Presented by Yung-Ting Chuang
|
|
|
- Brittney Porter
- 5 years ago
- Views:
Transcription
1 Presented by Yung-Ting Chuang Research conducted in collaboration with Isai Michel Lombera, Louise E. Moser and P. M. Melliar-Smith University of California, Santa Barbara Supported in part by NSF Grant CNS
2 Overview Introduction Design of itrust Implementation of itrust Analytical Foundations Detecting Malicious Attacks Defending against Malicious Attacks Experimental Evaluation Related Work Conclusions and Future Work
3 Introduction Today, we use centralized search engines on the Internet (Google, Yahoo!, Bing, etc) Benefits Drawbacks itrust is desirable for individuals who fear censorship of information accessed on the Internet itrust distributes metadata and requests to random participating nodes in the itrust membership Benefits Drawbacks
4 Design of itrust Source of Information
5 Design of itrust Source of Information Requester of Information Request Encounters Metadata
6 Design of itrust Source of Information Request Matched Requester of Information
7 HTTP Implementation of itrust apache PHP curl SQLite session log PECL http metadata functions metadata xml engine register metadata list apply xml publish xml list helper functions nodes wrapper keywords wrapper resource wrapper tag keyword resource search functions globals / navigation tika / lucene / dictionary public interface tools user settings statistics metadata inbox leave membership delete nodes search query inbox (a) (b) (c)
8 Analytical Foundations Assume All nodes have the same membership set Internet is reliable All nodes has enough memory to store source documents Variables Membership contains n participating nodes x is the proportion of participating nodes that are operational Metadata are distributed to m nodes Requests are distributed to r nodes k nodes report matches to a requesting node
9 itrust Properties Probability p of k matches is Probability p of one or more matches is:
10 Analytical Results
11 Detecting Malicious Attacks
12 Detecting Malicious Attacks Algorithm: Each requesting node Makes requests and collect number of responses Constructs empirical probabilities of number of matches Computes analytical probabilities of number of matches Uses Pearson s chi-squared goodness-of-fit test: Determines x from smallest obtained in Pearson s test
13 Detecting Malicious Attacks Example: For 45 requests, we have: 2 with 0 matches, 11 with1 match, 13 with 2 matches, 10 with 3 matches, 7 with 4 matches, 2 with 5 matches Divide by 45 requests to get: o k=1,2,3,4,5 =(0.244,0.289,0.222,0.156,0.044) For x=1, calculate: e k=1,2,3,4,5 =(0.089,0.175,0.221,0.204,0.145) Apply Chi-Square test to get: Repeat above steps for x=0.7, x=0.4, and x=0.2 Compare all 4 Chi-Square values (0.429, 0.022, 0.603, ) Smallest Chi-Square value=0.022, so the estimate is x =0.7
14 Detecting Malicious Attacks
15 Defending Malicious Attacks
16 Defending Malicious Attacks Algorithm: Each node finds new values of m and r :
17 Defending Malicious Attacks Example: Initially n=1000, x=1, r=m=60, y o = Next detection algorithm estimates x =0.7 Then the defense algorithm calculates: x =0.7, n=1000, r =m =60, y = x =0.7, n=1000, r =m =61, y = x =0.7, n=1000, r =m =62, y = x =0.7, n=1000, r =m =71, y = x =0.7, n=1000, r =m =72, y = > y o The program stops and returns the new value r =m =72
18 Evaluation Metrics Accuracy: Response Time:
19 Accuracy Experimental Evaluation (Accuracy) x=1 x=0.7 x= x= Number of requests in a window
20 Response Time Experimental Evaluation (Response Time) x=1 x=0.7 x= x= Number of requests in a window
21 Related Work Other unstructured publication, search, retrieval systems Gnutella - uses flooding of requests A node makes a copy of information when it receives the information it requested Distributes requests up to maximum depth or time-to-live Freenet uses replication of information Replicates information at a node, even if the node did not request it Nodes that respond successfully to requests receive more metadata and more requests
22 Related Work Several recent publication, search, and retrieval systems are concerned with malicious attacks Morselli uses a feedback mechanism to determine if an object is replicated sufficiently Jesi uses gossip and blacklist mechanisms to identify malicious nodes, and focuses on hub attacks Condie uses local trust scores to find malicious peers that upload corrupt, inauthentic or misnamed content, and moves them to the edge of the network
23 Conclusions itrust is desirable for individuals who fear censorship of information accessed on the Internet We have presented novel statistical algorithms for detecting and defending against malicious attacks Detection algorithm estimates the proportion of nodes that are subverted or non-operational, based on the number of responses that a requesting node receives Defensive adaptation algorithm determines the number of nodes to which the metadata and the requests must distributed to maintain the same probability of a match, as when all the nodes are operational
24 Future Work We plan to investigate other possible malicious attacks on itrust and countermeasures to such attacks We are developing another implementation of itrust based on SMS to operate on mobile phones We plan to make the itrust source code, tools, and documentation freely available to all
25 Questions? Comments? Our itrust Web Site Contact information Yung-Ting Chuang: Isai: Our project is supported by NSF CNS
A Distributed Ranking Algorithm for the itrust Information Search and Retrieval System
 A Distributed Ranking Algorithm for the itrust Information Search and Retrieval System Boyang Peng, L. E. Moser, P. M. Melliar-Smith, Y. T. Chuang, I. Michel Lombera Department of Electrical and Computer
A Distributed Ranking Algorithm for the itrust Information Search and Retrieval System Boyang Peng, L. E. Moser, P. M. Melliar-Smith, Y. T. Chuang, I. Michel Lombera Department of Electrical and Computer
Peer Management for itrust over Wi-Fi Direct
 Peer Management for itrust over Wi-Fi Direct Isaí Michel Lombera, L. E. Moser, P. M. Melliar-Smith, Yung-Ting Chuang Department of Electrical and Computer Engineering University of California, Santa Barbara
Peer Management for itrust over Wi-Fi Direct Isaí Michel Lombera, L. E. Moser, P. M. Melliar-Smith, Yung-Ting Chuang Department of Electrical and Computer Engineering University of California, Santa Barbara
DECLUSTERING THE ITRUST SEARCH AND RETRIEVAL NETWORK TO INCREASE TRUSTWORTHINESS
 DECLUSTERING THE ITRUST SEARCH AND RETRIEVAL NETWORK TO INCREASE TRUSTWORTHINESS Christopher M. Badger, Louise E. Moser, P. Michael Melliar-Smith, Isai Michel Lombera, Yung-Ting Chuang Departments of Computer
DECLUSTERING THE ITRUST SEARCH AND RETRIEVAL NETWORK TO INCREASE TRUSTWORTHINESS Christopher M. Badger, Louise E. Moser, P. Michael Melliar-Smith, Isai Michel Lombera, Yung-Ting Chuang Departments of Computer
User Guide for itrust over SMS and itrust over Wi-Fi Direct Installation and Use
 National Science Foundation CNS 10-16193 User Guide for itrust over SMS and itrust over Wi-Fi Direct Installation and Use University of California, Santa Barbara by Isaí Michel Lombera This documentation
National Science Foundation CNS 10-16193 User Guide for itrust over SMS and itrust over Wi-Fi Direct Installation and Use University of California, Santa Barbara by Isaí Michel Lombera This documentation
Trustworthy Distributed Search and Retrieval over the Internet
 UNIVERSITY OF CALIFORNIA Santa Barbara Trustworthy Distributed Search and Retrieval over the Internet A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy
UNIVERSITY OF CALIFORNIA Santa Barbara Trustworthy Distributed Search and Retrieval over the Internet A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy
Review Session. Ennan Zhai
 Review Session Ennan Zhai ennan.zhai@yale.edu Today s Mission USENET & Gossip Firewall & NATs Cryptographic tools Reputation Unstructured search Structured search Today s Mission USENET & Gossip Firewall
Review Session Ennan Zhai ennan.zhai@yale.edu Today s Mission USENET & Gossip Firewall & NATs Cryptographic tools Reputation Unstructured search Structured search Today s Mission USENET & Gossip Firewall
SELF-ORGANIZING TRUST MODEL FOR PEER TO PEER SYSTEMS
 SELF-ORGANIZING TRUST MODEL FOR PEER TO PEER SYSTEMS R. K. Prasad and Vipin Sharma 1 Department of Mechanical Engineering ABSTRACT: P A College of Engineering Nadupadavu, Mangalore, India In this implemented
SELF-ORGANIZING TRUST MODEL FOR PEER TO PEER SYSTEMS R. K. Prasad and Vipin Sharma 1 Department of Mechanical Engineering ABSTRACT: P A College of Engineering Nadupadavu, Mangalore, India In this implemented
run your own search engine. today: Cablecar
 run your own search engine. today: Cablecar Robert Kowalski @robinson_k http://github.com/robertkowalski Search nobody uses that, right? Services on the Market Google Bing Yahoo ask Wolfram Alpha Baidu
run your own search engine. today: Cablecar Robert Kowalski @robinson_k http://github.com/robertkowalski Search nobody uses that, right? Services on the Market Google Bing Yahoo ask Wolfram Alpha Baidu
Scalable overlay Networks
 overlay Networks Dr. Samu Varjonen 1 Lectures MO 15.01. C122 Introduction. Exercises. Motivation. TH 18.01. DK117 Unstructured networks I MO 22.01. C122 Unstructured networks II TH 25.01. DK117 Bittorrent
overlay Networks Dr. Samu Varjonen 1 Lectures MO 15.01. C122 Introduction. Exercises. Motivation. TH 18.01. DK117 Unstructured networks I MO 22.01. C122 Unstructured networks II TH 25.01. DK117 Bittorrent
Overlay and P2P Networks. Unstructured networks: Freenet. Dr. Samu Varjonen
 Overlay and P2P Networks Unstructured networks: Freenet Dr. Samu Varjonen 1.2.2015 Contents Last week Napster Skype Gnutella BitTorrent and analysis This week: Freenet Introduction to structured networks
Overlay and P2P Networks Unstructured networks: Freenet Dr. Samu Varjonen 1.2.2015 Contents Last week Napster Skype Gnutella BitTorrent and analysis This week: Freenet Introduction to structured networks
Content Overlays. Nick Feamster CS 7260 March 12, 2007
 Content Overlays Nick Feamster CS 7260 March 12, 2007 Content Overlays Distributed content storage and retrieval Two primary approaches: Structured overlay Unstructured overlay Today s paper: Chord Not
Content Overlays Nick Feamster CS 7260 March 12, 2007 Content Overlays Distributed content storage and retrieval Two primary approaches: Structured overlay Unstructured overlay Today s paper: Chord Not
Intro to Peer-to-Peer Search
 Intro to Peer-to-Peer Search (COSC 416) Nazli Goharian nazli@cs.georgetown.edu 1 Outline Peer-to-peer historical perspective Problem definition Local client data processing Ranking functions Metadata copying
Intro to Peer-to-Peer Search (COSC 416) Nazli Goharian nazli@cs.georgetown.edu 1 Outline Peer-to-peer historical perspective Problem definition Local client data processing Ranking functions Metadata copying
Censorship-Resistant File Storage
 Censorship-Resistant File Storage David Vargas, Robert Tran, Omar Gonzalez Summary This project tackles the problem of designing a file system that is resistant to censorship; that is the deletion, alteration,
Censorship-Resistant File Storage David Vargas, Robert Tran, Omar Gonzalez Summary This project tackles the problem of designing a file system that is resistant to censorship; that is the deletion, alteration,
Smart Bulk SMS & Voice SMS Marketing Script with 2-Way Messaging. Quick-Start Manual
 Mobiketa Smart Bulk SMS & Voice SMS Marketing Script with 2-Way Messaging Quick-Start Manual Overview Mobiketa Is a full-featured Bulk SMS and Voice SMS marketing script that gives you control over your
Mobiketa Smart Bulk SMS & Voice SMS Marketing Script with 2-Way Messaging Quick-Start Manual Overview Mobiketa Is a full-featured Bulk SMS and Voice SMS marketing script that gives you control over your
Overlay and P2P Networks. Unstructured networks. PhD. Samu Varjonen
 Overlay and P2P Networks Unstructured networks PhD. Samu Varjonen 25.1.2016 Contents Unstructured networks Last week Napster Skype This week: Gnutella BitTorrent P2P Index It is crucial to be able to find
Overlay and P2P Networks Unstructured networks PhD. Samu Varjonen 25.1.2016 Contents Unstructured networks Last week Napster Skype This week: Gnutella BitTorrent P2P Index It is crucial to be able to find
Web Development IB PRECISION EXAMS
 PRECISION EXAMS Web Development IB EXAM INFORMATION Items 53 Points 73 Prerequisites COMPUTER TECHNOLOGY Grade Level 10-12 Course Length ONE YEAR Career Cluster INFORMATION TECHNOLOGY Performance Standards
PRECISION EXAMS Web Development IB EXAM INFORMATION Items 53 Points 73 Prerequisites COMPUTER TECHNOLOGY Grade Level 10-12 Course Length ONE YEAR Career Cluster INFORMATION TECHNOLOGY Performance Standards
Secure web proxy resistant to probing attacks
 Technical Disclosure Commons Defensive Publications Series December 04, 2017 Secure web proxy resistant to probing attacks Benjamin Schwartz Follow this and additional works at: http://www.tdcommons.org/dpubs_series
Technical Disclosure Commons Defensive Publications Series December 04, 2017 Secure web proxy resistant to probing attacks Benjamin Schwartz Follow this and additional works at: http://www.tdcommons.org/dpubs_series
<Partner Name> <Partner Product> RSA NETWITNESS Logs Implementation Guide. Exabeam User Behavior Analytics 3.0
 RSA NETWITNESS Logs Implementation Guide Exabeam Daniel R. Pintal, RSA Partner Engineering Last Modified: May 5, 2017 Solution Summary The Exabeam User Behavior Intelligence
RSA NETWITNESS Logs Implementation Guide Exabeam Daniel R. Pintal, RSA Partner Engineering Last Modified: May 5, 2017 Solution Summary The Exabeam User Behavior Intelligence
Overlay and P2P Networks. Unstructured networks. Prof. Sasu Tarkoma
 Overlay and P2P Networks Unstructured networks Prof. Sasu Tarkoma 19.1.2015 Contents Unstructured networks Last week Napster Skype This week: Gnutella BitTorrent P2P Index It is crucial to be able to find
Overlay and P2P Networks Unstructured networks Prof. Sasu Tarkoma 19.1.2015 Contents Unstructured networks Last week Napster Skype This week: Gnutella BitTorrent P2P Index It is crucial to be able to find
Database Foundations. 4-1 Oracle SQL Developer Data Modeler. Copyright 2015, Oracle and/or its affiliates. All rights reserved.
 Database Foundations 4-1 Road Map You are here Oracle SQL Developer Data Modeler Converting a Logical Model to a Relational Model 3 Objectives This lesson covers the following objectives: Use to create:
Database Foundations 4-1 Road Map You are here Oracle SQL Developer Data Modeler Converting a Logical Model to a Relational Model 3 Objectives This lesson covers the following objectives: Use to create:
Overlay and P2P Networks. Unstructured networks. Prof. Sasu Tarkoma
 Overlay and P2P Networks Unstructured networks Prof. Sasu Tarkoma 20.1.2014 Contents P2P index revisited Unstructured networks Gnutella Bloom filters BitTorrent Freenet Summary of unstructured networks
Overlay and P2P Networks Unstructured networks Prof. Sasu Tarkoma 20.1.2014 Contents P2P index revisited Unstructured networks Gnutella Bloom filters BitTorrent Freenet Summary of unstructured networks
Information Retrieval in Peer to Peer Systems. Sharif University of Technology. Fall Dr Hassan Abolhassani. Author: Seyyed Mohsen Jamali
 Information Retrieval in Peer to Peer Systems Sharif University of Technology Fall 2005 Dr Hassan Abolhassani Author: Seyyed Mohsen Jamali [Slide 2] Introduction Peer-to-Peer systems are application layer
Information Retrieval in Peer to Peer Systems Sharif University of Technology Fall 2005 Dr Hassan Abolhassani Author: Seyyed Mohsen Jamali [Slide 2] Introduction Peer-to-Peer systems are application layer
Scalable overlay Networks
 overlay Networks Dr. Samu Varjonen 1 Lectures MO 15.01. C122 Introduction. Exercises. Motivation. TH 18.01. DK117 Unstructured networks I MO 22.01. C122 Unstructured networks II TH 25.01. DK117 Bittorrent
overlay Networks Dr. Samu Varjonen 1 Lectures MO 15.01. C122 Introduction. Exercises. Motivation. TH 18.01. DK117 Unstructured networks I MO 22.01. C122 Unstructured networks II TH 25.01. DK117 Bittorrent
The Highly Insidious Extreme Phishing Attacks
 The Highly Insidious Extreme Phishing Attacks Rui Zhao, Samantha John, Stacy Karas, Cara Bussell, Jennifer Roberts, Daniel Six, Brandon Gavett, and Chuan Yue Colorado School of Mines, Golden, CO 80401
The Highly Insidious Extreme Phishing Attacks Rui Zhao, Samantha John, Stacy Karas, Cara Bussell, Jennifer Roberts, Daniel Six, Brandon Gavett, and Chuan Yue Colorado School of Mines, Golden, CO 80401
SOLUTION BRIEF REMOTE ACCESS: WEBSHELLS SEE EVERYTHING, FEAR NOTHING
 REMOTE ACCESS: WEBSHELLS SEE EVERYTHING, FEAR NOTHING RSA Visibility Reconnaissance Weaponization Delivery Exploitation Installation C2 Action WHAT IS A WEBSHELL? A WebShell is a piece of code or a script
REMOTE ACCESS: WEBSHELLS SEE EVERYTHING, FEAR NOTHING RSA Visibility Reconnaissance Weaponization Delivery Exploitation Installation C2 Action WHAT IS A WEBSHELL? A WebShell is a piece of code or a script
Probabilistic Analysis of Message Forwarding
 Probabilistic Analysis of Message Forwarding Louise E. Moser and P. M. Melliar-Smith Department of Electrical and Computer Engineering University of California, Santa Barbara Santa Barbara, CA 93106 USA
Probabilistic Analysis of Message Forwarding Louise E. Moser and P. M. Melliar-Smith Department of Electrical and Computer Engineering University of California, Santa Barbara Santa Barbara, CA 93106 USA
D8L89G IBM Lotus Domino 8.5 System Administration Bootcamp
 Tel. +39 02 365738 info@overneteducation.it www.overneteducation.it D8L89G IBM Lotus Domino 8.5 System Administration Bootcamp Durata: 5 gg Descrizione In this course, you will: Be introduced to basic
Tel. +39 02 365738 info@overneteducation.it www.overneteducation.it D8L89G IBM Lotus Domino 8.5 System Administration Bootcamp Durata: 5 gg Descrizione In this course, you will: Be introduced to basic
An Introduction to JavaScript & Bootstrap Basic concept used in responsive website development Form Validation Creating templates
 PHP Course Contents An Introduction to HTML & CSS Basic Html concept used in website development Creating templates An Introduction to JavaScript & Bootstrap Basic concept used in responsive website development
PHP Course Contents An Introduction to HTML & CSS Basic Html concept used in website development Creating templates An Introduction to JavaScript & Bootstrap Basic concept used in responsive website development
Cybersecurity-Related Information Sharing Guidelines Draft Document Request For Comment
 Cybersecurity-Related Information Sharing Guidelines Draft Document Request For Comment SWG G 3 2016 v0.2 ISAO Standards Organization Standards Working Group 3: Information Sharing Kent Landfield, Chair
Cybersecurity-Related Information Sharing Guidelines Draft Document Request For Comment SWG G 3 2016 v0.2 ISAO Standards Organization Standards Working Group 3: Information Sharing Kent Landfield, Chair
Scalable overlay Networks
 overlay Networks Dr. Samu Varjonen 1 Contents Course overview Lectures Assignments/Exercises 2 Course Overview Overlay networks and peer-to-peer technologies have become key components for building large
overlay Networks Dr. Samu Varjonen 1 Contents Course overview Lectures Assignments/Exercises 2 Course Overview Overlay networks and peer-to-peer technologies have become key components for building large
CSCE 548 Building Secure Software SQL Injection Attack
 CSCE 548 Building Secure Software SQL Injection Attack Professor Lisa Luo Spring 2018 Previous class DirtyCOW is a special type of race condition problem It is related to memory mapping We learned how
CSCE 548 Building Secure Software SQL Injection Attack Professor Lisa Luo Spring 2018 Previous class DirtyCOW is a special type of race condition problem It is related to memory mapping We learned how
Robust Defenses for Cross-Site Request Forgery Review
 Robust Defenses for Cross-Site Request Forgery Review Network Security Instructor:Dr. Shishir Nagaraja Submitted By: Jyoti Leeka October 16, 2011 1 Introduction to the topic and the reason for the topic
Robust Defenses for Cross-Site Request Forgery Review Network Security Instructor:Dr. Shishir Nagaraja Submitted By: Jyoti Leeka October 16, 2011 1 Introduction to the topic and the reason for the topic
IT Security Training MS-500: Microsoft 365 Security Administration. Upcoming Dates. Course Description. Course Outline $2,
 IT Security Training MS-500: Microsoft 365 Security Administration $2,595.00 4 Days Upcoming Dates Course Description Day 1: Managing Microsoft 365 Identity and Access (MS-500T01-A) Help protect against
IT Security Training MS-500: Microsoft 365 Security Administration $2,595.00 4 Days Upcoming Dates Course Description Day 1: Managing Microsoft 365 Identity and Access (MS-500T01-A) Help protect against
Peer-to-peer systems and overlay networks
 Complex Adaptive Systems C.d.L. Informatica Università di Bologna Peer-to-peer systems and overlay networks Fabio Picconi Dipartimento di Scienze dell Informazione 1 Outline Introduction to P2P systems
Complex Adaptive Systems C.d.L. Informatica Università di Bologna Peer-to-peer systems and overlay networks Fabio Picconi Dipartimento di Scienze dell Informazione 1 Outline Introduction to P2P systems
Overlay and P2P Networks. Introduction. Prof. Sasu Tarkoma
 Overlay and P2P Networks Introduction Prof. Sasu Tarkoma 12.1.2015 Contents Course Overview Lectures Assignments/Exercises Course Overview Overlay networks and peer-to-peer technologies have become key
Overlay and P2P Networks Introduction Prof. Sasu Tarkoma 12.1.2015 Contents Course Overview Lectures Assignments/Exercises Course Overview Overlay networks and peer-to-peer technologies have become key
Matthew Harris Senior Project Proposal getnote The Mobile Application
 Matthew Harris Senior Project Proposal getnote The Mobile Application 1 Table of Contents Background and Motivation 3 Problems to be Addressed: 3 Solution: 4 Methodology: 4 Goal: 5 Deliverables: 5 Justification:
Matthew Harris Senior Project Proposal getnote The Mobile Application 1 Table of Contents Background and Motivation 3 Problems to be Addressed: 3 Solution: 4 Methodology: 4 Goal: 5 Deliverables: 5 Justification:
1Z Oracle Business Intelligence (OBI) Foundation Suite 11g Essentials Exam Summary Syllabus Questions
 1Z0-591 Oracle Business Intelligence (OBI) Foundation Suite 11g Essentials Exam Summary Syllabus Questions Table of Contents Introduction to 1Z0-591 Exam on Oracle Business Intelligence (OBI) Foundation
1Z0-591 Oracle Business Intelligence (OBI) Foundation Suite 11g Essentials Exam Summary Syllabus Questions Table of Contents Introduction to 1Z0-591 Exam on Oracle Business Intelligence (OBI) Foundation
Peer-to-Peer Internet Applications: A Review
 Peer-to-Peer Internet Applications: A Review Davide Quaglia 01/14/10 Introduction Key points Lookup task Outline Centralized (Napster) Query flooding (Gnutella) Distributed Hash Table (Chord) Simulation
Peer-to-Peer Internet Applications: A Review Davide Quaglia 01/14/10 Introduction Key points Lookup task Outline Centralized (Napster) Query flooding (Gnutella) Distributed Hash Table (Chord) Simulation
Reputation Management in P2P Systems
 Reputation Management in P2P Systems Pradipta Mitra Nov 18, 2003 1 We will look at... Overview of P2P Systems Problems in P2P Systems Reputation Management Limited Reputation Sharing Simulation Results
Reputation Management in P2P Systems Pradipta Mitra Nov 18, 2003 1 We will look at... Overview of P2P Systems Problems in P2P Systems Reputation Management Limited Reputation Sharing Simulation Results
IBM Lotus Domino 8.5 System Administration Bootcamp Information Length: Ref: 5.0 Days D8L89G Delivery method: Classroom. Price: INR.
 IBM Lotus Domino 8.5 System Administration Bootcamp Information Length: Ref: 5.0 Days D8L89G Delivery method: Classroom Overview Price: INR In this course, you will: Be introduced to basic concepts that
IBM Lotus Domino 8.5 System Administration Bootcamp Information Length: Ref: 5.0 Days D8L89G Delivery method: Classroom Overview Price: INR In this course, you will: Be introduced to basic concepts that
Overlay and P2P Networks. Introduction. Prof. Sasu Tarkoma
 Overlay and P2P Networks Introduction Prof. Sasu Tarkoma 13.1.2014 Contents Course Overview Lectures Assignments/Exercises Course Overview Overlay networks and peer-to-peer technologies have become key
Overlay and P2P Networks Introduction Prof. Sasu Tarkoma 13.1.2014 Contents Course Overview Lectures Assignments/Exercises Course Overview Overlay networks and peer-to-peer technologies have become key
The Continuous SEO Process. WebExpo 2016
 The Continuous SEO Process WebExpo 2016 SEO needs TLC SEO needs TLC The nature of SEO SEO is continuous by nature. So why aren t we? SEO Authority & Trust Content Content Content Technical Foundation SEO
The Continuous SEO Process WebExpo 2016 SEO needs TLC SEO needs TLC The nature of SEO SEO is continuous by nature. So why aren t we? SEO Authority & Trust Content Content Content Technical Foundation SEO
SocialLink: Utilizing Social Network and Transaction Links for Effective Trust Management in P2P File Sharing Systems
 SocialLink: Utilizing Social Network and Transaction Links for Effective Trust Management in P2P File Sharing Systems Kang Chen 1, Guoxin Liu 2, Haiying Shen 2 and Fang Qi 2 1 Dept. Of ECE Southern Illinois
SocialLink: Utilizing Social Network and Transaction Links for Effective Trust Management in P2P File Sharing Systems Kang Chen 1, Guoxin Liu 2, Haiying Shen 2 and Fang Qi 2 1 Dept. Of ECE Southern Illinois
John Coggeshall Copyright 2006, Zend Technologies Inc.
 PHP Security Basics John Coggeshall Copyright 2006, Zend Technologies Inc. Welcome! Welcome to PHP Security Basics Who am I: John Coggeshall Lead, North American Professional Services PHP 5 Core Contributor
PHP Security Basics John Coggeshall Copyright 2006, Zend Technologies Inc. Welcome! Welcome to PHP Security Basics Who am I: John Coggeshall Lead, North American Professional Services PHP 5 Core Contributor
intelop Stealth IPS false Positive
 There is a wide variety of network traffic. Servers can be using different operating systems, an FTP server application used in the demilitarized zone (DMZ) can be different from the one used in the corporate
There is a wide variety of network traffic. Servers can be using different operating systems, an FTP server application used in the demilitarized zone (DMZ) can be different from the one used in the corporate
Managing Microsoft 365 Identity and Access
 Course MS-500T01-A: Managing Microsoft 365 Identity and Access Page 1 of 3 Managing Microsoft 365 Identity and Access Course MS-500T01-A: 1 day; Instructor-Led Introduction Help protect against credential
Course MS-500T01-A: Managing Microsoft 365 Identity and Access Page 1 of 3 Managing Microsoft 365 Identity and Access Course MS-500T01-A: 1 day; Instructor-Led Introduction Help protect against credential
CS 640 Introduction to Computer Networks. Today s lecture. What is P2P? Lecture30. Peer to peer applications
 Introduction to Computer Networks Lecture30 Today s lecture Peer to peer applications Napster Gnutella KaZaA Chord What is P2P? Significant autonomy from central servers Exploits resources at the edges
Introduction to Computer Networks Lecture30 Today s lecture Peer to peer applications Napster Gnutella KaZaA Chord What is P2P? Significant autonomy from central servers Exploits resources at the edges
Media Mark Web Development, Marketing & Production. Media Mark custom websites recognize the fact that packaged products do not fit every need!
 Custom Websites Media Mark custom websites recognize the fact that packaged products do not fit every need! Think out of the box? We do that! There is nothing simple about custom web design. But we work
Custom Websites Media Mark custom websites recognize the fact that packaged products do not fit every need! Think out of the box? We do that! There is nothing simple about custom web design. But we work
Robust Defenses for Cross-Site Request Forgery
 University of Cyprus Department of Computer Science Advanced Security Topics Robust Defenses for Cross-Site Request Forgery Name: Elena Prodromou Instructor: Dr. Elias Athanasopoulos Authors: Adam Barth,
University of Cyprus Department of Computer Science Advanced Security Topics Robust Defenses for Cross-Site Request Forgery Name: Elena Prodromou Instructor: Dr. Elias Athanasopoulos Authors: Adam Barth,
Novetta Cyber Analytics
 Know your network. Arm your analysts. Introduction Novetta Cyber Analytics is an advanced network traffic analytics solution that empowers analysts with comprehensive, near real time cyber security visibility
Know your network. Arm your analysts. Introduction Novetta Cyber Analytics is an advanced network traffic analytics solution that empowers analysts with comprehensive, near real time cyber security visibility
Un SOC avanzato per una efficace risposta al cybercrime
 Un SOC avanzato per una efficace risposta al cybercrime Identificazione e conferma di un incidente @RSAEMEA #RSAEMEASummit @masiste75 Mauro Costantini - Presales Consultant Agenda A look into the threat
Un SOC avanzato per una efficace risposta al cybercrime Identificazione e conferma di un incidente @RSAEMEA #RSAEMEASummit @masiste75 Mauro Costantini - Presales Consultant Agenda A look into the threat
Distributed Systems. peer-to-peer Johan Montelius ID2201. Distributed Systems ID2201
 Distributed Systems ID2201 peer-to-peer Johan Montelius 1 Idéa use resources in edge of network computing storage communication 2 Computing 3 seti@home central server millions of clients hundred of thousands
Distributed Systems ID2201 peer-to-peer Johan Montelius 1 Idéa use resources in edge of network computing storage communication 2 Computing 3 seti@home central server millions of clients hundred of thousands
Building a missing item in INSPIRE: The Re3gistry
 Building a missing item in INSPIRE: The Re3gistry www.jrc.ec.europa.eu Serving society Stimulating innovation Supporting legislation Key pillars of data interoperability Conceptual data models Encoding
Building a missing item in INSPIRE: The Re3gistry www.jrc.ec.europa.eu Serving society Stimulating innovation Supporting legislation Key pillars of data interoperability Conceptual data models Encoding
VMware AirWatch Integration with Palo Alto Networks WildFire Integrate your application reputation service with AirWatch
 VMware AirWatch Integration with Palo Alto Networks WildFire Integrate your application reputation service with AirWatch Multiple AirWatch versions Have documentation feedback? Submit a Documentation Feedback
VMware AirWatch Integration with Palo Alto Networks WildFire Integrate your application reputation service with AirWatch Multiple AirWatch versions Have documentation feedback? Submit a Documentation Feedback
Kademlia: A peer-to peer information system based on XOR. based on XOR Metric,by P. Maymounkov and D. Mazieres
 : A peer-to peer information system based on XOR Metric,by P. Maymounkov and D. Mazieres March 10, 2009 : A peer-to peer information system based on XOR Features From past p2p experiences, it has been
: A peer-to peer information system based on XOR Metric,by P. Maymounkov and D. Mazieres March 10, 2009 : A peer-to peer information system based on XOR Features From past p2p experiences, it has been
Getting the most from your websites SEO. A seven point guide to understanding SEO and how to maximise results
 Getting the most from your websites SEO A seven point guide to understanding SEO and how to maximise results About this document SEO: What is it? This document is aimed at giving a SEO: What is it? 2 SEO
Getting the most from your websites SEO A seven point guide to understanding SEO and how to maximise results About this document SEO: What is it? This document is aimed at giving a SEO: What is it? 2 SEO
Information Retrieval Spring Web retrieval
 Information Retrieval Spring 2016 Web retrieval The Web Large Changing fast Public - No control over editing or contents Spam and Advertisement How big is the Web? Practically infinite due to the dynamic
Information Retrieval Spring 2016 Web retrieval The Web Large Changing fast Public - No control over editing or contents Spam and Advertisement How big is the Web? Practically infinite due to the dynamic
F5 DDoS Hybrid Defender : Setup. Version
 F5 DDoS Hybrid Defender : Setup Version 13.1.0.3 Table of Contents Table of Contents Introducing DDoS Hybrid Defender... 5 Introduction to DDoS Hybrid Defender...5 DDoS deployments... 5 Example DDoS Hybrid
F5 DDoS Hybrid Defender : Setup Version 13.1.0.3 Table of Contents Table of Contents Introducing DDoS Hybrid Defender... 5 Introduction to DDoS Hybrid Defender...5 DDoS deployments... 5 Example DDoS Hybrid
NACCHO Virtual Communities Guide
 NACCHO Virtual Communities Guide NACCHO Membership Team What are NACCHO s Virtual Communities? NACCHO s Virtual Communities (VC) grows out of NACCHO s desire create a community based platform that helps
NACCHO Virtual Communities Guide NACCHO Membership Team What are NACCHO s Virtual Communities? NACCHO s Virtual Communities (VC) grows out of NACCHO s desire create a community based platform that helps
Today. Architectural Styles
 Today Architectures for distributed systems (Chapter 2) Centralized, decentralized, hybrid Middleware Self-managing systems Lecture 2, page 1 Architectural Styles Important styles of architecture for distributed
Today Architectures for distributed systems (Chapter 2) Centralized, decentralized, hybrid Middleware Self-managing systems Lecture 2, page 1 Architectural Styles Important styles of architecture for distributed
P2_L12 Web Security Page 1
 P2_L12 Web Security Page 1 Reference: Computer Security by Stallings and Brown, Chapter (not specified) The web is an extension of our computing environment, because most of our daily tasks involve interaction
P2_L12 Web Security Page 1 Reference: Computer Security by Stallings and Brown, Chapter (not specified) The web is an extension of our computing environment, because most of our daily tasks involve interaction
File Sharing in Less structured P2P Systems
 File Sharing in Less structured P2P Systems. Bhosale S.P. 1, Sarkar A.R. 2 Computer Science And Engg. Dept., SVERI s College of Engineering Pandharpur Solapur, India1 Asst.Prof, Computer Science And Engg.
File Sharing in Less structured P2P Systems. Bhosale S.P. 1, Sarkar A.R. 2 Computer Science And Engg. Dept., SVERI s College of Engineering Pandharpur Solapur, India1 Asst.Prof, Computer Science And Engg.
Liferay Fundamentals Course Overview
 Liferay Fundamentals Course Overview LIFERAY Training Liferay Fundamentals Course Overview Liferay Fundamentals is recommended for all audiences before taking any other training course. Target Audience
Liferay Fundamentals Course Overview LIFERAY Training Liferay Fundamentals Course Overview Liferay Fundamentals is recommended for all audiences before taking any other training course. Target Audience
Web Honeypots for Spies
 Web Honeypots for Spies Blake T. Henderson, Sean F. McKenna, and Neil C. Rowe (presenter) U.S. Naval Postgraduate School Monterey, California, USA ncrowe@nps.edu Motivation We are building honeypots for
Web Honeypots for Spies Blake T. Henderson, Sean F. McKenna, and Neil C. Rowe (presenter) U.S. Naval Postgraduate School Monterey, California, USA ncrowe@nps.edu Motivation We are building honeypots for
Agent and Object Technology Lab Dipartimento di Ingegneria dell Informazione Università degli Studi di Parma. Distributed and Agent Systems
 Agent and Object Technology Lab Dipartimento di Ingegneria dell Informazione Università degli Studi di Parma Distributed and Agent Systems Peer-to-Peer Systems & JXTA Prof. Agostino Poggi What is Peer-to-Peer
Agent and Object Technology Lab Dipartimento di Ingegneria dell Informazione Università degli Studi di Parma Distributed and Agent Systems Peer-to-Peer Systems & JXTA Prof. Agostino Poggi What is Peer-to-Peer
ESORICS September Martin Johns
 SessionSafe: Implementing XSS Immune SessionHandling Universität Hamburg ESORICS 06 20. September 2006 Martin Johns Fachbereich Informatik SVS Sicherheit in Verteilten Systemen Me, myself and I Martin
SessionSafe: Implementing XSS Immune SessionHandling Universität Hamburg ESORICS 06 20. September 2006 Martin Johns Fachbereich Informatik SVS Sicherheit in Verteilten Systemen Me, myself and I Martin
CS50 Quiz Review. November 13, 2017
 CS50 Quiz Review November 13, 2017 Info http://docs.cs50.net/2017/fall/quiz/about.html 48-hour window in which to take the quiz. You should require much less than that; expect an appropriately-scaled down
CS50 Quiz Review November 13, 2017 Info http://docs.cs50.net/2017/fall/quiz/about.html 48-hour window in which to take the quiz. You should require much less than that; expect an appropriately-scaled down
Peer-to-Peer Systems. Chapter General Characteristics
 Chapter 2 Peer-to-Peer Systems Abstract In this chapter, a basic overview is given of P2P systems, architectures, and search strategies in P2P systems. More specific concepts that are outlined include
Chapter 2 Peer-to-Peer Systems Abstract In this chapter, a basic overview is given of P2P systems, architectures, and search strategies in P2P systems. More specific concepts that are outlined include
2/16/18. CYSE 411/AIT 681 Secure Software Engineering. Secure Coding. The Web. Topic #11. Web Security. Instructor: Dr. Kun Sun
 CYSE 411/AIT 681 Secure Software Engineering Topic #11. Web Security Instructor: Dr. Kun Sun Secure Coding String management Pointer Subterfuge Dynamic memory management Integer security Formatted output
CYSE 411/AIT 681 Secure Software Engineering Topic #11. Web Security Instructor: Dr. Kun Sun Secure Coding String management Pointer Subterfuge Dynamic memory management Integer security Formatted output
SEARCH ENGINE OPTIMIZATION
 SEARCH ENGINE OPTIMIZATION GRANT GESKE, PH.D. DIRECTOR OF SEO AND DIGITAL ANALYTICS CARNEGIE COMMUNICATIONS MARKETING CHANNEL LANDSCAPE WHY SEO MATTERS SEO JOURNEY FOR TODAY DEFINE SEO DISCUSS RANKING
SEARCH ENGINE OPTIMIZATION GRANT GESKE, PH.D. DIRECTOR OF SEO AND DIGITAL ANALYTICS CARNEGIE COMMUNICATIONS MARKETING CHANNEL LANDSCAPE WHY SEO MATTERS SEO JOURNEY FOR TODAY DEFINE SEO DISCUSS RANKING
Taming Text. How to Find, Organize, and Manipulate It MANNING GRANT S. INGERSOLL THOMAS S. MORTON ANDREW L. KARRIS. Shelter Island
 Taming Text How to Find, Organize, and Manipulate It GRANT S. INGERSOLL THOMAS S. MORTON ANDREW L. KARRIS 11 MANNING Shelter Island contents foreword xiii preface xiv acknowledgments xvii about this book
Taming Text How to Find, Organize, and Manipulate It GRANT S. INGERSOLL THOMAS S. MORTON ANDREW L. KARRIS 11 MANNING Shelter Island contents foreword xiii preface xiv acknowledgments xvii about this book
Peer-to-Peer Systems. Network Science: Introduction. P2P History: P2P History: 1999 today
 Network Science: Peer-to-Peer Systems Ozalp Babaoglu Dipartimento di Informatica Scienza e Ingegneria Università di Bologna www.cs.unibo.it/babaoglu/ Introduction Peer-to-peer (PP) systems have become
Network Science: Peer-to-Peer Systems Ozalp Babaoglu Dipartimento di Informatica Scienza e Ingegneria Università di Bologna www.cs.unibo.it/babaoglu/ Introduction Peer-to-peer (PP) systems have become
SEO ISSUES FOUND ON YOUR SITE (JANUARY 2, 2017)
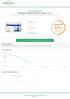 www.aircontrols.com SEO ISSUES FOUND ON YOUR SITE (JANUARY 2, 2017) This report shows the SEO issues that, when solved, will improve your site rankings and increase traffic to your website. 12 errors 4
www.aircontrols.com SEO ISSUES FOUND ON YOUR SITE (JANUARY 2, 2017) This report shows the SEO issues that, when solved, will improve your site rankings and increase traffic to your website. 12 errors 4
McAfee Advanced Threat Defense
 Advanced Threat Defense Detect advanced malware Advanced Threat Defense enables organizations to detect advanced, evasive malware and convert threat information into immediate action and protection. Unlike
Advanced Threat Defense Detect advanced malware Advanced Threat Defense enables organizations to detect advanced, evasive malware and convert threat information into immediate action and protection. Unlike
Architectures for distributed systems (Chapter 2)
 Today Architectures for distributed systems (Chapter 2) Architectural styles Client-server architectures Decentralized and peer-to-peer architectures Lecture 2, page!1 Module 1: Architectural Styles Important
Today Architectures for distributed systems (Chapter 2) Architectural styles Client-server architectures Decentralized and peer-to-peer architectures Lecture 2, page!1 Module 1: Architectural Styles Important
doi: / _32
 doi: 10.1007/978-3-319-12823-8_32 Simple Document-by-Document Search Tool Fuwatto Search using Web API Masao Takaku 1 and Yuka Egusa 2 1 University of Tsukuba masao@slis.tsukuba.ac.jp 2 National Institute
doi: 10.1007/978-3-319-12823-8_32 Simple Document-by-Document Search Tool Fuwatto Search using Web API Masao Takaku 1 and Yuka Egusa 2 1 University of Tsukuba masao@slis.tsukuba.ac.jp 2 National Institute
INTEGRATED WORKFLOW COPYEDITOR
 COPYEDITOR Content Asset or Learning Object Tagging INTEGRATED WORKFLOW CONTENT DEVELOPMENT PHASE In this Content Development workflow phase process, you add or modify Pearson, discipline-specific, and/or
COPYEDITOR Content Asset or Learning Object Tagging INTEGRATED WORKFLOW CONTENT DEVELOPMENT PHASE In this Content Development workflow phase process, you add or modify Pearson, discipline-specific, and/or
A New Adaptive, Semantically Clustered Peer-to-Peer Network Architecture
 A New Adaptive, Semantically Clustered Peer-to-Peer Network Architecture 1 S. Das 2 A. Thakur 3 T. Bose and 4 N.Chaki 1 Department of Computer Sc. & Engg, University of Calcutta, India, soumava@acm.org
A New Adaptive, Semantically Clustered Peer-to-Peer Network Architecture 1 S. Das 2 A. Thakur 3 T. Bose and 4 N.Chaki 1 Department of Computer Sc. & Engg, University of Calcutta, India, soumava@acm.org
Your Open Science and Research Publishing Platform. 1st SciShops Summer School
 Your Open Science and Research Publishing Platform 1st SciShops Summer School to researchers? to Open Science? Personal / project / community profile Thematic / personal / project repositories Enriched
Your Open Science and Research Publishing Platform 1st SciShops Summer School to researchers? to Open Science? Personal / project / community profile Thematic / personal / project repositories Enriched
Improving Search In Peer-to-Peer Systems
 Improving Search In Peer-to-Peer Systems Presented By Jon Hess cs294-4 Fall 2003 Goals Present alternative searching methods for systems with loose integrity constraints Probabilistically optimize over
Improving Search In Peer-to-Peer Systems Presented By Jon Hess cs294-4 Fall 2003 Goals Present alternative searching methods for systems with loose integrity constraints Probabilistically optimize over
Introduction to Peer-to-Peer Systems
 Introduction Introduction to Peer-to-Peer Systems Peer-to-peer (PP) systems have become extremely popular and contribute to vast amounts of Internet traffic PP basic definition: A PP system is a distributed
Introduction Introduction to Peer-to-Peer Systems Peer-to-peer (PP) systems have become extremely popular and contribute to vast amounts of Internet traffic PP basic definition: A PP system is a distributed
Intelligence Driven Incident Response Outwitting The Adversary
 Intelligence Driven Incident Response Outwitting The Adversary We have made it easy for you to find a PDF Ebooks without any digging. And by having access to our ebooks online or by storing it on your
Intelligence Driven Incident Response Outwitting The Adversary We have made it easy for you to find a PDF Ebooks without any digging. And by having access to our ebooks online or by storing it on your
Web Application Defense with Bayesian Attack Analysis
 Web Application Defense with Bayesian Attack Analysis Presented by: Ryan Barnett Senior Security Researcher OWASP ModSecurity CRS Leader Ryan Barnett - Background Trustwave Senior Security Researcher Member
Web Application Defense with Bayesian Attack Analysis Presented by: Ryan Barnett Senior Security Researcher OWASP ModSecurity CRS Leader Ryan Barnett - Background Trustwave Senior Security Researcher Member
The IAC s Publications Archive. Monique Gómez & Jorge A. Pérez Prieto Instituto de Astrofísica de Canarias Tenerife, Spain
 The IAC s Publications Archive Monique Gómez & Jorge A. Pérez Prieto Instituto de Astrofísica de Canarias Tenerife, Spain LISA VII, Naples 17-20 June 2014 Project birth Situation in 2012 IAC publications
The IAC s Publications Archive Monique Gómez & Jorge A. Pérez Prieto Instituto de Astrofísica de Canarias Tenerife, Spain LISA VII, Naples 17-20 June 2014 Project birth Situation in 2012 IAC publications
Automate Your Workflow Using Tableau Server Client and the REST API
 Welcome # T C 1 8 Automate Your Workflow Using Tableau Server Client and the REST API Chris Shin Software Engineer Developer Platform Ang Gao Software Engineer Developer Platform Enabling Integrations
Welcome # T C 1 8 Automate Your Workflow Using Tableau Server Client and the REST API Chris Shin Software Engineer Developer Platform Ang Gao Software Engineer Developer Platform Enabling Integrations
Types of Lesson Content
 Q U I CKSTART GUIDE Types of Lesson Content In Courses and Communities, you can add a variety of content. For example, videos, documents, tests, etc. 1 Navigate to 1-Courses/Communities > 2-Select Desired
Q U I CKSTART GUIDE Types of Lesson Content In Courses and Communities, you can add a variety of content. For example, videos, documents, tests, etc. 1 Navigate to 1-Courses/Communities > 2-Select Desired
Data Exchange and Conversion Utilities and Tools (DExT)
 Data Exchange and Conversion Utilities and Tools (DExT) Louise Corti, Angad Bhat, Herve L Hours UK Data Archive CAQDAS Conference, April 2007 An exchange format for qualitative data Data exchange models
Data Exchange and Conversion Utilities and Tools (DExT) Louise Corti, Angad Bhat, Herve L Hours UK Data Archive CAQDAS Conference, April 2007 An exchange format for qualitative data Data exchange models
Infoblox Dossier User Guide
 Infoblox Dossier User Guide 2017 Infoblox Inc. All rights reserved. ActiveTrust Platform Dossier and TIDE - June 2017 Page 1 of 16 1. Overview of Dossier... 3 2. Prerequisites... 3 3. Access to the Dossier
Infoblox Dossier User Guide 2017 Infoblox Inc. All rights reserved. ActiveTrust Platform Dossier and TIDE - June 2017 Page 1 of 16 1. Overview of Dossier... 3 2. Prerequisites... 3 3. Access to the Dossier
Chapter 27 Introduction to Information Retrieval and Web Search
 Chapter 27 Introduction to Information Retrieval and Web Search Copyright 2011 Pearson Education, Inc. Publishing as Pearson Addison-Wesley Chapter 27 Outline Information Retrieval (IR) Concepts Retrieval
Chapter 27 Introduction to Information Retrieval and Web Search Copyright 2011 Pearson Education, Inc. Publishing as Pearson Addison-Wesley Chapter 27 Outline Information Retrieval (IR) Concepts Retrieval
whitehvac.com SEO ISSUES FOUND ON YOUR SITE (JANUARY 2, 2017)
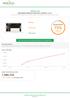 whitehvac.com SEO ISSUES FOUND ON YOUR SITE (JANUARY 2, 2017) This report shows the SEO issues that, when solved, will improve your site rankings and increase traffic to your website. 6 errors 4 warnings
whitehvac.com SEO ISSUES FOUND ON YOUR SITE (JANUARY 2, 2017) This report shows the SEO issues that, when solved, will improve your site rankings and increase traffic to your website. 6 errors 4 warnings
Conducting Remote Studies of Web Users Using WebLab UX
 Copyright 2006. Jan H. Spyridakis. All rights reserved. Designing the Future of Communication Conducting Remote Studies of Web Users Using WebLab UX Jan H. Spyridakis, Ph.D. Professor November 2006 Overview
Copyright 2006. Jan H. Spyridakis. All rights reserved. Designing the Future of Communication Conducting Remote Studies of Web Users Using WebLab UX Jan H. Spyridakis, Ph.D. Professor November 2006 Overview
Enhancing the Cybersecurity of Federal Information and Assets through CSIP
 TECH BRIEF How BeyondTrust Helps Government Agencies Address Privileged Access Management to Improve Security Contents Introduction... 2 Achieving CSIP Objectives... 2 Steps to improve protection... 3
TECH BRIEF How BeyondTrust Helps Government Agencies Address Privileged Access Management to Improve Security Contents Introduction... 2 Achieving CSIP Objectives... 2 Steps to improve protection... 3
Peer-to-Peer Networks
 Peer-to-Peer Networks 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross Administrivia Quiz #1 is next week
Peer-to-Peer Networks 14-740: Fundamentals of Computer Networks Bill Nace Material from Computer Networking: A Top Down Approach, 6 th edition. J.F. Kurose and K.W. Ross Administrivia Quiz #1 is next week
Today. Architectural Styles
 Today Architectures for distributed systems (Chapter 2) Centralized, decentralized, hybrid Middleware Self-managing systems Lecture 2, page 1 Architectural Styles Important styles of architecture for distributed
Today Architectures for distributed systems (Chapter 2) Centralized, decentralized, hybrid Middleware Self-managing systems Lecture 2, page 1 Architectural Styles Important styles of architecture for distributed
Federated XDMoD Requirements
 Federated XDMoD Requirements Date Version Person Change 2016-04-08 1.0 draft XMS Team Initial version Summary Definitions Assumptions Data Collection Local XDMoD Installation Module Support Data Federation
Federated XDMoD Requirements Date Version Person Change 2016-04-08 1.0 draft XMS Team Initial version Summary Definitions Assumptions Data Collection Local XDMoD Installation Module Support Data Federation
SEO ISSUES FOUND ON YOUR SITE (JANUARY 2, 2017)
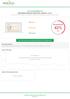 www.acornplumbing.com SEO ISSUES FOUND ON YOUR SITE (JANUARY 2, 217) This report shows the SEO issues that, when solved, will improve your site rankings and increase traffic to your website. 15 errors
www.acornplumbing.com SEO ISSUES FOUND ON YOUR SITE (JANUARY 2, 217) This report shows the SEO issues that, when solved, will improve your site rankings and increase traffic to your website. 15 errors
Maximise your return in search. Mark Lilley
 Maximise your return in search Mark Lilley 19.10.2017 Hello Mark Lilley Co- Founder & Director Groundswell groundswellgrowth.com Head of Ecommerce Chain Reaction Cycles 5 years Who are Groundswell? Ecommerce
Maximise your return in search Mark Lilley 19.10.2017 Hello Mark Lilley Co- Founder & Director Groundswell groundswellgrowth.com Head of Ecommerce Chain Reaction Cycles 5 years Who are Groundswell? Ecommerce
SEO ISSUES FOUND ON YOUR SITE (DECEMBER 30, 2016)
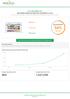 www.alpinebillings.com SEO ISSUES FOUND ON YOUR SITE (DECEMBER 30, ) This report shows the SEO issues that, when solved, will improve your site rankings and increase traffic to your website. 13 errors
www.alpinebillings.com SEO ISSUES FOUND ON YOUR SITE (DECEMBER 30, ) This report shows the SEO issues that, when solved, will improve your site rankings and increase traffic to your website. 13 errors
ISAO SO Product Outline
 Draft Document Request For Comment ISAO SO 2016 v0.2 ISAO Standards Organization Dr. Greg White, Executive Director Rick Lipsey, Deputy Director May 2, 2016 Copyright 2016, ISAO SO (Information Sharing
Draft Document Request For Comment ISAO SO 2016 v0.2 ISAO Standards Organization Dr. Greg White, Executive Director Rick Lipsey, Deputy Director May 2, 2016 Copyright 2016, ISAO SO (Information Sharing
Microsoft Architecting Microsoft Azure Solutions.
 Microsoft 70-535 Architecting Microsoft Azure Solutions https://killexams.com/pass4sure/exam-detail/70-535 QUESTION: 106 Your organization has developed and deployed several Azure App Service Web and API
Microsoft 70-535 Architecting Microsoft Azure Solutions https://killexams.com/pass4sure/exam-detail/70-535 QUESTION: 106 Your organization has developed and deployed several Azure App Service Web and API
