PASSWORD SECURITY GUIDELINE
|
|
|
- Claribel Holmes
- 6 years ago
- Views:
Transcription
1 Section: Information Security Revised: December 2004 Guideline: Description: Password Security Guidelines: are recommended processes, models, or actions to assist with implementing procedures with respect to the subject. Author: Information Security Office PASSWORD SECURITY GUIDELINE Strong passwords are required by multiple State and Federal requirements to protect University assets and data. Handbook of Operating Procedures policy and its associated standard fulfill those requirements for the University. The following pages represent industry best practices for implementing strong password security, whether at the individual workstation level or across the enterprise. This document reiterates University password requirements, and then presents guidelines, suggestions, and recommendations for implementing that policy at appropriate levels within the University. Finally, a template is presented as a removable, standalone document which can be edited to represent a department s tailored approach to local password security. Password Security Guideline Internal Use Only
2 Table of Contents 1. POLICY REQUIREMENTS CREATING EFFECTIVE PASSWORDS AVOIDING PROBLEM PASSWORDS CHANGING YOUR PASSWORD DID YOU FORGET YOUR PASSWORD? SOCIAL ENGINEERING... 4 Password Security Guideline i Internal Use Only
3 1. Policy It is the policy of The University of Texas Health Science Center at San Antonio (UTHSCSA) to protect its information resource assets and data with passwords, where appropriate. Since passwords act as the front-line of protection to University data, poorly chosen passwords or password behaviors may result in the compromise of the network and/or exposure of sensitive information. Information Security is everyone s responsibility, but management of information resources, systems, and their data within each department generally resides with departmental management. As such, each department must decide to conform to University policies and standards or to develop their own; local departmental policies may be more restrictive but not less. 2. Requirements All authorized users who have or are responsible for any account on any UTHSCSA computer system are required to create, maintain, and protect strong passwords for those system, where passwords are required. Thos users include, but are not limited to, faculty, staff, students, contractors, or guests. Within the limits of the operating system or application, those passwords must: Contain a minimum of eight (8) characters Contain at least three (3) of the following four (4) characters: o Upper case characters (A-Z). o Lower case characters (a-z). o Numerical characters (0-9) o Special characters (!@#$%^&*()_+ ~-=\`{}[]:";'<>?,./) Maintain sufficient complexity by avoiding dictionary words (English, foreign language, or technical), personally identifiable or publicly available information, jargon, or word or number patterns Have a maximum age of 60 days and a minimum age of 3 days Maintain a history of at least six (6) passwords Lock an account for at least 15 minutes after five (5) sequential invalid login attempts NOT be stored in clear text or in any easily reversible form 3. Creating Effective Passwords Here are three common sense, but very effective, rules to follow regarding your passwords: Password Security Guideline 1 Internal Use Only
4 Do not write your password down! If you do, someone else can find it and use it. Remember, anything done on a computer using your user name and password looks like it is coming from YOU. Never give your password to anyone. Follow these guidelines for constructing strong passwords: First and foremost, it must be easy for you to remember, but difficult for anyone else to guess Create a password at least eight (8) characters long and as complex as you can remember within the confines of the operating system, and that conforms to the published UTHSCSA Password Standard as described above. Take words that are easy for you to remember and embed numbers and punctuation throughout them Ca5dil4lac? ( 54 Cadillac) Use portions of names/words with numbers and punctuation separating them (Tom5Dic9Har! for Tom, Dick, and Harry) Pick a word that you can remember and move your fingers over on the keyboard (Security becomes Drvitoyu by moving one key to the right; add numbers and punctuation to improve the password) Remove the vowels from a word, but be sure to put some numbers and punctuation (information becomes 4Nf6rm=t[]n) Use a pass-phrase instead of a password. Pass-phrases are words or portions of words that make up a phrase or sentence. These may be longer than passwords but are safer and may be easier to remember. Examples of pass-phrases are: Now is the time for all good men NoIsThTiFoAlGoMe!@ takes the first two letters of each word and then ends the phrase with punctuation. Nit5tf9agm$ takes the first letter of the original phrase and adds numbers, punctuation, and mixes the case. Avoid using common pass-phrases that could be easily guessable, such as TeoTauy ( The eyes of Texas are upon you ). 4. Avoiding Problem Passwords Poorly constructed passwords are vulnerable to both social engineering attacks (people successfully guessing your password because they know something about you) or automated attacks (password cracking programs that use built-in rules and dictionaries to try to guess the password). To decrease the vulnerability of your password, use the password creation suggestions above and keep the following in mind: Don t use any word or phrase that people would associate with you from what they know about you (names, hobbies, interests, car license plates, hometown, etc.) Don t use any part of your name or your user name, or the name of anyone in your family (including pets) or close friends Password Security Guideline 2 Internal Use Only
5 Don t use any word found in any dictionary (including foreign language, medical, technical dictionaries). Password cracking programs use these for their attacks. Don t use any word or name found in current or recent popular culture (Star Trek, Harry Potter, music, NASCAR, sports, TV Shows, etc.). Password cracking programs have special dictionaries for these, including a Klingon language dictionary! Don t use any proper name Don t use names of famous people (Lincoln, Johnson, Carey) Don t use places (San Antonio, Beaumont, Virginia) Don t use things or objects (alligator, rodent, kangaroo) Don t take a dictionary word and add characters/numbers/punctuation to the beginning or end (armadillo32, oceans11, 54cadillac). Cracking programs know this trick too. Don t take a dictionary word and reverse it (rodeo oedor). This is also checked by cracking programs. Don t use strictly all letters or all numbers (FFGGHHJJ, ) Don t use any keyboard combinations (qwerty, asdfgh, cvbnm) Don t join common words together without something to break them up or change them (Moo$nS!tar instead of moonstar) Don t rely only on character substitutions that would be recognizable as hacker speak or l33t speak (pronounced leet speak ). The latest password crackers now recognize most of these substitutions. Some of the more common substitutions include numbers that look like letters (3 for e, 5 for s, 0 for o, 4 for A, etc.) 5. Changing Your Password Change your password when: Prompted to by the system. When your UTHSCSA password is about to expire, the system begins notifying you 14 days before. Change it promptly. If you have any reason to believe anyone else has obtained your password. 6. Did you forget your password? Faculty and Staff contact your Technical Support Representative or go to the Triage Help Desk Students Go to the Triage Help Desk or to the computer lab in the Briscoe Library The Triage Help Desk is in Computing Resources, Room 416.L in the Medical Building. You MUST bring your UTHSCSA identification card. NO passwords will be issued or reset over the phone. Password Security Guideline 3 Internal Use Only
6 7. Social Engineering Social engineering is the term given for convincing people to give confidential or compromising information about themselves or their organization by posing as someone in authority or as a technical representative. A common trick is for a cracker (posing as technical support) to contact the administrative staff of a busy department leader. Claiming to be working on the leader s account (always very important), the cracker will claim to need the leader s password to repair the account. No legitimate UTHSCSA employee will ever ask you to reveal your password. If anyone does ask for it, immediately contact your supervisor and the Triage Help Desk at Password Security Guideline 4 Internal Use Only
7 The following pages represent a template for creating departmental password security requirements; edit the pages following this one (where indicated in bold italic) to put in local information. For those sections regarding variation from University policy, minimum University requirements are shown; local policies may be more restrictive than University requirements, but can never be less restrictive. When editing, be sure to change any header and footer entries as well; once edited, the header and footer should appear properly. Password Security Guideline 5 Internal Use Only
8 Section: Information Security Revised: December 2004 Guideline: Description: Password Security Guidelines: are recommended processes, models, or actions to assist with implementing procedures with respect to the subject. Template Provider: Information Security Office PASSWORD SECURITY PROCEDURES for {insert departmental or organizational name here} Updated: {insert effective date here} Maintained by: Name: {insert local information} Department: {insert local information} Phone: {insert local information} {insert local information} {insert department name here} Password Procedures Confidentia
9 1. Policy It is the policy of The University of Texas Health Science Center at San Antonio (UTHSCSA) to protect its information resource assets and data with passwords, where appropriate. Since passwords act as the front-line of protection to University data, poorly chosen passwords or password behaviors may result in the compromise of the network and/or exposure of sensitive information. Information Security is everyone s responsibility, but management of information resources, systems, and their data within each department generally resides with departmental management. The following represents the password security requirements for {insert departmental information here}. 2. Password Use Rules Any password, whether it belongs to the user s UTHSCSA account or to a locally managed departmental server or system account, must be kept private and used only to the individual to whom it belongs. Administrators and system administrators in departments must put into place a routine for ensuring user accounts are not being misused and passwords are not being shared. This could involve security log checks compared to employee time records, or it could be implemented via an automated access auditing package in the server or application. 3. Password Strength Requirements Within the limits of the operating system or application, the password must meet the following requirements: Password length: {insert password length here; must be at least 8} characters Password complexity: at least {insert number of types of characters here; must be at least 3} of the following four (4) types of characters Upper case characters (A-Z). Lower case characters (a-z). Numerical characters (0-9) Special characters (!@#$%^&*()_+ ~-=\`{}[]:";'<>?,./) Passwords must maintain sufficient complexity by avoiding dictionary words (English, foreign language, or technical), personally identifiable or publicly available information, jargon, or word or number patterns Passwords must have a maximum age of {insert number of days here; must be 60 or less} days and a minimum age of {insert number of days here; must be 3 or more} days {insert department name here} Password Procedures 1 Confidentia
10 Each system must maintain a history of at least {insert number passwords remembered; must be at least 6} passwords Each system must lock an account for at least {insert lockout duration here; must be at least 15} minutes after {insert number of failed login attempts here; must be no more than 5} sequential invalid login attempts Passwords must NOT be stored in clear text or in any easily reversible form 4. Password Security Enforcement Password strength testing should be done periodically for all systems to assure that users are choosing secure passwords and following password guidelines. State and Federal requirements mandate that this function be limited to the Information Security Office for this University since knowledge of other users passwords constitutes an extremely HIGH security risk. 5. Password Generation Password generation utilities can be used if the resulting passwords are compliant with the Password Standard as described in paragraph 3 above. Steps must be taken that will prevent generated passwords from being stored in a readable or easily reversible form. Passwords created by web-based applications must be protected during generation and transmission using secure channels (i.e., SSL). {insert department name here} Password Procedures 2 Confidentia
Hitachi High Technologies America, Inc. Password Policy
 Hitachi High Technologies America, Inc. Password Policy Revision Date: 4/17/2015 Table of Contents Table of Contents...2 Overview...3 Scope. 3 Guidelines...3 A. General Password Construction Guidelines...3
Hitachi High Technologies America, Inc. Password Policy Revision Date: 4/17/2015 Table of Contents Table of Contents...2 Overview...3 Scope. 3 Guidelines...3 A. General Password Construction Guidelines...3
Create strong passwords
 Create strong passwords Passwords are the first line of defense against break-ins to your online accounts and computer, tablet, or phone. Poorly chosen passwords can render your information vulnerable
Create strong passwords Passwords are the first line of defense against break-ins to your online accounts and computer, tablet, or phone. Poorly chosen passwords can render your information vulnerable
PASSWORD POLICY. Policy Statement. Reason for Policy/Purpose. Who Needs to Know This Policy. Website Address for this Policy.
 Responsible University Administrator: Vice Provost for Academic Affairs Responsible Officer: Chief Information Officer Origination Date: N/A Current Revision Date: 02/19/13 Next Review Date: 02/19/17 End
Responsible University Administrator: Vice Provost for Academic Affairs Responsible Officer: Chief Information Officer Origination Date: N/A Current Revision Date: 02/19/13 Next Review Date: 02/19/17 End
Password Policy Best Practices
 Password Policy Best Practices 1.0 Overview Passwords are an important aspect of information security, and are the front line of protection for user accounts. A poorly chosen password may result in the
Password Policy Best Practices 1.0 Overview Passwords are an important aspect of information security, and are the front line of protection for user accounts. A poorly chosen password may result in the
TABLE OF CONTENTS. Lakehead University Password Maintenance Standard Operating Procedure
 TABLE OF CONTENTS 1.0 General Statement... 3 2.0 Purpose... 3 3.0 Scope... 3 4.0 Procedure... 3 4.1 General... 3 4.2 Requirements... 4 4.3 Guidelines... 4 5.0 Failure to comply... 6 2 1.0 GENERAL STATEMENT
TABLE OF CONTENTS 1.0 General Statement... 3 2.0 Purpose... 3 3.0 Scope... 3 4.0 Procedure... 3 4.1 General... 3 4.2 Requirements... 4 4.3 Guidelines... 4 5.0 Failure to comply... 6 2 1.0 GENERAL STATEMENT
COMPUTER PASSWORDS POLICY
 COMPUTER PASSWORDS POLICY 1.0 PURPOSE This policy describes the requirements for acceptable password selection and maintenance to maximize security of the password and minimize its misuse or theft. Passwords
COMPUTER PASSWORDS POLICY 1.0 PURPOSE This policy describes the requirements for acceptable password selection and maintenance to maximize security of the password and minimize its misuse or theft. Passwords
Password Standard Version 2.0 October 2006
 Password Standard Version 2.0 October 2006 TABLE OF CONTENTS 1.1 SCOPE 2 1.2 PRINCIPLES 2 1.3 REVISIONS 3 2.1 OBJECTIVE 4 3.1 POLICY 4 3.2 PROTECTION 4 3.3 LENGTH 4 3.4 SELECTIONS 4 3.5 EXPIRATION 5 3.6
Password Standard Version 2.0 October 2006 TABLE OF CONTENTS 1.1 SCOPE 2 1.2 PRINCIPLES 2 1.3 REVISIONS 3 2.1 OBJECTIVE 4 3.1 POLICY 4 3.2 PROTECTION 4 3.3 LENGTH 4 3.4 SELECTIONS 4 3.5 EXPIRATION 5 3.6
STEAM Clown Production. Passwords. STEAM Clown & Productions Copyright 2016 STEAM Clown. Page 1 - Cyber Security Class
 Production Passwords Page 1 - Cyber Security Class Copyright 2016 Does It Matter? Is your email password the same as your Facebook password? Is that Good? Bad? Why? Page 2 - Cyber Security Class Copyright
Production Passwords Page 1 - Cyber Security Class Copyright 2016 Does It Matter? Is your email password the same as your Facebook password? Is that Good? Bad? Why? Page 2 - Cyber Security Class Copyright
PASSWORD POLICY JANUARY 19, 2016 NEWBERRY COLLEGE 2100 College St., Newberry, SC 29108
 2016-2017 JANUARY 19, 2016 NEWBERRY COLLEGE 2100 College St., Newberry, SC 29108 Contents 1.0 Overview... 2 2.0 Purpose... 2 3.0 Scope... 2 4.0 Policy... 2 4.1 Guidelines... 2 4.2 Password Protection Standards...
2016-2017 JANUARY 19, 2016 NEWBERRY COLLEGE 2100 College St., Newberry, SC 29108 Contents 1.0 Overview... 2 2.0 Purpose... 2 3.0 Scope... 2 4.0 Policy... 2 4.1 Guidelines... 2 4.2 Password Protection Standards...
Troubleshooting. EAP-FAST Error Messages CHAPTER
 CHAPTER 6 This chapter describes EAP-FAST error messages. This chapter also provides guidelines for creating strong passwords. The following topics are covered in this chapter:, page 6-1 Creating Strong
CHAPTER 6 This chapter describes EAP-FAST error messages. This chapter also provides guidelines for creating strong passwords. The following topics are covered in this chapter:, page 6-1 Creating Strong
Signing up for My Lahey Chart
 Signing up for My Lahey Chart What is My Lahey Chart? My Lahey Chart is a helpful service that allows you to connect with your doctor and your health information online, anytime. Using your personal computer
Signing up for My Lahey Chart What is My Lahey Chart? My Lahey Chart is a helpful service that allows you to connect with your doctor and your health information online, anytime. Using your personal computer
POLICY 8200 NETWORK SECURITY
 POLICY 8200 NETWORK SECURITY Policy Category: Information Technology Area of Administrative Responsibility: Information Technology Services Board of Trustees Approval Date: April 17, 2018 Effective Date:
POLICY 8200 NETWORK SECURITY Policy Category: Information Technology Area of Administrative Responsibility: Information Technology Services Board of Trustees Approval Date: April 17, 2018 Effective Date:
5 MANAGING USER ACCOUNTS AND GROUPS
 MANAGING USER ACCOUNTS AND GROUPS.1 Introduction to user accounts Objectives.2 Types of User Accounts.2.1 Local User Account.2.2 Built-in User Account.2.3 Domain User Account.3 User Profile.3.1 Content
MANAGING USER ACCOUNTS AND GROUPS.1 Introduction to user accounts Objectives.2 Types of User Accounts.2.1 Local User Account.2.2 Built-in User Account.2.3 Domain User Account.3 User Profile.3.1 Content
Department of Public Health O F S A N F R A N C I S C O
 PAGE 1 of 9 Category: Information Technology Security and HIPAA DPH Unit of Origin: Department of Public Health Policy Owner: Phillip McDown, CISSP Phone: 255-3577 CISSPCISSP/C Distribution: DPH-wide Other:
PAGE 1 of 9 Category: Information Technology Security and HIPAA DPH Unit of Origin: Department of Public Health Policy Owner: Phillip McDown, CISSP Phone: 255-3577 CISSPCISSP/C Distribution: DPH-wide Other:
Maria Hishikawa MSIX Technical Lead Sarah Storms MSIX Contractor Security
 Migrant Student Information Exchange (MSIX) Security, Privacy and Account Management Webinar Deloitte Consulting LLP. February 22, 2018 Maria Hishikawa MSIX Technical Lead Sarah Storms MSIX Contractor
Migrant Student Information Exchange (MSIX) Security, Privacy and Account Management Webinar Deloitte Consulting LLP. February 22, 2018 Maria Hishikawa MSIX Technical Lead Sarah Storms MSIX Contractor
MANAGING LOCAL AUTHENTICATION IN WINDOWS
 MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
Configuring Facebook for a More Secure Social Networking Experience
 CPF 0037-14-CID361-9H-Facebook* 5 December 2014 Configuring Facebook for a More Secure Social Networking Experience Settings Settings are available under the Facebook Configuration Arrow. General Settings
CPF 0037-14-CID361-9H-Facebook* 5 December 2014 Configuring Facebook for a More Secure Social Networking Experience Settings Settings are available under the Facebook Configuration Arrow. General Settings
ANNUAL SECURITY AWARENESS TRAINING 2012
 UMW Information Technology Security Program Annual Security Awareness Training for UMW Faculty and Staff ANNUAL SECURITY AWARENESS TRAINING 2012 NETWORK AND COMPUTER USE POLICY Users of information technology
UMW Information Technology Security Program Annual Security Awareness Training for UMW Faculty and Staff ANNUAL SECURITY AWARENESS TRAINING 2012 NETWORK AND COMPUTER USE POLICY Users of information technology
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE. Microsoft Windows Security.
 AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE Microsoft Windows Security www.uscyberpatriot.org AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION
AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION PROGRAM UNIT FIVE Microsoft Windows Security www.uscyberpatriot.org AIR FORCE ASSOCIATION S CYBERPATRIOT NATIONAL YOUTH CYBER EDUCATION
Tennessee Technological University Policy No Password Management
 Tennessee Technological University Policy No. 852 Password Management Effective Date: January 1, 2014 Policy No: 852 Policy Name: Password Management Policy Policy Subject: Password Management Date Revised:
Tennessee Technological University Policy No. 852 Password Management Effective Date: January 1, 2014 Policy No: 852 Policy Name: Password Management Policy Policy Subject: Password Management Date Revised:
Red Flag Regulations
 Red Flag Regulations Identity Theft Put In Context Overview of Topics Red Flag Regulations Overview How UM Protects Information What is the Student Workers role in identity theft prevention? What s this
Red Flag Regulations Identity Theft Put In Context Overview of Topics Red Flag Regulations Overview How UM Protects Information What is the Student Workers role in identity theft prevention? What s this
SERVER HARDENING CHECKLIST
 SERVER HARDENING CHECKLIST WINDOWS 2003 SERVER CHECKLIST This checklist contains server hardening procedures for Windows 2003 Server. The procedures listed in this document are a balance of industry best
SERVER HARDENING CHECKLIST WINDOWS 2003 SERVER CHECKLIST This checklist contains server hardening procedures for Windows 2003 Server. The procedures listed in this document are a balance of industry best
Table of Contents. Blog and Personal Web Site Policy
 Table of Contents Blog and Personal Web Sites Policy... 2 Policy... 2 Rights to content... 3 Option for More Restrictive License Terms... 3 Attribution... 4 Guidelines... 4 Personal Website and Blog Guidelines
Table of Contents Blog and Personal Web Sites Policy... 2 Policy... 2 Rights to content... 3 Option for More Restrictive License Terms... 3 Attribution... 4 Guidelines... 4 Personal Website and Blog Guidelines
UT HEALTH SAN ANTONIO HANDBOOK OF OPERATING PROCEDURES
 ACCESS MANAGEMENT Policy UT Health San Antonio shall adopt access management processes to ensure that access to Information Resources is restricted to authorized users with minimal access rights necessary
ACCESS MANAGEMENT Policy UT Health San Antonio shall adopt access management processes to ensure that access to Information Resources is restricted to authorized users with minimal access rights necessary
Sensitive Data Security Primer
 Sensitive Data Security Primer Only You Can Prevent Security Incidents Keith R. Watson CoC Information Security Manager Sensitive Data Security Primer Page 1 of 12 Revision: 20100112A Abstract Everyone
Sensitive Data Security Primer Only You Can Prevent Security Incidents Keith R. Watson CoC Information Security Manager Sensitive Data Security Primer Page 1 of 12 Revision: 20100112A Abstract Everyone
Subject: University Information Technology Resource Security Policy: OUTDATED
 Policy 1-18 Rev. 2 Date: September 7, 2006 Back to Index Subject: University Information Technology Resource Security Policy: I. PURPOSE II. University Information Technology Resources are at risk from
Policy 1-18 Rev. 2 Date: September 7, 2006 Back to Index Subject: University Information Technology Resource Security Policy: I. PURPOSE II. University Information Technology Resources are at risk from
Medical Sciences Division IT Services (MSD IT)
 Medical Sciences Division IT Services (MSD IT) Security Policy Effective date: 1 December 2017 1 Overview MSD IT provides IT support services support and advice to the University of Oxford Medical Sciences
Medical Sciences Division IT Services (MSD IT) Security Policy Effective date: 1 December 2017 1 Overview MSD IT provides IT support services support and advice to the University of Oxford Medical Sciences
Activity 1: Using Windows XP Professional Security Checklist
 Activity 1: Using Windows XP Professional Security Checklist Verify that all Disk partitions are Formatted with NTFS NTFS partitions offer access controls and protections that aren't available with the
Activity 1: Using Windows XP Professional Security Checklist Verify that all Disk partitions are Formatted with NTFS NTFS partitions offer access controls and protections that aren't available with the
Computer Security 3e. Dieter Gollmann. Security.di.unimi.it/1516/ Chapter 4: 1
 Computer Security 3e Dieter Gollmann Security.di.unimi.it/1516/ Chapter 4: 1 Chapter 4: Identification & Authentication Chapter 4: 2 Agenda User authentication Identification & authentication Passwords
Computer Security 3e Dieter Gollmann Security.di.unimi.it/1516/ Chapter 4: 1 Chapter 4: Identification & Authentication Chapter 4: 2 Agenda User authentication Identification & authentication Passwords
Summary
 The Imperva Application Defense Center (ADC) ADC White Paper Summary In December 2009, a major password breach occurred that led to the release of 32 million passwords 1. Further, the hacker posted to
The Imperva Application Defense Center (ADC) ADC White Paper Summary In December 2009, a major password breach occurred that led to the release of 32 million passwords 1. Further, the hacker posted to
Sumy State University Department of Computer Science
 Sumy State University Department of Computer Science Lecture 1 (part 2). Access control. What is access control? A cornerstone in the foundation of information security is controlling how resources are
Sumy State University Department of Computer Science Lecture 1 (part 2). Access control. What is access control? A cornerstone in the foundation of information security is controlling how resources are
Security Awareness Training June 2016
 Security Awareness Training June 2016 What is Information Security Awareness? The University of North Carolina at Chapel Hill protects its data network from thousands of daily intrusion attempts, but technical
Security Awareness Training June 2016 What is Information Security Awareness? The University of North Carolina at Chapel Hill protects its data network from thousands of daily intrusion attempts, but technical
Cisco WebEx Best Practices for Secure Meetings for Site Administrators and Hosts
 Cisco WebEx Best Practices for Secure Meetings for Site Administrators and Hosts First Published: 2016-04-04 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA
Cisco WebEx Best Practices for Secure Meetings for Site Administrators and Hosts First Published: 2016-04-04 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA
Integration of Agilent OpenLAB CDS EZChrom Edition with OpenLAB ECM Compliance with 21 CFR Part 11
 OpenLAB CDS Integration of Agilent OpenLAB CDS EZChrom Edition with OpenLAB ECM Compliance with 21 CFR Part 11 Technical Note Introduction Part 11 in Title 21 of the Code of Federal Regulations includes
OpenLAB CDS Integration of Agilent OpenLAB CDS EZChrom Edition with OpenLAB ECM Compliance with 21 CFR Part 11 Technical Note Introduction Part 11 in Title 21 of the Code of Federal Regulations includes
Cleveland State University General Policy for University Information and Technology Resources
 Cleveland State University General Policy for University Information and Technology Resources 08/13/2007 1 Introduction As an institution of higher learning, Cleveland State University both uses information
Cleveland State University General Policy for University Information and Technology Resources 08/13/2007 1 Introduction As an institution of higher learning, Cleveland State University both uses information
Using your Employer Account
 Effective November 1, 2013, EIT Benefit Funds ( Fund Office ) the monthly Employer Work Reports are no longer sent via mail to you and are only available to be printed directly from the EIT Benefit Funds'
Effective November 1, 2013, EIT Benefit Funds ( Fund Office ) the monthly Employer Work Reports are no longer sent via mail to you and are only available to be printed directly from the EIT Benefit Funds'
Configuring Twitter for a More Secure Social Networking Experience
 CPF 0037-14-CID361-9H-Twitter* 5 December 2014 Configuring Twitter for a More Secure Social Networking Experience Basic Notes About Twitter Configuration Twitter is an integral thread in the fabric of
CPF 0037-14-CID361-9H-Twitter* 5 December 2014 Configuring Twitter for a More Secure Social Networking Experience Basic Notes About Twitter Configuration Twitter is an integral thread in the fabric of
Security Awareness. Presented by OSU Institute of Technology
 Security Awareness Presented by OSU Institute of Technology Information Technologies Division Security Awareness Topics Social Engineering Phishing Social Networks Displaying Sensitive Information Wireless
Security Awareness Presented by OSU Institute of Technology Information Technologies Division Security Awareness Topics Social Engineering Phishing Social Networks Displaying Sensitive Information Wireless
ADOPTED STANDARDS/POLICIES. Information Technology Security Policy
 INFORMATION TECHNOLOGY POLICY BOARD ADOPTED STANDARDS/POLICIES Information Technology Security Policy COUNTY OF SACRAMENTO Office of Communications and Information Technology TO: Agency Administrators,
INFORMATION TECHNOLOGY POLICY BOARD ADOPTED STANDARDS/POLICIES Information Technology Security Policy COUNTY OF SACRAMENTO Office of Communications and Information Technology TO: Agency Administrators,
UTAH VALLEY UNIVERSITY Policies and Procedures
 Page 1 of 5 POLICY TITLE Section Subsection Responsible Office Private Sensitive Information Facilities, Operations, and Information Technology Information Technology Office of the Vice President of Information
Page 1 of 5 POLICY TITLE Section Subsection Responsible Office Private Sensitive Information Facilities, Operations, and Information Technology Information Technology Office of the Vice President of Information
SWAMID Person-Proofed Multi-Factor Profile
 Document SWAMID Person-Proofed Multi-Factor Profile Identifier http://www.swamid.se/policy/assurance/al2mfa Version V1.0 Last modified 2018-09-12 Pages 10 Status FINAL License Creative Commons BY-SA 3.0
Document SWAMID Person-Proofed Multi-Factor Profile Identifier http://www.swamid.se/policy/assurance/al2mfa Version V1.0 Last modified 2018-09-12 Pages 10 Status FINAL License Creative Commons BY-SA 3.0
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
Activating your S Number User Guide
 Activating your S Number User Guide Griffith College Activating your S Number User Guide Activating your S Number User Guide Table of Contents Introduction... 3 Email sent to your G mail account... 3 Students
Activating your S Number User Guide Griffith College Activating your S Number User Guide Activating your S Number User Guide Table of Contents Introduction... 3 Email sent to your G mail account... 3 Students
Red Flags/Identity Theft Prevention Policy: Purpose
 Red Flags/Identity Theft Prevention Policy: 200.3 Purpose Employees and students depend on Morehouse College ( Morehouse ) to properly protect their personal non-public information, which is gathered and
Red Flags/Identity Theft Prevention Policy: 200.3 Purpose Employees and students depend on Morehouse College ( Morehouse ) to properly protect their personal non-public information, which is gathered and
Virtual Product Fair. Protect your agency data protect your business
 Virtual Product Fair Protect your agency data protect your business October 2011 2 Are you doing all that you can to protect your business? Agenda Background Fraudulent activities Sabre actions Steps you
Virtual Product Fair Protect your agency data protect your business October 2011 2 Are you doing all that you can to protect your business? Agenda Background Fraudulent activities Sabre actions Steps you
. Account & Google Message Center Guide. January Prepared by: Angela Mars IT Education and Training
 Email Account & Google Message Center Guide January 2019 Prepared by: Angela Mars IT Education and Training Table Of Contents Email Account Information Page 4 Safe Email Practices Page 5 Recommended Email
Email Account & Google Message Center Guide January 2019 Prepared by: Angela Mars IT Education and Training Table Of Contents Email Account Information Page 4 Safe Email Practices Page 5 Recommended Email
Cyber Security Program
 Cyber Security Program Cyber Security Program Goals and Objectives Goals Provide comprehensive Security Education and Awareness to the University community Build trust with the University community by
Cyber Security Program Cyber Security Program Goals and Objectives Goals Provide comprehensive Security Education and Awareness to the University community Build trust with the University community by
The Honest Advantage
 The Honest Advantage READY TO CHALLENGE THE STATUS QUO GSA Security Policy and PCI Guidelines The GreenStar Alliance 2017 2017 GreenStar Alliance All Rights Reserved Table of Contents Table of Contents
The Honest Advantage READY TO CHALLENGE THE STATUS QUO GSA Security Policy and PCI Guidelines The GreenStar Alliance 2017 2017 GreenStar Alliance All Rights Reserved Table of Contents Table of Contents
Chapter 3: User Authentication
 Chapter 3: User Authentication Comp Sci 3600 Security Outline 1 2 3 4 Outline 1 2 3 4 User Authentication NIST SP 800-63-3 (Digital Authentication Guideline, October 2016) defines user as: The process
Chapter 3: User Authentication Comp Sci 3600 Security Outline 1 2 3 4 Outline 1 2 3 4 User Authentication NIST SP 800-63-3 (Digital Authentication Guideline, October 2016) defines user as: The process
HELPFUL TIPS: MOBILE DEVICE SECURITY
 HELPFUL TIPS: MOBILE DEVICE SECURITY Privacy tips for Public Bodies/Trustees using mobile devices This document is intended to provide general advice to organizations on how to protect personal information
HELPFUL TIPS: MOBILE DEVICE SECURITY Privacy tips for Public Bodies/Trustees using mobile devices This document is intended to provide general advice to organizations on how to protect personal information
Security and Privacy. Security or Privacy? Computer Security
 2110413 Computer Security Security & Privacy: the definitions Security Components Supporting Concepts Krerk Piromsopa, Ph.D. Department of Computer Engineering Chulalongkorn University Authentication Security
2110413 Computer Security Security & Privacy: the definitions Security Components Supporting Concepts Krerk Piromsopa, Ph.D. Department of Computer Engineering Chulalongkorn University Authentication Security
HIPAA Assessment. Prepared For: ABC Medical Center Prepared By: Compliance Department
 HIPAA Assessment Prepared For: ABC Medical Center Prepared By: Compliance Department Agenda Environment Assessment Overview Risk and Issue Score Next Steps Environment NETWORK ASSESSMENT (changes) Domain
HIPAA Assessment Prepared For: ABC Medical Center Prepared By: Compliance Department Agenda Environment Assessment Overview Risk and Issue Score Next Steps Environment NETWORK ASSESSMENT (changes) Domain
2017_Privacy and Information Security_English_Content
 2017_Privacy and Information Security_English_Content 2.3 Staff includes all permanent or temporary, full-time, part-time, casual or contract employees, trainees and volunteers, including but not limited
2017_Privacy and Information Security_English_Content 2.3 Staff includes all permanent or temporary, full-time, part-time, casual or contract employees, trainees and volunteers, including but not limited
System Assessment Report Relating to Electronic Records and Electronic Signatures; 21 CFR Part 11. System: tiamo (Software Version 2.
 Page 1 /15 System Assessment Report Relating to Electronic Records and Electronic Signatures; 21 CFR Part 11 System: tiamo (Software Version 2.5) Page 2 /15 1 Procedures and Controls for Closed Systems
Page 1 /15 System Assessment Report Relating to Electronic Records and Electronic Signatures; 21 CFR Part 11 System: tiamo (Software Version 2.5) Page 2 /15 1 Procedures and Controls for Closed Systems
MODULE NO.28: Password Cracking
 SUBJECT Paper No. and Title Module No. and Title Module Tag PAPER No. 16: Digital Forensics MODULE No. 28: Password Cracking FSC_P16_M28 TABLE OF CONTENTS 1. Learning Outcomes 2. Introduction 3. Nature
SUBJECT Paper No. and Title Module No. and Title Module Tag PAPER No. 16: Digital Forensics MODULE No. 28: Password Cracking FSC_P16_M28 TABLE OF CONTENTS 1. Learning Outcomes 2. Introduction 3. Nature
Configuring Facebook for a More Secure Social Networking Experience
 CPF 00004-16-CID361-9H-Facebook* 8 March 2017 Configuring Facebook for a More Secure Social Networking Experience Settings Settings are available under the Facebook Configuration Arrow. General Account
CPF 00004-16-CID361-9H-Facebook* 8 March 2017 Configuring Facebook for a More Secure Social Networking Experience Settings Settings are available under the Facebook Configuration Arrow. General Account
Cisco WebEx Best Practices for Secure Meetings for Hosts. Cisco WebEx Best Practices for Secure Meetings
 Cisco WebEx Best Practices for Secure Meetings for Hosts Cisco WebEx Best Practices for Secure Meetings for Hosts 1 Overview of WebEx Security Overview of WebEx Security Cisco WebEx online solutions help
Cisco WebEx Best Practices for Secure Meetings for Hosts Cisco WebEx Best Practices for Secure Meetings for Hosts 1 Overview of WebEx Security Overview of WebEx Security Cisco WebEx online solutions help
PBX Fraud Information
 PBX Fraud Information Increasingly, hackers are gaining access to corporate phone and/or voice mail systems. These individuals place long distance and international calls through major telecom networks
PBX Fraud Information Increasingly, hackers are gaining access to corporate phone and/or voice mail systems. These individuals place long distance and international calls through major telecom networks
Applying for EMSWCD Small Project and Community Events (SPACE) Grants
 ZOOMGRANTS TUTORIAL Applying for EMSWCD Small Project and Community Events (SPACE) Grants Instructions for ZoomGrants ZoomGrants is an online tool that helps facilitate grant applications, committee review,
ZOOMGRANTS TUTORIAL Applying for EMSWCD Small Project and Community Events (SPACE) Grants Instructions for ZoomGrants ZoomGrants is an online tool that helps facilitate grant applications, committee review,
WELCOME TO ACE GROUP Table of Contents
 WELCOME TO ACE GROUP Table of Contents Introduction... 2 VDI s What are they, and why do we need them?... 2 Contacting the Help Desk... 2 Registering Symantec VIP... 3 Connecting to your ACE VDI via Web
WELCOME TO ACE GROUP Table of Contents Introduction... 2 VDI s What are they, and why do we need them?... 2 Contacting the Help Desk... 2 Registering Symantec VIP... 3 Connecting to your ACE VDI via Web
The English School Network
 The English School Network What is my NetID? Your NetID is the only username and password that is used to access computer systems at The English School. Email, workstations and WIFI all use the same user
The English School Network What is my NetID? Your NetID is the only username and password that is used to access computer systems at The English School. Email, workstations and WIFI all use the same user
Password-Handling Guidelines
 Tutorials, A. Allan, R. Witty Research Note 22 December 2003 Best Practices for Managing Passwords: Usage Guidelines Good password-handling rules limit opportunities for attackers to discover passwords.
Tutorials, A. Allan, R. Witty Research Note 22 December 2003 Best Practices for Managing Passwords: Usage Guidelines Good password-handling rules limit opportunities for attackers to discover passwords.
Policy & Procedure. IT Password Policy. Policy Area. Version Number 2. Approving Committee SMT. Date of Approval 26 September 2017
 Policy & Procedure Policy Area IT Password Policy IT Version Number 2 Approving Committee SMT Date of Approval 26 September 2017 Date of Equality Impact Assessment 03 August 2016 Date of Review 01 November
Policy & Procedure Policy Area IT Password Policy IT Version Number 2 Approving Committee SMT Date of Approval 26 September 2017 Date of Equality Impact Assessment 03 August 2016 Date of Review 01 November
Access to University Data Policy
 UNIVERSITY OF OKLAHOMA Health Sciences Center Information Technology Security Policy Access to University Data Policy 1. Purpose This policy defines roles and responsibilities for protecting OUHSC s non-public
UNIVERSITY OF OKLAHOMA Health Sciences Center Information Technology Security Policy Access to University Data Policy 1. Purpose This policy defines roles and responsibilities for protecting OUHSC s non-public
How to Build a Culture of Security
 How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in InCommon Federation ( Federation ) enables the participant to use Shibboleth identity attribute sharing technologies to manage access
a. UTRGV owned, leased or managed computers that fall within the regular UTRGV Computer Security Standard
 Kiosk Security Standard 1. Purpose This standard was created to set minimum requirements for generally shared devices that need to be easily accessible for faculty, staff, students, and the general public,
Kiosk Security Standard 1. Purpose This standard was created to set minimum requirements for generally shared devices that need to be easily accessible for faculty, staff, students, and the general public,
Scheduling WebEx Meetings
 Scheduling WebEx Meetings Instructions for ConnSCU Faculty and Staff using ConnSCU WebEx Table of Contents How Can Faculty and Staff Use WebEx?... 2 Meeting Attendees... 2 Schedule WebEx Meetings from
Scheduling WebEx Meetings Instructions for ConnSCU Faculty and Staff using ConnSCU WebEx Table of Contents How Can Faculty and Staff Use WebEx?... 2 Meeting Attendees... 2 Schedule WebEx Meetings from
Contents. Is Rumpus Secure? 2. Use Care When Creating User Accounts 2. Managing Passwords 3. Watch Out For Symbolic Links 4. Deploy A Firewall 5
 Contents Is Rumpus Secure? 2 Use Care When Creating User Accounts 2 Managing Passwords 3 Watch Out For Symbolic Links 4 Deploy A Firewall 5 Minimize Running Applications And Processes 5 Manage Physical
Contents Is Rumpus Secure? 2 Use Care When Creating User Accounts 2 Managing Passwords 3 Watch Out For Symbolic Links 4 Deploy A Firewall 5 Minimize Running Applications And Processes 5 Manage Physical
1. Federation Participant Information DRAFT
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES [NOTE: This document should be considered a as MIT is still in the process of spinning up its participation in InCommon.] Participation in InCommon
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES [NOTE: This document should be considered a as MIT is still in the process of spinning up its participation in InCommon.] Participation in InCommon
IDENTITY THEFT PREVENTION Policy Statement
 Responsible University Officials: Vice President for Financial Operations and Treasurer Responsible Office: Office of Financial Operations Origination Date: October 13, 2009 IDENTITY THEFT PREVENTION Policy
Responsible University Officials: Vice President for Financial Operations and Treasurer Responsible Office: Office of Financial Operations Origination Date: October 13, 2009 IDENTITY THEFT PREVENTION Policy
InCommon Federation: Participant Operational Practices
 InCommon Federation: Participant Operational Practices Participation in the InCommon Federation ( Federation ) enables a federation participating organization ( Participant ) to use Shibboleth identity
InCommon Federation: Participant Operational Practices Participation in the InCommon Federation ( Federation ) enables a federation participating organization ( Participant ) to use Shibboleth identity
OpenLAB ELN Supporting 21 CFR Part 11 Compliance
 OpenLAB ELN Supporting 21 CFR Part 11 Compliance White Paper Overview Part 11 in Title 21 of the Code of Federal Regulations includes the US Federal guidelines for storing and protecting electronic records
OpenLAB ELN Supporting 21 CFR Part 11 Compliance White Paper Overview Part 11 in Title 21 of the Code of Federal Regulations includes the US Federal guidelines for storing and protecting electronic records
Freedom of Information and Protection of Privacy (FOIPOP)
 Freedom of Information and Protection of Privacy (FOIPOP) No.: 6700 PR1 Policy Reference: 6700 Category: FOIPOP Department Responsible: Records Management and Privacy Current Approved Date: 2008 Sep 30
Freedom of Information and Protection of Privacy (FOIPOP) No.: 6700 PR1 Policy Reference: 6700 Category: FOIPOP Department Responsible: Records Management and Privacy Current Approved Date: 2008 Sep 30
Configuring Twitter for a More Secure Social Networking Experience
 CPF 00006-18-CID361-9H 8 November 2018 Configuring Twitter for a More Secure Social Networking Experience Basic Notes About Social Media The internet s social media ecosystem is vast. To some people, social
CPF 00006-18-CID361-9H 8 November 2018 Configuring Twitter for a More Secure Social Networking Experience Basic Notes About Social Media The internet s social media ecosystem is vast. To some people, social
Access Control Procedure
 HIPAA Security Procedure # Last Revised: 3/15/2006 Approved: Scope of Procedure The scope of this Policy covers the unique user identification and password, emergency access, automatic logoff, encryption
HIPAA Security Procedure # Last Revised: 3/15/2006 Approved: Scope of Procedure The scope of this Policy covers the unique user identification and password, emergency access, automatic logoff, encryption
Passwords. Secure Software Systems
 1 Passwords 2 Password Lifecycle Change/Reset Password Create Password (user choice) Use Password (user supplies for auth) Store Password (with user identifier) 3 Password Creation 4 Password Creation
1 Passwords 2 Password Lifecycle Change/Reset Password Create Password (user choice) Use Password (user supplies for auth) Store Password (with user identifier) 3 Password Creation 4 Password Creation
Scheduling WebEx Meetings
 Scheduling WebEx Meetings Table of Contents How Can Faculty and Staff Host WebEx Meetings?... 2 Meeting Attendees... 2 About your WebEx Personal Room... 2 How to Launch Your Personal Room from the CSCU
Scheduling WebEx Meetings Table of Contents How Can Faculty and Staff Host WebEx Meetings?... 2 Meeting Attendees... 2 About your WebEx Personal Room... 2 How to Launch Your Personal Room from the CSCU
IT Governance Committee Review and Recommendation
 IT Governance Committee Review and Recommendation Desired Change: Approval of this policy will establish Security Standards for the UCLA Logon Identity for anyone assigned a UCLA Logon ID/password and
IT Governance Committee Review and Recommendation Desired Change: Approval of this policy will establish Security Standards for the UCLA Logon Identity for anyone assigned a UCLA Logon ID/password and
Employee Security Awareness Training
 Employee Security Awareness Training September 2016 Purpose Employees have access to sensitive data through the work they perform for York. Examples of sensitive data include social security numbers, medical
Employee Security Awareness Training September 2016 Purpose Employees have access to sensitive data through the work they perform for York. Examples of sensitive data include social security numbers, medical
ChromQuest 5.0. Tools to Aid in 21 CFR Part 11 Compliance. Introduction. General Overview. General Considerations
 ChromQuest 5.0 Tools to Aid in 21 CFR Part 11 Compliance Introduction Thermo Scientific, Inc. is pleased to offer the ChromQuest chromatography data system (CDS) as a solution for chromatography labs seeking
ChromQuest 5.0 Tools to Aid in 21 CFR Part 11 Compliance Introduction Thermo Scientific, Inc. is pleased to offer the ChromQuest chromatography data system (CDS) as a solution for chromatography labs seeking
HIPAA Privacy & Security Training. HIPAA The Health Insurance Portability and Accountability Act of 1996
 HIPAA Privacy & Security Training HIPAA The Health Insurance Portability and Accountability Act of 1996 AMTA confidentiality requirements AMTA Professional Competencies 20. Documentation 20.7 Demonstrate
HIPAA Privacy & Security Training HIPAA The Health Insurance Portability and Accountability Act of 1996 AMTA confidentiality requirements AMTA Professional Competencies 20. Documentation 20.7 Demonstrate
Credentials Policy. Document Summary
 Credentials Policy Document Summary Document ID Credentials Policy Status Approved Information Classification Public Document Version 1.0 May 2017 1. Purpose and Scope The Royal Holloway Credentials Policy
Credentials Policy Document Summary Document ID Credentials Policy Status Approved Information Classification Public Document Version 1.0 May 2017 1. Purpose and Scope The Royal Holloway Credentials Policy
IAM Security & Privacy Policies Scott Bradner
 IAM Security & Privacy Policies Scott Bradner November 24, 2015 December 2, 2015 Tuesday Wednesday 9:30-10:30 a.m. 10:00-11:00 a.m. 6 Story St. CR Today s Agenda How IAM Security and Privacy Policies Complement
IAM Security & Privacy Policies Scott Bradner November 24, 2015 December 2, 2015 Tuesday Wednesday 9:30-10:30 a.m. 10:00-11:00 a.m. 6 Story St. CR Today s Agenda How IAM Security and Privacy Policies Complement
System Assessment Report Relating to Electronic Records and Electronic Signatures; 21 CFR Part 11. System: StabNet (Software Version 1.
 Page 1 /16 System Assessment Report Relating to Electronic Records and Electronic Signatures; 21 CFR Part 11 System: StabNet (Software Version 1.1) Page 2 /16 1 Procedures and Controls for Closed Systems
Page 1 /16 System Assessment Report Relating to Electronic Records and Electronic Signatures; 21 CFR Part 11 System: StabNet (Software Version 1.1) Page 2 /16 1 Procedures and Controls for Closed Systems
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES
 INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
INCOMMON FEDERATION: PARTICIPANT OPERATIONAL PRACTICES Participation in the InCommon Federation ( Federation ) enables a federation participating organization ("Participant") to use Shibboleth identity
CISNTWK-11. Microsoft Network Server. Chapter 4
 CISNTWK-11 Microsoft Network Server Chapter 4 User and Group Accounts 1 Usage Notes Throughout these slides, the term Active Directory Domain implies Domains Based on Windows Server 2008 Based on Windows
CISNTWK-11 Microsoft Network Server Chapter 4 User and Group Accounts 1 Usage Notes Throughout these slides, the term Active Directory Domain implies Domains Based on Windows Server 2008 Based on Windows
Hong Kong Access Federation (HKAF) Identity Management Practice Statement (IMPS)
 Hong Kong Access Federation (HKAF) Identity Management Practice Statement (IMPS) This document (IMPS) facilitates an organization to provide relevant information to describe how it fulfils the normative
Hong Kong Access Federation (HKAF) Identity Management Practice Statement (IMPS) This document (IMPS) facilitates an organization to provide relevant information to describe how it fulfils the normative
Conveying Emotion. Chapter 12: Computers In Polite Society: Social Implications of IT. Improving the Effectiveness of . Problems with
 Chapter 12: Computers In Polite Society: Social Implications of IT Fluency with Information Technology Third Edition by Lawrence Snyder Improving the Effectiveness of Email Problems with email: Conveying
Chapter 12: Computers In Polite Society: Social Implications of IT Fluency with Information Technology Third Edition by Lawrence Snyder Improving the Effectiveness of Email Problems with email: Conveying
HIPAA Privacy & Security Training. Privacy and Security of Protected Health Information
 HIPAA Privacy & Security Training Privacy and Security of Protected Health Information Course Competencies: This training module addresses the essential elements of maintaining the HIPAA Privacy and Security
HIPAA Privacy & Security Training Privacy and Security of Protected Health Information Course Competencies: This training module addresses the essential elements of maintaining the HIPAA Privacy and Security
BETTER LOOKING S
 BETTER LOOKING EMAILS First impressions matter. So if you want a positive response to your email campaign you need to make a positive first impression. Here are some simple design strategies to help you
BETTER LOOKING EMAILS First impressions matter. So if you want a positive response to your email campaign you need to make a positive first impression. Here are some simple design strategies to help you
Compliance & HIPAA Annual Education
 Compliance & HIPAA Annual Education 1 The purpose of this education is to UPDATE The purpose and of this education REFRESH is to UPDATE your and REFRESH understanding understanding of: of: Aultman s Compliance
Compliance & HIPAA Annual Education 1 The purpose of this education is to UPDATE The purpose and of this education REFRESH is to UPDATE your and REFRESH understanding understanding of: of: Aultman s Compliance
Recipe for a Breach: Uncontrolled Employee Access + Poor Security Habits Employee Security Habits Reveal Risky Imbalance
 Survey Report Recipe for a Breach: Uncontrolled Employee Access + Poor Security Habits Employee Security Habits Reveal Risky Imbalance November 2017 INTRODUCTION When thinking of insider threats, we often
Survey Report Recipe for a Breach: Uncontrolled Employee Access + Poor Security Habits Employee Security Habits Reveal Risky Imbalance November 2017 INTRODUCTION When thinking of insider threats, we often
T-SYSTEMS MULTIMEDIA SOLUTIONS ADMINISTRATION MANUAL
 T-SYSTEMS MULTIMEDIA SOLUTIONS ADMINISTRATION MANUAL DOCULIFE DESKTOP 5.6 DATE: 16.03.2015 Document Future AG 03/2015 Document Future AG holds the copyright to this documentation. No part of this documentation
T-SYSTEMS MULTIMEDIA SOLUTIONS ADMINISTRATION MANUAL DOCULIFE DESKTOP 5.6 DATE: 16.03.2015 Document Future AG 03/2015 Document Future AG holds the copyright to this documentation. No part of this documentation
System Assessment Report Relating to Electronic Records and Electronic Signatures; Final Rule, 21 CFR Part 11. System: tiamo 2.3
 Page 1 /14 System Assessment Report Relating to Electronic Records and Electronic Signatures; Final le, 21 CFR Part 11 System: tiamo 23 052011 / doe Page 2 /14 1 Procedures and Controls for Closed Systems
Page 1 /14 System Assessment Report Relating to Electronic Records and Electronic Signatures; Final le, 21 CFR Part 11 System: tiamo 23 052011 / doe Page 2 /14 1 Procedures and Controls for Closed Systems
Who are you? Enter userid and password. Means of Authentication. Authentication 2/19/2010 COMP Authentication is the process of verifying that
 Who are you? Authentication COMP620 Authentication is the process of verifying that the user or system is who they claim li to be. A system may be acting on behalf of a given principal. Authentication
Who are you? Authentication COMP620 Authentication is the process of verifying that the user or system is who they claim li to be. A system may be acting on behalf of a given principal. Authentication
WHY EFFECTIVE WEB WRITING MATTERS Web users read differently on the web. They rarely read entire pages, word for word.
 Web Writing 101 WHY EFFECTIVE WEB WRITING MATTERS Web users read differently on the web. They rarely read entire pages, word for word. Instead, users: Scan pages Pick out key words and phrases Read in
Web Writing 101 WHY EFFECTIVE WEB WRITING MATTERS Web users read differently on the web. They rarely read entire pages, word for word. Instead, users: Scan pages Pick out key words and phrases Read in
Using WebBoard at UIS
 Using WebBoard at UIS Accessing your WebBoard Course...3 Logging in to WebBoard...3 Understanding the WebBoard Environment...4 The Menubar...5 The Conferences Menu...5 Conferences...5 Topics...6 Messages
Using WebBoard at UIS Accessing your WebBoard Course...3 Logging in to WebBoard...3 Understanding the WebBoard Environment...4 The Menubar...5 The Conferences Menu...5 Conferences...5 Topics...6 Messages
Registration and Login
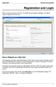 Registration and Login When a parent accesses txconnect, the following Login page is displayed. The parent needs to register as a new user. How to Register as a New User The registration process is self-administered,
Registration and Login When a parent accesses txconnect, the following Login page is displayed. The parent needs to register as a new user. How to Register as a New User The registration process is self-administered,
The Security Behind Sticky Password
 The Security Behind Sticky Password Technical White Paper Executive Summary When it comes to password management tools, concerns over secure data storage of passwords and personal information are often
The Security Behind Sticky Password Technical White Paper Executive Summary When it comes to password management tools, concerns over secure data storage of passwords and personal information are often
