Accessing an Extremely Secure LAN Via Remote Access That Was Not Possible With Previous Technologies
|
|
|
- Marcus Shields
- 5 years ago
- Views:
Transcription
1 Before, administrator rights were a necessity when setting up a remote access VPN. But by using the SecureNAT capability built in to SoftEther VPN Server and SoftEther VPN Bridge you can build a remote access VPN that does not require administrator rights but retains all of the same functionality. This section will explain how to use SecureNAT to enable you to access your LAN from a remote location Utilizing SecureNAT to Make Things More Convenient About SecureNAT As explained in section 3.7 Virtual NAT & Virtual DHCP Servers, SecureNAT consists of the TCP/IP stack operated in user mode and Virtual NAT/Virtual DHCP Server. In particular, when IP access via Virtual NAT is performed the data is automatically relayed to the host using Socket API at the user level. This is a very advanced and intriguing technology. Accessing an Extremely Secure LAN Via Remote Access That Was Not Possible With Previous Technologies As explained in section 10.4 Build a Generic Remote Access VPN, to set up a VPN to allow remote access to an existing LAN from a remote location you must first install VPN Server on the LAN you wish to connect to remotely. In addition, that VPN Server must be able to be seen from the Internet. Finally, use local bridging to connect the Virtual Hub to the physical LAN and your remote access VPN is complete. This type of configuration will allow you to connect to an existing LAN remotely, but you will need system administrator (or network administrator) rights to complete the set-up in the following two locations: 1. When using the local bridge functionality to make a bridged connection between the Virtual Hub and the existing LAN you will need system privileges or administrator rights on the computer you install VPN Server to in order to execute the vpnserver process in service mode or user mode. 2. To enable access to the VPN Server from the Internet you will need to have a global IP address or configure your NAT or firewall to enable port forwarding to your VPN Server. You will need network administrator privileges to perform this configuration. Therefore, if you want to enable secure and easy remote access to a device you have installed or are managing on a LAN, you will not be able to use VPN Server to set up a remote access VPN server as you would normally because you will need both system administrator and network administrator privileges on that LAN Using SecureNAT For Amazingly Simple, Secure Remote Access With No Administrator Rights Your network environment must meet the following criteria to set up a remote access VPN using SecureNAT. Please refer to section 3.7 Virtual NAT & Virtual DHCP Servers for more information about the SecureNAT functionality.? There must be a computer running Windows, Linux, FreeBSD, Solaris, or Mac OS X that you can log on to as at least a general user on the LAN you wish to connect to remotely.? Also, you should receive confirmation from your network or system administrator that it is OK to access the LAN remotely before you begin setting up anything. Normally, a LAN that meets the above conditions but consists of private IP addresses behind a NAT, firewall, or proxy server can not be connected to from outside the network. However, by utilizing the 1
2 revolutionary new SecureNAT technology available only with SoftEther VPN you will be able to connect to even this type of network freely and securely from a remote location A Practical Example Network Network Layout Example In order to make the explanation in this section easier to understand, the method described here is for the sample network layout shown in the image below. Network Layout. First, there is a very secure network protected by a firewall or NAT that can not be accessed from the Internet. For this example, the network's IP address is /24. However, web sites can be viewed on the network by routing traffic through the firewall or NAT proxy server first. Also, the computer at IP address is running Linux, although any other operating system that will run VPN Bridge such as Windows or Solaris is also acceptable. Assume that you do not have root access to this computer, but can log on to it as a general user. There is also a laser printer connected to the network at that needs to be maintained. Purpose The reasons for using SecureNAT in the example network layout above are the following:? You will be able to perform remote maintenance on the laser printer at on the network /24 which normally blocks all connections from the Internet. 2
3 ? If you explain to the administrator of /24 the situation and receive permission to set up such a VPN, but are worried about costs or the difficulty of changing the network's firewall settings, you can still set up the VPN without modifying the firewall. Now we will explain in detail how to perform remote maintenance on the laser printer at once you have reached this point in setting up the VPN. Preliminary Preparation The computer you set up with VPN Server beforehand at the IP address is the VPN Server computer. Create a Virtual Hub on this VPN Server (the default Virtual Hub "DEFAULT" will do) and create a user so that you can connect to that Virtual Hub later through VPN Bridge (assume you make the user "test" with password authentication for this example). Please refer to section 3. SoftEther VPN Server Manual for more information about configuring VPN Server Starting Up VPN Bridge on the Remote LAN Configuring and Starting Up VPN Bridge First, you will need to physically visit the remote LAN (in this case, the LAN that contains the laser printer for remote maintenance at ) at least once for the initial configuration process. What you will need to do here is to log in as a general user to the Linux computer with the IP address and install SoftEther VPN Bridge. VPN Bridge is free to use if you just want to use it to connect to VPN Server. After unpacking the VPN Bridge Linux install package's tar.gz file and installing VPN Bridge on the computer at , the executable file vpnbridge will be created. Assuming that you can only log on to as a general user, you will have to run VPN Bridge in user mode. As shown below, run vpnbridge with the start option. Please refer to section 5.2 Operating Modes for more detailed configuration information. $./vpnbridge start This will launch VPN Bridge on the computer at To launch VPN Bridge under Windows, use the /usermode option, not the start option. Beginning the Initial Configuration of VPN Bridge Next you will configure VPN Bridge using VPN Server Manager or the command line management utility vpncmd. If there is a Windows machine elsewhere on the network but an explanation is not given on how to configure something with VPN Server Manager, you can perform the same methods as described for vpncmd on a UNIX machine. Please refer to section 6. Command Line Management Utility Manual for more information about vpncmd. First, launch VPN Server Manager. 3
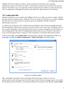
4 VPN Server Manager. Next, when you click [Create New Setting], the [Create New Connection Setting] window will appear. In the [Host Name] field of this window, input , the IP address of the computer you ran VPN Bridge on earlier. Click [OK]. 4
5 Creating a VPN Bridge Connection Configuration. If you double-click the connection configuration you just made, an administrative connection will be made to the VPN Bridge and the administration window will be displayed. If this is the first time you have connected to the VPN Bridge, a message asking you if you would like to set an administrator password will appear. Set a password at this time. 5
6 Connection to the VPN Bridge Completed. Enabling SecureNAT Clicking the [Manage Virtual Hub] button on the administration window will display a window labeled [Management of Virtual Hub - 'BRIDGE']. 6
7 The Virtual Hub Administration Window. On this window, click the [Virtual NAT and Virtual DHCP Server (SecureNAT)] button. This will display the [Virtual NAT and Virtual DHCP Function (SecureNAT) Setting] window. After reading the notices on this window carefully, click the [Enable SecureNAT] button. 7
8 Enabling SecureNAT. Now click the [Exit] button. This will take you back to the [Management of Virtual Hub - 'BRIDGE'] window. Configuring the Cascade Connection to the VPN Server On the Internet Next click the [Manage Cascade Connections] button. Then click [Create]. A window labeled [New VPN Connection Setting Properties] such as the one below will be displayed. 8
9 Configuring the Cascade Connection to the VPN Server On the Internet. You will input the following items in the [New VPN Connection Setting Properties] window:? [Setting Name] Designate some arbitrary name such as "Bridge".? [Host Name] Input the IP address of the computer that you installed VPN Server on beforehand. (In this example, )? [Port Number] Input one of the listener ports of the computer that you installed VPN Server on beforehand. We recommend using port number 443 if you have to go through any firewalls or proxy servers.? [Virtual Hub Name] Input the name of the Virtual Hub you created on the VPN Server beforehand.? Proxy Server Related Items If you must go through a HTTP proxy server or SOCKS proxy server to access the Internet on the /24 network, you would enter all the information about that proxy server here. (See section 4.4 Making Connection to VPN Server.)? [Auth Type] Input the authentication method used for the user registered to the Virtual Hub (in this example, 9
10 the user "test") on the computer that you installed VPN Server to beforehand. "Standard Password Authentication" should be sufficient under any normal circumstances.? [User Name] Input the user name of the user registered to the Virtual Hub (in this example, the user "test") on the computer that you installed VPN server to beforehand.? [Password] Input the password of the user registered to the Virtual Hub (the one you registered beforehand). After you have entered all the necessary information, click [OK]. This will take you back to the [Cascade connection on Bridge] window. The connection configuration you just created should be shown in the cascade connection list. Starting the Cascade Connection Now, click the new connection configuration you just created and click the [Online] button. If, after a few moments, the connection status changes to [Online (Connection Established)] then a connection has successfully been made to the Virtual Hub on the VPN Server you set up on the Internet. If an error message is displayed look up the details of the error and solve the problem. Once you have finished all the configuration and the cascade connection has successfully established a connection, close VPN Server Manager. Now you have completed all the necessary configuration on the remote LAN ( /24) Using Remote Access Now that you have completed all the configuration, you will be able to access the /24 network anywhere on the Internet through the computer running VPN Bridge. Now you can make a connection from VPN Client on a computer that is connected to the Internet to the VPN Server (in this example, ). That computer will then be connected as a single segment to the remote network via the SecureNAT Virtual NAT and Virtual DHCP Server functionality of the VPN Bridge ( ) you set up earlier on the VPN Server's Virtual Hub. Therefore, the VPN Client's Virtual Network Adapter will automatically receive a private IP address to be able to communicate only with computers on the network at /24 from the Virtual DHCP Server. The default gateway will also automatically be set to the SecureNAT's Virtual Host. This makes it possible to perform TCP/IP packet communication on the network that VPN Bridge is running on via the SecureNAT functionality enabled on that VPN Bridge. 10
11 Remote Access Via SecureNAT. Once you have confirmed that you have received an IP address via SecureNAT running on the VPN Bridge, you should now check to see if you can connect to and communicate with the laser printer at as if you were physically on the network. This communication is entirely handled by the Virtual NAT functionality running on the VPN Bridge. The user mode TCP/IP stack automatically performs all accesses using streamed Socket API, communicates with the physical host with user mode privileges only, and receives those results. Keep in mind that the Virtual NAT provided by the VPN Bridge on the remote network will be the default gateway to the VPN client computer in order to successfully allow remote access to that network. Therefore, when connected to the VPN any access to the Internet will not be directly performed by the client computer, but will instead be routed through the remote network. (If the remote network is another company's network, you should be especially careful as any Internet communication may be read or manipulated by a third party due to the information being routed through the remote network.) 11
12 Packet Flow When Accessing the Internet Via SecureNAT SecureNAT and Security A remote access VPN that combines VPN Bridge and SecureNAT such as the one in this example has the following security benefits:? SecureNAT utilizes many complicated techniques such as user mode TCP/IP stacks, but all processes required by SecureNAT can be executed in user mode. Therefore, in a network such as the example network given here where VPN Bridge is running under general user privileges, only processes that can be executed under that user's privileges can be performed, even if a buffer overflow or other such error occurs in VPN Bridge's or SecureNAT's program code. This means that, compared to a setup which requires VPN Bridge to be run under system privileges, one that runs under general user privileges has increased overall system integrity.? Of course, even when setting up a remote access VPN such as the one in this example that uses a combination of VPN Bridge with SecureNAT and VPN Server, all data under the SoftEther VPN protocol is encrypted via SSL by default. Even if you are sending data over the Internet, you will not have to worry about any third parties stealing or modifying the data you are transferring. You can also use server certificate authentication when making a cascade connection to the VPN Server (see section 3.4 Virtual Hub Functions for more details) to increase the security of your VPN even further.? This example shows how to set up a remote access VPN without having to change any of the firewall or NAT settings on the remote network. Generally, making modifications to a firewall or NAT to allow traffic to pass through certain ports can not only be a costly procedure, but can introduce new security risks to your network as well. Therefore, this method is not recommended unless you have absolutely no other choice. If you have a similar situation where you have received permission from the network or system administrator to set up a remote access VPN, but there is concern over the cost, security risks, or firewall/nat configuration, the method given in this 12
13 example of using SecureNAT and VPN Bridge together offers a simple, cost effective solution for your remote access needs.? All traffic that passes through SecureNAT is accurately logged in the security log file of the Virtual Hub on the VPN Bridge (or VPN Server) running SecureNAT The Dangers of Misusing SecureNAT As explained above, you now know that by using SecureNAT with VPN Bridge and VPN Server and running the proper software ahead of time you can connect to any network that has access to the Internet from the Internet remotely. Before the new technology introduced in SoftEther VPN, it was very difficult to set up a Virtual Hub with SecureNAT that could communicate with a physical network. However, be aware that mistakes made when using or configuring SecureNAT can lead to large security holes in your network. If you are thinking of setting up a network such as the one in this example that allows for remote access via VPN technology, please explain everything to your network or system administrator and get their permission beforehand. If you do not understand the principles behind SecureNAT, or are not familiar with TCP/IP or NAT in general, you should not use the SecureNAT functionality. Due to potential security hazards do not use SecureNAT in the following ways:? Do not make a network remotely accessible with general user privileges without receiving permission from the network administrator beforehand.? Do not install VPN Bridge with SecureNAT enabled on a computer managed by someone else (such as at a company, university, Internet cafe, government office, airport, or other public place) and then access the Internet from home using that computer as a stepping stone without obtaining permission to do so beforehand.? Do not install/configure VPN Bridge with SecureNAT enabled on an internal office network with the intention of illegally accessing that network from outside the office at a later time.? Do not use it on a network for any other reason without obtaining permission from the network or system administrator or someone who has administrator privileges on that network beforehand. All of the methods of use described above could be illegal under certain circumstances. 13
14 Forbidden Usages of SecureNAT. 14
SoftEther VPN Server supports the clustering function. This section explains the clustering function.
 SoftEther VPN Server supports the clustering function. This section explains the clustering function. 3.9.1 What is Clustering? Clustering Necessity In general terms, clustering is a processing method
SoftEther VPN Server supports the clustering function. This section explains the clustering function. 3.9.1 What is Clustering? Clustering Necessity In general terms, clustering is a processing method
Setup L2TP/IPsec VPN Server on SoftEther VPN Server
 Setup L2TP/IPsec VPN Server on SoftEther VPN Server The IPsec VPN Server Function is disabled by default. You can enable it easily as the following steps. Configuration Guide The VPN Server configuration
Setup L2TP/IPsec VPN Server on SoftEther VPN Server The IPsec VPN Server Function is disabled by default. You can enable it easily as the following steps. Configuration Guide The VPN Server configuration
5. Easy Installation and Management
 5. Easy Installation and Management 5.1. Provided as Software Programs SoftEther VPN is not a hardware VPN product. You can download it and install it today on your computer. If you want to try SoftEther
5. Easy Installation and Management 5.1. Provided as Software Programs SoftEther VPN is not a hardware VPN product. You can download it and install it today on your computer. If you want to try SoftEther
Create New Virtual Hub window.
 SoftEther VPN Server makes it possible to create a plurality of Virtual Hubs, and to separate administration objects and VPN session layer 2 communication between each Virtual Hub. This manual explains
SoftEther VPN Server makes it possible to create a plurality of Virtual Hubs, and to separate administration objects and VPN session layer 2 communication between each Virtual Hub. This manual explains
1.4 VPN Processing Principle and Communication Method
 This section contains a description of operation principle and communication method of VPN that can be constructed by SoftEther VPN. An overview of the modules and functions that was used by VPN communications.
This section contains a description of operation principle and communication method of VPN that can be constructed by SoftEther VPN. An overview of the modules and functions that was used by VPN communications.
How to Configure Mobile VPN for Forcepoint NGFW TECHNICAL DOCUMENT
 How to Configure Mobile VPN for Forcepoint NGFW TECHNICAL DOCUMENT Table of Contents TABLE OF CONTENTS 1 BACKGROUND 2 WINDOWS SERVER CONFIGURATION STEPS 2 CONFIGURING USER AUTHENTICATION 3 ACTIVE DIRECTORY
How to Configure Mobile VPN for Forcepoint NGFW TECHNICAL DOCUMENT Table of Contents TABLE OF CONTENTS 1 BACKGROUND 2 WINDOWS SERVER CONFIGURATION STEPS 2 CONFIGURING USER AUTHENTICATION 3 ACTIVE DIRECTORY
1. Ultimate Powerful VPN Connectivity
 1.1. Firewall, Proxy and NAT Transparency One of the key features of SoftEther VPN is the transparency for firewalls, proxy servers and NATs (Network Address Translators). NATs are sometimes implemented
1.1. Firewall, Proxy and NAT Transparency One of the key features of SoftEther VPN is the transparency for firewalls, proxy servers and NATs (Network Address Translators). NATs are sometimes implemented
WIALAN Technologies, Inc. Unit Configuration Thursday, March 24, 2005 Version 1.1
 WIALAN Technologies, Inc. Unit Configuration Thursday, March 24, 2005 Version 1.1 Table of Content I. Introduction...3 II. Logging into WiSAP... 3 III. WiSAP Overview... 5 Splash Screen... 5 System Status...
WIALAN Technologies, Inc. Unit Configuration Thursday, March 24, 2005 Version 1.1 Table of Content I. Introduction...3 II. Logging into WiSAP... 3 III. WiSAP Overview... 5 Splash Screen... 5 System Status...
CyberP3i Course Module Series
 CyberP3i Course Module Series Spring 2017 Designer: Dr. Lixin Wang, Associate Professor Firewall Configuration Firewall Configuration Learning Objectives 1. Be familiar with firewalls and types of firewalls
CyberP3i Course Module Series Spring 2017 Designer: Dr. Lixin Wang, Associate Professor Firewall Configuration Firewall Configuration Learning Objectives 1. Be familiar with firewalls and types of firewalls
Networking interview questions
 Networking interview questions What is LAN? LAN is a computer network that spans a relatively small area. Most LANs are confined to a single building or group of buildings. However, one LAN can be connected
Networking interview questions What is LAN? LAN is a computer network that spans a relatively small area. Most LANs are confined to a single building or group of buildings. However, one LAN can be connected
Features of a proxy server: - Nowadays, by using TCP/IP within local area networks, the relaying role that the proxy
 Que: -Proxy server Introduction: Proxy simply means acting on someone other s behalf. A Proxy acts on behalf of the client or user to provide access to a network service, and it shields each side from
Que: -Proxy server Introduction: Proxy simply means acting on someone other s behalf. A Proxy acts on behalf of the client or user to provide access to a network service, and it shields each side from
Advanced option settings on the command line. Set the interface and ports for the OpenVPN daemons
 Advanced option settings on the command line docs.openvpn.net/command-line/advanced-option-settings-on-the-command-line Set the interface and ports for the OpenVPN daemons In the Admin UI under Server
Advanced option settings on the command line docs.openvpn.net/command-line/advanced-option-settings-on-the-command-line Set the interface and ports for the OpenVPN daemons In the Admin UI under Server
HikCentral V.1.1.x for Windows Hardening Guide
 HikCentral V.1.1.x for Windows Hardening Guide Contents Introduction... 1 1. The Operating System - Microsoft Windows Security Configuration... 2 1.1 Strict Password Policy... 2 1.2 Turn Off Windows Remote
HikCentral V.1.1.x for Windows Hardening Guide Contents Introduction... 1 1. The Operating System - Microsoft Windows Security Configuration... 2 1.1 Strict Password Policy... 2 1.2 Turn Off Windows Remote
Distributed Systems. 27. Firewalls and Virtual Private Networks Paul Krzyzanowski. Rutgers University. Fall 2013
 Distributed Systems 27. Firewalls and Virtual Private Networks Paul Krzyzanowski Rutgers University Fall 2013 November 25, 2013 2013 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive
Distributed Systems 27. Firewalls and Virtual Private Networks Paul Krzyzanowski Rutgers University Fall 2013 November 25, 2013 2013 Paul Krzyzanowski 1 Network Security Goals Confidentiality: sensitive
Softether_on_R7000 BIG WARNING: THIS IS UTTERLY ALPHA, TESTING OUTPUT, NOT A SET OF INSTALL INSTRUCTIONS.
 BIG WARNING: THIS IS UTTERLY ALPHA, TESTING OUTPUT, NOT A SET OF INSTALL INSTRUCTIONS. Contents 1 Install notes 2 Runtime notes 2.1 Warnings 2.1.1 CPU scheduling priority 2.1.2 Open ports 2.1.3 Port conflicts
BIG WARNING: THIS IS UTTERLY ALPHA, TESTING OUTPUT, NOT A SET OF INSTALL INSTRUCTIONS. Contents 1 Install notes 2 Runtime notes 2.1 Warnings 2.1.1 CPU scheduling priority 2.1.2 Open ports 2.1.3 Port conflicts
How to Stay Safe on Public Wi-Fi Networks
 How to Stay Safe on Public Wi-Fi Networks Starbucks is now offering free Wi-Fi to all customers at every location. Whether you re clicking connect on Starbucks Wi-Fi or some other unsecured, public Wi-Fi
How to Stay Safe on Public Wi-Fi Networks Starbucks is now offering free Wi-Fi to all customers at every location. Whether you re clicking connect on Starbucks Wi-Fi or some other unsecured, public Wi-Fi
Step-by-Step Configuration
 Step-by-Step Configuration Kerio Technologies C 2001-2006 Kerio Technologies. All Rights Reserved. Printing Date: May 3, 2006 This guide provides detailed description on configuration of the local network
Step-by-Step Configuration Kerio Technologies C 2001-2006 Kerio Technologies. All Rights Reserved. Printing Date: May 3, 2006 This guide provides detailed description on configuration of the local network
REMOTE ACCESS IPSEC. Course /14/2014 Global Technology Associates, Inc.
 REMOTE ACCESS IPSEC Course 4002 1 Remote Access Features! Granular Network Access and Authorization based on groups and policies.! Windows, Linux, and MAC client support. Windows ShrewSoft Client MAC IPSecuritas
REMOTE ACCESS IPSEC Course 4002 1 Remote Access Features! Granular Network Access and Authorization based on groups and policies.! Windows, Linux, and MAC client support. Windows ShrewSoft Client MAC IPSecuritas
Using the Terminal Services Gateway Lesson 10
 Using the Terminal Services Gateway Lesson 10 Skills Matrix Technology Skill Objective Domain Objective # Deploying a TS Gateway Server Configure Terminal Services Gateway 2.2 Terminal Services (TS) Web
Using the Terminal Services Gateway Lesson 10 Skills Matrix Technology Skill Objective Domain Objective # Deploying a TS Gateway Server Configure Terminal Services Gateway 2.2 Terminal Services (TS) Web
A+ Guide to Software: Managing, Maintaining, and Troubleshooting, 5e. Chapter 8 Networking Essentials
 A+ Guide to Software: Managing, Maintaining, and Troubleshooting, 5e Chapter 8 Networking Essentials Objectives Learn about the protocols and standards Windows uses for networking Learn how to connect
A+ Guide to Software: Managing, Maintaining, and Troubleshooting, 5e Chapter 8 Networking Essentials Objectives Learn about the protocols and standards Windows uses for networking Learn how to connect
Making life simpler for remote and mobile workers
 : Technology GoToMyPC Technology Making life simpler for remote and mobile workers Learn why GoToMyPC is the most secure, cost-effective and easy-to-use solution for providing remote access to the desktop.
: Technology GoToMyPC Technology Making life simpler for remote and mobile workers Learn why GoToMyPC is the most secure, cost-effective and easy-to-use solution for providing remote access to the desktop.
HikCentral V1.3 for Windows Hardening Guide
 HikCentral V1.3 for Windows Hardening Guide Contents Introduction... 1 1. The Operating System - Microsoft Windows Security Configuration... 2 1.1Strict Password Policy... 2 1.2Turn Off Windows Remote
HikCentral V1.3 for Windows Hardening Guide Contents Introduction... 1 1. The Operating System - Microsoft Windows Security Configuration... 2 1.1Strict Password Policy... 2 1.2Turn Off Windows Remote
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Step-by-Step Configuration
 Step-by-Step Configuration Kerio Technologies Kerio Technologies. All Rights Reserved. Release Date: March 16, 2007 This guide provides detailed description on configuration of the local network which
Step-by-Step Configuration Kerio Technologies Kerio Technologies. All Rights Reserved. Release Date: March 16, 2007 This guide provides detailed description on configuration of the local network which
Gigabit SSL VPN Security Router
 As Internet becomes essential for business, the crucial solution to prevent your Internet connection from failure is to have more than one connection. PLANET is the ideal to help the SMBs increase the
As Internet becomes essential for business, the crucial solution to prevent your Internet connection from failure is to have more than one connection. PLANET is the ideal to help the SMBs increase the
Realtime Multimedia in Presence of Firewalls and Network Address Translation
 Realtime Multimedia in Presence of Firewalls and Network Address Translation Knut Omang Ifi/Oracle 9 Oct, 2017 1 Overview Real-time multimedia and connectivity Mobile users (roaming between devices) or
Realtime Multimedia in Presence of Firewalls and Network Address Translation Knut Omang Ifi/Oracle 9 Oct, 2017 1 Overview Real-time multimedia and connectivity Mobile users (roaming between devices) or
Realtime Multimedia in Presence of Firewalls and Network Address Translation. Knut Omang Ifi/Oracle 9 Nov, 2015
 Realtime Multimedia in Presence of Firewalls and Network Address Translation Knut Omang Ifi/Oracle 9 Nov, 2015 1 Overview Real-time multimedia and connectivity Mobile users (roaming between devices) or
Realtime Multimedia in Presence of Firewalls and Network Address Translation Knut Omang Ifi/Oracle 9 Nov, 2015 1 Overview Real-time multimedia and connectivity Mobile users (roaming between devices) or
Configuring OpenVPN on pfsense
 Configuring OpenVPN on pfsense Configuring OpenVPN on pfsense Posted by Glenn on Dec 29, 2013 in Networking 0 comments In this article I will go through the configuration of OpenVPN on the pfsense platform.
Configuring OpenVPN on pfsense Configuring OpenVPN on pfsense Posted by Glenn on Dec 29, 2013 in Networking 0 comments In this article I will go through the configuration of OpenVPN on the pfsense platform.
Application Note. Providing Secure Remote Access to Industrial Control Systems Using McAfee Firewall Enterprise (Sidewinder )
 Application Note Providing Secure Remote Access to Industrial Control Systems Using McAfee Firewall Enterprise (Sidewinder ) This document describes how to configure McAfee Firewall Enterprise to provide
Application Note Providing Secure Remote Access to Industrial Control Systems Using McAfee Firewall Enterprise (Sidewinder ) This document describes how to configure McAfee Firewall Enterprise to provide
Configuring Proxy Settings. STEP 1: (Gathering Proxy Information) Windows
 This guide is provided to Elluminate Live! users to assist them to make a successful connection to an Elluminate Live! session through a proxy firewall. In some cases settings discussed in this document
This guide is provided to Elluminate Live! users to assist them to make a successful connection to an Elluminate Live! session through a proxy firewall. In some cases settings discussed in this document
VPN Configuration Guide. NETGEAR FVG318 / FVS318G / FVS336G / FVS338 / DGFV338 FVX538 / SRXN3205 / SRX5308 / ProSecure UTM Series
 VPN Configuration Guide NETGEAR FVG318 / FVS318G / FVS336G / FVS338 / DGFV338 FVX538 / SRXN3205 / SRX5308 / ProSecure UTM Series 2010 equinux AG and equinux USA, Inc. All rights reserved. Under copyright
VPN Configuration Guide NETGEAR FVG318 / FVS318G / FVS336G / FVS338 / DGFV338 FVX538 / SRXN3205 / SRX5308 / ProSecure UTM Series 2010 equinux AG and equinux USA, Inc. All rights reserved. Under copyright
VII. Corente Services SSL Client
 VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
Configuring Actinic with ISA Server 2000
 Configuring Actinic with ISA Server 2000 Actinic Software Ltd. Author: Gordon Camley Date: 26 January 2004 Revision: 1.0 Introduction As of release 6.1.4, Actinic can be configured to work with an ISA
Configuring Actinic with ISA Server 2000 Actinic Software Ltd. Author: Gordon Camley Date: 26 January 2004 Revision: 1.0 Introduction As of release 6.1.4, Actinic can be configured to work with an ISA
Lab assignment #2 IPSec and VPN Tunnels
 University of Pittsburgh School of Information Science IS2820/TEL2813 - Security Management Lab assignment #2 IPSec and VPN Tunnels Lab GSA: Carlos Caicedo Page I. Lab resources for this assignment...
University of Pittsburgh School of Information Science IS2820/TEL2813 - Security Management Lab assignment #2 IPSec and VPN Tunnels Lab GSA: Carlos Caicedo Page I. Lab resources for this assignment...
Step-by-Step Configuration
 Step-by-Step Configuration Kerio Technologies C 2001-2004 Kerio Technologies. All Rights Reserved. Printing Date: April 25, 2004 This guide provides detailed description on configuration of the local network
Step-by-Step Configuration Kerio Technologies C 2001-2004 Kerio Technologies. All Rights Reserved. Printing Date: April 25, 2004 This guide provides detailed description on configuration of the local network
Machine Remote Access and Network Security Utilizing ewon
 Machine Remote Access and Network Security Utilizing ewon by Mike Wojda mwojda@vcail.com Vision Control and Automation, division of Standard Electric 1. Overview of ewon Technology Today, most modern production
Machine Remote Access and Network Security Utilizing ewon by Mike Wojda mwojda@vcail.com Vision Control and Automation, division of Standard Electric 1. Overview of ewon Technology Today, most modern production
PCI DSS Compliance. White Paper Parallels Remote Application Server
 PCI DSS Compliance White Paper Parallels Remote Application Server Table of Contents Introduction... 3 What Is PCI DSS?... 3 Why Businesses Need to Be PCI DSS Compliant... 3 What Is Parallels RAS?... 3
PCI DSS Compliance White Paper Parallels Remote Application Server Table of Contents Introduction... 3 What Is PCI DSS?... 3 Why Businesses Need to Be PCI DSS Compliant... 3 What Is Parallels RAS?... 3
TECHNOLOGY Introduction The Difference Protection at the End Points Security made Simple
 APPGATE TECHNOLOGY UNIFIED TECHNOLOGY Introduction The AppGate solution truly delivers holistic security and access control where other approaches fall short. It is designed to address the security and
APPGATE TECHNOLOGY UNIFIED TECHNOLOGY Introduction The AppGate solution truly delivers holistic security and access control where other approaches fall short. It is designed to address the security and
Chapter 3 LAN Configuration
 Chapter 3 LAN Configuration This chapter describes how to configure the advanced LAN features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. This chapter contains the following sections
Chapter 3 LAN Configuration This chapter describes how to configure the advanced LAN features of your ProSafe Dual WAN Gigabit Firewall with SSL & IPsec VPN. This chapter contains the following sections
Identify the features of network and client operating systems (Windows, NetWare, Linux, Mac OS)
 Course Outline Network+ Duration: 5 days (30 hours) Learning Objectives: Install and configure a network card Define the concepts of network layers Understand and implement the TCP/IP protocol Install
Course Outline Network+ Duration: 5 days (30 hours) Learning Objectives: Install and configure a network card Define the concepts of network layers Understand and implement the TCP/IP protocol Install
Clientless SSL VPN Remote Users
 This chapter summarizes configuration requirements and tasks for the user remote system. It also helps users get started with Clientless SSL VPN. It includes the following sections: Make sure that the
This chapter summarizes configuration requirements and tasks for the user remote system. It also helps users get started with Clientless SSL VPN. It includes the following sections: Make sure that the
Hacker Academy Ltd COURSES CATALOGUE. Hacker Academy Ltd. LONDON UK
 Hacker Academy Ltd COURSES CATALOGUE Hacker Academy Ltd. LONDON UK TABLE OF CONTENTS Basic Level Courses... 3 1. Information Security Awareness for End Users... 3 2. Information Security Awareness for
Hacker Academy Ltd COURSES CATALOGUE Hacker Academy Ltd. LONDON UK TABLE OF CONTENTS Basic Level Courses... 3 1. Information Security Awareness for End Users... 3 2. Information Security Awareness for
SIMATIC NET. Industrial Ethernet Security SCALANCE S615 Getting Started. Preface. Connecting SCALANCE S615 to the WAN 1
 Preface Connecting SCALANCE S615 to the WAN 1 SIMATIC NET VPN tunnel between SCALANCE S615 and 2 SINEMA RC Server Industrial Ethernet Security Getting Started 07/2017 C79000-G8976-C390-02 Legal information
Preface Connecting SCALANCE S615 to the WAN 1 SIMATIC NET VPN tunnel between SCALANCE S615 and 2 SINEMA RC Server Industrial Ethernet Security Getting Started 07/2017 C79000-G8976-C390-02 Legal information
Defending Yourself Against The Wily Wireless Hacker
 Defending Yourself Against The Wily Wireless Hacker Brian S. Walden NYCWireless Presentation October 27, 2004 http://wifidefense.cuzuco.com/ What You Expect Common Hacker Techniques Direct Break-In Man-In-The-Middle
Defending Yourself Against The Wily Wireless Hacker Brian S. Walden NYCWireless Presentation October 27, 2004 http://wifidefense.cuzuco.com/ What You Expect Common Hacker Techniques Direct Break-In Man-In-The-Middle
Clientless SSL VPN Overview
 Introduction to Clientless SSL VPN, page 1 Prerequisites for Clientless SSL VPN, page 2 Guidelines and Limitations for Clientless SSL VPN, page 2 Licensing for Clientless SSL VPN, page 3 Introduction to
Introduction to Clientless SSL VPN, page 1 Prerequisites for Clientless SSL VPN, page 2 Guidelines and Limitations for Clientless SSL VPN, page 2 Licensing for Clientless SSL VPN, page 3 Introduction to
A Technical Overview of the Lucent Managed Firewall
 Lucent Managed Version 2.0 A Technical Overview of the Lucent Managed This document provides a technical overview of the Lucent Managed architecture. Key technical features and potential application scenarios
Lucent Managed Version 2.0 A Technical Overview of the Lucent Managed This document provides a technical overview of the Lucent Managed architecture. Key technical features and potential application scenarios
A+ Certification Guide. Chapter 16 (Part B) Networking
 A+ Certification Guide Chapter 16 (Part B) Networking Chapter 16 (Part B) Objectives Installing and Configuring Network Interface Cards Networking Configuration for Small Network Switches and Routers Setting
A+ Certification Guide Chapter 16 (Part B) Networking Chapter 16 (Part B) Objectives Installing and Configuring Network Interface Cards Networking Configuration for Small Network Switches and Routers Setting
Remote Access via Cisco VPN Client
 Remote Access via Cisco VPN Client General Information This guide describes step by step the configuration of a remote access to the Astaro Security Gateway by using the Cisco VPN Client. The Cisco VPN
Remote Access via Cisco VPN Client General Information This guide describes step by step the configuration of a remote access to the Astaro Security Gateway by using the Cisco VPN Client. The Cisco VPN
Proxy server is a server (a computer system or an application program) that acts as an intermediary between for requests from clients seeking
 NETWORK MANAGEMENT II Proxy Servers Proxy server is a server (a computer system or an application program) that acts as an intermediary between for requests from clients seeking resources from the other
NETWORK MANAGEMENT II Proxy Servers Proxy server is a server (a computer system or an application program) that acts as an intermediary between for requests from clients seeking resources from the other
Once all of the features of Intel Active Management Technology (Intel
 Chapter11 Connecting and Communicating with Intel Active Management Technology Disconnecting from change does not recapture the past. It loses the future. Kathleen Norris, O Magazine, January 2004 Once
Chapter11 Connecting and Communicating with Intel Active Management Technology Disconnecting from change does not recapture the past. It loses the future. Kathleen Norris, O Magazine, January 2004 Once
Operating Systems Design Exam 3 Review: Spring Paul Krzyzanowski
 Operating Systems Design Exam 3 Review: Spring 2012 Paul Krzyzanowski pxk@cs.rutgers.edu 1 Question 1 An Ethernet device driver implements the: (a) Data Link layer. (b) Network layer. (c) Transport layer.
Operating Systems Design Exam 3 Review: Spring 2012 Paul Krzyzanowski pxk@cs.rutgers.edu 1 Question 1 An Ethernet device driver implements the: (a) Data Link layer. (b) Network layer. (c) Transport layer.
LevelOne Broadband Routers
 LevelOne Broadband Routers FBR-1100TX FBR-1400TX FBR-1401TX FBR-1700TX User's Guide TABLE OF CONTENTS CHAPTER 1 INTRODUCTION... 1 Features of your LevelOne Broadband Router... 1 Package Contents... 4
LevelOne Broadband Routers FBR-1100TX FBR-1400TX FBR-1401TX FBR-1700TX User's Guide TABLE OF CONTENTS CHAPTER 1 INTRODUCTION... 1 Features of your LevelOne Broadband Router... 1 Package Contents... 4
McAfee epo Deep Command
 Quick Start Guide McAfee epo Deep Command version 2.4.1 This Quick Start Guide provides high level instructions for setting up McAfee epo Deep Command 2.4.1. For detailed instructions, refer to the McAfee
Quick Start Guide McAfee epo Deep Command version 2.4.1 This Quick Start Guide provides high level instructions for setting up McAfee epo Deep Command 2.4.1. For detailed instructions, refer to the McAfee
Certificate-based authentication for data security
 Technical white paper Certificate-based authentication for data security Table of Contents Introduction... 2 Analogy: A simple checking account... 2 Verifying a digital certificate... 2 Summary... 8 Important
Technical white paper Certificate-based authentication for data security Table of Contents Introduction... 2 Analogy: A simple checking account... 2 Verifying a digital certificate... 2 Summary... 8 Important
The Features and Uses of Computer Networking. Unit 11 Task 1
 The Features and Uses of Computer Networking Unit 11 Task 1 Features Office Network Peer to peer A peer to peer network is mostly used in homes or small businesses. The network consists of two or more
The Features and Uses of Computer Networking Unit 11 Task 1 Features Office Network Peer to peer A peer to peer network is mostly used in homes or small businesses. The network consists of two or more
Accessing CharityMaster data from another location
 Accessing CharityMaster data from another location When all of your computers are on the same Local Area Network (LAN), you can place the back end files (including your data and the Word templates) onto
Accessing CharityMaster data from another location When all of your computers are on the same Local Area Network (LAN), you can place the back end files (including your data and the Word templates) onto
PPP Tunneling. Step by step explanation and configuration for creating PPP Tunnel
 PPP Tunneling Step by step explanation and configuration for creating PPP Tunnel 1 Point-to-Point Protocol Point-to-Point Protocol (PPP) is used to establish a tunnel (direct connection) between two nodes.
PPP Tunneling Step by step explanation and configuration for creating PPP Tunnel 1 Point-to-Point Protocol Point-to-Point Protocol (PPP) is used to establish a tunnel (direct connection) between two nodes.
VPN Solutions for Zerto Virtual Replication to Azure. SoftEther Installation Guide
 VPN Solutions for Zerto Virtual Replication to Azure SoftEther Installation Guide VERSION 1.0 JULY 2017 Table of Contents 1. Overview... 2 1.1 Use Cases... 2 2. Proofs of Concept and Lab Usage... 2 2.1
VPN Solutions for Zerto Virtual Replication to Azure SoftEther Installation Guide VERSION 1.0 JULY 2017 Table of Contents 1. Overview... 2 1.1 Use Cases... 2 2. Proofs of Concept and Lab Usage... 2 2.1
Internet. How to connect to the Internet. Microsoft.com. 2. Tap Start > Settings > Connections tab > Connections.
 Microsoft.com Internet How to connect to the Internet 1. Obtain the following information from your ISP: ISP server phone number, user name, and password. 2. Tap Start > Settings > Connections tab > Connections.
Microsoft.com Internet How to connect to the Internet 1. Obtain the following information from your ISP: ISP server phone number, user name, and password. 2. Tap Start > Settings > Connections tab > Connections.
Openvpn Client Do Not Change Default Gateway
 Openvpn Client Do Not Change Default Gateway I currently have a router using OpenVPN in client mode to connect to a host Is it possible to make OpenVPN the default gateway for everyone connected So what
Openvpn Client Do Not Change Default Gateway I currently have a router using OpenVPN in client mode to connect to a host Is it possible to make OpenVPN the default gateway for everyone connected So what
File services. Domains, DNS DHCP. Server Scripts. Intranet and Extranets. Web services. HNC COMPUTING - Network Concepts
 File services Domains, DNS 1 DHCP Server Scripts Intranet and Extranets Web services HNC COMPUTING - Network Concepts A domain is a logical grouping of networked computers that share a central directory
File services Domains, DNS 1 DHCP Server Scripts Intranet and Extranets Web services HNC COMPUTING - Network Concepts A domain is a logical grouping of networked computers that share a central directory
How to Configure a Remote Management Tunnel for an F-Series Firewall
 How to Configure a Remote Management Tunnel for an F-Series Firewall If the managed NextGen Firewall F-Series cannot directly reach the NextGen Control Center, it must connect via a remote management tunnel.
How to Configure a Remote Management Tunnel for an F-Series Firewall If the managed NextGen Firewall F-Series cannot directly reach the NextGen Control Center, it must connect via a remote management tunnel.
Users Guide. Kerio Technologies
 Users Guide Kerio Technologies C 1997-2006 Kerio Technologies. All rights reserved. Release Date: June 8, 2006 This guide provides detailed description on Kerio WebSTAR 5, version 5.4. Any additional modifications
Users Guide Kerio Technologies C 1997-2006 Kerio Technologies. All rights reserved. Release Date: June 8, 2006 This guide provides detailed description on Kerio WebSTAR 5, version 5.4. Any additional modifications
Overview. ACE Appliance Device Manager Overview CHAPTER
 1 CHAPTER This section contains the following: ACE Appliance Device Manager, page 1-1 Logging Into ACE Appliance Device Manager, page 1-3 Changing Your Account Password, page 1-4 ACE Appliance Device Manager
1 CHAPTER This section contains the following: ACE Appliance Device Manager, page 1-1 Logging Into ACE Appliance Device Manager, page 1-3 Changing Your Account Password, page 1-4 ACE Appliance Device Manager
NetExtender for SSL-VPN
 NetExtender for SSL-VPN Document Scope This document describes how to plan, design, implement, and manage the NetExtender feature in a SonicWALL SSL-VPN Environment. This document contains the following
NetExtender for SSL-VPN Document Scope This document describes how to plan, design, implement, and manage the NetExtender feature in a SonicWALL SSL-VPN Environment. This document contains the following
6.6 VPN Tools Command Reference
 6.6 VPN Tools Command Reference This section describes all commands that can be called when using vpncmd in Use VPN Tools Command (for example, certificate generating tools or traffic speed test tool)
6.6 VPN Tools Command Reference This section describes all commands that can be called when using vpncmd in Use VPN Tools Command (for example, certificate generating tools or traffic speed test tool)
Relay Proxy User Guide
 Relay Proxy User Guide DBL Technology Company Limited www.dbltek.com sales@dbltek.com support@dbltek.com 2016/5/30 Relay Proxy Relay Proxy is a server software developed by DBL Technology. Its main purposed
Relay Proxy User Guide DBL Technology Company Limited www.dbltek.com sales@dbltek.com support@dbltek.com 2016/5/30 Relay Proxy Relay Proxy is a server software developed by DBL Technology. Its main purposed
AWS Reference Architecture - CloudGen Firewall Auto Scaling Cluster
 AWS Reference Architecture - CloudGen Firewall Auto Scaling Cluster Protecting highly dynamic AWS resources with a static firewall setup is neither efficient nor economical. A CloudGen Firewall Auto Scaling
AWS Reference Architecture - CloudGen Firewall Auto Scaling Cluster Protecting highly dynamic AWS resources with a static firewall setup is neither efficient nor economical. A CloudGen Firewall Auto Scaling
Spring 2010 CS419. Computer Security. Vinod Ganapathy Lecture 14. Chapters 6 and 9 Intrusion Detection and Prevention
 Spring 2010 CS419 Computer Security Vinod Ganapathy Lecture 14 Chapters 6 and 9 Intrusion Detection and Prevention Firewalls and IPSes effective means of protecting LANs internet connectivity essential
Spring 2010 CS419 Computer Security Vinod Ganapathy Lecture 14 Chapters 6 and 9 Intrusion Detection and Prevention Firewalls and IPSes effective means of protecting LANs internet connectivity essential
Software Manual Net Configuration Tool Rev. 1.01
 Software Manual Net Configuration Tool Rev. 1.01 http://www.bixolon.com Table of Contents 1. Manual Information... 3 2. Operating System (OS) Environment... 3 3. Software Installation & Uninstallation...
Software Manual Net Configuration Tool Rev. 1.01 http://www.bixolon.com Table of Contents 1. Manual Information... 3 2. Operating System (OS) Environment... 3 3. Software Installation & Uninstallation...
VPN Configuration Guide. NETGEAR FVS318v3
 VPN Configuration Guide NETGEAR FVS318v3 equinux AG and equinux USA, Inc. 2009 equinux USA, Inc. All rights reserved. Under the copyright laws, this manual may not be copied, in whole or in part, without
VPN Configuration Guide NETGEAR FVS318v3 equinux AG and equinux USA, Inc. 2009 equinux USA, Inc. All rights reserved. Under the copyright laws, this manual may not be copied, in whole or in part, without
About This Document 3. Overview 3. System Requirements 3. Installation & Setup 4
 About This Document 3 Overview 3 System Requirements 3 Installation & Setup 4 Step By Step Instructions 5 1. Login to Admin Console 6 2. Show Node Structure 7 3. Create SSO Node 8 4. Create SAML IdP 10
About This Document 3 Overview 3 System Requirements 3 Installation & Setup 4 Step By Step Instructions 5 1. Login to Admin Console 6 2. Show Node Structure 7 3. Create SSO Node 8 4. Create SAML IdP 10
WHITE PAPER. Secure communication. - Security functions of i-pro system s
 WHITE PAPER Secure communication - Security functions of i-pro system s Panasonic Video surveillance systems Table of Contents 1. Introduction... 1 2. Outline... 1 3. Common security functions of the i-pro
WHITE PAPER Secure communication - Security functions of i-pro system s Panasonic Video surveillance systems Table of Contents 1. Introduction... 1 2. Outline... 1 3. Common security functions of the i-pro
Installation guide for Choic Multi User Edition
 Installation guide for ChoiceMail Multi User Edition March, 2004 Version 2.1 Copyright DigiPortal Software Inc., 2002 2004 All rights reserved ChoiceMail Multi User Installation Guide 1. Go to the URL
Installation guide for ChoiceMail Multi User Edition March, 2004 Version 2.1 Copyright DigiPortal Software Inc., 2002 2004 All rights reserved ChoiceMail Multi User Installation Guide 1. Go to the URL
Gigaset Router / en / A31008-E105-B / cover_front_router.fm / s Be inspired
 s Be inspired Table of Contents Table of Contents Safety precautions........................... 3 The Gigaset Router........................... 3 Features and Benefits..................................................
s Be inspired Table of Contents Table of Contents Safety precautions........................... 3 The Gigaset Router........................... 3 Features and Benefits..................................................
XenApp 5 Security Standards and Deployment Scenarios
 XenApp 5 Security Standards and Deployment Scenarios 2015-03-04 20:22:07 UTC 2015 Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement Contents XenApp 5 Security Standards
XenApp 5 Security Standards and Deployment Scenarios 2015-03-04 20:22:07 UTC 2015 Citrix Systems, Inc. All rights reserved. Terms of Use Trademarks Privacy Statement Contents XenApp 5 Security Standards
Computer Security and Privacy
 CSE P 590 / CSE M 590 (Spring 2010) Computer Security and Privacy Tadayoshi Kohno Thanks to Dan Boneh, Dieter Gollmann, John Manferdelli, John Mitchell, Vitaly Shmatikov, Bennet Yee, and many others for
CSE P 590 / CSE M 590 (Spring 2010) Computer Security and Privacy Tadayoshi Kohno Thanks to Dan Boneh, Dieter Gollmann, John Manferdelli, John Mitchell, Vitaly Shmatikov, Bennet Yee, and many others for
OpenVPN ANTELOPE USER GROUP 2017, VIENNA. Stefan Radman May 30, 2017
 1 OpenVPN ANTELOPE USER GROUP 2017, VIENNA Stefan Radman May 30, 2017 What is OpenVPN? https://en.wikipedia.org/wiki/openvpn 2 OpenVPN is an open-source software application that implements virtual private
1 OpenVPN ANTELOPE USER GROUP 2017, VIENNA Stefan Radman May 30, 2017 What is OpenVPN? https://en.wikipedia.org/wiki/openvpn 2 OpenVPN is an open-source software application that implements virtual private
Clientless SSL VPN End User Set-up
 71 CHAPTER This section is for the system administrator who sets up Clientless (browser-based) SSL VPN for end users. It summarizes configuration requirements and tasks for the user remote system. It also
71 CHAPTER This section is for the system administrator who sets up Clientless (browser-based) SSL VPN for end users. It summarizes configuration requirements and tasks for the user remote system. It also
QNAP VPN (Virtual Private Network) Secure network experience
 QNAP VPN (Virtual Private Network) Secure network experience What is VPN (Virtual Private Network) The general Internet style Internet What is VPN? UNENCRYPTED ENCRYPTED ANONYMOUS When you connect through
QNAP VPN (Virtual Private Network) Secure network experience What is VPN (Virtual Private Network) The general Internet style Internet What is VPN? UNENCRYPTED ENCRYPTED ANONYMOUS When you connect through
Installing and Configuring vcenter Multi-Hypervisor Manager
 Installing and Configuring vcenter Multi-Hypervisor Manager vcenter Server 5.1 vcenter Multi-Hypervisor Manager 1.1.2 This document supports the version of each product listed and supports all subsequent
Installing and Configuring vcenter Multi-Hypervisor Manager vcenter Server 5.1 vcenter Multi-Hypervisor Manager 1.1.2 This document supports the version of each product listed and supports all subsequent
TM1 9.0 SP2 UNIX Installation Help
 TM1 9.0 SP2 UNIX Installation Help Table of Contents TM1 Installation for UNIX...1 This document is a printed version of the online help available from the Applix Installation Wizard.Welcome to the Applix
TM1 9.0 SP2 UNIX Installation Help Table of Contents TM1 Installation for UNIX...1 This document is a printed version of the online help available from the Applix Installation Wizard.Welcome to the Applix
CONTENTS IN DETAIL INTRODUCTION
 CONTENTS IN DETAIL ACKNOWLEDGMENTS xiii INTRODUCTION xv 1 HOW A NETWORK WILL IMPROVE YOUR LIFE 1 What s a Network?... 2 Sneakernet... 3 Data Networks and What You Can Do with Them... 4 File Sharing...
CONTENTS IN DETAIL ACKNOWLEDGMENTS xiii INTRODUCTION xv 1 HOW A NETWORK WILL IMPROVE YOUR LIFE 1 What s a Network?... 2 Sneakernet... 3 Data Networks and What You Can Do with Them... 4 File Sharing...
Multi-Homing Broadband Router. User Manual
 Multi-Homing Broadband Router User Manual 1 Introduction... 4 Features... 4 Minimum Requirements... 4 Package Content... 4 Note... 4 Get to know the Broadband Router... 5 Back Panel... 5 Front Panel...
Multi-Homing Broadband Router User Manual 1 Introduction... 4 Features... 4 Minimum Requirements... 4 Package Content... 4 Note... 4 Get to know the Broadband Router... 5 Back Panel... 5 Front Panel...
Secure Communications Over a Network
 Secure Communications Over a Network Course: MITS:5400G Proffessor: Dr. Xiaodong Lin By: Geoff Vaughan 100309160 March 20th 2012 Abstract The purpose of this experiment is to transmit an encrypted message
Secure Communications Over a Network Course: MITS:5400G Proffessor: Dr. Xiaodong Lin By: Geoff Vaughan 100309160 March 20th 2012 Abstract The purpose of this experiment is to transmit an encrypted message
Microsoft Microsoft TS: MS Internet Security & Acceleration Server 2006, Configuring. Practice Test. Version:
 Microsoft 70-351 Microsoft 70-351 TS: MS Internet Security & Acceleration Server 2006, Configuring Practice Test Version: 2.2 QUESTION NO: 1 Your network consists of a single Active Directory domain named
Microsoft 70-351 Microsoft 70-351 TS: MS Internet Security & Acceleration Server 2006, Configuring Practice Test Version: 2.2 QUESTION NO: 1 Your network consists of a single Active Directory domain named
Practical Magic with SSH. By David F. Skoll Roaring Penguin Software Inc. 1 February
 Practical Magic with SSH By David F. Skoll Roaring Penguin Software Inc. 1 February 2001 http://www.roaringpenguin.com dfs@roaringpenguin.com Overview of Presentation Why SSH? Problems with Telnet & Friends
Practical Magic with SSH By David F. Skoll Roaring Penguin Software Inc. 1 February 2001 http://www.roaringpenguin.com dfs@roaringpenguin.com Overview of Presentation Why SSH? Problems with Telnet & Friends
User Manual. SSV Remote Access Gateway. Web ConfigTool
 SSV Remote Access Gateway Web ConfigTool User Manual SSV Software Systems GmbH Dünenweg 5 D-30419 Hannover Phone: +49 (0)511/40 000-0 Fax: +49 (0)511/40 000-40 E-mail: sales@ssv-embedded.de Document Revision:
SSV Remote Access Gateway Web ConfigTool User Manual SSV Software Systems GmbH Dünenweg 5 D-30419 Hannover Phone: +49 (0)511/40 000-0 Fax: +49 (0)511/40 000-40 E-mail: sales@ssv-embedded.de Document Revision:
Application Note Asterisk BE with Remote Phones - Configuration Guide
 Application Note Asterisk BE with Remote Phones - Configuration Guide 15 January 2009 Asterisk BE - Remote SIP Phones Table of Contents 1 ASTERISK BUSINESS EDITION AND INGATE... 1 1.1 REMOTE SIP PHONE
Application Note Asterisk BE with Remote Phones - Configuration Guide 15 January 2009 Asterisk BE - Remote SIP Phones Table of Contents 1 ASTERISK BUSINESS EDITION AND INGATE... 1 1.1 REMOTE SIP PHONE
WHITE PAPER Cloud FastPath: A Highly Secure Data Transfer Solution
 WHITE PAPER Cloud FastPath: A Highly Secure Data Transfer Solution Tervela helps companies move large volumes of sensitive data safely and securely over network distances great and small. We have been
WHITE PAPER Cloud FastPath: A Highly Secure Data Transfer Solution Tervela helps companies move large volumes of sensitive data safely and securely over network distances great and small. We have been
Securing the FOSS VistA Stack
 Securing the FOSS VistA Stack K.S. Bhaskar Development Director, FIS GT.M 2011 Fidelity National Information Services, Inc. and its subsidiaries. What is Security? 2 What is Security? Simplistic View Ensuring
Securing the FOSS VistA Stack K.S. Bhaskar Development Director, FIS GT.M 2011 Fidelity National Information Services, Inc. and its subsidiaries. What is Security? 2 What is Security? Simplistic View Ensuring
CLEO VLTrader Made Simple Guide
 CLEO VLTrader Made Simple Guide Table of Contents Quick Reference... 3 Miscellaneous Technical Notes... 3 CLEO VLTrader at a Glance... 3 Introduction... 5 Application Page Layout... 5 Preconfigured Hosts...
CLEO VLTrader Made Simple Guide Table of Contents Quick Reference... 3 Miscellaneous Technical Notes... 3 CLEO VLTrader at a Glance... 3 Introduction... 5 Application Page Layout... 5 Preconfigured Hosts...
4D WebSTAR V User Guide for Mac OS. Copyright (C) D SA / 4D, Inc. All rights reserved.
 4D WebSTAR V User Guide for Mac OS Copyright (C) 2002 4D SA / 4D, Inc. All rights reserved. The software described in this manual is governed by the grant of license provided in this package. The software
4D WebSTAR V User Guide for Mac OS Copyright (C) 2002 4D SA / 4D, Inc. All rights reserved. The software described in this manual is governed by the grant of license provided in this package. The software
CHAPTER 7 ADVANCED ADMINISTRATION PC
 ii Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband ADSL Router Features... 1 Package Contents... 3 Physical Details... 4 CHAPTER 2 INSTALLATION... 6 Requirements... 6 Procedure... 6 CHAPTER 3 SETUP...
ii Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband ADSL Router Features... 1 Package Contents... 3 Physical Details... 4 CHAPTER 2 INSTALLATION... 6 Requirements... 6 Procedure... 6 CHAPTER 3 SETUP...
TCP/IP CONFIGURATION 3-6
 TCP/IP CONFIGURATION 3. Type IPCONFIG /RENEW and press the Enter key. Verify that your IP Address is now 192.168.2.xxx, your Subnet Mask is 255.255.255.0 and your Default Gateway is 192.168.2.1. These
TCP/IP CONFIGURATION 3. Type IPCONFIG /RENEW and press the Enter key. Verify that your IP Address is now 192.168.2.xxx, your Subnet Mask is 255.255.255.0 and your Default Gateway is 192.168.2.1. These
What s New in Fireware v WatchGuard Training
 What s New in Fireware v12.2.1 What s New in Fireware v12.2.1 2 DNS enhancements for mobile VPN WAN interface monitors Loopback IP address support Certificate management enhancements DF bit setting for
What s New in Fireware v12.2.1 What s New in Fireware v12.2.1 2 DNS enhancements for mobile VPN WAN interface monitors Loopback IP address support Certificate management enhancements DF bit setting for
Operating Systems Design Exam 3 Review: Spring 2011
 Operating Systems Design Exam 3 Review: Spring 2011 Paul Krzyzanowski pxk@cs.rutgers.edu 1 1. Why does an IP driver need to use ARP, the address resolution protocol? IP is a logical network. An IP address
Operating Systems Design Exam 3 Review: Spring 2011 Paul Krzyzanowski pxk@cs.rutgers.edu 1 1. Why does an IP driver need to use ARP, the address resolution protocol? IP is a logical network. An IP address
VPN Configuration Guide LANCOM
 VPN Configuration Guide LANCOM equinux AG and equinux USA, Inc. 2015 equinux USA, Inc. All rights reserved. Under the copyright laws, this manual may not be copied, in whole or in part, without the written
VPN Configuration Guide LANCOM equinux AG and equinux USA, Inc. 2015 equinux USA, Inc. All rights reserved. Under the copyright laws, this manual may not be copied, in whole or in part, without the written
VMware Horizon View Deployment
 VMware Horizon View provides end users with access to their machines and applications through a unified workspace across multiple devices, locations, and connections. The Horizon View Connection Server
VMware Horizon View provides end users with access to their machines and applications through a unified workspace across multiple devices, locations, and connections. The Horizon View Connection Server
Secure Industrial Automation Remote Access Connectivity. Using ewon and Talk2M Pro solutions
 ewon Security Paper Secure Industrial Automation Remote Access Connectivity Using ewon and Talk2M Pro solutions www.ewon.us Last Modified: January 13, 2015 Overview ewon is a global provider of secure
ewon Security Paper Secure Industrial Automation Remote Access Connectivity Using ewon and Talk2M Pro solutions www.ewon.us Last Modified: January 13, 2015 Overview ewon is a global provider of secure
