Hostname (DNS Resolvable) Network Objects
|
|
|
- Wendy Fitzgerald
- 6 years ago
- Views:
Transcription
1 Introduction The following article explains the configuration of hostname (DNS Resolvable) network objects. Note that the maximum amount of a single DNS resolvable hostname is limited to 24 IP addresses. If a hostname is resolvable to more than 24 IP address, only the first 24 IP addresses will be resolved and processed. Firewall rulesets steer the processing of IP packets. As IP packets only know a destination IP address and not a host name, the allocation of host names to appropriate IP addresses must be managed through the firewall. Network objects of type Hostname allow specifying DNS resolvable host names as network addresses, and in this way make the use of host names in firewall rules possible. Only explicitly defined host names (for example but no comprehensive zone names may be used in network objects. A DNS server must be specified in the DNS Server IP field in the Box Settings file (How to Configure DNS Settings), in order to use network objects of type Hostname. Using DNS resolvable host names in firewall rulesets can cause problems because of the following: IP addresses that are allocated to DNS host names might change. A DNS record might contain multiple IP addresses. Creating Network Objects of Type Hostname Hostname objects may be created in: the Local Firewall ruleset. the Forwarding Firewall ruleset. as Global, Range- or Cluster-specific firewall objects. Hostname objects may NOT be created as explicit source or destination objects in firewall rules. To create a network object of type Hostname (see: How to Create Network Objects), select Hostname (DNS resolved) from the Type list in the Network Object window. Consider the following detail configuration options: 1 / 5
2 The following parameters can be configured: Type - The type defines specific object characteristics. Network objects of type Hostname expect specification of an explicit DNS resolvable host name in the Name field below. Once the object has been created its type cannot be changed. Name - Into this field insert the DNS resolvable name the object is to be created for. Description - Into this field insert a significant object description. The specified name is the name of the network object at the same time. The object name may be changed retroactively. Resolve - The functionality of this button is purely informational. Click it to execute a DNS query for the host name inserted into the Name field. The result of the query is displayed in the IP field in the Entry section. Note that the query is executed using the DNS server(s) known to the client running the graphical administration tool Barracuda NG Admin and NOT using the DNS server(s) known to the Barracuda NG Firewall running the firewall service. DNS Lifetime (Sec) - The DNS Lifetime defines the interval after which to refresh DNS entries for network objects of type Hostname that are configured for use in currently effective firewall rules (default: 600 s). Setting to a lower value than 30 seconds might cause problems in network object lists containing a huge number of hostname objects. DNS entries may also be refreshed manually in the Firewall Monitoring > Dynamic tab > Dynamic Rules tab. The DNS Lifetime has no effect on actively established connections, even if the DNS resolution of a network object that is currently used in a firewall rule changes. In this case to force a refresh terminate the active session in order to enable new connection establishment using the updated DNS entry. 2 / 5
3 The Include - and Exclude Entries sections may be used to restrict a network object and to force a condition to match explicitly or to exclude it from being part of it. For example, if a DNS host name entry matches four DNS A-records pointing to the IP addresses , , and , and it is wanted that connection requests must always point to addresses residing in the /24 network, but must never be addressed to the IP address , the following values need to be configured in the corresponding fields: Section Included Entry: IP /24, section Excluded Entry: IP The configuration stated above will be processed as follows, when it is utilized in a firewall rule: Connection requests may be addressed to IP addresses living in the network /24, but they may not address the excluded IP address Using Network Objects of Type Hostname Hostname objects may be used as: Source/Destination in rules within the Forwarding Firewall. Source/Destination in rules within the Local Firewall. Reference in the Entry list of Generic Network Objects. Hostname objects may NOT be used as reference in the Entry list of all other network object types. Hostname objects that cannot be resolved can never match in a rule. Consequently, when a non resolvable object is used in a rule, this rule cannot be processed correctly. Hostname objects will become non resolvable not only if they refer to a non existent host name, but also in case the DNS server queries are addressed to is unavailable. Do NOT use Hostname network objects in rules with the policy block. When the firewall is (re)started, it may take up to 10 seconds until DNS resolution is provided for all configured hostname network objects. Because the firewall is already active, it might happen that before the actually desired rule becomes active another rule matches a request. Active sessions are not revaluated when DNS resolution changes, but only when the rule itself is modified. Persistent sessions might are to be terminated manually in order to enable new connection establishment using the updated DNS entry. Monitoring Network Objects of Type Hostname DNS queries addressed to the DNS server configured in the box settings are triggered as soon as a hostname network objects is created. The result of these queries is visualized in the following places: In all views but the Dynamic Rules tab, DNS resolution is retrieved using the DNS server(s) known to the client running the graphical administration tool Barracuda NG Admin and NOT using the DNS server(s) known to the Barracuda NG Firewall running the firewall service. In the Entries column in the network object list. In the Rule Object list when the hostname object configured in the rule is used. In the Source/Destination window querying the rule object list when the hostname object is currently used. In the Rule Tester. In the Dynamic Rules tab of the Firewall Monitoring Interface. 3 / 5
4 Site Specific Network Objects Site specific network objects can be used to share single firewall rulesets for branch offices with template based network layout. This type of object inherits its content from the IP address or IP network defined in the Virtual Server s Server Properties of a branch office. 4 / 5
5 Figures 5 / 5
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings.
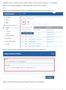 Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Application Rules - Allows the users to add or modify or remove Custom ruleset for firewall settings. Step [1]: Go to Endpoint Manager> CONFIGURATION TEMPLATES > Profiles Step [2]: Click Create icon and
Implementation Guide - VPN Network with Static Routing
 Implementation Guide - VPN Network with Static Routing This guide contains advanced topics and concepts. Follow the links in each section for step-by-step instructions on how to configure the following
Implementation Guide - VPN Network with Static Routing This guide contains advanced topics and concepts. Follow the links in each section for step-by-step instructions on how to configure the following
General Firewall Configuration
 To adjust resources used by your firewall service you can change the sizing parameters in the General Firewall Configuration (CONFIGURATION > Configuration Tree > Box > Infrastructure Services) of the
To adjust resources used by your firewall service you can change the sizing parameters in the General Firewall Configuration (CONFIGURATION > Configuration Tree > Box > Infrastructure Services) of the
Best Practice - Allow Aerohive Access Points Behind a CloudGen Firewall Access to Hive Manager NG
 Best Practice - Allow Aerohive Access Points Behind a CloudGen Firewall Access to Hive Manager NG Aerohive devices running HiveOS such as Aerohive Access Points must be able to communicate with either
Best Practice - Allow Aerohive Access Points Behind a CloudGen Firewall Access to Hive Manager NG Aerohive devices running HiveOS such as Aerohive Access Points must be able to communicate with either
History Page. Barracuda NextGen Firewall F
 The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
How to Configure DNS Sinkholing in the Firewall
 UDP DNS traffic handled by the Firewall service is monitored and, if a domain is found that is considered to be malicious, the A and AAAA DNS response is replaced by fake IP addresses. An access rule blocks
UDP DNS traffic handled by the Firewall service is monitored and, if a domain is found that is considered to be malicious, the A and AAAA DNS response is replaced by fake IP addresses. An access rule blocks
How to Set Up VPN Certificates
 For the VPN service, you can use either self-signed certificates or certificates that are generated by an external CA. In this article: Before You Begin Before you set up VPN certificates, verify that
For the VPN service, you can use either self-signed certificates or certificates that are generated by an external CA. In this article: Before You Begin Before you set up VPN certificates, verify that
BIG-IP Local Traffic Management: Basics. Version 12.1
 BIG-IP Local Traffic Management: Basics Version 12.1 Table of Contents Table of Contents Introduction to Local Traffic Management...7 About local traffic management...7 About the network map...7 Viewing
BIG-IP Local Traffic Management: Basics Version 12.1 Table of Contents Table of Contents Introduction to Local Traffic Management...7 About local traffic management...7 About the network map...7 Viewing
Load Balancing For Clustered Barracuda CloudGen WAF Instances in the New Microsoft Azure Management Portal
 Load Balancing For Clustered Barracuda CloudGen WAF Instances in the New Microsoft Azure Management This guide will walk you through the steps to load balance traffic across multiple instances of the Barracuda
Load Balancing For Clustered Barracuda CloudGen WAF Instances in the New Microsoft Azure Management This guide will walk you through the steps to load balance traffic across multiple instances of the Barracuda
How to Configure an ISP with DHCP
 This article provides information on how to configure an ISP with DHCP and specify the settings for the DHCP client. You can configure up to six DHCP links on a Barracuda NG Firewall. In this article:
This article provides information on how to configure an ISP with DHCP and specify the settings for the DHCP client. You can configure up to six DHCP links on a Barracuda NG Firewall. In this article:
How to Configure IPS Policies
 IPS policies control the behavior of the IPS when an attack is detected. You can define multiple IPS policies and apply them to individual firewall rules as needed. In this article: Default IPS Policy
IPS policies control the behavior of the IPS when an attack is detected. You can define multiple IPS policies and apply them to individual firewall rules as needed. In this article: Default IPS Policy
Step 3 - How to Configure Basic System Settings
 Before configuring the IP address and network settings, complete Step 2 - How to Configure IP Address, network Settings, and Firewall. Verify the computer and the are connected to the same network, with
Before configuring the IP address and network settings, complete Step 2 - How to Configure IP Address, network Settings, and Firewall. Verify the computer and the are connected to the same network, with
Barracuda Link Balancer
 Barracuda Networks Technical Documentation Barracuda Link Balancer Administrator s Guide Version 2.3 RECLAIM YOUR NETWORK Copyright Notice Copyright 2004-2011, Barracuda Networks www.barracuda.com v2.3-111215-01-1215
Barracuda Networks Technical Documentation Barracuda Link Balancer Administrator s Guide Version 2.3 RECLAIM YOUR NETWORK Copyright Notice Copyright 2004-2011, Barracuda Networks www.barracuda.com v2.3-111215-01-1215
The term "router" in this document refers to both routers and Layer 3 switches. Step Command Remarks. ipv6 host hostname ipv6-address
 Contents Configuring IPv6 DNS 1 Overview 1 Configuring the IPv6 DNS client 1 Configuring static domain name resolution 1 Configuring dynamic domain name resolution 1 Displaying and maintaining IPv6 DNS
Contents Configuring IPv6 DNS 1 Overview 1 Configuring the IPv6 DNS client 1 Configuring static domain name resolution 1 Configuring dynamic domain name resolution 1 Displaying and maintaining IPv6 DNS
OpenLM supports license monitoring of a wide, and ever growing variety of license managers.
 Interfacing the DSLS license manager KB4001c 1 Scope: OpenLM supports license monitoring of a wide, and ever growing variety of license managers. This application note elaborates the steps required to
Interfacing the DSLS license manager KB4001c 1 Scope: OpenLM supports license monitoring of a wide, and ever growing variety of license managers. This application note elaborates the steps required to
Configuring IPv6 DNS. Introduction to IPv6 DNS. Configuring the IPv6 DNS client. Configuring static domain name resolution
 Contents Configuring IPv6 DNS 2 Introduction to IPv6 DNS 2 Configuring the IPv6 DNS client 2 Configuring static domain name resolution 2 Configuring dynamic domain name resolution 2 Displaying and maintaining
Contents Configuring IPv6 DNS 2 Introduction to IPv6 DNS 2 Configuring the IPv6 DNS client 2 Configuring static domain name resolution 2 Configuring dynamic domain name resolution 2 Displaying and maintaining
Best Practice - Protect Against TCP SYN Flooding Attacks with TCP Accept Policies
 Best Practice - Protect Against TCP SYN Flooding Attacks with TCP Accept Policies In order to establish a TCP connection, the TCP three-way handshake must be completed. You can use different accept policies
Best Practice - Protect Against TCP SYN Flooding Attacks with TCP Accept Policies In order to establish a TCP connection, the TCP three-way handshake must be completed. You can use different accept policies
3. In the upper left hand corner, click the Barracuda logo ( ) then click Settings 4. Select the check box for SPoE as default.
 Week 1 Lab Lab 1: Connect to the Barracuda network. 1. Download the Barracuda NG Firewall Admin 5.4 2. Launch NG Admin 3. In the upper left hand corner, click the Barracuda logo ( ) then click Settings
Week 1 Lab Lab 1: Connect to the Barracuda network. 1. Download the Barracuda NG Firewall Admin 5.4 2. Launch NG Admin 3. In the upper left hand corner, click the Barracuda logo ( ) then click Settings
How to Configure an IPsec Site-to-Site VPN to a Windows Azure VPN Gateway
 How to Configure an IPsec Site-to-Site VPN to a Windows Azure VPN Gateway To connect your on-premise Barracuda NG Firewall to the static VPN gateway service in the Windows Azure cloud create a IPsec tunnel
How to Configure an IPsec Site-to-Site VPN to a Windows Azure VPN Gateway To connect your on-premise Barracuda NG Firewall to the static VPN gateway service in the Windows Azure cloud create a IPsec tunnel
Firewall Configuration Example
 In order to provide a comprehensive description of the possibilities of creating rules for the Barracuda NG Firewall, the following article shows an example setup configuration with a LAN, the internet,
In order to provide a comprehensive description of the possibilities of creating rules for the Barracuda NG Firewall, the following article shows an example setup configuration with a LAN, the internet,
Realms and Identity Policies
 The following topics describe realms and identity policies: Introduction:, page 1 Creating a Realm, page 5 Creating an Identity Policy, page 11 Creating an Identity Rule, page 15 Managing Realms, page
The following topics describe realms and identity policies: Introduction:, page 1 Creating a Realm, page 5 Creating an Identity Policy, page 11 Creating an Identity Rule, page 15 Managing Realms, page
How to Configure ATP in the Firewall
 Configure when and which types of files are uploaded to the Barracuda ATP Cloud. Files with a size is limited by the Large File Watermark of the virus scanner and the 8 MB upload limit for the ATP cloud,
Configure when and which types of files are uploaded to the Barracuda ATP Cloud. Files with a size is limited by the Large File Watermark of the virus scanner and the 8 MB upload limit for the ATP cloud,
How to Add Domains and DNS Records
 Configure the Barracuda NextGen X-Series Firewall to be the authoritative DNS server for your domains or subdomains to take advantage of Split DNS or dead link detection. Step 1. Make the X-Series Firewall
Configure the Barracuda NextGen X-Series Firewall to be the authoritative DNS server for your domains or subdomains to take advantage of Split DNS or dead link detection. Step 1. Make the X-Series Firewall
CC Box Execution Page
 This article describes the functionalities of the Box Execution view of the Barracuda NG Control Center. Introduction The Barracuda NG Control Center control facility allows remote execution of scripts
This article describes the functionalities of the Box Execution view of the Barracuda NG Control Center. Introduction The Barracuda NG Control Center control facility allows remote execution of scripts
Example - Reverse Proxy for Exchange Services
 The reverse proxy redirects incoming requests from Microsoft Exchange Server services to clients without providing the origin details. This example configuration shows how to configure a reverse proxy
The reverse proxy redirects incoming requests from Microsoft Exchange Server services to clients without providing the origin details. This example configuration shows how to configure a reverse proxy
BIG-IP Access Policy Manager : Secure Web Gateway. Version 13.0
 BIG-IP Access Policy Manager : Secure Web Gateway Version 13.0 Table of Contents Table of Contents BIG-IP APM Secure Web Gateway Overview...9 About APM Secure Web Gateway... 9 About APM benefits for web
BIG-IP Access Policy Manager : Secure Web Gateway Version 13.0 Table of Contents Table of Contents BIG-IP APM Secure Web Gateway Overview...9 About APM Secure Web Gateway... 9 About APM benefits for web
DEPLOYMENT GUIDE DEPLOYING F5 WITH ORACLE ACCESS MANAGER
 DEPLOYMENT GUIDE DEPLOYING F5 WITH ORACLE ACCESS MANAGER Table of Contents Table of Contents Introducing the F5 and Oracle Access Manager configuration Prerequisites and configuration notes... 1 Configuration
DEPLOYMENT GUIDE DEPLOYING F5 WITH ORACLE ACCESS MANAGER Table of Contents Table of Contents Introducing the F5 and Oracle Access Manager configuration Prerequisites and configuration notes... 1 Configuration
Table of Contents 1 IKE 1-1
 Table of Contents 1 IKE 1-1 IKE Overview 1-1 Security Mechanism of IKE 1-1 Operation of IKE 1-1 Functions of IKE in IPsec 1-2 Relationship Between IKE and IPsec 1-3 Protocols 1-3 Configuring IKE 1-3 Configuration
Table of Contents 1 IKE 1-1 IKE Overview 1-1 Security Mechanism of IKE 1-1 Operation of IKE 1-1 Functions of IKE in IPsec 1-2 Relationship Between IKE and IPsec 1-3 Protocols 1-3 Configuring IKE 1-3 Configuration
Running the Setup Web UI
 The Cisco Prime IP Express setup interview in the web UI takes you through a series of consecutive pages to set up a basic configuration. For an introduction and details on the basic navigation for the
The Cisco Prime IP Express setup interview in the web UI takes you through a series of consecutive pages to set up a basic configuration. For an introduction and details on the basic navigation for the
How to Configure Guest Access with the Ticketing System
 How to Configure Guest Access with the Ticketing System Set up a login or ticketing system to temporarily grant access to guest users. Ticketing admins assign guest tickets to the users. The user credentials
How to Configure Guest Access with the Ticketing System Set up a login or ticketing system to temporarily grant access to guest users. Ticketing admins assign guest tickets to the users. The user credentials
FieldView. Management Suite
 FieldView The FieldView Management Suite (FMS) system allows administrators to view the status of remote FieldView System endpoints, create and apply system configurations, and manage and apply remote
FieldView The FieldView Management Suite (FMS) system allows administrators to view the status of remote FieldView System endpoints, create and apply system configurations, and manage and apply remote
How to Configure CC Administrative Roles
 The global settings listed in the following article define the restrictions for administrative roles. They are needed when a new administrator is introduced (see: How to Create a New Admin Profile [1]
The global settings listed in the following article define the restrictions for administrative roles. They are needed when a new administrator is introduced (see: How to Create a New Admin Profile [1]
How to Configure DNS Zones
 The Barracuda NG Firewall DNS configuration object contains two predefined zones: _template and '.' To be able to edit and specify DNS zones within the Barracuda NG Firewall DNS configuration, you must
The Barracuda NG Firewall DNS configuration object contains two predefined zones: _template and '.' To be able to edit and specify DNS zones within the Barracuda NG Firewall DNS configuration, you must
Office and Express Print Release High Availability Setup Guide
 Office and Express Print Release High Availability Setup Guide Version 1.0 2017 EQ-HA-DCE-20170512 Print Release High Availability Setup Guide Document Revision History Revision Date May 12, 2017 September
Office and Express Print Release High Availability Setup Guide Version 1.0 2017 EQ-HA-DCE-20170512 Print Release High Availability Setup Guide Document Revision History Revision Date May 12, 2017 September
Managing Caching DNS Server
 This chapter explains how to set the Caching DNS server parameters. Before you proceed with the tasks in this chapter, see Introduction to the Domain Name System which explains the basics of DNS. Configuring
This chapter explains how to set the Caching DNS server parameters. Before you proceed with the tasks in this chapter, see Introduction to the Domain Name System which explains the basics of DNS. Configuring
EdgeConnect for Amazon Web Services (AWS)
 Silver Peak Systems EdgeConnect for Amazon Web Services (AWS) Dinesh Fernando 2-22-2018 Contents EdgeConnect for Amazon Web Services (AWS) Overview... 1 Deploying EC-V Router Mode... 2 Topology... 2 Assumptions
Silver Peak Systems EdgeConnect for Amazon Web Services (AWS) Dinesh Fernando 2-22-2018 Contents EdgeConnect for Amazon Web Services (AWS) Overview... 1 Deploying EC-V Router Mode... 2 Topology... 2 Assumptions
Servicing ACNS Devices and Origin Servers
 CHAPTER 13 This chapter explains how you can minimize the impact upon content delivery services when you perform maintenance on your ACNS network devices, such as replacing failed hardware or adding or
CHAPTER 13 This chapter explains how you can minimize the impact upon content delivery services when you perform maintenance on your ACNS network devices, such as replacing failed hardware or adding or
How to Configure and Use High Availability
 For redundancy and reliability, you can set up two Barracuda NextGen X-Series Firewalls in a high availability (HA) cluster. During normal operations, the primary unit is active while the secondary unit
For redundancy and reliability, you can set up two Barracuda NextGen X-Series Firewalls in a high availability (HA) cluster. During normal operations, the primary unit is active while the secondary unit
How to Configure a Site-to-Site IPsec IKEv1 VPN Tunnel
 How to Configure a Site-to-Site IPsec IKEv1 VPN Tunnel The Barracuda CloudGen Firewall can establish IPsec VPN tunnels to any standard-compliant, third-party IKEv1 IPsec VPN gateway. The Site-to-Site IPsec
How to Configure a Site-to-Site IPsec IKEv1 VPN Tunnel The Barracuda CloudGen Firewall can establish IPsec VPN tunnels to any standard-compliant, third-party IKEv1 IPsec VPN gateway. The Site-to-Site IPsec
Contents. Limitations. Prerequisites. Configuration
 Welcome to your Netmail Secure trial The trial version of Netmail Secure allows you to evaluate Netmail Secure from within your own corporate domain. Included is a sample mail feed that is automatically
Welcome to your Netmail Secure trial The trial version of Netmail Secure allows you to evaluate Netmail Secure from within your own corporate domain. Included is a sample mail feed that is automatically
BIG-IP DNS: Monitors Reference. Version 12.1
 BIG-IP DNS: Monitors Reference Version 12.1 Table of Contents Table of Contents Monitors Concepts...5 Purpose of monitors...5 Benefits of monitors...5 Methods of monitoring...5 Comparison of monitoring
BIG-IP DNS: Monitors Reference Version 12.1 Table of Contents Table of Contents Monitors Concepts...5 Purpose of monitors...5 Benefits of monitors...5 Methods of monitoring...5 Comparison of monitoring
Lab Guide. Barracuda NextGen Firewall F-Series Microsoft Azure - NGF0501
 Barracuda NextGen Firewall F-Series Microsoft Azure - NGF0501 Lab Guide Official training material for Barracuda certified trainings and Authorized Training Centers. Edition 2018 Revision 1.0 campus.barracuda.com
Barracuda NextGen Firewall F-Series Microsoft Azure - NGF0501 Lab Guide Official training material for Barracuda certified trainings and Authorized Training Centers. Edition 2018 Revision 1.0 campus.barracuda.com
How to Configure Authentication and Access Control (AAA)
 How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How to Configure ATP in the HTTP Proxy
 Configure when and which types of files are uploaded to the Barracuda ATP Cloud for traffic passing through the HTTP proxy service. Users will receive downloaded files immediately. When files with a risk
Configure when and which types of files are uploaded to the Barracuda ATP Cloud for traffic passing through the HTTP proxy service. Users will receive downloaded files immediately. When files with a risk
Barracuda Terminal Server Agent Debug Log Messages
 Barracuda Terminal Server Agent Debug Log Messages The Barracuda TS Agent writes a debug log to help you monitor activity on your server and identify possible problems. Viewing the Debug Log To view the
Barracuda Terminal Server Agent Debug Log Messages The Barracuda TS Agent writes a debug log to help you monitor activity on your server and identify possible problems. Viewing the Debug Log To view the
CC Remote Execution Page
 This article describes the functionalities of the Remote Execution page and provides a setup example. Remote execution can be used to execute nonrecurring tasks, such as the removal of unwanted files or
This article describes the functionalities of the Remote Execution page and provides a setup example. Remote execution can be used to execute nonrecurring tasks, such as the removal of unwanted files or
Installing Your System Using Manual Deployment
 Installing Your System Using Manual Deployment General Concepts For Your System Deployment, page 1 Installation Checklist, page 2 Required Information For a Manual Deployment, page 3 Deploying the OVA
Installing Your System Using Manual Deployment General Concepts For Your System Deployment, page 1 Installation Checklist, page 2 Required Information For a Manual Deployment, page 3 Deploying the OVA
AWS Reference Architecture - CloudGen Firewall Auto Scaling Cluster
 AWS Reference Architecture - CloudGen Firewall Auto Scaling Cluster Protecting highly dynamic AWS resources with a static firewall setup is neither efficient nor economical. A CloudGen Firewall Auto Scaling
AWS Reference Architecture - CloudGen Firewall Auto Scaling Cluster Protecting highly dynamic AWS resources with a static firewall setup is neither efficient nor economical. A CloudGen Firewall Auto Scaling
BIG-IP Local Traffic Manager : Monitors Reference 13.0
 BIG-IP Local Traffic Manager : Monitors Reference 13.0 Table of Contents Table of Contents Monitors Concepts... 5 Purpose of monitors...5 Benefits of monitors... 5 About icheck functionality for monitors...
BIG-IP Local Traffic Manager : Monitors Reference 13.0 Table of Contents Table of Contents Monitors Concepts... 5 Purpose of monitors...5 Benefits of monitors... 5 About icheck functionality for monitors...
Digi Connect WAN / ConnectPort WAN Cellular Setup of Surelink
 Digi Connect WAN / ConnectPort WAN Cellular Setup of Surelink 1. SureLink Settings The following options configure the SureLink settings for your Digi device. These settings ensure that your device is
Digi Connect WAN / ConnectPort WAN Cellular Setup of Surelink 1. SureLink Settings The following options configure the SureLink settings for your Digi device. These settings ensure that your device is
User Identity Sources
 The following topics describe Firepower System user identity sources, which are sources for user awareness. These users can be controlled with identity and access control policies: About, on page 1 The
The following topics describe Firepower System user identity sources, which are sources for user awareness. These users can be controlled with identity and access control policies: About, on page 1 The
ForeScout CounterACT. Configuration Guide. Version 1.2
 ForeScout CounterACT Core Extensions Module: NetFlow Plugin Version 1.2 Table of Contents About NetFlow Integration... 3 How it Works... 3 Supported NetFlow Versions... 3 What to Do... 3 Requirements...
ForeScout CounterACT Core Extensions Module: NetFlow Plugin Version 1.2 Table of Contents About NetFlow Integration... 3 How it Works... 3 Supported NetFlow Versions... 3 What to Do... 3 Requirements...
How to Deploy the Barracuda NG Firewall in an Amazon Virtual Private Cloud
 How to Deploy the Barracuda NG Firewall in an Amazon Virtual Private Cloud The Barracuda NG Firewall can run as a virtual appliance in the Amazon cloud as a gateway device for Amazon EC2 instances in an
How to Deploy the Barracuda NG Firewall in an Amazon Virtual Private Cloud The Barracuda NG Firewall can run as a virtual appliance in the Amazon cloud as a gateway device for Amazon EC2 instances in an
Avaya Aura TM System Platform R6.0.1 Service Pack Release Notes Issue 1.4
 Avaya Aura TM Service Pack Release Notes Issue 1.4 INTRODUCTION This document introduces the Avaya Aura TM System Platform Release 6.0.1 Service Pack and describes known issues and the issues resolved
Avaya Aura TM Service Pack Release Notes Issue 1.4 INTRODUCTION This document introduces the Avaya Aura TM System Platform Release 6.0.1 Service Pack and describes known issues and the issues resolved
The following topics explain how to get started configuring Firepower Threat Defense. Table 1: Firepower Device Manager Supported Models
 The following topics explain how to get started configuring Firepower Threat Defense. Is This Guide for You?, page 1 Logging Into the System, page 2 Setting Up the System, page 6 Configuration Basics,
The following topics explain how to get started configuring Firepower Threat Defense. Is This Guide for You?, page 1 Logging Into the System, page 2 Setting Up the System, page 6 Configuration Basics,
This option lets you reset the password that you use to log in if you do not remember it. To change the password,
 User s Guide Overview IDrive offers the most cost effective BMR functionality with onsite disk image backup for SMBs. Store entire data of hard disks including the operating system (OS) and application
User s Guide Overview IDrive offers the most cost effective BMR functionality with onsite disk image backup for SMBs. Store entire data of hard disks including the operating system (OS) and application
How to Configure Azure Route Tables (UDR) using Azure Portal and ARM
 How to Configure Azure Route Tables (UDR) using Azure Portal and ARM Azure Route Tables, or User Defined Routing, allow you to create network routes so that your F-Series Firewall VM can handle the traffic
How to Configure Azure Route Tables (UDR) using Azure Portal and ARM Azure Route Tables, or User Defined Routing, allow you to create network routes so that your F-Series Firewall VM can handle the traffic
How to Configure a Client-to-Site L2TP/IPsec VPN
 Follow the instructions in this article to configure a client-to-site L2TP/IPsec VPN. With this configuration, IPsec encrypts the payload data of the VPN because L2TP does not provide encryption. In this
Follow the instructions in this article to configure a client-to-site L2TP/IPsec VPN. With this configuration, IPsec encrypts the payload data of the VPN because L2TP does not provide encryption. In this
BIG-IP Network Firewall: Policies and Implementations. Version 13.0
 BIG-IP Network Firewall: Policies and Implementations Version 13.0 Table of Contents Table of Contents About the Network Firewall...9 What is the BIG-IP Network Firewall?...9 About firewall modes... 9
BIG-IP Network Firewall: Policies and Implementations Version 13.0 Table of Contents Table of Contents About the Network Firewall...9 What is the BIG-IP Network Firewall?...9 About firewall modes... 9
Cisco Expressway Cluster Creation and Maintenance
 Cisco Expressway Cluster Creation and Maintenance Deployment Guide First Published: December 2009 Last Updated: April 2017 Cisco Expressway X8.9.2 Cisco Systems, Inc. www.cisco.com Contents Preface 3 Change
Cisco Expressway Cluster Creation and Maintenance Deployment Guide First Published: December 2009 Last Updated: April 2017 Cisco Expressway X8.9.2 Cisco Systems, Inc. www.cisco.com Contents Preface 3 Change
For Trace and Log Central to work, you must resolve DNS lookup for all nodes in the cluster on the client machine.
 Trace and Log Central, page 1 Log Viewers, page 42 Plugins, page 45 Trace and Log Central For Trace and Log Central to work, you must resolve DNS lookup for all nodes in the cluster on the client machine.
Trace and Log Central, page 1 Log Viewers, page 42 Plugins, page 45 Trace and Log Central For Trace and Log Central to work, you must resolve DNS lookup for all nodes in the cluster on the client machine.
Exam Questions PCNSE6
 Exam Questions PCNSE6 Palo Alto Networks Certified Network Security Engineer 6.0 https://www.2passeasy.com/dumps/pcnse6/ 1.To create a custom signature object for an Application Override Policy, which
Exam Questions PCNSE6 Palo Alto Networks Certified Network Security Engineer 6.0 https://www.2passeasy.com/dumps/pcnse6/ 1.To create a custom signature object for an Application Override Policy, which
How to Configure an IKEv1 IPsec Site-to-Site VPN to the Static Microsoft Azure VPN Gateway
 How to Configure an IKEv1 IPsec Site-to-Site VPN to the Static Microsoft Azure VPN Gateway You can configure your local Barracuda NextGen Firewall F-Series to connect to the static IPsec VPN gateway service
How to Configure an IKEv1 IPsec Site-to-Site VPN to the Static Microsoft Azure VPN Gateway You can configure your local Barracuda NextGen Firewall F-Series to connect to the static IPsec VPN gateway service
A. Verify that the IKE gateway proposals on the initiator and responder are the same.
 Volume: 64 Questions Question: 1 You need to configure an IPsec tunnel between a remote site and a hub site. The SRX Series device at the remote site receives a dynamic IP address on the external interface
Volume: 64 Questions Question: 1 You need to configure an IPsec tunnel between a remote site and a hub site. The SRX Series device at the remote site receives a dynamic IP address on the external interface
Barracuda NextGen Report Creator
 The creates customized reports using statistics and logs collected on Barracuda NextGen F-Series Firewalls. Each report can be configured to use multiple appliances, custom or predefined report data templates,
The creates customized reports using statistics and logs collected on Barracuda NextGen F-Series Firewalls. Each report can be configured to use multiple appliances, custom or predefined report data templates,
Pexip Infinity and Amazon Web Services Deployment Guide
 Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
Pexip Infinity and Amazon Web Services Deployment Guide Contents Introduction 1 Deployment guidelines 2 Configuring AWS security groups 4 Deploying a Management Node in AWS 6 Deploying a Conferencing Node
How to Deploy a Barracuda NG Vx using Barracuda NG Install on a VMware Hypervisor
 How to Deploy a Barracuda NG Vx using Barracuda NG Install on a VMware Hypervisor The OVA package uses a default configuration that may not be suitable for your deployment. If you want to use multiple
How to Deploy a Barracuda NG Vx using Barracuda NG Install on a VMware Hypervisor The OVA package uses a default configuration that may not be suitable for your deployment. If you want to use multiple
Cisco TelePresence VCS Cluster Creation and Maintenance
 Cisco TelePresence VCS Cluster Creation and Maintenance Deployment Guide Cisco VCS X8.5 Cisco TMS 13.2 or later December 2014 Contents Introduction 4 Prerequisites 5 Upgrading an X7.1 or later cluster
Cisco TelePresence VCS Cluster Creation and Maintenance Deployment Guide Cisco VCS X8.5 Cisco TMS 13.2 or later December 2014 Contents Introduction 4 Prerequisites 5 Upgrading an X7.1 or later cluster
How to Create a *.vpn File
 You can import VPN profiles and Barracuda Personal Licenses to the Barracuda Network Access Client and the Barracuda VPN Client using configuration files with the suffix *.vpn that can be configured and
You can import VPN profiles and Barracuda Personal Licenses to the Barracuda Network Access Client and the Barracuda VPN Client using configuration files with the suffix *.vpn that can be configured and
Paloalto Networks. Exam Questions PCNSE6. Palo Alto Networks Certified Network Security Engineer 6.0. Version:Demo
 Paloalto Networks Exam Questions PCNSE6 Palo Alto Networks Certified Network Security Engineer 6.0 Version:Demo 1.To create a custom signature object for an Application Override Policy, which of the following
Paloalto Networks Exam Questions PCNSE6 Palo Alto Networks Certified Network Security Engineer 6.0 Version:Demo 1.To create a custom signature object for an Application Override Policy, which of the following
Configuring Cisco IOS IP SLAs DNS Operations
 Configuring Cisco IOS IP SLAs DNS Operations First Published: August 14, 2006 Last Updated: January 6, 2011 This module describes how to configure the Cisco IOS IP Service Level Agreements (SLAs) Domain
Configuring Cisco IOS IP SLAs DNS Operations First Published: August 14, 2006 Last Updated: January 6, 2011 This module describes how to configure the Cisco IOS IP Service Level Agreements (SLAs) Domain
IMC Network Traffic Analyzer 7.2 (E0401P04) Copyright 2016 Hewlett Packard Enterprise Development LP
 Network Traffic Analyzer 7.2 (E0401P04) Copyright 2016 Hewlett Packard Enterprise Development LP Table of Contents 1. What's New in this Release 2. Problems Fixed in this Release 3. Software Distribution
Network Traffic Analyzer 7.2 (E0401P04) Copyright 2016 Hewlett Packard Enterprise Development LP Table of Contents 1. What's New in this Release 2. Problems Fixed in this Release 3. Software Distribution
How to Configure a Dynamic Mesh VPN with the GTI Editor
 How to Configure a Dynamic Mesh VPN with the GTI Editor The GTI editor greatly simplifies creating a dynamic mesh VPN network with a large number of NG Firewalls. You can enable dynamic mesh for all VPN
How to Configure a Dynamic Mesh VPN with the GTI Editor The GTI editor greatly simplifies creating a dynamic mesh VPN network with a large number of NG Firewalls. You can enable dynamic mesh for all VPN
Monitoring the Device
 The system includes dashboards and an Event Viewer that you can use to monitor the device and traffic that is passing through the device. Enable Logging to Obtain Traffic Statistics, page 1 Monitoring
The system includes dashboards and an Event Viewer that you can use to monitor the device and traffic that is passing through the device. Enable Logging to Obtain Traffic Statistics, page 1 Monitoring
Remote Access via Cisco VPN Client
 Remote Access via Cisco VPN Client General Information This guide describes step by step the configuration of a remote access to the Astaro Security Gateway by using the Cisco VPN Client. The Cisco VPN
Remote Access via Cisco VPN Client General Information This guide describes step by step the configuration of a remote access to the Astaro Security Gateway by using the Cisco VPN Client. The Cisco VPN
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Contents. Platform Compatibility. Directory Connector SonicWALL Directory Services Connector 3.1.7
 Directory Connector SonicWALL Directory Services Connector 3.1.7 Contents Platform Compatibility... 1 New Features... 2 Known Issues... 3 Resolved Issues... 5 Overview... 7 About SonicWALL Single Sign-On
Directory Connector SonicWALL Directory Services Connector 3.1.7 Contents Platform Compatibility... 1 New Features... 2 Known Issues... 3 Resolved Issues... 5 Overview... 7 About SonicWALL Single Sign-On
GSS Administration and Troubleshooting
 CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
Contents. Platform Compatibility. Directory Connector SonicWALL Directory Services Connector 3.1.7
 Directory Connector SonicWALL Directory Services Connector 3.1.7 Contents Platform Compatibility... 1 New Features... 2 Known Issues... 3 Resolved Issues... 5 Overview... 7 About SonicWALL Single Sign-On
Directory Connector SonicWALL Directory Services Connector 3.1.7 Contents Platform Compatibility... 1 New Features... 2 Known Issues... 3 Resolved Issues... 5 Overview... 7 About SonicWALL Single Sign-On
RSA SecurID Implementation
 Partner Information Partner Name Website Product Name Barracuda Networks Version & Platform x60 Series Product Description Product Category Solution Summary www.barracudanetworks.com Product Information
Partner Information Partner Name Website Product Name Barracuda Networks Version & Platform x60 Series Product Description Product Category Solution Summary www.barracudanetworks.com Product Information
In ZENworks, Join Proxy is a role that is by default assigned to Primary Servers; you can also assign this role to Satellites.
 ZENworks Remote Management - Using Join Proxy August 2018 Typically, when you want to remote control a device that is in a private network or on the other side of a firewall or router that is behind NAT
ZENworks Remote Management - Using Join Proxy August 2018 Typically, when you want to remote control a device that is in a private network or on the other side of a firewall or router that is behind NAT
How to Configure a Site-to-Site IPsec IKEv1 VPN Tunnel
 How to Configure a Site-to-Site IPsec IKEv1 VPN Tunnel The Barracuda NextGen Firewall F-Series can establish IPsec VPN tunnels to any standard-compliant third party IKEv1 IPsec VPN gateway. The Site-to-Site
How to Configure a Site-to-Site IPsec IKEv1 VPN Tunnel The Barracuda NextGen Firewall F-Series can establish IPsec VPN tunnels to any standard-compliant third party IKEv1 IPsec VPN gateway. The Site-to-Site
How to Configure a Remote Management Tunnel for Barracuda NG Firewalls
 How to Configure a Remote Management Tunnel for Barracuda NG Firewalls If the managed NG Firewall can not directly reach the NG Control Center it must connect via a remote management tunnel. The remote
How to Configure a Remote Management Tunnel for Barracuda NG Firewalls If the managed NG Firewall can not directly reach the NG Control Center it must connect via a remote management tunnel. The remote
WhatsConfigured v3.1 User Guide
 WhatsConfigured v3.1 User Guide Contents Table of Contents Welcome to WhatsConfigured v3.1 Finding more information and updates... 1 Sending feedback... 2 Deploying WhatsConfigured STEP 1: Prepare the
WhatsConfigured v3.1 User Guide Contents Table of Contents Welcome to WhatsConfigured v3.1 Finding more information and updates... 1 Sending feedback... 2 Deploying WhatsConfigured STEP 1: Prepare the
Cisco Expressway Cluster Creation and Maintenance
 Cisco Expressway Cluster Creation and Maintenance Deployment Guide Cisco Expressway X8.6 July 2015 Contents Introduction 4 Prerequisites 5 Upgrading an X8.n cluster to X8.6 6 Prerequisites 6 Upgrade Expressway
Cisco Expressway Cluster Creation and Maintenance Deployment Guide Cisco Expressway X8.6 July 2015 Contents Introduction 4 Prerequisites 5 Upgrading an X8.n cluster to X8.6 6 Prerequisites 6 Upgrade Expressway
Deploying the BIG-IP System v10 with Oracle s BEA WebLogic
 DEPLOYMENT GUIDE Deploying the BIG-IP System v10 with Oracle s BEA WebLogic Version 1.0 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Oracle s BEA WebLogic Prerequisites and
DEPLOYMENT GUIDE Deploying the BIG-IP System v10 with Oracle s BEA WebLogic Version 1.0 Table of Contents Table of Contents Deploying the BIG-IP system v10 with Oracle s BEA WebLogic Prerequisites and
Managing the System Event Log
 Managing the System Event Log This chapter includes the following sections: System Event Log, page 1 Viewing the System Event Log for an Individual Server, page 2 Viewing the System Event Log for the Servers
Managing the System Event Log This chapter includes the following sections: System Event Log, page 1 Viewing the System Event Log for an Individual Server, page 2 Viewing the System Event Log for the Servers
Remote Authentication
 Authentication Services, page 1 Guidelines and Recommendations for Providers, page 2 User Attributes in Providers, page 2 Two-Factor Authentication, page 4 LDAP Providers and Groups, page 5 RADIUS Providers,
Authentication Services, page 1 Guidelines and Recommendations for Providers, page 2 User Attributes in Providers, page 2 Two-Factor Authentication, page 4 LDAP Providers and Groups, page 5 RADIUS Providers,
Configuring DNS Sticky
 CHAPTER 8 This chapter describes how to configure a GSS to support Domain Name System (DNS) stickiness to answer requests received from client D-proxies. The GSS supports DNS sticky both locally and globally
CHAPTER 8 This chapter describes how to configure a GSS to support Domain Name System (DNS) stickiness to answer requests received from client D-proxies. The GSS supports DNS sticky both locally and globally
Configuring IP SLAs TCP Connect Operations
 This module describes how to configure an IP Service Level Agreements (SLAs) TCP Connect operation to measure the response time taken to perform a TCP Connect operation between a Cisco router and devices
This module describes how to configure an IP Service Level Agreements (SLAs) TCP Connect operation to measure the response time taken to perform a TCP Connect operation between a Cisco router and devices
Cisco Unified Customer Voice Portal
 This chapter explains the procedures you must perform to configure the Cisco Unified CVP Call and OAMP servers on Side A and Side B. Validate Network Card, page 2 Configure Unified CVP Call Server, page
This chapter explains the procedures you must perform to configure the Cisco Unified CVP Call and OAMP servers on Side A and Side B. Validate Network Card, page 2 Configure Unified CVP Call Server, page
Using DNS Service for Amplification Attack
 Using DNS Service for Amplification Attack Outline Use DNS service to achieve load balancing for a server cluster Carry out an amplification attack by taking advantage of DNS service Enforce firewall rules
Using DNS Service for Amplification Attack Outline Use DNS service to achieve load balancing for a server cluster Carry out an amplification attack by taking advantage of DNS service Enforce firewall rules
How to Set Up External CA VPN Certificates
 To configure a client-to-site, or site-to-site VPN using s created by External CA, you must create the following VPN s for the VPN service to be able to authenticate Before you begin Use an external CA
To configure a client-to-site, or site-to-site VPN using s created by External CA, you must create the following VPN s for the VPN service to be able to authenticate Before you begin Use an external CA
HP Load Balancing Module
 HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-4218 Software version: Feature 3221 Document version: 6PW100-20130326 Legal and notice information Copyright 2013 Hewlett-Packard
HP Load Balancing Module Load Balancing Configuration Guide Part number: 5998-4218 Software version: Feature 3221 Document version: 6PW100-20130326 Legal and notice information Copyright 2013 Hewlett-Packard
Cluster creation and maintenance
 Cluster creation and maintenance Cisco TelePresence Deployment Guide Cisco VCS X6.1 Cisco TMS 12.6 or later D14367.08 May 2011 Contents Contents Document revision history... 5 Introduction... 6 Prerequisites...
Cluster creation and maintenance Cisco TelePresence Deployment Guide Cisco VCS X6.1 Cisco TMS 12.6 or later D14367.08 May 2011 Contents Contents Document revision history... 5 Introduction... 6 Prerequisites...
DHCP and DDNS Services for Threat Defense
 The following topics explain DHCP and DDNS services and how to configure them on Threat Defense devices. About DHCP and DDNS Services, on page 1 Guidelines for DHCP and DDNS Services, on page 3 Configure
The following topics explain DHCP and DDNS services and how to configure them on Threat Defense devices. About DHCP and DDNS Services, on page 1 Guidelines for DHCP and DDNS Services, on page 3 Configure
Administration Guide - NetApp File Archiver
 Page 1 of 100 Administration Guide - NetApp File Archiver TABLE OF CONTENTS OVERVIEW Introduction Key Features Terminology SYSTEM REQUIREMENTS DEPLOYMENT Installation Method 1: Interactive Install Method
Page 1 of 100 Administration Guide - NetApp File Archiver TABLE OF CONTENTS OVERVIEW Introduction Key Features Terminology SYSTEM REQUIREMENTS DEPLOYMENT Installation Method 1: Interactive Install Method
How to Perform a Manual High Availability Failover
 How to Perform a Manual High Availability Failover In an HA setup, the primary CloudGen Firewall stays active until a serious problem occurs. If virtual servers and services must be shut down (for example,
How to Perform a Manual High Availability Failover In an HA setup, the primary CloudGen Firewall stays active until a serious problem occurs. If virtual servers and services must be shut down (for example,
Active Directory as a Probe and a Provider
 Active Directory (AD) is a highly secure and precise source from which to receive user identity information, including user name, IP address and domain name. The AD probe, a Passive Identity service, collects
Active Directory (AD) is a highly secure and precise source from which to receive user identity information, including user name, IP address and domain name. The AD probe, a Passive Identity service, collects
Configuring WO Automation for Radio for TuneGenie
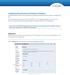 Configuring WO Automation for Radio for TuneGenie As WO Automation for Radio events fire, XML data is published through Device Server through a configured TCP port. First create the Device Server TCP Port,
Configuring WO Automation for Radio for TuneGenie As WO Automation for Radio events fire, XML data is published through Device Server through a configured TCP port. First create the Device Server TCP Port,
