Technical Requirements COMPLIANCE AND FRAUD HELPLINE AND CASE MANAGEMENT SERVICES
|
|
|
- Conrad Parsons
- 5 years ago
- Views:
Transcription
1 Technical Requirements COMPLIANCE AND FRAUD HELPLINE AND CASE MANAGEMENT SERVICES No. Requirement Vendor # Incident Reporting Reporting methods are available to all employees 24 hours per day, 365 days per year and allow for various methods for follow up support for both named and anonymous reporters. All incident data is retained and available for a minimum of thirty six (36) months from the date of the original report s closure date. All incident data is translated into (if necessary), and retained in English. All calls or web incident reports will originate within the continental U.S Telephonic Incident reporting calls will be placed using a toll free number for use throughout Missouri and Illinois. If applicable, Vendor can assume ownership of an existing number for incoming calls Automated Welcome Message Standard, prerecorded message validating to the caller that they have reached the appropriate phone number Call Greeting Call greeting can be customized with the specific name of Client s incident reporting program. Call greetings must not exceed 30 seconds Custom Questions In addition to a standard proprietary incident reporting script developed by Vendor, Client may request up to 5 additional custom questions Dissemination Incident reports can be disseminated to least 10 named recipients via , or Extensible Markup Language (XML) file by or File Transfer Protocol (FTP). Pretty Good Privacy (PGP) encryption is desired for transmissions. Page 1 of 14
2 Escalation Escalation is based on a 3 tiered escalation criteria (e.g., High, Medium, and Low priority) For High priority incident reports (i.e., incidents requiring Client s immediate action due to potential threat to a person, property, or environment), Vendor must immediately escalate initial report to up to three (3) Client contacts, by telephone on For Medium priority incident reports (i.e., incidents requiring Client s prompt, but not immediate, action), Vendor completes the report in the Vendor s incident reporting system and then alerts Client designated recipients via For Low priority incident reports (i.e., incidents that do not require Client s immediate action), Vendor completes the report in the Vendor s incident reporting system and then alerts Client designated recipients via . Page 2 of 14
3 Incident Report /Follow Up Reports The initial incident report and any follow up reports must include an Incident Report Control Number and access code provided to the Incident Reporter during his/her initial call. In addition, the Report will include a date given to the Reporter to call back for any follow up status. If Client wishes to provide a follow up response to the Reporter, Client will need to upload the response to the Case Management Application account before the designated follow up date. Client response to the Reporter may include, but need not be limited to, additional questions concerning the reported information, a statement concerning the status of the investigation of the reported information, or a request that the Reporter contact an internal Client representative. If the Reporter makes a follow up call to the Incident Reporting System phone number and can provide the Report Control Number and access code, the Vendor s customer service agent will read Client response to the Reporter. If the Reporter provides additional information, the Vendor s customer service agent will prepare a followup report containing the additional information, upload the report to Client Case Management Application account, and the report or a report notice to Client designated Report Recipient(s) Facility Locations The full addresses of Client s facility locations will be provided to the Vendor for uploading into Vendor s incident reporting system. Page 3 of 14
4 Incident Codes The following standard incident codes are required: a. Accounting/Audit Irregularities b. Computer Security Issues c. Conflicts of Interest d. Client Credit Card Abuse e. Customer Relations f. Discrimination g. Employee Relations h. Facility/Physical Security Issues i. Falsification of Agency Records j. Fraud k. Fraudulent Insurance Claims l. General Harassment m. Improper Loans to Executives n. Kickbacks o. Policy Issues p. Release of Proprietary Information q. Retaliation of Whistleblowers r. Safety Issues s. Sanitation Issues t. Security Issues u. Sexual Harassment v. Substance Abuse w. Theft of Cash x. Theft of Goods/Services y. Theft of Time z. Unauthorized Discounts aa. Unauthorized Gifts or Gratuities bb. Wage/Hour Issues cc. Workplace Violence/Threats If the Vendor has additional incident codes, or includes one or more incident codes as part of another incident code name, the Vendor must list them in their response. Page 4 of 14
5 Incident Code Definitions Text describing each Incident Code will default to those provided by the Vendor but can be customized for Client specific needs Incident Report Web Form Vendor must provide standard employee facing, web based method allowing Client employees, suppliers, and supporting contractors to enter incident reports and responses to certain critical questions in order to capture and centralize all reported incidents. Access to must be provided through Client Internet and Intranet web sites Branding Vendor will upload personalized logo provided by Client Incident Codes See section 1.3 above Custom Questions See section above File Attachments Supporting documentation in the form of electronic files can be attached to a reported incident. No more than 10 files can be attached to a single incident report and combined size of attached files cannot exceed 10 MB. No single attached file should exceed 3 MB Incident Report /Follow Up Web Form Vendor must provide standard Web based access allowing Client managers to enter responses to certain critical questions in order to capture and centralize all reported issues Branding Vendor will upload personalized logo provided by Client. Page 5 of 14
6 Incident Codes See section 1.3 above Custom Questions See section above File Attachments Supporting documentation in the form of electronic files can be attached to a reported incident. No more than 10 files can be attached to a single incident report and combined size of attached files cannot exceed 10 MB. No single attached file should exceed 3 MB Incident Reporting (Vendors are allowed to fulfill these requirements separately under a separate Case Management services section) Activity Detail Report Distributed monthly via to Client designated recipients, this report contains the following fields for each individual event within the most recently completed month: Location Report Number Date of Incident Incident Status Issue Type City State Previously Reported to Management (Yes/No) Incident Summary Page 6 of 14
7 Summary Report Distributed monthly via to Client designated recipients, this report contains monthly and year to date summaries of: Incident Report Activity o Anonymous vs. non anonymous incidents o Escalated incidents o Incidents previously reported to management reports o Incident Status Call Activity o Total calls o Original incident reports o Caller callbacks o Client follow up Issue Type Summary o Call number o Percentage by Incident Code o Incident Status Standard Report Library Client users have the ability to select Vendor provided standard reports, apply filters to those reports, and produce reports for print or electronic distribution Report Wizard Client users have the ability to create, save, and share custom reports to display specific details, summary overviews, or graphical representations. Page 7 of 14
8 Case Management The goals for Case Management are to: Ensure that every incident, regardless of how it is reported, is centrally managed and everyone involved knows what needs to be done, and is resolved in a timely manner. Provide a comprehensive view of all incident activity across Client, offering an audit trail of every incident from allegation to investigation to resolution, allowing instant analysis and the ability to address critical issues quickly. All case management data is retained and available for a minimum of thirty six (36) months from the case closed date All case information is to be displayed, retained, and reported on in English Incident Data The Case Management system will automatically populate with all incident data from all available network incident reporting mechanisms/services purchased by Client Initial User Setup Vendor will create initial user profiles, standard roles (Administrator, Case Manager, and Investigator) and at least three (3) customized work groups and workflows Location Hierarchy Vendor will configure system with the Client s facility locations and organizational hierarchy Standard Portal and Dashboard Implementation Vendor must provide Client users with a gateway to the Case Management system Branding Vendor will upload personalized logo provided by Client. Page 8 of 14
9 Workflows Case Management will utilize the Vendor s own defined standard best practice workflows for the incidents types identified in section 1.3 above Business rules Case Management will be configured with the following Vendor defined standard best practice business rules for : Notification upon Case Assignment (no conditionality applied) Notification upon /Follow up Received (no conditionality applied) System Configuration Vendor will work with Client to configure the following: Case Class Status Types Priority Types Risk Types Outcome Types Disposition Types File Categories Categories Involved Party Types Categories Reporting and Analytics User Permissions Client must have the ability to grant access to Reporting and Analytics to any user that has a login to Case Management Standard Reports Reporting and Analytics will be configured with the following Vendor defined standard best practice reports that cover: Activity by Location Activity by Hierarchy Case Status Count Cases Closed in Last X Days Workload by Assignee Cases due in Next X Days Page 9 of 14
10 Standard Dashboard Widgets Reporting and Analytics will be configured with Vendor defined standard best practice dashboard web based widgets that cover: Activity by Hierarchy Case Status Count Cases Closed in Last X Days Workload by Assignee Cases Due in Next X Days Client requires the ability to create custom reports utilizing the Vendor s standard templates Client desires to have the ability to create custom dashboard widgets from their custom reports Customizable Default Dashboard Roles Vendor will work with Client to determine the naming convention for up to 5 default dashboard roles to be used in Reporting and Analytics. (Building of the default dashboards will be done by Client staff assigned to those roles.) System Administration Two (2) Client Administrators will be identified for adding or deleting Administrator, Case Manager, and Investigator users, resetting passwords, and running ad hoc reports. Page 10 of 14
11 Employee Communication and Awareness (all items are optional and separately priced) Vendor will prepare ready made electronic versions of print media to educate and promote ethics hotline and ethics program to Client employees. Client will utilize Vendor s standard materials with only minimal customization. Since Client has its own in house print center, Vendor will authorize reproduction and provide originals in Adobe PDF format. Client will provide its logo in color in the Vendor s desired electronic format as much as possible Web Landing Page Themed Web page displaying program message, telephonic Incident reporting number(s), and Uniform Resource Locator (URL) for Incident Report Web Form (see section 1.4 above). Configurable components include Client specific list of Reportable Activities Employee Templates: Employee Template Vendor will provide a draft message to be used in a Client administered campaign notifying employees of program Manager Template Vendor will provide a draft message to be used in a Client administered campaign encouraging managers to promote program among employees Overview Presentation Vendor will provide their standard PowerPoint presentation template to be used in a Client administered incident reporting awareness campaign FAQs themed file containing questions frequently asked about incident reporting programs. Page 11 of 14
12 Brochure with Wallet Card Themed tri fold brochure (8.5 by 11 ) with removable wallet card displaying program message, telephonic Incident reporting number(s), and URL for Incident Report Web Form (see section 1.4 above). Configurable components include Client specific list of Reportable Activities Program Poster Vendor will provide a themed program poster (11 wide by 17 tall) displaying incident reporting program message, telephonic Incident reporting number(s), and URL for Incident Report Web Form (see section 1.4 above) Other Topical Posters Client may select four (4) posters (11 wide by 17 tall) for display from Vendor s library of Vendor developed posters Introductory Letter and Envelope Vendor will provide a single page letter for promoting the incidentreporting program to Client employees and contractors. Configurable components include: Client Letterhead Client will provide letterhead in monochrome and color in the vendor s desired electronic format as much as possible Signature Client provided image of signature from Client program promoter Letter Content Vendor will supply sample messaging that can be used by Client or Client can provide corporate messaging to be used Envelopes Client will provide its own #10 size pre printed envelopes for this mailing Training Vendor will provide role based Incident Reporting and Case Management training to Client Administrators (2), Case Managers (up to 10), and Investigators (up to 10). The Vendor will host all courses through webinars, or the Vendor s own in line training system or website. Page 12 of 14
13 Implementation Methodology Once this SOW is awarded with a subsequent contract award, Vendor will follow Vendor s standard implementation approach to ensure the timely delivery of a solution that meets or exceeds all defined Client requirements. Based on product selection and complexity of implementation, these steps may be conducted by , phone, or inperson meetings. Steps of this approach will include: 6.1. Establishment of Vendor and Client project teams Implementation kick off to outline the implementation process, develop a project schedule, and set the tone for the project Assessing and defining Client needs Making recommendations based on Vendor s best business practice experience (as needed) Defining required system configuration System testing and user acceptance testing Administrator and end user training (as needed) Client rollout and post implementation validation. Page 13 of 14
14 Post rollout support for up to 30 days after go live. 65. Note: Section 7 contains Fees Section 8 contains terms and definitions Change Management SOW Change Request Process. Scope control is a priority during the term of this SOW. A Change Request ( CR ) is defined as a written agreement between the Parties for additions, modifications, or deletions to this SOW 9.1. Client and/or Vendor will identify a desired change and give the other Party a written notice thereof ( Notice of Proposed Change ) Vendor will determine the impact of the desired change on Project scope, schedule, and/or budget, and will provide Client with a written statement of such impact ( Statement of Impact ) concurrently with any Notice of Proposed Change given to Client or within a commercially reasonable time after either Party documents a Notice of Proposed Change Client will review the Statement of Impact and may request additional information. Vendor may specify commercially reasonable fees to be charged, if any, to reimburse Vendor for expenses to be incurred in providing such additional information with respect to any Notice of Proposed Change initiated by Client If both Parties desire to implement the proposed change, the Parties will jointly develop a CR describing the proposed change and the rationale for such change. If the CR is acceptable to both Parties, the Client and Vendor will each sign and deliver the CR to the other, which will then constitute the Parties binding agreement to the proposed change and any associated fees provided for therein Vendor will invoice Client for any additional charges provided for in the CR. Page 14 of 14
Juniper Vendor Security Requirements
 Juniper Vendor Security Requirements INTRODUCTION This document describes measures and processes that the Vendor shall, at a minimum, implement and maintain in order to protect Juniper Data against risks
Juniper Vendor Security Requirements INTRODUCTION This document describes measures and processes that the Vendor shall, at a minimum, implement and maintain in order to protect Juniper Data against risks
Wireless Services Allowance Procedure
 Wireless Services Allowance Procedure Office: Information Technology Procedure Contact: Chief Information Officer Related Policy or Policies: Wireless Services Allowance Policy FAD.042 Revision History
Wireless Services Allowance Procedure Office: Information Technology Procedure Contact: Chief Information Officer Related Policy or Policies: Wireless Services Allowance Policy FAD.042 Revision History
IBM Managed Security Services for X-Force Hosted Threat Analysis Service
 IBM Managed Security Services for X-Force Hosted Threat Analysis Service Z125-8483-00 05-2010 Page 1 of 5 Table of Contents 1. Scope of Services... 3 1.1 Licensing... 3 1.1.1 Individual... 3 1.1.2 Distribution...
IBM Managed Security Services for X-Force Hosted Threat Analysis Service Z125-8483-00 05-2010 Page 1 of 5 Table of Contents 1. Scope of Services... 3 1.1 Licensing... 3 1.1.1 Individual... 3 1.1.2 Distribution...
Request For Proposal ONWAA Website & E-Learn Portal
 Request For Proposal ONWAA Website & E-Learn Portal ONWAA 880 17 E, Garden River, Ontario P6A 6Z5 Table Of Contents General information Project Overview Statement of Needs Proposal Format Proposal Preparation
Request For Proposal ONWAA Website & E-Learn Portal ONWAA 880 17 E, Garden River, Ontario P6A 6Z5 Table Of Contents General information Project Overview Statement of Needs Proposal Format Proposal Preparation
Managed Security Services - Endpoint Managed Security on Cloud
 Services Description Managed Security Services - Endpoint Managed Security on Cloud The services described herein are governed by the terms and conditions of the agreement specified in the Order Document
Services Description Managed Security Services - Endpoint Managed Security on Cloud The services described herein are governed by the terms and conditions of the agreement specified in the Order Document
IBM Case Manager on Cloud
 Service Description IBM Case Manager on Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means and includes the company, its authorized users or recipients of the
Service Description IBM Case Manager on Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means and includes the company, its authorized users or recipients of the
Welcome to the Vale Vendor Portal Guide
 Welcome to the Vale Vendor Portal Guide 1. Introductory 1.1 How to access? 1.2 Presenting the Portal 2. Onboarding Process 3. Negotiate Module 4. Purchase Module 5. Payment Module 1. Introductory Main
Welcome to the Vale Vendor Portal Guide 1. Introductory 1.1 How to access? 1.2 Presenting the Portal 2. Onboarding Process 3. Negotiate Module 4. Purchase Module 5. Payment Module 1. Introductory Main
WIRELESS DEVICES: ACCEPTABLE USE AND GUIDELINES
 Goodhue County Education District #6051 WIRELESS DEVICES: ACCEPTABLE USE AND GUIDELINES Procedures Manual Updated January 2016 Table of Contents Overview 3 Definitions 3 General Guidelines 4 Eligibility
Goodhue County Education District #6051 WIRELESS DEVICES: ACCEPTABLE USE AND GUIDELINES Procedures Manual Updated January 2016 Table of Contents Overview 3 Definitions 3 General Guidelines 4 Eligibility
WIRELESS DEVICES: ACCEPTABLE USE AND GUIDELINES
 Intermediate School District #917 WIRELESS DEVICES: ACCEPTABLE USE AND GUIDELINES Procedures Manual April 2009 Table of Contents Overview 3 Definitions 3 General Guidelines 4 Eligibility Requirements 5
Intermediate School District #917 WIRELESS DEVICES: ACCEPTABLE USE AND GUIDELINES Procedures Manual April 2009 Table of Contents Overview 3 Definitions 3 General Guidelines 4 Eligibility Requirements 5
ORACLE UTILITIES OPOWER PROFESSIONAL SERVICES DESCRIPTIONS
 ORACLE UTILITIES OPOWER PROFESSIONAL SERVICES DESCRIPTIONS Oracle Utilities Opower Service Bundle Fees...3 Oracle Utilities Opower Basic Service Bundle Fee... 3 Oracle Utilities Opower Standard Service
ORACLE UTILITIES OPOWER PROFESSIONAL SERVICES DESCRIPTIONS Oracle Utilities Opower Service Bundle Fees...3 Oracle Utilities Opower Basic Service Bundle Fee... 3 Oracle Utilities Opower Standard Service
IBM Security Intelligence on Cloud
 Service Description IBM Security Intelligence on Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means and includes the company, its authorized users or recipients
Service Description IBM Security Intelligence on Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means and includes the company, its authorized users or recipients
CONNECT TRANSIT CARD Pilot Program - Privacy Policy Effective Date: April 18, 2014
 CONNECT TRANSIT CARD Pilot Program - Privacy Policy Effective Date: April 18, 2014 1. Welcome 1.1 Welcome to the Connect Transit Card Program. The Connect Card Program makes using public transit easier
CONNECT TRANSIT CARD Pilot Program - Privacy Policy Effective Date: April 18, 2014 1. Welcome 1.1 Welcome to the Connect Transit Card Program. The Connect Card Program makes using public transit easier
Standard mobile phone a mobile device that can make and receive telephone calls, pictures, video, and text messages.
 Overview Fiscal Accountability Rule 10.9 Utilizing Mobile Devices to Conduct City Business establishes the mobile device rule for the City and County of Denver. This policy provides mobile device guidelines
Overview Fiscal Accountability Rule 10.9 Utilizing Mobile Devices to Conduct City Business establishes the mobile device rule for the City and County of Denver. This policy provides mobile device guidelines
Privacy Statement. Your privacy and trust are important to us and this Privacy Statement ( Statement ) provides important information
 Privacy Statement Introduction Your privacy and trust are important to us and this Privacy Statement ( Statement ) provides important information about how IT Support (UK) Ltd handle personal information.
Privacy Statement Introduction Your privacy and trust are important to us and this Privacy Statement ( Statement ) provides important information about how IT Support (UK) Ltd handle personal information.
IP Centrex Administrator Guide Release 2.0
 IP Centrex Administrator Guide Release 2.0 2012 by Cox Communications. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means, electronic, mechanical,
IP Centrex Administrator Guide Release 2.0 2012 by Cox Communications. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means, electronic, mechanical,
IP Office Intuity Mailbox Mode User Guide
 Intuity Mailbox Mode User Guide 15-601130 EN-S Issue 12b - (03 October 2011) 2011 AVAYA All Rights Reserved. Notices While reasonable efforts have been made to ensure that the information in this document
Intuity Mailbox Mode User Guide 15-601130 EN-S Issue 12b - (03 October 2011) 2011 AVAYA All Rights Reserved. Notices While reasonable efforts have been made to ensure that the information in this document
Trust Services Principles and Criteria
 Trust Services Principles and Criteria Security Principle and Criteria The security principle refers to the protection of the system from unauthorized access, both logical and physical. Limiting access
Trust Services Principles and Criteria Security Principle and Criteria The security principle refers to the protection of the system from unauthorized access, both logical and physical. Limiting access
Using Manage Alarm Tool
 Using Manage Alarm Tool Release 1.0 Issue 1 April 2013 2013 Avaya Inc. All Rights Reserved. Notice While reasonable efforts have been made to ensure that the information in this document is complete and
Using Manage Alarm Tool Release 1.0 Issue 1 April 2013 2013 Avaya Inc. All Rights Reserved. Notice While reasonable efforts have been made to ensure that the information in this document is complete and
Technical Overview. Access control lists define the users, groups, and roles that can access content as well as the operations that can be performed.
 Technical Overview Technical Overview Standards based Architecture Scalable Secure Entirely Web Based Browser Independent Document Format independent LDAP integration Distributed Architecture Multiple
Technical Overview Technical Overview Standards based Architecture Scalable Secure Entirely Web Based Browser Independent Document Format independent LDAP integration Distributed Architecture Multiple
Workflow Templates in Compliance 360 Version 2018
 Workflow Templates in Compliance 360 Version 2018 Workflow Templates 5 Workflow Elements 6 Workflow Teams 6 Workflow Template Changes 6 Create or Edit a Workflow Template 8 Import and Export Workflow Templates
Workflow Templates in Compliance 360 Version 2018 Workflow Templates 5 Workflow Elements 6 Workflow Teams 6 Workflow Template Changes 6 Create or Edit a Workflow Template 8 Import and Export Workflow Templates
RMU-IT-SEC-01 Acceptable Use Policy
 1.0 Purpose 2.0 Scope 2.1 Your Rights and Responsibilities 3.0 Policy 3.1 Acceptable Use 3.2 Fair Share of Resources 3.3 Adherence with Federal, State, and Local Laws 3.4 Other Inappropriate Activities
1.0 Purpose 2.0 Scope 2.1 Your Rights and Responsibilities 3.0 Policy 3.1 Acceptable Use 3.2 Fair Share of Resources 3.3 Adherence with Federal, State, and Local Laws 3.4 Other Inappropriate Activities
The Guide. A basic guide for setting up your Samanage application
 The Guide A basic guide for setting up your Samanage application Table of Contents Introduction.............................................................. 3 Contacting Samanage for Assistance.........................................
The Guide A basic guide for setting up your Samanage application Table of Contents Introduction.............................................................. 3 Contacting Samanage for Assistance.........................................
BBVA Compass Spend Net Payables
 User Guide BBVA Compass Spend Net Payables User Guide Vault Services Table of Contents Introduction 2 Technical Requirements 2 Getting started 3 Sign In 3 General Navigation 4 Upload/Create Payment 5
User Guide BBVA Compass Spend Net Payables User Guide Vault Services Table of Contents Introduction 2 Technical Requirements 2 Getting started 3 Sign In 3 General Navigation 4 Upload/Create Payment 5
YourStore A GUIDE TO
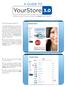 A GUIDE TO YourStore 3.0 Selling contact lenses online has never been easier! This is the homepage of YourStore 3.0. 1. The header displays just your company name as its default. The rectangular space
A GUIDE TO YourStore 3.0 Selling contact lenses online has never been easier! This is the homepage of YourStore 3.0. 1. The header displays just your company name as its default. The rectangular space
Adopter s Site Support Guide
 Adopter s Site Support Guide Provincial Client Registry Services Version: 1.0 Copyright Notice Copyright 2016, ehealth Ontario All rights reserved No part of this document may be reproduced in any form,
Adopter s Site Support Guide Provincial Client Registry Services Version: 1.0 Copyright Notice Copyright 2016, ehealth Ontario All rights reserved No part of this document may be reproduced in any form,
Privacy Policy Effective May 25 th 2018
 Privacy Policy Effective May 25 th 2018 1. General Information 1.1 This policy ( Privacy Policy ) explains what information Safety Management Systems, 2. Scope Inc. and its subsidiaries ( SMS ), it s brand
Privacy Policy Effective May 25 th 2018 1. General Information 1.1 This policy ( Privacy Policy ) explains what information Safety Management Systems, 2. Scope Inc. and its subsidiaries ( SMS ), it s brand
UNIVERSITY OF MASSACHUSETTS AMHERST INFORMATION SECURITY POLICY September 20, 2017
 UNIVERSITY OF MASSACHUSETTS AMHERST INFORMATION SECURITY POLICY September 20, 2017 I. Introduction Institutional information, research data, and information technology (IT) resources are critical assets
UNIVERSITY OF MASSACHUSETTS AMHERST INFORMATION SECURITY POLICY September 20, 2017 I. Introduction Institutional information, research data, and information technology (IT) resources are critical assets
Emergency Nurses Association Privacy Policy
 Emergency Nurses Association Privacy Policy The Emergency Nurses Association ( ENA, we, or us ) has created and posted this privacy policy in an effort to maintain efficient service while respecting your
Emergency Nurses Association Privacy Policy The Emergency Nurses Association ( ENA, we, or us ) has created and posted this privacy policy in an effort to maintain efficient service while respecting your
Cell Phone Policy. 1. Purpose: Establish a policy for cell phone use and compensation allowance.
 Cell Phone Policy 1. Purpose: Establish a policy for cell phone use and compensation allowance. 2. Authority: The Clinton County Board of Commissioners. 3. Application: This Cell Phone Policy (the Policy)
Cell Phone Policy 1. Purpose: Establish a policy for cell phone use and compensation allowance. 2. Authority: The Clinton County Board of Commissioners. 3. Application: This Cell Phone Policy (the Policy)
Oracle Data Cloud ( ODC ) Inbound Security Policies
 Oracle Data Cloud ( ODC ) Inbound Security Policies Contents Contents... 1 Overview... 2 Oracle Data Cloud Security Policy... 2 Oracle Information Security Practices - General... 2 Security Standards...
Oracle Data Cloud ( ODC ) Inbound Security Policies Contents Contents... 1 Overview... 2 Oracle Data Cloud Security Policy... 2 Oracle Information Security Practices - General... 2 Security Standards...
Overview Bank IT examination perspective Background information Elements of a sound plan Customer notifications
 Gramm-Leach Bliley Act Section 501(b) and Customer Notification Roger Pittman Director of Operations Risk Federal Reserve Bank of Atlanta Overview Bank IT examination perspective Background information
Gramm-Leach Bliley Act Section 501(b) and Customer Notification Roger Pittman Director of Operations Risk Federal Reserve Bank of Atlanta Overview Bank IT examination perspective Background information
CORPORATE GLOBAL ROAMING PRODUCT SPECIFICATION
 CORPORATE GLOBAL ROAMING PRODUCT SPECIFICATION 1. INTRODUCTION This document contains information on the Corporate Global Roaming service. If you require more detailed technical information, please contact
CORPORATE GLOBAL ROAMING PRODUCT SPECIFICATION 1. INTRODUCTION This document contains information on the Corporate Global Roaming service. If you require more detailed technical information, please contact
ORA HIPAA Security. All Affiliate Research Policy Subject: HIPAA Security File Under: For Researchers
 All Affiliate Research Policy Subject: HIPAA File Under: For Researchers ORA HIPAA Issuing Department: Office of Research Administration Original Policy Date Page 1 of 5 Approved by: May 9,2005 Revision
All Affiliate Research Policy Subject: HIPAA File Under: For Researchers ORA HIPAA Issuing Department: Office of Research Administration Original Policy Date Page 1 of 5 Approved by: May 9,2005 Revision
Agreements & Contracts: Electronic Documents User Agreement CUSTOMER SERVICE SKOWHEGAN SAVINGS
 Agreements & Contracts: Electronic Documents User Agreement CUSTOMER SERVICE SKOWHEGAN SAVINGS 800.303.9511 CUSTSERV@SKOWSAVINGS.COM TABLE OF CONTENTS ELECTRONIC DELIVERY OF DOCUMENTS...3 SYSTEM REQUIREMENTS...3
Agreements & Contracts: Electronic Documents User Agreement CUSTOMER SERVICE SKOWHEGAN SAVINGS 800.303.9511 CUSTSERV@SKOWSAVINGS.COM TABLE OF CONTENTS ELECTRONIC DELIVERY OF DOCUMENTS...3 SYSTEM REQUIREMENTS...3
First Federal Savings Bank of Mascoutah, IL Agreement and Disclosures
 Agreement and Disclosures INTERNET BANKING TERMS AND CONDITIONS AGREEMENT This Agreement describes your rights and obligations as a user of the Online Banking Service and all other services made available
Agreement and Disclosures INTERNET BANKING TERMS AND CONDITIONS AGREEMENT This Agreement describes your rights and obligations as a user of the Online Banking Service and all other services made available
IBM emessage Version 9 Release 1 February 13, User's Guide
 IBM emessage Version 9 Release 1 February 13, 2015 User's Guide Note Before using this information and the product it supports, read the information in Notices on page 471. This edition applies to version
IBM emessage Version 9 Release 1 February 13, 2015 User's Guide Note Before using this information and the product it supports, read the information in Notices on page 471. This edition applies to version
RFP/RFI Questions for Managed Security Services. Sample MSSP RFP Template
 RFP/RFI Questions for Managed Security Services Sample MSSP RFP Template Table of Contents Request for Proposal Template Overview 1 Introduction... 1 How to Use this Document... 1 Suggested RFP Outline
RFP/RFI Questions for Managed Security Services Sample MSSP RFP Template Table of Contents Request for Proposal Template Overview 1 Introduction... 1 How to Use this Document... 1 Suggested RFP Outline
etrac Company Documents Guide
 etrac Company Documents Guide Version: 5.0 Publish Date: 01/16/2019 Global DMS, 1555 Bustard Road, Suite 300, Lansdale, PA 19446 2019, All Rights Reserved. Table of Contents Introduction to etrac Company
etrac Company Documents Guide Version: 5.0 Publish Date: 01/16/2019 Global DMS, 1555 Bustard Road, Suite 300, Lansdale, PA 19446 2019, All Rights Reserved. Table of Contents Introduction to etrac Company
ISO/IEC Solution Brief ISO/IEC EventTracker 8815 Centre Park Drive, Columbia MD 21045
 Solution Brief 8815 Centre Park Drive, Columbia MD 21045 About delivers business critical software and services that transform high-volume cryptic log data into actionable, prioritized intelligence that
Solution Brief 8815 Centre Park Drive, Columbia MD 21045 About delivers business critical software and services that transform high-volume cryptic log data into actionable, prioritized intelligence that
IBM Hosted Application Security Services - Pre-Production Application Scanning
 IBM Hosted Application Security Services - Pre-Production Application Scanning FR_INTC-8839-02 2-2012 Page 1 of 21 Table of Contents IBM Hosted Application Security Services -...1 Pre-Production Application
IBM Hosted Application Security Services - Pre-Production Application Scanning FR_INTC-8839-02 2-2012 Page 1 of 21 Table of Contents IBM Hosted Application Security Services -...1 Pre-Production Application
TERMS OF USE Effective Date: January 1, 2015 To review material modifications and their effective dates scroll to the bottom of the page. 1.Parties.
 TERMS OF USE Effective Date: January 1, 2015 To review material modifications and their effective dates scroll to the bottom of the page. 1.Parties. The parties to these Terms of Use are you, and the owner
TERMS OF USE Effective Date: January 1, 2015 To review material modifications and their effective dates scroll to the bottom of the page. 1.Parties. The parties to these Terms of Use are you, and the owner
IBM Sterling B2B Services File Transfer Service
 Service Description IBM Sterling B2B Services File Transfer Service This Service Description describes the Cloud Service IBM provides to Client. Client means the company and its authorized users and recipients
Service Description IBM Sterling B2B Services File Transfer Service This Service Description describes the Cloud Service IBM provides to Client. Client means the company and its authorized users and recipients
Avaya CMS Supervisor Reports
 Avaya CMS Supervisor Reports Release 16.1 June 2010 2010 Avaya Inc. All Rights Reserved. Notice While reasonable efforts were made to ensure that the information in this document was complete and accurate
Avaya CMS Supervisor Reports Release 16.1 June 2010 2010 Avaya Inc. All Rights Reserved. Notice While reasonable efforts were made to ensure that the information in this document was complete and accurate
Concur Getting Started QuickStart Guide. Concur Technologies Version 1.3
 Concur Technologies Version 1.3 January 23, 2017 Page 1 Document Revision History Date Description Version Author 05/12/2016 11/30/2016 converted to new template updated proprietary statement 1.2 Concur
Concur Technologies Version 1.3 January 23, 2017 Page 1 Document Revision History Date Description Version Author 05/12/2016 11/30/2016 converted to new template updated proprietary statement 1.2 Concur
Policy Manager in Compliance 360 Version 2018
 Policy Manager in Compliance 360 Version 2018 Policy Manager Overview 3 Create a Policy 4 Relate a Policy to Other Policies, Departments, and Incidents 8 Edit a Policy 10 Edit a Policy by Using the Edit
Policy Manager in Compliance 360 Version 2018 Policy Manager Overview 3 Create a Policy 4 Relate a Policy to Other Policies, Departments, and Incidents 8 Edit a Policy 10 Edit a Policy by Using the Edit
ResWare Features. Adeptive Software 5370 Manhattan Circle, Suite 200 Boulder, Colorado
 ResWare Features Adeptive Softwareʼs flagship product, ResWare, is a revolutionary real estate transaction management system. More and more of the industryʼs leading companies are choosing ResWare. See
ResWare Features Adeptive Softwareʼs flagship product, ResWare, is a revolutionary real estate transaction management system. More and more of the industryʼs leading companies are choosing ResWare. See
IP Office Release 7.0 IP Office Essential Edition - Quick Version Embedded Voic User Guide
 IP Office Essential Edition - Quick Version Embedded Voicemail User Guide 15-604067 Issue 09a - (21 February 2011) 2011 AVAYA All Rights Reserved. Notices While reasonable efforts have been made to ensure
IP Office Essential Edition - Quick Version Embedded Voicemail User Guide 15-604067 Issue 09a - (21 February 2011) 2011 AVAYA All Rights Reserved. Notices While reasonable efforts have been made to ensure
Therapy Provider Portal. User Guide
 Therapy Provider Portal User Guide Page 2 of 16 UCare User Guide V1.7 Table of Contents I. Introduction...3 About HSM Therapy Management... 4 Terms of Use... 4 Contact Information... 6 II. Using the Therapy
Therapy Provider Portal User Guide Page 2 of 16 UCare User Guide V1.7 Table of Contents I. Introduction...3 About HSM Therapy Management... 4 Terms of Use... 4 Contact Information... 6 II. Using the Therapy
Washington State Emergency Management Association (WSEMA) Olympia, WA
 Washington State Emergency Management Association (WSEMA) Olympia, WA Request for Proposals Website Redesign and Content Management and Maintenance System Proposal Submittal Deadline: I. Introduction and
Washington State Emergency Management Association (WSEMA) Olympia, WA Request for Proposals Website Redesign and Content Management and Maintenance System Proposal Submittal Deadline: I. Introduction and
Sourcing Buyer User Guide
 Sourcing Buyer User Guide Version 6.4 August 2011 Copyright 2002-2011 Ion Wave Technologies, Inc. Springfield, Missouri Welcome to Enterprise Sourcing! This manual is intended to provide buyers an instructional
Sourcing Buyer User Guide Version 6.4 August 2011 Copyright 2002-2011 Ion Wave Technologies, Inc. Springfield, Missouri Welcome to Enterprise Sourcing! This manual is intended to provide buyers an instructional
Avaya Aura Contact Center Documentation Roadmap
 Documentation Roadmap Release 6.3 NN44400-113 Issue 04.02 May 2013 2013 Avaya Inc. All Rights Reserved. Notice While reasonable efforts have been made to ensure that the information in this document is
Documentation Roadmap Release 6.3 NN44400-113 Issue 04.02 May 2013 2013 Avaya Inc. All Rights Reserved. Notice While reasonable efforts have been made to ensure that the information in this document is
Page 1 of 15. Applicability. Compatibility EACMS PACS. Version 5. Version 3 PCA EAP. ERC NO ERC Low Impact BES. ERC Medium Impact BES
 002 5 R1. Each Responsible Entity shall implement a process that considers each of the following assets for purposes of parts 1.1 through 1.3: i. Control Centers and backup Control Centers; ii. Transmission
002 5 R1. Each Responsible Entity shall implement a process that considers each of the following assets for purposes of parts 1.1 through 1.3: i. Control Centers and backup Control Centers; ii. Transmission
IBM Resilient Incident Response Platform On Cloud
 Service Description IBM Resilient Incident Response Platform On Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means the contracting party and its authorized
Service Description IBM Resilient Incident Response Platform On Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means the contracting party and its authorized
PGTelco Internet TERMS OF SERVICE AND ACCEPTABLE USE POLICIES
 PGTelco Internet TERMS OF SERVICE AND ACCEPTABLE USE POLICIES Thank you for choosing a PGTelco Internet as your internet service provider. PGTelco Internet is an affiliate of The Prairie Grove Telephone
PGTelco Internet TERMS OF SERVICE AND ACCEPTABLE USE POLICIES Thank you for choosing a PGTelco Internet as your internet service provider. PGTelco Internet is an affiliate of The Prairie Grove Telephone
BCN Telecom, Inc. Customer Proprietary Network Information Certification Accompanying Statement
 BCN Telecom, Inc. Customer Proprietary Network Information Certification Accompanying Statement BCN TELECOM, INC. ( BCN" or "Company") has established practices and procedures adequate to ensure compliance
BCN Telecom, Inc. Customer Proprietary Network Information Certification Accompanying Statement BCN TELECOM, INC. ( BCN" or "Company") has established practices and procedures adequate to ensure compliance
Information Technology General Control Review
 Information Technology General Control Review David L. Shissler, Senior IT Auditor, CPA, CISA, CISSP Office of Internal Audit and Risk Assessment September 15, 2016 Background Presenter Senior IT Auditor
Information Technology General Control Review David L. Shissler, Senior IT Auditor, CPA, CISA, CISSP Office of Internal Audit and Risk Assessment September 15, 2016 Background Presenter Senior IT Auditor
Security Annex for Firewalls Additional Terms for Firewall Service
 CONTENTS 1 Glossary of Terms & Definitions... 2 2 Service Description... 2 2.1 Firewall Service... 2 2.2 Provisioning... 2 3 Firewall throughput... 3 4 Vendor Change... 3 5 Charges... 3 5.1 Charges payable
CONTENTS 1 Glossary of Terms & Definitions... 2 2 Service Description... 2 2.1 Firewall Service... 2 2.2 Provisioning... 2 3 Firewall throughput... 3 4 Vendor Change... 3 5 Charges... 3 5.1 Charges payable
Registration Agreement
 Registration Agreement Grove Technologies, LLC, doing business as GroveSite ( GroveSite ), owns proprietary GroveSite software and related documentation, and operates the GroveSite Platform (as defined
Registration Agreement Grove Technologies, LLC, doing business as GroveSite ( GroveSite ), owns proprietary GroveSite software and related documentation, and operates the GroveSite Platform (as defined
12/05/2017. Customer Service Management
 12/05/2017 Contents...3 Get started with... 3 Activate Customer Service... 5 Set up associated entities... 6 Set up communication channels... 16 Track and analyze Customer Service case data... 40 Create
12/05/2017 Contents...3 Get started with... 3 Activate Customer Service... 5 Set up associated entities... 6 Set up communication channels... 16 Track and analyze Customer Service case data... 40 Create
Section 7 - Custom Calling Services
 A. TERMS AND CONDITIONS Custom Calling Services are offered only from select central offices where the Company has arranged the facilities for these services and are furnished subject to the availability
A. TERMS AND CONDITIONS Custom Calling Services are offered only from select central offices where the Company has arranged the facilities for these services and are furnished subject to the availability
ATTACHMENT A POLICES AND PROCEDURES REGARDING CELLULAR TELEPHONES AND MOBILE COMMUNICATION DEVICES
 ATTACHMENT A POLICES AND PROCEDURES REGARDING CELLULAR TELEPHONES AND MOBILE COMMUNICATION DEVICES 1. INTRODUCTION 1.1 The Office of Information Technology Services ( OITS ) has the responsibility of managing
ATTACHMENT A POLICES AND PROCEDURES REGARDING CELLULAR TELEPHONES AND MOBILE COMMUNICATION DEVICES 1. INTRODUCTION 1.1 The Office of Information Technology Services ( OITS ) has the responsibility of managing
IP Office Platform. Using Voic Pro in Intuity Mode Issue 10a - (16 January 2015)
 Using Voicemail Pro in Intuity Mode 15-601066 Issue 10a - (16 January 2015) 2015 AVAYA All Rights Reserved. Notice While reasonable efforts have been made to ensure that the information in this document
Using Voicemail Pro in Intuity Mode 15-601066 Issue 10a - (16 January 2015) 2015 AVAYA All Rights Reserved. Notice While reasonable efforts have been made to ensure that the information in this document
CINCINNATI BELL TELEPHONE COMPANY LLC Residence Service Agreement - Local Telephone Services Nonresidence Service Agreement - Local Telephone Services
 A. TERMS AND CONDITIONS Custom Calling Services are offered only from select central offices where the Company has arranged the facilities for these services and are furnished subject to the availability
A. TERMS AND CONDITIONS Custom Calling Services are offered only from select central offices where the Company has arranged the facilities for these services and are furnished subject to the availability
Electronic Network Acceptable Use Policy
 Electronic Network Acceptable Use Policy 2016-2017 www.timothychristian.com ELECTRONIC NETWORK ACCEPTABLE USE POLICY Electronic Network This Policy is intended to serve as a guide to the scope of TCS s
Electronic Network Acceptable Use Policy 2016-2017 www.timothychristian.com ELECTRONIC NETWORK ACCEPTABLE USE POLICY Electronic Network This Policy is intended to serve as a guide to the scope of TCS s
Avaya Communications Process Manager Release 2.2 Web Portal Help for Administrative Users
 Avaya Communications Process Manager Release 2.2 Web Portal Help for Administrative Users Document No. 04-601163 August 2008 Issue 10 2008 Avaya Inc. All Rights Reserved. Notice While reasonable efforts
Avaya Communications Process Manager Release 2.2 Web Portal Help for Administrative Users Document No. 04-601163 August 2008 Issue 10 2008 Avaya Inc. All Rights Reserved. Notice While reasonable efforts
12/05/2017. Geneva ServiceNow Security Management
 12/05/2017 Security Management Contents... 3 Security Incident Response...3 Security Incident Response overview... 3 Get started with Security Incident Response... 6 Security incident creation... 40 Security
12/05/2017 Security Management Contents... 3 Security Incident Response...3 Security Incident Response overview... 3 Get started with Security Incident Response... 6 Security incident creation... 40 Security
ISO27001 Preparing your business with Snare
 WHITEPAPER Complying with ISO27001 Preparing your business with Snare T he technical controls imposed by ISO (International Organisation for Standardization) Standard 27001 cover a wide range of security
WHITEPAPER Complying with ISO27001 Preparing your business with Snare T he technical controls imposed by ISO (International Organisation for Standardization) Standard 27001 cover a wide range of security
Congratulations Silver Boeing Performance Excellence Award recipient!
 Congratulations Silver Boeing Performance Excellence Award recipient! This BPEA congratulations package explains the actions required and guidelines to follow to ensure your company realizes the full benefits
Congratulations Silver Boeing Performance Excellence Award recipient! This BPEA congratulations package explains the actions required and guidelines to follow to ensure your company realizes the full benefits
Enterprise Voice SUBSCRIBER GUIDE
 Enterprise Voice SUBSCRIBER GUIDE Conterra Networks Enterprise Voice SUBSCRIBER GUIDE 3 TABLE OF CONTENTS Table of Contents Introduction... 6 Logging in... 6 Navigation Bar, Sub-Menu and Page Layout...
Enterprise Voice SUBSCRIBER GUIDE Conterra Networks Enterprise Voice SUBSCRIBER GUIDE 3 TABLE OF CONTENTS Table of Contents Introduction... 6 Logging in... 6 Navigation Bar, Sub-Menu and Page Layout...
IP Office. IP Office Mailbox Mode User Guide Issue 11b - (15 May 2010)
 Mailbox Mode User Guide 15-601131 Issue 11b - (15 May 2010) 2010 AVAYA All Rights Reserved. Notices While reasonable efforts have been made to ensure that the information in this document is complete and
Mailbox Mode User Guide 15-601131 Issue 11b - (15 May 2010) 2010 AVAYA All Rights Reserved. Notices While reasonable efforts have been made to ensure that the information in this document is complete and
BPS Suite and the OCEG Capability Model. Mapping the OCEG Capability Model to the BPS Suite s product capability.
 BPS Suite and the OCEG Capability Model Mapping the OCEG Capability Model to the BPS Suite s product capability. BPS Contents Introduction... 2 GRC activities... 2 BPS and the Capability Model for GRC...
BPS Suite and the OCEG Capability Model Mapping the OCEG Capability Model to the BPS Suite s product capability. BPS Contents Introduction... 2 GRC activities... 2 BPS and the Capability Model for GRC...
BT Compute Protect Schedule to the General Terms
 BT Compute Protect Schedule to the General Terms Contents A note on you... 2 Words defined in the General Terms... 2 Part A The BT Compute Protect Service... 2 1 Service Summary... 2 2 Standard Service
BT Compute Protect Schedule to the General Terms Contents A note on you... 2 Words defined in the General Terms... 2 Part A The BT Compute Protect Service... 2 1 Service Summary... 2 2 Standard Service
QuickGifts Merchant Gift Card Program User Guide Updated: March 12, 2013
 QuickGifts Merchant Gift Card Program User Guide Updated: March 12, 2013 The purpose of this user guide is to provide our Merchant Partners with general information and instructions related to QuickGifts
QuickGifts Merchant Gift Card Program User Guide Updated: March 12, 2013 The purpose of this user guide is to provide our Merchant Partners with general information and instructions related to QuickGifts
Implementing Avaya Flare Experience for Windows
 Implementing Avaya Flare Experience for Windows 18-604043 Issue 1 July 2012 2012 Avaya Inc. All Rights Reserved. Notice While reasonable efforts have been made to ensure that the information in this document
Implementing Avaya Flare Experience for Windows 18-604043 Issue 1 July 2012 2012 Avaya Inc. All Rights Reserved. Notice While reasonable efforts have been made to ensure that the information in this document
Velocify Admin The Velocify Admin tab has been re-designed to provide a much better user experience, focusing on selfservice
 Contents Velocify Admin... 3 Objects Supported by... 3 Full Support for Accounts and Contacts... 4 How do I enable and configure new objects in Velocify?... 4 How do I build my Sales Strategy with my newly
Contents Velocify Admin... 3 Objects Supported by... 3 Full Support for Accounts and Contacts... 4 How do I enable and configure new objects in Velocify?... 4 How do I build my Sales Strategy with my newly
Throughout this Data Use Notice, we use plain English summaries which are intended to give you guidance about what each section is about.
 By visiting and using The Training Hub and associated companies and affiliate s websites, mobile sites, and/or applications (together, the Site ), registering to use our services offered through the Site,
By visiting and using The Training Hub and associated companies and affiliate s websites, mobile sites, and/or applications (together, the Site ), registering to use our services offered through the Site,
Archiving Service Reports Guide
 Email Archiving Service Reports Guide This guide is for Compliance and IT administrators reporting on the Email Archiving service. Service Version: ArchivingP_3.5 2009-07-31 Copyrights This documentation
Email Archiving Service Reports Guide This guide is for Compliance and IT administrators reporting on the Email Archiving service. Service Version: ArchivingP_3.5 2009-07-31 Copyrights This documentation
User s Guide FICO Online Support
 FICO Online Support User s Guide User s Guide FICO Online Support www.fico.com Make every decision count This document is the confidential, unpublished property of Fair Isaac Corporation. Receipt or possession
FICO Online Support User s Guide User s Guide FICO Online Support www.fico.com Make every decision count This document is the confidential, unpublished property of Fair Isaac Corporation. Receipt or possession
UNIVERSITY OF MASSACHUSETTS AMHERST INFORMATION SECURITY POLICY October 25, 2017
 UNIVERSITY OF MASSACHUSETTS AMHERST INFORMATION SECURITY POLICY October 25, 2017 I. Introduction Institutional information, research data, and information technology (IT) resources are critical assets
UNIVERSITY OF MASSACHUSETTS AMHERST INFORMATION SECURITY POLICY October 25, 2017 I. Introduction Institutional information, research data, and information technology (IT) resources are critical assets
Subcontracted Delivery Policy
 Subcontracted Delivery Policy Main points of policy 1. Background to the policy 2. Scope of the Policy 3. Policy Statement 4. Reasons for subcontracting 5. BCA contribution to improving own and subcontractor
Subcontracted Delivery Policy Main points of policy 1. Background to the policy 2. Scope of the Policy 3. Policy Statement 4. Reasons for subcontracting 5. BCA contribution to improving own and subcontractor
01.0 Policy Responsibilities and Oversight
 Number 1.0 Policy Owner Information Security and Technology Policy Policy Responsibility & Oversight Effective 01/01/2014 Last Revision 12/30/2013 Department of Innovation and Technology 1. Policy Responsibilities
Number 1.0 Policy Owner Information Security and Technology Policy Policy Responsibility & Oversight Effective 01/01/2014 Last Revision 12/30/2013 Department of Innovation and Technology 1. Policy Responsibilities
Xerox PagePack Program FAQs & Troubleshooting Tips
 Table of Contents PagePack Registration 1 SCOT Tool 2 PagePack Assistant 3 PagePack Customer Portal 3 Meter Reads 4 Supplies 5 Training 9 Service 9 Leasing / Purchase 10 Sales 10 Billing 11 PagePack Contract
Table of Contents PagePack Registration 1 SCOT Tool 2 PagePack Assistant 3 PagePack Customer Portal 3 Meter Reads 4 Supplies 5 Training 9 Service 9 Leasing / Purchase 10 Sales 10 Billing 11 PagePack Contract
Service Description. IBM Aspera Files. 1. Cloud Service. 1.1 IBM Aspera Files Personal Edition. 1.2 IBM Aspera Files Business Edition
 Service Description IBM Aspera Files This Service Description describes the Cloud Service IBM provides to Client. Client means the company and its authorized users and recipients of the Cloud Service.
Service Description IBM Aspera Files This Service Description describes the Cloud Service IBM provides to Client. Client means the company and its authorized users and recipients of the Cloud Service.
Customer Relationship Management Software Version 1.0
 Customer Relationship Management Software Version 1.0 Administrator Guide Guide Version 1.0.111218 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to CRM...5
Customer Relationship Management Software Version 1.0 Administrator Guide Guide Version 1.0.111218 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. Introduction to CRM...5
Request for Proposals for Data Assessment and Analysis
 Request for Proposals for Data Assessment and Analysis Introduction The Center for NYC Neighborhoods requires the services of a consultant to create a data architecture with the overall goal of assessing
Request for Proposals for Data Assessment and Analysis Introduction The Center for NYC Neighborhoods requires the services of a consultant to create a data architecture with the overall goal of assessing
Settings & Notifications
 Settings & Notifications CMS Settings Content Requirements Distributor Access Customs Folders DAL Settings Media Gallery Notifications NOTE: Some functions may not be available to all users depending on
Settings & Notifications CMS Settings Content Requirements Distributor Access Customs Folders DAL Settings Media Gallery Notifications NOTE: Some functions may not be available to all users depending on
Terms and Conditions between Easy Time Clock, Inc. And Easy Time Clock Client
 Terms and Conditions between Easy Time Clock, Inc. And Easy Time Clock Client Client s Responsibility Easy Time Clock, Inc. ( ETC ) is a client-led time and attendance program. The Client is solely responsible
Terms and Conditions between Easy Time Clock, Inc. And Easy Time Clock Client Client s Responsibility Easy Time Clock, Inc. ( ETC ) is a client-led time and attendance program. The Client is solely responsible
ADVANCED CUSTOMER SERVICES ORACLE TRANSITION SERVICE EXHIBIT
 ADVANCED CUSTOMER SERVICES ORACLE TRANSITION SERVICE EXHIBIT This exhibit incorporates by reference the terms of the order for Oracle Transition Service. A. Description of Services. i. If Your order contains
ADVANCED CUSTOMER SERVICES ORACLE TRANSITION SERVICE EXHIBIT This exhibit incorporates by reference the terms of the order for Oracle Transition Service. A. Description of Services. i. If Your order contains
Upgrading the Procura Database
 Procura Health Management Systems Contact Procura Corporate Office 600-1112 Fort Street, Victoria, BC, Canada V8V 3K8 Phone: 1.877.776.2872 FAX: 250.380.1866 support@goprocura.com Software version Procura
Procura Health Management Systems Contact Procura Corporate Office 600-1112 Fort Street, Victoria, BC, Canada V8V 3K8 Phone: 1.877.776.2872 FAX: 250.380.1866 support@goprocura.com Software version Procura
Avaya Callback Assist Release Notes
 Avaya Callback Assist Release Notes Release 4.1.6 May 2014 2014 Avaya Inc. All Rights Reserved. Notice While reasonable efforts were made to ensure that the information in this document was complete and
Avaya Callback Assist Release Notes Release 4.1.6 May 2014 2014 Avaya Inc. All Rights Reserved. Notice While reasonable efforts were made to ensure that the information in this document was complete and
Virginia State University Policies Manual. Title: Information Security Program Policy: 6110
 Purpose Virginia State University (VSU) uses information to perform the business services and functions necessary to fulfill its mission. VSU information is contained in many different mediums including
Purpose Virginia State University (VSU) uses information to perform the business services and functions necessary to fulfill its mission. VSU information is contained in many different mediums including
ENTERPRISE SUBSCRIBER GUIDE
 ENTERPRISE SUBSCRIBER GUIDE Enterprise Subscriber Guide 880 Montclair Road Suite 400 Birmingham, AL 353 www. TABLE OF CONTENTS Table of Contents Introduction...6 Logging In...6 Navigation Bar, Sub-Menu
ENTERPRISE SUBSCRIBER GUIDE Enterprise Subscriber Guide 880 Montclair Road Suite 400 Birmingham, AL 353 www. TABLE OF CONTENTS Table of Contents Introduction...6 Logging In...6 Navigation Bar, Sub-Menu
Spree Privacy Policy
 Spree Privacy Policy Effective as at 21 November 2018 Introduction Spree respects your privacy and it is important to us that you have an enjoyable experience buying and selling with us but also that you
Spree Privacy Policy Effective as at 21 November 2018 Introduction Spree respects your privacy and it is important to us that you have an enjoyable experience buying and selling with us but also that you
IP Office Release 9.0
 Embedded Voicemail User Guide (IP Office Mode) 15-604067 Issue 13a - (13 February 2014) 2014 AVAYA All Rights Reserved. Notice While reasonable efforts have been made to ensure that the information in
Embedded Voicemail User Guide (IP Office Mode) 15-604067 Issue 13a - (13 February 2014) 2014 AVAYA All Rights Reserved. Notice While reasonable efforts have been made to ensure that the information in
It s Me 247 Bill Pay (Payveris)
 It s Me 247 Bill Pay (Payveris) Product Overview & User Guide INTRODUCTION CU*Answers is proud to offer a native bill pay service through a relationship with Payveris. Bill payment via It s Me 247 Bill
It s Me 247 Bill Pay (Payveris) Product Overview & User Guide INTRODUCTION CU*Answers is proud to offer a native bill pay service through a relationship with Payveris. Bill payment via It s Me 247 Bill
AT&T IP Flexible Reach Department Administrator Guide
 AT&T IP Flexible Reach Department Administrator Guide 1 Contents Get Started... 5 Log In... 6 What a Department Administrator Can Do... 8 About Premier... 11 Use Premier... 12 Use the AT&T IP Flexible
AT&T IP Flexible Reach Department Administrator Guide 1 Contents Get Started... 5 Log In... 6 What a Department Administrator Can Do... 8 About Premier... 11 Use Premier... 12 Use the AT&T IP Flexible
Secure Messaging Mobile App Privacy Policy. Privacy Policy Highlights
 Secure Messaging Mobile App Privacy Policy Privacy Policy Highlights For ease of review, Everbridge provides these Privacy Policy highlights, which cover certain aspects of our Privacy Policy. Please review
Secure Messaging Mobile App Privacy Policy Privacy Policy Highlights For ease of review, Everbridge provides these Privacy Policy highlights, which cover certain aspects of our Privacy Policy. Please review
IP Office. Embedded Voic User Guide (IP Office Mode) Issue 12a (26 February 2013)
 Embedded Voicemail User Guide (IP Office Mode) 15-604067 Issue 12a (26 February 2013) 2013 AVAYA All Rights Reserved. Notice While reasonable efforts have been made to ensure that the information in this
Embedded Voicemail User Guide (IP Office Mode) 15-604067 Issue 12a (26 February 2013) 2013 AVAYA All Rights Reserved. Notice While reasonable efforts have been made to ensure that the information in this
M&T SupplierPay Supplier
 M&T SupplierPay Supplier USER GUIDE For informational purposes only, not considered an advertisement. With M&T SupplierPay, you receive payments from your customer by charging the purchase to a virtual
M&T SupplierPay Supplier USER GUIDE For informational purposes only, not considered an advertisement. With M&T SupplierPay, you receive payments from your customer by charging the purchase to a virtual
RIGHTNOW OSA COMPLEXITY MATRIX
 RIGHTNOW OSA COMPLEITY MATRI This document outlines RightNow Professional Services Outsourced Solution Administrations tasks that may be completed in a RightNow application. It also defines the risk level
RIGHTNOW OSA COMPLEITY MATRI This document outlines RightNow Professional Services Outsourced Solution Administrations tasks that may be completed in a RightNow application. It also defines the risk level
