Overview of Web Services API
|
|
|
- Augusta Fletcher
- 6 years ago
- Views:
Transcription
1 CHAPTER 1 The Cisco IP Interoperability and Collaboration System (IPICS) 4.0(x) application programming interface (API) provides a web services-based API that enables the management and control of various Cisco IPICS operations through programmatic interfaces and custom applications. The API includes a set of functions to control Cisco IPICS operations such as VTG creation, policy invocation, user management, and more. This chapter introduces general concepts that relate to the web services API. It also explains how to generate a client stub by using the Eclipse integrated development environment (IDE), and explains options for executing API requests. This chapter includes these topics: Generating a Web Services Client Stub, page 1-1 Creating and Executing API Client Code, page 1-3 API Client Code Example, page 1-4 API Security, page 1-7 API Logging, page 1-8 Generating a Web Services Client Stub Before using the Cisco IPICS API, you must generate a client stub on the PC that is to be used for the API development (the developer workstation). You can use a variety of tools to generate a client stub. The following sections describe how to generate the stub by using the Eclipse IDE. Obtaining and Configuring the Eclipse IDE, page 1-2 Generating a Client Stub on a Developer Workstation, page
2 Generating a Web Services Client Stub Chapter 1 Obtaining and Configuring the Eclipse IDE Before you generate a web services client stub for the Cisco IPICS API, follow these steps to obtain and configure the Eclipse IDE: Step 1 Step 2 Step 3 On the developer workstation, download the Eclipse IDE for Java Developers package from the Galileo (v 3.5.2) release of the Eclipse open-source IDE. This IDE is available from the Eclipse website. On the developer workstation, download and extract Axis2 version 1.3 from the Apache website Take these actions to configure Axis2 runtime in the Eclipse IDE: a. Launch the Eclipse IDE. b. Choose Windows > Preferences. c. In the Preferences window. expand Web Services. d. Click Axis2 Preferences. e. Click Browse and, in the Browse to a Folder window, click the folder in which you extracted Axis2. f. Click OK. g. Click OK to exit the Preference window. Generating a Client Stub on a Developer Workstation The following procedure describes how to use the Eclipse IDE to generate a client stub on a developer workstation. Before you perform this procedure, configure the Eclipse IDE on the developer workstation as described in the Obtaining and Configuring the Eclipse IDE section on page 1-2. Procedure Step 1 Step 2 Launch the Eclipse IDE and take these actions: a. Choose File > New > Other... > Web Services > Web ServiceClient. b. Click Next. The Web Services Client window appears. In the Web Services Client window, take these actions: a. In the service definition field, enter the following URL, where cisco_ipics_server is the host name or IP address of your server: b. Make sure that the Client type field displays Java Proxy. c. Click the Server: Tomcat version Server hyperlink. The Client Environment Configuration window appears. 1-2
3 Chapter 1 Creating and Executing API Client Code Step 3 Step 4 Step 5 Step 6 Step 7 Step 8 In the Client Environment Configuration window, take these actions: a. In the Server area, choose the server type that Eclipse uses when generating the stub (by default, the server type is Tomcat vx.x Server. b. Click OK. In the Web Services Client window, take these actions, click the Web service runtime: Apache Axis hyperlink. The Client Environment Configuration window appears. In the Client Environment Configuration window, take these actions: a. Click Apache Axis2 in the Web service runtime area. b. Click OK. In the Web Services Client window, take these actions, click the Client project hyperlink. In the Specify Client Project Settings window, take these actions: a. In the Client project field, enter a name for the client project. b. Make sure that the Client Project field displays Dynamic Web Project. c. Click OK. d. Click Next. The Web Service Client window appears. In the Web Service Client window, click Finish. The client stub is generated in a folder with the name that you specified in the Specify Client Project Settings window. Creating and Executing API Client Code Each API service function requires a valid session ID to access the API functions. To start a new web services session, the client code must call the startsession function and provide the login name and password that are used to authenticate the user who executes the API code. After authentication completes, the startsession method returns a unique SessionId value, which should be used when executing subsequent API methods in a web service session. To end a session, the API client code must call the endsession function, which invalidates the current SessionId and is important for security. For additional information about using the API, see the Function Guidelines section on page 2-1. After you create API client code, follow these steps to execute it: Procedure Step 1 Launch the Eclipse IDE and take these actions: a. Click the name of the client file in the left panel of the window. b. Choose Run > Run Configurations... The Run Configurations window appears. 1-3
4 API Client Code Example Chapter 1 Step 2 In the Run Configurations window, take these actions: a. Right-click Java Application in the left panel of the window. b. Choose New. c. Click Run. API Client Code Example The following is an example of Cisco API client code. In this example: The location of the keystore is specified. The keystore contains the SSL certificate that the Cisco IPICS server uses to verify its identity when a client attempts to connect to the server, and the URL for the web service endpoint. The startsession function is executed. This function returns a unique sessionid, which is needed to execute other web service functions. The getipicsversion is executed. This function returns the Cisco IPICS version that is running on the Cisco IPICS sever. These VTG functions are executed: createvtg Create a new VTG on the Cisco IPICS server and returns the ID of the VTG, activates VTG and returns list of all VTG's present in the system respectively. activatevtg Activates the newly-created VTG. getallvtgs Retrieves a list of all VTGs that are present in Cisco IPICS. The endsession function is executed. This function terminate the web service session. A terminated session cannot be used again. package com.example; import java.rmi.remoteexception; import com.example.ipicswebservicestub.*; public class IpicsWebServiceTestClient { // The web service stub private static IpicsWebServiceStub ws = null; // // Modify the following parameters as needed for your environment // // Update with your server's address. // Note: The use of HTTPS/SSL is optional, but highly recommended. private static final String WEB_SERVICE_ENDPOINT_URL = " // If you use SSL to connect to the server, update with the location // of your trusted SSL certificate key store (sometimes also called // a "trust store"). private static final String KEY_STORE_FILE = "c:\\client_truststore.jks"; // Choose the client type: IDC or IPHONE // Affects how clients show up in the Active Users page found in the // Cisco IPICS Administration Console. private static final String CLIENT_TYPE = "IDC"; 1-4
5 Chapter 1 API Client Code Example // Update with the IPICS user login used to connect to the server. // Use of the default "ipics" user account is not recommended, but // shown here for simplicity. private static final String USER_LOGIN = "ipics"; // Update with the corresponding IPICS user password. private static final String USER_PASSWORD = "secret"; public static void main(string[] args) { String sessionid = null; try { // Note: Use Java keytool to import the server's SSL certificate // into KEY_STORE_FILE before running this client application, // otherwise your SSL connection will fail. System.setProperty("javax.net.ssl.trustStore", KEY_STORE_FILE); // Create web service stub object using end-point URL ws = new IpicsWebServiceStub(WEB_SERVICE_ENDPOINT_URL); sessionid = teststartsession(); System.out.println("Session ID : " + sessionid); testgetipicsversion(sessionid); int vtgid = testcreatevtg(sessionid); testactivatevtg(sessionid, vtgid); testgetallvtgs(sessionid); testendsession(sessionid); catch (Exception e) { e.printstacktrace(); private static String teststartsession() throws Exception { ClientDescriptorVO cd = new ClientDescriptorVO(); cd.setclienttype(client_type); StartSession params = new StartSession(); params.setclientdescriptor(cd); params.setuserlogin(user_login); params.setpass(user_password); SessionVO result = ws.startsession(params).get_return(); if (result.geterrorvo()!= null) { System.out.println(result.getErrorVO().getErrorMessages()); return null; String sessionid = result.getsessionid(); return sessionid; private static String testgetipicsversion(string sessionid) throws RemoteException { System.out.println("\n GetIpicsVersion "); GetIpicsVersion params = new GetIpicsVersion(); 1-5
6 API Client Code Example Chapter 1 StringVO result = ws.getipicsversion(params).get_return(); if (result.geterrorvo() == null) { System.out.println("\nIPICS Version: " + result.getvalue()); return result.getvalue(); else { System.out.println("\nIPICS Version: " + result.geterrorvo().geterrormessages()); return null; private static int testcreatevtg(string sessionid) { System.out.println("\n Create VTG "); CreateVtg params = new CreateVtg(); params.setvtgname("vtg1"); params.setdescription("test VTG 1"); IntegerVO result = new IntegerVO(); try { result = ws.createvtg(params).get_return(); catch (RemoteException e) { e.printstacktrace(); if (result.geterrorvo()!= null) { System.out.println(result.getErrorVO().getErrorMessages()); return 0; System.out.println("\n VTG Id : " + result.getvalue()); return result.getvalue(); private static void testactivatevtg(string sessionid, int vtgid) throws Exception { System.out.println("\n Activate VTG "); ActivateVtg params = new ActivateVtg(); params.setvtgid(vtgid); BooleanVO result = ws.activatevtg(params).get_return(); if (result.geterrorvo()!= null) { System.out.println(result.getErrorVO().getErrorMessages()); return; System.out.println("\n Return Value : " + result.getvalue()); private static VtgContainerVO testgetallvtgs(string sessionid) throws Exception { System.out.println("\n Get All VTGs "); PaginationContextVO pc = new PaginationContextVO(); pc.setpagenumber(1); pc.setpagerecords(100); pc.settotalrecords(100); GetAllVtgs params = new GetAllVtgs(); params.setpc(pc); 1-6
7 Chapter 1 API Security VtgContainerVO result = ws.getallvtgs(params).get_return(); if (result.geterrorvo()!= null) { System.out.println(result.getErrorVO().getErrorMessages()); return null; System.out.println("VTG container length : " + result.getvtgvos().length); System.out.println("VTG Total Records : " + result.getpaginationcontextvo().gettotalrecords()); System.out.println("VTG Total Pages : " + result.getpaginationcontextvo().gettotalpages()); return result; private static void testendsession(string sessionid) throws Exception { System.out.println("\n End Session "); EndSession params = new EndSession(); ws.endsession(params); System.out.println("Session ID deleted successfully."); API Security The Cisco IPICS server and the Cisco IPICS API use SSL for secure communication between the server and client systems. The server uses a X.509 certificate (also called an SSL certificate) to verify its identity when a client attempts to connect to the server. By default, the Cisco IPICS server provides a self-signed certificate, which a client typically rejects. To prevent a client from rejecting this certificate, take one of the of the actions that Table 1-1 describes. Table 1-1 Methods for Preventing a Client from Rejecting the Cisco IPICS Server Self-Signed Certificate Method Replace the Cisco IPICS server self-signed certificate with a certificate that is signed by a well-known certificate authority (CA), such as VeriSign or a local CA in your organization. Remarks For additional information, see the Installing Third Party Certificates on the Cisco IPICS Server section in Cisco IPICS Server Installation and Upgrade Guide. 1-7
8 API Logging Chapter 1 Table 1-1 Methods for Preventing a Client from Rejecting the Cisco IPICS Server Self-Signed Certificate (continued) Method When using a Java client, configure the SSL libraries for your clients to trust the self-signed certificate by using the Java keytool to import the certificate into the client truststore. If you are using a client other than Java, configure the SSL libraries for your clients to trust the self-signed certificate. Modify the way in which your client code validates certificate trust chains. Remarks Procedure: 1. Use SSH to log in to the Cisco IPICS server as the root user. 2. Enter the following command: cd /opt/cisco/ipics/security 3. Download the self-signed certificate named server.cert.pem to the client system. 4. Enter the following command. Replace name with a unique name for the alias, replace certificate_file that you downloaded to the client, and replace path with the path to the client keystore: keytool -import -alias name -file certificate_file -keystore path You may be able to copy the self-signed certificate to a special directory on the client system. See your library documentation for detailed information. Some languages provide configurable SSL files that let you change the default certificate validation behavior. A client verifies its identity with a user name and password that are sent to the server by the client application. API Logging The Cisco IPICS server logs all web service invocations. Entries include the date and time of the invocation, the API function that was used, and the status of the response. This information is maintained in the Cisco IPICS log file. For more information about the log file, see Cisco IPICS Administration Guide. 1-8
Security configuration of the mail server IBM
 Security configuration of the mail server IBM ii Security configuration of the mail server Contents Security configuration of the mail server 1 Configuration of the SSL client to trust the SMTP server
Security configuration of the mail server IBM ii Security configuration of the mail server Contents Security configuration of the mail server 1 Configuration of the SSL client to trust the SMTP server
Access SharePoint using Basic Authentication and SSL (via Alternative Access URL) with SP 2016 (v 1.9)
 Access SharePoint using Basic Authentication and SSL (via Alternative Access URL) with SP 2016 (v 9) This page is part of the installation guide for the Confluence SharePoint Connector. It tells you how
Access SharePoint using Basic Authentication and SSL (via Alternative Access URL) with SP 2016 (v 9) This page is part of the installation guide for the Confluence SharePoint Connector. It tells you how
API Developer Notes. A Galileo Web Services Java Connection Class Using Axis. 29 June Version 1.3
 API Developer Notes A Galileo Web Services Java Connection Class Using Axis 29 June 2012 Version 1.3 THE INFORMATION CONTAINED IN THIS DOCUMENT IS CONFIDENTIAL AND PROPRIETARY TO TRAVELPORT Copyright Copyright
API Developer Notes A Galileo Web Services Java Connection Class Using Axis 29 June 2012 Version 1.3 THE INFORMATION CONTAINED IN THIS DOCUMENT IS CONFIDENTIAL AND PROPRIETARY TO TRAVELPORT Copyright Copyright
Getting Started with the Bullhorn SOAP API and Java
 Getting Started with the Bullhorn SOAP API and Java Introduction This article is targeted at developers who want to do custom development using the Bullhorn SOAP API and Java. You will create a sample
Getting Started with the Bullhorn SOAP API and Java Introduction This article is targeted at developers who want to do custom development using the Bullhorn SOAP API and Java. You will create a sample
Installation Guide for antegma accallio OX Version 1.0
 Installation Guide for antegma accallio OX 1.0.0 Version 1.0 INSTALLATION VIA PACKAGE MANAGER OF ADOBE EXPERIENCE MANAGER 3 Download of the content package 3 Install content package via AEM Package Manager
Installation Guide for antegma accallio OX 1.0.0 Version 1.0 INSTALLATION VIA PACKAGE MANAGER OF ADOBE EXPERIENCE MANAGER 3 Download of the content package 3 Install content package via AEM Package Manager
Certificate Properties File Realm
 Certificate Properties File Realm {scrollbar} This realm type allows you to configure Web applications to authenticate users against it. To get to that point, you will need to first configure Geronimo
Certificate Properties File Realm {scrollbar} This realm type allows you to configure Web applications to authenticate users against it. To get to that point, you will need to first configure Geronimo
ConnectUPS-X / -BD /-E How to use and install SSL, SSH
 ConnectUPS-X /-BD /-E product family Root CA Certificate installation Rev. B Page 1/16 Index 1. How to use and install SSL (Secure Socket Layer)...3 1.1. General Certificate warning message if not installed...3
ConnectUPS-X /-BD /-E product family Root CA Certificate installation Rev. B Page 1/16 Index 1. How to use and install SSL (Secure Socket Layer)...3 1.1. General Certificate warning message if not installed...3
Getting Started Guide
 BlackBerry Web Services for Enterprise Administration For Java developers Version: 1.0 Getting Started Guide Published: 2013-01-28 SWD-20130128151511069 Contents 1 Overview: BlackBerry Web Services...
BlackBerry Web Services for Enterprise Administration For Java developers Version: 1.0 Getting Started Guide Published: 2013-01-28 SWD-20130128151511069 Contents 1 Overview: BlackBerry Web Services...
PKI Cert Creation via Good Control: Reference Implementation
 PKI Cert Creation via Good Control: Reference Implementation Legal Notice Copyright 2016 BlackBerry Limited. All rights reserved. All use is subject to license terms posted at http://us.blackberry.com/legal/legal.html.
PKI Cert Creation via Good Control: Reference Implementation Legal Notice Copyright 2016 BlackBerry Limited. All rights reserved. All use is subject to license terms posted at http://us.blackberry.com/legal/legal.html.
Securing U2 Soap Server
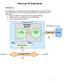 Securing U2 Soap Server Introduction To enable SSL on the Client(Consumer-to-U2SS side), we need a U2 soap server Certificate. There are three possible methods to obtain the Server Certificate: 1. Use
Securing U2 Soap Server Introduction To enable SSL on the Client(Consumer-to-U2SS side), we need a U2 soap server Certificate. There are three possible methods to obtain the Server Certificate: 1. Use
Setting Up the Server
 Managing Licenses, page 1 Cross-launch from Prime Collaboration Provisioning, page 5 Integrating Prime Collaboration Servers, page 6 Single Sign-On for Prime Collaboration, page 7 Changing the SSL Port,
Managing Licenses, page 1 Cross-launch from Prime Collaboration Provisioning, page 5 Integrating Prime Collaboration Servers, page 6 Single Sign-On for Prime Collaboration, page 7 Changing the SSL Port,
Enabling Secure Sockets Layer for a Microsoft SQL Server JDBC Connection
 Enabling Secure Sockets Layer for a Microsoft SQL Server JDBC Connection Secure Sockets Layer (SSL) is the standard security technology for establishing an encrypted link between a web server and a browser.
Enabling Secure Sockets Layer for a Microsoft SQL Server JDBC Connection Secure Sockets Layer (SSL) is the standard security technology for establishing an encrypted link between a web server and a browser.
Introducing Cisco IPICS
 CHAPTER1 The Cisco IP Interoperability and Collaboration System (Cisco IPICS) provides voice interoperability among disparate systems. It offers an IP standards-based solution that interconnects voice
CHAPTER1 The Cisco IP Interoperability and Collaboration System (Cisco IPICS) provides voice interoperability among disparate systems. It offers an IP standards-based solution that interconnects voice
JAVA - DRI Connection Test Manual
 JAVA - DRI Connection Test Manual This is a step by step guide on how to access the DRI Web service with native Java. 1. Install the NetBeans IDE Since the DRI Web service is developed in.net WCF, interoperability
JAVA - DRI Connection Test Manual This is a step by step guide on how to access the DRI Web service with native Java. 1. Install the NetBeans IDE Since the DRI Web service is developed in.net WCF, interoperability
2018/2/5 话费券企业客户接入文档 语雀
 1 2 2 1 2 1 1 138999999999 2 1 2 https:lark.alipay.com/kaidi.hwf/hsz6gg/ppesyh#2.4-%e4%bc%81%e4%b8%9a%e5%ae%a2%e6%88%b7%e6%8e%a5%e6%94%b6%e5%85%85%e5 1/8 2 1 3 static IAcsClient client = null; public static
1 2 2 1 2 1 1 138999999999 2 1 2 https:lark.alipay.com/kaidi.hwf/hsz6gg/ppesyh#2.4-%e4%bc%81%e4%b8%9a%e5%ae%a2%e6%88%b7%e6%8e%a5%e6%94%b6%e5%85%85%e5 1/8 2 1 3 static IAcsClient client = null; public static
OpenScape Voice V8 Application Developers Manual. Programming Guide A31003-H8080-R
 OpenScape Voice V8 Application Developers Manual Programming Guide A31003-H8080-R100-4-7620 Our Quality and Environmental Management Systems are implemented according to the requirements of the ISO9001
OpenScape Voice V8 Application Developers Manual Programming Guide A31003-H8080-R100-4-7620 Our Quality and Environmental Management Systems are implemented according to the requirements of the ISO9001
Creating and Installing SSL Certificates (for Stealthwatch System v6.10)
 Creating and Installing SSL Certificates (for Stealthwatch System v6.10) Copyrights and Trademarks 2017 Cisco Systems, Inc. All rights reserved. NOTICE THE SPECIFICATIONS AND INFORMATION REGARDING THE
Creating and Installing SSL Certificates (for Stealthwatch System v6.10) Copyrights and Trademarks 2017 Cisco Systems, Inc. All rights reserved. NOTICE THE SPECIFICATIONS AND INFORMATION REGARDING THE
Workspace ONE UEM Integration with RSA PKI. VMware Workspace ONE UEM 1810
 Workspace ONE UEM Integration with RSA PKI VMware Workspace ONE UEM 1810 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
Workspace ONE UEM Integration with RSA PKI VMware Workspace ONE UEM 1810 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments
SAML-Based SSO Configuration
 Prerequisites, page 1 SAML SSO Configuration Workflow, page 5 Reconfigure OpenAM SSO to SAML SSO After an Upgrade, page 9 Prerequisites NTP Setup In SAML SSO, Network Time Protocol (NTP) enables clock
Prerequisites, page 1 SAML SSO Configuration Workflow, page 5 Reconfigure OpenAM SSO to SAML SSO After an Upgrade, page 9 Prerequisites NTP Setup In SAML SSO, Network Time Protocol (NTP) enables clock
Configuring SSL CHAPTER
 7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
Signicat Connector for Java Version 2.6. Document version 3
 Signicat Connector for Java Version 2.6 Document version 3 About this document Purpose Target This document is a guideline for using Signicat Connector for Java. Signicat Connector for Java is a client
Signicat Connector for Java Version 2.6 Document version 3 About this document Purpose Target This document is a guideline for using Signicat Connector for Java. Signicat Connector for Java is a client
Getting Started. Overview CHAPTER
 CHAPTER 1 This chapter provides information that you need to get started with the IPICS Mobile Client. It includes these topics: Overview, page 1-1 Obtaining the IPICS Mobile Client, page 1-3, page 1-4
CHAPTER 1 This chapter provides information that you need to get started with the IPICS Mobile Client. It includes these topics: Overview, page 1-1 Obtaining the IPICS Mobile Client, page 1-3, page 1-4
IBM Security Secret Server Version Application Server API Guide
 IBM Security Secret Server Version 10.4 Application Server API Guide Contents Overview... 1 Concepts... 1 Standalone Java API... 1 Integrated Java API... 1 Integrated.NET Configuration API... 1 Application
IBM Security Secret Server Version 10.4 Application Server API Guide Contents Overview... 1 Concepts... 1 Standalone Java API... 1 Integrated Java API... 1 Integrated.NET Configuration API... 1 Application
Configuring SSL. SSL Overview CHAPTER
 CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
Configuring SSL. SSL Overview CHAPTER
 7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE. 31 January 2017
 BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
Getting Started. Overview CHAPTER
 1 CHAPTER This chapter provides information that you need to get started with the IPICS Mobile Client. It includes these topics: Overview, page 1-1 Obtaining the IPICS Mobile Client, page 1-4 Obtaining
1 CHAPTER This chapter provides information that you need to get started with the IPICS Mobile Client. It includes these topics: Overview, page 1-1 Obtaining the IPICS Mobile Client, page 1-4 Obtaining
SAML-Based SSO Configuration
 Prerequisites, page 1 SAML SSO Configuration Task Flow, page 5 Reconfigure OpenAM SSO to SAML SSO Following an Upgrade, page 9 SAML SSO Deployment Interactions and Restrictions, page 9 Prerequisites NTP
Prerequisites, page 1 SAML SSO Configuration Task Flow, page 5 Reconfigure OpenAM SSO to SAML SSO Following an Upgrade, page 9 SAML SSO Deployment Interactions and Restrictions, page 9 Prerequisites NTP
Public Key Enabling Oracle Weblogic Server
 DoD Public Key Enablement (PKE) Reference Guide Public Key Enabling Oracle Weblogic Server Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke URL: http://iase.disa.smil.mil/pki-pke Public Key Enabling
DoD Public Key Enablement (PKE) Reference Guide Public Key Enabling Oracle Weblogic Server Contact: dodpke@mail.mil URL: http://iase.disa.mil/pki-pke URL: http://iase.disa.smil.mil/pki-pke Public Key Enabling
Installation Guide for antegma accallio SP Version 1.0
 Installation Guide for antegma accallio SP 1.0.0 Version 1.0 INSTALLATION VIA PACKAGE MANAGER OF ADOBE EXPERIENCE MANAGER 3 Download of the content package 3 Install content package via AEM Package Manager
Installation Guide for antegma accallio SP 1.0.0 Version 1.0 INSTALLATION VIA PACKAGE MANAGER OF ADOBE EXPERIENCE MANAGER 3 Download of the content package 3 Install content package via AEM Package Manager
SSL Configuration Oracle Banking Liquidity Management Release [April] [2017]
![SSL Configuration Oracle Banking Liquidity Management Release [April] [2017] SSL Configuration Oracle Banking Liquidity Management Release [April] [2017]](/thumbs/74/70574223.jpg) SSL Configuration Oracle Banking Liquidity Management Release 12.4.0.0.0 [April] [2017] Table of Contents 1. CONFIGURING SSL ON ORACLE WEBLOGIC... 1-1 1.1 INTRODUCTION... 1-1 1.2 SETTING UP SSL ON ORACLE
SSL Configuration Oracle Banking Liquidity Management Release 12.4.0.0.0 [April] [2017] Table of Contents 1. CONFIGURING SSL ON ORACLE WEBLOGIC... 1-1 1.1 INTRODUCTION... 1-1 1.2 SETTING UP SSL ON ORACLE
Comodo Certificate Manager Version 5.4
 Comodo Certificate Manager Version 5.4 Introduction to Auto-Installer Comodo CA Limited, 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater Manchester M5 3EQ, United Kingdom.
Comodo Certificate Manager Version 5.4 Introduction to Auto-Installer Comodo CA Limited, 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater Manchester M5 3EQ, United Kingdom.
BEAAquaLogic. Service Bus. Interoperability With EJB Transport
 BEAAquaLogic Service Bus Interoperability With EJB Transport Version 3.0 Revised: February 2008 Contents EJB Transport Introduction...........................................................1-1 Invoking
BEAAquaLogic Service Bus Interoperability With EJB Transport Version 3.0 Revised: February 2008 Contents EJB Transport Introduction...........................................................1-1 Invoking
IBM Security Access Manager Version Appliance troubleshooting topics
 IBM Security Access Manager Version 8.0.0.5 Appliance troubleshooting topics IBM Security Access Manager Version 8.0.0.5 Appliance troubleshooting topics ii IBM Security Access Manager Version 8.0.0.5:
IBM Security Access Manager Version 8.0.0.5 Appliance troubleshooting topics IBM Security Access Manager Version 8.0.0.5 Appliance troubleshooting topics ii IBM Security Access Manager Version 8.0.0.5:
Configure DNA Center Assurance for Cisco ISE Integration
 Configure DNA Center Assurance for Cisco ISE Integration If your network uses Cisco ISE for user authentication, you can configure DNA Center Assurance for Cisco ISE integration. This will allow you to
Configure DNA Center Assurance for Cisco ISE Integration If your network uses Cisco ISE for user authentication, you can configure DNA Center Assurance for Cisco ISE integration. This will allow you to
Interfaces to tools: applications, libraries, Web applications, and Web services
 Interfaces to tools: applications, libraries, Web applications, and Web services Matúš Kalaš The Bioinformatics Lab SS 2013 14 th May 2013 Plurality of interfaces for accessible bioinformatics: Applications
Interfaces to tools: applications, libraries, Web applications, and Web services Matúš Kalaš The Bioinformatics Lab SS 2013 14 th May 2013 Plurality of interfaces for accessible bioinformatics: Applications
Entrust Connector (econnector) Venafi Trust Protection Platform
 Entrust Connector (econnector) For Venafi Trust Protection Platform Installation and Configuration Guide Version 1.0.5 DATE: 17 November 2017 VERSION: 1.0.5 Copyright 2017. All rights reserved Table of
Entrust Connector (econnector) For Venafi Trust Protection Platform Installation and Configuration Guide Version 1.0.5 DATE: 17 November 2017 VERSION: 1.0.5 Copyright 2017. All rights reserved Table of
Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at
 Document Date: May 16, 2017 THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL
Document Date: May 16, 2017 THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL
Troubleshooting the Installation
 CHAPTER 5 This chapter provides information about basic troubleshooting tips and error messages that you may encounter during the installation of the Cisco Linux operating system or the Cisco IPICS server
CHAPTER 5 This chapter provides information about basic troubleshooting tips and error messages that you may encounter during the installation of the Cisco Linux operating system or the Cisco IPICS server
Configuring Network Composer and workstations for Full SSL Filtering and Inspection
 January 20, 2011 Author: Audience: SWAT Team Evaluator Product: Cymphonix Network Composer EX Series, XLi OS version 9 Configuring Network Composer and workstations for Full SSL Filtering and Inspection
January 20, 2011 Author: Audience: SWAT Team Evaluator Product: Cymphonix Network Composer EX Series, XLi OS version 9 Configuring Network Composer and workstations for Full SSL Filtering and Inspection
Generic architecture
 Java-RMI Lab Outline Let first builds a simple home-made framework This is useful to understand the main issues We see later how java-rmi works and how it solves the same issues Generic architecture object
Java-RMI Lab Outline Let first builds a simple home-made framework This is useful to understand the main issues We see later how java-rmi works and how it solves the same issues Generic architecture object
HPE Enterprise Integration Module for SAP Solution Manager 7.1
 HPE Enterprise Integration Module for SAP Solution Manager 7.1 Software Version: 12.55 User Guide Document Release Date: August 2017 Software Release Date: August 2017 HPE Enterprise Integration Module
HPE Enterprise Integration Module for SAP Solution Manager 7.1 Software Version: 12.55 User Guide Document Release Date: August 2017 Software Release Date: August 2017 HPE Enterprise Integration Module
WEB SERVICES EXAMPLE 2
 INTERNATIONAL UNIVERSITY HCMC PROGRAMMING METHODOLOGY NONG LAM UNIVERSITY Instructor: Dr. Le Thanh Sach FACULTY OF IT WEBSITE SPECIAL SUBJECT Student-id: Instructor: LeMITM04015 Nhat Tung Course: IT.503
INTERNATIONAL UNIVERSITY HCMC PROGRAMMING METHODOLOGY NONG LAM UNIVERSITY Instructor: Dr. Le Thanh Sach FACULTY OF IT WEBSITE SPECIAL SUBJECT Student-id: Instructor: LeMITM04015 Nhat Tung Course: IT.503
Comodo Certificate Manager Software Version 5.0
 Comodo Certificate Manager Software Version 5.0 Introduction to Auto-Installer Comodo CA Limited, 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater Manchester M5 3EQ, United
Comodo Certificate Manager Software Version 5.0 Introduction to Auto-Installer Comodo CA Limited, 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater Manchester M5 3EQ, United
VMware AirWatch Integration with RSA PKI Guide
 VMware AirWatch Integration with RSA PKI Guide For VMware AirWatch Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com. This product
VMware AirWatch Integration with RSA PKI Guide For VMware AirWatch Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com. This product
SafeNet KMIP and Google Drive Integration Guide
 SafeNet KMIP and Google Drive Integration Guide Documentation Version: 20130802 Table of Contents CHAPTER 1 GOOGLE DRIVE......................................... 2 Introduction...............................................................
SafeNet KMIP and Google Drive Integration Guide Documentation Version: 20130802 Table of Contents CHAPTER 1 GOOGLE DRIVE......................................... 2 Introduction...............................................................
Using Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS)
 CHAPTER 2 Using Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS) This chapter contains information on the following topics: HTTPS Overview, page 2-1 HTTPS for Cisco Unified IP Phone Services,
CHAPTER 2 Using Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS) This chapter contains information on the following topics: HTTPS Overview, page 2-1 HTTPS for Cisco Unified IP Phone Services,
Enabling Microsoft Outlook Calendar Notifications for Meetings Scheduled from the Cisco Unified MeetingPlace End-User Web Interface
 Enabling Microsoft Outlook Calendar Notifications for Meetings Scheduled from the Cisco Unified MeetingPlace End-User Web Interface Release 7.1 Revised: March 5, 2013 1:53 pm This document describes the
Enabling Microsoft Outlook Calendar Notifications for Meetings Scheduled from the Cisco Unified MeetingPlace End-User Web Interface Release 7.1 Revised: March 5, 2013 1:53 pm This document describes the
SAML 2.0 SSO. Set up SAML 2.0 SSO. SAML 2.0 Terminology. Prerequisites
 SAML 2.0 SSO Agiloft integrates with a variety of SAML authentication providers, or Identity Providers (IdPs). SAML-based SSO is a leading method for providing federated access to multiple applications
SAML 2.0 SSO Agiloft integrates with a variety of SAML authentication providers, or Identity Providers (IdPs). SAML-based SSO is a leading method for providing federated access to multiple applications
Comodo Certificate Manager Version 5.7
 Comodo Certificate Manager Version 5.7 Introduction to Auto-Installer Comodo CA Limited, 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater Manchester M5 3EQ, United Kingdom.
Comodo Certificate Manager Version 5.7 Introduction to Auto-Installer Comodo CA Limited, 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater Manchester M5 3EQ, United Kingdom.
Getting Started with Cisco UCS Director Open Automation
 Getting Started with Cisco UCS Director Open Automation Cisco UCS Director Open Automation, page 1 Upgrading Your Connector to the Current Release, page 5 Modules, page 5 Cisco UCS Director Open Automation
Getting Started with Cisco UCS Director Open Automation Cisco UCS Director Open Automation, page 1 Upgrading Your Connector to the Current Release, page 5 Modules, page 5 Cisco UCS Director Open Automation
IBM Security Identity Governance and Intelligence. SDI-based IBM Security Privileged Identity Manager adapter Installation and Configuration Guide IBM
 IBM Security Identity Governance and Intelligence SDI-based IBM Security Privileged Identity Manager adapter Installation and Configuration Guide IBM IBM Security Identity Governance and Intelligence
IBM Security Identity Governance and Intelligence SDI-based IBM Security Privileged Identity Manager adapter Installation and Configuration Guide IBM IBM Security Identity Governance and Intelligence
Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS)
 Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
VII. Corente Services SSL Client
 VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
CS193k, Stanford Handout #12. Threads 4 / RMI
 CS193k, Stanford Handout #12 Spring, 99-00 Nick Parlante Threads 4 / RMI Semaphore1 Semaphore1 from last time uses the count in a precise way to know exactly how many threads are waiting. In this way,
CS193k, Stanford Handout #12 Spring, 99-00 Nick Parlante Threads 4 / RMI Semaphore1 Semaphore1 from last time uses the count in a precise way to know exactly how many threads are waiting. In this way,
Advanced Integration TLS Certificate on the NotifySCM Server
 Advanced Integration TLS Certificate on the NotifySCM Server TABLE OF CONTENTS 1 Enable a TLS Connection Between NotifySCM and a Reverse Proxy... 3 1.1 Generate a self-signed certificate... 3 1.2 Install
Advanced Integration TLS Certificate on the NotifySCM Server TABLE OF CONTENTS 1 Enable a TLS Connection Between NotifySCM and a Reverse Proxy... 3 1.1 Generate a self-signed certificate... 3 1.2 Install
Healthcare Database Connector
 Healthcare Database Connector Installation and Setup Guide Version: 1.0.x Written by: Product Knowledge, R&D Date: September 2016 2015 Lexmark International Technology, S.A. All rights reserved. Lexmark
Healthcare Database Connector Installation and Setup Guide Version: 1.0.x Written by: Product Knowledge, R&D Date: September 2016 2015 Lexmark International Technology, S.A. All rights reserved. Lexmark
SCCM Plug-in User Guide. Version 3.0
 SCCM Plug-in User Guide Version 3.0 JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF Software 301 4th Ave
SCCM Plug-in User Guide Version 3.0 JAMF Software, LLC 2012 JAMF Software, LLC. All rights reserved. JAMF Software has made all efforts to ensure that this guide is accurate. JAMF Software 301 4th Ave
ENTRUST CONNECTOR Installation and Configuration Guide Version April 21, 2017
 ENTRUST CONNECTOR Installation and Configuration Guide Version 0.5.1 April 21, 2017 2017 CygnaCom Solutions, Inc. All rights reserved. Contents What is Entrust Connector... 4 Installation... 5 Prerequisites...
ENTRUST CONNECTOR Installation and Configuration Guide Version 0.5.1 April 21, 2017 2017 CygnaCom Solutions, Inc. All rights reserved. Contents What is Entrust Connector... 4 Installation... 5 Prerequisites...
Web Service Integration
 SOAP Service, page 1 Rest Service, page 2 SOAP Service Web Services Element Web services are a common way for any kind of application to communicate with externally hosted servers to retrieve information
SOAP Service, page 1 Rest Service, page 2 SOAP Service Web Services Element Web services are a common way for any kind of application to communicate with externally hosted servers to retrieve information
UNT System Campus VPN Guide
 Contents Introduction... 3 SSL Web Portal... 4 Installing AnyConnect VPNClient... 12 Connecting AnyConnect VPN client... 16 IPSec Client Configuration... 18 Apple OS X Configuration... 21 Android Configuration...
Contents Introduction... 3 SSL Web Portal... 4 Installing AnyConnect VPNClient... 12 Connecting AnyConnect VPN client... 16 IPSec Client Configuration... 18 Apple OS X Configuration... 21 Android Configuration...
Deploy In-Memory Parallel Graph Analytics (PGX) to Oracle Java Cloud Service (JCS)
 Deploy In-Memory Parallel Graph Analytics (PGX) to Oracle Java Cloud Service (JCS) Overview This document provides detailed steps required to deploy PGX to Java Cloud Service Instance. This exercise is
Deploy In-Memory Parallel Graph Analytics (PGX) to Oracle Java Cloud Service (JCS) Overview This document provides detailed steps required to deploy PGX to Java Cloud Service Instance. This exercise is
Healthcare Database Connector
 Healthcare Database Connector Installation and Setup Guide Version: 3.1.1 Written by: Product Knowledge, R&D Date: May 2018 2008-2018 Hyland Software, Inc. and its affiliates. Table of Contents What is
Healthcare Database Connector Installation and Setup Guide Version: 3.1.1 Written by: Product Knowledge, R&D Date: May 2018 2008-2018 Hyland Software, Inc. and its affiliates. Table of Contents What is
Overview. Installation Overview CHAPTER
 CHAPTER 1 This chapter provides an overview of the Cisco IPICS server software installation. It also contains information about system requirements for the Cisco IPICS server software and the PMC application.
CHAPTER 1 This chapter provides an overview of the Cisco IPICS server software installation. It also contains information about system requirements for the Cisco IPICS server software and the PMC application.
Open XML Gateway User Guide. CORISECIO GmbH - Uhlandstr Darmstadt - Germany -
 Open XML Gateway User Guide Conventions Typographic representation: Screen text and KEYPAD Texts appearing on the screen, key pads like e.g. system messages, menu titles, - texts, or buttons are displayed
Open XML Gateway User Guide Conventions Typographic representation: Screen text and KEYPAD Texts appearing on the screen, key pads like e.g. system messages, menu titles, - texts, or buttons are displayed
Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS)
 Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
Perceptive SOAPBridge Connector
 Perceptive SOAPBridge Connector Installation and Setup Guide Version: 1.0.x Written by: Product Knowledge, R&D Date: June 2017 2016 Lexmark. All rights reserved. Lexmark is a trademark of Lexmark International,
Perceptive SOAPBridge Connector Installation and Setup Guide Version: 1.0.x Written by: Product Knowledge, R&D Date: June 2017 2016 Lexmark. All rights reserved. Lexmark is a trademark of Lexmark International,
IBM i Version 7.2. Security Digital Certificate Manager IBM
 IBM i Version 7.2 Security Digital Certificate Manager IBM IBM i Version 7.2 Security Digital Certificate Manager IBM Note Before using this information and the product it supports, read the information
IBM i Version 7.2 Security Digital Certificate Manager IBM IBM i Version 7.2 Security Digital Certificate Manager IBM Note Before using this information and the product it supports, read the information
Hitachi ID Systems Inc Identity Manager 8.2.6
 Systems Inc RSA SecurID Ready Implementation Guide Partner Information Last Modified: December 5, 2014 Product Information Partner Name Hitachi ID Systems Inc Web Site www.hitachi-id.com Product Name Identity
Systems Inc RSA SecurID Ready Implementation Guide Partner Information Last Modified: December 5, 2014 Product Information Partner Name Hitachi ID Systems Inc Web Site www.hitachi-id.com Product Name Identity
Managing AON Security
 CHAPTER 4 This chapter describes AON functions relating to security, authentication, and authorization. It includes the following topics. Managing Keystores, page 4-1 Configuring Security Properties, page
CHAPTER 4 This chapter describes AON functions relating to security, authentication, and authorization. It includes the following topics. Managing Keystores, page 4-1 Configuring Security Properties, page
About This Document 3. Overview 3. System Requirements 3. Installation & Setup 4
 About This Document 3 Overview 3 System Requirements 3 Installation & Setup 4 Step By Step Instructions 5 1. Login to Admin Console 6 2. Show Node Structure 7 3. Create SSO Node 8 4. Create SAML IdP 10
About This Document 3 Overview 3 System Requirements 3 Installation & Setup 4 Step By Step Instructions 5 1. Login to Admin Console 6 2. Show Node Structure 7 3. Create SSO Node 8 4. Create SAML IdP 10
HUB Web Service API. IPPC ephyto HUB v1.7. Public - FAO/IPPC
 IPPC ephyto HUB v1.7 Public - FAO/IPPC 04/01/2018 Table of Contents DOCUMENT PROFILE... 3 REVISION HISTORY... 3 DISTRIBUTION... 3 DOCUMENT ROADMAP... 3 1. INTRODUCTION... 4 1.1 Purpose... 4 1.2 Intended
IPPC ephyto HUB v1.7 Public - FAO/IPPC 04/01/2018 Table of Contents DOCUMENT PROFILE... 3 REVISION HISTORY... 3 DISTRIBUTION... 3 DOCUMENT ROADMAP... 3 1. INTRODUCTION... 4 1.1 Purpose... 4 1.2 Intended
Read Naturally SE Update Windows Network Installation Instructions
 Windows Network This document explains how to apply the Read Naturally Software Edition 2.0.3 update to existing installations of SE version 2.0, 2.0.1, or 2.0.2. First update the SE server software, and
Windows Network This document explains how to apply the Read Naturally Software Edition 2.0.3 update to existing installations of SE version 2.0, 2.0.1, or 2.0.2. First update the SE server software, and
SSO Authentication with ADFS SAML 2.0. Ephesoft Transact Documentation
 SSO Authentication with ADFS SAML 2.0 Ephesoft Transact Documentation 2017 Table of Contents Prerequisites... 1 Tools Used... 1 Setup... 1 Generating Server Certificates to Set Up SSL/TLS... 1 Creating
SSO Authentication with ADFS SAML 2.0 Ephesoft Transact Documentation 2017 Table of Contents Prerequisites... 1 Tools Used... 1 Setup... 1 Generating Server Certificates to Set Up SSL/TLS... 1 Creating
Quick Start Guide to Installing Your SSL-Explorer Server using the Linux RPM Installer
 Quick Start Guide to Installing Your SSL-Explorer Server using the Linux RPM Installer This article explains how to quickly set up a basic installation of SSL-Explorer using the RPM installer for Linux
Quick Start Guide to Installing Your SSL-Explorer Server using the Linux RPM Installer This article explains how to quickly set up a basic installation of SSL-Explorer using the RPM installer for Linux
ADFS Setup (SAML Authentication)
 ADFS Setup (SAML Authentication) Version 1.6 Corresponding Software Version Celonis 4.3 This document is copyright of the Celonis SE. Distribution or reproduction are only permitted by written approval
ADFS Setup (SAML Authentication) Version 1.6 Corresponding Software Version Celonis 4.3 This document is copyright of the Celonis SE. Distribution or reproduction are only permitted by written approval
Advanced Service Design. vrealize Automation 6.2
 vrealize Automation 6.2 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation, submit your feedback to
vrealize Automation 6.2 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation, submit your feedback to
Installing and Configuring VMware Identity Manager Connector (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.
 Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
Installing and Configuring VMware Identity Manager Connector 2018.8.1.0 (Windows) OCT 2018 VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on
How to Set Up External CA VPN Certificates
 To configure a client-to-site, or site-to-site VPN using s created by External CA, you must create the following VPN s for the VPN service to be able to authenticate Before you begin Use an external CA
To configure a client-to-site, or site-to-site VPN using s created by External CA, you must create the following VPN s for the VPN service to be able to authenticate Before you begin Use an external CA
Contents. SSL-Based Services: HTTPS and FTPS 2. Generating A Certificate 2. Creating A Self-Signed Certificate 3. Obtaining A Signed Certificate 4
 Contents SSL-Based Services: HTTPS and FTPS 2 Generating A Certificate 2 Creating A Self-Signed Certificate 3 Obtaining A Signed Certificate 4 Enabling Secure Services 5 A Note About Ports 5 Connecting
Contents SSL-Based Services: HTTPS and FTPS 2 Generating A Certificate 2 Creating A Self-Signed Certificate 3 Obtaining A Signed Certificate 4 Enabling Secure Services 5 A Note About Ports 5 Connecting
Using SSL to Secure Client/Server Connections
 Using SSL to Secure Client/Server Connections Using SSL to Secure Client/Server Connections, page 1 Using SSL to Secure Client/Server Connections Introduction This chapter contains information on creating
Using SSL to Secure Client/Server Connections Using SSL to Secure Client/Server Connections, page 1 Using SSL to Secure Client/Server Connections Introduction This chapter contains information on creating
Step-by-step installation guide for monitoring untrusted servers using Operations Manager
 Step-by-step installation guide for monitoring untrusted servers using Operations Manager Most of the time through Operations Manager, you may require to monitor servers and clients that are located outside
Step-by-step installation guide for monitoring untrusted servers using Operations Manager Most of the time through Operations Manager, you may require to monitor servers and clients that are located outside
Managing Users and Configuring Role-Based Access Control
 Managing s and Configuring Role-Based Access Control This section describes how to manage users in Prime Central, including defining users and passwords and configuring role-based access control (RBAC).
Managing s and Configuring Role-Based Access Control This section describes how to manage users in Prime Central, including defining users and passwords and configuring role-based access control (RBAC).
User guide NotifySCM Installer
 User guide NotifySCM Installer TABLE OF CONTENTS 1 Overview... 3 2 Office 365 Users synchronization... 3 3 Installation... 5 4 Starting the server... 17 2 P a g e 1 OVERVIEW This user guide provides instruction
User guide NotifySCM Installer TABLE OF CONTENTS 1 Overview... 3 2 Office 365 Users synchronization... 3 3 Installation... 5 4 Starting the server... 17 2 P a g e 1 OVERVIEW This user guide provides instruction
AirWatch Mobile Device Management
 RSA Ready Implementation Guide for 3rd Party PKI Applications Last Modified: November 26 th, 2014 Partner Information Product Information Partner Name Web Site Product Name Version & Platform Product Description
RSA Ready Implementation Guide for 3rd Party PKI Applications Last Modified: November 26 th, 2014 Partner Information Product Information Partner Name Web Site Product Name Version & Platform Product Description
OHF ATNA Audit Client. Architecture & API Documentation. Version seknoop[at]us[dot]ibm[dot]com Sarah Knoop
![OHF ATNA Audit Client. Architecture & API Documentation. Version seknoop[at]us[dot]ibm[dot]com Sarah Knoop OHF ATNA Audit Client. Architecture & API Documentation. Version seknoop[at]us[dot]ibm[dot]com Sarah Knoop](/thumbs/84/89169717.jpg) OHF ATNA Audit Client Architecture & API Documentation Version 0.0.2 seknoop[at]us[dot]ibm[dot]com Sarah Knoop Page 1 of 14 Contents 1. Introduction...3 2. Getting Started...4 2.1 Platform Requirements...4
OHF ATNA Audit Client Architecture & API Documentation Version 0.0.2 seknoop[at]us[dot]ibm[dot]com Sarah Knoop Page 1 of 14 Contents 1. Introduction...3 2. Getting Started...4 2.1 Platform Requirements...4
1Integrate for ArcGIS Installation Guide. Server Edition
 1Integrate for ArcGIS Installation Guide Server Edition Product version: v 2.1 Document version: v 1.9 Document date: 03/08/2018 Copyright 2018 1Spatial plc and its affiliates. All rights reserved. Other
1Integrate for ArcGIS Installation Guide Server Edition Product version: v 2.1 Document version: v 1.9 Document date: 03/08/2018 Copyright 2018 1Spatial plc and its affiliates. All rights reserved. Other
TIM TAM Integration. Planning to install the Tivoli Access Manager Combo Adapter
 TIM TAM Integration For TIM TAM Integration, TAM Combo Adapter is required. The installation and configuration details of TAM Combo Adapter is described below. Planning to install the Tivoli Access Manager
TIM TAM Integration For TIM TAM Integration, TAM Combo Adapter is required. The installation and configuration details of TAM Combo Adapter is described below. Planning to install the Tivoli Access Manager
3. Optionally, if you want to use the new Web SSO feature, complete the steps in Adding Web Single Sign-On Functionality.
 Webthority HOW TO Upgrade The steps required to upgrade depend on the version you are upgrading from: upgrading from 6.5 upgrading from 6.0. Upgrading from 6.5 To upgrade from 6.5 perform the following
Webthority HOW TO Upgrade The steps required to upgrade depend on the version you are upgrading from: upgrading from 6.5 upgrading from 6.0. Upgrading from 6.5 To upgrade from 6.5 perform the following
This document describes the configuration of Secure Sockets Layer (SSL) decryption on the FirePOWER Module using ASDM (On-Box Management).
 Contents Introduction Prerequisites Requirements Components Used Background Information Outbound SSL Decryption Inbound SSL Decryption Configuration for SSL Decryption Outbound SSL decryption (Decrypt
Contents Introduction Prerequisites Requirements Components Used Background Information Outbound SSL Decryption Inbound SSL Decryption Configuration for SSL Decryption Outbound SSL decryption (Decrypt
SETTING UP ORACLE ULTRA SEARCH FOR ORACLE PORTAL 10G (10.1.4)
 Oracle Application Server Portal Technical Note SETTING UP ORACLE ULTRA SEARCH FOR ORACLE PORTAL 10G (10.1.4) November 2005 INTRODUCTION This Technical Note describes how to setup up and configure Oracle
Oracle Application Server Portal Technical Note SETTING UP ORACLE ULTRA SEARCH FOR ORACLE PORTAL 10G (10.1.4) November 2005 INTRODUCTION This Technical Note describes how to setup up and configure Oracle
OpenAM Single Sign-On
 Single Sign-On Setup Task List, on page 1 Single Sign-On Setup Preparation, on page 3 Single Sign-On Setup and Management Tasks, on page 5 Single Sign-On Setup Task List The following figure provides the
Single Sign-On Setup Task List, on page 1 Single Sign-On Setup Preparation, on page 3 Single Sign-On Setup and Management Tasks, on page 5 Single Sign-On Setup Task List The following figure provides the
16-Dec-10. Consider the following method:
 Boaz Kantor Introduction to Computer Science IDC Herzliya Exception is a class. Java comes with many, we can write our own. The Exception objects, along with some Java-specific structures, allow us to
Boaz Kantor Introduction to Computer Science IDC Herzliya Exception is a class. Java comes with many, we can write our own. The Exception objects, along with some Java-specific structures, allow us to
User Inputs for Installation, Reinstallation, and Upgrade
 APPENDIXA User Inputs for Installation, Reinstallation, and Upgrade This appendix provides information on the user inputs during Service Monitor installation, reinstallation, and upgrade. This appendix
APPENDIXA User Inputs for Installation, Reinstallation, and Upgrade This appendix provides information on the user inputs during Service Monitor installation, reinstallation, and upgrade. This appendix
PROXY Pro RAS Installation Manual v10.1. December 2018
 PROXY Pro RAS Installation Manual v10.1 December 2018 Table of Contents 1. RAS Overview...3 2. PROXY Pro RAS Requirements...4 3. PROXY Pro RAS Installation...5 Installation Steps...6 PROXY Pro Web Console
PROXY Pro RAS Installation Manual v10.1 December 2018 Table of Contents 1. RAS Overview...3 2. PROXY Pro RAS Requirements...4 3. PROXY Pro RAS Installation...5 Installation Steps...6 PROXY Pro Web Console
Managing Administrative Security
 5 CHAPTER 5 Managing Administrative Security This chapter describes how to manage administrative security by using the secure administration feature. This chapter assumes that you are familiar with security
5 CHAPTER 5 Managing Administrative Security This chapter describes how to manage administrative security by using the secure administration feature. This chapter assumes that you are familiar with security
Workspace ONE UEM Certificate Authentication for Cisco IPSec VPN. VMware Workspace ONE UEM 1810
 Workspace ONE UEM Certificate Authentication for Cisco IPSec VPN VMware Workspace ONE UEM 1810 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Workspace ONE UEM Certificate Authentication for Cisco IPSec VPN VMware Workspace ONE UEM 1810 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
BEAAquaLogic. Service Bus. Upgrade Guide
 BEAAquaLogic Service Bus Upgrade Guide Version 2.5 Document Date: July 2006 Copyright Copyright 1995-2005 BEA Systems, Inc. All Rights Reserved. Restricted Rights Legend This software is protected by copyright,
BEAAquaLogic Service Bus Upgrade Guide Version 2.5 Document Date: July 2006 Copyright Copyright 1995-2005 BEA Systems, Inc. All Rights Reserved. Restricted Rights Legend This software is protected by copyright,
Integration Guide. SafeNet Authentication Client. Using SAC CBA for VMware Horizon 6 Client
 SafeNet Authentication Client Integration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information Document
SafeNet Authentication Client Integration Guide Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright 2013 SafeNet, Inc. All rights reserved. 1 Document Information Document
IBM Presentations: Implementing SSL Security in WebSphere Partner Gateway
 IBM Software Group IBM Presentations: Implementing SSL Security in WebSphere Partner Gateway Presenter: Max Terpolilli WPG L2 Support WebSphere Support Technical Exchange Agenda IBM Software Group Digital
IBM Software Group IBM Presentations: Implementing SSL Security in WebSphere Partner Gateway Presenter: Max Terpolilli WPG L2 Support WebSphere Support Technical Exchange Agenda IBM Software Group Digital
