Table of Contents. Chapter 1 Border Gateway Protocol (BGP) 1. Chapter 3 Enhanced Interior Gateway Routing 91 Protocol (EIGRP)
|
|
|
- Jessica Underwood
- 5 years ago
- Views:
Transcription
1
2 Table of Contents Chapter 1 Border Gateway Protocol (BGP) 1 Chapter 2 Access Control Lists 45 Chapter 3 Enhanced Interior Gateway Routing 91 Protocol (EIGRP) Chapter 4 Default Routing 149
3 TAB Insert Tab # 1 Here
4 Border Gateway Protocol (BGP)
5 2
6 BGP 4 Autonomous System Internet AS-86 AS-36 AS-82 AS-51 AS-7 AS-43 AS-66 An autonomous system is a collection of networks under a single administrative control which share a common routing strategy. The collection of autonomous systems interconnected using BGP form the backbone of the internet. The Internet is formed by the interconnection of many privately owned and autonomous networks, each one run by an independent organization. These organizations often have different policies for routing packets within their own networks and for exchanging packets with other organizations. This fundamental factor of ownership and management control leads to the internal-external distinction. Routing must still take place within an autonomous network, because there will usually be many alternative pathways that packets can travel. Nowadays, this routing is usually done using link-state protocols such as OSPF. An autonomous system is one network or set of networks under a single administrative control. An autonomous system might be the set of all computer networks owned by a company, or a college. Companies and organizations might own more than one autonomous system, but the idea is that each autonomous system is managed independently with respect to BGP. An autonomous system is often referred to as an AS. A good example is UUNet, who use one autonomous system as their European network, and a separate autonomous system for their domestic networks in the Americas. If you draw a network map of ASs, three distinct types can be identified: 1. A Stub AS is only connected to one other AS. For routing purposes, it could be regarded as a simple extension of the other AS. In fact, most networks with a single Internet connection don't have a unique AS number 3
7 assigned, and their network addresses are treated as part of the parent AS. 2. A Transit AS has connections to more than one other AS and allows itself to be used as a conduit for traffic (transit traffic) between other ASs. Most large Internet Service Providers are transit ASs. 3. A Multihomed AS has connections to more than one other AS, but does not allow transit traffic to pass, though its interior hosts may route traffic through multiple ASs. This is the typical configuration for a large corporate network with multiple redundant Internet connections, which does not wish to pass traffic for others. 4
8 Autonomous System Numbers AS # Provider 701 UUnet (U.S. domestic) (AS ) 1239 Sprintlink U.S. Domestic 3356 Level AT&T WorldNet 209 Qwest 3561 Cable and Wireless 3549 Global Crossing 2914 Verio 702 UUnet (International) The American Registry for Internet Numbers (ARIN) defines Autonomous System Numbers as: "Autonomous System Numbers (ASNs) are globally unique numbers that are used to identify autonomous systems (ASs) and which enable an AS to exchange exterior routing information between neighboring ASs. An AS is a connected group of IP networks that adhere to a single and clearly defined routing policy." To identify each autonomous system, a globally unique number is assigned to each one from a centralized authority (ARIN) so that there are no duplicate numbers. Globally Unique means exactly that within the entire Internet all around the globe, the AS number should be unique. The AS number will be from 1 to 64511, and the next highest unused number is what is generally assigned. These numbers are referred to as AS numbers. The American Registry for Internet Numbers (ARIN) is the authority responsible for tracking and assigning these numbers as well as managing IP address allocations and assignments. ARIN charges a fee to organizations wishing to obtain an AS number to cover the administrative costs associated with managing AS number registrations and assignments. To receive an AS number from ARIN, you must be able to prove you are dual homed to the Internet, which means that you have more than one Internet provider with which you plan to run BGP. You must also 5
9 have a unique routing policy that differs from your BGP peers. Some companies have difficulty getting an AS number. If it is not necessary to connect to the Internet, or you are part of a special type of BGP configuration, you can use any of the AS numbers through However, these numbers should NOT be seen on the global Internet. One example of when you might use private AS numbers is in BGP confederations. The confederation AS number should not be seen on the global Internet. BGP learns and exchanges path information regarding the route to a given destination network by keeping lists of AS numbers and associating them with destination networks. This is why AS numbers should be unique. BGP makes certain that an AS number does not appear in a path more than once, thereby preventing routing loops. 6
10 Interconnecting Autonomous Systems AS 1 BGP AS 2 BGP is designed to interconnect two different ASs. If a group of routers share a common AS, use an IGP. A routing protocol used to connect autonomous systems is referred to as an exterior gateway protocol (EGP). The Border Gateway Protocol (BGP) is an EGP used to make policy based routing decisions between ASs. BGP version 4 (BGP-4) is the latest version of BGP and is defined in RFC The Exterior Gateway Protocol (EGP) and BGP versions 1 through 3 do not support CIDR and are not used across the public Internet. The main goal of BGP is to provide an inter-domain routing system that guarantees the loop-free exchange of routing information between ASs. Routers exchange information about paths to destination networks. It is important that when two autonomous systems interconnect, that routing information between the two can be controlled. BGP gives the network administrator the capability to implement policies to control and/or manipulate the routing taking place between the two autonomous systems. BGP is not designed to operate as an interior gateway protocol (IGP) internal to an autonomous system. BGP is used by the WIN-T network routers to exchange routing information with the DISN NIPRNET and SIPRNET systems. 7
11 Internal vs. External Routing Interior Routing Works within an Autonomous System. Selects routes based on metrics or cost. - hop count, bandwidth, delay, reliability Exterior Routing Normally works between Autonomous Systems. Selects routes based on policy, not metrics. An interior routing protocol or IGP (interior gateway protocol) routes within an autonomous system (AS). An IGP determines the best path within a network topology utilizing variables such as bandwidth, delay, or hop count. RIP uses hop count; the path with the fewest number of layer three devices to reach the destination network is the preferred path. OSPF utilizes bandwidth and EIGRP utilizes bandwidth and delay assigned to an interface. All interior routing protocols use outbound metrics or costs to decide where to send packets. An exterior routing protocol or EGP (exterior gateway protocol) routes between autonomous systems. BGP is an example of an EGP. BGP does not utilize the same type of variables as IGPs to determine the best path. BGP is a policy based routing protocol that allows an administrator of an AS to control traffic based on a multitude of route attributes. It gives the flexibility to establish rules to fit the routing needs of the AS. Traffic entering, exiting or even transiting an AS can have policies established to manipulate the flow. This can allow for all available bandwidth to be utilized effectively. 8
12 External Routing History 1982 Exterior Gateway Protocol (EGP) 1989 BGP version & 91 BGP versions 2 & BGP version 4 (supports CIDR) Routing in the early Internet was done using a small number of centralized core routers that maintained complete information about network reachability on the Internet. They exchanged information using the historical interior routing protocol, the Gateway-to-Gateway Protocol (GGP). Around the periphery of this core were located other non-core routers, sometimes standalone and sometimes collected into groups. These exchanged network reachability information with the core routers using the first TCP/IP exterior routing protocol: the Exterior Gateway Protocol (EGP). Like its interior routing counterpart GGP, EGP was developed by Internet pioneers Bolt, Beranek and Newman (BBN) in the early 1980s. It was first formally described in an Internet standard in RFC 827, Exterior Gateway Protocol (EGP), published in October This draft document was superseded in April 1984 by RFC 904, Exterior Gateway Protocol Formal Specification. Like GGP, EGP is now considered obsolete, having been replaced by the Border Gateway Protocol (BGP). However, also like GGP, it is an important part of the history of TCP/IP routing When the Internet grew and moved to the autonomous system (AS) architecture, EGP was still able to function as the exterior routing protocol for the Internet. However, as the number of autonomous systems in an internetwork grows, the importance of communication between them grows as well. EGP was functional but had several weaknesses that became more problematic as the Internet grew 9
13 in size. It was necessary to define a new exterior routing protocol that would provide enhanced capabilities for use on the growing Internet. In June 1989, the first version of this new routing protocol was formalized, with the publishing of RFC 1105, A Border Gateway Protocol (BGP). This initial version of the BGP standard defined most of the concepts behind the protocol, as well as key fundamentals such as messaging, message formats and how devices operate in general terms. It established BGP as the Internet's exterior routing protocol of the future. Due to the importance of a protocol that spans the Internet, work continued on BGP for many years after the initial standard was published. The developers of BGP had to correct problems with the initial protocol, refine BGP's operation, improve efficiency, and add features. It was also necessary to make adjustments to allow BGP to keep pace with other changes in the TCP/IP protocol suite, such as the invention of classless addressing and routing. As you might imagine, changing the version of a protocol like BGP is not an easy undertaking. Any modification of the protocol would require the coordination of many different organizations. The larger the Internet grows, the more difficult this would be. As a result, despite frequent version changes in the early 1990s, BGP-4 remains today the current version of the standard, and is the one that is widely used. 10
14 When and When Not to use BGP BGP is appropriate when at least one of the following exist: An AS has multiple connections to other ASes. The flow of routing traffic entering or leaving an AS must be manipulated. An AS allows packets to transit through it to reach another AS. The effects and drawbacks of BGP are well understood. BGP should not be used if one of the following exist: A single connection to the Internet or other AS. Routing policy and route selection are not a concern for an AS. Lack of memory/processor power on BGP routers to handle constant updates. Limited understanding of route filtering and BGP path selection process. Low bandwidth between autonomous systems. BGP was designed to allow Internet Service Providers (ISPs) to communicate and exchange packets. These ISPs have multiple connections to one another at both public and private peering points. Since the major ISPs have multiple connections to one another, a routing protocol had to be developed to manipulate how and under what conditions a meeting point could be used to exchange packets. BGP is a policy based routing protocol used to implement this peering agreement between two or more autonomous systems. BGP, if not properly controlled and filtered, has the potential to allow an outside AS to affect your routing decisions. If only one entry/exit point exists in an AS, a default route should be considered. BGP is used to select a pathway to leave your AS or to recommend to an outside AS the preferred entry point. With only one point of entry/exit, using BGP would not accomplish anything except to use router CPU and memory resources. The only policy that can be changed is how a packet enters or leaves an AS. Once a packet enters another AS, that AS s policy will take over and decide how to route the packet. 11
15 BGP Features Open, non-proprietary. Supports VLSM. Supports route summarization & CIDR. Reliable update utilizes TCP (179). Incremental, triggered updates. Robust metrics path vectors/attributes. Designed to scale to very large internetworks. BGP is an open, non-proprietary protocol in the public domain. It is not owned by any one entity and can be used by any vendor. BGP supports variable length subnet masking to allow for the efficient allocation of IP addresses. BGP allows for route summarization and CIDR. This is extremely important when dealing with large networks so as to keep the routing tables at a manageable level and to reduce router latency when routing decisions are being made. It is also extremely important that it supports the implementation of CIDR. Currently there are approximately 120,000 routes in the routing table of Internet core routers. Without CIDR, this number would exceed 2,000,000. BGP utilizes TCP (port 179) as its reliable transport mechanism. T his insures the reliable delivery of update packets so that all routers are converged with the same routing information. Unlike IGPs with built in transport protocols which have a window size of one, BGP s utilization of TCP allows for a dynamic window which can transmit up to 65,576 bytes before it stops and waits for acknowledgement. This is a must for BGP, which can be responsible for the updating of thousands of routes at any one time. BGP sends updates only during network changes. This allows BGP traffic to be minimized and network bandwidth to be fully utilized for routing user traffic. 12
16 BGP is a policy based routing protocol. Policies or rules can be implemented based on a variety of routing attributes to manipulate traffic flow patterns. This allows a network administrator to implement policies to fit the needs of the autonomous system in question. BGP is designed to scale to very large internetworks. BGP tracks and utilizes as a routing attribute the autonomous system in the path to reach a destination network. This insures a loop free route, because a BGP router will not accept a route which includes its own AS in its path. 13
17 BGP Packets Open starts a BGP session between neighbors. Keepalive maintains neighbor connectivity. Update routing update. Notification notifies neighbor of error, connection closed. The open message opens a BGP communications session between neighbors. It is the first message sent by each side after a transport-protocol connection is established. The receiving neighbor confirms an open message by replying with a keepalive message. The open message must be confirmed before updates, notifications, and keepalives can be exchanged between neighbors. Open messages contain the following information: 14 - Version Number - AS Number - Holdtime - Router ID - Optional Parameters The keepalive message notifies BGP peers that a device is active. Keepalives are sent often enough to keep the sessions from expiring. The default for BGP is a keepalive interval of 60 seconds and a hold time of 180 seconds. An update message is used to provide routing updates to other BGP systems, allowing routers to construct a consistent view of the network topology. Updates are sent using TCP to ensure reliable delivery. An update message can advertise a route, withdraw a route, and advertise all associated attributes. An update contains information about one path only; multiple paths require multiple updates. A single update may contain information about numerous networks reachable through that path. The notification message is sent when an error condition is detected. Notifications are used to close an active session and to inform any connected routers of why the session is being closed.
18 BGP Databases Neighbor Table - list all BGP neighbors. BGP Topology Table - lists all networks learned from neighbors. IP Routing Table - lists preferred paths to destination networks. BGP establishes and/or maintains three different databases: neighbor table, topology table, and the routing table. Unlike IGP, BGP does not have automatic neighbor discovery. Each neighbor must be configured by IP address and AS number. BGP establishes a TCP connection with each neighbor and maintains the relationship by periodically sending keepalive packets. After the neighbor relationship is established, the routers exchange the BGP routes in their routing tables. These routes are then placed into the router s BGP topology database. All BGP information learned from a router s neighbors are placed into the BGP topology database. The best routes are then selected from the topology database using the BGP selection process. These routes are then offered to the routing table as candidates. The routing table selects the best routes from all candidate routes offered from all routing information sources. Utilizing the administrative distance and then metrics, the preferred candidates are selected for installation into the routing table. 15
19 BGP Network Lab AS - 1 f0/ /28 s0/1.5/30 s0/0.9/30 AS - 7 f0/ /28.10/30.13/30 s0/0 7 s0/3 AS /30 s0/0 4 f0/ /28 s0/1.17/30 AS - 2 s0/1.6/30 s0/0.18/30 AS - 5 f0/ /28 s0/0.26/30 f0/ /28.21/30 s0/1 AS - 3 s0/1.25/30.22/30 s0/0 AS - 6 f0/ / f0/ /28 Install the above directly connected network. The network is complete when the IP routing table shows the directly networks. Do not configure a routing protocol. 16
20 How do I turn it on? Router(config)# BGP Commands router bgp autonomous-system Autonomous-system Identifies the local autonomous system The router bgp command enables the bgp routing protocol. The syntax of basic BGP configuration commands is similar to the syntax for configuring internal routing protocols. However, there are significant differences in the way that an external protocol functions. Use the router bgp command to activate the BGP protocol and identify the local autonomous system. Only one instance of BGP can be enabled on a router it can only route for one autonomous system. 17
21 External vs. Internal BGP Neighbors External BGP Neighbor - a router whose administrative and policy control is outside of your Autonomous System. Internal BGP Neighbor - a router that falls under the administrative control of a single AS and is assumed to follow a consistent policy with other BGP speakers of that AS. BGP supports two types of exchanges of routing information: exchanges between different ASs and exchanges within a single AS. When used between ASs, BGP is called external BGP (EBGP) and BGP sessions perform inter-as routing. When used within an AS, BGP is called internal BGP (IBGP) and BGP sessions perform intra-as routing. A BGP system shares network reachability information with adjacent BGP systems, which are referred to as neighbors or peers. BGP systems are arranged into groups. In an internal BGP group, all peers in the group called internal peers are in the same AS. Internal peers can be anywhere in the local AS and do not have to be directly connected to each other. Internal groups use routes from an IGP to resolve forwarding addresses. They also propagate external routes among all other internal routers running internal BGP, computing the next hop by taking the BGP next hop received with the route and resolving it using information from one of the interior gateway protocols. The address that BGP points at for an internal BGP neighbor must also be reachable. This can be by a directly connected network or static routes, but it also can be reachable by the internal routing protocol. Since other routers 18
22 in an AS can usually be reached by multiple paths, a loopback address is generally used. In an external BGP group, the peers in the group called external peers are in different ASs and normally share a subnet. In an external group, the next hop is computed with respect to the interface that is shared between the external peer and the local router. An internal routing protocol (IGP) is not exchanged with an external BGP neighbor. The address, which your router points to, must be reachable without using a routing protocol. This can be accomplished either by pointing at an address that is reachable by a directly connected network or by using static routes to that IP address. Generally, the neighbor address that is used is a directly connected address of the other router. 19
23 Identify Your Neighbors AS BGP AS 2 EBGP neighbors expect to be directly connected EBGP neighbors expect to be directly connected. The neighbor is the IP address of the interface used for the BGP connection. Utilizing the network diagram on page 12, identify the neighbor IPs for your router. 20
24 BGP Commands - Neighbors Router(config-router)# neighbor ip-address remote-as autonomous-system Activates a BGP session on an interface. Used for both external and internal neighbors. The ip-address is the IP address of the neighboring router's interface to which you are directly connected. The autonomous-system is the AS number to which the neighboring router belongs. Two BGP speaking routers trying to become neighbors will first bring up the TCP connection between one another and then send open messages in order to exchange values such as the AS number, the BGP version, the BGP router ID, the keepalive hold time, etc. After these values are confirmed and accepted, the neighbor connection will be established. Any state other than established is an indication that the two routers did not become neighbors and hence the BGP updates will not be exchanged. Two BGP routers become neighbors or peers once they establish a TCP connection between one another. The TCP connection is essential in order for the two peer routers to start exchanging routing updates. The neighbor command used to establish a TCP connection is as follows: neighbor ip-address remote-as number The ip-address is the next hop directly connected address for EBGP and any IP address on the other router, which is reachable via any means (connected, static, or IGP) for IBGP. The remote-as number is the AS number where the neighbor is located. This number must be the same as the one used by the neighbor to enable BGP: external neighbor, different AS; internal neighbor, same AS. 21
25 In IGP, neighbor discovery is automatic and is initiated by utilizing the network statement. The network statement starts the IGP process on an interface. In BGP, neighbor discovery must be manually configured. The neighbor statement starts the BGP process on an interface. 22
26 Show IP BGP Summary router7#sho ip bgp sum BGP router identifier , local AS number 7 BGP table version is 14, main routing table version 14 7 network entries using 819 bytes of memory 7 path entries using 336 bytes of memory 8/7 BGP path/bestpath attribute entries using 928 bytes of memory 6 BGP AS-PATH entries using 144 bytes of memory 0 BGP route-map cache entries using 0 bytes of memory 0 BGP filter-list cache entries using 0 bytes of memory BGP using 2227 total bytes of memory BGP activity 7/0 prefixes, 7/0 paths, scan interval 60 secs Neighbor State/PfxRcd V AS MsgRcv MsgSent TblVer InQ OutQ Up/Down :48: :03:16 3 The show ip bgp summary command can be utilized to show the status of a BGP neighbor. BGP table version Internal version number of BGP database. Main routing table version Last version of BGP database that was injected into main routing table. Neighbor V AS MsgRcvd MsgSent TblVer InQ IP address of a neighbor. BGP version number spoken to that neighbor. That neighbors autonomous system number. BGP messages received from that neighbor. BGP messages sent to that neighbor. Last version of the BGP database that was sent to that neighbor. Number of messages from that neighbor waiting to be processed. 23
27 OutQ Up/Down State Number of messages waiting to be sent to that neighbor. The length of time that the BGP session has been in state Established, or the current state if it is not established. Current state of the BGP session. (reference next page) 24
28 State/PfxRcd Idle = The router is looking in the routing table to find a match for the address specified in the neighbor statement. Active = The router is establishing a TCP connection with the neighbor. Open = The router is exchanging BGP open messages with the neighbor. Number = The neighbor relationship is established. The number in the column indicates the actual number of networks advertised by the neighbor. Once the neighbor statement is entered, the router searches for a match for the address specified in the neighbor statement. This allows the router to begin the BGP neighbor establishment on the interface associated with that address. If the state stays in the idle mode, then a common cause is the address specified in the neighbor statement is incorrect. Once a match is found for the address specified in the neighbor statement, the router begins opening a TCP connection to the neighbor (three way handshake). This is the active mode. Once the TCP connection is established, the router begins sending open messages to the neighbor. If no response is received from the neighbor within 5 seconds, then the router returns to the active state. This process will continue until the neighbor responds. A common cause for the router to be stuck in the open state is an incorrect AS number in the neighbor statement. Once each neighbor has confirmed the open messages, the neighbor relationship is established. At this time, there should be a number in the state/prxrcd column, which indicates the number of networks being advertised by the neighbor. The number could very well be zero, though. This still indicates the neighbor relationship is established, just no networks are being advertised. 25
29 BGP Commands - Network Router(config-router)# network network-number mask network mask Allows BGP to advertise a route if it is in the Routing Table. - The network command must include all networks you want to advertise, not just those locally connected. - For the route designated in the network command to be advertised, there must be an exact match in the routing table. This command differs from the network command in IGPs in that it does not activate the protocol on an interface. The network command controls what networks the router advertises. This is a different concept from network commands used to configure IGPs. With this command we are not trying to run BGP on a certain interface (this is done by neighbor statements); rather we are trying to indicate to BGP what networks it should advertise to its neighbors. The mask portion is used because BGP4 supports subnetting/vlsm and super-netting (CIDR). A maximum of 200 entries of the network command are accepted. For the network command to advertise a network there must be an exact match (address & mask) in the routing table. It does not matter the source of this entry (connected, static, IGP, etc.), just that there is a match. Because the BGP network command will advertise a route learned from a source other than BGP, this can be considered a form of redistribution. 26
30 Show IP BGP router7#sho ip bgp BGP table version is 14, local router ID is Status codes: s suppressed, d damped, h history, * valid, > best, i - internal, r RIB-failure, S Stale Origin codes: i - IGP, e - EGP,? - incomplete Network Next Hop Metric LocPrf Weight Path *> / i *> / i *> / i *> / i *> / i *> / i *> / i The show ip bgp command displays the BGP topology database. All routing information learned from BGP neighbors is stored here. BGP table version local router ID Status Codes Internal version number of the table. This number is incremented whenever the table is updated. Router ID for BGP process. Status of the table entry. The status is displayed at the beginning of each line in the table. It can be one of the following values: s---the table entry is suppressed, (usually due to route summarization). *---The table entry is valid. >---The table entry is the best entry to use for that network. i----the table entry was learned via an internal BGP session. 27
31 Origin codes Indicates the origin of the entry. The origin code is placed at the end of each line in the table. It can be one of the following values: i----entry originated from IGP and was advertised with a network router configuration command. e---entry originated from EGP.?---Origin of the path is not clear. Usually, this is a route that is redistributed into BGP from an IGP. Network Next Hop Metric LocPrf Weight Path IP address of a network entity. IP address of the next system that is used when forwarding a packet to the destination network. An entry of indicates that the router is the owner of that network. Also called the multi-exit discriminator (MED). If shown, this is the value of the inter-autonomous system metric. The MED is an indication to external neighbors about the preferred path into an AS. This field is frequently not used. Local preference is an attribute provided to internal neighbors about the preferred path to exit the AS. The default value is 100. Weight is an attribute, which is used internal to the router for path selection. It is not exchanged with other routers in the network. Autonomous system paths to the destination network. There can be one entry in this field for each autonomous system in the path. Reference the origins codes above. 28
32 Clear IP BGP * or {address} This command should be performed after a configuration change to BGP. This forces the change to take effect immediately. Will interrupt the TCP connection. Use * to reset all connections. Use {address} to reset individual connection where {address} is the neighbor IP of the connection to reset. Discretion must be used when performing this command; all BGP routing information will be lost and may not reconverge for several minutes. When configuration changes are made to BGP, these will not necessarily take effect immediately. Configuration changes do not force an update message to be sent. Therefore, to implement these changes, the BGP connection must be reset. There are two options for doing this: reset all connections or reset an individual neighbor connection. To reset all neighbor connection, utilize the * in conjunction with the clear command. To reset a single neighbor connection, utilize the neighbor s ip address with the clear command. Special care must be given when utilizing this command. It will interrupt the routing of traffic utilizing BGP derived routing information. Prior to utilizing this command, coordination may have to be made with users to insure an untimely service interruption is not incurred. Also, for routers that are operating with multiple BGP neighbors, resetting all neighbor connections at the same time will cause all neighbor relationships to be reestablished at the same time and all BGP routing information to be exchanged simultaneously. If large amounts of routing information are received from multiple neighbors at the same time, this could overwhelm the router causing extended delays to the service interruption. 29
33 BGP Summarization Options Network command with no mask & auto summary enabled. - command advertises classful network if at least one subnet is present in routing table; auto summary is on by default. Static route pointing to Null 0, network command. - static route forces summarized network into routing allowing it to be advertised by network command. Aggregate address command. - advertises a summary route if a subnet of this exists in routing table. - summary-only extension suppresses subnets from being advertised. - as-set command causes all AS path info from subnets to be included in summary. There are three options when summarizing with BGP. 1. The network command can be utilized with no mask. This causes a classful network to be advertised when there is at least one subnet from the classful network in the routing table. This is referred to as automatic summarization (RIP & EIGRP). By default, the command autosummarization is configured in BGP. To disable this auto summarization feature, utilize the command no auto-summarization. Since classful networks are very rarely (if ever) used in today s routing, the command no auto-summ is a normal part of the BGP configuration. 2. The network command advertises the specified route and mask configured in the command if there is an exact match in the routing table. An easy way to advertise a summarized network is to force an entry into the routing table and then advertise this with the BGP network command. To force an entry into the routing table, configure a static route pointing to the null0 interface. It must be noted though that any more specific routes to the summarized static route are not automatically suppressed and may still be advertised. Also, the summarized route advertised by BGP shows it originating from that AS. If any of the subnets being summarized by this originated from another AS, this information is not carried forward. 30
34 3. The BGP aggregate address command summarizes and advertises the configured address and mask if one subnet of the summarized address exists in the BGP topology database. The summary extension to the command suppresses any subnets within the summarized address from being advertised. The as-set extension causes all as path information from each summarized subnet to be included in the advertised summarized network. This assists in avoiding routing loops. As stated earlier, for the summarized address to be advertised, there must be at least one subnet of this summarized address in the BGP database. It may be necessary to configure network commands for these subnets to install them in the BGP database. Technically, there only has to be one subnet of the summarized address in the BGP database but if for any reason this route is removed from the database, then the summarized address will no longer be advertised. If required, it is a good practice to insure multiple (if not all) of the summarized subnets are installed in the database. 31
35 BGP Summarization Commands Network Command and Static Route: router(config)# ip route ip address mask null0 - configures static route pointed at null0; address & mask are summarized network router(config-router)# network address mask mask - configures BGP to advertise summarized static route BGP Aggregate Address Command: router(config-router)# aggregate-address ip address mask [summary-only] [as-set] - configures BGP to advertise a summarized network - summary-only suppresses subnets of summarized network from being advertised - as-set causes as path info from subnets to be included in summarized advertisement To install a summarized static route, from the global configuration mode, use the ip route address mask interface command. The address and mask are the summarized network to advertise. The interface utilized is null0. The idea is that the routing table will have subnets or routes with a more exact match installed and the summarized route pointing to null0 will never be utilized. If for any reason it is, the packet is dumped. After the static route is configured, this will force the entry into the routing table. At this point, configure a network statement in BGP that matches the static route installed. This summarized network will then be advertised by BGP to its neighbors. Use the aggregate-address command to advertise a summarized route in BGP. The command is configured as part of BGP. The ip address and mask define the summarized network to be advertised. For this to be advertised, though, there must be at least one subnet of this network in the BGP database. If there are no subnet entries in the BGP database for this summarized network, a network statement for the subnets will have to be configured. With no extensions added to the command, the subnets will be advertised in addition to the summarized network. By adding the summary-only extension to the command, this will suppress any subnets of the summarized network from being advertised. By using the show ip bgp command, the suppressed subnets can be viewed. Adding the as-set extension will cause the AS path information from any summarized subnets to be included in the advertised summarized route. 32
36 BGP Summarization Lab (1) 1. Install the network on page Each router install a static route to null0 using the following networks: - router router router router router router router Configure a network command in BGP to match the static route. 4. Verify that the static route is being advertised to your neighbor(s). 5. Remove static route and network statement. Install the directly connected network from page 12 with each router in its own AS. Configure BGP neighbor relationships between each of the routers. Install the static routes listed above pointing to null0. Once this route is in the routing table, advertise it with a network statement in BGP. Take note that no subnets of this summarized route actually exist. This summarized route was just made up. When summarizing, it is important to insure that all parts of the summarized address are actually reachable. 33
37 BGP Summarization Lab (2) 1. Each router install the following loopback interfaces: - router 1 loopback 0 7 using networks each with a mask of router 2 loopback 0 7 using networks each /24 - router 3 loopback 0 7 using networks each /24 - router 4 loopback 0 7 using networks each /24 - router 5 loopback 0 7 using networks each /24 - router 6 loopback 0 7 using networks each /24 - router 7 loopback 0 7 using networks each /24 2. Configure a network command in BGP for each loopback network. Verify advertisement. 3. Configure aggregate-address command in BGP to summarize all loopback networks. Verify summarized address along with subnets are being advertised. 4. Add the summary-only extension. Verify subnets are being suppressed. Each router is installing several loopback interface networks. This is simply to generate networks for the purpose of route summarization. This is a classroom training tool only. Once the loop networks are installed, advertise these to your neighbors using networks commands in BGP. Once complete, use the aggregate-address command to advertise a summarized network to your neighbors. Note that all of the subnets are still being advertised. Add the summary-only extension to the aggregate address command. Note that the subnets are now not being advertised and are listed as suppressed in the BGP database. 34
38 BGP Summarization Lab (3) 1. Router 3 remove the aggregate route command. 2. All other routers verify that each of the loopback networks from router 3 are being advertised. Also verify that the AS path information is attached. 3. Router 1 install an aggregate address configuration with the summaryonly extension for router 3 s loopback networks. 4. Routers 7, 4, 5, & 6 verify the aggregate route is being received. Verify the AS path information. It should show the aggregate route originating from AS Router 1 remove the aggregate route command from BGP and then add the command back with both the summary-only and as-set extensions. 6. Routers 7, 4, 5, & 6 should now show the AS path for the aggregate route originating from AS 3. Router 3 removes its summarization. This allows the loopback networks to be advertised individually. Router 1 summarizes the loopback networks being advertised by router 3 and uses the summary-only extension. Routers 7, 4, 5, & 6 will see the summarized route with the subnets being suppressed. The AS path shows the summarized route as originating from AS 1. Router 1 removes the aggregate route configuration and then adds it back with the summary-only and the as-set extensions. Routers 7, 4, 5, & 6 should now show the summary route originating from AS 3. 35
39 BGP Lab AS /24 AS /24 /26 f0/0 s0/0 s0/0 f0/0 /26 s0/1 1 s0/2 1 s0/1 s0/2 /27 f0/0 2 s0/1 s0/0 /27 f0/0 s0/1 3 s0/0 /27 f0/0 2 s0/1 s0/0 /26 f0/0 s0/1 3 s0/0 /26 f0/0 s0/1 4 s0/0 /27 f0/0 s0/1 4 s0/0 Install the network above. Allocate and assign IP addresses within each AS. Enable OSPF in AS 1 and EIGRP in AS 2. Establish a BGP connection between the two ASs and perform route summarization. Advertise the summarized BGP route within each AS via the IGP. Ensure all subnets within both AS s are reachable from the distant AS. 36
40 BGP Review Questions 37
41 1. BGP is commonly used as a routing protocol? a. Interior b. Internal c. Exterior d. a and b 2. A network based on one authority for management is called. a. Known system b. An autonomous system c. Small system d. Singular system 3. What agency controls the distribution of AS numbers? a. IETF b. ARIN c. AFKN d. Microsoft 4. Two routers that have a direct BGP connection are called. a. Neighbors b. TCP c. Groups d. Packets 5. BGP uses what Transport protocol to ensure reliability? a. TCP b. UDP c. CDP d. LDP 6. Which of the following is a BGP message type? a. Open b. Update c. Notification d. Keepalive e. All of the above 7. Of the four BGP messages, which is used to provide routing updates? a. Keepalive b. Open c. Notification d. Update When does BGP send the entire routing table to its neighbors? a. During an update b. After the 5 th keepalive c. Immediately after the OPEN message d. After destination notification
42 9. What command is used to enable BGP on your router? a. Router bgp xxx b. Route bgp xxx c. Config Router bgp xxx d. ip Router bgp xxx 10. Neighbor statements are used to enable BGP on an interface. a. true b. false 11. Internal BGP neighbors have. a. the same AS number b. a high metric c. must be directly connected d. different AS numbers 12. An Autonomous system that allows packets to transit through it to reach another AS is considered what? a. A Transit Dynamic System b. A Transit Autonomous System c. A Transit Testing Center d. A Transit Encapsulation 13. BGP is an open protocol. a. True b. False 14. BGP supports redistribution. a. True b. False 15. BGP does not support route summarization. a. True b. False 16. Clear IP BGP* is used to do what? a. Reset all protocol connections b. Starts the BGP process during OSPF synchronization c. Stops the BGP process during OSPF synchronization d. Reset all BGP neighbor connections on that router 17. Sho IP BGP displays the IP routing table. a. True b. False 18. Sho IP route displays the BGP routing table. a. True b. False 39
43 19. To display the status of all BGP connections which command would you use? a. Show IP Router b. Sho IP BGP Sum c. Show BGP Sum d. Sho Router 20. In order to reset only one TCP connection between BGP Neighbors, what command must be used? a. Clear IP BGP xxx.xxx.xxx.xxx (x=the IP Address of your router) b. Clear IP BGP xxx.xxx.xxx.xxx (x=the Loopback Address of your neighbor) c. Clear IP BGP xxx.xxx.xxx.xxx (x=the OSPF Address of your router) d. Clear IP BGP xxx.xxx.xxx.xxx (x= the IP address of the neighbor) 21. What is the primary RFC for BGP? a. RFC 1221 b. RFC 1331 c. RFC 1661 d. RFC When performing a show IP BGP command, the I in the third column indicates what? a. An internal OSPF neighbor has old us about this network b. An internal BGP neighbor has told us about this network c. An interior BGP network has told us about this network d. An interior OSPF network has told us about this network 23. If the next hop address is shown as when performing a sho IP BGP Command, what does this signify? a. The neighbor router is the absolute owner of the network listed b. This router cannot find the network listed beside the c. This router is the absolute owner of the network listed beside the d. The neighbor router cannot find the network listed beside the Local Preference is used to determine the best pathway to leave the AS to reach an outside network in the case that you have more than one exit point. a. True b. False 25. The BGP Multi-Exit Discriminator (MED) is used to inform the distant AS of the recommended entrance points to your Autonomous System. a. True b. False External BGP has an administrative distance of.
44 a. 2 b. 20 c. 200 d Internal BGP has an administrative distance of. a. 2 b. 20 c. 200 d BGP will not accept updates that have originated from its own AS. a. True b. False 29. BGP uses what TCP port for establishing its connections? a. 179 b. 121 c. 800 d What does BGP use for its router ID? a. Your Subnet Mask b. Highest IP on an Active Interface c. Your Autonomous System Number d. Your BGP Neighbors IP Address e. All of the above 31. What protocol did BGP replace? a. AGP b. OGP c. EGP d. SGP 32. BGP is a CISCO product a. True b. False 33. By default, how often does BGP send updates? a. Every 30 seconds b. Every 60 seconds c. Whenever you change your password d. Whenever network changes occur 34. BGP stands for. a. Baseline Group Process b. Baseline Gateway Process c. Border Group Protocol d. Border Gateway Protocol 41
45 35. Which of the following is not an appropriate situation to use BGP? a. When the autonomous system is a transit autonomous system b. When there are multiple exit points c. When there is a single exit point d. When the network engineer understands BGP 36. When there is a single exit point into/out of and autonomous system, what is the preferred method? a. BGP b. OSPF c. Static d. IBGP 37. What command is used to advertise a network with BGP? a. ip route b. neighbor c. network d. default 38. You want to establish a BGP connection with directly connected interface in AS 69. Your address is in AS 101. What command should you used for this? a. network remote-as 69 b. network remote-as 101 c. neighbor mask 69 d. neighbor remote-as Autonomous System numbers are? a. arbitrary b. assigned c. classless d. between 1 and 6, EBGP neighbors expect to be? a. happy b. directly connected c. interconnected by an IGP d. classless 41. IGPs use to route traffic while BGP uses? a. distance, neighbor b. metric, policy c. cost, metric d. policy, cost 42. BGP supports CIDR? a. true b. false 42
46 43. What are three types of BGP route summarization? a. internal, external, & inter-area b. automatic, static route/network command, & aggregate address command c. automatic, intra-as, & inter-as d. automatic, static route/neighbor command, & aggregate address command 44. What does the summary-only extension to the aggregate address command do in BGP? a. suppresses as path information b. suppresses subnets of the summarized route c. will only accept summary routes d. supports CIDR 45. Which is true about the static route/network command summarization technique? a. the static route must be redistributed into BGP b. the static route distance must be set c. subnets of the summarized static route are not suppressed d. BGP must be redistributed into the static route 46. What is the range for private AS numbers? a through 6535 b through c through d. anything above the assigned range 43
47 Note Page 44
48 TAB Insert Tab # 2 Here
49 Access Control Lists
50 46
51 Why Use Access Lists?? Access List 10 deny permit any - Manage IP traffic as network access grows - Filter packets as they pass through the router The earliest routed networks connected a modest number of LANs and hosts. As the router connections increase to legacy and outside networks, and with the increased use of the Internet, there will be new challenges to control access. Network administrators face the following dilemma: how to deny unwanted connections while allowing appropriate access? Although other tools such as passwords, callback equipment, and physical security devices are helpful, they often lack the flexible and specific controls most administrators prefer. Access lists offer another powerful tool for network control. These lists add the flexibility to filter the packet flow in or out router interfaces. Such control can help limit network traffic and restrict network use by certain users or devices. 47
52 Access List Applications - Permit or deny packets moving through the router - Permit or deny vty access to or from the router - Permit or deny routing information Packet filtering helps control packet movement through the network. Such control can help limit network traffic and restrict network use by certain users or devices. To permit or deny packets from crossing specified router interfaces, Cisco provides access lists. An IP access list is a sequential list of permit and deny conditions that apply to IP addresses or upper-layer IP protocols. Access lists filter traffic going through the router but they do not filter traffic originated from the router. Access lists can also be applied to the vty ports of the router to permit or deny Telnet traffic into or out of the router s vty ports. You can use IP access lists to establish a finer granularity of control when differentiating traffic into priority and custom queues. An access list can also be used to identify interesting traffic that serves to trigger dialing in dial-on-demand routing (DDR). Access lists are also a fundamental component of route maps, which filter, and in some cases, alter the attributes within a routing protocol update. 48
53 What Are Access Lists? Access lists are properly called Access Control Lists (ACLs) E0 Incoming Packet Access List Processes Source and Destination Protocol Permit? Outgoing Packet S0 Optional Dialer Standard Simple address specifications Generally permits or denies entire protocol suite Extended More complex address specifications Generally permits or denies specific protocols Access lists are optional mechanisms in Cisco IOS software that can be configured to filter or test packets to determine whether to forward them toward their destination or to discard them. How access lists operate is the subject of the next several slides. There are two general types of access lists: 1. Standard access lists Standard access lists for IP check the source address of packets that could be routed. The result permits or denies output for an entire protocol suite, based on the source network/subnet/host IP address. 2. Extended access lists Extended IP access lists check for both source and destination packet addresses. They can also check for specific protocols, port numbers, and other parameters, which allow administrators more flexibility in describing what checking the access list will do. Access lists may be applied as: 1. Inbound access lists Incoming packets are processed before being routed to an outbound interface. An input access list is efficient because it saves the overhead of routing lookups if the packet is to be discarded because it is denied by the filtering tests. If the packet is permitted by the tests, it is then processed for routing. 49
54 2. Outbound access lists Incoming packets are routed to the outbound interface and then processed through the outbound access lists. Access lists express the set of rules that give added control for packets that enter inbound interfaces, packets that relay through the router and packets that exit outbound interfaces of the router. Access lists do not act on packets that originate from the router itself. Instead, access lists are statements that specify conditions on how the router will handle the traffic flow through specified interfaces. Access lists give added control for processing the specific packets in a unique way. 50
55 How Access Lists Work This example is applied as an outgoing ACL. The packet is permitted or denied at the exit interface. Packet Inbound Interface Packets Y Routing Table Entry? N Choose Interface Access List? Y N Test Access List Statements Permit? N Y Outbound Interfaces Packet Unwanted Packet Notify Sender Packet Discard Bucket The graphic shows an example of an outbound access list. The beginning of the process is the same regardless of whether outbound access lists are used or not. When a packet enters an interface, the router checks to see whether it is routable by checking the routing table. If not routable, the packet will be dropped. Next, the router checks to see whether the destination interface is grouped to an access list. If not, the packet can be sent to the output buffer. For example: a. If it will use S0, which has not been grouped to an outbound access list, the packet is sent to S0 directly. b. If it will use E0, which has been grouped to an outbound access list, before the packet can be sent out on E0, it is tested by a combination of access list statements associated with that interface. Based on the access list tests, the packet can be permitted or denied. For outbound lists, permit means send it to the output buffer; deny means discard the packet. For inbound lists, permit means continue to process the packet after receiving it on an inbound interface. Deny means discard the packet. When discarding packets, some protocols return a special packet to notify the sender that the destination is unreachable. 51
56 Access List Tests Top Down Processing Packet to interface Match First Test No Deny Deny DENY ALL Packet Discard Bucket Match Second Test No No Match Any Test Permit Permit Destination Interface Access list statements operate in sequential, logical order. They evaluate packets from the top down, one statement at a time. If a packet header and an access list statement match, the rest of the statements in the list are skipped and the packet is permitted or denied as specified in the matched statement. If a packet header does not match an access list statement, the packet will then be tested against the next statement in the list. This matching process continues until the end of the list is reached. A final implied statement covers all packets for which conditions did not test true. This final test condition matches all other packets and results in a deny. Instead of proceeding in or out an interface, all these remaining packets are dropped. This final statement is often referred to as the implicit deny any at the end of every access list. Because of the implicit deny any, an access list should have at least one permit statement in it; otherwise, the access list will block all traffic. An access list can be applied to multiple interfaces. However, there can be only one access list per protocol, per direction, per interface. 52
57 Configuration Guidelines Access list numbers indicate which protocol is filtered One access list per interface, per protocol, per direction Most restrictive statements should be at the top of the list There is a implicit deny any as the last access list testevery list should have at least one permit Create access lists before applying them to an interface Access list filter traffic going through the router; they do not apply to traffic originated from the router Follow these general principles to ensure the access lists you create have the intended results: Use numbers from the assigned range for the protocol and type of list you are creating. Only one access list per protocol, per direction, per interface is allowed. Multiple access lists are permitted per interface, but each must be for a different protocol. Top-down processing a. Organize your access list so that more specific references in a network or subnet appear before ones that are more general. Place more frequently occurring conditions before less frequent conditions. b. Subsequent additions are always added to the end of the access list. c. You cannot selectively add or remove lines when using numbered access lists, but you can when using named IP access lists 53
58 (a Cisco IOS Release 11.2 feature). With named IP access lists, additions are still added to the end of the access list. Implicit deny all a. Unless you end your access list with an explicit permit any, it will deny by default all traffic that fails to match any of the access list lines. b. Every access list should have at least one permit statement. Otherwise, all traffic will be denied. Create the access list before applying it to an interface. An interface with an empty access list applied to it allows (permits) all traffic. Access lists only filter traffic going through the router. They do not filter traffic originated from the router. In practice, access list commands can be lengthy character strings. Access lists can be complicated to enter or interpret. However, you can simplify understanding of general access list configuration commands by reducing the commands to two general elements. The access list contains global statements: This global statement identifies the access list, usually an access list number. This number refers to the type of access list this will be. In Cisco IOS Release 11.2 or later, access lists for IP may also use an access list name rather than a number. Named IP access lists will be covered later in this chapter. The permit or deny term in the global access list statement indicates how packets that meet the test conditions will be handled by Cisco IOS software. Permit usually means the packet will be allowed to use one or more interfaces that you will specify later. Deny usually means discard the packet. The final term or terms specify the test conditions used by this access list statement. The test can be as simple as checking for a single source address. However, usually test conditions are extended to include several test conditions. Use several global access list statements with the same access list number or name to stack several test conditions into a logical sequence or list of tests. 54
59 How to Identify Access Lists Access List Type Number Range/Identifier IP Standard Extended 1-99; Expanded ; Expanded Named (Cisco IOS 11.2 and later) IPX AppleTalk Standard Extended SAP filters Named (Cisco IOS F and later) Standard IP access lists (1-99) test conditions of all IP packets from the source address. - Extended access lists ( ) can test conditions of source and destination ports. Access lists can control most protocols on a Cisco router. The figure shows the protocols and number ranges of the access list types for IP and IPX. IPX access lists are covered in the Configuring Novell IPX chapter of this course. An administrator enters a number in the protocol number range as the first argument of the global access list statement. The router identifies which access list software to use based on this numbered entry. Access list test conditions follow as arguments. These arguments specify test according to the rules of the given protocol suite. The test conditions for an access list vary by protocol. Many access lists are possible for a protocol. Select a different number from the protocol number range for each new access list; however, the administrator can specify only one access list per protocol, per direction, per interface. Specifying an access list number from 1 to 99 instructs the router to accept standard IP access list statements. Specifying an access list number from 100 to 199 instructs the router to accept extended IP access list statements. Expanded ranges of for standard IP lists and for extended IP lists were added with Cisco IOS
60 Testing with Standard ACLs An Example from a TCP/IP Packet Frame Header (for example, HDLC) Packet (IP header) Segment (for example, TCP header) Data Source Address Deny Use access list statements to test the packet Permit Standard access lists only examine source address 56
61 Testing with Extended ACLs Extended access lists offer greater flexibility Frame Header (for example, HDLC) Packet (IP header) Segment (for example, TCP header) Data Source Address Destination Address Protocol Port Number Deny Use access list statements to test the packet Permit For TCP/IP packet filtering, Cisco IOS IP access lists check the packet & upperlayer headers for: Source IP addresses using standard access lists. Standard access lists are identified with a number in the range 1 to 99. Destination and source IP address, specific protocols, and TCP or UDP port numbers using extended access lists. Extended access lists are identified with a number in the range 100 to 199. For all of these IP access lists, after a packet is checked for a match with the access list statement, it can be denied or permitted to use an interface in the access group. 57
62 How to Use Wildcard Mask Bits Octet bit position and address value for bit = = = = = Examples check all address bits (match all) ignore last 6 address bits ignore last 4 address bits check last 2 address bits do not check address (ignore bits in octet) 0 means check corresponding bit value 1 means ignore value of corresponding bit Address filtering occurs using access list address wildcard masking to identify how to check or ignore corresponding IP address bits. Wildcard masking for IP address bits uses the number 1 and the number 0 to identify how to treat the corresponding IP address bits. A wildcard mask bit 0 means check the corresponding bit value. A wildcard mask bit 1 means do not check (ignore) that corresponding bit value. This type of mask is sometimes referred to as an inverted mask. By carefully setting wildcard masks, an administrator can select single or several IP addresses for permit or deny tests. Refer to the example in the figure. Note: Wildcard masking for access lists operates differently from an IP subnet mask. A 0 (zero) in a bit position of the access list mask indicates that the corresponding bit in the address must be checked; a 1 (one) in a bit position of the access list mask indicates the corresponding bit in the address is not interesting and can be ignored. 58
63 Matching Specific IP Host Address Test conditions: Check all the address bits (match all) An IP host address, for example: Wildcard mask: (check all bits) Example checks all the address bits Abbreviate the wildcard using the IP address preceded by the keyword host You have seen how the zero and one bits in an access list wildcard mask cause the access list to either check or ignore the corresponding bit in the IP address. In the figure, this wildcard masking process is applied in an example. Consider a network administrator who wants to specify that a specific IP host address will be denied in an access list test. To indicate a host IP address, the administrator would enter the full address for example, ; then to indicate that the access list should check all the bits in the address, the corresponding wildcard mask bits for this address would be all zeros, that is, Working with decimal representations of binary wildcard mask bits can be tedious. For the most common uses of wildcard masking, you can use abbreviation words. These abbreviation words reduce how many numbers an administrator will be required to enter while configuring address test conditions. One example where you can use an abbreviation instead of a long wildcard mask string is when you want to match a host address. The administrator can use the abbreviation host to communicate this same test condition to Cisco IOS access list software. In the example, instead of typing , the administrator can use the string host
64 Matching Any IP Address Test conditions: Ignore all the address bits (match any) Any IP address Wildcard mask: (ignore all) Accept any address: Abbreviate the expression using the keyword any A second common condition where Cisco IOS software will permit an abbreviation term in the access list wildcard mask is when the administrator wants to match all the bits of any IP address. Consider a network administrator who wants to specify that any destination address will be permitted in an access list test. To indicate any IP address, the administrator would enter ; then to indicate that the access list should ignore (allow without checking) any value, the corresponding wildcard mask bits for this address would be all ones ( ). The administrator can use the abbreviation any to communicate this same test condition to Cisco IOS access list software. Instead of typing , the administrator can use the work any by itself as the keyword. 60
65 Wildcard Bits to Match IP Subnets Test for IP subnets /24 to / Address Wildcard Mask Wildcard mask: match wildcard bits = = = = 31 An administrator wants to test a range of IP subnets that will be permitted or denied. Assume the IP address is a Class B address (the first two octets are the network number) with eight bits of sub-netting (the third octet is for subnets). The administrator wants to use the IP wildcard masking bits to match subnets /24 to /24. First, the wildcard mask will check the first two octets (172.30) using corresponding zero bits in the wildcard mask. Because there is no interest in an individual host, the wildcard mask will ignore the final octet by using corresponding one bit in the wildcard mask (The final octet of the wildcard mask is 255 in decimal for example). In the third octet, where the subnet address occurs, the wildcard mask will check that the bit position for the binary 16 is on and all the higher bits are off using corresponding zero bits in the wildcard mask. For the final (low-end) four bits in this octet, the wildcard mask will indicate that the bits can be ignored. In these positions, the address value can be binary 0 or binary 1. Thus, the wildcard mask matches subnet 16, 17, 18, and so on up to subnet 31. The wildcard mask will not match any other subnets. In this example, the address with the wildcard mask matches subnets /24 to /24. 61
66 Select IP Ranges with Wildcards router (config) # access-list 1 deny router (config) # access-list 1 permit any match can t change Address: = 192 Mask: = 63 Tested addresses: Range =
67 Standard Access Lists Router(config)# access-list access-list-number { permit deny } source { mask } Router(config)# - Sets parameters for this list entry. May be one of several statements. - IP standard access lists use Default wild card mask = No access-list access-list-number removes entire access list ip access-group access-list-number { in out } - Activates a list on an interface - Sets inbound or out bound testing - Default = Outbound - No ip access-group access-list-number removes access list from the interface 63
68 The access-list command creates an entry in a standard IP traffic filter list. Access-list Command Access-list-number permit deny source source-mask Description Identifies the list to which the entry belongs; a number From 1 to 99. Indicates whether this entry allows or blocks traffic from the specified address. Identifies source IP address. Identifies which bits in the address field are matched. The default mask is (match all bits). The ip access-group command links an existing access list to an interface. Only one access list per protocol, per direction, per interface is allowed. ip access-group Command access-list-number in out Description Indicates the number of the access list to be linked to this interface. Selects whether the access list is applied as an incoming or outgoing filter. If in or out is not specified, out is the default. Note: To remove an IP access list from an interface, first enter the no ip accessgroup access-list-number command on the interface then enter the global no access-list access-list-number command to remove the access list. The ip access-group interface command activates an IP access list on an interface. Note: If you apply an access list with the ip access-group command to an interface before any access list lines have been created, the result will be permit any. The list is live, so if you enter only one line, it goes from a permit any to a deny Most (because of the implicit deny all at the end) as soon as you press Return. For this reason, create your access list before you apply it to an interface. 64
69 Standard IP Access List Example 1 Permit my network only R s0 e0 e1 R Access-list 1 permit (implicit deny all not visible in the list) (access-list 1 deny ) interface serial 0 ip access-group 1 out The following table describes the access list presented in the figure: access-list Command Description 1 Access list number that indicates this is a standard list. permit Traffic that matches selected parameters will be forwarded IP address that will be used with the wildcard mask to identify the source network Wildcard mask; 0s indicate positions that must match, 1s indicate don t care positions. ip access-group 1 out Links the access list to the interface as an outbound filter. This access list allows only traffic from source network to be forwarded out on S0. Non network traffic is blocked. 65
70 Stand IP Access List Example 2 Deny a specific host e0 R1 s0 R2 R2 s configuration Access-list 1 deny Access-list 1 permit (implicit deny all not visible in the list) (access-list 1 deny ) interface ethernet 0 ip access-group 1 out e1 66
71 access-list Command Description 1 Access list number that indicates this is a standard list. deny Traffic that matches selected parameters will not be forwarded IP address of the source host This mask requires the test to match all bits (default mask). access-list Command Description 1 Access list number that indicates this is a standard list. permit Traffic that matches selected parameters will be forwarded IP address of the source host; all 0s indicate a placeholder Wildcard mask; 0s indicate positions that must match, 1s indicate don t care positions. All 1s in the mask indicate that all 32 bits will not be checked in the source address. This access list is designed to block traffic from a specific address, , and to allow all other traffic to be forwarded on interface Ethernet 0. The IP address and wildcard mask combination permits traffic from any source. This combination can also be written using the keyword any. 67
72 Standard IP Access List Example 3 Deny a specific subnet e0 R1 s0 e R2 s configuration R2 Access-list 1 deny Access-list 1 permit any (implicit deny all not visible in the list) (access-list 1 deny ) interface ethernet 0 ip access-group 1 out 68
73 In the example: access-list Command Description 1 Access list number that indicates this is a standard list. deny Traffic that matches selected parameters will not be forwarded IP address of the source subnet Wildcard mask; 0s indicate positions that must match, 1s indicate don t care positions. The mask with 0s in the first three octets indicates those positions must match; the 255 in the last octet indicates a don t care condition. access-list Command Description 1 Access list number that indicates this is a standard list. permit any traffic that matches selected parameters will be forwarded. Abbreviation for the IP address of the source; all 0s indicate a placeholder and the wildcard mask. All 1s in the mask indicates that all 32 bits will not be checked in the source address. This access list is designed to block traffic from a specific subnet, , and to allow all other traffic to be forwarded out E0. 69
74 Access List Exercise 1 Create a Standard IP Access List to filter traffic into your LAN. - Router 1 = You want to block Router 2 - Router 2 = You want to block Router 3 - Router 3 = You want to block Router 4 - Router 4 = You want to block Router 5 - Router 5 = You want to block Router 6 - Router 6 = You want to block Router 7 - Router 7 = You want to block Router 1 - Router 8 (if present) = Block Router 3 Test by pinging from laptop to laptop. All stations but the blocked router should be able to ping your laptop. 70
75 Standard vs Extended Access List Standard Filters based on Source Permit or deny entire TCP/IP protocol suite Range is 1 through 99 (expanded ) Extended Filters based on Source and Destination Specifies a specific IP Protocol and port number Range is 100 through 199 (expanded ) The standard access list (numbered 1 to 99) may not provide the traffic filtering control you need. Standard access lists filter based on a source address and mask. Standard access lists permit or deny the entire TCP/IP protocol suite. You may need a more precise way to filter your network traffic. For more precise traffic-filtering control, use extended IP access lists, which check for source and destination address. In addition, at the end of the extended access list statement, you can specify the protocol and optional TCP or UDP port number to filter more precisely. Port numbers can be the well known port numbers. A few of the most common port numbers are as follows: Well Known Port Number (Decimal) IP Protocol 20 (TCP) File Transfer Protocol (FTP) data 21 (TCP) FTP program 23 (TCP) Telnet 25 (TCP) Simple Mail Transport Protocol (SMTP) 53 (TCP/UDP) Domain Name System (DNS) 69 (UDP) Trivial File Transfer Protocol (TFTP) 80 (TCP) HyperText Transfer Protocol (HTTP) By using this option, you can specify the logical operation the extended access list will perform on specific protocols. IP extended access lists use a number from the range 100 to
76 Extended IP Access List Router (config) # access-list access-list-number { permit / deny } protocol source source-wildcard [ operator port ] destination destination-wildcard [ operator port ] [ established ] [log] - Sets parameters for this list entry Router (config-if)# ip access-group access-list-number {in / out} - Activates the extended list on an interface The access-list command creates an entry to express a condition statement in a complex filter. The following table explains the syntax of the command as shown in the figure. 72
77 access-list Command access-list-number Description Identifies the list using a number in the range 100 to 199 permit deny Indicates whether this entry allows or blocks the specified address. protocol IP, TCP, UDP, ICMP, GRE, IGRP source and destination Identifies source and destination IP addresses. Source-wildcard and destination-wildcard Wildcard mask; 0s indicate positions that must match, 1s indicate don t care positions. operator port established log It, gt, eq, neq, (less than, greater than, equal, not Equal), and a port number. For inbound TCP only. Allows TCP traffic to pass if packet uses an established connection (for example, it has ACK bits set). Sends a logging message to the console. Note: The syntax of the access-list command presented here is representational of the TCP protocol form. Not all parameters or options are given. For the complete syntax of all forms of the command, refer to the appropriate Cisco IOS documentation available on CD-ROM or at the CCO web site. 73
78 The ip access-group command links an existing extended access list to an interface. Only one access list per protocol, per direction, per interface is allowed. ip access-group Description access-list-number Indicates the number of the access list to be linked to an interface. in out Selects whether the access list is applied as an input or output filter. If in or out is not specified, out is the default. 74
79 Extended Access List Example 1 Non e0 s e1 Access-list 101 deny tcp eq 21 Access-list 101 deny tcp eq 20 Access-list 101 permit ip any any (implicit deny all) (Access-list 101 deny ip Interface ethernet 0 Ip access-group 101 out - Deny FTP from subnet to subnet out of e0 - Permit all other traffic 75
80 In the example: access-list Command Description 101 Access list number 101 indicates an extended IP access list. deny Traffic that matches selected parameters will be blocked. tcp TCP protocol Source IP address and mask; the first three octets must match but do not care about the last octet Destination IP address and mask; the first three match, but do not care about the last octet. eq 21 Specifies the well-known port number for FTP control eq 20 Specifies the well-known port number for FTP data. ip access-group 101 out Description links access list 101 to interface E0 as an output filter. The deny statements deny FTP traffic from subnet to subnet The permit statement allows all other IP traffic out interface E0 76
81 Extended Access List Example 2 Non e0 s0 e Access-list 101 deny tcp eq 23 Access-list 101 permit ip any any (implicit deny all) (Access-list 101 deny ip Interface ethernet 0 Ip access-group 101 out - Deny only Telnet from subnet out of e0 - Permit all other traffic 77
82 In the example: Access-list Command Description 101 Access list number; indicates extended IP access list. deny Traffic that matches selected parameters will not be. forwarded. tcp Transport-layer protocol Source IP address and mask; the first three octets must match but do not care about the last octet. any eq 23 permit ip any any Match any destination IP address Specifies well-known port number for Telnet. Traffic that matches selected parameters will be forwarded. Any IP protocol. Keyword matching traffic from any source. Keyword matching traffic to any destination. ip access-group 101 out Description Links access list 101 to interface E0 as an output filter. This example denies telnet traffic from being sent out interface E0. All other IP traffic from any other source to any destination is permitted out E0. 78
83 Access List Exercise 2 Create an Extended IP Access List to filter host telnet access through your router, apply this list to all applicable interfaces. - Router 1 = You want to filter computer 2 - Router 2 = You want to filter computer 3 - Router 3 = You want to filter computer 4 - Router 4 = You want to filter computer 5 - Router 5 = You want to filter computer 6 - Router 6 = You want to filter computer 7 - Router 7 = You want to filter computer 1 - Router 8 = You want to filter computer 4 All laptops except the blocked laptop should be able to telnet to your router. 79
84 Using Named IP Access Lists -Feature for Cisco IOS Release 11.2 or later Router (config)# ip access-list { standard / extended } name -Alphanumeric name string must be unique Router (config { standard / extended } name)# [enter either a standard and or extended access list as performed in the previous examples] No { permit / deny } { ip access list test conditions } - no removes the specific test from the named access-list Router (config-if)# ip access-group name { in / out } - Activates the IP named access list on an interface This feature allows IP standard and extended access lists to be identified with an alphanumeric string (name) instead of the current numeric (1 to 199) representations. With a numbered IP access list, an administrator wanting to alter an access list would first be required to delete the numbered access list then reconfigure it. Individual statements cannot be deleted. Named IP access lists allow you to delete or insert individual lines of a specific access list. Deleting individual entries enables you to modify your access lists without deleting and then reconfiguring them. Use named IP access list when: You want to intuitively identify access lists using an alphanumeric name. You have more than 99 standard and 100 extended access control lists to be configured in a router for a given protocol. 80
85 Consider the following before implementing named IP access lists: Named IP access lists are not compatible with Cisco IOS releases prior to Release You cannot use the same name for multiple access lists. In addition, access lists of different types cannot have the same name. For example, it is illegal to specify a standard access control list named George and an extended access control list with the same name. Note: Most of the commonly used IP access list commands accept named IP access lists. 81
86 Other Common ACL Applications Blocking telnet access in / out vty lines Standard ACLs can be applied to the vty lines, to permit or deny certain IPs from telnetting into, or once in, out of the router. -- Uses the access-class command to apply -- Does not affect local users consoled into the router Example: Access-list 12 permit ! Line vty 0 15 Access-class 12 in Filtering routing information ACLs can be used to limit the propagation of routing information -- Applied to the routing protocol with the distribute-list command -- Applied as route maps to route redistribution process (exchanging route info from one protocol or source to another) For security purposes, users can be denied virtual terminal (vty) access to the router, or users can be permitted vty access to the router but denied access to destinations from that router. Restricting virtual terminal access is less a traffic control mechanism than one technique for increasing network security. Telnet filtering is normally considered an extended IP access list function because it is filtering a higher-level protocol. However, we can filter incoming telnet sessions by source address and apply it to vty lines with the access-class command. We can use standard IP access list statements to do so. The access-class command also applies standard IP access list filtering to outgoing vty lines for people who have established telnet sessions to your router. Normally, set identical restrictions on all virtual terminal lines because you cannot control on which virtual terminal line a user will connect. 82
87 ACL Configuration Principles - Order of access list statements is crucial Recommended: use a text editor on a TFTP server or use PC to cut and paste. - Top-down processing Place more specific test statements first. - No reordering / removal of statements for numbered lists Use no access-list number command to remove entire list Exception: Named access lists permit addition and removal of individual statements. - Implicit deny all Unless access list ends with explicit permit any. The basic principles of access list configuration are given in the figure. The order of access list statements is crucial to proper filtering. It is recommended to create and download your access list on a TFTP server using a text editor or to use a PC to cut and paste the access list into the router. Access lists are processed from the top down. If you place more specific tests, and tests that will test true frequently, in the beginning of the access list you can reduce processing overhead. Only named access lists allow removal, but not reordering, of individual statements from a list. If you wish to reorder or remove access list statements, you must remove the whole list and recreate it in the desired order or with the desired statements. All access lists end with an implicit deny all statements. 83
88 Where to Apply Access Lists S0 S0/0 E0 A E0 To0 B TOKEN RING S1 S0/1 C E0 S1/1 E0 S1 D E1 Recommended: - Place extended access lists close to the source. - Place standard access lists close to the destination. Access lists are used to control traffic by filtering and eliminating unwanted packets. Proper placement of an access list statement can reduce unnecessary traffic. Traffic that will be denied at a remote destination should not use network resources along the route to that destination. Suppose an enterprise s policy aims at denying Token Ring traffic on Router A to the switched Ethernet LAN on Router D s E1 port. At the same time, other traffic must be permitted. Several approaches can accomplish this policy. The recommended approach uses an extended access list. It specifies both source and destination addresses. Place this extended access list in Router A. Then, packets do not cross Router A s Ethernet, do not cross the serial interfaces of Routers B and C, and do not enter Router D. Traffic with different source and destination addresses can still be permitted. Extended access lists should normally be placed as close as possible to the source of the traffic to be denied. Standard access lists do not specify destination addresses. The administrator would have to put the standard access list as near the destination as possible. For example, place an access list on E0 of Router D to prevent Token Ring traffic from Router A. 84
89 Verifying Access Lists Commands to Verify Access Lists - show ip interface Will show the access list applied to that interface. - show access-lists Will show all access lists on the router. - show access-lists {access-list number} Displays on the access list number you specify. -show {protocol} access-list {access-list number} Will show all access lists applied in that protocol. (Normally you would use IP for protocol). 85
90 Access List Review Questions 86
91 1. An IP standard access list can. a. Control traffic with the destination address b. Control traffic with the source address c. Control traffic with the source and destination address d. Control traffic using a port number e. All of the above 2. All access lists have by default the last statement of? a. Permit any b. Permit routes c. Deny any d. Deny routes 3. Standard Access lists permit or deny? a. Entire protocol suite b. Packets that originate from the router issuing the access list c. Specific protocols with-in a TCP/IP packet d. All of the above 4. When a standard access list is applied to an interface and you do not specify a direction, the access list is applied as. a. Incoming filter b. Out going filter c. In and out going filter d. Will not work 5. Which of the following is a standard access list entry? a. Access list 1 permit eq 21 b. Access list 100 permit eq 21 c. Access list 1 permit d. Access list 100 permit An IP extended access list can. a. Control traffic with the destination address b. Control traffic with the source address c. Control traffic using a port number d. Control traffic with the source and destination address e. All of the above 7. Extended Access lists permit or deny? a. Entire protocol suite b. Packets that originate from the router issuing the access list c. Specific protocols with-in a TCP/IP packet d. All of the above 87
92 8. When an extended access list is applied to an interface and you do not specify a direction, the access list is applied as. a. Incoming filter b. Out going filter c. In and out going filter d. Will not work 9. Which of the following is a valid extended access list entry? a. Access list 1 permit eq 21 b. Access list 100 permit eq 21 c. Access list 100 permit d. Access list 1 permit If you have an access list with the following entries applied (see below) to an interface what would the affects of the access list be on a packet with the source address of ? Access list 1 permit Access list 1 permit Access list 1 deny Access list 1 deny a. Allowed to pass b. Blocked 11. If you have, an access list with the following entries applied (see below) to an interface what would the affects of the access list be on a packet with the source address of ? Access list 1 permit Access list 1 permit Access list 1 deny Access list 1 deny a. Allowed to pass b. Blocked 12. If you have, an access list with the following entries applied (see below) to an interface what would the affects of the access list be on a packet with the source address of ? Access list 1 permit Access list 1 permit Access list 1 deny Access list 1 deny a. Allowed to pass b. Blocked 88
93 13. If you have, an access list with the following entries applied (see below) to an interface what would the affects of the access list be on a packet with the source address of ? Access list 1 permit Access list 1 permit Access list 1 deny Access list 1 deny a. Allowed to pass b. Blocked 14. If you have, an access list with the following entries applied (see below) to an interface what would the affects of the access list be on a packet with the source address of ? Access list 1 permit Access list 1 permit Access list 1 deny Access list 1 deny a. Allowed to pass b. Blocked 15. If you have, an access list with the following entries applied (see below) to an interface what would the affects of the access list be on a packet with the source address of and a destination address of ? Access list 100 permit Access list 100 permit Access list 100 deny Access list 100 deny Access list 100 permit any any a. Allowed to pass b. Blocked 16. If you have, an access list with the following entries applied (see below) to an interface what would the affects of the access list be on a packet with the source address of and a destination address of ? Access list 100 permit Access list 100 permit Access list 100 deny Access list 100 deny Access list 100 permit any any a. Allowed to pass b. Blocked 89
94 17. If you have, an access list with the following entries applied (see below) to an interface what would the affects of the access list be on a packet with the source address of and a destination address of ? Access list 100 permit Access list 100 permit Access list 100 deny Access list 100 deny Access list 100 permit any any a. Allowed to pass b. Blocked 18. If you have, an access list with the following entries applied (see below) to an interface what would the affects of the access list be on a packet with the source address of and a destination address of ? Access list 100 permit Access list 100 permit Access list 100 deny Access list 100 deny Access list 100 permit any any a. Allowed to pass b. Blocked 19. If you have, an access list with the following entries applied (see below) to an interface what would the affects of the access list be on a packet with the source address of and a destination address of ? Access list 100 permit Access list 100 permit Access list 100 deny Access list 100 deny Access list 100 permit any any a. Allowed to pass b. Blocked 20. If you have, an access list with the following entries applied (see below) to an interface what would the affects of the access list be on a packet with the source address of and a destination address of ? Access list 100 permit Access list 100 permit Access list 100 deny Access list 100 deny Access list 100 permit any any a. Allowed to pass b. Blocked 90
95 TAB Insert Tab # 3 Here
96 EIGRP Enhanced Interior Gateway Routing Protocol
97 92
98 Characteristics of EIGRP Cisco Proprietary Triggered routing updates and automatic neighbor discovery Utilizes multicast for updates and hello packets Advanced Distance Vector Uses Reliable Transport Protocol to send routing updates Eliminates the need for periodic full updates Maintains a route topology database Stores all routes received from neighbors DUAL Diffused Update Algorithm (loop free routing) Has backup route readily available (feasible successor) Actively queries neighbors if backup not available Simple configuration: classless, but programs like classful Manual route summarization at any point in the topology Load balancing available across unequal metric routes EIGRP is a Cisco proprietary protocol that combines the advantages of link-state and distance vector routing protocols. As a hybrid protocol, EIGRP includes the following features: Neighbor discovery and maintenance are dynamic through the use of the Hello Protocol. Routing updates are exchanged between neighbors upon changes to the network topology as opposed to periodic updates regardless of changes. EIGRP utilizes multicast addressing as opposed to broadcast for the hello protocol and routing updates. EIGRP is labeled an Advanced Distance Vector routing protocol. When exchanging information with neighbors it utilizes the reliable transport protocol (RTP). This guarantees delivery of information such as updates. It maintains a topology database similar to link state protocols which allow it to make routing decisions without waiting on information from neighboring routers. This also dramatically speeds up the convergence time required for the routers within the EIGRP topology. EIGRP utilizes the Diffusing Update Algorithm (DUAL) to determine the preferred route information within the topology database. Within the topology database are stored backup routes which can be automatically installed in the routing table upon failure of the primary route path. If there is not a back up available, EIGRP actively queries its neighbors for routing information. 93
99 EIGRP configuration is simple in that it programs like a classful protocol (classful network statements) but has all the advantages of a classless protocol. With it being a distance vector protocol, route filtering is also easy to configure. Route summarization can be installed on any router and/or interface within the EIGRP topology. This is a very powerful tool and simplifies EIGRP topology design and implementation since there is no concept of border routers. EIGRP has the option to load balance across unequal metric paths. This load balancing is proportional to the metric of each link. Other routing protocols have to see equal metrics on routes before load balancing. This causes some links to not be utilized at all while others may become saturated with traffic. 94
100 EIGRP Comparison Classful Classless Classless Distance Vector Advanced Distance Link State RIP / IGRP Vector EIGRP OSPF Metric Hop Count / Bandwidth, Delay by Default DUAL Algorithm based on Bandwidth and Delay of Link Dijkstra Algorithm based on Bandwidth of Link Neighbor States Any Router within same network directly connected and running like Routing Protocol Uses Hello protocol to dynamically learn of Neighbors resulting in faster convergence Uses Hello protocol to dynamically learn of Neighbors resulting in faster convergence Route Propagation Backup Routes Broadcast full table every 30 Seconds No, must wait for next broadcast of routing table Multicast partial updates only when path or metric changes and only to neighbors Yes, through topology database. Feasible successor requires no neighbor queries Multicast partial updates only when path or metric changes to all like routers in Area Yes, through topology database. Summarization Automatic at network boundaries; no manual summarization available Automatic at network boundaries; manual summarization available on all interfaces Manual only on ABRs; recommended towards the Backbone Area You can better understand the technology used in EIGRP by comparing it with other protocols well known to the internetworking industry. Routing protocols have two major approaches: Routing by Rumor Also known as distance-vector. This method is used by protocols, such as IGRP, RIP, and BGP, where each router knows only what its neighbor tells it. Routing by Propaganda Also known as link-state. This method is used by protocols such as OSPF, or IS-IS, where all the routers in a region of the network share a common understanding of the region s topology. EIGRP is most similar to a distance vector protocol using only information it receives from its directly connected neighbors for routing decisions, but unlike a pure distance vector where only the best route is stored, EIGRP stores all routes received. Knowledge of more than one route enables the ability to switch quickly to an alternate should the current become unavailable. Additionally EIGRP takes an active role and queries its neighbors when a destination becomes unreachable if an alternate path is not available. Traditional distance vector protocols passively wait for a reported route. 95
101 EIGRP Databases Neighbor Table Database Lists Neighbors Topology Database Lists All Routes (Feasible Successor) Routing Table Lists Best Routes Hello Packets Updates From Neighbors Calculated by Router using info from Topology Database (DUAL) The neighbor database tracks and maintains all EIGRP router neighbors. The neighbors are established through the used of hello packets. Once the neighbor relationship is established, the hello packets continue at set intervals to maintain the relationship. The hello packets when used for this purpose are sometimes referred to as keepalives. The neighbor database also tracks and averages the amount of time it takes for neighbors to respond to reliable packets. This averaged time is then used to determine the RTO. The topology database stores all EIGRP updates received from neighboring routers. Backup routes to routes selected for installation in the routing table (referred to as feasible successors) are designated and stored within the topology database. The DUAL algorithm is applied to the topology database. The preferred routes from the topology database are then offered to the routing table as candidates. Two criteria are utilized by the routing table in the selection of entries into the table: administrative distance and metrics. 96
102 EIGRP Packets Hello: Used to establish/maintain neighbor relationships. Update: Used to send routing updates. Query: Used to ask neighbors for routing information. Reply: Response to query. ACK: Used to acknowledge a reliable packet. EIGRP supports the following five generic packet types: Hello: Hello packets are used for neighbor discovery. They are sent as multicasts and carry a zero acknowledgment number. Update: An update is sent to provide information on the routes that a particular router has converged. These are sent as multicasts when a new route is discovered, or when convergence has completed (and the route is passive). They are also sent as Unicast when neighbors start up in order to synchronize the topology tables (since updates are not sent periodically as in IGRP). Queries: When a router is performing route computation, and it does not have a feasible successor, it will send a query packet to its neighbors asking if they have a feasible successor for the destination. Queries are always multicast. Replies: A reply packet is sent in response to a query packet. Replies are Unicast to the originator of the query. ACK: The ACK is used for acknowledging other types of packets described above. ACKs are hello packets that are sent as unicasts, and contain a nonzero acknowledgment number. Update, query, and reply packets are all sent reliably and require acknowledgement. 97
103 Neighbor Discovery Process EIGRP uses Hello protocol (multicast, ) on every interface whose address falls within the network statement range. Two routers become neighbors when they exchange hello packets - must agree on autonomous system number and K-values. Once neighbor discovery is complete, hello s continue as keepalives. Hellos sent once every 5 seconds on LAN s, point-to-point WANs, and high speed (>T-1) multi-point WANs. Hellos are sent once every 60 seconds on multi-point low speed WANs (<T-1). Neighbor is declared dead if no EIGRP packets are received within hold interval (default three times the hello interval). When EIGRP is enabled and an interface is found to be within its network range, the router sends periodic multicast hello packets out that interface. When another router running EIGRP within the same autonomous system receives a hello packet, it establishes a neighbor relationship between the two by responding with an update containing his complete routing information. This update packet will have the Init bit set, which indicates the initialization process. In response to the update, the first router sends an update with all his route information. Once acknowledged, the neighbors are considered adjacent. The hello mechanism not only dynamically discovers neighbors; it also discovers the loss of neighbors. After neighbor establishment, the hello packet is used as a keep alive. If a hello packet is not heard before the expiration of the hold time, then a topology change is detected. The neighbor adjacency is deleted, and all topology table entries learned from that neighbor are removed. This enables the routers to quickly re-converge if an alternate, feasible successor does not exist. The rate at which hello packets are sent is called the hello interval and can be adjusted per interface with the ip eigrp hello-interval command. The amount of time a router will consider a neighbor up without receiving a hello or any EIGRP packet is called the hold time, and can be adjusted per interface with the ip eigrp hold-time command. 98
104 Step by Step Neighboring Topology Database A I am Router A, is anyone here? Hello I am Router B, here are all my routes B Update Init Bit Set ACK Update Thanks!!! Here are all my routes Topology Database Thanks!!! ACK Neighbors have Converged Neighboring and route discovery occur at the same time in EIGRP. Router A comes up on a link and sends out a hello. Router B or any router on the link receiving the hello replies with an update containing all the routes they have, with the exception of any they may have learned previously on that interface (remember split horizon, Don t tell me what I told you!! ). This update will establish a neighbor relationship between the two routers. The update packet includes all information about the routes that the neighbor is aware of, which includes the metric the neighbor is reporting for each route. Additionally this update packet will have the Init bit set, which indicates this is the initialization process. Router A replies to the neighbor with an ACK packet, acknowledging receipt of its update. Router A then installs all received routes from the update packet into its topology database, and sends an update including all of its routes to Router B Router B installs the routes in his topology database and acknowledges the update. Each route will then run the DUAL algorithm with this new information received to determine which primary and backup routes it should store in the topology table. 99
105 Show IP EIGRP Neighbor sho ip eigrp neighbor IP-EIGRP neighbors for process 1 H Address Interface Hold Uptime SRTT RTO Q Seq (sec) (ms) Cnt Num S0/ :06: S0/ :59: H: Indicates order in which the neighbors were learned. Neighbor Address: Interface: Hold: Uptime: SRTT: RTO: Q Cnt: Seq Num: IP address assigned to the directly connected interface of of the neighbor. Interface on which hello packets are received from that neighbor. Indicates the hold-time remaining for that neighbor. If the hold-time expires, the neighbor is then declared dead and the relationship is reset. Refers to the total time the neighbor relationship has been established. Smooth round trip time, which refers to the average time from when a packet is transmitted to the neighbor and an ACK is received back from that neighbor. Retransmission time out, which refers to the amount of time the router will wait to retransmit an unacknowledged packet (reliable) from a neighbor. RTO is calculated based on SRTT. Indicates the number of packets waiting in queue for that neighbor. Indicates the sequence number of the last query, reply, or update packet. Sequence numbers are used on reliable packets for tracking purposes to insure delivery. 100
106 EIGRP Reliability Packets (1) EIGRP uses the Reliable Transport Protocol (RTP). Updates, Queries, and Replies require explicit acknowledgement. Updates & Queries initially use multicast to all neighbors. - transport window size is one, follow on packets cease until response (ACK) - responding neighbors continue to get packets via multicast, no waiting - if any neighbor fails to respond, packet is retransmitted unicast - unicast packets will be retransmitted if not acknowledged (RTO reached) - the neighbor relationship will be reset when retry limit (16) is reached. RTP is tasked with ensuring that ongoing communication is maintained between neighboring routers. As such, a retransmission list is maintained for each neighbor. This list indicates packets (which require acknowledgement) to which responses have not yet been received. Initially, reliable packets are sent via multi-cast. If an acknowledgment is not received, the packet is resent via Unicast to the non-responsive neighbor. Since the transport window is set to 1, follow on reliable packets will not be sent until an acknowledgement is received for the original packet. The original packet will be resent via Unicast 15 additional times (for a total of 16). If there is no acknowledgement after the 16 th attempt, then the neighbor relationship is reset. EIGRP tracks the amount of time it takes for a neighbor to reply each reliable packet. These times are then averaged to compute the smooth round trip time (SRTT). The SRTT is then utilized to compute the retransmission timeout (RTO). The RTO is the amount of time the router will wait for an acknowledgement before resending the original reliable packet. EIGRP reliability ensures delivery of critical route information to neighboring routers. This information is required to ensure a loop-free topology at all times. 101
107 EIGRP Reliability Packets (2) Multicast Update/ No Ack A update??? no ack from B B Unicast Update/ No Ack A update??? no ack from B B Unicast Update 15 times/no Ack A update??? no ack from B B Reset Neighbor Connection A B An update is sent from router A to router B via multicast addressing; no acknowledgment (ACK) is received by A from B. The amount of time A will wait for the reply is called the retransmission timeout (RTO). The RTO is calculated separately for each neighbor. Once the RTO has expired, router A will retransmit the update to B but this time utilizing Unicast addressing. Router A will repeat this process 15 additional times for a total of 16 Unicast retry attempts. If a response is not received by the expiration of the RTO after the 16 th attempt, the neighbor relationship is reset. 102
108 Administrative Distance Defaults Connected Interface 0 Static Route 1 RIP 120 IGRP 100 EIGRP 90 OSPF 110 BGP 20 Administrative distance is a value assigned to a route, usually categorized by protocol, which indicates to the IOS the value of trust that should be given. This allows the IOS to choose a route between two protocols in the event they had both learned of a route to the same destination. This should not be confused with a metric, which is used to choose a route learned by the same protocol. Administrative distance is a rating of the trustworthiness of a routing information source, such as an individual router or a group of routers. Distance is an integer from 0 to 255. In general, the higher the value, the lower the trust rating. A distance of 255 means the routing information source cannot be trusted at all and should be ignored. Specifying distance values enables the router to discriminate between sources of routing information. The router always picks the route whose routing protocol has the lowest distance. 103
109 EIGRP Metrics A Routing Update Vector Metrics Bandwidth 256 kbs Delay ms Load 147/255 Reliability 253/255 MTU 1500 Hop Count 3 B Composite Metric Calculation [K1xBW + ((K2xBW)/(256-load)) + K3xDelay]x[K5/(reliability + K4)] Composite Metric = EIGRP calculates/utilizes two different metrics: Vector & Composite. Vector consists of six elements and is advertised to neighbor routers. Composite is calculated using the vector elements and is not shared. Composite metric is used to determine the preferred route. EIGRP utilizes two types of metrics: Vector and Composite. Vector metrics consist of six different components. 1. Bandwidth 2. Delay 3. Load 4. Reliability 5. MTU 6. Hop Count The vector metric components are utilized to compute the composite metric. Vector metric components are exchanged between EIGRP neighbors. Under normal conditions, the only two components that actually affect the composite metric are bandwidth and delay. Load, reliability, and MTU are components left over from IGRP. Since IGRP sent periodic updates at set intervals, these components had value (load and reliability are averaged over time). But since EIGRP sends triggered updates in relation to network changes, the values for load and reliability are generally not accurate. Therefore, it is recommended that they not be used in the computation of the composite metric. EIGRP has a maximum allowable hop count of 255. If a route to a destination network exceeds this, then it is deemed unreachable. Hop count is not used as a variable unless there is a tie in the composite metric between two routes or all of the other components are turned off for the composite metric computation. The composite metric is a value derived by placing the vector metric values in a mathematical formula. The composite metric value is used by the router to determine the preferred routes. The lower the value, the more preferred. Composite metric is not shared with neighbor routers.
110 Displaying Vector Metrics router2#sho ip eigrp topo /17 IP-EIGRP (AS 1): Topology entry for /17 State is Passive, Query origin flag is 1, 1 Successor(s), FD is Routing Descriptor Blocks: (Serial0/0), from , Send flag is 0x0 Composite metric is ( /256), Route is Internal Vector metric: Minimum bandwidth is 1544 Kbit Total delay is microseconds Reliability is 0/255 Load is 1/255 Minimum MTU is 1500 Hop count is 1 To display the composite and vector metrics associated with a destination network, use the show ip eigrp topology command and specify the destination network. Example above: sho ip eigrp topo /17 105
111 Composite Metric Calculation [K1xBW + ((K2xBW)/(256-load)) + K3xDelay]x[K5/(reliability + K4)] K-values are numbers used in the conversion from vector to composite metric. By changing a K-value, preference or weight can be given to a certain vector metric. Default K-values: K1=1, K2=0, K3=1, K4=0, K5=0 K1xBW + K3xDelay BW* + Delay** *BW = 10 7 / minimum BW along path in kbs X 256 **Delay = sum of all delays in the path, in tens of microseconds, X 256 Note: If K5 = 0, the formula reduces to: [K1xBW + ((K2xBW)/(256-load)) + K3xDelay] The above formula is utilized for computing the composite metric. The vector metric component values are placed in the designated areas of the formula. K-values are numbers used for the conversion of vector metric values to composite metric. By changing the K-value number, preference or weighting can be given to certain vector metrics. By default, only K1 and K3 have a value associated, 1. This in turn means the only two vector metric values that are utilized are bandwidth and delay. All of the other associated vector metric values have a K-value of 0 which has the affect of zeroing out their value in the formula. The bandwidth value used in the composite metric formula is not actually the bandwidth value associated with the interface. It is a number derived from the formula 10 7 divided by (/) the minimum interface bandwidth value along the route in kilo-bits per seconds. This value is then multiplied by 256. Delay is the sum of all the delays in tens of microseconds assigned to each interface in the path to the destination network multiplied by 256. The bandwidth and delay metrics are applied on an outgoing basis. 106
112 displays K value settings Show IP Protocol nc3#show ip protocol Routing Protocol is "eigrp 1" Outgoing update filter list for all interfaces is Incoming update filter list for all interfaces is Default networks flagged in outgoing updates Default networks accepted from incoming updates EIGRP metric weight K1=1, K2=0, K3=1, K4=0, K5=0 EIGRP maximum hop count 100 EIGRP maximum metric variance 1 Redistributing: eigrp 1 Automatic network summarization is in effect Routing for Networks: Routing Information Sources: Gateway Distance Last Update :04: :04:35 Distance: internal 90 external 170 The show ip protocol command can be utilized to display the K value settings within an EIGRP process. Default K value settings are K1=1, K2=0, K3=1, K4=0, K5=0. For two EIGRP routers to become neighbors, the K value settings of each must be the same. As a general rule, the K values for EIGRP should be left at the default value. Enabling the K values associated with reliability and load should never be done. Using these values can cause inconsistencies in the calculation of the composite metric. Reliability and load values are based on calculations averaged over a period of time when the link is in an operational status. These work well with IGRP due to the fact that IGRP sends out periodic updates at set intervals (90 seconds). EIGRP on the other hand sends out triggered updates which are based a network changes. Once the network changes, the value associated with reliability and/or load may not accurately reflect how the link has been operating over a set period of time. 107
113 Composite Metric Calculation 10 [ ( 7 Minimum Bandwidth ) + Sum of all Delays] x 256 BW 1544 kbps Delay BW 115 kbps Delay BW kbps Delay 1000 T kbs [ ( 115 ) ] x 256 = Note: Bandwidth of 115 kbps is expressed in formula as 115. Delay is in tens of microseconds. Show interface shows microseconds and must be divided by 10 for use in the formula. When placing the values in the formula, insure the bandwidth is expressed in kbs; 115kbps would be entered as 115. The delay value shown utilizing the sho interface command is in microseconds. This must be converted to tens of microseconds by dividing it by 10 before it is used to calculate the metric. In the above example, 115 kbs is the lowest bandwidth in the path so it is utilized for the bandwidth value in the formula. The value of 115 is divided into The delay values listed in the path are divided by ten and added together for a composite value. These two values are then added together and multiplied by 256. This value is the composite metric. 108
114 Interface Default Values Interface Type Bandwidth (kbps) Delay (Microseconds) Ethernet Fast Ethernet Tunnel Serial Interface Low Speed Serial Int Below T-1 ISDN BRI ISDN PRI Dialer interface Channelized T1 or E1 Async interface Loopback N * 64 TTY line speed The default values of bandwidth and delay are usually correct for LAN interfaces but tend to be incorrect for the WAN interfaces. Bandwidth and sometimes delay must be specified for each WAN interface using the bandwidth or delay commands. The bandwidth and delay specified on an interface affect only the metric calculation and have no impact on the actual speed or time in the transfer of packets. 109
115 DUAL Algorithm Diffusing Update Algorithm (DUAL). Tracks all routes advertised by all neighbors. Selects loop-free path using a successor and feasible successors. If successor is lost: Use a feasible successor If no feasible successor: Query all neighbors and recompute new successor Once new Successor is selected, update all neighbors of new topology. All neighbors now must decide if new topology affects their Best Path election. The DUAL algorithm embodies the decision process for all route computations. It tracks all routes advertised by all neighbors. The metric information, known as a distance, is used by DUAL to select efficient loop-free paths. The lowest-cost route is calculated by adding the cost between the next-hop router and the destination (reported distance) to the cost between the local router and the nexthop router (the total is referred to as the feasible distance). A successor is a neighboring router used for packet forwarding that has a least-cost path to a destination that is guaranteed not to be part of a routing loop. Multiple successors can exist, if they have the same feasible distance and use different next-hop routers. All successors are added to the routing table. The next-hop router(s) for the backup path is referred to as the FS feasible successor. In order to qualify as a feasible successor, a next-hop router must have a RD reported distance less than the FD feasible distance of the current successor route. If the successor s route is no longer valid and a suitable feasible successor exists, this feasible successor replaces an invalid successor in the routing table without a recompilation. More than one feasible successor can be kept at one time. When there are no feasible successors but there are neighbors advertising the destination, a recompilation must occur. This is the process where a new successor is determined. The amount of time it takes to recalculate the route affects the convergence time. 110
116 DUAL - EIGRP Definitions REPORTED DISTANCE SUCCESSOR FEASIBLE DISTANCE FEASIBLE SUCCESSOR The metric to reach a destination network as advertised or reported by a router to each of its neighbors. A neighbor router used for packet forwarding to a destination network that has the lowest metric path, and is guaranteed loop-free. The metric to a destination network through the successor. The FD is a combination of the successor s RD and the metric of the local routers interface used to reach the successor. A neighbor router used as a back-up to the successor and is guaranteed loop-free. In order to become an FS, the router s RD must be less than the FD of the Successor. Requires no recompilation of topology table upon failure of the successor. The reported or advertised distance is the metric advertised by each router to a destination network. The router that is determining the best path (performing the DUAL operation) does not add its own interface metrics to compute the reported distance. It is simply the metric for a destination advertised by the neighbor. The feasible distance is the lowest metric route from the router performing the DUAL operation to the destination network. The router uses the reported distance and the metric on the interface it was received to calculate the feasible distance. A successor is the next-hop router (neighbor) for traffic from the current router to a destination. A successor is chosen based on it having the lowest feasible distance to a destination. There can be multiple successors. In this case, the multiple routes would have the same feasible distance and then load balancing would take place. A neighbor router that is not selected as the successor can qualify as a feasible successor if it meets the feasibility condition. The condition is met if a neighbor s reported distance to a destination is lower than the successor s feasible distance to that same destination. A feasible successor is simply a backup route within the topology database. There can be multiple feasible successors. When there are feasible successors present and the successor s route is lost, the process for determining a replacement path is very simple: the feasible successor is immediately chosen without a DUAL process taking place. The concept of feasible condition and feasible successors are central to loop avoidance. 111
117 Successor & Feasible Successor (1) RD= 5 FD= 10 S ROUTER A RD= 10 FD= 15 5 A RD= 5 FD= 10 5 RD= 5 FD= 5 FS ROUTER B RD= 10 FD= 20 Z 10 B 5 X 5 ROUTER C 5 RD= 5 FD= Network RD= /28 FD= 25 C All RD & FD values are based on network being the destination. The successor and feasible successor selections are based on router Z s network perspective. Router Z has determined that the lowest feasible distance (FD) to network /28 is 15. Based on this information, router A is elected as the successor. Candidates for a feasible successor are routers B and C. Router C is not eligible as its reported distance is higher than the feasible distance of the successor. Router B however has a reported distance of 10 which is lower than the feasible distance of 15, so it is chosen as a feasible successor. 112
118 Successor & Feasible Successor (2) RD= 5 FD= 10 ROUTER A RD= 10 FD= 15 5 A RD= 5 FD= 10 5 RD= 5 FD= 5 S ROUTER B RD= 10 FD= 20 Z 10 B 5 X 5 ROUTER C RD= 20 FD= 25 5 RD= 5 FD= 20 C 15 Network /28 Path from router Z to router A (successor) goes down. Router B automatically becomes the successor no DUAL algorithm performed. Router Z then goes through process to determine if there is a feasible successor available. The path between routers Z and A fails. Router B immediately becomes the successor. Z then begins the process to determine if there is a feasible successor available. Since router C s RD is equal to router B s FD, then C is not eligible to become a FS. 113
119 Query Process (1) RD= 5 FD= 10 S ROUTER A RD= 10 FD= 15 5 A RD= 5 FD= 15 5 RD= 5 FD= 5 ROUTER B RD= 15 FD= 25 Z 10 query B 10 X 5 ROUTER C RD= 20 FD= RD= 5 FD= 20 C 15 Network /28 Router A is the successor for router Z for network ; no feasible successor. The link from router Z to A goes down. Router Z sends queries to neighbors asking for route info for Router A is the successor for router Z to forward packets to network /28. There is no FS because no other router meets the feasibility condition. The path between routers Z and A fails. Router Z must send queries to each of its remaining neighbors requesting route information for network /
120 Query Process (2) RD= 5 FD= 10 ROUTER A RD= 10 FD= 15 5 A RD= 5 FD= 15 5 RD= 5 FD= 5 S ROUTER B RD= 15 FD= 25 Z 10 response to query B 10 X 5 FS ROUTER C RD= 20 FD= RD= 5 FD= 20 C 15 Network /28 Routers B & C respond to the query. Router B is selected as the successor. Router C is selected as the feasible successor. Routers B and C respond to router Z with route information to the requested network. Based on the RD sent by each, router B is selected as the successor based on it having the lowest FD. Router C is then selected as an FS because its RD is lower than the successor s FD. 115
121 Configuring EIGRP router(config)#router eigrp autonomous system number enables EIGRP and defines the autonomous system number. router(config-router)#network network-number [wildcard-mask] selects directly connected networks/interfaces that will participate in the EIGRP process. the network number can either be classful or can be used in conjunction with a wildcard mask to specify individual networks/interfaces. Use the router eigrp as number command to enable eigrp routing and define an autonomous system number. This does not actually have to be an assigned or valid AS number even though it could be. Each router within the EIGRP topology must use the same number though in order to from neighbor relationships. The network statement defines the interfaces or directly connected networks over which EIGRP will operate. Once a network statement is configured, EIGRP compares the network assigned to each interface to the range defined in the network statement. If the network assigned to an interface is within the range in the network statement, EIGRP will operate through that interface and will advertise the network assigned to the interface. If is not within the range, EIGRP will not operate on that interface. EIGRP network statements can be classful or can be used in conjunction with a wild-card mask. The wild card mask allows administrator to specify individual interfaces for EIGRP operation or in some cases to keep EIGRP from operating on a specific interface. 116
122 Passive Interface Router(config-router)#passive-interface interface Prevents routing protocol packets from being generated on the interface. If there is no EIGRP speaking device connected to the interface, there is no need to transmit EIGRP information from the interface. Still allows the announcement of the network to the rest of the EIGRP community. When a network statement is installed under EIGRP two things take place. EIGRP announces that it has the specified network to all neighbors, and EIGRP begins sending EIGRP packets, such as hello s and routing updates. There are cases where you need to announce the network but the network itself consists of non-eigrp speaking devices, such as a LAN with purely host computers. In this case there is no need to send EIGRP packets out this interface as none of the host computers need or understand EIGRP information. The use of the Passive Interface command allows the network to be announced but stops the transmitting of EIGRP packets out the interface. 117
123 EIGRP Network Diagram Loopback Address e1/ /32 e1/ / / Loopback Addresses Loopback Addresses /30 s0/0 s1/ / / /32 s0/1 s1/ f0/0 f0/ /28 s0/0 s0/ /28 s0/ s0/ / / / / / s0/1 e1/0 e1/ s0/ /29 Loopback Address /32 Loopback Address /32 s0/ s0/ /28 e1/0 e1/ / / /30 f0/0.178 s0/1 s0/ /28 3 Loopback Address / s0/1 s0/0.246 f0/ /28 Loopback Address /32 Install the network shown above. 118
124 Show IP Route router7#sho ip ro Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2 i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2 ia - IS-IS inter area, * - candidate default, U - per-user static route o - ODR, P - periodic downloaded static route Gateway of last resort is not set C D D D D D D D D D D D D /16 is variably subnetted, 26 subnets, 4 masks /32 is directly connected, Loopback /30 [90/ ] via , 00:03:56, Serial0/ /30 [90/ ] via , 00:03:56, Serial0/ /29 [90/ ] via , 00:03:56, Serial0/ /28 [90/ ] via , 00:03:56, Serial0/ /28 [90/ ] via , 00:03:56, Serial0/ /28 [90/ ] via , 00:03:56, Serial0/ /30 [90/ ] via , 00:03:56, Serial0/ /30 [90/ ] via , 00:03:56, Serial0/ /29 [90/ ] via , 00:03:56, Serial0/1 [90/ ] via , 00:03:56, Serial0/ /28 [90/ ] via , 00:03:57, Serial0/1 [90/ ] via , 00:03:57, Serial0/ /28 [90/ ] via , 00:03:57, Serial0/ /28 [90/ ] via , 00:03:57, Serial0/0.248 network.208 network.184 network NOTE: the show command displays on pages are not based on the network just installed on previous page. They are for use to explain the different information provided by each command. The D in the left hand column indicates the route was learned by EIGRP and originated internal to this autonomous system. An EX would indicate that the route was installed by EIGRP but it originated outside the AS and was redistributed into the EIGRP protocol. This is a flag to allow EIGRP to differentiate between internally and externally learned routes. Internal EIGRP routes have a distance of 90 and external have a distance of 170 Whenever two equal costs paths are learned by EIGRP, both will be installed in the routing table and automatic load balancing will take place across the two. Take note of the of the network entries above in red:.248,.208, &.184. On the next slides we will examine these in the topology database. 119
125 Show IP EIGRP Topology (1) router7#sho ip eigrp topo IP-EIGRP Topology Table for AS(1)/ID( ) Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply, r - reply Status, s - sia Status P /29, 1 successors, FD is via ( / ), Serial0/3 via ( / ), Serial0/2 only lists successors & FS possible to have multiple successors /29 1 successors FD is via ( / ) Serial0/3 via ( / ) Serial0/2 destination network number of successors for this network the feasible distance (metric) of successor address of successor (next hop) feasible distance/reported distance of this entry exit interface to reach this next hop address of feasible successor feasible distance/reported distance of this entry exit interface to reach this next hop The show ip eigrp topology command lists all EIGRP known destination networks and the successors and feasible successors for each. It is possible for other next hop routers for listed destination networks to be known by EIGRP but they are not shown when using this command. The table above provides a brief explanation for each of the entries corresponding to destination network entry. The entry lists the number of successors, the feasible distance of the successor(s), and then followed by the next hop addresses of the successor(s) and feasible successor(s) with the FD and RD for each. It is possible to have multiple successors and feasible successors. At a minimum there will always be at least a successor for an entry. It is possible to not have any feasible successors. There are several code listed at the top of the display. These codes are applied to each entry depending on its status: Passive Active This network is available and installation can occur in the routing table. Passive is the correct state for a stable network. Network is currently unavailable; there are outstanding queries for this network. 120
126 Update Query Reply SIA Network is being updated or waiting for an acknowledgment for an update sent. There is an outstanding query for this network (other than Active state) or waiting for acknowledgment on a reply sent to a query. Router is generating a reply pertaining to this network or waiting for an acknowledgement on a previously sent reply Stuck in Active, a query was generated for this network and a reply was not received within a three minute period. 121
127 Show IP EIGRP Topology (2) router7#sho ip eigrp topo IP-EIGRP Topology Table for AS(1)/ID( ) Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply, r - reply Status, s - sia Status P /29, 1 successors, FD is via ( / ), Serial0/3 via ( / ), Serial0/2 P /28, 1 successors, FD is via ( / ), Serial0/3 via ( / ), Serial0/2 P /28, 1 successors, FD is via ( /28160), Serial0/2 P /28, 1 successors, FD is via ( /28160), Serial0/3 P /30, 1 successors, FD is via ( / ), Serial0/0 P /30, 1 successors, FD is via ( / ), Serial0/1 P /29, 2 successors, FD is via ( / ), Serial0/0 via ( / ), Serial0/1 P /28, 2 successors, FD is via ( / ), Serial0/0 via ( / ), Serial0/1.248 network.208 network.184 network The sho ip eigrp topology command displays only successors and feasible successors. It is possible to have other network information within the topology database that has not been designated a successor or feasible successor. Now examine the networks noted on the previous page in the routing table:.248,.208, & : Listed as having one successor but has two next hop addresses through which it can be reached (via). The first,.110, is the successor and the second,.106, is the feasible successor. When utilizing this show command and it states 1 successor for a network entry, the first via entry is the successor and any follow on entries are feasible successors. This can be verified by comparing the feasible distance of the.110 entry ( ) with the reported distance of the.106 entry ( ). Since the RD of.106 is lower than the FD of the successor, then.106 is a feasible successor..208: Listed as having one successor. It only lists one next hop address for this destination network. This is the successor and there are no feasible successors. If there is route failure through this successor, there is no backup route and the.208 net will be removed from the routing table. 122
128 .184: Listed as having two successor followed by two next hop address entries. These are both successors with each having the same FD. There are no feasible successors. Both of these next hop addresses will be entered in the routing table for this destination network and load balancing will take place between the two. 123
129 Show IP EIGRP Topology All-Links router7#sho ip eigrp topo all IP-EIGRP Topology Table for AS(1)/ID( ) Codes: P - Passive, A - Active, U - Update, Q - Query, R - Reply, r - reply Status, s - sia Status P /29, 1 successors, FD is , serno 15 via ( / ), Serial0/3 via ( / ), Serial0/2 P /28, 1 successors, FD is , serno 14 via ( / ), Serial0/3 via ( / ), Serial0/2 P /28, 1 successors, FD is , serno 26 via ( /28160), Serial0/2 via ( / ), Serial0/3 P /28, 1 successors, FD is , serno 20 via ( /28160), Serial0/3 P /30, 1 successors, FD is , serno 30 via ( / ), Serial0/0 via ( / ), Serial0/1 P /30, 1 successors, FD is , serno 8 via ( / ), Serial0/1 via ( / ), Serial0/0 P /29, 2 successors, FD is , serno 36 via ( / ), Serial0/0 via ( / ), Serial0/1.248 network.208 network.184 network The show ip eigrp topology all-links command displays all network routes known by EIGRP, regardless if it is a successor, feasible successor, or a route advertised by a neighbor but did not meet the feasibility condition. To determine if the route is a feasible successor the reported distance must be less than the feasible distance. For network entries.248 and.184 the display above is the same as display for the show ip eigrp topology command. The.248 network still has only one successor and a feasible successor listed. The.184 network only has two successors listed. But for network entry.208 it now shows two next hop addresses. The entry indicates it has one successor, which is the.106 next hop address. It then lists a next hop of.110. By comparing the RD of.110 ( ) with the FD of.106 ( ), it can be seen that.110 does not meet the feasibility condition and therefore cannot be a feasible successor. Even though the router knows about the route to network.208 through the next hop address of.110, it will not use it as a backup upon failure of the successor,.106. It will go though the process of querying its neighbors for route information to this network to determine a new path. 124
130 Route Summarization EIGRP uses two methods of route summarization. Automatic (auto-summary) Manual (no auto-summary) Automatic gives EIGRP same classful behavior as RIP or IGRP. At major network boundaries the subnets will be summarized back to the Classful network mask when announced across the boundary. Manual enables support for discontinuous networks and allows summarization on any interface regardless of network. EIGRP utilizes two methods of route summarization: automatic and manual. Automatic summarization is the same type that is utilized by classful routing protocols. When routing updates are advertised across a network that is a different classful network than the update itself, the update is automatically summarized to the classful network. In today s classless network topologies, this is a feature that is seldom used and can cause serious network routing problems. It is generally turned off by utilizing the no auto-summary command in the EIGRP configuration. Manual route summarization is designed and configured by a network administrator. In the EIGRP routing protocol, manual summarization can be installed at any point in the network, to any EIGRP router. Unlike OSPF, EIGRP does not employ a hierarchical routing topology by grouping routers into areas and then designated border routers (summarization can only take place on these border routers). EIGRP allows the network administrator to employ summarization as required without drastic network redesign. This is a very important feature in networks that physically change on a regular basis such as those in tactical military communications. 125
131 Automatic Route Summarization / /16 Router A routing table C C C D D A / /8 is variably subnetted, 3 subnets, 2 masks /16 is directly connected, FastEthernet0/ /16 is directly connected, FastEthernet0/ /30 is directly connected, Serial0/ /8 [90/ ] via , 00:05:35, Serial0/ /8 [90/ ] via , 00:03:19, Serial0/1 B / C /16 Router C routing table D /8 [90/ ] via , 00:00:14, Serial0/ /8 is variably subnetted, 2 subnets, 2 masks D /8 is a summary, 00:00:14, Null0 C /30 is directly connected, Serial0/ /8 is variably subnetted, 2 subnets, 2 masks D /8 is a summary, 00:00:14, Null0 C /16 is directly connected, FastEthernet0/0 Router B routing table /8 is variably subnetted, 4 subnets, 3 masks D /16 [90/540160] via , 00:04:54, Serial0/1 D /8 is a summary, 00:04:54, Null0 D /16 [90/540160] via , 00:04:54, Serial0/1 C /30 is directly connected, Serial0/ /8 is variably subnetted, 2 subnets, 2 masks D /8 is a summary, 00:04:55, Null0 C /30 is directly connected, Serial0/0 D /8 [90/540160] via , 00:02:38, Serial0/0 With automatic route summarization enabled (default) in EIGRP, when an update is advertised across a subnet that is within a different classful network from the update, the update is automatically summarized to the classful network. Router A installs a network statement for All directly connected subnets on router A that fall within the /8 range will be announced individually to router B as he is also a member of the /8 network. Router B will install them individually and announce them to C as a summary route because C is not a member of the /8 network. B will install the summary route locally and point it to null 0. Pointing the /8 to null 0 may lead you to believe B is unable to route traffic to the /8 networks. Realize in the routing table more specific routes win, and B will have individual statements for each /8 sub-network, because he is a member. Router C will advertise the subnet /16 to router B, but because they are interconnected with a subnet from the network, C will auto summarize the advertisement to the classful network From C s perspective of the topology, it now believes that the whole network resides through router B. From A and B s perspective they now believe that the network resides through C. In a large routed network this could lead to packets being routed to destinations where subnets don t actually exist and the packets being discarded. 126
132 Manual Route Summarization A B Routing Table for A D D D D D D D D Summarization per interface. As well as announcing a summary route to the neighbor, an identical copy pointing to null 0 is installed locally which prevents routing loops. Summarization must be carefully planned and it begins before the router is even deployed with the allocation of IP addresses in contiguous blocks within the network topology. Contrary to the link state routing protocols such as OSPF or IS-IS, EIGRP enables the network designer to create a deep summarization hierarchy that reflects the designed network hierarchy. Therefore, you are not limited to a starshaped network consisting of a backbone plus other regions and required to summarize only on the region borders as you are in OSPF. You can configure per-interface IP address summarization with as many summarization ranges as you wish, as long as the ranges don t overlap. For each summary range configured over any interface belonging to an EIGRP process, the EIGRP process creates a summary route for the summarization range as soon as at least one more specific route falling within the summary range appears in the EIGRP topology table. This summary route points to null zero and has the minimum metric of all the more specific routes covered by the summary route. It is also inserted into the main IP routing table with an administrative distance of 5. This results in the suppression of more specific routes when updates are sent over the interface where the summarization range is configured. Another important factor to remember when summarizing is that there only has to be one subnet within the summarized range for the summarized address to be advertised. It is very possible to advertise subnets within this summarized range, which are not reachable by the router. 127
133 Creating Summary Routes Router7> en Router7# config t Router7 (config)# int s0/0 Router7 (config-if)# ip summary-address eigrp <as-number> <network> <mask> This command will cause all route announcements that fall within the <network> <mask> specified to be summarized before being sent out interface s0/0. Summarization Lab All routers do sho ip route and count the number of routing entries. All routers apply summarization as follows: router 1 s0/0 can use /26 router 2 s0/0 and s0/1 can use /27 router 3 s0/0 can use /26 router 4 s0/0 can use /26 router 5 s0/0 and s0/1 can use /27 router 6 s0/1 can use /26 router 7 all serials can use /27 and /28 All routers now do sho ip route and count number of routing entries. 128
134 EIGRP Route Summarization Problem.129 f0/ / s0/1.182 s0/1 e1/ /28 s0/0 s0/ s0/ e0/ /28 Routing table /16 is variably subnetted, 17 subnets, 5 masks C /30 is directly connected, Serial0/1 D /28 is a summary, 00:01:10, Null0 D /32 [90/ ] via , 00:01:10, Serial0/3 D /32 [90/ ] via , 00:01:10, Serial0/3 D /32 [90/ ] via , 00:01:10, Serial0/2 D /32 [90/ ] via , 00:01:10, Serial0/1 D /32 [90/ ] via , 00:01:10, Serial0/1 D /32 [90/ ] via , 00:01:10, Serial0/0 D /26 [90/ ] via , 00:01:10, Serial0/3 D /26 [90/ ] via , 00:01:10, Serial0/ s0/0.178 s0/1 3 s0/0.102 Router7#ping Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds:!!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 24/24/28 ms Router7#trace Tracing the route to msec 4 msec 8 msec msec 8 msec 8 msec msec * 8 msec The above diagram shows the routing table from router 7. Router 7 has route /26 via interface serial 0/1 installed in its table. S0/1 is directly connected to router 3. Router 1 and router 3 are both advertising the summary router /26 to router 7. But because router 3 is advertising a lower metric than router 1, only the advertisement from 3 is installed in the table. This does not seem to be a problem though because router three has connectivity to all of the summarized subnets. This is proven by conducting a ping and trace route to the address , which resides on a subnet directly connected to router 1. By viewing the results of the trace, it can be seen that the path to reach.129 travels from 7, through 3, then 2 and on to
135 EIGRP Route Summarization Problem f0/ / s0/1.182 s0/1 e1/ /28.97 s0/0 s0/ s0/0 7 e0/ /28 Routing table /16 is variably subnetted, 17 subnets, 5 masks C /30 is directly connected, Serial0/1 D /28 is a summary, 00:01:10, Null0 D /32 [90/ ] via , 00:01:10, Serial0/3 D /32 [90/ ] via , 00:01:10, Serial0/3 D /32 [90/ ] via , 00:01:10, Serial0/2 D /32 [90/ ] via , 00:01:10, Serial0/1 D /32 [90/ ] via , 00:01:10, Serial0/1 D /32 [90/ ] via , 00:01:10, Serial0/0 D /26 [90/ ] via , 00:01:10, Serial0/3 D /26 [90/ ] via , 00:01:10, Serial0/ s0/0.178 s0/1 3 s0/0.102 Router7#ping Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds: U.U.U Success rate is 0 percent (0/5) Router7#trace Tracing the route to msec 4 msec 4 msec !H *!H Problems can occur though when there are network disruptions within the summarized area. In the above example, the network connection between router 1 and 2 fails. But since there are still subnets being advertised by router 3 via interface s0/0 that fall within the summarized network configured on interface s0/0, router 3 continues to advertise the summarized network to router 7. It continues to do this even though it now cannot reach all the subnets that were originally covered by this summarization. Using the ping and trace tools again, the address is unreachable even though there is a network path to this subnet from router 7. EIGRP does not offer this path to the routing table as a candidate because the route through 3 still has a lower metric. As long as there is a single subnet that falls within a summarized range being advertised via an interface that has this summarization configured, the router advertises the summarized network. This can lead to certain subnets within the summarized range not being reachable in certain situations even though there is an operational network path to this subnet. Careful planning must be used when designing and implementing route summarization in an EIGRP topology. The benefits that route summarization provide can sometimes be outweighed by network reach ability issues. 130
136 Query Response Process (1)?????? query A B No entry in topology database for route in question, reply with unreachable. If querying router is the successor for route in question and feasible successor exists, the queried router replies with this information. If querying router is the successor for route in question and feasible successor does not exist, the queried router queries its neighbors. If the query was received from a neighbor that is not the successor for this destination, then the queried router replies with its successor information. When the route to a destination network through a successor fails and there is no feasible successor available, the EIGRP router issues a query to all of its neighbors asking for route information for the network in question. Depending on the status of the querying router and the neighbor, which is queried in relation to the network in question, there are four possible actions that can be taken (listed above). Each is covered in the next four slides. 131
137 Query Response Process (2) network x query for network X A unreachable B topo db no entry for network x No entry in topology database for route in question, reply with unreachable. In the example above, router A loses connectivity to network X through its successor. There is no feasible successor available. It sends a query to router B asking for route information to network X. Router B checks its topology database and finds it has no entry for network X. It then sends a reply to router A stating that network X is unreachable. Network unreachable is an acceptable response to a query. 132
138 Query Response Process (3) network x query for network X A reply route to x B topo db x succ. A x FS C C If querying router is the successor for route in question and feasible successor exists, the queried router replies with this information. In the example above, router A loses connectivity to network X through its successor. There is no feasible successor available. It sends a query to router B asking for route information to network X. Router B checks its topology database and finds that router A is the successor and that router C is the feasible successor. Router B then sends a reply to router A stating that its successor to network X is router C. 133
139 Query Response Process (4) network x query for network X A query for network X B topo db x succ. A no FS x C If querying router is the successor for route in question and feasible successor does not exist, the queried router queries its neighbors. In the example above, router A loses connectivity to network X through its successor. There is no feasible successor available. It sends a query to router B asking for route information to network X. Router B checks its topology database and finds that router A is the successor and there is no feasible successor. Router B then queries its neighbors for route information to network X. 134
140 Query Response Process (5) network x query for network X A reply succ. to x is C B topo db x succ. C C If the query was received from a neighbor that is not the successor for this destination, then the queried router replies with its successor information. In the example above, router A loses connectivity to network X through its successor. There is no feasible successor available. It sends a query to router B asking for route information to network X. Router B checks its topology database and finds that router C is the successor for network X. Router B then sends a reply to router A stating that its successor to network X is router C. 135
141 Stuck in Active (SIA) No answer locally, so this neighbor must query his neighbors and so on. Large Delay query C query A query B query D query 136 SIA occurs when queries are not answered in a timely manner. Can cause sever network disruptions. When the successor for a destination network is lost and there is no feasible successor, an EIGRP router sends a query to all of its neighbors requesting route information for the network in question. It can take so long time for a query to be answered that the router that issued the query gives up and clears its connection to the router that is not answering, effectively restarting the neighbor session. This is known as a stuck in active (SIA) state. SIA routes occur when it takes too long for a query to reach the end of the network and for a reply to travel back. In the example above, the neighbor relationship between router A and B could be reset simply because neighbor B could not respond to A until it receives a response from C. This is undesirable as traffic between A and D could flow with no problems. An SIA problem usually involves only one route. Routers A and B could be routing for hundreds of other networks with no problems. However, when the neighbor connection is reset, routing for all networks via routers A and B is temporarily disrupted. If SIA problems are occurring routinely within an EIGRP topology, it appears the network is congested. SIA problems are routinely misdiagnosed as other problems like insufficient bandwidth or router latency. The wait time for the answer to a query is three minutes. If any neighbor has not replied to a query within this time, the neighbor connection is reset. It is important to remember that for the query process to be completed, a router must receive replies from all queried neighbors. Example, if a router queries four neighbors and immediately receives replies from three, the router will continue to wait on the fourth neighbor to reply prior to making a routing decision on the queried network. It will wait the three-minute period at which time it will reset the neighbor connection.
142 Limiting the Query Range (1) 1. Route Summarization - keeps individual subnets from being advertised. - if there is not an exact match in topo database, query is answered immediately as network unreachable. - relies on neighbor router to perform summarization. 2. Route Filtering - can provide same benefits as route summarization. - does not rely on neighbor router to implement. 3. EIGRP Stub Option - routers designated as stubs are not sent queries by neighboring routers. Limiting the query range of an EIGRP topology is an effective way to control SIA route problems. Three techniques which can be implemented to limit the range are route summarization, route filtering, and EIGRP stub option. In all actuality, though, these techniques do not limit queries once they are sent by a router but limit the requirements for the router to send a query in the first place. These techniques limit the overall knowledge of network topology by EIGRP. There is a fine line between letting EIGRP know too much about the network topology so as to cause SIA problems and not know enough to effectively route packets. 137
143 Limiting the Query Range (2) summarization C Z A B D summarization Network failure on router Z is localized by the use of summarization and is not sent to routers A, B, C, & D; query process not started. Route summarization segments the EIGRP topology by combining multiple subnets from a region within the topology into larger consolidated networks. This basically hides various subnets from routers and tells them about a very large network. Any packet within this large range is simply routed to the summarizing router and it is then distributed to the various subnets by it. The way that this limits the query range is that when a single subnet within the summarized network fails, it is hidden from the routers receiving the summarized information. Basically, they do not know about this failure and do not have to go through the query process to find a new route to it. In using route summarization to limit the query range, routers must rely on their neighboring routers to implement it. In other words, the routers performing summarization do not see the affects or get the benefits from it. In situations where an administrator is not in charge of all the routers within the EIGRP topology, he must rely on another entity to perform the summarization. Since this summarization may not provide any direct benefits to them, they may or may not be willing to comply. 138
144 Limiting the Query Range (3) route filtering C Z A B D route filtering Network failure on router Z is localized by the use of route filtering and is not received by routers C & D nor forwarded to routers A & B. Query process not started. Route filtering is another technique that can be used to limit the query range. If implemented correctly, it can basically provide the same results as summarization. But unlike summarization, the routers performing the filtering can see the results immediately. Through the use of distribution lists and route maps, a network administrator can control what routing information is received and propagated by a router. Route filtering can be used to hide individual subnets from routers but other techniques must then be implemented to describe to them a consolidation of these subnets. Techniques such as static routes and default routing can be used for this function. 139
145 Limiting the Query Range (4) stub stub F query C Z A B query stub E D Network failure on router Z occurs. Router B only queries neighbors C & D. No queries are sent to routers A, E, or F because they are designated as stubs. The EIGRP stub option when configured on a router allows that router to send a flag to neighbor routers essentially telling them not to query it. This technique works very well in hub spoke topographies or where any router simply has a single network connection to another router. If a router only has a single connection to one EIGRP neighbor, it must route through that neighbor to reach any other subnets within the topology. Why then would the neighbor router query this single threaded router for information if it has to rely on the querying router for all of its information? Defining a router as a stub keeps neighboring routers from querying it. 140
146 EIGRP Stub Command router(config)#router eigrp autonomous system number router(config-router)#eigrp stub Extensions to command: [receive only connected static summary] receive only prevents router from sharing any if its routes with eigrp neighbors connected permits the router to send connected routes via eigrp static permits the router to send static routes via eigrp summary permits the router to send summary eigrp routes Use the eigrp stub command to define a router as a stub within the EIGRP topology. This command is configured to the EIGRP routing protocol. There are four extensions to the command: receive only, connected, static, summary. Receive only restricts the router from sharing any of its routes with any other router in the network. If configured, the other three options cannot be used. Connected permits the sharing of connected routes with EIGRP neighbors. If the connected routes are not covered by a network statement, it is necessary to redistribute the routes into EIGRP. Connected is enabled by default. Static permits the router to share static routes with EIGRP neighbors. These routes must be redistributed into the EIGRP protocol. Summary permits the router to share EIGRP summary routes to neighboring routers. This option is enabled by default. 141
147 EIGRP Review Questions 142
148 1. EIGRP is a protocol. a. link state b. distance vector c. enhanced d. hybrid 2. EIGRP is Cisco proprietary? a. true b. false 3. What are triggered updates? a. updates sent at set times regardless of network changes b. updates that are sent based on criteria within a route map c. updates sent in response to network changes d. there is no such thing as a triggered update 4. The hello protocol is used for: a. neighbor discovery only b. neighbor discovery and maintenance c. neighbor AS verification d. routing table maintenance 5. What are the 5 types of EIGRP packets? a. hello, update, query, ACK, resend b. hello, Unicast, query, ACK, reply c. hello, update, quest, ACK, reply d. hello, update, query, ACK, reply 6. These types of EIGRP packets require acknowledgment? a. update, query, reply b. ACK, hello, query c. hello, update, multicast d. multicast, Unicast, broadcast 7. What is the next step if a neighbor doesn t respond to a packet that requires acknowledgment? a. resend the packet as multicast b. break the neighbor connection c. resend the packet Unicast d. resend the packet broadcast 8. How many times will a router resend a packet Unicast prior to breaking the neighbor connection? a. 2 b. 14 c. 15 d When hello packets are used for link integrity purposes, they are referred to as. 143
149 a. ACK b. reply c. keepalives e. query 10. The destination address for hello packets is: a. neighbor s address b c d What are the hello & hold times for EIGRP on a LAN segment? a. 10/40 seconds b. 5/15 seconds c. 10/20 seconds d. 15/45 seconds 12. For two EIGRP routers to become neighbors they must agree on. a. K-values and AS number b. hello interval and area ID c. router ID and dead interval d. delay and bandwidth 13. In the show ip eigrp nei command, SRTT is what? a. refers to the average time it takes for a neighbor to reply b. the amount of time a router will wait for a reply c. amount of time it takes for a host to reply to an echo request d. neighbor router ID 14. Composite metrics are advertised to neighbor routers. a. true b. false 15. Vector metrics consist of components. a. 5 b. 4 c. 3 d A route has a minimum BW of 256k & a total delay of What is the composite metric? a b c d The successor is. a. neighbor with the highest reported distance 144
150 b. neighbor with highest router ID c. neighbor selected for packet forwarding to a destination network d. neighbor that passed the feasibility condition 18. To become a feasible successor, a router must a. have a reported distance less than the successor s feasible distance b. have a feasible distance lower than the successors reported distance c. have an SRTT less than the successors RTO d. have a metric less than the successors to the destination network 19. What is the reason for the feasibility condition? a. minimize the topology database b. minimize router latency c. insure loop free routing d. both a & b 20. DUAL stands for. a. 2 b. diffusing update algorithm c. database UNIX algorithm d. diffusing underlying algorithm 21. If the path to the successor fails, the router will use any matching route in the topology database. a. yes, this speeds up convergence b. yes, all routes are stored in the database c. no, only feasible successors d. no, a query must be sent first 22. EIGRP can be configured as a classful or classless protocol. a. true b. false 23. The show ip eigrp topology command shows all entries in the database. a. true b. false 24. Changing the bandwidth at any point in a route will change the metric. a. true b. false 25. Manipulating the metric can be used as a tool to build feasible successors into a topology. a. true b. false 26. The command to change the delay on an interface is. a. router(config)#delay xxxxx b. router(config-router)#delay xxxxx c. router(config-if)#delay xxxxx 145
151 146 d. router(config-line)#delay xxxxx 27. In EIGRP, load balancing occurs automatically on unequal paths. a. true b. false 28. The variance command does which of the following? a. causes all known routes to be candidates for load balancing b. multiples the feasible distance of the successor by the value used in the command c. varies the metric of the feasible successor d. causes EIGRP to alternate the interface route updates are sent 29. What are the two type of route summarization used in EIGRP? a. internal and external b. auto and manual c. composite and vector d. single and multiple 30. Route summarization is configured at what location on the router? a. within the EIGRP routing protocol b. from the global configuration mode c. on the interface d. none of the above 31. When summarizing, it is possible to advertise subnets that the router has no knowledge about. a. true b. false 32. What is SIA stuck in active? a. a reply has not been received from a hello b. the time to wait for the reply on a query has been exceeded c. a Unicast packet has been sent 16 times d. this is a normal operational state 33. What can be implemented to limit the query range? a. variance, summarization, filtering b. filtering, feasible successor, filtering c. summarization, filtering variance d. filtering, summarization, stub option 34. You are experiencing SIA problems with routes not under your control. What can you implement immediately to correct the problem? a. stub option b. filtering c. summarization d. variance
152 35. What does configuring an EIGRP router as a stub do? a. keeps external routing information from being forwarded to it b. can only be used on single homed routers c. keeps queries from being sent to it d. summarizes all routing information 36. A router receives a query and finds no entry for the route in its database. What does it do next? a. queries its neighbors b. runs the feasibility condition c. replies with unreachable d. route goes SIA 147
153 Note Page 148
154 TAB Insert Tab # 4 Here
155 Default Routing
156 150
157 What is a Default Route? /24 destination address s0 s /24 e0 s2 s /24 Gateway of last resort is to network /16 is variably subnetted, 23 subnets, 4 masks D /24 Serial0 D /24 Serial1 D /24 Serial2 D*EX /0 Serial3 Internet Default route in routing table listed as /0 (matches all IPs). Always used as a last resort longest match rule. Simply stated, a default route is one that is used when no matching routing table entry is found. It appears in the routing table as a route to network and you know it is set when the output of sho ip route contains an entry similar to the following entry at the top of the routing table: Gateway of last resort is to network Any packet whose destination address is not matched by any specific routing table entry will take the path to the gateway of last resort. The gateway of last resort is a router that has more complete routing information and can hopefully forward the packet to its destination. If there is no default route and the packet s destination address is not found in the routing table, then the packet is dropped and an ICMP Destination or Network Unreachable is returned to the source IP address. The term gateway originated in the early 1980s, when the world of networking equipment consisted of bridges and gateways. Bridges connect media that use the same (or nearly the same) data-link protocols, such as Ethernet to Ethernet. Gateway is the older term for a router and originated because it was the gateway through which one was able to send packets to a network that used different media and incompatible data-link protocols. In the late 1980s, the term router was coined to reflect the function of routing packets to the proper destination. Today, the term gateway refers to a networking component that converts a 151
158 higher-level protocol into a different higher-level protocol. An example of this is a mail gateway that converts the OSI X.400 mail protocol into the Internet s RFC822 protocol format. The older use of the term exists in a variety of places, including older RFCs, networking texts, and software. A review of RFC1009 clearly defines the terms router and gateway. 152
159 Default Routing Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area * - candidate default, U - per-user static route, o - ODR P - periodic downloaded static route Gateway of last resort is to network /16 is variably subnetted, 51 subnets, 6 masks D /30 [90/ ] via , 03:46:01, Serial2/0 D /30 [90/ ] via , 03:46:05, Serial3/0 S /30 [1/0] via (portions deleted) D*EX /0 [170/ ] via , 03:45:34, Serial2/0 Default route listed as gateway of last resort in routing table Possible for router to learn of multiple default routes Same rules apply as for other routes distance & metrics Gateway of last result does not have to be Internet hosts use routing tables to compute the next hop for a packet. Routing tables can take many forms, but here is a simple model that can explain most Internet routing. Each entry in a routing table has at least two fields - IP Address Prefix and Next Hop. The Next Hop is the IP address of another host or router that is directly reachable via an Ethernet, serial link, or some other physical connection. The IP Address Prefix specifies a set of destinations for which the routing entry is valid. In order to be in this set, the beginning of the destination IP address must match the IP Address Prefix, which can have from 0 to 32 significant bits. For example, an IP Address Prefix of /16 would match any IP Destination Address of the form X.X. If no routing table entries match a packet's Destination Address, the packet is discarded as undeliverable (possibly with an ICMP notification to the sender). If multiple routing tables entries match, the longest match is preferred. The longest match is the entry with the most 1 bits in its Routing Mask. To avoid needing routing entries for every possible Internet destination, most hosts and routers use a default route (some routing tables contain nothing but a single default route). A default route has a Routing Address/Mask pair of / In other words, it matches every IP address, but since there are no 1 bits in its Routing Mask, any other match would be selected by the longest match rule. The default route will only be used if there are no other matches in the routing table, thus its name. Default routes are quite common, and are put to best use on networks with only a single link connecting to the global Internet. On 153
160 such a network, routing tables will have entries for local nets and subnets, as well as a single default route leading to the outbound link. However, remember that all Next Hops must be directly reachable, so the default routes won't necessarily point to the same IP address. In addition, some networks (large Internet service providers, mostly) use defaultless routing tables that must be able to match every IP address in the global network. 154
161 Why use a Default Route? Provides a route for unknown destination networks. Packets for unknown destinations are not just dropped. Decreases the amount of information required to be carried in routing table. Decreases router latency due to lengthy route lookup. Limits the propagation of route updates. If implemented correctly, can dramatically increase the overall performance of a router and a routed network. Users want access to all parts of the network (Internet) at all times. If a packet is received from a user device with a destination address that does not have a matching network in the routing table, the packet is simply dumped. By having a default route/gateway of last result installed in the routing table, there will always be a match for any packet received. When a router is connected to the Internet (SIPR/NIPR), a default route can be very useful. Without a default route, the router would have to have a route for every destination on the Internet. This could very easily exceed 100,000 entries. With a default route, a router needs to know only about the destinations internal to its autonomous system. The default route will forward packets destined for external addresses to the Internet service provider. An even bigger problem in very large routed networks is topology changes. As the network increases in size, topology changes occur more frequently resulting in an increasing number of updates being propagated through the topology. Each update that is received by the router must be processed, which utilizes CPU cycles and memory. As this increases, the demands on the router also increase. This can cause latency issues to arise in the routing of user information. Very frequently this problem is blamed on lack of bandwidth. Installing a default route effectively hides these changes from the topology utilizing the default route. 155
162 Implementing a Default Route 1. Static Route 2. IP Default Network Command 3. Propagating into an IGP - OSPF -EIGRP There are different techniques for implementing a default route. The static route and IP default network command place a default route and gateway of last resort in the router these are configured. To share a default route with other routers in the topology, it must be propagated via an IGP. The two discussed in this chapter are OSPF and EIGRP. There is no one best way to configure a default route and then pass it throughout the topology. It is best to understand the different techniques and then utilize the one that best fits your needs. 156
163 Static Default Route Router(config)# ip route network mask [address interface] [distance] [permanent] Network Mask Address Interface distance Destination network for the static route. Prefix mask for the destination network. IP address of the next hop that can be used to reach that network. Interface number on router to exit to reach destination network. (Optional) Administrative distance for the static route. permanent (Optional) Specifies that the route will not be removed. Above is the command to configure a static route ip route. The network is the destination network. The mask is the subnet mask for this destination network. The address is the IP address of the next hop to reach this network. The interface is the interface on the router to exit to reach this network. The distance is used to set the administrative distance of this static route. The permanent command is used to keep the static route in the routing table regardless if the next hop address is reachable of the exit interface is up. 157
164 Static Default Route s0/ ip route s0/0 (points to exit interface) or ip route (next hop address connected) Either method will install default route into routing table. When configuring a default static route, it is the same process as any other static route except the network and mask are all 0s (this covers the range of all IPs). The route can be pointed to an exit interface or a next hop address of a directly connected neighbor router. By pointing it to an exit interface or directly connected address, it is possible for a route to not exist to actual Internet destinations, but simply be a layer two connection. This can somewhat be misleading because in the internal topology, the routers believe there is a default destination when in actuality, there isn t. 158
165 Static Default Route /24 BGP ip route (next hop address via protocol) Next hop address is learned via a routing protocol and placed into routing table. Static route is then pointed to that network. A default static route can also be set up by pointing the route to a destination network being advertised from a neighbor router via a routing protocol. This can be more realistic. If for any reason there are actual routing problems within the ISP networks, the network the static route is being pointed to would stop being advertised. This would lead to the route being removed from the routing table. Once this happens, the default static route would also be removed from the routing table. If the default static route is being advertised to neighbors within the topology, once it is removed from the edge routers table, it is no longer shared with the internal neighbors. A very common practice within DOD networks is when requesting service from the DISN or GIG, they will advertise a default network via BGP. This network is then utilized by the entity requesting service for the installation of a default route by pointing to it. 159
166 IP Default-Network Command Router(config)# ip default-network network Used to designate a classful network as a default route. Classful network must be installed in the routing table. When used in conjunction with EIGRP, network must be learned via EIGRP and then is propagated via EIGRP as gateway of last resort. The ip default-network command is classful. It is used to designate a classful network to be used as a default network. The classful network must be in the routing table for it to be considered as a gateway of last resort. Multiple default networks can be configured. All those configured that are in the routing table are tagged as candidate default routes. The router goes through the normal process (distance/metric) to determine the selection of the gateway of last resort. If a tagged default network is not chosen as the gateway of last resort, it is then used as a backup. When a classful network is learned by a router via EIGRP and this network number is used in the ip default-network command, the network is then advertised to its EIGRP neighbors as a default network automatically. The network is propagated thoughout the EIGRP topology as a default route. 160
167 IP Default-Network Command /16 BGP ip default-network Command designates classful network as default route and it is set as the gateway of last resort. Points to next hop address associated with network in routing table. In the above scenario, a router learns of a classful network via BGP. It is installed in the routing table. Utilizing the command ip default-network causes the network to be designated as a default route candidate. It will be installed as the gateway of last resort pointing to the next hop associated with the network in the routing table. 161
168 Propagating Default Route via an IGP EIGRP Two methods to distribute in EIGRP 1. IP default-network command. - network specified in command must be learned by EIGRP for it to share with neighbors as a default route. 2. Static default route - redistribute static into EIGRP. OSPF Default-information originate command - if gateway of last resort is set, causes default route to be redistributed into OSPF. Once an edge router has a default route installed, the next step is to propagate this information to its neighbors. The most effective way to do this is to propagate it via an existing IGP. Two of the more common are OSPF and EIGRP. There are two methods for propagating a default route in EIGRP. The first is to have a classful network, which was learned via EIGRP, and then reference this network in the ip default- network command. The network is then propagated through the EIGRP domain as a default route. The second method is to install a default static route. The static route is then redistributed into EIGRP. If there are multiple static routes within the routing table they will also be redistributed. Consideration must be given as to whether these should be filtered from the redistribution process. The method for distributing a default route within OSPF is to utilize the defaultinformation originate command. This is configured as part of the OSPF process. If a gateway of last resort is set on the router, the command causes a default route to be redistributed into the OSPF process. This is then propagated throughout the OSPF domain. 162
169 Propagating via an IGP - EIGRP / / /16 1 EIGRP /16 Classful network is advertised to router 1 via EIGRP. Router 1 configures ip default-network command. Router 1 advertises as default network to neighbors. Neighbors install as gateway of last resort. In the above example, network is advertised to route 1 via EIGRP. Router 1 enters the configuration ip default-network This tags the route as a default route candidate and it is entered in router 1 routing table as the gateway of last resort. The network is then advertised to the EIGRP neighbors as a default route candidate and it is entered into their routing tables as the gateway of last resort. The ip default-network command is classful. Therefore, it can only be used if there is a classful network to reference it to in the routing table. 163
170 Redistribute Static router(config)# router eigrp autonomous system number - enables EIGRP and defines the autonomous system number. router(config-router)# redistribute static - redistributes the default static route into the EIGRP routing process. - default route is then shared with EIGRP neighbors. - command will redistribute all static routes in the routing table, not just the default route. Once a static default route is in the edge router s routing table, by configuring the command redistribute static to the EIGRP routing process, the default route will be shared with the edge router s EIGRP neighbors. The default route will be shared by all EIGRP neighbors across the topology until all routers have learned it. As it is advertised from neighbor to neighbor, EIGRP will calculate the metric as it would with any other route. If there are multiple paths within the topology to the edge router, the preferred path will be installed I the routing table. The redistribute static command will cause all static routes installed in the routing table to be shared with EIGRP neighbors. If the desired result is to have only the default route shared and not other static routes, routing filtering must be configured. 164
171 Propagating via an IGP EIGRP / / /16 1 BGP /0 Network advertised to router 1 via BGP. Router 1 installs default static route to Router 1 redistributes static into EIGRP. Default route propagated to neighbors via EIGRP. In the above example, network is advertised to router 1 via BGP. It is installed into the routing table with BGP as the source. Router 1 installs a default static route pointing to network The static route is installed in the routing table and is selected as the gateway of last resort. Router 1 then redistributes static into EIGRP. The default route is then advertised to the EIGRP neighbors. Note that during this operation, the default static route does not have to be pointed to a classful network. It can be pointed to an exit interface, connected IP address, or any other route within the routing table. 165
172 /0 Propagating via an IGP OSPF / /16 1 BGP /0 Network advertised to router 1 via BGP. Router 1 installs default static route to or uses IP default-network command. Router 1 uses the default-information originate command within OSPF. Default route propagated to neighbors via OSPF. Network is advertised to router 1 via BGP. Router 1 then configures a default static route pointing to this network. The static route is then installed in the routing table and selected as the gateway of last resort. Router 1 configures OSPF with the default-information originate command. This redistributes a default route into OSPF. This default route is then advertised to the OSPF neighbors. Note that during this operation, the default static route does not have to be pointed to a classful network. It can be pointed to an exit interface, connected IP address, or any other route within the routing table. If there is a gateway of last resort set, then a default route is redistributed into OSPF. 166
173 Propagating via an IGP OSPF Router(config)# default-information originate [always] [metric metric-value] [metric-type type-value] [route-map map-name] default-information originate always metric metric-type route-map When a gateway of last resort is present in the router, causes a default route to be redistributed into OSPF. (Optional) Always advertises the default route regardless of whether the software has a default route. (Optional) Metric used for generating the default route. The default metric value is 10. (Optional) External link type: Type 1 or 2 external route. (Optional) References the designated route map. The default-information originate command is configured as part of OSPF. It redistributes a default route into OSPF if the gateway of last resort is set on the router. The always extension configures a default route to be redistributed regardless of whether the gateway of last resort is set or not. The metric extension allows the configuration of a seed metric to be set on the redistributed default route. The metric-type extension allows the redistributed route to be set as a type 1 or type 2 external OSPF route. The default is type 2. The route-map extension tells the redistribution process of the default route to reference a route map. The guidelines established within the route map are then applied to the redistribution process. 167
174 Default Routing Network Lab AS /24 f0/0 /26 1 s0/0 s0/1 AS - 7 f0/ /24 s0/0 s0/1 7 s0/1 AS /24 S0/0 4 f0/0 /27 s0/1 s0/0 f0/0 /26 2 s0/0 s0/1 5 /26 f0/0 s0/1 s0/0 f0/0 / /26 f0/0 Allocate IP addresses within each AS. Utilize IPs from within each block for connections to router 7. Install BGP between routers 1 & 7 and 4 & 7. Routers 1 & 4 perform route summarization to router 7. Advertise the network from router 7 to routers 1 and 4. This will be utilized by routers 1 & 4 as the default network. Configure EIGRP in AS-1 and AS-4. Install a default static route to the classful network. Redistribute static into EIGRP. Routers 1 6 should have their gateway of last resort set. Conduct a ping test from router 3 to router 6. In AS-1 and 4, turn off EIGRP and configure OSPF. Install a default static route to the classful network and configure OSPF with the default-information originate command. Routers 1 6 should have their gateway of last resort set. Conduct a ping test from router 3 to router
175 Default Routing Network Lab f0/0 AS / /24 AS /24 f0/0 /26 1 s0/0 s0/1 AS - 7 s0/0 s0/1 7 s0/3 s0/1 s0/2 S0/0 4 f0/0 /27 s0/1 s0/0 f0/0 /26 2 s0/0 s0/1 5 /26 f0/0 s0/1 s0/0 f0/0 /27 3 s0/0 s0/1 6 /26 f0/0 Configure BGP between the routers as shown above. Advertise the network from router 7 to other BGP routers. Operate each AS with EIGRP and then OSPF. Install default routing within each AS with each protocol. Conduct a ping test from router 2 to router 5. With two edge routers present, there will be multiple default route candidates. Note how each internal router (2 & 5) reacts to the multiple default routes. Make changes to the network link down, manipulate metrics, etc. - to see how the routers react from a default network standpoint. 169
176 Default Routing Review Questions 170
177 1. Which of the following best describes a default route? a. A backup for internal routes b. A routing table entry that matches all destination IP s c. A route that points to core internet routers d. A backup route for use if the routing protocol fails 2. What is the difference between a default route and a gateway of last resort? a. Nothing, they are the same b. Multiple default routes can be candidates for the gateway c. Multiple gateways can be candidates for default routes d. Gateways of last resort are Internet core routers and default routes are part of this 3. What are the options for pointing a static route? a. interface and next hop b. distance and metric c. ip default-network and default-information originate d. always and metric-type 4. Which of the following is a benefit of default routing? a. ease of configuration b. limits the spread of routing updates c. increases the amount of bandwidth d. decreases the reliance on ICMP 5. Which of the following is a benefit of default routing? a. requires no routing protocol configuration b. limits the spread of SNMP c. reduces the size of the routing table d. eliminates the need for routing updates 6. The ip default-network command is considered classful. a. true b. false 7. A router receives a classful network via BGP. This router is also operating with EIGRP. The router installs the ip default-network command with this classful network number. This default network will be shared with its EIGRP neighbors. a. true b. false 8. The default-information originate command within OSPF does what? a. installs a gateway of last resort into the routing table b. configures that router to become an ASBR c. sets up a default static route d. redistributes a default route into the OSPF process 171
178 9. It is possible to set the metric of the default route redistributed into OSPF. a. true b. false 10. Which of following can occur if default routing is not implemented? a. increased router performance b. decreased routing table size c. additional router configuration d. router latency 11. Within OSPF, the default route must be pointed at a classful network. a. false b. true 12. The ip-default network command redistributes a default route into EIGRP. a. true b. false 172
179
Module 6 Implementing BGP
 Module 6 Implementing BGP Lesson 1 Explaining BGP Concepts and Terminology BGP Border Gateway Protocol Using BGP to Connect to the Internet If only one ISP, do not need BGP. If multiple ISPs, use BGP,
Module 6 Implementing BGP Lesson 1 Explaining BGP Concepts and Terminology BGP Border Gateway Protocol Using BGP to Connect to the Internet If only one ISP, do not need BGP. If multiple ISPs, use BGP,
Configuring BGP. Cisco s BGP Implementation
 Configuring BGP This chapter describes how to configure Border Gateway Protocol (BGP). For a complete description of the BGP commands in this chapter, refer to the BGP s chapter of the Network Protocols
Configuring BGP This chapter describes how to configure Border Gateway Protocol (BGP). For a complete description of the BGP commands in this chapter, refer to the BGP s chapter of the Network Protocols
Introduction to BGP. ISP Workshops. Last updated 30 October 2013
 Introduction to BGP ISP Workshops Last updated 30 October 2013 1 Border Gateway Protocol p A Routing Protocol used to exchange routing information between different networks n Exterior gateway protocol
Introduction to BGP ISP Workshops Last updated 30 October 2013 1 Border Gateway Protocol p A Routing Protocol used to exchange routing information between different networks n Exterior gateway protocol
Introduction to BGP. ISP/IXP Workshops
 Introduction to BGP ISP/IXP Workshops 1 Border Gateway Protocol A Routing Protocol used to exchange routing information between different networks Exterior gateway protocol Described in RFC4271 RFC4276
Introduction to BGP ISP/IXP Workshops 1 Border Gateway Protocol A Routing Protocol used to exchange routing information between different networks Exterior gateway protocol Described in RFC4271 RFC4276
Multiprotocol BGP Extensions for IP Multicast Commands
 Multiprotocol BGP Extensions for IP Multicast Commands Use the commands in this chapter to configure and monitor multiprotocol BGP. Multiprotocol BGP is based on RFC 2283, Multiprotocol Extensions for
Multiprotocol BGP Extensions for IP Multicast Commands Use the commands in this chapter to configure and monitor multiprotocol BGP. Multiprotocol BGP is based on RFC 2283, Multiprotocol Extensions for
APNIC elearning: BGP Basics. 30 September :00 PM AEST Brisbane (UTC+10) Revision: 2.0
 APNIC elearning: BGP Basics 30 September 2015 1:00 PM AEST Brisbane (UTC+10) Issue Date: 07 July 2015 Revision: 2.0 Presenter Nurul Islam (Roman) Senior Training Specialist, APNIC Nurul maintains the APNIC
APNIC elearning: BGP Basics 30 September 2015 1:00 PM AEST Brisbane (UTC+10) Issue Date: 07 July 2015 Revision: 2.0 Presenter Nurul Islam (Roman) Senior Training Specialist, APNIC Nurul maintains the APNIC
Introduction. Keith Barker, CCIE #6783. YouTube - Keith6783.
 Understanding, Implementing and troubleshooting BGP 01 Introduction http:// Instructor Introduction Keith Barker, CCIE #6783 CCIE Routing and Switching 2001 CCIE Security 2003 kbarker@ine.com YouTube -
Understanding, Implementing and troubleshooting BGP 01 Introduction http:// Instructor Introduction Keith Barker, CCIE #6783 CCIE Routing and Switching 2001 CCIE Security 2003 kbarker@ine.com YouTube -
Contents. Introduction. Prerequisites. Requirements. Components Used
 Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations OSPF EIGRP RIP Troubleshoot Introduction This document describes how to redistribute Internal Border
Contents Introduction Prerequisites Requirements Components Used Configure Network Diagram Configurations OSPF EIGRP RIP Troubleshoot Introduction This document describes how to redistribute Internal Border
Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED
 Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED Topology Objectives Background For IBGP peers to correctly exchange routing information, use the next-hop-self command with
Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED Topology Objectives Background For IBGP peers to correctly exchange routing information, use the next-hop-self command with
This appendix contains supplementary Border Gateway Protocol (BGP) information and covers the following topics:
 Appendix C BGP Supplement This appendix contains supplementary Border Gateway Protocol (BGP) information and covers the following topics: BGP Route Summarization Redistribution with IGPs Communities Route
Appendix C BGP Supplement This appendix contains supplementary Border Gateway Protocol (BGP) information and covers the following topics: BGP Route Summarization Redistribution with IGPs Communities Route
internet technologies and standards
 Institute of Telecommunications Warsaw University of Technology internet technologies and standards Piotr Gajowniczek BGP (Border Gateway Protocol) structure of the Internet Tier 1 ISP Tier 1 ISP Google
Institute of Telecommunications Warsaw University of Technology internet technologies and standards Piotr Gajowniczek BGP (Border Gateway Protocol) structure of the Internet Tier 1 ISP Tier 1 ISP Google
Internet inter-as routing: BGP
 Internet inter-as routing: BGP BGP (Border Gateway Protocol): the de facto standard BGP provides each AS a means to: 1. Obtain subnet reachability information from neighboring ASs. 2. Propagate the reachability
Internet inter-as routing: BGP BGP (Border Gateway Protocol): the de facto standard BGP provides each AS a means to: 1. Obtain subnet reachability information from neighboring ASs. 2. Propagate the reachability
Configuring BGP community 43 Configuring a BGP route reflector 44 Configuring a BGP confederation 44 Configuring BGP GR 45 Enabling Guard route
 Contents Configuring BGP 1 Overview 1 BGP speaker and BGP peer 1 BGP message types 1 BGP path attributes 2 BGP route selection 6 BGP route advertisement rules 6 BGP load balancing 6 Settlements for problems
Contents Configuring BGP 1 Overview 1 BGP speaker and BGP peer 1 BGP message types 1 BGP path attributes 2 BGP route selection 6 BGP route advertisement rules 6 BGP load balancing 6 Settlements for problems
Connecting to a Service Provider Using External BGP
 Connecting to a Service Provider Using External BGP First Published: May 2, 2005 Last Updated: August 21, 2007 This module describes configuration tasks that will enable your Border Gateway Protocol (BGP)
Connecting to a Service Provider Using External BGP First Published: May 2, 2005 Last Updated: August 21, 2007 This module describes configuration tasks that will enable your Border Gateway Protocol (BGP)
Internetwork Expert s CCNP Bootcamp. Border Gateway Protocol (BGP) What Is BGP?
 Internetwork Expert s CCNP Bootcamp Border Gateway Protocol (BGP) http:// What Is BGP? Border Gateway Protocol Version 4 Standards based RFC 4271 A Border Gateway Protocol 4 (BGP-4) Exterior Gateway Protocol
Internetwork Expert s CCNP Bootcamp Border Gateway Protocol (BGP) http:// What Is BGP? Border Gateway Protocol Version 4 Standards based RFC 4271 A Border Gateway Protocol 4 (BGP-4) Exterior Gateway Protocol
Rev External BGP
 Rev. 00.. External BGP c c n a c o o k b o o k. c o m C O N C E P T S AS (Autonomous System) A network under a single administrative control, like a single company or a single ISP. ASN (AS Number) used
Rev. 00.. External BGP c c n a c o o k b o o k. c o m C O N C E P T S AS (Autonomous System) A network under a single administrative control, like a single company or a single ISP. ASN (AS Number) used
CertifyMe. CertifyMe
 CertifyMe Number: 642-661 Passing Score: 800 Time Limit: 120 min File Version: 7.6 http://www.gratisexam.com/ CertifyMe-642-661 Exam A QUESTION 1 Exhibit: Certkiller router#show ip route Codes: C - connected,
CertifyMe Number: 642-661 Passing Score: 800 Time Limit: 120 min File Version: 7.6 http://www.gratisexam.com/ CertifyMe-642-661 Exam A QUESTION 1 Exhibit: Certkiller router#show ip route Codes: C - connected,
Ravi Chandra cisco Systems Cisco Systems Confidential
 BGP4 1 Ravi Chandra cisco Systems 0799_04F7_c2 Cisco Systems Confidential 2 Border Gateway Protocol (BGP) Introduction to BGP BGP Peer Relationship BGP Attributes Applying Policy with BGP Putting it all
BGP4 1 Ravi Chandra cisco Systems 0799_04F7_c2 Cisco Systems Confidential 2 Border Gateway Protocol (BGP) Introduction to BGP BGP Peer Relationship BGP Attributes Applying Policy with BGP Putting it all
TDC 363 Introduction to LANs
 TDC 363 Introduction to LANs Routing Protocols and RIP Greg Brewster DePaul University TDC 363 1 Dynamic Routing Routing Protocols Distance Vector vs. Link State Protocols RIPv1 & RIPv2 RIP Problems Slow
TDC 363 Introduction to LANs Routing Protocols and RIP Greg Brewster DePaul University TDC 363 1 Dynamic Routing Routing Protocols Distance Vector vs. Link State Protocols RIPv1 & RIPv2 RIP Problems Slow
BGP can also be used for carrying routing information for IPv6 prefix over IPv6 networks.
 This chapter describes how to configure the Cisco ASA to route data, perform authentication, and redistribute routing information using the Border Gateway Protocol (). About, page 1 Guidelines for, page
This chapter describes how to configure the Cisco ASA to route data, perform authentication, and redistribute routing information using the Border Gateway Protocol (). About, page 1 Guidelines for, page
BGP Commands. Network Protocols Command Reference, Part 1 P1R-355
 BGP Commands Use the commands in this chapter to configure and monitor Border Gateway Protocol (BGP). For BGP configuration information and examples, refer to the Configuring BGP chapter of the Network
BGP Commands Use the commands in this chapter to configure and monitor Border Gateway Protocol (BGP). For BGP configuration information and examples, refer to the Configuring BGP chapter of the Network
Chapter 13 Configuring BGP4
 Chapter 13 Configuring BGP4 This chapter provides details on how to configure Border Gateway Protocol version 4 (BGP4) on HP products using the CLI and the Web management interface. BGP4 is supported on
Chapter 13 Configuring BGP4 This chapter provides details on how to configure Border Gateway Protocol version 4 (BGP4) on HP products using the CLI and the Web management interface. BGP4 is supported on
Border Gateway Protocol - BGP
 BGP Fundamentals Border Gateway Protocol - BGP Runs over TCP (port 179) TCP connection required before BGP session Need to be reachable! Path vector routing protocol Best path selection based on path attributes
BGP Fundamentals Border Gateway Protocol - BGP Runs over TCP (port 179) TCP connection required before BGP session Need to be reachable! Path vector routing protocol Best path selection based on path attributes
Configuration prerequisites 45 Configuring BGP community 45 Configuring a BGP route reflector 46 Configuring a BGP confederation 46 Configuring BGP
 Contents Configuring BGP 1 Overview 1 BGP speaker and BGP peer 1 BGP message types 1 BGP path attributes 2 BGP route selection 6 BGP route advertisement rules 6 BGP load balancing 6 Settlements for problems
Contents Configuring BGP 1 Overview 1 BGP speaker and BGP peer 1 BGP message types 1 BGP path attributes 2 BGP route selection 6 BGP route advertisement rules 6 BGP load balancing 6 Settlements for problems
Symbols. Numerics I N D E X
 I N D E X Symbols? (question mark), CLI help system, 126 Numerics A 2-router BGP topology, configuring, 279 284 4-router BGP topology, configuring, 266, 276 279 ABRs (area border routers), 9, 87, 95, 141
I N D E X Symbols? (question mark), CLI help system, 126 Numerics A 2-router BGP topology, configuring, 279 284 4-router BGP topology, configuring, 266, 276 279 ABRs (area border routers), 9, 87, 95, 141
CS4700/CS5700 Fundamentals of Computer Networks
 CS4700/CS5700 Fundamentals of Computer Networks Lecture 12: Inter-domain routing Slides used with permissions from Edward W. Knightly, T. S. Eugene Ng, Ion Stoica, Hui Zhang Alan Mislove amislove at ccs.neu.edu
CS4700/CS5700 Fundamentals of Computer Networks Lecture 12: Inter-domain routing Slides used with permissions from Edward W. Knightly, T. S. Eugene Ng, Ion Stoica, Hui Zhang Alan Mislove amislove at ccs.neu.edu
Unit 3: Dynamic Routing
 Unit 3: Dynamic Routing Basic Routing The term routing refers to taking a packet from one device and sending it through the network to another device on a different network. Routers don t really care about
Unit 3: Dynamic Routing Basic Routing The term routing refers to taking a packet from one device and sending it through the network to another device on a different network. Routers don t really care about
Internet Routing : Fundamentals of Computer Networks Bill Nace
 Internet Routing 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross Looking Ahead Lab #2 just due Quiz #2
Internet Routing 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross Looking Ahead Lab #2 just due Quiz #2
COMP/ELEC 429 Introduction to Computer Networks
 COMP/ELEC 429 Introduction to Computer Networks Lecture 11: Inter-domain routing Slides used with permissions from Edward W. Knightly, T. S. Eugene Ng, Ion Stoica, Hui Zhang T. S. Eugene Ng eugeneng at
COMP/ELEC 429 Introduction to Computer Networks Lecture 11: Inter-domain routing Slides used with permissions from Edward W. Knightly, T. S. Eugene Ng, Ion Stoica, Hui Zhang T. S. Eugene Ng eugeneng at
BGP Commands. Network Protocols Command Reference, Part 1 P1R-355
 BGP Commands Use the commands in this chapter to configure and monitor Border Gateway Protocol (BGP). For BGP configuration information and examples, refer to the Configuring BGP chapter of the Network
BGP Commands Use the commands in this chapter to configure and monitor Border Gateway Protocol (BGP). For BGP configuration information and examples, refer to the Configuring BGP chapter of the Network
Planning for Information Network
 Planning for Information Network Lecture 8: Network Routing Protocols Assistant Teacher Samraa Adnan Al-Asadi 1 Routing protocol features There are many ways to characterize routing protocols, including
Planning for Information Network Lecture 8: Network Routing Protocols Assistant Teacher Samraa Adnan Al-Asadi 1 Routing protocol features There are many ways to characterize routing protocols, including
Introduction to BGP ISP/IXP Workshops
 Introduction to BGP ISP/IXP Workshops 1 Border Gateway Protocol Routing Protocol used to exchange routing information between networks exterior gateway protocol RFC1771 work in progress to update draft-ietf-idr-bgp4-18.txt
Introduction to BGP ISP/IXP Workshops 1 Border Gateway Protocol Routing Protocol used to exchange routing information between networks exterior gateway protocol RFC1771 work in progress to update draft-ietf-idr-bgp4-18.txt
BGP Support for 4-byte ASN
 The Cisco implementation of 4-byte autonomous system (AS) numbers uses asplain (65538, for example) as the default regular expression match and the output display format for AS numbers. However, you can
The Cisco implementation of 4-byte autonomous system (AS) numbers uses asplain (65538, for example) as the default regular expression match and the output display format for AS numbers. However, you can
Why dynamic route? (1)
 Routing Why dynamic route? (1) Static route is ok only when Network is small There is a single connection point to other network No redundant route 2 Why dynamic route? (2) Dynamic Routing Routers update
Routing Why dynamic route? (1) Static route is ok only when Network is small There is a single connection point to other network No redundant route 2 Why dynamic route? (2) Dynamic Routing Routers update
Table of Contents. BGP Configuration 1
 Table of Contents BGP Configuration 1 BGP Overview 1 Formats of BGP Messages 2 BGP Path Attributes 5 BGP Route Selection 9 ibgp and IGP Synchronization 11 Settlements for Problems in Large Scale BGP Networks
Table of Contents BGP Configuration 1 BGP Overview 1 Formats of BGP Messages 2 BGP Path Attributes 5 BGP Route Selection 9 ibgp and IGP Synchronization 11 Settlements for Problems in Large Scale BGP Networks
Operation Manual BGP. Table of Contents
 Table of Contents Table of Contents... 1-1 1.1 BGP/MBGP Overview... 1-1 1.1.1 Introduction to BGP... 1-1 1.1.2 BGP Message Types... 1-2 1.1.3 BGP Routing Mechanism... 1-2 1.1.4 MBGP... 1-3 1.1.5 BGP Peer
Table of Contents Table of Contents... 1-1 1.1 BGP/MBGP Overview... 1-1 1.1.1 Introduction to BGP... 1-1 1.1.2 BGP Message Types... 1-2 1.1.3 BGP Routing Mechanism... 1-2 1.1.4 MBGP... 1-3 1.1.5 BGP Peer
Configuring Internal BGP Features
 This module describes how to configure internal Border Gateway Protocol (BGP) features. Internal BGP (ibgp) refers to running BGP on networking devices within one autonomous system. BGP is an interdomain
This module describes how to configure internal Border Gateway Protocol (BGP) features. Internal BGP (ibgp) refers to running BGP on networking devices within one autonomous system. BGP is an interdomain
MPLS VPN Multipath Support for Inter-AS VPNs
 The feature supports Virtual Private Network (VPN)v4 multipath for Autonomous System Boundary Routers (ASBRs) in the interautonomous system (Inter-AS) Multiprotocol Label Switching (MPLS) VPN environment.
The feature supports Virtual Private Network (VPN)v4 multipath for Autonomous System Boundary Routers (ASBRs) in the interautonomous system (Inter-AS) Multiprotocol Label Switching (MPLS) VPN environment.
Table of Contents 1 BGP Configuration 1-1
 Table of Contents 1 BGP Configuration 1-1 BGP Overview 1-1 Formats of BGP Messages 1-2 BGP Path Attributes 1-4 BGP Route Selection 1-8 ibgp and IGP Synchronization 1-11 Settlements for Problems in Large
Table of Contents 1 BGP Configuration 1-1 BGP Overview 1-1 Formats of BGP Messages 1-2 BGP Path Attributes 1-4 BGP Route Selection 1-8 ibgp and IGP Synchronization 1-11 Settlements for Problems in Large
BGP. BGP Overview. Formats of BGP Messages. I. Header
 Overview Three early versions of are -1 (RFC1105), -2 (RFC1163) and -3 (RFC1267). The current version in use is -4 (RFC1771). -4 is rapidly becoming the defacto Internet exterior routing protocol standard
Overview Three early versions of are -1 (RFC1105), -2 (RFC1163) and -3 (RFC1267). The current version in use is -4 (RFC1771). -4 is rapidly becoming the defacto Internet exterior routing protocol standard
BGP Protocol & Configuration. Scalable Infrastructure Workshop AfNOG2008
 BGP Protocol & Configuration Scalable Infrastructure Workshop AfNOG2008 Border Gateway Protocol (BGP4) Case Study 1, Exercise 1: Single upstream Part 6: BGP Protocol Basics Part 7: BGP Protocol - more
BGP Protocol & Configuration Scalable Infrastructure Workshop AfNOG2008 Border Gateway Protocol (BGP4) Case Study 1, Exercise 1: Single upstream Part 6: BGP Protocol Basics Part 7: BGP Protocol - more
CS 457 Networking and the Internet. The Global Internet (Then) The Global Internet (And Now) 10/4/16. Fall 2016
 CS 457 Networking and the Internet Fall 2016 The Global Internet (Then) The tree structure of the Internet in 1990 The Global Internet (And Now) A simple multi-provider Internet 1 The Global Internet Some
CS 457 Networking and the Internet Fall 2016 The Global Internet (Then) The tree structure of the Internet in 1990 The Global Internet (And Now) A simple multi-provider Internet 1 The Global Internet Some
Connecting to a Service Provider Using External BGP
 Connecting to a Service Provider Using External BGP This module describes configuration tasks that will enable your Border Gateway Protocol (BGP) network to access peer devices in external networks such
Connecting to a Service Provider Using External BGP This module describes configuration tasks that will enable your Border Gateway Protocol (BGP) network to access peer devices in external networks such
Internet Routing Protocols Lecture 01 & 02
 Internet Routing Protocols Lecture 01 & 02 Advanced Systems Topics Lent Term, 2010 Timothy G. Griffin Computer Lab Cambridge UK Internet Routing Outline Lecture 1 : Inter-domain routing architecture, the
Internet Routing Protocols Lecture 01 & 02 Advanced Systems Topics Lent Term, 2010 Timothy G. Griffin Computer Lab Cambridge UK Internet Routing Outline Lecture 1 : Inter-domain routing architecture, the
BGP Configuration. BGP Overview. Introduction to BGP. Formats of BGP Messages. Header
 Table of Contents BGP Configuration 1 BGP Overview 1 Introduction to BGP 1 Formats of BGP Messages 1 BGP Path Attributes 4 BGP Route Selection 8 Configuring BGP 8 Configuration Prerequisites 8 Configuration
Table of Contents BGP Configuration 1 BGP Overview 1 Introduction to BGP 1 Formats of BGP Messages 1 BGP Path Attributes 4 BGP Route Selection 8 Configuring BGP 8 Configuration Prerequisites 8 Configuration
Internet Interconnection Structure
 Internet Interconnection Structure Basic Concepts (1) Internet Service Provider (ISP) Provider who connects an end user customer with the Internet in one or few geographic regions. National & Regional
Internet Interconnection Structure Basic Concepts (1) Internet Service Provider (ISP) Provider who connects an end user customer with the Internet in one or few geographic regions. National & Regional
Configuring IPv6 Provider Edge over MPLS (6PE)
 Finding Feature Information, page 1 Configuring 6PE, page 1 Finding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature
Finding Feature Information, page 1 Configuring 6PE, page 1 Finding Feature Information Your software release may not support all the features documented in this module. For the latest caveats and feature
BGP Attributes and Path Selection
 BGP Attributes and Path Selection ISP Training Workshops 1 BGP Attributes The tools available for the job 2 What Is an Attribute?... Next Hop AS Path MED...... Part of a BGP Update Describes the characteristics
BGP Attributes and Path Selection ISP Training Workshops 1 BGP Attributes The tools available for the job 2 What Is an Attribute?... Next Hop AS Path MED...... Part of a BGP Update Describes the characteristics
Configuring a BGP Route Server
 BGP route server is a feature designed for internet exchange (IX) operators that provides an alternative to full ebgp mesh peering among the service providers who have a presence at the IX. The route server
BGP route server is a feature designed for internet exchange (IX) operators that provides an alternative to full ebgp mesh peering among the service providers who have a presence at the IX. The route server
Routing Between Autonomous Systems (Example: BGP4) RFC 1771
 CS 4/55231 Internet Engineering Kent State University Dept. of Computer Science LECT-7B Routing Between Autonomous Systems (Example: BGP4) RFC 1771 52 53 BGP4 Overview Example of Operations BGP4 is a path
CS 4/55231 Internet Engineering Kent State University Dept. of Computer Science LECT-7B Routing Between Autonomous Systems (Example: BGP4) RFC 1771 52 53 BGP4 Overview Example of Operations BGP4 is a path
Border Gateway Protocol (BGP-4)
 Vanguard Applications Ware IP and LAN Feature Protocols Border Gateway Protocol (BGP-4) Notice 2008 Vanguard Networks 25 Forbes Blvd Foxboro, MA 02035 Phone: (508) 964 6200 Fax: (508) 543 0237 All rights
Vanguard Applications Ware IP and LAN Feature Protocols Border Gateway Protocol (BGP-4) Notice 2008 Vanguard Networks 25 Forbes Blvd Foxboro, MA 02035 Phone: (508) 964 6200 Fax: (508) 543 0237 All rights
Inter-Domain Routing: BGP
 Inter-Domain Routing: BGP Richard T. B. Ma School of Computing National University of Singapore CS 3103: Compute Networks and Protocols Inter-Domain Routing Internet is a network of networks Hierarchy
Inter-Domain Routing: BGP Richard T. B. Ma School of Computing National University of Singapore CS 3103: Compute Networks and Protocols Inter-Domain Routing Internet is a network of networks Hierarchy
Table of Contents 1 MSDP Configuration 1-1
 Table of Contents 1 MSDP Configuration 1-1 MSDP Overview 1-1 Introduction to MSDP 1-1 How MSDP Works 1-2 Protocols and Standards 1-7 MSDP Configuration Task List 1-7 Configuring Basic Functions of MSDP
Table of Contents 1 MSDP Configuration 1-1 MSDP Overview 1-1 Introduction to MSDP 1-1 How MSDP Works 1-2 Protocols and Standards 1-7 MSDP Configuration Task List 1-7 Configuring Basic Functions of MSDP
EE 122: Inter-domain routing Border Gateway Protocol (BGP)
 EE 122: Inter-domain routing Border Gateway Protocol (BGP) Ion Stoica October 2, 2002 (* this presentation is based on Lakshmi Subramanian s slides) Big Picture Large ISP Large ISP St u b D i al - U p
EE 122: Inter-domain routing Border Gateway Protocol (BGP) Ion Stoica October 2, 2002 (* this presentation is based on Lakshmi Subramanian s slides) Big Picture Large ISP Large ISP St u b D i al - U p
Q&As. CCIP Configuring BGP on Cisco Routers (BGP) Pass Cisco Exam with 100% Guarantee
 642-661 Q&As CCIP Configuring BGP on Cisco Routers (BGP) Pass Cisco 642-661 Exam with 100% Guarantee Free Download Real Questions & Answers PDF and VCE file from: 100% Passing Guarantee 100% Money Back
642-661 Q&As CCIP Configuring BGP on Cisco Routers (BGP) Pass Cisco 642-661 Exam with 100% Guarantee Free Download Real Questions & Answers PDF and VCE file from: 100% Passing Guarantee 100% Money Back
Configuration and Management of Networks 2012
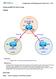 Configuring BGP with default routing Topology Objectives Background Instructions Configure BGP to exchange routing information with two ISPs. The International Travel Agency (ITA) relies extensively on
Configuring BGP with default routing Topology Objectives Background Instructions Configure BGP to exchange routing information with two ISPs. The International Travel Agency (ITA) relies extensively on
Routing Protocols --- Exterior Gateway Protocol
 Content Routing Protocols --- Exterior Gateway Protocol Linda Wu (CMPT 471 23-3) Limiting router interaction Autonomous system BGP protocol BGP messages Other issues on BGP Reference: chapter 15 Notes-13
Content Routing Protocols --- Exterior Gateway Protocol Linda Wu (CMPT 471 23-3) Limiting router interaction Autonomous system BGP protocol BGP messages Other issues on BGP Reference: chapter 15 Notes-13
Protecting an EBGP peer when memory usage reaches level 2 threshold 66 Configuring a large-scale BGP network 67 Configuring BGP community 67
 Contents Configuring BGP 1 Overview 1 BGP speaker and BGP peer 1 BGP message types 1 BGP path attributes 2 BGP route selection 6 BGP route advertisement rules 6 BGP load balancing 6 Settlements for problems
Contents Configuring BGP 1 Overview 1 BGP speaker and BGP peer 1 BGP message types 1 BGP path attributes 2 BGP route selection 6 BGP route advertisement rules 6 BGP load balancing 6 Settlements for problems
scope scope {global vrf vrf-name} no scope {global vrf vrf-name} Syntax Description
 Multi-Toplogy Routing Commands scope scope To define the scope for a Border Gateway Protocol (BGP) routing session and to enter router scope configuration mode, use the scope command in router configuration
Multi-Toplogy Routing Commands scope scope To define the scope for a Border Gateway Protocol (BGP) routing session and to enter router scope configuration mode, use the scope command in router configuration
ibgp Multipath Load Sharing
 ibgp Multipath Load haring Feature History Release 12.2(2)T 12.2(14) Modification This feature was introduced. This feature was integrated into. This feature module describes the ibgp Multipath Load haring
ibgp Multipath Load haring Feature History Release 12.2(2)T 12.2(14) Modification This feature was introduced. This feature was integrated into. This feature module describes the ibgp Multipath Load haring
Chapter 7 Lab 7-1, Configuring BGP with Default Routing
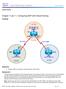 Chapter 7 Topology Objectives Configure BGP to exchange routing information with two ISPs. Background The International Travel Agency (ITA) relies extensively on the Internet for sales. For this reason,
Chapter 7 Topology Objectives Configure BGP to exchange routing information with two ISPs. Background The International Travel Agency (ITA) relies extensively on the Internet for sales. For this reason,
MPLS VPN--Inter-AS Option AB
 The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service provider
The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol Label Switching (MPLS) Virtual Private Network (VPN) service provider
Open Shortest Path First (OSPF)
 CHAPTER 42 Open Shortest Path First (OSPF) Background Open Shortest Path First (OSPF) is a routing protocol developed for Internet Protocol (IP) networks by the interior gateway protocol (IGP) working
CHAPTER 42 Open Shortest Path First (OSPF) Background Open Shortest Path First (OSPF) is a routing protocol developed for Internet Protocol (IP) networks by the interior gateway protocol (IGP) working
Module 6 More ibgp, and Basic ebgp Configuration
 ISP Workshop Lab Module 6 More ibgp, and Basic ebgp Configuration Objective: Simulate four different interconnected ISP backbones using a combination of ISIS, internal BGP, and external BGP. Prerequisites:
ISP Workshop Lab Module 6 More ibgp, and Basic ebgp Configuration Objective: Simulate four different interconnected ISP backbones using a combination of ISIS, internal BGP, and external BGP. Prerequisites:
Routing & Protocols 1
 Routing & Protocols 1 Paul Traina cisco Engineering 2 Today's Talk Terminology Routing Static Routes Interior Gateway Protocols Exterior Gateway Protocols Building an ISP network 3 Terminology network
Routing & Protocols 1 Paul Traina cisco Engineering 2 Today's Talk Terminology Routing Static Routes Interior Gateway Protocols Exterior Gateway Protocols Building an ISP network 3 Terminology network
CS 640: Introduction to Computer Networks. Intra-domain routing. Inter-domain Routing: Hierarchy. Aditya Akella
 CS 640: Introduction to Computer Networks Aditya Akella Lecture 11 - Inter-Domain Routing - BGP (Border Gateway Protocol) Intra-domain routing The Story So Far Routing protocols generate the forwarding
CS 640: Introduction to Computer Networks Aditya Akella Lecture 11 - Inter-Domain Routing - BGP (Border Gateway Protocol) Intra-domain routing The Story So Far Routing protocols generate the forwarding
Interdomain Routing Reading: Sections P&D 4.3.{3,4}
 Interdomain Routing Reading: Sections P&D 4.3.{3,4} EE122: Intro to Communication Networks Fall 2006 (MW 4:00-5:30 in Donner 155) Vern Paxson TAs: Dilip Antony Joseph and Sukun Kim http://inst.eecs.berkeley.edu/~ee122/
Interdomain Routing Reading: Sections P&D 4.3.{3,4} EE122: Intro to Communication Networks Fall 2006 (MW 4:00-5:30 in Donner 155) Vern Paxson TAs: Dilip Antony Joseph and Sukun Kim http://inst.eecs.berkeley.edu/~ee122/
Configuring a Basic BGP Network
 Configuring a Basic BGP Network Last Updated: October 19, 2011 This module describes the basic tasks to configure a basic Border Gateway Protocol (BGP) network. BGP is an interdomain routing protocol that
Configuring a Basic BGP Network Last Updated: October 19, 2011 This module describes the basic tasks to configure a basic Border Gateway Protocol (BGP) network. BGP is an interdomain routing protocol that
CS 43: Computer Networks. 24: Internet Routing November 19, 2018
 CS 43: Computer Networks 24: Internet Routing November 19, 2018 Last Class Link State + Fast convergence (reacts to events quickly) + Small window of inconsistency Distance Vector + + Distributed (small
CS 43: Computer Networks 24: Internet Routing November 19, 2018 Last Class Link State + Fast convergence (reacts to events quickly) + Small window of inconsistency Distance Vector + + Distributed (small
Border Gateway Protocol
 39 CHAPTER Chapter Goals Understand the purpose of the. Explain BGP attributes and their use in route selection. Examine the BGP route selection process. Introduction The (BGP) is an interautonomous system
39 CHAPTER Chapter Goals Understand the purpose of the. Explain BGP attributes and their use in route selection. Examine the BGP route selection process. Introduction The (BGP) is an interautonomous system
Multiprotocol BGP (MBGP)
 Multiprotocol BGP (MBGP) Module 5 2000, Cisco Systems, Inc. 1 Copyright 1998-2000, Cisco Systems, Inc. Module5.ppt 1 Module Objectives Understand that MBGP is NOT a replacement for PIM Understand the basic
Multiprotocol BGP (MBGP) Module 5 2000, Cisco Systems, Inc. 1 Copyright 1998-2000, Cisco Systems, Inc. Module5.ppt 1 Module Objectives Understand that MBGP is NOT a replacement for PIM Understand the basic
Configuring MSDP. Overview. How MSDP operates. MSDP peers
 Contents Configuring MSDP 1 Overview 1 How MSDP operates 1 MSDP support for VPNs 6 Protocols and standards 6 MSDP configuration task list 7 Configuring basic MSDP functions 7 Configuration prerequisites
Contents Configuring MSDP 1 Overview 1 How MSDP operates 1 MSDP support for VPNs 6 Protocols and standards 6 MSDP configuration task list 7 Configuring basic MSDP functions 7 Configuration prerequisites
Internet Routing Protocols Tuba Saltürk
 Internet Routing Protocols 15505068 Tuba Saltürk Outline Internet Routers Routing Protocol Interior Gateway Protocol (IGP) Distance- Vector Routing Protocol Routing Information Protocol (RIP) Interior
Internet Routing Protocols 15505068 Tuba Saltürk Outline Internet Routers Routing Protocol Interior Gateway Protocol (IGP) Distance- Vector Routing Protocol Routing Information Protocol (RIP) Interior
Chapter 7: Routing Dynamically. Routing & Switching
 Chapter 7: Routing Dynamically Routing & Switching The Evolution of Dynamic Routing Protocols Dynamic routing protocols used in networks since the late 1980s Newer versions support the communication based
Chapter 7: Routing Dynamically Routing & Switching The Evolution of Dynamic Routing Protocols Dynamic routing protocols used in networks since the late 1980s Newer versions support the communication based
BGP on IOS: Getting Started
 BGP on IOS: Getting Started ISP Workshops Last updated 30 October 2013 1 IOS Good Practices p ISPs should start off with the following BGP commands as a basic template: router bgp 64511 bgp deterministic-med
BGP on IOS: Getting Started ISP Workshops Last updated 30 October 2013 1 IOS Good Practices p ISPs should start off with the following BGP commands as a basic template: router bgp 64511 bgp deterministic-med
BGP-4 Border Gateway Protocol 4 (BGP-4) Primer
 BGP-4 Border Gateway Protocol 4 (BGP-4) Primer Diarmuid Ó Briain Last updated: 18 April 2017 2 Routing primer 2017 by C²S Consulting Policies made available under the Creative Commons Attribution-NonCommercial
BGP-4 Border Gateway Protocol 4 (BGP-4) Primer Diarmuid Ó Briain Last updated: 18 April 2017 2 Routing primer 2017 by C²S Consulting Policies made available under the Creative Commons Attribution-NonCommercial
Interdomain Routing Reading: Sections K&R EE122: Intro to Communication Networks Fall 2007 (WF 4:00-5:30 in Cory 277)
 Interdomain Routing Reading: Sections K&R 4.6.3 EE122: Intro to Communication Networks Fall 2007 (WF 4:00-5:30 in Cory 277) Guest Lecture by Brighten Godfrey Instructor: Vern Paxson TAs: Lisa Fowler, Daniel
Interdomain Routing Reading: Sections K&R 4.6.3 EE122: Intro to Communication Networks Fall 2007 (WF 4:00-5:30 in Cory 277) Guest Lecture by Brighten Godfrey Instructor: Vern Paxson TAs: Lisa Fowler, Daniel
MPLS VPN Inter-AS Option AB
 First Published: December 17, 2007 Last Updated: September 21, 2011 The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol
First Published: December 17, 2007 Last Updated: September 21, 2011 The feature combines the best functionality of an Inter-AS Option (10) A and Inter-AS Option (10) B network to allow a Multiprotocol
BGP. Autonomous system (AS) BGP version 4. Definition (AS Autonomous System)
 BGP Border Gateway Protocol (an introduction) Karst Koymans Informatics Institute University of Amsterdam (version 310, 2014/03/11 10:50:06) Monday, March 10, 2014 General ideas behind BGP Background Providers,
BGP Border Gateway Protocol (an introduction) Karst Koymans Informatics Institute University of Amsterdam (version 310, 2014/03/11 10:50:06) Monday, March 10, 2014 General ideas behind BGP Background Providers,
Contents. Configuring MSDP 1
 Contents Configuring MSDP 1 Overview 1 How MSDP works 1 MSDP support for VPNs 6 Protocols and standards 6 MSDP configuration task list 7 Configuring basic MSDP features 7 Configuration prerequisites 7
Contents Configuring MSDP 1 Overview 1 How MSDP works 1 MSDP support for VPNs 6 Protocols and standards 6 MSDP configuration task list 7 Configuring basic MSDP features 7 Configuration prerequisites 7
Configuring a Basic BGP Network
 Configuring a Basic BGP Network This module describes the basic tasks to configure a basic Border Gateway Protocol (BGP) network. BGP is an interdomain routing protocol that is designed to provide loop-free
Configuring a Basic BGP Network This module describes the basic tasks to configure a basic Border Gateway Protocol (BGP) network. BGP is an interdomain routing protocol that is designed to provide loop-free
CS 43: Computer Networks Internet Routing. Kevin Webb Swarthmore College November 16, 2017
 CS 43: Computer Networks Internet Routing Kevin Webb Swarthmore College November 16, 2017 1 Hierarchical routing Our routing study thus far - idealization all routers identical network flat not true in
CS 43: Computer Networks Internet Routing Kevin Webb Swarthmore College November 16, 2017 1 Hierarchical routing Our routing study thus far - idealization all routers identical network flat not true in
Table of Contents 1 MSDP Configuration 1-1
 Table of Contents 1 MSDP Configuration 1-1 MSDP Overview 1-1 Introduction to MSDP 1-1 How MSDP Works 1-2 Multi-Instance MSDP 1-7 Protocols and Standards 1-7 MSDP Configuration Task List 1-7 Configuring
Table of Contents 1 MSDP Configuration 1-1 MSDP Overview 1-1 Introduction to MSDP 1-1 How MSDP Works 1-2 Multi-Instance MSDP 1-7 Protocols and Standards 1-7 MSDP Configuration Task List 1-7 Configuring
Module 6 ibgp and Basic ebgp
 ISP Workshop Lab Module 6 ibgp and Basic ebgp Objective: Simulate four different interconnected ISP backbones using a combination of IS-IS, internal BGP, and external BGP. Prerequisites: Module 1 (IS-IS)
ISP Workshop Lab Module 6 ibgp and Basic ebgp Objective: Simulate four different interconnected ISP backbones using a combination of IS-IS, internal BGP, and external BGP. Prerequisites: Module 1 (IS-IS)
Top-Down Network Design, Ch. 7: Selecting Switching and Routing Protocols. Top-Down Network Design. Selecting Switching and Routing Protocols
 Top-Down Network Design Chapter Seven Selecting Switching and Routing Protocols Copyright 2010 Cisco Press & Priscilla Oppenheimer 1 Switching 2 Page 1 Objectives MAC address table Describe the features
Top-Down Network Design Chapter Seven Selecting Switching and Routing Protocols Copyright 2010 Cisco Press & Priscilla Oppenheimer 1 Switching 2 Page 1 Objectives MAC address table Describe the features
BGP. BGP Overview. BGP Operation. BGP Neighbors
 BGP BGP Overview BGP Operation BGP Neighbors BGP Overview AS - Autonomous Systems Multihoming IGP vs. EGP When to use BGP? 2 BGP Overview AS - Autonomous Systems Multihoming IGP vs. EGP When to use BGP?
BGP BGP Overview BGP Operation BGP Neighbors BGP Overview AS - Autonomous Systems Multihoming IGP vs. EGP When to use BGP? 2 BGP Overview AS - Autonomous Systems Multihoming IGP vs. EGP When to use BGP?
Troubleshooting High CPU Caused by the BGP Scanner or BGP Router Process
 Troubleshooting High CPU Caused by the BGP Scanner or BGP Router Process Document ID: 107615 Contents Introduction Before You Begin Conventions Prerequisites Components Used Understanding BGP Processes
Troubleshooting High CPU Caused by the BGP Scanner or BGP Router Process Document ID: 107615 Contents Introduction Before You Begin Conventions Prerequisites Components Used Understanding BGP Processes
Configuring Advanced BGP
 CHAPTER 6 This chapter describes how to configure advanced features of the Border Gateway Protocol (BGP) on the Cisco NX-OS switch. This chapter includes the following sections: Information About Advanced
CHAPTER 6 This chapter describes how to configure advanced features of the Border Gateway Protocol (BGP) on the Cisco NX-OS switch. This chapter includes the following sections: Information About Advanced
IP Addressing & Interdomain Routing. Next Topic
 IP Addressing & Interdomain Routing Next Topic IP Addressing Hierarchy (prefixes, class A, B, C, subnets) Interdomain routing Application Presentation Session Transport Network Data Link Physical Scalability
IP Addressing & Interdomain Routing Next Topic IP Addressing Hierarchy (prefixes, class A, B, C, subnets) Interdomain routing Application Presentation Session Transport Network Data Link Physical Scalability
Chapter 5: Maintaining and Troubleshooting Routing Solutions
 Chapter 5: Maintaining and Troubleshooting Routing Solutions CCNP TSHOOT: Maintaining and Troubleshooting IP Networks Course v6 1 Troubleshooting Network Layer Connectivity 2 Routing and Routing Data Structures
Chapter 5: Maintaining and Troubleshooting Routing Solutions CCNP TSHOOT: Maintaining and Troubleshooting IP Networks Course v6 1 Troubleshooting Network Layer Connectivity 2 Routing and Routing Data Structures
Module 6 ibgp and Basic ebgp
 ISP Workshop Lab Module 6 ibgp and Basic ebgp Objective: Simulate four different interconnected ISP backbones using a combination of OSPF, internal BGP, and external BGP. Prerequisites: Module 1 Topology
ISP Workshop Lab Module 6 ibgp and Basic ebgp Objective: Simulate four different interconnected ISP backbones using a combination of OSPF, internal BGP, and external BGP. Prerequisites: Module 1 Topology
Configuring BGP on Cisco Routers Volume 1
 Volume 1 I. Course Introduction A. Overview/Learner Skills and Knowledge B. Course Flow C. Additional References 1. Cisco Glossary of Terms D. Your Training Curriculum II. BGP Overview III. Introducing
Volume 1 I. Course Introduction A. Overview/Learner Skills and Knowledge B. Course Flow C. Additional References 1. Cisco Glossary of Terms D. Your Training Curriculum II. BGP Overview III. Introducing
Cisco CISCO Configuring BGP on Cisco Routers Exam. Practice Test. Version
 Cisco 642-661 CISCO 642-661 Configuring BGP on Cisco Routers Exam Practice Test Version 3.3 QUESTION NO: 1 Why can using the ip tcp path-mtu-discovery command improve BGP convergence? A. Smaller MSS sizes
Cisco 642-661 CISCO 642-661 Configuring BGP on Cisco Routers Exam Practice Test Version 3.3 QUESTION NO: 1 Why can using the ip tcp path-mtu-discovery command improve BGP convergence? A. Smaller MSS sizes
PART III. Implementing Inter-Network Relationships with BGP
 PART III Implementing Inter-Network Relationships with BGP ICNP 2002 Routing Protocols Autonomous System BGP-4 BGP = Border Gateway Protocol Is a Policy-Based routing protocol Is the de facto EGP of today
PART III Implementing Inter-Network Relationships with BGP ICNP 2002 Routing Protocols Autonomous System BGP-4 BGP = Border Gateway Protocol Is a Policy-Based routing protocol Is the de facto EGP of today
BGP. Autonomous system (AS) BGP version 4. Definition (AS Autonomous System)
 BGP Border Gateway Protocol (an introduction) Karst Koymans Informatics Institute University of Amsterdam (version 16.4, 2017/03/13 13:32:49) Tuesday, March 14, 2017 General ideas behind BGP Background
BGP Border Gateway Protocol (an introduction) Karst Koymans Informatics Institute University of Amsterdam (version 16.4, 2017/03/13 13:32:49) Tuesday, March 14, 2017 General ideas behind BGP Background
CS4450. Computer Networks: Architecture and Protocols. Lecture 15 BGP. Spring 2018 Rachit Agarwal
 CS4450 Computer Networks: Architecture and Protocols Lecture 15 BGP Spring 2018 Rachit Agarwal Autonomous System (AS) or Domain Region of a network under a single administrative entity Border Routers Interior
CS4450 Computer Networks: Architecture and Protocols Lecture 15 BGP Spring 2018 Rachit Agarwal Autonomous System (AS) or Domain Region of a network under a single administrative entity Border Routers Interior
CSCD 433/533 Network Programming Fall Lecture 14 Global Address Space Autonomous Systems, BGP Protocol Routing
 CSCD 433/533 Network Programming Fall 2012 Lecture 14 Global Address Space Autonomous Systems, BGP Protocol Routing 1 Topics Interdomain Routing BGP Interdomain Routing Benefits vs. Link State Routing
CSCD 433/533 Network Programming Fall 2012 Lecture 14 Global Address Space Autonomous Systems, BGP Protocol Routing 1 Topics Interdomain Routing BGP Interdomain Routing Benefits vs. Link State Routing
Building the Routing Table. Introducing the Routing Table Directly Connected Networks Static Routing Dynamic Routing Routing Table Principles
 Building the Routing Table Introducing the Routing Table Directly Connected Networks Static Routing Dynamic Routing Routing Table Principles Introducing the Routing Table R1# show ip route Codes: C - connected,
Building the Routing Table Introducing the Routing Table Directly Connected Networks Static Routing Dynamic Routing Routing Table Principles Introducing the Routing Table R1# show ip route Codes: C - connected,
Border Gateway Protocol (an introduction) Karst Koymans. Tuesday, March 8, 2016
 .. BGP Border Gateway Protocol (an introduction) Karst Koymans Informatics Institute University of Amsterdam (version 15.6, 2016/03/15 22:30:35) Tuesday, March 8, 2016 Karst Koymans (UvA) BGP Tuesday,
.. BGP Border Gateway Protocol (an introduction) Karst Koymans Informatics Institute University of Amsterdam (version 15.6, 2016/03/15 22:30:35) Tuesday, March 8, 2016 Karst Koymans (UvA) BGP Tuesday,
BGP Best External. Finding Feature Information
 The feature provides the network with a backup external route to avoid loss of connectivity of the primary external route. The feature advertises the most preferred route among those received from external
The feature provides the network with a backup external route to avoid loss of connectivity of the primary external route. The feature advertises the most preferred route among those received from external
