RFID & NFC. Erik Poll. Digital Security Radboud University Nijmegen
|
|
|
- Irma Knight
- 6 years ago
- Views:
Transcription
1 RFID & NFC Erik Poll Digital Security Radboud University Nijmegen 1
2 RFID tags RFID = Radio-Frequency IDentification RFID devices are called tags or transponders More powerful RFID tags also called contactless smartcards Inductive coupling is used for energy transfer to card transmission of clock signal data transfer simple tags are only support data transfer in one direction, from the tag to reader 2
3 Many kinds of RFID tags Animal identification RFID tags (ISO 11784, 11785) only transmit fixed id code Advanced transponders (ISO 14223) have more data and support writing & write-protection compatible with ISO Contactless smartcards close coupling: a few mm (ISO 10536) proximity: less than 10 cm (ISO 14443) vicinity: more than 10 cm (ISO 15693) Many of these tags are not very smart: memory cards instead of microprocessor cards 3
4 Many kinds of RFID tags Anti-theft systems (VDI 4470) only one bit of information Item management (ISO others) essentially RFID bar codes GTAG (Global Tag), joined effort of EAN (European Article Numbering Association) and UCC (Universal Code Council) Container identification (ISO 10374) active battery-operated transponder 4
5 ISO aka proximity tags Used in passports and many ID cards (incl. Dutch ID) contactless bank card many public transport cards Two types, A and B, with different RF modulation readers typically support both versions There are closely related industry standards: Mifare (similar to A), Calypso (similar to B), and Felica 5
6 read-only stupid memory tags ie tag just shouts its serial number communication one way only writable, no write-protection 1 byte to 64 Kbyte, in fixed blocks, eg 16 bit, 4 byte,.. no protection on writing writable, some write-protection password/key or more complicated authentication procedure possible offering segmented memory each memory segment with its own key important standard: MIFARE (Classic) others: DESfire, Calypso, ATMEL CryptoMemory, Legic, 6
7 smart microprocessor tags like normal smartcard, ie smart, but (also) wireless but with a lot less power ISO mw GSM mw ISO mw Hence: reduced resources for crypto & countermeasures Also: interaction time should ideally be very short (to prevent card tears, when card is moved away from reader) 7
8 Dual contact cards Dual contact cards have both contact and contactless interfaces eg your bank card Cards can expose different functionality via contact and contactless interface. Why would you want this? For security! Some early dual contact bank cards in UK & NL were misconfigured, to allow VERIFY PIN command not only over the contact interface, but also over the contactless interface 8
9 pros & cons of contact vs contactless? pros contactless ease of use no wear & tear of contacts on card and terminal less maintenance less susceptible to vandalism cons contactless easier to eavesdrop on communication? terminal communication easier to eavesdrop than tag communication communication possible without owner's consent for replay or relay man-in-the-middle attacks cheap tags have limited capabilities to provide security (eg amount of data, access control model, crypto) 9
10 passive vs active attacks on RFID passive attacks eavesdropping on communication between passport & reader possible from many meters if card is held to regular reader 18 meter reported by Engelhardt et al. active attacks unauthorised access to tag without owner's knowledge possible up to 50 cm activating RFID tag requires powerful field! aka virtual pickpocketing variant: relay attack [Engelhardt et al., Extending ISO/IEC Type A eavesdropping range using higher harmonics. In: SmartSysTech 2013] 10
11 Antenne for max. activation distance ISO14443 card can be used at 50 cm max, but width of gate at 80 cm works better. [Rene Habraken et al., An RFID Skimming Gate Using Higher Harmonics, RFIDSec 2015] 11
12 Anti-collision Additional complexity of contactless cards: several cards may be activated by reader anti-collision protocol needed for terminal to select one card to talk to: 1. tags report some number when actived 2. terminal chooses which number to talk to Note: this can be a privacy risk! most tags send out fixed number only few tags (eg most passports) report a random one You can check this using an NFC app on your smartphone. 12
13 NFC 13
14 NFC = Near Field Communication Implemented in mobile phones Compatible with ISO Phone can act as 1. reader (active mode) with an ISO tag 2. tag (passive mode) with an ISO tag 3. in NFC peer mode to talk to other NFC phone
15 Inside an NFC phone baseband processor Host CPU NFC controller, connected to phone s NFC antenna, determines which processor handles or can initiate NFC traffic, for each of the three modes embedded SE SIM NFC Controller Reader 15
16 inside an NFC phone NFC traffic can be handled by a. main processor (running say Android) b. embedded Secure Element (SE) in the phone c. SIM card using one of the unused ISO7816 contacts SIM is also a Secure Element, but removable one These processors offer very different security levels SEs (b&c) have smaller TCB and betterphysical protection Different parties control which software can be installed these processors: telco controls SIM phone manufacturer controls embedded SE less control over main processor, esp. when rooted 16
17 NFC modes & processor Possible combinations of modes & processors: Only main CPU can act as reader & NFC peer mode The SEs can only act in card mode this may even work without the phone s battery On some phones, the main processor can also act as card. This is called Host Card Emulation (HCE) Android has HCE since
18 Difference in solutions for mobile payments ING mobile payment uses HCE so only works with Android 4.4 or newer Rabo mobile payment uses either the phone s SE (only on some Samsung models) or a special KPN SIM, which can connect to the phone s NFC antenna What are the differences wrt security? 18
19 Exit hardware security? NFC payment solution that use HCE no longer involves some smartcard-like secure hardware key material stored in main memory, not on embedded SE or SIM Security risks mitigated using white-box crypto, ie obfuscating key in memory one-shot keys: a key can only be used for one transaction, after which phone requests a new one The online key server will still use secure hardware, but a Hardware Security Module (HSM) rather than a smartcard 19
20 Re-enter hardware security? Phones can provide hardware security for main processor for storage and/or processing Secure Key Storage hardware for storing & using keys eg Android Secure Key Storage but Android still in the TCB for access control to key store TEE (Trusted Execution Environment) hardware support in the main CPU to segregate trusted and untrusted applications TEE can provide a trusted path for I/O to the user, via screen & keyboard/touch screen, unlike a smartcard eg ARM TrustZone which is used by Samsung KNOX Android no longer in the TCB for access control or I/O 20
21 MIFARE Classic & Ultralight 21
22 MIFARE widely used proprietary standard by NXP (formerly Philips) closely related to and basis for - ISO14443 A several versions, incl. MIFARE Ultralight, provides only memory with some write restrictions (locking) MIFARE Classic, also provides authentication and encryption by proprietary CRYPTO-1 algorithm Crypto-1 has been logically reverse-engineered & broken. [Flavio Garcia et al., Dismantling MIFARE Classic, ESORICS 2008] [Carlo Meijer & Roel Verdult, Ciphertext-only Cryptanalysis on Hardened Mifare Classic Cards, CCS 2015] 22
23 or google for MIFARE & youtube 23
24 People still choosing crappy crypto The RFID card used for authentication at a EV (Electric Vehicle) charge points is... a Mifare Classic Worse still, it simply uses the card's UID for identification. There is no authentication with some challenge-response protocol using a crypto key 24
25 Other RFID tags with (broken) propietary crypto Investigated & broken by Radboud cryptanalysis team: Flavio Garcia, Gerhard de Koning Gans, and Roel Verdult ATMEL SecureMemory, CryptoMemory and CryptoRF HID iclass, iclass Elite Hitag2 (used in car keys) Megamos crypto (used in car immobilisers) Moral of the story: don t use proprietary crypto, obviously 25
26 Common weakness, irrespective of crypto used 75% of MIFARE RFID applications use default (transport) keys or keys used in examples in documentation [Lukas Grunwald, DEFCON14, 2007] A0A1A2A3A4A5 is an initial transport key that many tags ship with. Googling for A0A1A2A3A4A5 produces links to documentation with other example keys to try! 26
27 MIFARE Ultralight No keys or crypto to protect memory access Relies on read-only and write once memory for security Memory organised in 16 pages of 4 bytes first part is read-only includes 7 byte serial number second part is One Time Programmable (OTP) you can write 1's, not 0's includes data for locking third part is readable & writable NB security only provided by OTP, by locking pages, and having signed/encrypted data in pages, where crypto is done by terminals, not the tag 27
28 Fundamental weakness No way to protect against spoofing of tags. Ghost device for spoofing RFID signals 28
29 MIFARE Ultralight memory layout read only read/ write Page byte 0 byte 1 byte 2 byte 3 0 sn0 sn1 sn2 checksum 1 sn3 sn4 sn5 sn6 2 checksum??? lock 0 lock1 3 OTP 0 OTP 1 OTP 2 OTP serial no OTP application data
30 MIFARE ultralight memory access control 2 bytes for locking: 12 bits to lock data pages : L i 1 bit to lock OTP area (page 3) : L opt 3 bits to block locking of OTP, pp 4-9 and 10-15: All these bites are OTP BL OTP, BL 4-9, BL L 7 L 6 L 5 L 4 L OTP BL BL 4-9 BL OTP L 15 L 14 L 13 L 12 L 11 L 10 L 9 L 8 30
31 OV card MIFARE Ultralight for disposable tickets lock bytes initially 0x00F0, locking pages data in pages can still be read lock bytes set to 0xF8FF to invalidate card two bytes of the OTP used as counter in unary style, eg means one ride left pages 4-7 and 8-11 used to record last two transactions meaning of certain bits clear 000=purchase, 001=check in, 010=check out, 110=transfer pages used for unknown card-specific data [Source "Security Evaluation of the disposable OV chipkaart", by UvA students Pieter Siekerman and Maurits van der Schee, 2007] 31
32 flaw 1 lock bytes initially 0x00F0, set to 0xF8FF to invalidate tag We can change an invalid tag so that some terminals fail to recognize it as invalid; can you guess the flaw? remaining 3 lock bits can still be set to one, so that lock bytes become 0xFFFF flaw in terminals: tags with lock bytes 0xF8FF are recognized as invalid, but tags with 0xFFFF are not Can you guess the terminal code that causes this? enables easy experiments with "invalid" cards 32
33 flaw 2 on check-in, counter is incremented and transaction info written to pages 4-7 on check-out, transaction info written to pages 9-11 Can you guess how a ticket could be used for multiple checkouts? by rewriting the transaction info (which is not write protected), we can use the same card to check-out again How could you prevent this flaw? 33
34 flaw 3 More serious, and reportedly fixed Attack found purchase single/multiple ride ticket back-up data in page 4-11 (incl. purchase transaction) use card, checking in (which increases the OTP counter) and checking out (which does not) rewrite content of page 4-11, overwriting check-in and check-out transactions with purchase transaction card can now be used again, but OTP counter is not increased: infinite number of free rides Cause?? Counter not checked & increased if purchase transaction is found in memory? Or: counter is not increased but given a fixed value 1 if purchase transaction is found? 34
RFID tags. Inductive coupling is used for. energy transfer to card transmission of clock signal data transfer
 RFID 1 RFID tags RFID = Radio-Frequency IDentification RFID devices are called tags or transponders More powerful RFID tags can be called (contactless) smartcards Inductive coupling is used for energy
RFID 1 RFID tags RFID = Radio-Frequency IDentification RFID devices are called tags or transponders More powerful RFID tags can be called (contactless) smartcards Inductive coupling is used for energy
Fundamentals of Near Field Communication (NFC) Tvrtko Barbarić NXP Semiconductors
 Fundamentals of Near Field Communication (NFC) Tvrtko Barbarić NXP Semiconductors Automotive Identification Wireless Infrastructure Lighting Industrial Mobile Consumer Computing Global player with local
Fundamentals of Near Field Communication (NFC) Tvrtko Barbarić NXP Semiconductors Automotive Identification Wireless Infrastructure Lighting Industrial Mobile Consumer Computing Global player with local
Attacking smartcards. Erik Poll. Digital Security
 Attacking smartcards Erik Poll Digital Security Smartcard security Smartcards are not 100% secure ongoing arms race of attacks & countermeasures Ten year old cards may be easily broken today Crucial question:
Attacking smartcards Erik Poll Digital Security Smartcard security Smartcards are not 100% secure ongoing arms race of attacks & countermeasures Ten year old cards may be easily broken today Crucial question:
CRYPTOGRAPHIC ENGINEERING ASSIGNMENT II Theoretical: Design Weaknesses in MIFARE Classic
 CRYPTOGRAPHIC ENGINEERING ASSIGNMENT II Theoretical: Design Weaknesses in MIFARE Classic Özgecan Payzin, s4159721 ozgecan.payzin@student.ru.nl April 1, 2013 1 Introduction The MIFARE Classic is one of
CRYPTOGRAPHIC ENGINEERING ASSIGNMENT II Theoretical: Design Weaknesses in MIFARE Classic Özgecan Payzin, s4159721 ozgecan.payzin@student.ru.nl April 1, 2013 1 Introduction The MIFARE Classic is one of
NFC is the double click in the internet of the things
 NFC is the double click in the internet of the things Name Frank Graeber, Product Manager NFC Subject 3rd Workshop on RFID Systems and Technologies Date 12.06.2007 Content NFC Introduction NFC Technology
NFC is the double click in the internet of the things Name Frank Graeber, Product Manager NFC Subject 3rd Workshop on RFID Systems and Technologies Date 12.06.2007 Content NFC Introduction NFC Technology
Smartcards. ISO 7816 & smartcard operating systems. Erik Poll Digital Security Radboud University Nijmegen
 Smartcards ISO 7816 & smartcard operating systems Erik Poll Digital Security Radboud University Nijmegen 1 Standard for contact smartcards ISO7816 7816-1 Physical characteristics 7816-2 Dimension & size
Smartcards ISO 7816 & smartcard operating systems Erik Poll Digital Security Radboud University Nijmegen 1 Standard for contact smartcards ISO7816 7816-1 Physical characteristics 7816-2 Dimension & size
Dismantling MIFARE Classic
 Institute for Computing and Information Sciences, Radboud University Nijmegen, The Netherlands. ESORICS 2008 Joint work with: Gerhard de Koning Gans, Ruben Muijrers, Peter van Rossum, Roel Verdult, Ronny
Institute for Computing and Information Sciences, Radboud University Nijmegen, The Netherlands. ESORICS 2008 Joint work with: Gerhard de Koning Gans, Ruben Muijrers, Peter van Rossum, Roel Verdult, Ronny
DEFCON 26 - Playing with RFID. by Vanhoecke Vinnie
 DEFCON 26 - Playing with RFID by Vanhoecke Vinnie 1. Contents 2. Introduction... 3 3. RFID Frequencies... 3 Low frequency... 3 High frequency... 3 Ultra-high frequency... 3 4. MIFARE... 4 MIFARE Classic...
DEFCON 26 - Playing with RFID by Vanhoecke Vinnie 1. Contents 2. Introduction... 3 3. RFID Frequencies... 3 Low frequency... 3 High frequency... 3 Ultra-high frequency... 3 4. MIFARE... 4 MIFARE Classic...
Flavio D. Garcia Gerhard de Koning Gans Roel Verdult Exposing iclass Key Diversification
 Usenix WOOT 2011 Flavio D. Garcia Gerhard de Koning Gans Roel Verdult Exposing iclass Key Diversification Contents Introduction RFID iclass and Picopass Key Diversification iclass Key Diversification DES
Usenix WOOT 2011 Flavio D. Garcia Gerhard de Koning Gans Roel Verdult Exposing iclass Key Diversification Contents Introduction RFID iclass and Picopass Key Diversification iclass Key Diversification DES
RFID DEFCON 26 Vinnie Vanhoecke Lorenzo Bernardi
 RFID Workshop @ DEFCON 26 Vinnie Vanhoecke Lorenzo Bernardi Page 1 Content Introduction RFID theory Basics Tools Protocols Mifare Challenges Page 2 RFID basics RFID theory: RFID basics RFID = Radio Frequency
RFID Workshop @ DEFCON 26 Vinnie Vanhoecke Lorenzo Bernardi Page 1 Content Introduction RFID theory Basics Tools Protocols Mifare Challenges Page 2 RFID basics RFID theory: RFID basics RFID = Radio Frequency
Security of NFC payments
 Security of NFC payments Olga Korobova Department of Computer Science University of Massachusetts Amherst Abstract Our research objective was to examine the security features implemented by the bank cards
Security of NFC payments Olga Korobova Department of Computer Science University of Massachusetts Amherst Abstract Our research objective was to examine the security features implemented by the bank cards
Evaluation of the feasible attacks against RFID tags for access control systems
 Evaluation of the feasible attacks against RFID tags for access control systems Hristo Dimitrov & Kim van Erkelens University of Amsterdam February 4, 2014 1 / 20 Contents 1 Introduction 2 Background 3
Evaluation of the feasible attacks against RFID tags for access control systems Hristo Dimitrov & Kim van Erkelens University of Amsterdam February 4, 2014 1 / 20 Contents 1 Introduction 2 Background 3
Overview RFID-Systems
 Overview RFID-Systems MSE, Rumc, RFID, 1 References [1] Klaus Finkenzeller, RFID-Handbuch, 5. Auflage, Hanser, 2008. [2] R. Küng, M. Rupf, RFID-Blockkurs, ergänzende MSE-Veranstaltung, ZHAW, 2009. [3]
Overview RFID-Systems MSE, Rumc, RFID, 1 References [1] Klaus Finkenzeller, RFID-Handbuch, 5. Auflage, Hanser, 2008. [2] R. Küng, M. Rupf, RFID-Blockkurs, ergänzende MSE-Veranstaltung, ZHAW, 2009. [3]
NEAR FIELD COMMUNICATION
 NEAR FIELD COMMUNICATION (GUIDED BY:MISS ANUJA V NAIR) BY: REJOY MENDEZ ROLL NO:24 S7 ECE OVERVIEW INTRODUCTION FEATURES OF NFC TECHNOLOGICAL OVERVIEW COMPARISON WITH OTHER TECHNOLOGY SECURITY ASPECTS
NEAR FIELD COMMUNICATION (GUIDED BY:MISS ANUJA V NAIR) BY: REJOY MENDEZ ROLL NO:24 S7 ECE OVERVIEW INTRODUCTION FEATURES OF NFC TECHNOLOGICAL OVERVIEW COMPARISON WITH OTHER TECHNOLOGY SECURITY ASPECTS
Who we are. Eagle1753 (aka Matteo Beccaro) bughardy. (aka Matteo Collura)
 Who we are bughardy Eagle1753 (aka Matteo Beccaro) (aka Matteo Collura) bughardy@cryptolab.net eagle1753@onenetbeyond.org Italian student with passion of IT, networking and pentesting. In 2013 ended his
Who we are bughardy Eagle1753 (aka Matteo Beccaro) (aka Matteo Collura) bughardy@cryptolab.net eagle1753@onenetbeyond.org Italian student with passion of IT, networking and pentesting. In 2013 ended his
Mobile NFC Services Opportunities & Challenges. NGUYEN Anh Ton VNTelecom Conference 31/10/2010
 Mobile NFC Services Opportunities & Challenges NGUYEN Anh Ton VNTelecom Conference 31/10/2010 Agenda 1. Introduction 2. Mobile NFC Overview 3. NFC Ecosystem Key Findings 4. Main NFC challenges 5. What
Mobile NFC Services Opportunities & Challenges NGUYEN Anh Ton VNTelecom Conference 31/10/2010 Agenda 1. Introduction 2. Mobile NFC Overview 3. NFC Ecosystem Key Findings 4. Main NFC challenges 5. What
Security in NFC Readers
 Security in Readers Public Content and security, a different kind of wireless Under the hood of based systems Enhancing the security of an architecture Secure data exchange Information security goals Cryptographic
Security in Readers Public Content and security, a different kind of wireless Under the hood of based systems Enhancing the security of an architecture Secure data exchange Information security goals Cryptographic
Bluetooth mobile solutions APPLICATION NOTE / FAQ. Page 1 on 24
 Bluetooth mobile solutions APPLICATION NOTE / FAQ Page 1 on 24 Table of Contents I. Introduction... 5 II. Bluetooth Smart technology General principles... 5 III. Frequently Asked Questions... 5 A. STid
Bluetooth mobile solutions APPLICATION NOTE / FAQ Page 1 on 24 Table of Contents I. Introduction... 5 II. Bluetooth Smart technology General principles... 5 III. Frequently Asked Questions... 5 A. STid
Near Field Communication Security
 Near Field Communication Security Thomas Patzke 22.04.2015 Who am I... Thomas Patzke (formerly Skora) Who am I... Thomas Patzke (formerly Skora) Started with security related topics somewhere in the 90s
Near Field Communication Security Thomas Patzke 22.04.2015 Who am I... Thomas Patzke (formerly Skora) Who am I... Thomas Patzke (formerly Skora) Started with security related topics somewhere in the 90s
Dear John, Regards, Jaap-Henk
 Date: Tue, 15 Jul 2008 11:20:04 +0200 From: Jaap-Henk Hoepman To: John Young CC: gkoningg[at]sci.ru.nl, flaviog[at]cs.ru.nl, Bart Jacobs Subject:
Date: Tue, 15 Jul 2008 11:20:04 +0200 From: Jaap-Henk Hoepman To: John Young CC: gkoningg[at]sci.ru.nl, flaviog[at]cs.ru.nl, Bart Jacobs Subject:
ELECTRONIC PADLOCK GxP2
 //DATASHEET SALTO GEO Cylinder The next generation of electronic cylinder lock: Fully integrated with the SALTO XS4 platform, SALTO GEO is a versatile, cost effective solution and its compact size and
//DATASHEET SALTO GEO Cylinder The next generation of electronic cylinder lock: Fully integrated with the SALTO XS4 platform, SALTO GEO is a versatile, cost effective solution and its compact size and
AN MIFARE Type Identification Procedure. Application note COMPANY PUBLIC. Rev August Document information
 Document information Info Content Keywords, 14443 Abstract This document describes how to differentiate between the members of the card IC family. 14443-3 describes the initialization and anti-collision
Document information Info Content Keywords, 14443 Abstract This document describes how to differentiate between the members of the card IC family. 14443-3 describes the initialization and anti-collision
Power Analysis of Atmel CryptoMemory Recovering Keys from Secure EEPROMs
 Power Analysis of Atmel CryptoMemory Recovering Keys from Secure EEPROMs Josep Balasch 1, Benedikt Gierlichs 1, Roel Verdult 2, Lejla Batina 1,2, and Ingrid Verbauwhede 1 1 ESAT/COSIC, KU Leuven 2 ICIS/Digital
Power Analysis of Atmel CryptoMemory Recovering Keys from Secure EEPROMs Josep Balasch 1, Benedikt Gierlichs 1, Roel Verdult 2, Lejla Batina 1,2, and Ingrid Verbauwhede 1 1 ESAT/COSIC, KU Leuven 2 ICIS/Digital
Connecting to the future ELATEC RFID SYSTEMS
 Connecting to the future ELATEC RFID SYSTEMS ELATEC GmbH Enabling success RFID SYSTEMS Focus on the goal Adaptable to our customer s requirements, Elatec products and technologies are the core that has
Connecting to the future ELATEC RFID SYSTEMS ELATEC GmbH Enabling success RFID SYSTEMS Focus on the goal Adaptable to our customer s requirements, Elatec products and technologies are the core that has
Secure Elements 101. Sree Swaminathan Director Product Development, First Data
 Secure Elements 101 Sree Swaminathan Director Product Development, First Data Secure Elements Secure Element is a tamper resistant Smart Card chip that facilitates the secure storage and transaction of
Secure Elements 101 Sree Swaminathan Director Product Development, First Data Secure Elements Secure Element is a tamper resistant Smart Card chip that facilitates the secure storage and transaction of
Idesco OEM modules. Compact Module: 40,9 x 39,0 mm. Module: 72 x 37,8 x18 mm. 125 khz Prox. 13,56 MHz UID. MIFARE DESFire. MIFARE DESFire LEGIC - 1 -
 : Compact : 40,9 x 39,0 mm 125 khz Prox 13,56 MHz UID LEGIC - 1 - 7 AH EM4102, Sokymat Unique, Hitag2, HIDProx RS-232, Wiegand, USB, Clock&Data, USB Hi on request. 2 FET outputs, 1 General purpose input
: Compact : 40,9 x 39,0 mm 125 khz Prox 13,56 MHz UID LEGIC - 1 - 7 AH EM4102, Sokymat Unique, Hitag2, HIDProx RS-232, Wiegand, USB, Clock&Data, USB Hi on request. 2 FET outputs, 1 General purpose input
Advanced. Card. Systems. Ltd. by Eric Lee. June, Advanced Card Systems Ltd. Room 2910, The Center, 99 Queen's Road Central, Hong Kong.
 Advanced Card Systems Ltd. by Eric Lee June, 2004 1 2 What is a Contactless Smart Card? A kind of Smart Card which can be accessed without electrical contact A type of RFID tag What is RFID (Radio Frequency
Advanced Card Systems Ltd. by Eric Lee June, 2004 1 2 What is a Contactless Smart Card? A kind of Smart Card which can be accessed without electrical contact A type of RFID tag What is RFID (Radio Frequency
WHAT FUTURE FOR CONTACTLESS CARD SECURITY?
 WHAT FUTURE FOR CONTACTLESS CARD SECURITY? Alain Vazquez (alain.vazquez@louveciennes.sema.slb.com) 1/27 AV Contents Major contactless features : summary Contactless major constraints Major security issues
WHAT FUTURE FOR CONTACTLESS CARD SECURITY? Alain Vazquez (alain.vazquez@louveciennes.sema.slb.com) 1/27 AV Contents Major contactless features : summary Contactless major constraints Major security issues
Fare Media: Past, Present and Future. Hassan Tavassoli APTA Fare Collection Workshop San Diego, California March 29, 2010
 Fare Media: Past, Present and Future Hassan Tavassoli APTA Fare Collection Workshop San Diego, California March 29, 2010 Evolution of Transit Fare Media Other Form Factors (contactless tokens and tags,
Fare Media: Past, Present and Future Hassan Tavassoli APTA Fare Collection Workshop San Diego, California March 29, 2010 Evolution of Transit Fare Media Other Form Factors (contactless tokens and tags,
Notes on NFC ticket design on MIFARE Ultralight C (updated ) Tuomas Aura. Application is a data structure
 Notes on NFC ticket design on MIFARE Ultralight C (updated 2017-12-13) Tuomas Aura Application is a data structure The inexpensive smart cards used for ticketing applications, such as MIFARE Ultralight,
Notes on NFC ticket design on MIFARE Ultralight C (updated 2017-12-13) Tuomas Aura Application is a data structure The inexpensive smart cards used for ticketing applications, such as MIFARE Ultralight,
JMY600 Series IC Card Module
 MIFARE & ISO14443A & ISO14443B & ISO7816 & ISO15693 IC CARD MODULE JMY600 Series IC Card Module MIFARE Plus Card Operation Guide (Revision 1.00) Jinmuyu Electronics Co., LTD April 7, 2015 Please read this
MIFARE & ISO14443A & ISO14443B & ISO7816 & ISO15693 IC CARD MODULE JMY600 Series IC Card Module MIFARE Plus Card Operation Guide (Revision 1.00) Jinmuyu Electronics Co., LTD April 7, 2015 Please read this
ACR1255U-J1 Secure Bluetooth NFC Reader
 ACR1255U-J1 Secure Bluetooth NFC Reader Technical Specifications V1.07 Subject to change without prior notice Table of Contents 1.0. Introduction... 3 1.1. Smart Card Reader... 3 1.2. Compact Design...
ACR1255U-J1 Secure Bluetooth NFC Reader Technical Specifications V1.07 Subject to change without prior notice Table of Contents 1.0. Introduction... 3 1.1. Smart Card Reader... 3 1.2. Compact Design...
ABOUT CIVINTEC PLATFORM PRODUCT RANGE CIVINTEC GLOBAL. World Leading OEM/ODM Designer & Manufacturer
 CIVINTEC GLOBAL 01 World Leading OEM/ODM Designer & Manufacturer ABOUT CIVINTEC CIVINTEC is the world leading designer and manufacturer of smart card terminals and devices, established in 2006 and focusing
CIVINTEC GLOBAL 01 World Leading OEM/ODM Designer & Manufacturer ABOUT CIVINTEC CIVINTEC is the world leading designer and manufacturer of smart card terminals and devices, established in 2006 and focusing
Mobile Security Fall 2014
 Mobile Security Fall 2014 Patrick Tague Class #8 NFC & Mobile Payment 1 Announcements Reminder: first group of SoW presentations will be today, starting ~1/2 way through class Written SoW is a separate
Mobile Security Fall 2014 Patrick Tague Class #8 NFC & Mobile Payment 1 Announcements Reminder: first group of SoW presentations will be today, starting ~1/2 way through class Written SoW is a separate
Hacking new NFC cards
 Hacking new NFC cards NTAG2x, Ultralight EV1/C, Desfire EV2, ISO-15693, meal EMV cards abyssal see #brmlab IRC for contact 6.12.2018 New cards Mifare Ultralight C, Ultralight EV1 descendant of simple Ultralight
Hacking new NFC cards NTAG2x, Ultralight EV1/C, Desfire EV2, ISO-15693, meal EMV cards abyssal see #brmlab IRC for contact 6.12.2018 New cards Mifare Ultralight C, Ultralight EV1 descendant of simple Ultralight
ACR122S NFC Reader. Datenblatt / Specifications. Technical Specifications
 Datenblatt / Specifications NFC Reader Technical Specifications Table of Contents 1.0. Introduction 3 2.0. Features 4 3.0. Typical Applications 5 4.0. Technical Specifications 6 Page 2 of 6 1.0. Introduction
Datenblatt / Specifications NFC Reader Technical Specifications Table of Contents 1.0. Introduction 3 2.0. Features 4 3.0. Typical Applications 5 4.0. Technical Specifications 6 Page 2 of 6 1.0. Introduction
A Multi-Application Smart-Card ID System for George Mason University. - Suraj Ravichandran.
 A Multi-Application Smart-Card ID System for George Mason University - Suraj Ravichandran. Current System Magnetic Swipe Card based ID The card has three tracks They each store the following: Name, G#
A Multi-Application Smart-Card ID System for George Mason University - Suraj Ravichandran. Current System Magnetic Swipe Card based ID The card has three tracks They each store the following: Name, G#
Security in Mifare Classic RFID
 Security in Mifare Classic RFID Project 3, EITF55 Security, 2018 Issued 2018-01-15 Ben Smeets Dept. of Electrical and Information Technology, Lund University, Sweden Version 2018-01-15 What you will learn
Security in Mifare Classic RFID Project 3, EITF55 Security, 2018 Issued 2018-01-15 Ben Smeets Dept. of Electrical and Information Technology, Lund University, Sweden Version 2018-01-15 What you will learn
XS4 LOCKER LOCK Lx050
 //DATASHEET SALTO XS4 Electronic locker locks: SALTO XS4 electronic locker locks are designed to provide a high level of security protection and control access to a wide range of lockers, cupboards, display
//DATASHEET SALTO XS4 Electronic locker locks: SALTO XS4 electronic locker locks are designed to provide a high level of security protection and control access to a wide range of lockers, cupboards, display
NFC Technology Overview Jonathan Main MasterCard Worldwide Chairman, Technical Committee
 NFC Technology Overview Jonathan Main MasterCard Worldwide Chairman, Technical Committee September 2009 Agenda Review of Use Cases Architecture Overview Relationship to Other Standards Status of NFC Forum
NFC Technology Overview Jonathan Main MasterCard Worldwide Chairman, Technical Committee September 2009 Agenda Review of Use Cases Architecture Overview Relationship to Other Standards Status of NFC Forum
ACR1252U. NFC Forum Certified Reader. Technical Specifications V1.03. Subject to change without prior notice.
 ACR1252U NFC Forum Certified Reader Technical Specifications V1.03 Subject to change without prior notice Table of Contents 1.0. Introduction... 3 2.0. Features... 4 3.0. Typical Applications... 5 4.0.
ACR1252U NFC Forum Certified Reader Technical Specifications V1.03 Subject to change without prior notice Table of Contents 1.0. Introduction... 3 2.0. Features... 4 3.0. Typical Applications... 5 4.0.
Products and solutions for Secure Wearables
 Products and solutions for Secure Wearables Content Introduction... 3 Security... 4 Secure element and integrated NFC boosted solutions for wearable devices... 4 Secure element... 5 NFC booster and nfc
Products and solutions for Secure Wearables Content Introduction... 3 Security... 4 Secure element and integrated NFC boosted solutions for wearable devices... 4 Secure element... 5 NFC booster and nfc
Leveraging the full potential of NFC to reinvent physical access control. Friday seminar,
 Leveraging the full potential of NFC to reinvent physical access control Wireless@KTH Friday seminar, 2012-08-31 NFC (Near Field Communication) A new radio communication technology for mobile phones Uses
Leveraging the full potential of NFC to reinvent physical access control Wireless@KTH Friday seminar, 2012-08-31 NFC (Near Field Communication) A new radio communication technology for mobile phones Uses
Corey Benninger Max Sobell
 Corey Benninger Max Sobell NFC Overview What is NFC? Hardware basics behind NFC Antennas and waveforms Tags and access control NFC Data Exchange Format (NDEF) NFC Application Attacks Privacy Mobile Wallets
Corey Benninger Max Sobell NFC Overview What is NFC? Hardware basics behind NFC Antennas and waveforms Tags and access control NFC Data Exchange Format (NDEF) NFC Application Attacks Privacy Mobile Wallets
NFC Equipped Smartphones
 NFC Equipped Smartphones A two-edged sword for library RFID systems VALA Conference 2014 www.sybis.com.au NFC equipped Smartphones NFC Card Emulation Mode Near Field Communications n A form of RFID contactless
NFC Equipped Smartphones A two-edged sword for library RFID systems VALA Conference 2014 www.sybis.com.au NFC equipped Smartphones NFC Card Emulation Mode Near Field Communications n A form of RFID contactless
AT88RF1354 SPI User Guide For CryptoRF
 AT88RF1354 SPI User Guide For CryptoRF Table of Contents Section 1 Introduction... 1-1 1.1 Product Description... 1-1 1.2 System Diagram... 1-1 1.3 Scope...1-2 1.4 Conventions... 1-2 Section 2 AT88RF1354
AT88RF1354 SPI User Guide For CryptoRF Table of Contents Section 1 Introduction... 1-1 1.1 Product Description... 1-1 1.2 System Diagram... 1-1 1.3 Scope...1-2 1.4 Conventions... 1-2 Section 2 AT88RF1354
The MIFARE Classic Story
 The MIFARE Classic Story Keith E. Mayes Information Security Group Smart Card Centre Royal Holloway, University of London Egham, U.K. keith.mayes@rhul.ac.uk Carlos Cid Information Security Group Royal
The MIFARE Classic Story Keith E. Mayes Information Security Group Smart Card Centre Royal Holloway, University of London Egham, U.K. keith.mayes@rhul.ac.uk Carlos Cid Information Security Group Royal
1.264 Lecture 26. Security protocols. Next class: Anderson chapter 4. Exercise due before class
 1.264 Lecture 26 Security protocols Next class: Anderson chapter 4. Exercise due before class 1 Encryption Encryption is the process of: Transforming information (referred to as plaintext) Using an algorithm
1.264 Lecture 26 Security protocols Next class: Anderson chapter 4. Exercise due before class 1 Encryption Encryption is the process of: Transforming information (referred to as plaintext) Using an algorithm
Relay Attacks on Secure Elementenabled
 Relay Attacks on Secure Elementenabled Mobile Devices Virtual Pickpocketing Revisited Michael Roland University of Applied Sciences Upper Austria,, Austria SEC2012 IFIP International Information Security
Relay Attacks on Secure Elementenabled Mobile Devices Virtual Pickpocketing Revisited Michael Roland University of Applied Sciences Upper Austria,, Austria SEC2012 IFIP International Information Security
XS4 LOCKER LOCK Lx050
 //DATASHEET SALTO XS4 Electronic locker locks: SALTO XS4 electronic locker locks are designed to provide a high level of security protection and control access to a wide range of lockers, cupboards, display
//DATASHEET SALTO XS4 Electronic locker locks: SALTO XS4 electronic locker locks are designed to provide a high level of security protection and control access to a wide range of lockers, cupboards, display
ACR120 Contactless Reader/Writer
 ACR120 Contactless Reader/Writer Technical Specifications Subject to change without prior notice Table of Contents 1.0. Introduction... 3 2.0. Features... 4 3.0. Typical Applications... 5 4.0. Technical
ACR120 Contactless Reader/Writer Technical Specifications Subject to change without prior notice Table of Contents 1.0. Introduction... 3 2.0. Features... 4 3.0. Typical Applications... 5 4.0. Technical
RFID and Wiegand. Short manual. Version 0.1. Date Log v0.1. Adatis GmbH & Co.KG Seite 1 von 8
 RFID and Wiegand Short manual Version 0.1 Author Sandra Gilge Date 02.05.2018 Log v0.1 Adatis GmbH & Co.KG Seite 1 von 8 Inhalt 1 RFID 3 1.1 Introduction 3 1.2 Overview 3 1.3 Card types 3 1.4 Access Controll
RFID and Wiegand Short manual Version 0.1 Author Sandra Gilge Date 02.05.2018 Log v0.1 Adatis GmbH & Co.KG Seite 1 von 8 Inhalt 1 RFID 3 1.1 Introduction 3 1.2 Overview 3 1.3 Card types 3 1.4 Access Controll
Door release elements and Multitechnology-Reader
 Door release elements and Multitechnology-Reader High secure door release control deister electronic is an established supplier of RFID based readers. doorloxx supports all card technologies in the market
Door release elements and Multitechnology-Reader High secure door release control deister electronic is an established supplier of RFID based readers. doorloxx supports all card technologies in the market
NEAR FIELD COMMUNICATION - THE FUTURE TECHNOLOGY FOR AN INTERACTIVE WORLD
 Int. J. Engg. Res. & Sci. & Tech. 2013 Jignesh Patel and Badal Kothari, 2013 Research Paper ISSN 2319-5991 www.ijerst.com Vol. 2, No. 2, May 2013 2013 IJERST. All Rights Reserved NEAR FIELD COMMUNICATION
Int. J. Engg. Res. & Sci. & Tech. 2013 Jignesh Patel and Badal Kothari, 2013 Research Paper ISSN 2319-5991 www.ijerst.com Vol. 2, No. 2, May 2013 2013 IJERST. All Rights Reserved NEAR FIELD COMMUNICATION
Digital Payments Security Discussion Secure Element (SE) vs Host Card Emulation (HCE) 15 October Frazier D. Evans
 Digital Payments Security Discussion Secure Element (SE) vs Host Card Emulation (HCE) 15 October 2014 Frazier D. Evans Evans_Frazier@bah.com There are four key areas that need to be investigated when talking
Digital Payments Security Discussion Secure Element (SE) vs Host Card Emulation (HCE) 15 October 2014 Frazier D. Evans Evans_Frazier@bah.com There are four key areas that need to be investigated when talking
Authentication Technologies
 Authentication Technologies 1 Authentication The determination of identity, usually based on a combination of something the person has (like a smart card or a radio key fob storing secret keys), something
Authentication Technologies 1 Authentication The determination of identity, usually based on a combination of something the person has (like a smart card or a radio key fob storing secret keys), something
BL75R06SM 8K-bit EEPROM Contactless smart card chip
 Description BL75R06SM consists of the RF-Interface, the Digital Control Unit and the 8 Kbit EEPROM. Operating distance is up to 10cm(depending on antenna geometry). The communication layer complies to
Description BL75R06SM consists of the RF-Interface, the Digital Control Unit and the 8 Kbit EEPROM. Operating distance is up to 10cm(depending on antenna geometry). The communication layer complies to
How to NFC. Nick Pelly & Jeff Hamilton May 10 th, feedback: hashtags: #io2011 #Android questions:
 How to NFC Nick Pelly & Jeff Hamilton May 10 th, 2011 feedback: http://goo.gl/syzqy hashtags: #io2011 #Android questions: http://goo.gl/mod/ekbn Agenda What is NFC Why use NFC How to NFC 101 How to NFC
How to NFC Nick Pelly & Jeff Hamilton May 10 th, 2011 feedback: http://goo.gl/syzqy hashtags: #io2011 #Android questions: http://goo.gl/mod/ekbn Agenda What is NFC Why use NFC How to NFC 101 How to NFC
NFC Identity and Access Control
 NFC Identity and Access Control Peter Cattaneo Vice President, Business Development Agenda Basics NFC User Interactions Architecture (F)ICAM Physical Access Logical Access Future Evolution 2 NFC Identity
NFC Identity and Access Control Peter Cattaneo Vice President, Business Development Agenda Basics NFC User Interactions Architecture (F)ICAM Physical Access Logical Access Future Evolution 2 NFC Identity
RFID Beginner s Kit Command Reference Manual Copyright 2003 Intensecomp Pte Ltd All rights reserved.
 RFID Beginner s Kit Command Reference Manual Copyright 2003 Intensecomp Pte td All rights reserved. Intensecomp Pte td 190 Middle Road, #19-05,Fortune Centre, Singapore 188979 Tel: +65 6769 5772 Fax: +65
RFID Beginner s Kit Command Reference Manual Copyright 2003 Intensecomp Pte td All rights reserved. Intensecomp Pte td 190 Middle Road, #19-05,Fortune Centre, Singapore 188979 Tel: +65 6769 5772 Fax: +65
THE BEST OF BOTH WORLDS. Dual-frequency RAIN RFID cards add flexibility while increasing smarts and security. By Mahdi Mekic, NXP Semiconductors
 THE BEST OF BOTH WORLDS Dual-frequency RAIN RFID cards add flexibility while increasing smarts and security By Mahdi Mekic, NXP Semiconductors A new generation of contactless smartcards, built to support
THE BEST OF BOTH WORLDS Dual-frequency RAIN RFID cards add flexibility while increasing smarts and security By Mahdi Mekic, NXP Semiconductors A new generation of contactless smartcards, built to support
ACR1251U-A1 USB NFC Reader with SAM Slot
 ACR1251U-A1 USB NFC Reader with SAM Slot Technical Specifications V1.05 Subject to change without prior notice Table of Contents 1.0. Introduction... 3 2.0. Features... 4 3.0. Typical Applications... 5
ACR1251U-A1 USB NFC Reader with SAM Slot Technical Specifications V1.05 Subject to change without prior notice Table of Contents 1.0. Introduction... 3 2.0. Features... 4 3.0. Typical Applications... 5
Considering the Security of Mobile Commerce and Banking. Professor Keith Mayes Information Security Group ACE-CSR
 Considering the Security of Mobile Commerce and Banking Professor Keith Mayes Information Security Group ACE-CSR Information Security Group (ISG) Established 1992 17 Full-time Academics, 8+ Research Assistants
Considering the Security of Mobile Commerce and Banking Professor Keith Mayes Information Security Group ACE-CSR Information Security Group (ISG) Established 1992 17 Full-time Academics, 8+ Research Assistants
Mobile Access is the Killer App The Path to Flexible, Secure Credentials Brandon Arcement Senior Director, Product Marketing April 8, 2019
 Powering the trusted identities of the world s people, places & things Mobile Access is the Killer App The Path to Flexible, Secure Credentials Brandon Arcement Senior Director, Product Marketing April
Powering the trusted identities of the world s people, places & things Mobile Access is the Killer App The Path to Flexible, Secure Credentials Brandon Arcement Senior Director, Product Marketing April
Frequently Asked Questions
 Frequently Asked Questions 1. What is Samsung Pay? Samsung Pay is a secure and easy-to-use mobile payment service. You can add your SBI Debit Card issued on Visa and MasterCard platform on your Samsung
Frequently Asked Questions 1. What is Samsung Pay? Samsung Pay is a secure and easy-to-use mobile payment service. You can add your SBI Debit Card issued on Visa and MasterCard platform on your Samsung
mifare DESFire Contactless Multi-Application IC with DES and 3DES Security MF3 IC D40 INTEGRATED CIRCUITS Objective Short Form Specification
 INTEGRATED CIRCUITS mifare DESFire Contactless Multi-Application IC with DES and 3DES Security MF3 IC D4 Objective January 23 Revision 1.1 PUBLIC Philips Semiconductors CONTENTS 1 FEATURES...3 1.1 RF Interface:
INTEGRATED CIRCUITS mifare DESFire Contactless Multi-Application IC with DES and 3DES Security MF3 IC D4 Objective January 23 Revision 1.1 PUBLIC Philips Semiconductors CONTENTS 1 FEATURES...3 1.1 RF Interface:
IS23SC4439 Preliminary. 1K bytes EEPROM Contactless Smart Card Conform to ISO/IEC 14443A Standard. Table of contents
 1K bytes EEPROM Contactless Smart Card Conform to ISO/IEC 14443A Standard Table of contents 1 Features 2 2 General Description 2 3 Typical Transaction Time 2 4 Functional Description 2 41 Block Description
1K bytes EEPROM Contactless Smart Card Conform to ISO/IEC 14443A Standard Table of contents 1 Features 2 2 General Description 2 3 Typical Transaction Time 2 4 Functional Description 2 41 Block Description
Multifunctional Identifiers ESMART Access
 AIR TAG Multifunctional Identifiers ESMART Access Contents ESMART Access technology 4 Key advantages of ESMART Access 6 Multifunctional identifiers ESMART Access 8 AIRTAG RFID keyfobs 9 Silicone RFID
AIR TAG Multifunctional Identifiers ESMART Access Contents ESMART Access technology 4 Key advantages of ESMART Access 6 Multifunctional identifiers ESMART Access 8 AIRTAG RFID keyfobs 9 Silicone RFID
Near Field Communication: IoT with NFC. Dominik Gruntz Fachhochschule Nordwestschweiz Institut für Mobile und Verteilte Systeme
 Near Field Communication: IoT with NFC Dominik Gruntz Institut für Mobile und Verteilte Systeme NFC Experience at FHNW 2005/06 First NFC demonstrator (with Siemens CX70 Emoty) NFC was included in a removable
Near Field Communication: IoT with NFC Dominik Gruntz Institut für Mobile und Verteilte Systeme NFC Experience at FHNW 2005/06 First NFC demonstrator (with Siemens CX70 Emoty) NFC was included in a removable
Practical Attack Scenarios on Secure Element-enabled Mobile Devices
 Practical Attack Scenarios on Secure Element-enabled Mobile Devices Michael Roland University it of Applied Sciences Upper Austria,, Austria 4 th International Workshop on Near Field Communication 13 March
Practical Attack Scenarios on Secure Element-enabled Mobile Devices Michael Roland University it of Applied Sciences Upper Austria,, Austria 4 th International Workshop on Near Field Communication 13 March
LOCK IT AND STILL LOSE IT ON THE (IN)SECURITY OF AUTOMOTIVE REMOTE KEYLESS ENTRY SYSTEMS
 LOCK IT AND STILL LOSE IT ON THE (IN)SECURITY OF AUTOMOTIVE REMOTE KEYLESS ENTRY SYSTEMS FLAVIO GARCIA, DAVID OSWALD, TIMO KASPER, PIERRE PAVLIDES PRESENTED BY JACOB BEDNARD, WAYNE STATE UNIVERSITY CSC5991
LOCK IT AND STILL LOSE IT ON THE (IN)SECURITY OF AUTOMOTIVE REMOTE KEYLESS ENTRY SYSTEMS FLAVIO GARCIA, DAVID OSWALD, TIMO KASPER, PIERRE PAVLIDES PRESENTED BY JACOB BEDNARD, WAYNE STATE UNIVERSITY CSC5991
ACR120 Technical Specifications Version 4.00
 Datenblatt / Specifications ACR120 Contactless Reader/Writer Otto-Hesse-Straße 19 / T5 D-64293 Darmstadt Phone +49 6151 9926567 Fax +49 6151 3689296 1.0 Introduction The ACR120 is a compact and cost-effective
Datenblatt / Specifications ACR120 Contactless Reader/Writer Otto-Hesse-Straße 19 / T5 D-64293 Darmstadt Phone +49 6151 9926567 Fax +49 6151 3689296 1.0 Introduction The ACR120 is a compact and cost-effective
JMY600 Series IC Card Module
 MIFARE & ISO14443A & ISO14443B & ISO7816 & ISO15693 IC CARD MODULE JMY600 Series IC Card Module MIFARE DESfire Card Operation Guide (Revision 1.00) Jinmuyu Electronics Co., LTD April 7, 2015 Please read
MIFARE & ISO14443A & ISO14443B & ISO7816 & ISO15693 IC CARD MODULE JMY600 Series IC Card Module MIFARE DESfire Card Operation Guide (Revision 1.00) Jinmuyu Electronics Co., LTD April 7, 2015 Please read
Attacks on NFC enabled phones and their countermeasures
 Attacks on NFC enabled phones and their countermeasures Arpit Jain: 113050028 September 3, 2012 Philosophy This survey explains NFC, its utility in real world, various attacks possible in NFC enabled phones
Attacks on NFC enabled phones and their countermeasures Arpit Jain: 113050028 September 3, 2012 Philosophy This survey explains NFC, its utility in real world, various attacks possible in NFC enabled phones
NFC Payments: The Art of Relay & Replay Attacks. Salvador Mendoza August 14, 2018
 1 NFC Payments: The Art of Relay & Replay Attacks Salvador Mendoza August 14, 2018 2 Disclaimer This white paper is a shortened version of the actual research. Unfortunately, some techniques and exploitation
1 NFC Payments: The Art of Relay & Replay Attacks Salvador Mendoza August 14, 2018 2 Disclaimer This white paper is a shortened version of the actual research. Unfortunately, some techniques and exploitation
ACR1281U-C2. Card UID Reader. Reference Manual Subject to change without prior notice.
 ACR1281U-C2 Card UID Reader Reference Manual 1.01 Subject to change without prior notice Table of Contents 1.0. Introduction... 3 2.0. Features... 4 3.0. Typical Applications... 5 4.0. Reference Documents...
ACR1281U-C2 Card UID Reader Reference Manual 1.01 Subject to change without prior notice Table of Contents 1.0. Introduction... 3 2.0. Features... 4 3.0. Typical Applications... 5 4.0. Reference Documents...
Conditional Multiple Differential Attack on MiFare Classic
 Conditional Multiple Differential Attack on MiFare Classic or How to Steal Train Passes and Break into Buildings Worldwide Nicolas T. Courtois University College London, UK MiFare Classic Crypto-1 Stream
Conditional Multiple Differential Attack on MiFare Classic or How to Steal Train Passes and Break into Buildings Worldwide Nicolas T. Courtois University College London, UK MiFare Classic Crypto-1 Stream
Strong Authentication for Physical Access using Mobile Devices
 Strong Authentication for Physical Access using Mobile Devices DoD Identity Protection and Management Conference May 15-17, 2012 Dr. Sarbari Gupta, CISSP, CISA sarbari@electrosoft-inc.com 703-437-9451
Strong Authentication for Physical Access using Mobile Devices DoD Identity Protection and Management Conference May 15-17, 2012 Dr. Sarbari Gupta, CISSP, CISA sarbari@electrosoft-inc.com 703-437-9451
CV5XX0A-X-XX Access Control Door Reader supports Mifare DESFire EV1 and Mifare Plus The family members are: Security Features for Mifare DESFire
 CV5XX0A-X-XX Access Control Door Reader supports DESFire EV1 and Plus CV5XX0A-X-XX is access control door reader, it s a contactless read/write device that supports ISO 14443A including DESFire EV1 and
CV5XX0A-X-XX Access Control Door Reader supports DESFire EV1 and Plus CV5XX0A-X-XX is access control door reader, it s a contactless read/write device that supports ISO 14443A including DESFire EV1 and
ACM120S-SM Contactless Small Module
 ACM120S-SM Contactless Small Module Technical Specifications Subject to change without prior notice Table of Contents 1.0. Introduction... 3 2.0. Features... 4 3.0. Typical Applications... 5 4.0. Technical
ACM120S-SM Contactless Small Module Technical Specifications Subject to change without prior notice Table of Contents 1.0. Introduction... 3 2.0. Features... 4 3.0. Typical Applications... 5 4.0. Technical
Overview of some automotive RKE systems
 Overview of some automotive RKE systems Pierre Pavlidès OWASP Gothenburg Day 2016 November 24, 2016 Pierre Pavlidès Overview of some automotive RKE systems 1 / 42 Before we start Slides at http://r.rogdham.net/26
Overview of some automotive RKE systems Pierre Pavlidès OWASP Gothenburg Day 2016 November 24, 2016 Pierre Pavlidès Overview of some automotive RKE systems 1 / 42 Before we start Slides at http://r.rogdham.net/26
Extensive proximity connectivity capabilities for USB-enabled devices
 NXP Near Field Communication (NFC) controller Extensive proximity connectivity capabilities for -enabled devices NXP Semiconductors is a highly integrated transmission module for contactless communication
NXP Near Field Communication (NFC) controller Extensive proximity connectivity capabilities for -enabled devices NXP Semiconductors is a highly integrated transmission module for contactless communication
Spoofing iclass and iclass SE
 Introduction The concept of emulating (spoofing) security access cards has become more and more difficult with the introduction of smart card technology. The older proximity based RFID access cards were
Introduction The concept of emulating (spoofing) security access cards has become more and more difficult with the introduction of smart card technology. The older proximity based RFID access cards were
Getting Started. Proxmark III V2 User Guid. Overview. Feature.
 Proxmark III V2 User Guid Getting Started Overview The Proxmark III is an open-source device developed by Jonathan Westhues that enables sniffing, reading and cloning of RFID (Radio Frequency Identification)
Proxmark III V2 User Guid Getting Started Overview The Proxmark III is an open-source device developed by Jonathan Westhues that enables sniffing, reading and cloning of RFID (Radio Frequency Identification)
PROCONTROL Proxer7. Datasheet. RFID Proximity card reader. Procontrol Proxer7. November, PROCONTROL ELECTRONICS LTD
 . PROCONTROL Proxer7 RFID Proximity card reader Datasheet November, 2015 1. oldal / 44 General description The Proxer7 is a proximity card reader, which provides RFID cards and transponders (of various
. PROCONTROL Proxer7 RFID Proximity card reader Datasheet November, 2015 1. oldal / 44 General description The Proxer7 is a proximity card reader, which provides RFID cards and transponders (of various
10/02/2015. Introduction PROTOCOL EXAMPLES. e-passport. e-passports contain an RFID tag.
 Introduction PROTOCOL EXAMPLES Tom Chothia Intro. To Comp. Sec. This talk gives some example of protocol attacks from my research, and a research group in Cambridge. E-passports (me & Smirnov) Contactless
Introduction PROTOCOL EXAMPLES Tom Chothia Intro. To Comp. Sec. This talk gives some example of protocol attacks from my research, and a research group in Cambridge. E-passports (me & Smirnov) Contactless
COMPGA12 1 TURN OVER
 Applied Cryptography, COMPGA12, 2009-10 Answer ALL questions. 2 hours. Marks for each part of each question are indicated in square brackets Calculators are NOT permitted 1. Multiple Choice Questions.
Applied Cryptography, COMPGA12, 2009-10 Answer ALL questions. 2 hours. Marks for each part of each question are indicated in square brackets Calculators are NOT permitted 1. Multiple Choice Questions.
Secure Element APIs and Practical Attacks on Secure Element-enabled Mobile Devices
 Secure Element APIs and Practical Attacks on Secure Element-enabled Mobile Devices Michael Roland University it of Applied Sciences Upper Austria,, Austria WIMA 2012 NFC Research Track 11 April 2012, Monaco
Secure Element APIs and Practical Attacks on Secure Element-enabled Mobile Devices Michael Roland University it of Applied Sciences Upper Austria,, Austria WIMA 2012 NFC Research Track 11 April 2012, Monaco
Supports ISO14443A Mifare Classic 1K, Mifare Classic 4K, Mifare Ultralight. Fast data transfer - Contactless communication up to 106 KHz
 SM132-USB 13.56 MHz RFID Mifare Read / Write USB Module DATA SHEET Complete Read/Write module including antenna Supports ISO14443A Mifare Classic 1K, Mifare Classic 4K, Mifare Ultralight USB Interface
SM132-USB 13.56 MHz RFID Mifare Read / Write USB Module DATA SHEET Complete Read/Write module including antenna Supports ISO14443A Mifare Classic 1K, Mifare Classic 4K, Mifare Ultralight USB Interface
MC75A HF PREMIUM HF RFID CONTACTLESS MOBILE COMPUTER
 Page 1 of 6 PRODUCT SPEC SHEET MC75A HF MC75A HF PREMIUM HF RFID CONTACTLESS MOBILE COMPUTER THE RIGHT MOBILE SOLUTION FOR TICKETING, IDENTITY AND ACCESS MANAGEMENT Zebra's MC75A HF takes its place as
Page 1 of 6 PRODUCT SPEC SHEET MC75A HF MC75A HF PREMIUM HF RFID CONTACTLESS MOBILE COMPUTER THE RIGHT MOBILE SOLUTION FOR TICKETING, IDENTITY AND ACCESS MANAGEMENT Zebra's MC75A HF takes its place as
Getting Started. Proxmark III User Guid. Overview
 Proxmark III User Guid Getting Started Overview The Proxmark III is an open-source device developed by Jonathan Westhues that enables sniffing, reading and cloning of RFID (Radio Frequency Identification)
Proxmark III User Guid Getting Started Overview The Proxmark III is an open-source device developed by Jonathan Westhues that enables sniffing, reading and cloning of RFID (Radio Frequency Identification)
Near Field Comunications
 Near Field Comunications Bridging the Physical and Virtual Worlds This is going to get interesting! Ash@YLabz.com Siamak Ashrafi NFC Definition Near field communication, or NFC, is a set of short-range
Near Field Comunications Bridging the Physical and Virtual Worlds This is going to get interesting! Ash@YLabz.com Siamak Ashrafi NFC Definition Near field communication, or NFC, is a set of short-range
REV6 Multi Sector MIFARE Reader/Writer Data Sheet
 716-52 REV6 Multi Sector MIFARE Reader/Writer Data Sheet Overview The 716-52 REV6 multi sector MIFARE Reader/Writer is an intelligent 13.56MHz contactless reader writer designed to operate with the Mifare
716-52 REV6 Multi Sector MIFARE Reader/Writer Data Sheet Overview The 716-52 REV6 multi sector MIFARE Reader/Writer is an intelligent 13.56MHz contactless reader writer designed to operate with the Mifare
Android D/2D Barcode Scanner. 5 Inch Display NFC LF/HF RFID. Fingerprint Sensor 4G/LTE GPS. Camera USB. Bluetooth 4.0 WLAN.
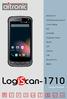 Android 6.0 1D/2D Barcode Scanner 5 Inch Display NFC LF/HF RFID Fingerprint Sensor 4G/LTE GPS Camera USB Bluetooth 4.0 WLAN Compact Terminal LogiScan-1710 This Android-based mobile computer features a
Android 6.0 1D/2D Barcode Scanner 5 Inch Display NFC LF/HF RFID Fingerprint Sensor 4G/LTE GPS Camera USB Bluetooth 4.0 WLAN Compact Terminal LogiScan-1710 This Android-based mobile computer features a
I. Background. Contents. Smart Cards in Public Transport: the Mifare Classic Case. Who is this guy?
 FACULTY OF SCIENCE Bart Jacobs & the Mifare Team Smart Cards in Public Transport: the Mifare Classic Case Contents I. Background II. OV-chipcard (Dutch Oyster, but nation-wide) III. Mifare vulnerabilities
FACULTY OF SCIENCE Bart Jacobs & the Mifare Team Smart Cards in Public Transport: the Mifare Classic Case Contents I. Background II. OV-chipcard (Dutch Oyster, but nation-wide) III. Mifare vulnerabilities
NFC ESSENTIALS JORDI JOFRE NFC EVERYWHERE MARCH 2018 PUBLIC
 NFC ESSENTIALS JORDI JOFRE NFC EVERYWHERE MARCH 2018 PUBLIC Learn all about NFC Session I, 15th March NFC applications and use cases https://attendee.gotowebinar.com/rt/1059402932312036099 Session II,
NFC ESSENTIALS JORDI JOFRE NFC EVERYWHERE MARCH 2018 PUBLIC Learn all about NFC Session I, 15th March NFC applications and use cases https://attendee.gotowebinar.com/rt/1059402932312036099 Session II,
It features compatibility for most controllers on the market, and it has unique multi-format interface.
 CV5XXX Access Control Door Reader with Multi-technology CV5XXX is access control door reader, it s a contactless read/write or read only (UID) device that supports ISO14443A/B, ISO15693, Mifare and EM125kHz
CV5XXX Access Control Door Reader with Multi-technology CV5XXX is access control door reader, it s a contactless read/write or read only (UID) device that supports ISO14443A/B, ISO15693, Mifare and EM125kHz
Condeco Group Ltd 2 Harbour Exchange Square London E14 9GE, UK
 Technical Overview Condeco Group Ltd 2 Harbour Exchange Square London E14 9GE, UK www.condecosoftware.com 2 Contents Product Overview... 3 Functionality... 4 Cloud Application functionality... 4 Screen
Technical Overview Condeco Group Ltd 2 Harbour Exchange Square London E14 9GE, UK www.condecosoftware.com 2 Contents Product Overview... 3 Functionality... 4 Cloud Application functionality... 4 Screen
NFC Payments: The Art of Relay & Replay Attacks
 NFC Payments: The Art of Relay & Replay Attacks Who am I? Security Researcher @Netxing Co-founder of Women in Tech Fund (WomenInTechFund.org) NFC Technology RFID Spectrum (Radio Frequency Identification)
NFC Payments: The Art of Relay & Replay Attacks Who am I? Security Researcher @Netxing Co-founder of Women in Tech Fund (WomenInTechFund.org) NFC Technology RFID Spectrum (Radio Frequency Identification)
Scrutinizing WPA2 Password Generating Algorithms in Wireless Routers
 Scrutinizing WPA2 Password Generating Algorithms in Wireless Routers Radboud University Nijmegen (The Netherlands) MSc Eduardo Novella MSc Carlo Meijer Dr. ir. Roel Verdult {ednolo@alumni.upv.es, carlo@youcontent.nl,
Scrutinizing WPA2 Password Generating Algorithms in Wireless Routers Radboud University Nijmegen (The Netherlands) MSc Eduardo Novella MSc Carlo Meijer Dr. ir. Roel Verdult {ednolo@alumni.upv.es, carlo@youcontent.nl,
