Informing Protocol Design Through Crowdsourcing
|
|
|
- Dominic Simpson
- 5 years ago
- Views:
Transcription
1 Informing Protocol Design Through Crowdsourcing Anna Maria Mandalari Marcelo Bagnulo Andra Lutu
2 Internet Innovation The Internet has successfully enabled multiple waves of innovation: Mobility Heterogeneity of devices Video Communication VoIP.. 2
3 Internet Innovation The Internet changes dramatically in terms of number and types of its nodes and running applications 3
4 Is the Internet Ossified? Today,many aspects appear to be set in stone Criticism: Middleboxes might filter traffic that does not conform to expected behaviors. Handley, M. (2006). Why the Internet only just works. BT Technology Journal, 24(3),
5 Is the Internet Ossified? How will Internet react to a new protocol? Understand the interaction of the new solutions with the middleboxes active along the path. 5
6 How to measure a thousand end-users? Have a friend in Google(or any other large Internet players) or Get your code to run on a thousand users machines through another delivery channel 6
7 Existing Large-Scale measurements platforms 7
8 Existing Large-Scale measurements platforms The limited and often special position of testbed nodes No possibility to deploy your own test Fixed line only Access to the results 8
9 Crowdsourcing platform Perform large-scale Internet measurement campaigns 9
10 Crowdsourcing platform 10
11 Is the Internet Ossified? Case Studies The case of the pervasive encryption TCP Fast Open HTTP/2
12 The case of pervasive encryption Many popular applications (e.g., web, Youtube video streaming) have migrated from HTTP to the HTTPS protocol Challenge: Provide encryption by default for all Internet communications Naylor, David, et al. "The Cost of the S in HTTPS." Proceedings of the 10th ACM International on Conference on emerging Networking Experiments and Technologies. ACM,
13 The case of pervasive encryption Understand the feasibility of pervasive encryption in the Internet. Understand the interaction of middleboxes with the TLS across the different TCP ports that currently use plain text protocols. 13
14 Experimental setup Establish both HTTP and TLS connections to 68 different ports: 10 well-known ports; 56 registered ports; 2 ephemeral ports. TLS connections over 68 different ports Measurement Server Measurement Agents 14
15 Experimental setup: Measurement Server LAMP model (Linux, Apache Server, MySQL relational database management system, PHP); Packets capture. 15
16 Experimental setup: Measurement Agent Common Procedure Limit of crowdsourcing platform: some information may not be available through the platform Users connect using a HTTP connection in port 80 to a webpage we provide 16
17 Experimental setup: Measurement Agent Common Procedure Users connected from Fixed line indicate the place from where they are connecting (Home, Hot Spot, University or or other institution, Company) Users connected from Mobile line indicate the technology they are using (2G, 3G, 4G) 17
18 Experimental setup: Measurement Agent Common Procedure Metadata collection 18
19 Experimental setup: Measurement Agent Common Procedure In the background, HTTP and HTTPS connections are performed from the measurement devices to our servers in all the 68 ports TLS connections over 68 different ports Measurement Server Measurement Agents 19
20 Data Set FIXED LINE: 1,165 workers; 53 different countries; 286 ASes. 20
21 Data Set MOBILE: 956 workers; 45 different countries; 183 ASes. Total of 114,228 connections Check workers User Agent The data set is freely available on 21
22 Aggregated results ERROR = (success [HTTP] success [TLS]) / success [HTTP] 25% of the users are not able to perform a TLS connection over port 80 in mobile network. 22
23 Proxies ERROR = (success [HTTP] success [TLS]) / success [HTTP] 70% of the users that use a proxy are not able to perform a TLS connection over port 80 in mobile network. 23
24 Packets analysis When users use a proxy, 90% of the SYN packets are missing 24
25 Case study: HTTP/2 From SPDY to HTTP/2
26 Case study: HTTP/2 HTTP/2: binary, instead of textual fully multiplexed connection for parallelism header compression pushing and priority
27 Case study: HTTP/2. Middleboxes compatibility HTTP/2: To encrypt or not to encrypt? Some implementations have stated that they will only support HTTP/2 when it is used over an encrypted connection (Google, Twitter ), and currently no browser supports HTTP/2 unencrypted! Implementation: HTTP/2 encrypted using ALPN (H2) HTTP/2 in clear using HTTP Upgrade mechanism (H2C) Again: Middleboxes might filter traffic that does not conform to expected behavior.
28 Experimental setup H2: Browser campaign H2 without ALPN: Android app campaign H2C: Android app campaign Check workers are not using WiFi H2C without Upgrade: Android app campaign 28
29 Experimental setup Establish both HTTP and HTTP/2 connections to 68 different ports using an Android app 29
30 Experimental setup 30
31 Data Set 628 workers; 38 different countries; 40 ISPs. The data set is freely available on 31
32 Results Browser (Fixed line) Android app (Mobile network) 32
33 Case study: TCP Fast Open (TFO) SYN + TFO Cookie Request SYN - ACK + TFO Cookie ACK APPLICATION DATA APPLICATION DATA S. Radhakrishnan, Y. Cheng, J. Chu, A. Jain, and B. Raghavan. TCP Fast Open. In Proceedings of the Seventh Conference on emerging Networking EXperiments and Technologies, page 21. ACM,
34 TCP Fast Open (TFO) SYN + TFO Cookie + APPLICATION DATA SYN - ACK (SYN & DATA) APPLICATION DATA ACK S. Radhakrishnan, Y. Cheng, J. Chu, A. Jain, and B. Raghavan. TCP Fast Open. In Proceedings of the Seventh Conference on emerging Networking EXperiments and Technologies, page 21. ACM,
35 Experimental setup Establish TFO connections to 68 different ports: 10 well-known ports; 56 registered ports; TFOExplorer 2 ephemeral ports. TFO Client (TC) TFO connections over 68 different ports TFO Server (TS) TFO Script (TSC) 35
36 TFOExplorer: TFO Needed Administrator Privileges Server NGINX LEMP model (Linux, NGinx Server, MySQL relational database management system, PHP); Packets capture. Check workers are not using a virtual machine 36
37 Data Set 46 workers; 18 different countries; 22 ISPs. The data set is freely available on 37
38 Results TC is able to perform a TFO connection (label Successful) SYN + TFO Cookie Request SYN - ACK + TFO Cookie ACK APPLICATION DATA APPLICATION DATA 38
39 Results Middleboxes drop packets with unknown TCP options and we receive the SYN without option (label No option SYN); SYN + TFO Cookie Request X SYN SYN - ACK ACK APPLICATION DATA APPLICATION DATA 39
40 Results Middleboxes drop packets with unknown TCP options and we do not receive the SYN without option (label No option no SYN); SYN + TFO Cookie Request X 40
41 Results Middleboxes drop packets with data in the SYN packet and we receive the SYN without data (label No data SYN); SYN + TFO Cookie + APPLICATION DATA X SYN SYN - ACK APPLICATION DATA ACK 41
42 Results: TFO CONNECTION 39% of the users are not able to perform a TFO connection over port 80 in mobile network. 42
43 Results: DATA IN THE SYN 50% of the users are not able to perform a TFO connection over port 80 in mobile network. 43
44 Crowdsourcing Platform Guidelines Type of test Users Time Cost Task Complexity Browser Thousands Days 0,05-0,25 $ 2/5 Android app Hundreds Days 0,40-1,00 $ 3.5/5 (no rooted devices) Linux app Dozens Week 0,80-1,00 $ 5/5 44
45 Crowdsourcing Platform Guidelines Download code: Google play Windows Linux Best moment to setup a campaign: Weekend! Surveys: 60% of the workers lie Short times are better 45
46 Conclusion Overcome several of the limitations of the crowdsourcing platforms to perform network measurements It is probably feasible to roll out TLS protection for most ports except for port 80, assuming a low failure rate (5%) New protocols at application layer need to be encrypted, in particular in mobile networks! New studies and more vantage points for TCP/UDP protocols are needed 46
47 References
48 ANY QUESTIONS? 48
49 FAQ 49
Experimental Evaluation of Transport Services CoAP, HTTP and SPDY for Internet of Things
 Experimental Evaluation of Transport Services CoAP, HTTP and SPDY for Internet of Things Laila Daniel, Markku Kojo and Mikael Latvala Department of Computer Science University of Helsinki Mosa Consulting,
Experimental Evaluation of Transport Services CoAP, HTTP and SPDY for Internet of Things Laila Daniel, Markku Kojo and Mikael Latvala Department of Computer Science University of Helsinki Mosa Consulting,
A Library and Proxy for SPDY
 A Library and Proxy for SPDY Interdisciplinary Project Andrey Uzunov Chair for Network Architectures and Services Department of Informatics Technische Universität München April 3, 2013 Andrey Uzunov (TUM)
A Library and Proxy for SPDY Interdisciplinary Project Andrey Uzunov Chair for Network Architectures and Services Department of Informatics Technische Universität München April 3, 2013 Andrey Uzunov (TUM)
A New Internet? Introduction to HTTP/2, QUIC and DOH
 A New Internet? Introduction to HTTP/2, QUIC and DOH and more LACNIC 29 - Panamá May 2018 Jordi Palet (jordi.palet@theipv6company.com) -1 Internet is Changing More and more, Internet traffic is moving
A New Internet? Introduction to HTTP/2, QUIC and DOH and more LACNIC 29 - Panamá May 2018 Jordi Palet (jordi.palet@theipv6company.com) -1 Internet is Changing More and more, Internet traffic is moving
A New Internet? RIPE76 - Marseille May Jordi Palet
 A New Internet? RIPE76 - Marseille May 2018 Jordi Palet (jordi.palet@theipv6company.com) -1 (a quick) Introduction to HTTP/2, QUIC and DOH and more RIPE76 - Marseille May 2018 Jordi Palet (jordi.palet@theipv6company.com)
A New Internet? RIPE76 - Marseille May 2018 Jordi Palet (jordi.palet@theipv6company.com) -1 (a quick) Introduction to HTTP/2, QUIC and DOH and more RIPE76 - Marseille May 2018 Jordi Palet (jordi.palet@theipv6company.com)
HTTP/2: What You Need to Know. Robert
 HTTP/2: What You Need to Know Robert Boedigheimer @boedie About Me Web developer since 1995 Pluralsight Author 3 rd Degree Black Belt, Tae Kwon Do ASP.NET MVP boedie@outlook.com @boedie weblogs.asp.net/boedie
HTTP/2: What You Need to Know Robert Boedigheimer @boedie About Me Web developer since 1995 Pluralsight Author 3 rd Degree Black Belt, Tae Kwon Do ASP.NET MVP boedie@outlook.com @boedie weblogs.asp.net/boedie
Paper survey related with web/app performance optimization and MEC. Youngseok Lee
 Paper survey related with web/app performance optimization and MEC Youngseok Lee lee@cnu.ac.kr cnu.lee@ucdavis.edu 1 1. Mobile Edge Computing: A Survey, in IEEE Internet of Things Journal, vol. 5, no.
Paper survey related with web/app performance optimization and MEC Youngseok Lee lee@cnu.ac.kr cnu.lee@ucdavis.edu 1 1. Mobile Edge Computing: A Survey, in IEEE Internet of Things Journal, vol. 5, no.
Advanced Computer Networking. CYBR 230 Jeff Shafer University of the Pacific QUIC
 CYBR 230 Jeff Shafer University of the Pacific QUIC 2 It s a Google thing. (Originally) 3 Google Engineering Motivations Goal: Decrease end-user latency on web To increase user engagement So they see more
CYBR 230 Jeff Shafer University of the Pacific QUIC 2 It s a Google thing. (Originally) 3 Google Engineering Motivations Goal: Decrease end-user latency on web To increase user engagement So they see more
HTTP/2: Ease the Transition, Remove Implementation Barriers. Robert Haynes Ronnie Dockery
 HTTP/2: Ease the Transition, Remove Implementation Barriers Robert Haynes Ronnie Dockery No One Likes Slow 3 No One Likes Slow 74% of users will leave a slow website after just 5 seconds or less 3 No One
HTTP/2: Ease the Transition, Remove Implementation Barriers Robert Haynes Ronnie Dockery No One Likes Slow 3 No One Likes Slow 74% of users will leave a slow website after just 5 seconds or less 3 No One
Passive Fingerprinting of HTTP/2 Clients
 Passive Fingerprinting of HTTP/2 Clients Elad Shuster Security Data Analyst Threat Research @ Akamai #> uname -a Elad Shuster Uptime ~ 37 years Security Data Analyst @ Akamai Technologies Deeply in love
Passive Fingerprinting of HTTP/2 Clients Elad Shuster Security Data Analyst Threat Research @ Akamai #> uname -a Elad Shuster Uptime ~ 37 years Security Data Analyst @ Akamai Technologies Deeply in love
HTTP/2 Out Of The Box
 HTTP/2 Out Of The Box Can you get it with stable Linux? Sergej Kurakin HTTP/2 was published at May 14, 2015 HTTP 1.1 was standardized in 1997 - it s 18 years old! HTTP/2 was published at May 14, 2015
HTTP/2 Out Of The Box Can you get it with stable Linux? Sergej Kurakin HTTP/2 was published at May 14, 2015 HTTP 1.1 was standardized in 1997 - it s 18 years old! HTTP/2 was published at May 14, 2015
The case for ubiquitous transport level encryption. Andrea Bittau, Mike Hamburg, Mark Handley, David Mazieres, Dan Boneh. UCL and Stanford.
 The case for ubiquitous transport level encryption Andrea Bittau, Mike Hamburg, Mark Handley, David Mazieres, Dan Boneh. UCL and Stanford. What would it take to encrypt all the traffic on the Internet,
The case for ubiquitous transport level encryption Andrea Bittau, Mike Hamburg, Mark Handley, David Mazieres, Dan Boneh. UCL and Stanford. What would it take to encrypt all the traffic on the Internet,
Schahin Rajab TCP or QUIC Which protocol is most promising for the future of the internet?
 Schahin Rajab sr2@kth.se 2016 04 20 TCP or QUIC Which protocol is most promising for the future of the internet? Table of contents 1 Introduction 3 2 Background 4 2.1 TCP 4 2.2 UDP 4 2.3 QUIC 4 2.4 HTTP
Schahin Rajab sr2@kth.se 2016 04 20 TCP or QUIC Which protocol is most promising for the future of the internet? Table of contents 1 Introduction 3 2 Background 4 2.1 TCP 4 2.2 UDP 4 2.3 QUIC 4 2.4 HTTP
Exam - Final. CSCI 1680 Computer Networks Fonseca. Closed Book. Maximum points: 100 NAME: 1. TCP Congestion Control [15 pts]
![Exam - Final. CSCI 1680 Computer Networks Fonseca. Closed Book. Maximum points: 100 NAME: 1. TCP Congestion Control [15 pts] Exam - Final. CSCI 1680 Computer Networks Fonseca. Closed Book. Maximum points: 100 NAME: 1. TCP Congestion Control [15 pts]](/thumbs/76/73116036.jpg) CSCI 1680 Computer Networks Fonseca Exam - Final Due: 11:00am, May 10th, 2012 Closed Book. Maximum points: 100 NAME: 1. TCP Congestion Control [15 pts] a. TCP Tahoe and Reno have two congestion-window
CSCI 1680 Computer Networks Fonseca Exam - Final Due: 11:00am, May 10th, 2012 Closed Book. Maximum points: 100 NAME: 1. TCP Congestion Control [15 pts] a. TCP Tahoe and Reno have two congestion-window
SHARE THIS WHITEPAPER. Fastest Website Acceleration for New HTTP Protocol with Alteon NG and Advanced HTTP/2 Gateway Whitepaper
 SHARE THIS WHITEPAPER Fastest Website Acceleration for New HTTP Protocol with Alteon NG and Advanced HTTP/2 Gateway Whitepaper Table of Contents Executive Summary...3 The Road to HTTP/2...3 How HTTP/2
SHARE THIS WHITEPAPER Fastest Website Acceleration for New HTTP Protocol with Alteon NG and Advanced HTTP/2 Gateway Whitepaper Table of Contents Executive Summary...3 The Road to HTTP/2...3 How HTTP/2
Network Security. Thierry Sans
 Network Security Thierry Sans HTTP SMTP DNS BGP The Protocol Stack Application TCP UDP Transport IPv4 IPv6 ICMP Network ARP Link Ethernet WiFi The attacker is capable of confidentiality integrity availability
Network Security Thierry Sans HTTP SMTP DNS BGP The Protocol Stack Application TCP UDP Transport IPv4 IPv6 ICMP Network ARP Link Ethernet WiFi The attacker is capable of confidentiality integrity availability
Solving HTTP Problems With Code and Protocols NATASHA ROONEY
 Solving HTTP Problems With Code and Protocols NATASHA ROONEY Web HTTP TLS TCP IP 7. Application Data HTTP / IMAP 6. Data Presentation, Encryption SSL / TLS 5. Session and connection management - 4. Transport
Solving HTTP Problems With Code and Protocols NATASHA ROONEY Web HTTP TLS TCP IP 7. Application Data HTTP / IMAP 6. Data Presentation, Encryption SSL / TLS 5. Session and connection management - 4. Transport
CCNA 1 Chapter 7 v5.0 Exam Answers 2013
 CCNA 1 Chapter 7 v5.0 Exam Answers 2013 1 A PC is downloading a large file from a server. The TCP window is 1000 bytes. The server is sending the file using 100-byte segments. How many segments will the
CCNA 1 Chapter 7 v5.0 Exam Answers 2013 1 A PC is downloading a large file from a server. The TCP window is 1000 bytes. The server is sending the file using 100-byte segments. How many segments will the
Introduction to data centers
 Introduction to data centers Paolo Giaccone Notes for the class on Switching technologies for data centers Politecnico di Torino December 2017 Cloud computing Section 1 Cloud computing Giaccone (Politecnico
Introduction to data centers Paolo Giaccone Notes for the class on Switching technologies for data centers Politecnico di Torino December 2017 Cloud computing Section 1 Cloud computing Giaccone (Politecnico
Investigating Transparent Web Proxies in Cellular Networks
 Investigating Transparent Web Proxies in Cellular Networks Xing Xu, Yurong Jiang, Tobias Flach, Ethan Katz-Bassett, David Choffnes, Ramesh Govindan USC & Northeastern University March 20, 2015 Introduction
Investigating Transparent Web Proxies in Cellular Networks Xing Xu, Yurong Jiang, Tobias Flach, Ethan Katz-Bassett, David Choffnes, Ramesh Govindan USC & Northeastern University March 20, 2015 Introduction
Validate Pre-Deployment and Live Networks and Applications
 IxChariot 8 Validate Pre-Deployment and Live Networks and Applications Key Features New HTML5-based web interface zero client installation; browser-based IxChariot 8 is a new version of the industry's
IxChariot 8 Validate Pre-Deployment and Live Networks and Applications Key Features New HTML5-based web interface zero client installation; browser-based IxChariot 8 is a new version of the industry's
Scaling Internet TV Content Delivery ALEX GUTARIN DIRECTOR OF ENGINEERING, NETFLIX
 Scaling Internet TV Content Delivery ALEX GUTARIN DIRECTOR OF ENGINEERING, NETFLIX Inventing Internet TV Available in more than 190 countries 104+ million subscribers Lots of Streaming == Lots of Traffic
Scaling Internet TV Content Delivery ALEX GUTARIN DIRECTOR OF ENGINEERING, NETFLIX Inventing Internet TV Available in more than 190 countries 104+ million subscribers Lots of Streaming == Lots of Traffic
Lec 17 Multimedia Transport: RTP, TCP/HTTP and QUIC
 Multimedia Communication Lec 17 Multimedia Transport: RTP, TCP/HTTP and QUIC Zhu Li Course Web: http://l.web.umkc.edu/lizhu/teaching/2016sp.video-communication/main.html Z. Li, Multimedia Communciation,
Multimedia Communication Lec 17 Multimedia Transport: RTP, TCP/HTTP and QUIC Zhu Li Course Web: http://l.web.umkc.edu/lizhu/teaching/2016sp.video-communication/main.html Z. Li, Multimedia Communciation,
Web as a Distributed System
 Web as a Distributed System The World Wide Web is a large distributed system. In 1998 comprises 70-75% of Internet traffic. With large transfers of streaming media and p2p, no longer a majority of bytes,
Web as a Distributed System The World Wide Web is a large distributed system. In 1998 comprises 70-75% of Internet traffic. With large transfers of streaming media and p2p, no longer a majority of bytes,
QOE: A MICRO AND MACRO PERSPECTIVE
 QOE: A MICRO AND MACRO PERSPECTIVE Henning Schulzrinne (with Kyung-Hwa Kim, Hyunwoo Nam, Vishal Singh, Daniel Song) Columbia University Micro vs. Macro Time & space local (user, HH) Internet-wide short-term
QOE: A MICRO AND MACRO PERSPECTIVE Henning Schulzrinne (with Kyung-Hwa Kim, Hyunwoo Nam, Vishal Singh, Daniel Song) Columbia University Micro vs. Macro Time & space local (user, HH) Internet-wide short-term
How to Make the Client IP Address Available to the Back-end Server
 How to Make the Client IP Address Available to the Back-end Server For Layer 4 - UDP and Layer 4 - TCP services, the actual client IP address is passed to the server in the TCP header. No further configuration
How to Make the Client IP Address Available to the Back-end Server For Layer 4 - UDP and Layer 4 - TCP services, the actual client IP address is passed to the server in the TCP header. No further configuration
Is it Still Possible to Extend TCP?
 Is it Still Possible to Extend TCP? Michio Honda, Keio University Yoshifumi Nishida, Keio University Costin Raiciu, Universitatea Politehnica Bucuresti Adam Greenhalgh, University College London Mark Handley,
Is it Still Possible to Extend TCP? Michio Honda, Keio University Yoshifumi Nishida, Keio University Costin Raiciu, Universitatea Politehnica Bucuresti Adam Greenhalgh, University College London Mark Handley,
RKN 2015 Application Layer Short Summary
 RKN 2015 Application Layer Short Summary HTTP standard version now: 1.1 (former 1.0 HTTP /2.0 in draft form, already used HTTP Requests Headers and body counterpart: answer Safe methods (requests): GET,
RKN 2015 Application Layer Short Summary HTTP standard version now: 1.1 (former 1.0 HTTP /2.0 in draft form, already used HTTP Requests Headers and body counterpart: answer Safe methods (requests): GET,
Studying TLS Usage in Android Apps
 Studying TLS Usage in Android Apps Abbas Razaghpanah, Arian Akhavan Niaki, Narseo Vallina-Rodriguez, Srikanth Sundaresan, Johanna Amann, Phillipa Gill Paper: ACM CoNext 2017 Encryption is Everywhere However
Studying TLS Usage in Android Apps Abbas Razaghpanah, Arian Akhavan Niaki, Narseo Vallina-Rodriguez, Srikanth Sundaresan, Johanna Amann, Phillipa Gill Paper: ACM CoNext 2017 Encryption is Everywhere However
(h)icn Socket Library for HTTP Leveraging (h)icn socket library for carrying HTTP messages
 (h)icn Socket Library for HTTP Leveraging (h)icn socket library for carrying HTTP messages Mauro Sardara, Luca Muscariello, Alberto Compagno Software Engineer ICNRG Interim Meeting, London, 18 th of March
(h)icn Socket Library for HTTP Leveraging (h)icn socket library for carrying HTTP messages Mauro Sardara, Luca Muscariello, Alberto Compagno Software Engineer ICNRG Interim Meeting, London, 18 th of March
Overview Content Delivery Computer Networking Lecture 15: The Web Peter Steenkiste. Fall 2016
 Overview Content Delivery 15-441 15-441 Computer Networking 15-641 Lecture 15: The Web Peter Steenkiste Fall 2016 www.cs.cmu.edu/~prs/15-441-f16 Web Protocol interactions HTTP versions Caching Cookies
Overview Content Delivery 15-441 15-441 Computer Networking 15-641 Lecture 15: The Web Peter Steenkiste Fall 2016 www.cs.cmu.edu/~prs/15-441-f16 Web Protocol interactions HTTP versions Caching Cookies
CSE 333 Lecture HTTP
 CSE 333 Lecture 19 -- HTTP Hal Perkins Paul G. Allen School of Computer Science & Engineering University of Washington Administrivia HW4 due a week from Thursday - How s it look? Today: http; finish networking/web
CSE 333 Lecture 19 -- HTTP Hal Perkins Paul G. Allen School of Computer Science & Engineering University of Washington Administrivia HW4 due a week from Thursday - How s it look? Today: http; finish networking/web
CNIT 129S: Securing Web Applications. Ch 3: Web Application Technologies
 CNIT 129S: Securing Web Applications Ch 3: Web Application Technologies HTTP Hypertext Transfer Protocol (HTTP) Connectionless protocol Client sends an HTTP request to a Web server Gets an HTTP response
CNIT 129S: Securing Web Applications Ch 3: Web Application Technologies HTTP Hypertext Transfer Protocol (HTTP) Connectionless protocol Client sends an HTTP request to a Web server Gets an HTTP response
Relay Proxy User Guide
 Relay Proxy User Guide DBL Technology Company Limited www.dbltek.com sales@dbltek.com support@dbltek.com 2016/5/30 Relay Proxy Relay Proxy is a server software developed by DBL Technology. Its main purposed
Relay Proxy User Guide DBL Technology Company Limited www.dbltek.com sales@dbltek.com support@dbltek.com 2016/5/30 Relay Proxy Relay Proxy is a server software developed by DBL Technology. Its main purposed
Scan Report Executive Summary
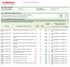 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: WineDirect ASV Company: Comodo CA Limited 10/11/2018 Scan expiration date: 01/09/2019 Part 2. Summary
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: WineDirect ASV Company: Comodo CA Limited 10/11/2018 Scan expiration date: 01/09/2019 Part 2. Summary
What HTTP/2 means to Java Developers?
 What HTTP/2 means to Java Developers? May 2016 David Delabassee @delabassee Oracle Copyright 2016, Oracle and/or its affiliates. All rights reserved. About me Copyright 2016, Oracle and/or its affiliates.
What HTTP/2 means to Java Developers? May 2016 David Delabassee @delabassee Oracle Copyright 2016, Oracle and/or its affiliates. All rights reserved. About me Copyright 2016, Oracle and/or its affiliates.
Review for Internet Introduction
 Review for Internet Introduction What s the Internet: Two Views View 1: Nuts and Bolts View billions of connected hosts routers and switches protocols control sending, receiving of messages network of
Review for Internet Introduction What s the Internet: Two Views View 1: Nuts and Bolts View billions of connected hosts routers and switches protocols control sending, receiving of messages network of
Scan Report Executive Summary
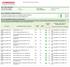 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 06/08/2018 Scan expiration date: 09/06/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 06/08/2018 Scan expiration date: 09/06/2018 Part 2. Component
AlertMobile Configuration Guide
 MICROMEDIA INTERNATIONAL ALERT - remote alarm management ALERT: AlertMobile Configuration Guide Author: GL Update: GL Pages: 36 Date: 04/07/2018 Version: 3.7.3 AlertMobile Configuration Guide Réf. : HOWTO-Configure
MICROMEDIA INTERNATIONAL ALERT - remote alarm management ALERT: AlertMobile Configuration Guide Author: GL Update: GL Pages: 36 Date: 04/07/2018 Version: 3.7.3 AlertMobile Configuration Guide Réf. : HOWTO-Configure
HTTP TRAFFIC CONSISTS OF REQUESTS AND RESPONSES. All HTTP traffic can be
 3 HTTP Transactions HTTP TRAFFIC CONSISTS OF REQUESTS AND RESPONSES. All HTTP traffic can be associated with the task of requesting content or responding to those requests. Every HTTP message sent from
3 HTTP Transactions HTTP TRAFFIC CONSISTS OF REQUESTS AND RESPONSES. All HTTP traffic can be associated with the task of requesting content or responding to those requests. Every HTTP message sent from
Web Mechanisms. Draft: 2/23/13 6:54 PM 2013 Christopher Vickery
 Web Mechanisms Draft: 2/23/13 6:54 PM 2013 Christopher Vickery Introduction While it is perfectly possible to create web sites that work without knowing any of their underlying mechanisms, web developers
Web Mechanisms Draft: 2/23/13 6:54 PM 2013 Christopher Vickery Introduction While it is perfectly possible to create web sites that work without knowing any of their underlying mechanisms, web developers
Cisco Intelligent WAN with Akamai Connect
 Data Sheet Cisco Intelligent WAN with Akamai Connect Deliver consistent, LAN-like user experiences using application acceleration and WAN optimization while lowering bandwidth costs. Users get world-class
Data Sheet Cisco Intelligent WAN with Akamai Connect Deliver consistent, LAN-like user experiences using application acceleration and WAN optimization while lowering bandwidth costs. Users get world-class
OSI Transport Layer. objectives
 LECTURE 5 OSI Transport Layer objectives 1. Roles of the Transport Layer 1. segmentation of data 2. error detection 3. Multiplexing of upper layer application using port numbers 2. The TCP protocol Communicating
LECTURE 5 OSI Transport Layer objectives 1. Roles of the Transport Layer 1. segmentation of data 2. error detection 3. Multiplexing of upper layer application using port numbers 2. The TCP protocol Communicating
Connecting with Computer Science Chapter 5 Review: Chapter Summary:
 Chapter Summary: The Internet has revolutionized the world. The internet is just a giant collection of: WANs and LANs. The internet is not owned by any single person or entity. You connect to the Internet
Chapter Summary: The Internet has revolutionized the world. The internet is just a giant collection of: WANs and LANs. The internet is not owned by any single person or entity. You connect to the Internet
Adaptive Bit Rate (ABR) Video Detection and Control
 OVERVIEW Adaptive Bit Rate (ABR) Video Detection and Control In recent years, Internet traffic has changed dramatically and this has impacted service providers and their ability to manage network traffic.
OVERVIEW Adaptive Bit Rate (ABR) Video Detection and Control In recent years, Internet traffic has changed dramatically and this has impacted service providers and their ability to manage network traffic.
Understanding Traffic Decryption
 The following topics provide an overview of SSL inspection, describe the prerequisites for SSL inspection configuration, and detail deployment scenarios. Traffic Decryption Overview, page 1 SSL Handshake
The following topics provide an overview of SSL inspection, describe the prerequisites for SSL inspection configuration, and detail deployment scenarios. Traffic Decryption Overview, page 1 SSL Handshake
SPDY. HTML5. Make the web fast
 SPDY. HTML5 Make the web fast Christian Horny GOOGLE: @igrigorik Devcon Usability Engineering DELAY USER REACTION 0-100 ms Instant 100 300 ms Feels sluggish 300-1000 ms Machine is working... 1 s+ Mental
SPDY. HTML5 Make the web fast Christian Horny GOOGLE: @igrigorik Devcon Usability Engineering DELAY USER REACTION 0-100 ms Instant 100 300 ms Feels sluggish 300-1000 ms Machine is working... 1 s+ Mental
Corrigendum 3. Tender Number: 10/ dated
 (A premier Public Sector Bank) Information Technology Division Head Office, Mangalore Corrigendum 3 Tender Number: 10/2016-17 dated 07.09.2016 for Supply, Installation and Maintenance of Distributed Denial
(A premier Public Sector Bank) Information Technology Division Head Office, Mangalore Corrigendum 3 Tender Number: 10/2016-17 dated 07.09.2016 for Supply, Installation and Maintenance of Distributed Denial
Adaptive Video Acceleration. White Paper. 1 P a g e
 Adaptive Video Acceleration White Paper 1 P a g e Version 1.0 Veronique Phan Dir. Technical Sales July 16 th 2014 2 P a g e 1. Preface Giraffic is the enabler of Next Generation Internet TV broadcast technology
Adaptive Video Acceleration White Paper 1 P a g e Version 1.0 Veronique Phan Dir. Technical Sales July 16 th 2014 2 P a g e 1. Preface Giraffic is the enabler of Next Generation Internet TV broadcast technology
SharkFest 17 Europe. 20 QUIC Dissection. Using Wireshark to Understand QUIC Quickly. Megumi Takeshita. ikeriri network service
 SharkFest 17 Europe 20 QUIC Dissection Using Wireshark to Understand QUIC Quickly ParkSuite Classroom 11 November 2017 11:15am-12:30pm Megumi Takeshita ikeriri network service supplimental files http://www.ikeriri.ne.jp/sharkfest
SharkFest 17 Europe 20 QUIC Dissection Using Wireshark to Understand QUIC Quickly ParkSuite Classroom 11 November 2017 11:15am-12:30pm Megumi Takeshita ikeriri network service supplimental files http://www.ikeriri.ne.jp/sharkfest
Networked Multimedia and Internet Video. Colin Perkins
 Networked Multimedia and Internet Video Colin Perkins IP video will represent 80% of all traffic by 2019, up from 67% in 2014 Source: Cisco Visual Networking Index, 2015 2 History MPEG TS YouTube MPEG
Networked Multimedia and Internet Video Colin Perkins IP video will represent 80% of all traffic by 2019, up from 67% in 2014 Source: Cisco Visual Networking Index, 2015 2 History MPEG TS YouTube MPEG
Quickly Starting Media Streams Using QUIC
 Quickly Starting Media Streams Using QUIC Packet Video Workshop 2018 Şevket Arısu and Ali C. Begen Agenda Motivation and our goal Previous work and our contributions Approach, setup and evaluation Results
Quickly Starting Media Streams Using QUIC Packet Video Workshop 2018 Şevket Arısu and Ali C. Begen Agenda Motivation and our goal Previous work and our contributions Approach, setup and evaluation Results
Networking with NSURLSession
 System Frameworks #WWDC15 Networking with NSURLSession Session 711 Luke Case Software Engineer Andreas Garkuscha Software Engineer Dan Vinegrad Software Engineer 2015 Apple Inc. All rights reserved. Redistribution
System Frameworks #WWDC15 Networking with NSURLSession Session 711 Luke Case Software Engineer Andreas Garkuscha Software Engineer Dan Vinegrad Software Engineer 2015 Apple Inc. All rights reserved. Redistribution
Matthew Harris Senior Project Proposal getnote The Mobile Application
 Matthew Harris Senior Project Proposal getnote The Mobile Application 1 Table of Contents Background and Motivation 3 Problems to be Addressed: 3 Solution: 4 Methodology: 4 Goal: 5 Deliverables: 5 Justification:
Matthew Harris Senior Project Proposal getnote The Mobile Application 1 Table of Contents Background and Motivation 3 Problems to be Addressed: 3 Solution: 4 Methodology: 4 Goal: 5 Deliverables: 5 Justification:
Why WAN accelerators (still) matter? Andrea Dainese Data Center Engineer
 Why WAN accelerators (still) matter? Data Center Engineer Presentation Data Center Engineer @ Cerved Group SpA Red Hat RHCE VMware VCP-DCV NetApp NCIE-SAN Cisco CCIE Who is Andrea Dainese Cisco Architecture
Why WAN accelerators (still) matter? Data Center Engineer Presentation Data Center Engineer @ Cerved Group SpA Red Hat RHCE VMware VCP-DCV NetApp NCIE-SAN Cisco CCIE Who is Andrea Dainese Cisco Architecture
TIBCO Cloud Integration Security Overview
 TIBCO Cloud Integration Security Overview TIBCO Cloud Integration is secure, best-in-class Integration Platform as a Service (ipaas) software offered in a multi-tenant SaaS environment with centralized
TIBCO Cloud Integration Security Overview TIBCO Cloud Integration is secure, best-in-class Integration Platform as a Service (ipaas) software offered in a multi-tenant SaaS environment with centralized
Protocol Buffers, grpc
 Protocol Buffers, grpc Szolgáltatásorientált rendszerintegráció Service-Oriented System Integration Dr. Balázs Simon BME, IIT Outline Remote communication application level vs. transport level protocols
Protocol Buffers, grpc Szolgáltatásorientált rendszerintegráció Service-Oriented System Integration Dr. Balázs Simon BME, IIT Outline Remote communication application level vs. transport level protocols
STATEFUL TCP/UDP traffic generation and analysis
 XENATM STATEFUL TCP/UDP traffic generation and analysis Ideal for validating firewalls, switches, routers, NAT routers, proxies, load-balancers, bandwidth shapers and more. VULCAN LAYER 4-7 GIGABIT ETHERNET
XENATM STATEFUL TCP/UDP traffic generation and analysis Ideal for validating firewalls, switches, routers, NAT routers, proxies, load-balancers, bandwidth shapers and more. VULCAN LAYER 4-7 GIGABIT ETHERNET
Content Deployment and Caching Techniques in Africa
 Content Deployment and Caching Techniques in Africa Presentation to the AfPIF Peering Coordinators Day Dar Es Salaam 2011 Mike Blanche 1 Agenda Current Content Hosting Situation Content Hosting Content
Content Deployment and Caching Techniques in Africa Presentation to the AfPIF Peering Coordinators Day Dar Es Salaam 2011 Mike Blanche 1 Agenda Current Content Hosting Situation Content Hosting Content
HTTP/2. HTML5. Make the web fast. Christian Horny
 HTTP/2. HTML5 Make the web fast Christian Horny HTTP/2 goals! Improve end-user perceived latency! Address the "head of line blocking"! Not require multiple connections! Retain the semantics of HTTP/1.1
HTTP/2. HTML5 Make the web fast Christian Horny HTTP/2 goals! Improve end-user perceived latency! Address the "head of line blocking"! Not require multiple connections! Retain the semantics of HTTP/1.1
IETF/W3C/etc De-facto STD Overview (in My Case)
 IETF/W3C/etc De-facto STD Overview (in My Case) 株式会社レピダム林達也 (@lef ) HAYASHI, Tatsuya / Lepidum Co. Ltd. IETF 標準化セミナー (2015/3/11) Speaker's Position Lepidum Co. Ltd. ( ) President, Founder and Owner Internet
IETF/W3C/etc De-facto STD Overview (in My Case) 株式会社レピダム林達也 (@lef ) HAYASHI, Tatsuya / Lepidum Co. Ltd. IETF 標準化セミナー (2015/3/11) Speaker's Position Lepidum Co. Ltd. ( ) President, Founder and Owner Internet
Microsoft Microsoft TS: MS Internet Security & Acceleration Server 2006, Configuring. Practice Test. Version:
 Microsoft 70-351 Microsoft 70-351 TS: MS Internet Security & Acceleration Server 2006, Configuring Practice Test Version: 2.2 QUESTION NO: 1 Your network consists of a single Active Directory domain named
Microsoft 70-351 Microsoft 70-351 TS: MS Internet Security & Acceleration Server 2006, Configuring Practice Test Version: 2.2 QUESTION NO: 1 Your network consists of a single Active Directory domain named
This release of the product includes these new features that have been added since NGFW 5.5.
 Release Notes Revision B McAfee Next Generation Firewall 5.7.3 Contents About this release New features Enhancements Known limitations Resolved issues System requirements Installation instructions Upgrade
Release Notes Revision B McAfee Next Generation Firewall 5.7.3 Contents About this release New features Enhancements Known limitations Resolved issues System requirements Installation instructions Upgrade
The Security Impact of HTTPS Interception
 The Security Impact of HTTPS Interception Zakir Durumeric, Zane Ma, Drew Springall, Richard Barnes, Nick Sullivan, Elie Bursztein, Michael Bailey, J. Alex Halderman, Vern Paxson University of Michigan,
The Security Impact of HTTPS Interception Zakir Durumeric, Zane Ma, Drew Springall, Richard Barnes, Nick Sullivan, Elie Bursztein, Michael Bailey, J. Alex Halderman, Vern Paxson University of Michigan,
Web Optimization of QUIC under Wireless Network
 AMSE JOURNALS-AMSE IIETA publication-2017-series: Advances B; Vol. 60; N 1; pp161-173 Submitted Jan. 2017; Revised March 15, 2017, Accepted April 15, 2017 https://doi.org/10.18280/ama_b.600110 Web Optimization
AMSE JOURNALS-AMSE IIETA publication-2017-series: Advances B; Vol. 60; N 1; pp161-173 Submitted Jan. 2017; Revised March 15, 2017, Accepted April 15, 2017 https://doi.org/10.18280/ama_b.600110 Web Optimization
This release of the product includes these new features that have been added since NGFW 5.5.
 Release Notes Revision A McAfee Next Generation Firewall 5.7.10 Contents About this release New features Enhancements Known limitations Resolved issues System requirements Installation instructions Upgrade
Release Notes Revision A McAfee Next Generation Firewall 5.7.10 Contents About this release New features Enhancements Known limitations Resolved issues System requirements Installation instructions Upgrade
Question No: 2 Which identifier is used to describe the application or process that submitted a log message?
 Volume: 65 Questions Question No: 1 Which definition of a fork in Linux is true? A. daemon to execute scheduled commands B. parent directory name of a file pathname C. macros for manipulating CPU sets
Volume: 65 Questions Question No: 1 Which definition of a fork in Linux is true? A. daemon to execute scheduled commands B. parent directory name of a file pathname C. macros for manipulating CPU sets
How the Web Works. Chapter 1. Modified by Marissa Schmidt Pearson
 How the Web Works Chapter 1 Modified by Marissa Schmidt 2015 Pearson Fundamentals ofhttp://www.funwebdev.com Web Development Objectives 1 Definitions and History 2 Internet Protocols 3 Client-Server Model
How the Web Works Chapter 1 Modified by Marissa Schmidt 2015 Pearson Fundamentals ofhttp://www.funwebdev.com Web Development Objectives 1 Definitions and History 2 Internet Protocols 3 Client-Server Model
Measuring KSA Broadband
 Measuring KSA Broadband Meqyas, Q2 218 Report In 217, the CITC in partnership with SamKnows launched a project to measure internet performance. The project, named Meqyas, gives internet users in Saudi
Measuring KSA Broadband Meqyas, Q2 218 Report In 217, the CITC in partnership with SamKnows launched a project to measure internet performance. The project, named Meqyas, gives internet users in Saudi
This release of the product includes these new features that have been added since NGFW 5.5.
 Release Notes Revision A McAfee Next Generation Firewall 5.7.9 Contents About this release New features Enhancements Known limitations Resolved issues System requirements Installation instructions Upgrade
Release Notes Revision A McAfee Next Generation Firewall 5.7.9 Contents About this release New features Enhancements Known limitations Resolved issues System requirements Installation instructions Upgrade
An In-depth Study of LTE: Effect of Network Protocol and Application Behavior on Performance
 An In-depth Study of LTE: Effect of Network Protocol and Application Behavior on Performance Authors: Junxian Huang, Feng Qian, Yihua Guo, Yuanyuan Zhou, Qiang Xu, Z. Morley Mao, Subhabrata Sen, Oliver
An In-depth Study of LTE: Effect of Network Protocol and Application Behavior on Performance Authors: Junxian Huang, Feng Qian, Yihua Guo, Yuanyuan Zhou, Qiang Xu, Z. Morley Mao, Subhabrata Sen, Oliver
SPDY - A Web Protocol. Mike Belshe Velocity, Dec 2009
 SPDY - A Web Protocol Mike Belshe Velocity, Dec 2009 What is SPDY? Concept SPDY is an application layer protocol for transporting content over the web with reduced latency. Basic Features 1. Multiplexed
SPDY - A Web Protocol Mike Belshe Velocity, Dec 2009 What is SPDY? Concept SPDY is an application layer protocol for transporting content over the web with reduced latency. Basic Features 1. Multiplexed
The State of TLS in httpd 2.4. William A. Rowe Jr.
 The State of TLS in httpd 2.4 William A. Rowe Jr. wrowe@apache.org Getting Started Web references have grown stale Web references have grown stale Guidance is changing annually https://www.ssllabs.com/ssltest/analyze.ht
The State of TLS in httpd 2.4 William A. Rowe Jr. wrowe@apache.org Getting Started Web references have grown stale Web references have grown stale Guidance is changing annually https://www.ssllabs.com/ssltest/analyze.ht
FlexiWeb: Network-Aware Compaction for Accelerating Mobile Web
 FlexiWeb: Network-Aware Compaction for Accelerating Mobile Web What s the impact of web latency? 100ms 1% Delay sales Source : https://speakerdeck.com/deanohume/faster-mobilewebsites! 100ms 1% Delay revenue
FlexiWeb: Network-Aware Compaction for Accelerating Mobile Web What s the impact of web latency? 100ms 1% Delay sales Source : https://speakerdeck.com/deanohume/faster-mobilewebsites! 100ms 1% Delay revenue
Hypertext Transport Protocol
 Hypertext Transport Protocol CSE 333 Summer 2018 Instructor: Hal Perkins Teaching Assistants: Renshu Gu William Kim Soumya Vasisht Administriia Section tomorrow: pthread tutorial/demo Followup exercise
Hypertext Transport Protocol CSE 333 Summer 2018 Instructor: Hal Perkins Teaching Assistants: Renshu Gu William Kim Soumya Vasisht Administriia Section tomorrow: pthread tutorial/demo Followup exercise
Testing & Assuring Mobile End User Experience Before Production Neotys
 Testing & Assuring Mobile End User Experience Before Production Neotys Henrik Rexed Agenda Introduction The challenges Best practices NeoLoad mobile capabilities Mobile devices are used more and more At
Testing & Assuring Mobile End User Experience Before Production Neotys Henrik Rexed Agenda Introduction The challenges Best practices NeoLoad mobile capabilities Mobile devices are used more and more At
jetnexus Virtual Load Balancer
 jetnexus Virtual Load Balancer Mitigate the Risk of Downtime and Optimise Application Delivery We were looking for a robust yet easy to use solution that would fit in with our virtualisation policy and
jetnexus Virtual Load Balancer Mitigate the Risk of Downtime and Optimise Application Delivery We were looking for a robust yet easy to use solution that would fit in with our virtualisation policy and
Network Programming With Go Essential Skills For Using And Securing Networks
 Network Programming With Go Essential Skills For Using And Securing Networks We have made it easy for you to find a PDF Ebooks without any digging. And by having access to our ebooks online or by storing
Network Programming With Go Essential Skills For Using And Securing Networks We have made it easy for you to find a PDF Ebooks without any digging. And by having access to our ebooks online or by storing
Computer Science 461 Midterm Exam March 14, :00-10:50am
 NAME: Login name: Computer Science 461 Midterm Exam March 14, 2012 10:00-10:50am This test has seven (7) questions, each worth ten points. Put your name on every page, and write out and sign the Honor
NAME: Login name: Computer Science 461 Midterm Exam March 14, 2012 10:00-10:50am This test has seven (7) questions, each worth ten points. Put your name on every page, and write out and sign the Honor
Fig. 2: Time gap between retransmission clusters for different connections.
 Domain-Sharding for Faster HTTP/2 in Lossy Cellular Networks Utkarsh Goel, Moritz Steiner, Mike P. Wittie, Stephen Ludin, Martin Flack Akamai Technologies, Inc. {ugoel, moritz, mflack, sludin}@akamai.com
Domain-Sharding for Faster HTTP/2 in Lossy Cellular Networks Utkarsh Goel, Moritz Steiner, Mike P. Wittie, Stephen Ludin, Martin Flack Akamai Technologies, Inc. {ugoel, moritz, mflack, sludin}@akamai.com
This FAQ is only applicable for hostings ordered after 23/6/2010
 Webhosting FAQ This FAQ is only applicable for hostings ordered after 23/6/2010 1. How do I access my Webhosting control panel?... 1 2. On which server is my hosting set up (IP)?... 4 3. How do I install
Webhosting FAQ This FAQ is only applicable for hostings ordered after 23/6/2010 1. How do I access my Webhosting control panel?... 1 2. On which server is my hosting set up (IP)?... 4 3. How do I install
McAfee Network Security Platform 8.3
 8.3.7.68-8.3.7.55-8.3.7.14 Manager-Virtual IPS Release Notes McAfee Network Security Platform 8.3 Revision A Contents About this release New features Enhancements Resolved issues Installation instructions
8.3.7.68-8.3.7.55-8.3.7.14 Manager-Virtual IPS Release Notes McAfee Network Security Platform 8.3 Revision A Contents About this release New features Enhancements Resolved issues Installation instructions
BlackBerry UEM Configuration Guide
 BlackBerry UEM Configuration Guide 12.9 2018-11-05Z 2 Contents Getting started... 7 Configuring BlackBerry UEM for the first time... 7 Configuration tasks for managing BlackBerry OS devices... 9 Administrator
BlackBerry UEM Configuration Guide 12.9 2018-11-05Z 2 Contents Getting started... 7 Configuring BlackBerry UEM for the first time... 7 Configuration tasks for managing BlackBerry OS devices... 9 Administrator
DYNAMIC ADAPTIVE STREAMING OVER HTTP/2.0
 DYNAMIC ADAPTIVE STREAMING OVER HTTP/2.0 Christopher Mueller, Stefan Lederer, Christian Timmerer, and Hermann Hellwagner Alpen-Adria-Universität Klagenfurt Universitätsstraße 65-67 9020 Klagenfurt am Wörthersee,
DYNAMIC ADAPTIVE STREAMING OVER HTTP/2.0 Christopher Mueller, Stefan Lederer, Christian Timmerer, and Hermann Hellwagner Alpen-Adria-Universität Klagenfurt Universitätsstraße 65-67 9020 Klagenfurt am Wörthersee,
Business Data Networks and Security 10th Edition by Panko Test Bank
 Business Data Networks and Security 10th Edition by Panko Test Bank Chapter 2 Network Standards 1) Internet standards are published as. A) RFCs B) IETFs C) TCP/IPs D) Internet Protocols Question: 1a Objective:
Business Data Networks and Security 10th Edition by Panko Test Bank Chapter 2 Network Standards 1) Internet standards are published as. A) RFCs B) IETFs C) TCP/IPs D) Internet Protocols Question: 1a Objective:
Internet Content Distribution
 Internet Content Distribution Chapter 1: Introduction Jussi Kangasharju Chapter Outline Introduction into content distribution Basic concepts TCP DNS HTTP Outline of the rest of the course Kangasharju:
Internet Content Distribution Chapter 1: Introduction Jussi Kangasharju Chapter Outline Introduction into content distribution Basic concepts TCP DNS HTTP Outline of the rest of the course Kangasharju:
SECURED SOCIAL TUBE FOR VIDEO SHARING IN OSN SYSTEM
 ABSTRACT: SECURED SOCIAL TUBE FOR VIDEO SHARING IN OSN SYSTEM J.Priyanka 1, P.Rajeswari 2 II-M.E(CS) 1, H.O.D / ECE 2, Dhanalakshmi Srinivasan Engineering College, Perambalur. Recent years have witnessed
ABSTRACT: SECURED SOCIAL TUBE FOR VIDEO SHARING IN OSN SYSTEM J.Priyanka 1, P.Rajeswari 2 II-M.E(CS) 1, H.O.D / ECE 2, Dhanalakshmi Srinivasan Engineering College, Perambalur. Recent years have witnessed
INGI1341: Project 2 Analysis of a website
 INGI3141:PROJECT 2 1 INGI1341: Project 2 Analysis of a website Sergio Alejandro Chávez Cárdenas Abstract The details of a remote website sopitas.com are analysed and its responses over the Internet are
INGI3141:PROJECT 2 1 INGI1341: Project 2 Analysis of a website Sergio Alejandro Chávez Cárdenas Abstract The details of a remote website sopitas.com are analysed and its responses over the Internet are
CSCI 466 Midterm Networks Fall 2013
 CSCI 466 Midterm Networks Fall 2013 Name: This exam consists of 6 problems on the following 7 pages. You may use your single-sided hand-written 8 ½ x 11 note sheet and a calculator during the exam. No
CSCI 466 Midterm Networks Fall 2013 Name: This exam consists of 6 problems on the following 7 pages. You may use your single-sided hand-written 8 ½ x 11 note sheet and a calculator during the exam. No
DoS Cyber Attack on a Government Agency in Europe- April 2012 Constantly Changing Attack Vectors
 DoS Cyber Attack on a Government Agency in Europe- April 2012 Constantly Changing Attack Vectors 1 Table of Content Preamble...3 About Radware s DefensePro... 3 About Radware s Emergency Response Team
DoS Cyber Attack on a Government Agency in Europe- April 2012 Constantly Changing Attack Vectors 1 Table of Content Preamble...3 About Radware s DefensePro... 3 About Radware s Emergency Response Team
FAST, FLEXIBLE, RELIABLE SEAMLESSLY ROUTING AND SECURING BILLIONS OF REQUESTS PER MONTH
 We help Big Brands, Scale WordPress. WORDPRESS HOSTING MANAGED BY PROFESSIONALS PAGELY, INC pagely.com THE PAGELY ARES APPLICATION GATEWAY FAST, FLEXIBLE, RELIABLE SEAMLESSLY ROUTING AND SECURING BILLIONS
We help Big Brands, Scale WordPress. WORDPRESS HOSTING MANAGED BY PROFESSIONALS PAGELY, INC pagely.com THE PAGELY ARES APPLICATION GATEWAY FAST, FLEXIBLE, RELIABLE SEAMLESSLY ROUTING AND SECURING BILLIONS
VMware Identity Manager Connector Installation and Configuration (Legacy Mode)
 VMware Identity Manager Connector Installation and Configuration (Legacy Mode) VMware Identity Manager This document supports the version of each product listed and supports all subsequent versions until
VMware Identity Manager Connector Installation and Configuration (Legacy Mode) VMware Identity Manager This document supports the version of each product listed and supports all subsequent versions until
Tuning NGINX for high performance. Nick Shadrin
 Tuning NGINX for high performance Nick Shadrin nick@nginx.com All links on one page shadrin.org/talks/ Twitter: @shadrin @nginx @nginxorg 2 About me Nick Shadrin Technical Solutions Architect with NGINX
Tuning NGINX for high performance Nick Shadrin nick@nginx.com All links on one page shadrin.org/talks/ Twitter: @shadrin @nginx @nginxorg 2 About me Nick Shadrin Technical Solutions Architect with NGINX
Tuning NGINX for high performance. Nick Shadrin
 Tuning NGINX for high performance Nick Shadrin nick@nginx.com All links on one page shadrin.org/talks/ Twitter: @shadrin @nginx @nginxorg 2 About me Nick Shadrin Product Manager at NGINX Based in San Francisco
Tuning NGINX for high performance Nick Shadrin nick@nginx.com All links on one page shadrin.org/talks/ Twitter: @shadrin @nginx @nginxorg 2 About me Nick Shadrin Product Manager at NGINX Based in San Francisco
CS 356 Internet Security Protocols. Fall 2013
 CS 356 Internet Security Protocols Fall 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists Chapter 5
CS 356 Internet Security Protocols Fall 2013 Review Chapter 1: Basic Concepts and Terminology Chapter 2: Basic Cryptographic Tools Chapter 3 User Authentication Chapter 4 Access Control Lists Chapter 5
Scan Report Executive Summary. Part 2. Component Compliance Summary Component (IP Address, domain, etc.):ekk.worldtravelink.com
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Travolutionary ASV Company: Comodo CA Limited 10-03-2018 Scan expiration date: 01-01-2019 Part 2.
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Travolutionary ASV Company: Comodo CA Limited 10-03-2018 Scan expiration date: 01-01-2019 Part 2.
Q. What technologies does Cisco WAAS Express use to optimize traffic? A. Cisco WAAS Express optimizes WAN bandwidth using these technologies:
 Q&A Cisco WAAS Express General Q. What is Cisco Wide Area Application Services (WAAS) Express? A. Cisco WAAS Express extends the Cisco WAAS product portfolio with a small-footprint, cost-effective solution
Q&A Cisco WAAS Express General Q. What is Cisco Wide Area Application Services (WAAS) Express? A. Cisco WAAS Express extends the Cisco WAAS product portfolio with a small-footprint, cost-effective solution
How can you implement this through a script that a scheduling daemon runs daily on the application servers?
 You ve been tasked with implementing an automated data backup solution for your application servers that run on Amazon EC2 with Amazon EBS volumes. You want to use a distributed data store for your backups
You ve been tasked with implementing an automated data backup solution for your application servers that run on Amazon EC2 with Amazon EBS volumes. You want to use a distributed data store for your backups
Chapter 3. Technology Adopted. 3.1 Introduction
 Chapter 3 Technology Adopted 3.1 Introduction The previous chapter described difference between the propose system and traditional methods and also about the existing similar systems. In this chapter,
Chapter 3 Technology Adopted 3.1 Introduction The previous chapter described difference between the propose system and traditional methods and also about the existing similar systems. In this chapter,
Tcp/ip Tutorial And Technical Overview - Ibm Redbooks
 Articles On Tcp Ip Including Internet Protocol Suite Transmission Control Protocol End To End Principle List Of Tcp And Udp Port Numbers Tcp Offload Engine Van Jacobson Tcp Ip Header Compression Tcp We
Articles On Tcp Ip Including Internet Protocol Suite Transmission Control Protocol End To End Principle List Of Tcp And Udp Port Numbers Tcp Offload Engine Van Jacobson Tcp Ip Header Compression Tcp We
Update Manual App World Blackberry Disappeared After Software
 Update Manual App World Blackberry Disappeared After Software Upgrade your BlackBerry 10 OS to the latest 10.3.2 software to enable advanced Android apps for BlackBerry If you haven't updated recently,
Update Manual App World Blackberry Disappeared After Software Upgrade your BlackBerry 10 OS to the latest 10.3.2 software to enable advanced Android apps for BlackBerry If you haven't updated recently,
