Bare SOAP-UI for WS-Security
|
|
|
- Reginald Francis
- 6 years ago
- Views:
Transcription
1 Draft Draft Bare SOAP-UI for WS-Security Paul Glezen, IBM Abstract This document is a member of the Bare Series of WAS topics distributed in both stand-alone and in collection form. The latest renderings and source are available on GitHub at Table of Contents 1. Generating the Keystore Configure SOAP-UI Add Keystore to SOAP-UI Add WS-Security to SOAP-UI Invoke CC Provider with Signature Troubleshooting... 7 If you lock down your service provider too tightly, not even your testers can invoke it with SOAP-UI. This section explains how to configure SOAP-UI to invoke a web service that only accepts payloads with timestamps signed by certain parties. Of course, one of those parties needs to be the tester. 1. Generating the Keystore These steps describe how to create a tester key store for use in signing requests to the provider. There is no requirement that this be done on WAS. One could use the JDK keytool if desired. The WAS admin console is just easier. Since there is no requirement to manage this keystore as part of a cell, it is not created within the cell configuration and synchronized across nodes. The public certifiate associated with the tester's key is exported so that it can be included within the provider's trust store. 1. In the WAS admin console, navigate to Security SSL Certificate and key management Key stores and certificates. 2. Click the Add button. a. For Name, enter Tester. b. For Description, enter Key store used by testers, not by WAS. c. For Path, enter a fully qualified path name outside the cell configuration directory. The filename extension should be.jks. d. Enter a password for the key store. e. For Type, select JKS. f. Click OK. The result is a new empty key store named Tester. Rendered: September 30, Git Commit: 213c4c
2 3. For the Tester key store, click the Personal certificates link to create a new public/private key pair. 4. Click the Create button and select self-signed Certificate from the dropdown list. a. For Alias, enter tester1. b. For Common name, enter Acme Tester 1. c. For Validity period, enter a suitable validity period. d. For Organization, enter Acme. e. Enter any of the other fields you like and click OK. Tester1 is now in your list of personal certificates. 5. Extract the Tester1 public certificate. Extract vs Export The Personal Certificates list has two buttons that appear similar in meaning: Extract and Export. The Extract button refers to a certificate associated with the key. The result is a certificate file for use in importing into a trust store. The Export button refers to a public/private key pair. Its destination is either a new or existing key store. a. In the personal certificates list, check the box next to tester1 alias and click the Extract button. b. In the Certificate file name field, enter the fully qualified file name of the certificate file with a.cer extension. This will be the location from which it will be imported into the service provider's trust store. c. Click OK. 6. Import the tester1 certificate into the provider trust store. a. Navigate to the Signer certificates section of the CC Provider trust store. b. Click the Add button. c. The alias is not so important. It's good to enter something related to the certificate to be imported. The tester1 alias used for creating the certificate is a good choice. d. Enter the fully qualified file name of the tester certificate you extracted in the previous step. e. Click OK. f. Save the configuration. The provider trust store should look similar to the screen shot in Figure 1. Rendered: September 30, Git Commit: 213c4c
3 Figure 1. CC Provider Trust Store with Tester Certificate The root entry is the WAS cell root that is created automatically for each new key store. It does not play a role here. The ccconsumer certificate belongs to the consumer application and tester1 is the tester certificate that was just imported. It will allow the service provider to accept requests signed by this tester. The next section will explain how to configure the tester's SOAP-UI installation to sign requests with the new key. 2. Configure SOAP-UI In SOAP-UI we start with a SOAP project that invokes a service provider. The SOAP-UI has no WS-Security configured. They keystore and its passwords from the previous step are readily available Add Keystore to SOAP-UI 1. Double-click on your SOAP project to bring up the project configuration panel. Figure 2. Double-click CC SOAP-UI Project 2. Select the WS-Security Configurations tab. 3. Select the Keystore tab. 4. Select the + button to add a new key store. Rendered: September 30, Git Commit: 213c4c
4 Figure 3. Project Keystore Configuration 5. Select the tester key store (with the.jks extension). 6. Enter the key store password. (There shouldn't be an alias password since we didn't password-protect the key.) This completes the configuration of the key store within SOAP-UI. The key store panel should look like Figure 4. Figure 4. Project Keystore Configuration 2.2. Add WS-Security to SOAP-UI This section continues from configuration panel of the previous section. 1. Select the Outgoing WS-Security Configurations sub-tab to the left of the Keystores sub-tab from the previous section. 2. Click the + button on the upper-left to add a new outgoing WS-Security configuration. 3. For the name of the configuration, enter Add+Sign Timestamp. 4. In the lower panel, click the + button to add a new WSS entry. Rendered: September 30, Git Commit: 213c4c
5 Figure 5. Add WS-Sec Timestamp a. For the first entry type, select Timestamp. b. Set Time to Live to a liberal value like 120 (seconds) to avoid any problems with clock skew between the test machine and the service provider. Uncheck the box for Millisecond precision. Figure 6. Configure WS-Sec Timestamp 5. Click the + again to add another WSS entry element. 6. Select Signature for the entry type. 7. Add the following settings to the signature configuration panel. a. For Keystore, select tester.jks. This entry comes from the SOAP-UI key store configuration in the previous section. b. For Alias, chose tester1. c. For Password, enter the key store password. d. For the next five fields choose the options shown in Figure 7. e. Click the + button in the Parts section. This creates a new row in the table. i. In the Name column, enter Timestamp. ii. iii. In the Namespace column, enter In the Content column, select Content. Rendered: September 30, Git Commit: 213c4c
6 Figure 7. Configure WS-Sec Signature 2.3. Invoke CC Provider with Signature This is the easy part. Start with any sample request payload (without the WS-Security header). Right-click in the request payload editor and select Outgoing WSS Apply "Add+Sign Timestamp" as shown in Figure 8. Figure 8. Add WS-Sec Signature This will slap the WS-Security header right into the payload. Caution Do not alter the WS-Security header after generating the timestamp and signature (such as reformating it). In most cases this will invalidate the signature. After generating the timestamp and signature, be sure to invoke the CC provider within 120 seconds (before the timestamp expires). After the timestamp expires, simply generate a new WS-Security header using the same menu option shown in Figure 8. It will replace the existing WS-Security header with a new one automatically. There is no Rendered: September 30, Git Commit: 213c4c
7 need to manually delete the old one. If you wish to simply remove the old WS-Security header without adding a new one, right-click into the request editor and select Outgoing WSS Remove all outgoing wss Troubleshooting Here are some troubleshooting tips for when things go wrong Logs Check the logs on both sides. For WAS, there is always the SystemOut.log file. For SOAP-UI there the SoapUI log and error log tabs at the bottom of the window as shown in Figure 9. Figure 9. SOAP-UI Logs Format Request As mentioned above, formatting the request payload corrupts the signature. But if you've already invoked the request (for better or worse) and you wish to view the security header, go ahead and reformat using by right-clicking in the request panel and selecting Format XML. This will allow you to see the header elements more clearly for troubleshooting. Rendered: September 30, Git Commit: 213c4c
Bare Timestamp Signatures with WS-Security
 Bare Timestamp Signatures with WS-Security Paul Glezen, IBM Abstract This document is a member of the Bare Series of WAS topics distributed in both stand-alone and in collection form. The latest renderings
Bare Timestamp Signatures with WS-Security Paul Glezen, IBM Abstract This document is a member of the Bare Series of WAS topics distributed in both stand-alone and in collection form. The latest renderings
HPE Enterprise Integration Module for SAP Solution Manager 7.1
 HPE Enterprise Integration Module for SAP Solution Manager 7.1 Software Version: 12.55 User Guide Document Release Date: August 2017 Software Release Date: August 2017 HPE Enterprise Integration Module
HPE Enterprise Integration Module for SAP Solution Manager 7.1 Software Version: 12.55 User Guide Document Release Date: August 2017 Software Release Date: August 2017 HPE Enterprise Integration Module
Security configuration of the mail server IBM
 Security configuration of the mail server IBM ii Security configuration of the mail server Contents Security configuration of the mail server 1 Configuration of the SSL client to trust the SMTP server
Security configuration of the mail server IBM ii Security configuration of the mail server Contents Security configuration of the mail server 1 Configuration of the SSL client to trust the SMTP server
Using Inventory Manager
 14 CHAPTER This chapter explains how Inventory Manager provides a method of managing mass changes to inventory and service model data in the Prime Provisioning provisioning process. In this process, Inventory
14 CHAPTER This chapter explains how Inventory Manager provides a method of managing mass changes to inventory and service model data in the Prime Provisioning provisioning process. In this process, Inventory
IBM Lotus Sametime Media Manager Cluster Deployment Walk-through Part VI- Bandwidth Manager IBM Corporation
 IBM Lotus Sametime 8.5.2 Media Manager Cluster Deployment Walk-through Part VI- Bandwidth Manager Prerequisites for this part of the walk-through We've completed parts I, II, II, IV, and V Lotus Domino
IBM Lotus Sametime 8.5.2 Media Manager Cluster Deployment Walk-through Part VI- Bandwidth Manager Prerequisites for this part of the walk-through We've completed parts I, II, II, IV, and V Lotus Domino
Newforma Contact Directory Quick Reference Guide
 Newforma Contact Directory Quick Reference Guide This topic provides a reference for the Newforma Contact Directory. Purpose The Newforma Contact Directory gives users access to the central list of companies
Newforma Contact Directory Quick Reference Guide This topic provides a reference for the Newforma Contact Directory. Purpose The Newforma Contact Directory gives users access to the central list of companies
IBM Workplace TM Collaboration Services
 IBM Workplace TM Collaboration Services Version 2.5 Mobile Client Guide G210-1962-00 Terms of Use Disclaimer THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS PROVIDED FOR INFORMATIONAL PURPOSES ONLY.
IBM Workplace TM Collaboration Services Version 2.5 Mobile Client Guide G210-1962-00 Terms of Use Disclaimer THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS PROVIDED FOR INFORMATIONAL PURPOSES ONLY.
edocs Home > BEA AquaLogic Service Bus 3.0 Documentation > Accessing ALDSP Data Services Through ALSB
 Accessing ALDSP 3.0 Data Services Through ALSB 3.0 edocs Home > BEA AquaLogic Service Bus 3.0 Documentation > Accessing ALDSP Data Services Through ALSB Introduction AquaLogic Data Services Platform can
Accessing ALDSP 3.0 Data Services Through ALSB 3.0 edocs Home > BEA AquaLogic Service Bus 3.0 Documentation > Accessing ALDSP Data Services Through ALSB Introduction AquaLogic Data Services Platform can
TIBCO ActiveMatrix Policy Director Administration
 TIBCO ActiveMatrix Policy Director Administration Software Release 2.0.0 November 2014 Document Updated: January 2015 Two-Second Advantage 2 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES
TIBCO ActiveMatrix Policy Director Administration Software Release 2.0.0 November 2014 Document Updated: January 2015 Two-Second Advantage 2 Important Information SOME TIBCO SOFTWARE EMBEDS OR BUNDLES
VIRTUAL GPU LICENSE SERVER VERSION AND 5.1.0
 VIRTUAL GPU LICENSE SERVER VERSION 2018.06 AND 5.1.0 DU-07754-001 _v6.0 through 6.2 July 2018 User Guide TABLE OF CONTENTS Chapter 1. Introduction to the NVIDIA vgpu Software License Server... 1 1.1. Overview
VIRTUAL GPU LICENSE SERVER VERSION 2018.06 AND 5.1.0 DU-07754-001 _v6.0 through 6.2 July 2018 User Guide TABLE OF CONTENTS Chapter 1. Introduction to the NVIDIA vgpu Software License Server... 1 1.1. Overview
INSTALLING ADOBE LIVECYCLE WORKBENCH 11
 INSTALLING ADOBE LIVECYCLE WORKBENCH 11 Legal notices Legal notices For legal notices, see http://help.adobe.com/en_us/legalnotices/index.html. iii Contents Chapter 1: About This Document 1.1 Who should
INSTALLING ADOBE LIVECYCLE WORKBENCH 11 Legal notices Legal notices For legal notices, see http://help.adobe.com/en_us/legalnotices/index.html. iii Contents Chapter 1: About This Document 1.1 Who should
Avaya Event Processor Release 2.2 Operations, Administration, and Maintenance Interface
 Avaya Event Processor Release 2.2 Operations, Administration, and Maintenance Interface Document ID: 13-603114 Release 2.2 July 2008 Issue No.1 2008 Avaya Inc. All Rights Reserved. Notice While reasonable
Avaya Event Processor Release 2.2 Operations, Administration, and Maintenance Interface Document ID: 13-603114 Release 2.2 July 2008 Issue No.1 2008 Avaya Inc. All Rights Reserved. Notice While reasonable
eroaming platform Secure Connection Guide
 eroaming platform Secure Connection Guide Contents 1. Revisions overview... 3 2. Abbrevations... 4 3. Preconditions... 5 3.1. OpenSSL... 5 3.2. Requirements for your PKCS10 CSR... 5 3.3. Java Keytool...
eroaming platform Secure Connection Guide Contents 1. Revisions overview... 3 2. Abbrevations... 4 3. Preconditions... 5 3.1. OpenSSL... 5 3.2. Requirements for your PKCS10 CSR... 5 3.3. Java Keytool...
Configure the IM and Presence Service to Integrate with the Microsoft Exchange Server
 Configure the IM and Presence Service to Integrate with the Microsoft Exchange Server Configure a Presence Gateway for Microsoft Exchange Integration, page 1 SAN and Wildcard Certificate Support, page
Configure the IM and Presence Service to Integrate with the Microsoft Exchange Server Configure a Presence Gateway for Microsoft Exchange Integration, page 1 SAN and Wildcard Certificate Support, page
Managing Users and Configuring Role-Based Access Control
 Managing s and Configuring Role-Based Access Control This section describes how to manage users in Prime Central, including defining users and passwords and configuring role-based access control (RBAC).
Managing s and Configuring Role-Based Access Control This section describes how to manage users in Prime Central, including defining users and passwords and configuring role-based access control (RBAC).
How to Configure S/MIME for WorxMail
 How to Configure S/MIME for WorxMail Windows Phone 8.1 This article describes how to configure S/MIME (Secure/Multipurpose Internet Mail Extensions) for WorxMail Windows Phone 8.1. Note: This feature works
How to Configure S/MIME for WorxMail Windows Phone 8.1 This article describes how to configure S/MIME (Secure/Multipurpose Internet Mail Extensions) for WorxMail Windows Phone 8.1. Note: This feature works
Enterprise Integration Module for SAP Solution Manager 7.2
 Enterprise Integration Module for SAP Solution Manager 7.2 Software Version: 12.53-12.55 User Guide Go to HELP CENTER ONLINE http://admhelp.microfocus.com/alm Document Release Date: May 2018 Software Release
Enterprise Integration Module for SAP Solution Manager 7.2 Software Version: 12.53-12.55 User Guide Go to HELP CENTER ONLINE http://admhelp.microfocus.com/alm Document Release Date: May 2018 Software Release
Configuring Remote Access using the RDS Gateway
 Configuring Remote Access using the RDS Gateway Author: AC, SNE Contents Introduction... 3 Pre-requisites... 3 Supported Operating Systems... 3 Installing the I.T. Services Certificate Authority Root Certificate...
Configuring Remote Access using the RDS Gateway Author: AC, SNE Contents Introduction... 3 Pre-requisites... 3 Supported Operating Systems... 3 Installing the I.T. Services Certificate Authority Root Certificate...
Procurement Contract Overview
 Procurement Contract Overview Understanding Contract Versioning: Core-CT allows for the creation of new versions to existing contracts. Versioning is only used when the expiration date of a current contract
Procurement Contract Overview Understanding Contract Versioning: Core-CT allows for the creation of new versions to existing contracts. Versioning is only used when the expiration date of a current contract
The Domino Certificate Authority Key Rollover Process. Author: Graham Farrell IBM Domino server Support Engineer
 The Domino Certificate Authority Key Rollover Process Author: Graham Farrell IBM Domino server Support Engineer 1 Introduction.... 3 Terms and Abbreviations... 4 The Domino Certificate Authority and The
The Domino Certificate Authority Key Rollover Process Author: Graham Farrell IBM Domino server Support Engineer 1 Introduction.... 3 Terms and Abbreviations... 4 The Domino Certificate Authority and The
Cisco TelePresence Management Suite Extension for IBM Lotus Notes
 Cisco TelePresence Management Suite Extension for IBM Lotus Notes Installation and Getting Started Guide Software version 11.3.2 D13561.19 April 2013 Contents Introduction 4 How to use this document 4
Cisco TelePresence Management Suite Extension for IBM Lotus Notes Installation and Getting Started Guide Software version 11.3.2 D13561.19 April 2013 Contents Introduction 4 How to use this document 4
vcloud Director Administrator's Guide vcloud Director 8.10
 vcloud Director Administrator's Guide vcloud Director 8.10 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation,
vcloud Director Administrator's Guide vcloud Director 8.10 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ If you have comments about this documentation,
User Management in Resource Manager
 CHAPTER 8 This section describes how to manage user profiles. Topics in this section include: Overview of User Management, page 8-1 Using User Management, page 8-1 Overview of User Management In Resource
CHAPTER 8 This section describes how to manage user profiles. Topics in this section include: Overview of User Management, page 8-1 Using User Management, page 8-1 Overview of User Management In Resource
Perceptive TransForm eauthorize Integration
 Perceptive TransForm eauthorize Integration Setup Guide Version: 8.x Written by: Product Knowledge, R&D Date: May 2018 2008-2018 Hyland Software, Inc. and its affiliates. Table of Contents About Perceptive
Perceptive TransForm eauthorize Integration Setup Guide Version: 8.x Written by: Product Knowledge, R&D Date: May 2018 2008-2018 Hyland Software, Inc. and its affiliates. Table of Contents About Perceptive
Synchronization of Services between the IBM WebSphere Services Registry & Repository and SAP s Services Registry
 Synchronization of Services between the IBM WebSphere Services Registry & Repository and SAP s Services Registry Applies to: This document describes how to use the WebSphere Services Registry & Repository
Synchronization of Services between the IBM WebSphere Services Registry & Repository and SAP s Services Registry Applies to: This document describes how to use the WebSphere Services Registry & Repository
Oracle Cloud Using the Trello Adapter. Release 17.3
 Oracle Cloud Using the Trello Adapter Release 17.3 E84579-03 September 2017 Oracle Cloud Using the Trello Adapter, Release 17.3 E84579-03 Copyright 2016, 2017, Oracle and/or its affiliates. All rights
Oracle Cloud Using the Trello Adapter Release 17.3 E84579-03 September 2017 Oracle Cloud Using the Trello Adapter, Release 17.3 E84579-03 Copyright 2016, 2017, Oracle and/or its affiliates. All rights
RSA Identity Governance and Lifecycle Data Sheet for IBM Tivoli Directory Server Connector
 RSA Identity Governance and Lifecycle Data Sheet for IBM Tivoli Directory Server Connector Version 1.1 March 2017 Contents PURPOSE... 4 SUPPO RTED SOFTWARE... 4 PREREQUISITES... 4 CONFIGURATION... 6 General...
RSA Identity Governance and Lifecycle Data Sheet for IBM Tivoli Directory Server Connector Version 1.1 March 2017 Contents PURPOSE... 4 SUPPO RTED SOFTWARE... 4 PREREQUISITES... 4 CONFIGURATION... 6 General...
Lookup Roles Application Programming Interface (API) Version Software User s Manual (SUM)
 Lookup Roles Application Programming Interface (API) Version 5.11 Software User s Manual (SUM) Document Version 5.11 June 29, 2014 Prepared by: CACI 50 N Laura Street Jacksonville FL 32202 Prepared for:
Lookup Roles Application Programming Interface (API) Version 5.11 Software User s Manual (SUM) Document Version 5.11 June 29, 2014 Prepared by: CACI 50 N Laura Street Jacksonville FL 32202 Prepared for:
Frequently Asked Questions: SmartForms and Reader DC
 Frequently Asked Questions: SmartForms and Reader DC Initial Check Browsers - Google Chrome - Other browsers Form functions - List of additional buttons and their function Field functions - Choosing a
Frequently Asked Questions: SmartForms and Reader DC Initial Check Browsers - Google Chrome - Other browsers Form functions - List of additional buttons and their function Field functions - Choosing a
HP Enterprise Integration Module for SAP Solution Manager
 HP Enterprise Integration Module for SAP Solution Manager Software Version: 12.01 User Guide Document Release Date: March 2015 Software Release Date: March 2015 Legal Notices Warranty The only warranties
HP Enterprise Integration Module for SAP Solution Manager Software Version: 12.01 User Guide Document Release Date: March 2015 Software Release Date: March 2015 Legal Notices Warranty The only warranties
Exostar LDAP Proxy/Secure Setup Guide September 2017
 Exostar LDAP Proxy/Secure Email Setup Guide September 2017 Copyright 2017 Exostar, LLC All rights reserved. 1 Table of Contents Email Encryption Set-up Outlook 2003... 4 Digitally Signing an Email... 4
Exostar LDAP Proxy/Secure Email Setup Guide September 2017 Copyright 2017 Exostar, LLC All rights reserved. 1 Table of Contents Email Encryption Set-up Outlook 2003... 4 Digitally Signing an Email... 4
Clearspan OpEasy Basic Provisioning Guide NOVEMBER Release
 Clearspan OpEasy Basic Provisioning Guide NOVEMBER 2016 Release 4.6 2827-012 NOTICE The information contained in this document is believed to be accurate in all respects but is not warranted by Mitel Communications,
Clearspan OpEasy Basic Provisioning Guide NOVEMBER 2016 Release 4.6 2827-012 NOTICE The information contained in this document is believed to be accurate in all respects but is not warranted by Mitel Communications,
Building Block Installation - Admins
 Building Block Installation - Admins Overview To use your Blackboard Server with Panopto, you first need to install the Panopto Building Block on your Blackboard server. You then need to add Blackboard
Building Block Installation - Admins Overview To use your Blackboard Server with Panopto, you first need to install the Panopto Building Block on your Blackboard server. You then need to add Blackboard
IBM Security Identity Manager Version Administration Topics
 IBM Security Identity Manager Version 6.0.0.5 Administration Topics IBM Security Identity Manager Version 6.0.0.5 Administration Topics ii IBM Security Identity Manager Version 6.0.0.5: Administration
IBM Security Identity Manager Version 6.0.0.5 Administration Topics IBM Security Identity Manager Version 6.0.0.5 Administration Topics ii IBM Security Identity Manager Version 6.0.0.5: Administration
Amazon WorkMail. User Guide Version 1.0
 Amazon WorkMail User Guide Amazon WorkMail: User Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection
Amazon WorkMail User Guide Amazon WorkMail: User Guide Copyright 2017 Amazon Web Services, Inc. and/or its affiliates. All rights reserved. Amazon's trademarks and trade dress may not be used in connection
Web Service Integration
 SOAP Service, page 1 Rest Service, page 2 SOAP Service Web Services Element Web services are a common way for any kind of application to communicate with externally hosted servers to retrieve information
SOAP Service, page 1 Rest Service, page 2 SOAP Service Web Services Element Web services are a common way for any kind of application to communicate with externally hosted servers to retrieve information
Server software page. Certificate Signing Request (CSR) Generation. Software
 Server software page Certificate Signing Request (CSR) Generation Software Apache (mod_ssl and OpenSSL)... 2 cpanel and WHM... 3 Microsoft Exchange 2007... 8 Microsoft Exchange 2010... 9 F5 BigIP... 13
Server software page Certificate Signing Request (CSR) Generation Software Apache (mod_ssl and OpenSSL)... 2 cpanel and WHM... 3 Microsoft Exchange 2007... 8 Microsoft Exchange 2010... 9 F5 BigIP... 13
Securing U2 Soap Server
 Securing U2 Soap Server Introduction To enable SSL on the Client(Consumer-to-U2SS side), we need a U2 soap server Certificate. There are three possible methods to obtain the Server Certificate: 1. Use
Securing U2 Soap Server Introduction To enable SSL on the Client(Consumer-to-U2SS side), we need a U2 soap server Certificate. There are three possible methods to obtain the Server Certificate: 1. Use
Agile Sugar to Google Apps Synchronizer User s Guide. v1.0.25
 Agile Sugar to Google Apps Synchronizer User s Guide v1.0.25 GrinMark Limited, 2006-2017 http://www.grinmark.com Contents Contents 1 Overview 2 1.1 Terminology..................................... 2 1.2
Agile Sugar to Google Apps Synchronizer User s Guide v1.0.25 GrinMark Limited, 2006-2017 http://www.grinmark.com Contents Contents 1 Overview 2 1.1 Terminology..................................... 2 1.2
DOCUMENT DESCRIPTION...
 Contents 1 DOCUMENT DESCRIPTION... 1 1.1 OVERVIEW... 1 1.2 GLOSSARY... 1 1.3 PREREQUISITES... 3 2 CONFIGURATION... 4 2.1 CREATE WEBLOGIC DOMAIN... 4 2.2 CONFIGURE WEBLOGIC MANAGED DOMAIN... 12 2.3 INSTALLATION
Contents 1 DOCUMENT DESCRIPTION... 1 1.1 OVERVIEW... 1 1.2 GLOSSARY... 1 1.3 PREREQUISITES... 3 2 CONFIGURATION... 4 2.1 CREATE WEBLOGIC DOMAIN... 4 2.2 CONFIGURE WEBLOGIC MANAGED DOMAIN... 12 2.3 INSTALLATION
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Certificate Renewal on Cisco Identity Services Engine Configuration Guide
 Certificate Renewal on Cisco Identity Services Engine Configuration Guide Document ID: 116977 Contributed by Roger Nobel, Cisco TAC Engineer. Jun 26, 2015 Contents Introduction Prerequisites Requirements
Certificate Renewal on Cisco Identity Services Engine Configuration Guide Document ID: 116977 Contributed by Roger Nobel, Cisco TAC Engineer. Jun 26, 2015 Contents Introduction Prerequisites Requirements
From time to time Google changes the way it does things, and old tutorials may not apply to some new procedures.
 From time to time Google changes the way it does things, and old tutorials may not apply to some new procedures. This is another tutorial which, in about 6 months, will probably be irrelevant. But until
From time to time Google changes the way it does things, and old tutorials may not apply to some new procedures. This is another tutorial which, in about 6 months, will probably be irrelevant. But until
IBM Security Identity Governance and Intelligence. SDI-based IBM Security Privileged Identity Manager adapter Installation and Configuration Guide IBM
 IBM Security Identity Governance and Intelligence SDI-based IBM Security Privileged Identity Manager adapter Installation and Configuration Guide IBM IBM Security Identity Governance and Intelligence
IBM Security Identity Governance and Intelligence SDI-based IBM Security Privileged Identity Manager adapter Installation and Configuration Guide IBM IBM Security Identity Governance and Intelligence
User Migration Tool. User Migration Tool Prerequisites
 Prerequisites, page 1 Features, page 2 Migration Scenarios, page 2 Internationalization (I18n) and Localization (L10n) Considerations, page 3 Security Considerations, page 3 User Migration Steps, page
Prerequisites, page 1 Features, page 2 Migration Scenarios, page 2 Internationalization (I18n) and Localization (L10n) Considerations, page 3 Security Considerations, page 3 User Migration Steps, page
CA SiteMinder Web Services Security
 CA SiteMinder Web Services Security Policy Configuration Guide 12.52 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation
CA SiteMinder Web Services Security Policy Configuration Guide 12.52 This Documentation, which includes embedded help systems and electronically distributed materials, (hereinafter referred to as the Documentation
TIM TAM Integration. Planning to install the Tivoli Access Manager Combo Adapter
 TIM TAM Integration For TIM TAM Integration, TAM Combo Adapter is required. The installation and configuration details of TAM Combo Adapter is described below. Planning to install the Tivoli Access Manager
TIM TAM Integration For TIM TAM Integration, TAM Combo Adapter is required. The installation and configuration details of TAM Combo Adapter is described below. Planning to install the Tivoli Access Manager
Funambol Exchange Connector Installation and Configuration Guide
 Funambol Exchange Connector Installation and Configuration Guide Last modified: July 22, 2009 Table of Contents 1. Introduction...3 1.1. Prerequisites...3 1.2. Related documents...3 2. Funambol Exchange
Funambol Exchange Connector Installation and Configuration Guide Last modified: July 22, 2009 Table of Contents 1. Introduction...3 1.1. Prerequisites...3 1.2. Related documents...3 2. Funambol Exchange
Contents Overview... 5 Downloading Primavera Gateway... 5 Primavera Gateway On-Premises Installation Prerequisites... 6
 Gateway Installation and Configuration Guide for On-Premises Version 17 September 2017 Contents Overview... 5 Downloading Primavera Gateway... 5 Primavera Gateway On-Premises Installation Prerequisites...
Gateway Installation and Configuration Guide for On-Premises Version 17 September 2017 Contents Overview... 5 Downloading Primavera Gateway... 5 Primavera Gateway On-Premises Installation Prerequisites...
Managing AON Security
 CHAPTER 4 This chapter describes AON functions relating to security, authentication, and authorization. It includes the following topics. Managing Keystores, page 4-1 Configuring Security Properties, page
CHAPTER 4 This chapter describes AON functions relating to security, authentication, and authorization. It includes the following topics. Managing Keystores, page 4-1 Configuring Security Properties, page
Configuring SAML-based Single Sign-on for Informatica Web Applications
 Configuring SAML-based Single Sign-on for Informatica Web Applications Copyright Informatica LLC 2017. Informatica LLC. Informatica, the Informatica logo, Informatica Big Data Management, and Informatica
Configuring SAML-based Single Sign-on for Informatica Web Applications Copyright Informatica LLC 2017. Informatica LLC. Informatica, the Informatica logo, Informatica Big Data Management, and Informatica
Microsoft ISA 2006 Integration. Microsoft Internet Security and Acceleration Server (ISA) Integration Notes Introduction
 Microsoft ISA 2006 Integration Contents 1 Microsoft Internet Security and Acceleration Server (ISA) Integration Notes 2 Introduction 3 Prerequisites 3.1 ISA 2006 Filter 3.2 TMG Filter 4 Baseline 5 Architecture
Microsoft ISA 2006 Integration Contents 1 Microsoft Internet Security and Acceleration Server (ISA) Integration Notes 2 Introduction 3 Prerequisites 3.1 ISA 2006 Filter 3.2 TMG Filter 4 Baseline 5 Architecture
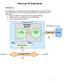
Datapower is both a security appliance & can provide a firewall mechanism to get into Systems of Record
 1 2 3 Datapower is both a security appliance & can provide a firewall mechanism to get into Systems of Record 5 White boxes show the access points for different kinds of security. That s what we will
1 2 3 Datapower is both a security appliance & can provide a firewall mechanism to get into Systems of Record 5 White boxes show the access points for different kinds of security. That s what we will
NetProfiler Web Based Functions Document Version 1.03
 NetProfiler Web Based Functions Document Version 1.03 When you purchase NetProfiler an information sheet is included for you to fill out. This gives X-Rite the information needed to create an organization,
NetProfiler Web Based Functions Document Version 1.03 When you purchase NetProfiler an information sheet is included for you to fill out. This gives X-Rite the information needed to create an organization,
ROC Site Instructions for using Medtronic CODE STAT software
 ROC Site Instructions for using Medtronic CODE STAT software All ECG files that are uploaded to ROC cases must have all patient identifiers removed. The following are instructions for configuring and using
ROC Site Instructions for using Medtronic CODE STAT software All ECG files that are uploaded to ROC cases must have all patient identifiers removed. The following are instructions for configuring and using
Monitoring WAAS Using XML API
 CHAPTER 4 This chapter describes how to use the WAAS API to monitor your WAAS devices and how to use soapui with the WAAS API interface. This chapter contains the following sections: Information About
CHAPTER 4 This chapter describes how to use the WAAS API to monitor your WAAS devices and how to use soapui with the WAAS API interface. This chapter contains the following sections: Information About
Enabling Microsoft Outlook Calendar Notifications for Meetings Scheduled from the Cisco Unified MeetingPlace End-User Web Interface
 Enabling Microsoft Outlook Calendar Notifications for Meetings Scheduled from the Cisco Unified MeetingPlace End-User Web Interface Release 7.1 Revised: March 5, 2013 1:53 pm This document describes the
Enabling Microsoft Outlook Calendar Notifications for Meetings Scheduled from the Cisco Unified MeetingPlace End-User Web Interface Release 7.1 Revised: March 5, 2013 1:53 pm This document describes the
VMware AirWatch Integration with RSA PKI Guide
 VMware AirWatch Integration with RSA PKI Guide For VMware AirWatch Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com. This product
VMware AirWatch Integration with RSA PKI Guide For VMware AirWatch Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com. This product
Selectica Contract Lifecycle Management. Release Notes. Selectica CLM Release 6.1. January 2014 v3.0
 Selectica Contract Lifecycle Management Release Notes Selectica CLM Release 6.1 January 2014 v3.0 Selectica CLM R.6.1 Release Notes Introduction... 3 Notable Changes... Error! Bookmark not defined. Certification
Selectica Contract Lifecycle Management Release Notes Selectica CLM Release 6.1 January 2014 v3.0 Selectica CLM R.6.1 Release Notes Introduction... 3 Notable Changes... Error! Bookmark not defined. Certification
BUILD AND DEPLOY SOA PROJECTS FROM DEVELOPER CLOUD SERVICE TO ORACLE SOA CLOUD SERVICE
 BUILD AND DEPLOY SOA PROJECTS FROM DEVELOPER CLOUD SERVICE TO ORACLE SOA CLOUD SERVICE Ashwini Sharma 1 CONTENTS 1. Introduction... 2 2 Prerequisites... 2 3 Patch the SOA Server Installation... 2 4. Use
BUILD AND DEPLOY SOA PROJECTS FROM DEVELOPER CLOUD SERVICE TO ORACLE SOA CLOUD SERVICE Ashwini Sharma 1 CONTENTS 1. Introduction... 2 2 Prerequisites... 2 3 Patch the SOA Server Installation... 2 4. Use
RSA Identity Governance and Lifecycle Generic SOAP Web Service Connector Application Guide. Generic SOAP Web Service Connector Application Guide
 Generic SOAP Web Service Connector Application Guide Version 1.3 Nov 2017 1 Contents Revision History... 4 Preface... 5 Audience... 5 In This Guide... 5 Configuring SSL client certificate based authentication...
Generic SOAP Web Service Connector Application Guide Version 1.3 Nov 2017 1 Contents Revision History... 4 Preface... 5 Audience... 5 In This Guide... 5 Configuring SSL client certificate based authentication...
Software User's Manual (UM)
 Software User's Manual (UM) The Log Angeles Community Garden Inventory and Locator Team 13 Ardalan Yousefi Cole Cecil Jeff Tonkovich Shi-Xuan Zeng (Gary) Project Manager Integrated Independent Verification
Software User's Manual (UM) The Log Angeles Community Garden Inventory and Locator Team 13 Ardalan Yousefi Cole Cecil Jeff Tonkovich Shi-Xuan Zeng (Gary) Project Manager Integrated Independent Verification
Configuring SSL CHAPTER
 7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
Office365 End User Training & Self-Service Migration Manual Simplified
 Office365 End User Training & Self-Service Migration Manual Simplified Version 1.0 University Systems and Security 5/25/2016 1 P a g e Table of Contents 2 P a g e Table of Contents Introduction to Office365...
Office365 End User Training & Self-Service Migration Manual Simplified Version 1.0 University Systems and Security 5/25/2016 1 P a g e Table of Contents 2 P a g e Table of Contents Introduction to Office365...
IBM Security Access Manager Version January Federation Administration topics IBM
 IBM Security Access Manager Version 9.0.2.1 January 2017 Federation Administration topics IBM IBM Security Access Manager Version 9.0.2.1 January 2017 Federation Administration topics IBM ii IBM Security
IBM Security Access Manager Version 9.0.2.1 January 2017 Federation Administration topics IBM IBM Security Access Manager Version 9.0.2.1 January 2017 Federation Administration topics IBM ii IBM Security
IoT Gateway PTC Inc. All Rights Reserved.
 2017 PTC Inc. All Rights Reserved. 2 Table of Contents IoT Gateway 1 Table of Contents 2 IoT Gateway 6 Overview 6 Architectural Summary 6 External Dependencies 8 General Operation 9 Configure the Gateway
2017 PTC Inc. All Rights Reserved. 2 Table of Contents IoT Gateway 1 Table of Contents 2 IoT Gateway 6 Overview 6 Architectural Summary 6 External Dependencies 8 General Operation 9 Configure the Gateway
Oracle Fusion Middleware
 Oracle Fusion Middleware Interoperability Guide for Oracle Web Services Manager 11g Release 1 (11.1.1) E16098-01 October 2009 This document describes how to implement the most common Oracle WSM interoperability
Oracle Fusion Middleware Interoperability Guide for Oracle Web Services Manager 11g Release 1 (11.1.1) E16098-01 October 2009 This document describes how to implement the most common Oracle WSM interoperability
BMC FootPrints 12 Integration with Remote Support
 BMC FootPrints 12 Integration with Remote Support 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks are
BMC FootPrints 12 Integration with Remote Support 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks are
ACM INTERNATIONAL COLLEGIATE PROGRAMMING CONTEST. California State University, Sacramento s. PC 2 Version 9.6. Judge s Guide
 ACM INTERNATIONAL COLLEGIATE PROGRAMMING CONTEST California State University, Sacramento s PC 2 Version 9.6 Judge s Guide Table of Contents 1 Introduction... 2 2 Logging in to
ACM INTERNATIONAL COLLEGIATE PROGRAMMING CONTEST California State University, Sacramento s PC 2 Version 9.6 Judge s Guide Table of Contents 1 Introduction... 2 2 Logging in to
Workspace ONE UEM Certificate Authentication for Cisco IPSec VPN. VMware Workspace ONE UEM 1810
 Workspace ONE UEM Certificate Authentication for Cisco IPSec VPN VMware Workspace ONE UEM 1810 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Workspace ONE UEM Certificate Authentication for Cisco IPSec VPN VMware Workspace ONE UEM 1810 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Clearspan OpEasy Basic Provisioning User Guide MAY Release
 Clearspan OpEasy Basic Provisioning User Guide MAY 2015 Release 4.2 2827-008 NOTICE The information contained in this document is believed to be accurate in all respects but is not warranted by Mitel Communications,
Clearspan OpEasy Basic Provisioning User Guide MAY 2015 Release 4.2 2827-008 NOTICE The information contained in this document is believed to be accurate in all respects but is not warranted by Mitel Communications,
Continuous Integration (CI) with Jenkins
 TDDC88 Lab 5 Continuous Integration (CI) with Jenkins This lab will give you some handson experience in using continuous integration tools to automate the integration periodically and/or when members of
TDDC88 Lab 5 Continuous Integration (CI) with Jenkins This lab will give you some handson experience in using continuous integration tools to automate the integration periodically and/or when members of
Using SSL/TLS with Active Directory / LDAP
 Purpose This document describes how to install the required certificate on the for use with LDAP or Active Directory (AD) Integration in. This process is required if your LDAP / AD server has a self signed
Purpose This document describes how to install the required certificate on the for use with LDAP or Active Directory (AD) Integration in. This process is required if your LDAP / AD server has a self signed
SafeNet KMIP and Google Drive Integration Guide
 SafeNet KMIP and Google Drive Integration Guide Documentation Version: 20130802 Table of Contents CHAPTER 1 GOOGLE DRIVE......................................... 2 Introduction...............................................................
SafeNet KMIP and Google Drive Integration Guide Documentation Version: 20130802 Table of Contents CHAPTER 1 GOOGLE DRIVE......................................... 2 Introduction...............................................................
ACS 5.x: LDAP Server Configuration Example
 ACS 5.x: LDAP Server Configuration Example Document ID: 113473 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Directory Service Authentication Using
ACS 5.x: LDAP Server Configuration Example Document ID: 113473 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Directory Service Authentication Using
Oracle Cloud Using the Gmail Adapter. Release 17.3
 Oracle Cloud Using the Gmail Adapter Release 17.3 E69237-09 September 2017 Oracle Cloud Using the Gmail Adapter, Release 17.3 E69237-09 Copyright 2016, 2017, Oracle and/or its affiliates. All rights reserved.
Oracle Cloud Using the Gmail Adapter Release 17.3 E69237-09 September 2017 Oracle Cloud Using the Gmail Adapter, Release 17.3 E69237-09 Copyright 2016, 2017, Oracle and/or its affiliates. All rights reserved.
IBM. Bulk Load Utilities Guide. IBM Emptoris Contract Management SaaS
 IBM Emptoris Contract Management IBM Bulk Load Utilities Guide 10.1.2 SaaS IBM Emptoris Contract Management IBM Bulk Load Utilities Guide 10.1.2 SaaS ii IBM Emptoris Contract Management: Bulk Load Utilities
IBM Emptoris Contract Management IBM Bulk Load Utilities Guide 10.1.2 SaaS IBM Emptoris Contract Management IBM Bulk Load Utilities Guide 10.1.2 SaaS ii IBM Emptoris Contract Management: Bulk Load Utilities
vcloud Director Administrator's Guide
 vcloud Director 5.1.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of
vcloud Director 5.1.1 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of
Keytool and Certificate Management
 Keytool and Certificate Management A guide to utilizing keytool to assist with Certificates for emedny SOAP 2/16/2013 TABLE OF CONTENTS TABLE OF CONTENTS 1 Introduction... 3 2 Creating a Certificate Signing
Keytool and Certificate Management A guide to utilizing keytool to assist with Certificates for emedny SOAP 2/16/2013 TABLE OF CONTENTS TABLE OF CONTENTS 1 Introduction... 3 2 Creating a Certificate Signing
User's Guide c-treeace SQL Explorer
 User's Guide c-treeace SQL Explorer Contents 1. c-treeace SQL Explorer... 4 1.1 Database Operations... 5 Add Existing Database... 6 Change Database... 7 Create User... 7 New Database... 8 Refresh... 8
User's Guide c-treeace SQL Explorer Contents 1. c-treeace SQL Explorer... 4 1.1 Database Operations... 5 Add Existing Database... 6 Change Database... 7 Create User... 7 New Database... 8 Refresh... 8
Assuming you have Icinga 2 installed properly, and the API is not enabled, the commands will guide you through the basics:
 Icinga 2 Contents This page references the GroundWork Cloud Hub and the Icinga 2 virtualization environment. 1.0 Prerequisites 1.1 Enable the API The Icinga 2 system you run needs to have the API feature
Icinga 2 Contents This page references the GroundWork Cloud Hub and the Icinga 2 virtualization environment. 1.0 Prerequisites 1.1 Enable the API The Icinga 2 system you run needs to have the API feature
Cisco TelePresence Management Suite Extension for IBM Lotus Notes
 Cisco TelePresence Management Suite Extension for IBM Lotus Notes Installation and Getting Started Guide D13561.18 June 2011 Software version 11.3.1 Contents Introduction 5 How to use this document 5 Requirements
Cisco TelePresence Management Suite Extension for IBM Lotus Notes Installation and Getting Started Guide D13561.18 June 2011 Software version 11.3.1 Contents Introduction 5 How to use this document 5 Requirements
Sample Spark Web-App. Overview. Prerequisites
 Sample Spark Web-App Overview Follow along with these instructions using the sample Guessing Game project provided to you. This guide will walk you through setting up your workspace, compiling and running
Sample Spark Web-App Overview Follow along with these instructions using the sample Guessing Game project provided to you. This guide will walk you through setting up your workspace, compiling and running
User Documentation. Administrator Manual.
 User Documentation Administrator Manual Proposal Software 1140 US Highway 287, Suite 400-102 Broomfield, CO 80020 USA Tel: 203.604.6597 www.proposalsoftware.com Table of Contents Open the WebPro Viewer...
User Documentation Administrator Manual Proposal Software 1140 US Highway 287, Suite 400-102 Broomfield, CO 80020 USA Tel: 203.604.6597 www.proposalsoftware.com Table of Contents Open the WebPro Viewer...
Nimsoft Service Desk. Single Sign-On Configuration Guide. [assign the version number for your book]
![Nimsoft Service Desk. Single Sign-On Configuration Guide. [assign the version number for your book] Nimsoft Service Desk. Single Sign-On Configuration Guide. [assign the version number for your book]](/thumbs/80/81218109.jpg) Nimsoft Service Desk Single Sign-On Configuration Guide [assign the version number for your book] Legal Notices Copyright 2012, CA. All rights reserved. Warranty The material contained in this document
Nimsoft Service Desk Single Sign-On Configuration Guide [assign the version number for your book] Legal Notices Copyright 2012, CA. All rights reserved. Warranty The material contained in this document
Welcome to the e-learning course for SAP Business One Analytics Powered by SAP HANA: Installation and Licensing. This course is valid for release
 Welcome to the e-learning course for SAP Business One Analytics Powered by SAP HANA: Installation and Licensing. This course is valid for release 9.0. 1 At the end of this course, you will be able to discuss
Welcome to the e-learning course for SAP Business One Analytics Powered by SAP HANA: Installation and Licensing. This course is valid for release 9.0. 1 At the end of this course, you will be able to discuss
Configuring the RTP Server
 Configuring the RTP Server To configure the RTP Server you can click on the little cog in the lower right hand corner of the banner area at the top of the window (If the RTP Server is running you will
Configuring the RTP Server To configure the RTP Server you can click on the little cog in the lower right hand corner of the banner area at the top of the window (If the RTP Server is running you will
VMware AirWatch Certificate Authentication for EAS with NDES-MSCEP
 VMware AirWatch Certificate Authentication for EAS with NDES-MSCEP For VMware AirWatch Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
VMware AirWatch Certificate Authentication for EAS with NDES-MSCEP For VMware AirWatch Have documentation feedback? Submit a Documentation Feedback support ticket using the Support Wizard on support.air-watch.com.
Integrating VMware Horizon Workspace and VMware Horizon View TECHNICAL WHITE PAPER
 Integrating VMware Horizon Workspace and VMware Horizon View TECHNICAL WHITE PAPER Table of Contents Introduction.... 3 Requirements.... 3 Horizon Workspace Components.... 3 SAML 2.0 Standard.... 3 Authentication
Integrating VMware Horizon Workspace and VMware Horizon View TECHNICAL WHITE PAPER Table of Contents Introduction.... 3 Requirements.... 3 Horizon Workspace Components.... 3 SAML 2.0 Standard.... 3 Authentication
Oracle Insurance Policy Administration Configuration of SAML 1.1 Between OIPA and OIDC
 Oracle Insurance Policy Administration Configuration of SAML 1.1 Between OIPA and OIDC Version 10.1.0.0 Documentation Part Number: E55027-01 June, 2014 Copyright 2009, 2014, Oracle and/or its affiliates.
Oracle Insurance Policy Administration Configuration of SAML 1.1 Between OIPA and OIDC Version 10.1.0.0 Documentation Part Number: E55027-01 June, 2014 Copyright 2009, 2014, Oracle and/or its affiliates.
To Setup your Business id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version
 To Setup your Business email id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version Depending on your MAC OS version, your screens may appear a bit different,
To Setup your Business email id in MacOS X El Capitan Mail (POP) To find MacOS version please visit: Apple Support macos version Depending on your MAC OS version, your screens may appear a bit different,
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.5.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.5.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
XProtect Corporate Integration with C CURE 9000 v2.60 User Manual April 25, 2018
 XProtect Corporate Integration with C CURE 9000 v2.60 User Manual April 25, 2018 1 Table of Contents 1 Document information... 3 2 Document revision history... 3 3 Version Compatibility... 4 4 Feature
XProtect Corporate Integration with C CURE 9000 v2.60 User Manual April 25, 2018 1 Table of Contents 1 Document information... 3 2 Document revision history... 3 3 Version Compatibility... 4 4 Feature
Cisco TelePresence Management Suite Extension for IBM Lotus Notes
 Cisco TelePresence Management Suite Extension for IBM Lotus Notes Installation and Getting Started Guide Software version 11.3.3 D13561.21 Revised October 2014 Contents Introduction 4 How to use this document
Cisco TelePresence Management Suite Extension for IBM Lotus Notes Installation and Getting Started Guide Software version 11.3.3 D13561.21 Revised October 2014 Contents Introduction 4 How to use this document
bbc Migrating and Sharing Secuity Settings: Using Security Settings Import/Export and FDF Files Acrobat and Adobe Reader PDF Creation Date:
 bbc PDF Creation Date: September 5, 2008 Migrating and Sharing Secuity Settings: Using Security Settings Import/Export and FDF Files Acrobat and Adobe Reader Version 9.0 2008 Adobe Systems Incorporated.
bbc PDF Creation Date: September 5, 2008 Migrating and Sharing Secuity Settings: Using Security Settings Import/Export and FDF Files Acrobat and Adobe Reader Version 9.0 2008 Adobe Systems Incorporated.
Quick Tips & Tricks. Important You must use SEMICOLONS ( ie; ) to separate address when sending mail to multiple users
 Quick Tips & Tricks Important You must use SEMICOLONS ( ie; ) to separate email address when sending mail to multiple users Customize Mail View Click, View, and then highlight Current View Click, Customize
Quick Tips & Tricks Important You must use SEMICOLONS ( ie; ) to separate email address when sending mail to multiple users Customize Mail View Click, View, and then highlight Current View Click, Customize
LDAP/AD v1.0 User Guide
 LDAP/AD v1.0 User Guide For v6.5 systems Catalog No. 11-808-615-01 Important changes are listed in Document revision history at the end of this document. UTC 2017. throughout the world. All trademarks
LDAP/AD v1.0 User Guide For v6.5 systems Catalog No. 11-808-615-01 Important changes are listed in Document revision history at the end of this document. UTC 2017. throughout the world. All trademarks
How do I configure my LPL client to use SSL for incoming mail?
 How do I configure my LPL email client to use SSL for incoming mail? When you begin using your modern graphical email client program (e.g., Thunderbird, Mac Mail, Outlook), it will present a series of
How do I configure my LPL email client to use SSL for incoming mail? When you begin using your modern graphical email client program (e.g., Thunderbird, Mac Mail, Outlook), it will present a series of
vcloud Director Administrator's Guide
 vcloud Director 5.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of
vcloud Director 5.5 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of
Managing Certificates
 CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
