Cisco Multicloud Portfolio: Cloud Connect
|
|
|
- Eileen Stevenson
- 5 years ago
- Views:
Transcription
1 Deployment Guide Cisco Multicloud Portfolio: Cloud Connect Private Network to Azure Transit Virtual Network October Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 1 of 50
2 Contents Executive summary... 3 Cisco Multicloud Portfolio: Overview... 3 Cloud Connect: Overview... 4 Cloud Connect: Use cases... 4 Cloud Connect: Benefits... 4 Technology overview... 5 Solution overview... 5 Technology considerations... 7 Virtual Routing and Forwarding (VRF)... 7 Route leaking... 7 Routing protocols... 7 Route redistribution... 7 Azure security groups... 8 High availability... 8 Scalability... 8 Solution deployment... 9 Configure the hub for DMVPN Procedure 1: Configure IKEv Procedure 2: Configure IPSec Procedure 3: Configure tunnel interface Procedure 4: Configure routing Configure the spokes for DMVPN Procedure 1: Create a Virtual Routing and Forwarding (VRF) instance Procedure 2: Configure IKEv Procedure 3: Configure IPSec Procedure 3: Configure tunnel interface Procedure 4: Configure routing Verify the solution Appendix A: Sample Cisco CSR 1000V-1 DMVPN spoke configuration Appendix B: Sample Cisco CSR 1000V-2 DMVPN spoke configuration Appendix C: Sample Cisco CSR 1000V DMVPN hub configuration Additional resources Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 2 of 50
3 Executive summary This guide is a continuation of the Azure Transit Virtual Network (VNet) with Cisco Cloud Services Router 1000V Design and Deployment Guide. It focuses on the connectivity solution for Microsoft Azure, while this guide focuses on the connectivity between the Azure Transit Virtual Network using a pair of Cisco CSR 1000V Series Routers to the private data center. The audience for this document includes network design engineers, network operations personnel, and security operations personnel who wish to implement secure VPN connectivity from their private data centers to an Azure Transit VNet. Cisco Multicloud Portfolio: Overview In a multicloud world, growing complexity is driving a cloud gap between what your customers require and what your people, processes, and tools can support. With the Cisco Multicloud Portfolio, we make it simple: simple to connect, simple to protect and simple to consume. The Cisco Multicloud Portfolio is a set of essential products, software, and services supported with simplified ordering and design deployment guides to help you when it comes to multicloud adoption. The Cisco Multicloud Portfolio consists of four component portfolios (Figure 1): Cloud Advisory: Helps you design, plan, accelerate, and remove risk from your multicloud migration. Cloud Connect: Securely extends your private networks into public clouds and helps ensure the appropriate application experience. Cloud Protect: Protects your multicloud identities, direct-to-cloud connectivity, data, and applications, including Software as a Service (SaaS), and detects infrastructure and application threats on premises and in public clouds. Cloud Consume: Helps you deploy, monitor, and optimize applications in multicloud and container environments. Figure 1. Multicloud Portfolio: Cloud Advisory, Cloud Connect, Cloud Protect, and Cloud Consume 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 3 of 50
4 Cloud Connect: Overview Cloud Connect consists of essential products that help securely extend your private networks including data center, branches, and campuses to public clouds and to help ensure that the application experience is optimal: Cisco Cloud Services Router (CSR) 1000V Series Viptela vedge with Cisco Umbrella For detailed use cases, see the section about Cloud Connect on the portfolio s solution page at For partners, use the following URL: Cloud Connect: Use cases Cloud Connect delivers value in the following use cases: Securely extending a private network to single or multiple public cloud environments. Includes multiple clouds (for example, multiple AWS and Azure), multiple regions in a cloud, or multiple VPCs in a cloud; VPN; multicloud and multi-vpc connectivity; scaling; and performance optimization-transit VPC. Also supports extending data centers into the cloud and enabling direct branch-to-cloud connectivity (when a branch has a Cisco 4000 Series Integrated Services Router [ISR] and wants to connect the clouds, or a branch has vedge and requires a software-defined WAN [SD-WAN] extension to the cloud). Optimizing data center and branch connectivity performance to cloud Infrastructure as a Service (IaaS) and SaaS. Includes best path to destination (SD-WAN), cloud segmentation, monitoring to assure best performance, visibility into traffic going to applications, and traffic shaping / Quality of Service (QoS). Also supports extending data centers into the cloud and enabling direct branch-to-cloud connectivity (when a branch has a 4000 Series ISR and wants to connect the clouds or a branch has vedge and requires an SD- WAN extension to the cloud). Securing access to the Internet and SaaS from the branch. Includes connecting and protecting branch office users directly to the multicloud environment using Direct Internet Access (DIA), SD-WAN (vedge), and secure Internet gateways (Cisco Umbrella). Cloud Connect: Benefits Cloud Connect benefits include the ability to: 1. Extend a private network to a multicloud environment while leveraging existing investments 2. Apply consistent security policies across a private and public cloud footprint 3. Enhance and secure the app experience on a cloud network by enabling visibility and path selection and optimization 4. Centralize management in a manner that is intuitive, fast, and easy to design, provision, and apply policies across the entire network 5. Achieve faster and more simple adoption of cloud 6. Improve TCO 7. Access a richer networking security feature set and higher performance 8. Improve ease of use through consistency of management tools for both on-premises and cloud 9. Simplify implementation through increased visibility into the public cloud network 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 4 of 50
5 Technology overview In a world where cloud computing is becoming the norm, IT managers are quickly realizing the benefits of services such as Infrastructure as a Service (IaaS). IaaS providers such as Azure allow organizations to deploy applications in a matter of minutes. Instead of procuring, installing, and managing hardware, which could take months to accomplish, you can easily use the on-demand and scalable compute services within Azure. This allows you to focus your resources on applications rather than on managing the data center and physical infrastructure. With the use of IaaS, expenses shift from fixed costs for hardware, software, and data center infrastructure to variable costs based on the usage of compute resources and the amount of data transferred between the private data center and the IaaS provider. To realize the full benefits that IaaS offers, secure and highly available connectivity to the Azure Transit VNet is needed. The use of Dynamic Multipoint VPN (DMVPN) connectivity to an Azure Transit VNet provides a costeffective solution for providing that connectivity. IP Security (IPSec) encryption of traffic, using strong cryptographic cipher-suites, provides secure connectivity between your private data center and the Azure Transit VNet. High availability is accomplished through the deployment of redundant Cisco CSR 1000V routers in the Azure Transit VNet. This deployment guide uses a pair of Cisco CSR 1000V Series Routers running Cisco IOS XE Software Release code. The current version of this deployment guide uses the Command-Line Interface (CLI) to configure the Cisco CSR 1000V. As stated, this deployment guide is a continuation of the Azure Transit VNet with Cisco Cloud Services Router 1000V Design and Deployment Guide. Therefore, it is assumed you have already deployed the Azure Transit VNet solution. Solution overview In the Azure Transit VNet with Cisco Cloud Services Router 1000V Deployment Guide, the focus is on providing connectivity between the Virtual Networks (VNet). Rather than creating a VNet peer to VNet peer for communications using the Azure native networking feature, we opt to use the Transit VNet architecture to simplify deployment and centralize operation. Dynamic Multipoint VPN (DMVPN) is used to create a VPN overlay in which spoke-to-spoke communication can occur without the traffic traversing the Transit VNet. In this use case, the Cisco CSR 1000V pair residing in the Transit VNet assumes the hub role and the CSR 1000V in the VNet is the spoke. DMVPN eliminates the need for spoke-to-spoke configuration for direct tunnels. When a spoke router wants to transmit a packet to another spoke router, it can now use Next Hop Resolution Protocol (NHRP) to determine dynamically the required destination address of the target spoke router. The hub router acts as the NHRP server, handling the request for the source spoke router. The two spoke routers dynamically create an IPSec tunnel between them to transfer the data directly. Figure 2 details this behavior as noted by the dotted line Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 5 of 50
6 Figure 2. Azure Transit VNet architecture All of this happens in the Azure platform. What happens if we want to connect our private data center to the Azure Transit VNet? How would we connect the private data center to the Azure Transit VNet? One solution would be to make the private data center edge device act as a spoke and connect it to the Azure Transit VNet. The private data center edge device would act just like a VNet spoke. An IPSec tunnel can be dynamically created between the VNet spoke and private data center edge device and direct spoke-to-spoke communication can occur. But what happens if we do not want the Azure Transit VNet to be our centralized point of communication and, instead, want to use the Cisco ASR 1000 in our private data center? Do we need to scrap our existing topology to accommodate the Azure Transit VNet architecture? If we want to use the private data center edge device as a centralized point of communication, we can make the edge device assume a DMVPN hub role, and the Cisco CSR 1000V in the Azure Transit VNet as a spoke. If this is the case, the Cisco CSR 1000V in the Azure Transit VNet would have a dual role: both DMVPN hub and spoke. The private data center edge device will act as DMVPN hubs. From the private data center edge device perspective, the CSR 1000V routers in the Azure Transit VNet would act as spokes. To the VNet spokes, the CSR 1000V routers in the Azure Transit VNet would act as hubs. How can we achieve this? 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 6 of 50
7 Technology considerations The following sections discuss technologies and configurations that are needed to make this solution work. Virtual Routing and Forwarding (VRF) To assume the dual role of a DMVPN hub and spoke, a separate routing table is needed. We use Virtual Routing and Forwarding (VRF) to solve this. When we deploy the Azure Transit VNet solution, a VRF is created. To deploy this particular solution, we need to create a VRF. The newly created VRF is then associated with a tunnel interface. This tunnel interface serves as an endpoint to the private data center edge. Route leaking Since we have two VRFs on each Cisco CSR 1000V in the Transit VNet, the VRFs maintain separate routes. The VNet spoke routers would not be able to communicate with the private data center edge device, and the private data center edge device would not be able to communicate with the VNet spokes. In order for the VNet spokes to communicate with the private data center edge and vice versa, routes must be shared between the VRFs. One way to do this is to use MP-BGP to leak routes between VRFs. In this case, Border Gateway Protocol (BGP) is aware of each of the VRFs and its contents, and selectively shares routes between them. Route Distinguishers (RD) are used to keep prefixes separate. If we need to share routes between VRFs, we need to export routes from certain VRFs and import them into selected VRFs. This is accomplished using Route Targets (RT). Routing protocols BGP is used to propagate routes from the private data center to the Azure Transit VNet, specifically internal BGP (ibgp), while Enhanced Interior Routing Gateway Protocol (EIGRP) is used for interior routing. An alternative is to use external BGP (ebgp) instead of ibgp to advertise routes to the private data center. Using ebgp will give you more flexibility as far as controlling which routes can be propagated via AS-path prepending. This is required if you are implementing Application Visibility and Control (AVC) or your traffic need to traverse a firewall. Also, keep in mind that route learned via ibgp will not be advertised back to another ibgp by default. Thus, it is recommended to use ebgp. If you do use ibgp, you can use route reflector to solve this issue. For the interior routing protocol, it is best to simply configure and troubleshoot by avoiding route redistribution. Instead of using EIGRP, you can use ebgp to avoid route redistribution. Another alternative is to use EIGRP throughout. For this deployment guide, we will use ibgp for private data center to Azure Transit VNet and EIGRP for the Azure Transit VNet to VNet spokes. This is done to accommodate the most use case scenarios, and also to demonstrate how a route redistribution would work if you have an existing EIGRP in your network. Route redistribution VNet spokes and the private data center need to share certain routes. Since we are running EIGRP in their respective networks, we will need route redistribution specifically, routes learned via EIGRP into BGP and routes learned via BGP into EIGRP Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 7 of 50
8 Azure security groups In order for the Multipoint Generic Routing Encapsulation (mgre) and IPSec tunnel to be established, we need to ensure that UDP port 500 and UDP port 4500 are open. This can be verified in the Azure security group associated with the Cisco CSR 1000V. For the private data center edge device, ensure that the necessary ports are open on your firewall. High availability Each of the Cisco CSR 1000V routers in the Azure Transit VNet will initiate an IPSec tunnel to the private data center edge device. The pair of CSR 1000Vs operates in active/active mode and provides redundancy. An issue with one CSR 1000V router will result in a failover. It is possible to provide redundancy on the private data center side, but this guide will not cover that scenario. In the private data center edge device, we will use a Cisco CSR 1000V. Configurations on the CSR 1000V can be applied to other Cisco devices that support the features used in this solution. Scalability Once we deploy the solution in this guide, additional spokes can be added to the existing topology. Any remote branch will assume a DMVPN spoke role and can initiate a connection to the private data center edge device. Any direct spoke-to-spoke communications can occur even with the VNet spokes in the Azure platform Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 8 of 50
9 Figure 3 depicts the overall topology when both solutions are deployed. Figure 3. Private data center to Azure Transit VNet Solution deployment This deployment guide focuses on the connectivity over the Internet between the Azure Transit VNet and an onpremises private data center. We will utilize a dynamic VPN overlay, specifically DMVPN to achieve this connectivity Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 9 of 50
10 Figure 4 depicts this particular connectivity. Figure 4. Private data center to Azure Transit VNet deployment The overall processes to deploy the solution are as follows: 1. Configure the hub for DMVPN. 2. Configure the spokes for DMVPN. 3. Verify the solution. Figure 5 provides guidelines on how to read commands given in this guide. Figure 5. How to read commands in this guide Configure the hub for DMVPN Use this process to configure DMVPN on the Cisco CSR 1000V Series routers in your on-premises data center. For this deployment guide, we are using the Cisco CSR 1000V, but you may use other Cisco routers, such as the Cisco ASR 1000 Series Aggregation Services Routers. This section describes the following configurations: 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 10 of 50
11 1. IKEv1 2. IPSec 3. Tunnel interfaces 4. Dynamic routing Procedure 1: Configure IKEv1 An IKE policy defines a combination of security parameters to be used during IKE negotiation. IKEv1 or IKEv2 may be used, depending on whether or not your device supports it. For our deployment scenario, we will use IKEv1. Note: The following configurations are taken from the existing deployment of the Azure Transit VNet. If you have deployed the Azure Transit VNet solution, you will have similar configurations. You can either use the configurations the Azure Transit VNet solution uses or create your own based on the steps given below. We recommend using the existing configurations to simplify deployment. Step 1. Configure the IKEv1 policies for the on-premises hub Cisco CSR 1000V deployment guide. crypto isakmp policy 300 encr aes authentication pre-share group 5 Step 2. Configure the IKE preshared keys. IKE preshared keys are used to authenticate the Cisco CSR 1000V with other routers in the DMVPN solution during the establishment of an Internet Security Association and Key Management Protocol (ISAKMP) Security Association (SA). The following configuration uses a keyring to store preshared keys for all of the IPSec VPN tunnels. crypto keyring keyring-tvnet-tun-11 local-address GigabitEthernet2 pre-shared-key address key ciscokey Procedure 2: Configure IPSec An IPSec transform set defines a combination of security parameters to be used for IPSec SAs. Step 1. Configure the IPSec transform sets. crypto ipsec transform-set transform-tvnet-tun-11 esp-aes esp-sha-hmac mode transport Step 2. Configure the IPSec profiles. crypto ipsec profile profile-tvnet-tun-11 set transform-set transform-tvnet-tun Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 11 of 50
12 We also recommend that you configure the following: 1. Increase the IPSec anti-replay window to the full 1024 window size, in order to eliminate any potential antireplay problems. 2. Configure IKE Dead Peer Detection (DPD) between the peers on an on-demand basis with a keep-alive interval of 30 seconds and a retry interval of 5 seconds. Step 3. Configure additional IKE and IPSec parameters on the on-premises Cisco CSR 1000V. crypto isakmp keepalive 30 5 crypto ipsec security-association replay window-size 1024 Procedure 3: Configure tunnel interface Once the IPSec profile is created, we need to associate it with a tunnel interface. Use the following steps to configure the hub router for mgre and IPSec integration as well as creating the tunnel interface. Step 1. Create the tunnel interface, and assign an IP address. interface Tunnel12 ip address Step 2. Configure Next Hop Resolution Protocol (NHRP) under the tunnel interface you just created. ip nhrp authentication cisco ip nhrp network-id 1025 ip nhrp redirect Step 3. Set the tunnel source address for the tunnel. This is a public-facing interface. tunnel source GigabitEthernet2 Step 4. Set the encapsulation mode to mgre, and set the tunnel key. All hubs and spokes that are in the same DMVPN network must have the same value. tunnel mode gre multipoint tunnel key Step 5. Associate the tunnel interface with an IPSec profile you created earlier. tunnel protection ipsec profile profile-tvnet-tun-11 We also recommend the following configuration under the tunnel interface: 1. Set the maximum transmission unit size. 2. Prevent the router from sending redirect messages to clients via Internet Control Message Protocol (ICMP). 3. Adjust the maximum segment size value of Transmission Control Protocol (TCP). Step 6. Configure additional parameters related to the tunnel interface. no ip redirects ip mtu 1400 ip tcp adjust-mss Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 12 of 50
13 Procedure 4: Configure routing This guide uses BGP routing between the spoke routers that reside in your Transit VNet and in your private data center. Within your private network, Enhanced Interior Gateway Routing Protocol (EIGRP) is implemented. The routes learned via BGP are redistributed into EIGRP. This guide assumes that you are familiar with routing protocols, specifically BGP and EIGRP. Detailed explanations of each command will be omitted. Step 1. Configure the EIGRP key chain and key. key chain EIGRP-KEY key 1 key-string C1sco123 Note: Use the global configuration command service password-encryption as an additional security setting within Cisco routers to hide passwords when viewing the configuration. Step 2. Configure EIGRP routing. Note that EIGRP autonomous-system 100 is configured within the private network. router eigrp Multicloud address-family ipv4 unicast autonomous-system 100 af-interface default passive-interface exit-af-interface af-interface GigabitEthernet3 authentication mode md5 authentication key-chain EIGRP-KEY no passive-interface exit-af-interface network exit-address-family Note: The EIGRP is configured using named mode. You should be able to achieve the same functionality using legacy methods. This guide uses two interfaces on the Cisco CSR 1000V Series routers (GigabitEthernet2 and GigabitEthernet3) to separate encrypted traffic from unencrypted traffic. Interface GigabitEthernet2 is the source interface for the IPSec connections, referenced by the tunnel source command, whereas GigabitEthernet3 is the private network and EIGRP is enabled on this particular interface. Step 3. Configure routes to the outside network. Depending on your environment, make sure you have routes to reach spoke routers. ip route x.x.x.x x.x.x.x Step 4. Configure BGP routing. This guide uses BGP routing between the spoke router and your private data center Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 13 of 50
14 router bgp bgp router-id bgp log-neighbor-changes neighbor remote-as neighbor next-hop-self neighbor remote-as neighbor next-hop-self Note: The above BGP configurations may look different, depending on whether or not you use address-family context. Either way, you should be able to achieve the same functionality with the commands listed. Step 5. Create an access list and a route-map to control what routes are being redistributed. In our scenario, we want the capability to control what routes are being redistributed from EIGRP into BGP and from BGP into EIGRP. There are multiple ways to accomplish this. For this guide, we will use route-maps. First, we need to create a criterion to use to match the routes. This will be in the form of an access-list. Two access lists will be created. One is onprem, which will be used to match the routes we want to redistribute coming from the private data center, while the other, vnetspokes, will be used to redistribute the routes coming from the VNet spokes in the Azure platform. Once the access lists are created, we can use them in a route-map to match the route specified in the access list. Use the commands below to create two access lists. ip access-list standard onprem permit ip access-list standard vnetspokes permit permit permit Use the commands below to create two route-maps and to match the routes created in the access lists. route-map onprem permit 10 match ip address onprem route-map vnetspokes permit 10 match ip address vnetspokes 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 14 of 50
15 Step 6. Redistribute routes learned via BGP into EIGRP. router eigrp Multicloud address-family ipv4 unicast autonomous-system 100 topology base redistribute bgp metric route-map vnetspokes exit-af-topology exit-address-family Routes learned via BGP from the spokes are redistributed into EIGRP. A route-map named vnetspokes is used to control which BGP-learned routes are redistributed into EIGRP. Step 7. Redistribute routes learned via EIGRP into BGP. router bgp redistributed connected redistribute eigrp 100 route-map onprem Routes learned via EIGRP are redistributed to BGP, rather than having the ebgp peer originate a default route, or simply configuring a network under the IPv4 address-family configuration. This is done primarily to demonstrate how route propagation can be used to limit access to spokes with certain subnets within the private network. A route-map named onprem is used to control which EIGRP-learned routes are redistributed to BGP. Note that we have also used the redistributed connected command. This is needed to propagate the connected interface, specifically the network of the tunnel interface. If you wish to filter other connected interfaces, use the route-map option to accomplish this. At this point, you should have the DMVPN hub configured. Refer to Appendix C: Sample Cisco CSR 1000V DMVPN hub configuration to see the final configurations. Configure the spokes for DMVPN This deployment guide assumes you have implemented the Transit VNet with the Cisco CSR 1000V solution. This solution uses DMVPN technology. For details on how to deploy the Transit VNet solution for the Azure platform, refer to the additional resources at the end of this document. In the Transit VNet architecture, the pair of Cisco CSR 1000V routers that are located in the Transit VNet act as a DMVPN hub.the VNet, which acts as a DMVPN spoke, connects to the hub via a Cisco CSR 1000V router. When we connect the pair of CSR 1000V routers in the Transit VNet back to the private network, their role switches to spoke. The on-premises device in the private data center acts as a hub. At the same time, the CSR 1000V routers within the Transit VNet maintain the hub role for the VNet spokes. We can accomplish this dual role by way of using Virtual Routing and Forwarding (VRF). Use this process to configure a DMVPN spoke on the Cisco CSR 1000V Series routers within your Transit VNet in the Azure platform Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 15 of 50
16 This section configures the following: 1. Virtual Routing and Forwarding (VRF) 2. IKEv1 3. IPSec 4. Tunnel interfaces 5. Dynamic routing Procedure 1: Create a Virtual Routing and Forwarding (VRF) instance As previously mentioned, in order for our solution to work, we need to create a Virtual Routing and Forwarding (VRF) instance on each of the Cisco CSR 1000V routers located in the Azure Transit VNet. This will give us the dual hub-and-spoke role necessary for this solution. Two Cisco CSR 1000V routers need to be configured within the Transit VNet. Ensure that you have configured both devices before you go through the following steps. Follow the steps below to create a VRF on both of the Cisco CSR 1000V routers. Step 1. Create a VRF on the Cisco CSR 1000V routers. If you have deployed the Azure Transit VNet, there should already be an existing VRF configuration complete with Route Distinguishers (RD) and route-target import and export statements. Sample VRF configurations on the existing CSR 1000V routers: ip vrf tvnet-tun-11 rd 65050:11 route-target export 65050:0 route-target import 65050:0 Use the commands below to create a new VRF as well as to modify the existing VRF. Note: The Route Distinguisher (RD) and the Route Target (RT) do not have to be the same. We have purposely kept it the same for ease of troubleshooting. CSR 1000v-1 ip vrf onprem-tun-12 rd 65041:12 route-target export 65041:12 route-target import 65041:12 route-target import 65040:11 ip vrf tvnet-tun-11 rd 65040:11 route-target export 65040:11 route-target import 65040:11 route-target import 65041: Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 16 of 50
17 CSR 1000v-2 ip vrf onprem-tun-12 rd 65041:12 route-target export 65041:12 route-target import 65041:12 route-target import 65040:11 ip vrf tvnet-tun-11 rd 65040:11 route-target export 65040:11 route-target import 65040:11 route-target import 65041:12 Procedure 2: Configure IKEv1 IKE policy configuration is similar to that shown in the previous section. To simplify deployment, we will use the existing configurations. This is the same configurations as is used in the Azure Transit VNet deployment. The IKEv1 must match the previous configurations. Listed below are the existing configurations on the DMVP spoke for IKEv1. Compare the IKEv1 configurations with your DMVPN hub device. Step 1. Verify IKEv1 configurations on both the Cisco CSR 1000V routers. crypto isakmp policy 300 encr aes authentication pre-share group 5 crypto keyring keyring-tvnet-tun-11 local-address GigabitEthernet2 pre-shared-key address key ciscokey Procedure 3: Configure IPSec Again, you should have an existing configuration on the Cisco CSR 1000V routers. Verify this to ensure the configuration matches with the DMVPN hub device. Step 1. Verify the IPSec configurations on both of the CSR 1000V routers. crypto ipsec transform-set transform-tvnet-tun-11 esp-aes esp-sha-hmac mode transport crypto ipsec profile profile-tvnet-tun-11 set transform-set transform-tvnet-tun-11 crypto isakmp keepalive Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 17 of 50
18 crypto ipsec security-association replay window-size 1024 Procedure 3: Configure tunnel interface Use the following steps to configure the hub router for mgre and IPSec integrations and for creating the tunnel interface. Step 1. Create the tunnel interface, place it in a VRF, and assign an IP address. Make sure this is configured on both Cisco CSR 1000V routers. CSR 1000v-1 interface Tunnel12 ip vrf forwarding onprem-tun-12 ip address CSR 1000v-1 interface Tunnel12 ip vrf forwarding onprem-tun-12 ip address Step 2. Configure Next Hop Resolution Protocol (NHRP) under the tunnel interface you just created. ip nhrp authentication cisco ip nhrp network-id 1025 Since this is the spoke configuration, we need to configure the hub router as the NHRP next-hop server. Use the following command to configure this. The first IP address is the tunnel IP of the hub router. The second IP address is the IP that is reachable from this particular spoke CSR 1000V. ip nhrp nhs nbma multicast Step 3. Set the tunnel source address for the tunnel. This is the public-facing interface. tunnel source GigabitEthernet1 Step 4. Set the encapsulation mode to mgre, and set the tunnel key. All hub and spokes that are in the same DMVPN network must have the same value. tunnel mode gre multipoint tunnel key Step 5. Associate the tunnel interface with the IPSec profile you created earlier. tunnel protection ipsec profile profile-tvnet-tun-11 shared Note: Ensure that the shared keyword is used. If not, you will get an error since we are sharing the IPSec profile with multiple VRFs. We also recommend the following configuration under the tunnel interface, in order to: 1. Set the maximum transmission unit size 2. Prevent the router from sending redirect messages to clients via ICMP 3. Adjust the maximum segment size value of TCP packets 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 18 of 50
19 Step 6. Configure additional parameters related to the tunnel interface: no ip redirects ip mtu 1400 ip tcp adjust-mss 1360 Procedure 4: Configure routing BGP is used to propagate routes between the spoke routers that reside on your Transit VNet and your private data center, whereas EIGRP is used between the Transit VNet spokes and the Transit VNet. The routes learned via BGP are redistributed to EIGRP, and routes learned via EIGRP are redistributed to BGP. Step 1. Verify EIGRP configurations on both the Cisco CSR 1000V routers. Note: You do not need to create or modify the existing configurations. This configuration is created when you deploy the Azure Transit VNet with the Cisco CSR 1000V solution. CSR 1000v-1 router eigrp address-family ipv4 vrf tvnet-tun-11 network CSR 1000v-2 passive-interface default no passive-interface Tunnel11 autonomous-system eigrp router-id exit-address-family router eigrp address-family ipv4 vrf tvnet-tun-11 network passive-interface default no passive-interface Tunnel11 autonomous-system eigrp router-id exit-address-family Step 2. Verify that a default route to the outside network exists. When you deploy the Azure Transit VNet solution, it creates a default route, which should look similar to the output below. ip route Step 3. Configure BGP routing. This guide uses BGP routing between the spoke router and your private data center. The following commands configure BGP with two address families, one for each VRF. It forms a neighbor with the hub router, , which is the tunnel IP address Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 19 of 50
20 CSR 1000v-1 router bgp bgp router-id bgp log-neighbor-changes address-family ipv4 vrf onprem-tun-12 neighbor remote-as neighbor activate neighbor next-hop-self exit-address-family address-family ipv4 vrf tvnet-tun-11 exit-address-family CSR 1000v-2 router bgp bgp router-id bgp log-neighbor-changes address-family ipv4 vrf onprem-tun-12 neighbor remote-as neighbor activate neighbor next-hop-self exit-address-family address-family ipv4 vrf tvnet-tun-11 exit-address-family Step 4. Create an access list and a route-map to control what routes are being redistributed. In our scenario, we want the capability to control what routes are being redistributed from EIGRP to BGP and from BGP to EIGRP. There are multiple ways to accomplish this. For this guide, we will use route-maps. First, we need to create a criterion that we can use to match the routes. This will be in the form of an access list. Two access lists will be created. One is onprem, which will be used to match the routes we want to redistribute coming from the private data center, whereas the other, vnetspokes, is used to redistribute specific routes coming from the VNet spokes in the Azure platform Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 20 of 50
21 Once the access lists are created, we can use them in a route-map to match the route specified in the lists. Use the commands below to create two access lists. Remember to configure them on both of the CSR 1000V routers. ip access-list standard onprem permit permit permit ip access-list standard vnetspoke permit permit Use the commands below to create two route-maps and to match the routes created in the access lists. route-map onprem permit 10 match ip address onprem route-map vnetspoke permit 10 match ip address vnetspoke Step 5. Redistribute the routes learned via BGP to EIGRP. router eigrp address-family ipv4 vrf vrf tvnet-tun-11 redistribute bgp metric route-map onprem Routes learned via BGP from the spokes are redistributed to EIGRP. A route-map named vnetspokes is used to control which BGP learned routes are redistributed to EIGRP. Step 6. Redistribute routes learned via EIGRP to BGP. Again, this should be configured on both of the CSR 1000V routers. router bgp address-family ipv4 vrf onprem-tun-12 redistributed connected redistribute eigrp 100 route-map onprem exit-address-family address-family ipv4 vrf tvnet-tun-11 redistribute connected redistribute eigrp route-map vnetspoke exit-address-family At this point, you should have both of the DMVPN spokes configured. Refer to Appendix A: Sample Cisco CSR 1000V-1 DMVPN spoke configuration and Appendix B: Sample Cisco CSR 1000V-2 DMVPN spoke configuration to see the final configurations Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 21 of 50
22 Verify the solution Once you have completed the configurations of the DMVPN hubs and spokes, you can use the following steps to verify the working state of the solution. You can use the steps in any order. The commands are verified on the CSR 1000V routers. 1. Show run interface tunnel xx. 2. Show crypto isakmp sa. 3. Show dmvpn. 4. Show ip router bgp. 5. Show ip route. Step 1. Verify the tunnel interface configuration. Things to look out for: 1. On the spoke static-nhrp mapping, indicating that the hub interface IP is behind a Non-Broadcast Multiple Access Network (NBMA) address. 2. On hub and spoke that the NHRP network ID is configured. 3. On the spoke that the tunnel protection profile is shared. 4. On the spoke that the tunnel interface is on a separate VRF. show run interface tunnel 12 Sample output: Show interface configuration. transitvnet-csr-1#show run interface tunnel 12 Building configuration... Current configuration : 398 bytes interface Tunnel12 ip vrf forwarding onprem-tun-12 ip address no ip redirects ip mtu 1400 ip nhrp authentication cisco ip nhrp network-id 1025 ip nhrp nhs nbma multicast ip tcp adjust-mss 1360 tunnel source GigabitEthernet1 tunnel mode gre multipoint tunnel key tunnel protection ipsec profile profile-tvnet-tun-11 shared end transitvnet-csr-1# 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 22 of 50
23 Step 2. Display the IKE SA. If IKE negotiations are successful, it will display a state of QM_IDLE. show crypto isakmp sa Sample output: Show IKE session. transitvnet-csr-1#show crypto isakmp sa IPv4 Crypto ISAKMP SA dst src state conn-id status QM_IDLE 1071 ACTIVE QM_IDLE 1072 ACTIVE QM_IDLE 1070 ACTIVE IPv6 Crypto ISAKMP SA transitvnet-csr-1# Step 3. Display DMVPN-specific session information. Refer to the sample output below: notice, on the Transit VNet CSR 1000V router, that it shows that this particular device is both a hub and a spoke. It is a hub to the spoke VNets and a spoke to the on-premise private data center device. show dmvpn Sample output: Show DMVPN sessions. transitvnet-csr-1#show dmvpn Legend: Attrb --> S - Static, D - Dynamic, I - Incomplete N - NATed, L - Local, X - No Socket T1 - Route Installed, T2 - Nexthop-override C - CTS Capable, I2 - Temporary # Ent --> Number of NHRP entries with same NBMA peer NHS Status: E --> Expecting Replies, R --> Responding, W --> Waiting UpDn Time --> Up or Down Time for a Tunnel ========================================================================== Interface: Tunnel11, IPv4 NHRP Details Type:Hub, NHRP Peers:2, # Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb UP 2w2d DN UP 2w2d DN Interface: Tunnel12, IPv4 NHRP Details 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 23 of 50
24 Type:Spoke, NHRP Peers:1, # Ent Peer NBMA Addr Peer Tunnel Add State UpDn Tm Attrb UP 3d03h S transitvnet-csr-1# Step 4. Verify BGP neighbors. show ip bgp vpnv4 vrf onprem-tun-12 summary show ip bgp summary Sample output: Show BGP neighbors. transitvnet-csr-1#show ip bgp vpnv4 vrf onprem-tun-12 summary BGP router identifier , local AS number BGP table version is 49, main routing table version network entries using 6144 bytes of memory 25 path entries using 3400 bytes of memory 18/11 BGP path/bestpath attribute entries using 5328 bytes of memory 1 BGP AS-PATH entries using 24 bytes of memory 4 BGP extended community entries using 774 bytes of memory 0 BGP route-map cache entries using 0 bytes of memory 0 BGP filter-list cache entries using 0 bytes of memory BGP using total bytes of memory BGP activity 543/495 prefixes, 638/589 paths, scan interval 60 secs Neighbor V AS MsgRcvd MsgSent TblVer InQ OutQ Up/Down State/PfxRcd d02h 19 transitvnet-csr-1# Step 5. Verify the routes on the spoke that resides on the Transit VNet, and that each of the spokes deployed is in a separate VRF. To verify the latter, we must specify the VRF we want to check the routes on. For the DMVPN hub, we can use the command without the VRF option. Also verify the routes on the hub and ensure that the hub is exchanging routes with the DMVPN spokes. show ip route show ip route vrf onprem-tun Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 24 of 50
25 Sample output: Show IP routes. transitvnet-csr-1#show ip route vrf onprem-tun-12 Routing Table: onprem-tun-12 Codes: L - local, C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route, H - NHRP, l - LISP a - application route + - replicated route, % - next hop override, p - overrides from PfR Gateway of last resort is not set /8 is variably subnetted, 22 subnets, 5 masks B /30 [200/15360] via , 3d02h B /30 [200/15360] via , 3d02h B /30 [200/20480] via , 3d02h B /32 [200/21120] via , 3d02h B /32 [200/21120] via , 3d02h B /32 [200/16000] via , 3d02h B /32 [200/0] via , 3d02h B /30 [200/25600] via , 3d02h B /30 [200/25600] via , 3d02h B /29 [200/0] via , 3d02h B /29 [200/0] via , 3d02h B /28 [200/15360] via , 3d02h B /29 [200/15360] via , 3d02h B /29 [200/15360] via , 3d02h B /29 [200/20480] via , 3d02h B /29 [200/15360] via , 3d02h B /24 [20/ ] via (tvnet-tun-11), 3d04h, Tunnel11 B /24 [20/ ] via (tvnet-tun-11), 3d04h, Tunnel11 B /24 [20/ ] via (tvnet-tun-11), 3d04h, Tunnel Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 25 of 50
26 B /24 [20/ ] via (tvnet-tun-11), 3d04h, Tunnel11 B /24 [200/0] via , 3d02h B /24 [200/0] via , 3d02h /16 is variably subnetted, 2 subnets, 2 masks B /24 is directly connected, 3d04h, Tunnel11 L /32 is directly connected, Tunnel /16 is variably subnetted, 2 subnets, 2 masks C /24 is directly connected, Tunnel12 L /32 is directly connected, Tunnel12 transitvnet-csr-1# Step 6. Repeat the steps above to verify Transit VNet CSR 1000V-2 and the on-premises CSR 1000V. The output is similar whether it is from a hub or a spoke CSR 1000V router. Appendix A: Sample Cisco CSR 1000V-1 DMVPN spoke configuration The following is the configuration of the first Cisco CSR 1000V Series Router used in the Transit VNet. It is running IOS XE version transitvnet-csr-1#show running-config Building configuration... Current configuration : 4558 bytes Last configuration change at 20:29:12 UTC Fri Sep by cisco version 16.7 service timestamps debug datetime msec service timestamps log datetime msec platform qfp utilization monitor load 80 no platform punt-keepalive disable-kernel-core platform console virtual hostname transitvnet-csr-1 boot-start-marker boot-end-marker logging persistent size filesize 8192 immediate 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 26 of 50
27 aaa new-model aaa authentication login default local aaa authorization exec default local none aaa session-id common ip vrf onprem-tun-12 rd 65041:12 route-target export 65041:12 route-target import 65041:12 route-target import 65040:11 ip vrf tvnet-tun-11 rd 65040:11 route-target export 65040:11 route-target import 65040:11 route-target import 65041:12 ip domain name transitvnet-csr-1.cloudapp.net 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 27 of 50
28 subscriber templating multilink bundle-name authenticated license udi pid CSR 1000V sn 93DURIBRV2D no license smart enable diagnostic bootup level minimal spanning-tree extend system-id username cisco privilege 15 password 0 poppee12345 redundancy 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 28 of 50
29 crypto keyring keyring-tvnet-tun-11 local-address GigabitEthernet1 pre-shared-key address key ciscokey crypto isakmp policy 300 encr aes authentication pre-share group 5 crypto isakmp keepalive 30 5 crypto ipsec security-association replay window-size 1024 crypto ipsec transform-set transform-tvnet-tun-11 esp-aes esp-sha-hmac mode transport crypto ipsec profile profile-tvnet-tun-11 set transform-set transform-tvnet-tun-11 interface Tunnel11 ip vrf forwarding tvnet-tun-11 ip address no ip redirects 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 29 of 50
30 ip mtu 1400 ip nhrp authentication cisco ip nhrp network-id 1024 ip nhrp redirect load-interval 30 tunnel source GigabitEthernet1 tunnel mode gre multipoint tunnel key tunnel protection ipsec profile profile-tvnet-tun-11 shared interface Tunnel12 ip vrf forwarding onprem-tun-12 ip address no ip redirects ip mtu 1400 ip nhrp authentication cisco ip nhrp network-id 1025 ip nhrp nhs nbma multicast ip tcp adjust-mss 1360 tunnel source GigabitEthernet1 tunnel mode gre multipoint tunnel key tunnel protection ipsec profile profile-tvnet-tun-11 shared interface VirtualPortGroup0 ip address ip nat inside no mop enabled no mop sysid interface GigabitEthernet1 ip address dhcp ip nat outside negotiation auto no mop enabled no mop sysid interface GigabitEthernet2 ip address dhcp negotiation auto 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 30 of 50
31 no mop enabled no mop sysid router eigrp address-family ipv4 vrf tvnet-tun-11 redistribute bgp metric route-map onprem network passive-interface default no passive-interface Tunnel11 autonomous-system eigrp router-id exit-address-family router bgp bgp router-id bgp log-neighbor-changes address-family ipv4 vrf onprem-tun-12 redistribute connected neighbor remote-as neighbor activate neighbor next-hop-self exit-address-family address-family ipv4 vrf tvnet-tun-11 redistribute connected redistribute eigrp route-map vnetspoke exit-address-family iox ip nat inside source list GS_NAT_ACL interface GigabitEthernet1 overload ip forward-protocol nd ip tcp window-size ip http server no ip http secure-server ip route ip ssh window-size Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 31 of 50
32 ip ssh rsa keypair-name sshkeys ip scp server enable ip access-list standard GS_NAT_ACL permit ip access-list standard onprem permit permit permit ip access-list standard vnetspoke permit permit route-map onprem permit 10 match ip address onprem route-map vnetspoke permit 10 match ip address vnetspoke control-plane line con 0 stopbits 1 line aux 0 stopbits 1 line vty 0 4 exec-timeout 25 0 transport input ssh line vty Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 32 of 50
33 transport input ssh wsma agent exec wsma agent config wsma agent filesys wsma agent notify app-hosting appid guestshell vnic gateway1 virtualportgroup 0 guest-interface 0 guest-ipaddress netmask gateway name-server end transitvnet-csr-1# Appendix B: Sample Cisco CSR 1000V-2 DMVPN spoke configuration The following is the configuration of the second Cisco CSR 1000V Series Router used in the Transit VNet. It is running IOS XE version transitvnet-csr-2#show running-config Building configuration... Current configuration : 4558 bytes Last configuration change at 01:33:20 UTC Wed Sep by cisco version 16.7 service timestamps debug datetime msec service timestamps log datetime msec platform qfp utilization monitor load 80 no platform punt-keepalive disable-kernel-core platform console virtual hostname transitvnet-csr Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 33 of 50
Cisco Multicloud Portfolio: Cloud Connect
 Design and Deployment Guide Cisco Multicloud Portfolio: Cloud Connect Design and Deployment Guide for Private Data Center to AWS VPC October 2018 2018 Cisco and/or its affiliates. All rights reserved.
Design and Deployment Guide Cisco Multicloud Portfolio: Cloud Connect Design and Deployment Guide for Private Data Center to AWS VPC October 2018 2018 Cisco and/or its affiliates. All rights reserved.
Shortcut Switching Enhancements for NHRP in DMVPN Networks
 Shortcut Switching Enhancements for NHRP in DMVPN Networks Routers in a Dynamic Multipoint VPN (DMVPN) Phase 3 network use Next Hop Resolution Protocol (NHRP) Shortcut Switching to discover shorter paths
Shortcut Switching Enhancements for NHRP in DMVPN Networks Routers in a Dynamic Multipoint VPN (DMVPN) Phase 3 network use Next Hop Resolution Protocol (NHRP) Shortcut Switching to discover shorter paths
Migrating from Dynamic Multipoint VPN Phase 2 to Phase 3: Why and How to Migrate to the Next Phase
 Migration Guide Migrating from Dynamic Multipoint VPN Phase 2 to Phase 3: Why and How to Migrate to the Next Phase This guide shows how a Dynamic Multipoint VPN (DMVPN) deployment can be migrated to make
Migration Guide Migrating from Dynamic Multipoint VPN Phase 2 to Phase 3: Why and How to Migrate to the Next Phase This guide shows how a Dynamic Multipoint VPN (DMVPN) deployment can be migrated to make
DMVPN to Group Encrypted Transport VPN Migration
 DMVPN to Group Encrypted Transport VPN Migration This document provides the steps for Dynamic Multipoint VPN (DMVPN) to Group Encrypted Transport VPN migration. DMVPN to Group Encrypted Transport VPN Migration
DMVPN to Group Encrypted Transport VPN Migration This document provides the steps for Dynamic Multipoint VPN (DMVPN) to Group Encrypted Transport VPN migration. DMVPN to Group Encrypted Transport VPN Migration
IPsec Virtual Tunnel Interfaces
 IPsec virtual tunnel interfaces (VTIs) provide a routable interface type for terminating IPsec tunnels and an easy way to define protection between sites to form an overlay network IPsec VTIs simplify
IPsec virtual tunnel interfaces (VTIs) provide a routable interface type for terminating IPsec tunnels and an easy way to define protection between sites to form an overlay network IPsec VTIs simplify
FlexVPN HA Dual Hub Configuration Example
 FlexVPN HA Dual Hub Configuration Example Document ID: 118888 Contributed by Piotr Kupisiewicz, Wen Zhang, and Frederic Detienne, Cisco TAC Engineers. Apr 08, 2015 Contents Introduction Prerequisites Requirements
FlexVPN HA Dual Hub Configuration Example Document ID: 118888 Contributed by Piotr Kupisiewicz, Wen Zhang, and Frederic Detienne, Cisco TAC Engineers. Apr 08, 2015 Contents Introduction Prerequisites Requirements
IPv6 over DMVPN. Finding Feature Information
 This document describes how to implement the Dynamic Multipoint VPN for IPv6 feature, which allows users to better scale large and small IPsec Virtual Private Networks (VPNs) by combining generic routing
This document describes how to implement the Dynamic Multipoint VPN for IPv6 feature, which allows users to better scale large and small IPsec Virtual Private Networks (VPNs) by combining generic routing
Basic Router Configuration
 This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
Implementing Dynamic Multipoint VPN for IPv6
 Implementing Dynamic Multipoint VPN for IPv6 First Published: July 11, 2008 Last Updated: November 24, 2010 This document describes how to implement Dynamic Multipoint VPN for IPv6 feature, which allows
Implementing Dynamic Multipoint VPN for IPv6 First Published: July 11, 2008 Last Updated: November 24, 2010 This document describes how to implement Dynamic Multipoint VPN for IPv6 feature, which allows
RR> RR> RR>en RR# RR# RR# RR# *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 RR#
 RR> RR> RR>en *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 term len 0 show run Building configuration... Current configuration : 2568 bytes version 15.4 service timestamps debug
RR> RR> RR>en *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 term len 0 show run Building configuration... Current configuration : 2568 bytes version 15.4 service timestamps debug
HOME-SYD-RTR02 GETVPN Configuration
 GETVPN OVER DMVPN Topology Details HOME-SYD-RTR02 is GETVPN KS. R2 & R3 are GETVPN Members. R2 is DMVPN Hub. R3 is DMVPN Spoke. HOME-PIX01 is Firewall between R2 and R3. IP Addressing Details HOME-SYD-RTR01
GETVPN OVER DMVPN Topology Details HOME-SYD-RTR02 is GETVPN KS. R2 & R3 are GETVPN Members. R2 is DMVPN Hub. R3 is DMVPN Spoke. HOME-PIX01 is Firewall between R2 and R3. IP Addressing Details HOME-SYD-RTR01
GRE and DM VPNs. Understanding the GRE Modes Page CHAPTER
 CHAPTER 23 You can configure Generic Routing Encapsulation (GRE) and Dynamic Multipoint (DM) VPNs that include GRE mode configurations. You can configure IPsec GRE VPNs for hub-and-spoke, point-to-point,
CHAPTER 23 You can configure Generic Routing Encapsulation (GRE) and Dynamic Multipoint (DM) VPNs that include GRE mode configurations. You can configure IPsec GRE VPNs for hub-and-spoke, point-to-point,
Configuring FlexVPN Spoke to Spoke
 Last Published Date: March 28, 2014 The FlexVPN Spoke to Spoke feature enables a FlexVPN client to establish a direct crypto tunnel with another FlexVPN client leveraging virtual tunnel interfaces (VTI),
Last Published Date: March 28, 2014 The FlexVPN Spoke to Spoke feature enables a FlexVPN client to establish a direct crypto tunnel with another FlexVPN client leveraging virtual tunnel interfaces (VTI),
Intelligent WAN Multiple VRFs Deployment Guide
 Cisco Validated design Intelligent WAN Multiple VRFs Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deploying the Cisco IWAN Multiple VRFs...
Cisco Validated design Intelligent WAN Multiple VRFs Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deploying the Cisco IWAN Multiple VRFs...
Configuring Easy Virtual Network Shared Services
 Configuring Easy Virtual Network Shared Services This chapter describes how to use route replication and redistribution to share services in an Easy Virtual Network (EVN). Finding Feature Information,
Configuring Easy Virtual Network Shared Services This chapter describes how to use route replication and redistribution to share services in an Easy Virtual Network (EVN). Finding Feature Information,
DMVPN for R&S CCIE Candidates Johnny Bass CCIE #6458
 DMVPN for R&S CCIE Candidates Johnny Bass CCIE #6458 BRKCCIE-3003 @CCIE6458 2015 Cisco and/or its affiliates. All rights reserved. Cisco Public About the Presenter Johnny Bass Networking industry since
DMVPN for R&S CCIE Candidates Johnny Bass CCIE #6458 BRKCCIE-3003 @CCIE6458 2015 Cisco and/or its affiliates. All rights reserved. Cisco Public About the Presenter Johnny Bass Networking industry since
MPLS VPN Half-Duplex VRF
 The feature provides scalable hub-and-spoke connectivity for subscribers of an Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service. This feature addresses the limitations of hub-and-spoke
The feature provides scalable hub-and-spoke connectivity for subscribers of an Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service. This feature addresses the limitations of hub-and-spoke
Quick Note. Configure an IPSec VPN tunnel in Aggressive mode between a TransPort LR router and a Cisco router. Digi Technical Support 7 October 2016
 Quick Note Configure an IPSec VPN tunnel in Aggressive mode between a TransPort LR router and a Cisco router. Digi Technical Support 7 October 2016 Contents 1 Introduction... 3 1.1 Outline... 3 1.2 Assumptions...
Quick Note Configure an IPSec VPN tunnel in Aggressive mode between a TransPort LR router and a Cisco router. Digi Technical Support 7 October 2016 Contents 1 Introduction... 3 1.1 Outline... 3 1.2 Assumptions...
L2TP IPsec Support for NAT and PAT Windows Clients
 L2TP IPsec Support for NAT and PAT Windows Clients The L2TP IPsec Support for NAT and PAT Windows Clients feature allows mulitple Windows client to connect to an IPsec-enabled Cisco IOS Layer 2 Tunneling
L2TP IPsec Support for NAT and PAT Windows Clients The L2TP IPsec Support for NAT and PAT Windows Clients feature allows mulitple Windows client to connect to an IPsec-enabled Cisco IOS Layer 2 Tunneling
Configuring IPv6 Provider Edge over MPLS (6PE)
 Finding Feature Information, page 1 Configuring 6PE, page 1 Finding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature
Finding Feature Information, page 1 Configuring 6PE, page 1 Finding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature
Lab Configuring Per-Interface Inter-VLAN Routing (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
IOS/CCP: Dynamic Multipoint VPN using Cisco Configuration Professional Configuration Example
 IOS/CCP: Dynamic Multipoint VPN using Cisco Configuration Professional Configuration Example Document ID: 113265 Contents Introduction Prerequisites Requirements Components Used Conventions Background
IOS/CCP: Dynamic Multipoint VPN using Cisco Configuration Professional Configuration Example Document ID: 113265 Contents Introduction Prerequisites Requirements Components Used Conventions Background
Lab Configuring Per-Interface Inter-VLAN Routing (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
(Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
DMVPN for R&S CCIE Candidates
 DMVPN for R&S CCIE Candidates Johnny Bass CCIE #6458 BRKCCIE-3003 @CCIE6458 2014 Cisco and/or its affiliates. All rights reserved. Cisco Public About the Presenter Johnny Bass Networking industry since
DMVPN for R&S CCIE Candidates Johnny Bass CCIE #6458 BRKCCIE-3003 @CCIE6458 2014 Cisco and/or its affiliates. All rights reserved. Cisco Public About the Presenter Johnny Bass Networking industry since
Lab Configuring IPv4 Static and Default Routes (Solution)
 (Solution) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.0.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A R3 G0/1 192.168.1.1 255.255.255.0
(Solution) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.0.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A R3 G0/1 192.168.1.1 255.255.255.0
Cisco Group Encrypted Transport VPN
 Cisco Group Encrypted Transport VPN Q. What is Cisco Group Encrypted Transport VPN? A. Cisco Group Encrypted Transport is a next-generation WAN VPN solution that defines a new category of VPN, one that
Cisco Group Encrypted Transport VPN Q. What is Cisco Group Encrypted Transport VPN? A. Cisco Group Encrypted Transport is a next-generation WAN VPN solution that defines a new category of VPN, one that
MPLS VPN--Inter-AS Option AB
 The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service provider
The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service provider
Configuring Dynamic Multipoint VPN Using GRE Over IPsec With OSPF, NAT, and Cisco IOS Firewall
 Configuring Dynamic Multipoint VPN Using GRE Over IPsec With OSPF, NAT, and Cisco IOS Firewall Document ID: 43068 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
Configuring Dynamic Multipoint VPN Using GRE Over IPsec With OSPF, NAT, and Cisco IOS Firewall Document ID: 43068 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
ARCHIVED DOCUMENT. - The topics in the document are now covered by more recent content.
 ARCHIVED DOCUMENT This document is archived and should only be used as a historical reference and should not be used for new deployments for one of the following reasons: - The topics in the document are
ARCHIVED DOCUMENT This document is archived and should only be used as a historical reference and should not be used for new deployments for one of the following reasons: - The topics in the document are
Sharing IPsec with Tunnel Protection
 The feature allows sharing an IPsec security association database (SADB) between two or more generic routing encapsulation (GRE) tunnel interfaces when tunnel protection is used. Shared tunnel interfaces
The feature allows sharing an IPsec security association database (SADB) between two or more generic routing encapsulation (GRE) tunnel interfaces when tunnel protection is used. Shared tunnel interfaces
Cisco Dynamic Multipoint VPN: Simple and Secure Branch-to-Branch Communications
 Data Sheet Cisco Dynamic Multipoint VPN: Simple and Secure Branch-to-Branch Communications Product Overview Cisco Dynamic Multipoint VPN (DMVPN) is a Cisco IOS Software-based security solution for building
Data Sheet Cisco Dynamic Multipoint VPN: Simple and Secure Branch-to-Branch Communications Product Overview Cisco Dynamic Multipoint VPN (DMVPN) is a Cisco IOS Software-based security solution for building
Advanced IPv6 Training Course. Lab Manual. v1.3 Page 1
 Advanced IPv6 Training Course Lab Manual v1.3 Page 1 Network Diagram AS66 AS99 10.X.0.1/30 2001:ffXX:0:01::a/127 E0/0 R 1 E1/0 172.X.255.1 2001:ffXX::1/128 172.16.0.X/24 2001:ff69::X/64 E0/1 10.X.0.5/30
Advanced IPv6 Training Course Lab Manual v1.3 Page 1 Network Diagram AS66 AS99 10.X.0.1/30 2001:ffXX:0:01::a/127 E0/0 R 1 E1/0 172.X.255.1 2001:ffXX::1/128 172.16.0.X/24 2001:ff69::X/64 E0/1 10.X.0.5/30
DYNAMIC MULTIPOINT VPN SPOKE TO SPOKE DIRECT TUNNELING
 DYNAMIC MULTIPOINT VPN SPOKE TO SPOKE DIRECT TUNNELING NOVEMBER 2004 1 Direct Spoke To Spoke Tunnels Initially, spoke to spoke traffic can only travel via the hub In DMVPN, spokes can send packets directly
DYNAMIC MULTIPOINT VPN SPOKE TO SPOKE DIRECT TUNNELING NOVEMBER 2004 1 Direct Spoke To Spoke Tunnels Initially, spoke to spoke traffic can only travel via the hub In DMVPN, spokes can send packets directly
Intelligent WAN Deployment Guide
 Cisco Validated design Intelligent WAN Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deployment Details...1 Configuring DMVPN Hub Router...2
Cisco Validated design Intelligent WAN Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deployment Details...1 Configuring DMVPN Hub Router...2
Sample Business Ready Branch Configuration Listings
 APPENDIX A Sample Business Ready Branch Configuration Listings The following is a sample configuration of a Business Ready Branch. There are many permutations of feature combinations when setting up the
APPENDIX A Sample Business Ready Branch Configuration Listings The following is a sample configuration of a Business Ready Branch. There are many permutations of feature combinations when setting up the
BGP Best External. Finding Feature Information
 The feature provides the network with a backup external route to avoid loss of connectivity of the primary external route. The feature advertises the most preferred route among those received from external
The feature provides the network with a backup external route to avoid loss of connectivity of the primary external route. The feature advertises the most preferred route among those received from external
CCIE R&S v5.0. Troubleshooting Lab. Q1. PC 110 cannot access R7/R8, fix the problem so that PC 110 can ping R7
 Troubleshooting Lab Q1. PC 110 cannot access R7/R8, fix the problem so that PC 110 can ping R7 Q2. R17 should have one default route which points to R12 via PPP as shown below R17# sh ip route S* 0.0.0.0/0
Troubleshooting Lab Q1. PC 110 cannot access R7/R8, fix the problem so that PC 110 can ping R7 Q2. R17 should have one default route which points to R12 via PPP as shown below R17# sh ip route S* 0.0.0.0/0
CCIE R&S LAB CFG H2/A5 (Jacob s & Jameson s)
 Contents Section 1 Layer 2 Technologies... 2 1.1 Jameson s Datacenter: Access port... 2 1.2 Jameson s Datacenter: Trunk ports... 4 1.3 Jameson s Datacenter: Link bundling... 5 1.4 Jameson s Branch Offices...
Contents Section 1 Layer 2 Technologies... 2 1.1 Jameson s Datacenter: Access port... 2 1.2 Jameson s Datacenter: Trunk ports... 4 1.3 Jameson s Datacenter: Link bundling... 5 1.4 Jameson s Branch Offices...
MPLS VPN Inter-AS Option AB
 First Published: December 17, 2007 Last Updated: September 21, 2011 The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol
First Published: December 17, 2007 Last Updated: September 21, 2011 The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol
Multiprotocol BGP Extensions for IP Multicast Commands
 Multiprotocol BGP Extensions for IP Multicast Commands Use the commands in this chapter to configure and monitor multiprotocol BGP. Multiprotocol BGP is based on RFC 2283, Multiprotocol Extensions for
Multiprotocol BGP Extensions for IP Multicast Commands Use the commands in this chapter to configure and monitor multiprotocol BGP. Multiprotocol BGP is based on RFC 2283, Multiprotocol Extensions for
scope scope {global vrf vrf-name} no scope {global vrf vrf-name} Syntax Description
 Multi-Toplogy Routing Commands scope scope To define the scope for a Border Gateway Protocol (BGP) routing session and to enter router scope configuration mode, use the scope command in router configuration
Multi-Toplogy Routing Commands scope scope To define the scope for a Border Gateway Protocol (BGP) routing session and to enter router scope configuration mode, use the scope command in router configuration
How to Configure Forcepoint NGFW Route-Based VPN to AWS with BGP TECHNICAL DOCUMENT
 How to Configure Forcepoint NGFW Route-Based VPN to AWS with BGP TECHNICAL DOCUMENT Table of Contents TABLE OF CONTENTS 1 INTRODUCTION 2 AWS Configuration: 2 Forcepoint Configuration 3 APPENDIX 7 Troubleshooting
How to Configure Forcepoint NGFW Route-Based VPN to AWS with BGP TECHNICAL DOCUMENT Table of Contents TABLE OF CONTENTS 1 INTRODUCTION 2 AWS Configuration: 2 Forcepoint Configuration 3 APPENDIX 7 Troubleshooting
Cisco Dynamic Multipoint VPN: Simple and Secure Branch-to-Branch Communications
 Cisco Dynamic Multipoint VPN: Simple and Secure Branch-to-Branch Communications Product Overview Cisco Dynamic Multipoint VPN (DMVPN) is a Cisco IOS Software-based security solution for building scalable
Cisco Dynamic Multipoint VPN: Simple and Secure Branch-to-Branch Communications Product Overview Cisco Dynamic Multipoint VPN (DMVPN) is a Cisco IOS Software-based security solution for building scalable
LAN to LAN IPsec Tunnel Between a Cisco VPN 3000 Concentrator and Router with AES Configuration Example
 LAN to LAN IPsec Tunnel Between a Cisco VPN 3000 Concentrator and Router with AES Configuration Example Document ID: 26402 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
LAN to LAN IPsec Tunnel Between a Cisco VPN 3000 Concentrator and Router with AES Configuration Example Document ID: 26402 Contents Introduction Prerequisites Requirements Components Used Conventions Configure
Cisco Virtual Office High-Scalability Design
 Solution Overview Cisco Virtual Office High-Scalability Design Contents Scope of Document... 2 Introduction... 2 Platforms and Images... 2 Design A... 3 1. Configure the ACE Module... 3 2. Configure the
Solution Overview Cisco Virtual Office High-Scalability Design Contents Scope of Document... 2 Introduction... 2 Platforms and Images... 2 Design A... 3 1. Configure the ACE Module... 3 2. Configure the
Dynamic Multipoint VPN Configuration Guide, Cisco IOS Release 15M&T
 Dynamic Multipoint VPN Configuration Guide, Cisco IOS Release 15M&T Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800
Dynamic Multipoint VPN Configuration Guide, Cisco IOS Release 15M&T Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800
ECMP Load Balancing. MPLS: Layer 3 VPNs Configuration Guide, Cisco IOS XE Release 3S (Cisco ASR 900 Series) 1
 Equal-cost multi-path routing (ECMP) is a routing strategy where next-hop packet forwarding to a single destination can occur over multiple "best paths" which tie for top place in routing metric calculations.
Equal-cost multi-path routing (ECMP) is a routing strategy where next-hop packet forwarding to a single destination can occur over multiple "best paths" which tie for top place in routing metric calculations.
MPLS VPN Multipath Support for Inter-AS VPNs
 The feature supports Virtual Private Network (VPN)v4 multipath for Autonomous System Boundary Routers (ASBRs) in the interautonomous system (Inter-AS) Multiprotocol Label Switching (MPLS) VPN environment.
The feature supports Virtual Private Network (VPN)v4 multipath for Autonomous System Boundary Routers (ASBRs) in the interautonomous system (Inter-AS) Multiprotocol Label Switching (MPLS) VPN environment.
How to Configure an IKEv1 IPsec VPN to an AWS VPN Gateway with BGP
 How to Configure an IKEv1 IPsec VPN to an AWS VPN Gateway with BGP If you are using the Amazon Virtual Private Cloud, you can transparently extend your local network to the cloud by connecting both networks
How to Configure an IKEv1 IPsec VPN to an AWS VPN Gateway with BGP If you are using the Amazon Virtual Private Cloud, you can transparently extend your local network to the cloud by connecting both networks
How to Configure an IPsec VPN to an AWS VPN Gateway with BGP
 How to Configure an IPsec VPN to an AWS VPN Gateway with BGP If you are using the Amazon Virtual Private Cloud, you can transparently extend your local network to the cloud by connecting both networks
How to Configure an IPsec VPN to an AWS VPN Gateway with BGP If you are using the Amazon Virtual Private Cloud, you can transparently extend your local network to the cloud by connecting both networks
Dynamic Multipoint VPN (DMVPN) Deployment Models
 Dynamic Multipoint VPN (DMVPN) Deployment Models BRKSEC-4054 Cisco Public 2 Agenda DMVPN Overview NHRP Details Deployment Models Recent and New Features Cisco Public 3 DMVPN Overview What is Dynamic Multipoint
Dynamic Multipoint VPN (DMVPN) Deployment Models BRKSEC-4054 Cisco Public 2 Agenda DMVPN Overview NHRP Details Deployment Models Recent and New Features Cisco Public 3 DMVPN Overview What is Dynamic Multipoint
LAB 5: DMVPN BGP. LAB 5: Diagram. Note: This Lab was developed on Cisco IOS Version15.2(4) M1 ADVENTERPRISEK9-M.
 LAB 5: DMVPN BGP LAB 5: Diagram Note: This Lab was developed on Cisco IOS Version15.2(4) M1 ADVENTERPRISEK9-M. LAB 5: Configure BGP over DMVPN Configuration Step 1: Enable loopback and physical interfaces
LAB 5: DMVPN BGP LAB 5: Diagram Note: This Lab was developed on Cisco IOS Version15.2(4) M1 ADVENTERPRISEK9-M. LAB 5: Configure BGP over DMVPN Configuration Step 1: Enable loopback and physical interfaces
Easy Virtual Network Configuration Example
 Easy Virtual Network Configuration Example Document ID: 117974 Contributed by Fabrice Ducomble, Cisco TAC Engineer. Aug 04, 2014 Contents Introduction Prerequisites Requirements Components Used Background
Easy Virtual Network Configuration Example Document ID: 117974 Contributed by Fabrice Ducomble, Cisco TAC Engineer. Aug 04, 2014 Contents Introduction Prerequisites Requirements Components Used Background
Reverse Route Injection
 Reverse Route Injection Last Updated: October 15, 2012 Reverse route injection (RRI) is the ability to automatically insert static routes in the routing process for those networks and hosts protected by
Reverse Route Injection Last Updated: October 15, 2012 Reverse route injection (RRI) is the ability to automatically insert static routes in the routing process for those networks and hosts protected by
Configure IOS-XE to display full show running-config for users with low Privilege Levels
 Configure IOS-XE to display full show running-config for users with low Privilege Levels Contents Introduction Prerequisites Requirements Components Used Configuration Problem Configuration Solution and
Configure IOS-XE to display full show running-config for users with low Privilege Levels Contents Introduction Prerequisites Requirements Components Used Configuration Problem Configuration Solution and
MPLS VPN Carrier Supporting Carrier Using LDP and an IGP
 MPLS VPN Carrier Supporting Carrier Using LDP and an IGP Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) Carrier Supporting Carrier (CSC) enables one MPLS VPN-based service provider
MPLS VPN Carrier Supporting Carrier Using LDP and an IGP Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) Carrier Supporting Carrier (CSC) enables one MPLS VPN-based service provider
Dynamic Multipoint VPN Configuration Guide
 First Published: 2011-10-14 Last Modified: 2014-01-10 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
First Published: 2011-10-14 Last Modified: 2014-01-10 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387)
Chapter 8 Lab Configuring a Site-to-Site VPN Using Cisco IOS
 Chapter 8 Lab Configuring a Site-to-Site VPN Using Cisco IOS Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2017 Cisco and/or its affiliates. All rights
Chapter 8 Lab Configuring a Site-to-Site VPN Using Cisco IOS Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2017 Cisco and/or its affiliates. All rights
How to Configure an IKEv1 IPsec VPN to an AWS VPN Gateway with BGP
 How to Configure an IKEv1 IPsec VPN to an AWS VPN Gateway with BGP If you are using the Amazon Virtual Private Cloud, you can transparently extend your local network to the cloud by connecting both networks
How to Configure an IKEv1 IPsec VPN to an AWS VPN Gateway with BGP If you are using the Amazon Virtual Private Cloud, you can transparently extend your local network to the cloud by connecting both networks
Flexible Dynamic Mesh VPN draft-detienne-dmvpn-00
 Flexible Dynamic Mesh VPN draft-detienne-dmvpn-00 Fred Detienne, Cisco Systems Manish Kumar, Cisco Systems Mike Sullenberger, Cisco Systems What is Dynamic Mesh VPN? DMVPN is a solution for building VPNs
Flexible Dynamic Mesh VPN draft-detienne-dmvpn-00 Fred Detienne, Cisco Systems Manish Kumar, Cisco Systems Mike Sullenberger, Cisco Systems What is Dynamic Mesh VPN? DMVPN is a solution for building VPNs
Managing Site-to-Site VPNs: The Basics
 CHAPTER 23 A virtual private network (VPN) consists of multiple remote peers transmitting private data securely to one another over an unsecured network, such as the Internet. Site-to-site VPNs use tunnels
CHAPTER 23 A virtual private network (VPN) consists of multiple remote peers transmitting private data securely to one another over an unsecured network, such as the Internet. Site-to-site VPNs use tunnels
DMVPN Topology. Page1
 DMVPN DMVPN Topology Page1 LAB 2: Configure EIGRP over DMVPN: Task 1: Configure EIGRP over DMVPN Process Step 1 In the configuration mode of router configure EIGRP over DMVPN by following command: R1:
DMVPN DMVPN Topology Page1 LAB 2: Configure EIGRP over DMVPN: Task 1: Configure EIGRP over DMVPN Process Step 1 In the configuration mode of router configure EIGRP over DMVPN by following command: R1:
Dynamic Multipoint VPN between CradlePoint and Cisco Router Example
 Dynamic Multipoint VPN between CradlePoint and Cisco Router Example Summary This article describes how to setup a Dynamic GRE over IPSec VPN tunnel with NHRP (more commonly referred to as Dynamic Multipoint
Dynamic Multipoint VPN between CradlePoint and Cisco Router Example Summary This article describes how to setup a Dynamic GRE over IPSec VPN tunnel with NHRP (more commonly referred to as Dynamic Multipoint
Cisco Multicloud Portfolio: Cloud Connect
 Deployment Guide Cisco Multicloud Portfolio: Cloud Connect Deployment Guide for Cisco SD-WAN Cloud onramp for SaaS August 2018 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco
Deployment Guide Cisco Multicloud Portfolio: Cloud Connect Deployment Guide for Cisco SD-WAN Cloud onramp for SaaS August 2018 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco
How to Configure BGP over IKEv2 IPsec Site-to- Site VPN to an Google Cloud VPN Gateway
 How to Configure BGP over IKEv2 IPsec Site-to- Site VPN to an Google Cloud VPN Gateway To connect to the Google Cloud VPN gateway, create an IPsec IKEv2 site-to-site VPN tunnel on your F-Series Firewall
How to Configure BGP over IKEv2 IPsec Site-to- Site VPN to an Google Cloud VPN Gateway To connect to the Google Cloud VPN gateway, create an IPsec IKEv2 site-to-site VPN tunnel on your F-Series Firewall
Lab - Configuring a Site-to-Site VPN Using Cisco IOS and CCP
 CCNA Security Lab - Configuring a Site-to-Site VPN Using Cisco IOS and CCP Topology Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet Interfaces. 2015 Cisco and/or its affiliates.
CCNA Security Lab - Configuring a Site-to-Site VPN Using Cisco IOS and CCP Topology Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet Interfaces. 2015 Cisco and/or its affiliates.
MPLS VPN Carrier Supporting Carrier Using LDP and an IGP
 MPLS VPN Carrier Supporting Carrier Using LDP and an IGP Last Updated: December 14, 2011 Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) Carrier Supporting Carrier (CSC) enables one
MPLS VPN Carrier Supporting Carrier Using LDP and an IGP Last Updated: December 14, 2011 Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) Carrier Supporting Carrier (CSC) enables one
Scalability Considerations
 3 CHAPTER This chapter presents the following steps to selecting Cisco products for a VPN solution: Sizing the headend Choosing Cisco products that can be deployed for headend devices Product sizing and
3 CHAPTER This chapter presents the following steps to selecting Cisco products for a VPN solution: Sizing the headend Choosing Cisco products that can be deployed for headend devices Product sizing and
Virtual Private Networks Advanced Technologies
 Virtual Private Networks Advanced Technologies Petr Grygárek rek Agenda: Supporting Technologies (GRE, NHRP) Dynamic Multipoint VPNs (DMVPN) Group Encrypted Transport VPNs (GET VPN) Multicast VPNs (mvpn)
Virtual Private Networks Advanced Technologies Petr Grygárek rek Agenda: Supporting Technologies (GRE, NHRP) Dynamic Multipoint VPNs (DMVPN) Group Encrypted Transport VPNs (GET VPN) Multicast VPNs (mvpn)
Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT
 Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT The Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT feature supports the forwarding of packets from a standby
Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT The Interchassis Asymmetric Routing Support for Zone-Based Firewall and NAT feature supports the forwarding of packets from a standby
VPN Connection through Zone based Firewall Router Configuration Example
 VPN Connection through Zone based Firewall Router Configuration Example Document ID: 112051 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
VPN Connection through Zone based Firewall Router Configuration Example Document ID: 112051 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
Contents. Introduction. Prerequisites. Requirements. Components Used
 Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations OSPF EIGRP RIP Troubleshoot Introduction This document describes how to redistribute Internal Border
Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations OSPF EIGRP RIP Troubleshoot Introduction This document describes how to redistribute Internal Border
Návrh inteligentní WAN sítě
 Návrh inteligentní WAN sítě EN2 Jaromír Pilař, CSE Agenda Úvod a základní pilíře inteligentní WAN sítě Tranport Independent Design Inteligentní výběr cesty Shrnutí Presentation Title: Intelligent WAN:
Návrh inteligentní WAN sítě EN2 Jaromír Pilař, CSE Agenda Úvod a základní pilíře inteligentní WAN sítě Tranport Independent Design Inteligentní výběr cesty Shrnutí Presentation Title: Intelligent WAN:
Contents. Introduction. Prerequisites. Requirements
 Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations Verify Inheritence with EIGRP Named mode Route Replication with EIGRP name mode Routing Context
Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations Verify Inheritence with EIGRP Named mode Route Replication with EIGRP name mode Routing Context
BGP mvpn BGP safi IPv4
 The BGP mvpn BGP safi 129 IPv4 feature provides the capability to support multicast routing in the service provider s core IPv4 network This feature is needed to support BGP-based MVPNs BGP MVPN provides
The BGP mvpn BGP safi 129 IPv4 feature provides the capability to support multicast routing in the service provider s core IPv4 network This feature is needed to support BGP-based MVPNs BGP MVPN provides
Enterprise SD-WAN Financial Profile (Hybrid WAN, Segmentation, Quality of Service, Centralized Policies)
 CVP CVP Enterprise SD-WAN Financial Profile (Hybrid WAN, Segmentation, Quality of Service, Centralized Policies) 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information.
CVP CVP Enterprise SD-WAN Financial Profile (Hybrid WAN, Segmentation, Quality of Service, Centralized Policies) 2018 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information.
MPLS VPN Inter-AS with ASBRs Exchanging VPN-IPv4 Addresses
 MPLS VPN Inter-AS with ASBRs Exchanging VPN-IPv4 Addresses The Multiprotocol Label Switching (MPLS) VPN Inter-AS with Autonomous System Boundary Routers (ASBRs) Exchanging VPN-IPv4 Addresses feature allows
MPLS VPN Inter-AS with ASBRs Exchanging VPN-IPv4 Addresses The Multiprotocol Label Switching (MPLS) VPN Inter-AS with Autonomous System Boundary Routers (ASBRs) Exchanging VPN-IPv4 Addresses feature allows
Converged Access CT 5760 AVC Deployment Guide, Cisco IOS XE Release 3.3
 Converged Access CT 5760 AVC Deployment Guide, Cisco IOS XE Release 3.3 Last Updated: November, 2013 Introduction This guide is designed to help you deploy and monitor new features introduced in the IOS
Converged Access CT 5760 AVC Deployment Guide, Cisco IOS XE Release 3.3 Last Updated: November, 2013 Introduction This guide is designed to help you deploy and monitor new features introduced in the IOS
IPsec Anti-Replay Window Expanding and Disabling
 IPsec Anti-Replay Window Expanding and Disabling Cisco IP security (IPsec) authentication provides anti-replay protection against an attacker duplicating encrypted packets by assigning a unique sequence
IPsec Anti-Replay Window Expanding and Disabling Cisco IP security (IPsec) authentication provides anti-replay protection against an attacker duplicating encrypted packets by assigning a unique sequence
IPv6 Commands: n to re
 IPv6 Commands: n to re nai (proxy mobile IPv6), page 3 neighbor override-capability-neg, page 4 neighbor send-label, page 6 neighbor translate-update, page 9 network (IPv6), page 12 nis address, page 14
IPv6 Commands: n to re nai (proxy mobile IPv6), page 3 neighbor override-capability-neg, page 4 neighbor send-label, page 6 neighbor translate-update, page 9 network (IPv6), page 12 nis address, page 14
Managing Site-to-Site VPNs
 CHAPTER 21 A virtual private network (VPN) consists of multiple remote peers transmitting private data securely to one another over an unsecured network, such as the Internet. Site-to-site VPNs use tunnels
CHAPTER 21 A virtual private network (VPN) consists of multiple remote peers transmitting private data securely to one another over an unsecured network, such as the Internet. Site-to-site VPNs use tunnels
IPsec Dead Peer Detection Periodic Message Option
 IPsec Dead Peer Detection Periodic Message The IPsec Dead Peer Detection Periodic Message feature is used to configure the router to query the liveliness of its Internet Key Exchange (IKE) peer at regular
IPsec Dead Peer Detection Periodic Message The IPsec Dead Peer Detection Periodic Message feature is used to configure the router to query the liveliness of its Internet Key Exchange (IKE) peer at regular
Cisco Service Advertisement Framework Deployment Guide
 Cisco Service Advertisement Framework Deployment Guide What You Will Learn Cisco Service Advertisement Framework (SAF) is a network-based, scalable, bandwidth-efficient approach to service advertisement
Cisco Service Advertisement Framework Deployment Guide What You Will Learn Cisco Service Advertisement Framework (SAF) is a network-based, scalable, bandwidth-efficient approach to service advertisement
Advanced Concepts of DMVPN (Dynamic Multipoint VPN)
 Advanced Concepts of DMVPN (Dynamic Multipoint VPN) Mike Sullenberger Distinguished Engineer Agenda DMVPN Design Overview DMVPN General IWAN Specific NHRP Details NHRP Overview NHRP Registrations/Resolutions/Redirects
Advanced Concepts of DMVPN (Dynamic Multipoint VPN) Mike Sullenberger Distinguished Engineer Agenda DMVPN Design Overview DMVPN General IWAN Specific NHRP Details NHRP Overview NHRP Registrations/Resolutions/Redirects
Managing Site-to-Site VPNs: The Basics
 CHAPTER 21 A virtual private network (VPN) consists of multiple remote peers transmitting private data securely to one another over an unsecured network, such as the Internet. Site-to-site VPNs use tunnels
CHAPTER 21 A virtual private network (VPN) consists of multiple remote peers transmitting private data securely to one another over an unsecured network, such as the Internet. Site-to-site VPNs use tunnels
Implementing Cisco IP Routing
 300-101 Implementing Cisco IP Routing NWExam.com SUCCESS GUIDE TO CISCO CERTIFICATION Exam Summary Syllabus Questions Table of Contents Introduction to 300-101 Exam on Implementing Cisco IP Routing...
300-101 Implementing Cisco IP Routing NWExam.com SUCCESS GUIDE TO CISCO CERTIFICATION Exam Summary Syllabus Questions Table of Contents Introduction to 300-101 Exam on Implementing Cisco IP Routing...
Chapter 7 Lab 7-1, Configuring BGP with Default Routing
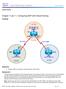 Chapter 7 Topology Objectives Configure BGP to exchange routing information with two ISPs. Background The International Travel Agency (ITA) relies extensively on the Internet for sales. For this reason,
Chapter 7 Topology Objectives Configure BGP to exchange routing information with two ISPs. Background The International Travel Agency (ITA) relies extensively on the Internet for sales. For this reason,
LISP Router IPv6 Configuration Commands
 ipv6 alt-vrf, page 2 ipv6 etr, page 4 ipv6 etr accept-map-request-mapping, page 6 ipv6 etr map-cache-ttl, page 8 ipv6 etr map-server, page 10 ipv6 itr, page 13 ipv6 itr map-resolver, page 15 ipv6 map-cache-limit,
ipv6 alt-vrf, page 2 ipv6 etr, page 4 ipv6 etr accept-map-request-mapping, page 6 ipv6 etr map-cache-ttl, page 8 ipv6 etr map-server, page 10 ipv6 itr, page 13 ipv6 itr map-resolver, page 15 ipv6 map-cache-limit,
Virtual Private Networks Advanced Technologies
 Virtual Private Networks Advanced Technologies Petr Grygárek rek Agenda: Supporting Technologies (GRE, NHRP) Dynamic Multipoint VPNs (DMVPN) Group Encrypted Transport VPNs (GET VPN) Multicast VPNs (mvpn)
Virtual Private Networks Advanced Technologies Petr Grygárek rek Agenda: Supporting Technologies (GRE, NHRP) Dynamic Multipoint VPNs (DMVPN) Group Encrypted Transport VPNs (GET VPN) Multicast VPNs (mvpn)
Configuring Multicast VPN Inter-AS Support
 Configuring Multicast VPN Inter-AS Support Last Updated: December 23, 2011 The Multicast VPN Inter-AS Support feature enables Multicast Distribution Trees (MDTs) used for Multicast VPNs (MVPNs) to span
Configuring Multicast VPN Inter-AS Support Last Updated: December 23, 2011 The Multicast VPN Inter-AS Support feature enables Multicast Distribution Trees (MDTs) used for Multicast VPNs (MVPNs) to span
CVP Enterprise Cisco SD-WAN Retail Profile (Hybrid WAN, Segmentation, Zone-Based Firewall, Quality of Service, and Centralized Policies)
 CVP CVP Enterprise Cisco SD-WAN Retail Profile (Hybrid WAN, Segmentation, Zone-Based Firewall, Quality of Service, and Centralized Policies) 2018 Cisco and/or its affiliates. All rights reserved. This
CVP CVP Enterprise Cisco SD-WAN Retail Profile (Hybrid WAN, Segmentation, Zone-Based Firewall, Quality of Service, and Centralized Policies) 2018 Cisco and/or its affiliates. All rights reserved. This
Configuring Redundant Routing on the VPN 3000 Concentrator
 Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
MPLS VPN C H A P T E R S U P P L E M E N T. BGP Advertising IPv4 Prefixes with a Label
 7 C H A P T E R S U P P L E M E N T This online supplement of Chapter 7 focuses on two important developments. The first one is Inter-Autonomous. Inter-Autonomous is a concept whereby two service provider
7 C H A P T E R S U P P L E M E N T This online supplement of Chapter 7 focuses on two important developments. The first one is Inter-Autonomous. Inter-Autonomous is a concept whereby two service provider
Configuring Internet Key Exchange Version 2 and FlexVPN Site-to-Site
 Configuring Internet Key Exchange Version 2 and FlexVPN Site-to-Site This module contains information about and instructions for configuring basic and advanced Internet Key Exchange Version 2 (IKEv2)and
Configuring Internet Key Exchange Version 2 and FlexVPN Site-to-Site This module contains information about and instructions for configuring basic and advanced Internet Key Exchange Version 2 (IKEv2)and
Deploying Transit VPC for Amazon Web Services
 This section contains the following topics: How to Deploy Transit VPC for DMVPN, page 1 How to Deploy Transit VPC for DMVPN Information About Deploying Transit VPC This is a summary about the deploying
This section contains the following topics: How to Deploy Transit VPC for DMVPN, page 1 How to Deploy Transit VPC for DMVPN Information About Deploying Transit VPC This is a summary about the deploying
BGP-MVPN SAFI 129 IPv6
 Subsequent Address Family Identifier (SAFI) 129, known as VPN Multicast SAFI, provides the capability to support multicast routing in the service provider's core IPv6 network. Border Gateway Protocol (BGP)
Subsequent Address Family Identifier (SAFI) 129, known as VPN Multicast SAFI, provides the capability to support multicast routing in the service provider's core IPv6 network. Border Gateway Protocol (BGP)
IPv6 Tunnel through an IPv4 Network
 IPv6 Tunnel through an IPv4 Network Document ID: 25156 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations (Manual IPv6 Mode) Configurations
IPv6 Tunnel through an IPv4 Network Document ID: 25156 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations (Manual IPv6 Mode) Configurations
Internet. SonicWALL IP Cisco IOS IP IP Network Mask
 Prepared by SonicWALL, Inc. 9/20/2001 Introduction: VPN standards are still evolving and interoperability between products is a continued effort. SonicWALL has made progress in this area and is interoperable
Prepared by SonicWALL, Inc. 9/20/2001 Introduction: VPN standards are still evolving and interoperability between products is a continued effort. SonicWALL has made progress in this area and is interoperable
Intelligent WAN Multiple Data Center Deployment Guide
 Cisco Validated design Intelligent WAN Multiple Data Center Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deployment Details...1 Deploying
Cisco Validated design Intelligent WAN Multiple Data Center Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deployment Details...1 Deploying
Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED
 Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED Topology Objectives Background For IBGP peers to correctly exchange routing information, use the next-hop-self command with
Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED Topology Objectives Background For IBGP peers to correctly exchange routing information, use the next-hop-self command with
