PROXY WORLD WRAPPED WORLD. link V V V. link FSV FSV DFSV. link. V: Vector FSV: FSVector DFS: DFSVector
|
|
|
- Russell Smith
- 5 years ago
- Views:
Transcription
1 Engineering Java Proxy Objects using Reection Karen Renaud & Huw Evans University of Glasgow Abstract Java programmers need to be able to locally specialise the run-time behaviour of externally developed code in order to increase software reuse. The various approaches to code specialisation are discussed. We then introduce a mechanism of using proxies to eect the required specialisation. Many issues which arise as a result of the use of proxies, such as the \self problem" and encapsulation problems, are discussed, and the resulting design and architecture are described in detail. 1 Introduction Java software developers need to be able to specialise the run-time behaviour of externally developed code to meet local needs. The original developer cannot identify every possible use of their software and so the local Java developer should be able to specialise its use as part of the run-time conguration of their system. When a program is run, we would like to be able to augment its behaviour to include the execution of code we dene locally. Giving ourselves control in this way allows us to add arbitrary behaviour to the program, to support system instrumentation, for example. However, in order for the program to retain the correct semantics, it must be able to access and execute all the code that was originally written. In addition, as the class is the fundamental building block of a Java program, we would like to be able to change program behaviour on a class by class basis. This will give the programmer the most exibility. Such run-time specialisation can be acheived in the Java 2 platform [8] in a number of ways: by changing the Java source code; by post-processing the Java bytecode; by providing a custom classloader; and by providing proxy objects. Changing the Java source code is only an option when the source code is available and as this is not likely to be the case when code has been obtained from another organisation is not a general solution. For this reason other researchers have investigated tools and techniques that allow Java bytecode to be changed without needing access to the source code. These tools can be divided into two categories, those that just support generic bytecode rewriting [3, 1] and those that rewrite bytecode for a particular situations, such as to provide a meta-object protocol [10] or to be able to dynamically adapt code at run-time [5]. The bytecode-rewriting tools in the rst category are very useful as they allow programmers to change a class denition to meet a local need. For example, the bytecode of a class can be changed to ensure it is compatible with the Java Object-Serialization mechanism so that instances of the modied class can be passed across a network or written to disk. However, bytecode rewriting has a number of disadvantages. Firstly, the changes to be made to the bytecode of a class must be recorded somewhere so that they can be reapplied whenever a new version of the class is compiled. In addition, systems that require bytecode to be rewritten, such as ObjectStore's PSE Pro [2], may burden the programmer with managing two sets of classes. For example, one class (A) may depend on another class that has to be post-processed (class B). Class B should therefore be compiled rst and post-processed before class A is compiled. Tracking these kinds of relationships for signicant bodies of code is a non-trivial problem. Thirdly, bytecode rewriting by-passes the Java compiler which enforces the Java language semantics. This allows a programmer to get access to all the elds of an object, even if some were marked as private in the source code. Meta-object protocols [6] are a powerful programming paradigm for associating new behaviour with a program. This is expressed by separating the object-level from the meta-level in an object-oriented programming language. The object-level implements the semantics of the application, whereas the meta-level deals with the language-based semantics of implementing that application. For example, for a word processing application, a class at the object-level might be Paragraph that handles the manipulation of paragraphs of text. At the meta-level, a programmer can dene a binding between the object-level class (Paragraph) and a meta-level class, e.g., MetaParagraph. The supporting language then delegates to the meta-level any operations that are performed over the Paragraph class. This includes operations such as method dispatch, eld 1
2 access and object creation. When a method is executed on a Paragraph object, the MetaParagraph object is checked with rst to see how this method should be handled. The meta-level can arrange for another method on a dierent object to be called instead, thus aecting the behaviour of the program at run-time. The authors of [10] have dened a meta-object protocol for Java that requires bytecodes to be rewritten and so it is subject to the problems identied above. Their system rewrites bytecode at run-time and so it imposes a run-time overhead on the program. This could be optimized to perform the post-processing once, before the program is run, however, all the classes that the program could possibly use would have to be identied. It is also not clear if the meta-object protocol only allows the addition of new behaviour to a class or if a class may be completely substituted with another one. The system described by Keller and Holzle in [5] is targetted at integrating Java classes with other, noncompatible classes. The classes are made compatible by the programmer identifying which class should have its bytecode modied at run-time to ensure the classes can inter-operate. This system also relies on bytecode rewriting and its focus is dierent to what is described. Their system ensures incompatible classes can be used together by adding, renaming or removing methods, or by changing the class hierarchy. We want to change the behaviour of an object at run-time by providing the system with access to alternative code. but we do not want to change the existing denition of that class. The Java 2 platform allows the programmer to dene custom classloaders so that a program can manage how and from where classes are loaded. However, certain restrictions are placed on the programmer. Firstly, Java's class equivalance is based on the name of the class and the identity of the classloader that loaded the class. Given this denition, two classes with the same name (but possibly dierent semantics) can be loaded by two dierent classloaders in the same virtual machine. However, if the program uses one class definition in a context where the other class denition is expected, a java.lang.classcastexception will be raised. Our solution adopts this approach, however, extreme care has to be taken to ensure the two sets of classes are kept apart (see section 3.1). Given the restrictions imposed by the above approaches, we have adopted a solution that exploits proxy objects [4]. A proxy object provides a surrogate object which controls access to the wrapped object by forcing all interaction with the wrapped object via the proxy. The rest of the paper is organised as follows. Section 2 gives an overview of our approach. Section 3 describes how the proxy classes are generated and Section 4 discusses how the proxy classes and the wrapped classes interact. Section 5 shows how a custom classloader was provided to support this system and section 6 describes some pitfalls with the approach. Section 8 summaries the paper. 2 System Overview In this system we would like to be able to execute the code given in the Run class (below), which makes use of the class FString, a new implementation of a string class. Both these classes have been written externally and we would like to be able to alter the behaviour of the program at run-time by providing an alternative implementation of the class FString. In our approach we do not assume the presence of the source code and we do not rewrite any bytecode. package application; public class Run { public static void main(string[] argv) { FString str = new FString(); char[] c = null; c = str.update( new char[] { '4', '3', '2', '1' ); System.out.println(c); package wrapped; public class FString { /* Original Version */ char[] data; public FString() { /* Initialise the data to some known value for this example. */ data = new char[] { '1', '2', '3', '4' ; public char[] update(char[] c) { char[] result = data; data = c; return result; If we execute Run outside the environment, str is created and the character array '1', '2', '3', '4' is initialised. The update() method is then called, initialising data with a new array of characters characters ('4', '3', '2', '1') but returning the old array. Therefore, when Run is executed, 1234 is printed on standard output. When executed inside the environment, the simplied version of the FString proxy below is substituted. In section 4, the proxy code will be explained in more detail 2
3 package wrapped; public class FString { /* Proxy for FString */ Object wrappedobject; static Class FStringClass = WrappingClassLoader.wcl.loadClass( "wrapped.fstring"); public FString() { wrappedobject = FStringClass.newInstance(); public char[] update(char[] c) { char[] r = null; System.out.println("update() called"); Method m = null; m = FStringClass.getMethod("update", new Class[] { char[].class ); r = (char[]) m.invoke(wrappedobject, new Object[] { c ); System.out.println("update() exiting"); return r; Note that name of the proxy class and its package is exactly the same as the original. This is crucial to having this system work. If either of these is dierent, the externally developed code would not work in the environment. The code in Run, expects the class wrapped.fstring to exist and so the fully-qualied package and class name must be used. The above proxy must provide a public method with exactly the same signature (number and type of parameters, result type and number and type of exceptions) as that provided by the original class. However, internally it can dene other protected and private methods and other elds. The proxy must provide all the methods that the original FString denes, this includes all the public methods of the superclasses it inherits from. It is possible for the original denition of FString to contain non-static elds that are public. Code will rely on these public elds being present in the proxy. However, the wrapped code may make use of the public elds within its methods and so it is not feasible to have copies of the elds in the proxy. In this approach we therefore assume a clean object model where there are no public non-static elds dened on any class that is being wrapped. Some Java programs rely heavily on dening public static elds in classes to provide global access to object state, for example, System.out. This is a similar problem to that described above. It is not possible 1 to hold a copy of the static eld in the proxy as the wrapped class may need access to it. As Java does not model eld access as method invocation, there is no opportunity in this approach to redirect the access to the static eld via the proxy. Therefore, we assume that static elds are always accessed via a static method dened on the wrapped class. This then provides the necessary support to call the method on the proxy. Dealing with public elds is an area for future work (section 7). Once the proxy has been compiled, it must be installed in the environment and the CLASSPATH changed to load the proxy class when the FString class is found for the rst time. The proxy FString will be loaded by the default classloader. The code inside the proxy then explicitly loads the wrapped FString using the WrappingClassLoader class. The call to the loadclass method dened on WrappingClassLoader.wcl method takes the string wrapped.fstring as an argument. This classloader loads the original denition of FString from a location that was supplied to the classloader when the environment was run. This is passed via a run-time variable -Dwrappedpath which is a list of directories for the classloader to search to load the wrapped classes. When an FString object is created, the above constructor is called which initialises wrappedobject. As wrappedobject is of type java.lang.object it is possible to create an instance of the original FString object inside the FString proxy class. A call to the update method dened on the proxy uses the java. lang.reflect.method object to retrieve the update method on the original class. This method object is then used to call the update method on the original class, passing the parameter c and returning the resulting character array, r. 3 Generating the Proxy Classes The rst step in providing this tool is to generate the Java source code for the proxy classes. In order to make this scheme at all viable, class les must be generated automatically using the java.lang.reflect package. These classes must be type compatible with the original classes (that is they must have the same fullyqualied class name), and present the same interface to the application as the wrapped classes. This means that they must provide the same constructors, meth- 1 In the case where the static eld is dened as final, a copy can be made as the eld cannot be updated. This assumes it is possible to initialise the eld in the same way as the original. 3
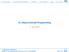
4 ods, and public elds. Using the Java introspection mechanism, a full description of the class can be derived, enough to generate a complete \look-alike" proxy class. A generator will produce the proxy classes in four separate stages: the skeleton, the public elds, the constructors, and the public methods. The generation of the skeleton and elds is straightforward, but the generation of constructors and methods merits some discussion which will be done in the following sections. PROXY WORLD V FSV link link WRAPPED WORLD V V V FSV FSV 3.1 Constructors DFSV link DFSV A proxy constructor is generated for each constructor in the wrapped class. The constructor establishes a link to an instance of the wrapped class, and maintains a reference to this object to be used in subsequent method invocations, as shown for class FString below. This seems straightforward, but there is a complication. The problem is that Java does not allow two different classes with the same name to be used within the same context, and that is precisely what this scheme proposes to do. To circumvent this, a specially written classloader, WrappingClassLoader (see Section 5), is used. The constructor calls the loadclass method in the WrappingClassLoader to load the wrapped class object (FStringClass below). The constructor then creates an instance of that class using the newinstance method 2 on the class object to initialise wrappedobject. Object wrappedobject; static Class FStringClass = WrappingClassLoader.wcl.loadClass( "utils.fstring") public FString() { FStringClass = CL.loadClass("utils.FString"); wrappedobject = FStringClass.newInstance(); It is important to note that wrappedobject is referred to as type Object, and not as type FString. If FString was used here it would refer to the proxy as this has been loaded via the default classloader. It is the wrapper that then explicitly loads the wrapped class. The design of the proxy has been done to ensure that the two worlds, the wrapped classes and the proxy classes, are kept apart. Within the proxy world, shown in the previous code segment, the notion of FString is the proxy class FString. Thus, wrappedobject is just an object, a reference into the separate world of the wrapped FString which happens to have the same fully-qualied class 2 This only works for constructors with a null parameter. The reection package is used to handle any parameters passed to a constructor. V: Vector FSV: FSVector DFS: DFSVector Figure 1: Erroneous Linking name as the proxy FString. You will also note that the FStringClass variable is declared as static. This variable describes the class of the wrapped object. This is currently used when invoking methods on the wrapped object and is an area for future work (section 7). Only one instance of this variable is needed for all proxy objects of a specic class, since the wrapped object class is the same for all objects of a specic proxy class. Another important detail that must be addressed is caused by the inheritance model of Java. This model ensures that, in our example utils package, DFSVector is also an FSVector which, in turn, is a Vector. Note from the structure of the Java inheritance mechanism that when an instance of DFSVector is created, all its superclass constructors will be automatically invoked. However, in the proxy class constructors shown above, each constructor will create a link to an equivalent object in the wrapped world. Since no-argument superclass constructors are automatically invoked when an instance of a subclass is instantiated, this leads to a situation as shown in Figure 1. How is this prevented? A proxy superclass constructor must be explicitly invoked, and this \special" constructor should not create a link to the wrapped object. The link should only exist in the object actually being instantiated, not in the superclasses. There is a diculty in creating such a constructor which will work for all objects. A \proxy" constructor must be created which does not duplicate any possible constructor which already exists for the class. This means it must behave as a sort of dummy constructor. In providing such a constructor it is essential that the existing constructors of the class should not be duplicated. Since the proxy generation is an automated process, it is dicult to determine the nature of the existing 4
5 PROXY WORLD V WRAPPED WORLD V public void displaystring() { Method m = FStringClass.getMethod( "displaystring", new Class[] { ); m.invoke(wrappedobject, new Object[] { ); FSV DFSV link V: Vector FSV: FSVector DFSV: DFSVector FSV DFSV Figure 2: Linking the two worlds constructors. In creating such a proxy constructor, we have to create a constructor which receives a parameter which could not possibly be used by any constructor in the class. To achieve this, the proxy constructor will take a Class object as a parameter. This constructor does not create a link to a wrappedobject, and is explicitly invoked when an instance of a subclass is created, preventing implicit invocation of the null parameter constructor. This prevents the automatic invocation of one of the other constructors, which would create a new wrapped object. The correct structure is shown in Figure 2. For example: Class FSVectorClass = WrappingClassLoader.wcl.loadClass( "utils.fsvector"); public FSVector (Class cls) { // Do not create a link here public FSVector() { super(fsvector.class); wrappedobject = FSVectorClass.newInstance(); 3.2 Methods A method is generated for each public method in the wrapped class. This method invokes the same method on the wrapped object using invoke on FStringClass. For example: Firstly, a reference to a method object (m) is obtained that reects over the method displaystring(). The method is then invoked on the wrapped object using the object m by calling its invoke() method, passing the wrappedobject reference and an empty list of method parameters. Since this method receives no parameters, the formal parameters for the method lookup and the array for passing method invocation parameters is empty. A more complicated example will be given further on. The mechanism described above works for the simplest interaction, when parameters are neither sent nor return values received. It can now be tested for methods which receive parameters, which in turn have to be relayed to the wrapped object. The implementation of the setname method in the proxy is as follows: public void setname(string name) { Method m = FStringClass.getMethod( "setname", new Class[] { String.class ); m.invoke(wrappedobject, new Object[] { name ); The setname method on the wrapper receives the String name as a parameter. The reected setname method on the wrapped class is retrieved by calling getmethod() on FStringClass. The setname() method is called on the wrapped class by calling the invoke() method on the reected method m. The wrappedobject and the name references are passed as parameters to the call to invoke(). As the class String has the same meaning for both the proxy and the wrapped class, this works well. However, the situation where an instance of one of the wrapped classes has to be passed as a parameter needs to be handled correctly. 3.3 Passing an Instance of a Wrapped Class In our approach the proxy class and the wrapped class are implemented separately. This leads to two problems, the \self problem" [7] and the encapsulation problem. The self problem arises because the meaning of self (or this in Java programs) is dierent in the proxy 5
6 and the wrapped class. If all references to this in the wrapped object are considered to really be references to the proxy, then this is a delegation model, where all eld and method accesses within the wrapped class are delegated to the proxy which delivers them to the wrapped instance. If all references to this in the wrapped instance are not considered to be references to the proxy but to the wrapped object, this is a forwarding model as only the initial method invocation on the proxy has been forwarded to the wrapped object. In [10] the authors present two forms of the encapsulation problem. When implementing the proxy and the wrapped class separately the wrapping is only logical, in the sense that, if the wrapped class can be referenced independently of its proxy, an instance of the wrapped class can be created without creating a wrapping proxy. In our solution, the proxy class and the wrapped class have the same name; no renaming is required as in [10]. In our approach the only dierence between the proxy class and the wrapped class is that the proxy class has been loaded by WrappingClassLoader. The only way for a programmer to get a direct reference to the wrapped class would be to write their own classloader that explicitly loaded it. In order to do this, they would have to discover the location of the wrapped classes. As this information is not exposed by our system, they could not discover this information by writing a Java program. The second encapsulation problem occurs if the wrapped instance returns a reference to itself (via this) or another wrapped instance and not a reference to the proxy for that instance. A programmer could then directly manipulate the wrapped object, bypassing its proxy Passing References to a Wrapped Instance The encapsulation problems are discussed with reference to the following addelement method on the FSVector proxy, as follows: public Object wrappedobject; static Class FSVectorClass; public void addelement(fstring name) { Method m = FSVectorClass.getMethod("addElement", new Class[] { FString.class ); m.invoke(wrappedobject,new Object[] {name); The application might do the following: an instance of the FString proxy class is passed as a parameter. This object is not understood by the wrapped class. Indeed, if it is sent, the wrapped class and the proxy class will cause a java.lang.class CastException to be thrown as the two dierent classes are being used in the same context. The proxy object should not be sent, since the wrapped objects only understand other wrapped objects. A solution is to pass through the wrappedobject reference to a method that expects a wrapped instance and not its proxy. For example, the preceding implementation of addelement would be changed to: public void addelement(fstring name) { Method m = FSVectorClass.getMethod("addElement", new Class[] { name.fstringclass ); m.invoke(wrappedobject, new Object[] { name.wrappedobject ); In our approach, the proxy is removed when calling forward to a method that expects an instance of a wrapped class. This is required because of the Java type system. Therefore, we cannot support a delegation model as described above and are forced to adopt a model based on forwarding. This means that any use of this inside the wrapped class will be a direct reference to the wrapeed instance and not to its proxy. Therefore, we have lost the ability to associate the proxy with that object while the call is in this object. However, we can reassociate the reference with a proxy assuming this unwrapped reference is passed back to the application via one of our proxies Passing References from a Wrapped Instance We also need to deal with passing results back that refer to a wrapped object and not its proxy. Consider this implementation of the getfirst method dened on the proxy version of FSVector. public FString getfirst() { Method m = FSVectorClass.getMethod("getFirst", new Class[] { ); Object r = m.invoke(wrappedobject, new Object[] { ); return (FString) r; FString mystring = new FString(); FSVector SV = new FSVector(); SV.addElement(myString); The references mystring and SV refer to instances of the proxy classes. When the application calls addelement, The reference r in the proxy version of the getfirst method is a reference to the rst wrapped object contained in the FSVector. If r is passed out from the proxy, we have broken the encapsulation provided by the proxy. The type of r is the wrapped form of FString. When this value is passed back, a cast will 6
7 Application Proxy Classes Translator Wrapped Classes Figure 3: Integrating the two Sets of Classes be attempted on r to the proxy FString class. These wrapper class and the proxy classe are incompatible as they were loaded by dierent classloaders and a java.lang.class CastException will be raised. It is clear that an intermediate object is required which will act as a buer between the wrapped and proxy classes, providing a way to translate from wrapped to proxy and visa versa. This translator will need to recognise a proxy object which is passed as a parameter, and substitute and pass the corresponding wrapped object as a parameter. If a wrapped object is returned by a method, the translator will return the corresponding proxy object to the caller. The next section outlines the design of this translator, which provides a \bridge" between these two separate type spaces. 4 Integrating the Two Type Spaces The previous discussion has concluded that some sort of translator is needed which will act as a bridge between the wrapped world and the proxy world. The architecture which incorporates the translator is illustrated in Figure 3. The Translator object ensures that the two worlds are kept apart. By using a translator object, the complexity can be removed from each individual proxy instance and contained within one translator for each class in the wrapped package. It maintains two tables, one to match the corresponding objects in the dierent worlds. The other static table, shared by all instances of the Translator class, keeps track of other translators. The table structure is shown in Figure 4. There will be one translator for each class that is being wrapped, and the translator object needs to know about other translators so as to enable wrapping and unwrapping of parameters and return values. In order to standardise the way objects communicate to and from the Translator, some help classes are de- ned.details of these classes are given in Identity: This object will serve as an object identier by which the translator will recognise the proxy object. All method invocations must be accompanied by this object, so that the translator can substitute the wrapped object for any parameters in method calls. Translator Lookup Table FSVector.class FString.class Translator Instances Proxy FSVector Proxy FSVector Proxy FString Proxy FString Figure 4: The Translator Tables Wrapped FSVector Wrapped FSVector Wrapped FString Wrapped FString Descriptor: This object describes the information which is passed between the proxy and wrapped classes. The Descriptor has two constructors. One is used for a Descriptor which describes constructor parameters, and another describes method parameters. Returner: This object will hold the return value for the method invocation. The Translator has three methods, which are invoked from the proxy instances: 1. public Identity createnew(descriptor): All wrapped objects are created by calling this method within the constructor of the proxy class. When the Translator has created an instance of the wrapped object, it will return a special Identity object to the proxy object. The proxy object will use that Identity object to identify itself in all future method invocations. 2. public Returner invokemethod(descriptor): All methods are invoked by calling this method. The parameters used by the method are described by means of a Descriptor object. All method invocations return a Returner object, which will simply hold no information if the method returns a void. If a value is returned, the proxy object can get it by calling getreturn() on the Returner object and return the value to the application program. 3. public void remove(identity): This facilitates the removal of the proxy and wrapped objects from the class instance table. It is called by the proxy object when the finalize method is invoked. The operation of the Translator has three possible stages: 7
8 1. Instantiation When a proxy is instantiated, it will check whether a Translator already exists for the class. If not, the Translator will be instantiated, and a reference stored for future use by all instances of that class. The Translator will then be called to create an instance of the wrapped class. The proxy will be given a unique identity which it will then use to identify its own identity to the Translator when instructing it to invoke methods on the wrapped object. 2. Method Invocation When a method is invoked on the proxy, for example the addelement method of FSVector, an FString is passed in as parameter. The proxy will send the parameter, within the Descriptor object, to the Translator. The Translator will: (a) detect that the parameter being passed is a member of the package being wrapped. (b) get a reference to the FString Translator instance from the static translator instances table. (c) get a reference to the wrapped object for the proxy FString. (d) pass this wrapped object to the wrapped FSVector object. If an FString return value is returned by the method, the Translator does the following: (a) detect that the return value is a member of the package being wrapped. (b) get a reference to the FString Translator instance from the translator instances table. (c) get a reference to the proxy object for the wrapped FString. If it doesn't exist, instruct the FString Translator to create a proxy for the object, and get an Identity object to reference the object. (d) return this proxy object to the proxy FSVector. To summarise, when the proxy passes an instance of a proxy class as a parameter, the translator substitutes the wrapped object. When the wrapped object returns a wrapped object as a return value, the translator substitutes the related proxy object and returns that to the proxy. 3. Removal When the application no longer has a reference to a particular proxy object, the JVM will automatically call the finalize method on the object. All proxy objects will override this method. When the proxy finalize method is invoked, the proxy will invoke the remove method on the Translator object so that the applicable entry can be removed from the instance table. This is to facilitate correct garbage collection, and prevent memory leaks. The proxy FString is now implemented as follows: public class FString { public Identity ID ; // my identity static Translator transfstring; static boolean transcreated=false; public static void settranslator() { if(!transcreated) { transfstring= new Translator("utils.FString"); transcreated=true; public FString() { settranslator(); Descriptor desc = new Descriptor( new Class[] {, new Object[] {, this); ID = transfstring.createnew(desc); public String setname(java.lang.string a) { Descriptor d = new Descriptor( new Object[] { a, "public void utils.setname()", ID); Returner r = transfstring.invokemethod(d); return (java.lang.string) r.getreturn(); protected void finalize() throws Throwable() { transfstring.remove(id); //... 5 The Class Loader The JVM internal class loader loads each class once, when it is encountered for the rst time. To make the system work, a second load of a class with the same name must be performed from within the Translator. This is done by using a separate class loader to maintain a separate namespace. The new class loader must only load those classes within the wrapped package. Using a separate class loader enables us to have two classes co-existing in the system with the same name, as long as they are loaded by dierent class loaders. The WrappingClassLoader is initialised and given the path where the wrapped classes are to be found. When the loadclass() method is invoked by the Translator to load a required class, the Wrapping 8
9 ClassLoader does the following to enforce the required separation: If the required class belongs to the wrapped package, the WrappingClassLoader loads the class explicitly from the wrappedpath location. If not, WrappingClassLoader invokes the JVM classloader to load the class from the CLASSPATH. Java's type system compares two classes for equality based on two things: the class name, and the class loader. By making use of a dierent class loader for a class of the same name, one can have two classes with the same name co-existing within the JVM. Thus the two identically named classes will only co-exist in harmony in the JVM as long as there is no named reference between them. 6 Pitfalls This mechanism does not work for packages which use platform-dependent native classes. Remember that this scheme only works if the two worlds, the wrapped and the proxies are kept strictly apart. The way a Java class usually makes use of system-dependent classes is to make use of an abstract class. This class, when loaded, triggers the loading of the system-dependent classes from the operating system-dependent libraries. If a wrapped class happens to need native classes, which have to be loaded from operating system libraries, the JVM Class Loader must be used to load these classes. What this means is that there is a link from the wrapped world into the proxy world, and the system fails. This can sometimes be overcome if the package has some sort of mechanism which allows the use of a proxy class. An example of this which applies to the java.awt package is discussed in [9]. If the package has interfaces in it, something special must be done. A proxy cannot be created for an interface. The application may have implemented an interface, and need to pass itself, as an instance of that interface, to one of the wrapped classes. This happens in addactionlistener in the java.awt package, where an application implements the ActionListener interface, and registers an interest in events by adding itself as a listener to a specic screen interface. This is going to cause problems because passing an instance of the application to a wrapped class is not going to work. The wrapped class loader diers from the class loader used to load the application in the rst place and you will get a ClassCast Exception. The way to overcome this diculty is to generate a special class, say ActionListenerImpl, which implements the interface, and which will operate in the wrapped world. When the application registers an interest in some event by means of a call to addactionlistener, the Translator will instantiate ActionListenerImpl, and when this object receives event notications, the Translator will relay the event notication to the application. Finally, the technique described in this paper makes use of manipulation of the CLASSPATH proxy-insertion technique. The CLASSPATH mechanism is used rather dierently in JDK 1.2, which expects to nd any class with a name starting with java, in a special place i.e. within the rt.jar le provided by Sun. It would be preferable to use the class loader mechanism of proxy insertion for Java core classes. 7 Future Work We are currently investigating the release of this system as a tool for Java programmers. This will be done after considering the issue of public elds in more depth. As currently dened, a proxy class denes a static Class reference which represents the wrapped class at run-time. When a proxy method is invoked, this class is used to retrieve a reective Method object which is used to call the wrapped method. Everytime the getmethod call is made on the Class object, a new instance of the method object is returned, when in fact, only one method object per method is required. This can be achieved by storing a static array of Method objects per proxy and retrieving the relevant object by indexing into the array from the proxy method. This removes the need for the static Class reference representing the wrapped class. Java programmers like to use public references for static and non-static elds in their classes. In the case of non-static elds, it can be argued that this is bad object-oriented programming as encapsulation is broken. A pair of get() and set() methods are likely to be inlined by the Java compiler or a JIT compiler, therefore removing the run-time overhead of using the method. Controlling access to static references via a static method is also better object-oriented programming. However, we need to be able to deal with the case when direct access is made and this is an area for future work. Keeping the state of the proxy synchronized with the state in the wrapped object is a challenge and Java may not provide enough support for this at the language level. 9
10 8 Summary We have outlined a mechanism for seamlessly determining usage patterns for classes in a Java package. This mechanism eliminates the need for making changes to the application source code, or to the package source code, to get these statistics. The application remains unchanged and there is no chance of spending hours debugging after having made a mistake in removing this type of code once the measurement has been made. It is as simple as generating a set of proxies for the package, changing the CLASSPATH to point to the proxy package, and starting the application with a special environment variable in the command line. To stop using the proxies, all that is needed is to simply change the CLASSPATH to what it used to be. This is a very useful tool to have, and is widely applicable in the world of constantly changing software. [8] S. Microsystems. Java 2 platform, standard edition. January Web Document. [9] K. V. Renaud. Tracking activity at the user interface in a Java application. Technical Report TR , Department of Computing Science, University of Glasgow, 17 Lilybank Gardens, Glasgow, G12 8RZ, April [10] I. Welch and R. Stroud. From Dalang to Kava the evolution of a reective Java extension. Lecture Notes in Computer Science, 1616:2{21, Acknowledgements Karen Renaud is supported by a scholarship from the Association of Commonwealth Universities and this work is also funded in part by a grant from the Foundation for Research and Development in South Africa, and the University of South Africa. References [1] G. A. Cohen, J. S. Chase, and D. L. Kaminsky. Automatic program transformation with JOIE. In Proceedings of the USENIX 1998 Annual Technical Conference, pages 167{178, Berkeley, USA, June 15{ USENIX Association. [2] E. Corporation. Objectstore enterprise edition homepage. May Web Document. [3] M. Dahm. Byte code engineering. In Proceedings of JIT'99., Duesseldorf, Germany, [4] E. Gamma, R. Helm, R. Johnson, and J. Vlissides. Design Patterns: Elements of Reusable Object-Oriented Software. Addison-Wesley, Reading, MA, [5] R. Keller and U. Holzle. Binary component adaptation. In E. Jul, editor, ECOOP '98 Object-Oriented Programming, volume 1445 of Lecture Notes in Computer Science, pages 307{329. Springer, [6] G. Kiczales, J. des Rivieres, and D. G. Bobrow. The Art of the Meta-Object Protocol. MIT Press, Cambridge (MA), USA, [7] H. Lieberman. Using prototypical objects to implement shared behavior in object-oriented systems. In N. Meyrowitz, editor, OOPSLA'86 Conference Proceedings: Object-Oriented Programming: Systems, Languages, and Applications, pages 214{223. ACM SIGPLAN, ACM Press,
Shigeru Chiba Michiaki Tatsubori. University of Tsukuba. The Java language already has the ability for reection [2, 4]. java.lang.
![Shigeru Chiba Michiaki Tatsubori. University of Tsukuba. The Java language already has the ability for reection [2, 4]. java.lang. Shigeru Chiba Michiaki Tatsubori. University of Tsukuba. The Java language already has the ability for reection [2, 4]. java.lang.](/thumbs/72/66404186.jpg) A Yet Another java.lang.class Shigeru Chiba Michiaki Tatsubori Institute of Information Science and Electronics University of Tsukuba 1-1-1 Tennodai, Tsukuba, Ibaraki 305-8573, Japan. Phone: +81-298-53-5349
A Yet Another java.lang.class Shigeru Chiba Michiaki Tatsubori Institute of Information Science and Electronics University of Tsukuba 1-1-1 Tennodai, Tsukuba, Ibaraki 305-8573, Japan. Phone: +81-298-53-5349
1 Shyam sir JAVA Notes
 1 Shyam sir JAVA Notes 1. What is the most important feature of Java? Java is a platform independent language. 2. What do you mean by platform independence? Platform independence means that we can write
1 Shyam sir JAVA Notes 1. What is the most important feature of Java? Java is a platform independent language. 2. What do you mean by platform independence? Platform independence means that we can write
Generating Continuation Passing Style Code for the Co-op Language
 Generating Continuation Passing Style Code for the Co-op Language Mark Laarakkers University of Twente Faculty: Computer Science Chair: Software engineering Graduation committee: dr.ing. C.M. Bockisch
Generating Continuation Passing Style Code for the Co-op Language Mark Laarakkers University of Twente Faculty: Computer Science Chair: Software engineering Graduation committee: dr.ing. C.M. Bockisch
C. E. McDowell August 25, Baskin Center for. University of California, Santa Cruz. Santa Cruz, CA USA. abstract
 Unloading Java Classes That Contain Static Fields C. E. McDowell E. A. Baldwin 97-18 August 25, 1997 Baskin Center for Computer Engineering & Information Sciences University of California, Santa Cruz Santa
Unloading Java Classes That Contain Static Fields C. E. McDowell E. A. Baldwin 97-18 August 25, 1997 Baskin Center for Computer Engineering & Information Sciences University of California, Santa Cruz Santa
Weiss Chapter 1 terminology (parenthesized numbers are page numbers)
 Weiss Chapter 1 terminology (parenthesized numbers are page numbers) assignment operators In Java, used to alter the value of a variable. These operators include =, +=, -=, *=, and /=. (9) autoincrement
Weiss Chapter 1 terminology (parenthesized numbers are page numbers) assignment operators In Java, used to alter the value of a variable. These operators include =, +=, -=, *=, and /=. (9) autoincrement
Lecture 9 : Basics of Reflection in Java
 Lecture 9 : Basics of Reflection in Java LSINF 2335 Programming Paradigms Prof. Kim Mens UCL / EPL / INGI (Slides partly based on the book Java Reflection in Action, on The Java Tutorials, and on slides
Lecture 9 : Basics of Reflection in Java LSINF 2335 Programming Paradigms Prof. Kim Mens UCL / EPL / INGI (Slides partly based on the book Java Reflection in Action, on The Java Tutorials, and on slides
DESIGN PATTERN - INTERVIEW QUESTIONS
 DESIGN PATTERN - INTERVIEW QUESTIONS http://www.tutorialspoint.com/design_pattern/design_pattern_interview_questions.htm Copyright tutorialspoint.com Dear readers, these Design Pattern Interview Questions
DESIGN PATTERN - INTERVIEW QUESTIONS http://www.tutorialspoint.com/design_pattern/design_pattern_interview_questions.htm Copyright tutorialspoint.com Dear readers, these Design Pattern Interview Questions
Martin P. Robillard and Gail C. Murphy. University of British Columbia. November, 1999
 Migrating a Static Analysis Tool to AspectJ TM Martin P. Robillard and Gail C. Murphy Department of Computer Science University of British Columbia 201-2366 Main Mall Vancouver BC Canada V6T 1Z4 fmrobilla,murphyg@cs.ubc.ca
Migrating a Static Analysis Tool to AspectJ TM Martin P. Robillard and Gail C. Murphy Department of Computer Science University of British Columbia 201-2366 Main Mall Vancouver BC Canada V6T 1Z4 fmrobilla,murphyg@cs.ubc.ca
Automatic Code Generation for Non-Functional Aspects in the CORBALC Component Model
 Automatic Code Generation for Non-Functional Aspects in the CORBALC Component Model Diego Sevilla 1, José M. García 1, Antonio Gómez 2 1 Department of Computer Engineering 2 Department of Information and
Automatic Code Generation for Non-Functional Aspects in the CORBALC Component Model Diego Sevilla 1, José M. García 1, Antonio Gómez 2 1 Department of Computer Engineering 2 Department of Information and
Implementing Software Connectors through First-Class Methods
 Implementing Software Connectors through First-Class Methods Cheoljoo Jeong and Sangduck Lee Computer & Software Technology Laboratory Electronics and Telecommunications Research Institute Taejon, 305-350,
Implementing Software Connectors through First-Class Methods Cheoljoo Jeong and Sangduck Lee Computer & Software Technology Laboratory Electronics and Telecommunications Research Institute Taejon, 305-350,
An Assertion Checking Wrapper Design for Java
 An Assertion Checking Wrapper Design for Java Roy Patrick Tan Department of Computer Science Virginia Tech 660 McBryde Hall, Mail Stop 0106 Blacksburg, VA 24061, USA rtan@vt.edu Stephen H. Edwards Department
An Assertion Checking Wrapper Design for Java Roy Patrick Tan Department of Computer Science Virginia Tech 660 McBryde Hall, Mail Stop 0106 Blacksburg, VA 24061, USA rtan@vt.edu Stephen H. Edwards Department
Using the Bridge Design Pattern for OSGi Service Update
 Using the Bridge Design Pattern for OSGi Service Update Hans Werner Pohl Jens Gerlach {hans,jens@first.fraunhofer.de Fraunhofer Institute for Computer Architecture and Software Technology (FIRST) Berlin
Using the Bridge Design Pattern for OSGi Service Update Hans Werner Pohl Jens Gerlach {hans,jens@first.fraunhofer.de Fraunhofer Institute for Computer Architecture and Software Technology (FIRST) Berlin
Chapter 5 Object-Oriented Programming
 Chapter 5 Object-Oriented Programming Develop code that implements tight encapsulation, loose coupling, and high cohesion Develop code that demonstrates the use of polymorphism Develop code that declares
Chapter 5 Object-Oriented Programming Develop code that implements tight encapsulation, loose coupling, and high cohesion Develop code that demonstrates the use of polymorphism Develop code that declares
Chapter 6 Introduction to Defining Classes
 Introduction to Defining Classes Fundamentals of Java: AP Computer Science Essentials, 4th Edition 1 Objectives Design and implement a simple class from user requirements. Organize a program in terms of
Introduction to Defining Classes Fundamentals of Java: AP Computer Science Essentials, 4th Edition 1 Objectives Design and implement a simple class from user requirements. Organize a program in terms of
COP 3330 Final Exam Review
 COP 3330 Final Exam Review I. The Basics (Chapters 2, 5, 6) a. comments b. identifiers, reserved words c. white space d. compilers vs. interpreters e. syntax, semantics f. errors i. syntax ii. run-time
COP 3330 Final Exam Review I. The Basics (Chapters 2, 5, 6) a. comments b. identifiers, reserved words c. white space d. compilers vs. interpreters e. syntax, semantics f. errors i. syntax ii. run-time
Graphical Interface and Application (I3305) Semester: 1 Academic Year: 2017/2018 Dr Antoun Yaacoub
 Lebanese University Faculty of Science Computer Science BS Degree Graphical Interface and Application (I3305) Semester: 1 Academic Year: 2017/2018 Dr Antoun Yaacoub 2 Crash Course in JAVA Classes A Java
Lebanese University Faculty of Science Computer Science BS Degree Graphical Interface and Application (I3305) Semester: 1 Academic Year: 2017/2018 Dr Antoun Yaacoub 2 Crash Course in JAVA Classes A Java
Topics. Java arrays. Definition. Data Structures and Information Systems Part 1: Data Structures. Lecture 3: Arrays (1)
 Topics Data Structures and Information Systems Part 1: Data Structures Michele Zito Lecture 3: Arrays (1) Data structure definition: arrays. Java arrays creation access Primitive types and reference types
Topics Data Structures and Information Systems Part 1: Data Structures Michele Zito Lecture 3: Arrays (1) Data structure definition: arrays. Java arrays creation access Primitive types and reference types
2 Egon Borger, Wolfram Schulte: Initialization Problems for Java 1 class A implements I{ } 2 3 interface I { static boolean dummy = Main.sideeffect =
 Initialization Problems for Java? Egon Borger 1, Wolfram Schulte 2 1 Universita di Pisa, Dipartimento di Informatica, I-56125 Pisa, Italy, e-mail: boerger@di.unipi.it 2 Universitat Ulm, Fakultat fur Informatik,
Initialization Problems for Java? Egon Borger 1, Wolfram Schulte 2 1 Universita di Pisa, Dipartimento di Informatica, I-56125 Pisa, Italy, e-mail: boerger@di.unipi.it 2 Universitat Ulm, Fakultat fur Informatik,
Distributed Objects and Remote Invocation. Programming Models for Distributed Applications
 Distributed Objects and Remote Invocation Programming Models for Distributed Applications Extending Conventional Techniques The remote procedure call model is an extension of the conventional procedure
Distributed Objects and Remote Invocation Programming Models for Distributed Applications Extending Conventional Techniques The remote procedure call model is an extension of the conventional procedure
A Meta-Model for Composition Techniques in Object-Oriented Software Development
 A Meta-Model for Composition Techniques in Object-Oriented Software Development Bedir Tekinerdogan Department of Computer Science University of Twente P.O. Box 217, 7500 AE Enschede, The Netherlands E-Mail:
A Meta-Model for Composition Techniques in Object-Oriented Software Development Bedir Tekinerdogan Department of Computer Science University of Twente P.O. Box 217, 7500 AE Enschede, The Netherlands E-Mail:
Introduction to Programming Using Java (98-388)
 Introduction to Programming Using Java (98-388) Understand Java fundamentals Describe the use of main in a Java application Signature of main, why it is static; how to consume an instance of your own class;
Introduction to Programming Using Java (98-388) Understand Java fundamentals Describe the use of main in a Java application Signature of main, why it is static; how to consume an instance of your own class;
Structural Reflection by Java Bytecode Instrumentation
 Vol. 42 No. 11 Nov. 2001 Java, Java API introspection API Javassist Java JVM Javassist JVM Javassist Structural Reflection by Java Bytecode Instrumentation Shigeru Chiba, and Michiaki Tatsubori The standard
Vol. 42 No. 11 Nov. 2001 Java, Java API introspection API Javassist Java JVM Javassist JVM Javassist Structural Reflection by Java Bytecode Instrumentation Shigeru Chiba, and Michiaki Tatsubori The standard
Idioms for Building Software Frameworks in AspectJ
 Idioms for Building Software Frameworks in AspectJ Stefan Hanenberg 1 and Arno Schmidmeier 2 1 Institute for Computer Science University of Essen, 45117 Essen, Germany shanenbe@cs.uni-essen.de 2 AspectSoft,
Idioms for Building Software Frameworks in AspectJ Stefan Hanenberg 1 and Arno Schmidmeier 2 1 Institute for Computer Science University of Essen, 45117 Essen, Germany shanenbe@cs.uni-essen.de 2 AspectSoft,
DOWNLOAD PDF CORE JAVA APTITUDE QUESTIONS AND ANSWERS
 Chapter 1 : Chapter-wise Java Multiple Choice Questions and Answers Interview MCQs Java Programming questions and answers with explanation for interview, competitive examination and entrance test. Fully
Chapter 1 : Chapter-wise Java Multiple Choice Questions and Answers Interview MCQs Java Programming questions and answers with explanation for interview, competitive examination and entrance test. Fully
As related works, OMG's CORBA (Common Object Request Broker Architecture)[2] has been developed for long years. CORBA was intended to realize interope
![As related works, OMG's CORBA (Common Object Request Broker Architecture)[2] has been developed for long years. CORBA was intended to realize interope As related works, OMG's CORBA (Common Object Request Broker Architecture)[2] has been developed for long years. CORBA was intended to realize interope](/thumbs/81/83176569.jpg) HORB: Distributed Execution of Java Programs HIRANO Satoshi Electrotechnical Laboratory and RingServer Project 1-1-4 Umezono Tsukuba, 305 Japan hirano@etl.go.jp http://ring.etl.go.jp/openlab/horb/ Abstract.
HORB: Distributed Execution of Java Programs HIRANO Satoshi Electrotechnical Laboratory and RingServer Project 1-1-4 Umezono Tsukuba, 305 Japan hirano@etl.go.jp http://ring.etl.go.jp/openlab/horb/ Abstract.
OBJECT ORIENTED PROGRAMMING USING C++ CSCI Object Oriented Analysis and Design By Manali Torpe
 OBJECT ORIENTED PROGRAMMING USING C++ CSCI 5448- Object Oriented Analysis and Design By Manali Torpe Fundamentals of OOP Class Object Encapsulation Abstraction Inheritance Polymorphism Reusability C++
OBJECT ORIENTED PROGRAMMING USING C++ CSCI 5448- Object Oriented Analysis and Design By Manali Torpe Fundamentals of OOP Class Object Encapsulation Abstraction Inheritance Polymorphism Reusability C++
Class, Variable, Constructor, Object, Method Questions
 Class, Variable, Constructor, Object, Method Questions http://www.wideskills.com/java-interview-questions/java-classes-andobjects-interview-questions https://www.careerride.com/java-objects-classes-methods.aspx
Class, Variable, Constructor, Object, Method Questions http://www.wideskills.com/java-interview-questions/java-classes-andobjects-interview-questions https://www.careerride.com/java-objects-classes-methods.aspx
The Compositional C++ Language. Denition. Abstract. This document gives a concise denition of the syntax and semantics
 The Compositional C++ Language Denition Peter Carlin Mani Chandy Carl Kesselman March 12, 1993 Revision 0.95 3/12/93, Comments welcome. Abstract This document gives a concise denition of the syntax and
The Compositional C++ Language Denition Peter Carlin Mani Chandy Carl Kesselman March 12, 1993 Revision 0.95 3/12/93, Comments welcome. Abstract This document gives a concise denition of the syntax and
CS 231 Data Structures and Algorithms, Fall 2016
 CS 231 Data Structures and Algorithms, Fall 2016 Dr. Bruce A. Maxwell Department of Computer Science Colby College Course Description Focuses on the common structures used to store data and the standard
CS 231 Data Structures and Algorithms, Fall 2016 Dr. Bruce A. Maxwell Department of Computer Science Colby College Course Description Focuses on the common structures used to store data and the standard
Outline. Computer Science 331. Information Hiding. What This Lecture is About. Data Structures, Abstract Data Types, and Their Implementations
 Outline Computer Science 331 Data Structures, Abstract Data Types, and Their Implementations Mike Jacobson 1 Overview 2 ADTs as Interfaces Department of Computer Science University of Calgary Lecture #8
Outline Computer Science 331 Data Structures, Abstract Data Types, and Their Implementations Mike Jacobson 1 Overview 2 ADTs as Interfaces Department of Computer Science University of Calgary Lecture #8
Zhifu Pei CSCI5448 Spring 2011 Prof. Kenneth M. Anderson
 Zhifu Pei CSCI5448 Spring 2011 Prof. Kenneth M. Anderson Introduction History, Characteristics of Java language Java Language Basics Data types, Variables, Operators and Expressions Anatomy of a Java Program
Zhifu Pei CSCI5448 Spring 2011 Prof. Kenneth M. Anderson Introduction History, Characteristics of Java language Java Language Basics Data types, Variables, Operators and Expressions Anatomy of a Java Program
Transaction Management in EJBs: Better Separation of Concerns With AOP
 Transaction Management in EJBs: Better Separation of Concerns With AOP Johan Fabry Vrije Universiteit Brussel, Pleinlaan 2 1050 Brussel, Belgium Johan.Fabry@vub.ac.be March 8, 2004 1 Introduction The long-term
Transaction Management in EJBs: Better Separation of Concerns With AOP Johan Fabry Vrije Universiteit Brussel, Pleinlaan 2 1050 Brussel, Belgium Johan.Fabry@vub.ac.be March 8, 2004 1 Introduction The long-term
Goals of Lecture. Lecture 27: OO Design Patterns. Pattern Resources. Design Patterns. Cover OO Design Patterns. Pattern Languages of Programming
 Goals of Lecture Lecture 27: OO Design Patterns Cover OO Design Patterns Background Examples Kenneth M. Anderson Object-Oriented Analysis and Design CSCI 6448 - Spring Semester, 2001 April 24, 2001 Kenneth
Goals of Lecture Lecture 27: OO Design Patterns Cover OO Design Patterns Background Examples Kenneth M. Anderson Object-Oriented Analysis and Design CSCI 6448 - Spring Semester, 2001 April 24, 2001 Kenneth
B2.52-R3: INTRODUCTION TO OBJECT ORIENTATED PROGRAMMING THROUGH JAVA
 B2.52-R3: INTRODUCTION TO OBJECT ORIENTATED PROGRAMMING THROUGH JAVA NOTE: 1. There are TWO PARTS in this Module/Paper. PART ONE contains FOUR questions and PART TWO contains FIVE questions. 2. PART ONE
B2.52-R3: INTRODUCTION TO OBJECT ORIENTATED PROGRAMMING THROUGH JAVA NOTE: 1. There are TWO PARTS in this Module/Paper. PART ONE contains FOUR questions and PART TWO contains FIVE questions. 2. PART ONE
Chapter 4 Defining Classes I
 Chapter 4 Defining Classes I This chapter introduces the idea that students can create their own classes and therefore their own objects. Introduced is the idea of methods and instance variables as the
Chapter 4 Defining Classes I This chapter introduces the idea that students can create their own classes and therefore their own objects. Introduced is the idea of methods and instance variables as the
Lecture 13: Design Patterns
 1 Lecture 13: Design Patterns Kenneth M. Anderson Object-Oriented Analysis and Design CSCI 6448 - Spring Semester, 2005 2 Pattern Resources Pattern Languages of Programming Technical conference on Patterns
1 Lecture 13: Design Patterns Kenneth M. Anderson Object-Oriented Analysis and Design CSCI 6448 - Spring Semester, 2005 2 Pattern Resources Pattern Languages of Programming Technical conference on Patterns
BCS THE CHARTERED INSTITUTE FOR IT. BCS HIGHER EDUCATION QUALIFICATIONS BCS Level 5 Diploma in IT OBJECT ORIENTED PROGRAMMING
 BCS THE CHARTERED INSTITUTE FOR IT BCS HIGHER EDUCATION QUALIFICATIONS BCS Level 5 Diploma in IT OBJECT ORIENTED PROGRAMMING Wednesady 23 rd March 2016 Afternoon Answer any FOUR questions out of SIX. All
BCS THE CHARTERED INSTITUTE FOR IT BCS HIGHER EDUCATION QUALIFICATIONS BCS Level 5 Diploma in IT OBJECT ORIENTED PROGRAMMING Wednesady 23 rd March 2016 Afternoon Answer any FOUR questions out of SIX. All
Java How to Program, 10/e. Copyright by Pearson Education, Inc. All Rights Reserved.
 Java How to Program, 10/e Education, Inc. All Rights Reserved. Each class you create becomes a new type that can be used to declare variables and create objects. You can declare new classes as needed;
Java How to Program, 10/e Education, Inc. All Rights Reserved. Each class you create becomes a new type that can be used to declare variables and create objects. You can declare new classes as needed;
Pattern Resources. Lecture 25: Design Patterns. What are Patterns? Design Patterns. Pattern Languages of Programming. The Portland Pattern Repository
 Pattern Resources Lecture 25: Design Patterns Kenneth M. Anderson Object-Oriented Analysis and Design CSCI 6448 - Spring Semester, 2003 Pattern Languages of Programming Technical conference on Patterns
Pattern Resources Lecture 25: Design Patterns Kenneth M. Anderson Object-Oriented Analysis and Design CSCI 6448 - Spring Semester, 2003 Pattern Languages of Programming Technical conference on Patterns
Assoc. Prof. Marenglen Biba. (C) 2010 Pearson Education, Inc. All rights reserved.
 Assoc. Prof. Marenglen Biba Exception handling Exception an indication of a problem that occurs during a program s execution. The name exception implies that the problem occurs infrequently. With exception
Assoc. Prof. Marenglen Biba Exception handling Exception an indication of a problem that occurs during a program s execution. The name exception implies that the problem occurs infrequently. With exception
Wrapping a complex C++ library for Eiffel. FINAL REPORT July 1 st, 2005
 Wrapping a complex C++ library for Eiffel FINAL REPORT July 1 st, 2005 Semester project Student: Supervising Assistant: Supervising Professor: Simon Reinhard simonrei@student.ethz.ch Bernd Schoeller Bertrand
Wrapping a complex C++ library for Eiffel FINAL REPORT July 1 st, 2005 Semester project Student: Supervising Assistant: Supervising Professor: Simon Reinhard simonrei@student.ethz.ch Bernd Schoeller Bertrand
When Java technology burst onto the Internet scene in 1995,
 MOBILE CODE SECURITY SECURE JAVA CLASS LOADING The class loading mechanism, LI GONG Sun Microsystems central to Java, plays a key role in JDK 1.2 by enabling When Java technology burst onto the Internet
MOBILE CODE SECURITY SECURE JAVA CLASS LOADING The class loading mechanism, LI GONG Sun Microsystems central to Java, plays a key role in JDK 1.2 by enabling When Java technology burst onto the Internet
Lesson 10A OOP Fundamentals. By John B. Owen All rights reserved 2011, revised 2014
 Lesson 10A OOP Fundamentals By John B. Owen All rights reserved 2011, revised 2014 Table of Contents Objectives Definition Pointers vs containers Object vs primitives Constructors Methods Object class
Lesson 10A OOP Fundamentals By John B. Owen All rights reserved 2011, revised 2014 Table of Contents Objectives Definition Pointers vs containers Object vs primitives Constructors Methods Object class
Do! environment. DoT
 The Do! project: distributed programming using Java Pascale Launay and Jean-Louis Pazat IRISA, Campus de Beaulieu, F35042 RENNES cedex Pascale.Launay@irisa.fr, Jean-Louis.Pazat@irisa.fr http://www.irisa.fr/caps/projects/do/
The Do! project: distributed programming using Java Pascale Launay and Jean-Louis Pazat IRISA, Campus de Beaulieu, F35042 RENNES cedex Pascale.Launay@irisa.fr, Jean-Louis.Pazat@irisa.fr http://www.irisa.fr/caps/projects/do/
which a value is evaluated. When parallelising a program, instances of this class need to be produced for all the program's types. The paper commented
 A Type-Sensitive Preprocessor For Haskell Noel Winstanley Department of Computer Science University of Glasgow September 4, 1997 Abstract This paper presents a preprocessor which generates code from type
A Type-Sensitive Preprocessor For Haskell Noel Winstanley Department of Computer Science University of Glasgow September 4, 1997 Abstract This paper presents a preprocessor which generates code from type
15CS45 : OBJECT ORIENTED CONCEPTS
 15CS45 : OBJECT ORIENTED CONCEPTS QUESTION BANK: What do you know about Java? What are the supported platforms by Java Programming Language? List any five features of Java? Why is Java Architectural Neutral?
15CS45 : OBJECT ORIENTED CONCEPTS QUESTION BANK: What do you know about Java? What are the supported platforms by Java Programming Language? List any five features of Java? Why is Java Architectural Neutral?
Transparent Access to Legacy Data in Java. Olivier Gruber. IBM Almaden Research Center. San Jose, CA Abstract
 Transparent Access to Legacy Data in Java Olivier Gruber IBM Almaden Research Center San Jose, CA 95120 Abstract We propose in this paper an extension to PJava in order to provide a transparent access
Transparent Access to Legacy Data in Java Olivier Gruber IBM Almaden Research Center San Jose, CA 95120 Abstract We propose in this paper an extension to PJava in order to provide a transparent access
School of Informatics, University of Edinburgh
 CS1Bh Solution Sheet 4 Software Engineering in Java This is a solution set for CS1Bh Question Sheet 4. You should only consult these solutions after attempting the exercises. Notice that the solutions
CS1Bh Solution Sheet 4 Software Engineering in Java This is a solution set for CS1Bh Question Sheet 4. You should only consult these solutions after attempting the exercises. Notice that the solutions
Late-bound Pragmatical Class Methods
 Late-bound Pragmatical Class Methods AXEL SCHMOLITZKY, MARK EVERED, J. LESLIE KEEDY, GISELA MENGER Department of Computer Structures University of Ulm 89069 Ulm, Germany {axel, markev, keedy, gisela@informatik.uni-ulm.de
Late-bound Pragmatical Class Methods AXEL SCHMOLITZKY, MARK EVERED, J. LESLIE KEEDY, GISELA MENGER Department of Computer Structures University of Ulm 89069 Ulm, Germany {axel, markev, keedy, gisela@informatik.uni-ulm.de
CSE P 501 Compilers. Java Implementation JVMs, JITs &c Hal Perkins Winter /11/ Hal Perkins & UW CSE V-1
 CSE P 501 Compilers Java Implementation JVMs, JITs &c Hal Perkins Winter 2008 3/11/2008 2002-08 Hal Perkins & UW CSE V-1 Agenda Java virtual machine architecture.class files Class loading Execution engines
CSE P 501 Compilers Java Implementation JVMs, JITs &c Hal Perkins Winter 2008 3/11/2008 2002-08 Hal Perkins & UW CSE V-1 Agenda Java virtual machine architecture.class files Class loading Execution engines
Language-Shifting Objects from Java to Smalltalk
 Language-Shifting Objects from Java to Smalltalk An exploration using JavaConnect Johan Brichau Université catholique de Louvain johan.brichau@uclouvain.be Coen De Roover Vrije Universiteit Brussel cderoove@vub.ac.be
Language-Shifting Objects from Java to Smalltalk An exploration using JavaConnect Johan Brichau Université catholique de Louvain johan.brichau@uclouvain.be Coen De Roover Vrije Universiteit Brussel cderoove@vub.ac.be
A Static Alternative To Java Dynamic Proxies
 A Static Alternative To Java Dynamic Proxies Abstract The Proxy design pattern is often used in applications, but induces generally an implementation overhead. To simplify the developer work, the Java
A Static Alternative To Java Dynamic Proxies Abstract The Proxy design pattern is often used in applications, but induces generally an implementation overhead. To simplify the developer work, the Java
PESIT Bangalore South Campus
 PESIT Bangalore South Campus 15CS45 : OBJECT ORIENTED CONCEPTS Faculty : Prof. Sajeevan K, Prof. Hanumanth Pujar Course Description: No of Sessions: 56 This course introduces computer programming using
PESIT Bangalore South Campus 15CS45 : OBJECT ORIENTED CONCEPTS Faculty : Prof. Sajeevan K, Prof. Hanumanth Pujar Course Description: No of Sessions: 56 This course introduces computer programming using
PROGRAMMING LANGUAGE 2
 31/10/2013 Ebtsam Abd elhakam 1 PROGRAMMING LANGUAGE 2 Java lecture (7) Inheritance 31/10/2013 Ebtsam Abd elhakam 2 Inheritance Inheritance is one of the cornerstones of object-oriented programming. It
31/10/2013 Ebtsam Abd elhakam 1 PROGRAMMING LANGUAGE 2 Java lecture (7) Inheritance 31/10/2013 Ebtsam Abd elhakam 2 Inheritance Inheritance is one of the cornerstones of object-oriented programming. It
Atelier Java - J1. Marwan Burelle. EPITA Première Année Cycle Ingénieur.
 marwan.burelle@lse.epita.fr http://wiki-prog.kh405.net Plan 1 2 Plan 3 4 Plan 1 2 3 4 A Bit of History JAVA was created in 1991 by James Gosling of SUN. The first public implementation (v1.0) in 1995.
marwan.burelle@lse.epita.fr http://wiki-prog.kh405.net Plan 1 2 Plan 3 4 Plan 1 2 3 4 A Bit of History JAVA was created in 1991 by James Gosling of SUN. The first public implementation (v1.0) in 1995.
CS/B.TECH/CSE(New)/SEM-5/CS-504D/ OBJECT ORIENTED PROGRAMMING. Time Allotted : 3 Hours Full Marks : 70 GROUP A. (Multiple Choice Type Question)
 CS/B.TECH/CSE(New)/SEM-5/CS-504D/2013-14 2013 OBJECT ORIENTED PROGRAMMING Time Allotted : 3 Hours Full Marks : 70 The figures in the margin indicate full marks. Candidates are required to give their answers
CS/B.TECH/CSE(New)/SEM-5/CS-504D/2013-14 2013 OBJECT ORIENTED PROGRAMMING Time Allotted : 3 Hours Full Marks : 70 The figures in the margin indicate full marks. Candidates are required to give their answers
COFFEESTRAINER - Statically Checking Structural Constraints on Java Programs
 COFFEESTRAINER - Statically Checking Structural Constraints on Java Programs Boris Bokowski bokowski@inf.fu-berlin.de Technical Report B-98-14 December 1998 Abstract It is generally desirable to detect
COFFEESTRAINER - Statically Checking Structural Constraints on Java Programs Boris Bokowski bokowski@inf.fu-berlin.de Technical Report B-98-14 December 1998 Abstract It is generally desirable to detect
CS111: PROGRAMMING LANGUAGE II
 1 CS111: PROGRAMMING LANGUAGE II Computer Science Department Lecture 4(b): Subclasses and Superclasses OOP OOP - Inheritance Inheritance represents the is a relationship between data types (e.g. student/person)
1 CS111: PROGRAMMING LANGUAGE II Computer Science Department Lecture 4(b): Subclasses and Superclasses OOP OOP - Inheritance Inheritance represents the is a relationship between data types (e.g. student/person)
Acknowledgments 2
 Program Slicing: An Application of Object-oriented Program Dependency Graphs Anand Krishnaswamy Dept. of Computer Science Clemson University Clemson, SC 29634-1906 anandk@cs.clemson.edu Abstract A considerable
Program Slicing: An Application of Object-oriented Program Dependency Graphs Anand Krishnaswamy Dept. of Computer Science Clemson University Clemson, SC 29634-1906 anandk@cs.clemson.edu Abstract A considerable
Lecture 06: Distributed Object
 Lecture 06: Distributed Object Distributed Systems Behzad Bordbar School of Computer Science, University of Birmingham, UK Lecture 0? 1 Recap Interprocess communication Synchronous and Asynchronous communication
Lecture 06: Distributed Object Distributed Systems Behzad Bordbar School of Computer Science, University of Birmingham, UK Lecture 0? 1 Recap Interprocess communication Synchronous and Asynchronous communication
M301: Software Systems & their Development. Unit 4: Inheritance, Composition and Polymorphism
 Block 1: Introduction to Java Unit 4: Inheritance, Composition and Polymorphism Aims of the unit: Study and use the Java mechanisms that support reuse, in particular, inheritance and composition; Analyze
Block 1: Introduction to Java Unit 4: Inheritance, Composition and Polymorphism Aims of the unit: Study and use the Java mechanisms that support reuse, in particular, inheritance and composition; Analyze
5 Distributed Objects: The Java Approach
 5 Distributed Objects: The Java Approach Main Points Why distributed objects Distributed Object design points Java RMI Dynamic Code Loading 5.1 What s an Object? An Object is an autonomous entity having
5 Distributed Objects: The Java Approach Main Points Why distributed objects Distributed Object design points Java RMI Dynamic Code Loading 5.1 What s an Object? An Object is an autonomous entity having
Reflection-based implementation of Java extensions: the double-dispatch use-case
 Reflection-based implementation of Java extensions: the double-dispatch use-case Abstract Reflection-based libraries could sometimes be used to extend the expressive power of Java without modifying the
Reflection-based implementation of Java extensions: the double-dispatch use-case Abstract Reflection-based libraries could sometimes be used to extend the expressive power of Java without modifying the
SAMOS: an Active Object{Oriented Database System. Stella Gatziu, Klaus R. Dittrich. Database Technology Research Group
 SAMOS: an Active Object{Oriented Database System Stella Gatziu, Klaus R. Dittrich Database Technology Research Group Institut fur Informatik, Universitat Zurich fgatziu, dittrichg@ifi.unizh.ch to appear
SAMOS: an Active Object{Oriented Database System Stella Gatziu, Klaus R. Dittrich Database Technology Research Group Institut fur Informatik, Universitat Zurich fgatziu, dittrichg@ifi.unizh.ch to appear
Week 3: Functions and Data. Working with objects. Members of an object. = n 1d 2 n 2 d 1. + n 2. = n 1d 2. = n 1n 2 / n 2. = n 2
 Week 3: Functions and Data In this section, we'll learn how functions create and encapsulate data structures. Exemple : Rational Numbers We want to design a package for doing rational arithmetic. A rational
Week 3: Functions and Data In this section, we'll learn how functions create and encapsulate data structures. Exemple : Rational Numbers We want to design a package for doing rational arithmetic. A rational
Parametric Polymorphism for Java: A Reflective Approach
 Parametric Polymorphism for Java: A Reflective Approach By Jose H. Solorzano and Suad Alagic Presented by Matt Miller February 20, 2003 Outline Motivation Key Contributions Background Parametric Polymorphism
Parametric Polymorphism for Java: A Reflective Approach By Jose H. Solorzano and Suad Alagic Presented by Matt Miller February 20, 2003 Outline Motivation Key Contributions Background Parametric Polymorphism
Week 3: Functions and Data
 Week 3: Functions and Data In this section, we'll learn how functions create and encapsulate data structures. Exemple : Rational Numbers We want to design a package for doing rational arithmetic. A rational
Week 3: Functions and Data In this section, we'll learn how functions create and encapsulate data structures. Exemple : Rational Numbers We want to design a package for doing rational arithmetic. A rational
Object-Oriented Design
 Object-Oriented Design Lecturer: Raman Ramsin Lecture 20: GoF Design Patterns Creational 1 Software Patterns Software Patterns support reuse of software architecture and design. Patterns capture the static
Object-Oriented Design Lecturer: Raman Ramsin Lecture 20: GoF Design Patterns Creational 1 Software Patterns Software Patterns support reuse of software architecture and design. Patterns capture the static
ICC++ Language Denition. Andrew A. Chien and Uday S. Reddy 1. May 25, 1995
 ICC++ Language Denition Andrew A. Chien and Uday S. Reddy 1 May 25, 1995 Preface ICC++ is a new dialect of C++ designed to support the writing of both sequential and parallel programs. Because of the signicant
ICC++ Language Denition Andrew A. Chien and Uday S. Reddy 1 May 25, 1995 Preface ICC++ is a new dialect of C++ designed to support the writing of both sequential and parallel programs. Because of the signicant
10. Object-oriented Programming. 7. Juli 2011
 7. Juli 2011 Einführung in die Programmierung Introduction to C/C++, Tobias Weinzierl page 1 of 47 Outline Object Case Study Brain Teaser Copy Constructor & Operators Object-oriented Programming, i.e.
7. Juli 2011 Einführung in die Programmierung Introduction to C/C++, Tobias Weinzierl page 1 of 47 Outline Object Case Study Brain Teaser Copy Constructor & Operators Object-oriented Programming, i.e.
CS555: Distributed Systems [Fall 2017] Dept. Of Computer Science, Colorado State University
![CS555: Distributed Systems [Fall 2017] Dept. Of Computer Science, Colorado State University CS555: Distributed Systems [Fall 2017] Dept. Of Computer Science, Colorado State University](/thumbs/83/88148270.jpg) CS 555: DISTRIBUTED SYSTEMS [RMI] Frequently asked questions from the previous class survey Shrideep Pallickara Computer Science Colorado State University L21.1 L21.2 Topics covered in this lecture RMI
CS 555: DISTRIBUTED SYSTEMS [RMI] Frequently asked questions from the previous class survey Shrideep Pallickara Computer Science Colorado State University L21.1 L21.2 Topics covered in this lecture RMI
8. Object-oriented Programming. June 15, 2010
 June 15, 2010 Introduction to C/C++, Tobias Weinzierl page 1 of 41 Outline Recapitulation Copy Constructor & Operators Object-oriented Programming Dynamic and Static Polymorphism The Keyword Static The
June 15, 2010 Introduction to C/C++, Tobias Weinzierl page 1 of 41 Outline Recapitulation Copy Constructor & Operators Object-oriented Programming Dynamic and Static Polymorphism The Keyword Static The
Introflection. Dave Landers BEA Systems, Inc.
 Introflection Dave Landers BEA Systems, Inc. dave.landers@bea.com Agenda What is Introflection? Primary Classes and Objects Loading Classes Creating Objects Invoking Methods Java Beans Proxy What is Introflection?
Introflection Dave Landers BEA Systems, Inc. dave.landers@bea.com Agenda What is Introflection? Primary Classes and Objects Loading Classes Creating Objects Invoking Methods Java Beans Proxy What is Introflection?
Cpt S 122 Data Structures. Introduction to C++ Part II
 Cpt S 122 Data Structures Introduction to C++ Part II Nirmalya Roy School of Electrical Engineering and Computer Science Washington State University Topics Objectives Defining class with a member function
Cpt S 122 Data Structures Introduction to C++ Part II Nirmalya Roy School of Electrical Engineering and Computer Science Washington State University Topics Objectives Defining class with a member function
Lecture 5: Object Interaction: RMI and RPC
 06-06798 Distributed Systems Lecture 5: Object Interaction: RMI and RPC Distributed Systems 1 Recap Message passing: send, receive synchronous versus asynchronous No global Time types of failure socket
06-06798 Distributed Systems Lecture 5: Object Interaction: RMI and RPC Distributed Systems 1 Recap Message passing: send, receive synchronous versus asynchronous No global Time types of failure socket
Chair of Software Engineering. Java and C# in depth. Carlo A. Furia, Marco Piccioni, Bertrand Meyer. Java: reflection
 Chair of Software Engineering Carlo A. Furia, Marco Piccioni, Bertrand Meyer Java: reflection Outline Introductory detour: quines Basic reflection Built-in features Introspection Reflective method invocation
Chair of Software Engineering Carlo A. Furia, Marco Piccioni, Bertrand Meyer Java: reflection Outline Introductory detour: quines Basic reflection Built-in features Introspection Reflective method invocation
Reuse Contracts As Component Interface. Descriptions. Koen De Hondt, Carine Lucas, and Patrick Steyaert. Programming Technology Lab
 Reuse Contracts As Component Interface Descriptions Koen De Hondt, Carine Lucas, and Patrick Steyaert Programming Technology Lab Computer Science Department Vrije Universiteit Brussel Pleinlaan 2, B-1050
Reuse Contracts As Component Interface Descriptions Koen De Hondt, Carine Lucas, and Patrick Steyaert Programming Technology Lab Computer Science Department Vrije Universiteit Brussel Pleinlaan 2, B-1050
Emulating the Java ME Platform on Java SE
 Emulating the Java ME Platform on Java SE Kenneth Russell Tony Wyant Sun Microsystems, Inc. Session TS-2515 2007 JavaOne SM Conference Session TS-2515 Goal of This Talk Learn advanced uses of Java bytecode
Emulating the Java ME Platform on Java SE Kenneth Russell Tony Wyant Sun Microsystems, Inc. Session TS-2515 2007 JavaOne SM Conference Session TS-2515 Goal of This Talk Learn advanced uses of Java bytecode
Java Class Visualization for Teaching Object-Oriented Concepts
 Java Class Visualization for Teaching Object-Oriented Concepts Herbert L. Dershem and James Vanderhyde Department of Computer Science Hope College Holland, MI 49422-9000 dershem@cs.hope.edu Abstract Visualization
Java Class Visualization for Teaching Object-Oriented Concepts Herbert L. Dershem and James Vanderhyde Department of Computer Science Hope College Holland, MI 49422-9000 dershem@cs.hope.edu Abstract Visualization
4.1 Introduction Programming preliminaries Constructors Destructors An example... 3
 Department of Computer Science Tackling Design Patterns Chapter 4: Factory Method design pattern Copyright c 2016 by Linda Marshall and Vreda Pieterse. All rights reserved. Contents 4.1 Introduction.................................
Department of Computer Science Tackling Design Patterns Chapter 4: Factory Method design pattern Copyright c 2016 by Linda Marshall and Vreda Pieterse. All rights reserved. Contents 4.1 Introduction.................................
Java: introduction to object-oriented features
 Chair of Software Engineering Carlo A. Furia, Marco Piccioni, Bertrand Meyer Java: introduction to object-oriented features Chair of Software Engineering Carlo A. Furia, Marco Piccioni, Bertrand Meyer
Chair of Software Engineering Carlo A. Furia, Marco Piccioni, Bertrand Meyer Java: introduction to object-oriented features Chair of Software Engineering Carlo A. Furia, Marco Piccioni, Bertrand Meyer
Java Threads and intrinsic locks
 Java Threads and intrinsic locks 1. Java and OOP background fundamentals 1.1. Objects, methods and data One significant advantage of OOP (object oriented programming) is data encapsulation. Each object
Java Threads and intrinsic locks 1. Java and OOP background fundamentals 1.1. Objects, methods and data One significant advantage of OOP (object oriented programming) is data encapsulation. Each object
Configuration Provider: A Pattern for Configuring Threaded Applications
 Configuration Provider: A Pattern for Configuring Threaded Applications Klaus Meffert 1 and Ilka Philippow 2 Technical University Ilmenau plop@klaus-meffert.de 1, ilka.philippow@tu-ilmena.de 2 Abstract
Configuration Provider: A Pattern for Configuring Threaded Applications Klaus Meffert 1 and Ilka Philippow 2 Technical University Ilmenau plop@klaus-meffert.de 1, ilka.philippow@tu-ilmena.de 2 Abstract
Inheritance. Benefits of Java s Inheritance. 1. Reusability of code 2. Code Sharing 3. Consistency in using an interface. Classes
 Inheritance Inheritance is the mechanism of deriving new class from old one, old class is knows as superclass and new class is known as subclass. The subclass inherits all of its instances variables and
Inheritance Inheritance is the mechanism of deriving new class from old one, old class is knows as superclass and new class is known as subclass. The subclass inherits all of its instances variables and
What are the characteristics of Object Oriented programming language?
 What are the various elements of OOP? Following are the various elements of OOP:- Class:- A class is a collection of data and the various operations that can be performed on that data. Object- This is
What are the various elements of OOP? Following are the various elements of OOP:- Class:- A class is a collection of data and the various operations that can be performed on that data. Object- This is
C++ Important Questions with Answers
 1. Name the operators that cannot be overloaded. sizeof,.,.*,.->, ::,? 2. What is inheritance? Inheritance is property such that a parent (or super) class passes the characteristics of itself to children
1. Name the operators that cannot be overloaded. sizeof,.,.*,.->, ::,? 2. What is inheritance? Inheritance is property such that a parent (or super) class passes the characteristics of itself to children
be used for more than one use case (for instance, for use cases Create User and Delete User, one can have one UserController, instead of two separate
 UNIT 4 GRASP GRASP: Designing objects with responsibilities Creator Information expert Low Coupling Controller High Cohesion Designing for visibility - Applying GoF design patterns adapter, singleton,
UNIT 4 GRASP GRASP: Designing objects with responsibilities Creator Information expert Low Coupling Controller High Cohesion Designing for visibility - Applying GoF design patterns adapter, singleton,
CS555: Distributed Systems [Fall 2017] Dept. Of Computer Science, Colorado State University
![CS555: Distributed Systems [Fall 2017] Dept. Of Computer Science, Colorado State University CS555: Distributed Systems [Fall 2017] Dept. Of Computer Science, Colorado State University](/thumbs/77/74873619.jpg) CS 555: DISTRIBUTED SYSTEMS [RPC & DISTRIBUTED OBJECTS] Shrideep Pallickara Computer Science Colorado State University Frequently asked questions from the previous class survey XDR Standard serialization
CS 555: DISTRIBUTED SYSTEMS [RPC & DISTRIBUTED OBJECTS] Shrideep Pallickara Computer Science Colorado State University Frequently asked questions from the previous class survey XDR Standard serialization
Data Structures (list, dictionary, tuples, sets, strings)
 Data Structures (list, dictionary, tuples, sets, strings) Lists are enclosed in brackets: l = [1, 2, "a"] (access by index, is mutable sequence) Tuples are enclosed in parentheses: t = (1, 2, "a") (access
Data Structures (list, dictionary, tuples, sets, strings) Lists are enclosed in brackets: l = [1, 2, "a"] (access by index, is mutable sequence) Tuples are enclosed in parentheses: t = (1, 2, "a") (access
2 Addressing the Inheritance Anomaly One of the major issues in correctly connecting task communication mechanisms and the object-oriented paradigm is
 Extendable, Dispatchable Task Communication Mechanisms Stephen Michell Maurya Software 29 Maurya Court Ottawa Ontario, Canada K1G 5S3 steve@maurya.on.ca Kristina Lundqvist Dept. of Computer Systems Uppsala
Extendable, Dispatchable Task Communication Mechanisms Stephen Michell Maurya Software 29 Maurya Court Ottawa Ontario, Canada K1G 5S3 steve@maurya.on.ca Kristina Lundqvist Dept. of Computer Systems Uppsala
Fighting Class Name Clashes in Java Component Systems
 Fighting Class Name Clashes in Java Component Systems Petr Hnětynka, Petr Tůma Charles University Department of Software Engineering Distributed System Research Group Malostranské náměstí 25, 118 00 Prague
Fighting Class Name Clashes in Java Component Systems Petr Hnětynka, Petr Tůma Charles University Department of Software Engineering Distributed System Research Group Malostranské náměstí 25, 118 00 Prague
Special Topics: Programming Languages
 Lecture #23 0 V22.0490.001 Special Topics: Programming Languages B. Mishra New York University. Lecture # 23 Lecture #23 1 Slide 1 Java: History Spring 1990 April 1991: Naughton, Gosling and Sheridan (
Lecture #23 0 V22.0490.001 Special Topics: Programming Languages B. Mishra New York University. Lecture # 23 Lecture #23 1 Slide 1 Java: History Spring 1990 April 1991: Naughton, Gosling and Sheridan (
Java Fundamentals p. 1 The Origins of Java p. 2 How Java Relates to C and C++ p. 3 How Java Relates to C# p. 4 Java's Contribution to the Internet p.
 Preface p. xix Java Fundamentals p. 1 The Origins of Java p. 2 How Java Relates to C and C++ p. 3 How Java Relates to C# p. 4 Java's Contribution to the Internet p. 5 Java Applets and Applications p. 5
Preface p. xix Java Fundamentals p. 1 The Origins of Java p. 2 How Java Relates to C and C++ p. 3 How Java Relates to C# p. 4 Java's Contribution to the Internet p. 5 Java Applets and Applications p. 5
M257 Past Paper Oct 2008 Attempted Solution
 M257 Past Paper Oct 2008 Attempted Solution Part 1 Question 1 A version of Java is a particular release of the language, which may be succeeded by subsequent updated versions at a later time. Some examples
M257 Past Paper Oct 2008 Attempted Solution Part 1 Question 1 A version of Java is a particular release of the language, which may be succeeded by subsequent updated versions at a later time. Some examples
Reflective Java and A Reflective Component-Based Transaction Architecture
 Reflective Java and A Reflective Component-Based Transaction Architecture Zhixue Wu APM Ltd., Poseidon House, Castle Park, Cambridge CB3 0RD UK +44 1223 568930 zhixue.wu@citrix.com ABSTRACT In this paper,
Reflective Java and A Reflective Component-Based Transaction Architecture Zhixue Wu APM Ltd., Poseidon House, Castle Park, Cambridge CB3 0RD UK +44 1223 568930 zhixue.wu@citrix.com ABSTRACT In this paper,
A stack eect (type signature) is a pair of input parameter types and output parameter types. We also consider the type clash as a stack eect. The set
 Alternative Syntactic Methods for Dening Stack Based Languages Jaanus Poial Institute of Computer Science University of Tartu, Estonia e-mail: jaanus@cs.ut.ee Abstract. Traditional formal methods of syntax
Alternative Syntactic Methods for Dening Stack Based Languages Jaanus Poial Institute of Computer Science University of Tartu, Estonia e-mail: jaanus@cs.ut.ee Abstract. Traditional formal methods of syntax
Automating Regression Testing of Java Programs the JSnoopy Way
 Automating Regression Testing of Java Programs the JSnoopy Way Theodore S. Norvell Electrical and Computer Engineering Memorial University of Newfoundland theo@engr.mun.ca Abstract As software systems
Automating Regression Testing of Java Programs the JSnoopy Way Theodore S. Norvell Electrical and Computer Engineering Memorial University of Newfoundland theo@engr.mun.ca Abstract As software systems
Java Security. Compiler. Compiler. Hardware. Interpreter. The virtual machine principle: Abstract Machine Code. Source Code
 Java Security The virtual machine principle: Source Code Compiler Abstract Machine Code Abstract Machine Code Compiler Concrete Machine Code Input Hardware Input Interpreter Output 236 Java programs: definitions
Java Security The virtual machine principle: Source Code Compiler Abstract Machine Code Abstract Machine Code Compiler Concrete Machine Code Input Hardware Input Interpreter Output 236 Java programs: definitions
Experiences in Building a Compiler for an Object-Oriented Language
 Experiences in Building a Compiler for an Object-Oriented Language José de Oliveira Guimarães Departamento de Computação UFSCar, São Carlos - SP, Brazil jose@dc.ufscar.br Abstract Traditionally books on
Experiences in Building a Compiler for an Object-Oriented Language José de Oliveira Guimarães Departamento de Computação UFSCar, São Carlos - SP, Brazil jose@dc.ufscar.br Abstract Traditionally books on
A practical and modular implementation of extended transaction models
 Oregon Health & Science University OHSU Digital Commons CSETech January 1995 A practical and modular implementation of extended transaction models Roger Barga Calton Pu Follow this and additional works
Oregon Health & Science University OHSU Digital Commons CSETech January 1995 A practical and modular implementation of extended transaction models Roger Barga Calton Pu Follow this and additional works
