Software change. Software maintenance
|
|
|
- Eugene Day
- 6 years ago
- Views:
Transcription
1 Software change 1 Software change is inevitable New requirements emerge when the software is used The business environment changes Errors must be repaired New equipment must be accommodated The performance or reliability may have to be improved A key problem for organizations is implementing and managing change to their legacy systems DISCUSSION Project A change to your project A change to someone else s project Another team in your class Another team from 2000 Another team from 1990 Software maintenance 2 Modifying a program after it has been put into use Maintenance does not normally involve major changes to the system s architecture Changes are implemented by modifying existing components and adding new components to the system 1
2 Maintenance is inevitable 3 The system requirements are likely to change while the system is being developed because the environment is changing. Therefore a delivered system won't meet its requirements! Systems are tightly coupled with their environment. When a system is installed in an environment it changes that environment and therefore changes the system requirements. Systems MUST be maintained if they are to remain useful in an environment Types of maintenance 4 Maintenance to repair software faults Changing a system to correct deficiencies in the way it meets its requirements Maintenance to adapt software to a different operating environment Changing a system so that it operates in a different environment (computer, OS, etc.) from its initial implementation Maintenance to add to or modify the system s functionality Modifying the system to satisfy new requirements Which one is most common? 2
3 Distribution of maintenance effort 5 Fault repair (17%) Software adaptation (18%) Functionality addition or modification (65%) Maintenance costs 6 Usually greater than development costs (2* to 100* depending on the application) Affected by both technical and nontechnical factors Increases as software is maintained. Maintenance corrupts the software structure so makes future maintenance more difficult. Ageing software can have high support costs (e.g. old languages, compilers etc.) 3
4 Development/maintenance costs 7 System 1 System $ Development costs Maintenance costs Maintenance cost factors 8 Team stability Maintenance costs are reduced if the same staff is involved with them for some time Contractual responsibility The developers of a system may have no contractual responsibility for maintenance so there is no incentive to design for future change Staff skills Maintenance staff is often inexperienced and has limited domain knowledge Program age and structure As programs age, their structure is degraded and they become harder to understand and change 4
5 Change requests 9 Change requests are requests for system changes from users, customers or management In principle, all change requests should be carefully analyzed as part of the maintenance process and then implemented In practice, some change requests must be implemented urgently Fault repair Changes to the system s environment Urgently required business changes The maintenance process 10 Change requests Impact analysis System release planning Change implementation System release Perfective maintenance Adaptive maintenance Corrective maintenance 5
6 Maintenance prediction 11 Maintenance prediction is concerned with assessing what parts of the system may cause problems and have high maintenance costs Change acceptance depends on the maintainability of the components affected by the change Implementing changes degrades the system and reduces its maintainability Maintenance costs depend on the number of changes and costs of change depend on maintainability Maintenance prediction 12 What parts of the system are most likely to be affected by change requests? Predicting maintainability What parts of the system will be the most expensive to maintain? Predicting system changes Predicting maintenance costs What will be the lifetime maintenance costs of this system? How many change requests can be expected? What will be the costs of maintaining this system over the next year? 6
7 Change prediction 13 Predicting the number of changes requires understanding the relationships between a system and its environment Tightly coupled systems require changes whenever the environment is changed Factors influencing this relationship are Number and complexity of system interfaces The business processes where the system is used Evolutionary software 14 Rather than think of separate development and maintenance phases, evolutionary software is software that is designed so that it can continuously evolve throughout its lifetime 7
8 Configuration management 15 New versions of software systems are created as they change For different machines/os Offering different functionality Tailored for particular user requirements Configuration management is concerned with managing evolving software systems System change is a team activity CM aims to control the costs and effort involved in making changes to a system Configuration management 16 Involves the development and application of procedures and standards to manage an evolving software product May be seen as part of a more general quality management process 8
9 Configuration management planning 17 All products of the software process may have to be managed Specifications Designs Programs Test data User manuals Thousands of separate documents are generated for a large software system DISCUSSION CM planning 18 Starts during the early phases of the project Must define the documents or document classes that are to be managed Documents which might be required for future system maintenance should be identified and specified as managed documents 9
10 The CM plan 19 Defines the types of documents to be managed and a document naming scheme Defines who takes responsibility for the CM procedures Defines policies for change and version management Defines the CM records which must be maintained The CM plan 20 Describes the tools which should be used to assist the CM process and any limitations on their use Defines the process of tool use Defines the CM database used to record configuration information May include information such as the CM of external software, process auditing, etc. 10
11 The configuration database 21 All CM information should be maintained in a configuration database This should allow queries about configurations to be answered Who has a particular system version? What platform is required for a particular version? What versions are affected by a change to component X? How many reported faults in version T? The CM database should preferably be linked to the software being managed 11
Software Maintenance. Maintenance is Inevitable. Types of Maintenance. Managing the processes of system change
 Software Maintenance Managing the processes of system change Maintenance is Inevitable The system requirements are likely to change while the system is being developed because the environment is changing.
Software Maintenance Managing the processes of system change Maintenance is Inevitable The system requirements are likely to change while the system is being developed because the environment is changing.
Legacy Systems. Older software systems that remain vital to an organisation. Legacy systems. Legacy system replacement
 Legacy Systems Older software systems that remain vital to an organisation Ian Sommerville 1995/2000 (Modified by Spiros Mancoridis 1999) Software Engineering, 6th edition. Chapters 26,27,28 Slide 1 Legacy
Legacy Systems Older software systems that remain vital to an organisation Ian Sommerville 1995/2000 (Modified by Spiros Mancoridis 1999) Software Engineering, 6th edition. Chapters 26,27,28 Slide 1 Legacy
Documentation & Maintenance
 Documentation & Maintenance Princípy tvorby softvéru, FMFI UK Jana Kostičová, 16.5.2016 Documentation Why documentation? 1. Facilitates communication Within the development team itself Between the development
Documentation & Maintenance Princípy tvorby softvéru, FMFI UK Jana Kostičová, 16.5.2016 Documentation Why documentation? 1. Facilitates communication Within the development team itself Between the development
ICS 52: Introduction to Software Engineering
 ICS 52: Introduction to Software Engineering Fall Quarter 2002 Professor Richard N. Taylor Lecture Notes: CM, Management, and Evolution Many slides taken from Ian Sommerville s text http://www.ics.uci.edu/~taylor/ics_52_fq02/syllabus.html
ICS 52: Introduction to Software Engineering Fall Quarter 2002 Professor Richard N. Taylor Lecture Notes: CM, Management, and Evolution Many slides taken from Ian Sommerville s text http://www.ics.uci.edu/~taylor/ics_52_fq02/syllabus.html
ICS 52: Introduction to Software Engineering
 ICS 52: Introduction to Software Engineering Fall Quarter 2004 Professor Richard N. Taylor Lecture Notes: CM, Management, and Evolution Several Illustrations from Ian Sommerville s text http://www.ics.uci.edu/~taylor/ics_52_fq04/syllabus.html
ICS 52: Introduction to Software Engineering Fall Quarter 2004 Professor Richard N. Taylor Lecture Notes: CM, Management, and Evolution Several Illustrations from Ian Sommerville s text http://www.ics.uci.edu/~taylor/ics_52_fq04/syllabus.html
Configuration management. Adapted from Ian Sommerville 2006, Software Engineering, 8th edition. Chapter 29 1
 Configuration management Adapted from Ian Sommerville 2006, Software Engineering, 8th edition. Chapter 29 1 Objectives To explain the importance of software configuration management (CM) To describe key
Configuration management Adapted from Ian Sommerville 2006, Software Engineering, 8th edition. Chapter 29 1 Objectives To explain the importance of software configuration management (CM) To describe key
CSC 408F/CSC2105F Lecture Notes
 CSC 408F/CSC2105F Lecture Notes These lecture notes are provided for the personal use of students taking CSC 408H/CSC 2105H in the Fall term 2004/2005 at the University of Toronto. Copying for purposes
CSC 408F/CSC2105F Lecture Notes These lecture notes are provided for the personal use of students taking CSC 408H/CSC 2105H in the Fall term 2004/2005 at the University of Toronto. Copying for purposes
Introduction to Software Engineering
 Introduction to Software Engineering Gérald Monard Ecole GDR CORREL - April 16, 2013 www.monard.info Bibliography Software Engineering, 9th ed. (I. Sommerville, 2010, Pearson) Conduite de projets informatiques,
Introduction to Software Engineering Gérald Monard Ecole GDR CORREL - April 16, 2013 www.monard.info Bibliography Software Engineering, 9th ed. (I. Sommerville, 2010, Pearson) Conduite de projets informatiques,
Software Engineering I. Chapters 8 & 9. SW Testing & Maintenance. Slide 1. 12/17/2017 SW Testing and Maintenance
 Software Engineering I Chapters 8 & 9 SW Testing & Maintenance 12/17/2017 SW Testing and Maintenance Slide 1 Chapter 8 Software Testing 12/17/2017 SW Testing and Maintenance Slide 2 Program testing Testing
Software Engineering I Chapters 8 & 9 SW Testing & Maintenance 12/17/2017 SW Testing and Maintenance Slide 1 Chapter 8 Software Testing 12/17/2017 SW Testing and Maintenance Slide 2 Program testing Testing
2. Draw and explain state transition diagram for a typical weather information system. (8M)
 1. Explain, with a neat diagram, the distinct phases of Rational Unified Process (RUP). 1b. List and explain the different stages involved in the object oriented design process. 2. Draw and explain state
1. Explain, with a neat diagram, the distinct phases of Rational Unified Process (RUP). 1b. List and explain the different stages involved in the object oriented design process. 2. Draw and explain state
Losing Control: Controls, Risks, Governance, and Stewardship of Enterprise Data
 Losing Control: Controls, Risks, Governance, and Stewardship of Enterprise Data an eprentise white paper tel: 407.591.4950 toll-free: 1.888.943.5363 web: www.eprentise.com Author: Helene Abrams www.eprentise.com
Losing Control: Controls, Risks, Governance, and Stewardship of Enterprise Data an eprentise white paper tel: 407.591.4950 toll-free: 1.888.943.5363 web: www.eprentise.com Author: Helene Abrams www.eprentise.com
Software Prototyping Animating and demonstrating system requirements. Uses of System Prototypes. Prototyping Benefits
 Software Prototyping Animating and demonstrating requirements Ian Sommerville 1995/2000 (Modified by Spiros Mancoridis 1999) Software Engineering, 6th edition. Chapter 8 Slide 1 Uses of System Prototypes
Software Prototyping Animating and demonstrating requirements Ian Sommerville 1995/2000 (Modified by Spiros Mancoridis 1999) Software Engineering, 6th edition. Chapter 8 Slide 1 Uses of System Prototypes
SOFTWARE ENGINEERING DECEMBER. Q2a. What are the key challenges being faced by software engineering?
 Q2a. What are the key challenges being faced by software engineering? Ans 2a. The key challenges facing software engineering are: 1. Coping with legacy systems, coping with increasing diversity and coping
Q2a. What are the key challenges being faced by software engineering? Ans 2a. The key challenges facing software engineering are: 1. Coping with legacy systems, coping with increasing diversity and coping
Incremental development A.Y. 2018/2019
 Incremental development A.Y. 2018/2019 Incremental development Interleaves the activities of specification, development, and validation. The system is developed as a series of versions (increments), with
Incremental development A.Y. 2018/2019 Incremental development Interleaves the activities of specification, development, and validation. The system is developed as a series of versions (increments), with
Process of Interaction Design and Design Languages
 Process of Interaction Design and Design Languages Process of Interaction Design This week, we will explore how we can design and build interactive products What is different in interaction design compared
Process of Interaction Design and Design Languages Process of Interaction Design This week, we will explore how we can design and build interactive products What is different in interaction design compared
ORACLE SERVICES FOR APPLICATION MIGRATIONS TO ORACLE HARDWARE INFRASTRUCTURES
 ORACLE SERVICES FOR APPLICATION MIGRATIONS TO ORACLE HARDWARE INFRASTRUCTURES SERVICE, SUPPORT AND EXPERT GUIDANCE FOR THE MIGRATION AND IMPLEMENTATION OF YOUR ORACLE APPLICATIONS ON ORACLE INFRASTRUCTURE
ORACLE SERVICES FOR APPLICATION MIGRATIONS TO ORACLE HARDWARE INFRASTRUCTURES SERVICE, SUPPORT AND EXPERT GUIDANCE FOR THE MIGRATION AND IMPLEMENTATION OF YOUR ORACLE APPLICATIONS ON ORACLE INFRASTRUCTURE
Training & Documentation. Different Users. Types of training. Reading: Chapter 10. User training (what the system does)
 Training & Documentation Reading: Chapter 10 Different Users Types of training User training (what the system does) Operator training (how the system works) Special training needs: new users vs. brush-up
Training & Documentation Reading: Chapter 10 Different Users Types of training User training (what the system does) Operator training (how the system works) Special training needs: new users vs. brush-up
Introduction to Software Engineering
 Chapter 1 Introduction to Software Engineering Content 1. Introduction 2. Components 3. Layered Technologies 4. Generic View of Software Engineering 4. Generic View of Software Engineering 5. Study of
Chapter 1 Introduction to Software Engineering Content 1. Introduction 2. Components 3. Layered Technologies 4. Generic View of Software Engineering 4. Generic View of Software Engineering 5. Study of
Business Phone System Buyer s Guide
 Business Phone System Buyer s Guide Types of Systems Available There are three primary types of of Voice over Internet Protocol (VoIP) phone systems on the market today: KSU-Less, KSU and PBX. Generally,
Business Phone System Buyer s Guide Types of Systems Available There are three primary types of of Voice over Internet Protocol (VoIP) phone systems on the market today: KSU-Less, KSU and PBX. Generally,
Session 4112 BW NLS Data Archiving: Keeping BW in Tip-Top Shape for SAP HANA. Sandy Speizer, PSEG SAP Principal Architect
 Session 4112 BW NLS Data Archiving: Keeping BW in Tip-Top Shape for SAP HANA Sandy Speizer, PSEG SAP Principal Architect Public Service Enterprise Group PSEG SAP ECC (R/3) Core Implementation SAP BW Implementation
Session 4112 BW NLS Data Archiving: Keeping BW in Tip-Top Shape for SAP HANA Sandy Speizer, PSEG SAP Principal Architect Public Service Enterprise Group PSEG SAP ECC (R/3) Core Implementation SAP BW Implementation
Reducing the costs of rework. Coping with change. Software prototyping. Ways to Cope with change. Benefits of prototyping
 Coping with change Change is inevitable in all large software projects. Business changes lead to new and changed system requirements New technologies open up new possibilities for improving implementations
Coping with change Change is inevitable in all large software projects. Business changes lead to new and changed system requirements New technologies open up new possibilities for improving implementations
CS 390 Software Engineering Lecture 3 Configuration Management
 CS 390 Software Engineering Lecture 3 Configuration Management Includes slides from the companion website for Sommerville, Software Engineering, 10/e. Pearson Higher Education, 2016. All rights reserved.
CS 390 Software Engineering Lecture 3 Configuration Management Includes slides from the companion website for Sommerville, Software Engineering, 10/e. Pearson Higher Education, 2016. All rights reserved.
Four Essential Steps for Removing Risk and Downtime from Your POWER9 Migration
 Four Essential Steps for Removing Risk and Downtime from Your POWER9 Migration Syncsort Four Essential Steps for Removing Risk and Downtime from Your POWER9 Migration With the introduction of IBM s POWER9
Four Essential Steps for Removing Risk and Downtime from Your POWER9 Migration Syncsort Four Essential Steps for Removing Risk and Downtime from Your POWER9 Migration With the introduction of IBM s POWER9
OCR Interchange Service Agreement
 Oxford Cambridge and RSA OCR Interchange Service Agreement This agreement sets out the rights and obligations of the customer ( You ) and Oxford Cambridge and RSA Examinations ( We, Us, Our ) in connection
Oxford Cambridge and RSA OCR Interchange Service Agreement This agreement sets out the rights and obligations of the customer ( You ) and Oxford Cambridge and RSA Examinations ( We, Us, Our ) in connection
Rethinking VDI: The Role of Client-Hosted Virtual Desktops. White Paper Virtual Computer, Inc. All Rights Reserved.
 Rethinking VDI: The Role of Client-Hosted Virtual Desktops White Paper 2011 Virtual Computer, Inc. All Rights Reserved. www.virtualcomputer.com The Evolving Corporate Desktop Personal computers are now
Rethinking VDI: The Role of Client-Hosted Virtual Desktops White Paper 2011 Virtual Computer, Inc. All Rights Reserved. www.virtualcomputer.com The Evolving Corporate Desktop Personal computers are now
RED HAT ENTERPRISE LINUX. STANDARDIZE & SAVE.
 RED HAT ENTERPRISE LINUX. STANDARDIZE & SAVE. Is putting Contact us INTRODUCTION You know the headaches of managing an infrastructure that is stretched to its limit. Too little staff. Too many users. Not
RED HAT ENTERPRISE LINUX. STANDARDIZE & SAVE. Is putting Contact us INTRODUCTION You know the headaches of managing an infrastructure that is stretched to its limit. Too little staff. Too many users. Not
SMARTnet provides you with the following advantages:
 SMARTnet Service is an award-winning technical support service that gives you and your IT staff direct, round the clock access to Cisco engineers and extensive Cisco.com resources. Cisco SMARTnet is essential
SMARTnet Service is an award-winning technical support service that gives you and your IT staff direct, round the clock access to Cisco engineers and extensive Cisco.com resources. Cisco SMARTnet is essential
Testing is a very big and important topic when it comes to software development. Testing has a number of aspects that need to be considered.
 Testing Testing is a very big and important topic when it comes to software development. Testing has a number of aspects that need to be considered. System stability is the system going to crash or not?
Testing Testing is a very big and important topic when it comes to software development. Testing has a number of aspects that need to be considered. System stability is the system going to crash or not?
Software Processes. Ian Sommerville 2006 Software Engineering, 8th edition. Chapter 4 Slide 1
 Software Processes Ian Sommerville 2006 Software Engineering, 8th edition. Chapter 4 Slide 1 Objectives To introduce software process models To describe three generic process models and when they may be
Software Processes Ian Sommerville 2006 Software Engineering, 8th edition. Chapter 4 Slide 1 Objectives To introduce software process models To describe three generic process models and when they may be
CS2112 Fall Assignment 4 Parsing and Fault Injection. Due: March 18, 2014 Overview draft due: March 14, 2014
 CS2112 Fall 2014 Assignment 4 Parsing and Fault Injection Due: March 18, 2014 Overview draft due: March 14, 2014 Compilers and bug-finding systems operate on source code to produce compiled code and lists
CS2112 Fall 2014 Assignment 4 Parsing and Fault Injection Due: March 18, 2014 Overview draft due: March 14, 2014 Compilers and bug-finding systems operate on source code to produce compiled code and lists
Session 4b: Review of Program Quality
 Session 4b: Review of Program Quality What makes one program "better" than another? COMP 170 -- Fall, 2013 Mr. Weisert What is a good program? Suppose we give the same assignment to two programmers (or
Session 4b: Review of Program Quality What makes one program "better" than another? COMP 170 -- Fall, 2013 Mr. Weisert What is a good program? Suppose we give the same assignment to two programmers (or
10 Cloud Myths Demystified
 10 Cloud s Demystified The Realities for Modern Campus Transformation Higher education is in an era of transformation. To stay competitive, institutions must respond to changing student expectations, demanding
10 Cloud s Demystified The Realities for Modern Campus Transformation Higher education is in an era of transformation. To stay competitive, institutions must respond to changing student expectations, demanding
The requirements engineering process
 3 rd Stage Lecture time: 8:30-12:30 AM Instructor: Ali Kadhum AL-Quraby Lecture No. : 5 Subject: Software Engineering Class room no.: Department of computer science Process activities The four basic process
3 rd Stage Lecture time: 8:30-12:30 AM Instructor: Ali Kadhum AL-Quraby Lecture No. : 5 Subject: Software Engineering Class room no.: Department of computer science Process activities The four basic process
Tackling the data analytics dilemma for predictive maintenance Dawen Nozdryn-Plotnicki Advanced Analytics Dave Kinney Technical Fellow September 2017
 Tackling the data analytics dilemma for predictive maintenance Dawen Nozdryn-Plotnicki Advanced Analytics Dave Kinney Technical Fellow September 2017 BOEING PROPRIETARY Copyright 2017 Boeing. All rights
Tackling the data analytics dilemma for predictive maintenance Dawen Nozdryn-Plotnicki Advanced Analytics Dave Kinney Technical Fellow September 2017 BOEING PROPRIETARY Copyright 2017 Boeing. All rights
Three Key Considerations for Your Public Cloud Infrastructure Strategy
 GOING PUBLIC: Three Key Considerations for Your Public Cloud Infrastructure Strategy Steve Follin ISG WHITE PAPER 2018 Information Services Group, Inc. All Rights Reserved The Market Reality The race to
GOING PUBLIC: Three Key Considerations for Your Public Cloud Infrastructure Strategy Steve Follin ISG WHITE PAPER 2018 Information Services Group, Inc. All Rights Reserved The Market Reality The race to
Provided as an educational service by: Introduction
 DPC TECHNOLOGY THE GUIDE DISASTER PLANNING ESSENTIALS CLAY ARCHER DPC TECHNOLOGY Provided as an educational service by: Clay Archer, CEO DPC Technology 7845 Baymeadows Way, Jacksonville, FL 32256 (844)
DPC TECHNOLOGY THE GUIDE DISASTER PLANNING ESSENTIALS CLAY ARCHER DPC TECHNOLOGY Provided as an educational service by: Clay Archer, CEO DPC Technology 7845 Baymeadows Way, Jacksonville, FL 32256 (844)
SPREADSHEETS AND SOLVENCY II
 SPREADSHEETS AND SOLVENCY II Dean Buckner Financial Services Authority July 2010 Agenda Solvency II is the new framework for insurance regulation in the European Union. It is currently scheduled for late
SPREADSHEETS AND SOLVENCY II Dean Buckner Financial Services Authority July 2010 Agenda Solvency II is the new framework for insurance regulation in the European Union. It is currently scheduled for late
IT323 - Software Engineering 2 1
 IT323 - Software Engineering 2 1 Explain how standards may be used to capture organizational wisdom about effective methods of software development. Suggest four types of knowledge that might be captured
IT323 - Software Engineering 2 1 Explain how standards may be used to capture organizational wisdom about effective methods of software development. Suggest four types of knowledge that might be captured
CMSC 435: Software Engineering Section 0201
 CMSC 435: Software Engineering Section 0201 Atif M. Memon (atif@cs.umd.edu) 4115 A.V.Williams building Phone: 301-405-3071 Office hours Tu.Th. (11:00am-1:00pm) Don t wait, don t hesitate, do communicate!!
CMSC 435: Software Engineering Section 0201 Atif M. Memon (atif@cs.umd.edu) 4115 A.V.Williams building Phone: 301-405-3071 Office hours Tu.Th. (11:00am-1:00pm) Don t wait, don t hesitate, do communicate!!
COLUMN. Responsive design for mobile intranets? How should the intranet be presented on mobile devices? JULY What is responsive design?
 KM COLUMN JULY 2012 Responsive design for mobile intranets? The mobile space continues to grow at breakneck pace. Many websites are now seeing upwards of 20 30% of their web traffic coming from mobile
KM COLUMN JULY 2012 Responsive design for mobile intranets? The mobile space continues to grow at breakneck pace. Many websites are now seeing upwards of 20 30% of their web traffic coming from mobile
Designing Next Generation Test Systems An In-Depth Developers Guide
 An In-Depth Developers Guide Designing Next Generation Test Systems An In-depth Developers Guide Contents Section 1 Executive Summary Chapter 1 Increasing Design Complexity...1-1 Shorter Product Development
An In-Depth Developers Guide Designing Next Generation Test Systems An In-depth Developers Guide Contents Section 1 Executive Summary Chapter 1 Increasing Design Complexity...1-1 Shorter Product Development
1 Visible deviation from the specification or expected behavior for end-user is called: a) an error b) a fault c) a failure d) a defect e) a mistake
 Sample ISTQB examination 1 Visible deviation from the specification or expected behavior for end-user is called: a) an error b) a fault c) a failure d) a defect e) a mistake 2 Regression testing should
Sample ISTQB examination 1 Visible deviation from the specification or expected behavior for end-user is called: a) an error b) a fault c) a failure d) a defect e) a mistake 2 Regression testing should
Static and dynamic Testing
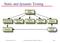 Static and dynamic Testing Static testing Requirements specification High-level design Formal specification Detailed design Program Prototype Dynamic testing Ian Sommerville 1995 Software Engineering,
Static and dynamic Testing Static testing Requirements specification High-level design Formal specification Detailed design Program Prototype Dynamic testing Ian Sommerville 1995 Software Engineering,
Part 5. Verification and Validation
 Software Engineering Part 5. Verification and Validation - Verification and Validation - Software Testing Ver. 1.7 This lecture note is based on materials from Ian Sommerville 2006. Anyone can use this
Software Engineering Part 5. Verification and Validation - Verification and Validation - Software Testing Ver. 1.7 This lecture note is based on materials from Ian Sommerville 2006. Anyone can use this
IT your way - Hybrid IT FAQs
 Hybrid IT IT your way - Hybrid IT FAQs Create a strategy that integrates in-house and outsourced IT services to meet ever-changing business requirements. Combine on-premise and off premise solutions Mix
Hybrid IT IT your way - Hybrid IT FAQs Create a strategy that integrates in-house and outsourced IT services to meet ever-changing business requirements. Combine on-premise and off premise solutions Mix
Benefits of Maintaining Computer Systems
 Benefits of Maintaining Computer Systems U14-Assignment 1 in BTEC Level 2. Benefits of Maintaining Hardware on Laptops and Desktops Part 1 - Benefits Benefits of Maintaining Hardware on a desktop Keeping
Benefits of Maintaining Computer Systems U14-Assignment 1 in BTEC Level 2. Benefits of Maintaining Hardware on Laptops and Desktops Part 1 - Benefits Benefits of Maintaining Hardware on a desktop Keeping
10 Cloud Myths Demystified
 10 Cloud s Demystified The Realities for Digital Healthcare Transformation It s a challenging time for the healthcare industry, with changing regulations, consolidation and the consumerization of healthcare
10 Cloud s Demystified The Realities for Digital Healthcare Transformation It s a challenging time for the healthcare industry, with changing regulations, consolidation and the consumerization of healthcare
Planning for Information Network
 Planning for Information Network Lecture 2: The network design methodology Assistant Teacher Samraa Adnan Al-Asadi 1 Contents The PPDIOO network lifecycle. Benefits of the lifecycle approach to network
Planning for Information Network Lecture 2: The network design methodology Assistant Teacher Samraa Adnan Al-Asadi 1 Contents The PPDIOO network lifecycle. Benefits of the lifecycle approach to network
OVM to UVM Migration, or There and Back Again: A Consultant s Tale. by Mark Litterick, Verification Consultant, Verilab GmbH
 OVM to UVM Migration, or There and Back Again: A Consultant s Tale. by Mark Litterick, Verification Consultant, Verilab GmbH ABSTRACT Many companies have a goal to migrate to UVM but this must be achieved
OVM to UVM Migration, or There and Back Again: A Consultant s Tale. by Mark Litterick, Verification Consultant, Verilab GmbH ABSTRACT Many companies have a goal to migrate to UVM but this must be achieved
Agile Accessibility. Presenters: Ensuring accessibility throughout the Agile development process
 Agile Accessibility Ensuring accessibility throughout the Agile development process Presenters: Andrew Nielson, CSM, PMP, MPA Ann Marie Davis, CSM, PMP, M. Ed. Cammie Truesdell, M. Ed. Overview What is
Agile Accessibility Ensuring accessibility throughout the Agile development process Presenters: Andrew Nielson, CSM, PMP, MPA Ann Marie Davis, CSM, PMP, M. Ed. Cammie Truesdell, M. Ed. Overview What is
WHITE PAPER. The General Data Protection Regulation: What Title It Means and How SAS Data Management Can Help
 WHITE PAPER The General Data Protection Regulation: What Title It Means and How SAS Data Management Can Help ii Contents Personal Data Defined... 1 Why the GDPR Is Such a Big Deal... 2 Are You Ready?...
WHITE PAPER The General Data Protection Regulation: What Title It Means and How SAS Data Management Can Help ii Contents Personal Data Defined... 1 Why the GDPR Is Such a Big Deal... 2 Are You Ready?...
Symantec Security Monitoring Services
 24x7 real-time security monitoring and protection Protect corporate assets from malicious global threat activity before it impacts your network. Partnering with Symantec skilled and experienced analysts
24x7 real-time security monitoring and protection Protect corporate assets from malicious global threat activity before it impacts your network. Partnering with Symantec skilled and experienced analysts
A Visual Guide to Automated MVC Reengineering
 D a t a b o r o u g h A Visual Guide to Automated MVC Reengineering Steve Kilner This guide has the following sections: 1. Three Steps To New and Improved Systems 2. Why Reengineer? 3. Bad Practices of
D a t a b o r o u g h A Visual Guide to Automated MVC Reengineering Steve Kilner This guide has the following sections: 1. Three Steps To New and Improved Systems 2. Why Reengineer? 3. Bad Practices of
Erasmus+ 2017/18 Timeline, Checklist & FAQs
 Erasmus+ 2017/18 Timeline, Checklist & FAQs When Document Tick when completed Notes / tips ( Before the Mobility section) This is the key document confirming what modules you will be studying while abroad,
Erasmus+ 2017/18 Timeline, Checklist & FAQs When Document Tick when completed Notes / tips ( Before the Mobility section) This is the key document confirming what modules you will be studying while abroad,
Get your business Skype d up. Lessons learned from Skype for Business adoption
 Get your business Skype d up Lessons learned from Skype for Business adoption On the rise with Skype for Business Recent figures from Microsoft found that 90% of Fortune 500 companies and over 100 million
Get your business Skype d up Lessons learned from Skype for Business adoption On the rise with Skype for Business Recent figures from Microsoft found that 90% of Fortune 500 companies and over 100 million
Incentives for IoT Security. White Paper. May Author: Dr. Cédric LEVY-BENCHETON, CEO
 White Paper Incentives for IoT Security May 2018 Author: Dr. Cédric LEVY-BENCHETON, CEO Table of Content Defining the IoT 5 Insecurity by design... 5 But why are IoT systems so vulnerable?... 5 Integrating
White Paper Incentives for IoT Security May 2018 Author: Dr. Cédric LEVY-BENCHETON, CEO Table of Content Defining the IoT 5 Insecurity by design... 5 But why are IoT systems so vulnerable?... 5 Integrating
DATABASE ADMINISTRATOR
 DATABASE ADMINISTRATOR Department FLSA Status Reports To Supervises Information Technology Exempt IT Director N/A DISTINGUISHING CHARACTERISTICS: The principal function of an employee in this class is
DATABASE ADMINISTRATOR Department FLSA Status Reports To Supervises Information Technology Exempt IT Director N/A DISTINGUISHING CHARACTERISTICS: The principal function of an employee in this class is
Principles of Information Security, Fourth Edition. Chapter 1 Introduction to Information Security
 Principles of Information Security, Fourth Edition Chapter 1 Introduction to Information Security Introduction Information security: a well-informed sense of assurance that the information risks and controls
Principles of Information Security, Fourth Edition Chapter 1 Introduction to Information Security Introduction Information security: a well-informed sense of assurance that the information risks and controls
Operating Systems. Memory Management. Lecture 9 Michael O Boyle
 Operating Systems Memory Management Lecture 9 Michael O Boyle 1 Memory Management Background Logical/Virtual Address Space vs Physical Address Space Swapping Contiguous Memory Allocation Segmentation Goals
Operating Systems Memory Management Lecture 9 Michael O Boyle 1 Memory Management Background Logical/Virtual Address Space vs Physical Address Space Swapping Contiguous Memory Allocation Segmentation Goals
Software Quality Assurance. David Janzen
 Software Quality Assurance David Janzen What is quality? Crosby: Conformance to requirements Issues: who establishes requirements? implicit requirements Juran: Fitness for intended use Issues: Who defines
Software Quality Assurance David Janzen What is quality? Crosby: Conformance to requirements Issues: who establishes requirements? implicit requirements Juran: Fitness for intended use Issues: Who defines
Rediffmail Enterprise High Availability Architecture
 Rediffmail Enterprise High Availability Architecture Introduction Rediffmail Enterprise has proven track record of 99.9%+ service availability. Multifold increase in number of users and introduction of
Rediffmail Enterprise High Availability Architecture Introduction Rediffmail Enterprise has proven track record of 99.9%+ service availability. Multifold increase in number of users and introduction of
Introduction To Software Testing. Brian Nielsen. Center of Embedded Software Systems Aalborg University, Denmark CSS
 Introduction To Software Testing Brian Nielsen bnielsen@cs.aau.dk Center of Embedded Software Systems Aalborg University, Denmark CSS 1010111011010101 1011010101110111 What is testing? Testing Testing:
Introduction To Software Testing Brian Nielsen bnielsen@cs.aau.dk Center of Embedded Software Systems Aalborg University, Denmark CSS 1010111011010101 1011010101110111 What is testing? Testing Testing:
Basic Concepts of Reliability
 Basic Concepts of Reliability Reliability is a broad concept. It is applied whenever we expect something to behave in a certain way. Reliability is one of the metrics that are used to measure quality.
Basic Concepts of Reliability Reliability is a broad concept. It is applied whenever we expect something to behave in a certain way. Reliability is one of the metrics that are used to measure quality.
Forecasting Technology Insertion Concurrent with Design Refresh Planning for COTS-Based Electronic Systems
 Forecasting Technology Insertion Concurrent with Design Refresh Planning for COTS-Based Electronic Systems Peter Sandborn and Pameet Singh CALCE, Dept. of Mechanical Engineering, University of Maryland
Forecasting Technology Insertion Concurrent with Design Refresh Planning for COTS-Based Electronic Systems Peter Sandborn and Pameet Singh CALCE, Dept. of Mechanical Engineering, University of Maryland
Simple Garbage Collection and Fast Allocation Andrew W. Appel
 Simple Garbage Collection and Fast Allocation Andrew W. Appel Presented by Karthik Iyer Background Motivation Appel s Technique Terminology Fast Allocation Arranging Generations Invariant GC Working Heuristic
Simple Garbage Collection and Fast Allocation Andrew W. Appel Presented by Karthik Iyer Background Motivation Appel s Technique Terminology Fast Allocation Arranging Generations Invariant GC Working Heuristic
Incident response in the energy
 Incident response in the energy sector Margrete Raaum, Statnett SF and FIRST, Forum of Incident Response and Security Teams 4SICS, October 23. 2014 Incident response IR is more than just a characterization
Incident response in the energy sector Margrete Raaum, Statnett SF and FIRST, Forum of Incident Response and Security Teams 4SICS, October 23. 2014 Incident response IR is more than just a characterization
Specifying and Prototyping
 Contents Specifying and Prototyping M. EVREN KIYMAÇ 2008639030 What is Specifying? Gathering Specifications Specifying Approach & Waterfall Model What is Prototyping? Uses of Prototypes Prototyping Process
Contents Specifying and Prototyping M. EVREN KIYMAÇ 2008639030 What is Specifying? Gathering Specifications Specifying Approach & Waterfall Model What is Prototyping? Uses of Prototypes Prototyping Process
WHITEPAPER. Embracing Containers & Microservices for future-proof application modernization
 WHITEPAPER Embracing Containers & Microservices for future-proof application modernization The need for application modernization: Legacy applications are typically based on a monolithic design, which
WHITEPAPER Embracing Containers & Microservices for future-proof application modernization The need for application modernization: Legacy applications are typically based on a monolithic design, which
STRUCTURED SYSTEM ANALYSIS AND DESIGN. System Concept and Environment
 STRUCTURED SYSTEM ANALYSIS AND DESIGN Definition: - System Concept and Environment A system is an orderly grouping of independent components linked together according to plan to achieve a specific objective.
STRUCTURED SYSTEM ANALYSIS AND DESIGN Definition: - System Concept and Environment A system is an orderly grouping of independent components linked together according to plan to achieve a specific objective.
A Security Model for Space Based Communication. Thom Stone Computer Sciences Corporation
 A Security Model for Space Based Communication Thom Stone Computer Sciences Corporation Prolog Everything that is not forbidden is compulsory -T.H. White They are after you Monsters in the Closet Virus
A Security Model for Space Based Communication Thom Stone Computer Sciences Corporation Prolog Everything that is not forbidden is compulsory -T.H. White They are after you Monsters in the Closet Virus
Bender Remote Assist
 Bender Remote Assist Efficient and of high quality safe remote service Installation analysis Connection protocols Bus recording Operating Assist Remote maintenance Event protocols Global History memory
Bender Remote Assist Efficient and of high quality safe remote service Installation analysis Connection protocols Bus recording Operating Assist Remote maintenance Event protocols Global History memory
SOFTWARE PRODUCT QUALITY SOFTWARE ENGINEERING SOFTWARE QUALITY SOFTWARE QUALITIES - PRODUCT AND PROCESS SOFTWARE QUALITY - QUALITY COMPONENTS
 SOFTWARE PRODUCT QUALITY Today: - Software quality - Quality Components - Good software properties SOFTWARE ENGINEERING SOFTWARE QUALITY Today we talk about quality - but what is quality? Suitable Fulfills
SOFTWARE PRODUCT QUALITY Today: - Software quality - Quality Components - Good software properties SOFTWARE ENGINEERING SOFTWARE QUALITY Today we talk about quality - but what is quality? Suitable Fulfills
5 STEPS for Turning Data into Actionable Insights
 5 STEPS for Turning Data into Actionable Insights Today, nearly every piece of equipment in a data center has at least one sensor attached to it. In fact, American Society of Heating, Refrigerating and
5 STEPS for Turning Data into Actionable Insights Today, nearly every piece of equipment in a data center has at least one sensor attached to it. In fact, American Society of Heating, Refrigerating and
Memory Allocation. Static Allocation. Dynamic Allocation. Dynamic Storage Allocation. CS 414: Operating Systems Spring 2008
 Dynamic Storage Allocation CS 44: Operating Systems Spring 2 Memory Allocation Static Allocation (fixed in size) Sometimes we create data structures that are fixed and don t need to grow or shrink. Dynamic
Dynamic Storage Allocation CS 44: Operating Systems Spring 2 Memory Allocation Static Allocation (fixed in size) Sometimes we create data structures that are fixed and don t need to grow or shrink. Dynamic
Klocwork Architecture Excavation Methodology. Nikolai Mansurov Chief Scientist & Architect
 Klocwork Architecture Excavation Methodology Nikolai Mansurov Chief Scientist & Architect Overview Introduction Production of software is evolutionary and involves multiple releases Evolution of existing
Klocwork Architecture Excavation Methodology Nikolai Mansurov Chief Scientist & Architect Overview Introduction Production of software is evolutionary and involves multiple releases Evolution of existing
Lecture 5: Requirements Specifications
 Lecture 5: Requirements Specifications Why we need to write specifications Purpose and audience Choosing an appropriate size and formality Desiderata for Specifications Properties of good specifications
Lecture 5: Requirements Specifications Why we need to write specifications Purpose and audience Choosing an appropriate size and formality Desiderata for Specifications Properties of good specifications
Lecture 19 Engineering Design Resolution: Generating and Evaluating Architectures
 Lecture 19 Engineering Design Resolution: Generating and Evaluating Architectures Software Engineering ITCS 3155 Fall 2008 Dr. Jamie Payton Department of Computer Science University of North Carolina at
Lecture 19 Engineering Design Resolution: Generating and Evaluating Architectures Software Engineering ITCS 3155 Fall 2008 Dr. Jamie Payton Department of Computer Science University of North Carolina at
Practical Database Design Methodology and Use of UML Diagrams Design & Analysis of Database Systems
 Practical Database Design Methodology and Use of UML Diagrams 406.426 Design & Analysis of Database Systems Jonghun Park jonghun@snu.ac.kr Dept. of Industrial Engineering Seoul National University chapter
Practical Database Design Methodology and Use of UML Diagrams 406.426 Design & Analysis of Database Systems Jonghun Park jonghun@snu.ac.kr Dept. of Industrial Engineering Seoul National University chapter
PDF - INTEL FORTRAN XE DOCUMENT
 03 January, 2018 PDF - INTEL FORTRAN XE DOCUMENT Document Filetype: PDF 365.77 KB 0 PDF - INTEL FORTRAN XE DOCUMENT Deliver top C++ and Fortran application performance with less effort. Intel Parallel
03 January, 2018 PDF - INTEL FORTRAN XE DOCUMENT Document Filetype: PDF 365.77 KB 0 PDF - INTEL FORTRAN XE DOCUMENT Deliver top C++ and Fortran application performance with less effort. Intel Parallel
Distributed Data Infrastructures, Fall 2017, Chapter 2. Jussi Kangasharju
 Distributed Data Infrastructures, Fall 2017, Chapter 2 Jussi Kangasharju Chapter Outline Warehouse-scale computing overview Workloads and software infrastructure Failures and repairs Note: Term Warehouse-scale
Distributed Data Infrastructures, Fall 2017, Chapter 2 Jussi Kangasharju Chapter Outline Warehouse-scale computing overview Workloads and software infrastructure Failures and repairs Note: Term Warehouse-scale
Verification and Validation. Assuring that a software system meets a user s needs. Verification vs Validation. The V & V Process
 Verification and Validation Assuring that a software system meets a user s needs Ian Sommerville 1995/2000 (Modified by Spiros Mancoridis 1999) Software Engineering, 6th edition. Chapters 19,20 Slide 1
Verification and Validation Assuring that a software system meets a user s needs Ian Sommerville 1995/2000 (Modified by Spiros Mancoridis 1999) Software Engineering, 6th edition. Chapters 19,20 Slide 1
OO Project Management
 OO Project Management Twin Cities Java User s Group November 17, 1999 Mary Poppendieck Poppendieck.LLC Object Oriented Development Objects Simulate the Real World Example: Process Control On/Off Switch
OO Project Management Twin Cities Java User s Group November 17, 1999 Mary Poppendieck Poppendieck.LLC Object Oriented Development Objects Simulate the Real World Example: Process Control On/Off Switch
Software processes. Objectives. Contents
 2 Software processes Objectives The objective of this chapter is to introduce you to the idea of a software process a coherent set of activities for software production. When you have read this chapter
2 Software processes Objectives The objective of this chapter is to introduce you to the idea of a software process a coherent set of activities for software production. When you have read this chapter
SOFTWARE MAINTENANCE: A
 SOFTWARE MAINTENANCE: A TUTORIAL BY KEITH H. BENNETT 2008.10.13 소프트웨어 200310612 조보경 Software Engineering Field Main problem of software engineering Scale and Complexity of the software Goal of software
SOFTWARE MAINTENANCE: A TUTORIAL BY KEITH H. BENNETT 2008.10.13 소프트웨어 200310612 조보경 Software Engineering Field Main problem of software engineering Scale and Complexity of the software Goal of software
Dilbert Scott Adams. CSc 233 Spring 2012
 Dilbert Scott Adams CSc 233 Spring 2012 Dilbert Scott Adams CSc 233 Spring 2012 2 Dilbert Scott Adams CSc 233 Spring 2012 3 prerequisites CSc 233 Spring 2012 I thought we had agreed long ago that the Department
Dilbert Scott Adams CSc 233 Spring 2012 Dilbert Scott Adams CSc 233 Spring 2012 2 Dilbert Scott Adams CSc 233 Spring 2012 3 prerequisites CSc 233 Spring 2012 I thought we had agreed long ago that the Department
McLaughlin Brunson Insurance Agency, LLP
 The following Risk Review Newsletter is being provided to you in electronic format for your convenience. If you would like additional copies sent to others in your firm or have questions or comments regarding
The following Risk Review Newsletter is being provided to you in electronic format for your convenience. If you would like additional copies sent to others in your firm or have questions or comments regarding
SIS Operation & Maintenance 15 minutes
 2005 Emerson Process Management. All rights reserved. View this and other courses online at www.plantwebuniversity.com. SIS 301 - Operation & Maintenance 15 minutes In this course: 1 Overview 2 Planning
2005 Emerson Process Management. All rights reserved. View this and other courses online at www.plantwebuniversity.com. SIS 301 - Operation & Maintenance 15 minutes In this course: 1 Overview 2 Planning
Reminder: Mechanics of address translation. Paged virtual memory. Reminder: Page Table Entries (PTEs) Demand paging. Page faults
 CSE 451: Operating Systems Autumn 2012 Module 12 Virtual Memory, Page Faults, Demand Paging, and Page Replacement Reminder: Mechanics of address translation virtual address virtual # offset table frame
CSE 451: Operating Systems Autumn 2012 Module 12 Virtual Memory, Page Faults, Demand Paging, and Page Replacement Reminder: Mechanics of address translation virtual address virtual # offset table frame
Paper. Delivering Strong Security in a Hyperconverged Data Center Environment
 Paper Delivering Strong Security in a Hyperconverged Data Center Environment Introduction A new trend is emerging in data center technology that could dramatically change the way enterprises manage and
Paper Delivering Strong Security in a Hyperconverged Data Center Environment Introduction A new trend is emerging in data center technology that could dramatically change the way enterprises manage and
One and a half hours. Appendices A and B are located at the back of the exam UNIVERSITY OF MANCHESTER SCHOOL OF COMPUTER SCIENCE
 One and a half hours Appendices A and B are located at the back of the exam UNIVERSITY OF MANCHESTER SCHOOL OF COMPUTER SCIENCE Software Evolution Date: Tuesday 20th May 2014 Time: 09:45-11:15 Please answer
One and a half hours Appendices A and B are located at the back of the exam UNIVERSITY OF MANCHESTER SCHOOL OF COMPUTER SCIENCE Software Evolution Date: Tuesday 20th May 2014 Time: 09:45-11:15 Please answer
2 Software life span models
 2 Software life span models Stages through which software goes, from conception to death Stages may be very different Software = product stages are similar to the stages in the life span of other products
2 Software life span models Stages through which software goes, from conception to death Stages may be very different Software = product stages are similar to the stages in the life span of other products
Hybrid IT Managed Services
 Hybrid IT Managed Services Working together on your digital journey Welcome to the new world of Hybrid IT Managed Services. Digital technology is rapidly changing and improving our world. As your organisation
Hybrid IT Managed Services Working together on your digital journey Welcome to the new world of Hybrid IT Managed Services. Digital technology is rapidly changing and improving our world. As your organisation
Ch 1: The Architecture Business Cycle
 Ch 1: The Architecture Business Cycle For decades, software designers have been taught to build systems based exclusively on the technical requirements. Software architecture encompasses the structures
Ch 1: The Architecture Business Cycle For decades, software designers have been taught to build systems based exclusively on the technical requirements. Software architecture encompasses the structures
Iowa Department of Transportation Statewide Coordinated GIS
 1998 TRANSPORTATION CONFERENCE PROCEEDINGS 187 Iowa Department of Transportation Statewide Coordinated GIS WILLIAM G. SCHUMAN, TIM STRAUSS, DAN GIESEMAN, AND REGINALD R. SOULEYRETTE This paper details
1998 TRANSPORTATION CONFERENCE PROCEEDINGS 187 Iowa Department of Transportation Statewide Coordinated GIS WILLIAM G. SCHUMAN, TIM STRAUSS, DAN GIESEMAN, AND REGINALD R. SOULEYRETTE This paper details
Sample Exam. Advanced Test Automation - Engineer
 Sample Exam Advanced Test Automation - Engineer Questions ASTQB Created - 2018 American Software Testing Qualifications Board Copyright Notice This document may be copied in its entirety, or extracts made,
Sample Exam Advanced Test Automation - Engineer Questions ASTQB Created - 2018 American Software Testing Qualifications Board Copyright Notice This document may be copied in its entirety, or extracts made,
Where Should the Brain of Your Mobile Application Live?
 Where Should the Brain of Your Mobile Application Live? Or, how Gilt architected its ios apps so compiled binaries released years ago can keep up with evolving server data models First, an introduction
Where Should the Brain of Your Mobile Application Live? Or, how Gilt architected its ios apps so compiled binaries released years ago can keep up with evolving server data models First, an introduction
Total Cost of Ownership: Benefits of ECM in the OpenText Cloud
 Total Cost of Ownership: Benefits of ECM in the OpenText Cloud OpenText Managed Services brings together the power of an enterprise cloud platform with the technical skills and business experience required
Total Cost of Ownership: Benefits of ECM in the OpenText Cloud OpenText Managed Services brings together the power of an enterprise cloud platform with the technical skills and business experience required
Total Cost of Ownership: Benefits of the OpenText Cloud
 Total Cost of Ownership: Benefits of the OpenText Cloud OpenText Managed Services in the Cloud delivers on the promise of a digital-first world for businesses of all sizes. This paper examines how organizations
Total Cost of Ownership: Benefits of the OpenText Cloud OpenText Managed Services in the Cloud delivers on the promise of a digital-first world for businesses of all sizes. This paper examines how organizations
Verification and Validation. Ian Sommerville 2004 Software Engineering, 7th edition. Chapter 22 Slide 1
 Verification and Validation Ian Sommerville 2004 Software Engineering, 7th edition. Chapter 22 Slide 1 Verification vs validation Verification: "Are we building the product right?. The software should
Verification and Validation Ian Sommerville 2004 Software Engineering, 7th edition. Chapter 22 Slide 1 Verification vs validation Verification: "Are we building the product right?. The software should
New Zealand Customs Service: Managing Trade Assurance capability risks
 New Zealand Customs Service: Managing Trade Assurance capability risks Progress in responding to the Auditor-General s recommendations This is an independent assurance report about a performance audit
New Zealand Customs Service: Managing Trade Assurance capability risks Progress in responding to the Auditor-General s recommendations This is an independent assurance report about a performance audit
