pyptlib Documentation
|
|
|
- Kristina Foster
- 5 years ago
- Views:
Transcription
1 pyptlib Documentation Release UNRELEASED Brandon Wiley March 21, 2014
2
3 Contents 1 pyptlib README 3 2 API overview General Overview Detailed API Overview Pluggable transports glossary pluggable transport (sometimes also called transport ) pluggable transport proxy obfsproxy upstream/downstream client-mode / server-mode external-mode proxy managed-mode proxy pyptlib extended orport pyptlib.client 11 5 pyptlib.server 13 6 pyptlib.util 15 7 Indices and tables 17 i
4 ii
5 pyptlib Documentation, Release UNRELEASED pyptlib is a little Python library that makes the job of writing pluggable transports easier. Contents 1
6 pyptlib Documentation, Release UNRELEASED 2 Contents
7 CHAPTER 1 pyptlib README What is pyptlib? pyptlib is a little Python library which understands the pluggable transport managed-proxy protocol. Who is interested in pyptlib? You might be interested in pyptlib if you have an application that obfuscates TCP traffic and you want to integrate it easily with Tor. What does pyptlib do? pyptlib speaks with Tor and informs your application about which pluggable transports Tor needs, in which ports they should listen for connections, in which filesystem directory they should keep state, etc. What does pyptlib not do? pyptlib doesn t help your application do networking or obfuscation. What does pyptlib expect from an application? pyptlib assumes that your application is executed by Tor as a managed-proxy. pyptlib assumes that your application acts as a proxy: it listens for traffic on a TCP port and pushes the traffic somewhere else. pyptlib assumes that your application has a SOCKS server when it acts as a client. This is needed because Tor needs to dynamically select where its data will be pushed to. How do I use pyptlib? Read the documentation, the examples and the source. What are these buzzwords? glossary.rst 3
8 pyptlib Documentation, Release UNRELEASED 4 Chapter 1. pyptlib README
9 CHAPTER 2 API overview Be sure to read API.rst and glossary.rst before reading this file. 2.1 General Overview Applications begin by initializing pyptlib. Then pyptlib informs the application about which transports it should spawn, in which ports they should listen for connections, etc. Then the application launches the appropriate transports as instructed, and for each transport it reports to pyptlib whether it was launched successfully or not. Finally, the application announces to pyptlib that it finished launching transports. From that point and on the application should forget about pyptlib and start accepting connections. 2.2 Detailed API Overview ) Find if it s a client or a server An application using pyptlib should start by calling pyptlib.config.checkclientmode() to learn whether Tor wants it to run as a client or as a server. You should then create a pyptlib.client.clienttransportplugin or pyptlib.server.servertransportplugin as appropriate. This object is your main entry point to the pyptlib API, so you should keep it somewhere for later access ) Get transport information from Tor The next step is to run init to parse the rest of the configuration and communicate the results to Tor. You should pass a list of names of the transports your application supports. The application should be prepared for pyptlib.config.enverror, which signifies that the environment was not prepared by Tor. Consider an example of the fictional application rot0r which implements the pluggable transports rot13 and rot26. If rot0r, in step 1, learned that Tor expects it to act as a client, it should now do: 5
10 pyptlib Documentation, Release UNRELEASED from pyptlib.client import ClientTransportPlugin from pyptlib.config import EnvError client = ClientTransportPlugin() try: client.init(supported_transports=["rot13", "rot26"]) except EnvError, err: print "pyptlib could not bootstrap ( %s )." % str(err) Afterwards, the API s config attribute provides methods to find out how Tor wants your application to be configured. For example, if you store state, it should go in client.config.getstatelocation(). For a complete list, see the documentation for that module ) Launch transports Client case (skip if you are a server) Your application should then use client.gettransports() to learn which transports it should launch. Proceeding with the previous example: if rot13 in client.gettransports(): launch_rot13_client() if rot26 in client.gettransports(): launch_rot26_client() For a full list of the methods available, see the module docs for client and client.config. Note: Since the application runs as a client, it should launch a SOCKS server in the upstream side of the proxy. Server case (skip if you are a client): Your application should then use server.getbindaddresses() to learn which transports it should launch. Since the application runs as a server, it will push data to Tor s ORPort, which you can get using server.config.getorport(). Proceeding with the previous example: transports = server.getbindaddresses() if rot13 in transports: launch_rot13_server(transports[ rot13 ], server.config.getorport()) if rot26 in transports: launch_rot26_server(transports[ rot26 ], server.config.getorport()) For a full list of the methods available, see the module docs for server and server.config ) Report results back to Tor. For every transport that the application launches, it reports to pyptlib whether it was launched successfully or not. This way, Tor is informed on whether a transport is expected to work or not. 6 Chapter 2. API overview
11 pyptlib Documentation, Release UNRELEASED Client case (skip if you are a server): Every time a transport is successfully launched, the application calls client.reportmethodsuccess with the name of the transport that was launched, the address where it is listening for connections, and the SOCKS version that the upstream SOCKS server supports. For example, if rot13 was launched successfully, waits for connections in :42042 and supports SOCKSv4, the appropriate call would be: client.reportmethodsuccess( rot13, socks5, ( , 42042)) Every time a transport failed to launch, the application calls client.reportmethoderror with the name of the transport and a message. For example, if rot26 failed to launch, the appropriate call would be: client.reportmethoderror( rot26, Could not bind to :666 (Operation not permitted) ) Server case (skip if you are a client): Everytime a transport is successfully launched, the application calls server.reportmethodsuccess with the name of the transport that was launched, and the address where it is listening for connections. For example, if rot13 was launched successfully and waits for connections in :42042, the appropriate call would be: server.reportmethodsuccess( rot13, ( , 42042)) Everytime a transport failed to launch, the application should call server.reportmethoderror with the name of the transport and a message. For example, if rot26 failed to launch, the appropriate call would be: server.reportmethoderror( rot26, Could not bind to :666 (Operation not permitted) ) ) Stop using pyptlib and start accepting connections When the application finishes launching connections, it should call reportmethodsend(), to announce to pyptlib that all transports were launched. This way, Tor knows that it can start pushing traffic to the application. After this point, the API object (in this current version of pyptlib) has no other use Detailed API Overview 7
12 pyptlib Documentation, Release UNRELEASED 8 Chapter 2. API overview
13 CHAPTER 3 Pluggable transports glossary 3.1 pluggable transport (sometimes also called transport ) Pluggable transports obfuscate network traffic. Specifically, pluggable transports transform the Tor traffic flow between the client and the bridge. This way, censors who monitor traffic between the client and the bridge see innocent-looking transformed traffic instead of the actual Tor traffic. 3.2 pluggable transport proxy Pluggable transport proxies are programs that implement pluggable transports. They also implement the networking system that a pluggable transport needs (so that it can proxy data). 3.3 obfsproxy obfsproxy is a pluggable transport proxy written in C. It implements the obfs2 pluggable transport. 3.4 upstream/downstream The upstream side of a pluggable transport proxy is the side that communicates with Tor. Upstream data is nonobfuscated. The downstream side of a pluggable transport proxy is the side that communicates with the other pluggable transport proxy. Downstream data is obfuscated. 3.5 client-mode / server-mode A pluggable transport is a client if it has a Tor client in its upstream side. A pluggable transport is a server if it has a Tor bridge in its upstream side. 9
14 pyptlib Documentation, Release UNRELEASED 3.6 external-mode proxy A pluggable transport proxy is in external-mode if the user explicitly configures it using its command-line interface. 3.7 managed-mode proxy A pluggable transport proxy is in managed-mode if it s launched and managed by Tor using the managed-proxy configuration protocol. The managed-proxy configuration protocol is defined in the pluggable transport specification. 3.8 pyptlib pyptlib is a library that implements the managed-proxy configuration protocol and makes it easier for application to be used as managed proxies. 3.9 extended orport Extended ORPort is an non-implemented feature of Tor that allows a pluggable transport proxy to communicate with Tor in real-time. 10 Chapter 3. Pluggable transports glossary
15 CHAPTER 4 pyptlib.client Client-side pyptlib API. 11
16 pyptlib Documentation, Release UNRELEASED 12 Chapter 4. pyptlib.client
17 CHAPTER 5 pyptlib.server Server-side pyptlib API. 13
18 pyptlib Documentation, Release UNRELEASED 14 Chapter 5. pyptlib.server
19 CHAPTER 6 pyptlib.util pyptlib utilities. 15
20 pyptlib Documentation, Release UNRELEASED 16 Chapter 6. pyptlib.util
21 CHAPTER 7 Indices and tables genindex modindex search 17
Pluggable Transports Roadmap
 Pluggable Transports Roadmap Steven J. Murdoch and George Kadianakis steven.murdoch@cl.cam.ac.uk,asn@torproject.org Tor Tech Report 2012-03-003 March 17, 2012 Abstract Of the currently available pluggable
Pluggable Transports Roadmap Steven J. Murdoch and George Kadianakis steven.murdoch@cl.cam.ac.uk,asn@torproject.org Tor Tech Report 2012-03-003 March 17, 2012 Abstract Of the currently available pluggable
yardstick Documentation
 yardstick Documentation Release 0.1.0 Kenny Freeman December 30, 2015 Contents 1 yardstick 3 1.1 What is yardstick?............................................ 3 1.2 Features..................................................
yardstick Documentation Release 0.1.0 Kenny Freeman December 30, 2015 Contents 1 yardstick 3 1.1 What is yardstick?............................................ 3 1.2 Features..................................................
API RI. Application Programming Interface Reference Implementation. Policies and Procedures Discussion
 API Working Group Meeting, Harris County, TX March 22-23, 2016 Policies and Procedures Discussion Developing a Mission Statement What do we do? How do we do it? Whom do we do it for? What value are we
API Working Group Meeting, Harris County, TX March 22-23, 2016 Policies and Procedures Discussion Developing a Mission Statement What do we do? How do we do it? Whom do we do it for? What value are we
Anonymous Network Concepts & Implementation
 FORENSIC INSIGHT; DIGITAL FORENSICS COMMUNITY IN KOREA Anonymous Network Concepts & Implementation kevinkoo001@gmail.com Overview 1. Overview & Background 2. Anonymous Network tor freenet Gnunet I2P 3.
FORENSIC INSIGHT; DIGITAL FORENSICS COMMUNITY IN KOREA Anonymous Network Concepts & Implementation kevinkoo001@gmail.com Overview 1. Overview & Background 2. Anonymous Network tor freenet Gnunet I2P 3.
Pusher Documentation. Release. Top Free Games
 Pusher Documentation Release Top Free Games January 18, 2017 Contents 1 Overview 3 1.1 Features.................................................. 3 1.2 The Stack.................................................
Pusher Documentation Release Top Free Games January 18, 2017 Contents 1 Overview 3 1.1 Features.................................................. 3 1.2 The Stack.................................................
Service Cloaking and Anonymous Access; Combining Tor with Single Packet Authorization (SPA)
 Service Cloaking and Anonymous Access; Combining Tor with Single Packet Authorization (SPA) Michael Rash CTO, Solirix Inc. michael.rash@solirix.com http://www.cipherdyne.org/ DEF CON 08/05/2006 Agenda
Service Cloaking and Anonymous Access; Combining Tor with Single Packet Authorization (SPA) Michael Rash CTO, Solirix Inc. michael.rash@solirix.com http://www.cipherdyne.org/ DEF CON 08/05/2006 Agenda
Scrapyd Documentation
 Scrapyd Documentation Release 1.2.0 Scrapy group Jan 19, 2018 Contents 1 Contents 3 1.1 Overview................................................. 3 1.2 Installation................................................
Scrapyd Documentation Release 1.2.0 Scrapy group Jan 19, 2018 Contents 1 Contents 3 1.1 Overview................................................. 3 1.2 Installation................................................
Pulp OSTree Documentation
 Pulp OSTree Documentation Release 1.0.0 Pulp Team November 06, 2015 Contents 1 Glossary 3 2 Concepts 5 3 User Guide 7 3.1 Installation................................................ 7 3.2 Configuration...............................................
Pulp OSTree Documentation Release 1.0.0 Pulp Team November 06, 2015 Contents 1 Glossary 3 2 Concepts 5 3 User Guide 7 3.1 Installation................................................ 7 3.2 Configuration...............................................
Stepic Plugins Documentation
 Stepic Plugins Documentation Release 0 Stepic Team May 06, 2015 Contents 1 Introduction 3 1.1 Quiz Architecture............................................ 3 1.2 Backend Overview............................................
Stepic Plugins Documentation Release 0 Stepic Team May 06, 2015 Contents 1 Introduction 3 1.1 Quiz Architecture............................................ 3 1.2 Backend Overview............................................
mri Documentation Release Nate Harada
 mri Documentation Release 1.0.0 Nate Harada September 18, 2015 Contents 1 Getting Started 3 1.1 Deploying A Server........................................... 3 1.2 Using Caffe as a Client..........................................
mri Documentation Release 1.0.0 Nate Harada September 18, 2015 Contents 1 Getting Started 3 1.1 Deploying A Server........................................... 3 1.2 Using Caffe as a Client..........................................
Internet Connectivity with
 Internet Connectivity with Introduction The purpose of this workshop is to help you g et acquainted with the basics of internet connectivity by leveraging ARM mbed tools. If you are not already familiar
Internet Connectivity with Introduction The purpose of this workshop is to help you g et acquainted with the basics of internet connectivity by leveraging ARM mbed tools. If you are not already familiar
lazy-object-proxy Release 1.3.1
 lazy-object-proxy Release 1.3.1 Jun 22, 2017 Contents 1 Overview 1 1.1 Installation................................................ 2 1.2 Documentation.............................................. 2
lazy-object-proxy Release 1.3.1 Jun 22, 2017 Contents 1 Overview 1 1.1 Installation................................................ 2 1.2 Documentation.............................................. 2
Bitdock. Release 0.1.0
 Bitdock Release 0.1.0 August 07, 2014 Contents 1 Installation 3 1.1 Building from source........................................... 3 1.2 Dependencies............................................... 3
Bitdock Release 0.1.0 August 07, 2014 Contents 1 Installation 3 1.1 Building from source........................................... 3 1.2 Dependencies............................................... 3
Dissecting Tor Bridges A Security Evaluation of their Private and Public Infrastructures
 Dissecting Tor Bridges A Security Evaluation of their Private and Public Infrastructures Srdjan Matic, Carmela Troncoso, Juan Caballero Dublin 31 March 2017 Privacy in electronic communications Alice Bob
Dissecting Tor Bridges A Security Evaluation of their Private and Public Infrastructures Srdjan Matic, Carmela Troncoso, Juan Caballero Dublin 31 March 2017 Privacy in electronic communications Alice Bob
HAProxy log analyzer Documentation
 HAProxy log analyzer Documentation Release 0.1 Gil Forcada Nov 08, 2017 Contents 1 HAProxy log analyzer 3 1.1 Tests and coverage............................................ 3 1.2 Documentation..............................................
HAProxy log analyzer Documentation Release 0.1 Gil Forcada Nov 08, 2017 Contents 1 HAProxy log analyzer 3 1.1 Tests and coverage............................................ 3 1.2 Documentation..............................................
OTX to MISP. Release 1.4.2
 OTX to MISP Release 1.4.2 May 11, 2018 Contents 1 Overview 1 1.1 Installation................................................ 1 1.2 Documentation.............................................. 1 1.3 Alienvault
OTX to MISP Release 1.4.2 May 11, 2018 Contents 1 Overview 1 1.1 Installation................................................ 1 1.2 Documentation.............................................. 1 1.3 Alienvault
APACHE COTTON. MySQL on Mesos. Yan Xu xujyan
 APACHE COTTON MySQL on Mesos Yan Xu xujyan 1 SHORT HISTORY Mesos: cornerstone of Twitter s compute platform. MySQL: backbone of Twitter s data platform. Mysos: started as a hackweek project @twitter. Apache
APACHE COTTON MySQL on Mesos Yan Xu xujyan 1 SHORT HISTORY Mesos: cornerstone of Twitter s compute platform. MySQL: backbone of Twitter s data platform. Mysos: started as a hackweek project @twitter. Apache
SOCKS Protocol Version 6 (update)
 SOCKS Protocol Version 6 (update) draft-olteanu-intarea-socks-6-05 Vladimir Olteanu New in -05 Different handling of first bytes of application data Reverse TCP proxy: can now handle concurrent incoming
SOCKS Protocol Version 6 (update) draft-olteanu-intarea-socks-6-05 Vladimir Olteanu New in -05 Different handling of first bytes of application data Reverse TCP proxy: can now handle concurrent incoming
Using Music Port with Home Automation Systems
 Using Music Port with Home Automation Systems This paper describes how to use the NuVo Music Port in conjunction with an automation controller that needs access to the RS232 port on the NuVo amplifier.
Using Music Port with Home Automation Systems This paper describes how to use the NuVo Music Port in conjunction with an automation controller that needs access to the RS232 port on the NuVo amplifier.
withenv Documentation
 withenv Documentation Release 0.7.0 Eric Larson Aug 02, 2017 Contents 1 withenv 3 2 Installation 5 3 Usage 7 3.1 YAML Format.............................................. 7 3.2 Command Substitutions.........................................
withenv Documentation Release 0.7.0 Eric Larson Aug 02, 2017 Contents 1 withenv 3 2 Installation 5 3 Usage 7 3.1 YAML Format.............................................. 7 3.2 Command Substitutions.........................................
Lab Assignment 3 for ECE374
 Lab Assignment 3 for ECE374 Posted: 02/25/18 Due: 03/08/18 In this lab, we ll take a quick look at the UDP and TCP transport protocol. Whenever possible you should hand in a Wireshark screenshot that you
Lab Assignment 3 for ECE374 Posted: 02/25/18 Due: 03/08/18 In this lab, we ll take a quick look at the UDP and TCP transport protocol. Whenever possible you should hand in a Wireshark screenshot that you
fragapy Documentation
 fragapy Documentation Release 1.0 2011, Fragaria, s.r.o November 09, 2011 CONTENTS 1 Adminhelp 3 2 Amazon 5 2.1 AWS branded scripts........................................... 5 2.2 SES SMTP relay.............................................
fragapy Documentation Release 1.0 2011, Fragaria, s.r.o November 09, 2011 CONTENTS 1 Adminhelp 3 2 Amazon 5 2.1 AWS branded scripts........................................... 5 2.2 SES SMTP relay.............................................
TPS Documentation. Release Thomas Roten
 TPS Documentation Release 0.1.0 Thomas Roten Sep 27, 2017 Contents 1 TPS: TargetProcess in Python! 3 2 Installation 5 3 Contributing 7 3.1 Types of Contributions..........................................
TPS Documentation Release 0.1.0 Thomas Roten Sep 27, 2017 Contents 1 TPS: TargetProcess in Python! 3 2 Installation 5 3 Contributing 7 3.1 Types of Contributions..........................................
pytest-benchmark Release 2.5.0
 pytest-benchmark Release 2.5.0 September 13, 2015 Contents 1 Overview 3 1.1 pytest-benchmark............................................ 3 2 Installation 7 3 Usage 9 4 Reference 11 4.1 pytest_benchmark............................................
pytest-benchmark Release 2.5.0 September 13, 2015 Contents 1 Overview 3 1.1 pytest-benchmark............................................ 3 2 Installation 7 3 Usage 9 4 Reference 11 4.1 pytest_benchmark............................................
Performance Evaluation of Tor Hidden Services
 University of Bamberg Distributed and Mobile Systems Group Paper on the Seminar Tor Research Topic: Performance Evaluation of Tor Hidden Services Presented by: Christian Wilms Supervisor: Karsten Loesing
University of Bamberg Distributed and Mobile Systems Group Paper on the Seminar Tor Research Topic: Performance Evaluation of Tor Hidden Services Presented by: Christian Wilms Supervisor: Karsten Loesing
WEBSHELL TO PHISHING UDURRANI
 WEBSHELL TO PHISHING UDURRANI SUMMARY: Attacker uploads the master webshell Attacker sets a password [ sha1(md5(password)) ] Attacker is able to load multiple modules including: { explorer", "terminal",
WEBSHELL TO PHISHING UDURRANI SUMMARY: Attacker uploads the master webshell Attacker sets a password [ sha1(md5(password)) ] Attacker is able to load multiple modules including: { explorer", "terminal",
Product Datasheet IPS Pager
 Product Datasheet IPS Pager Directory Phone Directory Jabber UDS Server Web Directory IPS Popup / Reverse Lookup Personal Directory H350 Video Conf directory Corporate Speed Dials ClickNDial Alerting Voice
Product Datasheet IPS Pager Directory Phone Directory Jabber UDS Server Web Directory IPS Popup / Reverse Lookup Personal Directory H350 Video Conf directory Corporate Speed Dials ClickNDial Alerting Voice
BlenderPanda Documentation. Release 0.1.0
 BlenderPanda Documentation Release 0.1.0 May 01, 2018 Contents 1 Getting Started 3 1.1 Installing BlenderPanda......................................... 3 1.2 Viewport Preview............................................
BlenderPanda Documentation Release 0.1.0 May 01, 2018 Contents 1 Getting Started 3 1.1 Installing BlenderPanda......................................... 3 1.2 Viewport Preview............................................
logstash-metlog extensions Documentation
 logstash-metlog extensions Documentation Release 0.1 Victor Ng October 06, 2016 Contents 1 logstash-metlog 1 1.1 Plugin Configuration........................................... 1 1.2 HDFS Configuration...........................................
logstash-metlog extensions Documentation Release 0.1 Victor Ng October 06, 2016 Contents 1 logstash-metlog 1 1.1 Plugin Configuration........................................... 1 1.2 HDFS Configuration...........................................
Unifer Documentation. Release V1.0. Matthew S
 Unifer Documentation Release V1.0 Matthew S July 28, 2014 Contents 1 Unifer Tutorial - Notes Web App 3 1.1 Setting up................................................. 3 1.2 Getting the Template...........................................
Unifer Documentation Release V1.0 Matthew S July 28, 2014 Contents 1 Unifer Tutorial - Notes Web App 3 1.1 Setting up................................................. 3 1.2 Getting the Template...........................................
Web Authentication Proxy Configuration Example
 Web Authentication Proxy Configuration Example Document ID: 116052 Contributed by Nick Tate, Cisco TAC Engineer. May 02, 2013 Contents Introduction Prerequisites Requirements Components Used Conventions
Web Authentication Proxy Configuration Example Document ID: 116052 Contributed by Nick Tate, Cisco TAC Engineer. May 02, 2013 Contents Introduction Prerequisites Requirements Components Used Conventions
Using git to circumvent censorship of access to the Tor network
 University of Amsterdam System & Network Engineering Using git to circumvent censorship of access to the Tor network July 24, 2013 Authors: Björgvin Ragnarsson Pieter Westein bjorgvin.ragnarsson@os3.nl
University of Amsterdam System & Network Engineering Using git to circumvent censorship of access to the Tor network July 24, 2013 Authors: Björgvin Ragnarsson Pieter Westein bjorgvin.ragnarsson@os3.nl
Biocomputing II Coursework guidance
 Biocomputing II Coursework guidance I refer to the database layer as DB, the middle (business logic) layer as BL and the front end graphical interface with CGI scripts as (FE). Standardized file headers
Biocomputing II Coursework guidance I refer to the database layer as DB, the middle (business logic) layer as BL and the front end graphical interface with CGI scripts as (FE). Standardized file headers
Contents: 1 Basic socket interfaces 3. 2 Servers 7. 3 Launching and Controlling Processes 9. 4 Daemonizing Command Line Programs 11
 nclib Documentation Release 0.7.0 rhelmot Apr 19, 2018 Contents: 1 Basic socket interfaces 3 2 Servers 7 3 Launching and Controlling Processes 9 4 Daemonizing Command Line Programs 11 5 Indices and tables
nclib Documentation Release 0.7.0 rhelmot Apr 19, 2018 Contents: 1 Basic socket interfaces 3 2 Servers 7 3 Launching and Controlling Processes 9 4 Daemonizing Command Line Programs 11 5 Indices and tables
Lessons learnt building Kubernetes controllers. David Cheney - Heptio
 Lessons learnt building Kubernetes controllers David Cheney - Heptio g day Contour A Kubernetes Ingress Controller Connaissez-vous Kubernetes? Kubernetes in one slide Replicated data store; etcd API
Lessons learnt building Kubernetes controllers David Cheney - Heptio g day Contour A Kubernetes Ingress Controller Connaissez-vous Kubernetes? Kubernetes in one slide Replicated data store; etcd API
Moodle Destroyer Tools Documentation
 Moodle Destroyer Tools Documentation Release 0.0.1 Manly Man Dec 22, 2017 With Web Services 1 Features and Screenshots 3 2 Grading with Webservices 7 2.1 Prerequisites...............................................
Moodle Destroyer Tools Documentation Release 0.0.1 Manly Man Dec 22, 2017 With Web Services 1 Features and Screenshots 3 2 Grading with Webservices 7 2.1 Prerequisites...............................................
How to Configure a Remote Management Tunnel for an F-Series Firewall
 How to Configure a Remote Management Tunnel for an F-Series Firewall If the managed NextGen Firewall F-Series cannot directly reach the NextGen Control Center, it must connect via a remote management tunnel.
How to Configure a Remote Management Tunnel for an F-Series Firewall If the managed NextGen Firewall F-Series cannot directly reach the NextGen Control Center, it must connect via a remote management tunnel.
Anonymity and censorship circumvention with Tor
 Anonymity and censorship circumvention with Tor Lunar July 8th, 2013 LSM2013, Brussels What is this Tor thing? Tor helps people Estimated 500,000 daily Tor users cf. https://metrics.torproject.org/users.html
Anonymity and censorship circumvention with Tor Lunar July 8th, 2013 LSM2013, Brussels What is this Tor thing? Tor helps people Estimated 500,000 daily Tor users cf. https://metrics.torproject.org/users.html
Lessons learnt building Kubernetes controllers. David Cheney - Heptio
 Lessons learnt building Kubernetes controllers David Cheney - Heptio g day Craig McLuckie and Joe Beda 2/3rds of a pod Connaissez-vous Kubernetes? Kubernetes is an open-source system for automating deployment,
Lessons learnt building Kubernetes controllers David Cheney - Heptio g day Craig McLuckie and Joe Beda 2/3rds of a pod Connaissez-vous Kubernetes? Kubernetes is an open-source system for automating deployment,
How to Deploy Virtual Test Agents in OpenStack
 How to Deploy Virtual Test Agents in OpenStack Executive Summary This guide explains how to deploy Netrounds Virtual Test Agents (vtas) in OpenStack and how to control these from Netrounds Control Center.
How to Deploy Virtual Test Agents in OpenStack Executive Summary This guide explains how to deploy Netrounds Virtual Test Agents (vtas) in OpenStack and how to control these from Netrounds Control Center.
Aimetis Symphony Mobile Bridge. 2.7 Installation Guide
 Aimetis Symphony Mobile Bridge 2.7 Installation Guide Contents Contents Introduction...3 Installation... 4 Install the Mobile Bridge... 4 Upgrade the Mobile Bridge...4 Network configuration... 4 Configuration...
Aimetis Symphony Mobile Bridge 2.7 Installation Guide Contents Contents Introduction...3 Installation... 4 Install the Mobile Bridge... 4 Upgrade the Mobile Bridge...4 Network configuration... 4 Configuration...
arxiv: v1 [cs.dc] 7 Apr 2014
![arxiv: v1 [cs.dc] 7 Apr 2014 arxiv: v1 [cs.dc] 7 Apr 2014](/thumbs/95/126042421.jpg) arxiv:1404.1814v1 [cs.dc] 7 Apr 2014 CernVM Online and Cloud Gateway: a uniform interface for CernVM contextualization and deployment G Lestaris 1, I Charalampidis 2, D Berzano, J Blomer, P Buncic, G Ganis
arxiv:1404.1814v1 [cs.dc] 7 Apr 2014 CernVM Online and Cloud Gateway: a uniform interface for CernVM contextualization and deployment G Lestaris 1, I Charalampidis 2, D Berzano, J Blomer, P Buncic, G Ganis
JupyterHub Documentation
 JupyterHub Documentation Release 0.4.0.dev Project Jupyter team January 30, 2016 User Documentation 1 Getting started with JupyterHub 3 2 Further reading 11 3 How JupyterHub works 13 4 Writing a custom
JupyterHub Documentation Release 0.4.0.dev Project Jupyter team January 30, 2016 User Documentation 1 Getting started with JupyterHub 3 2 Further reading 11 3 How JupyterHub works 13 4 Writing a custom
How to Configure a Remote Management Tunnel for Barracuda NG Firewalls
 How to Configure a Remote Management Tunnel for Barracuda NG Firewalls If the managed NG Firewall can not directly reach the NG Control Center it must connect via a remote management tunnel. The remote
How to Configure a Remote Management Tunnel for Barracuda NG Firewalls If the managed NG Firewall can not directly reach the NG Control Center it must connect via a remote management tunnel. The remote
Computer Networks - Midterm
 Computer Networks - Midterm October 30, 2015 Duration: 2h15m This is a closed-book exam Please write your answers on these sheets in a readable way, in English or in French You can use extra sheets if
Computer Networks - Midterm October 30, 2015 Duration: 2h15m This is a closed-book exam Please write your answers on these sheets in a readable way, in English or in French You can use extra sheets if
THE RMI PROXY USER GUIDE
 THE RMI PROXY USER GUIDE Copyright Telekinesis Pty Ltd, 2000, 2002. All rights reserved. 1 Introduction Java RMI allows Java programs executing within different Java Virtual Machines to communicate using
THE RMI PROXY USER GUIDE Copyright Telekinesis Pty Ltd, 2000, 2002. All rights reserved. 1 Introduction Java RMI allows Java programs executing within different Java Virtual Machines to communicate using
Surfing safely over the Tor anonymity network. Georg Koppen Philipp Winter
 Surfing safely over the Tor anonymity network Georg Koppen gk@torproject.org Philipp Winter phw@torproject.org How does Tor work? What are exit relays? Currently ~7,000 relays, ~1,000 are exits All run
Surfing safely over the Tor anonymity network Georg Koppen gk@torproject.org Philipp Winter phw@torproject.org How does Tor work? What are exit relays? Currently ~7,000 relays, ~1,000 are exits All run
GoCD Python API client Documentation
 GoCD Python API client Documentation Release 1.0.1 Grigory Chernyshev Dec 08, 2017 Contents 1 Intro 1 2 Contents: 3 2.1 Yet another GoCD python client..................................... 3 2.2 Usage...................................................
GoCD Python API client Documentation Release 1.0.1 Grigory Chernyshev Dec 08, 2017 Contents 1 Intro 1 2 Contents: 3 2.1 Yet another GoCD python client..................................... 3 2.2 Usage...................................................
Simple Jabber - Divide And Conquer XMPP
 Simple Jabber - Divide And Conquer XMPP Jan Klemkow 30.08.2015 Abstract The Extensible Messaging and Presence Protocol (XMPP) 1 is like the web. It is far too complex to be implemented in one program with
Simple Jabber - Divide And Conquer XMPP Jan Klemkow 30.08.2015 Abstract The Extensible Messaging and Presence Protocol (XMPP) 1 is like the web. It is far too complex to be implemented in one program with
Avaya AG250 Application Gateway Server Pre-Installation Checklist for Avaya Communication Manager
 Avaya AG250 Application Gateway Server Pre-Installation Checklist for Avaya Communication Manager The Application Gateway Server delivers business applications to Internet-enabled IP telephones, personal
Avaya AG250 Application Gateway Server Pre-Installation Checklist for Avaya Communication Manager The Application Gateway Server delivers business applications to Internet-enabled IP telephones, personal
Configuration Guide. BlackBerry UEM. Version 12.9
 Configuration Guide BlackBerry UEM Version 12.9 Published: 2018-07-16 SWD-20180713083904821 Contents About this guide... 8 Getting started... 9 Configuring BlackBerry UEM for the first time...9 Configuration
Configuration Guide BlackBerry UEM Version 12.9 Published: 2018-07-16 SWD-20180713083904821 Contents About this guide... 8 Getting started... 9 Configuring BlackBerry UEM for the first time...9 Configuration
IGMP Proxy. Finding Feature Information. Prerequisites for IGMP Proxy
 This module describes how to configure IGMP proxy to enable a device to send an IGMP report to a specified destination IP address. Finding Feature Information, page 1 Prerequisites for, page 1 Information
This module describes how to configure IGMP proxy to enable a device to send an IGMP report to a specified destination IP address. Finding Feature Information, page 1 Prerequisites for, page 1 Information
Dualog Connection Suite LDAP Server. User Manual and Configuration Guide
 Dualog Connection Suite LDAP Server User Manual and Configuration Guide Author Vidar Berg Date 10.Nov 2010 Description Revision Number User manual for setting up and maintaining the Dualog Connection Suite
Dualog Connection Suite LDAP Server User Manual and Configuration Guide Author Vidar Berg Date 10.Nov 2010 Description Revision Number User manual for setting up and maintaining the Dualog Connection Suite
txzmq Documentation Release Andrey Smirnov
 txzmq Documentation Release 0.8.0 Andrey Smirnov Apr 21, 2017 Contents 1 Installation 3 1.1 Requirements............................................... 3 1.2 MacOS X.................................................
txzmq Documentation Release 0.8.0 Andrey Smirnov Apr 21, 2017 Contents 1 Installation 3 1.1 Requirements............................................... 3 1.2 MacOS X.................................................
cget Documentation Release Paul Fultz II
 cget Documentation Release 0.1.0 Paul Fultz II Jun 27, 2018 Contents 1 Introduction 3 1.1 Installing cget.............................................. 3 1.2 Quickstart................................................
cget Documentation Release 0.1.0 Paul Fultz II Jun 27, 2018 Contents 1 Introduction 3 1.1 Installing cget.............................................. 3 1.2 Quickstart................................................
CSC Network Security
 CSC 474 -- Security Topic 9. Firewalls CSC 474 Dr. Peng Ning 1 Outline Overview of Firewalls Filtering Firewalls Proxy Servers CSC 474 Dr. Peng Ning 2 Overview of Firewalls CSC 474 Dr. Peng Ning 3 1 Internet
CSC 474 -- Security Topic 9. Firewalls CSC 474 Dr. Peng Ning 1 Outline Overview of Firewalls Filtering Firewalls Proxy Servers CSC 474 Dr. Peng Ning 2 Overview of Firewalls CSC 474 Dr. Peng Ning 3 1 Internet
Python wrapper for Viscosity.app Documentation
 Python wrapper for Viscosity.app Documentation Release Paul Kremer March 08, 2014 Contents 1 Python wrapper for Viscosity.app 3 1.1 Features.................................................. 3 2 Installation
Python wrapper for Viscosity.app Documentation Release Paul Kremer March 08, 2014 Contents 1 Python wrapper for Viscosity.app 3 1.1 Features.................................................. 3 2 Installation
Accessing an Extremely Secure LAN Via Remote Access That Was Not Possible With Previous Technologies
 Before, administrator rights were a necessity when setting up a remote access VPN. But by using the SecureNAT capability built in to SoftEther VPN Server and SoftEther VPN Bridge you can build a remote
Before, administrator rights were a necessity when setting up a remote access VPN. But by using the SecureNAT capability built in to SoftEther VPN Server and SoftEther VPN Bridge you can build a remote
Ftp Secure Connection Error Return Code 23
 Ftp Secure Connection Error Return Code 23 Sending the FTP server code 230 should establish a connection like it does when using the and if you get it call perror() or print an error made up with strerror(),
Ftp Secure Connection Error Return Code 23 Sending the FTP server code 230 should establish a connection like it does when using the and if you get it call perror() or print an error made up with strerror(),
Monitoring BGP. Configuring the Router
 You have to be extra careful if the prefix you want to announce over BGP is already present in the global routing table. This happens in the situation where your ISP announced your address block but you
You have to be extra careful if the prefix you want to announce over BGP is already present in the global routing table. This happens in the situation where your ISP announced your address block but you
Configuration Guide. BlackBerry UEM. Version 12.7 Maintenance Release 2
 Configuration Guide BlackBerry UEM Version 12.7 Maintenance Release 2 Published: 2017-12-04 SWD-20171130134721747 Contents About this guide... 8 Getting started... 9 Configuring BlackBerry UEM for the
Configuration Guide BlackBerry UEM Version 12.7 Maintenance Release 2 Published: 2017-12-04 SWD-20171130134721747 Contents About this guide... 8 Getting started... 9 Configuring BlackBerry UEM for the
The Parrot is Dead: Observing Unobservable Network Communications. Amir Houmansadr Chad Brubaker Vitaly Shmatikov
 The Parrot is Dead: Observing Unobservable Network Communications Amir Houmansadr Chad Brubaker Vitaly Shmatikov Internet Censorship The Internet is a big threat to repressive regimes! Repressive regimes
The Parrot is Dead: Observing Unobservable Network Communications Amir Houmansadr Chad Brubaker Vitaly Shmatikov Internet Censorship The Internet is a big threat to repressive regimes! Repressive regimes
Python Schema Generator Documentation
 Python Schema Generator Documentation Release 1.0.0 Peter Demin June 26, 2016 Contents 1 Mutant - Python code generator 3 1.1 Project Status............................................... 3 1.2 Design..................................................
Python Schema Generator Documentation Release 1.0.0 Peter Demin June 26, 2016 Contents 1 Mutant - Python code generator 3 1.1 Project Status............................................... 3 1.2 Design..................................................
Anonymous Communications
 Anonymous Communications Andrew Lewman andrew@torproject.org December 05, 2012 Andrew Lewman andrew@torproject.org () Anonymous Communications December 05, 2012 1 / 45 Who is this guy? 501(c)(3) non-profit
Anonymous Communications Andrew Lewman andrew@torproject.org December 05, 2012 Andrew Lewman andrew@torproject.org () Anonymous Communications December 05, 2012 1 / 45 Who is this guy? 501(c)(3) non-profit
Least-Privilege Isolation: The OKWS Web Server
 Least-Privilege Isolation: The OKWS Web Server Brad Karp UCL Computer Science CS GZ03 / M030 14 th December 2015 Can We Prevent All Exploits? Many varieties of exploits Stack smashing, format strings,
Least-Privilege Isolation: The OKWS Web Server Brad Karp UCL Computer Science CS GZ03 / M030 14 th December 2015 Can We Prevent All Exploits? Many varieties of exploits Stack smashing, format strings,
obfuscator Documentation
 obfuscator Documentation Release 1.1.5 Timothy McFadden July 17, 2015 Contents 1 Introduction 3 2 Install 5 3 Usage 7 4 Auto Generated API Documentation 9 4.1 obfuscator.file..............................................
obfuscator Documentation Release 1.1.5 Timothy McFadden July 17, 2015 Contents 1 Introduction 3 2 Install 5 3 Usage 7 4 Auto Generated API Documentation 9 4.1 obfuscator.file..............................................
Intercepting Web Requests
 This chapter contains the following sections: Overview of, on page 1 Tasks for, on page 1 Best Practices for, on page 2 Web Proxy Options for, on page 3 Client Options for Redirecting Web Requests, on
This chapter contains the following sections: Overview of, on page 1 Tasks for, on page 1 Best Practices for, on page 2 Web Proxy Options for, on page 3 Client Options for Redirecting Web Requests, on
Application Notes for Configuring Telcomp Pickup and Avaya IP Office using DevLink - Issue 1.0
 Avaya Solution & Interoperability Test Lab Application Notes for Configuring Telcomp Pickup and Avaya IP Office using DevLink - Issue 1.0 Abstract These Application Notes describe the procedure for configuring
Avaya Solution & Interoperability Test Lab Application Notes for Configuring Telcomp Pickup and Avaya IP Office using DevLink - Issue 1.0 Abstract These Application Notes describe the procedure for configuring
As a programmer, you know how easy it can be to get lost in the details
 Chapter 1 Congratulations, Your Problem Has Already Been Solved In This Chapter Introducing design patterns Knowing how design patterns can help Extending object-oriented programming Taking a look at some
Chapter 1 Congratulations, Your Problem Has Already Been Solved In This Chapter Introducing design patterns Knowing how design patterns can help Extending object-oriented programming Taking a look at some
Django Better Cache Documentation
 Django Better Cache Documentation Release 0.7.0 Calvin Spealman February 04, 2016 Contents 1 Table of Contents 3 1.1 bettercache template tags......................................... 3 1.2 CacheModel...............................................
Django Better Cache Documentation Release 0.7.0 Calvin Spealman February 04, 2016 Contents 1 Table of Contents 3 1.1 bettercache template tags......................................... 3 1.2 CacheModel...............................................
Operating Systems. 18. Remote Procedure Calls. Paul Krzyzanowski. Rutgers University. Spring /20/ Paul Krzyzanowski
 Operating Systems 18. Remote Procedure Calls Paul Krzyzanowski Rutgers University Spring 2015 4/20/2015 2014-2015 Paul Krzyzanowski 1 Remote Procedure Calls 2 Problems with the sockets API The sockets
Operating Systems 18. Remote Procedure Calls Paul Krzyzanowski Rutgers University Spring 2015 4/20/2015 2014-2015 Paul Krzyzanowski 1 Remote Procedure Calls 2 Problems with the sockets API The sockets
Django FTP server Documentation
 Django FTP server Documentation Release 0.5.0 Shinya Okano Oct 30, 2017 Contents 1 Django FTP server 3 1.1 Getting Started.............................................. 3 1.2 Requirements...............................................
Django FTP server Documentation Release 0.5.0 Shinya Okano Oct 30, 2017 Contents 1 Django FTP server 3 1.1 Getting Started.............................................. 3 1.2 Requirements...............................................
VSTHost Slavery Suite
 VSTHost Slavery Suite Slave Mode Add-Ons for VSTHost Version 1.09 Copyright 2005-2018 by Hermann Seib Download Information The latest versions of VSTHost and the VSTHost Slavery Suite can be found at http://www.hermannseib.com/english/vsthost.htm
VSTHost Slavery Suite Slave Mode Add-Ons for VSTHost Version 1.09 Copyright 2005-2018 by Hermann Seib Download Information The latest versions of VSTHost and the VSTHost Slavery Suite can be found at http://www.hermannseib.com/english/vsthost.htm
Caller dialled digit during recording. Fax routing Config? Yes. Route to Fax Extensions
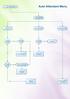 Auto Attendant Menu Caller dialled digit during recording Digits 0-7 Fax tone detected selection is made 2nd digit present Single Digit Config Fax routing Config? Ignore Fax Route to Extensions Route to
Auto Attendant Menu Caller dialled digit during recording Digits 0-7 Fax tone detected selection is made 2nd digit present Single Digit Config Fax routing Config? Ignore Fax Route to Extensions Route to
Using PowerOn Auto Provisioning
 This chapter describes how to deploy and use PowerOn Auto Provisioning (POAP) This chapter contains the following sections: Information About PowerOn Auto Provisioning, page 1 Guidelines and Limitations
This chapter describes how to deploy and use PowerOn Auto Provisioning (POAP) This chapter contains the following sections: Information About PowerOn Auto Provisioning, page 1 Guidelines and Limitations
PyZabbixObj Documentation
 PyZabbixObj Documentation Release 0.1 Fabio Toscano Aug 26, 2017 Contents Python Module Index 3 i ii PyZabbixObj Documentation, Release 0.1 PyZabbixObj is a Python module for working with Zabbix API,
PyZabbixObj Documentation Release 0.1 Fabio Toscano Aug 26, 2017 Contents Python Module Index 3 i ii PyZabbixObj Documentation, Release 0.1 PyZabbixObj is a Python module for working with Zabbix API,
Building Large Scale Distributed Systems with AMQP. Ted Ross
 Building Large Scale Distributed Systems with AMQP Ted Ross tross@apache.org Agenda What is AMQP? Why is AMQP important to large distributed enterprises? How is the Apache Community making AMQP a reality?
Building Large Scale Distributed Systems with AMQP Ted Ross tross@apache.org Agenda What is AMQP? Why is AMQP important to large distributed enterprises? How is the Apache Community making AMQP a reality?
Peer to Peer Instant Messaging
 Peer to Peer Instant Messaging Assignment in Computer Networks I, Department of Information Technology, Uppsala University. Overview In this assignment you will implement an instant messaging system that
Peer to Peer Instant Messaging Assignment in Computer Networks I, Department of Information Technology, Uppsala University. Overview In this assignment you will implement an instant messaging system that
utidylib Documentation Release 0.4
 utidylib Documentation Release 0.4 Michal Čihař Nov 01, 2018 Contents 1 Installing 3 2 Contributing 5 3 Running testsuite 7 4 Building documentation 9 5 License 11 6 Changes 13 6.1 0.5....................................................
utidylib Documentation Release 0.4 Michal Čihař Nov 01, 2018 Contents 1 Installing 3 2 Contributing 5 3 Running testsuite 7 4 Building documentation 9 5 License 11 6 Changes 13 6.1 0.5....................................................
Install and Configure the TS Agent
 Install or Upgrade the TS Agent, page 1 Start the TS Agent Configuration Interface, page 2 Configure the TS Agent, page 2 Creating the REST VDI Role, page 7 Install or Upgrade the TS Agent Before You Begin
Install or Upgrade the TS Agent, page 1 Start the TS Agent Configuration Interface, page 2 Configure the TS Agent, page 2 Creating the REST VDI Role, page 7 Install or Upgrade the TS Agent Before You Begin
502 / 504 GATEWAY_TIMEOUT errors when browsing to certain sites
 502 / 504 GATEWAY_TIMEOUT errors when browsing to certain sites Document ID: 118079 Contributed by Vladimir Sousa and Siddharth Rajpathak, Cisco TAC Engineers. Jul 25, 2014 Contents Question: Question:
502 / 504 GATEWAY_TIMEOUT errors when browsing to certain sites Document ID: 118079 Contributed by Vladimir Sousa and Siddharth Rajpathak, Cisco TAC Engineers. Jul 25, 2014 Contents Question: Question:
bootmachine Documentation
 bootmachine Documentation Release 0.6.0 Thomas Schreiber April 20, 2015 Contents 1 bootmachine 3 1.1 Configuration Management Tools.................................... 3 1.2 Providers.................................................
bootmachine Documentation Release 0.6.0 Thomas Schreiber April 20, 2015 Contents 1 bootmachine 3 1.1 Configuration Management Tools.................................... 3 1.2 Providers.................................................
SECURECOMM. JumpBox A Seamless Browser Proxy for Tor Pluggable Transports. Jeroen Massar, Farsight Security, Inc. IPv6 Golden Networks
 SECURECOMM 26 September 2014 Beijing Yulong International Hotel, Beijing, China JumpBox A Seamless Browser Proxy for Tor Pluggable Transports Jeroen Massar, Farsight Security, Inc. massar@fsi.io Ian Mason,
SECURECOMM 26 September 2014 Beijing Yulong International Hotel, Beijing, China JumpBox A Seamless Browser Proxy for Tor Pluggable Transports Jeroen Massar, Farsight Security, Inc. massar@fsi.io Ian Mason,
StratumGS Documentation
 StratumGS Documentation Release 0.1.0 Dave Korhumel May 14, 2016 Contents 1 Documentation 3 1.1 Design.................................................. 3 1.2 Guides..................................................
StratumGS Documentation Release 0.1.0 Dave Korhumel May 14, 2016 Contents 1 Documentation 3 1.1 Design.................................................. 3 1.2 Guides..................................................
Challenges in building overlay networks: a case study of Tor. Steven Murdoch Principal Research Fellow University College London
 Challenges in building overlay networks: a case study of Steven Murdoch Principal Research Fellow University College London Who uses? Ordinary people e.g. to avoid unscrupulous marketers, protect children,
Challenges in building overlay networks: a case study of Steven Murdoch Principal Research Fellow University College London Who uses? Ordinary people e.g. to avoid unscrupulous marketers, protect children,
Poetaster. Release 0.1.1
 Poetaster Release 0.1.1 September 21, 2016 Contents 1 Overview 1 1.1 Installation................................................ 1 1.2 Documentation.............................................. 1 1.3
Poetaster Release 0.1.1 September 21, 2016 Contents 1 Overview 1 1.1 Installation................................................ 1 1.2 Documentation.............................................. 1 1.3
Azrael Documentation. Release 0.2. Oliver Nagy
 Azrael Documentation Release 0.2 Oliver Nagy January 29, 2016 Contents 1 Overview 3 1.1 Philosophy................................................ 3 1.2 Architecture...............................................
Azrael Documentation Release 0.2 Oliver Nagy January 29, 2016 Contents 1 Overview 3 1.1 Philosophy................................................ 3 1.2 Architecture...............................................
pylog Documentation Release nir0s
 pylog Documentation Release 0.1.4 nir0s August 03, 2014 Contents 1 Quick Start 3 2 Installation 5 3 CLI 7 4 Configuration 9 5 Advanced Configuration 11 6 Formatters 13 7 Transports 15 8 API 17 9 Indices
pylog Documentation Release 0.1.4 nir0s August 03, 2014 Contents 1 Quick Start 3 2 Installation 5 3 CLI 7 4 Configuration 9 5 Advanced Configuration 11 6 Formatters 13 7 Transports 15 8 API 17 9 Indices
Operating-System Structures
 Operating-System Structures Chapter 2 Operating System Services One set provides functions that are helpful to the user: User interface Program execution I/O operations File-system manipulation Communications
Operating-System Structures Chapter 2 Operating System Services One set provides functions that are helpful to the user: User interface Program execution I/O operations File-system manipulation Communications
Secure Communications Over a Network
 Secure Communications Over a Network Course: MITS:5400G Proffessor: Dr. Xiaodong Lin By: Geoff Vaughan 100309160 March 20th 2012 Abstract The purpose of this experiment is to transmit an encrypted message
Secure Communications Over a Network Course: MITS:5400G Proffessor: Dr. Xiaodong Lin By: Geoff Vaughan 100309160 March 20th 2012 Abstract The purpose of this experiment is to transmit an encrypted message
python-quirc Documentation
 python-quirc Documentation Release 0.8.0 SvartalF May 27, 2012 CONTENTS 1 Install 3 1.1 Requirements............................................... 3 2 Usage 5 2.1 High-level API..............................................
python-quirc Documentation Release 0.8.0 SvartalF May 27, 2012 CONTENTS 1 Install 3 1.1 Requirements............................................... 3 2 Usage 5 2.1 High-level API..............................................
DIALUP ISP Connection in NetWare 4.x, 5.x and BorderManager.
 DIALUP ISP Connection in NetWare 4.x, 5.x and BorderManager. Beta version 1.0, Friday, March 09, 2001 Craig Johnson As long as you have the MPR (multi-protocol router) modules installed for NetWare (comes
DIALUP ISP Connection in NetWare 4.x, 5.x and BorderManager. Beta version 1.0, Friday, March 09, 2001 Craig Johnson As long as you have the MPR (multi-protocol router) modules installed for NetWare (comes
Lisa User Day Efficient use of file systems. John Donners
 Lisa User Day 2011 Efficient use of file systems John Donners John.Donners@sara.nl What filesystems are available? home directory scratch directory archive on request: global scratch directory DO NOT use
Lisa User Day 2011 Efficient use of file systems John Donners John.Donners@sara.nl What filesystems are available? home directory scratch directory archive on request: global scratch directory DO NOT use
(S//REL) Open Source Multi-Hop Networks
 TOP SECRET//SI/IRELTO USA,FVEY (C//REL) Types ofiat- Advanced Open Source Multi-Hop (S//REL) Open Source Multi-Hop Networks (S//REL) Tor (S//REL) Very widely used worldwide (S//REL) Open Source (S//REL)
TOP SECRET//SI/IRELTO USA,FVEY (C//REL) Types ofiat- Advanced Open Source Multi-Hop (S//REL) Open Source Multi-Hop Networks (S//REL) Tor (S//REL) Very widely used worldwide (S//REL) Open Source (S//REL)
diceware Documentation
 diceware Documentation Release 0.1 Uli Fouquet March 28, 2015 Contents 1 Install 3 2 Usage 5 3 What is it good for? 7 4 Is it secure? 9 5 Developer Install 11 5.1 Documentation Install..........................................
diceware Documentation Release 0.1 Uli Fouquet March 28, 2015 Contents 1 Install 3 2 Usage 5 3 What is it good for? 7 4 Is it secure? 9 5 Developer Install 11 5.1 Documentation Install..........................................
Socket Programming. Omer Ozarslan
 Socket Programming Omer Ozarslan omer@utdallas.edu 1 Outline Background Using TCP Example: hello_tcp Using UDP Example: hello_udp Blocking Calls and Threads Some Advises Code Examples Questions 2 Socket
Socket Programming Omer Ozarslan omer@utdallas.edu 1 Outline Background Using TCP Example: hello_tcp Using UDP Example: hello_udp Blocking Calls and Threads Some Advises Code Examples Questions 2 Socket
chatterbot-weather Documentation
 chatterbot-weather Documentation Release 0.1.1 Gunther Cox Nov 23, 2018 Contents 1 chatterbot-weather 3 1.1 Installation................................................ 3 1.2 Example.................................................
chatterbot-weather Documentation Release 0.1.1 Gunther Cox Nov 23, 2018 Contents 1 chatterbot-weather 3 1.1 Installation................................................ 3 1.2 Example.................................................
CLIENT SERVER SYNERGY USING VPN
 CLIENT SERVER SYNERGY USING VPN 1 CHETAN S MORE, 2 AMAN ANNAD, 3 KUSHAGRA RAIZADA, 4 MANUJ SRIVASTAVA 1,2,3,4 Department of Electronics and Telecommunication Engineering, Bharati Vidyapeeth (Deemed To
CLIENT SERVER SYNERGY USING VPN 1 CHETAN S MORE, 2 AMAN ANNAD, 3 KUSHAGRA RAIZADA, 4 MANUJ SRIVASTAVA 1,2,3,4 Department of Electronics and Telecommunication Engineering, Bharati Vidyapeeth (Deemed To
MySip.ch. SIP Network Address Translation (NAT) SIP Architecture with NAT Version 1.0 SIEMENS SCHWEIZ AKTIENGESELLSCHAFT
 s MySip.ch SIP Network Address Translation () SIP Architecture with Version 1.0 Issued by DS MS, Software house Albisriederstr. 245, CH-8047 Zurich Copyright Siemens Schweiz AG 2004 All Rights Reserved.
s MySip.ch SIP Network Address Translation () SIP Architecture with Version 1.0 Issued by DS MS, Software house Albisriederstr. 245, CH-8047 Zurich Copyright Siemens Schweiz AG 2004 All Rights Reserved.
OSM R1 - VNF PACKAGE CREATION, UI & ONBOARDING
 OSM R1 - VNF PACKAGE CREATION, UI & ONBOARDING Noel Charath (RIFT.io) OSM R1- VNF PACKAGE CREATION AND ON-BOARDING RX10033 GETTING STARTED WITH OSM R1 INSTALL OSM R1 CREATE VNF & NS PACKAGES ONBOARD VNF
OSM R1 - VNF PACKAGE CREATION, UI & ONBOARDING Noel Charath (RIFT.io) OSM R1- VNF PACKAGE CREATION AND ON-BOARDING RX10033 GETTING STARTED WITH OSM R1 INSTALL OSM R1 CREATE VNF & NS PACKAGES ONBOARD VNF
