Scan Report Executive Summary. Part 2. Component Compliance Summary Component (IP Address, domain, etc.):ekk.worldtravelink.com
|
|
|
- Kristopher Dawson
- 5 years ago
- Views:
Transcription
1 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Travolutionary ASV Company: Comodo CA Limited Scan expiration date: Part 2. Summary (IP Address, domain, etc.): Part 3a. Vulnerabilities Noted for each ASV may choose to omit vulnerabilities that do not impact compliance from this section, however, failing vulnerabilities that have been changed to "pass" via exceptions or after remediation / rescan must always be listed Vulnerabilities Noted per Strict Transport Security (STS) Detection 1221 / tcp / Nessus SYN scanner 4022 / tcp / Nessus SYN scanner 4020 / tcp / Nessus SYN scanner 4018 / tcp / Nessus SYN scanner 4016 / tcp / Nessus SYN scanner 1221 / tcp / Nessus SYN scanner 455 / tcp / Nessus SYN scanner 454 / tcp / Nessus SYN scanner 443 / tcp / Nessus SYN scanner 80 / tcp / HyperText Transfer Protocol (HTTP) Redirect Information 443 / tcp / HyperText Transfer Protocol (HTTP) Redirect Information 80 / tcp / Device Type 0 / tcp / SSL Root Certification Authority Certificate Information 455 / tcp / SSL Root Certification Authority Certificate Information 454 / tcp /
2 Vulnerabilities Noted per SSL Root Certification Authority Certificate Information 443 / tcp / CGI Generic Injectable Parameter 443 / tcp / SSL Cipher Suites Supported 455 / tcp / SSL Cipher Suites Supported 454 / tcp / SSL Cipher Suites Supported 443 / tcp / Web Server Directory Enumeration 443 / tcp / Common Platform Enumeration (CPE) 0 / tcp / HTTP Methods Allowed (per directory) 1221 / tcp / HTTP Methods Allowed (per directory) 80 / tcp / HTTP Methods Allowed (per directory) 443 / tcp / SSL Certificate Expiry - Future Expiry 443 / tcp / Web Application Sitemap 1221 / tcp / Web Application Sitemap 443 / tcp / Web Server Allows word Auto-Completion 443 / tcp / CGI Generic Tests Load Estimation (all tests) 443 / tcp / TLS ALPN Supported Protocol Enumeration 455 / tcp / TLS ALPN Supported Protocol Enumeration 454 / tcp / HSTS Missing From HTTPS Server 443 / tcp / HSTS Missing From HTTPS Server 454 / tcp / HSTS Missing From HTTPS Server 455 / tcp /
3 Vulnerabilities Noted per OpenSSL Detection 443 / tcp / Web Server No 404 Error Code Check 1221 / tcp / Web Application Potentially Sensitive CGI Parameter Detection 443 / tcp / TCP/IP Timestamps Supported 0 / tcp / SSL Certificate Chain Contains Certificates Expiring Soon 443 / tcp / Web Application Cookies Not Marked Secure 1221 / tcp / Web Application Cookies Not Marked Secure 80 / tcp / Web Application Cookies Not Marked Secure 443 / tcp / Web Application Cookies Not Marked Secure 454 / tcp / Web Application Cookies Not Marked Secure 455 / tcp / HTTP X-Content-Security-Policy Response Header Usage 443 / tcp / HyperText Transfer Protocol (HTTP) Information 1221 / tcp / HyperText Transfer Protocol (HTTP) Information 455 / tcp / HyperText Transfer Protocol (HTTP) Information 454 / tcp / HyperText Transfer Protocol (HTTP) Information 443 / tcp / HyperText Transfer Protocol (HTTP) Information 80 / tcp / SSL Certificate Information 455 / tcp / SSL Certificate Information 454 / tcp / SSL Certificate Information 443 / tcp / OS Identification 0 / tcp /
4 Vulnerabilities Noted per SSL / TLS Versions Supported 443 / tcp / SSL / TLS Versions Supported 455 / tcp / SSL / TLS Versions Supported 454 / tcp / Additional DNS Hostnames 0 / tcp / HTTP Server Type and Version 1221 / tcp / HTTP Server Type and Version 80 / tcp / HTTP Server Type and Version 443 / tcp / Web Server robots.txt Information Disclosure 443 / tcp / Non-compliant Strict Transport Security (STS) 1221 / tcp / Service Detection 1221 / tcp / Service Detection 80 / tcp / Service Detection 443 / tcp / Service Detection 454 / tcp / Service Detection 455 / tcp / Service Detection 454 / tcp / Service Detection 455 / tcp / Service Detection 443 / tcp / SSL Perfect Forward Secrecy Cipher Suites Supported 455 / tcp / SSL Perfect Forward Secrecy Cipher Suites Supported 454 / tcp / SSL Perfect Forward Secrecy Cipher Suites Supported 443 / tcp / SSL Cipher Block Chaining Cipher Suites Supported 443 / tcp / SSL Cipher Block Chaining Cipher Suites Supported 455 / tcp / SSL Cipher Block Chaining Cipher Suites Supported 454 / tcp /
5 Vulnerabilities Noted per HTTP X-Frame-Options Response Header Usage 443 / tcp / Consolidated Solution/Correction Plan for above IP address: Protect your target with an IP filter. Analyze the redirect(s) to verify that this is valid operation for your web server and/or application. Ensure that use of this root Certification Authority certificate complies with your organization's acceptable use and security policies. Purchase or generate a new SSL certificate in the near future to replace the existing one. Add the attribute 'autocomplete=off' to these fields to prevent browsers from caching credentials. Configure the remote web server to use HSTS. Ensure sensitive data is not disclosed by CGI parameters. In addition, do not use CGI parameters to control access to resources or privileges. Renew any soon to expire SSL certificates. Each cookie should be carefully reviewed to determine if it contains sensitive data or is relied upon for a security decision. If possible, ensure all communication occurs over an encrypted channel and add the 'secure' attribute to all session cookies or any cookies containing sensitive data. Set a non-permissive Content-Security-Policy frame-ancestors header for all requested resources. If you want to test them, re-scan using the special vhost syntax, such as :.example.com[ ] Review the contents of the site's robots.txt file, use Robots META tags instead of entries in the robots.txt file, and/or adjust the web server's access controls to limit access to sensitive material. Set a properly configured X-Frame-Options header for all requested resources. Part 3b. Special Notes by Special Note Item Noted Scan customer`s description of action taken and declaration that software is either implemented securely or removed Part 3c. Special notes -- Full Text Note Part 4a. Scope Submitted by Scan Customer for Discovery IP Addresses/ranges/subnets, domains, URLs, etc. DOMAIN:
6 Part 4b. Scan Customer Designated In-Scope s (Scanned) IP Addresses/ranges/subnets, domains, URLs, etc. Part 4c. Scan Customer Designated Out-of-Scope s (Not Scanned) Requires description for each IP Address/range/subnet, domain, URL ekkworldtravelink.azurewebsites.net: waws-prod-am2-013.cloudapp.net: waws-prod-am2-013.vip.azurewebsites.windows.net: worldtravelink.com:
Scan Report Executive Summary
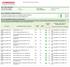 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 06/08/2018 Scan expiration date: 09/06/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 06/08/2018 Scan expiration date: 09/06/2018 Part 2. Component
Scan Report Executive Summary
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 11/20/2017 Scan expiration date: 02/18/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 11/20/2017 Scan expiration date: 02/18/2018 Part 2. Component
Scan Report Executive Summary
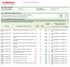 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: WineDirect ASV Company: Comodo CA Limited 10/11/2018 Scan expiration date: 01/09/2019 Part 2. Summary
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: WineDirect ASV Company: Comodo CA Limited 10/11/2018 Scan expiration date: 01/09/2019 Part 2. Summary
Scan Report Executive Summary. Part 2. Component Compliance Summary Component (IP Address, domain, etc.):
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 02/18/2018 Scan expiration date: 05/19/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 02/18/2018 Scan expiration date: 05/19/2018 Part 2. Component
Scan Report Executive Summary
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 08/28/2017 Scan expiration date: 11/26/2017 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 08/28/2017 Scan expiration date: 11/26/2017 Part 2. Component
Scan Report Executive Summary. Part 2. Component Compliance Summary IP Address :
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 03/18/2015 Scan expiration date: 06/16/2015 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 03/18/2015 Scan expiration date: 06/16/2015 Part 2. Component
Nessus Scan Report. Hosts Summary (Executive) Hosts Summary (Executive) Mon, 15 May :27:44 EDT
 Nessus Scan Report Mon, 15 May 2017 15:27:44 EDT Table Of Contents Hosts Summary (Executive) 192.168.168.134 Hosts Summary (Executive) [-] Collapse All [+] Expand All 192.168.168.134 Summary Critical High
Nessus Scan Report Mon, 15 May 2017 15:27:44 EDT Table Of Contents Hosts Summary (Executive) 192.168.168.134 Hosts Summary (Executive) [-] Collapse All [+] Expand All 192.168.168.134 Summary Critical High
Uniform Resource Locators (URL)
 The World Wide Web Web Web site consists of simply of pages of text and images A web pages are render by a web browser Retrieving a webpage online: Client open a web browser on the local machine The web
The World Wide Web Web Web site consists of simply of pages of text and images A web pages are render by a web browser Retrieving a webpage online: Client open a web browser on the local machine The web
How to Configure Authentication and Access Control (AAA)
 How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
SSL/TLS Server Test of
 SSL/TLS Server Test of www.rotenburger-gruene.de Test SSL/TLS implementation of any service on any port for compliance with PCI DSS requirements, HIPAA guidance and NIST guidelines. WWW.ROTENBURGER-GRUENE.DE
SSL/TLS Server Test of www.rotenburger-gruene.de Test SSL/TLS implementation of any service on any port for compliance with PCI DSS requirements, HIPAA guidance and NIST guidelines. WWW.ROTENBURGER-GRUENE.DE
The following topics describe how to configure correlation policies and rules.
 The following topics describe how to configure correlation policies and rules. Introduction to and Rules, page 1 Configuring, page 2 Configuring Correlation Rules, page 5 Configuring Correlation Response
The following topics describe how to configure correlation policies and rules. Introduction to and Rules, page 1 Configuring, page 2 Configuring Correlation Rules, page 5 Configuring Correlation Response
But where'd that extra "s" come from, and what does it mean?
 SSL/TLS While browsing Internet, some URLs start with "http://" while others start with "https://"? Perhaps the extra "s" when browsing websites that require giving over sensitive information, like paying
SSL/TLS While browsing Internet, some URLs start with "http://" while others start with "https://"? Perhaps the extra "s" when browsing websites that require giving over sensitive information, like paying
SSL/TLS Security Assessment of e-vo.ru
 SSL/TLS Security Assessment of e-vo.ru Test SSL/TLS implementation of any service on any port for compliance with industry best-practices, NIST guidelines and PCI DSS requirements. The server configuration
SSL/TLS Security Assessment of e-vo.ru Test SSL/TLS implementation of any service on any port for compliance with industry best-practices, NIST guidelines and PCI DSS requirements. The server configuration
Payment Card Industry (PCI) Executive Report 11/07/2017
 Payment Card Industry (PCI) Executive Report 11/07/2017 ASV Scan Report Attestation of Scan Compliance A1. Scan Customer Information A2. Approved Scanning Vendor Information Company: Allied Collection
Payment Card Industry (PCI) Executive Report 11/07/2017 ASV Scan Report Attestation of Scan Compliance A1. Scan Customer Information A2. Approved Scanning Vendor Information Company: Allied Collection
Securing Connections for IBM Traveler Apps. Bill Wimer STSM for IBM Collaboration Solutions December 13, 2016
 Securing Connections for IBM Traveler Apps Bill Wimer (bwimer@us.ibm.com), STSM for IBM Collaboration Solutions December 13, 2016 IBM Technote Article #21989980 Securing Connections for IBM Traveler mobile
Securing Connections for IBM Traveler Apps Bill Wimer (bwimer@us.ibm.com), STSM for IBM Collaboration Solutions December 13, 2016 IBM Technote Article #21989980 Securing Connections for IBM Traveler mobile
How-to Guide: Tenable.io for Microsoft Azure. Last Updated: November 16, 2018
 How-to Guide: Tenable.io for Microsoft Azure Last Updated: November 16, 2018 Table of Contents How-to Guide: Tenable.io for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
How-to Guide: Tenable.io for Microsoft Azure Last Updated: November 16, 2018 Table of Contents How-to Guide: Tenable.io for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
Tabular Presentation of the Application Software Extended Package for Web Browsers
 Tabular Presentation of the Application Software Extended Package for Web Browsers Version: 2.0 2015-06-16 National Information Assurance Partnership Revision History Version Date Comment v 2.0 2015-06-16
Tabular Presentation of the Application Software Extended Package for Web Browsers Version: 2.0 2015-06-16 National Information Assurance Partnership Revision History Version Date Comment v 2.0 2015-06-16
Configuring SSL. SSL Overview CHAPTER
 CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
SSL Report: ( )
 Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > www.workbench.nationaldataservice.org SSL Report: www.workbench.nationaldataservice.org (141.142.210.100) Assessed on:
Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > www.workbench.nationaldataservice.org SSL Report: www.workbench.nationaldataservice.org (141.142.210.100) Assessed on:
SSL Report: bourdiol.xyz ( )
 Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > bourdiol.xyz > 217.70.180.152 SSL Report: bourdiol.xyz (217.70.180.152) Assessed on: Sun Apr 19 12:22:55 PDT 2015 HIDDEN
Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > bourdiol.xyz > 217.70.180.152 SSL Report: bourdiol.xyz (217.70.180.152) Assessed on: Sun Apr 19 12:22:55 PDT 2015 HIDDEN
Merchant Certificate of Compliance
 Merchant Certificate of Compliance Awarded To: Consolid S.R.L. (55504923) Self - Assessment Questionnaire Passed: SAQ D, v3.2r1.1 Date Awarded: 03/01/2018 Most Recent Scan Date: 06/04/2018 Certificate
Merchant Certificate of Compliance Awarded To: Consolid S.R.L. (55504923) Self - Assessment Questionnaire Passed: SAQ D, v3.2r1.1 Date Awarded: 03/01/2018 Most Recent Scan Date: 06/04/2018 Certificate
Certified Secure Web Application Secure Development Checklist
 www.certifiedsecure.com info@certifiedsecure.com Tel.: +31 (0)70 310 13 40 Loire 128-A 2491 AJ The Hague The Netherlands About Certified Secure Checklist Certified Secure exists to encourage and fulfill
www.certifiedsecure.com info@certifiedsecure.com Tel.: +31 (0)70 310 13 40 Loire 128-A 2491 AJ The Hague The Netherlands About Certified Secure Checklist Certified Secure exists to encourage and fulfill
Can HTTP Strict Transport Security Meaningfully Help Secure the Web? nicolle neulist June 2, 2012 Security B-Sides Detroit
 Can HTTP Strict Transport Security Meaningfully Help Secure the Web? nicolle neulist June 2, 2012 Security B-Sides Detroit 1 2 o hai. 3 Why Think About HTTP Strict Transport Security? Roadmap what is HSTS?
Can HTTP Strict Transport Security Meaningfully Help Secure the Web? nicolle neulist June 2, 2012 Security B-Sides Detroit 1 2 o hai. 3 Why Think About HTTP Strict Transport Security? Roadmap what is HSTS?
Configuring SSL. SSL Overview CHAPTER
 7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
MQ Jumping... Or, move to the front of the queue, pass go and collect 200
 MQ Jumping.... Or, move to the front of the queue, pass go and collect 200 Martyn Ruks DEFCON 15 2007-08-03 One Year Ago Last year I talked about IBM Networking attacks and said I was going to continue
MQ Jumping.... Or, move to the front of the queue, pass go and collect 200 Martyn Ruks DEFCON 15 2007-08-03 One Year Ago Last year I talked about IBM Networking attacks and said I was going to continue
SSL Report: printware.co.uk ( )
 1 of 5 26/06/2015 14:27 Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > printware.co.uk SSL Report: printware.co.uk (194.143.166.5) Assessed on: Fri, 26 Jun 2015 12:53:08
1 of 5 26/06/2015 14:27 Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > printware.co.uk SSL Report: printware.co.uk (194.143.166.5) Assessed on: Fri, 26 Jun 2015 12:53:08
Certified Secure Web Application Security Test Checklist
 www.certifiedsecure.com info@certifiedsecure.com Tel.: +31 (0)70 310 13 40 Loire 128-A 2491 AJ The Hague The Netherlands Certified Secure Checklist About Certified Secure exists to encourage and fulfill
www.certifiedsecure.com info@certifiedsecure.com Tel.: +31 (0)70 310 13 40 Loire 128-A 2491 AJ The Hague The Netherlands Certified Secure Checklist About Certified Secure exists to encourage and fulfill
Payment Card Industry (PCI) Executive Report 11/01/2016
 Payment Card Industry (PCI) Executive Report 11/01/2016 ASV Scan Report Attestation of Scan Compliance Scan Customer Information Approved Scanning Vendor Information Company: Rural Computer Consultants
Payment Card Industry (PCI) Executive Report 11/01/2016 ASV Scan Report Attestation of Scan Compliance Scan Customer Information Approved Scanning Vendor Information Company: Rural Computer Consultants
Transport Level Security
 2 Transport Level Security : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 28 October 2013 css322y13s2l12, Steve/Courses/2013/s2/css322/lectures/transport.tex,
2 Transport Level Security : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 28 October 2013 css322y13s2l12, Steve/Courses/2013/s2/css322/lectures/transport.tex,
SSL/TLS Deployment Best Practices
 Version 1.0 24 Feb 2012 SSL/TLS Deployment Best Practices Ivan Ristic Qualys SSL Labs Introduction SSL/TLS is a deceptively simple technology. It is easy to deploy, and it just works... except that it
Version 1.0 24 Feb 2012 SSL/TLS Deployment Best Practices Ivan Ristic Qualys SSL Labs Introduction SSL/TLS is a deceptively simple technology. It is easy to deploy, and it just works... except that it
Configuring SSL CHAPTER
 7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT
 How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT Ta Table of Contents Table of Contents TA TABLE OF CONTENTS 1 TABLE OF CONTENTS 1 BACKGROUND 2 CONFIGURATION STEPS 2 Create a SSL
How to Configure SSL VPN Portal for Forcepoint NGFW TECHNICAL DOCUMENT Ta Table of Contents Table of Contents TA TABLE OF CONTENTS 1 TABLE OF CONTENTS 1 BACKGROUND 2 CONFIGURATION STEPS 2 Create a SSL
Overview of SSL/TLS. Luke Anderson. 12 th May University Of Sydney.
 Overview of SSL/TLS Luke Anderson luke@lukeanderson.com.au 12 th May 2017 University Of Sydney Overview 1. Introduction 1.1 Raw HTTP 1.2 Introducing SSL/TLS 2. Certificates 3. Attacks Introduction Raw
Overview of SSL/TLS Luke Anderson luke@lukeanderson.com.au 12 th May 2017 University Of Sydney Overview 1. Introduction 1.1 Raw HTTP 1.2 Introducing SSL/TLS 2. Certificates 3. Attacks Introduction Raw
ACS 5.x: LDAP Server Configuration Example
 ACS 5.x: LDAP Server Configuration Example Document ID: 113473 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Directory Service Authentication Using
ACS 5.x: LDAP Server Configuration Example Document ID: 113473 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Directory Service Authentication Using
The State of TLS in httpd 2.4. William A. Rowe Jr.
 The State of TLS in httpd 2.4 William A. Rowe Jr. wrowe@apache.org Getting Started Web references have grown stale Web references have grown stale Guidance is changing annually https://www.ssllabs.com/ssltest/analyze.ht
The State of TLS in httpd 2.4 William A. Rowe Jr. wrowe@apache.org Getting Started Web references have grown stale Web references have grown stale Guidance is changing annually https://www.ssllabs.com/ssltest/analyze.ht
User Manual. Admin Report Kit for IIS 7 (ARKIIS)
 User Manual Admin Report Kit for IIS 7 (ARKIIS) Table of Contents 1 Admin Report Kit for IIS 7... 1 1.1 About ARKIIS... 1 1.2 Who can Use ARKIIS?... 1 1.3 System requirements... 2 1.4 Technical Support...
User Manual Admin Report Kit for IIS 7 (ARKIIS) Table of Contents 1 Admin Report Kit for IIS 7... 1 1.1 About ARKIIS... 1 1.2 Who can Use ARKIIS?... 1 1.3 System requirements... 2 1.4 Technical Support...
SSL/TLS Server Test of grupoconsultorefe.com
 SSL/TLS Server Test of grupoconsultorefe.com Test SSL/TLS implementation of any service on any port for compliance with PCI DSS requirements, HIPAA guidance and NIST guidelines. GRUPOCONSULTOREFE.COM FINAL
SSL/TLS Server Test of grupoconsultorefe.com Test SSL/TLS implementation of any service on any port for compliance with PCI DSS requirements, HIPAA guidance and NIST guidelines. GRUPOCONSULTOREFE.COM FINAL
Managing Certificates
 CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
CHAPTER 12 The Cisco Identity Services Engine (Cisco ISE) relies on public key infrastructure (PKI) to provide secure communication for the following: Client and server authentication for Transport Layer
How to Configure SSL Interception in the Firewall
 Most applications encrypt outgoing connections with SSL or TLS. SSL Interception decrypts SSL-encrypted traffic to allow Application Control features (such as the Virus Scanner, ATD, URL Filter, Safe Search,
Most applications encrypt outgoing connections with SSL or TLS. SSL Interception decrypts SSL-encrypted traffic to allow Application Control features (such as the Virus Scanner, ATD, URL Filter, Safe Search,
DEPLOYMENT GUIDE HOW TO DEPLOY MICROSOFT SHAREPOINT 2016 WITH A10 THUNDER ADC
 DEPLOYMENT GUIDE HOW TO DEPLOY MICROSOFT SHAREPOINT 2016 WITH A10 THUNDER ADC OVERVIEW Microsoft SharePoint Server 2016 is a collaboration platform that organizations of all sizes can use to improve the
DEPLOYMENT GUIDE HOW TO DEPLOY MICROSOFT SHAREPOINT 2016 WITH A10 THUNDER ADC OVERVIEW Microsoft SharePoint Server 2016 is a collaboration platform that organizations of all sizes can use to improve the
Comodo Certificate Manager Software Version 5.0
 Comodo Certificate Manager Software Version 5.0 Introducing The Certificate Dashboard Comodo CA Limited, 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater Manchester M5 3EQ,
Comodo Certificate Manager Software Version 5.0 Introducing The Certificate Dashboard Comodo CA Limited, 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater Manchester M5 3EQ,
COMPUTER NETWORKS AND COMMUNICATION PROTOCOLS. Web Access: HTTP Mehmet KORKMAZ
 COMPUTER NETWORKS AND COMMUNICATION PROTOCOLS Web Access: HTTP 16501018 Mehmet KORKMAZ World Wide Web What is WWW? WWW = World Wide Web = Web!= Internet Internet is a global system of interconnected computer
COMPUTER NETWORKS AND COMMUNICATION PROTOCOLS Web Access: HTTP 16501018 Mehmet KORKMAZ World Wide Web What is WWW? WWW = World Wide Web = Web!= Internet Internet is a global system of interconnected computer
Security in Bomgar Remote Support
 Security in Bomgar Remote Support 2018 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of their
Security in Bomgar Remote Support 2018 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property of their
How to configure the UTM Web Application Firewall for Microsoft Remote Desktop Gateway connectivity
 How to configure the UTM Web Application Firewall for Microsoft Remote Desktop Gateway connectivity This article explains how to configure your Sophos UTM to allow access Microsoft s Remote Desktop Gateway
How to configure the UTM Web Application Firewall for Microsoft Remote Desktop Gateway connectivity This article explains how to configure your Sophos UTM to allow access Microsoft s Remote Desktop Gateway
The World Wide Web is widely used by businesses, government agencies, and many individuals. But the Internet and the Web are extremely vulnerable to
 1 The World Wide Web is widely used by businesses, government agencies, and many individuals. But the Internet and the Web are extremely vulnerable to compromises of various sorts, with a range of threats
1 The World Wide Web is widely used by businesses, government agencies, and many individuals. But the Internet and the Web are extremely vulnerable to compromises of various sorts, with a range of threats
SSL Report: sharplesgroup.com ( )
 1 of 5 26/06/2015 14:28 Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > sharplesgroup.com SSL Report: sharplesgroup.com (176.58.116.26) Assessed on: Fri, 26 Jun 2015
1 of 5 26/06/2015 14:28 Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > sharplesgroup.com SSL Report: sharplesgroup.com (176.58.116.26) Assessed on: Fri, 26 Jun 2015
Kenna Platform Security. A technical overview of the comprehensive security measures Kenna uses to protect your data
 Kenna Platform Security A technical overview of the comprehensive security measures Kenna uses to protect your data V3.0, MAY 2017 Multiple Layers of Protection Overview Password Salted-Hash Thank you
Kenna Platform Security A technical overview of the comprehensive security measures Kenna uses to protect your data V3.0, MAY 2017 Multiple Layers of Protection Overview Password Salted-Hash Thank you
Host Identity Sources
 The following topics provide information on host identity sources: Overview: Host Data Collection, on page 1 Determining Which Host Operating Systems the System Can Detect, on page 2 Identifying Host Operating
The following topics provide information on host identity sources: Overview: Host Data Collection, on page 1 Determining Which Host Operating Systems the System Can Detect, on page 2 Identifying Host Operating
Cryptography SSL/TLS. Network Security Workshop. 3-5 October 2017 Port Moresby, Papua New Guinea
 Cryptography SSL/TLS Network Security Workshop 3-5 October 2017 Port Moresby, Papua New Guinea 1 History Secure Sockets Layer was developed by Netscape in 1994 as a protocol which permitted persistent
Cryptography SSL/TLS Network Security Workshop 3-5 October 2017 Port Moresby, Papua New Guinea 1 History Secure Sockets Layer was developed by Netscape in 1994 as a protocol which permitted persistent
Chapter 2. Application Layer
 Chapter 2 Application Layer 2.1. 2-1 INTRODUCTION - The application layer provides services to the user - Communication is provided using a logical connection means that the two application layers assume
Chapter 2 Application Layer 2.1. 2-1 INTRODUCTION - The application layer provides services to the user - Communication is provided using a logical connection means that the two application layers assume
BIG-IP Access Policy Manager : Secure Web Gateway. Version 13.0
 BIG-IP Access Policy Manager : Secure Web Gateway Version 13.0 Table of Contents Table of Contents BIG-IP APM Secure Web Gateway Overview...9 About APM Secure Web Gateway... 9 About APM benefits for web
BIG-IP Access Policy Manager : Secure Web Gateway Version 13.0 Table of Contents Table of Contents BIG-IP APM Secure Web Gateway Overview...9 About APM Secure Web Gateway... 9 About APM benefits for web
Requirements from the Application Software Extended Package for Web Browsers
 Requirements from the Application Software Extended Package for Web Browsers Version: 2.0 2015-06-16 National Information Assurance Partnership Revision History Version Date Comment v 2.0 2015-06-16 Application
Requirements from the Application Software Extended Package for Web Browsers Version: 2.0 2015-06-16 National Information Assurance Partnership Revision History Version Date Comment v 2.0 2015-06-16 Application
MediaAUTH Draft Proposal
 MediaAUTH Draft Proposal August 21, 2012 Contents 1 Introduction 2 2 Service & User Perspective 2 2.1 Login...................................... 2 2.2 Soft Login.................................... 3
MediaAUTH Draft Proposal August 21, 2012 Contents 1 Introduction 2 2 Service & User Perspective 2 2.1 Login...................................... 2 2.2 Soft Login.................................... 3
SSL Report: cartridgeworld.co.uk ( )
 1 of 5 26/06/2015 14:21 Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > cartridgeworld.co.uk SSL Report: cartridgeworld.co.uk (95.138.147.104) Assessed on: Fri, 26 Jun
1 of 5 26/06/2015 14:21 Home Projects Qualys.com Contact You are here: Home > Projects > SSL Server Test > cartridgeworld.co.uk SSL Report: cartridgeworld.co.uk (95.138.147.104) Assessed on: Fri, 26 Jun
Configuring Vulnerability Assessment Devices
 CHAPTER 10 Revised: November 10, 2007 Vulnerability assessment (VA) devices provide MARS with valuable information about many of the possible targets of attacks and threats. They provide information useful
CHAPTER 10 Revised: November 10, 2007 Vulnerability assessment (VA) devices provide MARS with valuable information about many of the possible targets of attacks and threats. They provide information useful
Session 8. Reading and Reference. en.wikipedia.org/wiki/list_of_http_headers. en.wikipedia.org/wiki/http_status_codes
 Session 8 Deployment Descriptor 1 Reading Reading and Reference en.wikipedia.org/wiki/http Reference http headers en.wikipedia.org/wiki/list_of_http_headers http status codes en.wikipedia.org/wiki/_status_codes
Session 8 Deployment Descriptor 1 Reading Reading and Reference en.wikipedia.org/wiki/http Reference http headers en.wikipedia.org/wiki/list_of_http_headers http status codes en.wikipedia.org/wiki/_status_codes
Tenable.io User Guide. Last Revised: November 03, 2017
 Tenable.io User Guide Last Revised: November 03, 2017 Table of Contents Tenable.io User Guide 1 Getting Started with Tenable.io 10 Tenable.io Workflow 12 System Requirements 15 Scanners and Agents 16 Link
Tenable.io User Guide Last Revised: November 03, 2017 Table of Contents Tenable.io User Guide 1 Getting Started with Tenable.io 10 Tenable.io Workflow 12 System Requirements 15 Scanners and Agents 16 Link
Web as a Distributed System
 Web as a Distributed System The World Wide Web is a large distributed system. In 1998 comprises 70-75% of Internet traffic. With large transfers of streaming media and p2p, no longer a majority of bytes,
Web as a Distributed System The World Wide Web is a large distributed system. In 1998 comprises 70-75% of Internet traffic. With large transfers of streaming media and p2p, no longer a majority of bytes,
High -Tech Bridge s Web Server Security Service API Developer Documentation Version v1.3 February 13 th 2018
 HTB_WEBSECDOCS_v1.3.pdf Page 1 of 29 High -Tech Bridge s Web Server Security Service API Developer Documentation Version v1.3 February 13 th 2018 General Overview... 2 Meta-information... 4 HTTP Additional
HTB_WEBSECDOCS_v1.3.pdf Page 1 of 29 High -Tech Bridge s Web Server Security Service API Developer Documentation Version v1.3 February 13 th 2018 General Overview... 2 Meta-information... 4 HTTP Additional
How-to Guide: Tenable Nessus for Microsoft Azure. Last Updated: April 03, 2018
 How-to Guide: Tenable Nessus for Microsoft Azure Last Updated: April 03, 2018 Table of Contents How-to Guide: Tenable Nessus for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
How-to Guide: Tenable Nessus for Microsoft Azure Last Updated: April 03, 2018 Table of Contents How-to Guide: Tenable Nessus for Microsoft Azure 1 Introduction 3 Auditing the Microsoft Azure Cloud Environment
WHY CSRF WORKS. Implicit authentication by Web browsers
 WHY CSRF WORKS To explain the root causes of, and solutions to CSRF attacks, I need to share with you the two broad types of authentication mechanisms used by Web applications: 1. Implicit authentication
WHY CSRF WORKS To explain the root causes of, and solutions to CSRF attacks, I need to share with you the two broad types of authentication mechanisms used by Web applications: 1. Implicit authentication
Tenable.sc-Tenable.io Upgrade Assistant Guide, Version 2.0. Last Revised: January 16, 2019
 Tenable.sc-Tenable.io Upgrade Assistant Guide, Version 2.0 Last Revised: January 16, 2019 Table of Contents Welcome to the Tenable.sc-Tenable.io Upgrade Assistant 3 Get Started 4 Environment Requirements
Tenable.sc-Tenable.io Upgrade Assistant Guide, Version 2.0 Last Revised: January 16, 2019 Table of Contents Welcome to the Tenable.sc-Tenable.io Upgrade Assistant 3 Get Started 4 Environment Requirements
Attacks Against Websites. Tom Chothia Computer Security, Lecture 11
 Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
How to Set Up VPN Certificates
 For the VPN service, you can use either self-signed certificates or certificates that are generated by an external CA. In this article: Before You Begin Before you set up VPN certificates, verify that
For the VPN service, you can use either self-signed certificates or certificates that are generated by an external CA. In this article: Before You Begin Before you set up VPN certificates, verify that
Oracle Cloud Using Oracle Cloud Infrastructure Load Balancing Classic
 Oracle Cloud Using Oracle Cloud Infrastructure Load Balancing Classic E76938-02 December 2017 Oracle Cloud Using Oracle Cloud Infrastructure Load Balancing Classic, E76938-02 Copyright 2017, Oracle and/or
Oracle Cloud Using Oracle Cloud Infrastructure Load Balancing Classic E76938-02 December 2017 Oracle Cloud Using Oracle Cloud Infrastructure Load Balancing Classic, E76938-02 Copyright 2017, Oracle and/or
Content and Purpose of This Guide... 1 User Management... 2
 Contents Introduction--1 Content and Purpose of This Guide........................... 1 User Management........................................ 2 Security--3 Security Features.........................................
Contents Introduction--1 Content and Purpose of This Guide........................... 1 User Management........................................ 2 Security--3 Security Features.........................................
McAfee Certified Assessment Specialist Network
 McAfee MA0-150 McAfee Certified Assessment Specialist Network Version: 4.0 Topic 1, Volume A QUESTION NO: 1 An attacker has compromised a Linux/Unix host and discovers a suspicious file called "password"
McAfee MA0-150 McAfee Certified Assessment Specialist Network Version: 4.0 Topic 1, Volume A QUESTION NO: 1 An attacker has compromised a Linux/Unix host and discovers a suspicious file called "password"
Web Application Firewall Getting Started Guide. September 7, 2018
 Web Application Firewall Getting Started Guide September 7, 2018 Copyright 2014-2018 by Qualys, Inc. All Rights Reserved. Qualys and the Qualys logo are registered trademarks of Qualys, Inc. All other
Web Application Firewall Getting Started Guide September 7, 2018 Copyright 2014-2018 by Qualys, Inc. All Rights Reserved. Qualys and the Qualys logo are registered trademarks of Qualys, Inc. All other
WHITE PAPER. Authentication and Encryption Design
 WHITE PAPER Authentication and Encryption Design Table of Contents Introduction Applications and Services Account Creation Two-step Verification Authentication Passphrase Management Email Message Encryption
WHITE PAPER Authentication and Encryption Design Table of Contents Introduction Applications and Services Account Creation Two-step Verification Authentication Passphrase Management Email Message Encryption
VMware Workspace ONE Quick Configuration Guide. VMware AirWatch 9.1
 VMware Workspace ONE Quick Configuration Guide VMware AirWatch 9.1 A P R I L 2 0 1 7 V 2 Revision Table The following table lists revisions to this guide since the April 2017 release Date April 2017 June
VMware Workspace ONE Quick Configuration Guide VMware AirWatch 9.1 A P R I L 2 0 1 7 V 2 Revision Table The following table lists revisions to this guide since the April 2017 release Date April 2017 June
Security in the Privileged Remote Access Appliance
 Security in the Privileged Remote Access Appliance 2003-2018 BeyondTrust, Inc. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust, Inc. Other trademarks are the property
Security in the Privileged Remote Access Appliance 2003-2018 BeyondTrust, Inc. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust, Inc. Other trademarks are the property
01/02/2014 SECURITY ASSESSMENT METHODOLOGIES SENSEPOST 2014 ALL RIGHTS RESERVED
 01/02/2014 SECURITY ASSESSMENT METHODOLOGIES SENSEPOST 2014 ALL RIGHTS RESERVED Contents 1. Introduction 3 2. Security Testing Methodologies 3 2.1 Internet Footprint Assessment 4 2.2 Infrastructure Assessments
01/02/2014 SECURITY ASSESSMENT METHODOLOGIES SENSEPOST 2014 ALL RIGHTS RESERVED Contents 1. Introduction 3 2. Security Testing Methodologies 3 2.1 Internet Footprint Assessment 4 2.2 Infrastructure Assessments
ArcGIS Enterprise Security: An Introduction. Randall Williams Esri PSIRT
 ArcGIS Enterprise Security: An Introduction Randall Williams Esri PSIRT Agenda ArcGIS Enterprise Security for *BEGINNING to INTERMIDIATE* users ArcGIS Enterprise Security Model Portal for ArcGIS Authentication
ArcGIS Enterprise Security: An Introduction Randall Williams Esri PSIRT Agenda ArcGIS Enterprise Security for *BEGINNING to INTERMIDIATE* users ArcGIS Enterprise Security Model Portal for ArcGIS Authentication
PCI Compliance. Network Scanning. Getting Started Guide
 PCI Compliance Getting Started Guide Qualys PCI provides businesses, merchants and online service providers with the easiest, most cost effective and highly automated way to achieve compliance with the
PCI Compliance Getting Started Guide Qualys PCI provides businesses, merchants and online service providers with the easiest, most cost effective and highly automated way to achieve compliance with the
Elastic Load Balance. User Guide. Issue 01 Date HUAWEI TECHNOLOGIES CO., LTD.
 Issue 01 Date 2018-04-30 HUAWEI TECHNOLOGIES CO., LTD. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
Issue 01 Date 2018-04-30 HUAWEI TECHNOLOGIES CO., LTD. 2018. All rights reserved. No part of this document may be reproduced or transmitted in any form or by any means without prior written consent of
Transport Layer Security
 CEN585 Computer and Network Security Transport Layer Security Dr. Mostafa Dahshan Department of Computer Engineering College of Computer and Information Sciences King Saud University mdahshan@ksu.edu.sa
CEN585 Computer and Network Security Transport Layer Security Dr. Mostafa Dahshan Department of Computer Engineering College of Computer and Information Sciences King Saud University mdahshan@ksu.edu.sa
SSL Visibility and Troubleshooting
 Page 1 of 6 view online Avi Vantage provides a number of features to help understand the utilization of SSL traffic and troubleshoot SSL-related issues. Visibility Every virtual service provides a number
Page 1 of 6 view online Avi Vantage provides a number of features to help understand the utilization of SSL traffic and troubleshoot SSL-related issues. Visibility Every virtual service provides a number
BlackBerry UEM Configuration Guide
 BlackBerry UEM Configuration Guide 12.9 2018-11-05Z 2 Contents Getting started... 7 Configuring BlackBerry UEM for the first time... 7 Configuration tasks for managing BlackBerry OS devices... 9 Administrator
BlackBerry UEM Configuration Guide 12.9 2018-11-05Z 2 Contents Getting started... 7 Configuring BlackBerry UEM for the first time... 7 Configuration tasks for managing BlackBerry OS devices... 9 Administrator
RiskSense Attack Surface Validation for Web Applications
 RiskSense Attack Surface Validation for Web Applications 2018 RiskSense, Inc. Keeping Pace with Digital Business No Excuses for Not Finding Risk Exposure We needed a faster way of getting a risk assessment
RiskSense Attack Surface Validation for Web Applications 2018 RiskSense, Inc. Keeping Pace with Digital Business No Excuses for Not Finding Risk Exposure We needed a faster way of getting a risk assessment
Configuration Guide. BlackBerry UEM. Version 12.9
 Configuration Guide BlackBerry UEM Version 12.9 Published: 2018-07-16 SWD-20180713083904821 Contents About this guide... 8 Getting started... 9 Configuring BlackBerry UEM for the first time...9 Configuration
Configuration Guide BlackBerry UEM Version 12.9 Published: 2018-07-16 SWD-20180713083904821 Contents About this guide... 8 Getting started... 9 Configuring BlackBerry UEM for the first time...9 Configuration
Workspace ONE UEM Certificate Authentication for Cisco IPSec VPN. VMware Workspace ONE UEM 1810
 Workspace ONE UEM Certificate Authentication for Cisco IPSec VPN VMware Workspace ONE UEM 1810 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Workspace ONE UEM Certificate Authentication for Cisco IPSec VPN VMware Workspace ONE UEM 1810 You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/
Elastic Load Balancing. User Guide. Date
 Date 2018-07-20 Contents Contents 1 Product Description... 4 1.1 What Is Elastic Load Balancing (ELB)?... 4 1.2 Load Balancer Type... 4 1.3 Basic Architecture... 5 1.3.1 Classic Load Balancer... 5 1.3.2
Date 2018-07-20 Contents Contents 1 Product Description... 4 1.1 What Is Elastic Load Balancing (ELB)?... 4 1.2 Load Balancer Type... 4 1.3 Basic Architecture... 5 1.3.1 Classic Load Balancer... 5 1.3.2
Remote Desktop Services. Deployment Guide
 Deployment Guide UPDATED: 20 June 2018 Copyright Notices Copyright 2002-2018 KEMP Technologies, Inc. All rights reserved. KEMP Technologies and the KEMP Technologies logo are registered trademarks of KEMP
Deployment Guide UPDATED: 20 June 2018 Copyright Notices Copyright 2002-2018 KEMP Technologies, Inc. All rights reserved. KEMP Technologies and the KEMP Technologies logo are registered trademarks of KEMP
Understanding Traffic Decryption
 The following topics provide an overview of SSL inspection, describe the prerequisites for SSL inspection configuration, and detail deployment scenarios. Traffic Decryption Overview, page 1 SSL Handshake
The following topics provide an overview of SSL inspection, describe the prerequisites for SSL inspection configuration, and detail deployment scenarios. Traffic Decryption Overview, page 1 SSL Handshake
Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS)
 Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
Hypertext Transfer Protocol Over Secure Sockets Layer (HTTPS) This chapter provides information about Hypertext Transfer Protocol over Secure Sockets Layer. HTTPS, page 1 HTTPS for Cisco Unified IP Phone
Cisco SSL Encryption Utility
 About SSL Encryption Utility, page 1 About SSL Encryption Utility Unified ICM web servers are configured for secure access (HTTPS) using SSL. Cisco provides an application called the SSL Encryption Utility
About SSL Encryption Utility, page 1 About SSL Encryption Utility Unified ICM web servers are configured for secure access (HTTPS) using SSL. Cisco provides an application called the SSL Encryption Utility
PCI COMPLIANCE IS NO LONGER OPTIONAL
 PCI COMPLIANCE IS NO LONGER OPTIONAL YOUR PARTICIPATION IS MANDATORY To protect the data security of your business and your customers, the credit card industry introduced uniform Payment Card Industry
PCI COMPLIANCE IS NO LONGER OPTIONAL YOUR PARTICIPATION IS MANDATORY To protect the data security of your business and your customers, the credit card industry introduced uniform Payment Card Industry
Computer Forensics: Investigating Network Intrusions and Cyber Crime, 2nd Edition. Chapter 3 Investigating Web Attacks
 Computer Forensics: Investigating Network Intrusions and Cyber Crime, 2nd Edition Chapter 3 Investigating Web Attacks Objectives After completing this chapter, you should be able to: Recognize the indications
Computer Forensics: Investigating Network Intrusions and Cyber Crime, 2nd Edition Chapter 3 Investigating Web Attacks Objectives After completing this chapter, you should be able to: Recognize the indications
U.S. E-Authentication Interoperability Lab Engineer
 Using Digital Certificates to Establish Federated Trust chris.brown@enspier.com U.S. E-Authentication Interoperability Lab Engineer Agenda U.S. Federal E-Authentication Background Current State of PKI
Using Digital Certificates to Establish Federated Trust chris.brown@enspier.com U.S. E-Authentication Interoperability Lab Engineer Agenda U.S. Federal E-Authentication Background Current State of PKI
Comodo Certificate Manager Software Version 5.6
 Comodo Certificate Manager Software Version 5.6 Introducing The Certificate Dashboard Comodo CA Limited, 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater Manchester M5 3EQ,
Comodo Certificate Manager Software Version 5.6 Introducing The Certificate Dashboard Comodo CA Limited, 3rd Floor, 26 Office Village, Exchange Quay, Trafford Road, Salford, Greater Manchester M5 3EQ,
TIBCO Cloud Integration Security Overview
 TIBCO Cloud Integration Security Overview TIBCO Cloud Integration is secure, best-in-class Integration Platform as a Service (ipaas) software offered in a multi-tenant SaaS environment with centralized
TIBCO Cloud Integration Security Overview TIBCO Cloud Integration is secure, best-in-class Integration Platform as a Service (ipaas) software offered in a multi-tenant SaaS environment with centralized
Microsoft OWA 2013 IIS Integration
 Microsoft OWA 2013 IIS Integration Contents 1 Introduction 2 Compatibility 3 Prerequisites 4 File Downloads 5 Architecture 6 Installation 6.1 Software Installation 6.2 Configuration of the IIS Filter 6.2.1
Microsoft OWA 2013 IIS Integration Contents 1 Introduction 2 Compatibility 3 Prerequisites 4 File Downloads 5 Architecture 6 Installation 6.1 Software Installation 6.2 Configuration of the IIS Filter 6.2.1
Defeating All Man-in-the-Middle Attacks
 Defeating All Man-in-the-Middle Attacks PrecisionAccess Vidder, Inc. Defeating All Man-in-the-Middle Attacks 1 Executive Summary The man-in-the-middle attack is a widely used and highly preferred type
Defeating All Man-in-the-Middle Attacks PrecisionAccess Vidder, Inc. Defeating All Man-in-the-Middle Attacks 1 Executive Summary The man-in-the-middle attack is a widely used and highly preferred type
Web Security, Summer Term 2012
 IIG University of Freiburg Web Security, Summer Term 2012 Web Application: Testing Security Dr. E. Benoist Sommer Semester Web Security, Summer Term 2012 10) Web Application: Testing Security 1 Table of
IIG University of Freiburg Web Security, Summer Term 2012 Web Application: Testing Security Dr. E. Benoist Sommer Semester Web Security, Summer Term 2012 10) Web Application: Testing Security 1 Table of
Install the ExtraHop session key forwarder on a Windows server
 Install the ExtraHop session key forwarder on a Windows server Published: 2018-07-19 The ExtraHop session key forwarder runs as a process on a monitored Windows server running SSL services. The forwarder
Install the ExtraHop session key forwarder on a Windows server Published: 2018-07-19 The ExtraHop session key forwarder runs as a process on a monitored Windows server running SSL services. The forwarder
How to Configure SSL Interception in the Firewall
 Most applications encrypt outgoing connections with SSL or TLS. SSL Interception decrypts SSL-encrypted HTTPS and SMTPS traffic to allow Application Control features (such as the Virus Scanner, ATP, URL
Most applications encrypt outgoing connections with SSL or TLS. SSL Interception decrypts SSL-encrypted HTTPS and SMTPS traffic to allow Application Control features (such as the Virus Scanner, ATP, URL
Web Application Penetration Testing
 Web Application Penetration Testing COURSE BROCHURE & SYLLABUS Course Overview Web Application penetration Testing (WAPT) is the Security testing techniques for vulnerabilities or security holes in corporate
Web Application Penetration Testing COURSE BROCHURE & SYLLABUS Course Overview Web Application penetration Testing (WAPT) is the Security testing techniques for vulnerabilities or security holes in corporate
AppSpider Enterprise. Getting Started Guide
 AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
AppSpider Enterprise Getting Started Guide Contents Contents 2 About AppSpider Enterprise 4 Getting Started (System Administrator) 5 Login 5 Client 6 Add Client 7 Cloud Engines 8 Scanner Groups 8 Account
CAMSCANNER TURN YOUR PHONE AND TABLET INTO SCANNER FOR
 PDF NESSUS VULNERABILITY SCANNER - BASICS - SECURITYLEARN CAMSCANNER TURN YOUR PHONE AND TABLET INTO SCANNER FOR 1 / 6 2 / 6 3 / 6 website vulnerability scanner pdf Basics vulnerability scanning with NESSUS...
PDF NESSUS VULNERABILITY SCANNER - BASICS - SECURITYLEARN CAMSCANNER TURN YOUR PHONE AND TABLET INTO SCANNER FOR 1 / 6 2 / 6 3 / 6 website vulnerability scanner pdf Basics vulnerability scanning with NESSUS...
Penetration Testing with Kali Linux
 Penetration Testing with Kali Linux PWK Copyright Offensive Security Ltd. All rights reserved. Page 1 of 11 All rights reserved to Offensive Security No part of this publication, in whole or in part, may
Penetration Testing with Kali Linux PWK Copyright Offensive Security Ltd. All rights reserved. Page 1 of 11 All rights reserved to Offensive Security No part of this publication, in whole or in part, may
