elearning Program Course Descriptions
|
|
|
- Nigel Cameron
- 6 years ago
- Views:
Transcription
1 elearning Program Course Descriptions When a situation happens, you want to ensure that your staff understands and is comfortable using the LiveProcess solution. Our elearning program is designed to provide your organization with the training you need to get full usage from the application. The courses focus on the skills, techniques, concepts, use cases and best practices needed to effectively leverage LiveProcess. You can use this document to track the courses you have taken. Administrative Series Designed for staff members with LiveProcess Administrator access ADMIN1: New Administrator Introduction to LiveProcess (60 minutes) If you are new to LiveProcess and have been designated as an Administrator, congratulations! Attend this comprehensive class to learn the ins and outs of getting your facility set up and running. You will learn the following during this class: Contact Management overview, Intro to Communications: Codes, Notifications, and Event Log, Overview of EM tools. ADMIN2: Contact Management (60 minutes) Learn how to manage your contacts within LiveProcess. This course will cover: Adding & Deleting Contacts, Updating contact profiles, assisting your contacts with changes and access. Also covered in this course is the Automated Contacts Self Maintenance (ACSM), including: ACSM Settings, Managing Auto-Maintained Contacts and ACSM Best Practices. ADMIN3: Contact Group Management (60 minutes) Learn how LiveProcess can save you valuable time when you need to reach a group of people. You will learn how to reach a pre-configured group of resources through multi-modal communication. This session explores the details of setting up your Contact Group Management from team mobilization fields to building and using contact groups. Coverage includes: Extended Contact Information (ECI), Building Groups (Automated & Manual), and Editing existing Groups. LiveProcess elearning Courses Page 1 of 7
2 ADMIN4: Communication Management using Codes & Notifications This course will focus on the two methods of communicating with staff. Codes which are preconfigured communications, and ad-hoc notifications will be discussed. Date Taken: / / ADMIN5: Event Log Management (60 minutes) This training session covers the LiveProcess Event Log from A to Z. It includes: starting an Event Log, communicating within the Event Log, filtering and searching the log and concludes with editing an Event Log and the After Action Report (AAR). ADMIN6: Document Management (30 minutes) Learn how to use the LiveProcess Document Library including: Loading Documents, document Associations, Sharing, using documents in the Event Log and Compliance. ADMIN7: Hazard Vulnerability Assessment (30 minutes) Explore how to use the LiveProcess Hazard Vulnerability Assessment engine: determining assessments for your existing hazards, creating custom hazards and how to link the mitigation documents and events. ADMIN8: Incident Command (ICS) & Job Action Sheets (JAS) (30 minutes) An in-depth look at the LiveProcess Incident Command System (ICS), where we learn about: using the ICS, customizing Roles, customizing ICS by Hazard, customizing the ICS structure and using the ICS during an event (via the Event Log). We will also take time to explore the Job Action Sheets (JAS) and how they can be used, customized, and printed. LiveProcess elearning Courses Page 2 of 7
3 ADMIN9: LiveProcess Roles and Permissions (30 minutes) Please join us for a review of all the various roles and permissions available within the LiveProcess application. ADMIN10: Compliance Tool Sets A comprehensive review of all the compliance tools available in LiveProcess will be covered including NIMS, HICS and Joint Commission. We will cover how to track and report on your compliance. Date Taken: / / ADMIN11: Creating Custom Contact Fields (ECI) Custom contact fields is a great feature that allows you to expand the data that is used to filter and Select which staff to send codes or notifications. Date Taken: / / ADMIN12: Using Inventory The Inventory module within LiveProcess allows you to track and manage all inventory. Date Taken: / / LiveProcess elearning Courses Page 3 of 7
4 User Series Designed for staff members with Standard User, Codes Operator or Notification Only access levels. USER1: Are you a new user to LiveProcess? If you are a new user to LiveProcess (or just need a refresher!), take this basic course to get you started. The topics that will be covered are how to update your contact profile, how to call a code, how to send a notification and the best practices for using the event log. ASCM1: For those of you who are using the Automated Contact Self Maintenance System (ACSM): I received a request to update my Contacts data. Now what? This course is open to all of your staff members, who have been entered as either a contact or a user in LiveProcess. It provides a quick introduction on what to expect if you are a contact. We will discuss the types of s you will receive, where the s will come from, what to do with the and more importantly what not to do with the . COMM P1: CLICK: One Click Codes Learn how to call a code in your facility. Codes Operators, Nurses, Emergency team members should plan to attend this short class to learn how easy it is to call a code. The session will also cover receiving a code, and monitoring and clearing a code. COMM P2: Notifications This session will focus on Sending Notifications. We will review how to select recipients, enter custom responses and select delivery methods. We will also cover monitoring response and sending follow up messages. LiveProcess elearning Courses Page 4 of 7
5 COMM P3: Event Log You will learn how to post messages including resource and task requests. Replying to posts and how to filter discussions and searching through the log is also included. COMM P4: Best Practices for Mobilizing Your Staff The course will concentrate on the best methods to communication and mobilize your staff for any situation. Use of codes and notifications will be discussed and when is the best situation to which method. Date Taken: / / LiveProcess elearning Courses Page 5 of 7
6 Use Case Series Designed for staff members to learn specific examples of how LiveProcess can be used to plan, mobilize, coordinate and track situations. Use Case 1: How to use LiveProcess when you have a staff shortage Did you know that you can use LiveProcess for more than just big emergencies? The course will walk through all the components of the system that are used to notify staff of shortages and request coverage. You will learn how to create contact groups and send messages with responses. Use Case 2: Learn how to use LiveProcess when you experience an EMR Outage This course is designed to walk through planning, mobilizing and coordinating staff when you have a planned or unplanned outage of a critical IT system such as an EMR. LiveProcess elearning Courses Page 6 of 7
7 LiveProcess elearning Certificate Once you have completed all the courses appropriate to your user role, in a copy of the completed form and we will mail you a LiveProcess elearning Certificate. Please also complete the following information: Attendee Name: Organization: User Role: Address: Mailing Address: LiveProcess elearning Courses Page 7 of 7
LiveProcess Emergency Manager. User Guide
 LiveProcess Emergency Manager User Guide Table of Contents LOGIN... 6 Requirements... 6 Password Reset... 6 Remember Me... 7 DASHBOARD... 8 My Facilities... 9 Notifications Used... 9 Key Threats... 9 Quick
LiveProcess Emergency Manager User Guide Table of Contents LOGIN... 6 Requirements... 6 Password Reset... 6 Remember Me... 7 DASHBOARD... 8 My Facilities... 9 Notifications Used... 9 Key Threats... 9 Quick
COMMUNICATIONS EMERGENCY SUPPORT FUNCTION (ESF #2) FORMERLLY COMMUNICATIONS AND WARNING
 ICS Category: Operations ESF # 2 Responsible for the EOC message center, providing working radio & telephone equipment, and providing warning to vulnerable facilities Reports to the emergency management
ICS Category: Operations ESF # 2 Responsible for the EOC message center, providing working radio & telephone equipment, and providing warning to vulnerable facilities Reports to the emergency management
EXERCISE ACROSS ABBOTT How to Create an Event
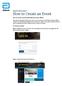 EXERCISE ACROSS ABBOTT How to Create an Event How to Create an Event with Exercise Across Abbott This step-by-step guide will show you how to create an Event on the Exercise Across Abbott website (www.exerciseacrossabbott.com).
EXERCISE ACROSS ABBOTT How to Create an Event How to Create an Event with Exercise Across Abbott This step-by-step guide will show you how to create an Event on the Exercise Across Abbott website (www.exerciseacrossabbott.com).
Building the Business Case for Emergency Notification
 Building the Business Case for Emergency Notification Presented by Michelle Gjerde, Marketing Director Amcom Software The Big Picture The fast growing BCM software market includes four components: Business
Building the Business Case for Emergency Notification Presented by Michelle Gjerde, Marketing Director Amcom Software The Big Picture The fast growing BCM software market includes four components: Business
Arizona Health Alert Network. Getting Started
 Arizona Health Alert Network Getting Started 1 2 Arizona Health Alert Network Uses The AzHan will serve as a redundant communication platform for your facilities to receive critical information from the
Arizona Health Alert Network Getting Started 1 2 Arizona Health Alert Network Uses The AzHan will serve as a redundant communication platform for your facilities to receive critical information from the
SECURITY TRAINING SECURITY TRAINING
 SECURITY TRAINING SECURITY TRAINING Addressing software security effectively means applying a framework of focused activities throughout the software lifecycle in addition to implementing sundry security
SECURITY TRAINING SECURITY TRAINING Addressing software security effectively means applying a framework of focused activities throughout the software lifecycle in addition to implementing sundry security
Introduction to Business continuity Planning
 Week - 06 Introduction to Business continuity Planning 1 Introduction The purpose of this lecture is to give an overview of what is Business Continuity Planning and provide some guidance and resources
Week - 06 Introduction to Business continuity Planning 1 Introduction The purpose of this lecture is to give an overview of what is Business Continuity Planning and provide some guidance and resources
: Course CDFOM : Certified Data Centre Facilities Operations Manager
 Module Title Duration : Course CDFOM : Certified Data Centre Facilities Operations Manager : 3 days Course Description Managing the facilities of today s hi-end and hi-availability data centres is an extremely
Module Title Duration : Course CDFOM : Certified Data Centre Facilities Operations Manager : 3 days Course Description Managing the facilities of today s hi-end and hi-availability data centres is an extremely
Emergency Management & Disaster Planning
 Emergency Management & Disaster Planning What we re going to talk about What is Emergency Management and Disaster Planning? What are the key elements of an EM Plan? Where does the University Architect
Emergency Management & Disaster Planning What we re going to talk about What is Emergency Management and Disaster Planning? What are the key elements of an EM Plan? Where does the University Architect
Business Continuity Planning Keeping Pace with New Technology
 Business Continuity Planning Keeping Pace with New Technology Old issues, new threats Force Majeure Increasing severe weather incidents, terrorist attacks Legacy modernization Cutover issues, system crashes,
Business Continuity Planning Keeping Pace with New Technology Old issues, new threats Force Majeure Increasing severe weather incidents, terrorist attacks Legacy modernization Cutover issues, system crashes,
GDPR: An Opportunity to Transform Your Security Operations
 GDPR: An Opportunity to Transform Your Security Operations McAfee SIEM solutions improve breach detection and response Is your security operations GDPR ready? General Data Protection Regulation (GDPR)
GDPR: An Opportunity to Transform Your Security Operations McAfee SIEM solutions improve breach detection and response Is your security operations GDPR ready? General Data Protection Regulation (GDPR)
Mission: Continuity BUILDING RESILIENCE AGAINST UNPLANNED SERVICE INTERRUPTIONS
 Mission: Continuity BUILDING RESILIENCE AGAINST UNPLANNED SERVICE INTERRUPTIONS Stephanie Poe, DNP, RN-BC CNIO, The Johns Hopkins Hospital and Health System Discussion Topics The Age of Acceleration Cyber
Mission: Continuity BUILDING RESILIENCE AGAINST UNPLANNED SERVICE INTERRUPTIONS Stephanie Poe, DNP, RN-BC CNIO, The Johns Hopkins Hospital and Health System Discussion Topics The Age of Acceleration Cyber
SECURITY & PRIVACY DOCUMENTATION
 Okta s Commitment to Security & Privacy SECURITY & PRIVACY DOCUMENTATION (last updated September 15, 2017) Okta is committed to achieving and preserving the trust of our customers, by providing a comprehensive
Okta s Commitment to Security & Privacy SECURITY & PRIVACY DOCUMENTATION (last updated September 15, 2017) Okta is committed to achieving and preserving the trust of our customers, by providing a comprehensive
Business Continuity Planning
 Business Continuity Planning The Unexpected Happens Be Ready Copyright -Business Survival Partners, llc. 2011 - All Rights Reserved www.survivalpartners.biz RISK 2 Risks to National Security A secure and
Business Continuity Planning The Unexpected Happens Be Ready Copyright -Business Survival Partners, llc. 2011 - All Rights Reserved www.survivalpartners.biz RISK 2 Risks to National Security A secure and
Continuous protection to reduce risk and maintain production availability
 Industry Services Continuous protection to reduce risk and maintain production availability Managed Security Service Answers for industry. Managing your industrial cyber security risk requires world-leading
Industry Services Continuous protection to reduce risk and maintain production availability Managed Security Service Answers for industry. Managing your industrial cyber security risk requires world-leading
Disclaimer Ground Rules
 Critical Success Factors in a Complex BCP Development Environment Don Groth Disclaimer Ground Rules The views and opinions expressed today do not necessarily reflect the position of Froedtert and Community
Critical Success Factors in a Complex BCP Development Environment Don Groth Disclaimer Ground Rules The views and opinions expressed today do not necessarily reflect the position of Froedtert and Community
CLASS ADMIN. Learning (SIU) Class Admin Responsibilities and Tools
 CLASS ADMIN Learning (SIU) Class Admin Responsibilities and Tools Table of Contents Select a line to jump to the corresponding section of the guide. SIU Class Admin... Role Description... Responsibility...
CLASS ADMIN Learning (SIU) Class Admin Responsibilities and Tools Table of Contents Select a line to jump to the corresponding section of the guide. SIU Class Admin... Role Description... Responsibility...
DXC Security Training
 DXC Security Training DXC Security Training Table of contents About DXC Security Training 2 About DXC Technology 3 Inforsec Registered Assessors Program (IRAP) 4 ISM Fundamentals 6 Cyber Security Incident
DXC Security Training DXC Security Training Table of contents About DXC Security Training 2 About DXC Technology 3 Inforsec Registered Assessors Program (IRAP) 4 ISM Fundamentals 6 Cyber Security Incident
2018 HIPAA One All Rights Reserved. Beyond HIPAA Compliance to Certification
 2018 HIPAA One All Rights Reserved. Beyond HIPAA Compliance to Certification Presenters Jared Hamilton CISSP CCSK, CCSFP, MCSE:S Healthcare Cybersecurity Leader, Crowe Horwath Erika Del Giudice CISA, CRISC,
2018 HIPAA One All Rights Reserved. Beyond HIPAA Compliance to Certification Presenters Jared Hamilton CISSP CCSK, CCSFP, MCSE:S Healthcare Cybersecurity Leader, Crowe Horwath Erika Del Giudice CISA, CRISC,
A Look Ahead: The RedVector Product Roadmap
 A Look Ahead: The RedVector Product Roadmap Agenda Overview 2016 Highlights 2017 YTD Coming Soon Q&A The RedVector Product Roadmap OVERVIEW RedVector Product Brands Architecture Basic Workplace Skills
A Look Ahead: The RedVector Product Roadmap Agenda Overview 2016 Highlights 2017 YTD Coming Soon Q&A The RedVector Product Roadmap OVERVIEW RedVector Product Brands Architecture Basic Workplace Skills
NA120 Network Automation 10.x Essentials
 Course Data Sheet NA120 Network Automation 10.x Essentials Course No.: NA120-101 Category/Sub Category: Operations Management/Network Management Center For software version(s): 9.0 10.1 Software version
Course Data Sheet NA120 Network Automation 10.x Essentials Course No.: NA120-101 Category/Sub Category: Operations Management/Network Management Center For software version(s): 9.0 10.1 Software version
FOUNDATION CERTIFICATE IN INFORMATION SECURITY v2.0 INTRODUCING THE TOP 5 DISCIPLINES IN INFORMATION SECURITY SUMMARY
 FOUNDATION CERTIFICATE IN INFORMATION SECURITY v2.0 INTRODUCING THE TOP 5 DISCIPLINES IN INFORMATION SECURITY SUMMARY The Foundation Certificate in Information Security (FCIS) course is designed to provide
FOUNDATION CERTIFICATE IN INFORMATION SECURITY v2.0 INTRODUCING THE TOP 5 DISCIPLINES IN INFORMATION SECURITY SUMMARY The Foundation Certificate in Information Security (FCIS) course is designed to provide
HEALTHCARE CERTIFICATION APPLICATION For CURENT FPEM s & FAEM s
 FLORIDA EMERGENCY PREPAREDNESS ASSOCIATION Applicant: Agency: FPEM-HC FAEM-HC HEALTHCARE CERTIFICATION APPLICATION For CURENT FPEM s & FAEM s February 19, 2017v.1 Applicants are encouraged to work with
FLORIDA EMERGENCY PREPAREDNESS ASSOCIATION Applicant: Agency: FPEM-HC FAEM-HC HEALTHCARE CERTIFICATION APPLICATION For CURENT FPEM s & FAEM s February 19, 2017v.1 Applicants are encouraged to work with
Simplifying Endpoint Management and Security For an Evolving and Complex Mobile Workforce
 Simplifying Endpoint Management and Security For an Evolving and Complex Mobile Workforce Michael Marfise Sr. Director, Product Management Yann Gaucher Sr. Director, Product Management Endpoint Protection
Simplifying Endpoint Management and Security For an Evolving and Complex Mobile Workforce Michael Marfise Sr. Director, Product Management Yann Gaucher Sr. Director, Product Management Endpoint Protection
ForeScout Extended Module for Splunk
 Enterprise Strategy Group Getting to the bigger truth. ESG Lab Review ForeScout Extended Module for Splunk Date: May 2017 Author: Tony Palmer, Senior Lab Analyst Abstract This report provides a first look
Enterprise Strategy Group Getting to the bigger truth. ESG Lab Review ForeScout Extended Module for Splunk Date: May 2017 Author: Tony Palmer, Senior Lab Analyst Abstract This report provides a first look
28: Manage WARN Notifications
 28: Manage WARN Notifications Chapter Contents WARN Overview... 28-1 Create WARN Notice (WARN Entry)... 28-2 Step 1 Company WARN Information... 28-3 Step 2 Company Location Information... 28-5 Step 3 Union
28: Manage WARN Notifications Chapter Contents WARN Overview... 28-1 Create WARN Notice (WARN Entry)... 28-2 Step 1 Company WARN Information... 28-3 Step 2 Company Location Information... 28-5 Step 3 Union
CISA Training.
 CISA Training www.austech.edu.au WHAT IS CISA TRAINING? The CISA, Certified Information Systems Auditor, is a professional designation which provides great benefits and increased influence for an individual
CISA Training www.austech.edu.au WHAT IS CISA TRAINING? The CISA, Certified Information Systems Auditor, is a professional designation which provides great benefits and increased influence for an individual
ITBA01IT IT Business Analytics Interactive Training Created by ART
 Course Data Sheet ITBA01IT IT Business Analytics 10.10 Interactive Training Created by ART Course No.: ITBA01IT-1010 Category/Sub Category: Operations Management / IT Business Analytics For software version(s):
Course Data Sheet ITBA01IT IT Business Analytics 10.10 Interactive Training Created by ART Course No.: ITBA01IT-1010 Category/Sub Category: Operations Management / IT Business Analytics For software version(s):
Measuring Critical Communications Effectiveness: An Analysis of Private Sector Broadcast Confirmation Data
 Measuring Critical Communications Effectiveness: An Analysis of Private Sector Broadcast Confirmation Data Executive Summary Successful crisis management depends on an organization s ability to manage
Measuring Critical Communications Effectiveness: An Analysis of Private Sector Broadcast Confirmation Data Executive Summary Successful crisis management depends on an organization s ability to manage
PROCESS SAFETY from POINT A to POINT Zed
 excellence in Dependable Automation PROCESS SAFETY from POINT A to POINT Zed From Functional Safety Assessment to Cybersecurity, exida can show you the way. www.exida.com exida: Your TRUSTED PARTNER Companies
excellence in Dependable Automation PROCESS SAFETY from POINT A to POINT Zed From Functional Safety Assessment to Cybersecurity, exida can show you the way. www.exida.com exida: Your TRUSTED PARTNER Companies
CPD for Financial Planners
 CPD for Financial Planners This leaflet is a quick guide to what is required to meet the CISI and/or RDR CPD requirements. The CISI CPD Scheme The CISI CPD Scheme is a free online logging system that enables
CPD for Financial Planners This leaflet is a quick guide to what is required to meet the CISI and/or RDR CPD requirements. The CISI CPD Scheme The CISI CPD Scheme is a free online logging system that enables
CompTIA Cybersecurity Analyst+
 CompTIA Cybersecurity Analyst+ Course CT-04 Five days Instructor-Led, Hands-on Introduction This five-day, instructor-led course is intended for those wishing to qualify with CompTIA CSA+ Cybersecurity
CompTIA Cybersecurity Analyst+ Course CT-04 Five days Instructor-Led, Hands-on Introduction This five-day, instructor-led course is intended for those wishing to qualify with CompTIA CSA+ Cybersecurity
Profound UI IBM Messaging System (After)
 Profound UI IBM Messaging System (After) We currently have a sidebar menu on each of our menu screens. We added a message bubble the user can click to enter the ICS Message Center: If the user has unread
Profound UI IBM Messaging System (After) We currently have a sidebar menu on each of our menu screens. We added a message bubble the user can click to enter the ICS Message Center: If the user has unread
Getting Started with the Teacher Information Management System (TIMS)
 Getting Started with the Teacher Information Management System (TIMS) How Will This Presentation Help Me? This presentation is designed to help you: Access TIMS for the first time Introduce you to your
Getting Started with the Teacher Information Management System (TIMS) How Will This Presentation Help Me? This presentation is designed to help you: Access TIMS for the first time Introduce you to your
Process Safety Management Training
 IHS OPERATIONAL EXCELLENCE & RISK MANAGEMENT Process Safety Management Training Leverage state-of-the-art resources and practical knowhow to learn about proven management system concepts and techniques.
IHS OPERATIONAL EXCELLENCE & RISK MANAGEMENT Process Safety Management Training Leverage state-of-the-art resources and practical knowhow to learn about proven management system concepts and techniques.
COURSE BROCHURE CISA TRAINING
 COURSE BROCHURE CISA TRAINING What is CISA? The CISA, Certified Information Systems Auditor, is a professional designation which provides great benefits and increased influence for an individual within
COURSE BROCHURE CISA TRAINING What is CISA? The CISA, Certified Information Systems Auditor, is a professional designation which provides great benefits and increased influence for an individual within
Curriculum Solutions Core curriculum FREE elearning over 300 courses FREE access to the ereference library MS Certifications
 1 2 3 4 What is the ITA Program let me give you a high level overview before we take a look at the top benefits in detail. The program is a global annual subscription program and offers an off the shelf
1 2 3 4 What is the ITA Program let me give you a high level overview before we take a look at the top benefits in detail. The program is a global annual subscription program and offers an off the shelf
Technical Review Managing Risk, Complexity, and Cost with SanerNow Endpoint Security and Management Platform
 Technical Review Managing Risk, Complexity, and Cost with SanerNow Endpoint Security and Management Platform Date: October, 2018 Author: Jack Poller, Sr. Analyst The Challenges Enterprise Strategy Group
Technical Review Managing Risk, Complexity, and Cost with SanerNow Endpoint Security and Management Platform Date: October, 2018 Author: Jack Poller, Sr. Analyst The Challenges Enterprise Strategy Group
Administrator Quick Reference
 Contents Adding a New User... 2 Adding a New Crew Member.... 4 Adding a New Location.... 6 Resetting a Forgotten Password... 8 Adding a New User Any member of your organization - field providers, reviewers,
Contents Adding a New User... 2 Adding a New Crew Member.... 4 Adding a New Location.... 6 Resetting a Forgotten Password... 8 Adding a New User Any member of your organization - field providers, reviewers,
Oman Medical Specialty Board (OMSB) Sultanate of Oman FAQs
 Oman Medical Specialty Board (OMSB) Sultanate of Oman FAQs 1. What is the DataFlow Group? The DataFlow Group is a leading global provider of specialized Primary Source Verification (PSV) solutions, and
Oman Medical Specialty Board (OMSB) Sultanate of Oman FAQs 1. What is the DataFlow Group? The DataFlow Group is a leading global provider of specialized Primary Source Verification (PSV) solutions, and
Healthcare Privacy and Security:
 Healthcare Privacy and Security: Breach prevention and mitigation/ Insuring for breach Colin J. Zick Foley Hoag LLP (617) 832-1000 www.foleyhoag.com www.securityprivacyandthelaw.com Boston Bar Association
Healthcare Privacy and Security: Breach prevention and mitigation/ Insuring for breach Colin J. Zick Foley Hoag LLP (617) 832-1000 www.foleyhoag.com www.securityprivacyandthelaw.com Boston Bar Association
EU General Data Protection Regulation (GDPR) Achieving compliance
 EU General Data Protection Regulation (GDPR) Achieving compliance GDPR enhancing data protection and privacy The new EU General Data Protection Regulation (GDPR) will apply across all EU member states,
EU General Data Protection Regulation (GDPR) Achieving compliance GDPR enhancing data protection and privacy The new EU General Data Protection Regulation (GDPR) will apply across all EU member states,
IBM Security Services Overview
 Services Overview Massimo Nardone Senior Lead IT Security Architect Global Technology Services, IBM Internet Security Systems massimo.nardone@fi.ibm.com THE VEHICLE THE SKILL THE SOLUTION Today s Business
Services Overview Massimo Nardone Senior Lead IT Security Architect Global Technology Services, IBM Internet Security Systems massimo.nardone@fi.ibm.com THE VEHICLE THE SKILL THE SOLUTION Today s Business
Recertification Handbook
 Recertification Handbook NACAS 3 Boar's Head Lane, Suite B Charlottesville, VA 22903 Phone 434-245-8425 Fax 434-245-8453 nacas.org/casp casp@nacas.org Congratulations on receiving the CASP designation!
Recertification Handbook NACAS 3 Boar's Head Lane, Suite B Charlottesville, VA 22903 Phone 434-245-8425 Fax 434-245-8453 nacas.org/casp casp@nacas.org Congratulations on receiving the CASP designation!
113 BSIMM Activities at a Glance
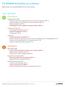 113 BSIMM Activities at a Glance (Red indicates most observed BSIMM activity in that practice) Level 1 Activities Governance Strategy & Metrics (SM) Publish process (roles, responsibilities, plan), evolve
113 BSIMM Activities at a Glance (Red indicates most observed BSIMM activity in that practice) Level 1 Activities Governance Strategy & Metrics (SM) Publish process (roles, responsibilities, plan), evolve
STANDARD ELECTRIC UNIVERSITY
 STANDARD ELECTRIC UNIVERSITY Technical Classes Catalog 2018 Bringing YOU the training you asked for! WHAT? Standard Electric Supply Co. offers numerous training opportunities to keep our customers as up-todate
STANDARD ELECTRIC UNIVERSITY Technical Classes Catalog 2018 Bringing YOU the training you asked for! WHAT? Standard Electric Supply Co. offers numerous training opportunities to keep our customers as up-todate
Florida State University
 Florida State University Disaster Recovery & Business Continuity Planning Overview October 24, 2017 1 Key Readiness Questions Has your department identified the business functions and infrastructure that
Florida State University Disaster Recovery & Business Continuity Planning Overview October 24, 2017 1 Key Readiness Questions Has your department identified the business functions and infrastructure that
Player Pathway System User Guide for Coaches and Team Managers
 Player Pathway System User Guide for Coaches and Team Managers I am a Coach I can see... A summary of my profile A summary of my profile Which squads I manage What certificates I have What roles I have
Player Pathway System User Guide for Coaches and Team Managers I am a Coach I can see... A summary of my profile A summary of my profile Which squads I manage What certificates I have What roles I have
Welcome to the Hyster Training Knowledge Center
 Welcome to the Hyster Training Knowledge Center 1. TKC Overview 1 2. User s Guide 3 3. Manager s Guide 7 4. Frequently Asked Questions CERTECH 15 5. Frequently Asked Questions CERTRACX 17 6. TKC Issues
Welcome to the Hyster Training Knowledge Center 1. TKC Overview 1 2. User s Guide 3 3. Manager s Guide 7 4. Frequently Asked Questions CERTECH 15 5. Frequently Asked Questions CERTRACX 17 6. TKC Issues
The Soccer Box Coaches & Managers
 The Soccer Box Coaches & Managers Quick Start - Building Your Team STEP 1 Register your team STEP 2 Receive Invitation for Bonzi Team Add your players to send invitation link for the team. STEP 3 Your
The Soccer Box Coaches & Managers Quick Start - Building Your Team STEP 1 Register your team STEP 2 Receive Invitation for Bonzi Team Add your players to send invitation link for the team. STEP 3 Your
Unified Incident Command and Decision Support (UICDS)
 Unified Incident Command and Decision Support (UICDS) UICDS is the middleware foundation that enables information sharing and decision support among commercial and government incident management technologies
Unified Incident Command and Decision Support (UICDS) UICDS is the middleware foundation that enables information sharing and decision support among commercial and government incident management technologies
DEVELOP YOUR TAILORED CYBERSECURITY ROADMAP
 ARINC cybersecurity solutions DEVELOP YOUR TAILORED CYBERSECURITY ROADMAP Getting started is as simple as assessing your baseline THE RIGHT CYBERSECURITY SOLUTIONS FOR YOUR UNIQUE NEEDS Comprehensive threat
ARINC cybersecurity solutions DEVELOP YOUR TAILORED CYBERSECURITY ROADMAP Getting started is as simple as assessing your baseline THE RIGHT CYBERSECURITY SOLUTIONS FOR YOUR UNIQUE NEEDS Comprehensive threat
Uptime and Proactive Support Services
 Uptime and Proactive Support Services We ll accelerate your journey to sustainable IT optimisation and ensure that your technology is delivering all that it can. We ll keep your IT infrastructure up and
Uptime and Proactive Support Services We ll accelerate your journey to sustainable IT optimisation and ensure that your technology is delivering all that it can. We ll keep your IT infrastructure up and
Mississippi Emergency Support Function #12 Energy Annex
 ESF #12 Coordinator Mississippi Public Utilities Staff Primary Agencies Mississippi Public Utilities Staff Support Agencies Mississippi Emergency Management Agency Mississippi Public Service Commission
ESF #12 Coordinator Mississippi Public Utilities Staff Primary Agencies Mississippi Public Utilities Staff Support Agencies Mississippi Emergency Management Agency Mississippi Public Service Commission
Emergency Operations Center Management Exercise Evaluation Guide
 Emergency Operations Center Management Exercise Evaluation Guide I respectfully submit the completed Exercise Evaluation Guide for the Canopy Oaks Tabletop Exercise conducted March 25 2010 for the Leon
Emergency Operations Center Management Exercise Evaluation Guide I respectfully submit the completed Exercise Evaluation Guide for the Canopy Oaks Tabletop Exercise conducted March 25 2010 for the Leon
Security Communications and Awareness
 Security Communications and Awareness elearning OVERVIEW Recent high-profile incidents underscore the need for security awareness training. In a world where your employees are frequently exposed to sophisticated
Security Communications and Awareness elearning OVERVIEW Recent high-profile incidents underscore the need for security awareness training. In a world where your employees are frequently exposed to sophisticated
Section 1 Metrics: Community Adoption
 FY07 NIMS Compliance Metrics: Local/Tribal Section 1 Metrics: Community Adoption Compliance Requirement: Adopt NIMS at the community level for all government departments and agencies; as well as promote
FY07 NIMS Compliance Metrics: Local/Tribal Section 1 Metrics: Community Adoption Compliance Requirement: Adopt NIMS at the community level for all government departments and agencies; as well as promote
FEMA Update. Tim Greten Technological Hazards Division Deputy Director. NREP April 2017
 FEMA Update Tim Greten Technological Hazards Division Deputy Director NREP April 2017 FEMA Strategic Priorities Priority 1: Be survivor-centric in mission and program delivery. Priority 2: Become an expeditionary
FEMA Update Tim Greten Technological Hazards Division Deputy Director NREP April 2017 FEMA Strategic Priorities Priority 1: Be survivor-centric in mission and program delivery. Priority 2: Become an expeditionary
Appendix 3 Disaster Recovery Plan
 Appendix 3 Disaster Recovery Plan DRAFT March 5, 2007 Revision XX Qwest Government Services, Inc. 4250 North Fairfax Drive Arlington, VA 22203 A3-i RFP: TQC-JTB-05-0002 March 5, 2007 REVISION HISTORY Revision
Appendix 3 Disaster Recovery Plan DRAFT March 5, 2007 Revision XX Qwest Government Services, Inc. 4250 North Fairfax Drive Arlington, VA 22203 A3-i RFP: TQC-JTB-05-0002 March 5, 2007 REVISION HISTORY Revision
IBM Security Intelligence on Cloud
 Service Description IBM Security Intelligence on Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means and includes the company, its authorized users or recipients
Service Description IBM Security Intelligence on Cloud This Service Description describes the Cloud Service IBM provides to Client. Client means and includes the company, its authorized users or recipients
Louisiana Firefighter and Emergency Responder Certification System
 Louisiana Firefighter and Emergency Responder Certification System Fire Officer IV (NFPA 1021, 2009 Edition) Approved April 24, 2013 by CAC Louisiana State University Fire & Emergency Training Institute
Louisiana Firefighter and Emergency Responder Certification System Fire Officer IV (NFPA 1021, 2009 Edition) Approved April 24, 2013 by CAC Louisiana State University Fire & Emergency Training Institute
Securing Your Digital Transformation
 Securing Your Digital Transformation Security Consulting Managed Security Leveraging experienced, senior experts to help define and communicate risk and security program strategy using real-world data,
Securing Your Digital Transformation Security Consulting Managed Security Leveraging experienced, senior experts to help define and communicate risk and security program strategy using real-world data,
365 Notify User Guide. 365 Mechanix Pty Ltd
 365 Notify User Guide About 365 Notify How it works 365 Notify is a Dynamics 365 add-on which delivers notifications to users, contacts, accounts or any other records based on your business needs and activity
365 Notify User Guide About 365 Notify How it works 365 Notify is a Dynamics 365 add-on which delivers notifications to users, contacts, accounts or any other records based on your business needs and activity
What Does the Future Look Like for Business Continuity Professionals?
 What Does the Future Look Like for Business Continuity Professionals? October 26, 2016 Brian Zawada, FBCI President, US Chapter of the Business Continuity Institute Agenda and Objectives Change Standards
What Does the Future Look Like for Business Continuity Professionals? October 26, 2016 Brian Zawada, FBCI President, US Chapter of the Business Continuity Institute Agenda and Objectives Change Standards
This course contains the subject matter to prepare candidates for the ivanti Certified Service Desk 2017 Administrator exam.
 Course Overview The Service Desk Administration 2017 course is a five-day training course covering topics for both administrative and design functions within the Service Desk 2017. Students will learn
Course Overview The Service Desk Administration 2017 course is a five-day training course covering topics for both administrative and design functions within the Service Desk 2017. Students will learn
Safety Systems are the New Target Design Security Using Safety Methods
 SESSION ID: SBX4-W4 Safety Systems are the New Target Design Security Using Safety Methods Marty Edwards Director of Strategic Initiatives International Society of Automation (ISA) @ICS_Marty Disclaimer
SESSION ID: SBX4-W4 Safety Systems are the New Target Design Security Using Safety Methods Marty Edwards Director of Strategic Initiatives International Society of Automation (ISA) @ICS_Marty Disclaimer
ZAXBY S LEARNING CENTER OTM USER GUIDE
 ZAXBY S LEARNING CENTER OTM USER GUIDE 33 2013 Revised September 2014 Version 5 HOME PAGE After successfully submitting login information, the Zaxby s Learning Center (ZLC) Home page appears. A red main
ZAXBY S LEARNING CENTER OTM USER GUIDE 33 2013 Revised September 2014 Version 5 HOME PAGE After successfully submitting login information, the Zaxby s Learning Center (ZLC) Home page appears. A red main
A guide to CompTIA training and certification DDLS Australia Pty Ltd
 A guide to CompTIA training and certification 1 DDLS DDLS is an accredited CompTIA training organisation, offering the courses needed to establish CompTIA A+, Linux+, Network+, and Security+. DDLS can
A guide to CompTIA training and certification 1 DDLS DDLS is an accredited CompTIA training organisation, offering the courses needed to establish CompTIA A+, Linux+, Network+, and Security+. DDLS can
The Role of IT in HIPAA Security & Compliance
 The Role of IT in HIPAA Security & Compliance Mario Cruz OFMQ Chief Information Officer For audio, you must use your phone: Step 1: Call (866) 906-0123. Step 2: Enter code 2071585#. Mario Cruz Mario Cruz
The Role of IT in HIPAA Security & Compliance Mario Cruz OFMQ Chief Information Officer For audio, you must use your phone: Step 1: Call (866) 906-0123. Step 2: Enter code 2071585#. Mario Cruz Mario Cruz
ORA HIPAA Security. All Affiliate Research Policy Subject: HIPAA Security File Under: For Researchers
 All Affiliate Research Policy Subject: HIPAA File Under: For Researchers ORA HIPAA Issuing Department: Office of Research Administration Original Policy Date Page 1 of 5 Approved by: May 9,2005 Revision
All Affiliate Research Policy Subject: HIPAA File Under: For Researchers ORA HIPAA Issuing Department: Office of Research Administration Original Policy Date Page 1 of 5 Approved by: May 9,2005 Revision
Excel Professionally.IMPACT Urban Youth
 TM Basic Etiquette/Protocol Certification Information Packet Excel Professionally.IMPACT Urban Youth NAUEP * P.O. Box 3641 * Cedar Hill, Texas * 75106 * 800.291.6492 * cert@urbangirlz.org 2010 2014. NAUEP.
TM Basic Etiquette/Protocol Certification Information Packet Excel Professionally.IMPACT Urban Youth NAUEP * P.O. Box 3641 * Cedar Hill, Texas * 75106 * 800.291.6492 * cert@urbangirlz.org 2010 2014. NAUEP.
Duration: 5 Days Course Code: M20764 Version: B Delivery Method: Elearning (Self-paced)
 Administering a SQL Database Infrastructure Duration: 5 Days Course Code: M20764 Version: B Delivery Method: Elearning (Self-paced) Overview: This five-day instructor-led course provides students who administer
Administering a SQL Database Infrastructure Duration: 5 Days Course Code: M20764 Version: B Delivery Method: Elearning (Self-paced) Overview: This five-day instructor-led course provides students who administer
Bonzi Team 101 (Youth Sports): What does Bonzi Team do?
 Bonzi Team 101 (Youth Sports): What does Bonzi Team do? AA-00427 Bonzi Team is an extension of your Club or League software that imports all team information directly from your software to Bonzi Team,
Bonzi Team 101 (Youth Sports): What does Bonzi Team do? AA-00427 Bonzi Team is an extension of your Club or League software that imports all team information directly from your software to Bonzi Team,
Advanced Health Features
 Family Access Health Information WS\FA\FM\PS\CF\DA if you want Vaccinations to show and if you want compliance status to show health information you want Families to see, and if you want Notes to display
Family Access Health Information WS\FA\FM\PS\CF\DA if you want Vaccinations to show and if you want compliance status to show health information you want Families to see, and if you want Notes to display
AROC Online Services (AOS) User Manual
 AROC Online Services (AOS) User Manual Version 5.0 (September 2014) FIM/WeeFIM (Workshops) Contents Introduction... 2 Flow chart of AOS functionality... 2 Computing requirements... 2 Session time-out...
AROC Online Services (AOS) User Manual Version 5.0 (September 2014) FIM/WeeFIM (Workshops) Contents Introduction... 2 Flow chart of AOS functionality... 2 Computing requirements... 2 Session time-out...
ACCREDITED HEALTH & SAFETY SHORT COURSES
 ACCREDITED HEALTH & SAFETY 2018 ACCREDITED HEALTH & SAFETY INTRODUCTION Our services benefit any organization dedicated to the development and enhancement of skills and knowledge through training. Frontline
ACCREDITED HEALTH & SAFETY 2018 ACCREDITED HEALTH & SAFETY INTRODUCTION Our services benefit any organization dedicated to the development and enhancement of skills and knowledge through training. Frontline
No IT Audit Staff? How to Hack an IT Audit. Presenters. Mark Bednarz, Partner-In-Charge, Risk Advisory PKF O Connor Davies, LLP
 No IT Audit Staff? How to Hack an IT Audit Presenters Mark Bednarz, Partner-In-Charge, Risk Advisory PKF O Connor Davies, LLP Learning Objectives After this session, participants will be able to: Devise
No IT Audit Staff? How to Hack an IT Audit Presenters Mark Bednarz, Partner-In-Charge, Risk Advisory PKF O Connor Davies, LLP Learning Objectives After this session, participants will be able to: Devise
Technical Education Catalog 2017
 Technical Education Webinars and Classroom Training JMA Wireless Technical Education Series offers instruction for people designing, installing, and commissioning the JMA Wireless TEKO DAS Platform, Transmission
Technical Education Webinars and Classroom Training JMA Wireless Technical Education Series offers instruction for people designing, installing, and commissioning the JMA Wireless TEKO DAS Platform, Transmission
Industrial Control Systems November 18, 2015
 Industrial Control Systems November 18, 2015 ABOUT SANS - TRAINING SANS provides intensive, hands-on, immersion training Highest quality 70+ courses covering basic security skills to cutting edge topics
Industrial Control Systems November 18, 2015 ABOUT SANS - TRAINING SANS provides intensive, hands-on, immersion training Highest quality 70+ courses covering basic security skills to cutting edge topics
Certificate in Security Management
 Certificate in Security Management Page 1 of 6 Why Attend This course will provide participants with an insight into the fundamentals of managing modern and effective security operations. It will address
Certificate in Security Management Page 1 of 6 Why Attend This course will provide participants with an insight into the fundamentals of managing modern and effective security operations. It will address
Developing a Holistic Strategy To Achieve Community Health Resilience
 Developing a Holistic Strategy To Achieve Community Health Resilience Paula Scalingi, Director Pacific Northwest Center for Regional Disaster Resilience Pacific Northwest Border Health Alliance Seventh
Developing a Holistic Strategy To Achieve Community Health Resilience Paula Scalingi, Director Pacific Northwest Center for Regional Disaster Resilience Pacific Northwest Border Health Alliance Seventh
Ultimate, Real-Time Mail Tracking and Notifications
 Ultimate, Real-Time Mail Tracking and Notifications Job List Summary See all of your most recent jobs in this comprehensive summary view that provides real-time scan and statistical information at the
Ultimate, Real-Time Mail Tracking and Notifications Job List Summary See all of your most recent jobs in this comprehensive summary view that provides real-time scan and statistical information at the
TS Advantage Feature Quick Reference Guide
 TS Advantage Feature Quick Reference Gold Deep Technology Platinum IT Agility Enhance IT Agility Bronze Operational Silver Technical Reduce time to restoration Reduce unplanned Reduce planned Reduce time
TS Advantage Feature Quick Reference Gold Deep Technology Platinum IT Agility Enhance IT Agility Bronze Operational Silver Technical Reduce time to restoration Reduce unplanned Reduce planned Reduce time
Standard CIP Cyber Security Electronic Security Perimeter(s)
 A. Introduction 1. Title: Cyber Security Electronic Security Perimeter(s) 2. Number: CIP-005-1 3. Purpose: Standard CIP-005 requires the identification and protection of the Electronic Security Perimeter(s)
A. Introduction 1. Title: Cyber Security Electronic Security Perimeter(s) 2. Number: CIP-005-1 3. Purpose: Standard CIP-005 requires the identification and protection of the Electronic Security Perimeter(s)
Securing the Grid and Your Critical Utility Functions. April 24, 2017
 Securing the Grid and Your Critical Utility Functions April 24, 2017 1 Securing the Grid Effectively and Efficiently Recent threats to the Electric Grid and the importance of security Standards and Requirements
Securing the Grid and Your Critical Utility Functions April 24, 2017 1 Securing the Grid Effectively and Efficiently Recent threats to the Electric Grid and the importance of security Standards and Requirements
Cisco SP Wi-Fi Solution Support, Optimize, Assurance, and Operate Services
 Service Overview Cisco SP Wi-Fi Solution Support, Optimize, Assurance, and Operate Services Cisco Service Provider (SP) Wi-Fi is a single, unified architecture for all types of Wi-Fi services and business
Service Overview Cisco SP Wi-Fi Solution Support, Optimize, Assurance, and Operate Services Cisco Service Provider (SP) Wi-Fi is a single, unified architecture for all types of Wi-Fi services and business
Certified Information Security Manager (CISM) Course Overview
 Certified Information Security Manager (CISM) Course Overview This course teaches students about information security governance, information risk management, information security program development,
Certified Information Security Manager (CISM) Course Overview This course teaches students about information security governance, information risk management, information security program development,
Enable Continuity for all users on all domains on the account to comply with business continuity regulations.
 If you make setting changes, allow a few minutes for the changes to take effect. Important If your organization is using LDAP Authentication and your LDAP server goes offline, the Barracuda Email Security
If you make setting changes, allow a few minutes for the changes to take effect. Important If your organization is using LDAP Authentication and your LDAP server goes offline, the Barracuda Email Security
Team Management. Coaches and Team Managers Guide
 Team Management Coaches and Team Managers Guide November 2015 Table of Contents Table of Contents Overview Audience About the Mobile App Examples Creating a Sport Ngin Account Accessing Team Center For
Team Management Coaches and Team Managers Guide November 2015 Table of Contents Table of Contents Overview Audience About the Mobile App Examples Creating a Sport Ngin Account Accessing Team Center For
CERT Organization. CERT Basic Training Unit 6
 CERT Organization Unit 6 Unit Objectives Describe the CERT structure Identify how CERTs interrelate with ICS Explain documentation requirements 6-1 Unit Topics CERT Organization Mobilization Documentation
CERT Organization Unit 6 Unit Objectives Describe the CERT structure Identify how CERTs interrelate with ICS Explain documentation requirements 6-1 Unit Topics CERT Organization Mobilization Documentation
Halo Administrator GUIDE
 Halo Administrator GUIDE Contents Welcome to Halo... 3 Secure Sign-In... 4 Forgot Password... 4 Messages... 5 Create and Send a Message... 5 Message Enhancements... 6 Quick Note... 6 Mark as Urgent...
Halo Administrator GUIDE Contents Welcome to Halo... 3 Secure Sign-In... 4 Forgot Password... 4 Messages... 5 Create and Send a Message... 5 Message Enhancements... 6 Quick Note... 6 Mark as Urgent...
Track Enhancement #2
 Track Enhancement #2 (Feature ID: 356) The Automate Waiting List enhancement (Feature ID: 356) has been incorporated into NavplusQA.nefec.org for District Admin quality assurance testing. The purpose of
Track Enhancement #2 (Feature ID: 356) The Automate Waiting List enhancement (Feature ID: 356) has been incorporated into NavplusQA.nefec.org for District Admin quality assurance testing. The purpose of
efundi Tutorial: Sign-up
 efundi Tutorial: Sign-up The Sign-up tool was created to replace the "sign up sheets on the door" with an online alternative. The tool allows students to sign up for office hours, meetings, review sessions
efundi Tutorial: Sign-up The Sign-up tool was created to replace the "sign up sheets on the door" with an online alternative. The tool allows students to sign up for office hours, meetings, review sessions
CLOUD GOVERNANCE SPECIALIST Certification
 CLOUD GOVERNANCE SPECIALIST Certification The Cloud Professional (CCP) program from Arcitura is dedicated to excellence in the fields of cloud computing technology, mechanisms, platforms, architecture,
CLOUD GOVERNANCE SPECIALIST Certification The Cloud Professional (CCP) program from Arcitura is dedicated to excellence in the fields of cloud computing technology, mechanisms, platforms, architecture,
Welcome to your LIVE EMS Online Training!
 Welcome to your LIVE EMS Online Training! Note: In order to receive credit for each lecture and gain access to the quiz you must attend each lecture for the duration and participate at a minimum every
Welcome to your LIVE EMS Online Training! Note: In order to receive credit for each lecture and gain access to the quiz you must attend each lecture for the duration and participate at a minimum every
VMware vcloud Air Accelerator Service
 DATASHEET AT A GLANCE The VMware vcloud Air Accelerator Service assists customers with extending their private VMware vsphere environment to a VMware vcloud Air public cloud. This Accelerator Service engagement
DATASHEET AT A GLANCE The VMware vcloud Air Accelerator Service assists customers with extending their private VMware vsphere environment to a VMware vcloud Air public cloud. This Accelerator Service engagement
Identifying the Skills and Team Members Needed to Support Synchronous Online Sessions and Webinars
 www.elearningguild.com Identifying the Skills and Team Members Needed to Support Synchronous Online Sessions and Webinars Karen Hyder, The elearning Guild 304 Identifying the Skills and Team Members Needed
www.elearningguild.com Identifying the Skills and Team Members Needed to Support Synchronous Online Sessions and Webinars Karen Hyder, The elearning Guild 304 Identifying the Skills and Team Members Needed
Addressing Vulnerabilities By Integrating Your Incident Response Plans. Brian Coates Enaxis Consulting
 Addressing Vulnerabilities By Integrating Your Incident Response Plans Brian Coates Enaxis Consulting Contents Enaxis Introduction Presenter Bio: Brian Coates Incident Response / Incident Management in
Addressing Vulnerabilities By Integrating Your Incident Response Plans Brian Coates Enaxis Consulting Contents Enaxis Introduction Presenter Bio: Brian Coates Incident Response / Incident Management in
EM L04 Using Workflow to Manage Your Patch Process and Follow CISSP Best Practices
 EM L04 Using Workflow to Manage Your Patch Process and Follow CISSP Best Practices Hands-On Lab Description Most corporations today have some form of patch process in place. In this session, you will learn
EM L04 Using Workflow to Manage Your Patch Process and Follow CISSP Best Practices Hands-On Lab Description Most corporations today have some form of patch process in place. In this session, you will learn
Agenda Event Analysis Subcommittee Conference Call
 Agenda Event Analysis Subcommittee Conference Call August 14, 2013 11:00 a.m. 1:00 p.m. Eastern Ready Talk Conference Call and Web Meeting Information: Dial-In: 1-866-740-1260 Access Code: 6517175 Security
Agenda Event Analysis Subcommittee Conference Call August 14, 2013 11:00 a.m. 1:00 p.m. Eastern Ready Talk Conference Call and Web Meeting Information: Dial-In: 1-866-740-1260 Access Code: 6517175 Security
