Privatizing user credential information of Web services in a shared user environment
|
|
|
- Adrian Simpson
- 5 years ago
- Views:
Transcription
1 Selected for proceedings of NETs2012 International Conference on Internet Studies held in Bangkok, Thailand from August 17-19, 2012 Privatizing user credential information of Web services in a shared user environment Pinaki Mitra Indian Institute of Technology Guwahati pinaki@iitg.ernet.in Rinku Das Indian Institute of Technology Guwahati rinku@iitg.ernet.in Girish Sundaram Technical Solution Architect IBM India Software Labs gisundar@in.ibm.com ABSTRACT--User credentials security is one of the most important tasks in Web World. Most Web sites on the Internet that support user accounts store the users' credentials in a database. Now a days, most of the web browsers offer auto login feature for the favourite web sites such as yahoo, google, gmail etc. using these credential information. This facilitates the misuse of user credentials. Privatizing user credential information of web services in a shared user environment provides a feature enhancement where the root user will be able to privatize his stored credentials by enforcing some masking techniques such that even a user logs on to the system with root user credentials, he will not be able to access privatized data. In case of web browsers' auto login feature, a root user can disable the feature manually by deleting entries from web browsers' saved password list. But this involves spending a considerable amount of time and the biggest problem is that he has to insert those credentials once again when he next visits these websites. This application resumes auto login feature whenever root user disable the masked mode. The application includes two parts: Masked Application Mode and Disabling the Masked Application Mode. When the system goes for masked application mode, the other user will not be able to use the credentials of the root user. If the other user tries to access any of the web pages which have been masked, the other user will have to authenticate with his own credentials. Disabling the masked mode requires authentication from the root user. As long as this credential is not shared, masked mode can be disabled only by the root user. Keywords-Biometric authentication, credentials, minutiae I. INTRODUCTION Many times it becomes essential for a user to share their physical machines with multiple users for various purposes. In such cases the user needs to share his root credentials with others. Then he needs to either delete all private data and to have a back up or create an third party user profile and limiting access capability. Sometimes it may not be possible since the other party would require root credentials to perform activities like upgrading a system or updating applications etc. Also now a days many applications store user credentials at OS service level and use them to start the application automatically. Hence we need a feature to privatize user credentials. The system will have a new mode of operation called as "Masked Application Mode". The root user of the system enables this mode by executing a command at the command line. Once the command is invoked, a list of all web sites where root user's credentials are stored comes up. Root user then select the web sites which he wants to mask. Then an application masked those web sites and the currently logged user even if he is the root user will not be able to use auto login property. He has to provide his credentials explicitly. Now the root user can pass on the system control to other users. If the other user tries to access any masked web sites, he will be prompted for his credentials. The other user
2 will have to authenticate with his own credentials. If only the other user has such privileges on web sites, he will be able to access these web sites. Using the above explained idea we are able to ensure that even if the other user has the root credentials, he will not be able to misuse or access masked information. To disable the masked mode, the original root user will need to authenticate using his personal credential. Once he authenticates, the system comes back to the normal mode of operation and all web sites will start using the cached root user credentials. II. RELATED APPROACHES One approach to disable auto login to web sites is to delete saved passwords from a list of all the usernames and passwords that have been saved by the browser. This list is stored in browser toolbar. The "Saved Passwords" window (Firefox 3.00+) or "Manage saved passwords"(google chrome) or "Autocomplete" window (IE) lists the web sites and user names for stored passwords. Firefox and Google chrome includes a "Show Passwords" button that lets us view stored passwords. Select the items that to delete and click the "Remove" button (Firefox) or click the X (Google chrome) that appears on the right. In Internet Explorer, from the Tools menu, select Internet Options. On the General tab, under "Browsing history", click Delete... One of the several options is delete password. Another approach is deleting cookies. Automatic logins are made possible by storing cookies onto users' computer, so one solution would be to get rid of those cookies. But main problem with these approaches is that user needs to insert credentials once again when he next visits these websites. Now-a-days one user has multiple accounts in single website. Hence these approaches can become tedious and time consuming. III. PROPOSED APPROACH Following algorithm can be used as a high level implementing idea: 1. Root user enables "Masked Application Mode". 2. List the web sites which have stored user credentials. 3. Host user selects the web sites which he wants to "mask". 4. Store the selection list from Step 3 for future reference. 5. Prompt the user to log off and login again. 6. The system is now in masked mode. 7. Does the currently logged user try to use masked websites? If Yes then prompt for user authentication. If No then goto next step. 8. Does the currently logged user select to disable the masked mode? If Yes then prompt for currently logged user to use personalized authentication mechanism. If successful then disable "Masked Application Mode". 9. End. For example Firefox password manager uses the file signons.sqlite to store the encrypted names and passwords which is a SQLite3 database file. It also uses key3.db file to store the encryption key and that file need to match the signons file. The database key3.db contains a key used to encrypt and decrypt saved passwords. SQLite is a software library that implements a self-contained, serverless, zero configuration, transactional SQL relational database management system (RDBMS). Since signons.sqlite file is a database file, we can edit the file using standard SQL queries. The new signons.sqlite database file has two tables, moz_disabledhosts and moz_logins. The moz_disabledhosts table contains list of excluded websites which are exempted from storing passwords by user. The moz_logins table contains all the saved website passwords. It is clear that we need to use the table called moz_logins. We can use standard sql query to extract the selected rows with entire entry and save it to another database table or file for future reference (As mentioned in implementing idea steps 3 and 4). The approach will be that first we select all rows from the table moz_logins. The result will be used to populate a list of web sites which has stored user credentials. User will select the web sites which he wants to mask. This selection will be used to execute another sql query to delete selected rows
3 and saving the entries in another place. When user wants to disable the masked mode another sql query will be executed to reinsert those rows with previously saved credentials. Corresponding to each entry in table moz_logins there is an entry in key3.db file which stores encryption and decryption key for the particular entry. Deleting entries from table moz_logins does not delete entries from key3.db. Hence as long as key3.db is not being corrupted, after inserting the rows with previously saved values, password manager will be able to use those entries for auto login correctly (step 8). Again in masked mode, all the root user specific credentials cached web sites are masked from further use unless and until the root user himself disable the mode. Hence to disable this mode (step 8) root user need to provide his true identity by a fool proof mechanism. Password or personal data are not entirely fool proof. One possible option is to use biometric authentication. There are several techniques which are used for biometric authentication. Some well known techniques are: Finger print technology Face recognition technology IRIS technology Hand geometry technology Retina geometry technology Speaker recognition technique Signature verification technique There are various parameters which measure the performance of any biometric authentication techniques. Factors of evaluation are: False Accept Rate(FAR) and False Match Rate(FMR) Equal Error Rate(EER) False Reject Rate (FFR) or False Non-Match Rate (FNMR) etc. Various studies shown that no two persons have the same fingerprints, they are unique for every individual, not even those of identical twins. Fingerprints remain constant throughout life. These properties make fingerprint a very popular biometric measurement. In 1888 Sir Francis Galton first observed that fingerprints are rich in details which are in the form of discontinuities in ridges known as minutiae. The position of these minutiae doesn t change over time; hence minutiae matching are a good way to authenticate fingerprints. A fingerprint recognition system consists of a fingerprint capturing device, and fingerprint matching SDK (to extract minutiae and to match minutiae). The basic idea is: 1. One or more fingerprint image is captured on the device (e.g., a personal computer system with integrated scanner). 2. This image is converted into minutiae data. Quality of these minutiae is checked to make sure that these minutiae is usable and then a template of this is stored in the Database. 3. When a user wants to log in, he must scan his finger again. It is converted again into minutiae and a second template is generated. Next, an analysis is performed by feature matching with already stored fingerprint in DB to determine if there is a match. This returns a matching score which is used to decide whether to consider this as same identity by using some threshold. The two most important minutiae which are used to determine the match are termination and bifurcation. Termination is the immediate ending of the ridge and Bifurcation is the point on the ridge from where it is divided into two ridges. IV. RESULTS AND DISCUSSIONS TABLE I. SYSTEM CONFIGURATION Components Specification Hard Disk 160 GB (Secondary storage) RAM (Primary 2 GB memory) Processor Intel Core 2 Duo Processor Speed 2.00 GHz
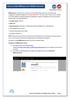
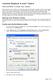
4 Operating System Ubuntu Compiler Gnu Compiler Collection(gcc), javac, ECJ(Eclipse Compiler for Java) A. DATABASE ACCESS To access the SQLite Database, we have used SQLite C/C++ database programming API. The interface to the SQLite library consists of three core functions, one opaque data structure, and some constants used as return values. The core interface is as follows: typedef struct sqlite sqlite ; #define SQLITE OK 0 /*Successful result */ sqlite *sqlite_open( const char *dbname, int mode, char **errmsg ) ; void sqlite_close (sqlite *db ) ; int sqlite_exec (sqlite *db, char *sql, int (*xcal lback ) ( void *, int, char **, char **), void *parg, char **errmsg ) ; The callback function is used to receive the results of a query. The sqlite_exec function is query execution interface. B. RESULTS The result of the execution of a select query is a file which contains list of URLs for which password manager stored usernames and passwords. This is used to generate a UI to select URLs to disable auto login. Figure 1. UI to select URLs to disable auto login. To delete a row we simply use standard sql query for deleting. Where clause consists the hostname selected to be disabled for auto login. It will delete the corresponding row in moz_logins table. Now it will disable the auto login method. It will also save the entry in another file for future reference. Next, system will prompt for log off and log on again Figure 2. Prompt for login off Now if any user tries to use any masked websites, it will ask for his own credentials.
5 signons.sqlite. These queries are embedded in a C program using C SQLite programming API. Approach for biometric authentication is fingerprint matching using fingerprint scanner and fingerprint SDK. However, biometrics has also some privacy and security related problems. Main problem with biometrics is that if it is compromised there is no way to invert it. One possible approach to secure biometric authentication is use of robust hash function. The robust hash function is a one-way transformation. REFERENCES Figure 3. Prompt for user authentication for masked application If currently logged user tries to disable the masking mode, it will ask for authentication first. As discussed earlier, the proposed method is fingerprint authentication. The Fingerprint SDK (by griaulebiometrics.com) is fingerprint recognition Software Development Kit (SDK) that allows integrating biometrics in an application. The fingerprint SDK for Java allows developing cross platform Java programs that can run even in Gnu/Linux. It can be used to develop the application which will check for authorization. The application will authorize the user to disable "Masked Application Mode" only if it is successful, otherwise it will prevent from do so. Disabling is done by executing a query to insert that entry again in the table moz_logins using standard sql insert command with field values previously saved for corresponding hostname, it will add a row in the table moz_logins. Encryption and decryption keys are already present in key3.db file. We are not modifying this file and deletion from signons.sqlite does not delete corresponding encryption and decryption keys from this file. Hence when root user again visits that particular website he will be able to do auto login again. [1] [2] Manager [3] word-management-concerns-ie-and-firefox [4] folder. [5] Biometric Authentication-Security And Usability by Vaclav Matyas and Zdenek [6] Biometric Authentication: A Review by Debnath Bhattacharyya, Rahul Ranjan, Farkhod Alisherov A., and Minkyu Choi [7] Biometrics: A Tool for Information Security by Jain A. K., Ross A. & Pankanti S. [8] SQLite Embedded Database tutorial(online) [9] The C language interface to SQLite; interface.html [10] One-Step Query Execution Interface; [11] A Secure Biometric Authentication Scheme Based on Robust Hashing by Yagiz Sutcu, Husrev Taha Sencar & Nasir Memon [12] Fingerprint Identification By Kuntal Barua, Samayita Bhattacharya & Dr. Kalyani Mali [13] Automatic Fingerprint Recognition: Minutiae based by Ispreet Singh Virk & Raman Maini. V. CONCLUSION In this approach sql queries are used to extract the information from the SQLite database file
MAIL PLUGIN FOR IBM MASHUP CENTER
 International Journal of Electronic Commerce Studies Vol.1, No.2, pp.139-148, 2010 MAIL PLUGIN FOR IBM MASHUP CENTER Pinaki Mitra, Indian Institute of Technology, Guwahati, India pinaki@iitg.ernet.in Girish
International Journal of Electronic Commerce Studies Vol.1, No.2, pp.139-148, 2010 MAIL PLUGIN FOR IBM MASHUP CENTER Pinaki Mitra, Indian Institute of Technology, Guwahati, India pinaki@iitg.ernet.in Girish
Biometric Security Roles & Resources
 Biometric Security Roles & Resources Part 1 Biometric Systems Skip Linehan Biometrics Systems Architect, Raytheon Intelligence and Information Systems Outline Biometrics Overview Biometric Architectures
Biometric Security Roles & Resources Part 1 Biometric Systems Skip Linehan Biometrics Systems Architect, Raytheon Intelligence and Information Systems Outline Biometrics Overview Biometric Architectures
Application Behavior Enforcement Based On Network Characteristics
 Selected for proceedings of NETs2012 International Conference on Internet Studies held in Bangkok, Thailand from August 17-19, 2012 Application Behavior Enforcement Based On Network Characteristics Pinaki
Selected for proceedings of NETs2012 International Conference on Internet Studies held in Bangkok, Thailand from August 17-19, 2012 Application Behavior Enforcement Based On Network Characteristics Pinaki
CSCE 548 Building Secure Software Biometrics (Something You Are) Professor Lisa Luo Spring 2018
 CSCE 548 Building Secure Software Biometrics (Something You Are) Professor Lisa Luo Spring 2018 Previous Class Credentials Something you know (Knowledge factors) Something you have (Possession factors)
CSCE 548 Building Secure Software Biometrics (Something You Are) Professor Lisa Luo Spring 2018 Previous Class Credentials Something you know (Knowledge factors) Something you have (Possession factors)
CIS 4360 Secure Computer Systems Biometrics (Something You Are)
 CIS 4360 Secure Computer Systems Biometrics (Something You Are) Professor Qiang Zeng Spring 2017 Previous Class Credentials Something you know (Knowledge factors) Something you have (Possession factors)
CIS 4360 Secure Computer Systems Biometrics (Something You Are) Professor Qiang Zeng Spring 2017 Previous Class Credentials Something you know (Knowledge factors) Something you have (Possession factors)
Finger Print Enhancement Using Minutiae Based Algorithm
 Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 8, August 2014,
Available Online at www.ijcsmc.com International Journal of Computer Science and Mobile Computing A Monthly Journal of Computer Science and Information Technology IJCSMC, Vol. 3, Issue. 8, August 2014,
Perceptive Experience Web Scan
 Perceptive Experience Web Scan Technical Specifications Version: 2.2.x Written by: Product Knowledge, R&D Date: Wednesday, April 05, 2017 2017 Lexmark. All rights reserved. Lexmark is a trademark of Lexmark
Perceptive Experience Web Scan Technical Specifications Version: 2.2.x Written by: Product Knowledge, R&D Date: Wednesday, April 05, 2017 2017 Lexmark. All rights reserved. Lexmark is a trademark of Lexmark
An Introduction to Google Chrome
 An Introduction to Google Chrome Box is an online file sharing and cloud content management service and it provides features such as: Getting Google Chrome 1. To get started with Google Chrome, you have
An Introduction to Google Chrome Box is an online file sharing and cloud content management service and it provides features such as: Getting Google Chrome 1. To get started with Google Chrome, you have
MYOB Advanced Business
 MYOB Advanced Business On-Premise Installation Last Updated: 24 November 2014 Contents Introduction 1 Pre-Requisites 1 Web Browsers... 1 Server Hardware and Software... 1 Database Hardware and Software...
MYOB Advanced Business On-Premise Installation Last Updated: 24 November 2014 Contents Introduction 1 Pre-Requisites 1 Web Browsers... 1 Server Hardware and Software... 1 Database Hardware and Software...
EveryonePrint. Mobile Gateway 4.2. Installation Guide. EveryonePrint Mobile Gateway Installation Guide Page 1 of 30
 EveryonePrint Mobile Gateway 4.2 Installation Guide EveryonePrint Mobile Gateway Installation Guide 2016.09.01 Page 1 of 30 1. Introduction... 3 1.1 Multiple networks (using Multicast Bonjour AirPrint)...
EveryonePrint Mobile Gateway 4.2 Installation Guide EveryonePrint Mobile Gateway Installation Guide 2016.09.01 Page 1 of 30 1. Introduction... 3 1.1 Multiple networks (using Multicast Bonjour AirPrint)...
WA2056 Building HTML5 Based Mobile Web Sites. Classroom Setup Guide. Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1
 WA2056 Building HTML5 Based Mobile Web Sites Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum
WA2056 Building HTML5 Based Mobile Web Sites Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE. 31 January 2017
 BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
Getting Started With the Cisco PAM Desktop Software
 CHAPTER 3 Getting Started With the Cisco PAM Desktop Software This chapter describes how to install the Cisco PAM desktop client software, log on to Cisco PAM, and begin configuring access control features
CHAPTER 3 Getting Started With the Cisco PAM Desktop Software This chapter describes how to install the Cisco PAM desktop client software, log on to Cisco PAM, and begin configuring access control features
Luther Consulting, LLC August 2015 All rights reserved. Enabling Pop-ups in EvaluationWeb
 Luther Consulting, LLC August 2015 All rights reserved. Enabling Pop-ups in EvaluationWeb Contents Enabling Pop-ups in EvaluationWeb... 3 Internet Explorer (Version 9 or later):... 4 Firefox Windows...
Luther Consulting, LLC August 2015 All rights reserved. Enabling Pop-ups in EvaluationWeb Contents Enabling Pop-ups in EvaluationWeb... 3 Internet Explorer (Version 9 or later):... 4 Firefox Windows...
Reducing FMR of Fingerprint Verification by Using the Partial Band of Similarity
 Reducing FMR of Fingerprint Verification by Using the Partial Band of Similarity Seung-Hoon Chae 1,Chang-Ho Seo 2, Yongwha Chung 3, and Sung Bum Pan 4,* 1 Dept. of Information and Communication Engineering,
Reducing FMR of Fingerprint Verification by Using the Partial Band of Similarity Seung-Hoon Chae 1,Chang-Ho Seo 2, Yongwha Chung 3, and Sung Bum Pan 4,* 1 Dept. of Information and Communication Engineering,
Recommended Browser Settings
 Recommended Browser Settings Internet Explorer Settings (PC) Mozilla Firefox Settings (PC) Mozilla Firefox Settings (Mac) Safari Settings (Mac) Chrome Settings (PC) Infinite Campus recommends modifying
Recommended Browser Settings Internet Explorer Settings (PC) Mozilla Firefox Settings (PC) Mozilla Firefox Settings (Mac) Safari Settings (Mac) Chrome Settings (PC) Infinite Campus recommends modifying
Browser Cookie Settings
 Browser Cookie Settings Error Messages: Browser's cookie functionality turned off Steps to Try 1. Try enabling cookies, close all browser windows and restart browser after enabling cookies 2. Try clearing
Browser Cookie Settings Error Messages: Browser's cookie functionality turned off Steps to Try 1. Try enabling cookies, close all browser windows and restart browser after enabling cookies 2. Try clearing
Contents Getting Started... 3 About Scribe Online and Connectors... 3 Scribe Online Services... 3 CDK Components... 3 Audience... 4 Prerequisites...
 Contents Getting Started... 3 About Scribe Online and Connectors... 3 Scribe Online Services... 3 CDK Components... 3 Audience... 4 Prerequisites... 4 Requirements... 4 CDK Workflow... 5 Scribe Online
Contents Getting Started... 3 About Scribe Online and Connectors... 3 Scribe Online Services... 3 CDK Components... 3 Audience... 4 Prerequisites... 4 Requirements... 4 CDK Workflow... 5 Scribe Online
docalpha Installation Guide
 ARTSYL DOCALPHA INSTALLATION GUIDE 1. docalpha Architecture Overview... 2 1.1. docalpha Server Components... 4 1.2. docalpha Production Environment Stations Overview... 4 1.3. docalpha Setup & Administration
ARTSYL DOCALPHA INSTALLATION GUIDE 1. docalpha Architecture Overview... 2 1.1. docalpha Server Components... 4 1.2. docalpha Production Environment Stations Overview... 4 1.3. docalpha Setup & Administration
Congratulations! You just ordered IdentaMaster software package featuring Biometric login, File/Folder Encryption and Entire Drive Encryption.
 INSTALLATION Congratulations! You just ordered IdentaMaster software package featuring Biometric login, File/Folder Encryption and Entire Drive Encryption. From this point on, you may install any additional
INSTALLATION Congratulations! You just ordered IdentaMaster software package featuring Biometric login, File/Folder Encryption and Entire Drive Encryption. From this point on, you may install any additional
Windows Authentication for Velocity Web service Client
 Windows Authentication for Velocity Web service Client Copyright 2019, Identiv. Overview Prior to Velocity 3.7 SP1 releases, the Velocity Web Service Client (VWSC) application used Anonymous Authentication
Windows Authentication for Velocity Web service Client Copyright 2019, Identiv. Overview Prior to Velocity 3.7 SP1 releases, the Velocity Web Service Client (VWSC) application used Anonymous Authentication
Getting Started Guide. This document provides step-by-step instructions for installing Max Secure Anti-Virus and its prerequisite software.
 Getting Started Guide This document provides step-by-step instructions for installing Max Secure Anti-Virus and its prerequisite software. Contents 2 Contents Introduction... 3 System Requirements... 4
Getting Started Guide This document provides step-by-step instructions for installing Max Secure Anti-Virus and its prerequisite software. Contents 2 Contents Introduction... 3 System Requirements... 4
WA2185 Platform Independent Mobile Development with jquery Mobile and Apache Cordova. Classroom Setup Guide. Web Age Solutions Inc.
 WA2185 Platform Independent Mobile Development with jquery Mobile and Apache Cordova Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware
WA2185 Platform Independent Mobile Development with jquery Mobile and Apache Cordova Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware
Controlsoft Identity and Access Management Software Controlsoft Identity Access Client Software
 Controlsoft Identity Access Client Software IA Client Software Installation Guide v8.0.229 2018 Controlsoft Ltd 9010-0046 Issue 8 Page 1 of 24 29/10/2018 Contents 1. Introduction... 2 1.1. PC Specifications...
Controlsoft Identity Access Client Software IA Client Software Installation Guide v8.0.229 2018 Controlsoft Ltd 9010-0046 Issue 8 Page 1 of 24 29/10/2018 Contents 1. Introduction... 2 1.1. PC Specifications...
Smart Card and Biometrics Used for Secured Personal Identification System Development
 Smart Card and Biometrics Used for Secured Personal Identification System Development Mădălin Ştefan Vlad, Razvan Tatoiu, Valentin Sgârciu Faculty of Automatic Control and Computers, University Politehnica
Smart Card and Biometrics Used for Secured Personal Identification System Development Mădălin Ştefan Vlad, Razvan Tatoiu, Valentin Sgârciu Faculty of Automatic Control and Computers, University Politehnica
Integrating IBM Security Privileged Identity Manager with ObserveIT Enterprise Session Recording
 Integrating IBM Security Privileged Identity Manager with ObserveIT Enterprise Session Recording Contents 1 About This Document... 2 2 Overview... 2 3 Before You Begin... 2 4 Deploying ObserveIT with IBM
Integrating IBM Security Privileged Identity Manager with ObserveIT Enterprise Session Recording Contents 1 About This Document... 2 2 Overview... 2 3 Before You Begin... 2 4 Deploying ObserveIT with IBM
D. Jagadeesan Assistant Professor, Dept. of Computer Science and Engineering, Adhiparasakthi College of Engineering, Kalavai,
 Volume 4, Issue 9, September 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Two Step Verification
Volume 4, Issue 9, September 2014 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com Two Step Verification
Login Troubleshooting
 Login Troubleshooting Scenario #1: I cannot log into my account and I am pretty sure I am using the correct credentials. Problem Solving Steps: 1. All MinuteClinic employees will use the username MC followed
Login Troubleshooting Scenario #1: I cannot log into my account and I am pretty sure I am using the correct credentials. Problem Solving Steps: 1. All MinuteClinic employees will use the username MC followed
Client Installation Guide
 GENView Provisioning and Portals Portal Server Client Installation Guide Release: 9.4 Document revision: 03.01 Describes the steps for installing the GVPP-PS client application. www.genband.com 630-01903-01
GENView Provisioning and Portals Portal Server Client Installation Guide Release: 9.4 Document revision: 03.01 Describes the steps for installing the GVPP-PS client application. www.genband.com 630-01903-01
Offline Photo & Biometric Capturing (Village level) Introduction to the Operations of Offline Photo and Fingerprint capture program
 Offline Photo & Biometric Capturing (Village level) Introduction to the Operations of Offline Photo and Fingerprint capture program Pre Operational Requirements Download the Blank Database form http://ipds.gujarat.gov.in/offlinepfp/grcc_blank.rar
Offline Photo & Biometric Capturing (Village level) Introduction to the Operations of Offline Photo and Fingerprint capture program Pre Operational Requirements Download the Blank Database form http://ipds.gujarat.gov.in/offlinepfp/grcc_blank.rar
SpaceShuttle User guide v3
 SpaceShuttle User guide v3 1.Get Started with SpaceShuttle p2 1.1 For Windows p2 How to download and install Aspera Connect p2 1.2 For Mac p4 How to download and install Aspera Connect p4 2. Accessing
SpaceShuttle User guide v3 1.Get Started with SpaceShuttle p2 1.1 For Windows p2 How to download and install Aspera Connect p2 1.2 For Mac p4 How to download and install Aspera Connect p4 2. Accessing
BIOMETRIC IDENTIFICATION OF PERSONS A SOLUTION FOR TIME & ATTENDANCE PROBLEMS
 BIOMETRIC IDENTIFICATION OF PERSONS A SOLUTION FOR TIME & ATTENDANCE PROBLEMS Emil PRICOP Petroleum-Gas University of Ploiesti, emil.pricop@gmail.com Keywords: fingerprint, RFID, access control, biometric,
BIOMETRIC IDENTIFICATION OF PERSONS A SOLUTION FOR TIME & ATTENDANCE PROBLEMS Emil PRICOP Petroleum-Gas University of Ploiesti, emil.pricop@gmail.com Keywords: fingerprint, RFID, access control, biometric,
WA1973 IBM Business Process Manager 8.0 Programming Using IBM Integration Designer. Classroom Setup Guide. Web Age Solutions Inc.
 WA1973 IBM Business Process Manager 8.0 Programming Using IBM Integration Designer Classroom Setup Guide Web Age Solutions Inc. Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware...3
WA1973 IBM Business Process Manager 8.0 Programming Using IBM Integration Designer Classroom Setup Guide Web Age Solutions Inc. Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware...3
Login Troubleshooting
 Login Troubleshooting Scenario #1: I cannot log into my account and I am pretty sure I am using the correct credentials. Problem Solving Steps: 1. Check with your scheduler to ensure you are using the
Login Troubleshooting Scenario #1: I cannot log into my account and I am pretty sure I am using the correct credentials. Problem Solving Steps: 1. Check with your scheduler to ensure you are using the
AccessData FTK Quick Installation Guide
 AccessData FTK Quick Installation Guide Document date: May 20, 2014 2014 AccessData Group, Inc. All rights reserved. No part of this publication may be reproduced, photocopied, stored on a retrieval system,
AccessData FTK Quick Installation Guide Document date: May 20, 2014 2014 AccessData Group, Inc. All rights reserved. No part of this publication may be reproduced, photocopied, stored on a retrieval system,
Recommended Browser Settings
 Recommended Browser Settings August 2015 This document is intended for restricted use only. Infinite Campus asserts that this document contains proprietary information that would give our competitors undue
Recommended Browser Settings August 2015 This document is intended for restricted use only. Infinite Campus asserts that this document contains proprietary information that would give our competitors undue
Content Encryption Application (Windows)
 Content Encryption Application (Windows) Download & Install RioCrypt for Windows Download Link: https://www.instamojo.com/recordshield/riocrypt2 System Requirements: Windows 7, 8, 8.1, 10. DirectX 9.0c
Content Encryption Application (Windows) Download & Install RioCrypt for Windows Download Link: https://www.instamojo.com/recordshield/riocrypt2 System Requirements: Windows 7, 8, 8.1, 10. DirectX 9.0c
BIOMETRIC MECHANISM FOR ONLINE TRANSACTION ON ANDROID SYSTEM ENHANCED SECURITY OF. Anshita Agrawal
 BIOMETRIC MECHANISM FOR ENHANCED SECURITY OF ONLINE TRANSACTION ON ANDROID SYSTEM 1 Anshita Agrawal CONTENTS Introduction Biometric Authentication Fingerprints Proposed System Conclusion References 2 INTRODUCTION
BIOMETRIC MECHANISM FOR ENHANCED SECURITY OF ONLINE TRANSACTION ON ANDROID SYSTEM 1 Anshita Agrawal CONTENTS Introduction Biometric Authentication Fingerprints Proposed System Conclusion References 2 INTRODUCTION
Perceptive Matching Engine
 Perceptive Matching Engine Advanced Design and Setup Guide Version: 1.0.x Written by: Product Development, R&D Date: January 2018 2018 Hyland Software, Inc. and its affiliates. Table of Contents Overview...
Perceptive Matching Engine Advanced Design and Setup Guide Version: 1.0.x Written by: Product Development, R&D Date: January 2018 2018 Hyland Software, Inc. and its affiliates. Table of Contents Overview...
Tivoli Common Reporting V Cognos report in a Tivoli Integrated Portal dashboard
 Tivoli Common Reporting V2.1.1 Cognos report in a Tivoli Integrated Portal dashboard Preethi C Mohan IBM India Ltd. India Software Labs, Bangalore +91 80 40255077 preethi.mohan@in.ibm.com Copyright IBM
Tivoli Common Reporting V2.1.1 Cognos report in a Tivoli Integrated Portal dashboard Preethi C Mohan IBM India Ltd. India Software Labs, Bangalore +91 80 40255077 preethi.mohan@in.ibm.com Copyright IBM
The Rockefeller University I NFORMATION T ECHNOLOGY E DUCATION & T RAINING. VPN Web Portal Usage Guide
 The Rockefeller University I NFORMATION T ECHNOLOGY E DUCATION & T RAINING VPN Web Portal Usage Guide Table of Contents WHAT IS VPN WEB CLIENT 4 SUPPORTED WEB BROWSERS 4 LOGGING INTO VPN WEB CLIENT 5 ESTABLISHING
The Rockefeller University I NFORMATION T ECHNOLOGY E DUCATION & T RAINING VPN Web Portal Usage Guide Table of Contents WHAT IS VPN WEB CLIENT 4 SUPPORTED WEB BROWSERS 4 LOGGING INTO VPN WEB CLIENT 5 ESTABLISHING
Perceptive Nolij Web. Technical Specifications. Version: 6.8.x
 Perceptive Nolij Web Technical Specifications Version: 6.8.x Written by: Product Knowledge, R&D Date: October 2018 Copyright 2014-2018 Hyland Software, Inc. and its affiliates. Table of Contents Introduction...
Perceptive Nolij Web Technical Specifications Version: 6.8.x Written by: Product Knowledge, R&D Date: October 2018 Copyright 2014-2018 Hyland Software, Inc. and its affiliates. Table of Contents Introduction...
Senstar Symphony. 7.2 Installation Guide
 Senstar Symphony 7.2 Installation Guide Contents Contents Introduction... 3 Symphony Server...3 Symphony Client... 3 Xnet... 3... 4 Symphony Server requirements...4 Symphony Client requirements...4 Symphony
Senstar Symphony 7.2 Installation Guide Contents Contents Introduction... 3 Symphony Server...3 Symphony Client... 3 Xnet... 3... 4 Symphony Server requirements...4 Symphony Client requirements...4 Symphony
Modern Requirements4TFS 2018 Update 1 Release Notes
 Modern Requirements4TFS 2018 Update 1 Release Notes Modern Requirements 6/22/2018 Table of Contents 1. INTRODUCTION... 3 2. SYSTEM REQUIREMENTS... 3 3. APPLICATION SETUP... 3 GENERAL... 4 1. FEATURES...
Modern Requirements4TFS 2018 Update 1 Release Notes Modern Requirements 6/22/2018 Table of Contents 1. INTRODUCTION... 3 2. SYSTEM REQUIREMENTS... 3 3. APPLICATION SETUP... 3 GENERAL... 4 1. FEATURES...
Configuring Vulnerability Assessment Devices
 CHAPTER 10 Revised: November 10, 2007 Vulnerability assessment (VA) devices provide MARS with valuable information about many of the possible targets of attacks and threats. They provide information useful
CHAPTER 10 Revised: November 10, 2007 Vulnerability assessment (VA) devices provide MARS with valuable information about many of the possible targets of attacks and threats. They provide information useful
International Journal of Emerging Technology & Research
 International Journal of Emerging Technology & Research Volume 1, Issue 5, July-Aug, 2014 (www.ijetr.org) ISSN (E): 2347-5900 ISSN (P): 2347-6079 Biometric Based Attendance Management System Using Wi-Fi
International Journal of Emerging Technology & Research Volume 1, Issue 5, July-Aug, 2014 (www.ijetr.org) ISSN (E): 2347-5900 ISSN (P): 2347-6079 Biometric Based Attendance Management System Using Wi-Fi
BIOMETRIC TECHNOLOGY: A REVIEW
 International Journal of Computer Science and Communication Vol. 2, No. 2, July-December 2011, pp. 287-291 BIOMETRIC TECHNOLOGY: A REVIEW Mohmad Kashif Qureshi Research Scholar, Department of Computer
International Journal of Computer Science and Communication Vol. 2, No. 2, July-December 2011, pp. 287-291 BIOMETRIC TECHNOLOGY: A REVIEW Mohmad Kashif Qureshi Research Scholar, Department of Computer
Zodiac Max OPERATOR GUIDE
 Zodiac Max OPERATOR GUIDE February 2015 Table of Contents INTRODUCTION... 5 PC Requirements... 6 USB Driver Installation... 7 ZODIAC SINGLE-STATION SOFTWARE... 8 Software Installation... 8 Communications
Zodiac Max OPERATOR GUIDE February 2015 Table of Contents INTRODUCTION... 5 PC Requirements... 6 USB Driver Installation... 7 ZODIAC SINGLE-STATION SOFTWARE... 8 Software Installation... 8 Communications
Table of Contents. Troubleshooting Guide for Home Users
 Table of Contents Introduction... 1 Chapter 1: System Requirements... 2 Recommended and Minimum Supported Requirements... 2 Additional Information... 3 Internet Connectivity... 3 Tablet Compatibility...
Table of Contents Introduction... 1 Chapter 1: System Requirements... 2 Recommended and Minimum Supported Requirements... 2 Additional Information... 3 Internet Connectivity... 3 Tablet Compatibility...
Using SQL Developer. Oracle University and Egabi Solutions use only
 Using SQL Developer Objectives After completing this appendix, you should be able to do the following: List the key features of Oracle SQL Developer Identify menu items of Oracle SQL Developer Create a
Using SQL Developer Objectives After completing this appendix, you should be able to do the following: List the key features of Oracle SQL Developer Identify menu items of Oracle SQL Developer Create a
Keywords: Fingerprint, Minutia, Thinning, Edge Detection, Ridge, Bifurcation. Classification: GJCST Classification: I.5.4, I.4.6
 Global Journal of Computer Science & Technology Volume 11 Issue 6 Version 1.0 April 2011 Type: Double Blind Peer Reviewed International Research Journal Publisher: Global Journals Inc. (USA) Online ISSN:
Global Journal of Computer Science & Technology Volume 11 Issue 6 Version 1.0 April 2011 Type: Double Blind Peer Reviewed International Research Journal Publisher: Global Journals Inc. (USA) Online ISSN:
Accessing the Curriculum Management System Off-campus Process for obtaining and installing a CMS certificate on a home Mac
 INFORMATION SERVICES ICT Service Delivery Accessing the Curriculum Management System Off-campus Process for obtaining and installing a CMS certificate on a home Mac Introduction This service enables staff
INFORMATION SERVICES ICT Service Delivery Accessing the Curriculum Management System Off-campus Process for obtaining and installing a CMS certificate on a home Mac Introduction This service enables staff
Modern Requirements4TFS 2018 Update 3 Release Notes
 Modern Requirements4TFS 2018 Update 3 Release Notes Modern Requirements 12/14/2018 Table of Contents 1. INTRODUCTION... 3 2. SYSTEM REQUIREMENTS... 3 3. APPLICATION SETUP... 4 GENERAL... 5 1. FEATURES...
Modern Requirements4TFS 2018 Update 3 Release Notes Modern Requirements 12/14/2018 Table of Contents 1. INTRODUCTION... 3 2. SYSTEM REQUIREMENTS... 3 3. APPLICATION SETUP... 4 GENERAL... 5 1. FEATURES...
SelfService Portal. Step By Step Documentation. This document will show you how to enroll your user account to the SelfService Portal
 SelfService Portal Step By Step Documentation This document will show you how to enroll your user account to the SelfService Portal There are three types of Authentication 1. Security Questions 2. Verification
SelfService Portal Step By Step Documentation This document will show you how to enroll your user account to the SelfService Portal There are three types of Authentication 1. Security Questions 2. Verification
Perceptive Nolij Web. Administrator Guide. Version: 6.8.x
 Perceptive Nolij Web Administrator Guide Version: 6.8.x Written by: Product Knowledge, R&D Date: June 2018 Copyright 2014-2018 Hyland Software, Inc. and its affiliates.. Table of Contents Introduction...
Perceptive Nolij Web Administrator Guide Version: 6.8.x Written by: Product Knowledge, R&D Date: June 2018 Copyright 2014-2018 Hyland Software, Inc. and its affiliates.. Table of Contents Introduction...
TIBCO LiveView Web Getting Started Guide
 TIBCO LiveView Web Getting Started Guide Contents Introduction... 1 Prerequisites... 1 Installation... 2 Installation Overview... 2 Downloading and Installing for Windows... 3 Downloading and Installing
TIBCO LiveView Web Getting Started Guide Contents Introduction... 1 Prerequisites... 1 Installation... 2 Installation Overview... 2 Downloading and Installing for Windows... 3 Downloading and Installing
How to install HDRestaurant CS(Client Server)?
 How to install HDRestaurant CS(Client Server)? HDRestaurant is a feature-rich, easy to use Point of Sale billing, inventory, and accounting management software available for a 30 days FREE TRIAL.The client
How to install HDRestaurant CS(Client Server)? HDRestaurant is a feature-rich, easy to use Point of Sale billing, inventory, and accounting management software available for a 30 days FREE TRIAL.The client
Cloud Help for Community Managers...3. Release Notes System Requirements Administering Jive for Office... 6
 for Office Contents 2 Contents Cloud Help for Community Managers...3 Release Notes... 4 System Requirements... 5 Administering Jive for Office... 6 Getting Set Up...6 Installing the Extended API JAR File...6
for Office Contents 2 Contents Cloud Help for Community Managers...3 Release Notes... 4 System Requirements... 5 Administering Jive for Office... 6 Getting Set Up...6 Installing the Extended API JAR File...6
Published by: PIONEER RESEARCH & DEVELOPMENT GROUP (www.prdg.org) 1
 Enhancing Security in Identity Documents Using QR Code RevathiM K 1, Annapandi P 2 and Ramya K P 3 1 Information Technology, Dr.Sivanthi Aditanar College of Engineering, Tiruchendur, Tamilnadu628215, India
Enhancing Security in Identity Documents Using QR Code RevathiM K 1, Annapandi P 2 and Ramya K P 3 1 Information Technology, Dr.Sivanthi Aditanar College of Engineering, Tiruchendur, Tamilnadu628215, India
Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS)
 Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
Mobile Login Extension User Manual
 Extension User Manual Magento provides secured and convenient login to Magento stores through mobile number along with OTP. Table of Content 1. Extension Installation Guide 2. API Configuration 3. General
Extension User Manual Magento provides secured and convenient login to Magento stores through mobile number along with OTP. Table of Content 1. Extension Installation Guide 2. API Configuration 3. General
A Novel Data Encryption Technique by Genetic Crossover of Robust Finger Print Based Key and Handwritten Signature Key
 www.ijcsi.org 209 A Novel Data Encryption Technique by Genetic Crossover of Robust Finger Print Based Key and Handwritten Signature Key Tanmay Bhattacharya 1, Sirshendu Hore 2 and S. R. Bhadra Chaudhuri
www.ijcsi.org 209 A Novel Data Encryption Technique by Genetic Crossover of Robust Finger Print Based Key and Handwritten Signature Key Tanmay Bhattacharya 1, Sirshendu Hore 2 and S. R. Bhadra Chaudhuri
Minutiae vs. Correlation: Analysis of Fingerprint Recognition Methods in Biometric Security System
 Minutiae vs. Correlation: Analysis of Fingerprint Recognition Methods in Biometric Security System Bharti Nagpal, Manoj Kumar, Priyank Pandey, Sonakshi Vij, Vaishali Abstract Identification and verification
Minutiae vs. Correlation: Analysis of Fingerprint Recognition Methods in Biometric Security System Bharti Nagpal, Manoj Kumar, Priyank Pandey, Sonakshi Vij, Vaishali Abstract Identification and verification
BIOMET: A Multimodal Biometric Authentication System for Person Identification and Verification using Fingerprint and Face Recognition
 BIOMET: A Multimodal Biometric Authentication System for Person Identification and Verification using Fingerprint and Face Recognition Hiren D. Joshi Phd, Dept. of Computer Science Rollwala Computer Centre
BIOMET: A Multimodal Biometric Authentication System for Person Identification and Verification using Fingerprint and Face Recognition Hiren D. Joshi Phd, Dept. of Computer Science Rollwala Computer Centre
Chapter 3: User Authentication
 Chapter 3: User Authentication Comp Sci 3600 Security Outline 1 2 3 4 Outline 1 2 3 4 User Authentication NIST SP 800-63-3 (Digital Authentication Guideline, October 2016) defines user as: The process
Chapter 3: User Authentication Comp Sci 3600 Security Outline 1 2 3 4 Outline 1 2 3 4 User Authentication NIST SP 800-63-3 (Digital Authentication Guideline, October 2016) defines user as: The process
Iowa IDEA Supported Browsers and Settings Updated 2/9/2009
 Iowa IDEA Supported Browsers and Settings Updated 2/9/2009 The Iowa IDEA applications are supported on the following platforms and browsers: Macintosh OS 10.4 with Firefox Versions 3.0 and newer Windows
Iowa IDEA Supported Browsers and Settings Updated 2/9/2009 The Iowa IDEA applications are supported on the following platforms and browsers: Macintosh OS 10.4 with Firefox Versions 3.0 and newer Windows
OPC UA Configuration Manager PTC Inc. All Rights Reserved.
 2017 PTC Inc. All Rights Reserved. 2 Table of Contents 1 Table of Contents 2 4 Overview 4 5 Project Properties - OPC UA 5 Server Endpoints 7 Trusted Clients 9 Discovery Servers 10 Trusted Servers 11 Instance
2017 PTC Inc. All Rights Reserved. 2 Table of Contents 1 Table of Contents 2 4 Overview 4 5 Project Properties - OPC UA 5 Server Endpoints 7 Trusted Clients 9 Discovery Servers 10 Trusted Servers 11 Instance
Internet Explorer 6 and 7 Users
 Internet Explorer 6 and 7 Users How and Why to Clear Your Cache Often referred to as the cache, the Temporary Internet Files folder contains a kind of travel record of the items you have seen, heard, or
Internet Explorer 6 and 7 Users How and Why to Clear Your Cache Often referred to as the cache, the Temporary Internet Files folder contains a kind of travel record of the items you have seen, heard, or
Introduction Secure Message Center (Webmail, Mobile & Visually Impaired) Webmail... 2 Mobile & Tablet... 4 Visually Impaired...
 WEB MESSAGE CENTER END USER GUIDE The Secure Web Message Center allows users to access and send and receive secure messages via any browser on a computer, tablet or other mobile devices. Introduction...
WEB MESSAGE CENTER END USER GUIDE The Secure Web Message Center allows users to access and send and receive secure messages via any browser on a computer, tablet or other mobile devices. Introduction...
MorphoManager User Manual. Table of Contents
 User Manual Table of Contents Introduction... 4 Support... 4 Overview... 5 What is a client?... 5 What is a server?... 5 What is a fingerprint enrollment device?... 5 What is a MorphoAccess?... 6 What
User Manual Table of Contents Introduction... 4 Support... 4 Overview... 5 What is a client?... 5 What is a server?... 5 What is a fingerprint enrollment device?... 5 What is a MorphoAccess?... 6 What
Perceptive Matching Engine
 Perceptive Matching Engine Installation and Setup Guide Version: 1.0.x Written by: Product Development, R&D Date: March 2018 2018 Hyland Software, Inc. and its affiliates. Table of Contents Overview...
Perceptive Matching Engine Installation and Setup Guide Version: 1.0.x Written by: Product Development, R&D Date: March 2018 2018 Hyland Software, Inc. and its affiliates. Table of Contents Overview...
QUICK SET-UP VERIFICATION...3
 TABLE OF CONTENTS 1 QUICK SET-UP VERIFICATION...3 2 INSTALLING CERTIFICATES...3 3 IF YOU USE MS INTERNET EXPLORER...3 3.1 INSTALLING THE CERTIFICATE...3 3.2 SSL3 ACTIVATION:...3 3.3 JAVASCRIPT ACTIVATION...3
TABLE OF CONTENTS 1 QUICK SET-UP VERIFICATION...3 2 INSTALLING CERTIFICATES...3 3 IF YOU USE MS INTERNET EXPLORER...3 3.1 INSTALLING THE CERTIFICATE...3 3.2 SSL3 ACTIVATION:...3 3.3 JAVASCRIPT ACTIVATION...3
TxEIS on Internet Explorer 8
 TxEIS on Internet Explorer 8 General Set Up Recommendations: Several modifications will need to be made to the computer settings in Internet Explorer to ensure TxEIS runs smoothly, reports pop up as desired,
TxEIS on Internet Explorer 8 General Set Up Recommendations: Several modifications will need to be made to the computer settings in Internet Explorer to ensure TxEIS runs smoothly, reports pop up as desired,
Perceptive Nolij Web. Technical Specifications. Version:
 Perceptive Nolij Web Technical Specifications Version: 6.8.24 Written by: Product Knowledge Date: October 2017 2014-2017 Lexmark. All rights reserved. Lexmark is a trademark of Lexmark International, Inc.,
Perceptive Nolij Web Technical Specifications Version: 6.8.24 Written by: Product Knowledge Date: October 2017 2014-2017 Lexmark. All rights reserved. Lexmark is a trademark of Lexmark International, Inc.,
WA2493 What's New in Java 8. Classroom Setup Guide. Web Age Solutions Inc.
 WA2493 What's New in Java 8 Classroom Setup Guide Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum Software Requirements...3 Part 3 - Software Provided...4
WA2493 What's New in Java 8 Classroom Setup Guide Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum Software Requirements...3 Part 3 - Software Provided...4
8.0 Help for Community Managers Release Notes System Requirements Administering Jive for Office... 6
 for Office Contents 2 Contents 8.0 Help for Community Managers... 3 Release Notes... 4 System Requirements... 5 Administering Jive for Office... 6 Getting Set Up...6 Installing the Extended API JAR File...6
for Office Contents 2 Contents 8.0 Help for Community Managers... 3 Release Notes... 4 System Requirements... 5 Administering Jive for Office... 6 Getting Set Up...6 Installing the Extended API JAR File...6
Browser Settings. Updated 4/30/ SSF
 Browser Settings Updated 4/30/2014 - SSF Contents How to Locate the Online Banking URL... 3 Initial Steps for Browser Settings... 8 Internet Explorer... 9 Firefox... 13 Chrome... 18 Safari 6.0.5 and up...
Browser Settings Updated 4/30/2014 - SSF Contents How to Locate the Online Banking URL... 3 Initial Steps for Browser Settings... 8 Internet Explorer... 9 Firefox... 13 Chrome... 18 Safari 6.0.5 and up...
WA EJB and JPA Programming with Java EE 6 - WebLogic 12 / Eclipse. Classroom Setup Guide. Web Age Solutions Inc.
 WA2091 - EJB and JPA Programming with Java EE 6 - WebLogic 12 / Eclipse Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3
WA2091 - EJB and JPA Programming with Java EE 6 - WebLogic 12 / Eclipse Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3
WA1827 Cloud Programming Workshop. Classroom Setup Guide. Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1
 WA1827 Cloud Programming Workshop Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum Software
WA1827 Cloud Programming Workshop Classroom Setup Guide Web Age Solutions Inc. Copyright Web Age Solutions Inc. 1 Table of Contents Part 1 - Minimum Hardware Requirements...3 Part 2 - Minimum Software
Aspera Connect Windows XP, 2003, Vista, 2008, 7. Document Version: 1
 Aspera Connect 2.6.3 Windows XP, 2003, Vista, 2008, 7 Document Version: 1 2 Contents Contents Introduction... 3 Setting Up... 4 Upgrading from a Previous Version...4 Installation... 4 Set Up Network Environment...
Aspera Connect 2.6.3 Windows XP, 2003, Vista, 2008, 7 Document Version: 1 2 Contents Contents Introduction... 3 Setting Up... 4 Upgrading from a Previous Version...4 Installation... 4 Set Up Network Environment...
Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS)
 Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
ForeScout Extended Module for IBM BigFix
 ForeScout Extended Module for IBM BigFix Version 1.0.0 Table of Contents About this Integration... 4 Use Cases... 4 Additional BigFix Documentation... 4 About this Module... 4 Concepts, Components, Considerations...
ForeScout Extended Module for IBM BigFix Version 1.0.0 Table of Contents About this Integration... 4 Use Cases... 4 Additional BigFix Documentation... 4 About this Module... 4 Concepts, Components, Considerations...
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Controlsoft Identity and Access Management Software Controlsoft Identity Access Management Software
 Controlsoft Identity Access Management Software IA Server Software Installation Guide v8.0.229 2018 Controlsoft Ltd 9010-0050 Issue 6 Page 1 of 39 29/10/2018 Contents 1. Introduction... 3 1.1. PC Specifications...
Controlsoft Identity Access Management Software IA Server Software Installation Guide v8.0.229 2018 Controlsoft Ltd 9010-0050 Issue 6 Page 1 of 39 29/10/2018 Contents 1. Introduction... 3 1.1. PC Specifications...
Zodiac iclass OPERATOR GUIDE
 Zodiac iclass OPERATOR GUIDE June 2008 Page 2 of 19 Table of Contents Introduction... 4 PC Requirements... 4 Installing the USB Fingerprint Scanner (Hamster)... 5 Installing the USB Smartcard Programmer...
Zodiac iclass OPERATOR GUIDE June 2008 Page 2 of 19 Table of Contents Introduction... 4 PC Requirements... 4 Installing the USB Fingerprint Scanner (Hamster)... 5 Installing the USB Smartcard Programmer...
Version 2.3 User Guide
 V Mware vcloud Usage Meter Version 2.3 User Guide 2012 VMware, Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual property laws. This product is covered
V Mware vcloud Usage Meter Version 2.3 User Guide 2012 VMware, Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual property laws. This product is covered
MarkLogic Server. Security Guide. MarkLogic 9 May, Copyright 2017 MarkLogic Corporation. All rights reserved.
 Security Guide 1 MarkLogic 9 May, 2017 Last Revised: 9.0-3, September, 2017 Copyright 2017 MarkLogic Corporation. All rights reserved. Table of Contents Table of Contents Security Guide 1.0 Introduction
Security Guide 1 MarkLogic 9 May, 2017 Last Revised: 9.0-3, September, 2017 Copyright 2017 MarkLogic Corporation. All rights reserved. Table of Contents Table of Contents Security Guide 1.0 Introduction
TIBCO LiveView Web Getting Started Guide
 TIBCO LiveView Web Getting Started Guide Introduction 2 Prerequisites 2 Installation 2 Installation Overview 3 Downloading and Installing for Windows 3 Downloading and Installing for macos 4 Installing
TIBCO LiveView Web Getting Started Guide Introduction 2 Prerequisites 2 Installation 2 Installation Overview 3 Downloading and Installing for Windows 3 Downloading and Installing for macos 4 Installing
Clear Cache Guide Click here for Windows guide Click here for Mac OS guide
 Velocity@ocbc Clear Cache Guide Click here for Windows guide Click here for Mac OS guide Version 1.0 1 of 18 Step 1: Check your browser version 1. Type www.whatismybrowser.com at the address bar and press
Velocity@ocbc Clear Cache Guide Click here for Windows guide Click here for Mac OS guide Version 1.0 1 of 18 Step 1: Check your browser version 1. Type www.whatismybrowser.com at the address bar and press
Republicbank.com Supported Browsers and Settings (Updated 03/12/13)
 Republicbank.com Supported Browsers and Settings (Updated 03/12/13) We support the Internet Explorer 8.0 & 9.0. If you are using Internet Explorer 7.0 or earlier you will need to update your browser. Click
Republicbank.com Supported Browsers and Settings (Updated 03/12/13) We support the Internet Explorer 8.0 & 9.0. If you are using Internet Explorer 7.0 or earlier you will need to update your browser. Click
Steps to View Online Lectures
 Steps to View Online Lectures Panopto recordings can be viewed on a multitude of operating systems such as Windows XP, Windows Vista, and Mac OS X (Intel Only) Panopto is also compatible with most major
Steps to View Online Lectures Panopto recordings can be viewed on a multitude of operating systems such as Windows XP, Windows Vista, and Mac OS X (Intel Only) Panopto is also compatible with most major
: BIOMETRIC AUTHENTICATION TOOL FOR USER IDENTIFICATION
 2006-287: BIOMETRIC AUTHENTICATION TOOL FOR USER IDENTIFICATION Mario Garcia, Texas A&M University-Corpus Christi American Society for Engineering Education, 2006 Page 11.277.1 Biometric Authentication
2006-287: BIOMETRIC AUTHENTICATION TOOL FOR USER IDENTIFICATION Mario Garcia, Texas A&M University-Corpus Christi American Society for Engineering Education, 2006 Page 11.277.1 Biometric Authentication
Zodiac iclass II OPERATOR GUIDE
 Zodiac iclass II OPERATOR GUIDE July 2013 Page 2 of 24 Table of Contents INTRODUCTION... 4 PC REQUIREMENTS... 5 INSTALLING THE USB FINGERPRINT SCANNER (HAMSTER)... 5 INSTALLING THE USB SMARTCARD PROGRAMMER
Zodiac iclass II OPERATOR GUIDE July 2013 Page 2 of 24 Table of Contents INTRODUCTION... 4 PC REQUIREMENTS... 5 INSTALLING THE USB FINGERPRINT SCANNER (HAMSTER)... 5 INSTALLING THE USB SMARTCARD PROGRAMMER
Mortgage Cadence System Minimum Requirements and Troubleshooting
 Purpose Mortgage Cadence System Minimum Requirements and Troubleshooting This document defines the browser requirements to operate Mortgage Cadence with the necessary encryption and how to troubleshoot
Purpose Mortgage Cadence System Minimum Requirements and Troubleshooting This document defines the browser requirements to operate Mortgage Cadence with the necessary encryption and how to troubleshoot
etrac Guide Vendor Module to the Version: 2.0 Published: 06/22/2014
 etrac Guide to the Vendor Module Version: 2.0 Published: 06/22/2014 Global DMS, 1555 Bustard Road, Suite 300, Lansdale, PA 19446 2014, All Rights Reserved. Table of Contents Minimum System Requirements...
etrac Guide to the Vendor Module Version: 2.0 Published: 06/22/2014 Global DMS, 1555 Bustard Road, Suite 300, Lansdale, PA 19446 2014, All Rights Reserved. Table of Contents Minimum System Requirements...
Halcyon Message Sender GUI. v6.0 User Guide
 GUI v6.0 User Guide Copyright Copyright HelpSystems, LLC. All rights reserved. www.helpsystems.com US: +1 952-933-0609 Outside the U.S.: +44 (0) 870 120 3148 IBM, AS/400, OS/400, System i, System i5, i5/os,
GUI v6.0 User Guide Copyright Copyright HelpSystems, LLC. All rights reserved. www.helpsystems.com US: +1 952-933-0609 Outside the U.S.: +44 (0) 870 120 3148 IBM, AS/400, OS/400, System i, System i5, i5/os,
Instruction Guide! VERITEXT VAULT - ONLINE DEPOSITORY
 Veritext Vault Instruction Guide 1 Logging In 1. Visit www.veritext.com/vault 2. Click Vault Login 3. Enter your user name and password. (Ensure you have @veritext at the end of your user name.) Be sure
Veritext Vault Instruction Guide 1 Logging In 1. Visit www.veritext.com/vault 2. Click Vault Login 3. Enter your user name and password. (Ensure you have @veritext at the end of your user name.) Be sure
Signing In to WebEx Assistant, page 1
 Use WebEx Assistant to quickly start or schedule meetings, and set up or change your WebEx account settings without going to your Cisco WebEx site., page 1 Switching Sites, page 2 Starting an Instant Meeting
Use WebEx Assistant to quickly start or schedule meetings, and set up or change your WebEx account settings without going to your Cisco WebEx site., page 1 Switching Sites, page 2 Starting an Instant Meeting
Portal Recipient Guide. The Signature Approval Process
 Portal Recipient Guide The Signature Approval Process Contents 1 Introduction... 3 2 Account Activation... 3 3 Document Signing... Error! Bookmark not defined. 4 Authenticating your Device & Browser...
Portal Recipient Guide The Signature Approval Process Contents 1 Introduction... 3 2 Account Activation... 3 3 Document Signing... Error! Bookmark not defined. 4 Authenticating your Device & Browser...
Fingerprint Authentication for SIS-based Healthcare Systems
 Fingerprint Authentication for SIS-based Healthcare Systems Project Report Introduction In many applications there is need for access control on certain sensitive data. This is especially true when it
Fingerprint Authentication for SIS-based Healthcare Systems Project Report Introduction In many applications there is need for access control on certain sensitive data. This is especially true when it
