Certificate Profile: Extensions. 5/7/2002 2:46 PM Some sample certificates provided by Jason Novotny DOE PKI certificate provided by John Long
|
|
|
- Byron Walker
- 5 years ago
- Views:
Transcription
1 Certificate Profile: Extensions 5/7/2002 2:46 PM Some sample certificates provided by Jason Novotny DOE PKI certificate provided by John Long 1
2 Certificate Profile: Extensions... 1 DOE Science Grid and ESnet... 3 People Certificate... 3 Service and Host Certificate... 4 CA - pki CA - root... 7 Federal - DOE PKI... 8 End Entity Certificate... 8 Thawte Commercial PKI Web Server Certificate: Thawte Server CA: Thawte Fre PKI Fre Certificate: Thawte Fre Issuer Thawte root VeriSign Web Server Certificate: Web Cert. Signer Certificate Class 3 Root CA certificate: Personal Certificate: Persona CA Certificate: Class 1 Root Certificate: Globus Personal Globus CA NCSA Personal NCSA CA NPACI NPACI CA NASA AMES SSL Server NASA Ames CA CERN CERN CA
3 DOE Science Grid and ESnet People Certificate Version: v3 Serial Number: SHA1withRSA Issuer: CN=pki1,OU=DOE Science Grid,OU=Certificate Authorities,DC=es,DC=net Algorithm: RSA Public Key: Exponent: Public Key Modulus: (1024 bits) : Extensions: Identifier: Netscape Certificate Type Critical: no SSL Client SSL Server Secure Identifier: Key Usage: Critical: yes Digital Signature Non Repudiation Key Encipherment Data Encipherment Identifier: Authority Key Identifier Critical: no Key Identifier: 54:17:88:CA:03:C1:39:26:B8:55:A6:C4:99:F4:2B:02:AB:BE:00:E9 Identifier: Subject Alternative Name Critical: no RFC822Name: name@mail.dom.ain Signature: Algorithm: SHA1withRSA
4 Service and Host Certificate Version: v3 Serial Number: SHA1withRSA Issuer: CN=pki1,OU=DOE Science Grid,OU=Certificate Authorities,DC=es,DC=net Algorithm: RSA Public Key: Exponent: Public Key Modulus: (1024 bits) : Extensions: Identifier: Netscape Certificate Type Critical: no SSL Client SSL Server Identifier: Key Usage: Critical: yes Digital Signature Non Repudiation Key Encipherment Data Encipherment Identifier: Authority Key Identifier Critical: no 54:17:88:CA:03:C1:39:26:B8:55:A6:C4:99:F4:2B:02:AB:BE:00:E9 Identifier: Subject Alternative Name Critical: no RFC822Name: name@mail.dom.ain Signature: Algorithm: SHA1withRSA
5 CA - pki1 Issuer of service/people certificates Version: v3 Serial Number: SHA1withRSA Issuer: CN=Certificate Manager,OU=Certificate Authorities,O=DOE Science Grid : Not Before: Friday, December 21, :48:37 PM GMT-08:00 Not After: Saturday, January 10, :48:37 PM GMT-08:00 Subject: CN=pki1,OU=DOE Science Grid,OU=Certificate Authorities,DC=es,DC=net Algorithm: RSA Public Key: Exponent: Public Key Modulus: (2048 bits) : Extensions: Identifier: Key Usage: Critical: yes Key Usage: Digital Signature Key CertSign Crl Sign Identifier: Subject Key Identifier Critical: no Key Identifier: 54:17:88:CA:03:C1:39:26:B8:55:A6:C4:99:F4:2B:02:AB:BE:00:E9 Identifier: Authority Key Identifier Critical: no Key Identifier: 9B:CE:4F:F2:BC:BD:58:70:31:D5:F2:32:0E:7E:9E:BD:E2:51:14:E7 Identifier: Basic Constraints Critical: yes Is CA: yes Path Length Constraint: UNLIMITED 5
6 Identifier: CRL Distribution Points Critical: no Value: Distribution Point Name: Full Name: URL= CRL Reason=Unspecified, Key Compromise, CA Compromise, Superseded, Cessation of Operation(EC) CRL Issuer: Directory Address: CN=Certificate Manager OU=Certificate Authorities O=DOE Science Grid Identifier: Certificate Policies Critical: no Value: [1]Certificate Policy: PolicyIdentifier= [1,1]Policy Qualifier Info: Policy Qualifier Id=User Notice Qualifier: Notice Reference: Organization=ESnet (Energy Sciences Network) Notice Number=1 Notice Text=ESnet-DOE Science Grid Certificate Policy [1,2]Policy Qualifier Info: Policy Qualifier Id=CPS Qualifier: y%20and%20cps.pdf Signature: Algorithm: SHA1withRSA
7 CA - root Version: v3 Serial Number: MD5withRSA Issuer: CN=Certificate Manager,OU=Certificate Authorities,O=DOE Science Grid : Not Before: Wednesday, March 1, :00:00 AM GMT-08:00 Not After: Tuesday, January 26, :00:00 AM GMT-08:00 Subject: CN=Certificate Manager,OU=Certificate Authorities,O=DOE Science Grid Algorithm: RSA Public Key: Exponent: Public Key Modulus: (1024 bits) : Extensions: Identifier: Netscape Certificate Type Critical: no Certificate Usage: SSL CA Secure CA ObjectSigning CA Identifier: Basic Constraints Critical: yes Is CA: yes Path Length Constraint: UNLIMITED Identifier: Authority Key Identifier Critical: no Identifier: 9B:CE:4F:F2:BC:BD:58:70:31:D5:F2:32:0E:7E:9E:BD:E2:51:14:E7 Identifier: Subject Key Identifier Critical: no Key Identifier: 9B:CE:4F:F2:BC:BD:58:70:31:D5:F2:32:0E:7E:9E:BD:E2:51:14:E7 Signature: Algorithm: MD5withRSA
8 Federal - DOE PKI We have not been able to locate the signer certificate or any cross-signing CA certificates. We assume the end entity certificate is a representative example. End Entity Certificate Serial Number: (0xabcdef01) sha1withrsaencryption Issuer: C=US, O=u.s. government, OU=department of energy, OU=Someplace National Laboratories Not Before: Feb 4 22:39: GMT Not After : Feb 4 23:09: GMT Subject: C=US, O=U.S. Government, OU=Department of Energy, OU=Someplace National Laboratories, OU=worker bees, SN=JEDoe, CN=John E Doe Modulus (1024 bit): X509v3 Key Usage: Digital Signature X509v3 Private Key Usage Period: Not Before: Feb 4 22:39: GMT, Not After: Mar 13 03:09: GMT X509v3 Subject Alternative Name: jedoe@somelab.org X509v3 CRL Distribution Points: DirName: /C=US/O=u.s. government/ou=department of energy/ou=someplace National Laboratories/CN=CRLidentifier X509v3 Authority Key Identifier: keyid:e4:c4:1e:e3:e9:6a:15:5d:5e:5d:b4:36:5f:a0:28:a9:9d:27:4d:56 X509v3 Subject Key Identifier: 0C:72:96:24:65:E8:11:95:EC:32:D4:8F:27:3B:AE:F9:A6:E0:62:9F X509v3 Basic Constraints: CA:FALSE 8
9 : 0..V sha1withrsaencryption 9
10 Thawte Commercial PKI The root CA for this infrastructure has not been found yet (the intermediate is installed in commercial web browsers). Web Server Certificate: Serial Number: (0x8a629) md5withrsaencryption Issuer: C=ZA, ST=Western Cape, L=Cape Town, O=Thawte Consulting cc, OU=Certification Services Division, CN=Thawte Server Not Before: Dec 19 12:09: GMT Not After : Dec 22 15:48: GMT Subject: C=ZA, ST=Western Cape, L=Cape Town, O=Thawte Consulting (Pty) Ltd, CN= Modulus (1024 bit): X509v3 Extended Key Usage: TLS Web Server Authentication X509v3 Basic Constraints: critical CA:FALSE md5withrsaencryption 10
11 Thawte Server CA: Serial Number: (Negative)6d:0c:44:59:b6:54:b0:5a:ee:2c:c4:46:d6:1d:87:b0 md5withrsaencryption Issuer: CN=Root SGC Authority Not Before: Jul 16 20:00: GMT Not After : Jul 16 20:00: GMT Subject: C=ZA, ST=Western Cape, L=Cape Town, O=Thawte Consulting cc, OU=Certification Services Division, CN=Thawte Server CA/ =servercerts@thawte.com Modulus (1024 bit): : 0... X509v3 Extended Key Usage: Microsoft Server Gated Crypto, Netscape Server Gated Crypto : ')..*..wx5g u...root SGC Authority...{.t. md5withrsaencryption 11
12 Thawte Fre PKI Fre Certificate: Serial Number: (0x6e1ae) md5withrsaencryption Issuer: C=ZA, ST=Western Cape, L=Cape Town, O=Thawte, OU=Certificate Services, CN=Personal Fre RSA Not Before: Mar 2 01:46: GMT Not After : Mar 2 01:46: GMT Subject: S=sur, G=name, CN=name sur/ =name@mail.dom.ain Modulus (1024 bit): X509v3 Key Usage: critical Digital Signature, Non Repudiation, Key Encipherment, Data Encipherment, Key Agreement Netscape Cert Type: SSL Client, S/MIME X509v3 Subject Alternative Name: name@mail.dom.ain X509v3 Basic Constraints: critical CA:FALSE md5withrsaencryption 12
13 Thawte Fre Issuer Serial Number: 66:45:72:b7:cc:74:f5:cf:63:76:45:84:d0:2e:91:01 md5withrsaencryption Issuer: C=ZA, ST=Western Cape, L=Cape Town, O=Thawte Consulting, OU=Certification Services Division, CN=Thawte Personal Fre Not Before: Aug 30 00:00: GMT Not After : Aug 27 23:59: GMT Subject: C=ZA, ST=Western Cape, L=Cape Town, O=Thawte, OU=Certificate Services, CN=Personal Fre RSA Modulus (1024 bit): X509v3 Subject Alternative Name: DirName:/CN=PrivateLabel1-297 X509v3 Basic Constraints: critical CA:TRUE, pathlen:0 X509v3 Key Usage: Certificate Sign, CRL Sign md5withrsaencryption 13
14 Thawte root Serial Number: 0 (0x0) md5withrsaencryption Issuer: C=ZA, ST=Western Cape, L=Cape Town, O=Thawte Consulting, OU=Certification Services Division, CN=Thawte Personal Fre CA/ =personal-fre @thawte.com Not Before: Jan 1 00:00: GMT Not After : Dec 31 23:59: GMT Subject: C=ZA, ST=Western Cape, L=Cape Town, O=Thawte Consulting, OU=Certification Services Division, CN=Thawte Personal Fre CA/ =personal-fre @thawte.com Modulus (1024 bit): X509v3 Basic Constraints: critical CA:TRUE md5withrsaencryption 14
15 VeriSign Web Server Certificate: Serial Number: ff:00:ff:00:ff:00:00:00:ff:ff:00:ff:00:ff:00:ff md5withrsaencryption Issuer: O=VeriSign Trust Network, OU=VeriSign, Inc., OU=VeriSign International Server CA - Class 3, OU= Incorp.by Ref. LIABILITY LTD.(c)97 VeriSign Not Before: Nov 1 00:00: GMT Not After : Nov 1 23:59: GMT Subject: C=US, ST=Christmas Island, L=Pango Pango, O=Misner, Wheeler, and Thorne, OU=OOPS, CN=some.dom.ain Modulus (1024 bit): X509v3 Basic Constraints: CA:FALSE X509v3 Certificate Policies: Policy: CPS: User Notice: Organization: VeriSign, Inc. Number: 1 Explicit Text: VeriSign's CPS incorp. by reference liab. ltd. (c)97 VeriSign Netscape Cert Type: SSL Server X509v3 Extended Key Usage: Netscape Server Gated Crypto, TLS Web Server Authentication, TLS Web Client Authentication : 0&0$
16 X509v3 CRL Distribution Points: URI: md5withrsaencryption 16
17 Web Cert. Signer Certificate Serial Number: 23:6c:97:1e:2b:c6:0d:0b:f9:74:60:de:f1:08:c3:c3 md2withrsaencryption Issuer: C=US, O=VeriSign, Inc., OU=Class 3 Public Primary Certification Authority Not Before: Apr 17 00:00: GMT Not After : Jan 7 23:59: GMT Subject: O=VeriSign Trust Network, OU=VeriSign, Inc., OU=VeriSign International Server CA - Class 3, OU= Incorp.by Ref. LIABILITY LTD.(c)97 VeriSign Modulus (1024 bit): X509v3 Basic Constraints: CA:TRUE, pathlen:0 X509v3 Key Usage: Certificate Sign, CRL Sign Netscape Cert Type: SSL CA, S/MIME CA 17
18 X509v3 Extended Key Usage: , Netscape Server Gated Crypto X509v3 Certificate Policies: Policy: CPS: User Notice: Organization: VeriSign, Inc. Number: 1 Explicit Text: VeriSign's Certification Practice Statement, governs this certificate & is incorporated by reference herein. SOME WARRANTIES DISCLAIMED & LIABILITY LTD. (c)1997 VeriSign md2withrsaencryption Class 3 Root CA certificate: Version: 1 (0x0) Serial Number: 70:ba:e4:1d:10:d9:29:34:b6:38:ca:7b:03:cc:ba:bf md2withrsaencryption Issuer: C=US, O=VeriSign, Inc., OU=Class 3 Public Primary Certification Authority Not Before: Jan 29 00:00: GMT Not After : Aug 1 23:59: GMT Subject: C=US, O=VeriSign, Inc., OU=Class 3 Public Primary Certification Authority Modulus (1024 bit): md2withrsaencryption 18
19 Personal Certificate: Serial Number: 78:77:[...] md5withrsaencryption Issuer: O=VeriSign, Inc., OU=VeriSign Trust Network, OU= Incorp. By Ref.,LIAB.LTD(c)98, CN=VeriSign Class 1 CA Individual Subscriber-Persona Not Validated Not Before: Apr 3 00:00: GMT Not After : Apr 3 23:59: GMT Subject: O=VeriSign, Inc., OU=VeriSign Trust Network, OU= Incorp. by Ref.,LIAB.LTD(c)98, OU=Persona Not Validated, OU=Digital ID Class 1 - Microsoft Full Service, CN=Personal Name/ =myaddr@dom.ain Modulus (1024 bit): X509v3 Basic Constraints: CA:FALSE X509v3 Certificate Policies: Policy: CPS: User Notice: Organization: VeriSign, Inc. Number: 1 Explicit Text: VeriSign's CPS incorp. by reference liab. ltd. (c)97 VeriSign Netscape Cert Type: SSL Client X509v3 CRL Distribution Points: URI: md5withrsaencryption 19
20 Persona CA Certificate: Serial Number: 0b:da:0b:17:c1:3f:89:8e:ab:09:74:7a:b4:ce:2e:33 md2withrsaencryption Issuer: C=US, O=VeriSign, Inc., OU=Class 1 Public Primary Certification Authority Not Before: May 12 00:00: GMT Not After : May 12 23:59: GMT Subject: O=VeriSign, Inc., OU=VeriSign Trust Network, OU= Incorp. By Ref.,LIAB.LTD(c)98, CN=VeriSign Class 1 CA Individual Subscriber-Persona Not Validated Modulus (1024 bit): X509v3 Basic Constraints: CA:TRUE, pathlen:0 X509v3 Certificate Policies: Policy: CPS: X509v3 CRL Distribution Points: URI: X509v3 Key Usage: Certificate Sign, CRL Sign Netscape Cert Type: SSL CA, S/MIME CA md2withrsaencryption 20
21 Class 1 Root Certificate: Version: 1 (0x0) Serial Number: 32:50:33:cf:50:d1:56:f3:5c:81:ad:65:5c:4f:c8:25 md2withrsaencryption Issuer: C=US, O=VeriSign, Inc., OU=Class 1 Public Primary Certification Authority Not Before: Jan 29 00:00: GMT Not After : Jan 7 23:59: GMT Subject: C=US, O=VeriSign, Inc., OU=Class 1 Public Primary Certification Authority Modulus (1024 bit): md2withrsaencryption 21
22 Globus Personal Serial Number: 2685 (0xa7d) md5withrsaencryption Issuer: C=US, O=Globus, CN=Globus Certification Authority Not Before: Aug 31 19:37: GMT Not After : Aug 31 19:37: GMT Subject: C=US, O=Globus, O=The University of Flatlands, OU=Toyland, CN=My Name Modulus (1024 bit): Netscape Cert Type: SSL Client, SL Server md5withrsaencryption Globus CA Serial Number: 0 (0x0) md5withrsaencryption Issuer: C=US, O=Globus, CN=Globus Certification Authority Not Before: Jan 23 19:20: GMT Not After : Jan 23 19:20: GMT Subject: C=US, O=Globus, CN=Globus Certification Authority 22
23 X509v3 Basic Constraints: CA:TRUE Netscape Cert Type: SSL CA, S/MIME CA, Object Signing CA md5withrsaencryption 23
24 NCSA Note: These may not be part of the same chain Personal Serial Number: 321 md5withrsaencryption Issuer: C=US, O=National Computational Science Alliance, OU=Certification Authority, CN=Certificate Manager Not Before: Jan 13 17:28: GMT Not After : Jan 12 17:28: GMT Subject: C=US, O=National Computational Science Alliance, CN=My Name Modulus (1024 bit): Netscape Cert Type: SSL Client, SSL Server X509v3 Key Usage: critical Digital Signature, Non Repudiation, Key Encipherment, Data Encipherment X509v3 Authority Key Identifier: keyid:64:d3:df:79:82:37:7d:ff:21:7d:d1:94:38:74:ae:f8:2a:2d:12:48 md5withrsaencryption 24
25 NCSA CA Serial Number: 1 (0x1) md5withrsaencryption Issuer: C=US, O=National Computational Science Alliance, OU=Certification Authority Not Before: Mar 8 06:00: GMT Not After : Mar 22 06:00: GMT Subject: C=US, O=National Computational Science Alliance, OU=Certification Authority RSA Public Key: (2048 bit) Modulus (2048 bit): X509v3 Basic Constraints: critical CA:TRUE X509v3 Authority Key Identifier: keyid:9f:2d:dc:82:f0:cc:81:b2:fe:9d:ac:8e:23:47:1b:b6:d5:be:b9:e2 X509v3 Subject Key Identifier: 9F:2D:DC:82:F0:CC:81:B2:FE:9D:AC:8E:23:47:1B:B6:D5:BE:B9:E2 md5withrsaencryption 25
26 NPACI NPACI CA Serial Number: 1 (0x1) md5withrsaencryption Issuer: C=US, O=NPACI, OU=SDSC, CN=Certificate Manager Not Before: Sep 14 07:00: GMT Not After : Sep 14 07:00: GMT Subject: C=US, O=NPACI, OU=SDSC, CN=Certificate Manager RSA Public Key: (2048 bit) Modulus (2048 bit): Netscape Cert Type: SSL CA, S/MIME CA, Object Signing CA X509v3 Basic Constraints: critical CA:TRUE X509v3 Authority Key Identifier: keyid:88:36:fe:bb:18:89:a2:57:47:9d:dc:3c:d0:f0:83:e5:7a:ea:5a:3f X509v3 Subject Key Identifier: 88:36:FE:BB:18:89:A2:57:47:9D:DC:3C:D0:F0:83:E5:7A:EA:5A:3F md5withrsaencryption 26
27 NASA AMES SSL Server Serial Number: 2 (0x2) sha1withrsaencryption Issuer: O=Grid, O=National Aeronautics and Space Administration, OU=Ames Research Center, CN=Certificate Manager Not Before: Jan 30 08:00: GMT Not After : Jan 30 08:00: GMT Subject: O=Grid, O=National Aeronautics and Space Administration, OU=Ames Research Center, CN=fqdn.nasa.gov RSA Public Key: (2048 bit) Modulus (2048 bit): Netscape Cert Type: SSL Client, SSL Server X509v3 Authority Key Identifier: keyid:e2:20:5a:29:cc:06:3e:02:da:6e:a1:2e:fe:ed:43:e3:1c:16:39:44 X509v3 Key Usage: critical Digital Signature, Key Encipherment sha1withrsaencryption 27
28 NASA Ames CA Serial Number: 0 (0x0) sha1withrsaencryption Issuer: O=Grid, O=National Aeronautics and Space Administration, OU=Ames Research Center, CN=Certificate Manager Not Before: Jan 30 08:00: GMT Not After : Jan 30 08:00: GMT Subject: O=Grid, O=National Aeronautics and Space Administration, OU=Ames Research Center, CN=Certificate Manager RSA Public Key: (2048 bit) Modulus (2048 bit): Netscape Cert Type: SSL CA, S/MIME CA, Object Signing CA X509v3 Basic Constraints: critical CA:TRUE X509v3 Authority Key Identifier: keyid: E2:20:5A:29:CC:06:3E:02:DA:6E:A1:2E:FE:ED:43:E3:1C:16:39:44 X509v3 Key Usage: critical Digital Signature, Certificate Sign, CRL Sign X509v3 Subject Key Identifier: E2:20:5A:29:CC:06:3E:02:DA:6E:A1:2E:FE:ED:43:E3:1C:16:39:44 sha1withrsaencryption 28
29 CERN CERN CA Data Serial Number: 0 (0x0) md5withrsaencryption Issuer: C=CH, O=CERN, CN=CERN CA Not Before: Oct 1 10:49: GMT Not After : Oct 1 10:49: GMT Subject: C=CH, O=CERN, CN=CERN CA Modulus (1024 bit): 29
30 X509v3 Basic Constraints: critical CA:TRUE Netscape CA Revocation Url: Netscape Comment: For DataGrid use only Netscape Cert Type: SSL CA, S/MIME CA, Object Signing CA X509v3 CRL Distribution Points: URI: X509v3 Subject Alternative Name: X509v3 Subject Key Identifier: 41:93:80:5B:99:92:A1:DA:40:7D:53:CA:F5:E9:64:2D:C1:A1:85:6D Netscape CA Policy Url: md5withrsaencryption 30
31 31
Certificate Updates for Polycom Trio Solution with UC Software 5.8.0AA
 TECHNICAL UPDATE January 2019 3725-24444-005A with UC Software Polycom, Inc. 1 Copyright 2019, Polycom, Inc. All rights reserved. No part of this document may be reproduced, translated into another language
TECHNICAL UPDATE January 2019 3725-24444-005A with UC Software Polycom, Inc. 1 Copyright 2019, Polycom, Inc. All rights reserved. No part of this document may be reproduced, translated into another language
Certificate Updates for Polycom UC Software 4.0.9
 TECHNICAL UPDATE Software 4.0.9 June 2015 3725-49116-003A Certificate Updates for Polycom UC Software 4.0.9 Polycom, Inc. 1 Copyright 2015, Polycom, Inc. All rights reserved. No part of this document may
TECHNICAL UPDATE Software 4.0.9 June 2015 3725-49116-003A Certificate Updates for Polycom UC Software 4.0.9 Polycom, Inc. 1 Copyright 2015, Polycom, Inc. All rights reserved. No part of this document may
X.509 and SSL. A look into the complex world of X.509 and SSL USC Linux Users Group 4/26/07
 X.509 and SSL A look into the complex world of X.509 and SSL http://www.phildev.net/ssl/ USC Linux Users Group 4/26/07 Phil Dibowitz http://www.phildev.net/ The Outline Introduction of concepts X.509 SSL
X.509 and SSL A look into the complex world of X.509 and SSL http://www.phildev.net/ssl/ USC Linux Users Group 4/26/07 Phil Dibowitz http://www.phildev.net/ The Outline Introduction of concepts X.509 SSL
Introduction to Cryptography Lecture 10
 Introduction to Cryptography Lecture 10 Digital signatures, Public Key Infrastructure (PKI) Benny Pinkas January 1, 2012 page 1 Non Repudiation Prevent signer from denying that it signed the message I.e.,
Introduction to Cryptography Lecture 10 Digital signatures, Public Key Infrastructure (PKI) Benny Pinkas January 1, 2012 page 1 Non Repudiation Prevent signer from denying that it signed the message I.e.,
Kerberized Certificate Issuance Protocol (KX509)
 Kerberized Certificate Issuance Protocol (KX509) Jet Propulsion Laboratory Copyright 2010 California Institute of Technology. Government sponsorship acknowledged. Overview and Purpose KX509 is a wire protocol
Kerberized Certificate Issuance Protocol (KX509) Jet Propulsion Laboratory Copyright 2010 California Institute of Technology. Government sponsorship acknowledged. Overview and Purpose KX509 is a wire protocol
What is a Digital Certificate? Basic Problem. Digital Certificates, Certification Authorities, and Public Key Infrastructure. Sections
 Digital Certificates, Certification Authorities, and Public Key Infrastructure Sections 14.3-14.5 Basic Problem What does a public-key signature verification tell you? Verification parameters include public
Digital Certificates, Certification Authorities, and Public Key Infrastructure Sections 14.3-14.5 Basic Problem What does a public-key signature verification tell you? Verification parameters include public
Digital Certificates, Certification Authorities, and Public Key Infrastructure. Sections
 Digital Certificates, Certification Authorities, and Public Key Infrastructure Sections 14.3-14.5 Basic Problem What does a public-key signature verification tell you? Verification parameters include public
Digital Certificates, Certification Authorities, and Public Key Infrastructure Sections 14.3-14.5 Basic Problem What does a public-key signature verification tell you? Verification parameters include public
Innovative uses as result of DNSSEC
 Innovative uses as result of DNSSEC AKA: Some happenings in the DANE* WG in the IETF. * DNS-based Authentication of Named Entities Some background... When you connect to https://www.example.com you use
Innovative uses as result of DNSSEC AKA: Some happenings in the DANE* WG in the IETF. * DNS-based Authentication of Named Entities Some background... When you connect to https://www.example.com you use
ovirt - PKI Alon Bar-Lev Red Hat
 ovirt - PKI Alon Bar-Lev Red Hat 2012-10-17 Ovirt PKI Back-end purposes Application Server TLS/SSL (Server identification) VDSM authentication (Client authentication) SSH authentication (PK) (Client authentication)
ovirt - PKI Alon Bar-Lev Red Hat 2012-10-17 Ovirt PKI Back-end purposes Application Server TLS/SSL (Server identification) VDSM authentication (Client authentication) SSH authentication (PK) (Client authentication)
Grid Computing Fall 2005 Lecture 16: Grid Security. Gabrielle Allen
 Grid Computing 7700 Fall 2005 Lecture 16: Grid Security Gabrielle Allen allen@bit.csc.lsu.edu http://www.cct.lsu.edu/~gallen Required Reading Chapter 16 of The Grid (version 1), freely available for download
Grid Computing 7700 Fall 2005 Lecture 16: Grid Security Gabrielle Allen allen@bit.csc.lsu.edu http://www.cct.lsu.edu/~gallen Required Reading Chapter 16 of The Grid (version 1), freely available for download
ECC Certificate Addendum to the Comodo EV Certification Practice Statement v.1.03
 ECC Certificate Addendum to the Comodo EV Certification Practice Statement v.1.03 Comodo CA, Ltd. ECC Certificate Addendum to Comodo EV CPS v. 1.03 6 March 2008 3rd Floor, Office Village, Exchange Quay,
ECC Certificate Addendum to the Comodo EV Certification Practice Statement v.1.03 Comodo CA, Ltd. ECC Certificate Addendum to Comodo EV CPS v. 1.03 6 March 2008 3rd Floor, Office Village, Exchange Quay,
August 2007 Intel Pro SSL Addendum to the Comodo Certification Practice Statement v.3.0
 August 2007 Intel Pro SSL Addendum to the Comodo Certification Practice Statement v.3.0 Comodo CA, Ltd. August 2007 Intel Pro SSL Addendum to Version 3.0 Amendments 17 August 2007 3rd Floor, Office Village,
August 2007 Intel Pro SSL Addendum to the Comodo Certification Practice Statement v.3.0 Comodo CA, Ltd. August 2007 Intel Pro SSL Addendum to Version 3.0 Amendments 17 August 2007 3rd Floor, Office Village,
Using Cryptography CMSC 414. October 16, 2017
 Using Cryptography CMSC 414 October 16, 2017 Digital Certificates Recall: K pub = (n, e) This is an RSA public key How do we know who this is for? Need to bind identity to a public key We can do this using
Using Cryptography CMSC 414 October 16, 2017 Digital Certificates Recall: K pub = (n, e) This is an RSA public key How do we know who this is for? Need to bind identity to a public key We can do this using
CERTIFICATE POLICY CIGNA PKI Certificates
 CERTIFICATE POLICY CIGNA PKI Certificates Version: 1.1 Effective Date: August 7, 2001 a Copyright 2001 CIGNA 1. Introduction...3 1.1 Important Note for Relying Parties... 3 1.2 Policy Identification...
CERTIFICATE POLICY CIGNA PKI Certificates Version: 1.1 Effective Date: August 7, 2001 a Copyright 2001 CIGNA 1. Introduction...3 1.1 Important Note for Relying Parties... 3 1.2 Policy Identification...
SSL Certificates Certificate Policy (CP)
 SSL Certificates Last Revision Date: February 26, 2015 Version 1.0 Revisions Version Date Description of changes Author s Name Draft 17 Jan 2011 Initial Release (Draft) Ivo Vitorino 1.0 26 Feb 2015 Full
SSL Certificates Last Revision Date: February 26, 2015 Version 1.0 Revisions Version Date Description of changes Author s Name Draft 17 Jan 2011 Initial Release (Draft) Ivo Vitorino 1.0 26 Feb 2015 Full
Progressively Securing RIOT-OS!
 + Progressively Securing RIOT-OS! USABILITY AND NECESSITY OF SSL / TLS Slide 1 / 33 We re going to talk about: 1. Why is security important? 2. What is SSL? 3. Where is SSL being used? 4. Features: What
+ Progressively Securing RIOT-OS! USABILITY AND NECESSITY OF SSL / TLS Slide 1 / 33 We re going to talk about: 1. Why is security important? 2. What is SSL? 3. Where is SSL being used? 4. Features: What
Digital Certificates Demystified
 Digital Certificates Demystified Ross Cooper, CISSP IBM Corporation RACF/PKI Development Poughkeepsie, NY Email: rdc@us.ibm.com August 9 th, 2012 Session 11622 Agenda Cryptography What are Digital Certificates
Digital Certificates Demystified Ross Cooper, CISSP IBM Corporation RACF/PKI Development Poughkeepsie, NY Email: rdc@us.ibm.com August 9 th, 2012 Session 11622 Agenda Cryptography What are Digital Certificates
Belgian eid Card Technicalities
 Belgian eid Card Technicalities Danny De Cock Danny.DeCock@esat.kuleuven.be Katholieke Universiteit Leuven/Dept. Elektrotechniek (ESAT) Computer Security and Industrial Cryptography (COSIC) Kasteelpark
Belgian eid Card Technicalities Danny De Cock Danny.DeCock@esat.kuleuven.be Katholieke Universiteit Leuven/Dept. Elektrotechniek (ESAT) Computer Security and Industrial Cryptography (COSIC) Kasteelpark
Issues in Assessing Commercial Certification Service Trust
 The Open Group Security Program Group Building Trust on the Net ---- San Diego -- April 30, 1998 Issues in Assessing Commercial Certification Service Trust Michael S. Baum, J.D., M.B.A. VP, Practices &
The Open Group Security Program Group Building Trust on the Net ---- San Diego -- April 30, 1998 Issues in Assessing Commercial Certification Service Trust Michael S. Baum, J.D., M.B.A. VP, Practices &
Cryptography SSL/TLS. Network Security Workshop. 3-5 October 2017 Port Moresby, Papua New Guinea
 Cryptography SSL/TLS Network Security Workshop 3-5 October 2017 Port Moresby, Papua New Guinea 1 History Secure Sockets Layer was developed by Netscape in 1994 as a protocol which permitted persistent
Cryptography SSL/TLS Network Security Workshop 3-5 October 2017 Port Moresby, Papua New Guinea 1 History Secure Sockets Layer was developed by Netscape in 1994 as a protocol which permitted persistent
Grid Computing. Public Key Infrastructures (PKIs) Why certificates? Grid Computing Fall 2006 Paul A. Farrell 10/11/2006
 Grid Computing Security Public Key Infrastructure, X.509 and Certificate Authorities (CA) Fall 2006 The Grid: Core Technologies Maozhen Li, Mark Baker John Wiley & Sons; 2005, ISBN 0-470-09417-6 Material
Grid Computing Security Public Key Infrastructure, X.509 and Certificate Authorities (CA) Fall 2006 The Grid: Core Technologies Maozhen Li, Mark Baker John Wiley & Sons; 2005, ISBN 0-470-09417-6 Material
thawte Certification Practice Statement Version 3.4
 thawte Certification Practice Statement Version 3.4 Effective Date: July, 2007 thawte Certification Practice Statement 2006 thawte, Inc. All rights reserved. Printed in the United States of America. Revision
thawte Certification Practice Statement Version 3.4 Effective Date: July, 2007 thawte Certification Practice Statement 2006 thawte, Inc. All rights reserved. Printed in the United States of America. Revision
CSE 565 Computer Security Fall 2018
 CSE 565 Computer Security Fall 2018 Lecture 11: Public Key Infrastructure Department of Computer Science and Engineering University at Buffalo 1 Lecture Outline Public key infrastructure Certificates Trust
CSE 565 Computer Security Fall 2018 Lecture 11: Public Key Infrastructure Department of Computer Science and Engineering University at Buffalo 1 Lecture Outline Public key infrastructure Certificates Trust
X.509. CPSC 457/557 10/17/13 Jeffrey Zhu
 X.509 CPSC 457/557 10/17/13 Jeffrey Zhu 2 3 X.509 Outline X.509 Overview Certificate Lifecycle Alternative Certification Models 4 What is X.509? The most commonly used Public Key Infrastructure (PKI) on
X.509 CPSC 457/557 10/17/13 Jeffrey Zhu 2 3 X.509 Outline X.509 Overview Certificate Lifecycle Alternative Certification Models 4 What is X.509? The most commonly used Public Key Infrastructure (PKI) on
Lecture 16 Public Key Certification and Revocation
 Lecture 16 Public Key Certification and Revocation 1 CertificationTree / Hierarchy Logical tree of CA-s root PK root [PK CA1 CA1 ]SK root CA3 [PK CA3 ]SK root [PK CA2 CA2 ]SK CA1 CA4 [PK CA4 ]SK CA3 2
Lecture 16 Public Key Certification and Revocation 1 CertificationTree / Hierarchy Logical tree of CA-s root PK root [PK CA1 CA1 ]SK root CA3 [PK CA3 ]SK root [PK CA2 CA2 ]SK CA1 CA4 [PK CA4 ]SK CA3 2
Department of Defense Public Key Infrastructure
 Department of Defense Public Key Infrastructure DoD Approved External PKIs Master Document Version 4.6.1 22 August 2014 Prepared for: DoD PKI Program Management Office (PMO) Prepared by: Booz Allen Hamilton
Department of Defense Public Key Infrastructure DoD Approved External PKIs Master Document Version 4.6.1 22 August 2014 Prepared for: DoD PKI Program Management Office (PMO) Prepared by: Booz Allen Hamilton
Bugzilla ID: Bugzilla Summary:
 Bugzilla ID: Bugzilla Summary: CAs wishing to have their certificates included in Mozilla products must 1) Comply with the requirements of the Mozilla CA certificate policy (http://www.mozilla.org/projects/security/certs/policy/)
Bugzilla ID: Bugzilla Summary: CAs wishing to have their certificates included in Mozilla products must 1) Comply with the requirements of the Mozilla CA certificate policy (http://www.mozilla.org/projects/security/certs/policy/)
Department of Defense Public Key Infrastructure
 Department of Defense Public Key Infrastructure DoD Approved External PKIs Master Document Version 5.6 January 26, 2016 Prepared for: DoD PKI Program Management Office 9800 Savage Road Suite 6718 Fort
Department of Defense Public Key Infrastructure DoD Approved External PKIs Master Document Version 5.6 January 26, 2016 Prepared for: DoD PKI Program Management Office 9800 Savage Road Suite 6718 Fort
Data Security and Privacy. Topic 14: Authentication and Key Establishment
 Data Security and Privacy Topic 14: Authentication and Key Establishment 1 Announcements Mid-term Exam Tuesday March 6, during class 2 Need for Key Establishment Encrypt K (M) C = Encrypt K (M) M = Decrypt
Data Security and Privacy Topic 14: Authentication and Key Establishment 1 Announcements Mid-term Exam Tuesday March 6, during class 2 Need for Key Establishment Encrypt K (M) C = Encrypt K (M) M = Decrypt
Grid Security Infrastructure
 Grid Computing Competence Center Grid Security Infrastructure Riccardo Murri Grid Computing Competence Center, Organisch-Chemisches Institut, University of Zurich Oct. 12, 2011 Facets of security Authentication
Grid Computing Competence Center Grid Security Infrastructure Riccardo Murri Grid Computing Competence Center, Organisch-Chemisches Institut, University of Zurich Oct. 12, 2011 Facets of security Authentication
Certificates, Certification Authorities and Public-Key Infrastructures
 (Digital) Certificates Certificates, Certification Authorities and Public-Key Infrastructures We need to be sure that the public key used to encrypt a message indeed belongs to the destination of the message
(Digital) Certificates Certificates, Certification Authorities and Public-Key Infrastructures We need to be sure that the public key used to encrypt a message indeed belongs to the destination of the message
PAA PKI Mutual Recognition Framework. Copyright PAA, All Rights Reserved 1
 PAA PKI Mutual Recognition Framework Copyright PAA, 2009. All Rights Reserved 1 Agenda Overview of the Framework Components of the Framework How It Works Other Considerations Questions and Answers Copyright
PAA PKI Mutual Recognition Framework Copyright PAA, 2009. All Rights Reserved 1 Agenda Overview of the Framework Components of the Framework How It Works Other Considerations Questions and Answers Copyright
Information Security CS 526
 Information Security CS 526 Topic 14: Key Distribution & Agreement, Secure Communication Topic 14: Secure Communication 1 Readings for This Lecture On Wikipedia Needham-Schroeder protocol (only the symmetric
Information Security CS 526 Topic 14: Key Distribution & Agreement, Secure Communication Topic 14: Secure Communication 1 Readings for This Lecture On Wikipedia Needham-Schroeder protocol (only the symmetric
Public-key Infrastructure Options and choices
 Public-key Infrastructure Options and choices Tim Moses Director, Advanced Security Technology April 98 1997 Entrust Technologies Overview General-purpose and Dedicated PKIs Trust models Two-key architecture
Public-key Infrastructure Options and choices Tim Moses Director, Advanced Security Technology April 98 1997 Entrust Technologies Overview General-purpose and Dedicated PKIs Trust models Two-key architecture
TIPS AND TRICKS. Johan Olivier SECURITY
 TIPS AND TRICKS Johan Olivier SECURITY Desktop JRE versions - Back office application Integrator 3 (FMW Forms 11GR2) JRE 1.6 and 1.7 Upgrade to JRE 1.8 The server must be on Java patch level 1.7 Integrator
TIPS AND TRICKS Johan Olivier SECURITY Desktop JRE versions - Back office application Integrator 3 (FMW Forms 11GR2) JRE 1.6 and 1.7 Upgrade to JRE 1.8 The server must be on Java patch level 1.7 Integrator
Server-based Certificate Validation Protocol
 Server-based Certificate Validation Protocol Digital Certificate and PKI a public-key certificate is a digital certificate that binds a system entity's identity to a public key value, and possibly to additional
Server-based Certificate Validation Protocol Digital Certificate and PKI a public-key certificate is a digital certificate that binds a system entity's identity to a public key value, and possibly to additional
CertDigital Certification Services Policy
 CertDigital Certification Services Policy Page: 2 ISSUED BY : DEPARTAMENT NAME DATE ELECTRONIC SERVICES COMPARTMENT COMPARTMENT CHIEF 19.03.2011 APPROVED BY : DEPARTMENT NAME DATE MANAGEMENT OF POLICIES
CertDigital Certification Services Policy Page: 2 ISSUED BY : DEPARTAMENT NAME DATE ELECTRONIC SERVICES COMPARTMENT COMPARTMENT CHIEF 19.03.2011 APPROVED BY : DEPARTMENT NAME DATE MANAGEMENT OF POLICIES
Security Protocols and Infrastructures. Winter Term 2015/2016
 Security Protocols and Infrastructures Winter Term 2015/2016 Nicolas Buchmann (Harald Baier) Chapter 5: Standards for Security Infrastructures Contents Introduction and naming scheme X.509 and its core
Security Protocols and Infrastructures Winter Term 2015/2016 Nicolas Buchmann (Harald Baier) Chapter 5: Standards for Security Infrastructures Contents Introduction and naming scheme X.509 and its core
X.509 CERTIFICATE X.509 CERTIFICATE PUBLIC-KEY CERTIFICATES THE CERTIFICATE TRIANGLE CERTIFICATE TRUST. INFS 766 Internet Security Protocols
 INFS 766 Internet Security Protocols X.509 CERTIFICATE Lecture 6 Digital Certificates VERSION SERIAL NUMBER SIGNATURE ALGORITHM ISSUER VALIDITY Prof. Ravi SUBJECT SUBJECT PUBLIC KEY INFO SIGNATURE 4 PUBLIC-KEY
INFS 766 Internet Security Protocols X.509 CERTIFICATE Lecture 6 Digital Certificates VERSION SERIAL NUMBER SIGNATURE ALGORITHM ISSUER VALIDITY Prof. Ravi SUBJECT SUBJECT PUBLIC KEY INFO SIGNATURE 4 PUBLIC-KEY
Lecture 14. Public Key Certification and Revocation
 Lecture 14 Public Key Certification and Revocation 1 CertificationTree / Hierarchy Logical tree of CA-s root PK root CA1 [PKCA1]SKroot CA3 [PK CA3 ]SK root [PK CA2 CA2 ]SK CA1 CA4 [PK CA4]SK CA3 2 Hierarchical
Lecture 14 Public Key Certification and Revocation 1 CertificationTree / Hierarchy Logical tree of CA-s root PK root CA1 [PKCA1]SKroot CA3 [PK CA3 ]SK root [PK CA2 CA2 ]SK CA1 CA4 [PK CA4]SK CA3 2 Hierarchical
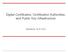
Lecture 13. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7.
![Lecture 13. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7. Lecture 13. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7.](/thumbs/84/91191448.jpg) Lecture 13 Public Key Distribution (certification) 1 PK-based Needham-Schroeder TTP 1. A, B 4. B, A 2. {PKb, B}SKT B}SKs 5. {PK a, A} SKT SKs A 3. [N a, A] PKb 6. [N a, N b ] PKa B 7. [N b ] PKb Here,
Lecture 13 Public Key Distribution (certification) 1 PK-based Needham-Schroeder TTP 1. A, B 4. B, A 2. {PKb, B}SKT B}SKs 5. {PK a, A} SKT SKs A 3. [N a, A] PKb 6. [N a, N b ] PKa B 7. [N b ] PKb Here,
PUBLIC-KEY CERTIFICATES
 INFS 766 Internet Security Protocols Lecture 6 Digital Certificates Prof. Ravi Sandhu PUBLIC-KEY CERTIFICATES reliable distribution of public-keys public-key encryption sender needs public key of receiver
INFS 766 Internet Security Protocols Lecture 6 Digital Certificates Prof. Ravi Sandhu PUBLIC-KEY CERTIFICATES reliable distribution of public-keys public-key encryption sender needs public key of receiver
CS549: Cryptography and Network Security
 CS549: Cryptography and Network Security by Xiang-Yang Li Department of Computer Science, IIT Cryptography and Network Security 1 Notice This lecture note (Cryptography and Network Security) is prepared
CS549: Cryptography and Network Security by Xiang-Yang Li Department of Computer Science, IIT Cryptography and Network Security 1 Notice This lecture note (Cryptography and Network Security) is prepared
CIMA Asia. Interactive Timetable Live Online
 CIMA Asia Interactive Timetable 2018 Live Online Information version 8 last updated 04/05/18 Please note information and dates are subject to change. Premium Learning Partner 2018 CIMA Cert BA Course Overview
CIMA Asia Interactive Timetable 2018 Live Online Information version 8 last updated 04/05/18 Please note information and dates are subject to change. Premium Learning Partner 2018 CIMA Cert BA Course Overview
Security Protocols and Infrastructures
 Security Protocols and Infrastructures Dr. Michael Schneider michael.schneider@h-da.de Chapter 5: Standards for Security Infrastructures November 13, 2017 h_da WS2017/18 Dr. Michael Schneider 1 1 Introduction
Security Protocols and Infrastructures Dr. Michael Schneider michael.schneider@h-da.de Chapter 5: Standards for Security Infrastructures November 13, 2017 h_da WS2017/18 Dr. Michael Schneider 1 1 Introduction
DEVELOPER S GUIDE. Managed PKI v7.2. Certificate Validation Module
 DEVELOPER S GUIDE Managed PKI v7.2 Certificate Validation Module VeriSign, Inc. March 10, 2008 Managed PKI Certificate Validation Module 2004-2008 VeriSign, Inc. All rights reserved. The information in
DEVELOPER S GUIDE Managed PKI v7.2 Certificate Validation Module VeriSign, Inc. March 10, 2008 Managed PKI Certificate Validation Module 2004-2008 VeriSign, Inc. All rights reserved. The information in
EuroCamp A federated framework for secure videoconference
 EuroCamp A federated framework for secure videoconference Daniel Kouril, Michal Prochazka Acknowledgement This work is funded by CESNET Development Fund Masaryk University EuroCamp '08 - Stockholm 2 Outline
EuroCamp A federated framework for secure videoconference Daniel Kouril, Michal Prochazka Acknowledgement This work is funded by CESNET Development Fund Masaryk University EuroCamp '08 - Stockholm 2 Outline
SSL Report: bourdiol.xyz ( )
 Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > bourdiol.xyz > 217.70.180.152 SSL Report: bourdiol.xyz (217.70.180.152) Assessed on: Sun Apr 19 12:22:55 PDT 2015 HIDDEN
Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > bourdiol.xyz > 217.70.180.152 SSL Report: bourdiol.xyz (217.70.180.152) Assessed on: Sun Apr 19 12:22:55 PDT 2015 HIDDEN
Action List Modify Configuration Mode Commands
 Action List Modify Configuration Mode Commands Chapter 2 CLI Commands Action List Modify Configuration Mode Commands Action list modify configuration mode commands allow you to configure ACE action lists.
Action List Modify Configuration Mode Commands Chapter 2 CLI Commands Action List Modify Configuration Mode Commands Action list modify configuration mode commands allow you to configure ACE action lists.
Apple Corporate Certificates Certificate Policy and Certification Practice Statement. Apple Inc.
 Apple Inc. Certificate Policy and Certification Practice Statement Version 1.0 Effective Date: March 12, 2015 Table of Contents 1. Introduction... 4 1.1. Trademarks... 4 1.2. Table of acronyms... 4 1.3.
Apple Inc. Certificate Policy and Certification Practice Statement Version 1.0 Effective Date: March 12, 2015 Table of Contents 1. Introduction... 4 1.1. Trademarks... 4 1.2. Table of acronyms... 4 1.3.
Validation Policy r tra is g e R ANF AC MALTA, LTD
 Maltese Registrar of Companies Number C75870 and VAT number MT ANF AC MALTA, LTD B2 Industry Street, Qormi, QRM 3000 Malta Telephone: (+356) 2299 3100 Fax:(+356) 2299 3101 Web: www.anfacmalta.com Security
Maltese Registrar of Companies Number C75870 and VAT number MT ANF AC MALTA, LTD B2 Industry Street, Qormi, QRM 3000 Malta Telephone: (+356) 2299 3100 Fax:(+356) 2299 3101 Web: www.anfacmalta.com Security
CIMA Asia. Interactive Timetable Live Online
 CIMA Asia Interactive Timetable 2017 2018 Live Online Version 1 Information last updated 09 October 2017 Please note: Information and dates in this timetable are subject to change. CIMA Cert BA Course
CIMA Asia Interactive Timetable 2017 2018 Live Online Version 1 Information last updated 09 October 2017 Please note: Information and dates in this timetable are subject to change. CIMA Cert BA Course
Certification Authority
 Certification Authority Overview Identifying CA Hierarchy Design Requirements Common CA Hierarchy Designs Documenting Legal Requirements Analyzing Design Requirements Designing a Hierarchy Structure Identifying
Certification Authority Overview Identifying CA Hierarchy Design Requirements Common CA Hierarchy Designs Documenting Legal Requirements Analyzing Design Requirements Designing a Hierarchy Structure Identifying
PKI Disclosure Statement Digidentity Certificates
 PKI Disclosure Statement Digidentity Certificates Title PKI Disclosure Statement Digidentity Certificates Date 25 March 2019 Author Digidentity Version 2019-v1 Classification Public Digidentity 2019 Revisions
PKI Disclosure Statement Digidentity Certificates Title PKI Disclosure Statement Digidentity Certificates Date 25 March 2019 Author Digidentity Version 2019-v1 Classification Public Digidentity 2019 Revisions
System Administration
 Changing the Management IP Address, on page 1 Changing the Application Management IP, on page 3 Changing the Firepower 4100/9300 Chassis Name, on page 5 Pre-Login Banner, on page 6 Rebooting the Firepower
Changing the Management IP Address, on page 1 Changing the Application Management IP, on page 3 Changing the Firepower 4100/9300 Chassis Name, on page 5 Pre-Login Banner, on page 6 Rebooting the Firepower
Symantec Managed PKI. Integration Guide for ActiveSync
 Symantec Managed PKI Integration Guide for ActiveSync ii Symantec Managed PKI Symantec Managed PKI Integration Guide for ActiveSync The software described in this book is furnished under a license agreement
Symantec Managed PKI Integration Guide for ActiveSync ii Symantec Managed PKI Symantec Managed PKI Integration Guide for ActiveSync The software described in this book is furnished under a license agreement
PKI Services. Text PKI Definition. PKI Definition #1. Public Key Infrastructure. What Does A PKI Do? Public Key Infrastructures
 Public Key Infrastructures Public Key Infrastructure Definition and Description Functions Components Certificates 1 2 PKI Services Security Between Strangers Encryption Integrity Non-repudiation Key establishment
Public Key Infrastructures Public Key Infrastructure Definition and Description Functions Components Certificates 1 2 PKI Services Security Between Strangers Encryption Integrity Non-repudiation Key establishment
HPE Knowledge Article
 HPE Knowledge Article HPE 5930/5940 Switch Series - Connect to OVSDB Client Article Number mmr_sf-en_us000021071 Environment HPE 5930/5940 switches can be configured as OVSDB servers. One common use case
HPE Knowledge Article HPE 5930/5940 Switch Series - Connect to OVSDB Client Article Number mmr_sf-en_us000021071 Environment HPE 5930/5940 switches can be configured as OVSDB servers. One common use case
Lecture 15 Public Key Distribution (certification)
 0 < i < 2 n = N X i,y i random secret keys index i = random (secret) value Merkle s Puzzles (1974) Puzzle P i = {index i,x i,s} Y i S fixed string, e.g., " Alice to Bob" { P 0 < i < 2 i n } Pick random
0 < i < 2 n = N X i,y i random secret keys index i = random (secret) value Merkle s Puzzles (1974) Puzzle P i = {index i,x i,s} Y i S fixed string, e.g., " Alice to Bob" { P 0 < i < 2 i n } Pick random
SSH Communications Tectia SSH
 Secured by RSA Implementation Guide for 3rd Party PKI Applications Last Modified: December 8, 2014 Partner Information Product Information Partner Name Web Site Product Name Version & Platform Product
Secured by RSA Implementation Guide for 3rd Party PKI Applications Last Modified: December 8, 2014 Partner Information Product Information Partner Name Web Site Product Name Version & Platform Product
AIMMS Function Reference - Date Time Related Identifiers
 AIMMS Function Reference - Date Time Related Identifiers This file contains only one chapter of the book. For a free download of the complete book in pdf format, please visit www.aimms.com Aimms 3.13 Date-Time
AIMMS Function Reference - Date Time Related Identifiers This file contains only one chapter of the book. For a free download of the complete book in pdf format, please visit www.aimms.com Aimms 3.13 Date-Time
DirectTrust Governmental Trust Anchor Bundle Standard Operating Procedure
 DirectTrust Governmental Trust Anchor Bundle Standard Operating Procedure Change Control Date Version Description of changes 15-December- 2016 1-December- 2016 17-March- 2016 4-February- 2016 3-February-
DirectTrust Governmental Trust Anchor Bundle Standard Operating Procedure Change Control Date Version Description of changes 15-December- 2016 1-December- 2016 17-March- 2016 4-February- 2016 3-February-
Key Management and Distribution
 Key Management and Distribution Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse571-14/
Key Management and Distribution Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse571-14/
Ten Risks of PKI : What You re not Being Told about Public Key Infrastructure By Carl Ellison and Bruce Schneier
 Presented by Joshua Schiffman & Archana Viswanath Ten Risks of PKI : What You re not Being Told about Public Key Infrastructure By Carl Ellison and Bruce Schneier Trust Models Rooted Trust Model! In a
Presented by Joshua Schiffman & Archana Viswanath Ten Risks of PKI : What You re not Being Told about Public Key Infrastructure By Carl Ellison and Bruce Schneier Trust Models Rooted Trust Model! In a
Secure Websites Using SSL And Certificates
 By punk0mi Published: 2007-05-16 17:14 Secure Websites Using SSL And Certificates This how-to will guide you through the entire process of setting up a secure website using SSL and digital certificates.
By punk0mi Published: 2007-05-16 17:14 Secure Websites Using SSL And Certificates This how-to will guide you through the entire process of setting up a secure website using SSL and digital certificates.
Encryption, Certificates and SSL DAVID COCHRANE PRESENTATION TO BELFAST OWASP CHAPTER OCTOBER 2018
 Encryption, Certificates and SSL DAVID COCHRANE PRESENTATION TO BELFAST OWASP CHAPTER OCTOBER 2018 Agenda Basic Theory: encryption and hashing Digital Certificates Tools for Digital Certificates Design
Encryption, Certificates and SSL DAVID COCHRANE PRESENTATION TO BELFAST OWASP CHAPTER OCTOBER 2018 Agenda Basic Theory: encryption and hashing Digital Certificates Tools for Digital Certificates Design
6 Public Key Infrastructure 6.1 Certificates Structure of an X.509 certificate X.500 Distinguished Name and X.509v3 subjectalternativename
 6 Public Key Infrastructure 6.1 Certificates Structure of an X.509 certificate X.500 Distinguished Name and X.509v3 subjectalternativename Certificate formats (DER, PEM, PKCS #12) 6.2 Certificate Authorities
6 Public Key Infrastructure 6.1 Certificates Structure of an X.509 certificate X.500 Distinguished Name and X.509v3 subjectalternativename Certificate formats (DER, PEM, PKCS #12) 6.2 Certificate Authorities
Certificate implementation The good, the bad, and the ugly
 Certificate implementation The good, the bad, and the ugly DOE Security Training Workshop James A. Rome Oak Ridge National Laboratory April 29, 1998 A wealth of riches? I decided to use certificates for
Certificate implementation The good, the bad, and the ugly DOE Security Training Workshop James A. Rome Oak Ridge National Laboratory April 29, 1998 A wealth of riches? I decided to use certificates for
Importing a Global Server Certificate from Verisign and other PKCS#7 certificates into the SonicWALL SSL Accelerator
 Importing a Global Server Certificate from Verisign and other PKCS#7 certificates into the SonicWALL SSL Accelerator Introduction When obtaining a 128 bit SSL certificate, the choice for many are Step-Up
Importing a Global Server Certificate from Verisign and other PKCS#7 certificates into the SonicWALL SSL Accelerator Introduction When obtaining a 128 bit SSL certificate, the choice for many are Step-Up
J. Basney, NCSA Category: Experimental October 10, MyProxy Protocol
 GWD-E J. Basney, NCSA Category: Experimental October 10, 2005 MyProxy Protocol Status of This Memo This memo provides information to the Grid community. Distribution is unlimited. Copyright Notice Copyright
GWD-E J. Basney, NCSA Category: Experimental October 10, 2005 MyProxy Protocol Status of This Memo This memo provides information to the Grid community. Distribution is unlimited. Copyright Notice Copyright
Public Key Infrastructure. What can it do for you?
 Public Key Infrastructure What can it do for you? What is PKI? Centrally-managed cryptography, for: Encryption Authentication Automatic negotiation Native support in most modern Operating Systems Allows
Public Key Infrastructure What can it do for you? What is PKI? Centrally-managed cryptography, for: Encryption Authentication Automatic negotiation Native support in most modern Operating Systems Allows
Federal PKI. Trust Store Management Guide
 Federal PKI Trust Store Management Guide V1.0 September 21, 2015 FINAL Disclaimer The Federal PKI Management Authority (FPKIMA) has designed and created the Trust Store Management Guide as an education
Federal PKI Trust Store Management Guide V1.0 September 21, 2015 FINAL Disclaimer The Federal PKI Management Authority (FPKIMA) has designed and created the Trust Store Management Guide as an education
Configuring SSL CHAPTER
 7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
Managing Certificates
 CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
Government PKI Factors Influencing Architecture for the Equal Employment Opportunity Commission
 Government PKI Factors Influencing Architecture for the Equal Employment Opportunity Commission December 14, 2000 Steve Bruck Khurram Chaudry Francis Yuan 1 EEOC Business Cases for PKI Citizens complaints
Government PKI Factors Influencing Architecture for the Equal Employment Opportunity Commission December 14, 2000 Steve Bruck Khurram Chaudry Francis Yuan 1 EEOC Business Cases for PKI Citizens complaints
Public Key Infrastructure
 Public Key Infrastructure Ed Crowley Summer 11 1 Topics Public Key Infrastructure Defined PKI Overview PKI Architecture Trust Models Components X.509 Certificates X.500 LDAP 2 Public Key Infrastructure
Public Key Infrastructure Ed Crowley Summer 11 1 Topics Public Key Infrastructure Defined PKI Overview PKI Architecture Trust Models Components X.509 Certificates X.500 LDAP 2 Public Key Infrastructure
ASA 8.x Manually Install 3rd Party Vendor Certificates for use with WebVPN Configuration Example
 ASA 8.x Manually Install 3rd Party Vendor Certificates for use with WebVPN Configuration Example Contents Introduction Prerequisites Requirements Components Used Conventions Configure Step 1. Verify that
ASA 8.x Manually Install 3rd Party Vendor Certificates for use with WebVPN Configuration Example Contents Introduction Prerequisites Requirements Components Used Conventions Configure Step 1. Verify that
Overview. SSL Cryptography Overview CHAPTER 1
 CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet. SSL ensures the secure transmission of data between a client and a server through
CHAPTER 1 Secure Sockets Layer (SSL) is an application-level protocol that provides encryption technology for the Internet. SSL ensures the secure transmission of data between a client and a server through
Federal Voting Assistance Program (FVAP)
 16th Annual Computer Security Application Conference (ACSAC) December 2000 Federal Voting Assistance Program (FVAP) Provide Background on VOI Pilot Effort Provide High Level Technical Overview Security
16th Annual Computer Security Application Conference (ACSAC) December 2000 Federal Voting Assistance Program (FVAP) Provide Background on VOI Pilot Effort Provide High Level Technical Overview Security
Information Security. message M. fingerprint f = H(M) one-way hash. 4/19/2006 Information Security 1
 Information Security message M one-way hash fingerprint f = H(M) 4/19/2006 Information Security 1 Outline and Reading Digital signatures Definition RSA signature and verification One-way hash functions
Information Security message M one-way hash fingerprint f = H(M) 4/19/2006 Information Security 1 Outline and Reading Digital signatures Definition RSA signature and verification One-way hash functions
Apple Inc. Certification Authority Certification Practice Statement
 Apple Inc. Certification Authority Certification Practice Statement Apple Application Integration Sub-CA Apple Application Integration 2 Sub-CA Apple Application Integration - G3 Sub-CA Version 6.3 Effective
Apple Inc. Certification Authority Certification Practice Statement Apple Application Integration Sub-CA Apple Application Integration 2 Sub-CA Apple Application Integration - G3 Sub-CA Version 6.3 Effective
Description Provides details about the CA s certificate and all certificates that the CA will issue.
 Boeing SecureBadge Medium G2 s Description Provides details about the CA s certificate and all certificates that the CA will issue. Content Owner Authentication Controls All future revisions to this document
Boeing SecureBadge Medium G2 s Description Provides details about the CA s certificate and all certificates that the CA will issue. Content Owner Authentication Controls All future revisions to this document
Configuring SSL. SSL Overview CHAPTER
 7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
Technical Trust Policy
 Technical Trust Policy Version 1.2 Last Updated: May 20, 2016 Introduction Carequality creates a community of trusted exchange partners who rely on each organization s adherence to the terms of the Carequality
Technical Trust Policy Version 1.2 Last Updated: May 20, 2016 Introduction Carequality creates a community of trusted exchange partners who rely on each organization s adherence to the terms of the Carequality
Cristina Nita-Rotaru. CS355: Cryptography. Lecture 17: X509. PGP. Authentication protocols. Key establishment.
 CS355: Cryptography Lecture 17: X509. PGP. Authentication protocols. Key establishment. Public Keys and Trust Public Key:P A Secret key: S A Public Key:P B Secret key: S B How are public keys stored How
CS355: Cryptography Lecture 17: X509. PGP. Authentication protocols. Key establishment. Public Keys and Trust Public Key:P A Secret key: S A Public Key:P B Secret key: S B How are public keys stored How
An Example Grid Middleware - The Globus Toolkit. MCSN N. Tonellotto Complements of Distributed Enabling Platforms
 An Example Grid Middleware - The Globus Toolkit 1 Globus Toolkit A software toolkit addressing key technical problems in the development of Grid enabled tools, services, and applications Offer a modular
An Example Grid Middleware - The Globus Toolkit 1 Globus Toolkit A software toolkit addressing key technical problems in the development of Grid enabled tools, services, and applications Offer a modular
Introduction to Network Security Missouri S&T University CPE 5420 Key Management and Distribution
 Introduction to Network Security Missouri S&T University CPE 5420 Key Management and Distribution Egemen K. Çetinkaya Egemen K. Çetinkaya Department of Electrical & Computer Engineering Missouri University
Introduction to Network Security Missouri S&T University CPE 5420 Key Management and Distribution Egemen K. Çetinkaya Egemen K. Çetinkaya Department of Electrical & Computer Engineering Missouri University
How to Set Up External CA VPN Certificates
 To configure a client-to-site, or site-to-site VPN using s created by External CA, you must create the following VPN s for the VPN service to be able to authenticate Before you begin Use an external CA
To configure a client-to-site, or site-to-site VPN using s created by External CA, you must create the following VPN s for the VPN service to be able to authenticate Before you begin Use an external CA
Buypass Class 2 Certificates
 CERTIFICATE AND CRL PROFILES Buypass Class 2 Certificates PUBLIC Version: 1.0.1 Document date: 26.10.2009 Buypass AS Nydalsveien 30A, PO Box 4364 Nydalen Tel.: +47 23 14 59 00 E-mail: kundeservice@buypass.no
CERTIFICATE AND CRL PROFILES Buypass Class 2 Certificates PUBLIC Version: 1.0.1 Document date: 26.10.2009 Buypass AS Nydalsveien 30A, PO Box 4364 Nydalen Tel.: +47 23 14 59 00 E-mail: kundeservice@buypass.no
SMPTE Standards Transition Issues for NIST/FIPS Requirements
 SMPTE Standards Transition Issues for NIST/FIPS Requirements Contents 2010.5.20 DRM inside Taehyun Kim 1 Introduction NIST (National Institute of Standards and Technology) published a draft special document
SMPTE Standards Transition Issues for NIST/FIPS Requirements Contents 2010.5.20 DRM inside Taehyun Kim 1 Introduction NIST (National Institute of Standards and Technology) published a draft special document
Signe Certification Authority. Certification Policy Degree Certificates
 Signe Certification Authority Certification Policy Degree Certificates Versión 1.0 Fecha: 2/11/2010 Table of contents 1 FOREWORD 1.1 GENERAL DESCRIPTION 1.2 DOCUMENT NAME AND IDENTIFICATION 2 PARTICIPATING
Signe Certification Authority Certification Policy Degree Certificates Versión 1.0 Fecha: 2/11/2010 Table of contents 1 FOREWORD 1.1 GENERAL DESCRIPTION 1.2 DOCUMENT NAME AND IDENTIFICATION 2 PARTICIPATING
SSL/TLS & 3D Secure. CS 470 Introduction to Applied Cryptography. Ali Aydın Selçuk. CS470, A.A.Selçuk SSL/TLS & 3DSec 1
 SSL/TLS & 3D Secure CS 470 Introduction to Applied Cryptography Ali Aydın Selçuk CS470, A.A.Selçuk SSL/TLS & 3DSec 1 SSLv2 Brief History of SSL/TLS Released in 1995 with Netscape 1.1 Key generation algorithm
SSL/TLS & 3D Secure CS 470 Introduction to Applied Cryptography Ali Aydın Selçuk CS470, A.A.Selçuk SSL/TLS & 3DSec 1 SSLv2 Brief History of SSL/TLS Released in 1995 with Netscape 1.1 Key generation algorithm
ON THE PROVISION OF CERTIFICATES FOR WEBSITE AUTHENTICATION BY BORICA AD
 POLICY ON THE PROVISION OF CERTIFICATES FOR WEBSITE AUTHENTICATION BY BORICA AD (B-Trust QCP-eIDAS Web SSL) Version 1.0 Effective date: July 1, 2018 Document history Version Author (s) Date Status Comment
POLICY ON THE PROVISION OF CERTIFICATES FOR WEBSITE AUTHENTICATION BY BORICA AD (B-Trust QCP-eIDAS Web SSL) Version 1.0 Effective date: July 1, 2018 Document history Version Author (s) Date Status Comment
Configure DNA Center Assurance for Cisco ISE Integration
 Configure DNA Center Assurance for Cisco ISE Integration If your network uses Cisco ISE for user authentication, you can configure DNA Center Assurance for Cisco ISE integration. This will allow you to
Configure DNA Center Assurance for Cisco ISE Integration If your network uses Cisco ISE for user authentication, you can configure DNA Center Assurance for Cisco ISE integration. This will allow you to
PKI Configuration Examples
 PKI Configuration Examples Keywords: PKI, CA, RA, IKE, IPsec, SSL Abstract: The Public Key Infrastructure (PKI) is a general security infrastructure for providing information security through public key
PKI Configuration Examples Keywords: PKI, CA, RA, IKE, IPsec, SSL Abstract: The Public Key Infrastructure (PKI) is a general security infrastructure for providing information security through public key
Digi-CPS. Certificate Practice Statement v3.6. Certificate Practice Statement from Digi-Sign Limited.
 Certificate Practice Statement v3.6 Certificate Practice Statement from Digi-Sign Limited. Digi-CPS Version 3.6. Produced by the Legal & Technical Departments For further information, please contact: CONTACT:
Certificate Practice Statement v3.6 Certificate Practice Statement from Digi-Sign Limited. Digi-CPS Version 3.6. Produced by the Legal & Technical Departments For further information, please contact: CONTACT:
MTAT Applied Cryptography
 MTAT.07.017 Applied Cryptography Public Key Infrastructure (PKI) Public Key Certificates (X.509) University of Tartu Spring 2017 1 / 45 The hardest problem Key Management How to obtain the key of the other
MTAT.07.017 Applied Cryptography Public Key Infrastructure (PKI) Public Key Certificates (X.509) University of Tartu Spring 2017 1 / 45 The hardest problem Key Management How to obtain the key of the other
U.S. E-Authentication Interoperability Lab Engineer
 Using Digital Certificates to Establish Federated Trust chris.brown@enspier.com U.S. E-Authentication Interoperability Lab Engineer Agenda U.S. Federal E-Authentication Background Current State of PKI
Using Digital Certificates to Establish Federated Trust chris.brown@enspier.com U.S. E-Authentication Interoperability Lab Engineer Agenda U.S. Federal E-Authentication Background Current State of PKI
Diffie-Hellman. Part 1 Cryptography 136
 Diffie-Hellman Part 1 Cryptography 136 Diffie-Hellman Invented by Williamson (GCHQ) and, independently, by D and H (Stanford) A key exchange algorithm o Used to establish a shared symmetric key Not for
Diffie-Hellman Part 1 Cryptography 136 Diffie-Hellman Invented by Williamson (GCHQ) and, independently, by D and H (Stanford) A key exchange algorithm o Used to establish a shared symmetric key Not for
Public-key Infrastructure
 Public-key Infrastructure Cryptosystems Cryptosystems Symmetric Asymmetric (public-key) RSA Public key: n=3233, e=17 Private key: d=2753 Let m=65 Encryption: c = 65 17 (mod 3233) = 2790 Decryption: m =
Public-key Infrastructure Cryptosystems Cryptosystems Symmetric Asymmetric (public-key) RSA Public key: n=3233, e=17 Private key: d=2753 Let m=65 Encryption: c = 65 17 (mod 3233) = 2790 Decryption: m =
