Outbound Routing Regular Expressions
|
|
|
- Howard Eustace Gordon
- 5 years ago
- Views:
Transcription
1 The Barracuda Phone System uses Perl-compatible regular expressions for pattern matching in outbound gateways. The vast majority of all patterns that must be matched in outbound routes are digit-based only, therefore, the following tables focus on matching number patterns. Basic Usage Regular expressions use a combination of standard and meta-characters to create a pattern against which to match a specific string. Characters in the regular expression can mean different things depending on the context. For the sake of simplicity, this article focuses on the basic operation of regular expressions. The basic use of a regular expression is in a pattern match. The system compares a regular expression to a string of characters to determine if the string of characters matches the pattern described by the regular expression. The answer is either yes or no. Sometimes a yes is called a positive match and a no is called a negative match. Sample Patterns Table 1 lists common characters in a regular expression. Table 1. Regular Expression Common Characters. Character 1 Match only the digit 1 5 Match only the digit 5 Meaning 411 Match digit sequence 411 ^411 Match string beginning with $ Match string ending with 411 ^411$ Match exact string 411 (1) [0-9] Match any digit between 0 and 9 [2-9] Match any digit between 2 and 9 [456] Match either the digit 4, 5, or 6 # Match the # sign \* Match a literal * (2) \d Match any digit between 0 and 9 ^ Match at beginning of string $ Match at end of string + Match one or more of the preceding character * Match zero or more of the preceding character {n} Match exactly n of the preceding character Notes: (1) See Table 2 for sample usage. (2) Note the backslash; this is different than a bare asterisk '*' The list of characters in Table 1 is by no means comprehensive, however it is a good representation of the kinds of characters that appear in regular expression number routes. Table 2 lists examples of how these expressions might be used in matching patterns for outbound dialing, illustrating some simple patterns, strings, and whether there is a match. Table 2. Sample Patterns. 1 / 5
2 Pattern Dialed Number Match? Notes Yes Yes Matches any number that includes 411 ^411$ 411 Yes ^411$ No Matches only the exact dialed 411 ^5[0-9][0-9][0-9] 5000 Yes Matches any four digit number beginning with 5 ^5\d\d\d$ 5000 Yes Same as previous pattern, \d matches any digit ^5\d{3}$ 5000 Yes Same as previous pattern, \d{3} same as \d\d\d ^71\d\d$ 7150 Yes ^71\d\d$ 7050 No Matches only dialed numbers from 7100 to 7199 ^\d{7}$ Yes ^\d{10}$ Yes The examples in Table 2 demonstrate the syntax for specifying dialed patterns. Syntax Rules To match an exact dial string, use ^ and $ at the beginning and end of your regular expression. The caret (^) means "match at the beginning of the string" and the dollar sign ($) means match at the end of the string. Reviewing the 411 examples in the previous table, the following syntax rules apply: The pattern 411 means match any string that contains 411 The pattern ^411 means match any string that begins with 411 The pattern 411$ means match any string that ends with 411 The pattern ^411$ means match any string that matches exactly 411 To match a range of numbers, use a combination of literal numbers and meta-characters. Consider these examples: The pattern 7\d\d\d matches 7000 through 7999 The pattern 74\d\d matches 7400 through 7499 The pattern 745\d matches 7450 through \d{7} matches calls made to area code \d{7} matches calls made to area code 212 Replacing and Trimming Digits In some cases you may want to add or remove digits before they are sent out, for example, "dial 9 to get an outside line." Table 3 lists examples of inserting digits. Table 3. Inserting Digits. Pattern Dialed Digits Digits Actually Sent Out ^9(1\d{10}):::$ ^9(\d{7}):::$ In the examples in Table 3, the leading digit 9 is matched, but not captured. Instead, all digits dialed after the 9 are captured. The expression ":::$1" means to replace what was actually dialed with what was captured inside the "(" and ")" characters. In some cases you may want to allow users to dial 9 (or not) and dial 1 (or not) and then have the system dial appropriately. For example, some carriers absolutely require you to send 1 + area code + phone number for all calls, even local ones. Others require all 10 digits of the phone number but do not want the leading 1. Table 4 lists some sample regular expressions for such situations: 2 / 5
3 Table 4. Sample Regular Expressions. Pattern Dialed Digits Sent Digits Application ^9?1?(\d{10})$:::$ Dialing 9 or 1 optional, send only 10 digits ^9?1?(\d{10})$:::1$ Dialing 9 or 1 optional, send digits ^9?(\d{7})$:::408$ ^9?(\d{7})$:::1408$ Regular Expression Caveats Dialing 9 optional, user s 7 digits, system adds and sends area code Dialing 9 optional, user s 7 digits, system adds/sends 1+area code There are occasions when regular expression matches may not function in the expected manner. Other times there are unintended consequences of using a specific pattern. One such caveat has to do with vanity numbers. For example, the outbound route pattern ^1?(\d{10})$:::1$1 (optional 1 plus exactly 10 digits) works for any typical North American 10-digit phone number, whether or not the caller dials a leading 1. But a vanity number such as ANTI-SPAM has 1 plus 11 digits which fails to match. Therefore, dialing 1 plus fails. There are two ways in which to prevent this: Educate your users on vanity numbers in your locale. In North America that would mean simply dialing the first 10 digits following the 1. In the case of ANTI-SPAM the call simply dials Write a pattern that explicitly handles these kinds of numbers. In North America this may mean matching an extra digit but not actually capturing it. The above pattern could be modified in the following manner: ^1?(\d{10})\d?$:::1$1 You can also modify the NANPA pattern to handle an extra digit: ^1?([2-9]\d{2}[2-9]\d{6})\d?$:::1$1 Both of the modified patterns allow an extra digit in the dialed which is not captured (it is ignored) so only the first 10 digits after the optional leading 1 are compared for a match. Handling E.164 Formatted Numbers Many contacts and phone numbers are in E.164 format. The primary characteristic of E.164 numbers is a leading + in the phone number. Examples of E.164 formatted numbers include: (USA) (UK) (Spain) (Australia) (South Africa) When the Barracuda Phone System receives an inbound call it automatically strips the leading + character because once the call is at the destination the + character serves no purpose. Outbound calls behave differently. Sometimes a registered endpoint sends a phone number that has a leading plus character. For example, a contact dialed from the Communication Command Center could contain a leading +. In this situation the Barracuda Phone System does not strip a leading + from an outbound dialed sequence. Outbound routes that might see E.164 formatted numbers must account for the leading plus. Table 5 lists regular expression patterns you can use to accomplish this. Table 5. Regular Expression Patterns to use with E.164 Formatted Numbers. ^\+? Expression Description Meaning match an optional leading plus character 3 / 5
4 ^\+(\d{5,15})$:::$1 A full E.164 Barracuda Phone System route which strips off the leading plus and sends only numeric digits to the destination. 4 / 5
5 5 / 5
Dial Peer Features and Configuration
 Establishing voice communication over a packet network is similar to configuring a static route: You are establishing a specific voice connection between two defined endpoints. Call legs define the discrete
Establishing voice communication over a packet network is similar to configuring a static route: You are establishing a specific voice connection between two defined endpoints. Call legs define the discrete
Grandstream Networks, Inc. Configuring UCM6XXX Series with HT503with
 Grandstream Networks, Inc. with Table of Contents OVERVIEW... 4 METHOD 1: REGISTER HT503 TO UCM6XXX... 5 Create Extension on UCM6XXX... 5 Create IVR on UCM6XXX... 6 Configure FXS Port on HT503... 7 Configure
Grandstream Networks, Inc. with Table of Contents OVERVIEW... 4 METHOD 1: REGISTER HT503 TO UCM6XXX... 5 Create Extension on UCM6XXX... 5 Create IVR on UCM6XXX... 6 Configure FXS Port on HT503... 7 Configure
Configure Call Routing
 Call Routing Overview, page 1 Call Routing Prerequisites, page 2 Call Routing Configuration Task Flow, page 2 Call Routing Overview The system uses route plans to determine how to route calls between clusters,
Call Routing Overview, page 1 Call Routing Prerequisites, page 2 Call Routing Configuration Task Flow, page 2 Call Routing Overview The system uses route plans to determine how to route calls between clusters,
Configure Call Routing
 Call Routing Overview Call Routing Overview, on page 1 Call Routing Prerequisites, on page 2 Call Routing Configuration Task Flow, on page 2 Call Routing Restrictions, on page 16 The system uses route
Call Routing Overview Call Routing Overview, on page 1 Call Routing Prerequisites, on page 2 Call Routing Configuration Task Flow, on page 2 Call Routing Restrictions, on page 16 The system uses route
Grandstream Networks, Inc. Configuring UCM6XXX with GXW410X
 Grandstream Networks, Inc. Table of Contents OVERVIEW... 4 CONNECT UCM6XXX TO GXW410X USING PEER SIP TRUNK... 5 Create IVR On UCM6XXX... 5 Create Peer SIP TRUNK On UCM6XXX... 5 Configure Outbound Rule
Grandstream Networks, Inc. Table of Contents OVERVIEW... 4 CONNECT UCM6XXX TO GXW410X USING PEER SIP TRUNK... 5 Create IVR On UCM6XXX... 5 Create Peer SIP TRUNK On UCM6XXX... 5 Configure Outbound Rule
Version Advanced Outbound Routing
 Version 20160226 Advanced Outbound Routing Goal of this Module How Outbound Rules Work Criteria Matching Outbound Blocking Rules System Extensions Outbound Routing for Emergency Numbers Achieve Least Cost
Version 20160226 Advanced Outbound Routing Goal of this Module How Outbound Rules Work Criteria Matching Outbound Blocking Rules System Extensions Outbound Routing for Emergency Numbers Achieve Least Cost
Office 365 Standalone Security
 The standalone Email Security option is available for purchase only through the Barracuda Self-Service Gateway or Barracuda MSP. Once you complete the Essentials for Office 365 Wizard, the Essentials page
The standalone Email Security option is available for purchase only through the Barracuda Self-Service Gateway or Barracuda MSP. Once you complete the Essentials for Office 365 Wizard, the Essentials page
How to Configure Office 365 for Inbound and Outbound Mail
 How to Configure Office 365 for Inbound and Outbound Mail You can configure Microsoft Office 365 with the Barracuda Email Security Service as your inbound and/or outbound mail gateway. If you make setting
How to Configure Office 365 for Inbound and Outbound Mail You can configure Microsoft Office 365 with the Barracuda Email Security Service as your inbound and/or outbound mail gateway. If you make setting
How Actuate Reports Process Adhoc Parameter Values and Expressions
 How Actuate Reports Process Adhoc Parameter Values and Expressions By Chris Geiss chris_geiss@yahoo.com How Actuate Reports Process Adhoc Parameter Values and Expressions By Chris Geiss (chris_geiss@yahoo.com)
How Actuate Reports Process Adhoc Parameter Values and Expressions By Chris Geiss chris_geiss@yahoo.com How Actuate Reports Process Adhoc Parameter Values and Expressions By Chris Geiss (chris_geiss@yahoo.com)
Symantec Security. Setup and Configuration Guide
 Symantec Email Security Setup and Configuration Guide I. Requirements A Symantec Email Security subscription A registered domain name Hosted email service Internet connection 2 II. Getting Started When
Symantec Email Security Setup and Configuration Guide I. Requirements A Symantec Email Security subscription A registered domain name Hosted email service Internet connection 2 II. Getting Started When
C How to Program, 6/e by Pearson Education, Inc. All Rights Reserved.
 C How to Program, 6/e 1992-2010 by Pearson Education, Inc. An important part of the solution to any problem is the presentation of the results. In this chapter, we discuss in depth the formatting features
C How to Program, 6/e 1992-2010 by Pearson Education, Inc. An important part of the solution to any problem is the presentation of the results. In this chapter, we discuss in depth the formatting features
Grandstream Networks, Inc. Peering HT8XX with GXW410X
 Grandstream Networks, Inc. Peering HT8XX with GXW410X Table of Contents OVERVIEW... 3 SCENARIO 1: PEERING ONE HT8XX WITH GXW410X... 4 HT8XX Configuration... 4 GXW410X Configuration... 6 One-To-One mapping...
Grandstream Networks, Inc. Peering HT8XX with GXW410X Table of Contents OVERVIEW... 3 SCENARIO 1: PEERING ONE HT8XX WITH GXW410X... 4 HT8XX Configuration... 4 GXW410X Configuration... 6 One-To-One mapping...
Voice Translation Rules
 Voice Translation Rules Document ID: 61083 Contents Introduction Prerequisites Requirements Components Used Conventions Simple Match and Replace Pattern Match with Wildcards Number Slice Number Type and
Voice Translation Rules Document ID: 61083 Contents Introduction Prerequisites Requirements Components Used Conventions Simple Match and Replace Pattern Match with Wildcards Number Slice Number Type and
Associate Users with Endpoints
 Users to Endpoints Association Overview, page 1 Prerequisites, page 1 Users and Devices Configuration Task Flow, page 1 Interactions and Restrictions, page 5 Users to Endpoints Association Overview This
Users to Endpoints Association Overview, page 1 Prerequisites, page 1 Users and Devices Configuration Task Flow, page 1 Interactions and Restrictions, page 5 Users to Endpoints Association Overview This
How to Use Adhoc Parameters in Actuate Reports
 How to Use Adhoc Parameters in Actuate Reports By Chris Geiss chris_geiss@yahoo.com http://www.chrisgeiss.com How to Use Adhoc Parameters in Actuate Reports By Chris Geiss Revised 3/31/2002 This document
How to Use Adhoc Parameters in Actuate Reports By Chris Geiss chris_geiss@yahoo.com http://www.chrisgeiss.com How to Use Adhoc Parameters in Actuate Reports By Chris Geiss Revised 3/31/2002 This document
Grandstream Networks, Inc. How to Manage Inbound / Outbound Routes on UCM6XXX
 Grandstream Networks, Inc. How to Manage Inbound / Outbound Routes on UCM6XXX Table of Contents OVERVIEW... 4 MANAGING OUTBOUND ROUTE... 5 Using Source Caller ID Filter... 5 Using Privilege Level... 7
Grandstream Networks, Inc. How to Manage Inbound / Outbound Routes on UCM6XXX Table of Contents OVERVIEW... 4 MANAGING OUTBOUND ROUTE... 5 Using Source Caller ID Filter... 5 Using Privilege Level... 7
This chapter provides information about Cisco Unified Communications Manager trunk configuration.
 Trunk setup This chapter provides information about Cisco Unified Communications Manager trunk configuration. About trunk setup, page 1 Find trunk, page 57 Set up trunk, page 57 Delete trunk, page 59 Reset
Trunk setup This chapter provides information about Cisco Unified Communications Manager trunk configuration. About trunk setup, page 1 Find trunk, page 57 Set up trunk, page 57 Delete trunk, page 59 Reset
Configure Digium G100 Gateway to operate with UCx Servers in Failover mode
 Published on Documentation (https://www.emetrotel.com/tsd) Home > Configure Digium G100 Gateway to operate with UCx Servers in Failover mode Configure Digium G100 Gateway to operate with UCx Servers in
Published on Documentation (https://www.emetrotel.com/tsd) Home > Configure Digium G100 Gateway to operate with UCx Servers in Failover mode Configure Digium G100 Gateway to operate with UCx Servers in
To begin this textbook, we need to start with a refresher of the topics of numbers and numbering systems.
 1.1 Integers To begin this textbook, we need to start with a refresher of the topics of numbers and numbering systems. We will start, here, with a recap of the simplest of numbering systems, the integers.
1.1 Integers To begin this textbook, we need to start with a refresher of the topics of numbers and numbering systems. We will start, here, with a recap of the simplest of numbering systems, the integers.
Phone Manager Application Support APRIL 2016 DOCUMENT RELEASE 4.3 APPLICATION SUPPORT
 Phone Manager Application Support APRIL 2016 DOCUMENT RELEASE 4.3 APPLICATION SUPPORT Microsoft Dynamics CRM NOTICE The information contained in this document is believed to be accurate in all respects
Phone Manager Application Support APRIL 2016 DOCUMENT RELEASE 4.3 APPLICATION SUPPORT Microsoft Dynamics CRM NOTICE The information contained in this document is believed to be accurate in all respects
Configure Hunt Pilots
 Hunt Pilot Overview, page 1 Hunt Pilot Configuration Task Flow, page 1 Hunt Pilot Overview Hunt pilots are strings of digits and wildcards that the system uses to route calls to directory numbers (DNs).
Hunt Pilot Overview, page 1 Hunt Pilot Configuration Task Flow, page 1 Hunt Pilot Overview Hunt pilots are strings of digits and wildcards that the system uses to route calls to directory numbers (DNs).
IP Access List Entry Sequence Numbering
 The feature allows you to apply sequence numbers to permit or deny statements as well as reorder, add, or remove such statements from a named IP access list. The IP Access List Entry Sequence Numbering
The feature allows you to apply sequence numbers to permit or deny statements as well as reorder, add, or remove such statements from a named IP access list. The IP Access List Entry Sequence Numbering
How to Make Anonymous Calls From a SIP Trunk
 How to Make Anonymous Calls From a SIP Trunk ScopTEL Software Prerequisites: You must have a valid copy of the ScopTEL software Minimum software release scopserv-telephony25-5.9.7.6.20170720 Minimum ScopServ
How to Make Anonymous Calls From a SIP Trunk ScopTEL Software Prerequisites: You must have a valid copy of the ScopTEL software Minimum software release scopserv-telephony25-5.9.7.6.20170720 Minimum ScopServ
Understanding Regular Expressions, Special Characters, and Patterns
 APPENDIXA Understanding Regular Expressions, Special Characters, and Patterns This appendix describes the regular expressions, special or wildcard characters, and patterns that can be used with filters
APPENDIXA Understanding Regular Expressions, Special Characters, and Patterns This appendix describes the regular expressions, special or wildcard characters, and patterns that can be used with filters
Filtering Service
 Secure E-Mail Gateway (SEG) Service Administrative Guides Email Filtering Service Regular Expressions Overview Regular Expressions Overview AT&T Secure E-Mail Gateway customers can use Regular Expressions
Secure E-Mail Gateway (SEG) Service Administrative Guides Email Filtering Service Regular Expressions Overview Regular Expressions Overview AT&T Secure E-Mail Gateway customers can use Regular Expressions
Regular Expressions. Regular expressions are a powerful search-and-replace technique that is widely used in other environments (such as Unix and Perl)
 Regular Expressions Regular expressions are a powerful search-and-replace technique that is widely used in other environments (such as Unix and Perl) JavaScript started supporting regular expressions in
Regular Expressions Regular expressions are a powerful search-and-replace technique that is widely used in other environments (such as Unix and Perl) JavaScript started supporting regular expressions in
Avaya PBX SIP TRUNKING Setup & User Guide
 Avaya PBX SIP TRUNKING Setup & User Guide Nextiva.com (800) 285-7995 2 P a g e Contents Description... 3 Avaya IP PBX Configuration... 3 Licensing and Physical Hardware... 4 System Tab Configuration...
Avaya PBX SIP TRUNKING Setup & User Guide Nextiva.com (800) 285-7995 2 P a g e Contents Description... 3 Avaya IP PBX Configuration... 3 Licensing and Physical Hardware... 4 System Tab Configuration...
Route Pattern Configuration
 CHAPTER 33 Use the following topics to find, add, update, copy, or delete a route pattern: Settings, page 33-1 Related Topics, page 33-11 Settings In Cisco Unified Communications Manager Administration,
CHAPTER 33 Use the following topics to find, add, update, copy, or delete a route pattern: Settings, page 33-1 Related Topics, page 33-11 Settings In Cisco Unified Communications Manager Administration,
Iridium. Roadpost Satellite Service. Customer Care. A free call from your Roadpost satellite phone:
 E E ID RVIC GU SE IS OUR TH Y D ING EA US R ORE F BE Roadpost Satellite Service Iridium User Guide Customer Care A free call from your Roadpost satellite phone: customercare@roadpost.com www.roadpost.com
E E ID RVIC GU SE IS OUR TH Y D ING EA US R ORE F BE Roadpost Satellite Service Iridium User Guide Customer Care A free call from your Roadpost satellite phone: customercare@roadpost.com www.roadpost.com
Hotline. Configuration Checklist for Hotline CHAPTER
 CHAPTER 26 The hotline feature extends the Private Line Automatic Ringdown (PLAR) feature, which allows you to configure a phone so that when the user goes off hook (or the NewCall softkey or line key
CHAPTER 26 The hotline feature extends the Private Line Automatic Ringdown (PLAR) feature, which allows you to configure a phone so that when the user goes off hook (or the NewCall softkey or line key
Connections & Call Routing
 Connections & Call Routing Mamta Buch Client Success Manager Mamta has been with netsapiens for about 8 years; with a background in Organization Development. She has worked with many aspects of netsapiens;
Connections & Call Routing Mamta Buch Client Success Manager Mamta has been with netsapiens for about 8 years; with a background in Organization Development. She has worked with many aspects of netsapiens;
Application Notes for Configuring Windstream SIP Trunking with Avaya IP Office - Issue 1.0
 Avaya Solution & Interoperability Test Lab Application Notes for Configuring Windstream SIP Trunking with Avaya IP Office - Issue 1.0 Abstract These Application Notes describe the procedures for configuring
Avaya Solution & Interoperability Test Lab Application Notes for Configuring Windstream SIP Trunking with Avaya IP Office - Issue 1.0 Abstract These Application Notes describe the procedures for configuring
Barracuda Link Balancer
 Barracuda Networks Technical Documentation Barracuda Link Balancer Administrator s Guide Version 2.3 RECLAIM YOUR NETWORK Copyright Notice Copyright 2004-2011, Barracuda Networks www.barracuda.com v2.3-111215-01-1215
Barracuda Networks Technical Documentation Barracuda Link Balancer Administrator s Guide Version 2.3 RECLAIM YOUR NETWORK Copyright Notice Copyright 2004-2011, Barracuda Networks www.barracuda.com v2.3-111215-01-1215
Cisco CRM Communications Connector for Cisco CallManager Express
 Cisco CRM Communications Connector for Cisco CallManager Express Cisco CRM Communications Connector (Cisco CCC) integrates Microsoft Customer Relationship Management (CRM) with Cisco CallManager Express
Cisco CRM Communications Connector for Cisco CallManager Express Cisco CRM Communications Connector (Cisco CCC) integrates Microsoft Customer Relationship Management (CRM) with Cisco CallManager Express
SIP dial rule setup. About SIP dial rule setup
 SIP dial rule setup This chapter provides information about SIP dial rules configuration. For additional information, see topics related to dial rules in the Cisco Unified Communications Manager System
SIP dial rule setup This chapter provides information about SIP dial rules configuration. For additional information, see topics related to dial rules in the Cisco Unified Communications Manager System
Common Components. Cisco Unified Border Element (SP Edition) Configuration Profile Examples 5 OL
 The following components of the Cisco Unified Border Element are common to all of the configuration profile examples in this document. Secure Media Adjacencies Call Policies CAC Policies SIP Profiles 5
The following components of the Cisco Unified Border Element are common to all of the configuration profile examples in this document. Secure Media Adjacencies Call Policies CAC Policies SIP Profiles 5
An SCTP-Protocol Data Unit with several chunks
 SCTP for Beginners Section 2 SCTP Packets he protocol data units (PDU) of SCTP are called SCTP packets. If SCTP runs over IP (as described in RFC2960 ), an SCTP packet forms the payload of an IP packet.
SCTP for Beginners Section 2 SCTP Packets he protocol data units (PDU) of SCTP are called SCTP packets. If SCTP runs over IP (as described in RFC2960 ), an SCTP packet forms the payload of an IP packet.
Below is a list of general guidelines for new SIP Trunking turnups that our customers + internal IDT staff should follow.
 Subject: SIP Trunking turnups General guidelines Version 1.0 Asterisk/Open Source Guide Date: December 12th, 2011 Below is a list of general guidelines for new SIP Trunking turnups that our customers +
Subject: SIP Trunking turnups General guidelines Version 1.0 Asterisk/Open Source Guide Date: December 12th, 2011 Below is a list of general guidelines for new SIP Trunking turnups that our customers +
Quick Installation Guide
 Quick Installation Guide BRI Gateway Version 2.1 Table of Contents Hardware Setup... 1 Accessing the WEB GUI... 2 Creating SIP Trunks... 3 Creating BRI Trunks... 4 Call Routing Rules... 4 Hardware Setup
Quick Installation Guide BRI Gateway Version 2.1 Table of Contents Hardware Setup... 1 Accessing the WEB GUI... 2 Creating SIP Trunks... 3 Creating BRI Trunks... 4 Call Routing Rules... 4 Hardware Setup
Oreka TR 1.4 User Manual
 Oreka TR 1.4 User Manual Rev. 3 August, 2012 2012 TABLE OF CONTENTS TABLE OF CONTENTS... 1 Chapter 1. Introduction... 2 1.1. What is Oreka... 2 1.2. Who should read this manual?... 2 Chapter 2. Recording
Oreka TR 1.4 User Manual Rev. 3 August, 2012 2012 TABLE OF CONTENTS TABLE OF CONTENTS... 1 Chapter 1. Introduction... 2 1.1. What is Oreka... 2 1.2. Who should read this manual?... 2 Chapter 2. Recording
Configuring an Error Response Code upon an Out-of-Dialog OPTIONS Ping Failure
 Configuring an Error Response Code upon an Out-of-Dialog OPTIONS Ping Failure Cisco Unified Border Element (Cisco UBE) provides an option to configure the error response code when a dial peer is busied
Configuring an Error Response Code upon an Out-of-Dialog OPTIONS Ping Failure Cisco Unified Border Element (Cisco UBE) provides an option to configure the error response code when a dial peer is busied
1. NORM.INV function Returns the inverse of the normal cumulative distribution for the specified mean and standard deviation.
 Excel Primer for Risk Management Course 1. NORM.INV function Returns the inverse of the normal cumulative distribution for the specified mean and standard deviation. 2. VLOOKUP The VLOOKUP function syntax
Excel Primer for Risk Management Course 1. NORM.INV function Returns the inverse of the normal cumulative distribution for the specified mean and standard deviation. 2. VLOOKUP The VLOOKUP function syntax
SARK 200 Mini PBX Sangoma Vega Gateways
 SARK 200 Mini PBX Sangoma Vega Gateways Quick start configuration guide for SARK and Sangoma Vega 50 BRI Gateway Before You Begin: The SARK PBX and Vega 50 appliance is connected to the network and all
SARK 200 Mini PBX Sangoma Vega Gateways Quick start configuration guide for SARK and Sangoma Vega 50 BRI Gateway Before You Begin: The SARK PBX and Vega 50 appliance is connected to the network and all
IP Access List Entry Sequence Numbering
 The feature allows you to apply sequence numbers to permit or deny statements as well as reorder, add, or remove such statements from a named IP access list. The IP Access List Entry Sequence Numbering
The feature allows you to apply sequence numbers to permit or deny statements as well as reorder, add, or remove such statements from a named IP access list. The IP Access List Entry Sequence Numbering
Hostname (DNS Resolvable) Network Objects
 Introduction The following article explains the configuration of hostname (DNS Resolvable) network objects. Note that the maximum amount of a single DNS resolvable hostname is limited to 24 IP addresses.
Introduction The following article explains the configuration of hostname (DNS Resolvable) network objects. Note that the maximum amount of a single DNS resolvable hostname is limited to 24 IP addresses.
IP Access List Entry Sequence Numbering
 The feature allows you to apply sequence numbers to permit or deny statements as well as reorder, add, or remove such statements from a named IP access list. The IP Access List Entry Sequence Numbering
The feature allows you to apply sequence numbers to permit or deny statements as well as reorder, add, or remove such statements from a named IP access list. The IP Access List Entry Sequence Numbering
Security Policy (EN) v1.3
 Security Policy (EN) v1.3 Author: Erik Klein Langenhorst Date: Sept 21, 2017 Classificatie: 2 Intended for stakeholders only Security Policy (EN) v1.5 Pagina 1 van 9 Version History Version Date Name Changes
Security Policy (EN) v1.3 Author: Erik Klein Langenhorst Date: Sept 21, 2017 Classificatie: 2 Intended for stakeholders only Security Policy (EN) v1.5 Pagina 1 van 9 Version History Version Date Name Changes
Application Notes for Configuring CenturyLink SIP Trunking with Avaya IP Office Issue 1.0
 Avaya Solution & Interoperability Test Lab Application Notes for Configuring CenturyLink SIP Trunking with Avaya IP Office 6.1 - Issue 1.0 Abstract These Application Notes describe the procedures for configuring
Avaya Solution & Interoperability Test Lab Application Notes for Configuring CenturyLink SIP Trunking with Avaya IP Office 6.1 - Issue 1.0 Abstract These Application Notes describe the procedures for configuring
1. Introduction to Microsoft Excel
 1. Introduction to Microsoft Excel A spreadsheet is an online version of an accountant's worksheet, which can automatically do most of the calculating for you. You can do budgets, analyze data, or generate
1. Introduction to Microsoft Excel A spreadsheet is an online version of an accountant's worksheet, which can automatically do most of the calculating for you. You can do budgets, analyze data, or generate
Identifiers. Identifiers are the words a programmer uses in a program Some identifiers are already defined. Some are made up by the programmer:
 C1 D6 Obj: cont. 1.3 and 1.4, to become familiar with identifiers and to understand how programming languages work HW: p.51 #1.8 1.9 (Short Answers) Chapter 1 Test in two class days!! Do Now: How is the
C1 D6 Obj: cont. 1.3 and 1.4, to become familiar with identifiers and to understand how programming languages work HW: p.51 #1.8 1.9 (Short Answers) Chapter 1 Test in two class days!! Do Now: How is the
Route Filter Configuration
 CHAPTER 30 Use the following topics to add, update, copy, or delete a route filter: Settings, page 30-1 Adding and Editing Route Filter Clauses, page 30-3 Removing Route Filter Clauses, page 30-4 Synchronizing
CHAPTER 30 Use the following topics to add, update, copy, or delete a route filter: Settings, page 30-1 Adding and Editing Route Filter Clauses, page 30-3 Removing Route Filter Clauses, page 30-4 Synchronizing
Hangzhou Synway Information Engineering Co., Ltd
 1 2 1. Abstract Elastix is an Open Source Software to establish Unified Communications. About this concept, Elastix goal is to incorporate all the communication alternatives, available at an enterprise
1 2 1. Abstract Elastix is an Open Source Software to establish Unified Communications. About this concept, Elastix goal is to incorporate all the communication alternatives, available at an enterprise
IP Access List Overview
 Access control lists (ACLs) perform packet filtering to control which packets move through a network and to where. The packet filtering provides security by helping to limit the network traffic, restrict
Access control lists (ACLs) perform packet filtering to control which packets move through a network and to where. The packet filtering provides security by helping to limit the network traffic, restrict
Pexip Infinity and Cisco VCS Deployment Guide
 Introduction Pexip Infinity and Cisco VCS Deployment Guide The Cisco TelePresence Video Communication Server (VCS) is a SIP/H.323 registrar and call control device. This guide describes how to integrate
Introduction Pexip Infinity and Cisco VCS Deployment Guide The Cisco TelePresence Video Communication Server (VCS) is a SIP/H.323 registrar and call control device. This guide describes how to integrate
Example Customer Scenarios
 Example Customer Scenarios Vodafone One Net Business Example Customer Scenarios How One Net Collaboration makes a difference Inbound and Outbound calls Inbound Calls in to a user from an operator or via
Example Customer Scenarios Vodafone One Net Business Example Customer Scenarios How One Net Collaboration makes a difference Inbound and Outbound calls Inbound Calls in to a user from an operator or via
Hunt pilot setup. About hunt pilot setup
 Hunt pilot setup This chapter provides information to add, configure, or delete a hunt pilot. For additional information about understanding route plans, wildcards and special characters in route patterns
Hunt pilot setup This chapter provides information to add, configure, or delete a hunt pilot. For additional information about understanding route plans, wildcards and special characters in route patterns
Chapter 2, Part I Introduction to C Programming
 Chapter 2, Part I Introduction to C Programming C How to Program, 8/e, GE 2016 Pearson Education, Ltd. All rights reserved. 1 2016 Pearson Education, Ltd. All rights reserved. 2 2016 Pearson Education,
Chapter 2, Part I Introduction to C Programming C How to Program, 8/e, GE 2016 Pearson Education, Ltd. All rights reserved. 1 2016 Pearson Education, Ltd. All rights reserved. 2 2016 Pearson Education,
Owner of the content within this article is Written by Marc Grote
 Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring and using the E-Mail protection feature in Microsoft Forefront Threat Management
Owner of the content within this article is www.isaserver.org Written by Marc Grote www.it-training-grote.de Configuring and using the E-Mail protection feature in Microsoft Forefront Threat Management
Application Notes for Configuring Cablevision Optimum Voice SIP Trunking with Avaya IP Office - Issue 1.1
 Avaya Solution & Interoperability Test Lab Application Notes for Configuring Cablevision Optimum Voice SIP Trunking with Avaya IP Office - Issue 1.1 Abstract These Application Notes describe the procedures
Avaya Solution & Interoperability Test Lab Application Notes for Configuring Cablevision Optimum Voice SIP Trunking with Avaya IP Office - Issue 1.1 Abstract These Application Notes describe the procedures
Hunt Pilot Configuration
 CHAPTER 36 Use the following topics to add, configure, or delete a hunt pilot: Settings, page 36-1 Related Topics, page 36-10 Settings In Cisco Unified Communications Manager Administration, use the Call
CHAPTER 36 Use the following topics to add, configure, or delete a hunt pilot: Settings, page 36-1 Related Topics, page 36-10 Settings In Cisco Unified Communications Manager Administration, use the Call
Cisco Unified Communications Manager Trunk Types
 Cisco Unified Communications Manager Trunk Types This chapter provides information about trunk types. In a distributed call-processing environment, Cisco Unified Communications Manager communicates with
Cisco Unified Communications Manager Trunk Types This chapter provides information about trunk types. In a distributed call-processing environment, Cisco Unified Communications Manager communicates with
Setting up the Grandstream Gateway for use with STAC VIP
 Setting up the Grandstream Gateway for use with STAC VIP Introduction The GXW4108 Gateway is a cost-effective way of converting the Comrex STAC VIP to use with POTS (or PSTN) telephone lines. The gateway
Setting up the Grandstream Gateway for use with STAC VIP Introduction The GXW4108 Gateway is a cost-effective way of converting the Comrex STAC VIP to use with POTS (or PSTN) telephone lines. The gateway
Cisco TelePresence ISDN GW MSE 8321
 Cisco TelePresence ISDN GW MSE 8321 Getting started 61-0020-05 Contents General information... 3 About the Cisco TelePresence ISDN GW MSE 8321... 3 Port and LED location... 3 LED behavior... 4 Installing
Cisco TelePresence ISDN GW MSE 8321 Getting started 61-0020-05 Contents General information... 3 About the Cisco TelePresence ISDN GW MSE 8321... 3 Port and LED location... 3 LED behavior... 4 Installing
OpenScape Business MS Skype for Business Interworking. Michael Trotz, Product
 OpenScape Business MS Skype for Business Interworking Michael Trotz, Product Manager@UNIFY Providing Telephony Connectivity from OSBiz to SfB Voice Interworking with existing Skype for Business environments
OpenScape Business MS Skype for Business Interworking Michael Trotz, Product Manager@UNIFY Providing Telephony Connectivity from OSBiz to SfB Voice Interworking with existing Skype for Business environments
CTI Server Overview. How CTI Server Works
 How CTI Server Works, page 1 Unified CCE Call Processing, page 2 CTI Server Configurations, page 4 CTI Server Message Set, page 7 How CTI Server Works The CTI Server provides an interface between Unified
How CTI Server Works, page 1 Unified CCE Call Processing, page 2 CTI Server Configurations, page 4 CTI Server Message Set, page 7 How CTI Server Works The CTI Server provides an interface between Unified
Application Notes for Configuring Windstream using Genband G9 SIP Trunking with Avaya IP Office Issue 1.0
 Avaya Solution & Interoperability Test Lab Application Notes for Configuring Windstream using Genband G9 SIP Trunking with Avaya IP Office 8.1 - Issue 1.0 Abstract These Application Notes describe the
Avaya Solution & Interoperability Test Lab Application Notes for Configuring Windstream using Genband G9 SIP Trunking with Avaya IP Office 8.1 - Issue 1.0 Abstract These Application Notes describe the
This chapter provides information about using Cisco Unified Communications Manager for working with and configuring Cisco gateways.
 This chapter provides information about using Cisco Unified Communications Manager for working with and configuring Cisco gateways. About gateway setup, page 1 Gateway reset, page 2 Gateway deletion, page
This chapter provides information about using Cisco Unified Communications Manager for working with and configuring Cisco gateways. About gateway setup, page 1 Gateway reset, page 2 Gateway deletion, page
Signed versions of the diurnal and semidiurnal clocks on this site use signed arithmetic notation, also known as reverse or balanced notation.
 SIGNED ARITHMETIC NOTATION for the Dozenal Clock Paul Rapoport Signed versions of the diurnal and semidiurnal clocks on this site use signed arithmetic notation, also known as reverse or balanced notation.
SIGNED ARITHMETIC NOTATION for the Dozenal Clock Paul Rapoport Signed versions of the diurnal and semidiurnal clocks on this site use signed arithmetic notation, also known as reverse or balanced notation.
CS 115 Data Types and Arithmetic; Testing. Taken from notes by Dr. Neil Moore
 CS 115 Data Types and Arithmetic; Testing Taken from notes by Dr. Neil Moore Statements A statement is the smallest unit of code that can be executed on its own. So far we ve seen simple statements: Assignment:
CS 115 Data Types and Arithmetic; Testing Taken from notes by Dr. Neil Moore Statements A statement is the smallest unit of code that can be executed on its own. So far we ve seen simple statements: Assignment:
Comparing Management Systems that Protect Against Spam, Viruses, Malware and Phishing Attacks
 Comparing Email Management Systems that Protect Against Spam, An Osterman Research White Paper Published December 2006 Osterman Research, Inc. P.O. Box 1058 Black Diamond, Washington 98010-1058 Phone:
Comparing Email Management Systems that Protect Against Spam, An Osterman Research White Paper Published December 2006 Osterman Research, Inc. P.O. Box 1058 Black Diamond, Washington 98010-1058 Phone:
Application Note for Open Text Fax Server (RightFax v9.4) and 3COM VCX platform
 Page 1 of 26 Application Note for Open Text Fax Server (RightFax v9.4) and 3COM VCX platform Issue: 1.0 Date: January 28, 2009 Authors: Abstract: Michael Hamlin (Open Text) and Ciaran O Shaughnessy (3Com)
Page 1 of 26 Application Note for Open Text Fax Server (RightFax v9.4) and 3COM VCX platform Issue: 1.0 Date: January 28, 2009 Authors: Abstract: Michael Hamlin (Open Text) and Ciaran O Shaughnessy (3Com)
South East Grid for Learning
 Instructions for Surrey schools on the SEGfL Video Conferencing Service South East Grid for Learning Version 1.1 Date: January 2007 SEGfL Video Conferencing Service Page 1 Registration of Endponts Introduction...3
Instructions for Surrey schools on the SEGfL Video Conferencing Service South East Grid for Learning Version 1.1 Date: January 2007 SEGfL Video Conferencing Service Page 1 Registration of Endponts Introduction...3
Figure 4-1. A Scenario of SIP outgoing calls in Vigor 3300V
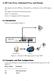 4. SIP Call, Proxy, Outbound Proxy and Domain This chapter shows how SIP Proxy, Outbound Proxy and Domain work in a SIP outgoing call. This chapter is divided into the following sections, Section 4.1:
4. SIP Call, Proxy, Outbound Proxy and Domain This chapter shows how SIP Proxy, Outbound Proxy and Domain work in a SIP outgoing call. This chapter is divided into the following sections, Section 4.1:
Call Display Restrictions
 Overview, on page 1 Configuration Task Flow, on page 1 Interactions, on page 11 Feature Restrictions, on page 12 Overview Cisco Unified Communications Manager provides flexible configuration options that
Overview, on page 1 Configuration Task Flow, on page 1 Interactions, on page 11 Feature Restrictions, on page 12 Overview Cisco Unified Communications Manager provides flexible configuration options that
Step 3 - How to Configure Basic System Settings
 Before configuring the IP address and network settings, complete Step 2 - How to Configure IP Address, network Settings, and Firewall. Verify the computer and the are connected to the same network, with
Before configuring the IP address and network settings, complete Step 2 - How to Configure IP Address, network Settings, and Firewall. Verify the computer and the are connected to the same network, with
Creating Your Buy Number
 Creating Your Buy Number When an advertising (i.e. Buy ) call comes in from a prospective home seller, it's critical that the call be answered live every time. Therefore, when your phone rings, it's important
Creating Your Buy Number When an advertising (i.e. Buy ) call comes in from a prospective home seller, it's critical that the call be answered live every time. Therefore, when your phone rings, it's important
GCC C++: Comment Text
 GCC C++: Comment Text Introduction Comment text is text included in source code that is ignored by the compiler and does not cause any machine-language object code to be generated. It is written into the
GCC C++: Comment Text Introduction Comment text is text included in source code that is ignored by the compiler and does not cause any machine-language object code to be generated. It is written into the
Application Notes for TelStrat Engage Record Version 3.3 with Avaya Business Communication Manger Release 6.0 VoIP Recording Issue 1.
 Avaya Solution & Interoperability Test Lab Application Notes for TelStrat Engage Record Version 3.3 with Avaya Business Communication Manger Release 6.0 VoIP Recording Issue 1.0 Abstract These Application
Avaya Solution & Interoperability Test Lab Application Notes for TelStrat Engage Record Version 3.3 with Avaya Business Communication Manger Release 6.0 VoIP Recording Issue 1.0 Abstract These Application
Multi-Site Support. Multi-Site Fundamentals
 This chapter contains general information about multi-site environments, as well as information on deploying a multi-site environment for your T-Server. This chapter is divided into the following sections:
This chapter contains general information about multi-site environments, as well as information on deploying a multi-site environment for your T-Server. This chapter is divided into the following sections:
The Integration of Lync Server/OCS 2007 and MyPBX
 The Integration of Lync Server/OCS 2007 and MyPBX 1. Introduction... 2 2. The Configuration of OCS... 3 2.1 The Configuration of OCS Global Properties and Voice Properties... 3 2.2 The Configuration of
The Integration of Lync Server/OCS 2007 and MyPBX 1. Introduction... 2 2. The Configuration of OCS... 3 2.1 The Configuration of OCS Global Properties and Voice Properties... 3 2.2 The Configuration of
ISDN Troubleshooting. All Mediatrix Units with ISDN cards. v
 All Mediatrix Units with ISDN cards v. 2.0.41.762 2018-03-29 Table of Contents Table of Contents 4 Protocols and Connection 5 Troubleshooting Tools 6 Troubleshooting 6 Capturing a Trace Using Wireshark
All Mediatrix Units with ISDN cards v. 2.0.41.762 2018-03-29 Table of Contents Table of Contents 4 Protocols and Connection 5 Troubleshooting Tools 6 Troubleshooting 6 Capturing a Trace Using Wireshark
6.25 x Type the given number into the calculator. 2. Click Mode, and select SCI. Then hit enter twice
 Name Date: Lesson 1-4: Scientific Notation Learning Goals: #1: How do we convert in and out of scientific notation? Scientific Notation Scientific Notation is a way of writing numbers that accommodates
Name Date: Lesson 1-4: Scientific Notation Learning Goals: #1: How do we convert in and out of scientific notation? Scientific Notation Scientific Notation is a way of writing numbers that accommodates
1 CS580W-01 Quiz 1 Solution
 1 CS580W-01 Quiz 1 Solution Date: Wed Sep 26 2018 Max Points: 15 Important Reminder As per the course Academic Honesty Statement, cheating of any kind will minimally result in receiving an F letter grade
1 CS580W-01 Quiz 1 Solution Date: Wed Sep 26 2018 Max Points: 15 Important Reminder As per the course Academic Honesty Statement, cheating of any kind will minimally result in receiving an F letter grade
Directory number setup
 Directory number setup This chapter provides information about working with and configuring directory numbers (DNs) in Cisco Unified Communications Manager Administration. For additional information, see
Directory number setup This chapter provides information about working with and configuring directory numbers (DNs) in Cisco Unified Communications Manager Administration. For additional information, see
Appia User Portal for SIP Trunks
 Appia User Portal for SIP Trunks The User Portal is available at https://userportal.appiaservices.com. Please contact Appia Support at 877-277-4297, option 3 or support@appiaservices.com if you need login
Appia User Portal for SIP Trunks The User Portal is available at https://userportal.appiaservices.com. Please contact Appia Support at 877-277-4297, option 3 or support@appiaservices.com if you need login
Mitel for Microsoft Dynamics CRM Client V5 Release Notes
 Mitel for Microsoft Dynamics CRM Client V5 Release Notes February 08, 2018. Mitel for Microsoft Dynamics CRM Client V5 Release Notes Description: This Application Note Consists of the dates and version
Mitel for Microsoft Dynamics CRM Client V5 Release Notes February 08, 2018. Mitel for Microsoft Dynamics CRM Client V5 Release Notes Description: This Application Note Consists of the dates and version
The IPsec protocols. Overview
 The IPsec protocols -- components and services -- modes of operation -- Security Associations -- Authenticated Header (AH) -- Encapsulated Security Payload () (c) Levente Buttyán (buttyan@crysys.hu) Overview
The IPsec protocols -- components and services -- modes of operation -- Security Associations -- Authenticated Header (AH) -- Encapsulated Security Payload () (c) Levente Buttyán (buttyan@crysys.hu) Overview
OpenScape Business MS Skype for Business Interworking. Michael Trotz, Product
 OpenScape Business MS Skype for Business Interworking Michael Trotz, Product Manager@UNIFY Providing Telephony Connectivity from OSBiz to SfB Voice Interworking with existing Skype for Business environments
OpenScape Business MS Skype for Business Interworking Michael Trotz, Product Manager@UNIFY Providing Telephony Connectivity from OSBiz to SfB Voice Interworking with existing Skype for Business environments
Alloc8 How to Guide: Adaptive Response
 Alloc8 How to Guide: Adaptive Response Adaptive Response Rules Adaptive Response allows administrators to specify rules based on data transfer which dynamically populate Network Objects. These Dynamic
Alloc8 How to Guide: Adaptive Response Adaptive Response Rules Adaptive Response allows administrators to specify rules based on data transfer which dynamically populate Network Objects. These Dynamic
TELEPHONE FEATURES GUIDE Updated August 2018
 TELEPHONE FEATURES GUIDE Updated August 2018 ourcontinuum.com/voice WELCOME. We value you as a customer and will continue to work to ensure you have a great experience. We are committed to offering a quality
TELEPHONE FEATURES GUIDE Updated August 2018 ourcontinuum.com/voice WELCOME. We value you as a customer and will continue to work to ensure you have a great experience. We are committed to offering a quality
Spectrum Enterprise SIP Trunking Service AsteriskNow V12 with Certified Asterisk R IP PBX Configuration Guide
 Spectrum Enterprise SIP Trunking Service AsteriskNow V12 with Certified Asterisk R11.16.0 IP PBX Configuration Guide About Spectrum Enterprise: Spectrum Enterprise is a division of Charter Communications
Spectrum Enterprise SIP Trunking Service AsteriskNow V12 with Certified Asterisk R11.16.0 IP PBX Configuration Guide About Spectrum Enterprise: Spectrum Enterprise is a division of Charter Communications
Translation pattern setup
 This chapter provides information to add, update, copy, or delete a translation pattern. For additional information, see topics related to understanding route plans in the Cisco Unified Communications
This chapter provides information to add, update, copy, or delete a translation pattern. For additional information, see topics related to understanding route plans in the Cisco Unified Communications
Fundamentals of Programming. Lecture 3: Introduction to C Programming
 Fundamentals of Programming Lecture 3: Introduction to C Programming Instructor: Fatemeh Zamani f_zamani@ce.sharif.edu Sharif University of Technology Computer Engineering Department Outline A Simple C
Fundamentals of Programming Lecture 3: Introduction to C Programming Instructor: Fatemeh Zamani f_zamani@ce.sharif.edu Sharif University of Technology Computer Engineering Department Outline A Simple C
Basic FXO Gateway Configuration
 Mediatrix units with FXO ports v. 2.0.41.762 2017-12-21 Table of Contents Table of Contents Configuring the Mediatrix Unit 3 Getting Started 3 Logging on to the Mediatrix Unit Web Interface 3 Configuring
Mediatrix units with FXO ports v. 2.0.41.762 2017-12-21 Table of Contents Table of Contents Configuring the Mediatrix Unit 3 Getting Started 3 Logging on to the Mediatrix Unit Web Interface 3 Configuring
Application Notes for Configuring Tidal Communications tnet Business VoIP with Avaya IP Office using SIP Registration - Issue 1.0
 Avaya Solution & Interoperability Test Lab Application Notes for Configuring Tidal Communications tnet Business VoIP with Avaya IP Office using SIP Registration - Issue 1.0 Abstract These Application Notes
Avaya Solution & Interoperability Test Lab Application Notes for Configuring Tidal Communications tnet Business VoIP with Avaya IP Office using SIP Registration - Issue 1.0 Abstract These Application Notes
Open Archives Forum - Technical Validation -
 Open Archives Forum - Technical Validation - Birgit Matthaei Humboldt University Berlin, Germany Computer and Media Service, Electronic Publishing Group birgit.matthaei@cms.hu-berlin.de Creating Information
Open Archives Forum - Technical Validation - Birgit Matthaei Humboldt University Berlin, Germany Computer and Media Service, Electronic Publishing Group birgit.matthaei@cms.hu-berlin.de Creating Information
Dial Peer Configuration on Voice Gateway Routers Configuration Guide
 Dial Peer Configuration on Voice Gateway Routers Configuration Guide Cisco IOS XE Release 3S Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Dial Peer Configuration on Voice Gateway Routers Configuration Guide Cisco IOS XE Release 3S Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Grandstream Networks, Inc. UCM6200 Basic Configuration Guide
 Grandstream Networks, Inc. Table of Contents OVERVIEW... 4 SETUP GUIDE SCENARIO... 4 QUICK INSTALLATION... 5 Connecting the UCM6200... 5 Access UCM6200 series Web Interface... 5 CREATE USER EXTENSION...
Grandstream Networks, Inc. Table of Contents OVERVIEW... 4 SETUP GUIDE SCENARIO... 4 QUICK INSTALLATION... 5 Connecting the UCM6200... 5 Access UCM6200 series Web Interface... 5 CREATE USER EXTENSION...
Directory Number Configuration
 CHAPTER 43 The following sections provide information about working with and configuring directory numbers (DNs) in Cisco Unified Communications Manager Administration: Settings, page 43-1 Synchronizing
CHAPTER 43 The following sections provide information about working with and configuring directory numbers (DNs) in Cisco Unified Communications Manager Administration: Settings, page 43-1 Synchronizing
To create a few test accounts during the evaluation period, use the Manually Add Users steps.
 Once you complete the Essentials for Office 365 Wizard, the Essentials page displays in Barracuda Cloud Control. Click Set up additional domains to go to the Barracuda Email Security Service Domains page,
Once you complete the Essentials for Office 365 Wizard, the Essentials page displays in Barracuda Cloud Control. Click Set up additional domains to go to the Barracuda Email Security Service Domains page,
