Migrating to EJBCA A Study Guide
|
|
|
- Alvin Lewis
- 5 years ago
- Views:
Transcription
1 Migrating to EJBCA A Study Guide PrimeKey
2 Contents Migrating to EJBCA Introduction Keon CA EJBCA Detailed HOW-TO Migration of KCAs signing keys Importing CA Importing user certificates About PrimeKey Solutions AB
3 PrimeKey Solutions AB - Migrating to EJBCA 3 Migrating to EJBCA Introduction This document is written to help illustrate how to migrate from an another CA to EJBCA. In order to demonstrate specific steps and to help reader reproduce those steps, one specific CA was chosen - RSA Keon CA. The general idea how to migrate is the same for other CA implemnentations. Migration from the another CA to EJBCA consists from following steps: Migration of the CAs signing keys on ncipher HSM, so that the keys kan be used by EJBCA Import of the CA within EJBCA Import of the user certificates in EJBCA This document outlines how to migrate a simple installation of KCA to EJBCA. We recommend to do first a test migration as to be familiar with the process. Keon CA An setup of KCA on a target environment: Windows Server 2003 KCA 6.5 One root CA TestKCARootCA One sub CA TestKCASubCA Signing keys for the CAs on ncipher nshield PCI card 5 users issued by TestKCASubCA After the installation of this environment, we make a backup of ncipher security world, cacertificates and user certificates. EJBCA A target environment for EJBCA is chosen: Utuntu Linux 7.04 AMD64 JBoss 4.2.0, MySQL 5.0 EJBCA 3.5 or later; 3.9 recommended One root CA TestKCARootCA One sub CA TestKCASubCA Signing keys for the CAs on ncipher nshield PCI kort 5 users issued by TestKCASubCA
4 4 PrimeKey Solutions AB - Migrating to EJBCA Detailed HOW-TO Migration of KCAs signing keys PKCS#11 Configure PKCS#11 for ncipher. For ncipher, the slot number is some virtual slot, where we do not know the name of it. Fortunately, one can use the default slot by simply omitting to give theslot number. In order to use ncipher PKCS#11, one has to set up some parameters. Create file /opt/nfast/cknfastrc with this content: CKNFAST_LOADSHARING=1 CKNFAST_NO_ACCELERATOR_SLOTS=1 CKNFAST_NO_UNWRAP=1 CKNFAST_OVERRIDE_SECURITY_ASSURANCES=import Signature Keys When KCA is installed, it generates keys on ncipher HSM. Those keys are in native format and can only be used by KCA. There is no public key associated on the HSM. We start by listing some general information about the HSM: C:\nfast\bin>enquiry Server: enquiry reply flags none enquiry reply level Six serial number B1BB-0EE mode operational version speed index 440 rec. queue level one flags Hardware HasTokens version string cam6, cam8 built on Oct :16:12 checked in dca98 Tue Sep 06 18:58: level two flags none max. write size 8192 level three flags KeyStorage level four flags OrderlyClearUnit HasRTC HasNVRAM HasNSOPermsCmd ServerHasPollCmds FastPollSlotList HasSEE HasKLF HasShareACL HasFeatureEnable Ha sfileop HasPCIPush HasKernelInterface HasLongJobs ServerHasLongJobs AESModuleKeys NTokenCmds LongJobsPreferred module type code 0 product name nfast server device name EnquirySix version 4 impath kx groups feature ctrl flags none features enabled none version serial 0 Module #1: enquiry reply flags none enquiry reply level Six serial number B1BB-0EE9-3511
5 PrimeKey Solutions AB - Migrating to EJBCA 5 mode operational version speed index 440 rec. queue level one flags Hardware HasTokens version string cam8 built on Oct :16:12 checked in f6a4d Fri Oct 13 12:28: level two flags none max. write size 8192 level three flags KeyStorage level four flags OrderlyClearUnit HasRTC HasNVRAM HasNSOPermsCmd ServerHasPollCmds FastPollSlotList HasSEE HasKLF HasShareACL HasFeatureEnable Ha sfileop HasPCIPush HasKernelInterface HasLongJobs ServerHasLongJobs AESModuleKeys NTokenCmds LongJobsPreferred module type code 7 product name nc1003p/nc3023p device name #1 PCI bus 7 slot 1 EnquirySix version 5 impath kx groups DHPrime1024 feature ctrl flags LongTerm features enabled StandardKM version serial 24 rec. LongJobs queue 18 SEE machine type PowerPCSXF C:\nfast\bin>nfkminfo.exe World generation 2 state 0x Initialised Usable Recovery!PINRecovery!ExistingClient RTC NVRAM FTO SEEDebug n_modules 1 hknso d6c fed89eba88c5082f2a1 hkm b08e66b01777fcf34dceb77c0684c8d1a071144e (type DES3) hkmwk 1d572201be533ebc89f30fdd8f3fac6ca3395bf0 hkre b0f5dbebedc703c6acd7685b261f6748bc4a9535 hkra 7368a945efc76505a19092c5115f493716de3172 hkmc 1d1e3fb769837be06e028bc038d1789ced2ac9e1 hkrtc 55f17755cae9ae49a588f deeae1f5cc hknv 82674f fbaac5a3aaa0fc08346dff34f37 hkdsee 6df83c268c25939c307f a2ac44e487ae hkfto cae32a48bd1b9e68e606ae723f8dcb93eb4ee9ab hkmnull 1d572201be533ebc89f30fdd8f3fac6ca3395bf0 ex.client none k-out-of-n 1/1 other quora m=1 r=1 nv=1 rtc=1 dsee=1 fto=1 createtime :58:41 nso timeout 10 min Module #1 generation 2 state 0x2 Usable flags 0x0!ShareTarget n_slots 2 esn B1BB-0EE hkml 5e43facc6aa d80a1954bded193b4b Module #1 Slot #0 IC 25 generation 1
6 6 PrimeKey Solutions AB - Migrating to EJBCA phystype SmartCard slotlistflags 0x2 SupportsAuthentication state 0x5 Operator flags 0x10000 Passphrase shareno 1 shares LTU(PIN) error OK Cardset name oper k-out-of-n 1/1 flags NotPersistent PINRecoveryForbidden(disabled)!RemoteEnabled timeout none card names hkltu 3126f2b3cf7d9d53e3ba278a081ef f8 gentime :00:07 Module #1 Slot #1 IC 0 generation 1 phystype SoftToken slotlistflags 0x0 state 0x2 Empty flags 0x0 shareno 0 shares error OK No Cardset No Pre-Loaded Objects One can see which keys are being used by command: C:\nfast\bin>nfkminfo -k Key list - 19 keys AppName rsa-keon-ca-65 Ident AppName rsa-keon-ca-65 Ident AppName rsa-keon-ca-65 Ident AppName rsa-keon-ca-65 Ident AppName rsa-keon-ca-65 Ident AppName rsa-keon-ca-65 Ident AppName rsa-keon-ca-65 Ident AppName rsa-keon-ca-65 Ident AppName rsa-keon-ca-65 Ident AppName rsa-keon-ca-65 Ident AppName rsa-keon-ca-65 Ident AppName rsa-keon-ca-65 Ident AppName rsa-keon-ca-65 Ident AppName rsa-keon-ca-65 Ident AppName rsa-keon-ca-65 Ident AppName rsa-keon-ca-65 Ident AppName rsa-keon-ca-65 Ident AppName rsa-keon-ca-65 Ident AppName rsa-keon-ca-65 Ident There are quite some keys, and we can t immediately say which one is the CA s signing key. This is deduced in the following way:
7 PrimeKey Solutions AB - Migrating to EJBCA 7 C:\nfast\bin>pubkey-find.exe c:\kca.pem input format cert ncore hash d0196ea2e070315e9e162c28dcdc5a524bf6380d unnamed appname rsa-keon-ca-65 ident After which we can add the corresponding public key: C:\nfast\bin>pubkey-find.exe --augment c:\kca.pem And now we move the ley as to be usable by PKCS#11: C:\nfast\bin>generatekey --retarget no-verify pkcs11 13:40:30 WARNING: nfgk_debug_output is now deprecated (see manual). from-application: Source application? (jcecsp, pkcs11, rsa-keon-ca-65) [default jcecsp] > rsa-keon-ca-65 from-ident: Source key identifier? ( , , , , , , , , , , , , , , , , , , ) [ ] > plainname: Key name? [] > ERROR: plainname: key name unspecified plainname: Key name? [] > kcasign key generation parameters: operation Operation to perform retarget application Application pkcs11 slot Slot to read cards from 0 verify Verify security of key no from-application Source application rsa-keon-ca-65 from-ident Source key identifier plainname Key name kcasign **************************************************** * WARNING: will not verify the security of the key * **************************************************** Loading `oper : Module 1: 0 cards of 1 read Module 1 slot 0: `oper #1 Module 1 slot 0:- passphrase supplied - reading card Card reading complete. Key successfully retargetted. Path to key: c:\nfast\kmdata\local\key_pkcs11_uc3126f2b3cf7d9d53e3ba278a081 ef f d430c6c0502fdb1a520fb84b9dc73c8372
8 8 PrimeKey Solutions AB - Migrating to EJBCA In order to be able to use the public key via PKCS#11, we have to associate a certificate to the key. For this, we take the actual certificate: C:\nfast\bin>ckcerttool.exe -c oper -f c:\ca\kca.pem -k uc3126f2b3cf7d9d53e3ba27 8a081ef f d430c6c0502fdb1a520fb84b9dc73c8372 -L kcasign Certificate found, processing... Please enter the passphrase for oper token (No echo set). Passphrase: Certificate successfully imported. Run cklist to view your certificate object. OK At this stage, we proceed to generate two more keys to be used by EJBCA. One of the keys will be used by EJBCA for internal encryption within EJBCA, and the other for testing of the HSM. This generation should be done as described in the EJBCA User Guide, using the regular EJBCA tools. Generate one RSA key of length 2048 bits with alias kcadefault and one RSA key of length 1024 with alias kcatest. keytool -generate -keystore NONE -storetype PKCS11-NFastJava -storepass foo123 -alias kcadefault -keyalg RSA -keysize 2048 keytool -generate -keystore NONE -storetype PKCS11-NFastJava -storepass foo123 -alias kcatest -keyalg RSA -keysize 1024 We use the EJBCA tools to get automatic association between the private key and a (dummy) certificate, so it can be used through the Java PKCS#11 provider. Importing CA After doing retarget on the keys for the Root CA and the Sub CA, we can import CA certificates into EJBCA. KCA does not use the same DN order as EJBCA does by default, so if you want issued certificate to look exactly the same you should uncheck the checkbox Use LDAP DN order in EJBCA after the installation. Install EJBCA as usual with one AdminCA, after which we can import the CAs from KCA from the help script. bin/ejbca.sh ca importca TestKCARootCA org.ejbca.core.model.ca.catoken. PKCS11CAToken foo123 rootca.properties TestKCARootCA.pem rootca.properties contains: defaultkey rootdefault certsignkey rootsign crlsignkey rootsign testkey roottest pin foo123 sharedlibrary /opt/nfast/toolkits/pkcs11/libcknfast.so We do the same for the SubCA: bin/ejbca.sh ca importca TestKCASubCA org.ejbca.core.model.ca.catoken. PKCS11CAToken foo123 subca.properties TestKCASubCA-chain.pem
9 PrimeKey Solutions AB - Migrating to EJBCA 9 subca.properties contains: defaultkey subdefault certsignkey subsign crlsignkey subsign testkey subtest pin foo123 sharedlibrary /opt/nfast/toolkits/pkcs11/libcknfast.so TestKCASubCA-chain.pem is created with: cat TestKCASubCA.pem TestKCARootCA.pem > TestKCASubCA-chain.pem After this, EJBCA has one Root CA and one Sub CA that use the same signing keys as KCA. Importing user certificates In EJBCA, there is a command to import user certificates: bin/ejbca.sh ca importcert kca1 foo123 TestKCASubCA ACTIVE user1.pem The command does not import information about revocation. Full revocation information is possible to implement in a programmatic way. You can easily write your own migration tool, speeding up the process by using the command line code as a template. It can be found in src/java/org/ejbca/ui/cli/caimportcertcommand.java. About PrimeKey Solutions AB The company s business idea is to provide solutions and services in IT-security with focus on two main areas; Public Key Infrastructure (PKI) and smart card appliances. Our vision is to provide state-of-the-art solutions that integrate with customer application environments. We help our customers to solve concrete business needs in a cost-effective way, with strong emphasis on security issues. Our goal is to maintain and improve our position as leaders in providing security solutions and services by employing the resources at our disposal combined with our unique expertise.
10 10 PrimeKey Solutions AB - Migrating to EJBCA
Entrust Authority Security Manager 8.1 SP1 Patch
 www. t ha lesesecur it y. com Thales e-security Entrust Authority Security Manager 8.1 SP1 Patch 197297 Integration Guide for RHEL 6.x Version: 1.8 Date: 06 December 2017 Copyright 2017 Thales UK Limited.
www. t ha lesesecur it y. com Thales e-security Entrust Authority Security Manager 8.1 SP1 Patch 197297 Integration Guide for RHEL 6.x Version: 1.8 Date: 06 December 2017 Copyright 2017 Thales UK Limited.
Axway API Gateway Appliance. Version 7.4.1
 I N S T A L L A T I O N A N D A D M I N I S T R A T I O N G U I D E Axway API Gateway Appliance Version 7.4.1 18 September 2017 Copyright 2017 Axway All rights reserved. This documentation describes the
I N S T A L L A T I O N A N D A D M I N I S T R A T I O N G U I D E Axway API Gateway Appliance Version 7.4.1 18 September 2017 Copyright 2017 Axway All rights reserved. This documentation describes the
API Gateway Appliance Version September Installation and Administration Guide
 API Gateway Appliance Version 7.5.2 15 September 2017 Installation and Administration Guide Copyright 2017 Axway All rights reserved. This documentation describes the following Axway software: Axway API
API Gateway Appliance Version 7.5.2 15 September 2017 Installation and Administration Guide Copyright 2017 Axway All rights reserved. This documentation describes the following Axway software: Axway API
Thales nshield Series
 RSA Secured Implementation Guide For 3rd Party PKI Applications Last Modified: November 16 th, 2011 Partner Information Product Information Partner Name Thales Web Site www.thales-esecurity.com Product
RSA Secured Implementation Guide For 3rd Party PKI Applications Last Modified: November 16 th, 2011 Partner Information Product Information Partner Name Thales Web Site www.thales-esecurity.com Product
The server performs full signature validation including path building and revocation checking, supporting both CRL and OCSP revocation checking
 Krestfield EzSign Installation and Configuration Guide version 2.1 Copyright Krestfield 2017 Introduction The Krestfield EzSign suite enables applications to quickly generate and verify digital signatures
Krestfield EzSign Installation and Configuration Guide version 2.1 Copyright Krestfield 2017 Introduction The Krestfield EzSign suite enables applications to quickly generate and verify digital signatures
EJBCA Enterprise Cloud Edition CloudHSM Integration Guide
 EJBCA Enterprise Cloud Edition CloudHSM Integration Guide PRINT DATE: 2019-03-26 Copyright 2019 PrimeKey Solutions Published by PrimeKey Solutions AB Solna Access, Sundbybergsvägen 1 SE-171 73 Solna, Sweden
EJBCA Enterprise Cloud Edition CloudHSM Integration Guide PRINT DATE: 2019-03-26 Copyright 2019 PrimeKey Solutions Published by PrimeKey Solutions AB Solna Access, Sundbybergsvägen 1 SE-171 73 Solna, Sweden
Public Key Enabling Oracle Weblogic Server
 DoD Public Key Enablement (PKE) Reference Guide Public Key Enabling Oracle Weblogic Server Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke URL: http://iase.disa.smil.mil/pki-pke Public Key Enabling
DoD Public Key Enablement (PKE) Reference Guide Public Key Enabling Oracle Weblogic Server Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke URL: http://iase.disa.smil.mil/pki-pke Public Key Enabling
Redline Networks E X Web I/O Accelerator. Supplemental Documentation Product Model: 3650-FIPS E X Version 3.1
 Redline Networks E X Web I/O Accelerator Supplemental Documentation Product Model: 3650-FIPS E X Version 3.1 Copyright 2003, 2004 Redline Networks, Inc. Redline Networks and The Redline Symbol are registered
Redline Networks E X Web I/O Accelerator Supplemental Documentation Product Model: 3650-FIPS E X Version 3.1 Copyright 2003, 2004 Redline Networks, Inc. Redline Networks and The Redline Symbol are registered
Securing U2 Soap Server
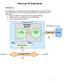 Securing U2 Soap Server Introduction To enable SSL on the Client(Consumer-to-U2SS side), we need a U2 soap server Certificate. There are three possible methods to obtain the Server Certificate: 1. Use
Securing U2 Soap Server Introduction To enable SSL on the Client(Consumer-to-U2SS side), we need a U2 soap server Certificate. There are three possible methods to obtain the Server Certificate: 1. Use
Public Key Infrastructures
 Public Key Infrastructures Chapter 6 Private Keys Cryptography and Computeralgebra Johannes Buchmann 1 How to store private keys? 2 Personal Security Environment (PSE) Private keys are stored in PSEs 3
Public Key Infrastructures Chapter 6 Private Keys Cryptography and Computeralgebra Johannes Buchmann 1 How to store private keys? 2 Personal Security Environment (PSE) Private keys are stored in PSEs 3
Public Key Infrastructures
 Public Key Infrastructures How to store private keys? Chapter 6 Private Keys Cryptography and Computeralgebra Vangelis Karatsiolis Alexander Wiesmaier 1 2 Personal Security Environment (PSE) Realisation
Public Key Infrastructures How to store private keys? Chapter 6 Private Keys Cryptography and Computeralgebra Vangelis Karatsiolis Alexander Wiesmaier 1 2 Personal Security Environment (PSE) Realisation
Personal Security Environment (PSE) Token properties. Realisation of PSEs : Tokens. How to store private keys? Chapter 6.
 Personal Security Environment (PSE) Public Key Infrastructures Chapter 6 Private Keys How to store private keys? Cryptography and Computeralgebra Prof. Dr. Johannes Buchmann Dr. Alexander Wiesmaier 2 Realisation
Personal Security Environment (PSE) Public Key Infrastructures Chapter 6 Private Keys How to store private keys? Cryptography and Computeralgebra Prof. Dr. Johannes Buchmann Dr. Alexander Wiesmaier 2 Realisation
Xceedium Xsuite. Secured by RSA Implementation Guide for 3rd Party PKI Applications. Partner Information. Last Modified: February 10 th, 2014
 Secured by RSA Implementation Guide for 3rd Party PKI Applications Last Modified: February 10 th, 2014 Partner Information Product Information Partner Name Xceedium Web Site www.xceedium.com Product Name
Secured by RSA Implementation Guide for 3rd Party PKI Applications Last Modified: February 10 th, 2014 Partner Information Product Information Partner Name Xceedium Web Site www.xceedium.com Product Name
SSL Configuration Oracle Banking Liquidity Management Release [April] [2017]
![SSL Configuration Oracle Banking Liquidity Management Release [April] [2017] SSL Configuration Oracle Banking Liquidity Management Release [April] [2017]](/thumbs/74/70574223.jpg) SSL Configuration Oracle Banking Liquidity Management Release 12.4.0.0.0 [April] [2017] Table of Contents 1. CONFIGURING SSL ON ORACLE WEBLOGIC... 1-1 1.1 INTRODUCTION... 1-1 1.2 SETTING UP SSL ON ORACLE
SSL Configuration Oracle Banking Liquidity Management Release 12.4.0.0.0 [April] [2017] Table of Contents 1. CONFIGURING SSL ON ORACLE WEBLOGIC... 1-1 1.1 INTRODUCTION... 1-1 1.2 SETTING UP SSL ON ORACLE
Public Key Infrastructures
 Public Key Infrastructures How to store private keys? Chapter 6 Private Keys Cryptography and Computeralgebra Vangelis Karatsiolis 1 2 Personal Security Environment (PSE) Realisation of PSEs : Tokens Secure
Public Key Infrastructures How to store private keys? Chapter 6 Private Keys Cryptography and Computeralgebra Vangelis Karatsiolis 1 2 Personal Security Environment (PSE) Realisation of PSEs : Tokens Secure
nshield HSM On-Premise Key Generation for Microsoft RMS
 www.thales-esecurity.com Thales e-security nshield HSM On-Premise Key Generation for Microsoft RMS Integration Guide for Windows Server 2008 R2 and 2012 Version: 1.1 Date: 14 October 2013 Copyright 2013
www.thales-esecurity.com Thales e-security nshield HSM On-Premise Key Generation for Microsoft RMS Integration Guide for Windows Server 2008 R2 and 2012 Version: 1.1 Date: 14 October 2013 Copyright 2013
Configure DNA Center Assurance for Cisco ISE Integration
 Configure DNA Center Assurance for Cisco ISE Integration If your network uses Cisco ISE for user authentication, you can configure DNA Center Assurance for Cisco ISE integration. This will allow you to
Configure DNA Center Assurance for Cisco ISE Integration If your network uses Cisco ISE for user authentication, you can configure DNA Center Assurance for Cisco ISE integration. This will allow you to
FortiNAC. Analytics SSL Certificates. Version: 5.x Date: 8/28/2018. Rev: D
 FortiNAC Analytics SSL Certificates Version: 5.x Date: 8/28/2018 Rev: D 1 FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET KNOWLEDGE BASE http://kb.fortinet.com
FortiNAC Analytics SSL Certificates Version: 5.x Date: 8/28/2018 Rev: D 1 FORTINET DOCUMENT LIBRARY http://docs.fortinet.com FORTINET VIDEO GUIDE http://video.fortinet.com FORTINET KNOWLEDGE BASE http://kb.fortinet.com
Assuming you have Icinga 2 installed properly, and the API is not enabled, the commands will guide you through the basics:
 Icinga 2 Contents This page references the GroundWork Cloud Hub and the Icinga 2 virtualization environment. 1.0 Prerequisites 1.1 Enable the API The Icinga 2 system you run needs to have the API feature
Icinga 2 Contents This page references the GroundWork Cloud Hub and the Icinga 2 virtualization environment. 1.0 Prerequisites 1.1 Enable the API The Icinga 2 system you run needs to have the API feature
SSH Communications Tectia SSH
 Secured by RSA Implementation Guide for 3rd Party PKI Applications Last Modified: December 8, 2014 Partner Information Product Information Partner Name Web Site Product Name Version & Platform Product
Secured by RSA Implementation Guide for 3rd Party PKI Applications Last Modified: December 8, 2014 Partner Information Product Information Partner Name Web Site Product Name Version & Platform Product
Application notes for supporting third-party certificate in Avaya Aura System Manager 6.3.x and 7.0.x. Issue 1.3. November 2017
 Application notes for supporting third-party certificate in Avaya Aura System Manager 6.3.x and 7.0.x Issue 1.3 November 2017 THE INFORMATION PROVIDED IN HEREIN IS PROVIDED AS IS WITHOUT ANY EXPRESS OR
Application notes for supporting third-party certificate in Avaya Aura System Manager 6.3.x and 7.0.x Issue 1.3 November 2017 THE INFORMATION PROVIDED IN HEREIN IS PROVIDED AS IS WITHOUT ANY EXPRESS OR
SSL/TLS Certificate Generation
 SSL/TLS Certificate Generation Target: Lightstreamer Server v. 7.0 or greater Last updated: 16/02/2018 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion
SSL/TLS Certificate Generation Target: Lightstreamer Server v. 7.0 or greater Last updated: 16/02/2018 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion
The Mobile Finnish Identity Certificate
 The Mobile Finnish Identity Certificate Dr.Tech. Göran Pulkkis and BSc (Eng.) Jonny Karlsson ARCADA Polytechnic Helsinki Finland PRESENTATION OUTLINE Finnish Electronic Identity (FINEID) as a Smartcard
The Mobile Finnish Identity Certificate Dr.Tech. Göran Pulkkis and BSc (Eng.) Jonny Karlsson ARCADA Polytechnic Helsinki Finland PRESENTATION OUTLINE Finnish Electronic Identity (FINEID) as a Smartcard
www. t ha les-esecur it y. com Thales e-security Integration Guide for Microsoft Windows Server 2012 and 2012 R2
 www. t ha les-esecur it y. com Thales e-security Microsoft AD CS and OCSP Integration Guide for Microsoft Windows Server 2012 and 2012 R2 Version: 1.3 Date: 09 November 2015 Copyright 2015 Thales UK Limited.
www. t ha les-esecur it y. com Thales e-security Microsoft AD CS and OCSP Integration Guide for Microsoft Windows Server 2012 and 2012 R2 Version: 1.3 Date: 09 November 2015 Copyright 2015 Thales UK Limited.
Genesys Security Deployment Guide. What You Need
 Genesys Security Deployment Guide What You Need 12/27/2017 Contents 1 What You Need 1.1 TLS Certificates 1.2 Generating Certificates using OpenSSL and Genesys Security Pack 1.3 Generating Certificates
Genesys Security Deployment Guide What You Need 12/27/2017 Contents 1 What You Need 1.1 TLS Certificates 1.2 Generating Certificates using OpenSSL and Genesys Security Pack 1.3 Generating Certificates
Symantec PKI Enterprise Gateway Deployment Guide. v8.15
 Symantec PKI Enterprise Gateway Deployment Guide v8.15 Legal Notice Copyright 2015 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo and are trademarks or registered
Symantec PKI Enterprise Gateway Deployment Guide v8.15 Legal Notice Copyright 2015 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo and are trademarks or registered
Cisco WCS Server Hardening
 APPENDIXD This appendix provides an instructional checklist for hardening a WCS server. Ideally, the goal of a hardened server is to leave it exposed on the Internet without any other form of protection.
APPENDIXD This appendix provides an instructional checklist for hardening a WCS server. Ideally, the goal of a hardened server is to leave it exposed on the Internet without any other form of protection.
SSL/TLS Certificate Generation
 SSL/TLS Certificate Generation Target: Lightstreamer Server v. 7.0 or greater Last updated: 08/03/2018 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion
SSL/TLS Certificate Generation Target: Lightstreamer Server v. 7.0 or greater Last updated: 08/03/2018 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion
www. t ha lesesecur it y. com Thales e-security Integration Guide for Microsoft Windows Server 2016
 www. t ha lesesecur it y. com Thales e-security Microsoft AD CS and OCSP Integration Guide for Microsoft Windows Server 2016 Version: 1.4.3 Date: 19 December 2017 Copyright 2017 Thales UK Limited. All
www. t ha lesesecur it y. com Thales e-security Microsoft AD CS and OCSP Integration Guide for Microsoft Windows Server 2016 Version: 1.4.3 Date: 19 December 2017 Copyright 2017 Thales UK Limited. All
Microsoft Network Device Enrollment Service
 www. t ha les-esecur it y. com Thales e-security Microsoft Network Device Enrollment Service Integration Guide Version: 1.0 Date: 12 February 2016 Copyright 2016 Thales UK Limited. All rights reserved.
www. t ha les-esecur it y. com Thales e-security Microsoft Network Device Enrollment Service Integration Guide Version: 1.0 Date: 12 February 2016 Copyright 2016 Thales UK Limited. All rights reserved.
Ultra Electronics AEP Networks Ltd Ultra Safe Keyper
 RSA Secured Implementation Guide For 3rd Party PKI Applications Last Modified: February 12 th, 2013 Partner Information Product Information Partner Name Ultra Electronics AEP Networks Ltd Web Site www.ultra-aep.com
RSA Secured Implementation Guide For 3rd Party PKI Applications Last Modified: February 12 th, 2013 Partner Information Product Information Partner Name Ultra Electronics AEP Networks Ltd Web Site www.ultra-aep.com
Generating a request for a subsequent certificate User Guide for browser Opera
 Generating a request for a subsequent certificate User Guide for browser Opera První certifikační autorita, a.s. Version 8.15 1 Contents 1. Introduction... 3 2. Software Requirements... 3 3. The process
Generating a request for a subsequent certificate User Guide for browser Opera První certifikační autorita, a.s. Version 8.15 1 Contents 1. Introduction... 3 2. Software Requirements... 3 3. The process
Thales e-security. Security Solutions. PosAm, 06th of May 2015 Robert Rüttgen
 Thales e-security Security Solutions PosAm, 06th of May 2015 Robert Rüttgen Hardware Security Modules Hardware vs. Software Key Management & Security Deployment Choices For Cryptography Software-based
Thales e-security Security Solutions PosAm, 06th of May 2015 Robert Rüttgen Hardware Security Modules Hardware vs. Software Key Management & Security Deployment Choices For Cryptography Software-based
Certificate Enrollment- and Signing Services for the Cloud. A behind-the-scenes presentation of a successful cooperation between
 Certificate Enrollment- and Signing Services for the Cloud A behind-the-scenes presentation of a successful cooperation between Introduction Based on our experience and the request from the market we would
Certificate Enrollment- and Signing Services for the Cloud A behind-the-scenes presentation of a successful cooperation between Introduction Based on our experience and the request from the market we would
Symantec Encryption Desktop
 RSA Ready Implementation Guide for RSA SecurID Last Modified: December 12, 2014 Partner Information Product Information Partner Name Web Site Product Name Version & Platform Product Description Symantec
RSA Ready Implementation Guide for RSA SecurID Last Modified: December 12, 2014 Partner Information Product Information Partner Name Web Site Product Name Version & Platform Product Description Symantec
Configure Cisco DNA Assurance
 Basic Workflow for Configuring Cisco DNA Assurance, on page 1 Assurance and Cisco ISE Integration, on page 2 Assurance Application, on page 6 Basic Workflow for Configuring Cisco DNA Assurance Before you
Basic Workflow for Configuring Cisco DNA Assurance, on page 1 Assurance and Cisco ISE Integration, on page 2 Assurance Application, on page 6 Basic Workflow for Configuring Cisco DNA Assurance Before you
Configuring the RTP Server
 Configuring the RTP Server To configure the RTP Server you can click on the little cog in the lower right hand corner of the banner area at the top of the window (If the RTP Server is running you will
Configuring the RTP Server To configure the RTP Server you can click on the little cog in the lower right hand corner of the banner area at the top of the window (If the RTP Server is running you will
Keytool and Certificate Management
 Keytool and Certificate Management A guide to utilizing keytool to assist with Certificates for emedny SOAP 2/16/2013 TABLE OF CONTENTS TABLE OF CONTENTS 1 Introduction... 3 2 Creating a Certificate Signing
Keytool and Certificate Management A guide to utilizing keytool to assist with Certificates for emedny SOAP 2/16/2013 TABLE OF CONTENTS TABLE OF CONTENTS 1 Introduction... 3 2 Creating a Certificate Signing
Using ISE 2.2 Internal Certificate Authority (CA) to Deploy Certificates to Cisco Platform Exchange Grid (pxgrid) Clients
 Using ISE 2.2 Internal Certificate Authority (CA) to Deploy Certificates to Cisco Platform Exchange Grid (pxgrid) Clients Author: John Eppich Table of Contents About this Document... 4 Using ISE 2.2 Internal
Using ISE 2.2 Internal Certificate Authority (CA) to Deploy Certificates to Cisco Platform Exchange Grid (pxgrid) Clients Author: John Eppich Table of Contents About this Document... 4 Using ISE 2.2 Internal
Security Policy. nshield F3 10+, nshield F3 500+, nshield F , nshield F for nshield Connect+,
 Security Policy nshield F3 10+, nshield F3 500+, nshield F3 6000+, nshield F3 500+ for nshield Connect+, nshield F3 1500+ for nshield Connect+, nshield F3 6000+ for nshield Connect+ in FIPS 140-2 level
Security Policy nshield F3 10+, nshield F3 500+, nshield F3 6000+, nshield F3 500+ for nshield Connect+, nshield F3 1500+ for nshield Connect+, nshield F3 6000+ for nshield Connect+ in FIPS 140-2 level
IEA 2048 Bit Key Support for CSR on IEA Configuration Example
 IEA 2048 Bit Key Support for CSR on IEA Configuration Example Document ID: 117964 Contributed by Kishore Yerramreddy, Cisco TAC Engineer. Jul 16, 2014 Contents Introduction Configure Generate a Certificate
IEA 2048 Bit Key Support for CSR on IEA Configuration Example Document ID: 117964 Contributed by Kishore Yerramreddy, Cisco TAC Engineer. Jul 16, 2014 Contents Introduction Configure Generate a Certificate
nshield/payshield Operator Guide Windows
 nshield/payshield Operator Guide Windows Version: 5.5 Date: 03 November 2005 Copyright 2005 ncipher Corporation Limited, Cambridge, United Kingdom. Neither the whole nor any part of the information contained
nshield/payshield Operator Guide Windows Version: 5.5 Date: 03 November 2005 Copyright 2005 ncipher Corporation Limited, Cambridge, United Kingdom. Neither the whole nor any part of the information contained
BIG-IP System and Thales HSM: Implementation. Version 12.1
 BIG-IP System and Thales HSM: Implementation Version 12.1 Table of Contents Table of Contents Setting Up the Thales HSM...5 Overview: Setting up the Thales HSM...5 Prerequisites for setting up Thales
BIG-IP System and Thales HSM: Implementation Version 12.1 Table of Contents Table of Contents Setting Up the Thales HSM...5 Overview: Setting up the Thales HSM...5 Prerequisites for setting up Thales
PKI Configuration Examples
 PKI Configuration Examples Keywords: PKI, CA, RA, IKE, IPsec, SSL Abstract: The Public Key Infrastructure (PKI) is a general security infrastructure for providing information security through public key
PKI Configuration Examples Keywords: PKI, CA, RA, IKE, IPsec, SSL Abstract: The Public Key Infrastructure (PKI) is a general security infrastructure for providing information security through public key
Creating an authorized SSL certificate
 Creating an authorized SSL certificate for MeetingSphere Meeting Center Server MeetingSphere Meeting Center Server requires an authorized SSL certificate by which its Meeting center is identified, and
Creating an authorized SSL certificate for MeetingSphere Meeting Center Server MeetingSphere Meeting Center Server requires an authorized SSL certificate by which its Meeting center is identified, and
ADFS Setup (SAML Authentication)
 ADFS Setup (SAML Authentication) Version 1.6 Corresponding Software Version Celonis 4.3 This document is copyright of the Celonis SE. Distribution or reproduction are only permitted by written approval
ADFS Setup (SAML Authentication) Version 1.6 Corresponding Software Version Celonis 4.3 This document is copyright of the Celonis SE. Distribution or reproduction are only permitted by written approval
McAfee Endpoint Encryption
 Secured by RSA Implementation Guide for SecurID Authenticators Last Modified: December 4, 2013 Partner Information Product Information Partner Name McAfee Web Site www.mcafee.com Product Name (EEPC) Version
Secured by RSA Implementation Guide for SecurID Authenticators Last Modified: December 4, 2013 Partner Information Product Information Partner Name McAfee Web Site www.mcafee.com Product Name (EEPC) Version
Adding value to your MS customers
 Securing Microsoft Adding value to your MS customers Authentication - Identity Protection Hardware Security Modules DataSecure - Encryption and Control Disc Encryption Offering the broadest range of authentication,
Securing Microsoft Adding value to your MS customers Authentication - Identity Protection Hardware Security Modules DataSecure - Encryption and Control Disc Encryption Offering the broadest range of authentication,
Using Certificates with HP Network Automation
 Using Certificates with HP Network Automation HP Network Automation / October 2010 This document provides an overview of how certificates are used within HP Network Automation (NA), including information
Using Certificates with HP Network Automation HP Network Automation / October 2010 This document provides an overview of how certificates are used within HP Network Automation (NA), including information
Oracle Insurance Policy Administration Configuration of SAML 1.1 Between OIPA and OIDC
 Oracle Insurance Policy Administration Configuration of SAML 1.1 Between OIPA and OIDC Version 10.1.0.0 Documentation Part Number: E55027-01 June, 2014 Copyright 2009, 2014, Oracle and/or its affiliates.
Oracle Insurance Policy Administration Configuration of SAML 1.1 Between OIPA and OIDC Version 10.1.0.0 Documentation Part Number: E55027-01 June, 2014 Copyright 2009, 2014, Oracle and/or its affiliates.
SAS Event Stream Processing 5.2: Visualizing Event Streams with Streamviewer
 SAS Event Stream Processing 5.2: Visualizing Event Streams with Streamviewer Overview Streamviewer is a graphical user interface that visualizes events streaming through event stream processing models.
SAS Event Stream Processing 5.2: Visualizing Event Streams with Streamviewer Overview Streamviewer is a graphical user interface that visualizes events streaming through event stream processing models.
www. t ha les-esecur it y. com Thales e-security Integration Guide for Microsoft Windows Server 2008 R2
 www. t ha les-esecur it y. com Thales e-security Microsoft AD CS and OCSP Integration Guide for Microsoft Windows Server 2008 R2 Version: 1.2 Date: 19 June 2014 Copyright 2014 Thales UK Limited. All rights
www. t ha les-esecur it y. com Thales e-security Microsoft AD CS and OCSP Integration Guide for Microsoft Windows Server 2008 R2 Version: 1.2 Date: 19 June 2014 Copyright 2014 Thales UK Limited. All rights
SAML with ADFS Setup Guide
 SAML with ADFS Setup Guide Version 1.0 Corresponding Software Version: 4.2 This document is copyright of the Celonis SE. Distribution or reproduction are only permitted by written approval of the Celonis
SAML with ADFS Setup Guide Version 1.0 Corresponding Software Version: 4.2 This document is copyright of the Celonis SE. Distribution or reproduction are only permitted by written approval of the Celonis
Digital signatures: How it s done in PDF
 Digital signatures: How it s done in PDF Agenda Why do we need digital signatures? Basic concepts applied to PDF Digital signatures and document workflow Long term validation Why do we need digital signatures?
Digital signatures: How it s done in PDF Agenda Why do we need digital signatures? Basic concepts applied to PDF Digital signatures and document workflow Long term validation Why do we need digital signatures?
V1.0 Nonkoliseko Ntshebe October 2015 V1.1 Nonkoliseko Ntshebe March 2018
 SAPO Trust Centre - Generating a SSL CSR for IIS with SAN V1.0 Nonkoliseko Ntshebe October 2015 V1.1 Nonkoliseko Ntshebe March 2018 1. Open Certificate MMC snap in for your computer 2. Click on Start >
SAPO Trust Centre - Generating a SSL CSR for IIS with SAN V1.0 Nonkoliseko Ntshebe October 2015 V1.1 Nonkoliseko Ntshebe March 2018 1. Open Certificate MMC snap in for your computer 2. Click on Start >
Kerberized Certificate Issuance Protocol (KX509)
 Kerberized Certificate Issuance Protocol (KX509) Jet Propulsion Laboratory Copyright 2010 California Institute of Technology. Government sponsorship acknowledged. Overview and Purpose KX509 is a wire protocol
Kerberized Certificate Issuance Protocol (KX509) Jet Propulsion Laboratory Copyright 2010 California Institute of Technology. Government sponsorship acknowledged. Overview and Purpose KX509 is a wire protocol
SSL Configuration: an example. July 2016
 SSL Configuration: an example July 2016 This document details a walkthrough example of SSL configuration in an EM managed mongodb environment. SSL certificates are used to enforce certificate based security
SSL Configuration: an example July 2016 This document details a walkthrough example of SSL configuration in an EM managed mongodb environment. SSL certificates are used to enforce certificate based security
Development Guide. BlackBerry Dynamics SDK for Windows 10
 Development Guide BlackBerry Dynamics SDK for Windows 10 Published: 2017-09-01 SWD-20171204142659563 Contents About this guide... 5 BlackBerry Dynamics background... 6 BlackBerry Dynamics API reference...6
Development Guide BlackBerry Dynamics SDK for Windows 10 Published: 2017-09-01 SWD-20171204142659563 Contents About this guide... 5 BlackBerry Dynamics background... 6 BlackBerry Dynamics API reference...6
Developers Integration Lab (DIL) Certificate Installation Instructions. Version 1.6
 Developers Integration Lab (DIL) Certificate Installation Instructions Version 1.6 May 28, 2014 REVISION HISTORY REVISION DATE DESCRIPTION 0.1 17 September 2011 First Draft Release DIL Certificate Installation
Developers Integration Lab (DIL) Certificate Installation Instructions Version 1.6 May 28, 2014 REVISION HISTORY REVISION DATE DESCRIPTION 0.1 17 September 2011 First Draft Release DIL Certificate Installation
PKI Contacts PKI for Fraunhofer Contacts
 Fraunhofer Competence Center PKI PKI Contacts PKI for Fraunhofer Contacts User manual for communication partners of the Fraunhofer-Gesellschaft Author[s]: Uwe Bendisch, Maximilian Gottwald As at: 03.02.2017
Fraunhofer Competence Center PKI PKI Contacts PKI for Fraunhofer Contacts User manual for communication partners of the Fraunhofer-Gesellschaft Author[s]: Uwe Bendisch, Maximilian Gottwald As at: 03.02.2017
AirWatch Mobile Device Management
 RSA Ready Implementation Guide for 3rd Party PKI Applications Last Modified: November 26 th, 2014 Partner Information Product Information Partner Name Web Site Product Name Version & Platform Product Description
RSA Ready Implementation Guide for 3rd Party PKI Applications Last Modified: November 26 th, 2014 Partner Information Product Information Partner Name Web Site Product Name Version & Platform Product Description
nshield Microsoft SQL Server
 www. t ha lesesecur it y. com Thales e-security nshield Microsoft SQL Server Integration Guide Version: 2.4 Date: 19 December 2017 Copyright 2017 Thales UK Limited. All rights reserved. Copyright in this
www. t ha lesesecur it y. com Thales e-security nshield Microsoft SQL Server Integration Guide Version: 2.4 Date: 19 December 2017 Copyright 2017 Thales UK Limited. All rights reserved. Copyright in this
SSL/TLS Certificate Generation
 SSL/TLS Certificate Generation Last updated: 11/01/2016 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion of an Existing Certificate Chain Available
SSL/TLS Certificate Generation Last updated: 11/01/2016 Table of contents 1 INTRODUCTION...3 2 PROCEDURES...4 2.1 Creation and Installation...4 2.2 Conversion of an Existing Certificate Chain Available
CertAgent. Certificate Authority Guide
 CertAgent Certificate Authority Guide Version 6.0.0 December 12, 2013 Information in this document is subject to change without notice and does not represent a commitment on the part of Information Security
CertAgent Certificate Authority Guide Version 6.0.0 December 12, 2013 Information in this document is subject to change without notice and does not represent a commitment on the part of Information Security
Public Key Infrastructure. What can it do for you?
 Public Key Infrastructure What can it do for you? What is PKI? Centrally-managed cryptography, for: Encryption Authentication Automatic negotiation Native support in most modern Operating Systems Allows
Public Key Infrastructure What can it do for you? What is PKI? Centrally-managed cryptography, for: Encryption Authentication Automatic negotiation Native support in most modern Operating Systems Allows
BlackVault Hardware Security Platform SECURE TRUSTED INTUITIVE. Cryptographic Appliances with Integrated Level 3+ Hardware Security Module
 BlackVault Hardware Security Platform SECURE TRUSTED INTUITIVE Cryptographic Appliances with Integrated Level 3+ Hardware Security Module The BlackVault hardware security platform keeps cryptographic material
BlackVault Hardware Security Platform SECURE TRUSTED INTUITIVE Cryptographic Appliances with Integrated Level 3+ Hardware Security Module The BlackVault hardware security platform keeps cryptographic material
Let's Encrypt - Free SSL certificates for the masses. Pete Helgren Bible Study Fellowship International San Antonio, TX
 Let's Encrypt - Free SSL certificates for the masses Pete Helgren Bible Study Fellowship International San Antonio, TX Agenda Overview of data security Encoding and Encryption SSL and TLS Certficate options
Let's Encrypt - Free SSL certificates for the masses Pete Helgren Bible Study Fellowship International San Antonio, TX Agenda Overview of data security Encoding and Encryption SSL and TLS Certficate options
How to use an EPR certificate with the MESH client
 Document filename: How to use an EPR certificate with the MESH client Directorate / Programme Operations and Assurance Services Project Spine Services/ MESH Document Reference Project Manager
Document filename: How to use an EPR certificate with the MESH client Directorate / Programme Operations and Assurance Services Project Spine Services/ MESH Document Reference Project Manager
When starting the installation PKI Install will try to find a high port available for https connection.
 created by: Rainer Bemsel Version 1.0 Dated: July/19/2003 The purpose of this TechNote is how to install & configure Net Tools PKI 1.0. There is one important change necessary that PKI will handle Certificate
created by: Rainer Bemsel Version 1.0 Dated: July/19/2003 The purpose of this TechNote is how to install & configure Net Tools PKI 1.0. There is one important change necessary that PKI will handle Certificate
Managing AON Security
 CHAPTER 4 This chapter describes AON functions relating to security, authentication, and authorization. It includes the following topics. Managing Keystores, page 4-1 Configuring Security Properties, page
CHAPTER 4 This chapter describes AON functions relating to security, authentication, and authorization. It includes the following topics. Managing Keystores, page 4-1 Configuring Security Properties, page
Enabling Smart Card Logon for Linux Using Centrify Suite
 DoD Public Key Enablement (PKE) Reference Guide Enabling Smart Card Logon for Linux Using Centrify Suite 2012.4 Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke/ URL: http://iase.disa.smil.mil/pki-pke/
DoD Public Key Enablement (PKE) Reference Guide Enabling Smart Card Logon for Linux Using Centrify Suite 2012.4 Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke/ URL: http://iase.disa.smil.mil/pki-pke/
OCSP Client Tool V2.2 User Guide
 Ascertia Limited 40 Occam Road Surrey Research Park Guildford Surrey GU2 7YG Tel: +44 1483 685500 Fax: +44 1483 573704 www.ascertia.com OCSP Client Tool V2.2 User Guide Document Version: 2.2.0.2 Document
Ascertia Limited 40 Occam Road Surrey Research Park Guildford Surrey GU2 7YG Tel: +44 1483 685500 Fax: +44 1483 573704 www.ascertia.com OCSP Client Tool V2.2 User Guide Document Version: 2.2.0.2 Document
Ciphermail HSM Configuration Guide
 CIPHERMAIL EMAIL ENCRYPTION Ciphermail HSM Configuration Guide April 12, 2017, Rev: 6852 Copyright c 2012-2017, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction 3 2 PKCS#11 Configuration 3 2.1
CIPHERMAIL EMAIL ENCRYPTION Ciphermail HSM Configuration Guide April 12, 2017, Rev: 6852 Copyright c 2012-2017, ciphermail.com. CONTENTS CONTENTS Contents 1 Introduction 3 2 PKCS#11 Configuration 3 2.1
How to Install Enterprise Certificate Authority on a Windows 2008 Server
 AD CS is the backbone of Microsoft s Public Key Infrastructure (PKI) implementation. It will allow you to issue certificates for SSL/TTL user on websites or digitally sign your email. Now let s take a
AD CS is the backbone of Microsoft s Public Key Infrastructure (PKI) implementation. It will allow you to issue certificates for SSL/TTL user on websites or digitally sign your email. Now let s take a
Install HSM Client Software on Oracle Key Vault Server (page 2) Protect the Oracle Key Vault TDE Master Key with the HSM (page 3)
 Oracle Key Vault Integration with Hardware Security Module (HSM) Release 12.2 BP 4 E75841-05 February 2017 Release 12.2 Bundle Patch 1 introduced Hardware Security Module (HSM) integration with Oracle
Oracle Key Vault Integration with Hardware Security Module (HSM) Release 12.2 BP 4 E75841-05 February 2017 Release 12.2 Bundle Patch 1 introduced Hardware Security Module (HSM) integration with Oracle
<Partner Name> <Partner Product> RSA SECURID ACCESS Implementation Guide. Cisco Adaptive Security Appliance 9.5(2)
 RSA SECURID ACCESS Implementation Guide Cisco Peter Waranowski, RSA Partner Engineering Last Modified: January 9 th, 2018 Solution Summary Cisco Adaptive Security Appliance
RSA SECURID ACCESS Implementation Guide Cisco Peter Waranowski, RSA Partner Engineering Last Modified: January 9 th, 2018 Solution Summary Cisco Adaptive Security Appliance
Provisioning Certificates
 CHAPTER 8 The Secure Socket Layer (SSL) protocol secures the network communication and allows data to be encrypted before transmission and provides security. Many application servers and web servers support
CHAPTER 8 The Secure Socket Layer (SSL) protocol secures the network communication and allows data to be encrypted before transmission and provides security. Many application servers and web servers support
Configuring SSL CHAPTER
 7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
NCP Secure Enterprise Management for Linux Release Notes
 Major Release: 4.01 r32851 Date: November 2016 Prerequisites The following x64 operating systems and databases with corresponding ODBC driver have been tested and released: Linux Distribution Database
Major Release: 4.01 r32851 Date: November 2016 Prerequisites The following x64 operating systems and databases with corresponding ODBC driver have been tested and released: Linux Distribution Database
Public Key Infrastructures Chapter 06 Private Keys
 Public Key Infrastructures Chapter 06 Private Keys Cryptography and Computer Algebra Prof. Dr. Johannes Buchmann Dr. Alexander Wiesmaier Personal security environments Store Private keys Certificates Other
Public Key Infrastructures Chapter 06 Private Keys Cryptography and Computer Algebra Prof. Dr. Johannes Buchmann Dr. Alexander Wiesmaier Personal security environments Store Private keys Certificates Other
Updated for Red Hat Certificate System 9.3
 Red Hat Certificate System 9 Release Notes Updated for Red Hat Certificate System 9.3 Last Updated: 2018-04-10 Red Hat Certificate System 9 Release Notes Updated for Red Hat Certificate System 9.3 Marc
Red Hat Certificate System 9 Release Notes Updated for Red Hat Certificate System 9.3 Last Updated: 2018-04-10 Red Hat Certificate System 9 Release Notes Updated for Red Hat Certificate System 9.3 Marc
Microsoft ADRMS Integration Guide for Windows Server 2012 Integration Guide
 www.ncipher.com Microsoft ADRMS Integration Guide for Windows Server 2012 Integration Guide Contents Chapter 1: Introduction 3 Product configuration 3 Supported ncipher nshield functionality 3 Requirements
www.ncipher.com Microsoft ADRMS Integration Guide for Windows Server 2012 Integration Guide Contents Chapter 1: Introduction 3 Product configuration 3 Supported ncipher nshield functionality 3 Requirements
Code Signing on Demand Cloud Version. InCommon c/o Internet Oakbrook Drive, Suite 300 Ann Arbor MI, 48104
 Code Signing on Demand Cloud Version InCommon c/o Internet2 1000 Oakbrook Drive, Suite 300 Ann Arbor MI, 48104 1 Introduction Code Signing on Demand (CSoD) offers customers a faster, more intuitive and
Code Signing on Demand Cloud Version InCommon c/o Internet2 1000 Oakbrook Drive, Suite 300 Ann Arbor MI, 48104 1 Introduction Code Signing on Demand (CSoD) offers customers a faster, more intuitive and
MSE System and Appliance Hardening Guidelines
 MSE System and Appliance Hardening Guidelines This appendix describes the hardening of MSE, which requires some services and processes to be exposed to function properly. This is referred to as MSE Appliance
MSE System and Appliance Hardening Guidelines This appendix describes the hardening of MSE, which requires some services and processes to be exposed to function properly. This is referred to as MSE Appliance
Mobile RA - User Guide
 DRAFT Mobile RA - User Guide Version 0.32 Mobile RA User Guide V0.32, PrimeKey Solutions AB, 2013-08-01 Page 1 of 9 Table of Contents 1 Introduction...3 2 Mobile RA System Overview...3 3 Mobile RA Operation...4
DRAFT Mobile RA - User Guide Version 0.32 Mobile RA User Guide V0.32, PrimeKey Solutions AB, 2013-08-01 Page 1 of 9 Table of Contents 1 Introduction...3 2 Mobile RA System Overview...3 3 Mobile RA Operation...4
Unified Management Portal
 Unified Management Portal Secure Sockets Layer Implementation Guide 6.0 Document Revision History Document Version Date Changes Beta 05/01/2012 Beta release. 1.0 08/01/2012 Initial release. 1.1 09/15/2012
Unified Management Portal Secure Sockets Layer Implementation Guide 6.0 Document Revision History Document Version Date Changes Beta 05/01/2012 Beta release. 1.0 08/01/2012 Initial release. 1.1 09/15/2012
BraindumpsVCE. Best vce braindumps-exam vce pdf free download
 BraindumpsVCE http://www.braindumpsvce.com Best vce braindumps-exam vce pdf free download Exam : 642-511 Title : VPN and Security Cisco Secure Virtual Private Networks (CSVPN) Vendors : Cisco Version :
BraindumpsVCE http://www.braindumpsvce.com Best vce braindumps-exam vce pdf free download Exam : 642-511 Title : VPN and Security Cisco Secure Virtual Private Networks (CSVPN) Vendors : Cisco Version :
TFS WorkstationControl White Paper
 White Paper Intelligent Public Key Credential Distribution and Workstation Access Control TFS Technology www.tfstech.com Table of Contents Overview 3 Introduction 3 Important Concepts 4 Logon Modes 4 Password
White Paper Intelligent Public Key Credential Distribution and Workstation Access Control TFS Technology www.tfstech.com Table of Contents Overview 3 Introduction 3 Important Concepts 4 Logon Modes 4 Password
Microsoft Active Directory Federation Service
 www. t ha lesesec u ri t y. c o m Thales esecurity Microsoft Active Directory Federation Service Integration Guide Version: 0.2 Date: Tuesday, September 11, 2018 Copyright 2018 Thales UK Limited. All rights
www. t ha lesesec u ri t y. c o m Thales esecurity Microsoft Active Directory Federation Service Integration Guide Version: 0.2 Date: Tuesday, September 11, 2018 Copyright 2018 Thales UK Limited. All rights
Redpaper. OpenPGP Key Exchange and Migration. Introduction. Exchanging OpenPGP certificates. Saheem Granados
 Redpaper Saheem Granados OpenPGP Key Exchange and Migration Introduction Business exchange processes must define the mechanism for establishing trust among partners. Using cryptography as the foundation
Redpaper Saheem Granados OpenPGP Key Exchange and Migration Introduction Business exchange processes must define the mechanism for establishing trust among partners. Using cryptography as the foundation
Server software page. Certificate Signing Request (CSR) Generation. Software
 Server software page Certificate Signing Request (CSR) Generation Software Apache (mod_ssl and OpenSSL)... 2 cpanel and WHM... 3 Microsoft Exchange 2007... 8 Microsoft Exchange 2010... 9 F5 BigIP... 13
Server software page Certificate Signing Request (CSR) Generation Software Apache (mod_ssl and OpenSSL)... 2 cpanel and WHM... 3 Microsoft Exchange 2007... 8 Microsoft Exchange 2010... 9 F5 BigIP... 13
Coding & Information Theory Lab.
 통합인증시스템설계및구현 연세대학교전기 전자공학과정연식, 송홍엽 Coding & Information Theory Lab. Introduction Previous Works Contents Design and Implementation of Public-Key Infrastructure Design and Implementation of Single Sign-On
통합인증시스템설계및구현 연세대학교전기 전자공학과정연식, 송홍엽 Coding & Information Theory Lab. Introduction Previous Works Contents Design and Implementation of Public-Key Infrastructure Design and Implementation of Single Sign-On
Automated Court Reporter Application. Digital Signatures
 Automated Court Reporter Application Digital Signatures Doc Version 1.5 December 1, 2010 Administrative Office of the U.S. Courts Revision History Date Version Description of Revision 2/10/2009 1.0 Initial
Automated Court Reporter Application Digital Signatures Doc Version 1.5 December 1, 2010 Administrative Office of the U.S. Courts Revision History Date Version Description of Revision 2/10/2009 1.0 Initial
Configure the Prime Infrastructure Server
 View the Prime Infrastructure Server Configuration, page 2 Available System Settings, page 2 Secure the Connectivity of the Prime Infrastructure Server, page 9 MIB to Prime Infrastructure Alert/Event Mapping,
View the Prime Infrastructure Server Configuration, page 2 Available System Settings, page 2 Secure the Connectivity of the Prime Infrastructure Server, page 9 MIB to Prime Infrastructure Alert/Event Mapping,
HP Operations Orchestration
 HP Operations Orchestration Software Version: 10.20 Windows and Linux Operating Systems Hardening Guide Document Release Date: November 2014 Software Release Date: November 2014 Legal Notices Warranty
HP Operations Orchestration Software Version: 10.20 Windows and Linux Operating Systems Hardening Guide Document Release Date: November 2014 Software Release Date: November 2014 Legal Notices Warranty
Managing Administrative Security
 5 CHAPTER 5 Managing Administrative Security This chapter describes how to manage administrative security by using the secure administration feature. This chapter assumes that you are familiar with security
5 CHAPTER 5 Managing Administrative Security This chapter describes how to manage administrative security by using the secure administration feature. This chapter assumes that you are familiar with security
Configuring SSL. SSL Overview CHAPTER
 7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
Integration Guide. SafeNet Authentication Client. Using SAC CBA for VMware Horizon 6 Client
 SafeNet Authentication Client Integration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information Document
SafeNet Authentication Client Integration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information Document
Workspace ONE UEM Integration with RSA PKI. VMware Workspace ONE UEM 1810
 Workspace ONE UEM Integration with RSA PKI VMware Workspace ONE UEM 1810 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
Workspace ONE UEM Integration with RSA PKI VMware Workspace ONE UEM 1810 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
Configure the Prime Infrastructure Server
 View the Prime Infrastructure Server Configuration, on page 1 Available System Settings, on page 2 Secure the Connectivity of the Prime Infrastructure Server, on page 7 MIB to Prime Infrastructure Alert/Event
View the Prime Infrastructure Server Configuration, on page 1 Available System Settings, on page 2 Secure the Connectivity of the Prime Infrastructure Server, on page 7 MIB to Prime Infrastructure Alert/Event
