DirectLine for Business AS2 USER GUIDE
|
|
|
- Maryann Dalton
- 6 years ago
- Views:
Transcription
1 DirectLine for Business AS2 USER GUIDE
2 Contents BMO AS2 Service...1 Introduction... 1 Overview... 1 ICS AS2 Mailbox User... 2 AS2 Mailbox Service Setup...3 Before You Begin... 3 Connectivity Testing... 3 Inbound (to BMO) Mail Slots...3 Outbound (from BMO) Mail Slots... 4 Appendix A AS2 Services Client Questionnaire...5 Appendix B - Definitions...8 File encoding... 8 Other definitions... 8 Use of DirectLine for Business is subject to applicable agreements. i DirectLine is a registered trade-mark of Bank of Montreal. Other products and services not listed above are trademarks, service marks, or registered trademarks of their respective companies. Interchange services is a service mark of GXS, Inc. BMO-FG-GXS-AS
3 BMO AS2 Service INTRODUCTION This guide explains how to configure your system to allow secured communication over the Internet via Applicability Statement 2, or AS2, with a client (third party software) and to begin exchanging files and reports with BMO Bank of Montreal (BMO). This service is provided in conjunction with Global exchange Services, Inc. (GXS). AS2 is a second-generation specification that is designed to be a secure method of transmitting business documents over the Internet using HTTP. The EDIINT (EDI over the Internet) Working Group of the Internet Engineering Task Force (IETF) developed the AS2 protocol. BMO s AS2 service is an AS2-compliant, Drummond Group /UCCnet certified system for sending and receiving EDI, XML, and other proprietary documents. This service is designed to interoperate efficiently with other external AS2 Drummond Group/UCCnet certified systems. The AS2 service supports both inbound and outbound data processing. It also allows both standard and secure connections using the Internet Security Facility. OVERVIEW BMO s AS2 service allows you to exchange various Cash Management files and reports over the Internet using the AS2 protocol, while providing security and authentication of document receipt. Security and encryption of the documents is provided using S/MIME Version 3, an IETF standard defined in RFC If you have existing AS2 software, the AS2 service allows you to leverage that software and connect to BMO. To use AS2 service, BMO will provide you with a mailbox and password in order to send and receive documents. If you do not have certified AS2 software, software can be provided at additional cost. PAGE 1 FOR ASSISTANCE, PLEASE CALL THE HELP DESK AT
4 ICS AS2 MAILBOX USER As an AS2 mailbox user, you use AS2 as the transport method to exchange data with BMO. Inbound Data to the BMO: When you want to send data to BMO, your AS2 software will encrypt the data, add the digital signature, and send the data out across the Internet to the GXS AS2 service ( The GXS AS2 web server receives your data, validates the sender, authenticates the data through the digital signature, decrypts the data, and routes the data to BMO. Outbound Data from BMO: When BMO sends files or reports to your mailbox, the GXS AS2 service will encrypt the data, add digital signatures, and send the data out across the Internet to your AS2 server. Picture 1 PAGE 2 FOR ASSISTANCE, PLEASE CALL THE HELP DESK AT
5 AS2 Mailbox Service Setup BEFORE YOU BEGIN The items listed below are required before you begin the setup. 1. Obtain a Security Certificate from one of the authorized providers. Authorized providers are: Verisign, Inc. Digital Signature Trust SM While it is strongly recommended that you use a 3 rd party certificate, we will also accept self-initiated certificates. The certificate may be a business or personal level certificate. 2. Obtain AS2 client software. Our service requires the use of a Drummond Group/UCCnet certified client. (Go to 3. Obtain your mailbox ID, password, and contact information. The BMO Implementation Specialist (IS) will provide this information, once implementation has started. CONNECTIVITY TESTING Follow the steps below to set up an AS2 mailbox. 1. Install and setup your AS2 client software. 2. An IS will contact you to exchange security certificate information (public key), and to obtain your AS2 listener URL for use in the AS2 setup on the service. We will install your filename.p7c certificate (public key) on the GXS side to facilitate the encryption. You will install the GXS.P7C certificate (public key) on your system (AS2 client software) to enable encryption on your side. 3. Once the certificates are installed on each side, an IS will schedule a test to ensure that connectivity has been setup successfully. 4. IS will confirm your inbound and outbound trading relationships (mail slots) with you. INBOUND (TO BMO) MAIL SLOTS Once you have been set up you can send files to BMO from your mailbox. In order to send files you must know your mail slots. Depending on the number of services with us, you may have more than one inbound mail slot. Your inbound mail slot consists of the following: Application name provided by IS; Application document type provided by IS; File encoding provided by you when implementation was requested. PAGE 3 FOR ASSISTANCE, PLEASE CALL THE HELP DESK AT
6 When you are sending an Electronic Funds Transfer (EFT) file to BMO, your inbound trading relationship will look as follows: DEFT-DEFT80-A where DEFT is application name, DEFT80 is document type, A is encoding. The above mail slot means that you can send BMO 80 byte EFT files in ASCII format. Please work with your IS to get details of all of your inbound trading relationships. IMPORTANT: AS2 requires a separate AS2 ID for each mail slot. IS will provide you with the AS2 Ids for each inbound mail slot. This will allow you to send files to BMO. OUTBOUND (FROM BMO) MAIL SLOTS BMO will send your reports and files to your mailbox. Depending on the number of services you have with us, you may have more than one outbound mail slot (also known as an outbound trading relationship). Your outbound mail slot consists of the following: Mailbox ID provided by IS Application name provided by IS Application document type provided by IS File encoding provided by you when implementation was requested. BMO will send your files / reports to one of the outbound mail slots. For example, if you are setup to receive EFT reports or files, your mail slot will look as follows: AAA12345-DEFT-WINTESTE20RPT-A where AAA12345 is your mailbox ID, DEFT is application name, WINTESTE20RPT is document type, A is encoding. The above mail slot will be receiving reports from EFT system in ASCII format. Please work with your IS to get details of all of your outbound trading relationships (mail slots). AS2 service will push files to your AS2 server, once received by your outbound mail slot. IMPORTANT: AS2 requires separate AS2 ID for each mail slot. Please provide AS2 ID for each outbound mail slot (see Appendix A). This will allow you to receive files from BMO. PAGE 4 FOR ASSISTANCE, PLEASE CALL THE HELP DESK AT
7 Appendix A AS2 Services Client Questionnaire SECTION I: B ASIC INFORMATION ABOUT YOUR COMPANY Client Name: Business Contact: Phone: Technical Contact: Phone: Address: What is your desired production date? Are you currently a Global exchange Services (GXS) client? YES, go to Section II NO, continue with Section III SECTION II: GXS INFORMATION Do you have a mailbox on GXS Interchange Service platform? YES, proceed to the next question NO, continue with Section III Would you like to use the same mailbox to exchange files/reports with BMO? YES, proceed to the next question NO, continue with Section III Please provide your mailbox ID here and go to section 3 Mailbox ID PAGE 5 FOR ASSISTANCE, PLEASE CALL THE HELP DESK AT
8 SECTION III: AS2 I NFORMATION Complete this section if your company will be connecting to BMO using AS2 communications to access your mailbox. We need the following information about your AS2 setup. AS2 ID used in AS2 Header: for mail slot: IMPORTANT: You will need to provide AS2 ID for each mail slot assigned to you. See AS2 mailbox setup section. Digital Certificate: Type: Digital Signature Trust Verisign Self-Signed Expiration Date: Encryption Algorithm: none DES triple DES RC2: RC4: Hashing Algorithm: SHA1 MD5 Signature Algorithm: SHA1 MD5 Please list all applications you are planning to use: EDI: EFT: ARS: BAI: PAGE 6 FOR ASSISTANCE, PLEASE CALL THE HELP DESK AT
9 PAYABLES FCCS/FBPS: : Indicate file encoding (See Appendix B for encoding description) Inbound files to BMO A (ASCII) E (EBCDICI) Outbound files from BMO W (WINDOWS) A (ASCII) E (EBCDICI) MDN Receipt Type: Signed (recommended) Unsigned AS2 Software: Version: AS2 Server URL for Test: URL for Production: Additional Notes: PAGE 7 FOR ASSISTANCE, PLEASE CALL THE HELP DESK AT
10 Appendix B - Definitions FILE ENCODING BMO supports several file encoding types. These are: W: Windows (ASCII machine) This encoding can be used in Outbound transmission from BMO ONLY. The default delimiter on the Windows platform is CR (Carriage Return) and Line Feed (LF). This means that the record terminators within the application files on the windows platform are CRLF. A: Unix (ASCII machine). The default delimiter on Unix platform is Line Feed (LF). This means that the record terminators within the application files on the Unix platform are LF. E: Mainframe (EBCDIC machine). There is no specific character as the record delimiter on mainframes (Unisys or IBM). The encoding of the data is EBCDIC. While sending and receiving files from the mainframes, no data conversion needs to be performed. OTHER DEFINITIONS Mailbox This is your user ID on the Secure FTP service. Mail slots (or trading relationships) Mail slots belong to a mailbox and are used to receive various Cash Management files and reports. BMO sends your files and reports to an appropriate mail slot. By using mail slots, you can easily identify the application to which your files and reports belong. PAGE 8 FOR ASSISTANCE, PLEASE CALL THE HELP DESK AT
DirectLine for Business VPN USER GUIDE
 DirectLine for Business VPN USER GUIDE Contents VPN Security Service...1 Overview... 1 Before You Set Up VPN Secure Remote... 1 Downloading and Installing VPN Software... 1 After Completing the Installation...
DirectLine for Business VPN USER GUIDE Contents VPN Security Service...1 Overview... 1 Before You Set Up VPN Secure Remote... 1 Downloading and Installing VPN Software... 1 After Completing the Installation...
Overview. SSL Cryptography Overview CHAPTER 1
 CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet. SSL ensures the secure transmission of data between a client and a server through
CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet. SSL ensures the secure transmission of data between a client and a server through
Technologies for Securing the Networked Supply Chain. Alex Deacon Advanced Products and Research Group VeriSign, Inc.
 Technologies for Securing the Networked Supply Chain Alex Deacon Advanced Products and Research Group VeriSign, Inc. Agenda Introduction Security challenges Security technologies in use today Applying
Technologies for Securing the Networked Supply Chain Alex Deacon Advanced Products and Research Group VeriSign, Inc. Agenda Introduction Security challenges Security technologies in use today Applying
To start the project, launch your Visual Studio, and then Open Project FrediAppEdifact_Solution.sln
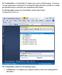 The FrediAppEdifact is a Visual Studio C# solution of an end-to-end EDI program. Its purpose is to give programmers a framework of a working EDI solution that they can build on or simply get inspiration
The FrediAppEdifact is a Visual Studio C# solution of an end-to-end EDI program. Its purpose is to give programmers a framework of a working EDI solution that they can build on or simply get inspiration
Request for Comments: 5402 Category: Informational February 2010 ISSN:
 Independent Submission T. Harding, Ed. Request for Comments: 5402 Axway Category: Informational February 2010 ISSN: 2070-1721 Abstract Compressed Data within an Internet Electronic Data Interchange (EDI)
Independent Submission T. Harding, Ed. Request for Comments: 5402 Axway Category: Informational February 2010 ISSN: 2070-1721 Abstract Compressed Data within an Internet Electronic Data Interchange (EDI)
BusinessMail X AS2-Gateway
 BusinessMail X.400 - AS2-Gateway For years X.400 has been the preferred protocol for reliably transmitting EDI data. The deciding factors for this include standardized reports and tracing every mail. Using
BusinessMail X.400 - AS2-Gateway For years X.400 has been the preferred protocol for reliably transmitting EDI data. The deciding factors for this include standardized reports and tracing every mail. Using
AS2. By John Radko, Chief Architect for GXS. A GXS White Paper for the Active Business
 AS2 By John Radko, Chief Architect for GXS for the Active Business Table of Contents Executive Summary...3 Why AS2? The Business Case...4 How AS2 Works...5 AS2 Meeting the Challenges of B2B Commerce...7
AS2 By John Radko, Chief Architect for GXS for the Active Business Table of Contents Executive Summary...3 Why AS2? The Business Case...4 How AS2 Works...5 AS2 Meeting the Challenges of B2B Commerce...7
Summary of PGP Services
 Table 15.1 Summary of PGP Services Function Algorithms Used Description Digital signature Message encryption Compression Email compatibility DSS/SHA or RSA/SHA CAST or IDEA or Three-key Triple DES with
Table 15.1 Summary of PGP Services Function Algorithms Used Description Digital signature Message encryption Compression Email compatibility DSS/SHA or RSA/SHA CAST or IDEA or Three-key Triple DES with
Copyright and Legal Disclaimers
 1 Copyright and Legal Disclaimers User Manual for DiConnect Enterprise R11. Document Release Date: June 25, 2014. Copyright 2014 by DiCentral Corporation. All rights reserved. This document and all content
1 Copyright and Legal Disclaimers User Manual for DiConnect Enterprise R11. Document Release Date: June 25, 2014. Copyright 2014 by DiCentral Corporation. All rights reserved. This document and all content
Overview and Benefits of SEEBURGER AS2 Spokes. Trading Partner Integration Using SEEBURGER'S BIS:AS2 Spoke
 Overview and Benefits of SEEBURGER AS2 Spokes Trading Partner Integration Using SEEBURGER'S BIS:AS2 Spoke Technical Documentation Contents 1 CLASSIC EDI AND ITS COST PROBLEM 2 1.1 VAN (VALUE ADDED NETWORK)...
Overview and Benefits of SEEBURGER AS2 Spokes Trading Partner Integration Using SEEBURGER'S BIS:AS2 Spoke Technical Documentation Contents 1 CLASSIC EDI AND ITS COST PROBLEM 2 1.1 VAN (VALUE ADDED NETWORK)...
Princess Nora Bint Abdulrahman University College of computer and information sciences Networks department Networks Security (NET 536)
 Princess Nora Bint Abdulrahman University College of computer and information sciences Networks department Networks Security (NET 536) Prepared by Dr. Samia Chelloug E-mail: samia_chelloug@yahoo.fr Content
Princess Nora Bint Abdulrahman University College of computer and information sciences Networks department Networks Security (NET 536) Prepared by Dr. Samia Chelloug E-mail: samia_chelloug@yahoo.fr Content
B2B Integration Using Seeburger AS2 Adapter with PI 7.1 Ehp1
 B2B Integration Using Seeburger AS2 Adapter with PI 7.1 Ehp1 Applies to: SAP NetWeaver Process Integration 7.1x, Seeburger 2.1x Summary This article is about preliminary design & configuration aspects
B2B Integration Using Seeburger AS2 Adapter with PI 7.1 Ehp1 Applies to: SAP NetWeaver Process Integration 7.1x, Seeburger 2.1x Summary This article is about preliminary design & configuration aspects
Revised (10/17) Overview Transmission Toolkit
 Revised (10/17) Overview Transmission Toolkit Copyright 2017 by KeyBank, N.A. Overview Transmission Toolkit All rights reserved. Reproduction of any part of this work beyond that permitted by Section 107
Revised (10/17) Overview Transmission Toolkit Copyright 2017 by KeyBank, N.A. Overview Transmission Toolkit All rights reserved. Reproduction of any part of this work beyond that permitted by Section 107
Final Report AS4 Interoperability Test 2018
 Final Report AS4 Interoperability Test 2018 Nov 18, 2018 Prepared & Administered By: DRUMMOND GROUP http://www.drummondgroup.com/ Copyright Drummond Group 2018 AS4-2018 Final Report page 1 Table of Contents
Final Report AS4 Interoperability Test 2018 Nov 18, 2018 Prepared & Administered By: DRUMMOND GROUP http://www.drummondgroup.com/ Copyright Drummond Group 2018 AS4-2018 Final Report page 1 Table of Contents
Contents. 7.0 Electronic Business Transactions Detroit Edison Website Communications Website Content 2
 Contents 7.0 Electronic Business Transactions 2 7.1 Detroit Edison Website Communications 2 7.1.1 Website Content 2 7.2 EBT Communications 3 7.2.1 Establishing XML with Detroit Edison 3 7.2.2 XML Transactions
Contents 7.0 Electronic Business Transactions 2 7.1 Detroit Edison Website Communications 2 7.1.1 Website Content 2 7.2 EBT Communications 3 7.2.1 Establishing XML with Detroit Edison 3 7.2.2 XML Transactions
AUTACK. Secure authentication and acknowledgement message. Edition 2012
 Secure authentication and acknowledgement message Edition 2012 1. Introduction... 2 2. Message Structure Chart... 3 3. Branching Diagram... 4 4. Segments Description... 5 5. Segments Layout... 6 6. Example(s)...
Secure authentication and acknowledgement message Edition 2012 1. Introduction... 2 2. Message Structure Chart... 3 3. Branching Diagram... 4 4. Segments Description... 5 5. Segments Layout... 6 6. Example(s)...
Medical Associates Health Plans and Health Choices
 Medical Associates Health Plans and Health Choices 270/271 HIPAA Transaction Companion Guide HIPAA V5010X279A1 VERSION: 2.0 DATE: 06/21/2016 1 Disclosure Statement This material contains confidential,
Medical Associates Health Plans and Health Choices 270/271 HIPAA Transaction Companion Guide HIPAA V5010X279A1 VERSION: 2.0 DATE: 06/21/2016 1 Disclosure Statement This material contains confidential,
novem car interior design gmbh Electronic Data Interchange (EDI) COMMUNICATION SHEET
 novem car interior design gmbh Electronic Data Interchange (EDI) COMMUNICATION SHEET Table of Content 1. Introduction 3 2. General Information Novem Car Interior Design 4 2.1 Address Headquarter 4 2.2
novem car interior design gmbh Electronic Data Interchange (EDI) COMMUNICATION SHEET Table of Content 1. Introduction 3 2. General Information Novem Car Interior Design 4 2.1 Address Headquarter 4 2.2
Secure Data Exchange Protocols
 COMPARISON GUIDE Secure Data Exchange Protocols Comparing transport protocols to securely exchange business data within and beyond the enterprise Table of Contents Introduction and Synopsis 3 Elements
COMPARISON GUIDE Secure Data Exchange Protocols Comparing transport protocols to securely exchange business data within and beyond the enterprise Table of Contents Introduction and Synopsis 3 Elements
CONTENTS. vii. Chapter 1 TCP/IP Overview 1. Chapter 2 Symmetric-Key Cryptography 33. Acknowledgements
 CONTENTS Preface Acknowledgements xiii xvii Chapter 1 TCP/IP Overview 1 1.1 Some History 2 1.2 TCP/IP Protocol Architecture 4 1.2.1 Data-link Layer 4 1.2.2 Network Layer 5 1.2.2.1 Internet Protocol 5 IPv4
CONTENTS Preface Acknowledgements xiii xvii Chapter 1 TCP/IP Overview 1 1.1 Some History 2 1.2 TCP/IP Protocol Architecture 4 1.2.1 Data-link Layer 4 1.2.2 Network Layer 5 1.2.2.1 Internet Protocol 5 IPv4
Sharing Secrets using Encryption Facility - Handson
 Sharing Secrets using Encryption Facility - Handson Lab Steven R. Hart IBM March 12, 2014 Session Number 14963 Encryption Facility for z/os Encryption Facility for z/os is a host based software solution
Sharing Secrets using Encryption Facility - Handson Lab Steven R. Hart IBM March 12, 2014 Session Number 14963 Encryption Facility for z/os Encryption Facility for z/os is a host based software solution
Pretty Good Privacy (PGP
 PGP - S/MIME - Internet Firewalls for Trusted System: Roles of Firewalls Firewall related terminology- Types of Firewalls - Firewall designs - SET for E-Commerce Transactions. Pretty Good Privacy (PGP
PGP - S/MIME - Internet Firewalls for Trusted System: Roles of Firewalls Firewall related terminology- Types of Firewalls - Firewall designs - SET for E-Commerce Transactions. Pretty Good Privacy (PGP
GS1 Finland Synkka Data Pool - AS2 Connection
 Synkka Data Pool - AS2 Connection Connectivity Guide Version 0.4, Draft/Approved, 2017.06.16. Document Summary Document Item Document Name Current Value GS1 Finland Synkka Data Pool - AS2 Connection (Connectivity
Synkka Data Pool - AS2 Connection Connectivity Guide Version 0.4, Draft/Approved, 2017.06.16. Document Summary Document Item Document Name Current Value GS1 Finland Synkka Data Pool - AS2 Connection (Connectivity
Chapter 5 Electronic mail security
 Chapter 5 Electronic mail security Dr. BHARGAVI H. GOSWAMI Department of Computer Science Christ University +91 9426669020 bhargavigoswami@gmail.com Topic List 1. Pretty good privacy 2. S/MIME Pretty Good
Chapter 5 Electronic mail security Dr. BHARGAVI H. GOSWAMI Department of Computer Science Christ University +91 9426669020 bhargavigoswami@gmail.com Topic List 1. Pretty good privacy 2. S/MIME Pretty Good
HTTPS--HTTP Server and Client with SSL 3.0
 The feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS software. SSL provides server authentication, encryption, and message integrity
The feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS software. SSL provides server authentication, encryption, and message integrity
Messaging Protocols in IBM Sterling B2B Integrator - Overview and Comparison
 Messaging Protocols in IBM Sterling B2B Integrator - Overview and Comparison Aparna D Dhenge (aparna.dhenge@in.ibm.com) Kamalakannan R (rkamalakannan@in.ibm.com) Manoj Kumar Goyal (manojgoyal16@in.ibm.com)
Messaging Protocols in IBM Sterling B2B Integrator - Overview and Comparison Aparna D Dhenge (aparna.dhenge@in.ibm.com) Kamalakannan R (rkamalakannan@in.ibm.com) Manoj Kumar Goyal (manojgoyal16@in.ibm.com)
< A symbol to indicate a value is less than another. For example, 2 < 3. This symbol is used in some BCBSNC proprietary error messages.
 Glossary < A symbol to indicate a value is less than another. For example, 2 < 3. This symbol is used in some BCBSNC proprietary error messages. > A symbol to indicate a value is greater than another.
Glossary < A symbol to indicate a value is less than another. For example, 2 < 3. This symbol is used in some BCBSNC proprietary error messages. > A symbol to indicate a value is greater than another.
Implementing Secure Socket Layer
 This module describes how to implement SSL. The Secure Socket Layer (SSL) protocol and Transport Layer Security (TLS) are application-level protocols that provide for secure communication between a client
This module describes how to implement SSL. The Secure Socket Layer (SSL) protocol and Transport Layer Security (TLS) are application-level protocols that provide for secure communication between a client
E-commerce security: SSL/TLS, SET and others. 4.1
 E-commerce security: SSL/TLS, SET and others. 4.1 1 Electronic payment systems Purpose: facilitate the safe and secure transfer of monetary value electronically between multiple parties Participating parties:
E-commerce security: SSL/TLS, SET and others. 4.1 1 Electronic payment systems Purpose: facilitate the safe and secure transfer of monetary value electronically between multiple parties Participating parties:
Actual4Test. Actual4test - actual test exam dumps-pass for IT exams
 Actual4Test http://www.actual4test.com Actual4test - actual test exam dumps-pass for IT exams Exam : 000-378 Title : IBM WebSphere DataPower SOA Appliances, Firmware V3.7.3 Vendors : IBM Version : DEMO
Actual4Test http://www.actual4test.com Actual4test - actual test exam dumps-pass for IT exams Exam : 000-378 Title : IBM WebSphere DataPower SOA Appliances, Firmware V3.7.3 Vendors : IBM Version : DEMO
It is recommended that separate transaction sets be used for different patients.
 ASC X12N 278 (004010X094A1) Health Care Services Request For Review And Response Companion Guide Notes The ISA segment terminator, which immediately follows the component element separator, must consist
ASC X12N 278 (004010X094A1) Health Care Services Request For Review And Response Companion Guide Notes The ISA segment terminator, which immediately follows the component element separator, must consist
Internet and Intranet Protocols and Applications
 Internet and Intranet Protocols and Applications Lecture 4: General Characteristics of Internet Protocols; the Email Protocol February 10, 2004 Arthur Goldberg Computer Science Department New York University
Internet and Intranet Protocols and Applications Lecture 4: General Characteristics of Internet Protocols; the Email Protocol February 10, 2004 Arthur Goldberg Computer Science Department New York University
IBM Systems and Technology Group
 IBM Systems and Technology Group Encryption Facility for z/os Update Steven R. Hart srhart@us.ibm.com 2013 IBM Corporation Topics Encryption Facility for z/os EF OpenPGP Support X.509 vs. OpenPGP Certificates
IBM Systems and Technology Group Encryption Facility for z/os Update Steven R. Hart srhart@us.ibm.com 2013 IBM Corporation Topics Encryption Facility for z/os EF OpenPGP Support X.509 vs. OpenPGP Certificates
Blue Cross Blue Shield of Louisiana
 Blue Cross Blue Shield of Louisiana Health Care Claim Payment/Advice (835) Standard Companion Guide Refers to the Implementation Guides Based on ASC X12N version: 005010X221A1 October 1, 2013 Version 1.0
Blue Cross Blue Shield of Louisiana Health Care Claim Payment/Advice (835) Standard Companion Guide Refers to the Implementation Guides Based on ASC X12N version: 005010X221A1 October 1, 2013 Version 1.0
Connectivity Implementation Guide
 Version 3.0, October 2017 Document History Version Date Update Origin Written by Verified by 1.00 3/25/2011 Initial Draft Mike DeAlto Sue Merk 1.08 11/03/11 Final for customer use Sue Merk Sue Merk 2.0
Version 3.0, October 2017 Document History Version Date Update Origin Written by Verified by 1.00 3/25/2011 Initial Draft Mike DeAlto Sue Merk 1.08 11/03/11 Final for customer use Sue Merk Sue Merk 2.0
Implementing Secure Shell
 Implementing Secure Shell Secure Shell (SSH) is an application and a protocol that provides a secure replacement to the Berkeley r-tools. The protocol secures sessions using standard cryptographic mechanisms,
Implementing Secure Shell Secure Shell (SSH) is an application and a protocol that provides a secure replacement to the Berkeley r-tools. The protocol secures sessions using standard cryptographic mechanisms,
Oracle B2B 11g Technical Note. Technical Note: 11g_006 Security. Table of Contents
 Oracle B2B 11g Technical Note Technical Note: 11g_006 Security This technical note lists the security options available in Oracle B2B Table of Contents Users... 2 Roles... 2 Step 1: Create the user in
Oracle B2B 11g Technical Note Technical Note: 11g_006 Security This technical note lists the security options available in Oracle B2B Table of Contents Users... 2 Roles... 2 Step 1: Create the user in
Implementation Guide for Delivery Notification in Direct
 Implementation Guide for Delivery Notification in Direct Contents Change Control... 2 Status of this Guide... 3 Introduction... 3 Overview... 3 Requirements... 3 1.0 Delivery Notification Messages... 4
Implementation Guide for Delivery Notification in Direct Contents Change Control... 2 Status of this Guide... 3 Introduction... 3 Overview... 3 Requirements... 3 1.0 Delivery Notification Messages... 4
HP Instant Support Enterprise Edition (ISEE) Security overview
 HP Instant Support Enterprise Edition (ISEE) Security overview Advanced Configuration A.03.50 Mike Brandon Interex 03 / 30, 2004 2003 Hewlett-Packard Development Company, L.P. The information contained
HP Instant Support Enterprise Edition (ISEE) Security overview Advanced Configuration A.03.50 Mike Brandon Interex 03 / 30, 2004 2003 Hewlett-Packard Development Company, L.P. The information contained
Category: Standards Track Drummond Group C. Shih Gartner Group September 2002
 Network Working Group Request for Comments: 3335 Category: Standards Track T. Harding Cyclone Commerce R. Drummond Drummond Group C. Shih Gartner Group September 2002 Status of this Memo MIME-based Secure
Network Working Group Request for Comments: 3335 Category: Standards Track T. Harding Cyclone Commerce R. Drummond Drummond Group C. Shih Gartner Group September 2002 Status of this Memo MIME-based Secure
C H A P T E R lpr Overview of the Print Server Program UNIX Print Facility lpr 8-1
 CHAPTER 8 USPOOL This chapter describes the print server program, USPOOL for the UNIX lpr command. It contains these sections: Overview of the Print Server Program Provides a brief overview of the print
CHAPTER 8 USPOOL This chapter describes the print server program, USPOOL for the UNIX lpr command. It contains these sections: Overview of the Print Server Program Provides a brief overview of the print
SMS Outbound. HTTP interface - v1.1
 SMS Outbound HTTP interface - v1.1 Table of contents 1. Version history... 5 2. Conventions... 5 3. Introduction... 6 4. Application Programming Interface (API)... 7 5. Gateway connection... 9 5.1 Main
SMS Outbound HTTP interface - v1.1 Table of contents 1. Version history... 5 2. Conventions... 5 3. Introduction... 6 4. Application Programming Interface (API)... 7 5. Gateway connection... 9 5.1 Main
HIPAA X 12 Transaction Standards
 HIPAA X 12 Transaction Standards Abbreviated Companion Guide 837 Institutional Health Care Claim Version 004010X096A1 Trading Partner Companion Guide Information and Considerations 837I 1. General Transaction
HIPAA X 12 Transaction Standards Abbreviated Companion Guide 837 Institutional Health Care Claim Version 004010X096A1 Trading Partner Companion Guide Information and Considerations 837I 1. General Transaction
Cryptography and Network Security. Sixth Edition by William Stallings
 Cryptography and Network Security Sixth Edition by William Stallings Chapter 19 Electronic Mail Security Despite the refusal of VADM Poindexter and LtCol North to appear, the Board's access to other sources
Cryptography and Network Security Sixth Edition by William Stallings Chapter 19 Electronic Mail Security Despite the refusal of VADM Poindexter and LtCol North to appear, the Board's access to other sources
Datapower is both a security appliance & can provide a firewall mechanism to get into Systems of Record
 1 2 3 Datapower is both a security appliance & can provide a firewall mechanism to get into Systems of Record 5 White boxes show the access points for different kinds of security. That s what we will
1 2 3 Datapower is both a security appliance & can provide a firewall mechanism to get into Systems of Record 5 White boxes show the access points for different kinds of security. That s what we will
SonicWALL Addendum. A Supplement to the SonicWALL Internet Security Appliance User's Guide
 SonicWALL 6.2.0.0 Addendum A Supplement to the SonicWALL Internet Security Appliance User's Guide Contents SonicWALL Addendum 6.2.0.0... 3 New Network Features... 3 NAT with L2TP Client... 3 New Tools
SonicWALL 6.2.0.0 Addendum A Supplement to the SonicWALL Internet Security Appliance User's Guide Contents SonicWALL Addendum 6.2.0.0... 3 New Network Features... 3 NAT with L2TP Client... 3 New Tools
CCNA Exploration1 Chapter 3: Application Layer Functionality and Protocols
 CCNA Exploration1 Chapter 3: Application Layer Functionality and Protocols LOCAL CISCO ACADEMY ELSYS TU INSTRUCTOR: STELA STEFANOVA 1 Objectives Functions of the three upper OSI model layers, network services
CCNA Exploration1 Chapter 3: Application Layer Functionality and Protocols LOCAL CISCO ACADEMY ELSYS TU INSTRUCTOR: STELA STEFANOVA 1 Objectives Functions of the three upper OSI model layers, network services
Transport Level Security
 2 Transport Level Security : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 28 October 2013 css322y13s2l12, Steve/Courses/2013/s2/css322/lectures/transport.tex,
2 Transport Level Security : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 28 October 2013 css322y13s2l12, Steve/Courses/2013/s2/css322/lectures/transport.tex,
ISACA CISA. ISACA CISA ( Certified Information Systems Auditor ) Download Full Version :
 ISACA CISA ISACA CISA ( Certified Information Systems Auditor ) Download Full Version : http://killexams.com/pass4sure/exam-detail/cisa QUESTION: 390 Applying a digital signature to data traveling in a
ISACA CISA ISACA CISA ( Certified Information Systems Auditor ) Download Full Version : http://killexams.com/pass4sure/exam-detail/cisa QUESTION: 390 Applying a digital signature to data traveling in a
BUSINESSMAIL X.400 WEB INTERFACE AS2 GATEWAY V2.9
 GATEWAY V2.9 User information (1) In the past it was necessary to use special forms or Excel sheets for the administration of your partners and trading relations. You had to send this information to central
GATEWAY V2.9 User information (1) In the past it was necessary to use special forms or Excel sheets for the administration of your partners and trading relations. You had to send this information to central
WV MMIS EDI File Exchange User Guide Version 1.0 West Virginia Trading Partner Account Electronic Data Interchange (EDI) File Exchange User Guide
 West Virginia Trading Partner Account Electronic Data Interchange (EDI) File Exchange User Guide Date of Publication: 01/19/2016 Document Version: 1.0 Privacy and Security Rules WV MMIS The Health Insurance
West Virginia Trading Partner Account Electronic Data Interchange (EDI) File Exchange User Guide Date of Publication: 01/19/2016 Document Version: 1.0 Privacy and Security Rules WV MMIS The Health Insurance
SMS Outbound. SMTP interface - v1.1
 SMS Outbound SMTP interface - v1.1 Table of contents 1. Version history... 5 2. Conventions... 5 3. Introduction... 6 4. Gateway connection... 7 4.1 E-mail message format... 7 4.2 Header section... 7 4.3
SMS Outbound SMTP interface - v1.1 Table of contents 1. Version history... 5 2. Conventions... 5 3. Introduction... 6 4. Gateway connection... 7 4.1 E-mail message format... 7 4.2 Header section... 7 4.3
Final Report ebms Interoperability Test Fourth Quarter 2018 (4Q18)
 Final Report ebms Interoperability Test Fourth Quarter 2018 (4Q18) Feb 4, 2019 Prepared & Administered By: DRUMMOND GROUP, LLC http://www.drummondgroup.com/ Copyright Drummond Group, LLC 2018 ebms 4Q18
Final Report ebms Interoperability Test Fourth Quarter 2018 (4Q18) Feb 4, 2019 Prepared & Administered By: DRUMMOND GROUP, LLC http://www.drummondgroup.com/ Copyright Drummond Group, LLC 2018 ebms 4Q18
HTTPS--HTTP Server and Client with SSL 3.0
 The feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS XE software. SSL provides server authentication, encryption, and message
The feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS XE software. SSL provides server authentication, encryption, and message
Lecture 9a: Secure Sockets Layer (SSL) March, 2004
 Internet and Intranet Protocols and Applications Lecture 9a: Secure Sockets Layer (SSL) March, 2004 Arthur Goldberg Computer Science Department New York University artg@cs.nyu.edu Security Achieved by
Internet and Intranet Protocols and Applications Lecture 9a: Secure Sockets Layer (SSL) March, 2004 Arthur Goldberg Computer Science Department New York University artg@cs.nyu.edu Security Achieved by
INTERNET & WORLD WIDE WEB (UNIT-1) MECHANISM OF INTERNET
 INTERNET & WORLD WIDE WEB (UNIT-1) MECHANISM OF INTERNET 1. INTRODUCTION Hello friends are topic is Internet and World Wide Web the most popular services of our topic is social networking and online shopping
INTERNET & WORLD WIDE WEB (UNIT-1) MECHANISM OF INTERNET 1. INTRODUCTION Hello friends are topic is Internet and World Wide Web the most popular services of our topic is social networking and online shopping
BusinessMail X.400 Web interface AS2 Gateway V3.0
 Web interface AS2 Gateway V3.0 User information (1) In the past it was necessary to use special forms or Excel sheets for the administration of your partners and trading relations. You had to send this
Web interface AS2 Gateway V3.0 User information (1) In the past it was necessary to use special forms or Excel sheets for the administration of your partners and trading relations. You had to send this
Integrating the Hardware Management Console s Broadband Remote Support Facility into your Enterprise
 System z Integrating the Hardware Management Console s Broadband Remote Support Facility into your Enterprise SC28-6880-00 System z Integrating the Hardware Management Console s Broadband Remote Support
System z Integrating the Hardware Management Console s Broadband Remote Support Facility into your Enterprise SC28-6880-00 System z Integrating the Hardware Management Console s Broadband Remote Support
Chapter 8 Web Security
 Chapter 8 Web Security Web security includes three parts: security of server, security of client, and network traffic security between a browser and a server. Security of server and security of client
Chapter 8 Web Security Web security includes three parts: security of server, security of client, and network traffic security between a browser and a server. Security of server and security of client
Configuring Secure Socket Layer HTTP
 This feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS software. SSL provides server authentication, encryption, and message integrity
This feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS software. SSL provides server authentication, encryption, and message integrity
AUTACK. Secure authentication and acknowledgement message. Edition 2016
 EANCOM 2002 S4 Secure authentication and acknowledgement message Edition 2016 1. Introduction... 2 2. Message Structure Chart... 3 3. Branching Diagram... 4 4. Segments Description... 5 5. Segments Layout...
EANCOM 2002 S4 Secure authentication and acknowledgement message Edition 2016 1. Introduction... 2 2. Message Structure Chart... 3 3. Branching Diagram... 4 4. Segments Description... 5 5. Segments Layout...
EDI Implementation Guide. Dayco Products, LLC. North America Aftermarket Division
 EDI Implementation Guide Dayco Products, LLC. North America Aftermarket Division Version: 1.0 Publication: 11/19/2013 Table of Contents Contents Change Control... 3 Overview... 4 Standard and Version...
EDI Implementation Guide Dayco Products, LLC. North America Aftermarket Division Version: 1.0 Publication: 11/19/2013 Table of Contents Contents Change Control... 3 Overview... 4 Standard and Version...
IBM Presentations: Implementing SSL Security in WebSphere Partner Gateway
 IBM Software Group IBM Presentations: Implementing SSL Security in WebSphere Partner Gateway Presenter: Max Terpolilli WPG L2 Support WebSphere Support Technical Exchange Agenda IBM Software Group Digital
IBM Software Group IBM Presentations: Implementing SSL Security in WebSphere Partner Gateway Presenter: Max Terpolilli WPG L2 Support WebSphere Support Technical Exchange Agenda IBM Software Group Digital
Design and Implementation of a RFC3161-Enhanced Time-Stamping Service
 Design and Implementation of a RFC3161-Enhanced Time-Stamping Service Chung-Huang Yang, 1 Chih-Ching Yeh, 2 and Fang-Dar Chu 3 1 Institute of Information and Computer Education, National Kaohsiung Normal
Design and Implementation of a RFC3161-Enhanced Time-Stamping Service Chung-Huang Yang, 1 Chih-Ching Yeh, 2 and Fang-Dar Chu 3 1 Institute of Information and Computer Education, National Kaohsiung Normal
Enhanced Routing and Naming Capabilities for truexchange IFS and DBF Files. Document Version 05.06
 Enhanced Routing and Naming Capabilities for truexchange IFS and DBF Files Document Version 05.06 2001-2006 nubridges, LLC. All rights reserved. nubridges is a trade name and registered trademark in the
Enhanced Routing and Naming Capabilities for truexchange IFS and DBF Files Document Version 05.06 2001-2006 nubridges, LLC. All rights reserved. nubridges is a trade name and registered trademark in the
Comprehensive Setup Guide for TLS on ESA
 Comprehensive Setup Guide for TLS on ESA Contents Introduction Prerequisites Requirements Components Used Background Information Functional Overview and Requirements Bring Your Own Certificate Update a
Comprehensive Setup Guide for TLS on ESA Contents Introduction Prerequisites Requirements Components Used Background Information Functional Overview and Requirements Bring Your Own Certificate Update a
Service Managed Gateway TM. Configuring IPSec VPN
 Service Managed Gateway TM Configuring IPSec VPN Issue 1.2 Date 12 November 2010 1: Introduction 1 Introduction... 3 1.1 What is a VPN?... 3 1.2 The benefits of an Internet-based VPN... 3 1.3 Tunnelling
Service Managed Gateway TM Configuring IPSec VPN Issue 1.2 Date 12 November 2010 1: Introduction 1 Introduction... 3 1.1 What is a VPN?... 3 1.2 The benefits of an Internet-based VPN... 3 1.3 Tunnelling
We currently are able to offer three different action types:
 SMS Inbound Introduction SMS Inbound provides a simple to use interface for receiving inbound MMS messages. Inbound Message Actions Inbound Message Actions in SMS Inbound are things that our system can
SMS Inbound Introduction SMS Inbound provides a simple to use interface for receiving inbound MMS messages. Inbound Message Actions Inbound Message Actions in SMS Inbound are things that our system can
IP Security. Have a range of application specific security mechanisms
 IP Security IP Security Have a range of application specific security mechanisms eg. S/MIME, PGP, Kerberos, SSL/HTTPS However there are security concerns that cut across protocol layers Would like security
IP Security IP Security Have a range of application specific security mechanisms eg. S/MIME, PGP, Kerberos, SSL/HTTPS However there are security concerns that cut across protocol layers Would like security
Electronic Data Interchange General Specifications
 Electronic Interchange General Specifications This guide contains the specifications to allow you to exchange financial data with CIT using the standard EDI formats. The accompanying document, General
Electronic Interchange General Specifications This guide contains the specifications to allow you to exchange financial data with CIT using the standard EDI formats. The accompanying document, General
Cryptography and Network Security
 Cryptography and Network Security Third Edition by William Stallings Lecture slides by Lawrie Brown Chapter 15 Electronic Mail Security Despite the refusal of VADM Poindexter and LtCol North to appear,
Cryptography and Network Security Third Edition by William Stallings Lecture slides by Lawrie Brown Chapter 15 Electronic Mail Security Despite the refusal of VADM Poindexter and LtCol North to appear,
HIPAA X 12 Transaction Standards
 HIPAA X 12 Transaction Standards Abbreviated Companion Guide 837 Professional Health Care Claim Version 004010X098A1 Trading Partner Companion Guide Information and Considerations 837P 1. General Transaction
HIPAA X 12 Transaction Standards Abbreviated Companion Guide 837 Professional Health Care Claim Version 004010X098A1 Trading Partner Companion Guide Information and Considerations 837P 1. General Transaction
PIDX PIP Specification. P11: Send Field Ticket. Version 1.0
 PIDX PIP Specification P11: Send Field Ticket Version 1.0 July 8, 2014 Table of Contents 1 Introduction... 4 1.1 Document Purpose... 4 1.2 Document Conventions... 4 1.3 Intended Audience... 4 1.4 References...
PIDX PIP Specification P11: Send Field Ticket Version 1.0 July 8, 2014 Table of Contents 1 Introduction... 4 1.1 Document Purpose... 4 1.2 Document Conventions... 4 1.3 Intended Audience... 4 1.4 References...
Network Working Group Internet Draft: SMTP Authentication Document: draft-myers-smtp-auth-00.txt April SMTP Service Extension for Authentication
 HTTP/1.1 200 OK Date: Tue, 09 Apr 2002 10:24:33 GMT Server: Apache/1.3.20 (Unix) Last-Modified: Mon, 01 May 1995 22:00:00 GMT ETag: "361c6c-32a5-2fa559e0" Accept-Ranges: bytes Content-Length: 12965 Connection:
HTTP/1.1 200 OK Date: Tue, 09 Apr 2002 10:24:33 GMT Server: Apache/1.3.20 (Unix) Last-Modified: Mon, 01 May 1995 22:00:00 GMT ETag: "361c6c-32a5-2fa559e0" Accept-Ranges: bytes Content-Length: 12965 Connection:
Expires in 6 months September Internet Public Key Infrastructure Online Certificate Status Protocol - OCSP <draft-ietf-pkix-ocsp-00.
 HTTP/1.1 200 OK Date: Tue, 09 Apr 2002 06:26:11 GMT Server: Apache/1.3.20 (Unix) Last-Modified: Thu, 23 Oct 1997 15:29:00 GMT ETag: "304c31-471a-344f6d3c" Accept-Ranges: bytes Content-Length: 18202 Connection:
HTTP/1.1 200 OK Date: Tue, 09 Apr 2002 06:26:11 GMT Server: Apache/1.3.20 (Unix) Last-Modified: Thu, 23 Oct 1997 15:29:00 GMT ETag: "304c31-471a-344f6d3c" Accept-Ranges: bytes Content-Length: 18202 Connection:
Which Communications Protocol Is Best for B2B Integration? Comparing AS2, FTP and other popular B2B e-commerce standards
 Which Communications Protocol Is Best for B2B Integration? Comparing AS2, FTP and other popular B2B e-commerce standards John Radko, Vice President, Enterprise Architecture, GXS Rochelle Cohen, Sr. Marketing
Which Communications Protocol Is Best for B2B Integration? Comparing AS2, FTP and other popular B2B e-commerce standards John Radko, Vice President, Enterprise Architecture, GXS Rochelle Cohen, Sr. Marketing
WHITE PAPER. Authentication and Encryption Design
 WHITE PAPER Authentication and Encryption Design Table of Contents Introduction Applications and Services Account Creation Two-step Verification Authentication Passphrase Management Email Message Encryption
WHITE PAPER Authentication and Encryption Design Table of Contents Introduction Applications and Services Account Creation Two-step Verification Authentication Passphrase Management Email Message Encryption
Lecture 33. Firewalls. Firewall Locations in the Network. Castle and Moat Analogy. Firewall Types. Firewall: Illustration. Security April 15, 2005
 Firewalls Lecture 33 Security April 15, 2005 Idea: separate local network from the Internet Trusted hosts and networks Intranet Firewall DMZ Router Demilitarized Zone: publicly accessible servers and networks
Firewalls Lecture 33 Security April 15, 2005 Idea: separate local network from the Internet Trusted hosts and networks Intranet Firewall DMZ Router Demilitarized Zone: publicly accessible servers and networks
HTTPS File Transfer. Specification
 HTTPS File Transfer Specification Version 1.4 5-Apr-2017 Date Version Description 30-Aug-2010 1.0 Original Version 30-Jun-2011 1.1 Added FAQ 29-Jun-2015 1.2 ilink administration added 1-Sep-2015 1.3 Updated
HTTPS File Transfer Specification Version 1.4 5-Apr-2017 Date Version Description 30-Aug-2010 1.0 Original Version 30-Jun-2011 1.1 Added FAQ 29-Jun-2015 1.2 ilink administration added 1-Sep-2015 1.3 Updated
Configuring SSL Security
 CHAPTER9 This chapter describes how to configure SSL on the Cisco 4700 Series Application Control Engine (ACE) appliance. This chapter contains the following sections: Overview Configuring SSL Termination
CHAPTER9 This chapter describes how to configure SSL on the Cisco 4700 Series Application Control Engine (ACE) appliance. This chapter contains the following sections: Overview Configuring SSL Termination
Business Data Networks and Security 10th Edition by Panko Test Bank
 Business Data Networks and Security 10th Edition by Panko Test Bank Chapter 2 Network Standards 1) Internet standards are published as. A) RFCs B) IETFs C) TCP/IPs D) Internet Protocols Question: 1a Objective:
Business Data Networks and Security 10th Edition by Panko Test Bank Chapter 2 Network Standards 1) Internet standards are published as. A) RFCs B) IETFs C) TCP/IPs D) Internet Protocols Question: 1a Objective:
TIBCO ActiveMatrix Policy Director Administration
 TIBCO ActiveMatrix Policy Director Administration Software Release 2.0.0 November 2014 Document Updated: January 2015 Two-Second Advantage 2 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES
TIBCO ActiveMatrix Policy Director Administration Software Release 2.0.0 November 2014 Document Updated: January 2015 Two-Second Advantage 2 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES
Concept Questions Demonstrate your knowledge of these concepts by answering the following questions in the space provided.
 113 Chapter 9 TCP/IP Transport and Application Layer Services that are located in the transport layer enable users to segment several upper-layer applications onto the same transport layer data stream.
113 Chapter 9 TCP/IP Transport and Application Layer Services that are located in the transport layer enable users to segment several upper-layer applications onto the same transport layer data stream.
CipherMail encryption. CipherMail white paper
 CipherMail email encryption CipherMail white paper Copyright 2009-2017, ciphermail.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in
CipherMail email encryption CipherMail white paper Copyright 2009-2017, ciphermail.com. Introduction Most email is sent as plain text. This means that anyone who can intercept email messages, either in
Nimsoft Service Desk. Single Sign-On Configuration Guide. [assign the version number for your book]
![Nimsoft Service Desk. Single Sign-On Configuration Guide. [assign the version number for your book] Nimsoft Service Desk. Single Sign-On Configuration Guide. [assign the version number for your book]](/thumbs/80/81218109.jpg) Nimsoft Service Desk Single Sign-On Configuration Guide [assign the version number for your book] Legal Notices Copyright 2012, CA. All rights reserved. Warranty The material contained in this document
Nimsoft Service Desk Single Sign-On Configuration Guide [assign the version number for your book] Legal Notices Copyright 2012, CA. All rights reserved. Warranty The material contained in this document
Oracle Payment Interface Token Proxy Service Security Guide Release 6.1 E November 2017
 Oracle Payment Interface Token Proxy Service Security Guide Release 6.1 E87635-01 November 2017 Copyright 2017, Oracle and/or its affiliates. All rights reserved. This software and related documentation
Oracle Payment Interface Token Proxy Service Security Guide Release 6.1 E87635-01 November 2017 Copyright 2017, Oracle and/or its affiliates. All rights reserved. This software and related documentation
Cisco Encryption
 This chapter contains the following sections: Overview of, page 1 How to Encrypt Messages with a Local Key Server, page 2 Encrypting Messages using the Email Security Appliance, page 3 Determining Which
This chapter contains the following sections: Overview of, page 1 How to Encrypt Messages with a Local Key Server, page 2 Encrypting Messages using the Email Security Appliance, page 3 Determining Which
Reference Manual for the Student and Exchange Visitor Information System Batch Interface
 U.S. Immigration & Naturalization Service Reference Manual for the Student and Exchange Visitor Information System Batch Interface September 20, 2002 DRAFT TABLE OF CONTENTS 1. INTRODUCTION... 1 1.1 Purpose...1
U.S. Immigration & Naturalization Service Reference Manual for the Student and Exchange Visitor Information System Batch Interface September 20, 2002 DRAFT TABLE OF CONTENTS 1. INTRODUCTION... 1 1.1 Purpose...1
Configuring Certificate Authorities and Digital Certificates
 CHAPTER 43 Configuring Certificate Authorities and Digital Certificates Public Key Infrastructure (PKI) support provides the means for the Cisco MDS 9000 Family switches to obtain and use digital certificates
CHAPTER 43 Configuring Certificate Authorities and Digital Certificates Public Key Infrastructure (PKI) support provides the means for the Cisco MDS 9000 Family switches to obtain and use digital certificates
Electronic mail security
 Electronic mail security Ola Flygt Växjö University, Sweden http://w3.msi.vxu.se/users/ofl/ Ola.Flygt@vxu.se +46 470 70 86 49 1 Outline Pretty Good Privacy (PGP) S/MIME 2 1 Pretty Good Privacy Philip R.
Electronic mail security Ola Flygt Växjö University, Sweden http://w3.msi.vxu.se/users/ofl/ Ola.Flygt@vxu.se +46 470 70 86 49 1 Outline Pretty Good Privacy (PGP) S/MIME 2 1 Pretty Good Privacy Philip R.
Send documentation comments to
 CHAPTER 6 Configuring Certificate Authorities and Digital Certificates This chapter includes the following topics: Information About Certificate Authorities and Digital Certificates, page 6-1 Default Settings,
CHAPTER 6 Configuring Certificate Authorities and Digital Certificates This chapter includes the following topics: Information About Certificate Authorities and Digital Certificates, page 6-1 Default Settings,
SAP Pharma Network Onboarding Guide
 Onboarding Guide - Final Review SAP Pharma Network Document Version: 0.18 2016-08-10 Typographic Conventions Type Style Example Description Words or characters quoted from the screen. These include field
Onboarding Guide - Final Review SAP Pharma Network Document Version: 0.18 2016-08-10 Typographic Conventions Type Style Example Description Words or characters quoted from the screen. These include field
PIDX PIP Specification. P22: Send Invoice Response. Version 1.0
 PIDX PIP Specification P22: Send Invoice Response Version 1.0 July 9, 2014 Table of Contents Document Version History... 4 1 Introduction... 5 1.1 Document Purpose... 5 1.2 Document Conventions... 5 1.3
PIDX PIP Specification P22: Send Invoice Response Version 1.0 July 9, 2014 Table of Contents Document Version History... 4 1 Introduction... 5 1.1 Document Purpose... 5 1.2 Document Conventions... 5 1.3
Cryptography in Lotus Notes/Domino Pragmatic Introduction for Administrators
 Cryptography in Lotus Notes/Domino Pragmatic Introduction for Administrators Belfast, 11-Nov-2010 Innovative Software Solutions. Thomas Bahn - graduated in mathematics, University of Hannover - developing
Cryptography in Lotus Notes/Domino Pragmatic Introduction for Administrators Belfast, 11-Nov-2010 Innovative Software Solutions. Thomas Bahn - graduated in mathematics, University of Hannover - developing
FIPS Management. FIPS Management Overview. Configuration Changes in FIPS Mode
 This chapter contains the following sections: Overview, on page 1 Configuration Changes in FIPS Mode, on page 1 Switching the Appliance to FIPS Mode, on page 2 Encrypting Sensitive Data in FIPS Mode, on
This chapter contains the following sections: Overview, on page 1 Configuration Changes in FIPS Mode, on page 1 Switching the Appliance to FIPS Mode, on page 2 Encrypting Sensitive Data in FIPS Mode, on
SECURE Gateway v4.7. TLS configuration guide
 SECURE Email Gateway v4.7 TLS configuration guide November 2017 Copyright Published by Clearswift Ltd. 1995 2017 Clearswift Ltd. All rights reserved. The materials contained herein are the sole property
SECURE Email Gateway v4.7 TLS configuration guide November 2017 Copyright Published by Clearswift Ltd. 1995 2017 Clearswift Ltd. All rights reserved. The materials contained herein are the sole property
Configuring Secure Socket Layer HTTP
 This feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS software. SSL provides server authentication, encryption, and message integrity
This feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS software. SSL provides server authentication, encryption, and message integrity
Presented by: Ahmed Atef Elnaggar Supervisor: Prof. Shawkat K.Guirguis
 2 nd Assignment of Comm. Sys. & Computer N.W Department of Information Technology, Institute of Graduate Studies and Research, University of Alexandria, Egypt. Presented by: Ahmed Atef Elnaggar Supervisor:
2 nd Assignment of Comm. Sys. & Computer N.W Department of Information Technology, Institute of Graduate Studies and Research, University of Alexandria, Egypt. Presented by: Ahmed Atef Elnaggar Supervisor:
Cryptography and Network Security
 Cryptography and Network Security Spring 2012 http://users.abo.fi/ipetre/crypto/ Lecture 14: Folklore, Course summary, Exam requirements Ion Petre Department of IT, Åbo Akademi University 1 Folklore on
Cryptography and Network Security Spring 2012 http://users.abo.fi/ipetre/crypto/ Lecture 14: Folklore, Course summary, Exam requirements Ion Petre Department of IT, Åbo Akademi University 1 Folklore on
Feature Express Enterprise Arcus. SSL/TLS - secure FTP communications Included Included Included
 Protocols SSL/TLS - secure FTP communications SSL key manager - manage, import, export, and create SSL certificates SSL Config - specify ciphers and versions allowed (SSL v2, v3, and TLS v1) Checkpoint
Protocols SSL/TLS - secure FTP communications SSL key manager - manage, import, export, and create SSL certificates SSL Config - specify ciphers and versions allowed (SSL v2, v3, and TLS v1) Checkpoint
