User Behaviors and Attitudes Under Password Expiration Policies
|
|
|
- Sherilyn Marsh
- 5 years ago
- Views:
Transcription
1 User Behaviors and Attitudes Under Password Expiration Policies Hana Habib, Pardis Emami Naeini, Summer Devlin, Maggie Oates, Chelse Swoopes, Lujo Bauer, Nicolas Christin, and Lorrie Faith Cranor
2 Let s talk about password expiration policies Sources:
3 Do expiration policies help improve security? No evidence that expiration protects from modern password guessing attacks Attackers can use password history to launch better attacks (Zhang et al. CCS 10) Sources: 3
4 Do users make weaker passwords? 1. What happens when people are FORCED to change their passwords? Do they have a harder time using their passwords? Do they have negative sentiments toward their policies? How important do they view password expiration? 4
5 2. How does human behavior impact the effectiveness of password expiration policies? 5
6 Conducted 2 Mechanical Turk surveys Workplace passwords survey and password perceptions survey Total of 695 participants Age 18 or older Residents of the United States 55% had an expiration policy for their main workplace password 6
7 Workplace passwords survey Screening Ensure at least one workplace password Full survey 31 multiple choice questions 5 open-ended response questions Password management experiences Creating, updating, and recalling passwords Sentiments toward password expiration 7
8 How do people CREATE passwords? Worplace passwords Use a word in English 41% Use a name 37% Add numbers to beginning or end 59% Add symbols to beginning or end 32% 8
9 How do people UPDATE passwords? Worplace passwords Modified their current password 67% Created a new password 24% Reused a password from another account 10% 9
10 Techniques to update passwords Worplace passwords Capitalizing a character soups# soups# 30% Incrementing a character soupsalad#1 soupsalad#2 17% Adding a sequence alphabetsoupa alphabetsoupabc 15% Adding a date noodlesoup noodlesoup % Substituting digits/special characters Hot!soup1 hot!soup9 12% 10
11 Coping with password expiration policies Worplace passwords Use the same strategy they used to create their passwords (64%) Password generator (7%) Substituting letters and symbols New fast food receipt looking37pickles1402 Updated password was believed to be about the same strength as previous (66%) Source: 11
12 Password perceptions survey Management behaviors 1. Using a complex password 2. Storing a password safely 3. Avoiding reuse 4. Changing passwords periodically Rate importance of management behaviors for account security Rank the harm of not following each practice Choose which practice contributes most to account security when shown pairs Anticipate behaviors in a hypothetical scenario where their workplace: Implemented expiration policy Removed expiration policy 12
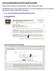
13 Expiration is important but not as important as others Use a complex password Store your password in a safe place Create a password you do not already use Change your password periodically Password expiration 0% % % Who Agreed the Practice was Important 13
14 It takes time to hack or steal a password and if it is changed frequently it is less likely that the hacker will have time to obtain the password. There will be less time for a hacker to retrieve your information. 14
15 Downsides of expiration Inconvenient Insecure Unusable Ineffective 15
16 I don t think [periodic password change] is as important as people say...a really strong password doesn t just automatically become weaker simply because you ve been using it for a while. I don t believe it s necessarily important to change your password, if you have a secure one in the first place 16
17 Expiration frequency had minor impact on usage No reported influence on: Update strategies Account lockouts Similarity with other passwords Sentiments about expiration Slight influence on: Password memorization Source: 17
18 People accept the advice they re told About 50% would continue changing their password if their expiration policy was removed Reported reasons: Habit Beneficial to security 18
19 It s the standard we use and it works well. It s just a natural habit to do now for my own security. 19
20 I would forget as it is not on my high priority list. 20
21 Expiration does not lead to weaker passwords or extremely negative reactions... BUT...people have developed coping mechanisms which may not benefit account security as much as one would like 21
22 Main recommendation Enable users to create and manage complex passwords Sufficiently random Password managers Password generators Source: 22
23 User Behaviors and Attitudes Under Password Expiration Policies Hana Habib, Pardis Emami Naeini, Summer Devlin, Maggie Oates, Chelse Swoopes, Lujo Bauer, Nicolas Christin, and Lorrie Faith Cranor For more on this: cups.cs.cmu.edu/passwords/ 23
User Behaviors and Attitudes Under Password Expiration Policies
 User Behaviors and Attitudes Under Password Expiration Policies Hana Habib, Pardis Emami-Naeini, Summer Devlin, Maggie Oates, Chelse Swoopes, Lujo Bauer, Nicolas Christin, Lorrie Faith Cranor Carnegie
User Behaviors and Attitudes Under Password Expiration Policies Hana Habib, Pardis Emami-Naeini, Summer Devlin, Maggie Oates, Chelse Swoopes, Lujo Bauer, Nicolas Christin, Lorrie Faith Cranor Carnegie
Diversify to Survive: Making Passwords Stronger with Adaptive Policies
 Diversify to Survive: Making Passwords Stronger with Adaptive Policies Sean Segreti, William Melicher, Saranga Komanduri, Darya Melicher, Richard Shay, Blase Ur, Lujo Bauer, Nicolas Christin, Lorrie Faith
Diversify to Survive: Making Passwords Stronger with Adaptive Policies Sean Segreti, William Melicher, Saranga Komanduri, Darya Melicher, Richard Shay, Blase Ur, Lujo Bauer, Nicolas Christin, Lorrie Faith
Opening Remarks: Security, Privacy & Human Behavior
 SESSION ID: SEM-M01 Opening Remarks: Security, Privacy & Human Behavior Lorrie Cranor Director, CyLab Security and Privacy Institute Carnegie Mellon University @lorrietweet The human threat Malicious
SESSION ID: SEM-M01 Opening Remarks: Security, Privacy & Human Behavior Lorrie Cranor Director, CyLab Security and Privacy Institute Carnegie Mellon University @lorrietweet The human threat Malicious
How does your password measure up? The effect of strength meters on password creation
 How does your password measure up? The effect of strength meters on password creation Blase Ur, Patrick Gage Kelley, Saranga Komanduri, Joel Lee, Michael Maass, Michelle L. Mazurek, Timothy Passaro, Richard
How does your password measure up? The effect of strength meters on password creation Blase Ur, Patrick Gage Kelley, Saranga Komanduri, Joel Lee, Michael Maass, Michelle L. Mazurek, Timothy Passaro, Richard
Fast, Lean, and Accurate: Modeling Password Guessability Using Neural Networks
 Fast, Lean, and Accurate: Modeling Password Guessability Using Neural Networks William Melicher, Blase Ur, Sean Segreti, Saranga Komanduri, Lujo Bauer, Nicolas Christin, Lorrie Faith Cranor First appeared
Fast, Lean, and Accurate: Modeling Password Guessability Using Neural Networks William Melicher, Blase Ur, Sean Segreti, Saranga Komanduri, Lujo Bauer, Nicolas Christin, Lorrie Faith Cranor First appeared
Passwords and User Behavior
 Passwords and User Behavior Tehreem Hussain*, Kiran Atta, N. Z. Bawany, Tehreem Qamar Department of Computer Science and IT, Jinnah University for Women, Karachi, Pakistan. * Corresponding author. Tel.:
Passwords and User Behavior Tehreem Hussain*, Kiran Atta, N. Z. Bawany, Tehreem Qamar Department of Computer Science and IT, Jinnah University for Women, Karachi, Pakistan. * Corresponding author. Tel.:
Adobe Security Survey
 Adobe Security Survey October 2016 Edelman + Adobe INTRODUCTION Methodology Coinciding with National Cyber Security Awareness Month (NCSAM), Edelman Intelligence, on behalf of Adobe, conducted a nationally
Adobe Security Survey October 2016 Edelman + Adobe INTRODUCTION Methodology Coinciding with National Cyber Security Awareness Month (NCSAM), Edelman Intelligence, on behalf of Adobe, conducted a nationally
Carnegie Mellon University. sarangak, billy, ssegreti, Figure 1: Yahoo s real-time password-creation feedback.
 A Spoonful of Sugar? The Impact of Guidance and Feedback on Password-Creation Behavior Richard Shay, Lujo Bauer, Nicolas Christin, Lorrie Faith Cranor, Alain Forget, Saranga Komanduri, Michelle L. Mazurek
A Spoonful of Sugar? The Impact of Guidance and Feedback on Password-Creation Behavior Richard Shay, Lujo Bauer, Nicolas Christin, Lorrie Faith Cranor, Alain Forget, Saranga Komanduri, Michelle L. Mazurek
Better passwords through science (and neural networks)
 Better passwords through science (and neural networks) William Melicher, Blase Ur, Sean M. Segreti, Lujo Bauer, Nicolas Christin, and Lorrie Faith Cranor We discuss how we use neural networks to accurately
Better passwords through science (and neural networks) William Melicher, Blase Ur, Sean M. Segreti, Lujo Bauer, Nicolas Christin, and Lorrie Faith Cranor We discuss how we use neural networks to accurately
The continuing quest for secure and usable passwords
 The continuing quest for secure and usable passwords Blase Ur and Sean Segreti Joint work with L. Bauer, N. Christin, L.F. Cranor, P.G. Kelley, S. Komanduri, M. Mazurek, R. Shay, T. Vidas, J. Bees, A.
The continuing quest for secure and usable passwords Blase Ur and Sean Segreti Joint work with L. Bauer, N. Christin, L.F. Cranor, P.G. Kelley, S. Komanduri, M. Mazurek, R. Shay, T. Vidas, J. Bees, A.
How to Register at the AMC Member Center and Select Electronic Delivery
 How to Register at the AMC Member Center and Select Electronic Delivery By Jeff Carden Registering with the AMC s Member Center at http://www.outdoors.org/membership/member-center.cfm provides you with
How to Register at the AMC Member Center and Select Electronic Delivery By Jeff Carden Registering with the AMC s Member Center at http://www.outdoors.org/membership/member-center.cfm provides you with
Analysis of Coping Mechanisms of Password Selection
 Running head: COPING MECHANISMS IN PASSWORD SELECTION 1 Analysis of Coping Mechanisms of Password Selection Brian Curnett, Paul Duselis, and Teri Flory INSURE Program, Purdue University April 25, 2014
Running head: COPING MECHANISMS IN PASSWORD SELECTION 1 Analysis of Coping Mechanisms of Password Selection Brian Curnett, Paul Duselis, and Teri Flory INSURE Program, Purdue University April 25, 2014
Points are not transferable. Aon employees are not eligible to receive Points.
 Q: What are Points? A: Talk to Aon uses a Points system to reward members for completing certain surveys. When you receive emails that invite you to participate in surveys, you ll be told whether the survey
Q: What are Points? A: Talk to Aon uses a Points system to reward members for completing certain surveys. When you receive emails that invite you to participate in surveys, you ll be told whether the survey
04. Studying Passwords. Blase Ur, April 5 th, 2017 CMSC / 33210
 04. Studying Passwords Blase Ur, April 5 th, 2017 CMSC 23210 / 33210 1 Announcements On Monday: Privacy discussion PSET 1 presentations Key verification Reading for Monday will be on Piazza 2 Today s class
04. Studying Passwords Blase Ur, April 5 th, 2017 CMSC 23210 / 33210 1 Announcements On Monday: Privacy discussion PSET 1 presentations Key verification Reading for Monday will be on Piazza 2 Today s class
REGULATED DOMESTIC ROAMING RESEARCH REPORT 2017
 REGULATED DOMESTIC ROAMING RESEARCH REPORT 2017 Researching the attitudes and perceptions of regional and remote Australians towards mobile providers and domestic roaming Vodafone Regional Roaming Research
REGULATED DOMESTIC ROAMING RESEARCH REPORT 2017 Researching the attitudes and perceptions of regional and remote Australians towards mobile providers and domestic roaming Vodafone Regional Roaming Research
REGULATED DOMESTIC ROAMING RESEARCH REPORT 2017
 REGULATED DOMESTIC ROAMING RESEARCH REPORT 2017 Researching the attitudes and perceptions of regional and remote Australians towards mobile providers and domestic roaming Vodafone Regional Roaming Research
REGULATED DOMESTIC ROAMING RESEARCH REPORT 2017 Researching the attitudes and perceptions of regional and remote Australians towards mobile providers and domestic roaming Vodafone Regional Roaming Research
Usable Privacy and Security, Fall 2011 Nov. 10, 2011
 Usable Privacy and Security, Fall 2011 Nov. 10, 2011 YoungSeok Yoon (youngseok@cs.cmu.edu) Institute for Software Research School of Computer Science Carnegie Mellon University picture/photo based vs.
Usable Privacy and Security, Fall 2011 Nov. 10, 2011 YoungSeok Yoon (youngseok@cs.cmu.edu) Institute for Software Research School of Computer Science Carnegie Mellon University picture/photo based vs.
Security and Usability Computer Security: Lecture 9. 9 February 2009 Guest Lecture by Mike Just
 Security and Usability Computer Security: Lecture 9 9 February 2009 Guest Lecture by Mike Just Introduction Who am I? Mike Just Visiting Research Fellow, School of Informatics Researching security and
Security and Usability Computer Security: Lecture 9 9 February 2009 Guest Lecture by Mike Just Introduction Who am I? Mike Just Visiting Research Fellow, School of Informatics Researching security and
Lesson Guides PRE-INTERMEDIATE
 Lesson Guides PRE-INTERMEDIATE British Council 2018 The British Council is the United Kingdom s international organisation for cultural relations and educational opportunities. PRE-INTERMEDIATE LESSON
Lesson Guides PRE-INTERMEDIATE British Council 2018 The British Council is the United Kingdom s international organisation for cultural relations and educational opportunities. PRE-INTERMEDIATE LESSON
Accounts and Passwords
 Accounts and Passwords Hello, I m Kate and we re here to learn how to set up an account on a website. Many websites allow you to create a personal account. Your account will have its own username and password.
Accounts and Passwords Hello, I m Kate and we re here to learn how to set up an account on a website. Many websites allow you to create a personal account. Your account will have its own username and password.
Survival of the Shortest: A Retrospective Analysis of Influencing Factors on Password Composition
 Survival of the Shortest: A Retrospective Analysis of Influencing Factors on Password Composition Emanuel von Zezschwitz, Alexander De Luca, and Heinrich Hussmann University of Munich (LMU), Media Informatics
Survival of the Shortest: A Retrospective Analysis of Influencing Factors on Password Composition Emanuel von Zezschwitz, Alexander De Luca, and Heinrich Hussmann University of Munich (LMU), Media Informatics
A Design Space for Security Indicators for Behavioural Biometrics on Mobile Touchscreen Devices
 A Design Space for Security Indicators for Behavioural Biometrics on Mobile Touchscreen Devices Lukas Mecke Munich University of Applied Sciences, Germany lukas.mecke@hm.edu Sarah Prange Munich University
A Design Space for Security Indicators for Behavioural Biometrics on Mobile Touchscreen Devices Lukas Mecke Munich University of Applied Sciences, Germany lukas.mecke@hm.edu Sarah Prange Munich University
Apply for Free School Meals Online Step-by-step Guide
 Apply for Free School Meals Online Step-by-step Guide Before you start Have your National insurance number to hand before you start your application. Get an email address you need one to apply. If you
Apply for Free School Meals Online Step-by-step Guide Before you start Have your National insurance number to hand before you start your application. Get an email address you need one to apply. If you
Password Strength Analysis
 Password Strength Analysis Brian Curnett 1, Teri Flory 2 1 Purdue University, bcurnett@purdue.edu, 2 Purdue University, tflory@purdue.edu Keywords: Coping Mechanism, Password, Password Analysis, Password
Password Strength Analysis Brian Curnett 1, Teri Flory 2 1 Purdue University, bcurnett@purdue.edu, 2 Purdue University, tflory@purdue.edu Keywords: Coping Mechanism, Password, Password Analysis, Password
Can Long Passwords Be Secure and Usable?
 Can Long Passwords Be Secure and Usable? Richard Shay, Saranga Komanduri, Adam L. Durity, Phillip (Seyoung) Huh, Michelle L. Mazurek, Sean M. Segreti, Blase Ur, Lujo Bauer, Nicolas Christin, and Lorrie
Can Long Passwords Be Secure and Usable? Richard Shay, Saranga Komanduri, Adam L. Durity, Phillip (Seyoung) Huh, Michelle L. Mazurek, Sean M. Segreti, Blase Ur, Lujo Bauer, Nicolas Christin, and Lorrie
Rethinking Authentication. Steven M. Bellovin
 Rethinking Authentication Steven M. https://www.cs.columbia.edu/~smb Why? I don t think we understand the real security issues with authentication Our defenses are ad hoc I regard this as a step towards
Rethinking Authentication Steven M. https://www.cs.columbia.edu/~smb Why? I don t think we understand the real security issues with authentication Our defenses are ad hoc I regard this as a step towards
Worksheet - Reading Guide for Keys and Passwords
 Unit 2 Lesson 15 Name(s) Period Date Worksheet - Reading Guide for Keys and Passwords Background Algorithms vs. Keys. An algorithm is how to execute the encryption and decryption and key is the secret
Unit 2 Lesson 15 Name(s) Period Date Worksheet - Reading Guide for Keys and Passwords Background Algorithms vs. Keys. An algorithm is how to execute the encryption and decryption and key is the secret
Frequently Asked Questions FOR REGISTRANTS
 CampDoc.com Frequently Asked Questions FOR REGISTRANTS We are committed to providing you excellent support! Our team has put together this support document with a collection of answers to the most common
CampDoc.com Frequently Asked Questions FOR REGISTRANTS We are committed to providing you excellent support! Our team has put together this support document with a collection of answers to the most common
2004 Customer Satisfaction Survey For Form 1120 e-file
 2004 Customer Satisfaction Survey For Form 1120 e-file The U.S. Corporation Income Tax Return Presented to: Fall 2004 BMF Integration Meetings Publication 4417 (09/2004) Catalog # 39128D Presented by:
2004 Customer Satisfaction Survey For Form 1120 e-file The U.S. Corporation Income Tax Return Presented to: Fall 2004 BMF Integration Meetings Publication 4417 (09/2004) Catalog # 39128D Presented by:
Security and human behavior. Some material from Lorrie Cranor, Mike Reiter, Rob Reeder, Blase Ur
 Security and human behavior Some material from Lorrie Cranor, Mike Reiter, Rob Reeder, Blase Ur 1 In these lectures Overview Minimizing effort Case studies Grey, password expiration, security images, password
Security and human behavior Some material from Lorrie Cranor, Mike Reiter, Rob Reeder, Blase Ur 1 In these lectures Overview Minimizing effort Case studies Grey, password expiration, security images, password
FAQ: Privacy, Security, and Data Protection at Libraries
 FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
Signing up for My Lahey Chart
 Signing up for My Lahey Chart What is My Lahey Chart? My Lahey Chart is a helpful service that allows you to connect with your doctor and your health information online, anytime. Using your personal computer
Signing up for My Lahey Chart What is My Lahey Chart? My Lahey Chart is a helpful service that allows you to connect with your doctor and your health information online, anytime. Using your personal computer
Password Creation in the Presence of Blacklists
 Password Creation in the Presence of Blacklists Hana Habib, Jessica Colnago, William Melicher, Blase Ur, Sean Segreti, Lujo Bauer, Nicolas Christin, and Lorrie Cranor Carnegie Mellon University {hana007,
Password Creation in the Presence of Blacklists Hana Habib, Jessica Colnago, William Melicher, Blase Ur, Sean Segreti, Lujo Bauer, Nicolas Christin, and Lorrie Cranor Carnegie Mellon University {hana007,
USE QUICK ASSIST TO REMOTELY TROUBLESHOOT A FRIEND S COMPUTER
 USE QUICK ASSIST TO REMOTELY TROUBLESHOOT A FRIEND S COMPUTER Windows 10 s Anniversary Update brings a new Quick Assist feature. Built into Windows 10, Quick Assist allows you to take remote control of
USE QUICK ASSIST TO REMOTELY TROUBLESHOOT A FRIEND S COMPUTER Windows 10 s Anniversary Update brings a new Quick Assist feature. Built into Windows 10, Quick Assist allows you to take remote control of
How to Build a Culture of Security
 How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
Have the students look at the editor on their computers. Refer to overhead projector as necessary.
 Intro to Programming (Time 15 minutes) Open the programming tool of your choice: If you ve installed, DrRacket, double-click the application to launch it. If you are using the online-tool, click here to
Intro to Programming (Time 15 minutes) Open the programming tool of your choice: If you ve installed, DrRacket, double-click the application to launch it. If you are using the online-tool, click here to
HCI Lecture 10: Guest Lecture Usability & Security 28 October 2008
 HCI Lecture 10: Guest Lecture Usability & Security 28 October 2008 Mike Just, Visiting Research Fellow Key Points: Reliance upon memory is a key factor for usability Usability and security can be achieved
HCI Lecture 10: Guest Lecture Usability & Security 28 October 2008 Mike Just, Visiting Research Fellow Key Points: Reliance upon memory is a key factor for usability Usability and security can be achieved
Kickstarter Privacy Policy - February 2017 changes
 Kickstarter Privacy Policy - February 2017 changes This Policy describes the information we collect from you and how we use that information. It applies to any of the Services that Kickstarter or any of
Kickstarter Privacy Policy - February 2017 changes This Policy describes the information we collect from you and how we use that information. It applies to any of the Services that Kickstarter or any of
Authentication KAMI VANIEA 1
 Authentication KAMI VANIEA FEBRUARY 1ST KAMI VANIEA 1 First, the news KAMI VANIEA 2 Today Basics of authentication Something you know passwords Something you have Something you are KAMI VANIEA 3 Most recommended
Authentication KAMI VANIEA FEBRUARY 1ST KAMI VANIEA 1 First, the news KAMI VANIEA 2 Today Basics of authentication Something you know passwords Something you have Something you are KAMI VANIEA 3 Most recommended
Information Technology
 Information Technology Operations Team Instructional Sharing Protected Data Contents Introduction... 3 Procedure... 3 How to Password Protect a MS Word Document... 3 MS Word 2010/2013/2016... 3 Word 2007...
Information Technology Operations Team Instructional Sharing Protected Data Contents Introduction... 3 Procedure... 3 How to Password Protect a MS Word Document... 3 MS Word 2010/2013/2016... 3 Word 2007...
5-899 / Usable Privacy and Security Text Passwords Lecture by Sasha Romanosky Scribe notes by Ponnurangam K March 30, 2006
 5-899 / 17-500 Usable Privacy and Security Text Passwords Lecture by Sasha Romanosky Scribe notes by Ponnurangam K March 30, 2006 1 Topics covered Authentication and authorization Pass-sentences, pass-phrases
5-899 / 17-500 Usable Privacy and Security Text Passwords Lecture by Sasha Romanosky Scribe notes by Ponnurangam K March 30, 2006 1 Topics covered Authentication and authorization Pass-sentences, pass-phrases
Psychology of Passwords: Neglect is Helping Hackers Win
 2018 Psychology of Passwords: Neglect is Helping Hackers Win Table of Contents Global Cyber Threats Skyrocket but Password Behaviors Unchanged Respondent Demographics Findings at-a-glance Attention IT:
2018 Psychology of Passwords: Neglect is Helping Hackers Win Table of Contents Global Cyber Threats Skyrocket but Password Behaviors Unchanged Respondent Demographics Findings at-a-glance Attention IT:
Norton Online Reputation Report: Why Millennials should manage their online footprint
 Norton Online Reputation Report: Why Millennials should manage their online footprint UK May 2016 Methodology A quantitative survey was conducted online among 1,000 mobile users aged 18-34 years who own
Norton Online Reputation Report: Why Millennials should manage their online footprint UK May 2016 Methodology A quantitative survey was conducted online among 1,000 mobile users aged 18-34 years who own
MU2b Authentication, Authorization and Accounting Questions Set 2
 MU2b Authentication, Authorization and Accounting Questions Set 2 1. You enable the audit of successful and failed policy changes. Where can you view entries related to policy change attempts? Lesson 2
MU2b Authentication, Authorization and Accounting Questions Set 2 1. You enable the audit of successful and failed policy changes. Where can you view entries related to policy change attempts? Lesson 2
PASSWORD POLICIES: RECENT DEVELOPMENTS AND POSSIBLE APPRAISE
 PASSWORD POLICIES: RECENT DEVELOPMENTS AND POSSIBLE APPRAISE Hazel Murray Department of Mathematics and Statistics/ Hamilton Institute, Maynooth University, Ireland David Malone Department of Mathematics
PASSWORD POLICIES: RECENT DEVELOPMENTS AND POSSIBLE APPRAISE Hazel Murray Department of Mathematics and Statistics/ Hamilton Institute, Maynooth University, Ireland David Malone Department of Mathematics
On Limitations of Designing LRPS: Attacks, Principles and Usability
 CAP6135 Malware & Software Vulnerability On Limitations of Designing LRPS: Attacks, Principles and Usability By Sagar Patel 04/21/2014 EECS Department Agenda Introduction Leakage-Resilient Password System
CAP6135 Malware & Software Vulnerability On Limitations of Designing LRPS: Attacks, Principles and Usability By Sagar Patel 04/21/2014 EECS Department Agenda Introduction Leakage-Resilient Password System
Privacy Policy. Collection of Personal Information
 Privacy Policy BY USING OR ACCESSING THIS WEBSITE YOU SIGNIFY YOUR ACKNOWLEDGMENT AND ASSENT TO THIS PRIVACY POLICY. PLEASE READ THIS POLICY CAREFULLY. IF YOU DO NOT AGREE TO THIS POLICY, PLEASE DO NOT
Privacy Policy BY USING OR ACCESSING THIS WEBSITE YOU SIGNIFY YOUR ACKNOWLEDGMENT AND ASSENT TO THIS PRIVACY POLICY. PLEASE READ THIS POLICY CAREFULLY. IF YOU DO NOT AGREE TO THIS POLICY, PLEASE DO NOT
Goals. Understand UNIX pw system. Understand Lamport s hash and its vulnerabilities. How it works How to attack
 Last Updated: Nov 7, 2017 Goals Understand UNIX pw system How it works How to attack Understand Lamport s hash and its vulnerabilities History of UNIX passwords Originally the actual passwords were stored
Last Updated: Nov 7, 2017 Goals Understand UNIX pw system How it works How to attack Understand Lamport s hash and its vulnerabilities History of UNIX passwords Originally the actual passwords were stored
. Account & Google Message Center Guide. January Prepared by: Angela Mars IT Education and Training
 Email Account & Google Message Center Guide January 2019 Prepared by: Angela Mars IT Education and Training Table Of Contents Email Account Information Page 4 Safe Email Practices Page 5 Recommended Email
Email Account & Google Message Center Guide January 2019 Prepared by: Angela Mars IT Education and Training Table Of Contents Email Account Information Page 4 Safe Email Practices Page 5 Recommended Email
Password Managers: Devil s in the Details
 Password Managers: Devil s in the Details How Can Giving all your Passwords to a Password Manager be Safe? AUGUST 2018 Passwords are dead; long live the password! Passwords are unequivocally the most used
Password Managers: Devil s in the Details How Can Giving all your Passwords to a Password Manager be Safe? AUGUST 2018 Passwords are dead; long live the password! Passwords are unequivocally the most used
THE GROVE COMMUNITY CHURCH. InFellowship Getting Started Guide
 InFellowship Getting Started Guide Creating an Account 1. Go to https://thegrovecc.infellowship.com and click on the Sign up! link on the bottom right of the gray box. 2. On the Your Information page,
InFellowship Getting Started Guide Creating an Account 1. Go to https://thegrovecc.infellowship.com and click on the Sign up! link on the bottom right of the gray box. 2. On the Your Information page,
The Context of Cryptography. Ramki Thurimella
 The Context of Cryptography Ramki Thurimella Role Professional Paranoia or Don t Trust Anything Blindly principle Cryptography by itself is useless, just as a lock by itself is useless Different weaknesses
The Context of Cryptography Ramki Thurimella Role Professional Paranoia or Don t Trust Anything Blindly principle Cryptography by itself is useless, just as a lock by itself is useless Different weaknesses
IT & DATA SECURITY BREACH PREVENTION
 IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
Bits and Bytes August 2014
 Bits and Bytes August 2014 Arkansas Premier Computer Club Bella Vista Computer Club - John Ruehle Center Highlands Crossing Center, 1801 Forest Hills Blvd, Suite 208, Bella Vista, AR 72715 Web Site: www.bvcompclub.org
Bits and Bytes August 2014 Arkansas Premier Computer Club Bella Vista Computer Club - John Ruehle Center Highlands Crossing Center, 1801 Forest Hills Blvd, Suite 208, Bella Vista, AR 72715 Web Site: www.bvcompclub.org
Enhanced Textual Password Scheme for Better Security and Memorability
 Enhanced Textual Password Scheme for Better Security and Memorability Hina Bhanbhro Department of Computer Syst. Eng. Faculty of Electrical, Electronics & Computer Systems Engineering Shaheed Benazir Bhutto
Enhanced Textual Password Scheme for Better Security and Memorability Hina Bhanbhro Department of Computer Syst. Eng. Faculty of Electrical, Electronics & Computer Systems Engineering Shaheed Benazir Bhutto
Journal of Global Research in Computer Science PASSWORD IN PRACTICE: AN USABILITY SURVEY
 Volume 2, No. 5, May 2011 Journal of Global Research in Computer Science TECHNICAL NOTE Available Online at www.jgrcs.info PASSWORD IN PRACTICE: AN USABILITY SURVEY Naveen Kumar Assistant Professor, School
Volume 2, No. 5, May 2011 Journal of Global Research in Computer Science TECHNICAL NOTE Available Online at www.jgrcs.info PASSWORD IN PRACTICE: AN USABILITY SURVEY Naveen Kumar Assistant Professor, School
Step by step guide to two-factor authentication in MYOB Advanced
 Step by step guide to two-factor authentication in MYOB Advanced September 2018 Version no. 1.0 Table of Contents Introduction... 3 Registration... 4 Standard registration process... 4 Two-factor authentication
Step by step guide to two-factor authentication in MYOB Advanced September 2018 Version no. 1.0 Table of Contents Introduction... 3 Registration... 4 Standard registration process... 4 Two-factor authentication
user guide IDI Visit 866myezpay.com Simply Call 866-MY-EZPAY EZpay User Guide
 Visit 866myezpay.com Simply Call 866-MY-EZPAY EZpay User Guide table of contents Welcome....3 Before You Get Online Setting Up an Account....4 Registering Opening an Account for Your Student(s)....5 Adding
Visit 866myezpay.com Simply Call 866-MY-EZPAY EZpay User Guide table of contents Welcome....3 Before You Get Online Setting Up an Account....4 Registering Opening an Account for Your Student(s)....5 Adding
ICVerify Installation Guide. For Help Call More information available at POSMicro.com
 For Help Call 1.800.241.6264 ICVerify Installation Guide More information available at POSMicro.com QUESTIONS? Ask the experts at POSMicro.com. 1.800.241.6264 Live Chat Now support@posmicro.com Monday
For Help Call 1.800.241.6264 ICVerify Installation Guide More information available at POSMicro.com QUESTIONS? Ask the experts at POSMicro.com. 1.800.241.6264 Live Chat Now support@posmicro.com Monday
MOBILE SECURITY. Fixing the Disconnect Between Employer and Employee for BYOD (Bring Your Own Device)
 MOBILE SECURITY Fixing the Disconnect Between Employer and Employee for BYOD (Bring Your Own Device) INTRODUCTION BYOD SECURITY 2014 It s no surprise that there are many articles and papers on Bring Your
MOBILE SECURITY Fixing the Disconnect Between Employer and Employee for BYOD (Bring Your Own Device) INTRODUCTION BYOD SECURITY 2014 It s no surprise that there are many articles and papers on Bring Your
PASSWORD SECURITY GUIDELINE
 Section: Information Security Revised: December 2004 Guideline: Description: Password Security Guidelines: are recommended processes, models, or actions to assist with implementing procedures with respect
Section: Information Security Revised: December 2004 Guideline: Description: Password Security Guidelines: are recommended processes, models, or actions to assist with implementing procedures with respect
Online Threats. This include human using them!
 Online Threats There are many dangers from using the web (and computer in general). One should watch out for malware, automated programs designed to cause harm to you, your data, and your system. You are
Online Threats There are many dangers from using the web (and computer in general). One should watch out for malware, automated programs designed to cause harm to you, your data, and your system. You are
CS 161 Computer Security
 Paxson Spring 2017 CS 161 Computer Security Discussion 4 Week of February 13, 2017 Question 1 Clickjacking (5 min) Watch the following video: https://www.youtube.com/watch?v=sw8ch-m3n8m Question 2 Session
Paxson Spring 2017 CS 161 Computer Security Discussion 4 Week of February 13, 2017 Question 1 Clickjacking (5 min) Watch the following video: https://www.youtube.com/watch?v=sw8ch-m3n8m Question 2 Session
CTU Data Management Systems External Log-in
 CTU Data Management Systems External Log-in General User Guide Revision History Version Author Date Reason for Revision 0.1 EL 15 Mar 2012 First draft 1.0 EL 02-Apr-2012 Comments from programmer incorporated
CTU Data Management Systems External Log-in General User Guide Revision History Version Author Date Reason for Revision 0.1 EL 15 Mar 2012 First draft 1.0 EL 02-Apr-2012 Comments from programmer incorporated
Recipe for a Breach: Uncontrolled Employee Access + Poor Security Habits Employee Security Habits Reveal Risky Imbalance
 Survey Report Recipe for a Breach: Uncontrolled Employee Access + Poor Security Habits Employee Security Habits Reveal Risky Imbalance November 2017 INTRODUCTION When thinking of insider threats, we often
Survey Report Recipe for a Breach: Uncontrolled Employee Access + Poor Security Habits Employee Security Habits Reveal Risky Imbalance November 2017 INTRODUCTION When thinking of insider threats, we often
Supporting Password-Security Decisions with Data
 Supporting Password-Security Decisions with Data Blase Ur CMU-ISR-16-110 September 2016 School of Computer Science Institute for Software Research Carnegie Mellon University Pittsburgh, PA Thesis Committee:
Supporting Password-Security Decisions with Data Blase Ur CMU-ISR-16-110 September 2016 School of Computer Science Institute for Software Research Carnegie Mellon University Pittsburgh, PA Thesis Committee:
STEPS TO REGISTERING FOR OUR ONLINE AUCTIONS:
 STEPS TO REGISTERING FOR OUR ONLINE AUCTIONS: Thank you for your interest in our Online Auctions! We offer a great variety of items - The registration process is easy, just follow these steps. Once you
STEPS TO REGISTERING FOR OUR ONLINE AUCTIONS: Thank you for your interest in our Online Auctions! We offer a great variety of items - The registration process is easy, just follow these steps. Once you
Improving the Usability of the University of Rochester River Campus Libraries Web Sites
 River Campus Libraries Improving the Usability of the University of Rochester River Campus Libraries Web Sites Susan K. Cardinal April 6, 2008 New Orleans ACS Meeting Outline What is Usability? Why is
River Campus Libraries Improving the Usability of the University of Rochester River Campus Libraries Web Sites Susan K. Cardinal April 6, 2008 New Orleans ACS Meeting Outline What is Usability? Why is
Human Computable Protocols: Password-based Authentication
 18733: Applied Cryptography Human Computable Protocols: Password-based Authentication Anupam Datta With Jeremiah Blocki and Manuel Blum Carnegie Mellon University Memory Experiment 1 Person Action Bill
18733: Applied Cryptography Human Computable Protocols: Password-based Authentication Anupam Datta With Jeremiah Blocki and Manuel Blum Carnegie Mellon University Memory Experiment 1 Person Action Bill
2013 NATIONAL ONLINE SAFETY STUDY
 2013 NATIONAL ONLINE SAFETY STUDY Methodology and Sample Characteristics The National Cyber Security Alliance has conducted a new study with PayPal to analyze the cyber security behaviors and perceptions
2013 NATIONAL ONLINE SAFETY STUDY Methodology and Sample Characteristics The National Cyber Security Alliance has conducted a new study with PayPal to analyze the cyber security behaviors and perceptions
The 10 Disaster Planning Essentials For A Small Business Network
 The 10 Disaster Planning Essentials For A Small Business Network If your data is important to your business and you cannot afford to have your operations halted for days or even weeks due to data loss
The 10 Disaster Planning Essentials For A Small Business Network If your data is important to your business and you cannot afford to have your operations halted for days or even weeks due to data loss
2 User Guide. Contents
 E-mail User Guide 2 E-mail User Guide Contents Logging in to your web mail... 3 Changing your password... 5 Editing your signature... 6 Adding an e-mail account to Outlook 2010/2013/2016... 7 Adding an
E-mail User Guide 2 E-mail User Guide Contents Logging in to your web mail... 3 Changing your password... 5 Editing your signature... 6 Adding an e-mail account to Outlook 2010/2013/2016... 7 Adding an
THALES DATA THREAT REPORT
 2018 THALES DATA THREAT REPORT Trends in Encryption and Data Security U.S. FEDERAL EDITION EXECUTIVE SUMMARY #2018DataThreat THE TOPLINE Federal agency data is under siege. Over half of all agency IT security
2018 THALES DATA THREAT REPORT Trends in Encryption and Data Security U.S. FEDERAL EDITION EXECUTIVE SUMMARY #2018DataThreat THE TOPLINE Federal agency data is under siege. Over half of all agency IT security
NORTON WI-FI RISK REPORT: U.S. Results
 NORTON WI-FI RISK REPORT: U.S. Results Research Objective Norton by Symantec commissioned its second annual online survey, this year expanded to 15 global markets, in order to better understand consumers
NORTON WI-FI RISK REPORT: U.S. Results Research Objective Norton by Symantec commissioned its second annual online survey, this year expanded to 15 global markets, in order to better understand consumers
MANAGING LOCAL AUTHENTICATION IN WINDOWS
 MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
What are PCI DSS? PCI DSS = Payment Card Industry Data Security Standards
 PCI DSS What are PCI DSS? PCI DSS = Payment Card Industry Data Security Standards Definition: A multifaceted security standard that includes requirements for security management, policies, procedures,
PCI DSS What are PCI DSS? PCI DSS = Payment Card Industry Data Security Standards Definition: A multifaceted security standard that includes requirements for security management, policies, procedures,
KeePass - to improve your process
 KeePass - to improve your process Before proceeding with the article, please take this quick password safety test. Password Safety Test Score one point for every YES answer.: Scoring: 1. Do you write your
KeePass - to improve your process Before proceeding with the article, please take this quick password safety test. Password Safety Test Score one point for every YES answer.: Scoring: 1. Do you write your
Hello, and welcome to the presentation NHSN Enrollment Instructions for Long Term Care Facilities.
 Hello, and welcome to the presentation NHSN Enrollment Instructions for Long Term Care Facilities. This presentation will provide long term care facilities with instructions for NHSN enrollment. My name
Hello, and welcome to the presentation NHSN Enrollment Instructions for Long Term Care Facilities. This presentation will provide long term care facilities with instructions for NHSN enrollment. My name
Frequently Asked Questions FOR FAMILIES
 Frequently Asked Questions FOR FAMILIES We are committed to providing you excellent support! Our team has put together this support document with a collection of answers to the most common questions families
Frequently Asked Questions FOR FAMILIES We are committed to providing you excellent support! Our team has put together this support document with a collection of answers to the most common questions families
Designing a System. We have lots of tools Tools are rarely interesting by themselves Let s design a system... Steven M. Bellovin April 10,
 Designing a System We have lots of tools Tools are rarely interesting by themselves Let s design a system... Steven M. Bellovin April 10, 2007 1 Some of Our Tools Encryption Authentication mechanisms Access
Designing a System We have lots of tools Tools are rarely interesting by themselves Let s design a system... Steven M. Bellovin April 10, 2007 1 Some of Our Tools Encryption Authentication mechanisms Access
Usable Security Introduction to User Authentication and Human Interaction Proof Research
 Usable Security Introduction to User Authentication and Human Interaction Proof Research Argyris C. Constantinides PhD Student Department of Computer Science University of Cyprus 1 Agenda Introduction
Usable Security Introduction to User Authentication and Human Interaction Proof Research Argyris C. Constantinides PhD Student Department of Computer Science University of Cyprus 1 Agenda Introduction
Knowledge Map. Tally.ERP 9
 Knowledge Map Tally.ERP 9 Preface What is a Knowledge Map? A Knowledge Map is a representation of a concept using levels of information. Each level provides deeper understanding than the previous one.
Knowledge Map Tally.ERP 9 Preface What is a Knowledge Map? A Knowledge Map is a representation of a concept using levels of information. Each level provides deeper understanding than the previous one.
UNLOCKED DOORS RESEARCH SHOWS PRINTERS ARE BEING LEFT VULNERABLE TO CYBER ATTACKS
 WHITE PAPER UNLOCKED DOORS RESEARCH SHOWS PRINTERS ARE BEING LEFT VULNERABLE TO CYBER ATTACKS While IT teams focus on other endpoints, security for corporate printers lags behind Printers make easy targets:
WHITE PAPER UNLOCKED DOORS RESEARCH SHOWS PRINTERS ARE BEING LEFT VULNERABLE TO CYBER ATTACKS While IT teams focus on other endpoints, security for corporate printers lags behind Printers make easy targets:
Security Awareness & Best Practices Best Practices for Maintaining Data Security in Your Business Environment
 Security Awareness & Best Practices Best Practices for Maintaining Data Security in Your Business Environment Ray Colado, Information Security Analyst Raise awareness around information security to help
Security Awareness & Best Practices Best Practices for Maintaining Data Security in Your Business Environment Ray Colado, Information Security Analyst Raise awareness around information security to help
Introduction to Information Security Prof. V. Kamakoti Department of Computer Science and Engineering Indian Institute of Technology, Madras
 Introduction to Information Security Prof. V. Kamakoti Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 09 Now, we discuss about the insecurity of passwords.
Introduction to Information Security Prof. V. Kamakoti Department of Computer Science and Engineering Indian Institute of Technology, Madras Lecture 09 Now, we discuss about the insecurity of passwords.
Telepathwords. Preventing Weak Passwords by Reading Users Minds
 Catalina Cumpanasoiu Erin Gibbons Telepathwords Preventing Weak Passwords by Reading Users Minds Authors: Saranga Komanduri, Richard Shay, and Lorrie Faith Cranor (Carnegie Mellon University) Cormac Herley
Catalina Cumpanasoiu Erin Gibbons Telepathwords Preventing Weak Passwords by Reading Users Minds Authors: Saranga Komanduri, Richard Shay, and Lorrie Faith Cranor (Carnegie Mellon University) Cormac Herley
Authentication SPRING 2018: GANG WANG. Slides credit: Michelle Mazurek (U-Maryland) and Blase Ur (CMU)
 Authentication SPRING 2018: GANG WANG Slides credit: Michelle Mazurek (U-Maryland) and Blase Ur (CMU) Passwords, Hashes, Salt Password database Username Plaintext Password Not a good idea to store plaintext
Authentication SPRING 2018: GANG WANG Slides credit: Michelle Mazurek (U-Maryland) and Blase Ur (CMU) Passwords, Hashes, Salt Password database Username Plaintext Password Not a good idea to store plaintext
GDPR, Information Security, and the IT Service Desk
 GDPR, Information Security, and the IT Service Desk A survey-based snapshot of the IT industry in May 2018 Executive Summary Information security is a growing concern and budget item for most, if not all,
GDPR, Information Security, and the IT Service Desk A survey-based snapshot of the IT industry in May 2018 Executive Summary Information security is a growing concern and budget item for most, if not all,
Welcome to Learn. 1. Your first task is to log into Learn. a. (click this link or copy and paste it into your browser)
 Welcome to Learn 1. Your first task is to log into Learn. a. http://learn.gov.sk.ca (click this link or copy and paste it into your browser) b. You will see this at the bottom of your screen: Login. c.
Welcome to Learn 1. Your first task is to log into Learn. a. http://learn.gov.sk.ca (click this link or copy and paste it into your browser) b. You will see this at the bottom of your screen: Login. c.
Proceed With Caution. BJHS 9 th Grade E-Cybermission Project
 Proceed With Caution BJHS 9 th Grade E-Cybermission 2009-10 Project Problem Many doctors and scientists believe cell phone radiation may be a serious health hazard. Billions of people worldwide including
Proceed With Caution BJHS 9 th Grade E-Cybermission 2009-10 Project Problem Many doctors and scientists believe cell phone radiation may be a serious health hazard. Billions of people worldwide including
Cryptography Lesson Plan
 Cryptography Lesson Plan Overview - Cryptography Summary There is a large amount of sensitive information being stored on computers and transmitted between computers today, including account passwords,
Cryptography Lesson Plan Overview - Cryptography Summary There is a large amount of sensitive information being stored on computers and transmitted between computers today, including account passwords,
KNOWLEDGE GAPS: AI AND MACHINE LEARNING IN CYBERSECURITY. Perspectives from U.S. and Japanese IT Professionals
 KNOWLEDGE GAPS: AI AND MACHINE LEARNING IN CYBERSECURITY Perspectives from U.S. and ese IT Professionals Executive Summary The use of artificial intelligence (AI) and machine learning (ML) in cybersecurity
KNOWLEDGE GAPS: AI AND MACHINE LEARNING IN CYBERSECURITY Perspectives from U.S. and ese IT Professionals Executive Summary The use of artificial intelligence (AI) and machine learning (ML) in cybersecurity
AT&T Disaster Preparedness Survey Hurricane Katrina & Rita Results. August 2006
 AT&T Disaster Preparedness Survey Hurricane Katrina & Rita Results August 2006 Methodology Results are drawn from N=400 completed surveys among residents age 18+ from 4 states: Alabama, Louisiana, Mississippi,
AT&T Disaster Preparedness Survey Hurricane Katrina & Rita Results August 2006 Methodology Results are drawn from N=400 completed surveys among residents age 18+ from 4 states: Alabama, Louisiana, Mississippi,
Introduction to Programming
 CHAPTER 1 Introduction to Programming Begin at the beginning, and go on till you come to the end: then stop. This method of telling a story is as good today as it was when the King of Hearts prescribed
CHAPTER 1 Introduction to Programming Begin at the beginning, and go on till you come to the end: then stop. This method of telling a story is as good today as it was when the King of Hearts prescribed
Properties and Definitions
 Section 0.1 Contents: Operations Defined Multiplication as an Abbreviation Visualizing Multiplication Commutative Properties Parentheses Associative Properties Identities Zero Product Answers to Exercises
Section 0.1 Contents: Operations Defined Multiplication as an Abbreviation Visualizing Multiplication Commutative Properties Parentheses Associative Properties Identities Zero Product Answers to Exercises
Changes to Government Gateway
 Changes to Government Gateway Accessing your RPW Online account From 11th December 2018 1. What s changing? Government Gateway is being upgraded to ensure it is more robust and resilient and can cope with
Changes to Government Gateway Accessing your RPW Online account From 11th December 2018 1. What s changing? Government Gateway is being upgraded to ensure it is more robust and resilient and can cope with
Chapter 12. Information Security Management
 Chapter 12 Information Security Management We Have to Design It for Privacy... and Security. Tension between Maggie and Ajit regarding terminology to use with Dr. Flores. Overly technical communication
Chapter 12 Information Security Management We Have to Design It for Privacy... and Security. Tension between Maggie and Ajit regarding terminology to use with Dr. Flores. Overly technical communication
User Authentication Protocol
 opass: A User Authentication Protocol Sao Vikram B., Gore Vishwanath P., Sankhe Bhakti A., Rananaware Rahul C., ABSTRACT Password security is significant for user authentication on small networking system
opass: A User Authentication Protocol Sao Vikram B., Gore Vishwanath P., Sankhe Bhakti A., Rananaware Rahul C., ABSTRACT Password security is significant for user authentication on small networking system
Setting up your new login
 Adviser Setting up your new login How to access your new platform 1 Contents Before you begin 3 Accessing the new platform 4 Activation reminder message 5 Activating your account 6 What now? 8 FAQ 9 2
Adviser Setting up your new login How to access your new platform 1 Contents Before you begin 3 Accessing the new platform 4 Activation reminder message 5 Activating your account 6 What now? 8 FAQ 9 2
PROTECTING YOUR BUSINESS ASSETS
 PROTECTING YOUR BUSINESS ASSETS How to Spot Danger Before Your Computer Gets Infected, Your Site Hosts Malware, and Your Credit Card Number Gets Stolen A MyNAMS Presentation by Regina Smola @2012 Regina
PROTECTING YOUR BUSINESS ASSETS How to Spot Danger Before Your Computer Gets Infected, Your Site Hosts Malware, and Your Credit Card Number Gets Stolen A MyNAMS Presentation by Regina Smola @2012 Regina
