NATIONAL SENIOR CERTIFICATE GRADE 12
|
|
|
- Calvin O’Connor’
- 5 years ago
- Views:
Transcription
1 NTIONL SENIOR ERTIFITE GRE 12 OMPUTER PPLITIONS TEHNOLOGY P2 (THEORY) NOVEMER 2011 MRKS: 150 TIME: 3 hours This question paper consists of 16 pages.
2 omputer pplications Technology/P2 2 E/November 2011 INSTRUTIONS N INFORMTION This question paper consists of SETION and SETION. nswer LL the questions. Number the answers correctly according to the numbering system used in this question paper. Start EH question on a NEW page. o NOT write in the right-hand margin. Leave a line between each subquestion.
3 omputer pplications Technology/P2 3 E/November 2011 SETION QUESTION 1: MTHING ITEMS hoose a term/concept from OLUMN that matches a description in OLUMN. Write only the letter ( R) next to the question number ( ) in the NSWER OOK, for example 1.11 S. 1.1 OLUMN component that determines the quality of the display on the screen OLUMN NI (network interface card) disk defragmenter 1.2 utility program that will speed up disk access by rearranging the contents of a hard disk malware switch/hub device that protects your computer against power dips The main memory of the computer E F G PU lu-ray router Software that secretly monitors activity on a computer central node where all the computers on a network plug in H I J disk clean-up spyware RM 1.7 The component in your computer that allows you to connect the computer to a network K L graphics/video card shareware 1.8 term used to describe high-speed connections to the Internet M N power supply memory card The group or class of software that is specifically created to protect against detrimental or harmful influences type of V technology O P Q R HMI broadband power bus UPS (10 x 1) [10]
4 omputer pplications Technology/P2 4 E/November 2011 QUESTION 2: MULTIPLE-HOIE QUESTIONS Various options are provided as possible answers to the following questions. hoose the answer and write only the letter ( ) next to the question number ( ) in the NSWER OOK, for example 2.11 E. 2.1 Which ONE of the following components is the least important in terms of the functioning of a computer? Memory Hard disk Processor V-writer 2.2 Which ONE of the following statements about good password practice or policy is FLSE? Passwords should be changed frequently. It is better to use the same password for every situation that requires one. Your identity number is not a good example of a secure password. Never tell other people what your password is. 2.3 Which ONE of the following is the best option to choose if you think the web page you are viewing, is outdated (old)? hange to a different ISP Update your antivirus software Refresh the web page hange to a 3G connection 2.4 Which ONE of the following options would be the most effective device for inputting large quantities of numbers? virtual keyboard numeric keypad mouse calculator program 2.5 Which ONE of the following components should be upgraded to allow more programs and data to be simultaneously loaded into memory? RM ROM PU Hard drive
5 omputer pplications Technology/P2 5 E/November Which ONE of the following refers to software that is designed to fix bugs (errors) and provide new features for existing software? Updates rivers Virus definitions Wizards 2.7 Which ONE of the following refers to the use of material and sources without acknowledging them? ata theft Identity theft Piracy Plagiarism 2.8 Which ONE of the following ports is the best to use to transfer videos from a digital video camera to a P? VG HMI FireWire US 2.9 Which ONE of the following can you use to decrease the size of a large document to be ed? WinZip Paint Snipping Tool Screenshot 2.10 Which ONE of the following statements about a firewall is TRUE? firewall is not needed if you have an Internet connection. firewall monitors communication between your computer and the Internet. Firewall software must be updated daily. firewall will prevent software piracy. (10 x 1) TOTL SETION : [10] 20
6 omputer pplications Technology/P2 6 E/November 2011 SETION The scenario below sets the scene for the questions that follow. SENRIO team of omputer pplications Technology (T) learners have decided to work at a cyber café to raise funds for their school. They will be required to answer computer-related questions for the owner, Mr Wu. QUESTION 3 The first task is to replace the old administration computer. Mr Wu saw the following advertisement for a laptop: 21" LPTOP Processor: RM: Hard drive: onnectivity: Intel eleron 1.8 Hz 4 G 150 G WLN/LN ual-layer V writer Integrated webcam Windows 7 Professional Multidata card reader 12 month on-site warranty 3.1 The reason why the old administration computer has to be replaced is that it often crashes. Give TWO reasons why a computer would crash. (2) 3.2 Name TWO hardware components from the advertisement above that will play a significant role in determining the overall performance of this computer. (2) 3.3 State TWO advantages of purchasing a laptop computer rather than a desktop computer. (2)
7 omputer pplications Technology/P2 7 E/November Mr Wu wants to experiment with video editing using the laptop. Name TWO hardware components from the advertisement where the specifications are not suitable for video editing. riefly motivate the use of each hardware component in the context of video editing. (4) 3.5 Many of the devices that can be connected to the laptop connect via US ports and are therefore plug-and-play. What do we mean when we say a device is plug-and-play? (2) 3.6 The V drive is listed as a 'dual-layer' drive. How could Mr Wu benefit from a dual-layer drive? (1) 3.7 Explain the function of the card reader listed in the advertisement. (2) 3.8 The advertisement for the laptop lists an 'integrated webcam' riefly explain what the term integrated means in this context. (1) State ONE advantage of having an integrated webcam on a laptop. (1) Mr Wu used Skype to contact his cousin in Taiwan. Mr Wu complained that his cap soon 'disappeared' when he used the webcam during the Skype session. Explain why this happened by referring to the concept of a cap in your answer. (4) Mr Wu thinks it would be a good idea to have webcams installed in the cyber café for surveillance purposes. Give ONE reason why some customers could consider this practice unethical. (1) 3.9 The advert refers to an 'on-site warranty'. Explain what an on-site warranty means. (2) 3.10 Mr Wu is considering purchasing an external hard drive to backup the data on his new administration computer. State TWO advantages of using an external hard drive for backup copies. (2)
8 omputer pplications Technology/P2 8 E/November Mr Wu connected a printer to his laptop to print his accounts but then experienced some problems with his printing. The first problem was a message that appeared, that said that a printer driver could not be found riefly explain what a driver is by referring to its function. (2) Suggest TWO places where Mr Wu can try and find this driver. (2) The problem with the driver was successfully sorted out. However, Mr Wu found that the printer did not print any hard copies and no error message appeared when he tried to print. Give TWO possible reasons for this. (2) 3.12 number of customers are visually impaired and struggle to use the computers in the cyber café. Name TWO utilities or features of the operating system that can be used to try and help these customers to use the computers more easily. (2) [34]
9 omputer pplications Technology/P2 9 E/November 2011 QUESTION Mr Wu cannot understand why a computer needs an operating system and application programs Name THREE functions of an operating system. (3) State TWO advantages of using an office suite rather than the individual programs available. (2) 4.2 Give ONE reason why many people still use proprietary software such as Microsoft Office instead of an open-source software package, such as OpenOffice, which is free. (1) 4.3 Mr Wu says that there are too many programs on his computer and decides to remove some. Give TWO reasons why a program should be uninstalled rather than just deleted. (2) 4.4 Mr Wu finds that his computer has suddenly become slower. Name TWO instances where, or reasons why, software might cause a computer to become slower. (2) 4.5 Mr Wu is concerned about computer virus infections in the cyber café Explain TWO ways in which customers can infect the cyber café's computers with viruses. (2) Name THREE possible ways in which Mr Wu would know if any of the computers have been infected with viruses. (3) Mr Wu says that he will scan the computers for viruses once a month. Give TWO reasons why this will not be a good policy to follow. (2) 4.6 Name TWO computer housekeeping tasks or good maintenance habits, besides the regular updating of security software, that Mr Wu should carry out regularly. (2) 4.7 Mr Wu has heard of a single-user license, multi-user license and a site license. He feels that single-user licenses would be too costly for his purposes. riefly explain the difference between a multi-user license and a site license. (2) [21]
10 omputer pplications Technology/P2 10 E/November 2011 QUESTION The T learners noticed that all the computers in Mr Wu's cyber café are linked to a network There are a number of benefits having a network. What would the most important reason be for having a network, specifically in a cyber café? riefly motivate your answer. (2) Would the network in the cyber café be an example of a LN or a WN? riefly motivate your answer. (2) iscuss TWO possible disadvantages of establishing and running a network in the cyber café. (2) 5.2 The cyber café has a hotspot. Explain what a hotspot is. (2) 5.3 State TWO ways in which Mr Wu can, in terms of his business, help to bridge or reduce the digital divide. (2) 5.4 Mr Wu would like to order supplies for his cyber café over the Internet and have them delivered to the shop. He would also like to do his banking over the Internet What is the general term used to describe doing business over the Internet? (1) Name ONE way in which he would know that he is using a secure connection to his Internet banking website. (1) State THREE advantages of Internet banking when compared with conventional banking. (3) 5.5 The cyber café is in Johannesburg. One of the customers urgently wants to send a document of 20 G to somebody in ape Town. He does not want to use or pay a courier service. Explain how this can be done over the Internet. The service cannot be used as it has a 5 M limit for attachments. (1) 5.6 Mr Wu has read about RSS feeds offered by websites. escribe clearly how RSS feeds can make a user's life that much easier. (2)
11 omputer pplications Technology/P2 11 E/November lot of young people use the Internet facilities at Mr Wu's cyber café. They often use Facebook and Twitter What is a tweet? (2) Give TWO reasons why many schools and companies block sites such as Facebook. (2) [22]
12 omputer pplications Technology/P2 12 E/November 2011 QUESTION Mr Wu would like to be able to assist people when they send s from his cyber café. Name THREE netiquette rules to keep in mind when adding and sending attachments. (3) 6.2 onsider the following address: abcgenius@bluecross.org.za Identify the user name in the address above. (1) What does the.org.za part of the address indicate? (2) 6.3 iscuss the differences between a web browser and a search engine. (o not give the names of web browsers or search engines in your answer). (4) 6.4 onsider the following To PWu2@webmail.co.za c cc Subject: Savings ank of ttach: Good day Sir Your bank account has had multiple access attempts. Please click on the address below to reset your password and gain access to your account. Yours faithfully Jonass ank Manager ity ranch Explain what the difference is between the c field and cc field in an . (2) Name TWO ways in which the amount of spam received at the cyber café can be reduced. (2)
13 omputer pplications Technology/P2 13 E/November RFI tags are becoming commonplace riefly explain what an RFI tag is. o not simply write down what the abbreviation stands for. (2) State ONE application of RFI tags in the cyber café environment. (1) 6.6 Mr Wu is concerned about paying high electricity accounts for the cyber café. escribe TWO ways, related to the use of the computers in the cyber café, in which electricity can be saved. (2) 6.7 Mr Wu needs to replace broken computer equipment Explain why the broken computers should not be thrown away on rubbish dumps. (2) Write down the collective name used for broken, discarded or unwanted electronic hardware. (1) 6.8 The Internet provides a host of communication modes and methods What is the main benefit of using VoIP technology like Skype? (1) State TWO disadvantages when using a chatroom or instant messaging technologies to stay in contact with friends. (2) 6.9 Mr Wu says that when he searched for information on the Internet about other types of coffee, a very large number of results were displayed. Name TWO ways in which he could reduce unnecessary results and obtain a shorter list of more relevant information. (2) [27]
14 omputer pplications Technology/P2 14 E/November 2011 QUESTION Mr Wu wants to help some people to improve their word processing skills. Help him to answer their questions One person says that a word processing document that he has sent to a friend, cannot be opened by the friend as they do not have the same program. What is the best file format to save the document in so that it can be opened and edited using most word processors? (1) Give TWO reasons why one would make use of footnotes or endnotes. (2) What word processing feature should be used to allow both portrait- and landscape-orientated pages in the same document? (1) Give Mr Wu TWO reasons why some documents are distributed in PF format. (2) 7.2 One of the learners was trying to help Mr Wu with a spreadsheet. Study the screenshot of the spreadsheet below. E F G 6 Percentage 10% 7 Name Rate Hours onus Fees Total Statistics 8 eth Ruby #VLUE! James #NME? 11 Sharney #VLUE! lessing Happiness #VLUE! 7 14 Julie #IV/0? Name TWO ways in which to change the appearance of the spreadsheet above so that it is easier to read and more meaningful to Mr Wu. (2) How can Mr Wu prevent column E from showing in his spreadsheet (without deleting the data)? (1) State TWO possible causes for the error message that displays in cell G10 as #NME, as shown in the screenshot. (2) State ONE possible cause for the error message that displays in cell G14 as #IV/0!, as shown in the screenshot. (1)
15 omputer pplications Technology/P2 15 E/November Name the function that could be used to find the number appearing most often in a column. (1) The value in cell F8 is calculated by using the formula =E8*F6. When this formula is copied down to the rest of the column, error messages and incorrect values appear in column F. Suggest ONE way of solving this problem. (1) Which function could be used to work out how many numbers in column are greater than 15? (1) 7.3 database table with I, Term and Explanation columns appears as follows: I Term Explanation W1 Windows Server 2003 n operating system for servers W2 Symbian n operating system for a mobile device W3 ndroid n operating system for a mobile device W4 Windows NT server n operating system for servers W5 Windows NT workstation n operating system for workstations W6 Windows 7 modern operating system The field Explanation is presently defined as a text field. Suggest a new data type for the field that would enable the field to accommodate much longer explanations. (1) What is the most appropriate data type for a field that will contain pictures? (1) The following query was created on the given data table: Name the field that will NOT appear in the query results. (1)
16 omputer pplications Technology/P2 16 E/November riefly describe the difference in the results produced by each of the following queries: (2) 7.4 Use the database table below to answer the questions that follow Only the and classes in the grade work at the cyber café. Suggest a validation rule that would prevent Mr Wu from entering any other letter in the Grade_Graad field. (2) report is created and grouped first by Grade_Graad and then by Log off. Which surname will appear last in the report? (1) 7.5 The following formula was inserted in a query to calculate how long the person has been logged onto the Internet: Hours:([Log off] [Log on]) * Name the calculated field created in the query. (1) What is the purpose of the square brackets, [ ], and the round brackets, ( ), in the formula above? (2) [26] TOTL SETION : GRN TOTL:
NATIONAL SENIOR CERTIFICATE GRADE 12
 NTIONL SENIOR ERTIFITE GRE 12 OMPUTER PPLITIONS TEHNOLOGY P2 (THEORY) FERURY/MRH 2011 MRKS: 150 TIME: 3 hours This question paper consists of 14 pages. omputer pplications Technology/P2 2 E/Feb. Mar. 2011
NTIONL SENIOR ERTIFITE GRE 12 OMPUTER PPLITIONS TEHNOLOGY P2 (THEORY) FERURY/MRH 2011 MRKS: 150 TIME: 3 hours This question paper consists of 14 pages. omputer pplications Technology/P2 2 E/Feb. Mar. 2011
NATIONAL SENIOR CERTIFICATE GRADE 12
 NTIONL SENIOR ERTIFITE GRE 12 OMPUTER PPLITIONS TEHNOLOGY P2 NOVEMER 2014 MRKS: 150 TIME: 3 hours This question paper consists of 15 pages. Please turn over omputer pplications Technology/P2 2 E/November
NTIONL SENIOR ERTIFITE GRE 12 OMPUTER PPLITIONS TEHNOLOGY P2 NOVEMER 2014 MRKS: 150 TIME: 3 hours This question paper consists of 15 pages. Please turn over omputer pplications Technology/P2 2 E/November
NATIONAL SENIOR CERTIFICATE GRADE 12
 NTIONL SENIOR ERTIFITE GRE 12 OMPUTER PPLITIONS TEHNOLOGY P2 (THEORY) NOVEMER 2010 MRKS: 150 TIME: 3 hours This question paper consists of 15 pages. omputer pplications Technology/P2 2 E/November 2010
NTIONL SENIOR ERTIFITE GRE 12 OMPUTER PPLITIONS TEHNOLOGY P2 (THEORY) NOVEMER 2010 MRKS: 150 TIME: 3 hours This question paper consists of 15 pages. omputer pplications Technology/P2 2 E/November 2010
NATIONAL SENIOR CERTIFICATE GRADE 12
 NTIONL SENIOR ERTIFITE GRE 12 OMPUTER PPLITIONS TEHNOLOGY P2 NOVEMER 2017 MRKS: 150 TIME: 3 hours This question paper consists of 17 pages. Please turn over omputer pplications Technology/P2 2 E/November
NTIONL SENIOR ERTIFITE GRE 12 OMPUTER PPLITIONS TEHNOLOGY P2 NOVEMER 2017 MRKS: 150 TIME: 3 hours This question paper consists of 17 pages. Please turn over omputer pplications Technology/P2 2 E/November
NATIONAL SENIOR CERTIFICATE GRADE 12
 NTIONL SENIOR ERTIFITE GRE 12 OMPUTER PPLITIONS TEHNOLOGY P2 NOVEMER 2016 MRKS: 150 TIME: 3 hours This question paper consists of 17 pages. omputer pplications Technology/P2 2 E/November 2016 INSTRUTIONS
NTIONL SENIOR ERTIFITE GRE 12 OMPUTER PPLITIONS TEHNOLOGY P2 NOVEMER 2016 MRKS: 150 TIME: 3 hours This question paper consists of 17 pages. omputer pplications Technology/P2 2 E/November 2016 INSTRUTIONS
NATIONAL SENIOR CERTIFICATE GRADE 12
 NTIONL SENIOR ERTIFITE GRE 12 OMPUTER PPLITIONS TEHNOLOGY P2 FERURY/MRH 2018 MRKS: 150 TIME: 3 hours This question paper consists of 18 pages. Please turn over omputer pplications Technology/P2 2 E/Feb.
NTIONL SENIOR ERTIFITE GRE 12 OMPUTER PPLITIONS TEHNOLOGY P2 FERURY/MRH 2018 MRKS: 150 TIME: 3 hours This question paper consists of 18 pages. Please turn over omputer pplications Technology/P2 2 E/Feb.
NATIONAL SENIOR CERTIFICATE GRADE 12
 NTIONL SENIOR ERTIFITE GRE 12 OMPUTER PPLITIONS TEHNOLOGY P2 FERURY/MRH 2009 MRKS: 150 TIME: 3 hours This question paper consists of 16 pages. omputer pplications Technology/P2 2 oe/feb. March 2009 INSTRUTIONS
NTIONL SENIOR ERTIFITE GRE 12 OMPUTER PPLITIONS TEHNOLOGY P2 FERURY/MRH 2009 MRKS: 150 TIME: 3 hours This question paper consists of 16 pages. omputer pplications Technology/P2 2 oe/feb. March 2009 INSTRUTIONS
GRADE 11 NOVEMBER 2012 COMPUTER APPLICATIONS TECHNOLOGY P2
 Province of the EASTERN CAPE EDUCATION NATIONAL SENIOR CERTIFICATE GRADE 11 NOVEMBER 2012 COMPUTER APPLICATIONS TECHNOLOGY P2 MARKS: 150 TIME: 3 hours *CATDM2* This question paper consists of 11 pages.
Province of the EASTERN CAPE EDUCATION NATIONAL SENIOR CERTIFICATE GRADE 11 NOVEMBER 2012 COMPUTER APPLICATIONS TECHNOLOGY P2 MARKS: 150 TIME: 3 hours *CATDM2* This question paper consists of 11 pages.
NATIONAL SENIOR CERTIFICATE GRADE 12
 NTIONL SENIOR ERTIFITE GRE 12 INFORMTION TEHNOLOGY P2 EXEMPLR 2008 MRKS: 180 TIME: 3 hours This question paper consists of 16 pages. Information Technology/P2 2 oe/exemplar 2008 INSTRUTIONS N INFORMTION
NTIONL SENIOR ERTIFITE GRE 12 INFORMTION TEHNOLOGY P2 EXEMPLR 2008 MRKS: 180 TIME: 3 hours This question paper consists of 16 pages. Information Technology/P2 2 oe/exemplar 2008 INSTRUTIONS N INFORMTION
Information and Communication Technology
 Write your name here Surname Other names entre Number andidate Number Edexcel IGSE Information and ommunication Technology Paper 1: Written paper Thursday 16 June 2011 - fternoon Time: 1 hour 30 minutes
Write your name here Surname Other names entre Number andidate Number Edexcel IGSE Information and ommunication Technology Paper 1: Written paper Thursday 16 June 2011 - fternoon Time: 1 hour 30 minutes
Study Opportunities. June 2012
 Study Opportunities June 2012 COMPUTER APPLICATIONS TECHNOLOGY Grade 10 Paper 2 Written question paper Time: 2 hours Total: 120 This question paper consists of 10 pages (including the front page) Instructions
Study Opportunities June 2012 COMPUTER APPLICATIONS TECHNOLOGY Grade 10 Paper 2 Written question paper Time: 2 hours Total: 120 This question paper consists of 10 pages (including the front page) Instructions
Chapter 8 Operating Systems and Utility Programs
 Chapter 8 Operating Systems and Utility Programs Chapter 8 Objectives Identify the types of system software Summarize the startup process on a personal computer Summarize the features of several stand-alone
Chapter 8 Operating Systems and Utility Programs Chapter 8 Objectives Identify the types of system software Summarize the startup process on a personal computer Summarize the features of several stand-alone
INFORMATION TECHNOLOGY: PAPER I. 1. This question paper consists of 12 pages. Please check that your question paper is complete.
 NTIONL SENIOR ERTIFITE EXMINTION NOVEMER 2014 INFORMTION TEHNOLOGY: PPER I Time: 3 hours 180 marks PLESE RE THE FOLLOWING INSTRUTIONS REFULLY 1. This question paper consists of 12 pages. Please check that
NTIONL SENIOR ERTIFITE EXMINTION NOVEMER 2014 INFORMTION TEHNOLOGY: PPER I Time: 3 hours 180 marks PLESE RE THE FOLLOWING INSTRUTIONS REFULLY 1. This question paper consists of 12 pages. Please check that
Chapter 8 Operating Systems and Utility Programs أ.أمل زهران
 Chapter 8 Operating Systems and Utility Programs Chapter 8 Objectives Identify the types of system software Summarize the startup process on a personal computer Summarize the features of several stand-alone
Chapter 8 Operating Systems and Utility Programs Chapter 8 Objectives Identify the types of system software Summarize the startup process on a personal computer Summarize the features of several stand-alone
I. Ch 5 System Software
 I. Ch 5 System Software A. Competencies 1. Describe the differences between system software and application software 2. Discuss the four types of system software 3. Discuss the basic functions, features
I. Ch 5 System Software A. Competencies 1. Describe the differences between system software and application software 2. Discuss the four types of system software 3. Discuss the basic functions, features
PROVINCIAL EXAMINATION COMPUTER APPLICATIONS TECHNOLOGY PAPER 2 NOVEMBER 2015 GRADE 10. This paper consists of 11 pages
 PROVINCIAL EXAMINATION COMPUTER APPLICATIONS TECHNOLOGY PAPER NOVEMBER 05 GRADE 0 MARKS: 0 TIME: ½ HOURS This paper consists of pages INSTRUCTIONS AND INFORMATION. This question paper consists of THREE
PROVINCIAL EXAMINATION COMPUTER APPLICATIONS TECHNOLOGY PAPER NOVEMBER 05 GRADE 0 MARKS: 0 TIME: ½ HOURS This paper consists of pages INSTRUCTIONS AND INFORMATION. This question paper consists of THREE
A Comprehensive Guide. IC3 - Module 1: Computing Fundamentals
 Appendix A A Comprehensive Guide to IC 3 IC3 - Module 1: Computing Fundamentals Standardized Coding Number Objective 1.1 Objectives & Abbreviated Skill Sets Page Identify types of computers, how they process
Appendix A A Comprehensive Guide to IC 3 IC3 - Module 1: Computing Fundamentals Standardized Coding Number Objective 1.1 Objectives & Abbreviated Skill Sets Page Identify types of computers, how they process
COMPUTER APPLICATIONS TECHNOLOGY: PAPER I. 1. This paper consists of 12 pages. Please check that your question paper is complete.
 NATIONAL SENIOR CERTIFICATE EXAMINATION NOVEMBER 2011 COMPUTER APPLICATIONS TECHNOLOGY: PAPER I Time: 3 hours 150 marks PLEASE READ THE FOLLOWING INSTRUCTIONS CAREFULLY 1. This paper consists of 12 pages.
NATIONAL SENIOR CERTIFICATE EXAMINATION NOVEMBER 2011 COMPUTER APPLICATIONS TECHNOLOGY: PAPER I Time: 3 hours 150 marks PLEASE READ THE FOLLOWING INSTRUCTIONS CAREFULLY 1. This paper consists of 12 pages.
Grey High School. June COMPUTER APPLICATIONS TECHNOLOGY Grade 10 Paper 2 Written MEMORANDUM
 Grey High School June 2018 COMPUTER APPLICATIONS TECHNOLOGY Grade 10 Paper 2 Written MEMORANDUM TIME: 2 HOURS MARKS: 100 This memorandum consists of 6 pages (cover page included Question 1 1.1 1.2 1.3
Grey High School June 2018 COMPUTER APPLICATIONS TECHNOLOGY Grade 10 Paper 2 Written MEMORANDUM TIME: 2 HOURS MARKS: 100 This memorandum consists of 6 pages (cover page included Question 1 1.1 1.2 1.3
Module 1 Concepts of Information and Communication Technology (ICT)
 Module 1 Concepts of Information and Communication Technology (ICT) The following is the Syllabus for Module 1, Concepts of Information and Communication Technology (ICT), which provides the basis for
Module 1 Concepts of Information and Communication Technology (ICT) The following is the Syllabus for Module 1, Concepts of Information and Communication Technology (ICT), which provides the basis for
London Examinations IGCSE
 Centre No. Candidate No. Surname Signature Initial(s) Paper Reference(s) 4385/1F London Examinations IGCSE Information and Communication Technology Paper 1F Foundation Tier Monday 14 May 2007 Morning Time:
Centre No. Candidate No. Surname Signature Initial(s) Paper Reference(s) 4385/1F London Examinations IGCSE Information and Communication Technology Paper 1F Foundation Tier Monday 14 May 2007 Morning Time:
User s Guide. SingNet Desktop Security Copyright 2010 F-Secure Corporation. All rights reserved.
 User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
Vocabulary Bank organized by module
 Vocabulary Bank organized by module Module 1: Choosing a Computer Application: also called an "app," it is computer software created for a particular task or tasks; it is increasingly used to mean software
Vocabulary Bank organized by module Module 1: Choosing a Computer Application: also called an "app," it is computer software created for a particular task or tasks; it is increasingly used to mean software
Bridge Program Computer Skills Self-Inventory
 Name Date Bridge Program Computer Skills Self-Inventory This inventory is a lengthy but non-comprehensive list of beginning, intermediate and advanced computer skills a typical college graduate would have.
Name Date Bridge Program Computer Skills Self-Inventory This inventory is a lengthy but non-comprehensive list of beginning, intermediate and advanced computer skills a typical college graduate would have.
GREY HIGH SCHOOL. June COMPUTER APPLICATIONS TECHNOLOGY Grade 10 Paper 2 Written
 GREY HIGH SCHOOL June 2017 COMPUTER APPLICATIONS TECHNOLOGY Grade 10 Paper 2 Written TIME: 1½ HOURS MARKS: 100 Examiner: SM Moderator: RW This question paper consists of 10 pages (cover page included)
GREY HIGH SCHOOL June 2017 COMPUTER APPLICATIONS TECHNOLOGY Grade 10 Paper 2 Written TIME: 1½ HOURS MARKS: 100 Examiner: SM Moderator: RW This question paper consists of 10 pages (cover page included)
GRADE 12 SEPTEMBER 2012 INFORMATION TECHNOLOGY P2
 Province of the EASTERN CAPE EDUCATION NATIONAL SENIOR CERTIFICATE GRADE 12 SEPTEMBER 2012 INFORMATION TECHNOLOGY P2 MARKS: 180 TIME: 3 hours *INFDM2* This question paper consists of 12 pages. 2 INFORMATION
Province of the EASTERN CAPE EDUCATION NATIONAL SENIOR CERTIFICATE GRADE 12 SEPTEMBER 2012 INFORMATION TECHNOLOGY P2 MARKS: 180 TIME: 3 hours *INFDM2* This question paper consists of 12 pages. 2 INFORMATION
Which one of the following terms describes the physical components of a computer system?
 Exercise 23 1.1.1 Which one of the following terms describes the physical components of a computer system? a. Hardware. b. Freeware. c. Software. d. Courseware. 1.1.2 Which one of the following is a portable
Exercise 23 1.1.1 Which one of the following terms describes the physical components of a computer system? a. Hardware. b. Freeware. c. Software. d. Courseware. 1.1.2 Which one of the following is a portable
Zillya Internet Security User Guide
 Zillya Internet Security User Guide Content Download Zillya Internet Security... 4 Installation Zillya Internet Security... 4 System Status... 7 System Scanning... 9 When Zillya Internet Security finds
Zillya Internet Security User Guide Content Download Zillya Internet Security... 4 Installation Zillya Internet Security... 4 System Status... 7 System Scanning... 9 When Zillya Internet Security finds
Clean & Speed Up Windows with AWO
 Clean & Speed Up Windows with AWO C 400 / 1 Manage Windows with this Powerful Collection of System Tools Every version of Windows comes with at least a few programs for managing different aspects of your
Clean & Speed Up Windows with AWO C 400 / 1 Manage Windows with this Powerful Collection of System Tools Every version of Windows comes with at least a few programs for managing different aspects of your
NATIONAL CERTIFICATE (VOCATIONAL) COMPUTER PROGRAMMING (First Paper) (Theory) NQF LEVEL 4 NOVEMBER EXAMINATION
 NTIONL ERTIFITE (VOTIONL) OMPUTER PROGRMMING (First Paper) (Theory) NQF LEVEL 4 NOVEMER EXMINTION (10041024) 15 November 2013 (Y-Paper) 13:00 15:00 This question paper consists of 10 pages. opyright reserved
NTIONL ERTIFITE (VOTIONL) OMPUTER PROGRMMING (First Paper) (Theory) NQF LEVEL 4 NOVEMER EXMINTION (10041024) 15 November 2013 (Y-Paper) 13:00 15:00 This question paper consists of 10 pages. opyright reserved
SECONDARY SCHOOL - IMRIEĦEL HALF-YEARLY EXAMINATIONS 2017/2018
 FORM: 4 SECONDARY SCHOOL - IMRIEĦEL HALF-YEARLY EXAMINATIONS 2017/2018 ICT I Time: 1.5 hrs Name: Class: Section A: Computer Essentials The following questions are about software. 1. Mark True or False
FORM: 4 SECONDARY SCHOOL - IMRIEĦEL HALF-YEARLY EXAMINATIONS 2017/2018 ICT I Time: 1.5 hrs Name: Class: Section A: Computer Essentials The following questions are about software. 1. Mark True or False
ST VENERA BOYS SECONDARY SCHOOL HALF-YEARLY EXAMINATIONS 2014~15 Information and Communication Technology
 Form 4 ST VENERA BOYS SECONDARY SCHOOL HALF-YEARLY EXAMINATIONS 2014~15 Information and Communication Technology Time: 1hr 30mins Name: Class: Please read the following instructions carefully: 1. Answer
Form 4 ST VENERA BOYS SECONDARY SCHOOL HALF-YEARLY EXAMINATIONS 2014~15 Information and Communication Technology Time: 1hr 30mins Name: Class: Please read the following instructions carefully: 1. Answer
Keep Your Computer Healthy
 Keep Your Computer Healthy In this class, you will learn about hardware and software maintenance. We will start with hardware and then we will move to software. Software has many different utilities that
Keep Your Computer Healthy In this class, you will learn about hardware and software maintenance. We will start with hardware and then we will move to software. Software has many different utilities that
In order to use Redborne Remote Services you must have at least the minimum specification:-
 Redborne Upper School Redborne Remote Services Rev 1.3 October 2011 Redborne Remote Services can be located at www.redborne.com Contents 1 Introduction 2 Setting Up 3 Logging In 4 Opening Applications
Redborne Upper School Redborne Remote Services Rev 1.3 October 2011 Redborne Remote Services can be located at www.redborne.com Contents 1 Introduction 2 Setting Up 3 Logging In 4 Opening Applications
RPS Technology Standards Grades 9 through 12 Technology Standards and Expectations
 RPS Technology Standards Grades 9 through 12 Technology Standards and Expectations Throughout high school, as students take courses to prepare themselves for college and the working world, they should
RPS Technology Standards Grades 9 through 12 Technology Standards and Expectations Throughout high school, as students take courses to prepare themselves for college and the working world, they should
Quick Heal Total Security for Mac. Simple, fast and seamless protection for Mac.
 Simple, fast and seamless protection for Mac. Product Highlights Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth email
Simple, fast and seamless protection for Mac. Product Highlights Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth email
Airtel PC Secure Trouble Shooting Guide
 Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Northstar Digital Literacy Assessment Project Standards
 Northstar Digital Literacy Assessment Project Standards Gradually being updated as we build out version 2.0. Topics marked below as appropriate. Basic Computer Skills (2.0) 1. Distinguish between different
Northstar Digital Literacy Assessment Project Standards Gradually being updated as we build out version 2.0. Topics marked below as appropriate. Basic Computer Skills (2.0) 1. Distinguish between different
TPP Kick Off 9/15/2017
 TPP Kick Off 9/15/2017 Agenda Adopting the Northstar Digital Literacy Standards Digital Literacy Courses on Learner Moodle Digital Literacy Curriculum Distance Education Questions Guiding Principles 1.
TPP Kick Off 9/15/2017 Agenda Adopting the Northstar Digital Literacy Standards Digital Literacy Courses on Learner Moodle Digital Literacy Curriculum Distance Education Questions Guiding Principles 1.
Cyber Security Basics. Presented by Darrel Karbginsky
 Cyber Security Basics Presented by Darrel Karbginsky What s to come In the following slides I am going to discuss amongst other things and in no particular order things to enlighten, frighten, educate,
Cyber Security Basics Presented by Darrel Karbginsky What s to come In the following slides I am going to discuss amongst other things and in no particular order things to enlighten, frighten, educate,
Available Instructor Resources Resource File Name Found
 Instructor s Manual Exploring Computing Concepts 2016, Chapter 1: Getting Started with Computer Concepts Student Data Files Solution Files Answer Keys Matching Multiple Choice Concepts Checks Scorecards
Instructor s Manual Exploring Computing Concepts 2016, Chapter 1: Getting Started with Computer Concepts Student Data Files Solution Files Answer Keys Matching Multiple Choice Concepts Checks Scorecards
THINGS TO REMEMBER INTRODUCTION TO COMPUTERS
 PREMIER CURRICULUM SERIES Based on the Sunshine State Standards for Secondary Education, established by the State of Florida, Department of Education THINGS TO REMEMBER INTRODUCTION TO COMPUTERS Copyright
PREMIER CURRICULUM SERIES Based on the Sunshine State Standards for Secondary Education, established by the State of Florida, Department of Education THINGS TO REMEMBER INTRODUCTION TO COMPUTERS Copyright
BCS IT User Syllabus ECDL Unit 2 Using the Computer and Managing Files/IT User Fundamentals Level 1. Version 5.0
 BCS IT User Syllabus ECDL Unit 2 Using the Computer and Managing Files/IT User Fundamentals Level 1 Version 5.0 March 2009 2.1 Operating System 2.2 File Management 2.1.1 First Steps 2.1.1.1 Start the computer
BCS IT User Syllabus ECDL Unit 2 Using the Computer and Managing Files/IT User Fundamentals Level 1 Version 5.0 March 2009 2.1 Operating System 2.2 File Management 2.1.1 First Steps 2.1.1.1 Start the computer
Which one of the following terms describes the physical components of a computer system?
 Which one of the following terms describes the physical components of a computer system? a. Hardware. b. Freeware. c. Software. d. Courseware. Which one of the following can slow down the computers performance?
Which one of the following terms describes the physical components of a computer system? a. Hardware. b. Freeware. c. Software. d. Courseware. Which one of the following can slow down the computers performance?
The process by which a user can associate specific permissions to each username.
 Jargon Buster A Antispyware A program that detects and removes malicious programs on your computer called spyware. Once it is installed can collect information without the users consent, that can be almost
Jargon Buster A Antispyware A program that detects and removes malicious programs on your computer called spyware. Once it is installed can collect information without the users consent, that can be almost
NATIONAL SENIOR CERTIFICATE GRADE 12
 NATIONAL SENIOR CERTIFICATE GRADE 12 COMPUTER APPLICATIONS TECHNOLOGY P2 FEBRUARY/MARCH 2018 MARKING GUIDELINES MARKS: 150 These marking guidelines consist of 13 pages. Computer Applications Technology/P2
NATIONAL SENIOR CERTIFICATE GRADE 12 COMPUTER APPLICATIONS TECHNOLOGY P2 FEBRUARY/MARCH 2018 MARKING GUIDELINES MARKS: 150 These marking guidelines consist of 13 pages. Computer Applications Technology/P2
WatchManager SQL Installation Guide
 WatchManager SQL Installation Guide WatchManager SQL Installation Guide All rights reserved. No parts of this work may be reproduced in any form or by any means - graphic, electronic, or mechanical, including
WatchManager SQL Installation Guide WatchManager SQL Installation Guide All rights reserved. No parts of this work may be reproduced in any form or by any means - graphic, electronic, or mechanical, including
GRADE 12 SEPTEMBER 2016 COMPUTER APPLICATIONS TECHNOLOGY P2
 NATIONAL SENIOR CERTIFICATE GRADE 12 SEPTEMBER 2016 COMPUTER APPLICATIONS TECHNOLOGY P2 MARKS: 150 TIME: 3 hours *CATNE* This question paper consists of 14 pages. 2 COMPUTER APPLICATIONS TECHNOLOGY P2
NATIONAL SENIOR CERTIFICATE GRADE 12 SEPTEMBER 2016 COMPUTER APPLICATIONS TECHNOLOGY P2 MARKS: 150 TIME: 3 hours *CATNE* This question paper consists of 14 pages. 2 COMPUTER APPLICATIONS TECHNOLOGY P2
City College Computing
 City College Computing European Computer Driving Licence Module 1 Sample Test 1 1. Which of these is an input device? A. CD-ROM B. Mouse C. Printer D. Zip drive 2. What does RSI mean? A. Repeated Syndrome
City College Computing European Computer Driving Licence Module 1 Sample Test 1 1. Which of these is an input device? A. CD-ROM B. Mouse C. Printer D. Zip drive 2. What does RSI mean? A. Repeated Syndrome
NATIONAL SENIOR CERTIFICATE GRADE 12
 NATIONAL SENIOR CERTIFICATE GRADE 12 INFORMATION TECHNOLOGY P2 NOVEMBER 2015 MARKS: 150 TIME: 3 hours This question paper consists of 17 pages. Information Technology/P2 2 DBE/November 2015 INSTRUCTIONS
NATIONAL SENIOR CERTIFICATE GRADE 12 INFORMATION TECHNOLOGY P2 NOVEMBER 2015 MARKS: 150 TIME: 3 hours This question paper consists of 17 pages. Information Technology/P2 2 DBE/November 2015 INSTRUCTIONS
Quick Heal Total Security for Mac. Simple, fast and seamless protection for Mac.
 Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth
Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth
/ / / Chapter-8 INTRODUCTION TO HTML Difference between. 1. WYSIWYG editor & Text Editor.
 Grade- 7 Computer Chapter-2 MS EXCEL Chapter-8 INTRODUCTION TO HTML Chapter-9 COMPUTER VIRUSES Chapter-10 COMPUTER SECURITY Chapter-2 MS EXCEL 1. What is a formula? A formula in MS Excel Starts with an
Grade- 7 Computer Chapter-2 MS EXCEL Chapter-8 INTRODUCTION TO HTML Chapter-9 COMPUTER VIRUSES Chapter-10 COMPUTER SECURITY Chapter-2 MS EXCEL 1. What is a formula? A formula in MS Excel Starts with an
E4-E5 (CFA) For internal circulation of BSNLonly
 E4-E5 (CFA) IT Tools for Office Management Objective The objective of this session is to make the executives of BSNL familiar with day-to-day use of different utilities of IT and demonstrate various practices
E4-E5 (CFA) IT Tools for Office Management Objective The objective of this session is to make the executives of BSNL familiar with day-to-day use of different utilities of IT and demonstrate various practices
COMPUTER APPLICATIONS TECHNOLOGY: PAPER I. 1. This paper consists of 15 pages. Please check that your question paper is complete.
 NTIONL SENIOR ERTIFITE EXMINTION NOVEMER 2012 OMPUTER PPLITIONS TEHNOLOGY: PPER I Time: 3 hours 150 marks PLESE RE THE FOLLOWING INSTRUTIONS REFULLY 1. This paper consists of 15 pages. Please check that
NTIONL SENIOR ERTIFITE EXMINTION NOVEMER 2012 OMPUTER PPLITIONS TEHNOLOGY: PPER I Time: 3 hours 150 marks PLESE RE THE FOLLOWING INSTRUTIONS REFULLY 1. This paper consists of 15 pages. Please check that
GOZO COLLEGE BOYS SECONDARY
 GOZO COLLEGE BOYS SECONDARY Half Yearly Examinations 2013-2014 Subject: INFORMATION & COMMUNICATION TECHNOLOGY Form: 4 Track 3 Time: 1 hr NAME: CLASS: INDEX NO: Instructions to Candidates Answer ALL questions
GOZO COLLEGE BOYS SECONDARY Half Yearly Examinations 2013-2014 Subject: INFORMATION & COMMUNICATION TECHNOLOGY Form: 4 Track 3 Time: 1 hr NAME: CLASS: INDEX NO: Instructions to Candidates Answer ALL questions
Discovering Computers Fundamentals, 2011 Edition. Living in a Digital World
 Discovering Computers Fundamentals, 2011 Edition Living in a Digital World Objectives Overview Define system software and identify the two types of system software Describe the functions of an operating
Discovering Computers Fundamentals, 2011 Edition Living in a Digital World Objectives Overview Define system software and identify the two types of system software Describe the functions of an operating
Functional Skills. Entry 3 to Level 2. IT Basics Information
 Functional Skills Skills ICT Entry 3 to Level 2 YOU DO NOT NEED TO WORK THROUGH THIS. IT IS AN PACK TO TEACH YOU THE SKILLS NEEDED TO COMPLETE THE TASKS. YOU CAN USE IT WHILST WORKING THROUGH THE TASKS,
Functional Skills Skills ICT Entry 3 to Level 2 YOU DO NOT NEED TO WORK THROUGH THIS. IT IS AN PACK TO TEACH YOU THE SKILLS NEEDED TO COMPLETE THE TASKS. YOU CAN USE IT WHILST WORKING THROUGH THE TASKS,
2017 Rate Sheet Upfront prices and quality work backed by our 15-day Guarantee
 2017 Rate Sheet Upfront prices and quality work backed by our 15-day Guarantee Hourly Rates, Mileage Fees and Deposits: (SOME RATES ARE NEGOTIABLE) 79.00 First Hour, $19.75 each 15-minute increment over
2017 Rate Sheet Upfront prices and quality work backed by our 15-day Guarantee Hourly Rates, Mileage Fees and Deposits: (SOME RATES ARE NEGOTIABLE) 79.00 First Hour, $19.75 each 15-minute increment over
Foreword...xv Introduction...1 Part I: Buying and Getting Started with Your Computer...5
 Contents at a Glance Foreword...xv Introduction...1 Part I: Buying and Getting Started with Your Computer...5 Chapter 1: Buying a Computer...7 Chapter 2: Setting Up Your Computer...25 Chapter 3: Getting
Contents at a Glance Foreword...xv Introduction...1 Part I: Buying and Getting Started with Your Computer...5 Chapter 1: Buying a Computer...7 Chapter 2: Setting Up Your Computer...25 Chapter 3: Getting
Dell SupportAssist for PCs. User s Guide
 Dell SupportAssist for PCs User s Guide Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either potential
Dell SupportAssist for PCs User s Guide Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either potential
D Facebook A. E Twitter B. F WhatsApp C. C Skype D. A Snapchat E. SECTION 1 Matching
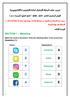 SETION 1 Matching Match the word to the picture. Write the matching letter in the correct box. Question (1) Terms Explanations D Facebook E Twitter F Whatspp Skype D Snapchat E 1 Instagram F Question (2)
SETION 1 Matching Match the word to the picture. Write the matching letter in the correct box. Question (1) Terms Explanations D Facebook E Twitter F Whatspp Skype D Snapchat E 1 Instagram F Question (2)
OPERATING SYSTEMS & UTILITY PROGRAMS
 OPERATING SYSTEMS & UTILITY PROGRAMS System Software System software consists of the programs that control the operations of the computer and its devices. Functions that system software performs include:
OPERATING SYSTEMS & UTILITY PROGRAMS System Software System software consists of the programs that control the operations of the computer and its devices. Functions that system software performs include:
Manual Removal Norton Internet Security Won't Open Or
 Manual Removal Norton Internet Security Won't Open Or Dec 3, 2014. Finally during the reinstall - I had to delete a key to get a new key other wise I would I have it shown on the prgrams and features -
Manual Removal Norton Internet Security Won't Open Or Dec 3, 2014. Finally during the reinstall - I had to delete a key to get a new key other wise I would I have it shown on the prgrams and features -
AVANTUS TRAINING PTE LTD
 [ICDL-CS]: WSQ ICDL Computer Essentials Length Technology Delivery Method : 2 Days : Computers, Microsoft Windows : Instructor-led (Classroom) Course Overview This module sets out essential concepts and
[ICDL-CS]: WSQ ICDL Computer Essentials Length Technology Delivery Method : 2 Days : Computers, Microsoft Windows : Instructor-led (Classroom) Course Overview This module sets out essential concepts and
Discovering Computers Living in a Digital World
 Discovering Computers 2010 Living in a Digital World Objectives Overview Define system software and identify the two types of system software Describe the functions of an operating system Summarize the
Discovering Computers 2010 Living in a Digital World Objectives Overview Define system software and identify the two types of system software Describe the functions of an operating system Summarize the
Study Opportunities. June COMPUTER APPLICATIONS TECHNOLOGY Grade 12 Paper 2 Written
 Study Opportunities June 2014 COMPUTER APPLICATIONS TECHNOLOGY Grade 12 Paper 2 Written TIME: 3 HOURS MARKS: 150 This question paper consists of 14 pages (cover page included) Instructions and information
Study Opportunities June 2014 COMPUTER APPLICATIONS TECHNOLOGY Grade 12 Paper 2 Written TIME: 3 HOURS MARKS: 150 This question paper consists of 14 pages (cover page included) Instructions and information
User Guide. Rebit Backup. https://rebitbackup.rebitgo.com
 User Guide Information in this document is subject to change without notice. 2017 Rebit Inc. All rights reserved. Reproduction of this material in any manner whatsoever without the written permission of
User Guide Information in this document is subject to change without notice. 2017 Rebit Inc. All rights reserved. Reproduction of this material in any manner whatsoever without the written permission of
IT JARGON BUSTERS NETWORKING TERMS
 IT JARGON BUSTERS NETWORKING TERMS WAN Wide Area The WAN is associated with connections over a large area. In most circumstances this is referred to as the Internet connection you will have at home or
IT JARGON BUSTERS NETWORKING TERMS WAN Wide Area The WAN is associated with connections over a large area. In most circumstances this is referred to as the Internet connection you will have at home or
Grey High School. June COMPUTER APPLICATIONS TECHNOLOGY Grade 10 Paper 2 Written MEMORANDUM
 Grey High School June 2017 COMPUTER APPLICATIONS TECHNOLOGY Grade 10 Paper 2 Written MEMORANDUM Moderated 07/06/2017 TIME: 2 HOURS MARKS: 100 This memorandum consists of 7 pages (cover page included) SECTION
Grey High School June 2017 COMPUTER APPLICATIONS TECHNOLOGY Grade 10 Paper 2 Written MEMORANDUM Moderated 07/06/2017 TIME: 2 HOURS MARKS: 100 This memorandum consists of 7 pages (cover page included) SECTION
Module 11 Technical Troubleshooting for Restaurant Managers
 Module 11 Technical Troubleshooting for Restaurant Managers Overview This module is about troubleshooting at an introductory level and to help you gain confidence and knowledge to problem-solve Pilot POS
Module 11 Technical Troubleshooting for Restaurant Managers Overview This module is about troubleshooting at an introductory level and to help you gain confidence and knowledge to problem-solve Pilot POS
3.5 SECURITY. How can you reduce the risk of getting a virus?
 3.5 SECURITY 3.5.4 MALWARE WHAT IS MALWARE? Malware, short for malicious software, is any software used to disrupt the computer s operation, gather sensitive information without your knowledge, or gain
3.5 SECURITY 3.5.4 MALWARE WHAT IS MALWARE? Malware, short for malicious software, is any software used to disrupt the computer s operation, gather sensitive information without your knowledge, or gain
Using Skype. Created by the Columbia Basin Alliance for Literacy. Joan Exley & Ann Cavicchi
 Created by the Columbia Basin Alliance for Literacy This project is funded by Government of Canada s New Horizons for Seniors Program and is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike
Created by the Columbia Basin Alliance for Literacy This project is funded by Government of Canada s New Horizons for Seniors Program and is licensed under a Creative Commons Attribution-NonCommercial-ShareAlike
A SIMPLE STEP-BY-STEP GUIDE FOR COMPUTER BEGINNERS
 A SIMPLE STEP-BY-STEP GUIDE FOR COMPUTER BEGINNERS EXPLORING THE INTERNET through HOBBIES AND INTERESTS. LEARN HOW TO KEEP IN TOUCH WITH FRIENDS AND FAMILY USING THE INTERNET In these busy times it s easy
A SIMPLE STEP-BY-STEP GUIDE FOR COMPUTER BEGINNERS EXPLORING THE INTERNET through HOBBIES AND INTERESTS. LEARN HOW TO KEEP IN TOUCH WITH FRIENDS AND FAMILY USING THE INTERNET In these busy times it s easy
Atlanta Urban Debate League E-Debate Teaching Project
 Atlanta Urban Debate League E-Debate Teaching Project Atlanta Urban Debate League... 1 Invitation to Participate... 2 School and Coach Expectations... 4 Technology Needs... 5 Downloading Skype... 6 Installing
Atlanta Urban Debate League E-Debate Teaching Project Atlanta Urban Debate League... 1 Invitation to Participate... 2 School and Coach Expectations... 4 Technology Needs... 5 Downloading Skype... 6 Installing
2016 HSC Information and Digital Technology Networking and hardware Marking Guidelines
 2016 HSC Information and Digital Technology Networking and hardware Marking Guidelines Section I Multiple-choice Answer Key Question Answer 1 B 2 B 3 A 4 D 5 A 6 D 7 B 8 A 9 B 10 C 11 B 12 C 13 A 14 C
2016 HSC Information and Digital Technology Networking and hardware Marking Guidelines Section I Multiple-choice Answer Key Question Answer 1 B 2 B 3 A 4 D 5 A 6 D 7 B 8 A 9 B 10 C 11 B 12 C 13 A 14 C
Quick Heal Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac.
 Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to
Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to
2013 HSC Information Technology Marking Guidelines
 201 HSC Information Technology Marking Guidelines Section I Multiple-choice Answer Key Question Answer 1 A 2 B D 4 A 5 C 6 B 7 D 8 B 9 B 10 D 11 C 12 A 1 C 14 A 15 C 1 Section II Question 16 (a) Identifies
201 HSC Information Technology Marking Guidelines Section I Multiple-choice Answer Key Question Answer 1 A 2 B D 4 A 5 C 6 B 7 D 8 B 9 B 10 D 11 C 12 A 1 C 14 A 15 C 1 Section II Question 16 (a) Identifies
MICROSOFT WINDOWS - LEVEL 2
 MICROSOFT WINDOWS - LEVEL 2 Based on SAQA Unit Standard 117867 This course will introduce you to Windows, which is the operating System of the computer. You will become more familiar with working with
MICROSOFT WINDOWS - LEVEL 2 Based on SAQA Unit Standard 117867 This course will introduce you to Windows, which is the operating System of the computer. You will become more familiar with working with
DEL or DELETE - Deletes the character at cursor and/or characters to the right of the cursor and all highlighted (or selected) text.
 Computer Basics II Handout Objectives: 1. Getting familiar with your Keyboard. 2. How to Install Programs. a. From Web b. From CD c. How to Uninstall 3. How to Create Users 4. Group Permissions and Full
Computer Basics II Handout Objectives: 1. Getting familiar with your Keyboard. 2. How to Install Programs. a. From Web b. From CD c. How to Uninstall 3. How to Create Users 4. Group Permissions and Full
Start to Finish: Set up a New Account or Use Your Own
 Better Technology, Onsite and Personal Connecting NIOGA s Communities www.btopexpress.org www.nioga.org [Type Email Start to Finish: Set up a New Account or Use Your Own Overview: Set up a free email account
Better Technology, Onsite and Personal Connecting NIOGA s Communities www.btopexpress.org www.nioga.org [Type Email Start to Finish: Set up a New Account or Use Your Own Overview: Set up a free email account
E3-E4 (CM) IT UTILITIES
 E3-E4 (CM) IT UTILITIES Objective The objective of this session is to make the executives of BSNL familiar with day-to-day use of different utilities of IT and demonstrate various practices for Personal
E3-E4 (CM) IT UTILITIES Objective The objective of this session is to make the executives of BSNL familiar with day-to-day use of different utilities of IT and demonstrate various practices for Personal
Configuring Windows Security Features
 04_0789737213_ch03.qxd 10/26/07 3:31 PM Page 77 3 CHAPTER THREE Configuring Windows Security Features This chapter covers the following objectives: Configure and troubleshoot User Account Control. Configure
04_0789737213_ch03.qxd 10/26/07 3:31 PM Page 77 3 CHAPTER THREE Configuring Windows Security Features This chapter covers the following objectives: Configure and troubleshoot User Account Control. Configure
CompTIA IT Fundamentals V5 (Course & Lab) Course Outline. CompTIA IT Fundamentals V5 (Course & Lab) 24 Jan
 Course Outline CompTIA IT Fundamentals V5 (Course & Lab) 24 Jan 2019 Contents 1. Course Objective 2. Pre-Assessment 3. Exercises, Quizzes, Flashcards & Glossary Number of Questions 4. Expert Instructor-Led
Course Outline CompTIA IT Fundamentals V5 (Course & Lab) 24 Jan 2019 Contents 1. Course Objective 2. Pre-Assessment 3. Exercises, Quizzes, Flashcards & Glossary Number of Questions 4. Expert Instructor-Led
Speed Up Windows by Disabling Startup Programs
 Speed Up Windows by Disabling Startup Programs Increase Your PC s Speed by Preventing Unnecessary Programs from Running Windows All S 630 / 1 When you look at the tray area beside the clock, do you see
Speed Up Windows by Disabling Startup Programs Increase Your PC s Speed by Preventing Unnecessary Programs from Running Windows All S 630 / 1 When you look at the tray area beside the clock, do you see
 UNIVERSITY OF CAMBRIDGE INTERNATIONAL EXAMINATIONS International General Certificate of Secondary Education *4063456* INFORMATION AND COMMUNICATION TECHNOLOGY 047/3 Paper May/June 00 hours Candidates answer
UNIVERSITY OF CAMBRIDGE INTERNATIONAL EXAMINATIONS International General Certificate of Secondary Education *4063456* INFORMATION AND COMMUNICATION TECHNOLOGY 047/3 Paper May/June 00 hours Candidates answer
Panda Antivirus Server for Mac User Manual
 Panda Antivirus Server for Mac User Manual !"#$%&'()*+,$-'*(& Use of this product is subject to acceptance of the Panda Security End User License Agreement enclosed. Panda Security is registered in the
Panda Antivirus Server for Mac User Manual !"#$%&'()*+,$-'*(& Use of this product is subject to acceptance of the Panda Security End User License Agreement enclosed. Panda Security is registered in the
ITConnect KEEPING TRACK OF YOUR EXPENSES WITH YNAB
 ITConnect Technology made practical for home APRIL 06 Edit PDF files with Word Word is the best tool we have at hand to edit PDFs without having to purchase extra software. Viruses distributed by email
ITConnect Technology made practical for home APRIL 06 Edit PDF files with Word Word is the best tool we have at hand to edit PDFs without having to purchase extra software. Viruses distributed by email
Chapter 2 SOFTWARE CONCEPTS
 Page1 Chapter 2 SOFTWARE CONCEPTS Software Software is a program or set of programs that govern the operation of a computer system and make the hardware run. These are the components of the computer system
Page1 Chapter 2 SOFTWARE CONCEPTS Software Software is a program or set of programs that govern the operation of a computer system and make the hardware run. These are the components of the computer system
College of Pharmacy Windows 10
 College of Pharmacy Windows 10 Windows 10 is the version of Microsoft s flagship operating system that follows Windows 8; the OS was released in July 2015. Windows 10 is designed to address common criticisms
College of Pharmacy Windows 10 Windows 10 is the version of Microsoft s flagship operating system that follows Windows 8; the OS was released in July 2015. Windows 10 is designed to address common criticisms
SAFEGUARDING YOUR LAPTOP/PC FOR FOSTER CARERS Part One Messaging
 SAFEGUARDING YOUR LAPTOP/PC FOR FOSTER CARERS Part One Messaging 1 Note to Readers This guide has been created to provide a simple to follow step by step guide to increase the security on your home PC/laptop
SAFEGUARDING YOUR LAPTOP/PC FOR FOSTER CARERS Part One Messaging 1 Note to Readers This guide has been created to provide a simple to follow step by step guide to increase the security on your home PC/laptop
Applying for Jobs Online
 Applying for Jobs Online Hi, I m Sarah. I m here to show you how to apply for a job using an online application form. Most jobs now require you to fill out an application on the Internet. In this course
Applying for Jobs Online Hi, I m Sarah. I m here to show you how to apply for a job using an online application form. Most jobs now require you to fill out an application on the Internet. In this course
Foothill-De Anza Community College District Wireless Networking Guidelines. Problems Connecting to or Using the Wireless Network
 Foothill-De Anza Community College District Wireless Networking Guidelines Problems Connecting to or Using the Wireless Network My login name and password are not working. HELP! There are different wireless
Foothill-De Anza Community College District Wireless Networking Guidelines Problems Connecting to or Using the Wireless Network My login name and password are not working. HELP! There are different wireless
Microsoft. Exam Questions Windows Operating System Fundamentals. Version:Demo
 Microsoft Exam Questions 98-349 Windows Operating System Fundamentals Version:Demo 1. A Windows service is a: A. Program or process that runs in the background and does not require user intervention. B.
Microsoft Exam Questions 98-349 Windows Operating System Fundamentals Version:Demo 1. A Windows service is a: A. Program or process that runs in the background and does not require user intervention. B.
Owner of the content within this article is Written by Marc Grote
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de What s new in Forefront TMG Beta 2 Part 1 Abstract In this two part article series, I will show
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de What s new in Forefront TMG Beta 2 Part 1 Abstract In this two part article series, I will show
Main Parts of Personal Computer
 Main Parts of Personal Computer System Unit The System Unit: This is simply the box like case called the tower, which houses the motherboard, which houses the CPU. It also houses all the drives, such as
Main Parts of Personal Computer System Unit The System Unit: This is simply the box like case called the tower, which houses the motherboard, which houses the CPU. It also houses all the drives, such as
SECTION A. 10 questions [10 x 1=10] Answer All Questions
![SECTION A. 10 questions [10 x 1=10] Answer All Questions SECTION A. 10 questions [10 x 1=10] Answer All Questions](/thumbs/95/125068522.jpg) SETION 10 questions [10 x 1=10] nswer ll Questions irection: Each question is followed by four possible choices of answers. hoose the correct answer and write it in the space provided. a) The device which
SETION 10 questions [10 x 1=10] nswer ll Questions irection: Each question is followed by four possible choices of answers. hoose the correct answer and write it in the space provided. a) The device which
Security Awareness. Presented by OSU Institute of Technology
 Security Awareness Presented by OSU Institute of Technology Information Technologies Division Security Awareness Topics Social Engineering Phishing Social Networks Displaying Sensitive Information Wireless
Security Awareness Presented by OSU Institute of Technology Information Technologies Division Security Awareness Topics Social Engineering Phishing Social Networks Displaying Sensitive Information Wireless
GREY HIGH SCHOOL. June COMPUTER APPLICATIONS TECHNOLOGY Grade 12 Paper 2 Written
 GREY HIGH SCHOOL June 2017 COMPUTER APPLICATIONS TECHNOLOGY Grade 12 Paper 2 Written TIME: 3 HOURS MARKS: 150 This question paper consists of 12 pages (cover page included) Instructions and information
GREY HIGH SCHOOL June 2017 COMPUTER APPLICATIONS TECHNOLOGY Grade 12 Paper 2 Written TIME: 3 HOURS MARKS: 150 This question paper consists of 12 pages (cover page included) Instructions and information
Mobile Security for Android devices
 Mobile Security for Android 2.2 3.2 devices 1 Swisscom Mobile Security for Android 2.2 3.2 devices This guide covers mobile devices (smartphones, tablets) that use the Android operating system (version
Mobile Security for Android 2.2 3.2 devices 1 Swisscom Mobile Security for Android 2.2 3.2 devices This guide covers mobile devices (smartphones, tablets) that use the Android operating system (version
Case Study for Assignment 2
 The Open Polytechnic of New Zealand Case Study for Assignment 2 550/71155 Business Computing Weighting: This assignment is worth 18% of your final mark. Due date: The quiz closes on Thursday, week 7. The
The Open Polytechnic of New Zealand Case Study for Assignment 2 550/71155 Business Computing Weighting: This assignment is worth 18% of your final mark. Due date: The quiz closes on Thursday, week 7. The
