Filtering Service
|
|
|
- Kristin Hall
- 6 years ago
- Views:
Transcription
1 Secure Gateway (SEG) Service Administrative Guides Filtering Service Regular Expressions Overview
2 Regular Expressions Overview AT&T Secure Gateway customers can use Regular Expressions to define custom content groups for filtering outbound mail within the SEG service. The feature is meant to be used by customers to help with Data Loss Prevention. With DLP customers can setup rules to help prevent messages with specific terms from being sent out of their environment. NOTE AT&T SEG Technical Support will not provide support to create or debug regular expressions. Regular expressions are an advanced feature that should be undertaken only by those customer administrators that are completely familiar with the creation, use and debugging of such expressions. Parameters The SEG service uses PCRE (Perl-compatible Regular Expressions). Customers are limited to 255 characters per expression (including comments). An error will be displayed if a regex goes beyond the 255 character limit. A regex that takes too long to be processed may be skipped and the service will move on to the next step for processing the message. Message Audit does not show regex information. Definitions Literal A literal is any character used in a search or matching expression Metacharacter One or more special characters that have a unique meaning and are NOT used as literals (for example the ^ ) Search Expression The expression that we are using to search the target string ( ) Escape Sequence A way of indicating that a metacharacter is to be used as a literal. Used for special characters like <CR><LF> or to find directory structures specified in text Syntax
3 [ ] Matches anything inside the square brackets for ONE character position once and only once. For example [12] will look for either a 1 or 2 in that character position [ ] will look for any digit in the range of 0 through 9 - The dash ( - ) when used inside the square brackets acts as a range separator and allows definition of a range for that character position For example [0-9] will look for any digit in the range of 0 through 9 [0-9A-E] will look for either a digit in the range of 0 through 9 OR a capital A through capital E Positional (Anchor) Metacharacters ^ The caret ( ^ ) indicates an exception to what is shown inside the square brackets. For example [^Ff] means anything except upper or lower case F [^a-z] means anything except lower case a through z When used outside the square brackets, the expression will look only at the beginning of the target string (Subject line of the ). For example - ^Inv will find Invoice and Inventory and Invention as the first word of the subject of an but will NOT find invoice, inventory and invention $ The $ will look only at the END of the . For example send$ will find any that ends with the word send without punctuation afterward
4 . The period (. ) means any character(s) in this position. For example, ept. will find exception and excepted but will not find except or inept because there are no characters that follow the ept Iteration Metacharacters? The? matches the preceding character 0 or 1 time only. For example colou?r will match either color or colour * The * matches the preceding character 0 or more times For example tre* will match tree (2 times), tread (1 time) and trough (0 times) + The + matches the previous character 1 or more times For example tre+ will match tree (2 times) and tread (1 time) but not trough (0 times) {n} Matches the preceding character or character range exactly n times. This is useful for phone numbers and account numbers. For example to find a phone number you could use the following: [0-9]{3}-[0-9]{3}-[0-9]{4} To find an 7 digit account number that starts with either AX or XX followed by a hyphen and 5 digits you could use the following: [AX]X-[0-9]{5} {n,m} Matches the preceding character at least n times but not more than m times
5 For example ba{2,3}b will find baab and baaab but not bab Additional Operations The pipe symbol ( ) is a Boolean OR that can be used in expressions to signify a match on 2 or more characters For example [W L]in will find Windows OR Linux. ( ) Open/Closed parenthesis can be used to group parts of the search expression together For example gr(a e)y will find both gray or grey \ Escape character required to treat special characters as their literal equivalents. For example [A-Z]{5}\)$ will find a string of 5 capital letters followed by a ) at the end of a line in an Advanced Expressions If-Then-Else There probably is really no good reason for a customer to try to set up an If-Then- Else scenario but if anyone thinks of it, we can try to provide example syntax as needed Comments It is ALWAYS a good idea to use comments so that you know what you intended to do (versus what is actually happening) with your regex. The syntax for a comment is (?#comment) where comment is whatever you want as long as it doesn t contain a closing parenthesis. Regex engines should ignore everything after the (?# and before the ending )
6 Compare these two examples the first without comments, the second with comments: Ex1 - (19 20)[0-9]{2}[- /.](0[1-9] 1[012])[- /.](0[1-9] [12][0-9] 3[01]) Ex2 - (?#YEAR)(19 20)[0-9]{2}[- /.](?#MONTH)(0[1-9] 1[012])[- /.](?#DAY)(0[1-9] [12][0-9] 3[01]) The comments in Ex2 are bolded above. CAUTION When using comments, if you put a space between the ending ) and the search string, you may not get the expected results For example, consider the difference between these two regex statements: Ex1 - (?#Comment - should be ignored)[a-z]{5}\#$ Ex2 - (?#Comment - should be ignored) [A-Z]{5}\#$ Note that the space at end of the comment in Ex2 will only match a string with a leading space. Performance Considerations Generally, from a performance perspective, customers should only be aware that using a Boolean OR ( ) is less efficient than specifying the characters side by side. Even though they effectively do the same thing, there is a cost in processing time. For example: [AaBbCcDd] is more efficient than [A a B b C c D d] How to Enable Regular Expressions in a Custom Content Group A Customer Administrator can enable Regular Expressions in an existing Content Group or by creating a new Content Group:
7 1. Login to the Control Console 2. Select the Protection tab 3. Select the Policies tab 4. Click Outbound Policies 5. Select the appropriate Outbound Policy and click Edit 6. Select the Content Tab 7. Select the Custom Content Groups tab 8. Select the appropriate Content Group 9. Add the expression in the Content box 10. Select the Enable regular expressions check box 11. Click Save How to Test a Regular Expression To test a Regular Expression being created follow these steps: 1. Login to the Control Console 2. Click the Protection tab
8 3. Click Policies 4. Click the Content tab 5. Click the Custom Content Groups tab 6. Enter the Regular Expression you are testing in the Regular Expression text box 7. Enter sample text to be searched in the Sample Text text box. The Regular Expression will be run against this sample text 8. Click Test Results will be displayed in the Results section. Note that the test will only return the first match of the expression. To test additional variations, edit the sample text accordingly.
Regular Expressions. Michael Wrzaczek Dept of Biosciences, Plant Biology Viikki Plant Science Centre (ViPS) University of Helsinki, Finland
 Regular Expressions Michael Wrzaczek Dept of Biosciences, Plant Biology Viikki Plant Science Centre (ViPS) University of Helsinki, Finland November 11 th, 2015 Regular expressions provide a flexible way
Regular Expressions Michael Wrzaczek Dept of Biosciences, Plant Biology Viikki Plant Science Centre (ViPS) University of Helsinki, Finland November 11 th, 2015 Regular expressions provide a flexible way
Introduction to Regular Expressions Version 1.3. Tom Sgouros
 Introduction to Regular Expressions Version 1.3 Tom Sgouros June 29, 2001 2 Contents 1 Beginning Regular Expresions 5 1.1 The Simple Version........................ 6 1.2 Difficult Characters........................
Introduction to Regular Expressions Version 1.3 Tom Sgouros June 29, 2001 2 Contents 1 Beginning Regular Expresions 5 1.1 The Simple Version........................ 6 1.2 Difficult Characters........................
Dr. Sarah Abraham University of Texas at Austin Computer Science Department. Regular Expressions. Elements of Graphics CS324e Spring 2017
 Dr. Sarah Abraham University of Texas at Austin Computer Science Department Regular Expressions Elements of Graphics CS324e Spring 2017 What are Regular Expressions? Describe a set of strings based on
Dr. Sarah Abraham University of Texas at Austin Computer Science Department Regular Expressions Elements of Graphics CS324e Spring 2017 What are Regular Expressions? Describe a set of strings based on
Regular Expressions. Perl PCRE POSIX.NET Python Java
 ModSecurity rules rely heavily on regular expressions to allow you to specify when a rule should or shouldn't match. This appendix teaches you the basics of regular expressions so that you can better make
ModSecurity rules rely heavily on regular expressions to allow you to specify when a rule should or shouldn't match. This appendix teaches you the basics of regular expressions so that you can better make
Regular Expressions 1
 Regular Expressions 1 Basic Regular Expression Examples Extended Regular Expressions Extended Regular Expression Examples 2 phone number 3 digits, dash, 4 digits [[:digit:]][[:digit:]][[:digit:]]-[[:digit:]][[:digit:]][[:digit:]][[:digit:]]
Regular Expressions 1 Basic Regular Expression Examples Extended Regular Expressions Extended Regular Expression Examples 2 phone number 3 digits, dash, 4 digits [[:digit:]][[:digit:]][[:digit:]]-[[:digit:]][[:digit:]][[:digit:]][[:digit:]]
CA Unified Infrastructure Management
 CA Unified Infrastructure Management Probe Guide for Log Monitoring logmon v3.4 series Copyright Notice This online help system (the "System") is for your informational purposes only and is subject to
CA Unified Infrastructure Management Probe Guide for Log Monitoring logmon v3.4 series Copyright Notice This online help system (the "System") is for your informational purposes only and is subject to
Regular Expressions. Todd Kelley CST8207 Todd Kelley 1
 Regular Expressions Todd Kelley kelleyt@algonquincollege.com CST8207 Todd Kelley 1 POSIX character classes Some Regular Expression gotchas Regular Expression Resources Assignment 3 on Regular Expressions
Regular Expressions Todd Kelley kelleyt@algonquincollege.com CST8207 Todd Kelley 1 POSIX character classes Some Regular Expression gotchas Regular Expression Resources Assignment 3 on Regular Expressions
Regular Expressions. Regular expressions match input within a line Regular expressions are very different than shell meta-characters.
 ULI101 Week 09 Week Overview Regular expressions basics Literal matching.wildcard Delimiters Character classes * repetition symbol Grouping Anchoring Search Search and replace in vi Regular Expressions
ULI101 Week 09 Week Overview Regular expressions basics Literal matching.wildcard Delimiters Character classes * repetition symbol Grouping Anchoring Search Search and replace in vi Regular Expressions
Paolo Santinelli Sistemi e Reti. Regular expressions. Regular expressions aim to facilitate the solution of text manipulation problems
 aim to facilitate the solution of text manipulation problems are symbolic notations used to identify patterns in text; are supported by many command line tools; are supported by most programming languages;
aim to facilitate the solution of text manipulation problems are symbolic notations used to identify patterns in text; are supported by many command line tools; are supported by most programming languages;
Regular Expressions Explained
 Found at: http://publish.ez.no/article/articleprint/11/ Regular Expressions Explained Author: Jan Borsodi Publishing date: 30.10.2000 18:02 This article will give you an introduction to the world of regular
Found at: http://publish.ez.no/article/articleprint/11/ Regular Expressions Explained Author: Jan Borsodi Publishing date: 30.10.2000 18:02 This article will give you an introduction to the world of regular
Here's an example of how the method works on the string "My text" with a start value of 3 and a length value of 2:
 CS 1251 Page 1 Friday Friday, October 31, 2014 10:36 AM Finding patterns in text A smaller string inside of a larger one is called a substring. You have already learned how to make substrings in the spreadsheet
CS 1251 Page 1 Friday Friday, October 31, 2014 10:36 AM Finding patterns in text A smaller string inside of a larger one is called a substring. You have already learned how to make substrings in the spreadsheet
Some (semi-)advanced tips for LibreOffice
 Some (semi-)advanced tips for LibreOffice by Andy Pepperdine Introduction We cover several tips on special things in Writer and Calc and anything else that turns up. Although I use LibreOffice, these should
Some (semi-)advanced tips for LibreOffice by Andy Pepperdine Introduction We cover several tips on special things in Writer and Calc and anything else that turns up. Although I use LibreOffice, these should
Describing Languages with Regular Expressions
 University of Oslo : Department of Informatics Describing Languages with Regular Expressions Jonathon Read 25 September 2012 INF4820: Algorithms for AI and NLP Outlook How can we write programs that handle
University of Oslo : Department of Informatics Describing Languages with Regular Expressions Jonathon Read 25 September 2012 INF4820: Algorithms for AI and NLP Outlook How can we write programs that handle
Understanding Regular Expressions, Special Characters, and Patterns
 APPENDIXA Understanding Regular Expressions, Special Characters, and Patterns This appendix describes the regular expressions, special or wildcard characters, and patterns that can be used with filters
APPENDIXA Understanding Regular Expressions, Special Characters, and Patterns This appendix describes the regular expressions, special or wildcard characters, and patterns that can be used with filters
Bioinformatics Programming. EE, NCKU Tien-Hao Chang (Darby Chang)
 Bioinformatics Programming EE, NCKU Tien-Hao Chang (Darby Chang) 1 Regular Expression 2 http://rp1.monday.vip.tw1.yahoo.net/res/gdsale/st_pic/0469/st-469571-1.jpg 3 Text patterns and matches A regular
Bioinformatics Programming EE, NCKU Tien-Hao Chang (Darby Chang) 1 Regular Expression 2 http://rp1.monday.vip.tw1.yahoo.net/res/gdsale/st_pic/0469/st-469571-1.jpg 3 Text patterns and matches A regular
Functional Programming in Haskell Prof. Madhavan Mukund and S. P. Suresh Chennai Mathematical Institute
 Functional Programming in Haskell Prof. Madhavan Mukund and S. P. Suresh Chennai Mathematical Institute Module # 02 Lecture - 03 Characters and Strings So, let us turn our attention to a data type we have
Functional Programming in Haskell Prof. Madhavan Mukund and S. P. Suresh Chennai Mathematical Institute Module # 02 Lecture - 03 Characters and Strings So, let us turn our attention to a data type we have
Code Editor. The Code Editor is made up of the following areas: Toolbar. Editable Area Output Panel Status Bar Outline. Toolbar
 Code Editor Wakanda s Code Editor is a powerful editor where you can write your JavaScript code for events and functions in datastore classes, attributes, Pages, widgets, and much more. Besides JavaScript,
Code Editor Wakanda s Code Editor is a powerful editor where you can write your JavaScript code for events and functions in datastore classes, attributes, Pages, widgets, and much more. Besides JavaScript,
ITST Searching, Extracting & Archiving Data
 ITST 1136 - Searching, Extracting & Archiving Data Name: Step 1 Sign into a Pi UN = pi PW = raspberry Step 2 - Grep - One of the most useful and versatile commands in a Linux terminal environment is the
ITST 1136 - Searching, Extracting & Archiving Data Name: Step 1 Sign into a Pi UN = pi PW = raspberry Step 2 - Grep - One of the most useful and versatile commands in a Linux terminal environment is the
Regular Expressions. Regular expressions are a powerful search-and-replace technique that is widely used in other environments (such as Unix and Perl)
 Regular Expressions Regular expressions are a powerful search-and-replace technique that is widely used in other environments (such as Unix and Perl) JavaScript started supporting regular expressions in
Regular Expressions Regular expressions are a powerful search-and-replace technique that is widely used in other environments (such as Unix and Perl) JavaScript started supporting regular expressions in
IT441. Regular Expressions. Handling Text: DRAFT. Network Services Administration
 IT441 Network Services Administration Handling Text: DRAFT Regular Expressions Searching for Text in a File Make note of the following directory: /home/ckelly/course_files/it441_files Given the file gettysburg.txt
IT441 Network Services Administration Handling Text: DRAFT Regular Expressions Searching for Text in a File Make note of the following directory: /home/ckelly/course_files/it441_files Given the file gettysburg.txt
(Refer Slide Time: 01:12)
 Internet Technology Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture No #22 PERL Part II We continue with our discussion on the Perl
Internet Technology Prof. Indranil Sengupta Department of Computer Science and Engineering Indian Institute of Technology, Kharagpur Lecture No #22 PERL Part II We continue with our discussion on the Perl
Regular Expressions. Computer Science and Engineering College of Engineering The Ohio State University. Lecture 9
 Regular Expressions Computer Science and Engineering College of Engineering The Ohio State University Lecture 9 Language Definition: a set of strings Examples Activity: For each above, find (the cardinality
Regular Expressions Computer Science and Engineering College of Engineering The Ohio State University Lecture 9 Language Definition: a set of strings Examples Activity: For each above, find (the cardinality
Shorthand for values: variables
 Chapter 2 Shorthand for values: variables 2.1 Defining a variable You ve typed a lot of expressions into the computer involving pictures, but every time you need a different picture, you ve needed to find
Chapter 2 Shorthand for values: variables 2.1 Defining a variable You ve typed a lot of expressions into the computer involving pictures, but every time you need a different picture, you ve needed to find
Configuring the RADIUS Listener LEG
 CHAPTER 16 Revised: July 28, 2009, Introduction This module describes the configuration procedure for the RADIUS Listener LEG. The RADIUS Listener LEG is configured using the SM configuration file p3sm.cfg,
CHAPTER 16 Revised: July 28, 2009, Introduction This module describes the configuration procedure for the RADIUS Listener LEG. The RADIUS Listener LEG is configured using the SM configuration file p3sm.cfg,
Using Lex or Flex. Prof. James L. Frankel Harvard University
 Using Lex or Flex Prof. James L. Frankel Harvard University Version of 1:07 PM 26-Sep-2016 Copyright 2016, 2015 James L. Frankel. All rights reserved. Lex Regular Expressions (1 of 4) Special characters
Using Lex or Flex Prof. James L. Frankel Harvard University Version of 1:07 PM 26-Sep-2016 Copyright 2016, 2015 James L. Frankel. All rights reserved. Lex Regular Expressions (1 of 4) Special characters
Searching Guide. September 16, Version 9.3
 Searching Guide September 16, 2016 - Version 9.3 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Searching Guide September 16, 2016 - Version 9.3 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
STREAM EDITOR - REGULAR EXPRESSIONS
 STREAM EDITOR - REGULAR EXPRESSIONS http://www.tutorialspoint.com/sed/sed_regular_expressions.htm Copyright tutorialspoint.com It is the regular expressions that make SED powerful and efficient. A number
STREAM EDITOR - REGULAR EXPRESSIONS http://www.tutorialspoint.com/sed/sed_regular_expressions.htm Copyright tutorialspoint.com It is the regular expressions that make SED powerful and efficient. A number
CST Lab #5. Student Name: Student Number: Lab section:
 CST8177 - Lab #5 Student Name: Student Number: Lab section: Working with Regular Expressions (aka regex or RE) In-Lab Demo - List all the non-user accounts in /etc/passwd that use /sbin as their home directory.
CST8177 - Lab #5 Student Name: Student Number: Lab section: Working with Regular Expressions (aka regex or RE) In-Lab Demo - List all the non-user accounts in /etc/passwd that use /sbin as their home directory.
Lecture 05 I/O statements Printf, Scanf Simple statements, Compound statements
 Programming, Data Structures and Algorithms Prof. Shankar Balachandran Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 05 I/O statements Printf, Scanf Simple
Programming, Data Structures and Algorithms Prof. Shankar Balachandran Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 05 I/O statements Printf, Scanf Simple
Flow Control. So Far: Writing simple statements that get executed one after another.
 Flow Control So Far: Writing simple statements that get executed one after another. Flow Control So Far: Writing simple statements that get executed one after another. Flow control allows the programmer
Flow Control So Far: Writing simple statements that get executed one after another. Flow Control So Far: Writing simple statements that get executed one after another. Flow control allows the programmer
Mobile Computing Professor Pushpendra Singh Indraprastha Institute of Information Technology Delhi Java Basics Lecture 02
 Mobile Computing Professor Pushpendra Singh Indraprastha Institute of Information Technology Delhi Java Basics Lecture 02 Hello, in this lecture we will learn about some fundamentals concepts of java.
Mobile Computing Professor Pushpendra Singh Indraprastha Institute of Information Technology Delhi Java Basics Lecture 02 Hello, in this lecture we will learn about some fundamentals concepts of java.
PHP and MySQL for Dynamic Web Sites. Intro Ed Crowley
 PHP and MySQL for Dynamic Web Sites Intro Ed Crowley Class Preparation If you haven t already, download the sample scripts from: http://www.larryullman.com/books/phpand-mysql-for-dynamic-web-sitesvisual-quickpro-guide-4thedition/#downloads
PHP and MySQL for Dynamic Web Sites Intro Ed Crowley Class Preparation If you haven t already, download the sample scripts from: http://www.larryullman.com/books/phpand-mysql-for-dynamic-web-sitesvisual-quickpro-guide-4thedition/#downloads
Principles of Compiler Design Prof. Y. N. Srikant Department of Computer Science and Automation Indian Institute of Science, Bangalore
 (Refer Slide Time: 00:20) Principles of Compiler Design Prof. Y. N. Srikant Department of Computer Science and Automation Indian Institute of Science, Bangalore Lecture - 4 Lexical Analysis-Part-3 Welcome
(Refer Slide Time: 00:20) Principles of Compiler Design Prof. Y. N. Srikant Department of Computer Science and Automation Indian Institute of Science, Bangalore Lecture - 4 Lexical Analysis-Part-3 Welcome
Getting to grips with Unix and the Linux family
 Getting to grips with Unix and the Linux family David Chiappini, Giulio Pasqualetti, Tommaso Redaelli Torino, International Conference of Physics Students August 10, 2017 According to the booklet At this
Getting to grips with Unix and the Linux family David Chiappini, Giulio Pasqualetti, Tommaso Redaelli Torino, International Conference of Physics Students August 10, 2017 According to the booklet At this
Server-side Web Development (I3302) Semester: 1 Academic Year: 2017/2018 Credits: 4 (50 hours) Dr Antoun Yaacoub
 Lebanese University Faculty of Science Computer Science BS Degree Server-side Web Development (I3302) Semester: 1 Academic Year: 2017/2018 Credits: 4 (50 hours) Dr Antoun Yaacoub 2 Regular expressions
Lebanese University Faculty of Science Computer Science BS Degree Server-side Web Development (I3302) Semester: 1 Academic Year: 2017/2018 Credits: 4 (50 hours) Dr Antoun Yaacoub 2 Regular expressions
Contents. Jairo Pava COMS W4115 June 28, 2013 LEARN: Language Reference Manual
 Jairo Pava COMS W4115 June 28, 2013 LEARN: Language Reference Manual Contents 1 Introduction...2 2 Lexical Conventions...2 3 Types...3 4 Syntax...3 5 Expressions...4 6 Declarations...8 7 Statements...9
Jairo Pava COMS W4115 June 28, 2013 LEARN: Language Reference Manual Contents 1 Introduction...2 2 Lexical Conventions...2 3 Types...3 4 Syntax...3 5 Expressions...4 6 Declarations...8 7 Statements...9
Laboratory Assignment #3 Eclipse CDT
 Lab 3 September 12, 2010 CS-2303, System Programming Concepts, A-term 2012 Objective Laboratory Assignment #3 Eclipse CDT Due: at 11:59 pm on the day of your lab session To learn to learn to use the Eclipse
Lab 3 September 12, 2010 CS-2303, System Programming Concepts, A-term 2012 Objective Laboratory Assignment #3 Eclipse CDT Due: at 11:59 pm on the day of your lab session To learn to learn to use the Eclipse
HTML/CSS Lesson Plans
 HTML/CSS Lesson Plans Course Outline 8 lessons x 1 hour Class size: 15-25 students Age: 10-12 years Requirements Computer for each student (or pair) and a classroom projector Pencil and paper Internet
HTML/CSS Lesson Plans Course Outline 8 lessons x 1 hour Class size: 15-25 students Age: 10-12 years Requirements Computer for each student (or pair) and a classroom projector Pencil and paper Internet
Intro to Programming. Unit 7. What is Programming? What is Programming? Intro to Programming
 Intro to Programming Unit 7 Intro to Programming 1 What is Programming? 1. Programming Languages 2. Markup vs. Programming 1. Introduction 2. Print Statement 3. Strings 4. Types and Values 5. Math Externals
Intro to Programming Unit 7 Intro to Programming 1 What is Programming? 1. Programming Languages 2. Markup vs. Programming 1. Introduction 2. Print Statement 3. Strings 4. Types and Values 5. Math Externals
BoredGames Language Reference Manual A Language for Board Games. Brandon Kessler (bpk2107) and Kristen Wise (kew2132)
 BoredGames Language Reference Manual A Language for Board Games Brandon Kessler (bpk2107) and Kristen Wise (kew2132) 1 Table of Contents 1. Introduction... 4 2. Lexical Conventions... 4 2.A Comments...
BoredGames Language Reference Manual A Language for Board Games Brandon Kessler (bpk2107) and Kristen Wise (kew2132) 1 Table of Contents 1. Introduction... 4 2. Lexical Conventions... 4 2.A Comments...
Fundamentals: Expressions and Assignment
 Fundamentals: Expressions and Assignment A typical Python program is made up of one or more statements, which are executed, or run, by a Python console (also known as a shell) for their side effects e.g,
Fundamentals: Expressions and Assignment A typical Python program is made up of one or more statements, which are executed, or run, by a Python console (also known as a shell) for their side effects e.g,
Searching Guide. November 17, Version 9.5
 Searching Guide November 17, 2017 - Version 9.5 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Searching Guide November 17, 2017 - Version 9.5 - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Lesson 1: Writing Your First JavaScript
 JavaScript 101 1-1 Lesson 1: Writing Your First JavaScript OBJECTIVES: In this lesson you will be taught how to Use the tag Insert JavaScript code in a Web page Hide your JavaScript
JavaScript 101 1-1 Lesson 1: Writing Your First JavaScript OBJECTIVES: In this lesson you will be taught how to Use the tag Insert JavaScript code in a Web page Hide your JavaScript
Object oriented programming. Instructor: Masoud Asghari Web page: Ch: 3
 Object oriented programming Instructor: Masoud Asghari Web page: http://www.masses.ir/lectures/oops2017sut Ch: 3 1 In this slide We follow: https://docs.oracle.com/javase/tutorial/index.html Trail: Learning
Object oriented programming Instructor: Masoud Asghari Web page: http://www.masses.ir/lectures/oops2017sut Ch: 3 1 In this slide We follow: https://docs.oracle.com/javase/tutorial/index.html Trail: Learning
Introduction to Programming in C Department of Computer Science and Engineering. Lecture No. #54. Organizing Code in multiple files
 Introduction to Programming in C Department of Computer Science and Engineering Lecture No. #54 Organizing Code in multiple files (Refer Slide Time: 00:09) In this lecture, let us look at one particular
Introduction to Programming in C Department of Computer Science and Engineering Lecture No. #54 Organizing Code in multiple files (Refer Slide Time: 00:09) In this lecture, let us look at one particular
SEER AKADEMI LINUX PROGRAMMING AND SCRIPTINGPERL 7
 SEER AKADEMI LINUX PROGRAMMING AND SCRIPTINGPERL 7 Hi everyone once again welcome to this lecture we are actually the course is Linux programming and scripting we have been talking about the Perl, Perl
SEER AKADEMI LINUX PROGRAMMING AND SCRIPTINGPERL 7 Hi everyone once again welcome to this lecture we are actually the course is Linux programming and scripting we have been talking about the Perl, Perl
Indian Institute of Technology Kharagpur. PERL Part III. Prof. Indranil Sen Gupta Dept. of Computer Science & Engg. I.I.T.
 Indian Institute of Technology Kharagpur PERL Part III Prof. Indranil Sen Gupta Dept. of Computer Science & Engg. I.I.T. Kharagpur, INDIA Lecture 23: PERL Part III On completion, the student will be able
Indian Institute of Technology Kharagpur PERL Part III Prof. Indranil Sen Gupta Dept. of Computer Science & Engg. I.I.T. Kharagpur, INDIA Lecture 23: PERL Part III On completion, the student will be able
Version June 2017
 Version 2.7.0 19 June 2017 Published by Just Great Software Co. Ltd. Copyright 2009 2017 Jan Goyvaerts. All rights reserved. RegexMagic and Just Great Software are trademarks of Jan Goyvaerts i Table of
Version 2.7.0 19 June 2017 Published by Just Great Software Co. Ltd. Copyright 2009 2017 Jan Goyvaerts. All rights reserved. RegexMagic and Just Great Software are trademarks of Jan Goyvaerts i Table of
CHAD Language Reference Manual
 CHAD Language Reference Manual INTRODUCTION The CHAD programming language is a limited purpose programming language designed to allow teachers and students to quickly code algorithms involving arrays,
CHAD Language Reference Manual INTRODUCTION The CHAD programming language is a limited purpose programming language designed to allow teachers and students to quickly code algorithms involving arrays,
CODESYS V3 Quick Start
 Programming a Garage Door Drive with CODESYS V3 On the following pages we would like to show you how easy it is to program a simple automation project with CODESYS V3. To start with, we would like to make
Programming a Garage Door Drive with CODESYS V3 On the following pages we would like to show you how easy it is to program a simple automation project with CODESYS V3. To start with, we would like to make
Voice Translation Rules
 Voice Translation Rules Document ID: 61083 Contents Introduction Prerequisites Requirements Components Used Conventions Simple Match and Replace Pattern Match with Wildcards Number Slice Number Type and
Voice Translation Rules Document ID: 61083 Contents Introduction Prerequisites Requirements Components Used Conventions Simple Match and Replace Pattern Match with Wildcards Number Slice Number Type and
9.2 Linux Essentials Exam Objectives
 9.2 Linux Essentials Exam Objectives This chapter will cover the topics for the following Linux Essentials exam objectives: Topic 3: The Power of the Command Line (weight: 10) 3.3: Turning Commands into
9.2 Linux Essentials Exam Objectives This chapter will cover the topics for the following Linux Essentials exam objectives: Topic 3: The Power of the Command Line (weight: 10) 3.3: Turning Commands into
First Java Program - Output to the Screen
 First Java Program - Output to the Screen These notes are written assuming that the reader has never programmed in Java, but has programmed in another language in the past. In any language, one of the
First Java Program - Output to the Screen These notes are written assuming that the reader has never programmed in Java, but has programmed in another language in the past. In any language, one of the
Programming Fundamentals
 Programming Fundamentals Computers are really very dumb machines -- they only do what they are told to do. Most computers perform their operations on a very primitive level. The basic operations of a computer
Programming Fundamentals Computers are really very dumb machines -- they only do what they are told to do. Most computers perform their operations on a very primitive level. The basic operations of a computer
Regular Expressions. Regular Expression Syntax in Python. Achtung!
 1 Regular Expressions Lab Objective: Cleaning and formatting data are fundamental problems in data science. Regular expressions are an important tool for working with text carefully and eciently, and are
1 Regular Expressions Lab Objective: Cleaning and formatting data are fundamental problems in data science. Regular expressions are an important tool for working with text carefully and eciently, and are
R E G U L A R E X P R E S S I O N S
 R E G U L A R E X P R E S S I O N S F O R D ATA C L E A N U P I N S I E R R A Lloyd Chittenden Union Catalog Coordinator Marmot Library Network WHAT ARE REGULAR EXPRESSIONS? Combine literal characters
R E G U L A R E X P R E S S I O N S F O R D ATA C L E A N U P I N S I E R R A Lloyd Chittenden Union Catalog Coordinator Marmot Library Network WHAT ARE REGULAR EXPRESSIONS? Combine literal characters
Java Bytecode (binary file)
 Java is Compiled Unlike Python, which is an interpreted langauge, Java code is compiled. In Java, a compiler reads in a Java source file (the code that we write), and it translates that code into bytecode.
Java is Compiled Unlike Python, which is an interpreted langauge, Java code is compiled. In Java, a compiler reads in a Java source file (the code that we write), and it translates that code into bytecode.
Quick Start Guide. CRM Business Machine
 Quick Start Guide CRM Business Machine If you need assistance or find an error in this guide, or if you d like to suggest an addition to this guide, just post a Trouble Ticket at www.lmrhelp.com This guide
Quick Start Guide CRM Business Machine If you need assistance or find an error in this guide, or if you d like to suggest an addition to this guide, just post a Trouble Ticket at www.lmrhelp.com This guide
Premium POS Pizza Order Entry Module. Introduction and Tutorial
 Premium POS Pizza Order Entry Module Introduction and Tutorial Overview The premium POS Pizza module is a replacement for the standard order-entry module. The standard module will still continue to be
Premium POS Pizza Order Entry Module Introduction and Tutorial Overview The premium POS Pizza module is a replacement for the standard order-entry module. The standard module will still continue to be
Programming in ROBOTC ROBOTC Rules
 Programming in ROBOTC ROBOTC Rules In this lesson, you will learn the basic rules for writing ROBOTC programs. ROBOTC is a text-based programming language Commands to the robot are first written as text
Programming in ROBOTC ROBOTC Rules In this lesson, you will learn the basic rules for writing ROBOTC programs. ROBOTC is a text-based programming language Commands to the robot are first written as text
PowerGREP. Manual. Version October 2005
 PowerGREP Manual Version 3.2 3 October 2005 Copyright 2002 2005 Jan Goyvaerts. All rights reserved. PowerGREP and JGsoft Just Great Software are trademarks of Jan Goyvaerts i Table of Contents How to
PowerGREP Manual Version 3.2 3 October 2005 Copyright 2002 2005 Jan Goyvaerts. All rights reserved. PowerGREP and JGsoft Just Great Software are trademarks of Jan Goyvaerts i Table of Contents How to
COMS 469: Interactive Media II
 COMS 469: Interactive Media II Agenda Review Data Types & Variables Decisions, Loops, and Functions Review gunkelweb.com/coms469 Review Basic Terminology Computer Languages Interpreted vs. Compiled Client
COMS 469: Interactive Media II Agenda Review Data Types & Variables Decisions, Loops, and Functions Review gunkelweb.com/coms469 Review Basic Terminology Computer Languages Interpreted vs. Compiled Client
Regexs with DFA and Parse Trees. CS230 Tutorial 11
 Regexs with DFA and Parse Trees CS230 Tutorial 11 Regular Expressions (Regex) This way of representing regular languages using metacharacters. Here are some of the most important ones to know: -- OR example:
Regexs with DFA and Parse Trees CS230 Tutorial 11 Regular Expressions (Regex) This way of representing regular languages using metacharacters. Here are some of the most important ones to know: -- OR example:
Draw beautiful and intricate patterns with Python Turtle, while learning how to code with Python.
 Raspberry Pi Learning Resources Turtle Snowflakes Draw beautiful and intricate patterns with Python Turtle, while learning how to code with Python. How to draw with Python Turtle 1. To begin, you will
Raspberry Pi Learning Resources Turtle Snowflakes Draw beautiful and intricate patterns with Python Turtle, while learning how to code with Python. How to draw with Python Turtle 1. To begin, you will
Essentials for Scientific Computing: Stream editing with sed and awk
 Essentials for Scientific Computing: Stream editing with sed and awk Ershaad Ahamed TUE-CMS, JNCASR May 2012 1 Stream Editing sed and awk are stream processing commands. What this means is that they are
Essentials for Scientific Computing: Stream editing with sed and awk Ershaad Ahamed TUE-CMS, JNCASR May 2012 1 Stream Editing sed and awk are stream processing commands. What this means is that they are
YOLOP Language Reference Manual
 YOLOP Language Reference Manual Sasha McIntosh, Jonathan Liu & Lisa Li sam2270, jl3516 and ll2768 1. Introduction YOLOP (Your Octothorpean Language for Optical Processing) is an image manipulation language
YOLOP Language Reference Manual Sasha McIntosh, Jonathan Liu & Lisa Li sam2270, jl3516 and ll2768 1. Introduction YOLOP (Your Octothorpean Language for Optical Processing) is an image manipulation language
Configuring the RADIUS Listener Login Event Generator
 CHAPTER 19 Configuring the RADIUS Listener Login Event Generator Published: December 21, 2012 Introduction This chapter describes the configuration procedure for the RADIUS listener Login Event Generator
CHAPTER 19 Configuring the RADIUS Listener Login Event Generator Published: December 21, 2012 Introduction This chapter describes the configuration procedure for the RADIUS listener Login Event Generator
Getting started with Java
 Getting started with Java Magic Lines public class MagicLines { public static void main(string[] args) { } } Comments Comments are lines in your code that get ignored during execution. Good for leaving
Getting started with Java Magic Lines public class MagicLines { public static void main(string[] args) { } } Comments Comments are lines in your code that get ignored during execution. Good for leaving
Access: You will have to
 Access: You will have to Create a new blank database Import data from a text file and set up the fields correctly Add some records to the table Create some reports. o For these reports you will need to
Access: You will have to Create a new blank database Import data from a text file and set up the fields correctly Add some records to the table Create some reports. o For these reports you will need to
Operating System Interaction via bash
 Operating System Interaction via bash bash, or the Bourne-Again Shell, is a popular operating system shell that is used by many platforms bash uses the command line interaction style generally accepted
Operating System Interaction via bash bash, or the Bourne-Again Shell, is a popular operating system shell that is used by many platforms bash uses the command line interaction style generally accepted
Tips and Tricks for Making the Most of Create Lists
 Tips and Tricks for Making the Most of Create Lists Matching and More Mike Monaco Coordinator, Cataloging Services The University of Akron mmonaco@uakron.edu OH-IUG October 12, 2018 The University of Akron
Tips and Tricks for Making the Most of Create Lists Matching and More Mike Monaco Coordinator, Cataloging Services The University of Akron mmonaco@uakron.edu OH-IUG October 12, 2018 The University of Akron
JavaScript Functions, Objects and Array
 JavaScript Functions, Objects and Array Defining a Function A definition starts with the word function. A name follows that must start with a letter or underscore, followed by any number of letters, digits,
JavaScript Functions, Objects and Array Defining a Function A definition starts with the word function. A name follows that must start with a letter or underscore, followed by any number of letters, digits,
The Warhol Language Reference Manual
 The Warhol Language Reference Manual Martina Atabong maa2247 Charvinia Neblett cdn2118 Samuel Nnodim son2105 Catherine Wes ciw2109 Sarina Xie sx2166 Introduction Warhol is a functional and imperative programming
The Warhol Language Reference Manual Martina Atabong maa2247 Charvinia Neblett cdn2118 Samuel Nnodim son2105 Catherine Wes ciw2109 Sarina Xie sx2166 Introduction Warhol is a functional and imperative programming
HCA Tech Note 103. Expressions. Example: Conversion
 Expressions This technical note provides several examples on some of the common uses of expressions and the Compute element. The Compute element opens a lower level of HCA than available from the Visual
Expressions This technical note provides several examples on some of the common uses of expressions and the Compute element. The Compute element opens a lower level of HCA than available from the Visual
Part II Composition of Functions
 Part II Composition of Functions The big idea in this part of the book is deceptively simple. It s that we can take the value returned by one function and use it as an argument to another function. By
Part II Composition of Functions The big idea in this part of the book is deceptively simple. It s that we can take the value returned by one function and use it as an argument to another function. By
Perl. Interview Questions and Answers
 and Answers Prepared by Abhisek Vyas Document Version 1.0 Team, www.sybaseblog.com 1 of 13 Q. How do you separate executable statements in perl? semi-colons separate executable statements Example: my(
and Answers Prepared by Abhisek Vyas Document Version 1.0 Team, www.sybaseblog.com 1 of 13 Q. How do you separate executable statements in perl? semi-colons separate executable statements Example: my(
More regular expressions, synchronizing data, comparing files
 More regular expressions, synchronizing data, comparing files Laboratory of Genomics & Bioinformatics in Parasitology Department of Parasitology, ICB, USP Regular expressions POSIX regular expressions
More regular expressions, synchronizing data, comparing files Laboratory of Genomics & Bioinformatics in Parasitology Department of Parasitology, ICB, USP Regular expressions POSIX regular expressions
Welcome Back! Without further delay, let s get started! First Things First. If you haven t done it already, download Turbo Lister from ebay.
 Welcome Back! Now that we ve covered the basics on how to use templates and how to customise them, it s time to learn some more advanced techniques that will help you create outstanding ebay listings!
Welcome Back! Now that we ve covered the basics on how to use templates and how to customise them, it s time to learn some more advanced techniques that will help you create outstanding ebay listings!
I/O and Shell Scripting
 I/O and Shell Scripting File Descriptors Redirecting Standard Error Shell Scripts Making a Shell Script Executable Specifying Which Shell Will Run a Script Comments in Shell Scripts File Descriptors Resources
I/O and Shell Scripting File Descriptors Redirecting Standard Error Shell Scripts Making a Shell Script Executable Specifying Which Shell Will Run a Script Comments in Shell Scripts File Descriptors Resources
Student Learning Assessment Management System Assessment Committee Member Directions
 Student Learning Assessment Management System Assessment Committee Member Directions https://prd-stem.temple.edu/slam Click on the links below to navigate to the corresponding section of the document.
Student Learning Assessment Management System Assessment Committee Member Directions https://prd-stem.temple.edu/slam Click on the links below to navigate to the corresponding section of the document.
Lab # 2. For today s lab:
 1 ITI 1120 Lab # 2 Contributors: G. Arbez, M. Eid, D. Inkpen, A. Williams, D. Amyot 1 For today s lab: Go the course webpage Follow the links to the lab notes for Lab 2. Save all the java programs you
1 ITI 1120 Lab # 2 Contributors: G. Arbez, M. Eid, D. Inkpen, A. Williams, D. Amyot 1 For today s lab: Go the course webpage Follow the links to the lab notes for Lab 2. Save all the java programs you
SPEECH RECOGNITION COMMON COMMANDS
 SPEECH RECOGNITION COMMON COMMANDS FREQUENTLY USED COMMANDS The table below shows some of the most commonly used commands in Windows Speech Recognition. The words in italics indicate that many different
SPEECH RECOGNITION COMMON COMMANDS FREQUENTLY USED COMMANDS The table below shows some of the most commonly used commands in Windows Speech Recognition. The words in italics indicate that many different
Thoroughbred Basic TM Customization and Tuning Guide
 Thoroughbred Basic TM Customization and Tuning Guide Volume I: Terminals, Printers, Directories, Ghost Tasks Version 8.8.0 46 Vreeland Drive Skillman, NJ 08558-2638 Telephone: 732-560-1377 Outside NJ 800-524-0430
Thoroughbred Basic TM Customization and Tuning Guide Volume I: Terminals, Printers, Directories, Ghost Tasks Version 8.8.0 46 Vreeland Drive Skillman, NJ 08558-2638 Telephone: 732-560-1377 Outside NJ 800-524-0430
Considerations for Constructing Twitter Queries in SMA
 Considerations for Constructing Twitter Queries in SMA This document is intended for users who write BoardReader queries in SMA to trigger collection of Twitter content via a GNIP Power Track instance.
Considerations for Constructing Twitter Queries in SMA This document is intended for users who write BoardReader queries in SMA to trigger collection of Twitter content via a GNIP Power Track instance.
Who This Book Is For What This Book Covers How This Book Is Structured What You Need to Use This Book. Source Code
 Contents Introduction Who This Book Is For What This Book Covers How This Book Is Structured What You Need to Use This Book Conventions Source Code Errata p2p.wrox.com xxi xxi xxii xxii xxiii xxiii xxiv
Contents Introduction Who This Book Is For What This Book Covers How This Book Is Structured What You Need to Use This Book Conventions Source Code Errata p2p.wrox.com xxi xxi xxii xxii xxiii xxiii xxiv
successes without magic London,
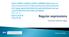 (\d)(?:\u0020 \u0209 \u202f \u200a){0,1}((m mm cm km V mv µv l ml C Nm A ma bar s kv Hz khz M Hz t kg g mg W kw MW Ah mah N kn obr min µm µs Pa MPa kpa hpa mbar µf db)\b) ^\t*'.+?' => ' (\d+)(,)(\d+)k
(\d)(?:\u0020 \u0209 \u202f \u200a){0,1}((m mm cm km V mv µv l ml C Nm A ma bar s kv Hz khz M Hz t kg g mg W kw MW Ah mah N kn obr min µm µs Pa MPa kpa hpa mbar µf db)\b) ^\t*'.+?' => ' (\d+)(,)(\d+)k
Hands on Assignment 1
 Hands on Assignment 1 CSci 2021-10, Fall 2018. Released Sept 10, 2018. Due Sept 24, 2018 at 11:55 PM Introduction Your task for this assignment is to build a command-line spell-checking program. You may
Hands on Assignment 1 CSci 2021-10, Fall 2018. Released Sept 10, 2018. Due Sept 24, 2018 at 11:55 PM Introduction Your task for this assignment is to build a command-line spell-checking program. You may
22-Sep CSCI 2132 Software Development Lecture 8: Shells, Processes, and Job Control. Faculty of Computer Science, Dalhousie University
 Lecture 8 p.1 Faculty of Computer Science, Dalhousie University CSCI 2132 Software Development Lecture 8: Shells, Processes, and Job Control 22-Sep-2017 Location: Goldberg CS 127 Time: 14:35 15:25 Instructor:
Lecture 8 p.1 Faculty of Computer Science, Dalhousie University CSCI 2132 Software Development Lecture 8: Shells, Processes, and Job Control 22-Sep-2017 Location: Goldberg CS 127 Time: 14:35 15:25 Instructor:
Unix Tutorial Haverford Astronomy 2014/2015
 Unix Tutorial Haverford Astronomy 2014/2015 Overview of Haverford astronomy computing resources This tutorial is intended for use on computers running the Linux operating system, including those in the
Unix Tutorial Haverford Astronomy 2014/2015 Overview of Haverford astronomy computing resources This tutorial is intended for use on computers running the Linux operating system, including those in the
Outbound Routing Regular Expressions
 The Barracuda Phone System uses Perl-compatible regular expressions for pattern matching in outbound gateways. The vast majority of all patterns that must be matched in outbound routes are digit-based
The Barracuda Phone System uses Perl-compatible regular expressions for pattern matching in outbound gateways. The vast majority of all patterns that must be matched in outbound routes are digit-based
Introduction to Unix
 Introduction to Unix Part 1: Navigating directories First we download the directory called "Fisher" from Carmen. This directory contains a sample from the Fisher corpus. The Fisher corpus is a collection
Introduction to Unix Part 1: Navigating directories First we download the directory called "Fisher" from Carmen. This directory contains a sample from the Fisher corpus. The Fisher corpus is a collection
Problem Solving through Programming In C Prof. Anupam Basu Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur
 Problem Solving through Programming In C Prof. Anupam Basu Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur Lecture 17 Switch Statement (Refer Slide Time: 00:23) In
Problem Solving through Programming In C Prof. Anupam Basu Department of Computer Science & Engineering Indian Institute of Technology, Kharagpur Lecture 17 Switch Statement (Refer Slide Time: 00:23) In
Creating a C++ Program
 Program A computer program (also software, or just a program) is a sequence of instructions written in a sequence to perform a specified task with a computer. 1 Creating a C++ Program created using an
Program A computer program (also software, or just a program) is a sequence of instructions written in a sequence to perform a specified task with a computer. 1 Creating a C++ Program created using an
Pattern Matching. An Introduction to File Globs and Regular Expressions
 Pattern Matching An Introduction to File Globs and Regular Expressions Copyright 2006 2009 Stewart Weiss The danger that lies ahead Much to your disadvantage, there are two different forms of patterns
Pattern Matching An Introduction to File Globs and Regular Expressions Copyright 2006 2009 Stewart Weiss The danger that lies ahead Much to your disadvantage, there are two different forms of patterns
Computers and Computation. The Modern Computer. The Operating System. The Operating System
 The Modern Computer Computers and Computation What is a computer? A machine that manipulates data according to instructions. Despite their apparent complexity, at the lowest level computers perform simple
The Modern Computer Computers and Computation What is a computer? A machine that manipulates data according to instructions. Despite their apparent complexity, at the lowest level computers perform simple
Learning Excel VBA. Creating User Defined Functions. ComboProjects. Prepared By Daniel Lamarche
 Learning Excel VBA Creating User Defined Functions Prepared By Daniel Lamarche ComboProjects Creating User Defined Functions By Daniel Lamarche (Last update January 2016). User Defined Functions or UDFs
Learning Excel VBA Creating User Defined Functions Prepared By Daniel Lamarche ComboProjects Creating User Defined Functions By Daniel Lamarche (Last update January 2016). User Defined Functions or UDFs
Crayon (.cry) Language Reference Manual. Naman Agrawal (na2603) Vaidehi Dalmia (vd2302) Ganesh Ravichandran (gr2483) David Smart (ds3361)
 Crayon (.cry) Language Reference Manual Naman Agrawal (na2603) Vaidehi Dalmia (vd2302) Ganesh Ravichandran (gr2483) David Smart (ds3361) 1 Lexical Elements 1.1 Identifiers Identifiers are strings used
Crayon (.cry) Language Reference Manual Naman Agrawal (na2603) Vaidehi Dalmia (vd2302) Ganesh Ravichandran (gr2483) David Smart (ds3361) 1 Lexical Elements 1.1 Identifiers Identifiers are strings used
正则表达式 Frank from https://regex101.com/
 符号 英文说明 中文说明 \n Matches a newline character 新行 \r Matches a carriage return character 回车 \t Matches a tab character Tab 键 \0 Matches a null character Matches either an a, b or c character [abc] [^abc]
符号 英文说明 中文说明 \n Matches a newline character 新行 \r Matches a carriage return character 回车 \t Matches a tab character Tab 键 \0 Matches a null character Matches either an a, b or c character [abc] [^abc]
CS125 : Introduction to Computer Science. Lecture Notes #4 Type Checking, Input/Output, and Programming Style
 CS125 : Introduction to Computer Science Lecture Notes #4 Type Checking, Input/Output, and Programming Style c 2005, 2004, 2002, 2001, 2000 Jason Zych 1 Lecture 4 : Type Checking, Input/Output, and Programming
CS125 : Introduction to Computer Science Lecture Notes #4 Type Checking, Input/Output, and Programming Style c 2005, 2004, 2002, 2001, 2000 Jason Zych 1 Lecture 4 : Type Checking, Input/Output, and Programming
Security Provider Integration: Kerberos Server
 Security Provider Integration: Kerberos Server 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks are the
Security Provider Integration: Kerberos Server 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks are the
