Cryptography Introduction
|
|
|
- Clyde Kelley
- 6 years ago
- Views:
Transcription
1 Cryptgraphy Intrductin Last Updated: Sep 7, 2017
2 Cryptgraphy Literal definitin means hidden writing Until mdern times, cryptgraphy was synnymus with encryptin, but the field has expanded This lecture reviews a high-level descriptin f fur cryptgraphic primitives we will learn abut this semester Symmetric Encryptin (AES) Public-Key Cryptgraphy (RSA) Secure One-Way Hash (SHA-256) Message Authenticatin Cde (MAC)
3 What is Encryptin? Transfrming infrmatin s that its true meaning is hidden Requires special knwledge t retrieve Mdern encryptin algrithms use transpsitin and substitutin in cmplex ways that are hard t reverse Examples frm histry that are easy t break ROT-13 (aka Caesar Cipher) is easy t break, simple substitutin cipher Vigenere cipher plyalphabetic substitutin cipher Examples f strng encryptin AES 3DES RC4 RSA
4 Types f Encryptin Schemes Cipher Classical Rtr Machines Mdern Substitutin Stegangraphy Transpsitin Public Key Secret Key GOOD DOG PLLX XLP PLSX TWF GOOD DOG DGOGDOO Hierarchy & Examples based n:
5 Perfect Encryptin Scheme? One-Time Pad (XOR message with key) Example*: Message: ONETIMEPAD Key: TBFRGFARFM Ciphertext: IPKLPSFHGQ The key TBFRGFARFM decrypts the message t ONETIMEPAD The key POYYAEAAZX decrypts the message t SALMONEGGS The key BXFGBMTMXM decrypts the message t GREENFLUID *Frm Applied Cryptgraphy (Schneier)
6 Symmetric Encryptin Als knwn as Cnventinal encryptin Secret-key encryptin Single-key encryptin
7 Symmetric Encryptin Mdel Alice Bb Key Key Plaintext Ciphertext Plaintext Encryptin Algrithm Decryptin Algrithm
8 Use Cases Web brwsing using HTTPS Encrypted chat (WhatsApp and Signal) Encrypted (PGP)
9 Cryptgraphic Hash Functin Surce:
10 Hashing Use Cases Digital signature File integrity verificatin (TripWire) Passwrd hashing Rtkit detectin
11 Message Authenticatin Cde (MAC) Surce: Netwrk Security Essentials (Stallings)
12 HMAC Use Cases Web brwser message integrity (HTTPS) Integrity f messages in authenticatin prtcls Ckie integrity Web applicatin remte prcedure calls
13 Mdel fr Encryptin with Public Key Cryptgraphy Alice Bb s Public Key Bb Bb s Private Key Plaintext Ciphertext Plaintext Encryptin Algrithm Decryptin Algrithm
14 Mdel fr Digital Signature with Public Key Cryptgraphy Alice Bb Alice s Private Key Alice s Public Key Plaintext Signing Algrithm Verificatin Algrithm? Plaintext
15 Symmetric Encryptin
16 Requirements 1. Strng algrithm (cipher) Attacker is unable t decrypt ciphertext r discver the key even if attacker has samples f ciphertext/plaintext created using the secret key 2. Fast Assumptin: Sender and receiver must securely btain and stre the secret key
17 Kerckhffs Principle The security f the symmetric encryptin depends n the secrecy f the key, nt the secrecy f the algrithm Dr. Auguste Kerckhffs ( ) Dutch linguist and cryptgrapher
18 Types f Ciphers Blck cipher (3DES, AES) Plaintext is brken up int fixed-size blcks Typical blck size (64, 128 bits) Stream cipher (RC4) Prcess plaintext cntinuusly Usually ne byte at a time
19 What can g wrng? Algrithm Relying n the secrecy f the algrithm Example: Substitutin ciphers Using an algrithm incrrectly Example: WEP used RC4 incrrectly Key T big Slw Strage T small Vulnerable t brute frce attack try all pssible keys
20 Big Numbers Cryptgraphy uses REALLY big numbers 1 in 2 61 dds f winning the ltt and being hit by lightning n the same day 2 92 atms in the average human bdy pssible keys in a 128-bit key atms in the planet atms in the sun atms in the galaxy pssible keys in a 256-bit key
21 Thermdynamic Limitatins* Physics: T set r clear a bit requires n less than kt k is the Bltzman cnstant (1.38*10-16 erg/ºk) T is the abslute temperature f the system Assuming T = 3.2ºK (ambient temperature f universe) kt = 4.4*10-16 ergs Annual energy utput f the sun 1.21*10 41 ergs Enugh t cycle thrugh a 187-bit cunter Build a Dysn sphere arund the sun and cllect all energy fr 32 years Enugh energy t cycle thrugh a 192-bit cunter. Supernva prduces in the neighbrhd f ergs Enugh t cycle thrugh a 219-bit cunter *Frm Applied Cryptgraphy (Schneier)
22 Public Key Cryptgraphy Terminlgy Public Key Private Key Digital Signature Cnfidentiality Yu encrypt with a public key, and yu decrypt with a private key Integrity/Authenticatin Yu sign with a private key, and yu verify the signature with the crrespnding public key Examples Diffie-Hellman RSA Elliptic Curve Cryptgraphy (ECC) Identity-based Encryptin (IBE)
23 Assignment Review this slide deck regularly t learn the high level abstractins fr these primitives. I ll expect yu t describe them t me n an exam withut any ntes. Yu dn t really knw smething until yu can teach it t smene else Study the AES NIST spec and watch the flash dem
Cryptography Introduction
 Cryptography Introduction Last Updated: Aug 20, 2013 Terminology Access Control o Authentication Assurance that entities are who they claim to be o Authorization Assurance that entities have permission
Cryptography Introduction Last Updated: Aug 20, 2013 Terminology Access Control o Authentication Assurance that entities are who they claim to be o Authorization Assurance that entities have permission
Introduction To Cryptography. plaintext >>>>>>>>>> ciphertext >>>>>>>>> plaintext. cryptographer: invent clever secret codes.
 Intrductin T Cryptgraphy Traditinal use f cryptgraphy: plaintext >>>>>>>>>> ciphertext >>>>>>>>> plaintext (encryptin) (decryptin) cryptgrapher: invent clever secret cdes. cryptanalyst: attempt t break
Intrductin T Cryptgraphy Traditinal use f cryptgraphy: plaintext >>>>>>>>>> ciphertext >>>>>>>>> plaintext (encryptin) (decryptin) cryptgrapher: invent clever secret cdes. cryptanalyst: attempt t break
Pastry dough mixing. Problems with traditional systems. Data Encryption Standard. CS349 Cryptography
 Pastry dugh mixing Data Encryptin Standard CS349 Cryptgraphy Department f Cmputer Science Wellesley Cllege Prblems with traditinal systems We assume that an attacker has at least sme knwledge f the statistical
Pastry dugh mixing Data Encryptin Standard CS349 Cryptgraphy Department f Cmputer Science Wellesley Cllege Prblems with traditinal systems We assume that an attacker has at least sme knwledge f the statistical
Security+ Guide to Network Security Fundamentals, Third Edition. Chapter 11 Basic Cryptography
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 11 Basic Cryptography Objectives Define cryptography Describe hashing List the basic symmetric cryptographic algorithms 2 Objectives
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 11 Basic Cryptography Objectives Define cryptography Describe hashing List the basic symmetric cryptographic algorithms 2 Objectives
Cryptography MIS
 Cryptography MIS-5903 http://community.mis.temple.edu/mis5903sec011s17/ Cryptography History Substitution Monoalphabetic Polyalphabetic (uses multiple alphabets) uses Vigenere Table Scytale cipher (message
Cryptography MIS-5903 http://community.mis.temple.edu/mis5903sec011s17/ Cryptography History Substitution Monoalphabetic Polyalphabetic (uses multiple alphabets) uses Vigenere Table Scytale cipher (message
Cryptography and Network Security
 Cryptography and Network Security Spring 2012 http://users.abo.fi/ipetre/crypto/ Lecture 14: Folklore, Course summary, Exam requirements Ion Petre Department of IT, Åbo Akademi University 1 Folklore on
Cryptography and Network Security Spring 2012 http://users.abo.fi/ipetre/crypto/ Lecture 14: Folklore, Course summary, Exam requirements Ion Petre Department of IT, Åbo Akademi University 1 Folklore on
Computer Security: Principles and Practice
 Computer Security: Principles and Practice Chapter 2 Cryptographic Tools First Edition by William Stallings and Lawrie Brown Lecture slides by Lawrie Brown Cryptographic Tools cryptographic algorithms
Computer Security: Principles and Practice Chapter 2 Cryptographic Tools First Edition by William Stallings and Lawrie Brown Lecture slides by Lawrie Brown Cryptographic Tools cryptographic algorithms
CSE 127: Computer Security Cryptography. Kirill Levchenko
 CSE 127: Computer Security Cryptography Kirill Levchenko October 24, 2017 Motivation Two parties want to communicate securely Secrecy: No one else can read messages Integrity: messages cannot be modified
CSE 127: Computer Security Cryptography Kirill Levchenko October 24, 2017 Motivation Two parties want to communicate securely Secrecy: No one else can read messages Integrity: messages cannot be modified
Introduction to Symmetric Cryptography
 Introduction to Symmetric Cryptography Tingting Chen Cal Poly Pomona 1 Some slides are from Dr. Cliff Zou. www.cs.ucf.edu/~czou/cis3360-12/ch08-cryptoconcepts.ppt Basic Cryptography Private Key Cryptography
Introduction to Symmetric Cryptography Tingting Chen Cal Poly Pomona 1 Some slides are from Dr. Cliff Zou. www.cs.ucf.edu/~czou/cis3360-12/ch08-cryptoconcepts.ppt Basic Cryptography Private Key Cryptography
About the Tutorial. Audience. Prerequisites. Disclaimer & Copyright. Cryptography
 Abut the Tutrial This tutrial cvers the basics f the science f cryptgraphy. It explains hw prgrammers and netwrk prfessinals can use cryptgraphy t maintain the privacy f cmputer data. Starting with the
Abut the Tutrial This tutrial cvers the basics f the science f cryptgraphy. It explains hw prgrammers and netwrk prfessinals can use cryptgraphy t maintain the privacy f cmputer data. Starting with the
FIPS Level 1 Security Policy Version Number: 1.5 Date: February 29, 2016
 Nn-Prprietary Bx JCA Cryptgraphic Mdule 1.0 FIPS 140-2 Level 1 Security Plicy Versin Number: 1.5 Date: February 29, 2016 Table f Cntents 1. MODULE OVERVIEW 3 2. MODES OF OPERATION 5 2.1 APPROVED CRYPTOGRAPHIC
Nn-Prprietary Bx JCA Cryptgraphic Mdule 1.0 FIPS 140-2 Level 1 Security Plicy Versin Number: 1.5 Date: February 29, 2016 Table f Cntents 1. MODULE OVERVIEW 3 2. MODES OF OPERATION 5 2.1 APPROVED CRYPTOGRAPHIC
APNIC elearning: Cryptography Basics
 APNIC elearning: Cryptography Basics 27 MAY 2015 03:00 PM AEST Brisbane (UTC+10) Issue Date: Revision: Introduction Presenter Sheryl Hermoso Training Officer sheryl@apnic.net Specialties: Network Security
APNIC elearning: Cryptography Basics 27 MAY 2015 03:00 PM AEST Brisbane (UTC+10) Issue Date: Revision: Introduction Presenter Sheryl Hermoso Training Officer sheryl@apnic.net Specialties: Network Security
Computer Security. 08r. Pre-exam 2 Last-minute Review Cryptography. Paul Krzyzanowski. Rutgers University. Spring 2018
 Computer Security 08r. Pre-exam 2 Last-minute Review Cryptography Paul Krzyzanowski Rutgers University Spring 2018 March 26, 2018 CS 419 2018 Paul Krzyzanowski 1 Cryptographic Systems March 26, 2018 CS
Computer Security 08r. Pre-exam 2 Last-minute Review Cryptography Paul Krzyzanowski Rutgers University Spring 2018 March 26, 2018 CS 419 2018 Paul Krzyzanowski 1 Cryptographic Systems March 26, 2018 CS
ECE 545 Project Deliverables
 Tp-level flder: _ Secnd-level flders: 1_assumptins 2_blck_diagrams 3_interface 4_ASM_charts 5_surce_cdes 6_verificatin 7_timing_analysis 8_results 9_benchmarking 10_bug_reprts
Tp-level flder: _ Secnd-level flders: 1_assumptins 2_blck_diagrams 3_interface 4_ASM_charts 5_surce_cdes 6_verificatin 7_timing_analysis 8_results 9_benchmarking 10_bug_reprts
Ephorus Integration Kit
 Ephrus Integratin Kit Authr: Rbin Hildebrand Versin: 2.0 Date: May 9, 2007 Histry Versin Authr Cmment v1.1 Remc Verhef Created. v1.2 Rbin Hildebrand Single Sign On (Remved v1.7). v1.3 Rbin Hildebrand Reprting
Ephrus Integratin Kit Authr: Rbin Hildebrand Versin: 2.0 Date: May 9, 2007 Histry Versin Authr Cmment v1.1 Remc Verhef Created. v1.2 Rbin Hildebrand Single Sign On (Remved v1.7). v1.3 Rbin Hildebrand Reprting
Telecommunication Protocols Laboratory Course
 Telecmmunicatin Prtcls Labratry Curse Lecture 2 March 11, 2004 http://www.ab.fi/~lpetre/teleprt/teleprt.html 1 Last time We examined sme key terms: prtcl, service, layer, netwrk architecture We examined
Telecmmunicatin Prtcls Labratry Curse Lecture 2 March 11, 2004 http://www.ab.fi/~lpetre/teleprt/teleprt.html 1 Last time We examined sme key terms: prtcl, service, layer, netwrk architecture We examined
Lecture 9a: Secure Sockets Layer (SSL) March, 2004
 Internet and Intranet Protocols and Applications Lecture 9a: Secure Sockets Layer (SSL) March, 2004 Arthur Goldberg Computer Science Department New York University artg@cs.nyu.edu Security Achieved by
Internet and Intranet Protocols and Applications Lecture 9a: Secure Sockets Layer (SSL) March, 2004 Arthur Goldberg Computer Science Department New York University artg@cs.nyu.edu Security Achieved by
Ref:
 Cryptography & digital signature Dec. 2013 Ref: http://cis.poly.edu/~ross/ 2 Cryptography Overview Symmetric Key Cryptography Public Key Cryptography Message integrity and digital signatures References:
Cryptography & digital signature Dec. 2013 Ref: http://cis.poly.edu/~ross/ 2 Cryptography Overview Symmetric Key Cryptography Public Key Cryptography Message integrity and digital signatures References:
NTP Security Algorithms
 NTP Security Algrithms David L. Mills University f Delaware http://www.eecis.udel.edu/~mills mailt:mills@udel.edu Sir Jhn Tenniel; Alice s Adventures in Wnderland,Lewis Carrll 31-Oct-05 1 Symmetric key
NTP Security Algrithms David L. Mills University f Delaware http://www.eecis.udel.edu/~mills mailt:mills@udel.edu Sir Jhn Tenniel; Alice s Adventures in Wnderland,Lewis Carrll 31-Oct-05 1 Symmetric key
Implementation of Authentication Mechanism for a Virtual File System
 Implementatin f Authenticatin Mechanism fr a Virtual File System Prject fr Operating Systems Curse (CS 5204) Implemented by- Vinth Jagannathan Abhishek Ram Under the guidance f Dr Dennis Kafura Abstract
Implementatin f Authenticatin Mechanism fr a Virtual File System Prject fr Operating Systems Curse (CS 5204) Implemented by- Vinth Jagannathan Abhishek Ram Under the guidance f Dr Dennis Kafura Abstract
Cryptographic Concepts
 Outline Identify the different types of cryptography Learn about current cryptographic methods Chapter #23: Cryptography Understand how cryptography is applied for security Given a scenario, utilize general
Outline Identify the different types of cryptography Learn about current cryptographic methods Chapter #23: Cryptography Understand how cryptography is applied for security Given a scenario, utilize general
Encryption. INST 346, Section 0201 April 3, 2018
 Encryption INST 346, Section 0201 April 3, 2018 Goals for Today Symmetric Key Encryption Public Key Encryption Certificate Authorities Secure Sockets Layer Simple encryption scheme substitution cipher:
Encryption INST 346, Section 0201 April 3, 2018 Goals for Today Symmetric Key Encryption Public Key Encryption Certificate Authorities Secure Sockets Layer Simple encryption scheme substitution cipher:
PROTECTING CONVERSATIONS
 PROTECTING CONVERSATIONS Basics of Encrypted Network Communications Naïve Conversations Captured messages could be read by anyone Cannot be sure who sent the message you are reading Basic Definitions Authentication
PROTECTING CONVERSATIONS Basics of Encrypted Network Communications Naïve Conversations Captured messages could be read by anyone Cannot be sure who sent the message you are reading Basic Definitions Authentication
Cisco Tetration Analytics, Release , Release Notes
 Cisc Tetratin Analytics, Release 1.102.21, Release Ntes This dcument describes the features, caveats, and limitatins fr the Cisc Tetratin Analytics sftware. Additinal prduct Release ntes are smetimes updated
Cisc Tetratin Analytics, Release 1.102.21, Release Ntes This dcument describes the features, caveats, and limitatins fr the Cisc Tetratin Analytics sftware. Additinal prduct Release ntes are smetimes updated
On the road again. The network layer. Data and control planes. Router forwarding tables. The network layer data plane. CS242 Computer Networks
 On the rad again The netwrk layer data plane CS242 Cmputer Netwrks The netwrk layer The transprt layer is respnsible fr applicatin t applicatin transprt. The netwrk layer is respnsible fr hst t hst transprt.
On the rad again The netwrk layer data plane CS242 Cmputer Netwrks The netwrk layer The transprt layer is respnsible fr applicatin t applicatin transprt. The netwrk layer is respnsible fr hst t hst transprt.
Dynamic Storage (ECS)
 User Guide Dynamic Strage (ECS) Swisscm (Schweiz) AG 1 / 10 Cntent 1 Abut Dynamic Strage... 3 2 Virtual drive, the EMC CIFS-ECS Tl... 4 3 Amazn S3 Brwer... 6 4 Strage Gateway Appliance... 9 5 Amazn S3
User Guide Dynamic Strage (ECS) Swisscm (Schweiz) AG 1 / 10 Cntent 1 Abut Dynamic Strage... 3 2 Virtual drive, the EMC CIFS-ECS Tl... 4 3 Amazn S3 Brwer... 6 4 Strage Gateway Appliance... 9 5 Amazn S3
Cryptography Basics. IT443 Network Security Administration Slides courtesy of Bo Sheng
 Cryptography Basics IT443 Network Security Administration Slides courtesy of Bo Sheng 1 Outline Basic concepts in cryptography systems Secret key cryptography Public key cryptography Hash functions 2 Encryption/Decryption
Cryptography Basics IT443 Network Security Administration Slides courtesy of Bo Sheng 1 Outline Basic concepts in cryptography systems Secret key cryptography Public key cryptography Hash functions 2 Encryption/Decryption
9/30/2016. Cryptography Basics. Outline. Encryption/Decryption. Cryptanalysis. Caesar Cipher. Mono-Alphabetic Ciphers
 Cryptography Basics IT443 Network Security Administration Slides courtesy of Bo Sheng Basic concepts in cryptography systems Secret cryptography Public cryptography 1 2 Encryption/Decryption Cryptanalysis
Cryptography Basics IT443 Network Security Administration Slides courtesy of Bo Sheng Basic concepts in cryptography systems Secret cryptography Public cryptography 1 2 Encryption/Decryption Cryptanalysis
CCNA Security v2.0 Chapter 2 Exam Answers
 CCNA Security v2.0 Chapter 2 Exam Answers 1. An administratr defined a lcal user accunt with a secret passwrd n ruter R1 fr use with SSH. Which three additinal steps are required t cnfigure R1 t accept
CCNA Security v2.0 Chapter 2 Exam Answers 1. An administratr defined a lcal user accunt with a secret passwrd n ruter R1 fr use with SSH. Which three additinal steps are required t cnfigure R1 t accept
CCNA Security v2.0 Chapter 1 Exam Answers
 CCNA Security v2.0 Chapter 1 Exam Answers 1. What methd can be used t mitigate ping sweeps? using encrypted r hashed authenticatin prtcls installing antivirus sftware n hsts deplying antisniffer sftware
CCNA Security v2.0 Chapter 1 Exam Answers 1. What methd can be used t mitigate ping sweeps? using encrypted r hashed authenticatin prtcls installing antivirus sftware n hsts deplying antisniffer sftware
NTP Security Model. David L. Mills University of Delaware 24-Aug-04 1
 NTP Security Mdel David L. Mills University f Delaware http://www.eecis.udel.edu/~mills mailt:mills@udel.edu Sir Jhn Tenniel; Alice s Adventures in Wnderland,Lewis Carrll 24-Aug-04 1 NTP security mdel
NTP Security Mdel David L. Mills University f Delaware http://www.eecis.udel.edu/~mills mailt:mills@udel.edu Sir Jhn Tenniel; Alice s Adventures in Wnderland,Lewis Carrll 24-Aug-04 1 NTP security mdel
2. When logging is used, which severity level indicates that a device is unusable?
 CCNA 4 Chapter 8 v5.0 Exam Answers 2015 (100%) 1. What are the mst cmmn syslg messages? thse that ccur when a packet matches a parameter cnditin in an access cntrl list link up and link dwn messages utput
CCNA 4 Chapter 8 v5.0 Exam Answers 2015 (100%) 1. What are the mst cmmn syslg messages? thse that ccur when a packet matches a parameter cnditin in an access cntrl list link up and link dwn messages utput
Chapter 8. Network Security. Cryptography. Need for Security. An Introduction to Cryptography 10/7/2010
 Cryptography Chapter 8 Network Security Introduction to Cryptography Substitution Ciphers Transposition Ciphers One-Time Pads Two Fundamental Cryptographic Principles Need for Security An Introduction
Cryptography Chapter 8 Network Security Introduction to Cryptography Substitution Ciphers Transposition Ciphers One-Time Pads Two Fundamental Cryptographic Principles Need for Security An Introduction
CRYPTOLOGY KEY MANAGEMENT CRYPTOGRAPHY CRYPTANALYSIS. Cryptanalytic. Brute-Force. Ciphertext-only Known-plaintext Chosen-plaintext Chosen-ciphertext
 CRYPTOLOGY CRYPTOGRAPHY KEY MANAGEMENT CRYPTANALYSIS Cryptanalytic Brute-Force Ciphertext-only Known-plaintext Chosen-plaintext Chosen-ciphertext 58 Types of Cryptographic Private key (Symmetric) Public
CRYPTOLOGY CRYPTOGRAPHY KEY MANAGEMENT CRYPTANALYSIS Cryptanalytic Brute-Force Ciphertext-only Known-plaintext Chosen-plaintext Chosen-ciphertext 58 Types of Cryptographic Private key (Symmetric) Public
Symmetric, Asymmetric, and One Way Technologies
 Symmetric, Asymmetric, and One Way Technologies Crypto Basics Ed Crowley Fall 2010 1 Topics: Symmetric & Asymmetric Technologies Kerckhoff s Principle Symmetric Crypto Overview Key management problem Attributes
Symmetric, Asymmetric, and One Way Technologies Crypto Basics Ed Crowley Fall 2010 1 Topics: Symmetric & Asymmetric Technologies Kerckhoff s Principle Symmetric Crypto Overview Key management problem Attributes
COMP4109 : Applied Cryptography
 COMP4109 : Applied Cryptography Fall 2013 M. Jason Hinek Carleton University Applied Cryptography Day 4 (and 5 and maybe 6) secret-key primitives symmetric-key encryption security notions and types of
COMP4109 : Applied Cryptography Fall 2013 M. Jason Hinek Carleton University Applied Cryptography Day 4 (and 5 and maybe 6) secret-key primitives symmetric-key encryption security notions and types of
CSC 580 Cryptography and Computer Security
 CSC 580 Cryptography and Computer Security Encryption Concepts, Classical Crypto, and Binary Operations January 30, 2018 Overview Today: Cryptography concepts and classical crypto Textbook sections 3.1,
CSC 580 Cryptography and Computer Security Encryption Concepts, Classical Crypto, and Binary Operations January 30, 2018 Overview Today: Cryptography concepts and classical crypto Textbook sections 3.1,
2.1 Basic Cryptography Concepts
 ENEE739B Fall 2005 Part 2 Secure Media Communications 2.1 Basic Cryptography Concepts Min Wu Electrical and Computer Engineering University of Maryland, College Park Outline: Basic Security/Crypto Concepts
ENEE739B Fall 2005 Part 2 Secure Media Communications 2.1 Basic Cryptography Concepts Min Wu Electrical and Computer Engineering University of Maryland, College Park Outline: Basic Security/Crypto Concepts
Lecture 6: Symmetric Cryptography. CS 5430 February 21, 2018
 Lecture 6: Symmetric Cryptography CS 5430 February 21, 2018 The Big Picture Thus Far Attacks are perpetrated by threats that inflict harm by exploiting vulnerabilities which are controlled by countermeasures.
Lecture 6: Symmetric Cryptography CS 5430 February 21, 2018 The Big Picture Thus Far Attacks are perpetrated by threats that inflict harm by exploiting vulnerabilities which are controlled by countermeasures.
EEC-484/584 Computer Networks
 EEC-484/584 Computer Networks Lecture 23 wenbing@ieee.org (Lecture notes are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Outline 2 Review of last lecture Introduction to
EEC-484/584 Computer Networks Lecture 23 wenbing@ieee.org (Lecture notes are based on materials supplied by Dr. Louise Moser at UCSB and Prentice-Hall) Outline 2 Review of last lecture Introduction to
Distributed Systems. 26. Cryptographic Systems: An Introduction. Paul Krzyzanowski. Rutgers University. Fall 2015
 Distributed Systems 26. Cryptographic Systems: An Introduction Paul Krzyzanowski Rutgers University Fall 2015 1 Cryptography Security Cryptography may be a component of a secure system Adding cryptography
Distributed Systems 26. Cryptographic Systems: An Introduction Paul Krzyzanowski Rutgers University Fall 2015 1 Cryptography Security Cryptography may be a component of a secure system Adding cryptography
Introduction to Cryptography. Vasil Slavov William Jewell College
 Introduction to Cryptography Vasil Slavov William Jewell College Crypto definitions Cryptography studies how to keep messages secure Cryptanalysis studies how to break ciphertext Cryptology branch of mathematics,
Introduction to Cryptography Vasil Slavov William Jewell College Crypto definitions Cryptography studies how to keep messages secure Cryptanalysis studies how to break ciphertext Cryptology branch of mathematics,
Packet Tracer - Skills Integration Challenge Topology
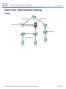 Packet Tracer - Skills Integratin Challenge Tplgy 2015 Cisc and/r its affiliates. All rights reserved. This dcument is Cisc Public. Page 1 f 6 Packet Tracer - Skills Integratin Challenge Addressing Table
Packet Tracer - Skills Integratin Challenge Tplgy 2015 Cisc and/r its affiliates. All rights reserved. This dcument is Cisc Public. Page 1 f 6 Packet Tracer - Skills Integratin Challenge Addressing Table
Garantía y Seguridad en Sistemas y Redes
 Garantía y Seguridad en Sistemas y Redes Tema 2. Cryptographic Tools Esteban Stafford Departamento de Ingeniería Informá2ca y Electrónica Este tema se publica bajo Licencia: Crea2ve Commons BY- NC- SA
Garantía y Seguridad en Sistemas y Redes Tema 2. Cryptographic Tools Esteban Stafford Departamento de Ingeniería Informá2ca y Electrónica Este tema se publica bajo Licencia: Crea2ve Commons BY- NC- SA
CS61A Lecture #39: Cryptography
 Announcements: CS61A Lecture #39: Cryptography Homework 13 is up: due Monday. Homework 14 will be judging the contest. HKN surveys on Friday: 7.5 bonus points for filling out their survey on Friday (yes,
Announcements: CS61A Lecture #39: Cryptography Homework 13 is up: due Monday. Homework 14 will be judging the contest. HKN surveys on Friday: 7.5 bonus points for filling out their survey on Friday (yes,
Cryptography. Andreas Hülsing. 6 September 2016
 Cryptography Andreas Hülsing 6 September 2016 1 / 21 Announcements Homepage: http: //www.hyperelliptic.org/tanja/teaching/crypto16/ Lecture is recorded First row might be on recordings. Anything organizational:
Cryptography Andreas Hülsing 6 September 2016 1 / 21 Announcements Homepage: http: //www.hyperelliptic.org/tanja/teaching/crypto16/ Lecture is recorded First row might be on recordings. Anything organizational:
You can upload all your banking cards to the app and select the one you wish to make payment with.
 Mbile Pay Digital Wallet Mbile Pay - User Guide Mbile Pay applicatin fr smartphnes with Andrid 4.4 Operating System. Mbile Pay is an app that enables yu t make cntactless payments with VTB Bank card in
Mbile Pay Digital Wallet Mbile Pay - User Guide Mbile Pay applicatin fr smartphnes with Andrid 4.4 Operating System. Mbile Pay is an app that enables yu t make cntactless payments with VTB Bank card in
ASM Educational Center (ASM) Est Authorized SCNP Security Certified Network Professional Boot Camp
 ASM Educatinal Center (ASM) Est. 1992 11200 Rckville Pike, Suite 220 Rckville, MD 20852 Phne: 301-984-7400 Fax: 301-984-7401 Web: www.asmed.cm E-mail: inf@asmed.cm Authrized SCNP Security Certified Netwrk
ASM Educatinal Center (ASM) Est. 1992 11200 Rckville Pike, Suite 220 Rckville, MD 20852 Phne: 301-984-7400 Fax: 301-984-7401 Web: www.asmed.cm E-mail: inf@asmed.cm Authrized SCNP Security Certified Netwrk
Dr. Jinyuan (Stella) Sun Dept. of Electrical Engineering and Computer Science University of Tennessee Fall 2010
 CS 494/594 Computer and Network Security Dr. Jinyuan (Stella) Sun Dept. of Electrical Engineering and Computer Science University of Tennessee Fall 2010 1 Public Key Cryptography Modular Arithmetic RSA
CS 494/594 Computer and Network Security Dr. Jinyuan (Stella) Sun Dept. of Electrical Engineering and Computer Science University of Tennessee Fall 2010 1 Public Key Cryptography Modular Arithmetic RSA
16/07/2012. Design Patterns. By Võ Văn Hải Faculty of Information Technologies - HUI. Behavioral Patterns. Session objectives. Strategy.
 Design Patterns By Võ Văn Hải Faculty f Infrmatin Technlgies - HUI Behaviral Patterns Sessin bjectives Strategy Observer 2 1 Behaviral Patterns 3 Mtivating example - SimpleUDuck Je wrks fr a cmpany that
Design Patterns By Võ Văn Hải Faculty f Infrmatin Technlgies - HUI Behaviral Patterns Sessin bjectives Strategy Observer 2 1 Behaviral Patterns 3 Mtivating example - SimpleUDuck Je wrks fr a cmpany that
Cryptography Functions
 Cryptography Functions Lecture 3 1/29/2013 References: Chapter 2-3 Network Security: Private Communication in a Public World, Kaufman, Perlman, Speciner Types of Cryptographic Functions Secret (Symmetric)
Cryptography Functions Lecture 3 1/29/2013 References: Chapter 2-3 Network Security: Private Communication in a Public World, Kaufman, Perlman, Speciner Types of Cryptographic Functions Secret (Symmetric)
UML : MODELS, VIEWS, AND DIAGRAMS
 UML : MODELS, VIEWS, AND DIAGRAMS Purpse and Target Grup f a Mdel In real life we ften bserve that the results f cumbersme, tedius, and expensive mdeling simply disappear in a stack f paper n smene's desk.
UML : MODELS, VIEWS, AND DIAGRAMS Purpse and Target Grup f a Mdel In real life we ften bserve that the results f cumbersme, tedius, and expensive mdeling simply disappear in a stack f paper n smene's desk.
Public Key Cryptography, OpenPGP, and Enigmail. 31/5/ Geek Girls Carrffots GVA
 Public Key Cryptography, OpenPGP, and Enigmail Cryptography is the art and science of transforming (encrypting) a message so only the intended recipient can read it Symmetric Cryptography shared secret
Public Key Cryptography, OpenPGP, and Enigmail Cryptography is the art and science of transforming (encrypting) a message so only the intended recipient can read it Symmetric Cryptography shared secret
CSE 361S Intro to Systems Software Lab #2
 Due: Thursday, September 22, 2011 CSE 361S Intr t Systems Sftware Lab #2 Intrductin This lab will intrduce yu t the GNU tls in the Linux prgramming envirnment we will be using fr CSE 361S this semester,
Due: Thursday, September 22, 2011 CSE 361S Intr t Systems Sftware Lab #2 Intrductin This lab will intrduce yu t the GNU tls in the Linux prgramming envirnment we will be using fr CSE 361S this semester,
Iteration Part 2. Review: Iteration [Part 1] Flow charts for two loop constructs. Review: Syntax of loops. while continuation_condition : statement1
![Iteration Part 2. Review: Iteration [Part 1] Flow charts for two loop constructs. Review: Syntax of loops. while continuation_condition : statement1 Iteration Part 2. Review: Iteration [Part 1] Flow charts for two loop constructs. Review: Syntax of loops. while continuation_condition : statement1](/thumbs/72/66928591.jpg) Review: Iteratin [Part 1] Iteratin Part 2 CS111 Cmputer Prgramming Department f Cmputer Science Wellesley Cllege Iteratin is the repeated executin f a set f statements until a stpping cnditin is reached.
Review: Iteratin [Part 1] Iteratin Part 2 CS111 Cmputer Prgramming Department f Cmputer Science Wellesley Cllege Iteratin is the repeated executin f a set f statements until a stpping cnditin is reached.
L13. Reviews. Rocky K. C. Chang, April 10, 2015
 L13. Reviews Rocky K. C. Chang, April 10, 2015 1 Foci of this course Understand the 3 fundamental cryptographic functions and how they are used in network security. Understand the main elements in securing
L13. Reviews Rocky K. C. Chang, April 10, 2015 1 Foci of this course Understand the 3 fundamental cryptographic functions and how they are used in network security. Understand the main elements in securing
Protecting Information Assets - Week 11 - Cryptography, Public Key Encryption and Digital Signatures. MIS 5206 Protecting Information Assets
 Protecting Information Assets - Week 11 - Cryptography, Public Key Encryption and Digital Signatures MIS5206 Week 11 Identity and Access Control Week 10 continued Cryptography, Public Key Encryption and
Protecting Information Assets - Week 11 - Cryptography, Public Key Encryption and Digital Signatures MIS5206 Week 11 Identity and Access Control Week 10 continued Cryptography, Public Key Encryption and
Cryptographic Systems
 CPSC 426/526 Cryptographic Systems Ennan Zhai Computer Science Department Yale University Recall: Lec-10 In lec-10, we learned: - Consistency models - Two-phase commit - Consensus - Paxos Lecture Roadmap
CPSC 426/526 Cryptographic Systems Ennan Zhai Computer Science Department Yale University Recall: Lec-10 In lec-10, we learned: - Consistency models - Two-phase commit - Consensus - Paxos Lecture Roadmap
IS312T Information Security Essentials [Onsite]
![IS312T Information Security Essentials [Onsite] IS312T Information Security Essentials [Onsite]](/thumbs/95/123014954.jpg) IS312T [Onsite] Curse Descriptin: This curse is an intrductin t the security essentials. The curse identifies and examines types f infrmatin security used in industry and hw they are implemented. Prerequisite(s)
IS312T [Onsite] Curse Descriptin: This curse is an intrductin t the security essentials. The curse identifies and examines types f infrmatin security used in industry and hw they are implemented. Prerequisite(s)
CIS 3362 Final Exam 12/4/2013. Name:
 CIS 3362 Final Exam 12/4/2013 Name: 1) (10 pts) Since the use of letter frequencies was known to aid in breaking substitution ciphers, code makers in the Renaissance added "twists" to the standard substitution
CIS 3362 Final Exam 12/4/2013 Name: 1) (10 pts) Since the use of letter frequencies was known to aid in breaking substitution ciphers, code makers in the Renaissance added "twists" to the standard substitution
Application Note. Digi Connect Wi-SP Troubleshooting Guide. Digi Technical Support 10 May 2016
 Applicatin Nte Digi Cnnect Wi-SP Trubleshting Guide Digi Technical Supprt 10 May 2016 Cntents 1 Intrductin... 3 1.1 Assumptins... 3 1.2 Crrectins... 3 2 Quick Facts... 3 2.1 Cmmn Questins Abut the Cnnect
Applicatin Nte Digi Cnnect Wi-SP Trubleshting Guide Digi Technical Supprt 10 May 2016 Cntents 1 Intrductin... 3 1.1 Assumptins... 3 1.2 Crrectins... 3 2 Quick Facts... 3 2.1 Cmmn Questins Abut the Cnnect
SSH, SSL, and IPsec: wtf?
 SSH, SSL, and IPsec: wtf? Eric Rescrla RTFM, Inc. ekr@rtfm.cm Eric Rescrla SSH, SSL, and IPsec 1 What are we trying t accmplish? Alice, Bb want t talk t each ther But they re wrried abut attack Hw d yu
SSH, SSL, and IPsec: wtf? Eric Rescrla RTFM, Inc. ekr@rtfm.cm Eric Rescrla SSH, SSL, and IPsec 1 What are we trying t accmplish? Alice, Bb want t talk t each ther But they re wrried abut attack Hw d yu
Lecture 4: Symmetric Key Encryption
 Lecture 4: Symmetric ey Encryption CS6903: Modern Cryptography Spring 2009 Nitesh Saxena Let s use the board, please take notes 2/20/2009 Lecture 1 - Introduction 2 Data Encryption Standard Encrypts by
Lecture 4: Symmetric ey Encryption CS6903: Modern Cryptography Spring 2009 Nitesh Saxena Let s use the board, please take notes 2/20/2009 Lecture 1 - Introduction 2 Data Encryption Standard Encrypts by
David Wetherall, with some slides from Radia Perlman s security lectures.
 David Wetherall, with some slides from Radia Perlman s security lectures. djw@cs.washington.edu Networks are shared: Want to secure communication between legitimate participants from others with (passive
David Wetherall, with some slides from Radia Perlman s security lectures. djw@cs.washington.edu Networks are shared: Want to secure communication between legitimate participants from others with (passive
Computer Security. 10r. Recitation assignment & concept review. Paul Krzyzanowski. Rutgers University. Spring 2018
 Computer Security 10r. Recitation assignment & concept review Paul Krzyzanowski Rutgers University Spring 2018 April 3, 2018 CS 419 2018 Paul Krzyzanowski 1 1. What is a necessary condition for perfect
Computer Security 10r. Recitation assignment & concept review Paul Krzyzanowski Rutgers University Spring 2018 April 3, 2018 CS 419 2018 Paul Krzyzanowski 1 1. What is a necessary condition for perfect
Understand the TLS handshake Understand client/server authentication in TLS. Understand session resumption Understand the limitations of TLS
 Last Updated: Oct 31, 2017 Understand the TLS handshake Understand client/server authentication in TLS RSA key exchange DHE key exchange Explain certificate ownership proofs in detail What cryptographic
Last Updated: Oct 31, 2017 Understand the TLS handshake Understand client/server authentication in TLS RSA key exchange DHE key exchange Explain certificate ownership proofs in detail What cryptographic
EEC-682/782 Computer Networks I
 EEC-682/782 Computer Networks I Lecture 23 Wenbing Zhao wenbingz@gmail.com http://academic.csuohio.edu/zhao_w/teaching/eec682.htm (Lecture nodes are based on materials supplied by Dr. Louise Moser at UCSB
EEC-682/782 Computer Networks I Lecture 23 Wenbing Zhao wenbingz@gmail.com http://academic.csuohio.edu/zhao_w/teaching/eec682.htm (Lecture nodes are based on materials supplied by Dr. Louise Moser at UCSB
Cryptography Introduction to Computer Security. Chapter 8
 Cryptography Introduction to Computer Security Chapter 8 Introduction Cryptology: science of encryption; combines cryptography and cryptanalysis Cryptography: process of making and using codes to secure
Cryptography Introduction to Computer Security Chapter 8 Introduction Cryptology: science of encryption; combines cryptography and cryptanalysis Cryptography: process of making and using codes to secure
Outline. Public Key Cryptography. Applications of Public Key Crypto. Applications (Cont d)
 Outline AIT 682: Network and Systems Security 1. Introduction 2. RSA 3. Diffie-Hellman Key Exchange 4. Digital Signature Standard Topic 5.2 Public Key Cryptography Instructor: Dr. Kun Sun 2 Public Key
Outline AIT 682: Network and Systems Security 1. Introduction 2. RSA 3. Diffie-Hellman Key Exchange 4. Digital Signature Standard Topic 5.2 Public Key Cryptography Instructor: Dr. Kun Sun 2 Public Key
Lecture 3: Symmetric Key Encryption
 Lecture 3: Symmetric Key Encryption CS996: Modern Cryptography Spring 2007 Nitesh Saxena Outline Symmetric Key Encryption Continued Discussion of Potential Project Topics Project proposal due 02/22/07
Lecture 3: Symmetric Key Encryption CS996: Modern Cryptography Spring 2007 Nitesh Saxena Outline Symmetric Key Encryption Continued Discussion of Potential Project Topics Project proposal due 02/22/07
Lecture 1 Applied Cryptography (Part 1)
 Lecture 1 Applied Cryptography (Part 1) Patrick P. C. Lee Tsinghua Summer Course 2010 1-1 Roadmap Introduction to Security Introduction to Cryptography Symmetric key cryptography Hash and message authentication
Lecture 1 Applied Cryptography (Part 1) Patrick P. C. Lee Tsinghua Summer Course 2010 1-1 Roadmap Introduction to Security Introduction to Cryptography Symmetric key cryptography Hash and message authentication
MAGNET identity management proposal for Personal Networks. Dimitris M. Kyriazanos
 Internatinal Telecmmunicatin Unin MAGNET identity management prpsal fr Persnal Netwrks Dimitris M. Kyriazans PhD Student NTUA Geneva, 5 December 2006 Persnal Netwrk - A Definitin A Persnal Netwrk (PN)
Internatinal Telecmmunicatin Unin MAGNET identity management prpsal fr Persnal Netwrks Dimitris M. Kyriazans PhD Student NTUA Geneva, 5 December 2006 Persnal Netwrk - A Definitin A Persnal Netwrk (PN)
In-Class Exercise. Hashing Used in: Hashing Algorithm
 In-Class Exercise Hashing Used in: Encryptin fr authenticatin Hash a digital signature, get the value assciated with the digital signature,and bth are sent separately t receiver. The receiver then uses
In-Class Exercise Hashing Used in: Encryptin fr authenticatin Hash a digital signature, get the value assciated with the digital signature,and bth are sent separately t receiver. The receiver then uses
Cryptography (Overview)
 Cryptography (Overview) Some history Caesar cipher, rot13 substitution ciphers, etc. Enigma (Turing) Modern secret key cryptography DES, AES Public key cryptography RSA, digital signatures Cryptography
Cryptography (Overview) Some history Caesar cipher, rot13 substitution ciphers, etc. Enigma (Turing) Modern secret key cryptography DES, AES Public key cryptography RSA, digital signatures Cryptography
CSC 474/574 Information Systems Security
 CSC 474/574 Information Systems Security Topic 2.1 Introduction to Cryptography CSC 474/574 By Dr. Peng Ning 1 Cryptography Cryptography Original meaning: The art of secret writing Becoming a science that
CSC 474/574 Information Systems Security Topic 2.1 Introduction to Cryptography CSC 474/574 By Dr. Peng Ning 1 Cryptography Cryptography Original meaning: The art of secret writing Becoming a science that
Introduction to Network Security Missouri S&T University CPE 5420 Data Integrity Algorithms
 Introduction to Network Security Missouri S&T University CPE 5420 Data Integrity Algorithms Egemen K. Çetinkaya Egemen K. Çetinkaya Department of Electrical & Computer Engineering Missouri University of
Introduction to Network Security Missouri S&T University CPE 5420 Data Integrity Algorithms Egemen K. Çetinkaya Egemen K. Çetinkaya Department of Electrical & Computer Engineering Missouri University of
Study Guide to Mideterm Exam
 YALE UNIVERSITY DEPARTMENT OF COMPUTER SCIENCE CPSC 467b: Cryptography and Computer Security Handout #7 Professor M. J. Fischer February 20, 2012 Study Guide to Mideterm Exam For the exam, you are responsible
YALE UNIVERSITY DEPARTMENT OF COMPUTER SCIENCE CPSC 467b: Cryptography and Computer Security Handout #7 Professor M. J. Fischer February 20, 2012 Study Guide to Mideterm Exam For the exam, you are responsible
PHP / JAVA Summer Training Program 2012
 PHP / JAVA Summer Training Prgram 2012 Curse Duratin: 45 days Pre-Requisite: Basic Knwledge f Internet Curse Fee: 10,000 ( Online Examinatin Fee, Bks, Certificatin, Tls & Sftware's Included ) Intrductin
PHP / JAVA Summer Training Prgram 2012 Curse Duratin: 45 days Pre-Requisite: Basic Knwledge f Internet Curse Fee: 10,000 ( Online Examinatin Fee, Bks, Certificatin, Tls & Sftware's Included ) Intrductin
KALASALINGAM UNIVERSITY
 KALASALINGAM UNIVERSITY (Kalasalingam Academy of Research and Education) DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERING CLASS NOTES CRYPTOGRAPHY AND NETWOTK SECURITY (CSE 405) Prepared by M.RAJA AP/CSE
KALASALINGAM UNIVERSITY (Kalasalingam Academy of Research and Education) DEPARTMENT OF COMPUTER SCIENCE AND ENGINEERING CLASS NOTES CRYPTOGRAPHY AND NETWOTK SECURITY (CSE 405) Prepared by M.RAJA AP/CSE
Some Stuff About Crypto
 Some Stuff About Crypto Adrian Frith Laboratory of Foundational Aspects of Computer Science Department of Mathematics and Applied Mathematics University of Cape Town This work is licensed under a Creative
Some Stuff About Crypto Adrian Frith Laboratory of Foundational Aspects of Computer Science Department of Mathematics and Applied Mathematics University of Cape Town This work is licensed under a Creative
Chapter 8 Security. Computer Networking: A Top Down Approach. 6 th edition Jim Kurose, Keith Ross Addison-Wesley March 2012
 Chapter 8 Security A note on the use of these ppt slides: We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you see the animations; and can add,
Chapter 8 Security A note on the use of these ppt slides: We re making these slides freely available to all (faculty, students, readers). They re in PowerPoint form so you see the animations; and can add,
Sometimes it's necessary to issue requests to objects without knowing anything about the operation being requested or the receiver of the request.
 Cmmand 1 Intent Encapsulate a request as an bject, thereby letting yu parameterize clients with different requests, queue r lg requests, and supprt undable peratins. Als Knwn As Actin, Transactin Mtivatin
Cmmand 1 Intent Encapsulate a request as an bject, thereby letting yu parameterize clients with different requests, queue r lg requests, and supprt undable peratins. Als Knwn As Actin, Transactin Mtivatin
Chapter 8. Network Security. Need for Security. An Introduction to Cryptography. Transposition Ciphers One-Time Pads
 Cryptography p y Chapter 8 Network Security Introduction to Cryptography Substitution Ciphers Transposition Ciphers One-Time Pads Two Fundamental Cryptographic Principles Need for Security An Introduction
Cryptography p y Chapter 8 Network Security Introduction to Cryptography Substitution Ciphers Transposition Ciphers One-Time Pads Two Fundamental Cryptographic Principles Need for Security An Introduction
Sankalchand Patel College of Engineering, Visnagar Department of Computer Engineering & Information Technology. Question Bank
 Sankalchand Patel College of Engineering, Visnagar Department of Computer Engineering & Information Technology Question Bank Subject: Information Security (160702) Class: BE Sem. VI (CE/IT) Unit-1: Conventional
Sankalchand Patel College of Engineering, Visnagar Department of Computer Engineering & Information Technology Question Bank Subject: Information Security (160702) Class: BE Sem. VI (CE/IT) Unit-1: Conventional
Kaltura MediaSpace TM Enterprise 2.0 Requirements and Installation
 Kaltura MediaSpace TM Enterprise 2.0 Requirements and Installatin Updated Aug 30, 2011 Server Requirements Hardware The hardware requirements are mstly dependent n the number f cncurrent users yu expect
Kaltura MediaSpace TM Enterprise 2.0 Requirements and Installatin Updated Aug 30, 2011 Server Requirements Hardware The hardware requirements are mstly dependent n the number f cncurrent users yu expect
IRDS: Data Mining Process
 IRDS: Data Mining Prcess Charles Suttn University f Edinburgh (many figures used frm Murphy. Machine Learning: A Prbabilistic Perspective.) Data Science Our wrking definitin Data science is the study f
IRDS: Data Mining Prcess Charles Suttn University f Edinburgh (many figures used frm Murphy. Machine Learning: A Prbabilistic Perspective.) Data Science Our wrking definitin Data science is the study f
Public Key Algorithms
 Public Key Algorithms 1 Public Key Algorithms It is necessary to know some number theory to really understand how and why public key algorithms work Most of the public key algorithms are based on modular
Public Key Algorithms 1 Public Key Algorithms It is necessary to know some number theory to really understand how and why public key algorithms work Most of the public key algorithms are based on modular
ip.buffer App Note AN009 : Security Considerations
 ip.buffer App Nte AN009 : Security Cnsideratins Date Authr Release 2008-12-18 MP Initial draft UK 2008 Scannex Electrnics Limited. All rights reserved wrldwide. Scannex Electrnics Ltd, UK t: +44(0)8707
ip.buffer App Nte AN009 : Security Cnsideratins Date Authr Release 2008-12-18 MP Initial draft UK 2008 Scannex Electrnics Limited. All rights reserved wrldwide. Scannex Electrnics Ltd, UK t: +44(0)8707
Outline. Data Encryption Standard. Symmetric-Key Algorithms. Lecture 4
 EEC 693/793 Special Topics in Electrical Engineering Secure and Dependable Computing Lecture 4 Department of Electrical and Computer Engineering Cleveland State University wenbing@ieee.org Outline Review
EEC 693/793 Special Topics in Electrical Engineering Secure and Dependable Computing Lecture 4 Department of Electrical and Computer Engineering Cleveland State University wenbing@ieee.org Outline Review
Chapter 8 Web Security
 Chapter 8 Web Security Web security includes three parts: security of server, security of client, and network traffic security between a browser and a server. Security of server and security of client
Chapter 8 Web Security Web security includes three parts: security of server, security of client, and network traffic security between a browser and a server. Security of server and security of client
Key Exchange. References: Applied Cryptography, Bruce Schneier Cryptography and Network Securiy, Willian Stallings
 Key Exchange References: Applied Cryptography, Bruce Schneier Cryptography and Network Securiy, Willian Stallings Outlines Primitives Root Discrete Logarithm Diffie-Hellman ElGamal Shamir s Three Pass
Key Exchange References: Applied Cryptography, Bruce Schneier Cryptography and Network Securiy, Willian Stallings Outlines Primitives Root Discrete Logarithm Diffie-Hellman ElGamal Shamir s Three Pass
Cipher Suite Configuration Mode Commands
 The Cipher Suite Configuration Mode is used to configure the building blocks for SSL cipher suites, including the encryption algorithm, hash function, and key exchange. Important The commands or keywords/variables
The Cipher Suite Configuration Mode is used to configure the building blocks for SSL cipher suites, including the encryption algorithm, hash function, and key exchange. Important The commands or keywords/variables
PASSWORDS & ENCRYPTION
 PASSWORDS & ENCRYPTION Villanova University Department of Computing Sciences D. Justin Price Fall 2014 CRYPTOGRAPHY Hiding the meaning of a message from unintended recipients. Open source algorithms are
PASSWORDS & ENCRYPTION Villanova University Department of Computing Sciences D. Justin Price Fall 2014 CRYPTOGRAPHY Hiding the meaning of a message from unintended recipients. Open source algorithms are
Lab 1 - Calculator. K&R All of Chapter 1, 7.4, and Appendix B1.2
 UNIVERSITY OF CALIFORNIA, SANTA CRUZ BOARD OF STUDIES IN COMPUTER ENGINEERING CMPE13/L: INTRODUCTION TO PROGRAMMING IN C SPRING 2012 Lab 1 - Calculatr Intrductin In this lab yu will be writing yur first
UNIVERSITY OF CALIFORNIA, SANTA CRUZ BOARD OF STUDIES IN COMPUTER ENGINEERING CMPE13/L: INTRODUCTION TO PROGRAMMING IN C SPRING 2012 Lab 1 - Calculatr Intrductin In this lab yu will be writing yur first
A keyboard that manages your passwords in Android
 A keybard that manages yur passwrds in Andrid PRISMS 2014 Aalbrg, 11-14 May 2014 Faysal Bukayua Vincent Naessens Bart De Decker KU Leuven Overview Mtivatin Apprach Implementatin Other cnsideratins Evaluatin
A keybard that manages yur passwrds in Andrid PRISMS 2014 Aalbrg, 11-14 May 2014 Faysal Bukayua Vincent Naessens Bart De Decker KU Leuven Overview Mtivatin Apprach Implementatin Other cnsideratins Evaluatin
ECE 646 Fall 2009 Final Exam December 15, Multiple-choice test
 ECE 646 Fall 2009 Final Exam December 15, 2009 Multiple-choice test 1. (1 pt) Parallel processing can be used to speed up the following cryptographic transformations (please note that multiple answers
ECE 646 Fall 2009 Final Exam December 15, 2009 Multiple-choice test 1. (1 pt) Parallel processing can be used to speed up the following cryptographic transformations (please note that multiple answers
Refresher: Applied Cryptography
 Refresher: Applied Cryptography (emphasis on common tools for secure processors) Chris Fletcher Fall 2017, 598 CLF, UIUC Complementary reading Intel SGX Explained (ISE) Victor Costan, Srini Devadas https://eprint.iacr.org/2016/086.pdf
Refresher: Applied Cryptography (emphasis on common tools for secure processors) Chris Fletcher Fall 2017, 598 CLF, UIUC Complementary reading Intel SGX Explained (ISE) Victor Costan, Srini Devadas https://eprint.iacr.org/2016/086.pdf
Double-DES, Triple-DES & Modes of Operation
 Double-DES, Triple-DES & Modes of Operation Prepared by: Dr. Mohamed Abd-Eldayem Ref.: Cryptography and Network Security by William Stallings & Lecture slides by Lawrie Brown Multiple Encryption & DES
Double-DES, Triple-DES & Modes of Operation Prepared by: Dr. Mohamed Abd-Eldayem Ref.: Cryptography and Network Security by William Stallings & Lecture slides by Lawrie Brown Multiple Encryption & DES
Encryption 2. Tom Chothia Computer Security: Lecture 3
 Encryption 2 Tom Chothia Computer Security: Lecture 3 This Lecture Counter Mode (CTR) enryption Diffie Helleman key exchange Public Key Encryption RSA Signing Combining public and symmetric key encryption
Encryption 2 Tom Chothia Computer Security: Lecture 3 This Lecture Counter Mode (CTR) enryption Diffie Helleman key exchange Public Key Encryption RSA Signing Combining public and symmetric key encryption
1.264 Lecture 28. Cryptography: Asymmetric keys
 1.264 Lecture 28 Cryptography: Asymmetric keys Next class: Anderson chapters 20. Exercise due before class (Reading doesn t cover same topics as lecture) 1 Asymmetric or public key encryption Receiver
1.264 Lecture 28 Cryptography: Asymmetric keys Next class: Anderson chapters 20. Exercise due before class (Reading doesn t cover same topics as lecture) 1 Asymmetric or public key encryption Receiver
