INTEGRATION OF TURKISH EID WITH E-GOVERNMENT & E-BUSINESS SERVICES
|
|
|
- Rodney Davis
- 5 years ago
- Views:
Transcription
1 INTEGRATION OF TURKISH EID WITH E-GOVERNMENT & E-BUSINESS SERVICES Oktay Adalier TÜBİTAK BİLGEM UEKAE, 41470, Kocaeli, Turkey Mucahit Mutlugun TÜBİTAK BİLGEM UEKAE, 41470, Kocaeli, Turkey Ahmet Fatih Mustacoglu TÜBİTAK BİLGEM UEKAE, 41470, Kocaeli, Turkey Abstract eid cards and electronic authentication known as E-authentication are becoming more and more popular at Government and Business institutions for recent years and both concepts will continue to remain important for the next decade. Especially in Europe, almost all of the countries have an eid project and the level of the progress varies based on the countries. The citizens have gained great benefits from those e-government Applications in terms of easy use of the services, and rapid return of the results. But there is a big issue from the service provider point of view. Since the resource which is shared by the service requester is very big and the eligibility of the requester is not easy to identify in electronic environments. The main necessity of the entire e- Government and e-business system is to provide a common electronic authentication system that guaranties the eligibility of the service requester (citizen) of a service in an electronic environment is the right person. After stating the principles of Authentication, we introduce Turkish eid card and Electronic Authentication, System (EAS) respectively. We share the experiences that we have obtained during the pilot application of the projects. We discuss the abilities of reducing the bureaucracy in business services via the support of eid card and EAS. As a future work, we identify the requirements for a Turkish eid Integration Center for eid integration with e- Government and e-business applications. Key Words: eid, Electronic Authentication, eservices. JEL Classification: H7 - State and Local Government 1. INTRODUCTION eid cards and electronic authentication known as E-authentication are becoming more and more popular at Government and Business institutions for recent years and both concepts will continue to remain important for the next decade. Especially in Europe, almost all of the countries have an eid project and the level of the progress varies based on the countries. For instance, some of the countries have already finished the deployment of the projects, several of the countries are making pilot projects and the rest of the countries have a plan to prepare projects. 125
2 The main motivation for eid is transforming the business processes from classical environment into electronic ones through the e-transform program. State Planning Organization (DPT) has started the Turkish e-transform Program at The first 5 years of the program has been completed. There are more than 100 action-items to be implemented for several government institutions. At every action, the responsible institution conducts some research and effort to develop a huge e-government application to convert its business services into services that run in electronic environment. Some of them can be listed as MERNİS, TAKBİS, UYAP and Government Portal. The citizens have gained great benefits from those e-government Applications in terms of easy use of the services, and rapid return of the results. But there is a big issue from the service provider point of view. Since the resource which is shared by the service requester is very big and the eligibility of the requester is not easy to identify in electronic environments. Due to the weak authentication in electronic environments, the economical size of unfair issuance of eservices exceeds an amount of 10 billion TL in each year. The main necessity of the entire e-government and e-business system is to provide a common electronic authentication system that guaranties the eligibility of the service requester (citizen) of a service in an electronic environment is the right person. With the motivation of Turkish Prime Ministry circler and under the sponsor of TUBİTAK TARAL program, the Turkish eid project has been developed and a pilot application has been established successfully at the city of Bolu. During the pilot project period, the Turkish Electronic Authentication System has been integrated successfully with several e-government and e-business applications. In this paper, we present integration principles of Turkish eid with e-government and e-business services. Firstly, the current eid developments in the world, especially in Europe, are mentioned. After stating the principles of Authentication, we introduce Turkish eid card and Electronic Authentication, System (EAS) respectively. We share the experiences that we have obtained during the pilot application of the projects. In the next section, the principles of the integration process of eid with e-applications are discussed in detail. Then in the following section, we represent case studies with examples from e-government, e-finance and e-business applications. From e-government point of view, we discuss the integration of MEDULA and Health Automation systems with the EAS including e-receipt. In addition, we model the integration of Turkish Notary business system with EAS. On the finance domain, we discuss the integration of individual and institutional banking applications that use EAS infrastructure including ATM using of eid cards, while on the business domain, we give the integration of Turkish e-government Portal as a key issue for business integration. At the end of the paper, we discuss the abilities of reducing the bureaucracy in business services via the support of eid card and EAS. As a future work, we identify the requirements for a Turkish eid Integration Center for eid integration with e-government and e-business applications. 126
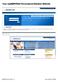
3 2. TURKISH EID AUTHENTICATION SYSTEM 2.1 The Infrastructure of Turksich Authentication Architecture of the Turkish eid authentication system, its components and the flow of the authentication system are depicted in Figure1 below (Mutlugün, 2009): Figure1: Architecture of the Turkish eid Authentication System In the proposed system, Citizen Claim owner Finger print, PIN, ID, certificate Proving units ID Access Device Authenticator Institution Service System (Client / Server) Trusting part 127
4 Above roles are defined. After having a citizen's request for having a service or accessing information, the Turkish eid Authentication steps that are using the eid Authentication System Components will be as follow: 1. Institution service client creates an eid Authentication request. Then, institution service client sends the prepared request to ID Access Device (IDAD) through the other subcomponents called as Security Services Platform (SSP). SSP is explained in detail in section xxx. The client sends a request including authentication reason and its role tag (service requester/service participant) and role information for eid Authentication to SSP. Next, SSP sends the coming request to the related IDAD. 2. IDAD asks citizen for his/her ID card. 3. Depending on authentication role, the citizen inserts his/her card into the IDAD's related slot. Then, IDAD authenticate ID owner's unique id in the citizen's card by validating the signature. 4. SSP communicate with the predefined ID Authentication Policy Server (IDAPS) by using the ID Authentication Summary (IDAS). IDAS includes the rol and the Turkish Citizen Identification Number. Then, IDAPS prepares the policy data for the related application and the citizen. After that, IDAPS signs the policy data and send it to SSP. The most important variable in the policy data is the security level. SSP has the ability to hold policies in its cache and can use them until their expiration date. If SSP can not reach the IDAPS, then it notifies the IDAD resulting in the authentication level to be the highest. 5. To check the validity of the ID Authentication Certificate, SSP sends an OCSP request that is prepared by the IDAD to the Certificate Server. SSP sends the incoming OCSP result from the server to the IDAD. Based on the coming OCSP result (ID is cancelled or not), IDAD either terminate the process or continue to the process. If the SSP can not reach the OCSP, then it inform the IDAD and then IDAD continue to its process and includes that it can not reach the OCSP. Furthermore, SSP has the ability to move OCSP requests to its cache and reuse them if necessary. 6. IDAD requests the PIN/Finger Print based on the security level defined at the coming result from the IDAPS. In the case of security level 1 and 2 that only requires ID card, IDAD continue to process its job. The process is cancelled if the citizen can not provide the requested properties. 7. The citizen gives the requested PIN/Finger Print to IDAD. 8. After performing the authentication processes based on the requested security level, IDAD prepares ID Authentication Summary (IDAS) and sends it to SSP if the authentication is successful. IDAS is only signed by Security Access Modul (SAM) and ID Card if the security access level requires PIN. Otherwise, IDAS is only signed by SAM. 9. Institution Service Client (ISC) sends the IDAS to its own server. 10. Institution Service Server sends the IDAS to ID Authentication Server via secure channels. 11. ID Authentication Server checks the validity of the SAM's certificate that signed the IDAS by either using the Certificate Revocation List (CRL) or by sending a request to OCSP. ID Authentication Server checks the validity of the certificate by in the means of CRL or OCSP if IDAD did not checks the validity of the certificate. 128
5 12. ID Authentication Server executes the authentication process, saves the IDAS to database and sends the result to the Institution Service Server. 13. ID Authentication Server decides whether giving a permission to the requested service based on the authentication result and returns the decision to the Institution Service Client. 2.2 Turkish eid Components eid Card Turkish eid Card composed of the following components: Turkish Identification Number, name and certificate number that are signed by NVI. Electronically signed picture of the citizen Electronically signed finger print of the citizen eid Authentication certificate Electronically signed personal identification information Turkish eid Card holds many physical properties for security and it also contains many other properties electronically for security as well. Operating system of the smart card has the Common Criteria EAL4+ and smart card chip has the Common Criteria EAL5+ security certificate. eid Authentication certificate located on the smart card is compatible with the X.509 standards ID Access Device ID Access Device is used as an authentication tool in the Turkish eid Authentication System. It has also special module called as Security Access Module on it and its main duty is to authenticate the eid card. Security Access Module is responsible for cryptographic processes eid Authentication Server eid Authentication Server is responsible for authenticating the ID Authentication Summary eid Authentication Policy Server eid Authentication Policy Server is responsible for defining a policy for eid authentication eid Authentication Policy eid Authentication policy is produced digitally by eid Authentication Policy Server, and it is constructed in ASN.1 structure. Its contents are as follow: eid Autentication Role Security Level Security level of the finger print Policy validity date Validty period of the ID authentication summary ID authentication condition 129
6 Generic policy Permission for reusing the security level Permission of the mediator eid Authenticaion Server Certificate and signature eid Authentication Sub-Components eid authentication requests have to use eid Authentication sub-components in order to access ID Access Device. There are two types of sub-components: Secure Services Platform for ID Access Devices that are using ethernet interface OYA for ID Access Devices that are using USB interface eid Authentication Summary The data that are generated in the eid Authentication Summary is given below: eid Authentication Summary Sample Id eid Authentication Summary Version 1.00 Summary No 257 Card Serial No PL TC No Name Last Name MEHMET İNALTEKİN Card Validty Date Is mediator used? Mediator Card Serial No --- Mediator TC No --- Mediator Name --- Mediator Last Name --- Mediator Card Validity Date --- Person who is a part of the authentication no Person who is a part of the authentication Card Serial No --- Person who is a part of the authentication TC No --- Person who is a part of the authentication Name --- Person who is a part of the authentication Last Name --- Person who is a part of the authentication Card Validity Date --- Execution Sticker Execution Sticker Explanation no hastakabul@sgk.gov.tr Patient Admission 130
7 Security Level Level-3 Expiration Date Role Biometric Authentication Status Service requester A/D Device chasing No Service Provider chasing No SAM chasing No 1,0203E c91ff274fda141c15 Creation Date :38 IDAD Driver Version Is card cancellation checked? Institution No SAM Signature eid Card Signature 3. CASE STUDIES OF INTEGRATION OF EID WITH ESERVICES 3.1. Integration EAS with Social Security System MEDULA In the current system, permission for a patient from Turkish Health Care System is obtained by TC Identification Number and this process is converted to use ID Authentication Summary instead of the TC Identification Number (Mutlugün, 2010). This process is executed as follow: A citizen goes to application point to get a service. The responsible person at the application desk uses Hospital Data Management System (HDMS) software to initiate the id authentication process. HDMS requests the id authentication from the SSP. HDMS sends hastakabul@sgk.gov.tr execution sticker, role of the service requester and information for which IDAD to use. to SSP. SSP completes the id authentication process by using IDAD. During the id authentication, SSP obtains the policy from ID Authentication Policy Server belongs to Government Healthcare Institution. The security level at the policy is defined by the Government Healthcare Institution so that PIN and finger print is requested or not during the id authentication. SSP sends the ID Authentication Summary coming from IDAD to Government Healthcare Institution. Government Healthcare Institution calls the MEDULA web service by using ID Authentication Summary in order to identify the patient's eligibility. MEDULA uses ID Authentication Server to authenticate the coming ID Authentication Summary. yes 131
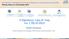
8 MEDULA uses TC Identification Number coming from the ID Authentication Server to query the database in order to identify the eligibility of the patient. And returns the result to the Government Healthcare Institution. If the coming result from MEDULA is successfull then the patient is directed to the related doctor Integration EAS with Financial Services The financial sector has an important place in Turkey. It leads to technological advancement in the everyday life. The online banking application is used by many customers and ATM are scattered around the country. Turkey has the third place within Europe continent by owning the credit and debits cards. The use of those cards exceeds billon of Euros yearly. Every Bank has its own online authentication system. The customers should memorize several passwords and access words for online banking system. On the other hand every online banking system has different authentication system. This situation makes the life for customers difficult and increases the maintenance of the system. Managing the debit cards is another problem for the banks. The Turkish ID card and Electronical Authentication System (EAS) eases the life for both sides. The customers use the national ID cards at ATM environments. For authentication the national EAS is used. For online banking environments the customers should own standard smartcard readers. From the home/office they can connect to the banking services by using national ID cards. After authentication by using EAS they can benefit from the services. As a result the customers should only know one PIN code and use a single eid card. It makes the life ease for both sides Integration of Turkish e-government Portal e-devlet Kapisi is to be Turkey s first egovernment gateway and is well under operation. The portal aims to provide Turkey's 70 million citizens with a single point of access to egovernment services. Currently it support s more than 150 eservices which is owned from several governmental institutions. The gateway also serves a third group of users the public sector agencies themselves allowing them to interact with each other and exchange information. There are for ways to enter to the portal. The first one is by using a username and password. Citizens can hold a username and password pair from post offices. But they very often lost the password. The second one is by using esign certificate which is given by official certificate provider. This case is a little bit costly since the qualified certificate can be owned by paying some amount. The third one is by using Mobile Sign certificate. There are two cell phone operators in Turkey who give mobile esigning support. It requires using cell phones to enter the portal. It also cost some amount of money. The last one is by using national eid card and a card reader. Figure - 2 shows the access window of Turkish Governmental Portal via eid. 132
9 Figure-2: Access window to Turkish Governmental Portal via eid 4. CONCLUSION The integration of Turkish eid and EAS with eservices has reduced the complexity of authentication process. Reduce the maintenance cost. Simplify the use of authentication for user side. Increase the security and unify the infrastructure. As a future work, we identify the requirements for a Turkish eid Integration Center for eid integration with e-government and e-business applications. There will be and authority for guiding the integration process with eservice owner. System analyst support will be given those who have complex applications and process. There will be a testing team ready for qualifying the integration. BIBLIOGRAPHY M. Mutlugün, O. Adalıer (2009), Turkish National Electronic Identity Card, International Conference on Security of Information Networks. M. Mutlugün, O. Adalıer (2010), Turkish Authentication System Definitions Document. Turkish egovernment Portal via national eid (2011), 133
Can eid card make life easier and more secure? Michal Ševčík Industry Solution Consultant Hewlett-Packard, Slovakia ITAPA, November 9 th, 2010
 Can eid card make life easier and more secure? Michal Ševčík Industry Solution Consultant Hewlett-Packard, Slovakia ITAPA, November 9 th, 2010 Content eid Primary Functions eid Privacy Features and Security
Can eid card make life easier and more secure? Michal Ševčík Industry Solution Consultant Hewlett-Packard, Slovakia ITAPA, November 9 th, 2010 Content eid Primary Functions eid Privacy Features and Security
Electronic signature framework
 R E P U B L I C O F S E R B I A Negotation Team for the Accession of Republic of Serbia to the European Union Working Group for Chapter 10 Information society and media Electronic signature framework Contents
R E P U B L I C O F S E R B I A Negotation Team for the Accession of Republic of Serbia to the European Union Working Group for Chapter 10 Information society and media Electronic signature framework Contents
State Planning Organization Information Society Department
 Information Society Department - October TR. Information Society Department Information Society Strategy Duration / Pro- Post- 1 Formulating the Information Society Strategy All Public Institutions Universities
Information Society Department - October TR. Information Society Department Information Society Strategy Duration / Pro- Post- 1 Formulating the Information Society Strategy All Public Institutions Universities
Public Key Infrastructure PKI. National Digital Certification Center Information Technology Authority Sultanate of Oman
 Public Key Infrastructure PKI National Digital Certification Center Information Technology Authority Sultanate of Oman Agenda Objectives PKI Features etrust Components Government eservices Oman National
Public Key Infrastructure PKI National Digital Certification Center Information Technology Authority Sultanate of Oman Agenda Objectives PKI Features etrust Components Government eservices Oman National
INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT
 INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT SUBSCRIBER S GUIDE VERSION 1.3 ECB-PUBLIC 15-April-2014 ESCB-PKI - Subscriber's Procedures v.1.3.docx Page 2 of 26 TABLE OF CONTENTS GLOSSARY AND ACRONYMS...
INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT SUBSCRIBER S GUIDE VERSION 1.3 ECB-PUBLIC 15-April-2014 ESCB-PKI - Subscriber's Procedures v.1.3.docx Page 2 of 26 TABLE OF CONTENTS GLOSSARY AND ACRONYMS...
Want to know more about the PayFlex system?
 Want to know more about the PayFlex system? This newsletter explains how the PayFlex system works, and the steps you need to take to access your accounts and use your funds. 1 Step 1: Log in to PayFlex
Want to know more about the PayFlex system? This newsletter explains how the PayFlex system works, and the steps you need to take to access your accounts and use your funds. 1 Step 1: Log in to PayFlex
Your guide to
 Your guide to www.mypayflex.com PayFlex Systems USA, Inc. 10802 Farnam Drive *Omaha, NE 68154 800.284.4885 * www.mypayflex.com Table of Contents Home Page for www.mypayflex.com...3 How do I login to www.mypayflex.com...4
Your guide to www.mypayflex.com PayFlex Systems USA, Inc. 10802 Farnam Drive *Omaha, NE 68154 800.284.4885 * www.mypayflex.com Table of Contents Home Page for www.mypayflex.com...3 How do I login to www.mypayflex.com...4
GLOBAL PKI TRENDS STUDY
 2018 GLOBAL PKI TRENDS STUDY Sponsored by Thales esecurity Independently conducted by Ponemon Institute LLC SEPTEMBER 2018 EXECUTIVE SUMMARY #2018GlobalPKI Mi Ponemon Institute is pleased to present the
2018 GLOBAL PKI TRENDS STUDY Sponsored by Thales esecurity Independently conducted by Ponemon Institute LLC SEPTEMBER 2018 EXECUTIVE SUMMARY #2018GlobalPKI Mi Ponemon Institute is pleased to present the
Your guide to
 Your guide to www.mypayflex.com PayFlex Systems USA, Inc. 700 Blackstone Centre *Omaha, NE 68131 800.284.4885 * www.mypayflex.com Table of Contents Home Page for www.mypayflex.com...3 How do I login to
Your guide to www.mypayflex.com PayFlex Systems USA, Inc. 700 Blackstone Centre *Omaha, NE 68131 800.284.4885 * www.mypayflex.com Table of Contents Home Page for www.mypayflex.com...3 How do I login to
National Information Center. Ministry of Communication and Information Technology
 National Information Center Ministry of Communication and Information Technology 1 National Information Center The national information center -NIC- founded in 1999 supported with an act issued the same
National Information Center Ministry of Communication and Information Technology 1 National Information Center The national information center -NIC- founded in 1999 supported with an act issued the same
A HOLISTIC APPROACH TO IDENTITY AND AUTHENTICATION. Establish Create Use Manage
 A HOLISTIC APPROACH TO IDENTITY AND AUTHENTICATION Establish Create Use Manage SIMPLE. SECURE. SMART. ALL FROM A SINGLE SOURCE. As the ways to access your organization and its sensitive data increase,
A HOLISTIC APPROACH TO IDENTITY AND AUTHENTICATION Establish Create Use Manage SIMPLE. SECURE. SMART. ALL FROM A SINGLE SOURCE. As the ways to access your organization and its sensitive data increase,
Two types of market (3.3B cellphones WW) City center / USA and European (10%) Rural and urban (90%)
 Two types of market (3.3B cellphones WW) City center / USA and European (10%) Rural and urban (90%) Rural / Urban characteristics (BOP) Very large numbers of people / Socially based systems Very low income
Two types of market (3.3B cellphones WW) City center / USA and European (10%) Rural and urban (90%) Rural / Urban characteristics (BOP) Very large numbers of people / Socially based systems Very low income
Digital Austria = egov best practice in d Europe
 Digital Austria = egov best practice in d Europe egovernment ICT Digital Agenda - Digital Roadmap eidas Univ.Lect. Christian Rupp, CMC ICT in the public sector is like a large vessel - it needs clear
Digital Austria = egov best practice in d Europe egovernment ICT Digital Agenda - Digital Roadmap eidas Univ.Lect. Christian Rupp, CMC ICT in the public sector is like a large vessel - it needs clear
Axway Validation Authority Suite
 Axway Validation Authority Suite PKI safeguards for secure applications Around the world, banks, healthcare organizations, governments, and defense agencies rely on public key infrastructures (PKIs) to
Axway Validation Authority Suite PKI safeguards for secure applications Around the world, banks, healthcare organizations, governments, and defense agencies rely on public key infrastructures (PKIs) to
Certification Report. EAL 4+ (ALC_DVS.2) Evaluation of TÜBİTAK BİLGEM UEKAE. AKİS v1.4i PASAPORT
 Certification Report EAL 4+ (ALC_DVS.2) Evaluation of TÜBİTAK BİLGEM UEKAE AKİS v1.4i PASAPORT issued by Turkish Standards Institution Common Criteria Certification Scheme SOFTWARE TEST and CERTIFICATION
Certification Report EAL 4+ (ALC_DVS.2) Evaluation of TÜBİTAK BİLGEM UEKAE AKİS v1.4i PASAPORT issued by Turkish Standards Institution Common Criteria Certification Scheme SOFTWARE TEST and CERTIFICATION
Non Person Identities After all, who cares about me? Gilles Lisimaque & Dave Auman Identification technology Partners, Inc.
 Identities Non Person Identities After all, who cares about me? Gilles Lisimaque & Dave Auman Identification technology Partners, Inc. Device Identifiers Most devices we are using everyday have (at least)
Identities Non Person Identities After all, who cares about me? Gilles Lisimaque & Dave Auman Identification technology Partners, Inc. Device Identifiers Most devices we are using everyday have (at least)
Electronic Prescribing of Controlled Substance (EPCS) Registration Single Provider Process
 Allscripts eprescribe Electronic Prescribing of Controlled Substance (EPCS) Registration Single Provider Process Copyright 2013 Allscripts Healthcare, LLC. www.allscripts.com Single Provider Registration
Allscripts eprescribe Electronic Prescribing of Controlled Substance (EPCS) Registration Single Provider Process Copyright 2013 Allscripts Healthcare, LLC. www.allscripts.com Single Provider Registration
BCU Pay Anyone Terms and Conditions Credit Union Pay Anyone Service Agreement and Terms of Use ("Terms of Use") 1. Description of Service and Consent
 BCU Pay Anyone Terms and Conditions Credit Union Pay Anyone Service Agreement and Terms of Use ("Terms of Use") 1. Description of Service and Consent You may use your debit card information to send funds
BCU Pay Anyone Terms and Conditions Credit Union Pay Anyone Service Agreement and Terms of Use ("Terms of Use") 1. Description of Service and Consent You may use your debit card information to send funds
INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY
 INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY A PATH FOR HORIZING YOUR INNOVATIVE WORK A PROPOSAL FOR UNIQUE IDENTIFICATION NUMBER FOR ALL ONLINE ACCOUNT HOLDERS TO CURB
INTERNATIONAL JOURNAL OF PURE AND APPLIED RESEARCH IN ENGINEERING AND TECHNOLOGY A PATH FOR HORIZING YOUR INNOVATIVE WORK A PROPOSAL FOR UNIQUE IDENTIFICATION NUMBER FOR ALL ONLINE ACCOUNT HOLDERS TO CURB
Modify Tenancy Contact - User Manual
 Modify Tenancy Contact - User Manual Table of Contents About Service... 3 Service requirements... 3 Required Documents... 3 Service fees... 3 How to apply for this service... 4 Validation Messages... 26
Modify Tenancy Contact - User Manual Table of Contents About Service... 3 Service requirements... 3 Required Documents... 3 Service fees... 3 How to apply for this service... 4 Validation Messages... 26
Singapore s National Digital Identity (NDI):
 Singapore s National Digital Identity (NDI): Leaving no one behind Kwok Quek Sin Director, National Digital Identity Programme Government Technology Agency PART 1 INTRODUCTION TO NDI Better Living For
Singapore s National Digital Identity (NDI): Leaving no one behind Kwok Quek Sin Director, National Digital Identity Programme Government Technology Agency PART 1 INTRODUCTION TO NDI Better Living For
Legal Regulations and Vulnerability Analysis
 Legal Regulations and Vulnerability Analysis Bundesamt für Sicherheit in der Informationstechnik (BSI) (Federal Office for Information Security) Germany Introduction of the BSI National Authority for Information
Legal Regulations and Vulnerability Analysis Bundesamt für Sicherheit in der Informationstechnik (BSI) (Federal Office for Information Security) Germany Introduction of the BSI National Authority for Information
ACCOUNT SWITCH KIT. The Honesdale National Bank
 ACCOUNT SWITCH KIT Move your accounts to quickly and easily. To get started, follow the steps below and submit the form online or through your local HNB Office. Step 1 Complete our New Account Information
ACCOUNT SWITCH KIT Move your accounts to quickly and easily. To get started, follow the steps below and submit the form online or through your local HNB Office. Step 1 Complete our New Account Information
Securing Americans Identities: The Future of the Social Security Number
 Cha : Testimony, SASC 04 /25 /2017 1 Statement Before the House Ways and Means Subcommittee on Social Security Securing Americans Identities: The Future of the Social Security Number A Testimony by: James
Cha : Testimony, SASC 04 /25 /2017 1 Statement Before the House Ways and Means Subcommittee on Social Security Securing Americans Identities: The Future of the Social Security Number A Testimony by: James
Mobile App. IBEW-NECA Benefits Administration Association - Proprietary
 Before you can login to the mobile app, you must set up your account on the HRA Participant Portal at https://necaibew.lh1ondemand.com. For instructions on setting up your account, please refer to this
Before you can login to the mobile app, you must set up your account on the HRA Participant Portal at https://necaibew.lh1ondemand.com. For instructions on setting up your account, please refer to this
Technical Trust Policy
 Technical Trust Policy Version 1.2 Last Updated: May 20, 2016 Introduction Carequality creates a community of trusted exchange partners who rely on each organization s adherence to the terms of the Carequality
Technical Trust Policy Version 1.2 Last Updated: May 20, 2016 Introduction Carequality creates a community of trusted exchange partners who rely on each organization s adherence to the terms of the Carequality
Worker s (Employee) Self-Service User Guide. Ohio Unemployment Employee Benefit Information at Your Fingertips
 Worker s (Employee) Self-Service User Guide Ohio Unemployment Employee Benefit Information at Your Fingertips Why Use Employee Self Service? Employee Self-Service offers many benefits in processing your
Worker s (Employee) Self-Service User Guide Ohio Unemployment Employee Benefit Information at Your Fingertips Why Use Employee Self Service? Employee Self-Service offers many benefits in processing your
Citizen Biometric Authentication based on e-document verification. e-government perspective. Mindshare Ruslans Arzaniks Head of Development
 Citizen Biometric Authentication based on e-document verification. e-government perspective. Mindshare 2017 Ruslans Arzaniks Head of Development About us WHO WE ARE X Infotech is a global provider of software
Citizen Biometric Authentication based on e-document verification. e-government perspective. Mindshare 2017 Ruslans Arzaniks Head of Development About us WHO WE ARE X Infotech is a global provider of software
esign - Evolving Opportunities and Applications C E N T R E F O R D E V ELOPMENT O F A D VANCED C O MPUTING N O V E M B E R 1 5,
 esign - Evolving Opportunities and Applications C E N T R E F O R D E V ELOPMENT O F A D VANCED C O MPUTING N O V E M B E R 1 5, 2 0 1 7 Presentation Outline e-sign Architecture Interesting Challenges
esign - Evolving Opportunities and Applications C E N T R E F O R D E V ELOPMENT O F A D VANCED C O MPUTING N O V E M B E R 1 5, 2 0 1 7 Presentation Outline e-sign Architecture Interesting Challenges
The new standard for user authentication
 + + The new standard for user authentication the convenient authentication 03 Summary 04 How does it work? 05 Benefits of convenient authentication for end users 06 Use cases 07 Click & Mortar 08 Natural
+ + The new standard for user authentication the convenient authentication 03 Summary 04 How does it work? 05 Benefits of convenient authentication for end users 06 Use cases 07 Click & Mortar 08 Natural
IDEX company presentation. January 2009
 IDEX company presentation January 2009 About IDEX ASA IDEX ASA is a public company traded on the Oslo OTC list. IDEX is headquartered near Oslo, Norway with its US office in Foster City, California. IDEX
IDEX company presentation January 2009 About IDEX ASA IDEX ASA is a public company traded on the Oslo OTC list. IDEX is headquartered near Oslo, Norway with its US office in Foster City, California. IDEX
Next Generation Physical Access Control Systems A Smart Card Alliance Educational Institute Workshop
 Next Generation Physical Access Control Systems A Smart Card Alliance Educational Institute Workshop PACS Integration into the Identity Infrastructure Salvatore D Agostino CEO, IDmachines LLC 8 th Annual
Next Generation Physical Access Control Systems A Smart Card Alliance Educational Institute Workshop PACS Integration into the Identity Infrastructure Salvatore D Agostino CEO, IDmachines LLC 8 th Annual
Vietnam: Current status of IT Policy and IT flagship Projects
 Vietnam: Current status of IT Policy and IT flagship Projects Mr. Nguyen Phu Tien Deputy Director General Authority of Information Technology Application Ministry of Information and Communications, Vietnam
Vietnam: Current status of IT Policy and IT flagship Projects Mr. Nguyen Phu Tien Deputy Director General Authority of Information Technology Application Ministry of Information and Communications, Vietnam
Identify adequate calls and analyze the call text
 TURKEY IN HORIZON 2020 ALTUN/HORIZ/TR2012/0740.14-2/SER/005 H2020 General Training Finding Calls Understanding the call texts Identify adequate calls and analyze the call text "From an idea to a proposal"
TURKEY IN HORIZON 2020 ALTUN/HORIZ/TR2012/0740.14-2/SER/005 H2020 General Training Finding Calls Understanding the call texts Identify adequate calls and analyze the call text "From an idea to a proposal"
IT Security Evaluation : Common Criteria
 AfriNIC-9 MEETING Mauritius 22-28 November 2008 IT Security Evaluation : Common Criteria Ministry of Communication Technologies National Digital Certification Agency Mounir Ferjani November 2008 afrinic
AfriNIC-9 MEETING Mauritius 22-28 November 2008 IT Security Evaluation : Common Criteria Ministry of Communication Technologies National Digital Certification Agency Mounir Ferjani November 2008 afrinic
FSN-PalmSecureID-for ATM Machines
 T he application of biometric solutions in ATMs and electronic point-of-sale solutions provide a high- security environment. By using a smartcard, on which the client's unique palm vein pattern is stored,
T he application of biometric solutions in ATMs and electronic point-of-sale solutions provide a high- security environment. By using a smartcard, on which the client's unique palm vein pattern is stored,
Public-Key Infrastructure NETS E2008
 Public-Key Infrastructure NETS E2008 Many slides from Vitaly Shmatikov, UT Austin slide 1 Authenticity of Public Keys? private key Alice Bob public key Problem: How does Alice know that the public key
Public-Key Infrastructure NETS E2008 Many slides from Vitaly Shmatikov, UT Austin slide 1 Authenticity of Public Keys? private key Alice Bob public key Problem: How does Alice know that the public key
Humana Access Online User Guide. Simplify your healthcare finances with convenient, online access to your tax-advantaged benefit account
 Humana Access Online User Guide Simplify your healthcare finances with convenient, online access to your tax-advantaged benefit account 1 Humana Access Contents Getting Started... 2 HOW TO REGISTER YOUR
Humana Access Online User Guide Simplify your healthcare finances with convenient, online access to your tax-advantaged benefit account 1 Humana Access Contents Getting Started... 2 HOW TO REGISTER YOUR
DEPARTMENT OF HIGHER EDUCATION, HARYANA ONLINE ADMISSIONS. URL:
 DEPARTMENT OF HIGHER EDUCATION, HARYANA ONLINE ADMISSIONS User Manual for Online Admissions 2018-2019 URL: http://www.online.highereduhry.com Overview is a unit of the Government of Haryana in India that
DEPARTMENT OF HIGHER EDUCATION, HARYANA ONLINE ADMISSIONS User Manual for Online Admissions 2018-2019 URL: http://www.online.highereduhry.com Overview is a unit of the Government of Haryana in India that
Public. Atos Trustcenter. Server Certificates + Codesigning Certificates. Version 1.2
 Atos Trustcenter Server Certificates + Codesigning Certificates Version 1.2 20.11.2015 Content 1 Introduction... 3 2 The Atos Trustcenter Portfolio... 3 3 TrustedRoot PKI... 4 3.1 TrustedRoot Hierarchy...
Atos Trustcenter Server Certificates + Codesigning Certificates Version 1.2 20.11.2015 Content 1 Introduction... 3 2 The Atos Trustcenter Portfolio... 3 3 TrustedRoot PKI... 4 3.1 TrustedRoot Hierarchy...
E-services instructions https://asiointi.hel.fi. The City of Helsinki e-services support, open Mon-Fri from 8 AM to 6 PM Tel.
 1 E-services instructions https://asiointi.hel.fi The City of Helsinki e-services support, open Mon-Fri from 8 AM to 6 PM Tel. (09) 310 88800 Contents 1. First page and phone support number 3. What is
1 E-services instructions https://asiointi.hel.fi The City of Helsinki e-services support, open Mon-Fri from 8 AM to 6 PM Tel. (09) 310 88800 Contents 1. First page and phone support number 3. What is
Discussion on MS contribution to the WP2018
 Discussion on MS contribution to the WP2018, 30 January 2018 European Union Agency for Network and Information Security Possibilities for MS contribution to the WP2018 Expert Groups ENISA coordinates several
Discussion on MS contribution to the WP2018, 30 January 2018 European Union Agency for Network and Information Security Possibilities for MS contribution to the WP2018 Expert Groups ENISA coordinates several
Your mymeritain Personalized Member Website
 Your mymeritain Personalized Member Website 2008 Meritain Health, Inc. Last Updated 5.23.2008 Your mymeritain Member Website The mymeritain Member Website offers Members a user-friendly web experience,
Your mymeritain Personalized Member Website 2008 Meritain Health, Inc. Last Updated 5.23.2008 Your mymeritain Member Website The mymeritain Member Website offers Members a user-friendly web experience,
The Business Case for Electronic or Digital Signatures
 The Business Case for Electronic or Digital Signatures Testimony Before the NCVHS Subcommittee on Standards and Security. October 26, 2000 Gunther Schadow, M.D. Regenstrief Institute for Health Care, Indianapolis,
The Business Case for Electronic or Digital Signatures Testimony Before the NCVHS Subcommittee on Standards and Security. October 26, 2000 Gunther Schadow, M.D. Regenstrief Institute for Health Care, Indianapolis,
CAMP USER S GUIDE IFMA CREDENTIALS CREDENTIALS APPLICATION AND MAINTENANCE PROGRAM
 CAMP USER S GUIDE IFMA CREDENTIALS CREDENTIALS APPLICATION AND MAINTENANCE PROGRAM VV0118CREDENTIALS APPLICATION AND MAINTENANCE PROGRAM CA User's Guide for IFMA's Credential Application and Maintenance
CAMP USER S GUIDE IFMA CREDENTIALS CREDENTIALS APPLICATION AND MAINTENANCE PROGRAM VV0118CREDENTIALS APPLICATION AND MAINTENANCE PROGRAM CA User's Guide for IFMA's Credential Application and Maintenance
By accessing your Congressional Federal Credit Union account(s) electronically with the use of Online Banking through a personal computer or any other
 CONGRESSIONAL FEDERAL CREDIT UNION ELECTRONIC CORRESPONDENCE DISCLOSURE & AGREEMENT Please read this information carefully and print a copy and/or retain this information electronically for your records.
CONGRESSIONAL FEDERAL CREDIT UNION ELECTRONIC CORRESPONDENCE DISCLOSURE & AGREEMENT Please read this information carefully and print a copy and/or retain this information electronically for your records.
eauthentication and Cross Boarder etransaction
 eauthentication and Cross Boarder etransaction James Wu / jrsys CEO 1 1 Taiwan s e-gov Journey Efficiency & Effectiveness Infrastructure Development & Penetration Online Service Development Integrated,
eauthentication and Cross Boarder etransaction James Wu / jrsys CEO 1 1 Taiwan s e-gov Journey Efficiency & Effectiveness Infrastructure Development & Penetration Online Service Development Integrated,
Certificate Revocation Checking using OCSP and CRL in View 4.5 T E C H N I C A L W H I T E P A P E R
 Certificate Revocation Checking using OCSP and CRL in View 4.5 T E C H N I C A L W H I T E P A P E R Certificate Revocation Checking using OCSP/CRL in View4.5 Table of Contents Introduction... 2 About
Certificate Revocation Checking using OCSP and CRL in View 4.5 T E C H N I C A L W H I T E P A P E R Certificate Revocation Checking using OCSP/CRL in View4.5 Table of Contents Introduction... 2 About
Certification Authority
 Certification Authority Overview Identifying CA Hierarchy Design Requirements Common CA Hierarchy Designs Documenting Legal Requirements Analyzing Design Requirements Designing a Hierarchy Structure Identifying
Certification Authority Overview Identifying CA Hierarchy Design Requirements Common CA Hierarchy Designs Documenting Legal Requirements Analyzing Design Requirements Designing a Hierarchy Structure Identifying
Procedure for Online Bill Payment & Registration of Consumers through
 Procedure for Online Bill Payment & Registration of Consumers through www.apdcl.org Consumers can pay their electricity bills through our official website www.apdcl.org. The following two options are currently
Procedure for Online Bill Payment & Registration of Consumers through www.apdcl.org Consumers can pay their electricity bills through our official website www.apdcl.org. The following two options are currently
white paper SMS Authentication: 10 Things to Know Before You Buy
 white paper SMS Authentication: 10 Things to Know Before You Buy SMS Authentication white paper Introduction Delivering instant remote access is no longer just about remote employees. It s about enabling
white paper SMS Authentication: 10 Things to Know Before You Buy SMS Authentication white paper Introduction Delivering instant remote access is no longer just about remote employees. It s about enabling
University Health Network (UHN)
 University Health Network (UHN) RESOURCE MATCHING AND REFERRAL (RM&R) AND ONLINE REFERRAL BUSINESS INTELLIGENCE TOOL (ORBIT) Policy Governing User Account Management Version: 4.0 Date: Last modified on
University Health Network (UHN) RESOURCE MATCHING AND REFERRAL (RM&R) AND ONLINE REFERRAL BUSINESS INTELLIGENCE TOOL (ORBIT) Policy Governing User Account Management Version: 4.0 Date: Last modified on
Start with MULTILINE MARCH 2015
 Start with MULTILINE MARCH 2015 Table of contents Welcome to Multiline... 2 MultiLine contains many opportunities to increase your efficiency... 2 Features to make your life easier:... 3 Terminology...
Start with MULTILINE MARCH 2015 Table of contents Welcome to Multiline... 2 MultiLine contains many opportunities to increase your efficiency... 2 Features to make your life easier:... 3 Terminology...
Deliverable D3.5 Harmonised e-authentication architecture in collaboration with STORK platform (M40) ATTPS. Achieving The Trust Paradigm Shift
 Deliverable D3.5 Harmonised e-authentication architecture in collaboration with STORK platform (M40) Version 1.0 Author: Bharadwaj Pulugundla (Verizon) 25.10.2015 Table of content 1. Introduction... 3
Deliverable D3.5 Harmonised e-authentication architecture in collaboration with STORK platform (M40) Version 1.0 Author: Bharadwaj Pulugundla (Verizon) 25.10.2015 Table of content 1. Introduction... 3
PEOPLES COMMUNITY BANK IT S AS EASY AS 1,2,3!
 Switch To A True Community Bank. PEOPLES COMMUNITY BANK IT S AS EASY AS 1,2,3! Here s All You Need To Do. 1. Complete the New Account Application and other applicable information sheets. If you don t want
Switch To A True Community Bank. PEOPLES COMMUNITY BANK IT S AS EASY AS 1,2,3! Here s All You Need To Do. 1. Complete the New Account Application and other applicable information sheets. If you don t want
ONE ID Identity and Access Management System
 ONE ID Identity and Access Management System Local Registration Authority User Guide Document Identifier: 2274 Version: 1.8 Page 1 Copyright Notice Copyright 2011, ehealth Ontario All rights reserved No
ONE ID Identity and Access Management System Local Registration Authority User Guide Document Identifier: 2274 Version: 1.8 Page 1 Copyright Notice Copyright 2011, ehealth Ontario All rights reserved No
How to Register with the Medical Use of Marijuana Program: Instructions for Patients
 CHARLES D. BAKER Governor KARYN E. POLITO Lieutenant Governor The Commonwealth of Massachusetts Executive Office of Health and Human Services Department of Public Health Bureau of Health Care Safety and
CHARLES D. BAKER Governor KARYN E. POLITO Lieutenant Governor The Commonwealth of Massachusetts Executive Office of Health and Human Services Department of Public Health Bureau of Health Care Safety and
Harmonisation of Digital Markets in the EaP. Vassilis Kopanas European Commission, DG CONNECT
 Harmonisation of Digital Markets in the EaP Vassilis Kopanas European Commission, DG CONNECT vassilis.kopanas@ec.europa.eu The cost of non-europe European Parliament Research Study, March 2014 Fully realising
Harmonisation of Digital Markets in the EaP Vassilis Kopanas European Commission, DG CONNECT vassilis.kopanas@ec.europa.eu The cost of non-europe European Parliament Research Study, March 2014 Fully realising
Overview of PBI-blockchain cooperation technology
 FOR IMMEDIATE RELEASE Biometric authentication technology to realize secure trade on blockchain Enabling IoT payments and automatic transactions through PBI (1) -blockchain cooperation technology Overview
FOR IMMEDIATE RELEASE Biometric authentication technology to realize secure trade on blockchain Enabling IoT payments and automatic transactions through PBI (1) -blockchain cooperation technology Overview
WHITE PAPER Cloud FastPath: A Highly Secure Data Transfer Solution
 WHITE PAPER Cloud FastPath: A Highly Secure Data Transfer Solution Tervela helps companies move large volumes of sensitive data safely and securely over network distances great and small. We have been
WHITE PAPER Cloud FastPath: A Highly Secure Data Transfer Solution Tervela helps companies move large volumes of sensitive data safely and securely over network distances great and small. We have been
Single Secure Credential to Access Facilities and IT Resources
 Single Secure Credential to Access Facilities and IT Resources HID PIV Solutions Securing access to premises, applications and networks Organizational Challenges Organizations that want to secure access
Single Secure Credential to Access Facilities and IT Resources HID PIV Solutions Securing access to premises, applications and networks Organizational Challenges Organizations that want to secure access
CEF eid SMO The use of eid in ehealth. ehealth Network meeting 7 June 2016 Amsterdam
 CEF eid SMO The use of eid in ehealth ehealth Network meeting 7 June 2016 Amsterdam Agenda Introduction to the study Introduction to eidas Regulation and CEF eid Identification/ authentication for ehealth
CEF eid SMO The use of eid in ehealth ehealth Network meeting 7 June 2016 Amsterdam Agenda Introduction to the study Introduction to eidas Regulation and CEF eid Identification/ authentication for ehealth
Configuring SSL CHAPTER
 7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
Portal User Guide Member Features
 Portal User Guide Member Features Updated: 04/22/2017 Accessing your claims just got easier WorkAbility Absence Management System Our WorkAbility website makes it easy to access your claims. You get online
Portal User Guide Member Features Updated: 04/22/2017 Accessing your claims just got easier WorkAbility Absence Management System Our WorkAbility website makes it easy to access your claims. You get online
Put Identity at the Heart of Security
 Put Identity at the Heart of Security Strong Authentication via Hitachi Biometric Technology Tadeusz Woszczyński Country Manager Poland, Hitachi Europe Ltd. 20 September 2017 Financial security in the
Put Identity at the Heart of Security Strong Authentication via Hitachi Biometric Technology Tadeusz Woszczyński Country Manager Poland, Hitachi Europe Ltd. 20 September 2017 Financial security in the
hidglobal.com HID ActivOne USER FRIENDLY STRONG AUTHENTICATION
 HID ActivOne USER FRIENDLY STRONG AUTHENTICATION We understand IT security is one of the TOUGHEST business challenges today. HID Global is your trusted partner in the fight against data breach due to misused
HID ActivOne USER FRIENDLY STRONG AUTHENTICATION We understand IT security is one of the TOUGHEST business challenges today. HID Global is your trusted partner in the fight against data breach due to misused
WHITE PAPER. OAuth A new era in Identity Management and its Applications. Abstract
 WHITE PAPER OAuth A new era in Identity Management and its Applications Abstract OAuth protocol is a standard which allows end users to share their web resources with the third-party applications without
WHITE PAPER OAuth A new era in Identity Management and its Applications Abstract OAuth protocol is a standard which allows end users to share their web resources with the third-party applications without
Architecture Assessment Case Study. Single Sign on Approach Document PROBLEM: Technology for a Changing World
 Technology for a Changing World Architecture Assessment Case Study Single Sign on Approach Document PROBLEM: Existing portal has Sign on Capabilities based on the SQL Server database and it s not having
Technology for a Changing World Architecture Assessment Case Study Single Sign on Approach Document PROBLEM: Existing portal has Sign on Capabilities based on the SQL Server database and it s not having
INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT
 INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT ESCB-PKI REGISTRATION AUTHORITY APPLICATION MOST COMMON ERRORS VERSION 1.2 ECB-PUBLIC 15-November-2012 ESCB-PKI - Common errors v.1.2.docx Page 2 of 20
INFORMATION TECHNOLOGY COMMITTEE ESCB-PKI PROJECT ESCB-PKI REGISTRATION AUTHORITY APPLICATION MOST COMMON ERRORS VERSION 1.2 ECB-PUBLIC 15-November-2012 ESCB-PKI - Common errors v.1.2.docx Page 2 of 20
E-Signature Law of Iraq no. ( 78) of 2012
 INTER-REGIONAL STANDARDIZATION FORUM FOR BRIDGING THE STANDARDIZATION GAP (BSG) Muscat, Oman, 11-12 December 2017 E-Signature Law of Iraq no. ( 78) of 2012 Halah Alrubaye Projects follow-up manager, Ministry
INTER-REGIONAL STANDARDIZATION FORUM FOR BRIDGING THE STANDARDIZATION GAP (BSG) Muscat, Oman, 11-12 December 2017 E-Signature Law of Iraq no. ( 78) of 2012 Halah Alrubaye Projects follow-up manager, Ministry
DCCKI Interface Design Specification. and. DCCKI Repository Interface Design Specification
 DCCKI Interface Design Specification and DCCKI Repository Interface Design Specification 1 INTRODUCTION Document Purpose 1.1 Pursuant to Section L13.13 of the Code (DCCKI Interface Design Specification),
DCCKI Interface Design Specification and DCCKI Repository Interface Design Specification 1 INTRODUCTION Document Purpose 1.1 Pursuant to Section L13.13 of the Code (DCCKI Interface Design Specification),
Mehmet İzzet Hacıalioğlu Digital Special Projects & Security Manager
 Current and Future Digital Transformation Mehmet İzzet Hacıalioğlu Digital Special Projects & Security Manager @mehmetizzet Overview of Turkey 80 M population young 67 % young population 94 % mobile penetration
Current and Future Digital Transformation Mehmet İzzet Hacıalioğlu Digital Special Projects & Security Manager @mehmetizzet Overview of Turkey 80 M population young 67 % young population 94 % mobile penetration
SIAM R3.0 USER GUIDE
 SIAM R3.0 USER GUIDE Document Reference: 8295 September 2016 Revision: 3 Version Date Author Changes Number 1 Mar 2015 John Lindsay 2 Jun Sam Unsuspending a SIM card description updated. 2016 Smith 3 Sep
SIAM R3.0 USER GUIDE Document Reference: 8295 September 2016 Revision: 3 Version Date Author Changes Number 1 Mar 2015 John Lindsay 2 Jun Sam Unsuspending a SIM card description updated. 2016 Smith 3 Sep
Participant Reference Guide
 Participant Reference Guide Welcome to FlexSystem and to the tax saving benefits of a Section 125 Cafeteria Plan. We hope you will find FlexSystem to be an efficient and valuable service. Our Participant
Participant Reference Guide Welcome to FlexSystem and to the tax saving benefits of a Section 125 Cafeteria Plan. We hope you will find FlexSystem to be an efficient and valuable service. Our Participant
eduroam Managed IdP Product Presentation
 eduroam Managed IdP Product Presentation Stefan Winter GeGC Technical Expert, Task Leader eduroam Development @GEANT R&D Engineer, RESTENA Foundation, Luxembourg Last updated: 13 June 2017 eduroam Managed
eduroam Managed IdP Product Presentation Stefan Winter GeGC Technical Expert, Task Leader eduroam Development @GEANT R&D Engineer, RESTENA Foundation, Luxembourg Last updated: 13 June 2017 eduroam Managed
Wireless Communication Stipend Effective Date: 9/1/2008
 Category: Financial Policy applicable for: Faculty/Staff Policy Title: Policy Number: Wireless Communication Stipend Effective Date: 9/1/2008 Enabling Act(s) IRS rule 2.1.7 Policy Owner: Sr. VP for Administration
Category: Financial Policy applicable for: Faculty/Staff Policy Title: Policy Number: Wireless Communication Stipend Effective Date: 9/1/2008 Enabling Act(s) IRS rule 2.1.7 Policy Owner: Sr. VP for Administration
eservice Andreas Meier & Luis Terán Information Systems Research Group University of Fribourg
 eservice Andreas Meier & Luis Terán Information Systems Research Group University of Fribourg Second International Seminar on edemocracy and egovernment. Quito - Ecuador Learning Targets!!! How can the
eservice Andreas Meier & Luis Terán Information Systems Research Group University of Fribourg Second International Seminar on edemocracy and egovernment. Quito - Ecuador Learning Targets!!! How can the
CERN Certification Authority
 CERN Certification Authority Emmanuel Ormancey (IT/IS) What are Certificates? What are Certificates? Digital certificates are electronic credentials that are used to certify the identities of individuals,
CERN Certification Authority Emmanuel Ormancey (IT/IS) What are Certificates? What are Certificates? Digital certificates are electronic credentials that are used to certify the identities of individuals,
Requirements for NCOWCICB certification with Business Succession Exemption Please read and follow carefully.
 Requirements for NCOWCICB certification with Business Succession Exemption Please read and follow carefully. To be exempt from taking the 18 hour introductory course, the applicant must provide the following
Requirements for NCOWCICB certification with Business Succession Exemption Please read and follow carefully. To be exempt from taking the 18 hour introductory course, the applicant must provide the following
CELL PHONE POLICY Page 1 of 5 City of Manteca Administrative Policy and Procedure
 CELL PHONE POLICY Page 1 of 5 Section 1: Purpose The City of Manteca recognizes that cellular telephones enhance the level of City services by allowing employees to remain in contact with the office or
CELL PHONE POLICY Page 1 of 5 Section 1: Purpose The City of Manteca recognizes that cellular telephones enhance the level of City services by allowing employees to remain in contact with the office or
egov & PKI By: Alaa Eldin Mahmoud Aly YOUR LOGO
 egov & PKI By: Alaa Eldin Mahmoud Aly YOUR LOGO e-government Survey 2014 United Nations Page 2 EGDI: E-Government Development Index National ID & Digital Signature Estonian Prime Minister Andrus Ansip
egov & PKI By: Alaa Eldin Mahmoud Aly YOUR LOGO e-government Survey 2014 United Nations Page 2 EGDI: E-Government Development Index National ID & Digital Signature Estonian Prime Minister Andrus Ansip
1. Publishable Summary
 1. Publishable Summary 1.1Project objectives and context Identity management (IdM) has emerged as a promising technology to distribute identity information across security domains. In e-business scenarios,
1. Publishable Summary 1.1Project objectives and context Identity management (IdM) has emerged as a promising technology to distribute identity information across security domains. In e-business scenarios,
CERTIFICATE POLICY CIGNA PKI Certificates
 CERTIFICATE POLICY CIGNA PKI Certificates Version: 1.1 Effective Date: August 7, 2001 a Copyright 2001 CIGNA 1. Introduction...3 1.1 Important Note for Relying Parties... 3 1.2 Policy Identification...
CERTIFICATE POLICY CIGNA PKI Certificates Version: 1.1 Effective Date: August 7, 2001 a Copyright 2001 CIGNA 1. Introduction...3 1.1 Important Note for Relying Parties... 3 1.2 Policy Identification...
Phishing Read Behind The Lines
 Phishing Read Behind The Lines Veljko Pejović veljko@cs.ucsb.edu What is Phishing? "Phishing attacks use both social engineering and technical subterfuge to steal consumers' personal identity data and
Phishing Read Behind The Lines Veljko Pejović veljko@cs.ucsb.edu What is Phishing? "Phishing attacks use both social engineering and technical subterfuge to steal consumers' personal identity data and
Oracle Banking Digital Experience
 Oracle Banking Digital Experience Retail Customer Services User Manual Release 18.2.0.0.0 Part No. E97823-01 June 2018 Retail Customer Services User Manual June 2018 Oracle Financial Services Software
Oracle Banking Digital Experience Retail Customer Services User Manual Release 18.2.0.0.0 Part No. E97823-01 June 2018 Retail Customer Services User Manual June 2018 Oracle Financial Services Software
Aaple Sarkar DBT Portal
 Aaple Sarkar DBT Portal Aaple Sarkar DBT Portal (Direct Benefit Transfer) is an initiative taken by the Government of Maharashtra, which is a unique Platform for Citizens to help them to avail benefits
Aaple Sarkar DBT Portal Aaple Sarkar DBT Portal (Direct Benefit Transfer) is an initiative taken by the Government of Maharashtra, which is a unique Platform for Citizens to help them to avail benefits
IMEI Database. Manufacturer / Brand Owner User Guide. Version September Copyright Notice. Copyright 2015 GSM Association
 IMEI Database Manufacturer / Brand Owner User Guide Version 4.0 01 September 2015 Copyright Notice Copyright 2015 GSM Association GSM and the GSM logo are registered and owned by the GSM Association. Antitrust
IMEI Database Manufacturer / Brand Owner User Guide Version 4.0 01 September 2015 Copyright Notice Copyright 2015 GSM Association GSM and the GSM logo are registered and owned by the GSM Association. Antitrust
Standard mobile phone a mobile device that can make and receive telephone calls, pictures, video, and text messages.
 Overview Fiscal Accountability Rule 10.9 Utilizing Mobile Devices to Conduct City Business establishes the mobile device rule for the City and County of Denver. This policy provides mobile device guidelines
Overview Fiscal Accountability Rule 10.9 Utilizing Mobile Devices to Conduct City Business establishes the mobile device rule for the City and County of Denver. This policy provides mobile device guidelines
Now there is: Asignio web-based signature authentication.
 THE COST OF KYC AND AML Know Your Customer (KYC) technology and Anti-Money Laundering (AML) compliance are crucial elements of modern banking. Financial institutions are trusted to verify and authenticate
THE COST OF KYC AND AML Know Your Customer (KYC) technology and Anti-Money Laundering (AML) compliance are crucial elements of modern banking. Financial institutions are trusted to verify and authenticate
GRANTS AND CONTRIBUTIONS ONLINE SERVICES USER GUIDE: CANADA SUMMER JOBS
 GRANTS AND CONTRIBUTIONS ONLINE SERVICES USER GUIDE: CANADA SUMMER JOBS DECEMBER 2016 TABLE OF CONTENTS IMPORTANT THINGS TO REMEMBER... 4 1. SUBMITTING A CANADA SUMMER JOBS APPLICATION... 4 1.1 How to
GRANTS AND CONTRIBUTIONS ONLINE SERVICES USER GUIDE: CANADA SUMMER JOBS DECEMBER 2016 TABLE OF CONTENTS IMPORTANT THINGS TO REMEMBER... 4 1. SUBMITTING A CANADA SUMMER JOBS APPLICATION... 4 1.1 How to
ELECTRONIC TAXATION IN HUNGARY. Prof. Iván Futó
 ELECTRONIC TAXATION IN HUNGARY Prof. Iván Futó Corvinus University of Budapest ifuto@informatika.uni-corvinus.hu April 2007 Eastern European egov Days 1 The electronic services of the Hungarian Tax Office
ELECTRONIC TAXATION IN HUNGARY Prof. Iván Futó Corvinus University of Budapest ifuto@informatika.uni-corvinus.hu April 2007 Eastern European egov Days 1 The electronic services of the Hungarian Tax Office
TPM v.s. Embedded Board. James Y
 TPM v.s. Embedded Board James Y What Is A Trusted Platform Module? (TPM 1.2) TPM 1.2 on the Enano-8523 that: How Safe is your INFORMATION? Protects secrets from attackers Performs cryptographic functions
TPM v.s. Embedded Board James Y What Is A Trusted Platform Module? (TPM 1.2) TPM 1.2 on the Enano-8523 that: How Safe is your INFORMATION? Protects secrets from attackers Performs cryptographic functions
Team One Mobile Banking App DETAILED ENHANCEMENTS
 Team One Mobile Banking App DETAILED ENHANCEMENTS Team One Mobile Banking App DETAILED ENHANCEMENTS Table of Contents Page Touch ID 3 QuickBalance 4 MiSnap 6 Bill Pay Enhancement 6 AnyWhereMobile Set Up
Team One Mobile Banking App DETAILED ENHANCEMENTS Team One Mobile Banking App DETAILED ENHANCEMENTS Table of Contents Page Touch ID 3 QuickBalance 4 MiSnap 6 Bill Pay Enhancement 6 AnyWhereMobile Set Up
ECA Trusted Agent Handbook
 Revision 8.0 September 4, 2015 Introduction This Trusted Agent Handbook provides instructions for individuals authorized to perform personal presence identity verification of subscribers enrolling for
Revision 8.0 September 4, 2015 Introduction This Trusted Agent Handbook provides instructions for individuals authorized to perform personal presence identity verification of subscribers enrolling for
Identity Federation: security for multiple services in a trusted environment.
 Italian Chapter of Identity Federation: security for multiple services in a trusted environment. enabling a community of interest Elio Molteni President of AIPSI info@aipsi.org Agenda Introduction to AIPSI
Italian Chapter of Identity Federation: security for multiple services in a trusted environment. enabling a community of interest Elio Molteni President of AIPSI info@aipsi.org Agenda Introduction to AIPSI
Clarification to Bidders Batch no.: 3 RFP No. 38/S/HAAD/PT/ Patient ID Authentication Clarification issue date : 17-Jan- 2015
 Q. S/R Questions & Answers 1. Q. Page 12 of the RFP requests that the service should Procure, configure and deploy related hardware and communication infrastructure at the HAAD specified data Centre, can
Q. S/R Questions & Answers 1. Q. Page 12 of the RFP requests that the service should Procure, configure and deploy related hardware and communication infrastructure at the HAAD specified data Centre, can
4.3 Case Study #09: National ehealth network in Denmark
 4.3 Case Study #09: National ehealth network in Denmark Author of case study within the estandards project: Morten Bruun-Rasmussen Project name: National ehealth network in Denmark Project
4.3 Case Study #09: National ehealth network in Denmark Author of case study within the estandards project: Morten Bruun-Rasmussen Project name: National ehealth network in Denmark Project
Charting the Progress of Smart City Development in Shanghai
 Charting the Progress of Smart City Development in Shanghai Xueguo Wen Executive Vice President of Shanghai Academy 2017 TM Forum 1 C ONTENTS Current situation Experience and outlook Strategic cooperation
Charting the Progress of Smart City Development in Shanghai Xueguo Wen Executive Vice President of Shanghai Academy 2017 TM Forum 1 C ONTENTS Current situation Experience and outlook Strategic cooperation
DIGIPASS Authentication for O2 Succendo
 DIGIPASS Authentication for O2 Succendo for IDENTIKEY Authentication Server IDENTIKEY Appliance 2009 Integration VASCO Data Security. Guideline All rights reserved. Page 1 of 30 Disclaimer Disclaimer of
DIGIPASS Authentication for O2 Succendo for IDENTIKEY Authentication Server IDENTIKEY Appliance 2009 Integration VASCO Data Security. Guideline All rights reserved. Page 1 of 30 Disclaimer Disclaimer of
ebanking User Guide ebanking echeck edelivery Mobile Banking & Deposit We Make Banking About You
 ebanking User Guide ebanking echeck edelivery Mobile Banking & Deposit Member FDIC We Make Banking About You 1-800-288-2229 www.abbybank.com 1 Account Access To log into your ebanking account, go to www.abbybank.com.
ebanking User Guide ebanking echeck edelivery Mobile Banking & Deposit Member FDIC We Make Banking About You 1-800-288-2229 www.abbybank.com 1 Account Access To log into your ebanking account, go to www.abbybank.com.
