PascalCoin Exchange Integration Guide. Compatible with version 4 of PascalCoin
|
|
|
- Emily Wheeler
- 5 years ago
- Views:
Transcription
1 Exchange Integration Guide Compatible with version 4 of PascalCoin
2 Introduction This document will explain how to integrate PascalCoin V4 into your exchange with the help of the inbuilt JSON RPC API. In PascalCoin there are two types of digital assets that can be exchanged: - PASC This is the cryptocurrency and is the most common type of asset. It has 4 decimals. - PASA These are PascalCoin accounts which are necessary to send and receive PASC. Most exchanges will only trade PASC and not PASA. PASC can be exchanged in the same way as other cryptocurrencies are. However, trading PASA is different since they are non-fungible assets. This means that some PASA are more valuable than others, due to their desirable numbers and/or names. For PASA exchanges, an 1 auction-style market is recommended, such as PascWallet. In order to support a large number of users, exchanges do not require a PASA for each user. They are able to integrate PascalCoin into their exchange using a single PASA owned by the exchange which acts as a custodian account for all their users. User deposits can be identified via payload inside the deposit transactions. This documentation focuses on integrating PASC. Make sure to explore for examples on how to use the JSON-RPC API of PascalCoin / 15
3 Install PascalCoin Installing PascalCoin is simple and can be installed on Linux or Windows. Minimum requirements are 2GB RAM, 2 CPU's and at least 20GB of storage. You can find the downloads on our github.com 2 releases page. The server should be isolated from the public network! The following ports are used by your node: Port 4004 This is the default PascalCoin network protocol port. It is used to keep your installation in sync with the network, so it must be accessible publicly. Port 4003 This is the default JSON RPC port. This port should only be accessible by the IP s that are allowed to communicate with PascalCoin to either query the blockchain or to create transactions. The PascalCoin software releases contains 2 executables: 1. GUI wallet The GUI wallet is the wallet that is also used by the end-users of PascalCoin. It s a full featured wallet, explorer, node and API server at the same time 2. The Daemon The daemon is a service that provides the same functionalities as the GUI, just without GUI. It is advised to use the daemon for your server(s), but during development it might help to use the GUI wallet to have a visual feedback on everything that happens in your exchange wallet as well as the PascalCoin Blockchain. To start the daemon use the following command:./pascalcoin_daemon[.exe] -r By default, the JSON-RPC API is only accessible from the same server. The GUI as well as the daemon can be configured to allow access from more IP s - but not or all IP s. In the GUI wallet, select Project Options from the main menu and change the Allowed IP s for the JSON-RPC API to a list of IPs divided by a semicolon. In the daemon, open the pascalcoin_daemoni.ini file in the same folder as the executable and edit the RPC_WHITELIST value. The same rules apply as for the GUI wallet / 15
4 Prepare your wallet After installing and starting the software, the wallet will sync with the network. While this happens, you must set a wallet password to make sure your wallet is safe. By default the password is an empty string, so the wallet is not protected. Everyone with access to it (e.g. JSON RPC) can execute private key related methods and possibly drain your wallet. If you use the GUI, go to Project Private keys and set the wallet password. If you use the daemon, 3 use the JSON-RPC method setwalletpassword to change it. A PascalCoin installation manages a single wallet. Each wallet contains one or more public/private key pairs as well as one or more public keys. Each public key holds one or more PASA. Once you set the password, operations related to private keys (e.g. making a transaction) require you to unlock the wallet, execute the private key related JSON-RPC method and lock the wallet again using 4 5 the lock and unlock JSON RPC API methods / 15
5 Create your Exchange's key In order to send/receive PASC with your installation, you ll need at least 1 key-pair. This key-pair will be associated to your exchange account (PASA). On the first run, PascalCoin will examine your wallet for keys and if none are found, it will add one for you automatically. 6 To add new key pairs to your wallet, you can use the JSON RPC addnewkey method. Calling this method will generate a new private/public key pair. The private key will be saved by the application internally. The Public Key is returned and accessible. For operational and maintenance simplicity, it's a good idea to name your key in a relevant way in order to avoid later confusion. Key names are only stored in the wallet and are not public. It is advised to start with only one key-pair for your integration. You can add other keys later and manage multiple PASAs to, e.g., avoid paying fees when withdrawing by using a load-balancing approach with multiple keys. It is important that you backup your keys. As mentioned above, the keys are stored internally. They are stored in a file in the home directory of the user that runs the wallet. Unix/Linux Systems Your keys as well as the blockchain data are stored in the %APPDATA%/PascalCoin folder. Windows Systems Your keys as well as the blockchain data are stored in the $USER/PascalCoin folder. The file WalletKeys.dat in the folder contains all your keys, so this is the file you ll need to backup. This file can also be copied to other installations of the software for re-use. Please ensure that your wallet keys are backed up all the time. 7 To programmatically determine the available keys in PascalCoin, you can use the getwalletpubkeys method / 15
6 5 / 15
7 Acquire your exchange account In order to receive deposits and send withdrawals, your exchange needs an account (PASA). Getting an account is easy: - PascalCoin Team Ask the PascalCoin team for a proper exchange account. - getpasa.com Buy a random account for 3 PASC - pascwallet.com Buy an account you like via this PASA exchange - Discord server Join #free-pasa-bot to obtain a free random PASA - In-Wallet purchase Use the wallets in-protocol PASA exchanging features. Many accounts are available for purchase directly in the network. It is advised to use a recognizable and memorable PASA account number for your exchange. PASA account numbers are 32 bit unsigned integers. They contain a checksum that makes it easier for users to verify if the account they entered is valid. The checksum is appended via - after the account number and is calculated as follows: ((AccountNumber * 101) MOD 89)+10 After you acquired an account, you are able to either receive or send PASC. 6 / 15
8 Understanding payloads Accepting and assigning deposits is easier as it is in other currencies. Everything is managed via payloads, which, in essence, are nothing more than additional data that can be added to a transaction and can be read by certain persons. Payloads from the API are in HEX format (called HexaString in the docs) without any preceding 0X. You need to instruct your users to include a payload with their transaction to your exchange account to identify a deposit. This payload needs to be encoded to hex by you in case of a withdrawal or decoded by you in case of a deposit. 8 Payloads can be encrypted by the user. This functionality is explained in detail here, but to give you a brief introduction, we will explain the possibilities in short here. Please refer to the documentation for more info. - No encryption (none) No encryption will take place and the payload is added to the operation "as is". Everyone can read the payload. - Destination public key (dest) The encryption will be executed using the destination PASA public key. PascalCoin will take the public key that owns the receiving account (destination) and encrypts the payload. The payload can only be decrypted by the owner of the receiving public key (the one that also knows the private key). No-one else will be able to decrypt the value. - Senders public key (sender) The encryption is done through the senders public key. PascalCoin will take the public key of the sender account and encrypts the payload. The payload can only be decrypted by the owner of the public key (the one that also knows the private key). No-one else will be able to decrypt the value. - AES256 with password (pwd) The third and last encryption method is to use a password. PascalCoin will take the defined password to create an initialization vector (IV) and Key to encrypt the payload using AES256-CBC. The payload can be decrypted by everyone who knows the password. This means that you cannot accept every transaction that arrives in your PASA. You can only read payloads the are either unencrypted or encrypted using your public key. How you handle invalid/unrecognizable transactions is up to you. Sending back the transaction to the sender is a valid approach and is covered at the end of this document. The withdraw payload should be free to set by your users on your exchange / 15
9 Proposed workflow for accepting user deposits Suppose the exchange account (PASA) is All deposits and withdrawals will operate through this account on your exchange. This is a proposed workflow to show how it can work, but if your structure is completely different and not adaptable from your point of view feeld free to get in touch with the PascalCoin team. Every action that alters the PascalCoin BlockChain is called an operation. There are various types available, but we will only cover 1 operation type which is an operation to transfer PASC from one account (PASA) to another account. Users Table Imagine your users table to look like this. Each user in your database contains a unique payload string to identify PascalCoin deposits. Payload strings are at max a string of 512 bytes. ID Name pascal_payload Other fields 523 bob@mail.com Bob XH42SD alice@mail.com Alice S82DG2... Deposits / Withdrawals Table(s) Imagine you record each deposit and withdrawal of your users. This is how it might look like: ID type User-ID PASC OPHASH status Other fields 1 deposit 523 XXXXX.. success... 2 withdraw YYYYY.. error... 3 withdraw ZZZZZ.. pending... 9 The operation hash of a PascalCoin operation is a string of 32 bytes / 15
10 Accepting user deposits Your node is operational. You have setup your keys and have a working PASA. Now you need to scan for deposits using the same workflow you would use for other cryptocurrencies. Here is an example scenario: - For Bob to deposit PASC into his exchange account he sends transactions to with payload XH42SD. - For Alice to deposit PASC into her exchange account she sends transactions to with payload S82DG2. The users payload encryption can either be none (no encryption) or dest (using your public key) for you to identify the deposit.. It is advised to follow this workflow: 1. (optional) Get pending operations If you want your users to get immediate feedback of a transaction to your account (deposit) 10 or to their account (withdraw), use the method getpendings. This will list all pending transactions that are not included in any block yet. Pending operations are visible more or less immediately and the amount of the transaction is already reflected in the receiving wallets balance (0-confirmation). 2. Get operations of new block Use getblockoperations to fetch the operations of a block. Use getblockcount to check the number of blocks (and check for new ones). Both of these methods give you a list of operations. Loop all these operations (take care, the getblockoperations and getpendings results are paged). WIth this list, check if: - operation.optype = 1 This identifies a transaction. - operation.receivers[0].account = exchange account This identifies the receiving account of the transaction (yours). - operation.receivers[0].payload = match in database This is the payload of the transaction for you to use to identify your user / 15
11 Payloads are user submitted values, so make sure you don t use them in your (database) backend without proper escaping! To decrypt a payload and associate the transaction with one of your users the following way is advised: 1. Take the payload as is and transform the Hex-String to a string (no encryption) 2. Check your user database if there is a payload associated with the payload of the transaction. If one is found, the transaction is valid If the above fails, try to decrypt the payload using the payloaddecrypt RPC API and a possible set of passwords. PascalCoin will try to decrypt the payload with the available private keys in your wallet and the possible passwords (can be left empty). Repeat 1 and 2 with the decrypted payload. If the above fails, the payload got encrypted and you ll will never know what the payload means. Possible reasons: - The user used his own public key to encrypt the payload. - The user used an unknown password to encrypt the payload. - Or.. there is a misunderstanding and the sender simply used a wrong payload value. In case the transaction can be identified successfully, record it in your deposit/withdrawal database. Each operation contains a field called maturation. It shows the age of an operation in terms of blocks. To verify a deposit to your account or to handle malicious transactions, it is advised to wait for at least 2 confirmations / 15
12 Withdrawing When a user wants to withdraw it s PASC from your exchange, your withdrawal form should (at best) look like this: PASA Account PASA account: The account to withdraw to. Checksums of accounts are an important feature to make sure the user did not input a wrong account number. Additionally you could add a button for users to get their own PASA. You can either distribute your own PASA and subtract the price from the withdrawal or use an external service like getpasa.com. Payload Payload: The payload the user wants to specify. You can add another option to let the user define the encryption method of the payload, but if not it is advised to not use any encryption (none). 14 Use the sendto JSON RPC method to create a new transaction. When an operation is created, it will be in the pending state. So no block is associated with it and it will have no maturation. The resulting operation hash starts with 8 zeros until the operation is included. After the operation got included, the first 8 bytes will represent the block number, so the ophash will change! The JSON-RPC 15 findoperation method is able to find the operation with either the pending ophash or the altered ophash after the operation is included. Just make sure your backend can handle the change of an operation hash sendto / 15
13 Checklist This checklist can be used to make sure your implementation works. - Check that your node is secured Port 4004 open, port 4003 only accessible for allowed IPs - Deposit with valid payload using no encryption. This deposit should be successful. - Deposit with valid payload using destination encryption. This deposit should be successful. - Deposit with valid payload using sender encryption. This deposit should fail. Optional: send back the transaction with the origin ophash. - Deposit with valid payload using a password. This deposit should fail. Optional: send back the transaction with the origin ophash. - Withdraw to an invalid account. 16 This should fail, use getaccount to check if an account exists. - Withdraw to a valid account. This should be successful. - Check if your wallet is password protected. Calls to payloaddecrypt or sendto should return an error code / 15
14 Appendix A list of technical explanations. HexaString Conversion Pseudo Code from string to HexaString. originalstring hexastring foreach 8BitChar in originalstring byte = to-decimal(8bitchar) hex = to-hex(8bitchar) hex = pad-left(hex, length=2, '0') append hex to hexastring end foreach Pseudo Code from HexaString to string. hexastring originalstring foreach 2chars in hexastring dec = to-decimal(2chars) 8BitChar = to-ascii(dec) append 8BitChar to originalstring end foreach Examples: Decrypted Hello World @domain.de Encrypted 48656C6C6F20576F726C d61696C40646F6D61696E2E6465 E282AC Checksum calculation The formula to calculate the checksum of an account is as follows: ((AccountNumber * 101) MOD 89)+10 Examples: 13 / 15
15 Account Number Checksum Deposit Payload Decryption Simple Pseudo-Code example on how to decode payloads. Operation Payload = Operation.receiver[n].payload Decoded = HexaToString(payload) If NOT DB.User.exists(Decoded) JSON-RPC.decodepayload(Payload) Decoded = HexaToString(payload) If NOT DB.User.exists(Decoded) NotFound() Else Deposit() EndIf Deposit() 14 / 15
PascalCoin - A Comprehensive Guide for Noobs
 PascalCoin - A Comprehensive Guide for Noobs What/who/when/why by: Jason Knapp (donations welcome - 291000-95), date: Aug 16, 2017 PascalCoin (PASC) was created by Albert Molina in 2016. It is written
PascalCoin - A Comprehensive Guide for Noobs What/who/when/why by: Jason Knapp (donations welcome - 291000-95), date: Aug 16, 2017 PascalCoin (PASC) was created by Albert Molina in 2016. It is written
CLN CLN TOKEN SALE. How to Participate Using MyEtherWallter
 CLN CLN TOKEN SALE How to Participate Using MyEtherWallter Colu Technologies DLT limited 3 Table of Contents Introduction 4 Create New Account 5 Step 1: Go to https://www.myetherwallet.com 5 Step 2: Go
CLN CLN TOKEN SALE How to Participate Using MyEtherWallter Colu Technologies DLT limited 3 Table of Contents Introduction 4 Create New Account 5 Step 1: Go to https://www.myetherwallet.com 5 Step 2: Go
Theta Token - SLIVER.tv Deposit Guide
 Theta Token - SLIVER.tv Deposit Guide Introduction & Overview In this guide we ll detail how you can acquire Theta Tokens (THETA) and deposit them to SLIVER.tv. The process can be confusing at first, but
Theta Token - SLIVER.tv Deposit Guide Introduction & Overview In this guide we ll detail how you can acquire Theta Tokens (THETA) and deposit them to SLIVER.tv. The process can be confusing at first, but
DTX Token. Starter guide
 DTX Token Starter guide 2 Choosing for the DTX token to buy and sell sensor data enables you to perform real microtransactions on DataBroker DAO. Every beginning is difficult, but this step-by-step introduction
DTX Token Starter guide 2 Choosing for the DTX token to buy and sell sensor data enables you to perform real microtransactions on DataBroker DAO. Every beginning is difficult, but this step-by-step introduction
Token Sale. Participation guide
 Token Sale Participation guide 2 As the DataBroker DAO token sale is closing in, we want to inform our future participants on how to properly take part in our presale on 19th of March. At first glance,
Token Sale Participation guide 2 As the DataBroker DAO token sale is closing in, we want to inform our future participants on how to properly take part in our presale on 19th of March. At first glance,
TOKENSALE PARTICIPATION GUIDE
 NEXT GENERATION INTERNET An open source platform for creation of 3D and VR compatible web-spaces (websites) and objects, powered by Blockchain. TOKENSALE PARTICIPATION GUIDE TABLE OF CONTENTS Contribute
NEXT GENERATION INTERNET An open source platform for creation of 3D and VR compatible web-spaces (websites) and objects, powered by Blockchain. TOKENSALE PARTICIPATION GUIDE TABLE OF CONTENTS Contribute
Presearch Token [Symbol: PRE] Withdrawal Instructions
![Presearch Token [Symbol: PRE] Withdrawal Instructions Presearch Token [Symbol: PRE] Withdrawal Instructions](/thumbs/78/77242238.jpg) Presearch Token [Symbol: PRE] Withdrawal Instructions Version 1.1 Last updated October 24th, 12:40PM ET Presearch Withdrawal Instructions 1 Step 1: Go to https://www.myetherwallet.com/ Go to https://www.myetherwallet.com,
Presearch Token [Symbol: PRE] Withdrawal Instructions Version 1.1 Last updated October 24th, 12:40PM ET Presearch Withdrawal Instructions 1 Step 1: Go to https://www.myetherwallet.com/ Go to https://www.myetherwallet.com,
Bitcoin, Security for Cloud & Big Data
 Bitcoin, Security for Cloud & Big Data CS 161: Computer Security Prof. David Wagner April 18, 2013 Bitcoin Public, distributed, peer-to-peer, hash-chained audit log of all transactions ( block chain ).
Bitcoin, Security for Cloud & Big Data CS 161: Computer Security Prof. David Wagner April 18, 2013 Bitcoin Public, distributed, peer-to-peer, hash-chained audit log of all transactions ( block chain ).
a new cryptocurrency STK GLOBAL PAYMENTS USER GUIDE USER GUIDE: PARTICIPATING IN IN STK STK TOKEN TOKEN SALE USING SALE MYETHERWALLET
 a new cryptocurrency STK GLOBAL PAYMENTS USER GUIDE USER GUIDE: PARTICIPATING IN IN STK STK TOKEN TOKEN SALE USING SALE MYETHERWALLET USING MYETHERWALLET 1 TABLE OF CONTENTS INTRODUCTION 3 CREATING A NEW
a new cryptocurrency STK GLOBAL PAYMENTS USER GUIDE USER GUIDE: PARTICIPATING IN IN STK STK TOKEN TOKEN SALE USING SALE MYETHERWALLET USING MYETHERWALLET 1 TABLE OF CONTENTS INTRODUCTION 3 CREATING A NEW
MyEtherWallet Step by Step Tutorial
 MyEtherWallet Step by Step Tutorial Step 1 1. Visit www.myetherwallet.com. The first thing you will see is Create New Wallet Create a strong password and fill it in the Enter a password field. You need
MyEtherWallet Step by Step Tutorial Step 1 1. Visit www.myetherwallet.com. The first thing you will see is Create New Wallet Create a strong password and fill it in the Enter a password field. You need
MYETHERWALLET GUIDE 1
 MYETHERWALLET GUIDE 1 Introduction...3 Create New Account... 4 Step 1: Go to www.myetherwallet.com...4 Step 2: Go to the New Wallet Tab...4 Step 3: Provide a Strong Password...5 Step 4: Save Your Keystore
MYETHERWALLET GUIDE 1 Introduction...3 Create New Account... 4 Step 1: Go to www.myetherwallet.com...4 Step 2: Go to the New Wallet Tab...4 Step 3: Provide a Strong Password...5 Step 4: Save Your Keystore
Senior Math Circles Cryptography and Number Theory Week 1
 Senior Math Circles Cryptography and Number Theory Week 1 Dale Brydon Feb. 2, 2014 1 One-Time Pads Cryptography deals with the problem of encoding a message in such a way that only the intended recipient
Senior Math Circles Cryptography and Number Theory Week 1 Dale Brydon Feb. 2, 2014 1 One-Time Pads Cryptography deals with the problem of encoding a message in such a way that only the intended recipient
Activity Guide - Public Key Cryptography
 Unit 2 Lesson 19 Name(s) Period Date Activity Guide - Public Key Cryptography Introduction This activity is similar to the cups and beans encryption we did in a previous lesson. However, instead of using
Unit 2 Lesson 19 Name(s) Period Date Activity Guide - Public Key Cryptography Introduction This activity is similar to the cups and beans encryption we did in a previous lesson. However, instead of using
Metaverse Light Wallet Manual V1
 Metaverse Light Wallet Manual V1 Contents How to make a New wallet creation... 2 How to Login with Existing Account... 3 How to transfer your ETP... 4 How to check all your address... 5 How to check transaction
Metaverse Light Wallet Manual V1 Contents How to make a New wallet creation... 2 How to Login with Existing Account... 3 How to transfer your ETP... 4 How to check all your address... 5 How to check transaction
LEOcoin Private Chat wallet FAQ V 1
 LEOcoin Private Chat wallet F V 1 Staking. With the old LEOcoin wallet, I was staking twice a day and getting my rewards within the hour. New wallet says staking opportunities will be every 30 days. Do
LEOcoin Private Chat wallet F V 1 Staking. With the old LEOcoin wallet, I was staking twice a day and getting my rewards within the hour. New wallet says staking opportunities will be every 30 days. Do
How Can I See My ENJ? 15. Acquiring Ether (ETH) 16
 Create New MEW Account 2 Step 1: Go to https://www.myetherwallet.com/ 2 Step 2: Go to the New Wallet Tab 2 Step 3: Enter a Strong Password 3 Step 4: Save Your Keystore File 3 Step 5 (optional): Backup
Create New MEW Account 2 Step 1: Go to https://www.myetherwallet.com/ 2 Step 2: Go to the New Wallet Tab 2 Step 3: Enter a Strong Password 3 Step 4: Save Your Keystore File 3 Step 5 (optional): Backup
Technical Specifications for Platform Development
 Technical Specifications for Platform Development Contents 1. General Information about the Product... 2 2. Software Requirements... 3 2.1. Functional Requirements... 3 2.2. Server Requirements... 4 3.
Technical Specifications for Platform Development Contents 1. General Information about the Product... 2 2. Software Requirements... 3 2.1. Functional Requirements... 3 2.2. Server Requirements... 4 3.
Tungsten Security Whitepaper
 Tungsten Labs UG (haftungsbeschränkt) Email: contact@tungsten-labs.com Web: http://tungsten-labs.com Monbijouplatz 5, 10178 Berlin Tungsten Security Whitepaper Berlin, May 2018 Version 1 Contents Introduction
Tungsten Labs UG (haftungsbeschränkt) Email: contact@tungsten-labs.com Web: http://tungsten-labs.com Monbijouplatz 5, 10178 Berlin Tungsten Security Whitepaper Berlin, May 2018 Version 1 Contents Introduction
NAV Coin NavTech Server Installation and setup instructions
 NAV Coin NavTech Server Installation and setup instructions NavTech disconnects sender and receiver Unique double-blockchain Technology V4.0.5 October 2017 2 Index General information... 5 NavTech... 5
NAV Coin NavTech Server Installation and setup instructions NavTech disconnects sender and receiver Unique double-blockchain Technology V4.0.5 October 2017 2 Index General information... 5 NavTech... 5
Wallet Setup Guide WINDOWS. Version 1 /
 Wallet Setup Guide WINDOWS Version 1 / 1-1-2018 Downloading and Installing the COLX Wallet If this is the first time you are installing the COLX desktop wallet, please follow these steps. 1. Visit the
Wallet Setup Guide WINDOWS Version 1 / 1-1-2018 Downloading and Installing the COLX Wallet If this is the first time you are installing the COLX desktop wallet, please follow these steps. 1. Visit the
As a 3rd generation currency, not only are transactions secured, private and fast, you actually get paid for holding DigitalPrice coins.
 Introduction With the circulation of cryptocurrency becoming common, there is a need for additional information. The scope of this white paper is to provide that information. If you are under the impression
Introduction With the circulation of cryptocurrency becoming common, there is a need for additional information. The scope of this white paper is to provide that information. If you are under the impression
Computer Security. 14. Blockchain & Bitcoin. Paul Krzyzanowski. Rutgers University. Spring 2019
 Computer Security 14. Blockchain & Bitcoin Paul Krzyzanowski Rutgers University Spring 2019 April 15, 2019 CS 419 2019 Paul Krzyzanowski 1 Bitcoin & Blockchain Bitcoin cryptocurrency system Introduced
Computer Security 14. Blockchain & Bitcoin Paul Krzyzanowski Rutgers University Spring 2019 April 15, 2019 CS 419 2019 Paul Krzyzanowski 1 Bitcoin & Blockchain Bitcoin cryptocurrency system Introduced
Blum-Blum-Shub cryptosystem and generator. Blum-Blum-Shub cryptosystem and generator
 BBS encryption scheme A prime p is called a Blum prime if p mod 4 = 3. ALGORITHM Alice, the recipient, makes her BBS key as follows: BBS encryption scheme A prime p is called a Blum prime if p mod 4 =
BBS encryption scheme A prime p is called a Blum prime if p mod 4 = 3. ALGORITHM Alice, the recipient, makes her BBS key as follows: BBS encryption scheme A prime p is called a Blum prime if p mod 4 =
Smalltalk 3/30/15. The Mathematics of Bitcoin Brian Heinold
 Smalltalk 3/30/15 The Mathematics of Bitcoin Brian Heinold What is Bitcoin? Created by Satoshi Nakamoto in 2008 What is Bitcoin? Created by Satoshi Nakamoto in 2008 Digital currency (though not the first)
Smalltalk 3/30/15 The Mathematics of Bitcoin Brian Heinold What is Bitcoin? Created by Satoshi Nakamoto in 2008 What is Bitcoin? Created by Satoshi Nakamoto in 2008 Digital currency (though not the first)
Feedback Week 4 - Problem Set
 4/26/13 Homework Feedback Introduction to Cryptography Feedback Week 4 - Problem Set You submitted this homework on Mon 17 Dec 2012 11:40 PM GMT +0000. You got a score of 10.00 out of 10.00. Question 1
4/26/13 Homework Feedback Introduction to Cryptography Feedback Week 4 - Problem Set You submitted this homework on Mon 17 Dec 2012 11:40 PM GMT +0000. You got a score of 10.00 out of 10.00. Question 1
How to buy LIVE Token with Ethereum and Bitcoin step by step
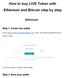 How to buy LIVE Token with Ethereum and Bitcoin step by step Ethereum Step 1. Create new wallet. Go to https://www.myetherwallet.com/, think of a strong password and enter it here: Click the button Create
How to buy LIVE Token with Ethereum and Bitcoin step by step Ethereum Step 1. Create new wallet. Go to https://www.myetherwallet.com/, think of a strong password and enter it here: Click the button Create
University of Duisburg-Essen Bismarckstr Duisburg Germany HOW BITCOIN WORKS. Matthäus Wander. June 29, 2011
 University of Duisburg-Essen Bismarckstr. 90 47057 Duisburg Germany HOW BITCOIN WORKS June 29, 2011 Overview Electronic currency system Decentralized No trusted third party involved Unstructured peer-to-peer
University of Duisburg-Essen Bismarckstr. 90 47057 Duisburg Germany HOW BITCOIN WORKS June 29, 2011 Overview Electronic currency system Decentralized No trusted third party involved Unstructured peer-to-peer
SKBI Cryptocurrency Technical Seminar Series Seminar 1: Basics: Cryptography and Transactions
 SKBI Cryptocurrency Technical Seminar Series Seminar 1: Basics: Cryptography and Transactions Zhiguo Wan Sim Kee Boon Institute for Financial Economics Singapore Management University Schedule of bitcoin
SKBI Cryptocurrency Technical Seminar Series Seminar 1: Basics: Cryptography and Transactions Zhiguo Wan Sim Kee Boon Institute for Financial Economics Singapore Management University Schedule of bitcoin
CazCoin VPS Masternode Setup December 2018
 Contents 1. Introduction... 3 2. Requirements... 3 3. VPS Preparation... 4 4. Local Wallet Setup... 4 5. Edit Local Configuration Files... 6 6. VPS Setup... 7 7. Starting the Masternode... 10 8. Wallet
Contents 1. Introduction... 3 2. Requirements... 3 3. VPS Preparation... 4 4. Local Wallet Setup... 4 5. Edit Local Configuration Files... 6 6. VPS Setup... 7 7. Starting the Masternode... 10 8. Wallet
CazCoin VPS Masternode Setup May 2018
 VPS Masternode Setup May 2018 VPS Masternode Setup May 2018 Contents 1. Introduction... 3 2. Requirements... 3 3. Block Rewards?... 4 4. VPS Preparation... 4 5. Local Wallet Setup... 5 6. Edit Local Config
VPS Masternode Setup May 2018 VPS Masternode Setup May 2018 Contents 1. Introduction... 3 2. Requirements... 3 3. Block Rewards?... 4 4. VPS Preparation... 4 5. Local Wallet Setup... 5 6. Edit Local Config
For further information about the GRID token sale, please visit gridplus.io/token-sale.
 1 1 Introduction Thank you for your interest in purchasing GRID tokens. The following information has been organized to help you complete your purchase using MyEtherWallet, Mist, or MetaMask. For further
1 1 Introduction Thank you for your interest in purchasing GRID tokens. The following information has been organized to help you complete your purchase using MyEtherWallet, Mist, or MetaMask. For further
PascalCoin Version 2 By Albert Molina ( ), Herman Schoenfeld ( )
 PascalCoin Version 2 By Albert Molina ( bpascalblockchain@gmail.com ), Herman Schoenfeld ( herman@sphere10.com ) preamble PascalCoin is a next-generation cryptocurrency that pioneers a new tier of scalability
PascalCoin Version 2 By Albert Molina ( bpascalblockchain@gmail.com ), Herman Schoenfeld ( herman@sphere10.com ) preamble PascalCoin is a next-generation cryptocurrency that pioneers a new tier of scalability
AEGEUS Official Aegeus FAQ
 AEGEUS Official Aegeus FAQ Written and rights reserved by the Aegeus Team September 2018 1 Contents Wallets Q1: How do I download the Aegeus wallet? Q2: How do I backup my wallet? Q3: How often should
AEGEUS Official Aegeus FAQ Written and rights reserved by the Aegeus Team September 2018 1 Contents Wallets Q1: How do I download the Aegeus wallet? Q2: How do I backup my wallet? Q3: How often should
Team One Mobile Banking App DETAILED ENHANCEMENTS
 Team One Mobile Banking App DETAILED ENHANCEMENTS Team One Mobile Banking App DETAILED ENHANCEMENTS Table of Contents Page Touch ID 3 QuickBalance 4 MiSnap 6 Bill Pay Enhancement 6 AnyWhereMobile Set Up
Team One Mobile Banking App DETAILED ENHANCEMENTS Team One Mobile Banking App DETAILED ENHANCEMENTS Table of Contents Page Touch ID 3 QuickBalance 4 MiSnap 6 Bill Pay Enhancement 6 AnyWhereMobile Set Up
Master Node Setup Guide
 Introduction Welcome to this step by step guide that will take you through the process of creating your own Masternode. This guide is aimed at the casual Windows 10 PC user who has purchased Satoshi Coin
Introduction Welcome to this step by step guide that will take you through the process of creating your own Masternode. This guide is aimed at the casual Windows 10 PC user who has purchased Satoshi Coin
Official Aegeus FAQ s
 Official Aegeus FAQ s Wallets Q1: How do I download the Aegeus wallet? Q2: How do I backup my wallet? Q3: How often should I backup my wallet? Q4: How do I encrypt my wallet? Q5: How do I unlock my wallet?
Official Aegeus FAQ s Wallets Q1: How do I download the Aegeus wallet? Q2: How do I backup my wallet? Q3: How often should I backup my wallet? Q4: How do I encrypt my wallet? Q5: How do I unlock my wallet?
FLP Merchant Website. User Guide. Version 0.14
 FLP Merchant Website User Guide Version 0.14 Revision History Responsible Revision Date Version Vitalii Vysotskyi Created the initial version of the user guide 2017-11-28 0.1 Vitalii Vysotskyi Small updates
FLP Merchant Website User Guide Version 0.14 Revision History Responsible Revision Date Version Vitalii Vysotskyi Created the initial version of the user guide 2017-11-28 0.1 Vitalii Vysotskyi Small updates
Privacy-Enabled NFTs: User-Mintable, Non-Fungible Tokens With Private Off-Chain Data
 Privacy-Enabled NFTs: User-Mintable, Non-Fungible Tokens With Private Off-Chain Data Philip Stehlik Lucas Vogelsang August 8, 2018 1 Abstract Privacy-enabled NFTs (non-fungible tokens) are user-mintable
Privacy-Enabled NFTs: User-Mintable, Non-Fungible Tokens With Private Off-Chain Data Philip Stehlik Lucas Vogelsang August 8, 2018 1 Abstract Privacy-enabled NFTs (non-fungible tokens) are user-mintable
CS Computer Networks 1: Authentication
 CS 3251- Computer Networks 1: Authentication Professor Patrick Traynor 4/14/11 Lecture 25 Announcements Homework 3 is due next class. Submit via T-Square or in person. Project 3 has been graded. Scores
CS 3251- Computer Networks 1: Authentication Professor Patrick Traynor 4/14/11 Lecture 25 Announcements Homework 3 is due next class. Submit via T-Square or in person. Project 3 has been graded. Scores
Unit 8: Working with Actions
 Unit 8: Working with Actions Questions Covered What are actions? How are actions triggered? Where can we access actions to create or edit them? How do we automate the sending of email notifications? How
Unit 8: Working with Actions Questions Covered What are actions? How are actions triggered? Where can we access actions to create or edit them? How do we automate the sending of email notifications? How
Introduction to Cryptography in Blockchain Technology. December 23, 2018
 Introduction to Cryptography in Blockchain Technology December 23, 2018 What is cryptography? The practice of developing protocols that prevent third parties from viewing private data. Modern cryptography
Introduction to Cryptography in Blockchain Technology December 23, 2018 What is cryptography? The practice of developing protocols that prevent third parties from viewing private data. Modern cryptography
Chapter 13. Digital Cash. Information Security/System Security p. 570/626
 Chapter 13 Digital Cash Information Security/System Security p. 570/626 Introduction While cash is used in illegal activities such as bribing money laundering tax evasion it also protects privacy: not
Chapter 13 Digital Cash Information Security/System Security p. 570/626 Introduction While cash is used in illegal activities such as bribing money laundering tax evasion it also protects privacy: not
NEW TOKEN SWAP INSTRUCTIONS For action after July 23, 2018.
 1 NEW TOKEN SWAP INSTRUCTIONS For action after July 23, 2018. www.sophiatx.com 2 Table of contents 1. Introduction 2. Prerequesites 3. Generate a new SPHTX keypair (SophiaTX new Wallet) 4. Register the
1 NEW TOKEN SWAP INSTRUCTIONS For action after July 23, 2018. www.sophiatx.com 2 Table of contents 1. Introduction 2. Prerequesites 3. Generate a new SPHTX keypair (SophiaTX new Wallet) 4. Register the
Contents. Crave Masternode Setup Guides. Single / Multiple Local Masternode(s) Single Masternode using a VPS. Multiple Masternodes using a VPS
 Contents Crave Masternode Setup Guides Single / Multiple Local Masternode(s) 1 Requirements...1 2 Preparing Masternodes...1 3 Preparing Controller Wallet...2 4 Masternode Configuration...3 5 Starting Masternodes...3
Contents Crave Masternode Setup Guides Single / Multiple Local Masternode(s) 1 Requirements...1 2 Preparing Masternodes...1 3 Preparing Controller Wallet...2 4 Masternode Configuration...3 5 Starting Masternodes...3
CS 161 Computer Security
 Paxson Spring 2017 CS 161 Computer Security Discussion 6 Week of March 6, 2017 Question 1 Password Hashing (10 min) When storing a password p for user u, a website randomly generates a string s (called
Paxson Spring 2017 CS 161 Computer Security Discussion 6 Week of March 6, 2017 Question 1 Password Hashing (10 min) When storing a password p for user u, a website randomly generates a string s (called
Investing in BIG Token
 Step-by-Step Guide to: Investing in BIG Token 6 STEPS TO INVEST IN BIG TOKEN Step 1: Creating an Ethereum wallet Step 2: Get Whitelisted Step 3: Create an Account on a Cryptoexchange Step 4: Transfer Money
Step-by-Step Guide to: Investing in BIG Token 6 STEPS TO INVEST IN BIG TOKEN Step 1: Creating an Ethereum wallet Step 2: Get Whitelisted Step 3: Create an Account on a Cryptoexchange Step 4: Transfer Money
Cryptography (Overview)
 Cryptography (Overview) Some history Caesar cipher, rot13 substitution ciphers, etc. Enigma (Turing) Modern secret key cryptography DES, AES Public key cryptography RSA, digital signatures Cryptography
Cryptography (Overview) Some history Caesar cipher, rot13 substitution ciphers, etc. Enigma (Turing) Modern secret key cryptography DES, AES Public key cryptography RSA, digital signatures Cryptography
CVS Application. William Jiang
 CVS Application William Jiang CVS Brief CVS (Concurrent Versions System), is an open-source version control system. Using it, we can record the history of our source files, coordinate with team developing,
CVS Application William Jiang CVS Brief CVS (Concurrent Versions System), is an open-source version control system. Using it, we can record the history of our source files, coordinate with team developing,
TeleX AI. Cryptocurrency Wallet and Exchange Services on Telegram. Telex AI Company Ltd telexai.com November 2017
 TeleX AI Cryptocurrency Wallet and Exchange Services on Telegram Telex AI Company Ltd telexai.com November 2017 TeleX AI is a chatbot powered by artificial intelligence, designed to provide cryptocurrency-related
TeleX AI Cryptocurrency Wallet and Exchange Services on Telegram Telex AI Company Ltd telexai.com November 2017 TeleX AI is a chatbot powered by artificial intelligence, designed to provide cryptocurrency-related
Controller-Cold-Setup
 Controller-Cold-Setup This is the advised Method to setup your Masternodes. The wallet containing the coins does not have to be exposed and can run on your local computer. It does not have to run all the
Controller-Cold-Setup This is the advised Method to setup your Masternodes. The wallet containing the coins does not have to be exposed and can run on your local computer. It does not have to run all the
COPYRIGHTED MATERIAL. Getting Started with Windows 7. P a r t. In This Part
 P a r t I Getting Started with Windows 7 In This Part Chapter 1: Selecting the Right Version Chapter 2: Installing Windows 7 Chapter 3: Safe Tweaking COPYRIGHTED MATERIAL C h a p t e r 1 Selecting the
P a r t I Getting Started with Windows 7 In This Part Chapter 1: Selecting the Right Version Chapter 2: Installing Windows 7 Chapter 3: Safe Tweaking COPYRIGHTED MATERIAL C h a p t e r 1 Selecting the
CSCI 454/554 Computer and Network Security. Topic 5.2 Public Key Cryptography
 CSCI 454/554 Computer and Network Security Topic 5.2 Public Key Cryptography Outline 1. Introduction 2. RSA 3. Diffie-Hellman Key Exchange 4. Digital Signature Standard 2 Introduction Public Key Cryptography
CSCI 454/554 Computer and Network Security Topic 5.2 Public Key Cryptography Outline 1. Introduction 2. RSA 3. Diffie-Hellman Key Exchange 4. Digital Signature Standard 2 Introduction Public Key Cryptography
CIS 194: Homework 5. Due Wednesday, 25 February, Preface. Setup. JSON files. String theory
 CIS 194: Homework 5 Due Wednesday, 25 February, 2015 Preface Setup You will need two packages that are not part of Haskell s standard library for this assignment. They are aeson and text. You can install
CIS 194: Homework 5 Due Wednesday, 25 February, 2015 Preface Setup You will need two packages that are not part of Haskell s standard library for this assignment. They are aeson and text. You can install
Technical White Paper. Cube Engine Version 1.0
 Technical White Paper Cube Engine Version 1.0 Last Updated: Feb 06. 2018 1 Contents 1. Summary 1) Introduction 2) Overview 2. Features of Cube Chain 1) Cubing 2) Indexing Block 3) Statistics Block 4) Escrow
Technical White Paper Cube Engine Version 1.0 Last Updated: Feb 06. 2018 1 Contents 1. Summary 1) Introduction 2) Overview 2. Features of Cube Chain 1) Cubing 2) Indexing Block 3) Statistics Block 4) Escrow
Outline. CSCI 454/554 Computer and Network Security. Introduction. Topic 5.2 Public Key Cryptography. 1. Introduction 2. RSA
 CSCI 454/554 Computer and Network Security Topic 5.2 Public Key Cryptography 1. Introduction 2. RSA Outline 3. Diffie-Hellman Key Exchange 4. Digital Signature Standard 2 Introduction Public Key Cryptography
CSCI 454/554 Computer and Network Security Topic 5.2 Public Key Cryptography 1. Introduction 2. RSA Outline 3. Diffie-Hellman Key Exchange 4. Digital Signature Standard 2 Introduction Public Key Cryptography
CONVERT OPPORTUNITIES INTO SOLUTIONS WITH A CRYPTOCURRENCY BROKER YOU CAN TRUST USER GUIDE
 CONVERT OPPORTUNITIES INTO SOLUTIONS WITH A CRYPTOCURRENCY BROKER YOU CAN TRUST USER GUIDE This guide will help you successfully open a live trading account as well as learn the basics of our web trading
CONVERT OPPORTUNITIES INTO SOLUTIONS WITH A CRYPTOCURRENCY BROKER YOU CAN TRUST USER GUIDE This guide will help you successfully open a live trading account as well as learn the basics of our web trading
Token sale is live now
 The new Operating System of $7.6 trillion Healthcare Industry Token sale is live now PLEASE FOLLOW THE INSTRUCTIONS CAREFULLY IN ORDER THAT YOU WILL BE ABLE TO SAFELY PARTICIPATE IN ETHEAL TOKEN SALE.
The new Operating System of $7.6 trillion Healthcare Industry Token sale is live now PLEASE FOLLOW THE INSTRUCTIONS CAREFULLY IN ORDER THAT YOU WILL BE ABLE TO SAFELY PARTICIPATE IN ETHEAL TOKEN SALE.
Kerberos V5. Raj Jain. Washington University in St. Louis
 Kerberos V5 Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse571-07/ 11-1
Kerberos V5 Raj Jain Washington University in Saint Louis Saint Louis, MO 63130 Jain@cse.wustl.edu Audio/Video recordings of this lecture are available at: http://www.cse.wustl.edu/~jain/cse571-07/ 11-1
BUYING HEARDBEATS VIA KRAKEN
 BUYING HEARDBEATS VIA KRAKEN Step by step guide to creating your Kraken account, getting verified, adding & withdrawing funds and buying & selling cryptocurrency. STEP 1 Navigate to the Kraken website
BUYING HEARDBEATS VIA KRAKEN Step by step guide to creating your Kraken account, getting verified, adding & withdrawing funds and buying & selling cryptocurrency. STEP 1 Navigate to the Kraken website
Visualizing and Tracing Bitcoin Transactions
 Visualizing and Tracing Bitcoin Transactions Matthew Consterdine & Dennis Parchkov & Altay Adademir Abstract This project demonstrates the ability to visualize, and trace transactions through the Bitcoin
Visualizing and Tracing Bitcoin Transactions Matthew Consterdine & Dennis Parchkov & Altay Adademir Abstract This project demonstrates the ability to visualize, and trace transactions through the Bitcoin
LOCAL WALLET (COLD WALLET):
 This tutorial will teach you how to create a masternode with a "cold/hot" setup. The whole process is as follows. LOCAL WALLET (COLD WALLET): Visit TRAID platform s official repository on GitHub and download
This tutorial will teach you how to create a masternode with a "cold/hot" setup. The whole process is as follows. LOCAL WALLET (COLD WALLET): Visit TRAID platform s official repository on GitHub and download
Outline. Public Key Cryptography. Applications of Public Key Crypto. Applications (Cont d)
 Outline AIT 682: Network and Systems Security 1. Introduction 2. RSA 3. Diffie-Hellman Key Exchange 4. Digital Signature Standard Topic 5.2 Public Key Cryptography Instructor: Dr. Kun Sun 2 Public Key
Outline AIT 682: Network and Systems Security 1. Introduction 2. RSA 3. Diffie-Hellman Key Exchange 4. Digital Signature Standard Topic 5.2 Public Key Cryptography Instructor: Dr. Kun Sun 2 Public Key
XSN coin. TPoS Setup Guide. https://discord.gg/cyf5yca. https://xsncoin.io
 XSN coin TPoS Setup Guide https://discord.gg/cyf5yca https://xsncoin.io Contents Introduction... 3 What is TPoS?... 3 DISCLAIMER:... 4 How to be an Owner... 4 How to be a merchant... 5 Step 1. Controller
XSN coin TPoS Setup Guide https://discord.gg/cyf5yca https://xsncoin.io Contents Introduction... 3 What is TPoS?... 3 DISCLAIMER:... 4 How to be an Owner... 4 How to be a merchant... 5 Step 1. Controller
1 Identification protocols
 ISA 562: Information Security, Theory and Practice Lecture 4 1 Identification protocols Now that we know how to authenticate messages using MACs, a natural question is, how can we use MACs to prove that
ISA 562: Information Security, Theory and Practice Lecture 4 1 Identification protocols Now that we know how to authenticate messages using MACs, a natural question is, how can we use MACs to prove that
FLIP Token (FLP) How to Participate in the FLIP Token (FLP) Sale Event. 1 Disclaimer 2. 2 What You Will Need 2
 FLIP Token (FLP) How to Participate in the FLIP Token (FLP) Sale Event 1 Disclaimer 2 2 What You Will Need 2 3 Create a New MEW Account 2 Step 1: Go to https://www.myetherwallet.com 3 Step 2: Go to the
FLIP Token (FLP) How to Participate in the FLIP Token (FLP) Sale Event 1 Disclaimer 2 2 What You Will Need 2 3 Create a New MEW Account 2 Step 1: Go to https://www.myetherwallet.com 3 Step 2: Go to the
INSE 6110 Midterm LAST NAME FIRST NAME. Fall 2016 Duration: 80 minutes ID NUMBER. QUESTION Total GRADE. Notes:
 A INSE 6110 Midterm Fall 2016 Duration: 80 minutes LAST NAME FIRST NAME ID NUMBER QUESTION 1 2 3 4 Total GRADE Notes: 1) Calculator (non-programming) allowed, nothing else permitted 2) Each page contains
A INSE 6110 Midterm Fall 2016 Duration: 80 minutes LAST NAME FIRST NAME ID NUMBER QUESTION 1 2 3 4 Total GRADE Notes: 1) Calculator (non-programming) allowed, nothing else permitted 2) Each page contains
What you need: 5001 AEG. Computer with wallet installed. Make sure the wallet contains the Masternode Collateral of at least 5001 AEGEUS
 What you need: 5001 AEG Computer with wallet installed. Make sure the wallet contains the Masternode Collateral of at least 5001 AEGEUS Download Windows Wallet Here Step 1: Install AEGEUS wallet on Windows
What you need: 5001 AEG Computer with wallet installed. Make sure the wallet contains the Masternode Collateral of at least 5001 AEGEUS Download Windows Wallet Here Step 1: Install AEGEUS wallet on Windows
Lecture 10. A2 - will post tonight - due in two weeks
 Lecture 10 A2 - will post tonight - due in two weeks The DAO - $72M USD in Ether Decentralized Dragon's Den or Shark's Tank A pot of money that you could contribute to and receive voting shares for You
Lecture 10 A2 - will post tonight - due in two weeks The DAO - $72M USD in Ether Decentralized Dragon's Den or Shark's Tank A pot of money that you could contribute to and receive voting shares for You
CREDITS Web-version 2 Web-version specification CREDITS Desktop Client vs. Web-client What is the CREDITS Wallet? 2 1.
 CREDITS Web-version 2 Web-version specification 2 1.1 CREDITS Desktop Client vs. Web-client 2 1.2 What is the CREDITS Wallet? 2 1.3 Essential Functionality 2 2. System Requirements 4 3. Creating New Account
CREDITS Web-version 2 Web-version specification 2 1.1 CREDITS Desktop Client vs. Web-client 2 1.2 What is the CREDITS Wallet? 2 1.3 Essential Functionality 2 2. System Requirements 4 3. Creating New Account
Citizenship Coin. Installation Instructions
 Citizenship Coin Installation Instructions Please download and install our wallet software which works in Windows (32 bit, 64 bit), MacosX (64 bit) and Linux (64 bit). Once you run the software, it will
Citizenship Coin Installation Instructions Please download and install our wallet software which works in Windows (32 bit, 64 bit), MacosX (64 bit) and Linux (64 bit). Once you run the software, it will
Cryptully Documentation
 Cryptully Documentation Release 5.0.0 Shane Tully Mar 12, 2018 Contents 1 Introduction 1 2 Features 3 2.1 How does it work and how is it secure?................................. 3 3 Quick Start 5 4 Doesn
Cryptully Documentation Release 5.0.0 Shane Tully Mar 12, 2018 Contents 1 Introduction 1 2 Features 3 2.1 How does it work and how is it secure?................................. 3 3 Quick Start 5 4 Doesn
Distributed Systems Fall 2009 Final
 15-440 Distributed Systems Fall 2009 Final Name: Andrew: ID November 29, 2010 Please write your name and Andrew ID above before starting this exam. This exam has 10 pages, including this title page. Please
15-440 Distributed Systems Fall 2009 Final Name: Andrew: ID November 29, 2010 Please write your name and Andrew ID above before starting this exam. This exam has 10 pages, including this title page. Please
Stonelaw High School. Computing Science. BGE - Computer Systems
 Stonelaw High School Computing Science BGE - Computer Systems Contents Computer Systems... 3 Computer Systems... 3 Hardware & Software... 3 Data Representation... 3 Representing Positive Integers... 3
Stonelaw High School Computing Science BGE - Computer Systems Contents Computer Systems... 3 Computer Systems... 3 Hardware & Software... 3 Data Representation... 3 Representing Positive Integers... 3
CS 161 Computer Security
 Raluca Popa Spring 2018 CS 161 Computer Security Homework 2 Due: Wednesday, February 14, at 11:59pm Instructions. This homework is due Wednesday, February 14, at 11:59pm. No late homeworks will be accepted.
Raluca Popa Spring 2018 CS 161 Computer Security Homework 2 Due: Wednesday, February 14, at 11:59pm Instructions. This homework is due Wednesday, February 14, at 11:59pm. No late homeworks will be accepted.
Lab 08. Command Line and Git
 Lab 08 Command Line and Git Agenda Final Project Information All Things Git! Make sure to come to lab next week for Python! Final Projects Connect 4 Arduino ios Creative AI Being on a Team - How To Maximize
Lab 08 Command Line and Git Agenda Final Project Information All Things Git! Make sure to come to lab next week for Python! Final Projects Connect 4 Arduino ios Creative AI Being on a Team - How To Maximize
Digital it Signatures. Message Authentication Codes. Message Hash. Security. COMP755 Advanced OS 1
 Digital Signatures Digital it Signatures Offer similar protections as handwritten signatures in the real world. 1. Difficult to forge. 2. Easily verifiable. 3. Not deniable. 4. Easy to implement. 5. Differs
Digital Signatures Digital it Signatures Offer similar protections as handwritten signatures in the real world. 1. Difficult to forge. 2. Easily verifiable. 3. Not deniable. 4. Easy to implement. 5. Differs
Talend Component tgoogledrive
 Talend Component tgoogledrive Purpose and procedure This component manages files on a Google Drive. The component provides these capabilities: 1. Providing only the client for other tgoogledrive components
Talend Component tgoogledrive Purpose and procedure This component manages files on a Google Drive. The component provides these capabilities: 1. Providing only the client for other tgoogledrive components
P2P BitCoin: Technical details
 ELT-53206 Peer-to-Peer Networks P2P BitCoin: Technical details Mathieu Devos Tampere University of Technology Department of Electronics & Communications Engineering mathieu.devos@tut.fi TG406 2 Outline
ELT-53206 Peer-to-Peer Networks P2P BitCoin: Technical details Mathieu Devos Tampere University of Technology Department of Electronics & Communications Engineering mathieu.devos@tut.fi TG406 2 Outline
SPARROW Gateway. Custom Payment Redirect. Version (Build 7373)
 SPARROW Gateway Custom Payment Redirect Version 3.2.0 (Build 7373) Released September 2016 Revision History Date Revision Comments Author 2015 06 09 1.0 Initial document created Blinova Alexandra 2 Table
SPARROW Gateway Custom Payment Redirect Version 3.2.0 (Build 7373) Released September 2016 Revision History Date Revision Comments Author 2015 06 09 1.0 Initial document created Blinova Alexandra 2 Table
Public-Key Cryptography. Professor Yanmin Gong Week 3: Sep. 7
 Public-Key Cryptography Professor Yanmin Gong Week 3: Sep. 7 Outline Key exchange and Diffie-Hellman protocol Mathematical backgrounds for modular arithmetic RSA Digital Signatures Key management Problem:
Public-Key Cryptography Professor Yanmin Gong Week 3: Sep. 7 Outline Key exchange and Diffie-Hellman protocol Mathematical backgrounds for modular arithmetic RSA Digital Signatures Key management Problem:
 Web Security 2 https://www.xkcd.com/177/ http://xkcd.com/1323/ Encryption basics Plaintext message key secret Encryp)on Func)on Ciphertext Insecure network Decryp)on Func)on Curses! Foiled again! key Plaintext
Web Security 2 https://www.xkcd.com/177/ http://xkcd.com/1323/ Encryption basics Plaintext message key secret Encryp)on Func)on Ciphertext Insecure network Decryp)on Func)on Curses! Foiled again! key Plaintext
ENEE 457: E-Cash and Bitcoin
 ENEE 457: E-Cash and Bitcoin Charalampos (Babis) Papamanthou cpap@umd.edu Money today Any problems? Cash is cumbersome and can be forged Credit card transactions require centralized online bank are not
ENEE 457: E-Cash and Bitcoin Charalampos (Babis) Papamanthou cpap@umd.edu Money today Any problems? Cash is cumbersome and can be forged Credit card transactions require centralized online bank are not
Source Control: Perforce
 USER GUIDE MADCAP FLARE 2018 Source Control: Perforce Copyright 2018 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in this
USER GUIDE MADCAP FLARE 2018 Source Control: Perforce Copyright 2018 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in this
Instruction for creating an Ethereum based wallet and MUH ICO participation
 Instruction for creating an Ethereum based wallet and MUH ICO participation MUST HAVE TOKEN 1. Create your EHT Wallet In order to participate to the MUH ICO, you must have an Ethereum based wallet. You
Instruction for creating an Ethereum based wallet and MUH ICO participation MUST HAVE TOKEN 1. Create your EHT Wallet In order to participate to the MUH ICO, you must have an Ethereum based wallet. You
KINGSTON COIN VPS MASTERNODE SETUP GUIDE
 KINGSTON COIN VPS MASTERNODE SETUP GUIDE ** THIS GUIDE ASSUMES YOU HAVE PURCHASED A VPS THROUGH A SERVICE LIKE DIGITALOCEAN. COM OR VULTR.COM AND HAVE CONNECTED TO YOUR VPS THROUGH SSH/TERMINAL** STEP
KINGSTON COIN VPS MASTERNODE SETUP GUIDE ** THIS GUIDE ASSUMES YOU HAVE PURCHASED A VPS THROUGH A SERVICE LIKE DIGITALOCEAN. COM OR VULTR.COM AND HAVE CONNECTED TO YOUR VPS THROUGH SSH/TERMINAL** STEP
What did we talk about last time? Public key cryptography A little number theory
 Week 4 - Friday What did we talk about last time? Public key cryptography A little number theory If p is prime and a is a positive integer not divisible by p, then: a p 1 1 (mod p) Assume a is positive
Week 4 - Friday What did we talk about last time? Public key cryptography A little number theory If p is prime and a is a positive integer not divisible by p, then: a p 1 1 (mod p) Assume a is positive
Problem Set 10 Due: Start of class December 11
 CS242 Computer Networks Handout # 20 Randy Shull December 4, 2017 Wellesley College Problem Set 10 Due: Start of class December 11 Reading: Kurose & Ross, Sections 7.1 7.3, 8.1 8.4 Wireshark Lab [16] Recall
CS242 Computer Networks Handout # 20 Randy Shull December 4, 2017 Wellesley College Problem Set 10 Due: Start of class December 11 Reading: Kurose & Ross, Sections 7.1 7.3, 8.1 8.4 Wireshark Lab [16] Recall
Algorithms (III) Yijia Chen Shanghai Jiaotong University
 Algorithms (III) Yijia Chen Shanghai Jiaotong University Review of the Previous Lecture Factoring: Given a number N, express it as a product of its prime factors. Many security protocols are based on the
Algorithms (III) Yijia Chen Shanghai Jiaotong University Review of the Previous Lecture Factoring: Given a number N, express it as a product of its prime factors. Many security protocols are based on the
Important Notice. Important Notice
 Important Notice Varien reserves the right to make corrections, modifications, enhancements, improvements, and other changes to its products and services at any time and to discontinue any product or service
Important Notice Varien reserves the right to make corrections, modifications, enhancements, improvements, and other changes to its products and services at any time and to discontinue any product or service
Enigma v1.0. A private, secure and untraceable transaction system for CloakCoin. 18th February 2017
 Enigma v1.0 A private, secure and untraceable transaction system for CloakCoin. 18th February 2017 1. Abstract CloakCoin is a cryptocurrency designed to facilitate private, secure and untraceable decentralized
Enigma v1.0 A private, secure and untraceable transaction system for CloakCoin. 18th February 2017 1. Abstract CloakCoin is a cryptocurrency designed to facilitate private, secure and untraceable decentralized
Computer Security Spring 2010 Paxson/Wagner HW 4. Due Thursday April 15, 5:00pm
 CS 161 Computer Security Spring 2010 Paxson/Wagner HW 4 Due Thursday April 15, 5:00pm Instructions: Submit your solution by Thursday, April 15, 5:00pm electronically. Write up your answers in either PDF
CS 161 Computer Security Spring 2010 Paxson/Wagner HW 4 Due Thursday April 15, 5:00pm Instructions: Submit your solution by Thursday, April 15, 5:00pm electronically. Write up your answers in either PDF
EECS 122: Introduction to Communication Networks Final Exam Solutions
 EECS 22: Introduction to Communication Networks Final Exam Solutions Problem. (6 points) How long does it take for a 3000-byte IP packet to go from host A to host B in the figure below. Assume the overhead
EECS 22: Introduction to Communication Networks Final Exam Solutions Problem. (6 points) How long does it take for a 3000-byte IP packet to go from host A to host B in the figure below. Assume the overhead
Smart Bulk SMS & Voice SMS Marketing Script with 2-Way Messaging. Quick-Start Manual
 Mobiketa Smart Bulk SMS & Voice SMS Marketing Script with 2-Way Messaging Quick-Start Manual Overview Mobiketa Is a full-featured Bulk SMS and Voice SMS marketing script that gives you control over your
Mobiketa Smart Bulk SMS & Voice SMS Marketing Script with 2-Way Messaging Quick-Start Manual Overview Mobiketa Is a full-featured Bulk SMS and Voice SMS marketing script that gives you control over your
Cryptocurrencies for Investigators
 Cryptocurrencies for Investigators By Nick Furneaux CSITech Ltd Course Description Cryptocurrencies in their many forms, based on the blockchain concept, are here to stay and will increasingly pervade
Cryptocurrencies for Investigators By Nick Furneaux CSITech Ltd Course Description Cryptocurrencies in their many forms, based on the blockchain concept, are here to stay and will increasingly pervade
Transaction Cordinator: Design and Planning
 Transaction Cordinator: Design and Planning Joshua Lee, Damon McCormick, Kim Ly, Chris Orimoto, John Wang, and Daniel LeCheminant October 4, 2004 Contents 1 Overview 2 2 Document Revision History 2 3 System
Transaction Cordinator: Design and Planning Joshua Lee, Damon McCormick, Kim Ly, Chris Orimoto, John Wang, and Daniel LeCheminant October 4, 2004 Contents 1 Overview 2 2 Document Revision History 2 3 System
Subscriptions and Recurring Payments 2.X
 Documentation / Documentation Home Subscriptions and Recurring 2.X Created by Unknown User (bondarev), last modified by Unknown User (malynow) on Mar 22, 2017 Installation Set up cron (for eway) Configuration
Documentation / Documentation Home Subscriptions and Recurring 2.X Created by Unknown User (bondarev), last modified by Unknown User (malynow) on Mar 22, 2017 Installation Set up cron (for eway) Configuration
EFILive HD File Conversion Guide
 EFILive 1998 EFILive Limited All rights reserved First published 26 January 2018 Revised 12 February 2018 EFILive, EFILive FlashScan and EFILive AutoCal are registered trademarks of EFILive Limited. All
EFILive 1998 EFILive Limited All rights reserved First published 26 January 2018 Revised 12 February 2018 EFILive, EFILive FlashScan and EFILive AutoCal are registered trademarks of EFILive Limited. All
Register. Account Registration & Deposit / Withdrawal Guide
 Register Account Registration & Deposit / Withdrawal Guide Registration 1 Click here to register your account 2 Enter your details here 3 Check these to agree and proceed 4 Click Register to continue Page
Register Account Registration & Deposit / Withdrawal Guide Registration 1 Click here to register your account 2 Enter your details here 3 Check these to agree and proceed 4 Click Register to continue Page
RSA. Public Key CryptoSystem
 RSA Public Key CryptoSystem DIFFIE AND HELLMAN (76) NEW DIRECTIONS IN CRYPTOGRAPHY Split the Bob s secret key K to two parts: K E, to be used for encrypting messages to Bob. K D, to be used for decrypting
RSA Public Key CryptoSystem DIFFIE AND HELLMAN (76) NEW DIRECTIONS IN CRYPTOGRAPHY Split the Bob s secret key K to two parts: K E, to be used for encrypting messages to Bob. K D, to be used for decrypting
Source Control: Subversion
 USER GUIDE MADCAP FLARE 2018 Source Control: Subversion Copyright 2018 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in
USER GUIDE MADCAP FLARE 2018 Source Control: Subversion Copyright 2018 MadCap Software. All rights reserved. Information in this document is subject to change without notice. The software described in
