CCB The Condor Connection Broker. Dan Bradley Condor Project CS and Physics Departments University of Wisconsin-Madison
|
|
|
- Baldwin Roberts
- 5 years ago
- Views:
Transcription
1 CCB The Condor Connection Broker Dan Bradley Condor Project CS and Physics Departments University of Wisconsin-Madison
2 Condor Connections Central Manager advertise negotiate run this job advertise you ve been matched transfer files
3 node is behind a firewall or is NATed. Unreachable Central Manager advertise negotiate no go! run this job transfer files advertise you ve been matched
4 Submit Unreachable Central Manager Submit node is behind a firewall or is NATed. advertise negotiate no go! run this job transfer files advertise you ve been matched
5 Common Scenarios Why cross private network boundaries? Flocking Multi-site Condor pool Glidein
6 CCB: Condor Connection Broker Condor wants two-way connectivity With CCB, one-way is good enough run this job CCB_ADDRESS=ccb.host.name I want to connect to the submit node transfer files reversed connection
7 CCB: Condor Connection Broker Works in the mirror case too I want to connect to the execute node run this job reversed connection transfer files CCB_ADDRESS=ccb.host.name
8 Limitations of CCB 1. Doesn t help with standard universe 2. Requires one-way connectivity no go! CCB_ADDRESS=ccb1.host CCB_ADDRESS=ccb2.host GCB or VPN can help
9 Connecting to CCB CCB server must be reachable by both sides. CCB connect CCB Server READ authorization level CCB listen DAEMON authorization level CCB_ADDRESS=ccb.host
10 CCB Server Behind Must have an open port to connect to CCB Firewall CCB Server CCB connect open port here (default 9618) CCB listen CCB_ADDRESS=ccb.host
11 Client and server security policies are enforced in logical direction Security on Reversed Connection CCB Server CCB connect client-side run this job reversed connection CCB listen daemon-side CCB_ADDRESS=ccb.host
12 GCB: Generic Connection Broker GCB: Condor Clever: mostly invisible to Condor code However, this makes some things difficult! CCB: Condor Inspired by GCB More tightly integrated into Condor Not a complete replacement
13 Why CCB? Secure supports full Condor security set Robust supports reconnect, failover Portable supports all Condor platforms, not just Linux
14 Why CCB? Dynamic CCB clients and servers configurable without restart Informative log messages Connection errors are propagated Names and local IP addresses reported (GCB replaces local IP with broker IP) Easy to configure automatically switches UDP to TCP in Condor protocols CCB server only needs one open port
15 The Server: Configuring CCB The collector is a CCB server UNIX: MAX_FILE_DESCRIPTORS=10000 The Client: 1. CCB_ADDRESS = $(COLLECTOR_HOST) 2. PRIVATE_NETWORK_NAME = your.domain (optimization: hosts with same network name don t use CCB to connect to each other)
16 Tests of CCB Igor Sfiligoi s Cross-Atlantic Mega Condor Glidein Test Pool for CMS one machine with 70 CCB collectors execute nodes in private networks GSI authentication 100,000 registered Condor daemons 200,000 jobs/day with one schedd
17 Summary CCB makes Condor work if You have one-way connectivity Fine Print: And using Condor 7.3+ And the private side sets CCB_ADDRESS And the private side is authorized at the DAEMON authorization level by CCB And the public side can connect to CCB And the public side is authorized at the READ authorization level by CCB And not using standard universe
An update on the scalability limits of the Condor batch system
 An update on the scalability limits of the Condor batch system D Bradley 1, T St Clair 1, M Farrellee 1, Z Guo 1, M Livny 1, I Sfiligoi 2, T Tannenbaum 1 1 University of Wisconsin, Madison, WI, USA 2 University
An update on the scalability limits of the Condor batch system D Bradley 1, T St Clair 1, M Farrellee 1, Z Guo 1, M Livny 1, I Sfiligoi 2, T Tannenbaum 1 1 University of Wisconsin, Madison, WI, USA 2 University
What s new in Condor? What s c Condor Week 2010
 What s new in Condor? What s c Condor Week 2010 Condor Project Computer Sciences Department University of Wisconsin-Madison What s new in Condor? What s coming up? Condor Week 2010 Condor Project Computer
What s new in Condor? What s c Condor Week 2010 Condor Project Computer Sciences Department University of Wisconsin-Madison What s new in Condor? What s coming up? Condor Week 2010 Condor Project Computer
glideinwms Frontend Installation
 glideinwms Training @ UCSD glideinwms Frontend Installation Part 1 Condor Installation by Igor Sfiligoi (UCSD) UCSD Jan 17th 2012 Condor Install 1 Overview Introduction Planning and Common setup Central
glideinwms Training @ UCSD glideinwms Frontend Installation Part 1 Condor Installation by Igor Sfiligoi (UCSD) UCSD Jan 17th 2012 Condor Install 1 Overview Introduction Planning and Common setup Central
glideinwms UCSD Condor tunning by Igor Sfiligoi (UCSD) UCSD Jan 18th 2012 Condor Tunning 1
 glideinwms Training @ UCSD Condor tunning by Igor Sfiligoi (UCSD) UCSD Jan 18th 2012 Condor Tunning 1 Regulating User Priorities UCSD Jan 18th 2012 Condor Tunning 2 User priorities By default, the Negotiator
glideinwms Training @ UCSD Condor tunning by Igor Sfiligoi (UCSD) UCSD Jan 18th 2012 Condor Tunning 1 Regulating User Priorities UCSD Jan 18th 2012 Condor Tunning 2 User priorities By default, the Negotiator
Scalability and interoperability within glideinwms
 Journal of Physics: Conference Series Scalability and interoperability within glideinwms To cite this article: D Bradley et al 2010 J. Phys.: Conf. Ser. 219 062036 View the article online for updates and
Journal of Physics: Conference Series Scalability and interoperability within glideinwms To cite this article: D Bradley et al 2010 J. Phys.: Conf. Ser. 219 062036 View the article online for updates and
Networking and High Throughput Computing. Garhan Attebury HTCondor Week 2015
 Networking and High Throughput Computing Garhan Attebury HTCondor Week 2015 A simpler time or at least blissfully ignorant time Host A magic network cable Host B What network communication? Single host,
Networking and High Throughput Computing Garhan Attebury HTCondor Week 2015 A simpler time or at least blissfully ignorant time Host A magic network cable Host B What network communication? Single host,
glideinwms Training Glidein Internals How they work and why by Igor Sfiligoi, Jeff Dost (UCSD) glideinwms Training Glidein internals 1
 Glidein Internals How they work and why by Igor Sfiligoi, Jeff Dost (UCSD) Glidein internals 1 Refresher glidein_startup the glidein_startup script configures and starts Condor on the worker node Glidein
Glidein Internals How they work and why by Igor Sfiligoi, Jeff Dost (UCSD) Glidein internals 1 Refresher glidein_startup the glidein_startup script configures and starts Condor on the worker node Glidein
glideinwms architecture by Igor Sfiligoi, Jeff Dost (UCSD)
 glideinwms architecture by Igor Sfiligoi, Jeff Dost (UCSD) Outline A high level overview of the glideinwms Description of the components 2 glideinwms from 10k feet 3 Refresher - HTCondor A Condor pool
glideinwms architecture by Igor Sfiligoi, Jeff Dost (UCSD) Outline A high level overview of the glideinwms Description of the components 2 glideinwms from 10k feet 3 Refresher - HTCondor A Condor pool
Shooting for the sky: Testing the limits of condor. HTCondor Week May 2015 Edgar Fajardo On behalf of OSG Software and Technology
 Shooting for the sky: Testing the limits of condor 21 May 2015 Edgar Fajardo On behalf of OSG Software and Technology 1 Acknowledgement Although I am the one presenting. This work is a product of a collaborative
Shooting for the sky: Testing the limits of condor 21 May 2015 Edgar Fajardo On behalf of OSG Software and Technology 1 Acknowledgement Although I am the one presenting. This work is a product of a collaborative
HTCondor overview. by Igor Sfiligoi, Jeff Dost (UCSD)
 HTCondor overview by Igor Sfiligoi, Jeff Dost (UCSD) Acknowledgement These slides are heavily based on the presentation Todd Tannenbaum gave at CERN in Feb 2011 https://indico.cern.ch/event/124982/timetable/#20110214.detailed
HTCondor overview by Igor Sfiligoi, Jeff Dost (UCSD) Acknowledgement These slides are heavily based on the presentation Todd Tannenbaum gave at CERN in Feb 2011 https://indico.cern.ch/event/124982/timetable/#20110214.detailed
Corral: A Glide-in Based Service for Resource Provisioning
 : A Glide-in Based Service for Resource Provisioning Gideon Juve USC Information Sciences Institute juve@usc.edu Outline Throughput Applications Grid Computing Multi-level scheduling and Glideins Example:
: A Glide-in Based Service for Resource Provisioning Gideon Juve USC Information Sciences Institute juve@usc.edu Outline Throughput Applications Grid Computing Multi-level scheduling and Glideins Example:
CMS experience of running glideinwms in High Availability mode
 CMS experience of running glideinwms in High Availability mode I Sfiligoi 1, J Letts 1, S Belforte 2, A McCrea 1, K Larson 3, M Zvada 4, B Holzman 3, P Mhashilkar 3, D C Bradley 5, M D Saiz Santos 1, F
CMS experience of running glideinwms in High Availability mode I Sfiligoi 1, J Letts 1, S Belforte 2, A McCrea 1, K Larson 3, M Zvada 4, B Holzman 3, P Mhashilkar 3, D C Bradley 5, M D Saiz Santos 1, F
Securing A Basic HTCondor Pool
 Securing A Basic HTCondor Pool Basic Concepts You have an HTCondor pool Personal HTCondor (1 node) 1000 node cluster Who can use your pool? Basic Concepts Who can use it is really two concepts: The Who
Securing A Basic HTCondor Pool Basic Concepts You have an HTCondor pool Personal HTCondor (1 node) 1000 node cluster Who can use your pool? Basic Concepts Who can use it is really two concepts: The Who
Building Campus HTC Sharing Infrastructures. Derek Weitzel University of Nebraska Lincoln (Open Science Grid Hat)
 Building Campus HTC Sharing Infrastructures Derek Weitzel University of Nebraska Lincoln (Open Science Grid Hat) HCC: Campus Grids Motivation We have 3 clusters in 2 cities. Our largest (4400 cores) is
Building Campus HTC Sharing Infrastructures Derek Weitzel University of Nebraska Lincoln (Open Science Grid Hat) HCC: Campus Grids Motivation We have 3 clusters in 2 cities. Our largest (4400 cores) is
Configuring a glideinwms factory
 GlideinWMS Training @ UCSD Configuring a glideinwms factory by Igor Sfiligoi (UCSD) UCSD Nov 8th Factory configuration 1 Refresher Glidein factory The glidein factory knows about the sites and does the
GlideinWMS Training @ UCSD Configuring a glideinwms factory by Igor Sfiligoi (UCSD) UCSD Nov 8th Factory configuration 1 Refresher Glidein factory The glidein factory knows about the sites and does the
Care and Feeding of HTCondor Cluster. Steven Timm European HTCondor Site Admins Meeting 8 December 2014
 Care and Feeding of HTCondor Cluster Steven Timm European HTCondor Site Admins Meeting 8 December 2014 Disclaimer Some HTCondor configuration and operations questions are more religion than science. There
Care and Feeding of HTCondor Cluster Steven Timm European HTCondor Site Admins Meeting 8 December 2014 Disclaimer Some HTCondor configuration and operations questions are more religion than science. There
Routing in the Internet
 Routing in the Internet Daniel Zappala CS 460 Computer Networking Brigham Young University Scaling Routing for the Internet 2/29 scale 200 million destinations - can t store all destinations or all prefixes
Routing in the Internet Daniel Zappala CS 460 Computer Networking Brigham Young University Scaling Routing for the Internet 2/29 scale 200 million destinations - can t store all destinations or all prefixes
Introducing the HTCondor-CE
 Introducing the HTCondor-CE CHEP 2015 Presented by Edgar Fajardo 1 Introduction In summer 2012, OSG performed an internal review of major software components, looking for strategic weaknesses. One highlighted
Introducing the HTCondor-CE CHEP 2015 Presented by Edgar Fajardo 1 Introduction In summer 2012, OSG performed an internal review of major software components, looking for strategic weaknesses. One highlighted
Containerized Cloud Scheduling Environment
 University of Victoria Engineering & Computer Science Co-op Work Term Report Fall 2017 Containerized Cloud Scheduling Environment Department of Physics University of Victoria Victoria, BC Tahya Weiss-Gibbons
University of Victoria Engineering & Computer Science Co-op Work Term Report Fall 2017 Containerized Cloud Scheduling Environment Department of Physics University of Victoria Victoria, BC Tahya Weiss-Gibbons
How to Create a TINA VPN Tunnel between F- Series Firewalls
 How to Create a TINA VPN Tunnel between F- Series Firewalls As the TINA protocol offers significant advantages over IPsec, it is the main protocol that is used for VPN connections between F-Series Firewalls.
How to Create a TINA VPN Tunnel between F- Series Firewalls As the TINA protocol offers significant advantages over IPsec, it is the main protocol that is used for VPN connections between F-Series Firewalls.
View4.6 PCoIP Secure Gateway FAQs.
 View4.6 PCoIP Secure Gateway FAQs npeter@vmware.com Contents 1. How can I get PCoIP Secure Gateway functionality... 3 2. Is PCoIP Secure Gateway enabled by default once I install connection server or security
View4.6 PCoIP Secure Gateway FAQs npeter@vmware.com Contents 1. How can I get PCoIP Secure Gateway functionality... 3 2. Is PCoIP Secure Gateway enabled by default once I install connection server or security
glideinwms: Quick Facts
 glideinwms: Quick Facts glideinwms is an open-source Fermilab Computing Sector product driven by CMS Heavy reliance on HTCondor from UW Madison and we work closely with them http://tinyurl.com/glideinwms
glideinwms: Quick Facts glideinwms is an open-source Fermilab Computing Sector product driven by CMS Heavy reliance on HTCondor from UW Madison and we work closely with them http://tinyurl.com/glideinwms
Factory Ops Site Debugging
 Factory Ops Site Debugging This talk shows detailed examples of how we debug site problems By Jeff Dost (UCSD) Factory Ops Site Debugging 1 Overview Validation Rundiff Held Waiting Pending Unmatched Factory
Factory Ops Site Debugging This talk shows detailed examples of how we debug site problems By Jeff Dost (UCSD) Factory Ops Site Debugging 1 Overview Validation Rundiff Held Waiting Pending Unmatched Factory
What s new in HTCondor? What s coming? HTCondor Week 2018 Madison, WI -- May 22, 2018
 What s new in HTCondor? What s coming? HTCondor Week 2018 Madison, WI -- May 22, 2018 Todd Tannenbaum Center for High Throughput Computing Department of Computer Sciences University of Wisconsin-Madison
What s new in HTCondor? What s coming? HTCondor Week 2018 Madison, WI -- May 22, 2018 Todd Tannenbaum Center for High Throughput Computing Department of Computer Sciences University of Wisconsin-Madison
Routing. Info 341 Networking and Distributed Applications. Addresses, fragmentation, reassembly. end-to-end communication UDP, TCP
 outing Info 341 Networking and Distributed Applications Context Layer 3 Addresses, fragmentation, reassembly Layer 4 end-to-end communication UDP, TCP outing At layer 3 Often relies on layer 4 Application
outing Info 341 Networking and Distributed Applications Context Layer 3 Addresses, fragmentation, reassembly Layer 4 end-to-end communication UDP, TCP outing At layer 3 Often relies on layer 4 Application
Proxy Protocol Support for Sophos UTM on AWS. Sophos XG Firewall How to Configure VPN Connections for Azure
 Proxy Protocol Support for Sophos UTM on AWS Sophos XG Firewall How to Configure VPN Connections for Azure Document date: April 2017 1 Contents 1 Overview... 3 2 Azure Virtual Network and VPN Gateway...
Proxy Protocol Support for Sophos UTM on AWS Sophos XG Firewall How to Configure VPN Connections for Azure Document date: April 2017 1 Contents 1 Overview... 3 2 Azure Virtual Network and VPN Gateway...
One Pool To Rule Them All The CMS HTCondor/glideinWMS Global Pool. D. Mason for CMS Software & Computing
 One Pool To Rule Them All The CMS HTCondor/glideinWMS Global Pool D. Mason for CMS Software & Computing 1 Going to try to give you a picture of the CMS HTCondor/ glideinwms global pool What s the use case
One Pool To Rule Them All The CMS HTCondor/glideinWMS Global Pool D. Mason for CMS Software & Computing 1 Going to try to give you a picture of the CMS HTCondor/ glideinwms global pool What s the use case
Case 1: VPN direction from Vigor2130 to Vigor2820
 LAN to LAN IPSec VPN between Vigor2130 and Vigor2820 using Aggressive mode In this document we will introduce how to create a LAN to LAN IPSec VPN between Vigor2130 and a Vigor2820 using Aggressive mode.
LAN to LAN IPSec VPN between Vigor2130 and Vigor2820 using Aggressive mode In this document we will introduce how to create a LAN to LAN IPSec VPN between Vigor2130 and a Vigor2820 using Aggressive mode.
Homepage. My Internet Connection No internet access, unstable or slow connection or unable to browse.
 Homepage Help me resolve a problem with My Internet Connection No internet access, unstable or slow connection or unable to browse. My Wi-Fi Setup my Wi-Fi or unable to connect. Change Wi-Fi Name/Password
Homepage Help me resolve a problem with My Internet Connection No internet access, unstable or slow connection or unable to browse. My Wi-Fi Setup my Wi-Fi or unable to connect. Change Wi-Fi Name/Password
What s new in Condor? What s coming? Condor Week 2011
 What s new in Condor? What s coming? Condor Week 2011 Condor Project Computer Sciences Department University of Wisconsin-Madison The Condor Torpedo of TRUTH Talk Condor Project Computer Sciences Department
What s new in Condor? What s coming? Condor Week 2011 Condor Project Computer Sciences Department University of Wisconsin-Madison The Condor Torpedo of TRUTH Talk Condor Project Computer Sciences Department
Example File Systems Using Replication CS 188 Distributed Systems February 10, 2015
 Example File Systems Using Replication CS 188 Distributed Systems February 10, 2015 Page 1 Example Replicated File Systems NFS Coda Ficus Page 2 NFS Originally NFS did not have any replication capability
Example File Systems Using Replication CS 188 Distributed Systems February 10, 2015 Page 1 Example Replicated File Systems NFS Coda Ficus Page 2 NFS Originally NFS did not have any replication capability
Look What I Can Do: Unorthodox Uses of HTCondor in the Open Science Grid
 Look What I Can Do: Unorthodox Uses of HTCondor in the Open Science Grid Mátyás Selmeci Open Science Grid Software Team / Center for High- Throughput Computing HTCondor Week 2015 More Than a Batch System
Look What I Can Do: Unorthodox Uses of HTCondor in the Open Science Grid Mátyás Selmeci Open Science Grid Software Team / Center for High- Throughput Computing HTCondor Week 2015 More Than a Batch System
Condor and BOINC. Distributed and Volunteer Computing. Presented by Adam Bazinet
 Condor and BOINC Distributed and Volunteer Computing Presented by Adam Bazinet Condor Developed at the University of Wisconsin-Madison Condor is aimed at High Throughput Computing (HTC) on collections
Condor and BOINC Distributed and Volunteer Computing Presented by Adam Bazinet Condor Developed at the University of Wisconsin-Madison Condor is aimed at High Throughput Computing (HTC) on collections
Using Double-Take in a Network Address Translation (NAT) Environment
 Using Double-Take in a Network Address Translation (NAT) Environment Using Double-Take in a Network Address Translation (NAT) Environment published October 2002 NSI and Double-Take are registered trademarks
Using Double-Take in a Network Address Translation (NAT) Environment Using Double-Take in a Network Address Translation (NAT) Environment published October 2002 NSI and Double-Take are registered trademarks
CHTC Policy and Configuration. Greg Thain HTCondor Week 2017
 CHTC Policy and Configuration Greg Thain HTCondor Week 2017 Image credit: flickr user shanelin cc Image credit: wikipedia CHTC Pool Mission CHTC Pool Mission To improve computational research on campus
CHTC Policy and Configuration Greg Thain HTCondor Week 2017 Image credit: flickr user shanelin cc Image credit: wikipedia CHTC Pool Mission CHTC Pool Mission To improve computational research on campus
On-demand target, up and running
 On-demand target, up and running ii On-demand target, up and running Contents Chapter 1. Assumptions........ 1 Chapter 2. Overview......... 3 Chapter 3. Component purpose.... 5 Chapter 5. Starting a session
On-demand target, up and running ii On-demand target, up and running Contents Chapter 1. Assumptions........ 1 Chapter 2. Overview......... 3 Chapter 3. Component purpose.... 5 Chapter 5. Starting a session
Creation of a physical Standby Database using OEM GC
 Creation of a physical Standby Database using OEM GC Author: Rob Zoeteweij Date: July 19, 2010 http://oemgc.wordpress.com In this paper I will show how easy it is to create a physical Standby Database.
Creation of a physical Standby Database using OEM GC Author: Rob Zoeteweij Date: July 19, 2010 http://oemgc.wordpress.com In this paper I will show how easy it is to create a physical Standby Database.
Advanced option settings on the command line. Set the interface and ports for the OpenVPN daemons
 Advanced option settings on the command line docs.openvpn.net/command-line/advanced-option-settings-on-the-command-line Set the interface and ports for the OpenVPN daemons In the Admin UI under Server
Advanced option settings on the command line docs.openvpn.net/command-line/advanced-option-settings-on-the-command-line Set the interface and ports for the OpenVPN daemons In the Admin UI under Server
Flying HTCondor at 100gbps Over the Golden State
 Flying HTCondor at 100gbps Over the Golden State Jeff Dost (UCSD) HTCondor Week 2016 1 What is PRP? Pacific Research Platform: - 100 gbit network extending from Southern California to Washington - Interconnects
Flying HTCondor at 100gbps Over the Golden State Jeff Dost (UCSD) HTCondor Week 2016 1 What is PRP? Pacific Research Platform: - 100 gbit network extending from Southern California to Washington - Interconnects
Deploying and Provisioning the Barracuda CloudGen WAF in the Classic Microsoft Azure Management Portal
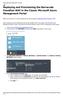 Deploying and Provisioning the Barracuda CloudGen WAF in the Classic Microsoft Azure Management Portal Before you proceed, it is recommended that you go through the Deployment Best Practices article. Before
Deploying and Provisioning the Barracuda CloudGen WAF in the Classic Microsoft Azure Management Portal Before you proceed, it is recommended that you go through the Deployment Best Practices article. Before
Configuring Advanced Firewall Settings
 Configuring Advanced Firewall Settings This section provides advanced firewall settings for configuring detection prevention, dynamic ports, source routed packets, connection selection, and access rule
Configuring Advanced Firewall Settings This section provides advanced firewall settings for configuring detection prevention, dynamic ports, source routed packets, connection selection, and access rule
Practical Magic with SSH. By David F. Skoll Roaring Penguin Software Inc. 1 February
 Practical Magic with SSH By David F. Skoll Roaring Penguin Software Inc. 1 February 2001 http://www.roaringpenguin.com dfs@roaringpenguin.com Overview of Presentation Why SSH? Problems with Telnet & Friends
Practical Magic with SSH By David F. Skoll Roaring Penguin Software Inc. 1 February 2001 http://www.roaringpenguin.com dfs@roaringpenguin.com Overview of Presentation Why SSH? Problems with Telnet & Friends
UNIT 5 MANAGING COMPUTER NETWORKS LEVEL 3 NETWORK PROTOCOLS
 UNIT 5 MANAGING COMPUTER NETWORKS LEVEL 3 NETWORK PROTOCOLS NETWORK PROTOCOLS A network manager needs to be aware of a number of different protocols, especially those that exist in the Application Layer
UNIT 5 MANAGING COMPUTER NETWORKS LEVEL 3 NETWORK PROTOCOLS NETWORK PROTOCOLS A network manager needs to be aware of a number of different protocols, especially those that exist in the Application Layer
Recovering Internet Symmetry in Distributed Computing
 Recovering Internet Symmetry in Distributed Computing Sechang Son and Miron Livny Computer Science Department, University of Wisconsin {sschang, miron}@cs.wisc.edu Abstract This paper describes two systems
Recovering Internet Symmetry in Distributed Computing Sechang Son and Miron Livny Computer Science Department, University of Wisconsin {sschang, miron}@cs.wisc.edu Abstract This paper describes two systems
SANGFOR WANO POC Guideline
 SANGFOR WANO POC Guideline 1. The preparation before the testing and deployment The network environment checklist URL:http://sangforserver.no-ip.org/cms/uploads/soft/130920/SANGFORIAM_PrePOCche cklist_v201309.xlsx
SANGFOR WANO POC Guideline 1. The preparation before the testing and deployment The network environment checklist URL:http://sangforserver.no-ip.org/cms/uploads/soft/130920/SANGFORIAM_PrePOCche cklist_v201309.xlsx
Connecting Restricted, High-Availability, or Low-Latency Resources to a Seamless Global Pool for CMS
 Journal of Physics: Conference Series PAPER OPEN ACCESS Connecting Restricted, High-Availability, or Low-Latency Resources to a Seamless Global Pool for CMS To cite this article: J Balcas et al 2017 J.
Journal of Physics: Conference Series PAPER OPEN ACCESS Connecting Restricted, High-Availability, or Low-Latency Resources to a Seamless Global Pool for CMS To cite this article: J Balcas et al 2017 J.
the Corba/Java Firewall
 Firewall Security for Corba and J2EE/EJB with the IIOP Domain Boundary Controller Corba and Java-RMI based applications can be directly and securely made accessible to users outside the internal network,
Firewall Security for Corba and J2EE/EJB with the IIOP Domain Boundary Controller Corba and Java-RMI based applications can be directly and securely made accessible to users outside the internal network,
Cisco Expressway with Jabber Guest
 Cisco Expressway with Jabber Guest Deployment Guide First Published: Decemeber 2016 Cisco Expressway X8.9 Cisco Jabber Guest Server 10.6.9 (or later) Cisco Systems, Inc. www.cisco.com Contents Preface
Cisco Expressway with Jabber Guest Deployment Guide First Published: Decemeber 2016 Cisco Expressway X8.9 Cisco Jabber Guest Server 10.6.9 (or later) Cisco Systems, Inc. www.cisco.com Contents Preface
PrepAwayExam. High-efficient Exam Materials are the best high pass-rate Exam Dumps
 PrepAwayExam http://www.prepawayexam.com/ High-efficient Exam Materials are the best high pass-rate Exam Dumps Exam : 250-530 Title : Administration of Symantec Network Access Control 12.1 Vendors : Symantec
PrepAwayExam http://www.prepawayexam.com/ High-efficient Exam Materials are the best high pass-rate Exam Dumps Exam : 250-530 Title : Administration of Symantec Network Access Control 12.1 Vendors : Symantec
How to Configure a Client-to-Site L2TP/IPsec VPN
 Follow the instructions in this article to configure a client-to-site L2TP/IPsec VPN. With this configuration, IPsec encrypts the payload data of the VPN because L2TP does not provide encryption. In this
Follow the instructions in this article to configure a client-to-site L2TP/IPsec VPN. With this configuration, IPsec encrypts the payload data of the VPN because L2TP does not provide encryption. In this
Configuring NAT for IP Address Conservation
 This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about
This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about
Chapter 4: Network Layer
 Chapter 4: Network Layer 4. 1 Introduction 4.2 Virtual circuit and datagram networks 4.3 What s inside a router 4.4 IP: Internet Protocol Datagram format IPv4 addressing ICMP IPv6 4.5 Routing algorithms
Chapter 4: Network Layer 4. 1 Introduction 4.2 Virtual circuit and datagram networks 4.3 What s inside a router 4.4 IP: Internet Protocol Datagram format IPv4 addressing ICMP IPv6 4.5 Routing algorithms
Finding Feature Information
 This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about
This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about
How to Configure a Dynamic Mesh VPN with the GTI Editor
 How to Configure a Dynamic Mesh VPN with the GTI Editor The GTI editor greatly simplifies creating a dynamic mesh VPN network with a large number of NextGen F- Series Firewalls. You can enable dynamic
How to Configure a Dynamic Mesh VPN with the GTI Editor The GTI editor greatly simplifies creating a dynamic mesh VPN network with a large number of NextGen F- Series Firewalls. You can enable dynamic
First Principles Vulnerability Assessment. Motivation
 First Principles Vulnerability Assessment James A. Kupsch Barton P. Miller Computer Sciences Department University of Wisconsin Elisa Heymann Eduardo César Computer Architecture and Operating Systems Department
First Principles Vulnerability Assessment James A. Kupsch Barton P. Miller Computer Sciences Department University of Wisconsin Elisa Heymann Eduardo César Computer Architecture and Operating Systems Department
Cassia MQTT User Guide
 Cassia MQTT User Guide Contents 1. Introduction... 2 1.1. Client and Broker... 2 1.2. MQTT Connection... 2 1.3. Cassia MQTT Bypass Mode... 3 2. Settings on MQTT Server/Broker... 4 2.1. Configuration Files...
Cassia MQTT User Guide Contents 1. Introduction... 2 1.1. Client and Broker... 2 1.2. MQTT Connection... 2 1.3. Cassia MQTT Bypass Mode... 3 2. Settings on MQTT Server/Broker... 4 2.1. Configuration Files...
3. In the upper left hand corner, click the Barracuda logo ( ) then click Settings 4. Select the check box for SPoE as default.
 Week 1 Lab Lab 1: Connect to the Barracuda network. 1. Download the Barracuda NG Firewall Admin 5.4 2. Launch NG Admin 3. In the upper left hand corner, click the Barracuda logo ( ) then click Settings
Week 1 Lab Lab 1: Connect to the Barracuda network. 1. Download the Barracuda NG Firewall Admin 5.4 2. Launch NG Admin 3. In the upper left hand corner, click the Barracuda logo ( ) then click Settings
Install a LensMechanix network license
 Install a LensMechanix network license This article explains how to install a network license for LensMechanix. For instructions on how to install a single-user license for LensMechanix, see Activate a
Install a LensMechanix network license This article explains how to install a network license for LensMechanix. For instructions on how to install a single-user license for LensMechanix, see Activate a
VNS3 3.5 Container System Add-Ons
 VNS3 3.5 Container System Add-Ons Instructions for VNS3 2015 copyright 2015 1 Table of Contents Introduction 3 Docker Container Network 7 Uploading a Image or Dockerfile 9 Allocating a Container 13 Saving
VNS3 3.5 Container System Add-Ons Instructions for VNS3 2015 copyright 2015 1 Table of Contents Introduction 3 Docker Container Network 7 Uploading a Image or Dockerfile 9 Allocating a Container 13 Saving
Chapter 4: outline. Network Layer 4-1
 Chapter 4: outline 4.1 introduction 4.2 virtual circuit and datagram networks 4.3 what s inside a router 4.4 IP: Internet Protocol datagram format IPv4 addressing ICMP IPv6 4.5 routing algorithms link
Chapter 4: outline 4.1 introduction 4.2 virtual circuit and datagram networks 4.3 what s inside a router 4.4 IP: Internet Protocol datagram format IPv4 addressing ICMP IPv6 4.5 routing algorithms link
Load Balancing For Clustered Barracuda CloudGen WAF Instances in the New Microsoft Azure Management Portal
 Load Balancing For Clustered Barracuda CloudGen WAF Instances in the New Microsoft Azure Management This guide will walk you through the steps to load balance traffic across multiple instances of the Barracuda
Load Balancing For Clustered Barracuda CloudGen WAF Instances in the New Microsoft Azure Management This guide will walk you through the steps to load balance traffic across multiple instances of the Barracuda
Autonomic Condor Clouds. David Wolinsky ACIS P2P Group University of Florida
 Autonomic Condor Clouds David Wolinsky ACIS P2P Group University of Florida So What's the Big Deal Support connectivity across the Internet, in constrained locations, and with clouds Simplify packaging
Autonomic Condor Clouds David Wolinsky ACIS P2P Group University of Florida So What's the Big Deal Support connectivity across the Internet, in constrained locations, and with clouds Simplify packaging
Cloud Computing with HTCondor
 Cloud Computing with HTCondor Background At the University of Liverpool, the Advanced Research Computing team support a variety of research computing facilities including two HPC clusters and a high throughput
Cloud Computing with HTCondor Background At the University of Liverpool, the Advanced Research Computing team support a variety of research computing facilities including two HPC clusters and a high throughput
How to disable VPN block on Windows Firewall
 How to disable VPN block on Windows Firewall You may have experienced VPN block issues by Windows firewall, usually it s a default setting, but there s always a way to get around it and get connected again.
How to disable VPN block on Windows Firewall You may have experienced VPN block issues by Windows firewall, usually it s a default setting, but there s always a way to get around it and get connected again.
First evaluation of the Globus GRAM Service. Massimo Sgaravatto INFN Padova
 First evaluation of the Globus GRAM Service Massimo Sgaravatto INFN Padova massimo.sgaravatto@pd.infn.it Draft version release 1.0.5 20 June 2000 1 Introduction...... 3 2 Running jobs... 3 2.1 Usage examples.
First evaluation of the Globus GRAM Service Massimo Sgaravatto INFN Padova massimo.sgaravatto@pd.infn.it Draft version release 1.0.5 20 June 2000 1 Introduction...... 3 2 Running jobs... 3 2.1 Usage examples.
RSA NetWitness Platform
 RSA NetWitness Platform Event Source Log Configuration Guide Check Point Security Suite, IPS-1 Last Modified: Wednesday, May 9, 2018 Event Source Product Information: Vendor: Check Point Event Source:
RSA NetWitness Platform Event Source Log Configuration Guide Check Point Security Suite, IPS-1 Last Modified: Wednesday, May 9, 2018 Event Source Product Information: Vendor: Check Point Event Source:
Grid Computing Fall 2005 Lecture 5: Grid Architecture and Globus. Gabrielle Allen
 Grid Computing 7700 Fall 2005 Lecture 5: Grid Architecture and Globus Gabrielle Allen allen@bit.csc.lsu.edu http://www.cct.lsu.edu/~gallen Concrete Example I have a source file Main.F on machine A, an
Grid Computing 7700 Fall 2005 Lecture 5: Grid Architecture and Globus Gabrielle Allen allen@bit.csc.lsu.edu http://www.cct.lsu.edu/~gallen Concrete Example I have a source file Main.F on machine A, an
CS 43: Computer Networks Internet Routing. Kevin Webb Swarthmore College November 16, 2017
 CS 43: Computer Networks Internet Routing Kevin Webb Swarthmore College November 16, 2017 1 Hierarchical routing Our routing study thus far - idealization all routers identical network flat not true in
CS 43: Computer Networks Internet Routing Kevin Webb Swarthmore College November 16, 2017 1 Hierarchical routing Our routing study thus far - idealization all routers identical network flat not true in
BOSCO Architecture. Derek Weitzel University of Nebraska Lincoln
 BOSCO Architecture Derek Weitzel University of Nebraska Lincoln Goals We want an easy to use method for users to do computational research It should be easy to install, use, and maintain It should be simple
BOSCO Architecture Derek Weitzel University of Nebraska Lincoln Goals We want an easy to use method for users to do computational research It should be easy to install, use, and maintain It should be simple
How to Configure Route 53 for F-Series Firewalls in AWS
 How to Configure Route 53 for F-Series Firewalls in AWS If you are running multiple stacks in different AWS regions, or multiple deployments in a single region, you must configure AWS Route 53 to access
How to Configure Route 53 for F-Series Firewalls in AWS If you are running multiple stacks in different AWS regions, or multiple deployments in a single region, you must configure AWS Route 53 to access
050-v71x-CSESECURID RSA. RSA SecurID Certified Systems Engineer 7.1x
 RSA 050-v71x-CSESECURID RSA SecurID Certified Systems Engineer 7.1x Download Full Version : http://killexams.com/pass4sure/exam-detail/050-v71x-csesecurid QUESTION: 61 What default ports need to be opened
RSA 050-v71x-CSESECURID RSA SecurID Certified Systems Engineer 7.1x Download Full Version : http://killexams.com/pass4sure/exam-detail/050-v71x-csesecurid QUESTION: 61 What default ports need to be opened
Why dynamic route? (1)
 Routing Why dynamic route? (1) Static route is ok only when Network is small There is a single connection point to other network No redundant route 2 Why dynamic route? (2) Dynamic Routing Routers update
Routing Why dynamic route? (1) Static route is ok only when Network is small There is a single connection point to other network No redundant route 2 Why dynamic route? (2) Dynamic Routing Routers update
Tutorial 4: Condor. John Watt, National e-science Centre
 Tutorial 4: Condor John Watt, National e-science Centre Tutorials Timetable Week Day/Time Topic Staff 3 Fri 11am Introduction to Globus J.W. 4 Fri 11am Globus Development J.W. 5 Fri 11am Globus Development
Tutorial 4: Condor John Watt, National e-science Centre Tutorials Timetable Week Day/Time Topic Staff 3 Fri 11am Introduction to Globus J.W. 4 Fri 11am Globus Development J.W. 5 Fri 11am Globus Development
CSCE 463/612 Networks and Distributed Processing Spring 2018
 CSCE 463/612 Networks and Distributed Processing Spring 2018 Network Layer IV Dmitri Loguinov Texas A&M University April 12, 2018 Original slides copyright 1996-2004 J.F Kurose and K.W. Ross 1 Chapter
CSCE 463/612 Networks and Distributed Processing Spring 2018 Network Layer IV Dmitri Loguinov Texas A&M University April 12, 2018 Original slides copyright 1996-2004 J.F Kurose and K.W. Ross 1 Chapter
Grid Compute Resources and Grid Job Management
 Grid Compute Resources and Job Management March 24-25, 2007 Grid Job Management 1 Job and compute resource management! This module is about running jobs on remote compute resources March 24-25, 2007 Grid
Grid Compute Resources and Job Management March 24-25, 2007 Grid Job Management 1 Job and compute resource management! This module is about running jobs on remote compute resources March 24-25, 2007 Grid
How to Configure Guest Access with the Ticketing System
 How to Configure Guest Access with the Ticketing System Set up a login or ticketing system to temporarily grant access to guest users. Ticketing admins assign guest tickets to the users. The user credentials
How to Configure Guest Access with the Ticketing System Set up a login or ticketing system to temporarily grant access to guest users. Ticketing admins assign guest tickets to the users. The user credentials
Intro to LAN/WAN. Transport Layer
 Intro to LAN/WAN Transport Layer Transport Layer Topics Introduction (6.1) Elements of Transport Protocols (6.2) Internet Transport Protocols: TDP (6.5) Internet Transport Protocols: UDP (6.4) socket interface
Intro to LAN/WAN Transport Layer Transport Layer Topics Introduction (6.1) Elements of Transport Protocols (6.2) Internet Transport Protocols: TDP (6.5) Internet Transport Protocols: UDP (6.4) socket interface
High Availability Options
 , on page 1 Load Balancing, on page 2 Distributed VPN Clustering, Load balancing and Failover are high-availability features that function differently and have different requirements. In some circumstances
, on page 1 Load Balancing, on page 2 Distributed VPN Clustering, Load balancing and Failover are high-availability features that function differently and have different requirements. In some circumstances
Chapter 4: Network Layer. Lecture 12 Internet Routing Protocols. Chapter goals: understand principles behind network layer services:
 NET 331 Computer Networks Lecture 12 Internet Routing Protocols Dr. Anis Koubaa Reformatted slides from textbook Computer Networking a top-down appraoch, Fifth Edition by Kurose and Ross, (c) Pearson Education
NET 331 Computer Networks Lecture 12 Internet Routing Protocols Dr. Anis Koubaa Reformatted slides from textbook Computer Networking a top-down appraoch, Fifth Edition by Kurose and Ross, (c) Pearson Education
Cisco AnyConnect Secure Mobility Solution. György Ács Regional Security Consultant
 Cisco AnyConnect Secure Mobility Solution György Ács Regional Security Consultant Mobile User Challenges Mobile and Security Services Web Security Deployment Methods Live Q&A 2011 Cisco and/or its affiliates.
Cisco AnyConnect Secure Mobility Solution György Ács Regional Security Consultant Mobile User Challenges Mobile and Security Services Web Security Deployment Methods Live Q&A 2011 Cisco and/or its affiliates.
PROOF-Condor integration for ATLAS
 PROOF-Condor integration for ATLAS G. Ganis,, J. Iwaszkiewicz, F. Rademakers CERN / PH-SFT M. Livny, B. Mellado, Neng Xu,, Sau Lan Wu University Of Wisconsin Condor Week, Madison, 29 Apr 2 May 2008 Outline
PROOF-Condor integration for ATLAS G. Ganis,, J. Iwaszkiewicz, F. Rademakers CERN / PH-SFT M. Livny, B. Mellado, Neng Xu,, Sau Lan Wu University Of Wisconsin Condor Week, Madison, 29 Apr 2 May 2008 Outline
Foreword xxiii Preface xxvii IPv6 Rationale and Features
 Contents Foreword Preface xxiii xxvii 1 IPv6 Rationale and Features 1 1.1 Internet Growth 1 1.1.1 IPv4 Addressing 1 1.1.2 IPv4 Address Space Utilization 3 1.1.3 Network Address Translation 5 1.1.4 HTTP
Contents Foreword Preface xxiii xxvii 1 IPv6 Rationale and Features 1 1.1 Internet Growth 1 1.1.1 IPv4 Addressing 1 1.1.2 IPv4 Address Space Utilization 3 1.1.3 Network Address Translation 5 1.1.4 HTTP
Design of a Simple, Distributed Network Access Control System
 1 Design of a Simple, Distributed Network Access Control System By David Boen, Daniel Dent, Victor Chan, Andrew Tjia Abstract Network access control describes the measures used to control network nodes
1 Design of a Simple, Distributed Network Access Control System By David Boen, Daniel Dent, Victor Chan, Andrew Tjia Abstract Network access control describes the measures used to control network nodes
Condor-G: HTCondor for grid submission. Jaime Frey (UW-Madison), Jeff Dost (UCSD)
 Condor-G: HTCondor for grid submission Jaime Frey (UW-Madison), Jeff Dost (UCSD) Acknowledgement These slides are heavily based on the presentation Jaime Frey gave at UCSD in Feb 2011 http://www.t2.ucsd.edu/twiki2/bin/view/main/glideinfactory1111
Condor-G: HTCondor for grid submission Jaime Frey (UW-Madison), Jeff Dost (UCSD) Acknowledgement These slides are heavily based on the presentation Jaime Frey gave at UCSD in Feb 2011 http://www.t2.ucsd.edu/twiki2/bin/view/main/glideinfactory1111
Configuring MWTM to Run with Various Networking Options
 APPENDIXH Configuring MWTM to Run with Various Networking Options In addition to running on standard IP-connected networks, the Cisco Mobile Wireless Transport Manager (MWTM) has the flexibility to adapt
APPENDIXH Configuring MWTM to Run with Various Networking Options In addition to running on standard IP-connected networks, the Cisco Mobile Wireless Transport Manager (MWTM) has the flexibility to adapt
How to Configure BGP over IKEv2 IPsec Site-to- Site VPN to an Google Cloud VPN Gateway
 How to Configure BGP over IKEv2 IPsec Site-to- Site VPN to an Google Cloud VPN Gateway To connect to the Google Cloud VPN gateway, create an IPsec IKEv2 site-to-site VPN tunnel on your F-Series Firewall
How to Configure BGP over IKEv2 IPsec Site-to- Site VPN to an Google Cloud VPN Gateway To connect to the Google Cloud VPN gateway, create an IPsec IKEv2 site-to-site VPN tunnel on your F-Series Firewall
CS475 Networks Lecture 8 Chapter 3 Internetworking. Ethernet or Wi-Fi).
 Assignments Reading for Lecture 9: Section 3.3 3.2 Basic Internetworking (IP) Bridges and LAN switches from last section have limited ability CS475 Networks Lecture 8 Chapter 3 Internetworking is a logical
Assignments Reading for Lecture 9: Section 3.3 3.2 Basic Internetworking (IP) Bridges and LAN switches from last section have limited ability CS475 Networks Lecture 8 Chapter 3 Internetworking is a logical
HTCondor: Virtualization (without Virtual Machines)
 HTCondor: Virtualization (without Virtual Machines) Brian Bockelman HTCondor Week 2013 Dictionary Definition vir tu al ize [vur-choo-uh-lahyz] verb to create a virtual version of (a computer, operating
HTCondor: Virtualization (without Virtual Machines) Brian Bockelman HTCondor Week 2013 Dictionary Definition vir tu al ize [vur-choo-uh-lahyz] verb to create a virtual version of (a computer, operating
Installing and Configuring VMware Identity Manager Connector (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.
 Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
Intercommunication between Two MyPBX (Peer to Peer Mode)
 Intercommunication between Two MyPBX (Peer to Peer Mode) Version 1.0 Yeastar Information Technology Co. Ltd. 1. Link Two MyPBX in the Same Network... 3 2. Link Two MyPBX in Different Locations... 9 2.1
Intercommunication between Two MyPBX (Peer to Peer Mode) Version 1.0 Yeastar Information Technology Co. Ltd. 1. Link Two MyPBX in the Same Network... 3 2. Link Two MyPBX in Different Locations... 9 2.1
Setting Up Windows 2K VPN Connection Through The Symantec Raptor Firewall Firewall
 Setting Up Windows 2K VPN Connection Through The Symantec Raptor Firewall Firewall By: Loc Huynh Date: 24 March 2003 Table of Contents 1.0 Foreword...2 2.0 Setting VPN on VPN Server...2 3.0 Setting Symantec
Setting Up Windows 2K VPN Connection Through The Symantec Raptor Firewall Firewall By: Loc Huynh Date: 24 March 2003 Table of Contents 1.0 Foreword...2 2.0 Setting VPN on VPN Server...2 3.0 Setting Symantec
CS 43: Computer Networks Internet Routing. Kevin Webb Swarthmore College November 14, 2013
 CS 43: Computer Networks Internet Routing Kevin Webb Swarthmore College November 14, 2013 1 Reading Quiz Hierarchical routing Our routing study thus far - idealization all routers identical network flat
CS 43: Computer Networks Internet Routing Kevin Webb Swarthmore College November 14, 2013 1 Reading Quiz Hierarchical routing Our routing study thus far - idealization all routers identical network flat
AT&T Cloud Web Security Service
 AT&T Cloud Web Security Service Troubleshooting Guide Table of Contents 1 Summary... 3 2 Explicit Proxy Access Method... 4 2.1 Explicit Proxy Flow Diagram... 4 3 Proxy Forwarding Access Method... 6 3.1
AT&T Cloud Web Security Service Troubleshooting Guide Table of Contents 1 Summary... 3 2 Explicit Proxy Access Method... 4 2.1 Explicit Proxy Flow Diagram... 4 3 Proxy Forwarding Access Method... 6 3.1
HP A5500 EI & A5500 SI Switch Series Network Management and Monitoring. Configuration Guide. Abstract
 HP A5500 EI & A5500 SI Switch Series Network Management and Monitoring Configuration Guide Abstract This document describes the software features for the HP A Series products and guides you through the
HP A5500 EI & A5500 SI Switch Series Network Management and Monitoring Configuration Guide Abstract This document describes the software features for the HP A Series products and guides you through the
How to Configure Forcepoint NGFW Route-Based VPN to AWS with BGP TECHNICAL DOCUMENT
 How to Configure Forcepoint NGFW Route-Based VPN to AWS with BGP TECHNICAL DOCUMENT Table of Contents TABLE OF CONTENTS 1 INTRODUCTION 2 AWS Configuration: 2 Forcepoint Configuration 3 APPENDIX 7 Troubleshooting
How to Configure Forcepoint NGFW Route-Based VPN to AWS with BGP TECHNICAL DOCUMENT Table of Contents TABLE OF CONTENTS 1 INTRODUCTION 2 AWS Configuration: 2 Forcepoint Configuration 3 APPENDIX 7 Troubleshooting
Avaya Port Matrix: Avaya Proprietary Use pursuant to the terms of your signed agreement or Avaya policy.
 Avaya Matrix: Release 3.0 Issue 2 April 2016 April 2016 Avaya Matrix: 3.0 1 ALL INFORMATION IS BELIEVED TO BE CORRECT AT THE TIME OF PUBLICATION AND IS PROVIDED "AS IS". AVAYA INC. DISCLAIMS ALL WARRANTIES,
Avaya Matrix: Release 3.0 Issue 2 April 2016 April 2016 Avaya Matrix: 3.0 1 ALL INFORMATION IS BELIEVED TO BE CORRECT AT THE TIME OF PUBLICATION AND IS PROVIDED "AS IS". AVAYA INC. DISCLAIMS ALL WARRANTIES,
CS 43: Computer Networks. 24: Internet Routing November 19, 2018
 CS 43: Computer Networks 24: Internet Routing November 19, 2018 Last Class Link State + Fast convergence (reacts to events quickly) + Small window of inconsistency Distance Vector + + Distributed (small
CS 43: Computer Networks 24: Internet Routing November 19, 2018 Last Class Link State + Fast convergence (reacts to events quickly) + Small window of inconsistency Distance Vector + + Distributed (small
Xrootd Monitoring for the CMS Experiment
 Journal of Physics: Conference Series Xrootd Monitoring for the CMS Experiment To cite this article: L A T Bauerdick et al 2012 J. Phys.: Conf. Ser. 396 042058 View the article online for updates and enhancements.
Journal of Physics: Conference Series Xrootd Monitoring for the CMS Experiment To cite this article: L A T Bauerdick et al 2012 J. Phys.: Conf. Ser. 396 042058 View the article online for updates and enhancements.
Computer Networking Introduction
 Computer Networking Introduction Halgurd S. Maghdid Software Engineering Department Koya University-Koya, Kurdistan-Iraq Lecture No.15 Chapter 4: outline 4.1 introduction 4.2 virtual circuit and datagram
Computer Networking Introduction Halgurd S. Maghdid Software Engineering Department Koya University-Koya, Kurdistan-Iraq Lecture No.15 Chapter 4: outline 4.1 introduction 4.2 virtual circuit and datagram
Remote Access via Cisco VPN Client
 Remote Access via Cisco VPN Client General Information This guide describes step by step the configuration of a remote access to the Astaro Security Gateway by using the Cisco VPN Client. The Cisco VPN
Remote Access via Cisco VPN Client General Information This guide describes step by step the configuration of a remote access to the Astaro Security Gateway by using the Cisco VPN Client. The Cisco VPN
