/Event-Triggered Distributed Ebedded Systes Traian Pop, Petru Eles, Zebo Peng Dept. of Coputer and Inforation Science, Linköping University {trapo, petel, zebpe}@ida.liu.se
EE 364B Convex Optimization An ADMM Solution to the Sparse Coding Problem. Sonia Bhaskar, Will Zou Final Project Spring 2011
 EE 364B Convex Optiization An ADMM Solution to the Sparse Coding Proble Sonia Bhaskar, Will Zou Final Project Spring 20 I. INTRODUCTION For our project, we apply the ethod of the alternating direction
EE 364B Convex Optiization An ADMM Solution to the Sparse Coding Proble Sonia Bhaskar, Will Zou Final Project Spring 20 I. INTRODUCTION For our project, we apply the ethod of the alternating direction
Adaptive Holistic Scheduling for In-Network Sensor Query Processing
 Adaptive Holistic Scheduling for In-Network Sensor Query Processing Hejun Wu and Qiong Luo Departent of Coputer Science and Engineering Hong Kong University of Science & Technology Clear Water Bay, Kowloon,
Adaptive Holistic Scheduling for In-Network Sensor Query Processing Hejun Wu and Qiong Luo Departent of Coputer Science and Engineering Hong Kong University of Science & Technology Clear Water Bay, Kowloon,
IN many interactive multimedia streaming applications, such
 840 IEEE TRANSACTIONS ON MULTIMEDIA, VOL. 8, NO. 5, MAY 06 A Geoetric Approach to Server Selection for Interactive Video Streaing Yaochen Hu, Student Meber, IEEE, DiNiu, Meber, IEEE, and Zongpeng Li, Senior
840 IEEE TRANSACTIONS ON MULTIMEDIA, VOL. 8, NO. 5, MAY 06 A Geoetric Approach to Server Selection for Interactive Video Streaing Yaochen Hu, Student Meber, IEEE, DiNiu, Meber, IEEE, and Zongpeng Li, Senior
1 Extended Boolean Model
 1 EXTENDED BOOLEAN MODEL It has been well-known that the Boolean odel is too inflexible, requiring skilful use of Boolean operators to obtain good results. On the other hand, the vector space odel is flexible
1 EXTENDED BOOLEAN MODEL It has been well-known that the Boolean odel is too inflexible, requiring skilful use of Boolean operators to obtain good results. On the other hand, the vector space odel is flexible
Efficient Learning of Generalized Linear and Single Index Models with Isotonic Regression
 Efficient Learning of Generalized Linear and Single Index Models with Isotonic Regression Sha M. Kakade Microsoft Research and Wharton, U Penn skakade@icrosoft.co Varun Kanade SEAS, Harvard University
Efficient Learning of Generalized Linear and Single Index Models with Isotonic Regression Sha M. Kakade Microsoft Research and Wharton, U Penn skakade@icrosoft.co Varun Kanade SEAS, Harvard University
MAPPING THE DATA FLOW MODEL OF COMPUTATION INTO AN ENHANCED VON NEUMANN PROCESSOR * Peter M. Maurer
 MAPPING THE DATA FLOW MODEL OF COMPUTATION INTO AN ENHANCED VON NEUMANN PROCESSOR * Peter M. Maurer Departent of Coputer Science and Engineering University of South Florida Tapa, FL 33620 Abstract -- The
MAPPING THE DATA FLOW MODEL OF COMPUTATION INTO AN ENHANCED VON NEUMANN PROCESSOR * Peter M. Maurer Departent of Coputer Science and Engineering University of South Florida Tapa, FL 33620 Abstract -- The
Efficient Estimation of Inclusion Coefficient using HyperLogLog Sketches
 Efficient Estiation of Inclusion Coefficient using HyperLogLog Sketches Azade Nazi, Bolin Ding, Vivek Narasayya, Surajit Chaudhuri Microsoft Research {aznazi, bolind, viveknar, surajitc}@icrosoft.co ABSTRACT
Efficient Estiation of Inclusion Coefficient using HyperLogLog Sketches Azade Nazi, Bolin Ding, Vivek Narasayya, Surajit Chaudhuri Microsoft Research {aznazi, bolind, viveknar, surajitc}@icrosoft.co ABSTRACT
Secure Wireless Multihop Transmissions by Intentional Collisions with Noise Wireless Signals
 Int'l Conf. Wireless etworks ICW'16 51 Secure Wireless Multihop Transissions by Intentional Collisions with oise Wireless Signals Isau Shiada 1 and Hiroaki Higaki 1 1 Tokyo Denki University, Japan Abstract
Int'l Conf. Wireless etworks ICW'16 51 Secure Wireless Multihop Transissions by Intentional Collisions with oise Wireless Signals Isau Shiada 1 and Hiroaki Higaki 1 1 Tokyo Denki University, Japan Abstract
BP-MAC: A High Reliable Backoff Preamble MAC Protocol for Wireless Sensor Networks
 BP-MAC: A High Reliable Backoff Preable MAC Protocol for Wireless Sensor Networks Alexander Klein* Jirka Klaue Josef Schalk EADS Innovation Works, Gerany *Eail: klein@inforatik.uni-wuerzburg.de ABSTRACT:
BP-MAC: A High Reliable Backoff Preable MAC Protocol for Wireless Sensor Networks Alexander Klein* Jirka Klaue Josef Schalk EADS Innovation Works, Gerany *Eail: klein@inforatik.uni-wuerzburg.de ABSTRACT:
Optimal Route Queries with Arbitrary Order Constraints
 IEEE TRANSACTIONS ON KNOWLEDGE AND DATA ENGINEERING, VOL.?, NO.?,? 20?? 1 Optial Route Queries with Arbitrary Order Constraints Jing Li, Yin Yang, Nikos Maoulis Abstract Given a set of spatial points DS,
IEEE TRANSACTIONS ON KNOWLEDGE AND DATA ENGINEERING, VOL.?, NO.?,? 20?? 1 Optial Route Queries with Arbitrary Order Constraints Jing Li, Yin Yang, Nikos Maoulis Abstract Given a set of spatial points DS,
Data Caching for Enhancing Anonymity
 Data Caching for Enhancing Anonyity Rajiv Bagai and Bin Tang Departent of Electrical Engineering and Coputer Science Wichita State University Wichita, Kansas 67260 0083, USA Eail: {rajiv.bagai, bin.tang}@wichita.edu
Data Caching for Enhancing Anonyity Rajiv Bagai and Bin Tang Departent of Electrical Engineering and Coputer Science Wichita State University Wichita, Kansas 67260 0083, USA Eail: {rajiv.bagai, bin.tang}@wichita.edu
Predicting x86 Program Runtime for Intel Processor
 Predicting x86 Progra Runtie for Intel Processor Behra Mistree, Haidreza Haki Javadi, Oid Mashayekhi Stanford University bistree,hrhaki,oid@stanford.edu 1 Introduction Progras can be equivalent: given
Predicting x86 Progra Runtie for Intel Processor Behra Mistree, Haidreza Haki Javadi, Oid Mashayekhi Stanford University bistree,hrhaki,oid@stanford.edu 1 Introduction Progras can be equivalent: given
ACNS: Adaptive Complementary Neighbor Selection in BitTorrent-like Applications
 ACNS: Adaptive Copleentary Neighbor Selection in BitTorrent-like Applications Zhenbao Zhou 1, 2, Zhenyu Li 1, 2, Gaogang Xie 1 1 Institute of Coputing Technology, Chinese Acadey of Sciences, Beijing 100190,
ACNS: Adaptive Copleentary Neighbor Selection in BitTorrent-like Applications Zhenbao Zhou 1, 2, Zhenyu Li 1, 2, Gaogang Xie 1 1 Institute of Coputing Technology, Chinese Acadey of Sciences, Beijing 100190,
Joint Measurement- and Traffic Descriptor-based Admission Control at Real-Time Traffic Aggregation Points
 Joint Measureent- and Traffic Descriptor-based Adission Control at Real-Tie Traffic Aggregation Points Stylianos Georgoulas, Panos Triintzios and George Pavlou Centre for Counication Systes Research, University
Joint Measureent- and Traffic Descriptor-based Adission Control at Real-Tie Traffic Aggregation Points Stylianos Georgoulas, Panos Triintzios and George Pavlou Centre for Counication Systes Research, University
Improve Peer Cooperation using Social Networks
 Iprove Peer Cooperation using Social Networks Victor Ponce, Jie Wu, and Xiuqi Li Departent of Coputer Science and Engineering Florida Atlantic University Boca Raton, FL 33431 Noveber 5, 2007 Corresponding
Iprove Peer Cooperation using Social Networks Victor Ponce, Jie Wu, and Xiuqi Li Departent of Coputer Science and Engineering Florida Atlantic University Boca Raton, FL 33431 Noveber 5, 2007 Corresponding
Image Filter Using with Gaussian Curvature and Total Variation Model
 IJECT Vo l. 7, Is s u e 3, Ju l y - Se p t 016 ISSN : 30-7109 (Online) ISSN : 30-9543 (Print) Iage Using with Gaussian Curvature and Total Variation Model 1 Deepak Kuar Gour, Sanjay Kuar Shara 1, Dept.
IJECT Vo l. 7, Is s u e 3, Ju l y - Se p t 016 ISSN : 30-7109 (Online) ISSN : 30-9543 (Print) Iage Using with Gaussian Curvature and Total Variation Model 1 Deepak Kuar Gour, Sanjay Kuar Shara 1, Dept.
A Low-Cost Multi-Failure Resilient Replication Scheme for High Data Availability in Cloud Storage
 216 IEEE 23rd International Conference on High Perforance Coputing A Low-Cost Multi-Failure Resilient Replication Schee for High Data Availability in Cloud Storage Jinwei Liu* and Haiying Shen *Departent
216 IEEE 23rd International Conference on High Perforance Coputing A Low-Cost Multi-Failure Resilient Replication Schee for High Data Availability in Cloud Storage Jinwei Liu* and Haiying Shen *Departent
Ascending order sort Descending order sort
 Scalable Binary Sorting Architecture Based on Rank Ordering With Linear Area-Tie Coplexity. Hatrnaz and Y. Leblebici Departent of Electrical and Coputer Engineering Worcester Polytechnic Institute Abstract
Scalable Binary Sorting Architecture Based on Rank Ordering With Linear Area-Tie Coplexity. Hatrnaz and Y. Leblebici Departent of Electrical and Coputer Engineering Worcester Polytechnic Institute Abstract
A CRYPTANALYTIC ATTACK ON RC4 STREAM CIPHER
 A CRYPTANALYTIC ATTACK ON RC4 STREAM CIPHER VIOLETA TOMAŠEVIĆ, SLOBODAN BOJANIĆ 2 and OCTAVIO NIETO-TALADRIZ 2 The Mihajlo Pupin Institute, Volgina 5, 000 Belgrade, SERBIA AND MONTENEGRO 2 Technical University
A CRYPTANALYTIC ATTACK ON RC4 STREAM CIPHER VIOLETA TOMAŠEVIĆ, SLOBODAN BOJANIĆ 2 and OCTAVIO NIETO-TALADRIZ 2 The Mihajlo Pupin Institute, Volgina 5, 000 Belgrade, SERBIA AND MONTENEGRO 2 Technical University
A Fast Multi-Objective Genetic Algorithm for Hardware-Software Partitioning In Embedded System Design
 A Fast Multi-Obective Genetic Algorith for Hardware-Software Partitioning In Ebedded Syste Design 1 M.Jagadeeswari, 2 M.C.Bhuvaneswari 1 Research Scholar, P.S.G College of Technology, Coibatore, India
A Fast Multi-Obective Genetic Algorith for Hardware-Software Partitioning In Ebedded Syste Design 1 M.Jagadeeswari, 2 M.C.Bhuvaneswari 1 Research Scholar, P.S.G College of Technology, Coibatore, India
On the Computation and Application of Prototype Point Patterns
 On the Coputation and Application of Prototype Point Patterns Katherine E. Tranbarger Freier 1 and Frederic Paik Schoenberg 2 Abstract This work addresses coputational probles related to the ipleentation
On the Coputation and Application of Prototype Point Patterns Katherine E. Tranbarger Freier 1 and Frederic Paik Schoenberg 2 Abstract This work addresses coputational probles related to the ipleentation
I-0 Introduction. I-1 Introduction. Objectives: Quote:
 I-0 Introduction Objectives: Explain necessity of parallel/ultithreaded algoriths Describe different fors of parallel processing Present coonly used architectures Introduce a few basic ters Coents: Try
I-0 Introduction Objectives: Explain necessity of parallel/ultithreaded algoriths Describe different fors of parallel processing Present coonly used architectures Introduce a few basic ters Coents: Try
Multipath Selection and Channel Assignment in Wireless Mesh Networks
 Multipath Selection and Channel Assignent in Wireless Mesh Networs Soo-young Jang and Chae Y. Lee Dept. of Industrial and Systes Engineering, KAIST, 373-1 Kusung-dong, Taejon, Korea Tel: +82-42-350-5916,
Multipath Selection and Channel Assignent in Wireless Mesh Networs Soo-young Jang and Chae Y. Lee Dept. of Industrial and Systes Engineering, KAIST, 373-1 Kusung-dong, Taejon, Korea Tel: +82-42-350-5916,
Relocation of Gateway for Enhanced Timeliness in Wireless Sensor Networks Abstract 1. Introduction
 Relocation of ateway for Enhanced Tieliness in Wireless Sensor Networks Keal Akkaya and Mohaed Younis Departent of oputer Science and Electrical Engineering University of Maryland, altiore ounty altiore,
Relocation of ateway for Enhanced Tieliness in Wireless Sensor Networks Keal Akkaya and Mohaed Younis Departent of oputer Science and Electrical Engineering University of Maryland, altiore ounty altiore,
Integrating fast mobility in the OLSR routing protocol
 Integrating fast obility in the OLSR routing protocol Mounir BENZAID 1,2, Pascale MINET 1 and Khaldoun AL AGHA 1,2 1 INRIA, Doaine de Voluceau - B.P.105, 78153 Le Chesnay Cedex, FRANCE ounir.benzaid, pascale.inet@inria.fr
Integrating fast obility in the OLSR routing protocol Mounir BENZAID 1,2, Pascale MINET 1 and Khaldoun AL AGHA 1,2 1 INRIA, Doaine de Voluceau - B.P.105, 78153 Le Chesnay Cedex, FRANCE ounir.benzaid, pascale.inet@inria.fr
A New Generic Model for Vision Based Tracking in Robotics Systems
 A New Generic Model for Vision Based Tracking in Robotics Systes Yanfei Liu, Ada Hoover, Ian Walker, Ben Judy, Mathew Joseph and Charly Heranson lectrical and Coputer ngineering Departent Cleson University
A New Generic Model for Vision Based Tracking in Robotics Systes Yanfei Liu, Ada Hoover, Ian Walker, Ben Judy, Mathew Joseph and Charly Heranson lectrical and Coputer ngineering Departent Cleson University
A Learning Framework for Nearest Neighbor Search
 A Learning Fraework for Nearest Neighbor Search Lawrence Cayton Departent of Coputer Science University of California, San Diego lcayton@cs.ucsd.edu Sanjoy Dasgupta Departent of Coputer Science University
A Learning Fraework for Nearest Neighbor Search Lawrence Cayton Departent of Coputer Science University of California, San Diego lcayton@cs.ucsd.edu Sanjoy Dasgupta Departent of Coputer Science University
A Novel 2D Texture Classifier For Gray Level Images
 2012, TextRoad Publication ISSN 2090-4304 Journal of Basic and Applied Scientific Research www.textroad.co A Novel 2D Texture Classifier For Gray Level Iages B.S. Mousavi 1 Young Researchers Club, Zahedan
2012, TextRoad Publication ISSN 2090-4304 Journal of Basic and Applied Scientific Research www.textroad.co A Novel 2D Texture Classifier For Gray Level Iages B.S. Mousavi 1 Young Researchers Club, Zahedan
Boosted Detection of Objects and Attributes
 L M M Boosted Detection of Objects and Attributes Abstract We present a new fraework for detection of object and attributes in iages based on boosted cobination of priitive classifiers. The fraework directly
L M M Boosted Detection of Objects and Attributes Abstract We present a new fraework for detection of object and attributes in iages based on boosted cobination of priitive classifiers. The fraework directly
Privacy-preserving String-Matching With PRAM Algorithms
 Privacy-preserving String-Matching With PRAM Algoriths Report in MTAT.07.022 Research Seinar in Cryptography, Fall 2014 Author: Sander Sii Supervisor: Peeter Laud Deceber 14, 2014 Abstract In this report,
Privacy-preserving String-Matching With PRAM Algoriths Report in MTAT.07.022 Research Seinar in Cryptography, Fall 2014 Author: Sander Sii Supervisor: Peeter Laud Deceber 14, 2014 Abstract In this report,
HKBU Institutional Repository
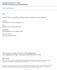 Hong Kong Baptist University HKBU Institutional Repository HKBU Staff Publication 18 Towards why-not spatial keyword top-k ueries: A direction-aware approach Lei Chen Hong Kong Baptist University, psuanle@gail.co
Hong Kong Baptist University HKBU Institutional Repository HKBU Staff Publication 18 Towards why-not spatial keyword top-k ueries: A direction-aware approach Lei Chen Hong Kong Baptist University, psuanle@gail.co
Different criteria of dynamic routing
 Procedia Coputer Science Volue 66, 2015, Pages 166 173 YSC 2015. 4th International Young Scientists Conference on Coputational Science Different criteria of dynaic routing Kurochkin 1*, Grinberg 1 1 Kharkevich
Procedia Coputer Science Volue 66, 2015, Pages 166 173 YSC 2015. 4th International Young Scientists Conference on Coputational Science Different criteria of dynaic routing Kurochkin 1*, Grinberg 1 1 Kharkevich
Control Message Reduction Techniques in Backward Learning Ad Hoc Routing Protocols
 Control Message Reduction Techniques in Backward Learning Ad Hoc Routing Protocols Navodaya Garepalli Kartik Gopalan Ping Yang Coputer Science, Binghaton University (State University of New York) Contact:
Control Message Reduction Techniques in Backward Learning Ad Hoc Routing Protocols Navodaya Garepalli Kartik Gopalan Ping Yang Coputer Science, Binghaton University (State University of New York) Contact:
A Beam Search Method to Solve the Problem of Assignment Cells to Switches in a Cellular Mobile Network
 A Bea Search Method to Solve the Proble of Assignent Cells to Switches in a Cellular Mobile Networ Cassilda Maria Ribeiro Faculdade de Engenharia de Guaratinguetá - DMA UNESP - São Paulo State University
A Bea Search Method to Solve the Proble of Assignent Cells to Switches in a Cellular Mobile Networ Cassilda Maria Ribeiro Faculdade de Engenharia de Guaratinguetá - DMA UNESP - São Paulo State University
Adaptive Parameter Estimation Based Congestion Avoidance Strategy for DTN
 Proceedings of the nd International onference on oputer Science and Electronics Engineering (ISEE 3) Adaptive Paraeter Estiation Based ongestion Avoidance Strategy for DTN Qicai Yang, Futong Qin, Jianquan
Proceedings of the nd International onference on oputer Science and Electronics Engineering (ISEE 3) Adaptive Paraeter Estiation Based ongestion Avoidance Strategy for DTN Qicai Yang, Futong Qin, Jianquan
Evaluation of the Timing Properties of Two Control Networks: CAN and PROFIBUS
 Evaluation of the Tiing Properties of Two Control Networs: CAN and PROFIBUS Max Mauro Dias Santos 1, Marcelo Ricardo Steer 2 and Francisco Vasques 3 1 UnilesteMG, CEP 35170-056, Coronel Fabriciano MG Brasil.
Evaluation of the Tiing Properties of Two Control Networs: CAN and PROFIBUS Max Mauro Dias Santos 1, Marcelo Ricardo Steer 2 and Francisco Vasques 3 1 UnilesteMG, CEP 35170-056, Coronel Fabriciano MG Brasil.
The Internal Conflict of a Belief Function
 The Internal Conflict of a Belief Function Johan Schubert Abstract In this paper we define and derive an internal conflict of a belief function We decopose the belief function in question into a set of
The Internal Conflict of a Belief Function Johan Schubert Abstract In this paper we define and derive an internal conflict of a belief function We decopose the belief function in question into a set of
Multi Packet Reception and Network Coding
 The 2010 Military Counications Conference - Unclassified Progra - etworking Protocols and Perforance Track Multi Packet Reception and etwork Coding Aran Rezaee Research Laboratory of Electronics Massachusetts
The 2010 Military Counications Conference - Unclassified Progra - etworking Protocols and Perforance Track Multi Packet Reception and etwork Coding Aran Rezaee Research Laboratory of Electronics Massachusetts
Verifying the structure and behavior in UML/OCL models using satisfiability solvers
 IET Cyber-Physical Systes: Theory & Applications Review Article Verifying the structure and behavior in UML/OCL odels using satisfiability solvers ISSN 2398-3396 Received on 20th October 2016 Revised on
IET Cyber-Physical Systes: Theory & Applications Review Article Verifying the structure and behavior in UML/OCL odels using satisfiability solvers ISSN 2398-3396 Received on 20th October 2016 Revised on
Minimax Sensor Location to Monitor a Piecewise Linear Curve
 NSF GRANT #040040 NSF PROGRAM NAME: Operations Research Miniax Sensor Location to Monitor a Piecewise Linear Curve To M. Cavalier The Pennsylvania State University University Par, PA 680 Whitney A. Conner
NSF GRANT #040040 NSF PROGRAM NAME: Operations Research Miniax Sensor Location to Monitor a Piecewise Linear Curve To M. Cavalier The Pennsylvania State University University Par, PA 680 Whitney A. Conner
A Learning Framework for Nearest Neighbor Search
 A Learning Fraework for Nearest Neighbor Search Lawrence Cayton Departent of Coputer Science University of California, San Diego lcayton@cs.ucsd.edu Sanjoy Dasgupta Departent of Coputer Science University
A Learning Fraework for Nearest Neighbor Search Lawrence Cayton Departent of Coputer Science University of California, San Diego lcayton@cs.ucsd.edu Sanjoy Dasgupta Departent of Coputer Science University
Distributed Multicast Tree Construction in Wireless Sensor Networks
 Distributed Multicast Tree Construction in Wireless Sensor Networks Hongyu Gong, Luoyi Fu, Xinzhe Fu, Lutian Zhao 3, Kainan Wang, and Xinbing Wang Dept. of Electronic Engineering, Shanghai Jiao Tong University,
Distributed Multicast Tree Construction in Wireless Sensor Networks Hongyu Gong, Luoyi Fu, Xinzhe Fu, Lutian Zhao 3, Kainan Wang, and Xinbing Wang Dept. of Electronic Engineering, Shanghai Jiao Tong University,
The Hopcount to an Anycast Group
 The Hopcount to an Anycast Group Piet Van Mieghe Delft University of Technology Abstract The probability density function of the nuber of hops to the ost nearby eber of the anycast group consisting of
The Hopcount to an Anycast Group Piet Van Mieghe Delft University of Technology Abstract The probability density function of the nuber of hops to the ost nearby eber of the anycast group consisting of
Using Imperialist Competitive Algorithm in Optimization of Nonlinear Multiple Responses
 International Journal of Industrial Engineering & Production Research Septeber 03, Volue 4, Nuber 3 pp. 9-35 ISSN: 008-4889 http://ijiepr.iust.ac.ir/ Using Iperialist Copetitive Algorith in Optiization
International Journal of Industrial Engineering & Production Research Septeber 03, Volue 4, Nuber 3 pp. 9-35 ISSN: 008-4889 http://ijiepr.iust.ac.ir/ Using Iperialist Copetitive Algorith in Optiization
Carving Differential Unit Test Cases from System Test Cases
 Carving Differential Unit Test Cases fro Syste Test Cases Sebastian Elbau, Hui Nee Chin, Matthew B. Dwyer, Jonathan Dokulil Departent of Coputer Science and Engineering University of Nebraska - Lincoln
Carving Differential Unit Test Cases fro Syste Test Cases Sebastian Elbau, Hui Nee Chin, Matthew B. Dwyer, Jonathan Dokulil Departent of Coputer Science and Engineering University of Nebraska - Lincoln
MIDA: AN IDA SEARCH WITH DYNAMIC CONTROL
 April 1991 UILU-ENG-91-2216 CRHC-91-9 Center fo r Reliable and High-Perforance Coputing MIDA: AN IDA SEARCH WITH DYNAMIC CONTROL Benjain W. Wah Coordinated Science Laboratory College of Engineering UNIVERSITY
April 1991 UILU-ENG-91-2216 CRHC-91-9 Center fo r Reliable and High-Perforance Coputing MIDA: AN IDA SEARCH WITH DYNAMIC CONTROL Benjain W. Wah Coordinated Science Laboratory College of Engineering UNIVERSITY
A Broadband Spectrum Sensing Algorithm in TDCS Based on ICoSaMP Reconstruction
 MATEC Web of Conferences 73, 03073(08) https://doi.org/0.05/atecconf/087303073 SMIMA 08 A roadband Spectru Sensing Algorith in TDCS ased on I Reconstruction Liu Yang, Ren Qinghua, Xu ingzheng and Li Xiazhao
MATEC Web of Conferences 73, 03073(08) https://doi.org/0.05/atecconf/087303073 SMIMA 08 A roadband Spectru Sensing Algorith in TDCS ased on I Reconstruction Liu Yang, Ren Qinghua, Xu ingzheng and Li Xiazhao
RECONFIGURABLE AND MODULAR BASED SYNTHESIS OF CYCLIC DSP DATA FLOW GRAPHS
 RECONFIGURABLE AND MODULAR BASED SYNTHESIS OF CYCLIC DSP DATA FLOW GRAPHS AWNI ITRADAT Assistant Professor, Departent of Coputer Engineering, Faculty of Engineering, Hasheite University, P.O. Box 15459,
RECONFIGURABLE AND MODULAR BASED SYNTHESIS OF CYCLIC DSP DATA FLOW GRAPHS AWNI ITRADAT Assistant Professor, Departent of Coputer Engineering, Faculty of Engineering, Hasheite University, P.O. Box 15459,
Efficient Constraint Evaluation Algorithms for Hierarchical Next-Best-View Planning
 Efficient Constraint Evaluation Algoriths for Hierarchical Next-Best-View Planning Ko-Li Low National University of Singapore lowl@cop.nus.edu.sg Anselo Lastra University of North Carolina at Chapel Hill
Efficient Constraint Evaluation Algoriths for Hierarchical Next-Best-View Planning Ko-Li Low National University of Singapore lowl@cop.nus.edu.sg Anselo Lastra University of North Carolina at Chapel Hill
Shortest Path Determination in a Wireless Packet Switch Network System in University of Calabar Using a Modified Dijkstra s Algorithm
 International Journal of Engineering and Technical Research (IJETR) ISSN: 31-869 (O) 454-4698 (P), Volue-5, Issue-1, May 16 Shortest Path Deterination in a Wireless Packet Switch Network Syste in University
International Journal of Engineering and Technical Research (IJETR) ISSN: 31-869 (O) 454-4698 (P), Volue-5, Issue-1, May 16 Shortest Path Deterination in a Wireless Packet Switch Network Syste in University
An Ad Hoc Adaptive Hashing Technique for Non-Uniformly Distributed IP Address Lookup in Computer Networks
 An Ad Hoc Adaptive Hashing Technique for Non-Uniforly Distributed IP Address Lookup in Coputer Networks Christopher Martinez Departent of Electrical and Coputer Engineering The University of Texas at San
An Ad Hoc Adaptive Hashing Technique for Non-Uniforly Distributed IP Address Lookup in Coputer Networks Christopher Martinez Departent of Electrical and Coputer Engineering The University of Texas at San
