ENGR/CS 101 CS Session Lecture 13
|
|
|
- Molly Patrick
- 5 years ago
- Views:
Transcription
1 ENGR/CS 101 CS Session Lecture 13 Log into Windows/ACENET (reboot if in Linux) Start Microsoft Visual Studio 2012 and open the Substitution Cipher Project Has everyone finished the program from last class so that it can encipher and decipher using the Vigenere cipher? Lecture 13 ENGR/CS 101 Computer Science Session 1
2 Outline Problem: Loading messages from and saving messages to files File streams Open/Save Dialogs Lecture 13 ENGR/CS 101 Computer Science Session 2
3 Problem: Loading & Saving Messages Typing in long messages is tedious and error prone. Also, message often come in textfiles. Keeping a record of the resulting messages would require writing down the messages on a piece of paper, also tedious and error prone. We would like to enhance our project to be able to read messages from a file and write the results to a textfile. Lecture 13 ENGR/CS 101 Computer Science Session 3
4 GUI Interface Add four buttons to the GUI to be clicked to do the following actions. Set their Name properties as indicated Load Plaintext - loadplainbtn Save Plaintext - saveplainbtn Load Ciphertext - loadcipherbtn Save Ciphertext - savecipherbtn Style them however you like. Lecture 13 ENGR/CS 101 Computer Science Session 4
5 Reading from a File Double-click on the Load Plaintext button. The handler for this button must read a plaintext message from a file and load it into the plaintext box. A file stream is a program object that is opened (i.e., attached to a physical file) when it is created. StreamReader objects are used to read data from a file. Lecture 13 ENGR/CS 101 Computer Science Session 5
6 OpenFileDialog An OpenFileDialog is the window that pops up when a user wants to open a file. It is used to connect a file stream to a physical file. Lecture 13 ENGR/CS 101 Computer Science Session 6
7 OpenFileDialog An OpenFileDialog is declared and initialized as follows: OpenFileDialog filechooser = new OpenFileDialog(); To make the dialog pop up and get the file name from the user, call the ShowDialog method and save the result in a DialogResult variable DialogResult result = filechooser.showdialog(); Lecture 13 ENGR/CS 101 Computer Science Session 7
8 OpenFileDialog If a user clicks on the Cancel button, our application must go back to waiting, so we test the DialogResult. // Check if user clicked Cancel if (result == DialogResult.Cancel) { return; // Go back to waiting } Lecture 13 ENGR/CS 101 Computer Science Session 8
9 StreamReader Now we create a StreamReader object using the chosen file name, then read the entire file into the plaintext box. // Open (attach) the file chosen in the dialog StreamReader fileinput = new StreamReader (filechooser.filename); // Read entire file contents into plaintext box plaintextbox.text = fileinput.readtoend(); Lecture 13 ENGR/CS 101 Computer Science Session 9
10 StreamReader The squiggly red lines under "StreamReader", means that the program needs to import the library that defines StreamReader. Do this by right-clicking on "StreamReader", selecting "Resolve", then "using System.IO". Lecture 13 ENGR/CS 101 Computer Science Session 10
11 StreamReader All file streams should be closed (i.e. detached from the physical file). fileinput.close(); // Detach the physical file Finally, the ciphertext box should be cleared, since whatever was in it is no longer related to what is now in the plaintext box ciphertextbox.text = ""; // Clear ciphertext box Lecture 13 ENGR/CS 101 Computer Science Session 11
12 In-class Exercise, Part 1 Test the program. Create a message file by using FILE->New, select Text File. Then use FILE->Save As to give it a name like "message.txt" and put it in the project folder. Click on the Load Plaintext button. An OpenFileDialog should pop up. Browse to your message file and click Open. The text in the file should appear in the plaintext box. Lecture 13 ENGR/CS 101 Computer Science Session 12
13 In-class Exercise, Part 1 Double-click on the Load Ciphertext button Write the click handler code for this button. It is almost exactly the same as the code for the Load Plaintext button. The only difference is that the file contents are put into the ciphertext box (instead of the plaintext box) and the plaintext box is cleared. Test you program again. Lecture 13 ENGR/CS 101 Computer Science Session 13
14 Writing to a File Double-click on the Save Ciphertext button This handler must write a ciphertext message to a file. StreamWriter objects are used to write data to a file. Lecture 13 ENGR/CS 101 Computer Science Session 14
15 SaveFileDialog Getting a file name for saving a file is done with a SaveFileDialog. It works exactly the same way as the OpenFileDialog for getting a file name from the user. (I.e., it is the same code with SaveFileDialog instead of OpenFileDialog.) Lecture 13 ENGR/CS 101 Computer Science Session 15
16 StreamWriter Now we create a StreamWriter object using the chosen file name, then write the Text of the ciphertext box to the file: // Open (attach) the file chosen in the dialog StreamWriter fileoutput = new StreamWriter (filechooser.filename); // Write ciphertext to file fileoutput.writeline (ciphertextbox.text); fileoutput.close(); // Detach the physical file Lecture 13 ENGR/CS 101 Computer Science Session 16
17 In-class Exercise, Part 2 Test the program. After loading a plaintext message and enciphering it, click on the Save Ciphertext button. A SaveFileDialog should pop up. Type in a file name like "secret.txt", make sure it will be saved into the project folder, and click Save. You can look at the saved file by using FILE - >Open->File. Lecture 13 ENGR/CS 101 Computer Science Session 17
18 In-class Exercise, Part 2 Double-click on the Save Plaintext button and write the click handler for it. It is almost exactly the same as the code for the Save Ciphertext button. The only difference is that plaintextbox.text is saved to the file instead. Lecture 13 ENGR/CS 101 Computer Science Session 18
ENGR/CS 101 CS Session Lecture 9
 ENGR/CS 101 CS Session Lecture 9 Log into Windows/ACENET (reboot if in Linux) Start Python, open program from last time. Has everyone finished the program from last class so that it can encipher and decipher
ENGR/CS 101 CS Session Lecture 9 Log into Windows/ACENET (reboot if in Linux) Start Python, open program from last time. Has everyone finished the program from last class so that it can encipher and decipher
ENGR/CS 101 CS Session Lecture 4
 ENGR/CS 101 CS Session Lecture 4 Log into Windows/ACENET (reboot if in Linux) Start Microsoft Visual Studio 2010 Finish exercise from last time Lecture 4 ENGR/CS 101 Computer Science Session 1 Outline
ENGR/CS 101 CS Session Lecture 4 Log into Windows/ACENET (reboot if in Linux) Start Microsoft Visual Studio 2010 Finish exercise from last time Lecture 4 ENGR/CS 101 Computer Science Session 1 Outline
ENGR/CS 101 CS Session Lecture 5
 ENGR/CS 101 CS Session Lecture 5 No programming today Submission system will be demonstrated at the end of class. Lecture 5 ENGR/CS 101 Computer Science Session 1 Outline Problem: How to send a secret
ENGR/CS 101 CS Session Lecture 5 No programming today Submission system will be demonstrated at the end of class. Lecture 5 ENGR/CS 101 Computer Science Session 1 Outline Problem: How to send a secret
How to read/write text file
 How to read/write text file Contents Use StreamWriter... 1 Create button click event handler... 2 Create StreamWriter... 3 Write to file... 5 Close file... 8 Test file writing... 9 Use StreamReader...
How to read/write text file Contents Use StreamWriter... 1 Create button click event handler... 2 Create StreamWriter... 3 Write to file... 5 Close file... 8 Test file writing... 9 Use StreamReader...
ENGR/CS 101 CS Session Lecture 3
 ENGR/CS 101 CS Session Lecture 3 Log into Windows/ACENET (reboot if in Linux) Start Microsoft Visual Studio 2010 Windows button -> All Programs -> 02 Programming -> Microsoft Visual Studio 2010 -> Microsoft
ENGR/CS 101 CS Session Lecture 3 Log into Windows/ACENET (reboot if in Linux) Start Microsoft Visual Studio 2010 Windows button -> All Programs -> 02 Programming -> Microsoft Visual Studio 2010 -> Microsoft
C# Continued. Learning Objectives:
 Learning Objectives: C# Continued Open File Dialog and Save File Dialog File Input/Output Importing Pictures from Files and saving Bitmaps Reading and Writing Text Files Try and Catch Working with Strings
Learning Objectives: C# Continued Open File Dialog and Save File Dialog File Input/Output Importing Pictures from Files and saving Bitmaps Reading and Writing Text Files Try and Catch Working with Strings
C# Continued. Learning Objectives:
 Learning Objectives: C# Continued Open File Dialog and Save File Dialog File Input/Output Importing Pictures from Files and saving Bitmaps Reading and Writing Text Files Try and Catch Working with Strings
Learning Objectives: C# Continued Open File Dialog and Save File Dialog File Input/Output Importing Pictures from Files and saving Bitmaps Reading and Writing Text Files Try and Catch Working with Strings
Chapter 11. Data Files The McGraw-Hill Companies, Inc. All rights reserved. McGraw-Hill
 Chapter 11 Data Files McGraw-Hill 2010 The McGraw-Hill Companies, Inc. All rights reserved. Chapter Objectives Store and retrieve data in files using streams Save the values from a list box and reload
Chapter 11 Data Files McGraw-Hill 2010 The McGraw-Hill Companies, Inc. All rights reserved. Chapter Objectives Store and retrieve data in files using streams Save the values from a list box and reload
05/31/2009. Data Files
 Data Files Store and retrieve data in files using streams Save the values from a list box and reload for the next program run Check for the end of file Test whether a file exists Display the standard Open
Data Files Store and retrieve data in files using streams Save the values from a list box and reload for the next program run Check for the end of file Test whether a file exists Display the standard Open
6. Symmetric Block Cipher BLOWFISH Performance. Memory space. 3. Simplicity The length of the key. The length of the data block is 64.
 belongs to the same class of conventional symmetric ciphers. The basic principles of have been published in 1994 by Bruce Schneier, as an alternative to the Data encryption standard (DES) to satisfy the
belongs to the same class of conventional symmetric ciphers. The basic principles of have been published in 1994 by Bruce Schneier, as an alternative to the Data encryption standard (DES) to satisfy the
ENGR/CS 101 CS Session Lecture 15
 ENGR/CS 101 CS Session Lecture 15 Log into Windows/ACENET (reboot if in Linux) Use web browser to go to session webpage http://csserver.evansville.edu/~hwang/f14-courses/cs101.html Right-click on lecture15.py
ENGR/CS 101 CS Session Lecture 15 Log into Windows/ACENET (reboot if in Linux) Use web browser to go to session webpage http://csserver.evansville.edu/~hwang/f14-courses/cs101.html Right-click on lecture15.py
Files. C# Programming: From Problem Analysis to Program Design 2nd Edition. David McDonald, Ph.D. Director of Emerging Technologies
 12 Working with Files C# Programming: From Problem Analysis to Program Design 2nd Edition David McDonald, Ph.D. Director of Emerging Technologies Chapter Objectives Learn about the System.IO namespace
12 Working with Files C# Programming: From Problem Analysis to Program Design 2nd Edition David McDonald, Ph.D. Director of Emerging Technologies Chapter Objectives Learn about the System.IO namespace
ENGR/CS 101 CS Session Lecture 12
 ENGR/CS 101 CS Session Lecture 12 Log into Windows/ACENET (reboot if in Linux) Use web browser to go to session webpage http://csserver.evansville.edu/~hwang/f14-courses/cs101.html Right-click on lecture12.py
ENGR/CS 101 CS Session Lecture 12 Log into Windows/ACENET (reboot if in Linux) Use web browser to go to session webpage http://csserver.evansville.edu/~hwang/f14-courses/cs101.html Right-click on lecture12.py
2/7/2013. CS 472 Network and System Security. Mohammad Almalag Lecture 2 January 22, Introduction To Cryptography
 CS 472 Network and System Security Mohammad Almalag malmalag@cs.odu.edu Lecture 2 January 22, 2013 Introduction To Cryptography 1 Definitions Cryptography = the science (art) of encryption Cryptanalysis
CS 472 Network and System Security Mohammad Almalag malmalag@cs.odu.edu Lecture 2 January 22, 2013 Introduction To Cryptography 1 Definitions Cryptography = the science (art) of encryption Cryptanalysis
Algebraic Solutions of Caesar and Multiplicative Ciphers
 Spring 2015 Chris Christensen MAT/CSC 483 Algebraic Solutions of Caesar and Multiplicative Ciphers The Caesar cipher and the multiplicative cipher each involve one algebraic operation addition modulo 26
Spring 2015 Chris Christensen MAT/CSC 483 Algebraic Solutions of Caesar and Multiplicative Ciphers The Caesar cipher and the multiplicative cipher each involve one algebraic operation addition modulo 26
Programming with Microsoft Visual Basic.NET. Array. What have we learnt in last lesson? What is Array?
 What have we learnt in last lesson? Programming with Microsoft Visual Basic.NET Using Toolbar in Windows Form. Using Tab Control to separate information into different tab page Storage hierarchy information
What have we learnt in last lesson? Programming with Microsoft Visual Basic.NET Using Toolbar in Windows Form. Using Tab Control to separate information into different tab page Storage hierarchy information
LECTURE NOTES ON COMPUTER AND DATA SECURITY
 Department of Software The University of Babylon LECTURE NOTES ON COMPUTER AND DATA SECURITY By College of Information Technology, University of Babylon, Iraq Samaher@itnet.uobabylon.edu.iq Computer an
Department of Software The University of Babylon LECTURE NOTES ON COMPUTER AND DATA SECURITY By College of Information Technology, University of Babylon, Iraq Samaher@itnet.uobabylon.edu.iq Computer an
JDirectoryChooser Documentation
 JDirectoryChooser Documentation Page 1 of 7 How to Use JDirectoryChooser The JDirectoryChooser provides user-friendly GUI for manipulating directories from Java application. User can either simply choose
JDirectoryChooser Documentation Page 1 of 7 How to Use JDirectoryChooser The JDirectoryChooser provides user-friendly GUI for manipulating directories from Java application. User can either simply choose
// Program 2 - Extra Credit // CIS // Spring // Due: 3/11/2015. // By: Andrew L. Wright. //Edited by : Ben Spalding
 // Program 2 - Extra Credit // CIS 200-01 // Spring 2015 // Due: 3/11/2015 // By: Andrew L. Wright //Edited by : Ben Spalding // File: Prog2Form.cs // This class creates the main GUI for Program 2. It
// Program 2 - Extra Credit // CIS 200-01 // Spring 2015 // Due: 3/11/2015 // By: Andrew L. Wright //Edited by : Ben Spalding // File: Prog2Form.cs // This class creates the main GUI for Program 2. It
C# 2008 and.net Programming for Electronic Engineers - Elektor - ISBN
 Contents Contents 5 About the Author 12 Introduction 13 Conventions used in this book 14 1 The Visual Studio C# Environment 15 1.1 Introduction 15 1.2 Obtaining the C# software 15 1.3 The Visual Studio
Contents Contents 5 About the Author 12 Introduction 13 Conventions used in this book 14 1 The Visual Studio C# Environment 15 1.1 Introduction 15 1.2 Obtaining the C# software 15 1.3 The Visual Studio
Chapter 14: Files and Streams
 Chapter 14: Files and Streams Files and the File and Directory Temporary storage Classes Usually called computer memory or random access memory (RAM) Variables use temporary storage Volatile Permanent
Chapter 14: Files and Streams Files and the File and Directory Temporary storage Classes Usually called computer memory or random access memory (RAM) Variables use temporary storage Volatile Permanent
Windows File I/O. Files. Collections of related data stored on external storage media and assigned names so that they can be accessed later
 Windows File I/O Files Collections of related data stored on external storage media and assigned names so that they can be accessed later Entire collection is a file A file is made up of records One record
Windows File I/O Files Collections of related data stored on external storage media and assigned names so that they can be accessed later Entire collection is a file A file is made up of records One record
Module 8: Building a Windows Forms User Interface
 Module 8: Building a Windows Forms User Interface Table of Contents Module Overview 8-1 Lesson 1: Managing Forms and Dialog Boxes 8-2 Lesson 2: Creating Menus and Toolbars 8-13 Lab: Implementing Menus
Module 8: Building a Windows Forms User Interface Table of Contents Module Overview 8-1 Lesson 1: Managing Forms and Dialog Boxes 8-2 Lesson 2: Creating Menus and Toolbars 8-13 Lab: Implementing Menus
Question: How do I move my mobile account from the Corporate to my Personal Account?
 Question: How do I move my mobile account from the Corporate to my Personal Account? Answer: A user leaving Nortel can move his/her account off of the corporate program and into a personal liable account.
Question: How do I move my mobile account from the Corporate to my Personal Account? Answer: A user leaving Nortel can move his/her account off of the corporate program and into a personal liable account.
Fundamentals of Computer Security
 Fundamentals of Computer Security Spring 2015 Radu Sion Ciphers 2005-15 Portions copyright by Matt Bishop and Wikipedia. Used with permission Overview m 3 m 2 m 1 cipher c i Bob Alice cipher -1 m 1 m 2
Fundamentals of Computer Security Spring 2015 Radu Sion Ciphers 2005-15 Portions copyright by Matt Bishop and Wikipedia. Used with permission Overview m 3 m 2 m 1 cipher c i Bob Alice cipher -1 m 1 m 2
Security Management System Configuring Secondary Storage Access from CMS
 Security Management System Configuring Secondary Storage Access from CMS Introduction Security management system server software supports secondary recording feature, in which the camera streams are recorded
Security Management System Configuring Secondary Storage Access from CMS Introduction Security management system server software supports secondary recording feature, in which the camera streams are recorded
CIS 3260 Intro to Programming with C#
 Menus and Common Dialog Boxes McGraw-Hill 2010 The McGraw-Hill Companies, Inc. All rights reserved. Create menus and submenus for program control Display and use the Windows common dialog boxes McGraw-Hill
Menus and Common Dialog Boxes McGraw-Hill 2010 The McGraw-Hill Companies, Inc. All rights reserved. Create menus and submenus for program control Display and use the Windows common dialog boxes McGraw-Hill
Cryptography (DES+RSA) by Amit Konar Dept. of Math and CS, UMSL
 Cryptography (DES+RSA) by Amit Konar Dept. of Math and CS, UMSL Transpositional Ciphers-A Review Decryption 1 2 3 4 5 6 7 8 1 2 3 4 5 6 7 8 Encryption 1 2 3 4 5 6 7 8 A G O O D F R I E N D I S A T R E
Cryptography (DES+RSA) by Amit Konar Dept. of Math and CS, UMSL Transpositional Ciphers-A Review Decryption 1 2 3 4 5 6 7 8 1 2 3 4 5 6 7 8 Encryption 1 2 3 4 5 6 7 8 A G O O D F R I E N D I S A T R E
Substitution Ciphers, continued. 3. Polyalphabetic: Use multiple maps from the plaintext alphabet to the ciphertext alphabet.
 Substitution Ciphers, continued 3. Polyalphabetic: Use multiple maps from the plaintext alphabet to the ciphertext alphabet. Non-periodic case: Running key substitution ciphers use a known text (in a standard
Substitution Ciphers, continued 3. Polyalphabetic: Use multiple maps from the plaintext alphabet to the ciphertext alphabet. Non-periodic case: Running key substitution ciphers use a known text (in a standard
Cryptography and Network Security 2. Symmetric Ciphers. Lectured by Nguyễn Đức Thái
 Cryptography and Network Security 2. Symmetric Ciphers Lectured by Nguyễn Đức Thái Outline Symmetric Encryption Substitution Techniques Transposition Techniques Steganography 2 Symmetric Encryption There
Cryptography and Network Security 2. Symmetric Ciphers Lectured by Nguyễn Đức Thái Outline Symmetric Encryption Substitution Techniques Transposition Techniques Steganography 2 Symmetric Encryption There
Chapter 7 Lab A: Exploring Encryption Methods
 Chapter 7 Lab A: Exploring Encryption Methods Topology Objectives Part 1: (Optional) Build the Network and Configure the PCs Connect the PCs and configure IP addresses. Part 2: Decipher a Pre-encrypted
Chapter 7 Lab A: Exploring Encryption Methods Topology Objectives Part 1: (Optional) Build the Network and Configure the PCs Connect the PCs and configure IP addresses. Part 2: Decipher a Pre-encrypted
Chapter 6 Dialogs. Creating a Dialog Style Form
 Chapter 6 Dialogs We all know the importance of dialogs in Windows applications. Dialogs using the.net FCL are very easy to implement if you already know how to use basic controls on forms. A dialog is
Chapter 6 Dialogs We all know the importance of dialogs in Windows applications. Dialogs using the.net FCL are very easy to implement if you already know how to use basic controls on forms. A dialog is
// Precondition: None // Postcondition: The address' name has been set to the // specified value set;
 // File: Address.cs // This classes stores a typical US address consisting of name, // two address lines, city, state, and 5 digit zip code. using System; using System.Collections.Generic; using System.Linq;
// File: Address.cs // This classes stores a typical US address consisting of name, // two address lines, city, state, and 5 digit zip code. using System; using System.Collections.Generic; using System.Linq;
You can call the project anything you like I will be calling this one project slide show.
 C# Tutorial Load all images from a folder Slide Show In this tutorial we will see how to create a C# slide show where you load everything from a single folder and view them through a timer. This exercise
C# Tutorial Load all images from a folder Slide Show In this tutorial we will see how to create a C# slide show where you load everything from a single folder and view them through a timer. This exercise
Print Audit 5 - How to Move Print Audit 5 and a SQL Server 2005 Express Database to a New Server
 Print Audit 5 - How to Move Print Audit 5 and a SQL Server 2005 Express Database to a New Server Overview This document includes the steps to move Print Audit 5 and a SQL Server 2005 Express database to
Print Audit 5 - How to Move Print Audit 5 and a SQL Server 2005 Express Database to a New Server Overview This document includes the steps to move Print Audit 5 and a SQL Server 2005 Express database to
Chapter 8 Advanced GUI Features
 159 Chapter 8 Advanced GUI Features There are many other features we can easily add to a Windows C# application. We must be able to have menus and dialogs along with many other controls. One workhorse
159 Chapter 8 Advanced GUI Features There are many other features we can easily add to a Windows C# application. We must be able to have menus and dialogs along with many other controls. One workhorse
OVE EDFORS ELECTRICAL AND INFORMATION TECHNOLOGY
 1 Information Transmission Chapter 6 Cryptology OVE EDFORS ELECTRICAL AND INFORMATION TECHNOLOGY Learning outcomes After this lecture the student should undertand what cryptology is and how it is used,
1 Information Transmission Chapter 6 Cryptology OVE EDFORS ELECTRICAL AND INFORMATION TECHNOLOGY Learning outcomes After this lecture the student should undertand what cryptology is and how it is used,
To start we will be using visual studio Start a new C# windows form application project and name it motivational quotes viewer
 C# Tutorial Create a Motivational Quotes Viewer Application in Visual Studio In this tutorial we will create a fun little application for Microsoft Windows using Visual Studio. You can use any version
C# Tutorial Create a Motivational Quotes Viewer Application in Visual Studio In this tutorial we will create a fun little application for Microsoft Windows using Visual Studio. You can use any version
Classical Encryption Techniques
 Classical Encryption Techniques Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse571-14/
Classical Encryption Techniques Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse571-14/
Block Cipher Modes of Operation
 Block Cipher Modes of Operation Luke Anderson luke@lukeanderson.com.au 23 rd March 2018 University Of Sydney Overview 1. Crypto-Bulletin 2. Modes Of Operation 2.1 Evaluating Modes 2.2 Electronic Code Book
Block Cipher Modes of Operation Luke Anderson luke@lukeanderson.com.au 23 rd March 2018 University Of Sydney Overview 1. Crypto-Bulletin 2. Modes Of Operation 2.1 Evaluating Modes 2.2 Electronic Code Book
Image Data Binding. Save images in database An image needs large amount of storage space. Only binary variable length fields may hold images.
 Image Data Binding Contents Save images in database... 1 Data Binding... 2 Update images... 3 Create method to select image into the Picture Box... 3 Execute SelectMethod when the Picture Box is clicked...
Image Data Binding Contents Save images in database... 1 Data Binding... 2 Update images... 3 Create method to select image into the Picture Box... 3 Execute SelectMethod when the Picture Box is clicked...
Cryptography Part II Introduction to Computer Security. Chapter 8
 Cryptography Part II Introduction to Computer Security Chapter 8 Vigènere Cipher Like Cæsar cipher, but use phrase Example Message: THE BOY HAS THE BALL Key: VIG Encipher using Cæsar cipher for each letter:
Cryptography Part II Introduction to Computer Security Chapter 8 Vigènere Cipher Like Cæsar cipher, but use phrase Example Message: THE BOY HAS THE BALL Key: VIG Encipher using Cæsar cipher for each letter:
Module 13 Network Security. Version 1 ECE, IIT Kharagpur
 Module 13 Network Security Lesson 40 Network Security 13.1.1 INTRODUCTION Network Security assumes a great importance in the current age. In this chapter we shall look at some of the security measures
Module 13 Network Security Lesson 40 Network Security 13.1.1 INTRODUCTION Network Security assumes a great importance in the current age. In this chapter we shall look at some of the security measures
Cryptography and Network Security Block Ciphers + DES. Lectured by Nguyễn Đức Thái
 Cryptography and Network Security Block Ciphers + DES Lectured by Nguyễn Đức Thái Outline Block Cipher Principles Feistel Ciphers The Data Encryption Standard (DES) (Contents can be found in Chapter 3,
Cryptography and Network Security Block Ciphers + DES Lectured by Nguyễn Đức Thái Outline Block Cipher Principles Feistel Ciphers The Data Encryption Standard (DES) (Contents can be found in Chapter 3,
How to design and print cards using a database connection with. emedia CS Software
 How to design and print cards using a database connection with emedia CS Software For this exercise, we will use a Database that has been created in EXCEL. The example below shows the database fields populated
How to design and print cards using a database connection with emedia CS Software For this exercise, we will use a Database that has been created in EXCEL. The example below shows the database fields populated
File Handling Programming 1 C# Programming. Rob Miles
 08101 Programming 1 C# Programming Rob Miles Files At the moment when our program stops all the data in it is destroyed We need a way of persisting data from our programs The way to do this is to use files
08101 Programming 1 C# Programming Rob Miles Files At the moment when our program stops all the data in it is destroyed We need a way of persisting data from our programs The way to do this is to use files
Computer measurement and control
 Computer measurement and control Instructors: András Magyarkuti, Zoltán Kovács-Krausz BME TTK, Department of Physics 2017/2018 spring semester Copyright 2008-2018 András Magyarkuti, Attila Geresdi, András
Computer measurement and control Instructors: András Magyarkuti, Zoltán Kovács-Krausz BME TTK, Department of Physics 2017/2018 spring semester Copyright 2008-2018 András Magyarkuti, Attila Geresdi, András
CSE509: (Intro to) Systems Security
 CSE509: (Intro to) Systems Security Fall 2012 Radu Sion Ciphers 2005-12 Portions copyright by Matt Bishop. Used with permission Ciphers Overview Naïve Usage Types of Ciphers Systems Security September
CSE509: (Intro to) Systems Security Fall 2012 Radu Sion Ciphers 2005-12 Portions copyright by Matt Bishop. Used with permission Ciphers Overview Naïve Usage Types of Ciphers Systems Security September
L9: Stream and Block Ciphers. Hui Chen, Ph.D. Dept. of Engineering & Computer Science Virginia State University Petersburg, VA 23806
 L9: Stream and Block Ciphers Hui Chen, Ph.D. Dept. of Engineering & Computer Science Virginia State University Petersburg, VA 23806 10/19/2016 CSCI 451 -Fall 2016 1 Acknowledgement Many slides are from
L9: Stream and Block Ciphers Hui Chen, Ph.D. Dept. of Engineering & Computer Science Virginia State University Petersburg, VA 23806 10/19/2016 CSCI 451 -Fall 2016 1 Acknowledgement Many slides are from
2.3 SUBTITUTION CIPHERS.
 Lec 5 : Data Security Substitution Cipher Systems 1 2.3 SUBTITUTION CIPHERS. 2.3.1 SIMPLE SUBTTTUION CIPHERS: In simple substitution (or monoalphabetic) ciphers, each character of the plaintext is replaced
Lec 5 : Data Security Substitution Cipher Systems 1 2.3 SUBTITUTION CIPHERS. 2.3.1 SIMPLE SUBTTTUION CIPHERS: In simple substitution (or monoalphabetic) ciphers, each character of the plaintext is replaced
Security Management System Central Monitoring Station with Push Mode Connectivity
 Security Management System Central Monitoring Station with Push Mode Connectivity Introduction Security Management System supports distributed deployment architecture, which involves (a) Central Monitoring
Security Management System Central Monitoring Station with Push Mode Connectivity Introduction Security Management System supports distributed deployment architecture, which involves (a) Central Monitoring
Block Cipher Modes of Operation
 Block Cipher Modes of Operation Luke Anderson luke@lukeanderson.com.au 24th March 2016 University Of Sydney Overview 1. Crypto-Bulletin 2. Modes Of Operation 2.1 Evaluating Modes 2.2 Electronic Code Book
Block Cipher Modes of Operation Luke Anderson luke@lukeanderson.com.au 24th March 2016 University Of Sydney Overview 1. Crypto-Bulletin 2. Modes Of Operation 2.1 Evaluating Modes 2.2 Electronic Code Book
1. A Web Form created in Visual Basic can only be displayed in Internet Explorer. True False
 True / False Questions 1. A Web Form created in Visual Basic can only be displayed in Internet Explorer. 2. Windows Explorer and Internet Explorer are Web browsers. 3. Developing Web applications requires
True / False Questions 1. A Web Form created in Visual Basic can only be displayed in Internet Explorer. 2. Windows Explorer and Internet Explorer are Web browsers. 3. Developing Web applications requires
Modern Cryptography Activity 1: Caesar Ciphers
 Activity 1: Caesar Ciphers Preliminaries: The Caesar cipher is one of the oldest codes in existence. It is an example of a substitution cipher, where each letter in the alphabet is replaced by another
Activity 1: Caesar Ciphers Preliminaries: The Caesar cipher is one of the oldest codes in existence. It is an example of a substitution cipher, where each letter in the alphabet is replaced by another
Use Default Form Instances
 Use Default Form Instances Created: 2011-01-03 Modified:2012-07-05 Contents Introduction... 2 Add Form Classes... 3 Starting Form (Home Page)... 5 Use Multiple Forms... 6 Different Ways of Showing Forms...
Use Default Form Instances Created: 2011-01-03 Modified:2012-07-05 Contents Introduction... 2 Add Form Classes... 3 Starting Form (Home Page)... 5 Use Multiple Forms... 6 Different Ways of Showing Forms...
CS61A Lecture #39: Cryptography
 Announcements: CS61A Lecture #39: Cryptography Homework 13 is up: due Monday. Homework 14 will be judging the contest. HKN surveys on Friday: 7.5 bonus points for filling out their survey on Friday (yes,
Announcements: CS61A Lecture #39: Cryptography Homework 13 is up: due Monday. Homework 14 will be judging the contest. HKN surveys on Friday: 7.5 bonus points for filling out their survey on Friday (yes,
TuneTown Lab Instructions
 TuneTown Lab Instructions Purpose: Practice creating a modal dialog. Incidentally, learn to use a list view control. Credit: This program was designed by Jeff Prosise and published in MSDN Magazine. However,
TuneTown Lab Instructions Purpose: Practice creating a modal dialog. Incidentally, learn to use a list view control. Credit: This program was designed by Jeff Prosise and published in MSDN Magazine. However,
Assignment 1. Application Development
 Application Development Assignment 1 Content Application Development Day 1 Lecture The lecture provides an introduction to programming, the concept of classes and objects in Java and the Eclipse development
Application Development Assignment 1 Content Application Development Day 1 Lecture The lecture provides an introduction to programming, the concept of classes and objects in Java and the Eclipse development
Cryptographic Techniques. Information Technologies for IPR Protections 2003/11/12 R107, CSIE Building
 Cryptographic Techniques Information Technologies for IPR Protections 2003/11/12 R107, CSIE Building Outline Data security Cryptography basics Cryptographic systems DES RSA C. H. HUANG IN CML 2 Cryptography
Cryptographic Techniques Information Technologies for IPR Protections 2003/11/12 R107, CSIE Building Outline Data security Cryptography basics Cryptographic systems DES RSA C. H. HUANG IN CML 2 Cryptography
Introduction to Cryptography
 T H E U N I V E R S I T Y O F B R I T I S H C O L U M B I A Introduction to Cryptography EECE 412 Session 3 Copyright 2004 Konstantin Beznosov Session Outline Historical background Caesar and Vigenère
T H E U N I V E R S I T Y O F B R I T I S H C O L U M B I A Introduction to Cryptography EECE 412 Session 3 Copyright 2004 Konstantin Beznosov Session Outline Historical background Caesar and Vigenère
Security Management System - Managing Infinova 307X NVR channels. Video display in Security Management System server software
 Security Management System - Managing Infinova 307X NVR channels This document describes steps to configure Infinova 307X NVR cameras in Security Management System software. Note Microsoft Visual C++ 2015
Security Management System - Managing Infinova 307X NVR channels This document describes steps to configure Infinova 307X NVR cameras in Security Management System software. Note Microsoft Visual C++ 2015
Introduction to Cryptology. Lecture 2
 Introduction to Cryptology Lecture 2 Announcements Access to Canvas? 2 nd Edition vs. 1 st Edition HW1 due on Tuesday, 2/7 Discrete Math Readings/Quizzes on Canvas due on Tuesday, 2/14 Agenda Last time:
Introduction to Cryptology Lecture 2 Announcements Access to Canvas? 2 nd Edition vs. 1 st Edition HW1 due on Tuesday, 2/7 Discrete Math Readings/Quizzes on Canvas due on Tuesday, 2/14 Agenda Last time:
How do I apply the patch files?
 How do I apply the patch files? 1. Once the patch file has been saved to your hard disk, use Windows Explorer (Start > Programs > [Accessories > ] Windows Explorer) to browse to the directory where the
How do I apply the patch files? 1. Once the patch file has been saved to your hard disk, use Windows Explorer (Start > Programs > [Accessories > ] Windows Explorer) to browse to the directory where the
Cryptography MIS
 Cryptography MIS-5903 http://community.mis.temple.edu/mis5903sec011s17/ Cryptography History Substitution Monoalphabetic Polyalphabetic (uses multiple alphabets) uses Vigenere Table Scytale cipher (message
Cryptography MIS-5903 http://community.mis.temple.edu/mis5903sec011s17/ Cryptography History Substitution Monoalphabetic Polyalphabetic (uses multiple alphabets) uses Vigenere Table Scytale cipher (message
COMP-421 Compiler Design. Presented by Dr Ioanna Dionysiou
 COMP-421 Compiler Design Presented by Dr Ioanna Dionysiou Administrative! Next time reading assignment [ALSU07] Chapters 1,2 [ALSU07] Sections 1.1-1.5 (cover in class) [ALSU07] Section 1.6 (read on your
COMP-421 Compiler Design Presented by Dr Ioanna Dionysiou Administrative! Next time reading assignment [ALSU07] Chapters 1,2 [ALSU07] Sections 1.1-1.5 (cover in class) [ALSU07] Section 1.6 (read on your
A New Symmetric Key Algorithm for Modern Cryptography Rupesh Kumar 1 Sanjay Patel 2 Purushottam Patel 3 Rakesh Patel 4
 IJSRD - International Journal for Scientific Research & Development Vol. 2, Issue 08, 2014 ISSN (online): 2321-0613 A New Symmetric Key Algorithm for Modern Cryptography Rupesh Kumar 1 Sanjay Patel 2 Purushottam
IJSRD - International Journal for Scientific Research & Development Vol. 2, Issue 08, 2014 ISSN (online): 2321-0613 A New Symmetric Key Algorithm for Modern Cryptography Rupesh Kumar 1 Sanjay Patel 2 Purushottam
Creating a Role Playing Game with XNA Game Studio Part 50 Items - Part 4b
 Creating a Role Playing Game with XNA Game Studio Part 50 Items - Part 4b To follow along with this tutorial you will have to have read the previous tutorials to understand much of what it going on. You
Creating a Role Playing Game with XNA Game Studio Part 50 Items - Part 4b To follow along with this tutorial you will have to have read the previous tutorials to understand much of what it going on. You
How do I apply the patch files? The instructions shown here are only for the version patch.
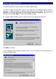 How do I apply the patch files? The instructions shown here are only for the version 10.2.1 patch. 1. Once the patch file has been saved to your hard disk, use Windows Explorer (Start > Programs > Windows
How do I apply the patch files? The instructions shown here are only for the version 10.2.1 patch. 1. Once the patch file has been saved to your hard disk, use Windows Explorer (Start > Programs > Windows
Server Manager User and Permissions Setup
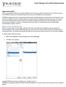 Login and Security Once you successfully create your company databases, the next step is to define the groups and users that can access the TRAVERSE data and the functionality they will have within the
Login and Security Once you successfully create your company databases, the next step is to define the groups and users that can access the TRAVERSE data and the functionality they will have within the
ISP-PACS End User Training Curriculum Page 1
 PACS Training Curriculum End User The following curriculum is an overview limited to the features in Intellispace PACS commonly used. It will provide the foundations of knowledge about Intellispace PACS.
PACS Training Curriculum End User The following curriculum is an overview limited to the features in Intellispace PACS commonly used. It will provide the foundations of knowledge about Intellispace PACS.
Unit 4 Advanced Features of VB.Net
 Dialog Boxes There are many built-in dialog boxes to be used in Windows forms for various tasks like opening and saving files, printing a page, providing choices for colors, fonts, page setup, etc., to
Dialog Boxes There are many built-in dialog boxes to be used in Windows forms for various tasks like opening and saving files, printing a page, providing choices for colors, fonts, page setup, etc., to
Figure 1 Forms category in the Insert panel. You set up a form by inserting it and configuring options through the Properties panel.
 Adobe Dreamweaver CS6 Project 3 guide How to create forms You can use forms to interact with or gather information from site visitors. With forms, visitors can provide feedback, sign a guest book, take
Adobe Dreamweaver CS6 Project 3 guide How to create forms You can use forms to interact with or gather information from site visitors. With forms, visitors can provide feedback, sign a guest book, take
A nice outline of the RSA algorithm and implementation can be found at:
 Cryptography Lab: RSA Encryption and Decryption Lab Objectives: After this lab, the students should be able to Explain the simple concepts of encryption and decryption to protect information in transmission.
Cryptography Lab: RSA Encryption and Decryption Lab Objectives: After this lab, the students should be able to Explain the simple concepts of encryption and decryption to protect information in transmission.
Lecture 3: Symmetric Key Encryption
 Lecture 3: Symmetric Key Encryption CS996: Modern Cryptography Spring 2007 Nitesh Saxena Outline Symmetric Key Encryption Continued Discussion of Potential Project Topics Project proposal due 02/22/07
Lecture 3: Symmetric Key Encryption CS996: Modern Cryptography Spring 2007 Nitesh Saxena Outline Symmetric Key Encryption Continued Discussion of Potential Project Topics Project proposal due 02/22/07
Adding Existing Source Code in NetBeans CS288, Autumn 2005 Lab 002
 Adding Existing Source Code in NetBeans CS288, Autumn 2005 Lab 002 Purpose This document will show how to incorporate existing source code within a NetBeans project. It will also introduce the concept
Adding Existing Source Code in NetBeans CS288, Autumn 2005 Lab 002 Purpose This document will show how to incorporate existing source code within a NetBeans project. It will also introduce the concept
TYX CORPORATION. Productivity Enhancement Systems. PAWS Studio Release Notes
 TYX CORPORATION Productivity Enhancement Systems PAWS Studio Release Notes 1 Version 1.39.10 July 12, 2012 Table of contents 1 Paws Developer's Studio 3 1.1 Critical Items 3 1.2 Known Limitations 3 1.3
TYX CORPORATION Productivity Enhancement Systems PAWS Studio Release Notes 1 Version 1.39.10 July 12, 2012 Table of contents 1 Paws Developer's Studio 3 1.1 Critical Items 3 1.2 Known Limitations 3 1.3
Classic Cryptography: From Caesar to the Hot Line
 Classic Cryptography: From Caesar to the Hot Line Wenyuan Xu Department of Computer Science and Engineering University of South Carolina Overview of the Lecture Overview of Cryptography and Security Classical
Classic Cryptography: From Caesar to the Hot Line Wenyuan Xu Department of Computer Science and Engineering University of South Carolina Overview of the Lecture Overview of Cryptography and Security Classical
L2. An Introduction to Classical Cryptosystems. Rocky K. C. Chang, 23 January 2015
 L2. An Introduction to Classical Cryptosystems Rocky K. C. Chang, 23 January 2015 This and the next set of slides 2 Outline Components of a cryptosystem Some modular arithmetic Some classical ciphers Shift
L2. An Introduction to Classical Cryptosystems Rocky K. C. Chang, 23 January 2015 This and the next set of slides 2 Outline Components of a cryptosystem Some modular arithmetic Some classical ciphers Shift
Cryptography Basics. IT443 Network Security Administration Slides courtesy of Bo Sheng
 Cryptography Basics IT443 Network Security Administration Slides courtesy of Bo Sheng 1 Outline Basic concepts in cryptography systems Secret key cryptography Public key cryptography Hash functions 2 Encryption/Decryption
Cryptography Basics IT443 Network Security Administration Slides courtesy of Bo Sheng 1 Outline Basic concepts in cryptography systems Secret key cryptography Public key cryptography Hash functions 2 Encryption/Decryption
1.264 Lecture 27. Security protocols Symmetric cryptography. Next class: Anderson chapter 10. Exercise due after class
 1.264 Lecture 27 Security protocols Symmetric cryptography Next class: Anderson chapter 10. Exercise due after class 1 Exercise: hotel keys What is the protocol? What attacks are possible? Copy Cut and
1.264 Lecture 27 Security protocols Symmetric cryptography Next class: Anderson chapter 10. Exercise due after class 1 Exercise: hotel keys What is the protocol? What attacks are possible? Copy Cut and
Introduction to Programming in C Department of Computer Science and Engineering. Lecture No. #03 The Programming Cycle
 Introduction to Programming in C Department of Computer Science and Engineering Lecture No. #03 The Programming Cycle (Refer Slide Time: 00:22) Once we are understood what algorithms are, we will start
Introduction to Programming in C Department of Computer Science and Engineering Lecture No. #03 The Programming Cycle (Refer Slide Time: 00:22) Once we are understood what algorithms are, we will start
1 Introduction. ThinPrint Client Installation Page 1
 ThinPrint Client Installation Page 1 1 Introduction In order to reduce the amount of bandwidth used when printing and to improve the overall performance and online experience for the customers that we
ThinPrint Client Installation Page 1 1 Introduction In order to reduce the amount of bandwidth used when printing and to improve the overall performance and online experience for the customers that we
Acknowledgments...xvii. Introduction... Chapter 1: Getting Started Chapter 2: Build a Hi-Lo Guessing Game App!... 19
 Brief Contents Acknowledgments...xvii Introduction... xix Chapter 1: Getting Started... 1 Chapter 2: Build a Hi-Lo Guessing Game App!... 19 Chapter 3: Creating a GUI for Our Guessing Game... 43 Chapter
Brief Contents Acknowledgments...xvii Introduction... xix Chapter 1: Getting Started... 1 Chapter 2: Build a Hi-Lo Guessing Game App!... 19 Chapter 3: Creating a GUI for Our Guessing Game... 43 Chapter
Darshan Institute of Engineering & Technology for Diploma Studies
 Dialog Box: There are many built-in dialog boxes to be used in Windows forms for various tasks like opening and saving files, printing a page, providing choices for colors, fonts, page setup, etc., to
Dialog Box: There are many built-in dialog boxes to be used in Windows forms for various tasks like opening and saving files, printing a page, providing choices for colors, fonts, page setup, etc., to
Block Ciphers Tutorial. c Eli Biham - May 3, Block Ciphers Tutorial (5)
 Block Ciphers Tutorial c Eli Biham - May 3, 2005 146 Block Ciphers Tutorial (5) A Known Plaintext Attack on 1-Round DES After removing the permutations IP and FP we get: L R 48 K=? F L R c Eli Biham -
Block Ciphers Tutorial c Eli Biham - May 3, 2005 146 Block Ciphers Tutorial (5) A Known Plaintext Attack on 1-Round DES After removing the permutations IP and FP we get: L R 48 K=? F L R c Eli Biham -
Assignment #5 The Enigma Machine
 Eric Roberts Handout #37 CS 106J May 15, 2017 Assignment #5 The Enigma Machine Due: Friday, May 26, 5:00 P.M. Note: This assignment may be done in pairs Your task in this assignment is to write a program
Eric Roberts Handout #37 CS 106J May 15, 2017 Assignment #5 The Enigma Machine Due: Friday, May 26, 5:00 P.M. Note: This assignment may be done in pairs Your task in this assignment is to write a program
Lecture 3: The UNIX Style
 CS2042 - UNIX Tools October 3, 2008 Lecture Outline 1 2 Windows Structure Highest-level directory is Desktop Uses C:, D:, etc. to represent different disks/volumes User programs in Program Files, Windows
CS2042 - UNIX Tools October 3, 2008 Lecture Outline 1 2 Windows Structure Highest-level directory is Desktop Uses C:, D:, etc. to represent different disks/volumes User programs in Program Files, Windows
Developer s Tip Print to Scale Feature in Slide
 Developer s Tip Print to Scale Feature in Slide The latest update to Slide 5.0 brings a number of improvements related to printing functionality, giving the user greater control over printed output. Users
Developer s Tip Print to Scale Feature in Slide The latest update to Slide 5.0 brings a number of improvements related to printing functionality, giving the user greater control over printed output. Users
Computer Security. 08r. Pre-exam 2 Last-minute Review Cryptography. Paul Krzyzanowski. Rutgers University. Spring 2018
 Computer Security 08r. Pre-exam 2 Last-minute Review Cryptography Paul Krzyzanowski Rutgers University Spring 2018 March 26, 2018 CS 419 2018 Paul Krzyzanowski 1 Cryptographic Systems March 26, 2018 CS
Computer Security 08r. Pre-exam 2 Last-minute Review Cryptography Paul Krzyzanowski Rutgers University Spring 2018 March 26, 2018 CS 419 2018 Paul Krzyzanowski 1 Cryptographic Systems March 26, 2018 CS
Recap. Definition (Encryption: Caesar Cipher)
 Recap Definition (Encryption: Caesar Cipher) + 3 = mod 26 Recap Definition (Encryption: Caesar Cipher) + 3 = mod 26 Definition (Encryption: Shift Cipher) + d = mod 26, d anumber Recap Definition (Encryption:
Recap Definition (Encryption: Caesar Cipher) + 3 = mod 26 Recap Definition (Encryption: Caesar Cipher) + 3 = mod 26 Definition (Encryption: Shift Cipher) + d = mod 26, d anumber Recap Definition (Encryption:
Introduction to Cryptology Dr. Sugata Gangopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Roorkee
 Introduction to Cryptology Dr. Sugata Gangopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Roorkee Lecture 09 Cryptanalysis and its variants, linear attack Welcome
Introduction to Cryptology Dr. Sugata Gangopadhyay Department of Computer Science and Engineering Indian Institute of Technology, Roorkee Lecture 09 Cryptanalysis and its variants, linear attack Welcome
Working with Printers
 Chapter 17 Working with Printers After completing this chapter, you will be able to: Print graphics from a Microsoft Visual Basic program. Print text from a Visual Basic program. Print multipage documents.
Chapter 17 Working with Printers After completing this chapter, you will be able to: Print graphics from a Microsoft Visual Basic program. Print text from a Visual Basic program. Print multipage documents.
Web Dialogue and Child Page
 Web Dialogue and Child Page Create date: March 3, 2012 Last modified: March 3, 2012 Contents Introduction... 2 Parent Page Programming... 2 Methods... 2 ShowChildDialog... 2 ShowChildWindow... 4 ShowPopupWindow...
Web Dialogue and Child Page Create date: March 3, 2012 Last modified: March 3, 2012 Contents Introduction... 2 Parent Page Programming... 2 Methods... 2 ShowChildDialog... 2 ShowChildWindow... 4 ShowPopupWindow...
James Foxall. Sams Teach Yourself. Visual Basic 2012 *24. Hours. sams. 800 East 96th Street, Indianapolis, Indiana, USA
 James Foxall Sams Teach Yourself Visual Basic 2012 *24 Hours sams 800 East 96th Street, Indianapolis, Indiana, 46240 USA Table of Contents Introduction 1 PART I: The Visual Basic 2012 Environment HOUR
James Foxall Sams Teach Yourself Visual Basic 2012 *24 Hours sams 800 East 96th Street, Indianapolis, Indiana, 46240 USA Table of Contents Introduction 1 PART I: The Visual Basic 2012 Environment HOUR
Principles of Information Security, Fourth Edition. Chapter 8 Cryptography
 Principles of Information Security, Fourth Edition Chapter 8 Cryptography Learning Objectives Upon completion of this material, you should be able to: Chronicle the most significant events and discoveries
Principles of Information Security, Fourth Edition Chapter 8 Cryptography Learning Objectives Upon completion of this material, you should be able to: Chronicle the most significant events and discoveries
CaliberRM 5.1 Integration for Describe Enterprise
 CaliberRM 5.1 Integration for Describe Enterprise Describe Enterprise integration is now available from within the Borland CaliberRM 5.1 software suite. This document describes how to set up and configure
CaliberRM 5.1 Integration for Describe Enterprise Describe Enterprise integration is now available from within the Borland CaliberRM 5.1 software suite. This document describes how to set up and configure
Silverlight memory board ( Part 2 )
 Silverlight memory board ( Part 2 ) In the first part this tutorial we created a new Silverlight project and designed the user interface. In this part, we will add some code to the project to make the
Silverlight memory board ( Part 2 ) In the first part this tutorial we created a new Silverlight project and designed the user interface. In this part, we will add some code to the project to make the
Carrera: Analista de Sistemas/Licenciatura en Sistemas. Asignatura: Programación Orientada a Objetos
 Carrera: / Asignatura: Programación Orientada a Objetos REFACTORING EXERCISE WITH ECLIPSE - 2008- Observation: This refactoring exercise was extracted of the web site indicated in the section Reference
Carrera: / Asignatura: Programación Orientada a Objetos REFACTORING EXERCISE WITH ECLIPSE - 2008- Observation: This refactoring exercise was extracted of the web site indicated in the section Reference
Dreamweaver CS6. Table of Contents. Setting up a site in Dreamweaver! 2. Templates! 3. Using a Template! 3. Save the template! 4. Views!
 Dreamweaver CS6 Table of Contents Setting up a site in Dreamweaver! 2 Templates! 3 Using a Template! 3 Save the template! 4 Views! 5 Properties! 5 Editable Regions! 6 Creating an Editable Region! 6 Modifying
Dreamweaver CS6 Table of Contents Setting up a site in Dreamweaver! 2 Templates! 3 Using a Template! 3 Save the template! 4 Views! 5 Properties! 5 Editable Regions! 6 Creating an Editable Region! 6 Modifying
Implementing and Supporting Windows Intune
 Implementing and Supporting Windows Intune Lab 4: Managing System Services Lab Manual Information in this document, including URL and other Internet Web site references, is subject to change without notice.
Implementing and Supporting Windows Intune Lab 4: Managing System Services Lab Manual Information in this document, including URL and other Internet Web site references, is subject to change without notice.
