Designing an Exchange 2000/2003 Routing Group Connector Topology
|
|
|
- Sabrina Logan
- 6 years ago
- Views:
Transcription
1 Pg. 1 Designing an Exchange 2000/2003 Routing Group Connector Topology By: Craig Borysowich Chief Technology Architect Imagination Edge Inc. Version 3.7
2 BACKGROUND Large Exchange 5.5 environments use X.400 connectors to route both mail and replication traffic. Most implementations have selected a Hub and Spoke design for their X.400 topology. Most servers have an X.400 connector directly to the hub, but some sites will go through a Bridgehead X.400 connector to the Exchange routing hub. OBJECTIVE As migrations into Exchange 2000/2003 environments increase, we need to design an efficient way to route mail messages while managing overall governance. The SMTP mail routing is required for the following: 1. Within the Sites (Intra-Site), 2. Inter-Site 3. Internet Mail Microsoft Exchange 2000 enables great performance improvements with its message routing when compared to Exchange 5.5. One of the improvements is the ability to split Exchange 5.5 sites into Routing Groups and Administrative Groups. Routing Groups are based upon network topology and are designed to enhance the efficiency of message delivery. Exchange 2000 also utilizes SMTP to deliver messages as its preferred protocol instead of X.400. It is anticipated that each Exchange site or group of sites will develop a mail routing topology and strategy in concert with the rest of the Exchange sites in an organization as an integral part of the overall mail routing design. In cases where an organization has distributed management and administration of their Exchange Infrastructure, a team should be established to agree to a set of standards and a common design approach. This team should include members that are familiar with the current LAN/WAN topology, current Active Directory implementation and Design, and current Exchange 5.5 background for the organization. Page. 1
3 Exchange 2000/2003 routing basics Terminology Routing Topology The routing topology denotes the overall interconnections that multiple sites in an Exchange organization route mail between themselves and with the Internet and other foreign mail systems. Routing Group (RG) A Routing Group is the management unit in the Routing Topology focused on systems that are: always connected; connected via reliable/always available network links; configured for point-to-point connectivity Administrative Group (AG) An Administrative Group is an object management unit where the objects that can be managed include: servers, routing groups, folders, etc. The Administrative Groups can be delegated to manage any grouping of objects. So, Administrative Groups are created for managing objects. The Routing Groups are created for managing the Routing Toplogy. Routing Groups must be created within an Administrative Group they are subordinate to an Administrative Group. A single Administrative Group could contain all of the Routing Groups with other Administrative Groups managing other server and service components. Servers can be Drag & dropped between Routing Groups. Routing Group Master (RGM) Each Routing Group contains a Routing Group Master, which is the first server added to a Routing Group. The Routing Group Master Role can be changed by an administrator. The Master co-ordinates changes to the Link State information within the Routing Group. Link State Information (LST) Information about the state of messaging routes (links) in an Exchange 2000/2003 messaging system derived from the link state algorithm to quickly and frequently calculate the state of system links for up-todate status about routes. Exchange 2000 servers use link state information to make the best routing choice at the source rather than sending a message down a path where a link is not working. This eliminates message bounce and looping. Bridgehead Server (BH) The Bridgehead Server is an Exchange server that connects to other Exchange servers using the same communications protocols so information can be passed from one server to another. In Exchange 2000, a bridgehead server is a connection point from a routing group to another routing group, remote mail system, or other external mail system. Page. 2
4 Routing Group Connector (RGC) A connector that specifies the connection of a local routing group to a server in a remote routing group. It also specifies the local bridgehead server, if any, and the connection cost, schedule, and other configuration properties. All of the Bridgehead servers in a Routing Group communicate their connectivity information to the Routing Group Master, but only for changes. The Master then maintains/rebuilds the link state information and communicates it to all of the servers in the Routing Group. If the Master goes offline, then the servers continue as normal based on the last report of the Link State information received from the Master. The normal flow of mail within a Routing Group will also pass Link State Information. The Connectivity between all servers within a Routing Group is SMTP. For link state updates, Microsoft uses a proprietary binary data protocol that does not use the SMTP virtual Server. The Microsoft Exchange Routing Service handles all routing updates within the Routing Group. This service executes within the INETINFO.EXE and each Bridgehead server binds to the Master on TCP port 691 and vice versa to all servers in the Routing Group for link state updates. Connectivity between Routing Groups is via a Bridgehead server. A Simplified overview of Message routing in Exchange 2000/2003 follows: Page. 3
5 Fig 1: Simplified Message Flow for Exchange 2000/2003 Page. 4
6 The following three routing methodologies should be considered when designing a routing topology: 1. Full Mesh Topology 2. Limited Mesh Topology 3. Modified Hub & Spoke Topology. TOPOLOGY Pros Cons Full Mesh 1. While this topology offers greater efficiency of mail routing, this topology is highly dependant on the underlying network topology - If underlying Network topology is Hub-and-spoke then mesh does not add as much efficiency as it could. It does allow for redundant paths and will bypass the overhead required of the HUB to route the messages.). 2. No single point of failure 3. Most redundant topology mail routes calculated and delivered based on OSPF, dynamically modified when outages in bridgeheads occur thus taking advantage of performance characteristics. Limited Mesh Modified Huband- Spoke 1. While this topology offers greater efficiency of mail routing, this topology is highly dependant on the underlying network topology - If underlying Network topology is Hub-and-spoke then mesh does not add much efficiency as it could. It does allow for redundant paths and will bypass the overhead required of the HUB to route the messages). 2. No single point of failure 3. Semi-redundant topology- mail routed over various paths due to performance characteristics 1. Offers optimum governance in managing: a. Virus outbreaks b. Spam c. Tracing mail 2. Reduces the number of connectors from the site bridgehead server to the hub. 1. Lacks adequate governance to manage: a. virus, b. spam c. mail flow trace d. and other threats to mail environment. 2. An equal partner in mail flow and Exchange 2000 from functional perspective (Site bridgeheads could be routing other sites mail if redundant bridgeheads are not implemented for each site) 1. Moderate governance to manage: a. virus, b. spam c. mail flow trace d. and other threats to mail environment. 2. An equal partner in mail flow and Exchange 2000 from functional perspective (Site bridgeheads could be routing other sites mail if redundant bridgeheads are not implemented for each site) 1. Limited to risk to intra-site and internet mail flow if both servers became unavailable. Mail within a site would not be impacted. 2. Would require a centralized redundant environment to offer high service availability. 3. Follows old style 5.5 design models. Routing improvements in Exchange 2000/2003 should eliminate the need for this model. Page. 5
7 ROUTING GROUP TOPOLOGY RECOMMENDATION Considerations Whether you are coexisting and migrating from an existing Exchange 5.5 organization or building a new organization, you should take the following design considerations into account when selecting a topology: In native mode, Exchange 2000 can be extremely dynamic because you can change the memberships of the routing groups and administrative groups. This is useful when administration models or network topologies change. Exchange 2000 provides load balancing in the form of a round-robin DNS between servers, both sources and targets. A round-robin DNS is a mechanism that directs incoming requests to servers on a rotating basis. This is done by looping through a list of IP addresses belonging to the servers in the configuration. When an client attempts to access a mailbox on an Exchange server, the client is given the first IP address on the list. The second client request is given the second IP address in the list, and so on. If there are four servers on the round-robin list, all four IP addresses are used before the first IP address is used again, and the loop starts over. In addition, Exchange 2000 offers improvements over the Exchange 5.5 Site Connector if one of the source bridgehead servers is down Exchange connectors automatically try not to use that server until it comes back up. If there are multiple connectors with the same cost, each server picks a random connector and uses it for a period of time. Over multiple servers, this functionality simulates round-robin behaviour. When a client must use an alternate server to access public folder content, Exchange 2000 uses routing groups to calculate the closest available server, which it determines by using a cost property set on the Routing Group connector. The cost for each Routing Group connector is stored in a single cost database that is shared with routing calculations. Redundant cost tables maintained in previous versions of Exchange are eliminated. In Exchange 5.5, site affinities were not transitive. For example, if you establish an affinity between site 1 and site 2, and between site 2 and site 3, you do not automatically get affinity between site 1 and site 3. In Exchange 2000, affinities are transitive. If all routing groups in an organization are connected to allow to flow, all servers receive public folder referrals. If a server does not contain replicas of public folders, you can mark specific Routing Group connectors to deny public folder referrals; the client contacts the next server in the referral list. Because SMTP is used in a routing group and SMTP is more resilient over slow links, routing groups can span slow networks more effectively than RPC, which is the native transfer mechanism for Exchange 5.5. Thus, your organization may be able to deploy fewer routing groups by using Exchange 2000 than by using sites with Exchange 5.5. SMTP mail is not compressed; though you reduce network bandwidth requirements with SMTP, the increased load on the Exchange server CPU would reduce server performance. Unlike Exchange 5.5, where intra-site and inter-site RPC communications are encrypted, SMTP communications in Exchange 2000 are not encrypted. However, each server uses SMTP authentication with Kerberos. There are two options for encryption, although neither is done by default: Internet Protocol security (IPSec), which is built into Microsoft Windows 2000, and Transport Layer Security (TLS) encryption, which is built into the SMTP service. Upgrading an Exchange 5.5 hub, in a hub-and-spoke design, can significantly increase hub performance and stability because performance is enhanced by Exchange 2000 and the use of SMTP. Link state routing is most effective in an organization with multiple routing groups using multiple paths. In a traditional hub-and-spoke design, you do not see as much improvement as you do in a mesh network or a network with multiple connections. Page. 6
8 Adding routing groups increases the size of the link state table and increases potential link state status messages. This can increase the amount of link state message traffic. Exchange no longer includes a Dynamic RAS connector. Instead, Exchange 2000/2003 uses the on-demand capabilities in Windows 2000/2003, specifically, the combination of the Routing Group connector and the Routing and Remote Access demand-dial interface. Exchange 2003 Specifics Microsoft highlights that Exchange 2003 further improves upon the link state routing features of Exchange 2000 by reducing the amount of link state traffic in two ways. Performance is improved over what are commonly known as oscillating links, or links that are intermittently available and unavailable. Exchange 2003 reduces link state traffic by attempting to determine if the connector is oscillating. If there are multiple conflicting state changes in the link state queue for a connector in a given interval, the connector is considered an oscillating link and its link state remains up (in service or available for that period). Leaving an oscillating connector up rather than continually changing the link state reduces the amount of link state traffic that is replicated between servers. Performance is improved in the case of a site to which there is only one route. In this case, Exchange 2003 reduces link state traffic by determining that no alternate path exists and suppressing the link state information. If no alternate path exists for a link, the link state is always marked as up (in service). Exchange lets mail queue for delivery and sends it when the route becomes available. Both of these changes enhance performance because they reduce the propagation of link state information. Other than the above, there is not much in the Exchange 2003 product that would really impact your routing topology decision. Routing Group Topology Preference In evaluating the various topologies, an organization should prioritize moving to the full-mesh topology. Scaling back to the limited mesh topology if necessary, and then falling back to a 5.5 style hub/spoke topology only in the most dire of circumstances. Any perceived benefits in the hub/spoke topology to aid in combating virus or spam outbreaks are essentially mythical. In a properly designed and managed Exchange 2000/2003 environment, you should be able to halt routing in the mesh faster and more easily than in a hub/spoke implementation. Final Notes on Routing Group Connection Options Assuming that the Full Mesh Routing Group Topology that is recommended above is accepted, we must now look at how the Routing Group(RG) Connectors are going to be configured. In current X.400 connection topologies, sites have either a single or a redundant connection with the Hub, if this connection goes down, outbound messages from the site are queued locally until the connection is back up. As well inbound messages to the site are queued at the hub until the connection again becomes available. This configuration has a single point of failure to each site as well as a single point of failure at the hub. Full Mesh topology removes the need for running a hub as a single point of failure and allows for mail to find an operation route through a myriad of avenues. Remember that is a communications tool and that all parties within all Exchange sites should want mail to get to its destination. Even if that means that a few microseconds of CPU time has to be spent forwarding mail between two sites that have lost a direct connection. Page. 7
9 Fig 2: Detailed Exchange Message Flow Diagram Page. 8
10 Planning Routing Groups A routing group must consist of servers in the same forest. In fact your entire Org must be contained in the same forest. Major mail routing issues will occur if you try to split an Org between multiple forests. A permanent connection must exist between all servers participating in the same Routing Group. Servers that are on intermittent or on-demand connections must be isolated in their own Routing Group. All servers within the routing group must be able to contact the Routing Master. When you use multiple Routing Groups, you need to have connectors (i.e. bridgeheads) between two servers in those routing groups. All mail traffic being routed will go in and out through the bridgehead. You can have multiple servers in a Routing Group acting as bridgeheads to other Routing Groups. Exchange 2000/2003 will load balance the connections after a period of time and if one connection goes down, Exchange will re-select an operational route. In most cases the Routing Groups should be connected and configured as a Routing Group Connector. In cases where you are routing mail to through the Internet, then you connectors should be configured as SMTP. Only when routing to a legacy X.400 Administrative Management Domain (ADMD) or metadirectory should you use the X.400 Routing Group Connector configuration. Configuring the Routing Group Connector in RGC mode is protocol independent with SMTP native mode and RPC available for 5.5 co-existence. The connector is Directory aware for the Remote Bridgehead server. Securing Mail Routing Security for routing mail can be a big issue for many organizations. Legacy X.400 connections were obfuscated, but not encrypted. SMTP connections are not encrypted, but also obfuscated using Transport Neutral Encapsulated Format. There are two ways to secure mail routing: SMTP encryption/authentication; or using IPSec. It is highly recommended to look at using IPSec for transport security between Exchange Servers. Not only with this secure and encrypt your mail being routed between sites, but it will secure all IP-based communications between your Exchange servers. IPSec can play one of three Roles on a server: -Basic IP port filtering - like a firewall on the server -Authenticating Hosts before and during communications -Encrypting data exchanged between servers IPSec can also perform all three of these functions on a server at the same time. Page. 9
Owner of the content within this article is Written by Marc Grote
 Owner of the content within this article is www.msexchange.org Written by Marc Grote www.it-training-grote.de Exchange 2003 Mailflow Part I Written by Marc Grote - mailto:grotem@it-training-grote.de Abstract
Owner of the content within this article is www.msexchange.org Written by Marc Grote www.it-training-grote.de Exchange 2003 Mailflow Part I Written by Marc Grote - mailto:grotem@it-training-grote.de Abstract
CISNTWK-492e. Microsoft Exchange Server 2003 Administration. Chapter Eight Managing Routing and Internet Connectivity
 CISNTWK-492e Microsoft Exchange Server 2003 Administration Chapter Eight Managing Routing and Internet Connectivity 1 Objectives Understand SMTP and how it works Understand how Exchange Server 2003 makes
CISNTWK-492e Microsoft Exchange Server 2003 Administration Chapter Eight Managing Routing and Internet Connectivity 1 Objectives Understand SMTP and how it works Understand how Exchange Server 2003 makes
Course 10233: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010
 Course 10233: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Page 1 Course 10233: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 4 days;
Course 10233: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Page 1 Course 10233: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 4 days;
Microsoft Design and Deploy Messaging Solutions with Microsoft Exchange Server 2010
 1800 ULEARN (853 276) www.ddls.com.au Microsoft 10233 - Design and Deploy Messaging Solutions with Microsoft Exchange Server 2010 Length 5 days Price $4290.00 (inc GST) Overview This five-day, instructor-led
1800 ULEARN (853 276) www.ddls.com.au Microsoft 10233 - Design and Deploy Messaging Solutions with Microsoft Exchange Server 2010 Length 5 days Price $4290.00 (inc GST) Overview This five-day, instructor-led
Pro:Deploying Messaging Solutions w/ms Exchange Server Exam.
 Microsoft 70-238 Pro:Deploying Messaging Solutions w/ms Exchange Server 2007 Exam TYPE: DEMO http://www.examskey.com/70-238.html Examskey Microsoft70-238 exam demo product is here for you to test the quality
Microsoft 70-238 Pro:Deploying Messaging Solutions w/ms Exchange Server 2007 Exam TYPE: DEMO http://www.examskey.com/70-238.html Examskey Microsoft70-238 exam demo product is here for you to test the quality
Implementation Guide - VPN Network with Static Routing
 Implementation Guide - VPN Network with Static Routing This guide contains advanced topics and concepts. Follow the links in each section for step-by-step instructions on how to configure the following
Implementation Guide - VPN Network with Static Routing This guide contains advanced topics and concepts. Follow the links in each section for step-by-step instructions on how to configure the following
Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010
 Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Course No.10233B 5 Days Instructor-led, Hands-on Introduction This five-day, instructor-led course provides you with the
Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Course No.10233B 5 Days Instructor-led, Hands-on Introduction This five-day, instructor-led course provides you with the
Microsoft Installing, Configuring, and Administering Microsoft Exchange 2003 Server Implementing &Managing MS Exchange Server 2003
 Microsoft 70-284 Microsoft 70-284 Installing, Configuring, and Administering Microsoft Exchange 2003 Server Implementing &Managing MS Exchange Server 2003 Practice Test Version 2.5 QUESTION NO: 1 Microsoft
Microsoft 70-284 Microsoft 70-284 Installing, Configuring, and Administering Microsoft Exchange 2003 Server Implementing &Managing MS Exchange Server 2003 Practice Test Version 2.5 QUESTION NO: 1 Microsoft
Microsoft Exam
 Microsoft Exam 70-662 TS: Microsoft Exchange Server 2010, Configuring Skills Being Measured This exam measures your ability to accomplish the technical tasks listed below. The percentages indicate the
Microsoft Exam 70-662 TS: Microsoft Exchange Server 2010, Configuring Skills Being Measured This exam measures your ability to accomplish the technical tasks listed below. The percentages indicate the
SD-WAN Deployment Guide (CVD)
 SD-WAN Deployment Guide (CVD) All Cisco Meraki security appliances are equipped with SD-WAN capabilities that enable administrators to maximize network resiliency and bandwidth efficiency. This guide introduces
SD-WAN Deployment Guide (CVD) All Cisco Meraki security appliances are equipped with SD-WAN capabilities that enable administrators to maximize network resiliency and bandwidth efficiency. This guide introduces
This Exchange 2003 Guidelines document is a work in progress, and is current as of May 5, 2004.
 This Exchange 2003 Guidelines document is a work in progress, and is current as of May 5, 2004. docad.cgiar.org Home Exchange 2003 Site Map Exch 2003 Site Map 1. 2. System-wide Policies - open for review
This Exchange 2003 Guidelines document is a work in progress, and is current as of May 5, 2004. docad.cgiar.org Home Exchange 2003 Site Map Exch 2003 Site Map 1. 2. System-wide Policies - open for review
Case Study by Rodrisan PRO: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Case Study Based Exam
 70-663 Case Study by Rodrisan Number: 70-663 Passing Score: 700 Time Limit: 24 min File Version: 1.0 http://www.gratisexam.com/ 70-663 PRO: Designing and Deploying Messaging Solutions with Microsoft Exchange
70-663 Case Study by Rodrisan Number: 70-663 Passing Score: 700 Time Limit: 24 min File Version: 1.0 http://www.gratisexam.com/ 70-663 PRO: Designing and Deploying Messaging Solutions with Microsoft Exchange
Active Directory trust relationships
 Active Directory trust relationships A trust relationship consists of two domains and provides the necessary configuration between them to grant security principals on one side of the trust permission
Active Directory trust relationships A trust relationship consists of two domains and provides the necessary configuration between them to grant security principals on one side of the trust permission
Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010
 Course 10233A: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Length: 5 Days Published: June 09, 2010 Language(s): Audience(s): English IT Professionals Level: 200 Technology:
Course 10233A: Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 Length: 5 Days Published: June 09, 2010 Language(s): Audience(s): English IT Professionals Level: 200 Technology:
70-647: Windows Server Enterprise Administration Course 01 Planning for Active Directory
 70-647: Windows Server Enterprise Administration Course 01 Planning for Active Directory Slide 1 Course 1 Planning for Active Directory Planning the Domains and Forest Structure Planning for Sites and
70-647: Windows Server Enterprise Administration Course 01 Planning for Active Directory Slide 1 Course 1 Planning for Active Directory Planning the Domains and Forest Structure Planning for Sites and
Microsoft PRO- Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010
 http://www.ipass4sure.com Microsoft PRO- Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 http://www.ipass4sure.com/exams.asp?examcode= The practice exam is written and formatted
http://www.ipass4sure.com Microsoft PRO- Designing and Deploying Messaging Solutions with Microsoft Exchange Server 2010 http://www.ipass4sure.com/exams.asp?examcode= The practice exam is written and formatted
R5: Configuring Windows Server 2008 R2 Network Infrastructure
 70-642 R5: Configuring Windows Server 2008 R2 Network Infrastructure Course Introduction Course Introduction Chapter 01 - Understanding and Configuring IP Lesson 1: Introducing the OSI Model Understanding
70-642 R5: Configuring Windows Server 2008 R2 Network Infrastructure Course Introduction Course Introduction Chapter 01 - Understanding and Configuring IP Lesson 1: Introducing the OSI Model Understanding
Mobile MOUSe EXCHANGE SERVER 2010 CONFIGURATION ONLINE COURSE OUTLINE
 Mobile MOUSe EXCHANGE SERVER 2010 CONFIGURATION ONLINE COURSE OUTLINE COURSE TITLE EXCHANGE SERVER 2010 CONFIGURATION COURSE DURATION 16 Hour(s) of Interactive Training COURSE OVERVIEW Prepare for Microsoft's
Mobile MOUSe EXCHANGE SERVER 2010 CONFIGURATION ONLINE COURSE OUTLINE COURSE TITLE EXCHANGE SERVER 2010 CONFIGURATION COURSE DURATION 16 Hour(s) of Interactive Training COURSE OVERVIEW Prepare for Microsoft's
GRE and DM VPNs. Understanding the GRE Modes Page CHAPTER
 CHAPTER 23 You can configure Generic Routing Encapsulation (GRE) and Dynamic Multipoint (DM) VPNs that include GRE mode configurations. You can configure IPsec GRE VPNs for hub-and-spoke, point-to-point,
CHAPTER 23 You can configure Generic Routing Encapsulation (GRE) and Dynamic Multipoint (DM) VPNs that include GRE mode configurations. You can configure IPsec GRE VPNs for hub-and-spoke, point-to-point,
NGF0401 Instructor Slides
 Advanced Site to Site VPN Barracuda NextGen Firewall F VPN Tunnel Routing Separate routing table Default behavior Uses source based routing Creates separate premain routing tables for every VPN tunnel
Advanced Site to Site VPN Barracuda NextGen Firewall F VPN Tunnel Routing Separate routing table Default behavior Uses source based routing Creates separate premain routing tables for every VPN tunnel
Overview of Networking Concepts
 , page 1 Overview Each Cisco Unity Connection server or cluster has a maximum number of users that it can serve. When the messaging needs of your organization require more than one Unity Connection server
, page 1 Overview Each Cisco Unity Connection server or cluster has a maximum number of users that it can serve. When the messaging needs of your organization require more than one Unity Connection server
Brocade Virtual Traffic Manager and Parallels Remote Application Server
 White Paper Parallels Brocade Virtual Traffic Manager and Parallels Deployment Guide 01 Contents Preface...4 About This Guide...4 Audience...4 Contacting Brocade...4 Internet...4 Technical Support...4
White Paper Parallels Brocade Virtual Traffic Manager and Parallels Deployment Guide 01 Contents Preface...4 About This Guide...4 Audience...4 Contacting Brocade...4 Internet...4 Technical Support...4
Hochverfügbarkeit in Campusnetzen
 Hochverfügbarkeit in Campusnetzen Für die deutsche Airheads Community 04. Juli 2017, Tino H. Seifert, System Engineer Aruba Differences between Campus Edge and Campus Core Campus Edge In many cases no
Hochverfügbarkeit in Campusnetzen Für die deutsche Airheads Community 04. Juli 2017, Tino H. Seifert, System Engineer Aruba Differences between Campus Edge and Campus Core Campus Edge In many cases no
Double-Take Software
 Whitepaper Exchange 2010 Advanced Protection Enhancing the Availability of Microsoft Exchange Server 2010 Double-Take Software Overview Native backup can provide higher levels of data and system protection,
Whitepaper Exchange 2010 Advanced Protection Enhancing the Availability of Microsoft Exchange Server 2010 Double-Take Software Overview Native backup can provide higher levels of data and system protection,
Active Directory Replicationm
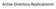 Active Directory Replicationm Site 1 Read/Write copy of Active Directory Database Ntds.dit Site 1 C D All domain controllers host a full replica of the domain information for its own domain Replication:
Active Directory Replicationm Site 1 Read/Write copy of Active Directory Database Ntds.dit Site 1 C D All domain controllers host a full replica of the domain information for its own domain Replication:
TestsDumps. Latest Test Dumps for IT Exam Certification
 TestsDumps http://www.testsdumps.com Latest Test Dumps for IT Exam Certification Exam : 70-350 Title : Implementing Microsoft Internet Security and Acceleration (ISA) Server 2004 Vendors : Microsoft Version
TestsDumps http://www.testsdumps.com Latest Test Dumps for IT Exam Certification Exam : 70-350 Title : Implementing Microsoft Internet Security and Acceleration (ISA) Server 2004 Vendors : Microsoft Version
Troubleshooting SMTP Routing. Chris Miller Director of Messaging/Collab Connectria
 Troubleshooting SMTP Routing Chris Miller Director of Messaging/Collab Connectria What We ll Cover Following the breadcrumbs in the forest Planning to be an archeologist Running relay races, jumping hurdles
Troubleshooting SMTP Routing Chris Miller Director of Messaging/Collab Connectria What We ll Cover Following the breadcrumbs in the forest Planning to be an archeologist Running relay races, jumping hurdles
Configuring BGP. Cisco s BGP Implementation
 Configuring BGP This chapter describes how to configure Border Gateway Protocol (BGP). For a complete description of the BGP commands in this chapter, refer to the BGP s chapter of the Network Protocols
Configuring BGP This chapter describes how to configure Border Gateway Protocol (BGP). For a complete description of the BGP commands in this chapter, refer to the BGP s chapter of the Network Protocols
Services: Monitoring and Logging. 9/16/2018 IST346: Info Tech Management & Administration 1
 Services: Monitoring and Logging 9/16/2018 IST346: Info Tech Management & Administration 1 Recall: Server vs. Service A server is a computer. A service is an offering provided by server(s). HTTP 9/16/2018
Services: Monitoring and Logging 9/16/2018 IST346: Info Tech Management & Administration 1 Recall: Server vs. Service A server is a computer. A service is an offering provided by server(s). HTTP 9/16/2018
How Cisco IT Deployed Enterprise Messaging on Cisco UCS
 Cisco IT Case Study July 2012 Enterprise Messaging on Cisco UCS How Cisco IT Deployed Enterprise Messaging on Cisco UCS Messaging platform upgrade and new servers reduce costs and improve management, availability,
Cisco IT Case Study July 2012 Enterprise Messaging on Cisco UCS How Cisco IT Deployed Enterprise Messaging on Cisco UCS Messaging platform upgrade and new servers reduce costs and improve management, availability,
Designing Windows Server 2008 Network and Applications Infrastructure
 Designing Windows Server 2008 Network and Applications Infrastructure Course No. 6435B - 5 Days Instructor-led, Hands-on Introduction This five-day course will provide students with an understanding of
Designing Windows Server 2008 Network and Applications Infrastructure Course No. 6435B - 5 Days Instructor-led, Hands-on Introduction This five-day course will provide students with an understanding of
Comendo mail- & spamfence
 Upgrade Guide Resellers Comendo mail- & spamfence VERSION 10-05-2016 TABLE OF CONTENTS INTRODUCTION... 3 OVERVIEW... 4 1. Preparation... 4 2. Provisioning... 4 3. Upgrade... 4 4. Finalisation... 4 COMPARISON...
Upgrade Guide Resellers Comendo mail- & spamfence VERSION 10-05-2016 TABLE OF CONTENTS INTRODUCTION... 3 OVERVIEW... 4 1. Preparation... 4 2. Provisioning... 4 3. Upgrade... 4 4. Finalisation... 4 COMPARISON...
Routing, Routing Algorithms & Protocols
 Routing, Routing Algorithms & Protocols Computer Networks Lecture 6 http://goo.gl/pze5o8 Circuit-Switched and Packet-Switched WANs 2 Circuit-Switched Networks Older (evolved from telephone networks), a
Routing, Routing Algorithms & Protocols Computer Networks Lecture 6 http://goo.gl/pze5o8 Circuit-Switched and Packet-Switched WANs 2 Circuit-Switched Networks Older (evolved from telephone networks), a
Module 7: Implementing Sites to Manage Active Directory Replication
 Module 7: Implementing Sites to Manage Active Directory Replication Contents Overview 1 Lesson: to Active Directory Replication 2 Lesson: Creating and Configuring Sites 14 Lesson: Managing Site Topology
Module 7: Implementing Sites to Manage Active Directory Replication Contents Overview 1 Lesson: to Active Directory Replication 2 Lesson: Creating and Configuring Sites 14 Lesson: Managing Site Topology
COPYRIGHTED MATERIAL. Contents at a Glance. Introduction... xxiii. Chapter 1 Getting to Know Exchange Server
 Contents at a Glance Introduction... xxiii Chapter 1 Getting to Know Exchange Server 2007...1 Chapter 2 Exchange Server 2007 Administration...53 Chapter 3 Start Your Engines Preparing for Migration...85
Contents at a Glance Introduction... xxiii Chapter 1 Getting to Know Exchange Server 2007...1 Chapter 2 Exchange Server 2007 Administration...53 Chapter 3 Start Your Engines Preparing for Migration...85
Microsoft Exchange 2016 Quiz [Solved] https://msexchangemaster.blogspot.com/
![Microsoft Exchange 2016 Quiz [Solved] https://msexchangemaster.blogspot.com/ Microsoft Exchange 2016 Quiz [Solved] https://msexchangemaster.blogspot.com/](/thumbs/71/65837708.jpg) Microsoft Exchange 2016 Quiz [Solved] https://msexchangemaster.blogspot.com/ 1. The oldest version of forest functionality level supported by Exchange 2016 is:(1. Windows Server 2012 Windows Server 2016
Microsoft Exchange 2016 Quiz [Solved] https://msexchangemaster.blogspot.com/ 1. The oldest version of forest functionality level supported by Exchange 2016 is:(1. Windows Server 2012 Windows Server 2016
Managing Site-to-Site VPNs: The Basics
 CHAPTER 23 A virtual private network (VPN) consists of multiple remote peers transmitting private data securely to one another over an unsecured network, such as the Internet. Site-to-site VPNs use tunnels
CHAPTER 23 A virtual private network (VPN) consists of multiple remote peers transmitting private data securely to one another over an unsecured network, such as the Internet. Site-to-site VPNs use tunnels
Connecting to Mimecast
 Page 1 of 5 0 KBID10577 Connecting to Mimecast Congratulations and welcome to Mimecast! Thank you for making the choice to move your email management to the cloud with the Mimecast Unified Email Management
Page 1 of 5 0 KBID10577 Connecting to Mimecast Congratulations and welcome to Mimecast! Thank you for making the choice to move your email management to the cloud with the Mimecast Unified Email Management
Managing Site-to-Site VPNs
 CHAPTER 21 A virtual private network (VPN) consists of multiple remote peers transmitting private data securely to one another over an unsecured network, such as the Internet. Site-to-site VPNs use tunnels
CHAPTER 21 A virtual private network (VPN) consists of multiple remote peers transmitting private data securely to one another over an unsecured network, such as the Internet. Site-to-site VPNs use tunnels
- Hubs vs. Switches vs. Routers -
 1 Layered Communication - Hubs vs. Switches vs. Routers - Network communication models are generally organized into layers. The OSI model specifically consists of seven layers, with each layer representing
1 Layered Communication - Hubs vs. Switches vs. Routers - Network communication models are generally organized into layers. The OSI model specifically consists of seven layers, with each layer representing
Replicator. Product and Concepts Guide VERSION November 20,
 Replicator Product and Concepts Guide VERSION 7.4.0 November 20, 2017 www.metalogix.com info@metalogix.com 202.609.9100 Copyright International GmbH, 2002-2017. All rights reserved. No part or section
Replicator Product and Concepts Guide VERSION 7.4.0 November 20, 2017 www.metalogix.com info@metalogix.com 202.609.9100 Copyright International GmbH, 2002-2017. All rights reserved. No part or section
Deploying the BIG-IP System for LDAP Traffic Management
 Deploying the BIG-IP System for LDAP Traffic Management Welcome to the F5 deployment guide for LDAP traffic management. This document provides guidance for configuring the BIG-IP system version 11.4 and
Deploying the BIG-IP System for LDAP Traffic Management Welcome to the F5 deployment guide for LDAP traffic management. This document provides guidance for configuring the BIG-IP system version 11.4 and
Cisco Dynamic Multipoint VPN: Simple and Secure Branch-to-Branch Communications
 Cisco Dynamic Multipoint VPN: Simple and Secure Branch-to-Branch Communications Product Overview Cisco Dynamic Multipoint VPN (DMVPN) is a Cisco IOS Software-based security solution for building scalable
Cisco Dynamic Multipoint VPN: Simple and Secure Branch-to-Branch Communications Product Overview Cisco Dynamic Multipoint VPN (DMVPN) is a Cisco IOS Software-based security solution for building scalable
MOM MESSAGE ORIENTED MIDDLEWARE OVERVIEW OF MESSAGE ORIENTED MIDDLEWARE TECHNOLOGIES AND CONCEPTS. MOM Message Oriented Middleware
 MOM MESSAGE ORIENTED MOM Message Oriented Middleware MIDDLEWARE OVERVIEW OF MESSAGE ORIENTED MIDDLEWARE TECHNOLOGIES AND CONCEPTS Peter R. Egli 1/25 Contents 1. Synchronous versus asynchronous interaction
MOM MESSAGE ORIENTED MOM Message Oriented Middleware MIDDLEWARE OVERVIEW OF MESSAGE ORIENTED MIDDLEWARE TECHNOLOGIES AND CONCEPTS Peter R. Egli 1/25 Contents 1. Synchronous versus asynchronous interaction
Managing Site-to-Site VPNs: The Basics
 CHAPTER 21 A virtual private network (VPN) consists of multiple remote peers transmitting private data securely to one another over an unsecured network, such as the Internet. Site-to-site VPNs use tunnels
CHAPTER 21 A virtual private network (VPN) consists of multiple remote peers transmitting private data securely to one another over an unsecured network, such as the Internet. Site-to-site VPNs use tunnels
NE Designing and Deploying Microsoft Exchange Server 2016
 NE-20345-2 Designing and Deploying Microsoft Exchange Server 2016 Summary Duration 5 Days Audience Microsoft Exchange Level 300 Technology Exchange Server 2016 Delivery Method Instructor-led (Classroom)
NE-20345-2 Designing and Deploying Microsoft Exchange Server 2016 Summary Duration 5 Days Audience Microsoft Exchange Level 300 Technology Exchange Server 2016 Delivery Method Instructor-led (Classroom)
Maintaining High Availability for Enterprise Voice in Microsoft Office Communication Server 2007
 Maintaining High Availability for Enterprise Voice in Microsoft Office Communication Server 2007 A Dell Technical White Paper By Farrukh Noman Dell Product Group - Enterprise THIS WHITE PAPER IS FOR INFORMATIONAL
Maintaining High Availability for Enterprise Voice in Microsoft Office Communication Server 2007 A Dell Technical White Paper By Farrukh Noman Dell Product Group - Enterprise THIS WHITE PAPER IS FOR INFORMATIONAL
Cisco Dynamic Multipoint VPN: Simple and Secure Branch-to-Branch Communications
 Data Sheet Cisco Dynamic Multipoint VPN: Simple and Secure Branch-to-Branch Communications Product Overview Cisco Dynamic Multipoint VPN (DMVPN) is a Cisco IOS Software-based security solution for building
Data Sheet Cisco Dynamic Multipoint VPN: Simple and Secure Branch-to-Branch Communications Product Overview Cisco Dynamic Multipoint VPN (DMVPN) is a Cisco IOS Software-based security solution for building
Lecture (08, 09) Routing in Switched Networks
 Agenda Lecture (08, 09) Routing in Switched Networks Dr. Ahmed ElShafee Routing protocols Fixed Flooding Random Adaptive ARPANET Routing Strategies ١ Dr. Ahmed ElShafee, ACU Fall 2011, Networks I ٢ Dr.
Agenda Lecture (08, 09) Routing in Switched Networks Dr. Ahmed ElShafee Routing protocols Fixed Flooding Random Adaptive ARPANET Routing Strategies ١ Dr. Ahmed ElShafee, ACU Fall 2011, Networks I ٢ Dr.
5.1. Functional Level
 5.1. Functional Level A functional level is a set of operation constraints that determine the functions that can be performed by an Active Directory domain or forest. A functional level defines: Which
5.1. Functional Level A functional level is a set of operation constraints that determine the functions that can be performed by an Active Directory domain or forest. A functional level defines: Which
You can find more information about the service at
 Introduction The purpose of this guide is to familiarize you with ExchangeDefender and walk you through the configuration, management and deployment of the service. ExchangeDefender is a transparent, cloud-based
Introduction The purpose of this guide is to familiarize you with ExchangeDefender and walk you through the configuration, management and deployment of the service. ExchangeDefender is a transparent, cloud-based
QUESTION: 1 You have been asked to establish a design that will allow your company to migrate from a WAN service to a Layer 3 VPN service. In your des
 Vendor: Cisco Exam Code: 352-001 Exam Name: ADVDESIGN Version: Demo www.dumpspdf.com QUESTION: 1 You have been asked to establish a design that will allow your company to migrate from a WAN service to
Vendor: Cisco Exam Code: 352-001 Exam Name: ADVDESIGN Version: Demo www.dumpspdf.com QUESTION: 1 You have been asked to establish a design that will allow your company to migrate from a WAN service to
What's in this guide... 4 Documents related to NetBackup in highly available environments... 5
 Contents Chapter 1 About in this guide... 4 What's in this guide... 4 Documents related to NetBackup in highly available environments... 5 Chapter 2 NetBackup protection against single points of failure...
Contents Chapter 1 About in this guide... 4 What's in this guide... 4 Documents related to NetBackup in highly available environments... 5 Chapter 2 NetBackup protection against single points of failure...
Cisco Unified MeetingPlace Integration
 CHAPTER 14 This chapter covers system-level design and implementation of Cisco Unified MeetingPlace 5.4 in a Cisco Unified Communications Manager 5.x environment. The following aspects of design and configuration
CHAPTER 14 This chapter covers system-level design and implementation of Cisco Unified MeetingPlace 5.4 in a Cisco Unified Communications Manager 5.x environment. The following aspects of design and configuration
Practice Test. Microsoft Microsoft PRO: Deploying Messaging Solutions with Microsoft Exchange Server Version 2.
 Microsoft 70-238 Microsoft 70-238 PRO: Deploying Messaging Solutions with Microsoft Exchange Server 2007 Practice Test Version 2.1 QUESTION NO: 1 Microsoft 70-238: Practice Exam You are a messaging professional.
Microsoft 70-238 Microsoft 70-238 PRO: Deploying Messaging Solutions with Microsoft Exchange Server 2007 Practice Test Version 2.1 QUESTION NO: 1 Microsoft 70-238: Practice Exam You are a messaging professional.
Service Mesh and Microservices Networking
 Service Mesh and Microservices Networking WHITEPAPER Service mesh and microservice networking As organizations adopt cloud infrastructure, there is a concurrent change in application architectures towards
Service Mesh and Microservices Networking WHITEPAPER Service mesh and microservice networking As organizations adopt cloud infrastructure, there is a concurrent change in application architectures towards
Federal Agencies and the Transition to IPv6
 Federal Agencies and the Transition to IPv6 Introduction Because of the federal mandate to transition from IPv4 to IPv6, IT departments must include IPv6 as a core element of their current and future IT
Federal Agencies and the Transition to IPv6 Introduction Because of the federal mandate to transition from IPv4 to IPv6, IT departments must include IPv6 as a core element of their current and future IT
Avoiding the Cost of Confusion: SQL Server Failover Cluster Instances versus Basic Availability Group on Standard Edition
 One Stop Virtualization Shop Avoiding the Cost of Confusion: SQL Server Failover Cluster Instances versus Basic Availability Group on Standard Edition Written by Edwin M Sarmiento, a Microsoft Data Platform
One Stop Virtualization Shop Avoiding the Cost of Confusion: SQL Server Failover Cluster Instances versus Basic Availability Group on Standard Edition Written by Edwin M Sarmiento, a Microsoft Data Platform
Cisco Group Encrypted Transport VPN
 Cisco Group Encrypted Transport VPN Q. What is Cisco Group Encrypted Transport VPN? A. Cisco Group Encrypted Transport is a next-generation WAN VPN solution that defines a new category of VPN, one that
Cisco Group Encrypted Transport VPN Q. What is Cisco Group Encrypted Transport VPN? A. Cisco Group Encrypted Transport is a next-generation WAN VPN solution that defines a new category of VPN, one that
68199.book Page 1 Friday, August 10, :39 PM. Chapter. Exchange Server 2007 and Active Directory Review COPYRIGHTED MATERIAL
 68199.book Page 1 Friday, August 10, 2007 3:39 PM Chapter 1 Exchange Server 2007 and Active Directory Review COPYRIGHTED MATERIAL 68199.book Page 2 Friday, August 10, 2007 3:39 PM Perhaps the most abused,
68199.book Page 1 Friday, August 10, 2007 3:39 PM Chapter 1 Exchange Server 2007 and Active Directory Review COPYRIGHTED MATERIAL 68199.book Page 2 Friday, August 10, 2007 3:39 PM Perhaps the most abused,
The Collaboration Cornerstone
 E-Mail: The Collaboration Cornerstone On Demand Insurance Business Problems 1. We lose customers because we process new policy applications too slowly. 2. Our claims processing is time-consuming and inefficient.
E-Mail: The Collaboration Cornerstone On Demand Insurance Business Problems 1. We lose customers because we process new policy applications too slowly. 2. Our claims processing is time-consuming and inefficient.
Securely Access Services Over AWS PrivateLink. January 2019
 Securely Access Services Over AWS PrivateLink January 2019 Notices This document is provided for informational purposes only. It represents AWS s current product offerings and practices as of the date
Securely Access Services Over AWS PrivateLink January 2019 Notices This document is provided for informational purposes only. It represents AWS s current product offerings and practices as of the date
Atlas Technology White Paper
 Atlas Technology White Paper 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of their respective
Atlas Technology White Paper 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of their respective
Designing and Deploying Microsoft Exchange Server 2016
 Course 20345-2A: Designing and Deploying Microsoft Exchange Server 2016 Course Outline Module 1: Planning Exchange Server 2016 deployments This module explains the requirements and considerations for planning
Course 20345-2A: Designing and Deploying Microsoft Exchange Server 2016 Course Outline Module 1: Planning Exchange Server 2016 deployments This module explains the requirements and considerations for planning
A Guide to Architecting the Active/Active Data Center
 White Paper A Guide to Architecting the Active/Active Data Center 2015 ScaleArc. All Rights Reserved. White Paper The New Imperative: Architecting the Active/Active Data Center Introduction With the average
White Paper A Guide to Architecting the Active/Active Data Center 2015 ScaleArc. All Rights Reserved. White Paper The New Imperative: Architecting the Active/Active Data Center Introduction With the average
20413B: Designing and Implementing a Server Infrastructure
 20413B: Designing and Implementing a Server Infrastructure Course Outline Course Introduction Course Introduction Module 01 - Planning a Server Upgrade and Migration Lesson 1: Upgrade and Migration Considerations
20413B: Designing and Implementing a Server Infrastructure Course Outline Course Introduction Course Introduction Module 01 - Planning a Server Upgrade and Migration Lesson 1: Upgrade and Migration Considerations
MCITP CURRICULUM Windows 7
 MCITP CURRICULUM 70-680 Windows 7 Installing, Upgrading, and Migrating to Windows 7 Describe the key features, editions, and hardware requirements of Windows 7 Perform a clean installation of Windows 7
MCITP CURRICULUM 70-680 Windows 7 Installing, Upgrading, and Migrating to Windows 7 Describe the key features, editions, and hardware requirements of Windows 7 Perform a clean installation of Windows 7
This Lecture. BUS Computer Facilities Network Management. Switching Network. Simple Switching Network
 This Lecture BUS0 - Computer Facilities Network Management Switching networks Circuit switching Packet switching gram approach Virtual circuit approach Routing in switching networks Faculty of Information
This Lecture BUS0 - Computer Facilities Network Management Switching networks Circuit switching Packet switching gram approach Virtual circuit approach Routing in switching networks Faculty of Information
Enhanced Location Call Admission Control
 The following sections provide information about the feature. Configure, page 1 Feature, page 2 Architecture, page 4 Location Bandwidth Service Parameters, page 8 Shadow System Location, page 8 Devices
The following sections provide information about the feature. Configure, page 1 Feature, page 2 Architecture, page 4 Location Bandwidth Service Parameters, page 8 Shadow System Location, page 8 Devices
Chapter -4 OSI Reference Model
 Chapter -4 OSI Reference Model Objectives Concept of Reference Model. OSI Reference Model Concept. Layers of OSI Reference Model. 4.1 Introduction Layered Architecture, Peer-to- Peer Processes, Interfaces
Chapter -4 OSI Reference Model Objectives Concept of Reference Model. OSI Reference Model Concept. Layers of OSI Reference Model. 4.1 Introduction Layered Architecture, Peer-to- Peer Processes, Interfaces
Migrating from Dynamic Multipoint VPN Phase 2 to Phase 3: Why and How to Migrate to the Next Phase
 Migration Guide Migrating from Dynamic Multipoint VPN Phase 2 to Phase 3: Why and How to Migrate to the Next Phase This guide shows how a Dynamic Multipoint VPN (DMVPN) deployment can be migrated to make
Migration Guide Migrating from Dynamic Multipoint VPN Phase 2 to Phase 3: Why and How to Migrate to the Next Phase This guide shows how a Dynamic Multipoint VPN (DMVPN) deployment can be migrated to make
PassTorrent. Pass your actual test with our latest and valid practice torrent at once
 PassTorrent http://www.passtorrent.com Pass your actual test with our latest and valid practice torrent at once Exam : 352-011 Title : Cisco Certified Design Expert Practical Exam Vendor : Cisco Version
PassTorrent http://www.passtorrent.com Pass your actual test with our latest and valid practice torrent at once Exam : 352-011 Title : Cisco Certified Design Expert Practical Exam Vendor : Cisco Version
EXAM Advanced Solutions of Microsoft Exchange Server Buy Full Product.
 Microsoft EXAM - 70-342 Advanced Solutions of Microsoft Exchange Server 2013 Buy Full Product http://www.examskey.com/70-342.html Examskey Microsoft 70-342 exam demo product is here for you to test the
Microsoft EXAM - 70-342 Advanced Solutions of Microsoft Exchange Server 2013 Buy Full Product http://www.examskey.com/70-342.html Examskey Microsoft 70-342 exam demo product is here for you to test the
SJTU 2018 Fall Computer Networking. Wireless Communication
 SJTU 2018 Fall Computer Networking 1 Wireless Communication Internet Protocol Stack 2 Application: supporting network applications - FTP, SMTP, HTTP Transport: data transfer between processes - TCP, UDP
SJTU 2018 Fall Computer Networking 1 Wireless Communication Internet Protocol Stack 2 Application: supporting network applications - FTP, SMTP, HTTP Transport: data transfer between processes - TCP, UDP
Information About Routing
 19 CHAPTER This chapter describes underlying concepts of how routing behaves within the adaptive security appliance, and the routing protocols that are supported. The chapter includes the following sections:,
19 CHAPTER This chapter describes underlying concepts of how routing behaves within the adaptive security appliance, and the routing protocols that are supported. The chapter includes the following sections:,
Reference Architecture
 vrealize Automation 7.0.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions
vrealize Automation 7.0.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions
Best Practice Active Directory Design for Managing Windows Networks
 Best Practice Active Directory Design for Managing Windows Networks A structured approach to Active Directory design makes enterprise scale directory service deployment straightforward and easy to understand.
Best Practice Active Directory Design for Managing Windows Networks A structured approach to Active Directory design makes enterprise scale directory service deployment straightforward and easy to understand.
Setting up Microsoft Office 365
 Integration Guide Revision G McAfee SaaS Email Protection Securing Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Integration Guide Revision G McAfee SaaS Email Protection Securing Exchange Online in Microsoft Office 365 Setting up Microsoft Office 365 Use this guide to configure Microsoft Office 365 and Microsoft
Cloud Services. Introduction
 Introduction adi Digital have developed a resilient, secure, flexible, high availability Software as a Service (SaaS) cloud platform. This Platform provides a simple to use, cost effective and convenient
Introduction adi Digital have developed a resilient, secure, flexible, high availability Software as a Service (SaaS) cloud platform. This Platform provides a simple to use, cost effective and convenient
Hyper-V - VM Live Migration
 Hyper-V - VM Live Migration Hyper-V Live Migration is first introduced in Windows Server 2008 R2 and enhanced lot in later versions. Hyper-V live migration moves running virtual machines from one physical
Hyper-V - VM Live Migration Hyper-V Live Migration is first introduced in Windows Server 2008 R2 and enhanced lot in later versions. Hyper-V live migration moves running virtual machines from one physical
Military Messaging. Over Low. Bandwidth. Connections
 Military Messaging Over Low Bandwidth Connections White Paper Contents Paper Overview 3 The Technical Challenges 4 Low Bandwidth 4 High Latency 4 High Error Rates 4 Multicast 4 Emission Control (EMCON)
Military Messaging Over Low Bandwidth Connections White Paper Contents Paper Overview 3 The Technical Challenges 4 Low Bandwidth 4 High Latency 4 High Error Rates 4 Multicast 4 Emission Control (EMCON)
Inter-VSAN Routing Configuration
 CHAPTER 16 This chapter explains the inter-vsan routing (IVR) feature and provides details on sharing resources across VSANs using IVR management interfaces provided in the switch. This chapter includes
CHAPTER 16 This chapter explains the inter-vsan routing (IVR) feature and provides details on sharing resources across VSANs using IVR management interfaces provided in the switch. This chapter includes
Advanced Architecture Design for Cloud-Based Disaster Recovery WHITE PAPER
 Advanced Architecture Design for Cloud-Based Disaster Recovery WHITE PAPER Introduction Disaster Recovery (DR) is a fundamental tool for mitigating IT and business risks. But because it is perceived as
Advanced Architecture Design for Cloud-Based Disaster Recovery WHITE PAPER Introduction Disaster Recovery (DR) is a fundamental tool for mitigating IT and business risks. But because it is perceived as
Designing and Deploying Microsoft Exchange Server 2016
 Course Content Course Description: This course provides experienced Exchange Server administrators with the knowledge to design and implement an Exchange Server 2016 messaging environment. Students will
Course Content Course Description: This course provides experienced Exchange Server administrators with the knowledge to design and implement an Exchange Server 2016 messaging environment. Students will
Intelligent WAN Multiple VRFs Deployment Guide
 Cisco Validated design Intelligent WAN Multiple VRFs Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deploying the Cisco IWAN Multiple VRFs...
Cisco Validated design Intelligent WAN Multiple VRFs Deployment Guide September 2017 Table of Contents Table of Contents Deploying the Cisco Intelligent WAN... 1 Deploying the Cisco IWAN Multiple VRFs...
Certified SonicWALL Security Administrator (CSSA) Instructor-led Training
 Instructor-led Training Comprehensive Services from Your Trusted Security Partner Additional Information Recommended prerequisite for the Certified SonicWALL Security Administrator (CSSA) exam Course Description:
Instructor-led Training Comprehensive Services from Your Trusted Security Partner Additional Information Recommended prerequisite for the Certified SonicWALL Security Administrator (CSSA) exam Course Description:
Routing in packet-switching networks
 Routing in packet-switching networks Circuit switching vs. Packet switching Most of WANs based on circuit or packet switching Circuit switching designed for voice Resources dedicated to a particular call
Routing in packet-switching networks Circuit switching vs. Packet switching Most of WANs based on circuit or packet switching Circuit switching designed for voice Resources dedicated to a particular call
William Stallings Data and Computer Communications. Chapter 10 Packet Switching
 William Stallings Data and Computer Communications Chapter 10 Packet Switching Principles Circuit switching designed for voice Resources dedicated to a particular call Much of the time a data connection
William Stallings Data and Computer Communications Chapter 10 Packet Switching Principles Circuit switching designed for voice Resources dedicated to a particular call Much of the time a data connection
It s Time for WAN Optimization to Evolve to Meet the Needs of File Collaboration
 It s Time for WAN Optimization to Evolve to Meet the Needs of File Collaboration By Zeus Kerravala, Founder and Principal Analyst with ZK Research Contents Introduction: Effective File Collaboration Is
It s Time for WAN Optimization to Evolve to Meet the Needs of File Collaboration By Zeus Kerravala, Founder and Principal Analyst with ZK Research Contents Introduction: Effective File Collaboration Is
WHITE PAPER: BEST PRACTICES. Sizing and Scalability Recommendations for Symantec Endpoint Protection. Symantec Enterprise Security Solutions Group
 WHITE PAPER: BEST PRACTICES Sizing and Scalability Recommendations for Symantec Rev 2.2 Symantec Enterprise Security Solutions Group White Paper: Symantec Best Practices Contents Introduction... 4 The
WHITE PAPER: BEST PRACTICES Sizing and Scalability Recommendations for Symantec Rev 2.2 Symantec Enterprise Security Solutions Group White Paper: Symantec Best Practices Contents Introduction... 4 The
Installing and Configuring VMware Identity Manager Connector (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.
 Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
Planning for Information Network
 Planning for Information Network Lecture 7: Introduction to IPv6 Assistant Teacher Samraa Adnan Al-Asadi 1 IPv6 Features The ability to scale networks for future demands requires a limitless supply of
Planning for Information Network Lecture 7: Introduction to IPv6 Assistant Teacher Samraa Adnan Al-Asadi 1 IPv6 Features The ability to scale networks for future demands requires a limitless supply of
Virtual Private Cloud. User Guide. Issue 03 Date
 Issue 03 Date 2016-10-19 Change History Change History Release Date What's New 2016-10-19 This issue is the third official release. Modified the following content: Help Center URL 2016-07-15 This issue
Issue 03 Date 2016-10-19 Change History Change History Release Date What's New 2016-10-19 This issue is the third official release. Modified the following content: Help Center URL 2016-07-15 This issue
Windows Server 2008 Training
 Windows Server 2008 Training Day -4 Vijay Bhalerao BCS, MCM, CISA, DCL,MCTS, ISO 27001 LA univijay2001@yahoo.com 1 Day-4 Troubleshooting AD & issues- Solutions Server Security Measures - Installation &
Windows Server 2008 Training Day -4 Vijay Bhalerao BCS, MCM, CISA, DCL,MCTS, ISO 27001 LA univijay2001@yahoo.com 1 Day-4 Troubleshooting AD & issues- Solutions Server Security Measures - Installation &
Citrix SD-WAN for Optimal Office 365 Connectivity and Performance
 Solution Brief Citrix SD-WAN for Optimal Office 365 Connectivity and Performance Evolving Needs for WAN Network Architecture Enterprise networks have historically been architected to provide users access
Solution Brief Citrix SD-WAN for Optimal Office 365 Connectivity and Performance Evolving Needs for WAN Network Architecture Enterprise networks have historically been architected to provide users access
March 10, Distributed Hash-based Lookup. for Peer-to-Peer Systems. Sandeep Shelke Shrirang Shirodkar MTech I CSE
 for for March 10, 2006 Agenda for Peer-to-Peer Sytems Initial approaches to Their Limitations CAN - Applications of CAN Design Details Benefits for Distributed and a decentralized architecture No centralized
for for March 10, 2006 Agenda for Peer-to-Peer Sytems Initial approaches to Their Limitations CAN - Applications of CAN Design Details Benefits for Distributed and a decentralized architecture No centralized
PASS4TEST. IT Certification Guaranteed, The Easy Way! We offer free update service for one year
 PASS4TEST IT Certification Guaranteed, The Easy Way! \ http://www.pass4test.com We offer free update service for one year Exam : 70-237 Title : Designing Messaging Solutions with Microsoft Exchange Server
PASS4TEST IT Certification Guaranteed, The Easy Way! \ http://www.pass4test.com We offer free update service for one year Exam : 70-237 Title : Designing Messaging Solutions with Microsoft Exchange Server
Exam Questions Demo Microsoft. Exam Questions
 Microsoft Exam Questions 70-341 Core Solutions of Microsoft Exchange Server 2013 Version:Demo 1. You have an Exchange Server 2013 organization that contains two Client Access servers named SERVER1 and
Microsoft Exam Questions 70-341 Core Solutions of Microsoft Exchange Server 2013 Version:Demo 1. You have an Exchange Server 2013 organization that contains two Client Access servers named SERVER1 and
Microsoft Designing and Deploying Microsoft Exchange Server 2016
 1800 ULEARN (853 276) www.ddls.com.au Microsoft 20345-2 Designing and Deploying Microsoft Exchange Server 2016 Length 5 days Price $4290.00 (inc GST) Version A Overview This course provides experienced
1800 ULEARN (853 276) www.ddls.com.au Microsoft 20345-2 Designing and Deploying Microsoft Exchange Server 2016 Length 5 days Price $4290.00 (inc GST) Version A Overview This course provides experienced
GFI MailSecurity 2011 for Exchange/SMTP. Administration & Configuration Manual
 GFI MailSecurity 2011 for Exchange/SMTP Administration & Configuration Manual http://www.gfi.com info@gfi.com The information and content in this document is provided for informational purposes only and
GFI MailSecurity 2011 for Exchange/SMTP Administration & Configuration Manual http://www.gfi.com info@gfi.com The information and content in this document is provided for informational purposes only and
