TOOLSMITHING AN IDA BRIDGE: A TOOL BUILDING CASE STUDY. Adam Pridgen Matt Wollenweber
|
|
|
- Lewis Singleton
- 6 years ago
- Views:
Transcription
1 TOOLSMITHING AN IDA BRIDGE: A TOOL BUILDING CASE STUDY Adam Pridgen Matt Wollenweber
2 Presentation Agenda Motivation and Purpose Toolsmithing Identifying the short-cuts to meet project needs Processes for Expediting Development Prototyping, Modifying, Testing, Restart?!? Extension development with WinDbg Idabridge demonstration
3 Introductions: Adam TODO Add pertinent Information Who I am. What I have done. Where I am going.
4 Introductions: Matt TODO Add pertinent Information Who I am. What I have done. Where I am going.
5 Motivation and Purpose Learn and teach methods for developing tools Introduce toolsmithing to those interested in tool development Discuss what we learned from implementing our tool Release an Alpha version of our idabridge
6 Toolsmithing Toolsmithing is the process of making tools Tools can be in any space Generally, not a standalone application Ranges from short scripts to full blown libraries Focus on utility not usability Takes on the following forms X is needed to make Y create widgets Z needs to be built, but nothing exists currently
7 Toolsmithing Tools High Level Languages (Python or Ruby) HL Programming Environments (ipython) Debuggers (PDB, WinDbg, Olly, etc.) Network Sniffers for network debugging Books and code lying around the home or net Anything that gets the job done fast
8 Our Toolsmithing Process Building is Believing Loner Development Squads The World is Big Chances are it exists Don t reinvent the wheel, steal one KISS your tools they love you
9 Building is Believing Good tools are not built overnight Sometimes maybe Build it once to get an idea Build it again because the 2 nd time shine Third time is a charm More than one implementation is likely idabridge s cmd handling took 3 iterations Build to what is needed now
10 Loner Development Squads Creating Milestones Milestones should aggregate into something Keep milestones small when developing alone Keep a friend (esp one who cares) on speed dial Writing concise and re-usable Think about what is being developed Make it abstract and re-usable Time is critical, if you can think of anything, just go
11 The World is Big Open Source is the best source for help Code can be reviewed and repurposed Existing code is fantastic for real-world examples Documentation and APIs don t run in debuggers Implementing complex components Building a fuzzer, take someone elses protocol impl. Building a DNS Mapping tool, use BIND for the DNS
12 Introducing idabridge Extensible network listener for IDA Pro Gives IDA users a remote control Implements a async. Network listener Provides extensibility using a Python Class Aims to be a middleware layer for other tools: Binary Diffing Debuggers Other frameworks such as Radare
13 Current State of Tings Users are moving to cloud based solutions Collaboration among analysts and users Federation of data Moving data from whatever to wherever Heterogenous tool chests and chains Employers and contracts Cool tools are developed, but may not leave closed environments
14 Goals and Challenges Investigate cloud based reversing tools Evaluate the feasibility for a middleware for our current tools Determine what tools will make a difference Future direction for supporting technologies Cloud based Python Interpreter Migration of Binaries and environment for analysis
15 Idabridge Components IDA Pro networking client WinDbg network server Python environment Exported from IDAPython Command Handler for Debuggers and IDA Pro VDB/Vtrace WinDbg IDA Pro
16 Tools Used for Development Visual Studio for C/C++ on Windows Debugging a debugger?!? IDE ipython & Python Used to create scripts to write code and classes Functional code testing Data manipulation and verification Server mock-ups to test the initial cmd handling
17 Development Environments Windows 7, 64-bit VS 2010 IPython Windows XP VM, 32-bit VS 2010
18 Overall Lessons Learned Debugging Debuggers Write Scripts to Implement code Parsing IDAPython APIs Implementing Python Command Handlers Writing Long Logic C++ Statements Creating Stub Functions
19 Toolsmithing: Research Phase Initial Research and Development: 90 Hours Researching code and capabilities (IDA Pro and WinDbg) Learning APIs and how to use them Planning, Testing, Adjusting Includes Coding and Testing Created a GUI to simulate a debugger Implemented IDA Commands Manually Using C++ only Implemented Separate Command Handling on Platforms Mostly Get it working phase
20 Toolsmithing: Research Phase Lessons Learned Write scripts to write code and functions Wrote a dumb server to send and reply to msg.s Documentation is not your friend find examples Find examples that have been repeated
21 Toolsmithing: Phase 2 Defcon Talk accepted, resumed development Development: 60 Hours (2 weeks) Developed an Abstract Cmd Handler Based on Names Included Typed Argument Marshaling (str, int, long, byte) Combined the Network Stack and Handling Never tested and threw out most of the code Realized atm there was no added value Breakthrough was the command handling Combined source and functionality
22 Toolsmithing: Cmd Handler Development: 30 Hours (1.5 weeks) Developed the abstract handler Added IDAPython Bridge to the mix Figured out how to add IDA Python Bridging
23 Toolsmithing: Cmd Handler Development: 20 Hours Added Python as the Main Command Handling Co-Developed Vtrace/VDB command handling
24 Idabridge Demonstration
25 Conclusions Creativity, Patience, Persistence, and Tenacity Motivation relies on small milestones Expectations are limited by time frame Tool Code quality!= production CQ <FINAL PROJECT Data>
26 Idabridge information Special Thanks To: Praetorian C. Eagle and T. Vidas for Collabreate E. Erdelyi for IDAPython Pusscat / Lin0xx for Byakugan Code URL Presentation URL
27 Questions & Comments thecoverofnight.com praetorian.com]
T Hands-on 2. User-mode debuggers OllyDbg
 T-110.6220 Hands-on 2 User-mode debuggers OllyDbg Disassemblers vs debuggers Static analysis / Disassemblers Theoretic approach Give us a static view of the binary Example: IDA Dynamic analysis / Debuggers
T-110.6220 Hands-on 2 User-mode debuggers OllyDbg Disassemblers vs debuggers Static analysis / Disassemblers Theoretic approach Give us a static view of the binary Example: IDA Dynamic analysis / Debuggers
Diaphora An IDA Python BinDiffing plugin
 Diaphora An IDA Python BinDiffing plugin Index Introduction...2 Files distributed with the diaphora distribution...2 Running Diaphora...2 Diaphora quick start...4 Finding differences in new versions (Patch
Diaphora An IDA Python BinDiffing plugin Index Introduction...2 Files distributed with the diaphora distribution...2 Running Diaphora...2 Diaphora quick start...4 Finding differences in new versions (Patch
In-Memory Fuzzing in JAVA
 Your texte here. In-Memory Fuzzing in JAVA 2012.12.17 Xavier ROUSSEL Summary I. What is Fuzzing? Your texte here. Introduction Fuzzing process Targets Inputs vectors Data generation Target monitoring Advantages
Your texte here. In-Memory Fuzzing in JAVA 2012.12.17 Xavier ROUSSEL Summary I. What is Fuzzing? Your texte here. Introduction Fuzzing process Targets Inputs vectors Data generation Target monitoring Advantages
Who am I? I m a python developer who has been working on OpenStack since I currently work for Aptira, who do OpenStack, SDN, and orchestration
 Who am I? I m a python developer who has been working on OpenStack since 2011. I currently work for Aptira, who do OpenStack, SDN, and orchestration consulting. I m here today to help you learn from my
Who am I? I m a python developer who has been working on OpenStack since 2011. I currently work for Aptira, who do OpenStack, SDN, and orchestration consulting. I m here today to help you learn from my
Programming Robots with ROS, Morgan Quigley, Brian Gerkey & William D. Smart
 Programming Robots with ROS, Morgan Quigley, Brian Gerkey & William D. Smart O Reilly December 2015 CHAPTER 23 Using C++ in ROS We chose to use Python for this book for a number of reasons. First, it s
Programming Robots with ROS, Morgan Quigley, Brian Gerkey & William D. Smart O Reilly December 2015 CHAPTER 23 Using C++ in ROS We chose to use Python for this book for a number of reasons. First, it s
Profilers and Debuggers. Introductory Material. One-Slide Summary
 Profilers and Debuggers #1 Introductory Material First, who doesn t know assembly language? You ll get to answer all the assembly questions. Yes, really. Lecture Style: Sit on the table and pose questions.
Profilers and Debuggers #1 Introductory Material First, who doesn t know assembly language? You ll get to answer all the assembly questions. Yes, really. Lecture Style: Sit on the table and pose questions.
CS 220: Introduction to Parallel Computing. Arrays. Lecture 4
 CS 220: Introduction to Parallel Computing Arrays Lecture 4 Note: Windows I updated the VM image on the website It now includes: Sublime text Gitkraken (a nice git GUI) And the git command line tools 1/30/18
CS 220: Introduction to Parallel Computing Arrays Lecture 4 Note: Windows I updated the VM image on the website It now includes: Sublime text Gitkraken (a nice git GUI) And the git command line tools 1/30/18
Boot Camp. Dave Eckhardt Bruce Maggs
 Boot Camp Dave Eckhardt de0u@andrew.cmu.edu Bruce Maggs bmm@cs.cmu.edu 1 This Is a Hard Class Traditional hazards 410 letter grade one lower than other classes All other classes this semester: one grade
Boot Camp Dave Eckhardt de0u@andrew.cmu.edu Bruce Maggs bmm@cs.cmu.edu 1 This Is a Hard Class Traditional hazards 410 letter grade one lower than other classes All other classes this semester: one grade
MEAP Edition Manning Early Access Program Get Programming with Java Version 1
 MEAP Edition Manning Early Access Program Get Programming with Java Version 1 Copyright 2018 Manning Publications For more information on this and other Manning titles go to www.manning.com welcome First,
MEAP Edition Manning Early Access Program Get Programming with Java Version 1 Copyright 2018 Manning Publications For more information on this and other Manning titles go to www.manning.com welcome First,
C 1. Recap: Finger Table. CSE 486/586 Distributed Systems Remote Procedure Call. Chord: Node Joins and Leaves. Recall? Socket API
 Recap: Finger Table Finding a using fingers CSE 486/586 Distributed Systems Remote Procedure Call Steve Ko Computer Sciences and Engineering University at Buffalo N102" 86 + 2 4! N86" 20 +
Recap: Finger Table Finding a using fingers CSE 486/586 Distributed Systems Remote Procedure Call Steve Ko Computer Sciences and Engineering University at Buffalo N102" 86 + 2 4! N86" 20 +
Autosave for Research Where to Start with Checkpoint/Restart
 Autosave for Research Where to Start with Checkpoint/Restart Brandon Barker Computational Scientist Cornell University Center for Advanced Computing (CAC) brandon.barker@cornell.edu Workshop: High Performance
Autosave for Research Where to Start with Checkpoint/Restart Brandon Barker Computational Scientist Cornell University Center for Advanced Computing (CAC) brandon.barker@cornell.edu Workshop: High Performance
12/3/ Introduction to CenterStage Spaces and roles. My Community My Spaces, My Favorite Spaces
 Introduction to CenterStage Spaces and roles My Community My Spaces, My Favorite Spaces Inside the space Navigate, watch, share Files Open, import, edit, tag, copy, share Communication tools Wikis, blogs,
Introduction to CenterStage Spaces and roles My Community My Spaces, My Favorite Spaces Inside the space Navigate, watch, share Files Open, import, edit, tag, copy, share Communication tools Wikis, blogs,
Notes from a Short Introductory Lecture on Scala (Based on Programming in Scala, 2nd Ed.)
 Notes from a Short Introductory Lecture on Scala (Based on Programming in Scala, 2nd Ed.) David Haraburda January 30, 2013 1 Introduction Scala is a multi-paradigm language that runs on the JVM (is totally
Notes from a Short Introductory Lecture on Scala (Based on Programming in Scala, 2nd Ed.) David Haraburda January 30, 2013 1 Introduction Scala is a multi-paradigm language that runs on the JVM (is totally
Reverse Engineering with IDA Pro. CS4379/5375 Software Reverse Engineering Dr. Jaime C. Acosta
 1 Reverse Engineering with IDA Pro CS4379/5375 Software Reverse Engineering Dr. Jaime C. Acosta 2 Reversing Techniques Static Analysis Dynamic Analysis 3 Reversing Techniques Static Analysis (e.g., strings,
1 Reverse Engineering with IDA Pro CS4379/5375 Software Reverse Engineering Dr. Jaime C. Acosta 2 Reversing Techniques Static Analysis Dynamic Analysis 3 Reversing Techniques Static Analysis (e.g., strings,
GNU Radio Technical Update
 GNU Radio Technical Update Johnathan Corgan GRCON17 GRCON17 GNU GNU Radio Radio Technical Technical Update Update September September 2017 2017 Topics Release 3.8 Features and capabilities Milestones and
GNU Radio Technical Update Johnathan Corgan GRCON17 GRCON17 GNU GNU Radio Radio Technical Technical Update Update September September 2017 2017 Topics Release 3.8 Features and capabilities Milestones and
1.1 For Fun and Profit. 1.2 Common Techniques. My Preferred Techniques
 1 Bug Hunting Bug hunting is the process of finding bugs in software or hardware. In this book, however, the term bug hunting will be used specifically to describe the process of finding security-critical
1 Bug Hunting Bug hunting is the process of finding bugs in software or hardware. In this book, however, the term bug hunting will be used specifically to describe the process of finding security-critical
Next Generation Collaborative Reversing with Ida Pro and CollabREate. Chris Eagle and Tim Vidas Naval Postgraduate School
 Next Generation Collaborative Reversing with Ida Pro and CollabREate Chris Eagle and Tim Vidas Naval Postgraduate School Shameless Plug Coming soon to finer book stores Prepare for Demo Blackhat demo package
Next Generation Collaborative Reversing with Ida Pro and CollabREate Chris Eagle and Tim Vidas Naval Postgraduate School Shameless Plug Coming soon to finer book stores Prepare for Demo Blackhat demo package
02291: System Integration
 02291: System Integration Hubert Baumeister hub@imm.dtu.dk Spring 2011 Contents 1 Recap 1 2 More UML Diagrams 2 2.1 Object Diagrams........................................... 2 2.2 Communication Diagrams......................................
02291: System Integration Hubert Baumeister hub@imm.dtu.dk Spring 2011 Contents 1 Recap 1 2 More UML Diagrams 2 2.1 Object Diagrams........................................... 2 2.2 Communication Diagrams......................................
Debugging Your Python Code: For Dummies
 Debugging Your Python Code: For Dummies Tyler J. Metivier University of Connecticut Dept. of Physics May 4, 2018 1 What s the problem? It doesn t matter if you ve written 1 script or programmed a space
Debugging Your Python Code: For Dummies Tyler J. Metivier University of Connecticut Dept. of Physics May 4, 2018 1 What s the problem? It doesn t matter if you ve written 1 script or programmed a space
Alan J. Perlis - Epigrams on Programming
 Programming Languages (CS302 2007S) Alan J. Perlis - Epigrams on Programming Comments on: Perlis, Alan J. (1982). Epigrams on Programming. ACM SIGPLAN Notices 17(9), September 1982, pp. 7-13. 1. One man
Programming Languages (CS302 2007S) Alan J. Perlis - Epigrams on Programming Comments on: Perlis, Alan J. (1982). Epigrams on Programming. ACM SIGPLAN Notices 17(9), September 1982, pp. 7-13. 1. One man
Introducing Computer Programming
 ok4 01 f2 5/24/17 9:59 AM Page 3 Chapter 1 Introducing Computer Programming Intended Learning Outcomes After completing this chapter, you should be able to: Explain the difference between computers and
ok4 01 f2 5/24/17 9:59 AM Page 3 Chapter 1 Introducing Computer Programming Intended Learning Outcomes After completing this chapter, you should be able to: Explain the difference between computers and
Designing largescale applications. in Python. EuroPython 2013 Florence, Italy. Marc-André Lemburg
 Designing largescale applications in Python Florence, Italy Marc-André Lemburg (c) 2013 egenix.com com Software GmbH, info@egenix.com 2 Agenda 1. Introduction 2. Application Design 3. Before you start...
Designing largescale applications in Python Florence, Italy Marc-André Lemburg (c) 2013 egenix.com com Software GmbH, info@egenix.com 2 Agenda 1. Introduction 2. Application Design 3. Before you start...
Hidden Gems in JD Edwards Orchestrator and AIS Server
 Hidden Gems in JD Edwards Orchestrator and AIS Server Darryl Shakespeare Senior Director Product Development Oracle JD Edwards EnterpriseOne November 12-17, 2017 Safe Harbor Statement The following is
Hidden Gems in JD Edwards Orchestrator and AIS Server Darryl Shakespeare Senior Director Product Development Oracle JD Edwards EnterpriseOne November 12-17, 2017 Safe Harbor Statement The following is
Distributed Systems. How do regular procedure calls work in programming languages? Problems with sockets RPC. Regular procedure calls
 Problems with sockets Distributed Systems Sockets interface is straightforward [connect] read/write [disconnect] Remote Procedure Calls BUT it forces read/write mechanism We usually use a procedure call
Problems with sockets Distributed Systems Sockets interface is straightforward [connect] read/write [disconnect] Remote Procedure Calls BUT it forces read/write mechanism We usually use a procedure call
Holberton takes on full-stack software engineering with a project based approach, we have a mission to cultivate community and encourage innovation.
 Syllabus - Year 1 Holberton takes on full-stack software engineering with a project based approach, we have a mission to cultivate community and encourage innovation. Our syllabus walks through the major
Syllabus - Year 1 Holberton takes on full-stack software engineering with a project based approach, we have a mission to cultivate community and encourage innovation. Our syllabus walks through the major
Learning vrealize Orchestrator in action V M U G L A B
 Learning vrealize Orchestrator in action V M U G L A B Lab Learning vrealize Orchestrator in action Code examples If you don t feel like typing the code you can download it from the webserver running on
Learning vrealize Orchestrator in action V M U G L A B Lab Learning vrealize Orchestrator in action Code examples If you don t feel like typing the code you can download it from the webserver running on
The COS 333 Project. Robert M. Dondero, Ph.D. Princeton University
 The COS 333 Project Robert M. Dondero, Ph.D. Princeton University 1 Overview A simulation of reality In groups of 3-5 people... Build a substantial three tier software system 2 Three-Tier Systems "Three
The COS 333 Project Robert M. Dondero, Ph.D. Princeton University 1 Overview A simulation of reality In groups of 3-5 people... Build a substantial three tier software system 2 Three-Tier Systems "Three
Blended Learning Outline: Cloudera Data Analyst Training (171219a)
 Blended Learning Outline: Cloudera Data Analyst Training (171219a) Cloudera Univeristy s data analyst training course will teach you to apply traditional data analytics and business intelligence skills
Blended Learning Outline: Cloudera Data Analyst Training (171219a) Cloudera Univeristy s data analyst training course will teach you to apply traditional data analytics and business intelligence skills
CSE : Python Programming
 CSE 399-004: Python Programming Lecture 08: Graphical User Interfaces with wxpython March 12, 2005 http://www.seas.upenn.edu/~cse39904/ Plan for today and next time Today: wxpython (part 1) Aside: Arguments
CSE 399-004: Python Programming Lecture 08: Graphical User Interfaces with wxpython March 12, 2005 http://www.seas.upenn.edu/~cse39904/ Plan for today and next time Today: wxpython (part 1) Aside: Arguments
Checkpointing using DMTCP, Condor, Matlab and FReD
 Checkpointing using DMTCP, Condor, Matlab and FReD Gene Cooperman (presenting) High Performance Computing Laboratory College of Computer and Information Science Northeastern University, Boston gene@ccs.neu.edu
Checkpointing using DMTCP, Condor, Matlab and FReD Gene Cooperman (presenting) High Performance Computing Laboratory College of Computer and Information Science Northeastern University, Boston gene@ccs.neu.edu
Outline. Background. Motivation. Developer meetings. Meeting outcome. Marcus Oskarsson Page 2
 1 Outline Background Motivation Developer meetings Meeting outcome Page 2 UI API - Background Matias gave a talk less is more at the last meeting (http://mxcube.github.io/mxcube/doc/meetings_2018_diamond/mxcubemeeting_dls_lessismore.pdf)
1 Outline Background Motivation Developer meetings Meeting outcome Page 2 UI API - Background Matias gave a talk less is more at the last meeting (http://mxcube.github.io/mxcube/doc/meetings_2018_diamond/mxcubemeeting_dls_lessismore.pdf)
Semantic Analysis. Lecture 9. February 7, 2018
 Semantic Analysis Lecture 9 February 7, 2018 Midterm 1 Compiler Stages 12 / 14 COOL Programming 10 / 12 Regular Languages 26 / 30 Context-free Languages 17 / 21 Parsing 20 / 23 Extra Credit 4 / 6 Average
Semantic Analysis Lecture 9 February 7, 2018 Midterm 1 Compiler Stages 12 / 14 COOL Programming 10 / 12 Regular Languages 26 / 30 Context-free Languages 17 / 21 Parsing 20 / 23 Extra Credit 4 / 6 Average
PYTHON TRAINING COURSE CONTENT
 SECTION 1: INTRODUCTION What s python? Why do people use python? Some quotable quotes A python history lesson Advocacy news What s python good for? What s python not good for? The compulsory features list
SECTION 1: INTRODUCTION What s python? Why do people use python? Some quotable quotes A python history lesson Advocacy news What s python good for? What s python not good for? The compulsory features list
Oracle SQL Developer & REST Data Services
 Oracle SQL Developer & REST Data Services What s New Jeff Smith Senior Principal Product Manager Database Development Tools Jeff.d.smith@oracle.com @thatjeffsmith http://www.thatjeffsmith.com Agenda New
Oracle SQL Developer & REST Data Services What s New Jeff Smith Senior Principal Product Manager Database Development Tools Jeff.d.smith@oracle.com @thatjeffsmith http://www.thatjeffsmith.com Agenda New
Last Class: OS and Computer Architecture. Last Class: OS and Computer Architecture
 Last Class: OS and Computer Architecture System bus Network card CPU, memory, I/O devices, network card, system bus Lecture 4, page 1 Last Class: OS and Computer Architecture OS Service Protection Interrupts
Last Class: OS and Computer Architecture System bus Network card CPU, memory, I/O devices, network card, system bus Lecture 4, page 1 Last Class: OS and Computer Architecture OS Service Protection Interrupts
Introduction to Programming System Design CSCI 455x (4 Units)
 Introduction to Programming System Design CSCI 455x (4 Units) Description This course covers programming in Java and C++. Topics include review of basic programming concepts such as control structures,
Introduction to Programming System Design CSCI 455x (4 Units) Description This course covers programming in Java and C++. Topics include review of basic programming concepts such as control structures,
CME 193: Introduction to Scientific Python Lecture 1: Introduction
 CME 193: Introduction to Scientific Python Lecture 1: Introduction Nolan Skochdopole stanford.edu/class/cme193 1: Introduction 1-1 Contents Administration Introduction Basics Variables Control statements
CME 193: Introduction to Scientific Python Lecture 1: Introduction Nolan Skochdopole stanford.edu/class/cme193 1: Introduction 1-1 Contents Administration Introduction Basics Variables Control statements
CMPSCI 187 / Spring 2015 Postfix Expression Evaluator
 CMPSCI 187 / Spring 2015 Postfix Expression Evaluator Due on Thursday, 05 March, 8:30 a.m. Marc Liberatore and John Ridgway Morrill I N375 Section 01 @ 10:00 Section 02 @ 08:30 1 CMPSCI 187 / Spring 2015
CMPSCI 187 / Spring 2015 Postfix Expression Evaluator Due on Thursday, 05 March, 8:30 a.m. Marc Liberatore and John Ridgway Morrill I N375 Section 01 @ 10:00 Section 02 @ 08:30 1 CMPSCI 187 / Spring 2015
INSIDE THE ULTIMA ONLINE CLIENT - INSERTING A SLEEP
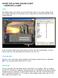 INSIDE THE ULTIMA ONLINE CLIENT - INSERTING A SLEEP GOAL The Ultima Online client utilizes too much CPU power when it s not doing anything useful. For example, when we are at the logon screen or when we
INSIDE THE ULTIMA ONLINE CLIENT - INSERTING A SLEEP GOAL The Ultima Online client utilizes too much CPU power when it s not doing anything useful. For example, when we are at the logon screen or when we
Today s Agenda. Today s Agenda 9/8/17. Networking and Messaging
 CS 686: Special Topics in Big Data Networking and Messaging Lecture 7 Today s Agenda Project 1 Updates Networking topics in Big Data Message formats and serialization techniques CS 686: Big Data 2 Today
CS 686: Special Topics in Big Data Networking and Messaging Lecture 7 Today s Agenda Project 1 Updates Networking topics in Big Data Message formats and serialization techniques CS 686: Big Data 2 Today
Week - 01 Lecture - 04 Downloading and installing Python
 Programming, Data Structures and Algorithms in Python Prof. Madhavan Mukund Department of Computer Science and Engineering Indian Institute of Technology, Madras Week - 01 Lecture - 04 Downloading and
Programming, Data Structures and Algorithms in Python Prof. Madhavan Mukund Department of Computer Science and Engineering Indian Institute of Technology, Madras Week - 01 Lecture - 04 Downloading and
Elliotte Rusty Harold August From XML to Flat Buffers: Markup in the Twenty-teens
 Elliotte Rusty Harold elharo@ibiblio.org August 2018 From XML to Flat Buffers: Markup in the Twenty-teens Warning! The Contenders XML JSON YAML EXI Protobufs Flat Protobufs XML JSON YAML EXI Protobuf Flat
Elliotte Rusty Harold elharo@ibiblio.org August 2018 From XML to Flat Buffers: Markup in the Twenty-teens Warning! The Contenders XML JSON YAML EXI Protobufs Flat Protobufs XML JSON YAML EXI Protobuf Flat
Luigi Build Data Pipelines of batch jobs. - Pramod Toraskar
 Luigi Build Data Pipelines of batch jobs - Pramod Toraskar I am a Principal Solution Engineer & Pythonista with more than 8 years of work experience, Works for a Red Hat India an open source solutions
Luigi Build Data Pipelines of batch jobs - Pramod Toraskar I am a Principal Solution Engineer & Pythonista with more than 8 years of work experience, Works for a Red Hat India an open source solutions
Language Translation. Compilation vs. interpretation. Compilation diagram. Step 1: compile. Step 2: run. compiler. Compiled program. program.
 Language Translation Compilation vs. interpretation Compilation diagram Step 1: compile program compiler Compiled program Step 2: run input Compiled program output Language Translation compilation is translation
Language Translation Compilation vs. interpretation Compilation diagram Step 1: compile program compiler Compiled program Step 2: run input Compiled program output Language Translation compilation is translation
Web Application Expectations
 Effective Ruby on Rails Development Using CodeGear s Ruby IDE Shelby Sanders Principal Engineer CodeGear Copyright 2007 CodeGear. All Rights Reserved. 2007/6/14 Web Application Expectations Dynamic Static
Effective Ruby on Rails Development Using CodeGear s Ruby IDE Shelby Sanders Principal Engineer CodeGear Copyright 2007 CodeGear. All Rights Reserved. 2007/6/14 Web Application Expectations Dynamic Static
DSD-Tracer. Boris Lau, SophosLabs Virus Bulletin 2007, Vienna
 DSD-Tracer Boris Lau, SophosLabs Virus Bulletin 2007, Vienna What does DSD stand for? Dynamic Static DSD A framework which allows data to be passed between dynamic and static analysis stages seamlessly
DSD-Tracer Boris Lau, SophosLabs Virus Bulletin 2007, Vienna What does DSD stand for? Dynamic Static DSD A framework which allows data to be passed between dynamic and static analysis stages seamlessly
L4/Darwin: Evolving UNIX. Charles Gray Research Engineer, National ICT Australia
 L4/Darwin: Evolving UNIX Charles Gray Research Engineer, National ICT Australia charles.gray@nicta.com.au Outline 1. Project Overview 2. BSD on the Mach microkernel 3. Porting Darwin to the L4 microkernel
L4/Darwin: Evolving UNIX Charles Gray Research Engineer, National ICT Australia charles.gray@nicta.com.au Outline 1. Project Overview 2. BSD on the Mach microkernel 3. Porting Darwin to the L4 microkernel
CptS 360 (System Programming) Unit 2: Introduction to UNIX and Linux
 CptS 360 (System Programming) Unit 2: Introduction to UNIX and Linux Bob Lewis School of Engineering and Applied Sciences Washington State University Spring, 2018 Motivation APIs have a history: Learn
CptS 360 (System Programming) Unit 2: Introduction to UNIX and Linux Bob Lewis School of Engineering and Applied Sciences Washington State University Spring, 2018 Motivation APIs have a history: Learn
Which tools should you use to design? DESIGN FUNDAMENTALS
 Which tools should you use to design? DESIGN FUNDAMENTALS VS. Software Browser Software Pros Software Pros What you see is what you get What you see is what you get More likely to push the boundaries of
Which tools should you use to design? DESIGN FUNDAMENTALS VS. Software Browser Software Pros Software Pros What you see is what you get What you see is what you get More likely to push the boundaries of
Enterprise Architect. User Guide Series. Profiling
 Enterprise Architect User Guide Series Profiling Investigating application performance? The Sparx Systems Enterprise Architect Profiler finds the actions and their functions that are consuming the application,
Enterprise Architect User Guide Series Profiling Investigating application performance? The Sparx Systems Enterprise Architect Profiler finds the actions and their functions that are consuming the application,
Enterprise Architect. User Guide Series. Profiling. Author: Sparx Systems. Date: 10/05/2018. Version: 1.0 CREATED WITH
 Enterprise Architect User Guide Series Profiling Author: Sparx Systems Date: 10/05/2018 Version: 1.0 CREATED WITH Table of Contents Profiling 3 System Requirements 8 Getting Started 9 Call Graph 11 Stack
Enterprise Architect User Guide Series Profiling Author: Sparx Systems Date: 10/05/2018 Version: 1.0 CREATED WITH Table of Contents Profiling 3 System Requirements 8 Getting Started 9 Call Graph 11 Stack
LLDB for your hardware: Remote Debugging the Hexagon DSP
 LLDB for your hardware: Remote Debugging the Hexagon DSP Colin Riley Games Technology Director 1 Outline Introductions Adapting LLDB for your hardware The Why and How? The 3 steps Summary Q&A 2 Introductions
LLDB for your hardware: Remote Debugging the Hexagon DSP Colin Riley Games Technology Director 1 Outline Introductions Adapting LLDB for your hardware The Why and How? The 3 steps Summary Q&A 2 Introductions
EVENT-DRIVEN PROGRAMMING
 LESSON 13 EVENT-DRIVEN PROGRAMMING This lesson shows how to package JavaScript code into self-defined functions. The code in a function is not executed until the function is called upon by name. This is
LESSON 13 EVENT-DRIVEN PROGRAMMING This lesson shows how to package JavaScript code into self-defined functions. The code in a function is not executed until the function is called upon by name. This is
State of the Port to x86_64 July 2017
 State of the Port to x86_64 July 2017 July 7, 2017 Update Topics Executive Summary Development Plan Release Plan Engineering Details Compilers Objects & Images Binary Translator Early Boot Path Boot Manager
State of the Port to x86_64 July 2017 July 7, 2017 Update Topics Executive Summary Development Plan Release Plan Engineering Details Compilers Objects & Images Binary Translator Early Boot Path Boot Manager
From theory to practice: Standard tools Software carpentry, Part II. Pietro Berkes, Brandeis University
 From theory to practice: Standard tools Software carpentry, Part II Pietro Berkes, Brandeis University Outline Collaborating: SVN Profiling: timeit, cprofile Debugging: pdb Documentation, code clarity:
From theory to practice: Standard tools Software carpentry, Part II Pietro Berkes, Brandeis University Outline Collaborating: SVN Profiling: timeit, cprofile Debugging: pdb Documentation, code clarity:
Mitchell Adair January, 2014
 Mitchell Adair January, 2014 Know Owen from our time at Sandia National Labs Currently work for Raytheon Founded UTDallas s Computer Security Group (CSG) in Spring 2010 Reversing, binary auditing, fuzzing,
Mitchell Adair January, 2014 Know Owen from our time at Sandia National Labs Currently work for Raytheon Founded UTDallas s Computer Security Group (CSG) in Spring 2010 Reversing, binary auditing, fuzzing,
CHAPTER 2: SYSTEM STRUCTURES. By I-Chen Lin Textbook: Operating System Concepts 9th Ed.
 CHAPTER 2: SYSTEM STRUCTURES By I-Chen Lin Textbook: Operating System Concepts 9th Ed. Chapter 2: System Structures Operating System Services User Operating System Interface System Calls Types of System
CHAPTER 2: SYSTEM STRUCTURES By I-Chen Lin Textbook: Operating System Concepts 9th Ed. Chapter 2: System Structures Operating System Services User Operating System Interface System Calls Types of System
CS Programming Languages: Python
 CS 3101-1 - Programming Languages: Python Lecture 5: Exceptions / Daniel Bauer (bauer@cs.columbia.edu) October 08 2014 Daniel Bauer CS3101-1 Python - 05 - Exceptions / 1/35 Contents Exceptions Daniel Bauer
CS 3101-1 - Programming Languages: Python Lecture 5: Exceptions / Daniel Bauer (bauer@cs.columbia.edu) October 08 2014 Daniel Bauer CS3101-1 Python - 05 - Exceptions / 1/35 Contents Exceptions Daniel Bauer
What do we actually care about? Charles Edge Jamf :: krypted.com :: MacAdmins Podcast
 What do we actually care about? Charles Edge Jamf :: krypted.com :: MacAdmins Podcast A good reason to complain! Who builds the tools of the future? Those with the domain knowledge What do we care about?
What do we actually care about? Charles Edge Jamf :: krypted.com :: MacAdmins Podcast A good reason to complain! Who builds the tools of the future? Those with the domain knowledge What do we care about?
Middleware. Adapted from Alonso, Casati, Kuno, Machiraju Web Services Springer 2004
 Middleware Adapted from Alonso, Casati, Kuno, Machiraju Web Services Springer 2004 Outline Web Services Goals Where do they come from? Understanding middleware Middleware as infrastructure Communication
Middleware Adapted from Alonso, Casati, Kuno, Machiraju Web Services Springer 2004 Outline Web Services Goals Where do they come from? Understanding middleware Middleware as infrastructure Communication
GOOGLE APPS. GETTING STARTED Page 02 Prerequisites What You Will Learn. INTRODUCTION Page 03 What is Google? SETTING UP AN ACCOUNT Page 03 Gmail
 GOOGLE APPS GETTING STARTED Page 02 Prerequisites What You Will Learn INTRODUCTION Page 03 What is Google? SETTING UP AN ACCOUNT Page 03 Gmail DRIVE Page 07 Uploading Files to Google Drive Sharing/Unsharing
GOOGLE APPS GETTING STARTED Page 02 Prerequisites What You Will Learn INTRODUCTION Page 03 What is Google? SETTING UP AN ACCOUNT Page 03 Gmail DRIVE Page 07 Uploading Files to Google Drive Sharing/Unsharing
Important From Last Time
 Important From Last Time Embedded C Ø Pros and cons Macros and how to avoid them Intrinsics Interrupt syntax Inline assembly Today Advanced C What C programs mean How to create C programs that mean nothing
Important From Last Time Embedded C Ø Pros and cons Macros and how to avoid them Intrinsics Interrupt syntax Inline assembly Today Advanced C What C programs mean How to create C programs that mean nothing
Getting Started. Excerpted from Hello World! Computer Programming for Kids and Other Beginners
 Getting Started Excerpted from Hello World! Computer Programming for Kids and Other Beginners EARLY ACCESS EDITION Warren D. Sande and Carter Sande MEAP Release: May 2008 Softbound print: November 2008
Getting Started Excerpted from Hello World! Computer Programming for Kids and Other Beginners EARLY ACCESS EDITION Warren D. Sande and Carter Sande MEAP Release: May 2008 Softbound print: November 2008
Lesson 13 Transcript: User-Defined Functions
 Lesson 13 Transcript: User-Defined Functions Slide 1: Cover Welcome to Lesson 13 of DB2 ON CAMPUS LECTURE SERIES. Today, we are going to talk about User-defined Functions. My name is Raul Chong, and I'm
Lesson 13 Transcript: User-Defined Functions Slide 1: Cover Welcome to Lesson 13 of DB2 ON CAMPUS LECTURE SERIES. Today, we are going to talk about User-defined Functions. My name is Raul Chong, and I'm
Hello World! Computer Programming for Kids and Other Beginners. Chapter 1. by Warren Sande and Carter Sande. Copyright 2009 Manning Publications
 Hello World! Computer Programming for Kids and Other Beginners by Warren Sande and Carter Sande Chapter 1 Copyright 2009 Manning Publications brief contents Preface xiii Acknowledgments xix About this
Hello World! Computer Programming for Kids and Other Beginners by Warren Sande and Carter Sande Chapter 1 Copyright 2009 Manning Publications brief contents Preface xiii Acknowledgments xix About this
Most of the class will focus on if/else statements and the logical statements ("conditionals") that are used to build them. Then I'll go over a few
 With notes! 1 Most of the class will focus on if/else statements and the logical statements ("conditionals") that are used to build them. Then I'll go over a few useful functions (some built into standard
With notes! 1 Most of the class will focus on if/else statements and the logical statements ("conditionals") that are used to build them. Then I'll go over a few useful functions (some built into standard
SERIOUS ABOUT SOFTWARE. Qt Core features. Timo Strömmer, May 26,
 SERIOUS ABOUT SOFTWARE Qt Core features Timo Strömmer, May 26, 2010 1 Contents C++ refresher Core features Object model Signals & slots Event loop Shared data Strings Containers Private implementation
SERIOUS ABOUT SOFTWARE Qt Core features Timo Strömmer, May 26, 2010 1 Contents C++ refresher Core features Object model Signals & slots Event loop Shared data Strings Containers Private implementation
It was a dark and stormy night. Seriously. There was a rain storm in Wisconsin, and the line noise dialing into the Unix machines was bad enough to
 1 2 It was a dark and stormy night. Seriously. There was a rain storm in Wisconsin, and the line noise dialing into the Unix machines was bad enough to keep putting garbage characters into the command
1 2 It was a dark and stormy night. Seriously. There was a rain storm in Wisconsin, and the line noise dialing into the Unix machines was bad enough to keep putting garbage characters into the command
Lab 4: Interrupts and Realtime
 Lab 4: Interrupts and Realtime Overview At this point, we have learned the basics of how to write kernel driver module, and we wrote a driver kernel module for the LCD+shift register. Writing kernel driver
Lab 4: Interrupts and Realtime Overview At this point, we have learned the basics of how to write kernel driver module, and we wrote a driver kernel module for the LCD+shift register. Writing kernel driver
Practical Malware Analysis
 Practical Malware Analysis Ch 4: A Crash Course in x86 Disassembly Revised 1-16-7 Basic Techniques Basic static analysis Looks at malware from the outside Basic dynamic analysis Only shows you how the
Practical Malware Analysis Ch 4: A Crash Course in x86 Disassembly Revised 1-16-7 Basic Techniques Basic static analysis Looks at malware from the outside Basic dynamic analysis Only shows you how the
Information Security II Prof. Kamakoti Department of Computer Science and Engineering Indian Institute of Technology, Madras
 Information Security II Prof. Kamakoti Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 30 Task Switch recap - Week 6 (Refer Slide Time: 00:09) So welcome back
Information Security II Prof. Kamakoti Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 30 Task Switch recap - Week 6 (Refer Slide Time: 00:09) So welcome back
Adding content to your Blackboard 9.1 class
 Adding content to your Blackboard 9.1 class There are quite a few options listed when you click the Build Content button in your class, but you ll probably only use a couple of them most of the time. Note
Adding content to your Blackboard 9.1 class There are quite a few options listed when you click the Build Content button in your class, but you ll probably only use a couple of them most of the time. Note
Nathan Rittenhouse
 Nathan Rittenhouse nathan_@mit.edu Used for the Downadup worm Aff t l t i f NT b d Affects almost every version of NT based Windows systems Two main binary RPC protocols SunRPC/ONCRPC and DCERPC Both are
Nathan Rittenhouse nathan_@mit.edu Used for the Downadup worm Aff t l t i f NT b d Affects almost every version of NT based Windows systems Two main binary RPC protocols SunRPC/ONCRPC and DCERPC Both are
Cloud-Native File Systems
 Cloud-Native File Systems Remzi H. Arpaci-Dusseau Andrea C. Arpaci-Dusseau University of Wisconsin-Madison Venkat Venkataramani Rockset, Inc. How And What We Build Is Always Changing Earliest days Assembly
Cloud-Native File Systems Remzi H. Arpaci-Dusseau Andrea C. Arpaci-Dusseau University of Wisconsin-Madison Venkat Venkataramani Rockset, Inc. How And What We Build Is Always Changing Earliest days Assembly
How to Break Software by James Whittaker
 How to Break Software by James Whittaker CS 470 Practical Guide to Testing Consider the system as a whole and their interactions File System, Operating System API Application Under Test UI Human invokes
How to Break Software by James Whittaker CS 470 Practical Guide to Testing Consider the system as a whole and their interactions File System, Operating System API Application Under Test UI Human invokes
Today CSCI Communication. Communication in Distributed Systems. Communication in Distributed Systems. Remote Procedure Calls (RPC)
 Today CSCI 5105 Communication in Distributed Systems Overview Types Remote Procedure Calls (RPC) Instructor: Abhishek Chandra 2 Communication How do program modules/processes communicate on a single machine?
Today CSCI 5105 Communication in Distributed Systems Overview Types Remote Procedure Calls (RPC) Instructor: Abhishek Chandra 2 Communication How do program modules/processes communicate on a single machine?
Alan Bateman Java Platform Group, Oracle November Copyright 2018, Oracle and/or its affiliates. All rights reserved.!1
 Alan Bateman Java Platform Group, Oracle November 2018 Copyright 2018, Oracle and/or its affiliates. All rights reserved.!1 Project Loom Continuations Fibers Tail-calls Copyright 2018, Oracle and/or its
Alan Bateman Java Platform Group, Oracle November 2018 Copyright 2018, Oracle and/or its affiliates. All rights reserved.!1 Project Loom Continuations Fibers Tail-calls Copyright 2018, Oracle and/or its
CSE 374 Programming Concepts & Tools
 CSE 374 Programming Concepts & Tools Hal Perkins Fall 2017 Lecture 11 gdb and Debugging 1 Administrivia HW4 out now, due next Thursday, Oct. 26, 11 pm: C code and libraries. Some tools: gdb (debugger)
CSE 374 Programming Concepts & Tools Hal Perkins Fall 2017 Lecture 11 gdb and Debugging 1 Administrivia HW4 out now, due next Thursday, Oct. 26, 11 pm: C code and libraries. Some tools: gdb (debugger)
From the RCP Book To Reality. Jean-Michel Lemieux IBM Rational, Ottawa, Canada
 From the RCP Book To Reality Jean-Michel Lemieux IBM Rational, Ottawa, Canada 2008 by Jean-Michel Lemieux made available under the EPL v1.0 March 2008 Past, Present, Future Eclipse committer since it s
From the RCP Book To Reality Jean-Michel Lemieux IBM Rational, Ottawa, Canada 2008 by Jean-Michel Lemieux made available under the EPL v1.0 March 2008 Past, Present, Future Eclipse committer since it s
Python: Getting Started. Ben
 Python: Getting Started Ben Ramseth bramseth@esri.com @esrimapninja E M E R A L D S A P P H I R E T H A N K Y O U T O O UR SPONSORS Topics covered What s is python? Why use python? Basics of python ArcPy
Python: Getting Started Ben Ramseth bramseth@esri.com @esrimapninja E M E R A L D S A P P H I R E T H A N K Y O U T O O UR SPONSORS Topics covered What s is python? Why use python? Basics of python ArcPy
ADO.NET In A Nutshell Download Free (EPUB, PDF)
 ADO.NET In A Nutshell Download Free (EPUB, PDF) Written by experts on the MicrosoftÂ.NET programming platform, ADO.NET in a Nutshell delivers everything.net programmers will need to get a jump-start on
ADO.NET In A Nutshell Download Free (EPUB, PDF) Written by experts on the MicrosoftÂ.NET programming platform, ADO.NET in a Nutshell delivers everything.net programmers will need to get a jump-start on
Chapter 2. Operating-System Structures
 Chapter 2 Operating-System Structures 2.1 Chapter 2: Operating-System Structures Operating System Services User Operating System Interface System Calls Types of System Calls System Programs Operating System
Chapter 2 Operating-System Structures 2.1 Chapter 2: Operating-System Structures Operating System Services User Operating System Interface System Calls Types of System Calls System Programs Operating System
SQL Server Whitepaper DEMYSTIFYING DEBUGGING TECHNIQUES WITH SQL SERVER BY PINAL DAVE
 SQL Server Whitepaper DEMYSTIFYING DEBUGGING TECHNIQUES WITH SQL SERVER BY PINAL DAVE INTRODUCTION The greatest happiness for a father is to see our children grow in front of our very own eyes. My daughter
SQL Server Whitepaper DEMYSTIFYING DEBUGGING TECHNIQUES WITH SQL SERVER BY PINAL DAVE INTRODUCTION The greatest happiness for a father is to see our children grow in front of our very own eyes. My daughter
RESTful APIs ECS 189 WEB PROGRAMMING. Browser s view. Browser s view. Browser s view. Browser s view. Which will It be for photobooth?
 RESTful APIs ECS 189 WEB PROGRAMMING 5/19! We re implementing what is called a RESTful API! ReST stands for representational state transfer! The term was coined in 2000 by Roy Fielding, who at the time
RESTful APIs ECS 189 WEB PROGRAMMING 5/19! We re implementing what is called a RESTful API! ReST stands for representational state transfer! The term was coined in 2000 by Roy Fielding, who at the time
Safe Harbor Statement
 Safe Harbor Statement The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment
Safe Harbor Statement The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment
Introduction to Bro-IDS. Seth Hall The Ohio State University
 Introduction to Bro-IDS Seth Hall The Ohio State University Concepts Fundamentally, Bro provides a real-time network analysis framework. Not necessarily aiming to create an IDS turns
Introduction to Bro-IDS Seth Hall The Ohio State University Concepts Fundamentally, Bro provides a real-time network analysis framework. Not necessarily aiming to create an IDS turns
Model-Based Systems Engineering: Documentation and Analysis
 Week 1: What Is MBSE? Project Name Jane Doe 1 Instructions Before you begin, you should save your Project Portfolio on your local drive. We recommend the following format: Lastname_Firstname_Course3_Week1
Week 1: What Is MBSE? Project Name Jane Doe 1 Instructions Before you begin, you should save your Project Portfolio on your local drive. We recommend the following format: Lastname_Firstname_Course3_Week1
Java GUI Testing Tools
 Java GUI Testing Tools Well, this is my take, and while I try to be unbiased, I *am* the author of one of the frameworks. Be sure to take a look at some of the yahoo java-guitesting archives as well; there
Java GUI Testing Tools Well, this is my take, and while I try to be unbiased, I *am* the author of one of the frameworks. Be sure to take a look at some of the yahoo java-guitesting archives as well; there
Asking for information (with three complex questions, so four main paragraphs)
 Structures of different kinds of emails Write typical paragraph plans for the kinds of emails, describing the paragraphs in the body and what kinds of opening lines and closing lines you need. Asking for
Structures of different kinds of emails Write typical paragraph plans for the kinds of emails, describing the paragraphs in the body and what kinds of opening lines and closing lines you need. Asking for
Traditional Ajax vs. New business targeted Ajax
 Traditional Ajax vs. New business targeted Ajax By Itzik Spitzen Introduction This article compares between the traditional Ajax represented by ASP.NET to that of the new Ajax approach represented by Visual
Traditional Ajax vs. New business targeted Ajax By Itzik Spitzen Introduction This article compares between the traditional Ajax represented by ASP.NET to that of the new Ajax approach represented by Visual
Python Programming: Your Step By Step Guide To Easily Learn Python In 7 Days By icode Academy READ ONLINE
 Python Programming: Your Step By Step Guide To Easily Learn Python In 7 Days By icode Academy READ ONLINE We're moving to our new free All-in-One app! Get it here: https://play.google.com/store/apps/details?id=com.sololearn.
Python Programming: Your Step By Step Guide To Easily Learn Python In 7 Days By icode Academy READ ONLINE We're moving to our new free All-in-One app! Get it here: https://play.google.com/store/apps/details?id=com.sololearn.
Software Engineering I (02161)
 Software Engineering I (02161) Week 10 Assoc. Prof. Hubert Baumeister DTU Compute Technical University of Denmark Spring 2016 Last Time Project Planning Non-agile Agile Refactoring Contents Basic Principles
Software Engineering I (02161) Week 10 Assoc. Prof. Hubert Baumeister DTU Compute Technical University of Denmark Spring 2016 Last Time Project Planning Non-agile Agile Refactoring Contents Basic Principles
Intro. Scheme Basics. scm> 5 5. scm>
 Intro Let s take some time to talk about LISP. It stands for LISt Processing a way of coding using only lists! It sounds pretty radical, and it is. There are lots of cool things to know about LISP; if
Intro Let s take some time to talk about LISP. It stands for LISt Processing a way of coding using only lists! It sounds pretty radical, and it is. There are lots of cool things to know about LISP; if
Russ McRee Bryan Casper
 Russ McRee Bryan Casper About us We re part of the security incident response team for Microsoft Online Services Security & Compliance We ask more questions than provide answers This presentation is meant
Russ McRee Bryan Casper About us We re part of the security incident response team for Microsoft Online Services Security & Compliance We ask more questions than provide answers This presentation is meant
Word Found Meaning Innovation
 AP CSP Quarter 1 Study Guide Vocabulary from Unit 1 & 3 Word Found Meaning Innovation A novel or improved idea, device, product, etc, or the development 1.1 thereof Binary 1.2 A way of representing information
AP CSP Quarter 1 Study Guide Vocabulary from Unit 1 & 3 Word Found Meaning Innovation A novel or improved idea, device, product, etc, or the development 1.1 thereof Binary 1.2 A way of representing information
What is a compiler? Xiaokang Qiu Purdue University. August 21, 2017 ECE 573
 What is a compiler? Xiaokang Qiu Purdue University ECE 573 August 21, 2017 What is a compiler? What is a compiler? Traditionally: Program that analyzes and translates from a high level language (e.g.,
What is a compiler? Xiaokang Qiu Purdue University ECE 573 August 21, 2017 What is a compiler? What is a compiler? Traditionally: Program that analyzes and translates from a high level language (e.g.,
CS61A Notes Week 6: Scheme1, Data Directed Programming You Are Scheme and don t let anyone tell you otherwise
 CS61A Notes Week 6: Scheme1, Data Directed Programming You Are Scheme and don t let anyone tell you otherwise If you re not already crazy about Scheme (and I m sure you are), then here s something to get
CS61A Notes Week 6: Scheme1, Data Directed Programming You Are Scheme and don t let anyone tell you otherwise If you re not already crazy about Scheme (and I m sure you are), then here s something to get
Reverse Engineering Malware Binary Obfuscation and Protection
 Reverse Engineering Malware Binary Obfuscation and Protection Jarkko Turkulainen F-Secure Corporation Protecting the irreplaceable f-secure.com Binary Obfuscation and Protection What is covered in this
Reverse Engineering Malware Binary Obfuscation and Protection Jarkko Turkulainen F-Secure Corporation Protecting the irreplaceable f-secure.com Binary Obfuscation and Protection What is covered in this
Developing large-scale Applications in Python
 Developing large-scale Applications in Python Lessons learned from 10 years of Python Application Design EuroPython Conference 2004 Göteborg, Sweden Marc-André Lemburg EGENIX.COM Software GmbH Germany
Developing large-scale Applications in Python Lessons learned from 10 years of Python Application Design EuroPython Conference 2004 Göteborg, Sweden Marc-André Lemburg EGENIX.COM Software GmbH Germany
Programming Project 1: Introduction to the BLITZ Tools
 Programming Project 1: Introduction to the BLITZ Tools Due Date: 2nd October 2017 before 11:30 AM. Duration: One Week Overview and Goal In this course you will be creating an operating system kernel. You
Programming Project 1: Introduction to the BLITZ Tools Due Date: 2nd October 2017 before 11:30 AM. Duration: One Week Overview and Goal In this course you will be creating an operating system kernel. You
