How to configure SecureW2
|
|
|
- Marianna Norton
- 6 years ago
- Views:
Transcription
1 How to configure SecureW2
2 Disclaimer The software described in this document is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Copyright Notice Copyright 2009 SecureW2 B.V. All rights reserved Released: Juli 2009 This document may not, in whole or in part, be copied, photocopied, reproduced, translated, or reduced to any electronic medium or machine-readable form without prior consent in writing from SecureW2 B.V. Every effort has been made to ensure the accuracy of this manual. However, SecureW2 makes no warranties with respect to this documentation and disclaims any implied warranties of merchantability and fitness for a particular purpose. SecureW2 shall not be liable for any errors or for incidental or consequential damages in connection with the furnishing, performance, or use of this manual or the examples herein. The information of this document is subject to change without notice. Trademarks SecureW2 is a trademark of SecureW2 B.V. Other product names mentioned in this manual may be trademarks or registered trademarks of their related companies and are the sole property of their respective manufacturers. Page 2
3 1 SecureW2 TTLS and PEAP Configuration 1.1 Profile SecureW2 uses profiles to configure the TTLS and PEAP methods. This window allows you to create, edit and delete profiles as you wish. Profile New Configure Delete This drop down box lets you select the current profile for this connection. Tap on this button to create a new profile. Tap on this button to configure the profile currently selected in the drop down box. Tap on this button to delete the profile currently selected in the drop down box. NOTE:Administrative users have full access to all options displayed. Non-administrators are only able to configure the selected profile. They cannot create, select or delete a profile. Page 3
4 1.2 SecureW2 Profile Configuration After creating a new profile or when you wish to configure an existing profile you will be presented with the SecureW2 Profile Configuration window. This window is built up out of four tabs: Connection in which you specify connection settings; Certificates in which you specify how you wish to handle certificates of network authentication servers you connect to; Authentication in which you specify how you wish to authenticate; User account in which you specify how the user will present his/her credentials. NOTE: Non-Administrative users can only access the User account tab Connection In this tab you can specify connection settings: Use alternate outer identity Use anonymous outer identity Allows the use of a different outer identity. Sets the outer identity to an anonymous identity. If for example the username entered in the user credentials window is: usenamer@domain, selecting this option sets the outer identity to anonymous@domain. Page 4
5 Specify outer identity Enable session resumption (quick connect) This allows you to specify the Outer Identity that is to be used during authentication. Once a user has successfully been authenticated it is possible to use session resumption whenever the user s session times out or if a user has roamed to another access point Certificates In this tab you specify how you wish to handle certificates of network authentication servers that you connect to Verify Server Certificate Select this option if you want the SecureW2 Client to verify the certificate of the remote server that will carry out the authentication. NOTE: The certificate will be verified using the certificate trust of the local computer. Trusted Root CA Add CA Remove CA Verify This selection box contains the certificate authorities currently trusted by SecureW2. When you select this option a dialog box is shown with the current certificate authorities installed on the local computer. Select the appropriate ca and click on OK. The certificate authority will now appear in the selection box Trusted Root CA. When you select this option the highlighted certification authority will be removed from the selection box Trusted Root CA. Select this option to allow SecureW2 to verify the Page 5
6 server name Common Name in the certificate of the authenticating server. For example by specifying domain.com SecureW2 will connect to all servers with a Common Name ending in domain.com. NOTE: If you leave the Trusted Root CA empty you will receive a warning stated that SecureW2 will use the default Microsoft certificate trust to verify the certificates Authentication In this tab, you configure how you wish to authenticate when connecting to the network: Select Authentication Method EAP Type Configure This drop down box let's you select the inner authentication used by SecureW2. Currently you have two choices: 1. PAP (username password) 2. EAP (SecureW2 will use another EAP module to authenticate the user) When you select EAP as the inner authentication type this drop down box will be enabled. It shows the current EAP modules installed on the device from you may choose to use as the inner authentication. If an inner EAP module is configurable you can use this button to configure the selected inner EAP module. Page 6
7 1.2.4 User Account In this tab, you configure how the user will present her/his credentials when connecting: Prompt user for credentials Use this account to logon computer When this option is selected the user is prompted to enter his or her credentials during the authentication sequence. When this option is selected the user credentials will also be used to logon the computer during start up. Page 7
8 1.3 Advanced Configuration In this window, you configure the advanced options of SecureW2: Use alternate account to logon computer Server certificate must be installed on local computer Check for Microsoft Key extension When this option is selected the credentials entered in the fields Username, Password and Domain are used to authenticate the connection when the system itself wants to setup a 802.1X connection. When this option is selected the certificate of the server must be installed in the certificate store of the local computer. When this option is selected the certificate of the server must have the Enhanced Key Usage: Server Authentication. The options Server certificate must be installed on local computer and Check For Microsoft Key extension will only work if the option Verify Server Certificate is enabled in the Connection tab. Allow users to setup new connections Renew IP Select this option to allow users to setup new connections. By default, users are not allowed to setup new connections (meaning install unknown certificates). This is to prevent hackers from trying to trick users into connecting to their access point by inserting a certificate that appears to be from the user s organization. When this option is selected the SecureW2 client Page 8
9 address after authentication will try to renew the adapters IP address after successful authentication. IMPORTANT:Use only if necessary. This option is only applicable to setups where the DHCP renewal is not working correctly. Do NOT use in normal circumstances. 1.4 Connecting to the Network As soon as you have configured SecureW2, the authentication procedure for connecting to the network will start automatically Windows XP and Vista User Interface Windows XP and Vista use a specific user interface in which, before a user can interact, the user must first click on an Information pop-up in the bottom-right hand side of the screen. Simply click anywhere in the Information pop-up and the actual interaction window will appear in which the user may for example enter a username. There are two types of Information pop-ups used during the 802.1x authentication. IMPORTANT: Make sure the Show icon in notification area when connected is selected in the adapter properties. This will allow the Wired and Wireless Zero Config to interact with the user when needed. 1. When the user needs to enter his/her credentials: 2. When the Unknown server (See section 2.2 Unknown Server) window is to be displayed: Page 9
10 The first time you connect to an authentication server and the server certificate is not trusted; SecureW2 will pop up the Unknown server window. 'NOTE: The Unknown Server window will only appear if the option Allow users to setup new connections is selected.' This shows the certificate hierarchy in which the unknown server certificate resides. This window will only pop up if you have selected Verify server certificate in the certificate handling options of SecureW2. Before you can connect to the server all the certificates in the chain must be trusted. To trust a certificate is must be installed onto the device. Indicates a trusted certificate Indicates a certificate is not trusted Install All Certificates Install Certificate Installs the selected certificate as trusted. View Certificate Installs all displayed certificates as trusted. Lets you examine a certificate. Page 10
SecureW2 Client for Windows Administrator Guide. Version 2.2
 SecureW2 Client for Windows Administrator Guide Version 2.2 The software described in this document is furnished under a license agreement and may be used only in accordance with the terms of the agreement.
SecureW2 Client for Windows Administrator Guide Version 2.2 The software described in this document is furnished under a license agreement and may be used only in accordance with the terms of the agreement.
TippingPoint Best Practice Guide. RADIUS PEAP Configuration for IPS Devices and Cisco ACS. Version:
 TippingPoint Best Practice Guide RADIUS PEAP Configuration for IPS Devices and Cisco ACS Version: 16.1.1 Copyright Statement Copyright 2016 Trend Micro. Trend Micro Incorporated ( Trend Micro ) makes no
TippingPoint Best Practice Guide RADIUS PEAP Configuration for IPS Devices and Cisco ACS Version: 16.1.1 Copyright Statement Copyright 2016 Trend Micro. Trend Micro Incorporated ( Trend Micro ) makes no
How to connect to Wi-Fi
 41 How to connect to Wi-Fi LSBU uses the eduroam service to connect Wi-Fi devices. Once you are set up you will automatically be connected whenever you are in range. Wireless Internet access is available
41 How to connect to Wi-Fi LSBU uses the eduroam service to connect Wi-Fi devices. Once you are set up you will automatically be connected whenever you are in range. Wireless Internet access is available
Internet Access: Wireless WVU.Encrypted Network Connecting a Windows 7 Device
 Internet Access: Wireless WVU.Encrypted Network Connecting a Windows 7 Device Prerequisites An activated MyID account is required to use ResNet s wireless network. If you have not activated your MyID account,
Internet Access: Wireless WVU.Encrypted Network Connecting a Windows 7 Device Prerequisites An activated MyID account is required to use ResNet s wireless network. If you have not activated your MyID account,
IT Quick Reference Guides Connecting to SU-Secure using Windows 8
 IT Quick Reference Guides Connecting to SU-Secure using Windows 8 Windows Guides CONNECTING TO SU-SECURE WI-FI This document will give you instructions on how to connect your Windows 8 Computer to our
IT Quick Reference Guides Connecting to SU-Secure using Windows 8 Windows Guides CONNECTING TO SU-SECURE WI-FI This document will give you instructions on how to connect your Windows 8 Computer to our
Wireless for Windows 7
 Wireless for Windows 7 The new CWSL wireless network consists of three different wireless networks CWSL Faculty-Staff - This network is for faculty and staff only. (uses WPA2-Enterprise encryption) CWSL
Wireless for Windows 7 The new CWSL wireless network consists of three different wireless networks CWSL Faculty-Staff - This network is for faculty and staff only. (uses WPA2-Enterprise encryption) CWSL
BEFORE INSTALLATION: INSTALLATION:
 QUICK USER GUIDE INFORMATION TECHNOLOGY SERVICES SWINWIFI INSTALLATION GUIDE FOR WINDOWS XP BEFORE INSTALLATION: 1. Download Swinwifi installer to your desktop. You may download it from http://www.swinburne.edu.my/current_students.php.
QUICK USER GUIDE INFORMATION TECHNOLOGY SERVICES SWINWIFI INSTALLATION GUIDE FOR WINDOWS XP BEFORE INSTALLATION: 1. Download Swinwifi installer to your desktop. You may download it from http://www.swinburne.edu.my/current_students.php.
Quick Start Program Installation Guide
 Quick Start Program Installation Guide Copyright 2010 GroupLink Corporation. All Rights Reserved. ContactWise is a registered trademark of GroupLink Corporation. All other trademarks are the property of
Quick Start Program Installation Guide Copyright 2010 GroupLink Corporation. All Rights Reserved. ContactWise is a registered trademark of GroupLink Corporation. All other trademarks are the property of
Residence Towers Network Access for Windows XP / 2000 Computers
 Residence Towers Network Access for Windows XP / 2000 Computers These instructions will help you set up your wired connection on campus. Before beginning, you need: An activated student account on Gila
Residence Towers Network Access for Windows XP / 2000 Computers These instructions will help you set up your wired connection on campus. Before beginning, you need: An activated student account on Gila
Manually Configuring Windows 8 for Wireless PittNet
 Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Manually Configuring Windows 8 for Wireless PittNet If you are not able to connect to Wireless PittNet using our automated wizard, you
Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Manually Configuring Windows 8 for Wireless PittNet If you are not able to connect to Wireless PittNet using our automated wizard, you
Instructions for connecting to winthropsecure
 Instructions for connecting to winthropsecure Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Windows 10 Quick Connect Windows 10 Wireless Set Up Apple Quick Connect Apple Settings Check Windows
Instructions for connecting to winthropsecure Windows 7/8 Quick Connect Windows 7/8 Manual Wireless Set Up Windows 10 Quick Connect Windows 10 Wireless Set Up Apple Quick Connect Apple Settings Check Windows
Partner Information. Integration Overview Authentication Methods Supported
 Partner Information Partner Name Product Name Integration Overview Authentication Methods Supported Client Integration F5 Networks FirePass VPN User Name - Security Code User Name - Password - Security
Partner Information Partner Name Product Name Integration Overview Authentication Methods Supported Client Integration F5 Networks FirePass VPN User Name - Security Code User Name - Password - Security
Configuring EAP-FAST CHAPTER
 CHAPTER 3 This chapter explains how to configure EAP-FAST module settings, such as connection settings, user credentials, and authentication methods. The following topics are covered in this chapter: Accessing
CHAPTER 3 This chapter explains how to configure EAP-FAST module settings, such as connection settings, user credentials, and authentication methods. The following topics are covered in this chapter: Accessing
NCD ThinPATH PC Installation Guide and Release Notes
 NCD ThinPATH PC Installation Guide and Release s Copyright Copyright 2001 by Network Computing Devices, Inc. (NCD).The information contained in this document is subject to change without notice. Network
NCD ThinPATH PC Installation Guide and Release s Copyright Copyright 2001 by Network Computing Devices, Inc. (NCD).The information contained in this document is subject to change without notice. Network
Installing Act! for New Users
 Installing Act! for New Users Installing Act! for New Users 2017 Swiftpage ACT! LLC. All Rights Reserved. Swiftpage, Act!, and the Swiftpage product and service names mentioned herein are registered trademarks
Installing Act! for New Users Installing Act! for New Users 2017 Swiftpage ACT! LLC. All Rights Reserved. Swiftpage, Act!, and the Swiftpage product and service names mentioned herein are registered trademarks
Symantec Managed PKI. Integration Guide for ActiveSync
 Symantec Managed PKI Integration Guide for ActiveSync ii Symantec Managed PKI Symantec Managed PKI Integration Guide for ActiveSync The software described in this book is furnished under a license agreement
Symantec Managed PKI Integration Guide for ActiveSync ii Symantec Managed PKI Symantec Managed PKI Integration Guide for ActiveSync The software described in this book is furnished under a license agreement
Securewireless Windows 7 Setup Guide
 Securewireless Windows 7 Setup Guide 1. Click on the wireless icon in the lower right-hand corner of the taskbar and then click on Open Network and Sharing Center. 2. From the Network and Sharing Center
Securewireless Windows 7 Setup Guide 1. Click on the wireless icon in the lower right-hand corner of the taskbar and then click on Open Network and Sharing Center. 2. From the Network and Sharing Center
Part 1: Connecting to HawkNET on your Windows XP PC
 Students are NOT permitted to use any device or product that extends the HawkNET network beyond the intended personal use. These restrictions include, but are not limited to, the use of personal routers,
Students are NOT permitted to use any device or product that extends the HawkNET network beyond the intended personal use. These restrictions include, but are not limited to, the use of personal routers,
EacStudent Wireless Access for Windows XP / 2000 Computers
 EacStudent Wireless Access for Windows XP / 2000 Computers These instructions will help you set up your wireless connection on campus. Before beginning, you need: An activated student account on Gila Hank
EacStudent Wireless Access for Windows XP / 2000 Computers These instructions will help you set up your wireless connection on campus. Before beginning, you need: An activated student account on Gila Hank
Instructions for connecting to the FDIBA Wireless Network (Windows Vista)
 Instructions for connecting to the FDIBA Wireless Network (Windows Vista) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Instructions for connecting to the FDIBA Wireless Network (Windows Vista) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Connecting to the NJITSecure wireless network.
 Connecting to the NJITSecure wireless network. 1. Start by going to the Start menu and selecting Control Panel 2. Your control Panel will most likely be in Category view, you will need to change it to
Connecting to the NJITSecure wireless network. 1. Start by going to the Start menu and selecting Control Panel 2. Your control Panel will most likely be in Category view, you will need to change it to
IMPORTANT INFORMATION FOR CURTIN WIRELESS ACCESS - STUDENT / WINDOWS XP -
 IMPORTANT INFORMATION FOR CURTIN WIRELESS ACCESS - STUDENT / WINDOWS XP - Information required for connection to the Curtin Wireless network: Wireless network names There are two wireless networks operating
IMPORTANT INFORMATION FOR CURTIN WIRELESS ACCESS - STUDENT / WINDOWS XP - Information required for connection to the Curtin Wireless network: Wireless network names There are two wireless networks operating
Manually Configuring Windows 7 for Wireless PittNet
 Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Manually Configuring Windows 7 for Wireless PittNet If you are not able to connect to Wireless PittNet using our automated wizard, you
Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Manually Configuring Windows 7 for Wireless PittNet If you are not able to connect to Wireless PittNet using our automated wizard, you
Connecting to the eduroam Wireless Network. 1. If you are using a PC, move the. 2. Next Click or Tap the Settings. Help Sheet Windows 8.
 Connecting to the eduroam Wireless Network Help Sheet Windows 8 October 2013 This Help Sheet assists Windows 8 users to access the eduroam Wireless Network. 1. If you are using a PC, move the mouse to
Connecting to the eduroam Wireless Network Help Sheet Windows 8 October 2013 This Help Sheet assists Windows 8 users to access the eduroam Wireless Network. 1. If you are using a PC, move the mouse to
Partner Information. Integration Overview. Remote Access Integration Architecture
 Partner Information Partner Name Product Name Integration Overview Authentication Methods Supported Client Integration OTP Barracuda Networks Barracuda SSL VPN User Name + Security Code VIP Enterprise
Partner Information Partner Name Product Name Integration Overview Authentication Methods Supported Client Integration OTP Barracuda Networks Barracuda SSL VPN User Name + Security Code VIP Enterprise
Configure Wireless for Windows 7
 Configure Wireless for Windows 7 There are two main procedures for configuring Windows 7 to access McGill's wireless network. You can also add the steps at the bottom if you don't want your username and
Configure Wireless for Windows 7 There are two main procedures for configuring Windows 7 to access McGill's wireless network. You can also add the steps at the bottom if you don't want your username and
SignWare-Pro. User s Guide. SignWare-Pro v1.2.
 SignWare-Pro User s Guide SignWare-Pro v1.2 www.smartavi.com Table of Contents Introduction... 3 Disclaimer Notice... 4 What s in the Box?... 5 Limited Warranty Statement... 6 Section 1 -Setting up the
SignWare-Pro User s Guide SignWare-Pro v1.2 www.smartavi.com Table of Contents Introduction... 3 Disclaimer Notice... 4 What s in the Box?... 5 Limited Warranty Statement... 6 Section 1 -Setting up the
Cisco 802.1x Wireless using PEAP Quick Reference Guide
 Cisco 802.1x Wireless using PEAP Quick Reference Guide Copyright Copyright 2006, CRYPTOCard Inc. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in
Cisco 802.1x Wireless using PEAP Quick Reference Guide Copyright Copyright 2006, CRYPTOCard Inc. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in
Mobile Admin GETTING STARTED GUIDE. Version 8.2. Last Updated: Thursday, May 25, 2017
 GETTING STARTED GUIDE Mobile Admin Version 8.2 Last Updated: Thursday, May 25, 2017 Retrieve the latest version from: https://support.solarwinds.com/success_center/mobile_admin/mobile_admin_documentation
GETTING STARTED GUIDE Mobile Admin Version 8.2 Last Updated: Thursday, May 25, 2017 Retrieve the latest version from: https://support.solarwinds.com/success_center/mobile_admin/mobile_admin_documentation
x10data Smart Client 6.5 for Windows Mobile Installation Guide
 x10data Smart Client 6.5 for Windows Mobile Installation Guide Copyright Copyright 2009 Automated Data Capture (ADC) Technologies, Incorporated. All rights reserved. Complying with all applicable copyright
x10data Smart Client 6.5 for Windows Mobile Installation Guide Copyright Copyright 2009 Automated Data Capture (ADC) Technologies, Incorporated. All rights reserved. Complying with all applicable copyright
Manual UCSFwpa Configuration for Windows 7
 Image not found https://it.ucsf.edu/sites/it.ucsf.edu/themes/custom/it_new/logo.png it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu) Home > Manual UCSFwpa Configuration for Windows 7 Manual UCSFwpa
Image not found https://it.ucsf.edu/sites/it.ucsf.edu/themes/custom/it_new/logo.png it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu) Home > Manual UCSFwpa Configuration for Windows 7 Manual UCSFwpa
Connect to Wireless, certificate install and setup Citrix Receiver
 Connect to Wireless, certificate install and setup Citrix Receiver This document explains how to connect to the Wireless Network and access applications using Citrix Receiver on a Bring Your Own Device
Connect to Wireless, certificate install and setup Citrix Receiver This document explains how to connect to the Wireless Network and access applications using Citrix Receiver on a Bring Your Own Device
Agilent CytoGenomics 2.5
 Agilent CytoGenomics 2.5 Installation and Administration Guide Research Use Only. Not for Diagnostic Procedures. Agilent Technologies Notices Agilent Technologies, Inc. 2012 No part of this manual may
Agilent CytoGenomics 2.5 Installation and Administration Guide Research Use Only. Not for Diagnostic Procedures. Agilent Technologies Notices Agilent Technologies, Inc. 2012 No part of this manual may
Reference Card: How to connect Windows 7 to UniWireless
 Reference Card: How to connect Windows 7 to UniWireless Important Information Windows 7 is not supported by ITS. These instructions provided are only a guide and do not provide any troubleshooting assistance.
Reference Card: How to connect Windows 7 to UniWireless Important Information Windows 7 is not supported by ITS. These instructions provided are only a guide and do not provide any troubleshooting assistance.
Instructions for connecting to the FDIBA Wireless Network. (Windows XP)
 Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Instructions for connecting to the FDIBA Wireless Network (Windows XP) In order to connect, you need your username and password, as well as the FDIBA Root Certificate which you need to install on your
Contents. Windows 7 Instructions Windows 10 Instructions Android Instructions Mac OS Instructions ios Instructions...
 The following provides instructions on how to connect to the SJCD-Secure Wireless Network from a variety of operating systems and devices. If you experience any difficulty with these instructions, please
The following provides instructions on how to connect to the SJCD-Secure Wireless Network from a variety of operating systems and devices. If you experience any difficulty with these instructions, please
Internet access system through the Wireless Network of the University of Bologna (last update )
 Internet access system through the Wireless Network of the University of Bologna (last update 7.03.2012) Printable service summary document: the updated version is available online at the following address
Internet access system through the Wireless Network of the University of Bologna (last update 7.03.2012) Printable service summary document: the updated version is available online at the following address
Worldox Integration with Canon imageformula DR-C225 Scanner. Version 1.0
 Worldox Integration with Canon imageformula DR-C225 Scanner Version 1.0 WARRANTIES AND COPYRIGHT NOTICES Disclaimer of Warranty World Software Corporation makes no representations or warranties, either
Worldox Integration with Canon imageformula DR-C225 Scanner Version 1.0 WARRANTIES AND COPYRIGHT NOTICES Disclaimer of Warranty World Software Corporation makes no representations or warranties, either
Your use of AirUWS-Lite is subject to the University s IT Acceptable Use of Resources Policy.
 AirUWS-Lite is the University s wireless network. This fact sheet describes connecting to AirUWS-Lite using a UWS laptop running Windows XP (SP3) and standard Windows network card drivers. AirUWS-Lite
AirUWS-Lite is the University s wireless network. This fact sheet describes connecting to AirUWS-Lite using a UWS laptop running Windows XP (SP3) and standard Windows network card drivers. AirUWS-Lite
VISTA - CTI Multi-port Serial Adapter. Install Guide
 VISTA - CTI Multi-port Serial Adapter Install Guide The information contained in this document is subject to change without notice. Connect Tech, Inc. shall not be liable for errors contained herein or
VISTA - CTI Multi-port Serial Adapter Install Guide The information contained in this document is subject to change without notice. Connect Tech, Inc. shall not be liable for errors contained herein or
Johns Hopkins
 Wireless Configuration Guide: Windows Vista Additional hopkins wireless network instructions and requirements for Windows 8, 7, XP, Mac OS X, Linux, and Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Wireless Configuration Guide: Windows Vista Additional hopkins wireless network instructions and requirements for Windows 8, 7, XP, Mac OS X, Linux, and Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
NT 0018 Instructions for Setting Up UoE_Secure (XP)
 Academic Services Information & Computing Services Division Network Team NT 0018 Instructions for Setting Up UoE_Secure (XP) Document reference: Document type: Document status: Review period: NT0018 Network
Academic Services Information & Computing Services Division Network Team NT 0018 Instructions for Setting Up UoE_Secure (XP) Document reference: Document type: Document status: Review period: NT0018 Network
Johns Hopkins
 Wireless Configuration Guide: Windows 8 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, 7, Mac OS X, Linux, and other Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Wireless Configuration Guide: Windows 8 Additional hopkins wireless network instructions and requirements for Windows XP, Vista, 7, Mac OS X, Linux, and other Mobile versions can be found at: http://www.it.johnshopkins.edu/services/network/wireless/
Configuring WPA2 for Windows XP
 Configuring WPA2 for Windows XP Requirements for wireless using WPA2 on Windows XP Your wireless card must support 802.1x, AES, and WPA2. Your computer must have Windows XP service pack 2 installed and
Configuring WPA2 for Windows XP Requirements for wireless using WPA2 on Windows XP Your wireless card must support 802.1x, AES, and WPA2. Your computer must have Windows XP service pack 2 installed and
Dell SonicWALL Aventail Connect Tunnel User s Guide
 Dell SonicWALL Aventail 10.6.2 Connect Tunnel User s Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION
Dell SonicWALL Aventail 10.6.2 Connect Tunnel User s Guide 1 Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your system. CAUTION: A CAUTION
Windows 8.1 and Windows 10 a) Connect to wireless network Click on the wireless icon in taskbar. Select detnsw and click on Connect.
 1 HSHS BYOD Wireless Connection Windows 8.1 and Windows 10 a) Connect to wireless network Click on the wireless icon in taskbar. Windows 8.1 icon: Windows 10 icon: Select detnsw and click on Connect. or
1 HSHS BYOD Wireless Connection Windows 8.1 and Windows 10 a) Connect to wireless network Click on the wireless icon in taskbar. Windows 8.1 icon: Windows 10 icon: Select detnsw and click on Connect. or
x10data Smart Client 7.0 for Windows Mobile Installation Guide
 x10data Smart Client 7.0 for Windows Mobile Installation Guide Copyright Copyright 2009 Automated Data Capture (ADC) Technologies, Incorporated. All rights reserved. Complying with all applicable copyright
x10data Smart Client 7.0 for Windows Mobile Installation Guide Copyright Copyright 2009 Automated Data Capture (ADC) Technologies, Incorporated. All rights reserved. Complying with all applicable copyright
One Identity Active Roles 7.2. Replication: Best Practices and Troubleshooting Guide
 One Identity Active Roles 7.2 Replication: Best Practices and Troubleshooting Copyright 2017 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The
One Identity Active Roles 7.2 Replication: Best Practices and Troubleshooting Copyright 2017 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The
Authorized Send User s Guide Version 4.0
 Canon Authorized Send User s Guide Version 4.0 08011-40-UD1-003 This page is intentionally left blank. 2 Authorized Send User s Guide Contents Preface...5 How to Use This Manual... 5 Symbols Used in This
Canon Authorized Send User s Guide Version 4.0 08011-40-UD1-003 This page is intentionally left blank. 2 Authorized Send User s Guide Contents Preface...5 How to Use This Manual... 5 Symbols Used in This
To Activate your Wireless Account
 To Activate your Wireless Account Access to the WVU Wireless network will require you to have an active WVU Active Directory account. Activation involves authenticating your account and setting a password.
To Activate your Wireless Account Access to the WVU Wireless network will require you to have an active WVU Active Directory account. Activation involves authenticating your account and setting a password.
simplifying... Wireless Access
 simplifying... Wireless Access Contents Introduction... 1 Android Devices... 1 Apple Devices... 4 ipad, iphone & ipod... 4 Macbook... 6 Windows Devices... 7 Windows 7... 7 Windows Vista... 9 Windows XP...
simplifying... Wireless Access Contents Introduction... 1 Android Devices... 1 Apple Devices... 4 ipad, iphone & ipod... 4 Macbook... 6 Windows Devices... 7 Windows 7... 7 Windows Vista... 9 Windows XP...
Authorized Send User s Guide for imagerunner Machines Version 4.1
 Canon Authorized Send User s Guide for imagerunner Machines Version 4.1 08011-41-UD1-003 This page is intentionally left blank. 2 Authorized Send User s Guide for imagerunner Machines Contents Preface...5
Canon Authorized Send User s Guide for imagerunner Machines Version 4.1 08011-41-UD1-003 This page is intentionally left blank. 2 Authorized Send User s Guide for imagerunner Machines Contents Preface...5
Threat Analysis Reporter
 Threat Analysis Reporter Ethernet Tap Installation For TAR-MSA Threat Analysis Reporter UPDATED: 02.29.08 8e6 Threat Analysis Reporter: Ethernet Tap Installation 2008 8e6 Technologies. All rights reserved.
Threat Analysis Reporter Ethernet Tap Installation For TAR-MSA Threat Analysis Reporter UPDATED: 02.29.08 8e6 Threat Analysis Reporter: Ethernet Tap Installation 2008 8e6 Technologies. All rights reserved.
Dell Secure Mobile Access Connect Tunnel Service User Guide
 Dell Secure Mobile Access 11.4 Connect Tunnel Service 2016 Dell Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished
Dell Secure Mobile Access 11.4 Connect Tunnel Service 2016 Dell Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished
Marathon. Quick Start Guide. Hand-Held Computer
 Marathon Hand-Held Computer With Microsoft Windows 7 Professional or Microsoft Windows Embedded Standard 2009 or Microsoft Windows XP Professional Operating System Quick Start Guide MARATHON-QS Rev A 4/12
Marathon Hand-Held Computer With Microsoft Windows 7 Professional or Microsoft Windows Embedded Standard 2009 or Microsoft Windows XP Professional Operating System Quick Start Guide MARATHON-QS Rev A 4/12
Configuring 802.1X Authentication Client for Windows 8
 Configuring 802.1X Authentication Client for Windows 8 1. At the Metro Screen, press the windows key on your keyboard together with the alphabets x to go to the Control Panel. Page 1 1.1 In the Control
Configuring 802.1X Authentication Client for Windows 8 1. At the Metro Screen, press the windows key on your keyboard together with the alphabets x to go to the Control Panel. Page 1 1.1 In the Control
REMOVE TSUWIRELESS WIRELESS NETWORK 2 CONNECTING TO TSU_SECURE WIRELESS NETWORK 7 CONNECT TO TNSTATE.EDU USING MOBILE DEVICE 11
 REMOVE TSUWIRELESS WIRELESS NETWORK 2 APPLE MAC OS X VERSIONS 10.5 10.8 2 MICROSOFT WINDOWS 7 (ALSO WINDOWS VISTA) 3 APPLE IPHONE/APPLE IPAD - IOS 3 ANDROID PHONES 4 WINDOWS XP 5 CONNECTING TO TSU_SECURE
REMOVE TSUWIRELESS WIRELESS NETWORK 2 APPLE MAC OS X VERSIONS 10.5 10.8 2 MICROSOFT WINDOWS 7 (ALSO WINDOWS VISTA) 3 APPLE IPHONE/APPLE IPAD - IOS 3 ANDROID PHONES 4 WINDOWS XP 5 CONNECTING TO TSU_SECURE
Client Configuration Guide
 Email Client Configuration Guide Contents Prerequisites... 1 Microsoft Outlook 2007... 2 Microsoft Outlook 2002/XP and 2003... 7 Microsoft Windows Mail (available with Vista only)... 11 Microsoft Outlook
Email Client Configuration Guide Contents Prerequisites... 1 Microsoft Outlook 2007... 2 Microsoft Outlook 2002/XP and 2003... 7 Microsoft Windows Mail (available with Vista only)... 11 Microsoft Outlook
Configuring Remote Access using the RDS Gateway
 Configuring Remote Access using the RDS Gateway Author: AC, SNE Contents Introduction... 3 Pre-requisites... 3 Supported Operating Systems... 3 Installing the I.T. Services Certificate Authority Root Certificate...
Configuring Remote Access using the RDS Gateway Author: AC, SNE Contents Introduction... 3 Pre-requisites... 3 Supported Operating Systems... 3 Installing the I.T. Services Certificate Authority Root Certificate...
Using EAP Authentication
 CHAPTER 6 This chapter explains the sequence of events that occurs and the actions you must take when a profile that is set for EAP authentication is selected for use. The following topics are covered
CHAPTER 6 This chapter explains the sequence of events that occurs and the actions you must take when a profile that is set for EAP authentication is selected for use. The following topics are covered
Setting Up Cisco SSC. Introduction CHAPTER
 CHAPTER 2 This chapter provides an overview of the Cisco Secure Services Client and provides instructions for adding, configuring, and testing the user profiles. This chapter contains these sections: Introduction,
CHAPTER 2 This chapter provides an overview of the Cisco Secure Services Client and provides instructions for adding, configuring, and testing the user profiles. This chapter contains these sections: Introduction,
Upgrading BankLink Books
 Upgrading BankLink Books Contents Upgrading BankLink Books... 4 Upgrading BankLink Books using the automatic upgrade 4 Upgrading BankLink Books when asked to upgrade 5 Upgrading BankLink Books Page 2 of
Upgrading BankLink Books Contents Upgrading BankLink Books... 4 Upgrading BankLink Books using the automatic upgrade 4 Upgrading BankLink Books when asked to upgrade 5 Upgrading BankLink Books Page 2 of
VeriSign Managed PKI for SSL and Symantec Protection Center Integration Guide
 VeriSign Managed PKI for SSL and Symantec Protection Center Integration Guide VeriSign Managed PKI for SSL and Symantec Protection Center Integration Guide The software described in this book is furnished
VeriSign Managed PKI for SSL and Symantec Protection Center Integration Guide VeriSign Managed PKI for SSL and Symantec Protection Center Integration Guide The software described in this book is furnished
Browser Set-Up Instructions
 Browser Set-Up Instructions Before visiting the Assessment LinkBC site for the first time, you must configure your Internet Explorer browser: o to recognize the Assessment LinkBC site as a trusted site,
Browser Set-Up Instructions Before visiting the Assessment LinkBC site for the first time, you must configure your Internet Explorer browser: o to recognize the Assessment LinkBC site as a trusted site,
Enterprise Vault.cloud CloudLink Google Account Synchronization Guide. CloudLink to 4.0.3
 Enterprise Vault.cloud CloudLink Google Account Synchronization Guide CloudLink 4.0.1 to 4.0.3 Enterprise Vault.cloud: CloudLink Google Account Synchronization Guide Last updated: 2018-06-08. Legal Notice
Enterprise Vault.cloud CloudLink Google Account Synchronization Guide CloudLink 4.0.1 to 4.0.3 Enterprise Vault.cloud: CloudLink Google Account Synchronization Guide Last updated: 2018-06-08. Legal Notice
Connect to eduroam WiFi
 Connect to eduroam WiFi List Procedure for Windows 10... 2 Procedure for Windows 8... 4 Procedure for Windows 7... 6 Procedure for Mac... 11 Procedure for iphone, ipod Touch and ipad... 15 Procedure for
Connect to eduroam WiFi List Procedure for Windows 10... 2 Procedure for Windows 8... 4 Procedure for Windows 7... 6 Procedure for Mac... 11 Procedure for iphone, ipod Touch and ipad... 15 Procedure for
AST2500 ibmc Configuration Guide
 AST2500 ibmc Configuration Guide Version 1.0 Copyright Copyright 2017 MITAC COMPUTING TECHNOLOGY CORPORATION. All rights reserved. No part of this manual may be reproduced or translated without prior written
AST2500 ibmc Configuration Guide Version 1.0 Copyright Copyright 2017 MITAC COMPUTING TECHNOLOGY CORPORATION. All rights reserved. No part of this manual may be reproduced or translated without prior written
Wireless Setup Instructions for Windows 7
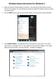 Wireless Setup Instructions for Windows 7 1. Make sure that your wireless feature is turned on. (You may need to flip a switch or press a button on your laptop.) On most laptops you should see a light
Wireless Setup Instructions for Windows 7 1. Make sure that your wireless feature is turned on. (You may need to flip a switch or press a button on your laptop.) On most laptops you should see a light
NeoAccel NeoAccel Management Console: Gateway Gateway Administration version version 2.3
 SSL VPN-Plus TM NeoAccel NeoAccel Management Console: Console: Gateway Gateway Administration version version 2.3 2.0 Copyright 2005-2006. 2005-2009. NeoAccel Inc. NeoAccel Inc. NMC - Volume II -SSL VPN-Plus-v2.33
SSL VPN-Plus TM NeoAccel NeoAccel Management Console: Console: Gateway Gateway Administration version version 2.3 2.0 Copyright 2005-2006. 2005-2009. NeoAccel Inc. NeoAccel Inc. NMC - Volume II -SSL VPN-Plus-v2.33
GETTING STARTED GUIDE. Mobile Admin. Version 8.2
 GETTING STARTED GUIDE Mobile Admin Version 8.2 Last Updated: April 24, 2018 GETTING STARTED GUIDE: MOBILE ADMIN 2018 SolarWinds Worldwide, LLC. All rights reserved. This document may not be reproduced
GETTING STARTED GUIDE Mobile Admin Version 8.2 Last Updated: April 24, 2018 GETTING STARTED GUIDE: MOBILE ADMIN 2018 SolarWinds Worldwide, LLC. All rights reserved. This document may not be reproduced
StarWind iscsi SAN Software: Using StarWind Tape Redirector and CA ARCserve Backup
 StarWind iscsi SAN Software: Using StarWind Tape Redirector and CA ARCserve Backup www.starwindsoftware.com Copyright 2008-2011. All rights reserved. COPYRIGHT Copyright 2008-2011. All rights reserved.
StarWind iscsi SAN Software: Using StarWind Tape Redirector and CA ARCserve Backup www.starwindsoftware.com Copyright 2008-2011. All rights reserved. COPYRIGHT Copyright 2008-2011. All rights reserved.
Connecting Devices to the PSD-BYOD Network
 Connecting Devices to the PSD-BYOD Network Students and staff can use the PSD-BYOD (Bring Your Own Device) network for internet access. Below are directions for connecting different types of devices. Selecting
Connecting Devices to the PSD-BYOD Network Students and staff can use the PSD-BYOD (Bring Your Own Device) network for internet access. Below are directions for connecting different types of devices. Selecting
LAB: Configuring LEAP. Learning Objectives
 LAB: Configuring LEAP Learning Objectives Configure Cisco ACS Radius server Configure a WLAN to use the 802.1X security protocol and LEAP Authenticate with an access point using 802.1X security and LEAP
LAB: Configuring LEAP Learning Objectives Configure Cisco ACS Radius server Configure a WLAN to use the 802.1X security protocol and LEAP Authenticate with an access point using 802.1X security and LEAP
eduroam for Windows Vista
 Please note: You must read the Wireless Network Fair Usage and Security Policy at the end of this guide. This ensures that you are aware of all the rules regarding Wireless services and prevent your internet
Please note: You must read the Wireless Network Fair Usage and Security Policy at the end of this guide. This ensures that you are aware of all the rules regarding Wireless services and prevent your internet
Configuring the Client Adapter through the Windows XP Operating System
 APPENDIX E Configuring the Client Adapter through the Windows XP Operating System This appendix explains how to configure and use the client adapter with Windows XP. The following topics are covered in
APPENDIX E Configuring the Client Adapter through the Windows XP Operating System This appendix explains how to configure and use the client adapter with Windows XP. The following topics are covered in
Configuring Microsoft Outlook to Connect to Hosted Exchange Service
 Configuring Microsoft Outlook to Connect to Hosted Exchange Service Configuring Microsoft Outlook for Hosted Exchange Service Version: 1.0 Updated on: April 27, 2011 Page 1 of 7 TABLE OF CONTENTS Configuring
Configuring Microsoft Outlook to Connect to Hosted Exchange Service Configuring Microsoft Outlook for Hosted Exchange Service Version: 1.0 Updated on: April 27, 2011 Page 1 of 7 TABLE OF CONTENTS Configuring
Nimsoft Monitor. exchange_response Guide. v2.5 series
 Nimsoft Monitor exchange_response Guide v2.5 series Legal Notices Copyright 2014, CA. All rights reserved. Warranty The material contained in this document is provided "as is," and is subject to being
Nimsoft Monitor exchange_response Guide v2.5 series Legal Notices Copyright 2014, CA. All rights reserved. Warranty The material contained in this document is provided "as is," and is subject to being
Blue Coat ProxySG First Steps Solution for Controlling HTTPS SGOS 6.7
 Blue Coat ProxySG First Steps Solution for Controlling HTTPS SGOS 6.7 Legal Notice Copyright 2018 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the
Blue Coat ProxySG First Steps Solution for Controlling HTTPS SGOS 6.7 Legal Notice Copyright 2018 Symantec Corp. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Blue Coat, and the
Made in U.S.A. 1
 Made in U.S.A. www.smartavi.com 1 1-800-AVI-2131 TABLE OF CONTENTS INTRODUCTION & FEATURES 2 Getting Started and Installation 3 Start-Up 4 Managing Streams and Environment 5 Frequently Asked Questions
Made in U.S.A. www.smartavi.com 1 1-800-AVI-2131 TABLE OF CONTENTS INTRODUCTION & FEATURES 2 Getting Started and Installation 3 Start-Up 4 Managing Streams and Environment 5 Frequently Asked Questions
12.0 Setting up the PC ready for BESA 11
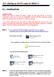 12.0 Setting up the PC ready for BESA 11 12.1 - Installing Driver. Important Note: Before you start to install the driver, please do not plug BESA 11 into the computer s USB port or else the installation
12.0 Setting up the PC ready for BESA 11 12.1 - Installing Driver. Important Note: Before you start to install the driver, please do not plug BESA 11 into the computer s USB port or else the installation
Scribe Monitor App. Version 1.0
 Scribe Monitor App Version 1.0 Important Notice No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, photocopying, recording, or otherwise,
Scribe Monitor App Version 1.0 Important Notice No part of this publication may be reproduced, stored in a retrieval system, or transmitted in any form or by any means, photocopying, recording, or otherwise,
KINGSTAR 3.2. SOFT PLC RUNTIME INSTALLATION AND USER GUIDE KS-DOC-x R3
 KINGSTAR 3.2 SOFT PLC RUNTIME INSTALLATION AND USER GUIDE KS-DOC-x64-0021-R3 Copyright 1996-2017 by All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
KINGSTAR 3.2 SOFT PLC RUNTIME INSTALLATION AND USER GUIDE KS-DOC-x64-0021-R3 Copyright 1996-2017 by All rights reserved. No part of this document may be reproduced or transmitted in any form or by any
Corporate Registry: Access Code Guide. Corporate Registry
 Corporate Registry: Access Code Guide Corporate Registry April 2017 Disclaimer Materials in this document are for demonstration purposes only. The characters and events depicted are fictional. Any similarity
Corporate Registry: Access Code Guide Corporate Registry April 2017 Disclaimer Materials in this document are for demonstration purposes only. The characters and events depicted are fictional. Any similarity
KnapSac Windows Server User's Guide
 KnapSac Windows Server User's Guide Table of Contents KnapSac Server for WIndows... 3 Introduction... 3 Windows Server... 3 License File... 5 License File System ID... 5 License File Options... 5 Server
KnapSac Windows Server User's Guide Table of Contents KnapSac Server for WIndows... 3 Introduction... 3 Windows Server... 3 License File... 5 License File System ID... 5 License File Options... 5 Server
Wireless Fusion Enterprise Mobility Suite. User Guide for Version 3.20
 Wireless Fusion Enterprise Mobility Suite User Guide for Version 3.20 Wireless Fusion Enterprise Mobility Suite User Guide for Version 3.20 72E-135868-01 Rev. A July 2010 ii Wireless Fusion Enterprise
Wireless Fusion Enterprise Mobility Suite User Guide for Version 3.20 Wireless Fusion Enterprise Mobility Suite User Guide for Version 3.20 72E-135868-01 Rev. A July 2010 ii Wireless Fusion Enterprise
NetApp Cloud Volumes Service for AWS
 NetApp Cloud Volumes Service for AWS AWS Account Setup Cloud Volumes Team, NetApp, Inc. March 29, 2019 Abstract This document provides instructions to set up the initial AWS environment for using the NetApp
NetApp Cloud Volumes Service for AWS AWS Account Setup Cloud Volumes Team, NetApp, Inc. March 29, 2019 Abstract This document provides instructions to set up the initial AWS environment for using the NetApp
Metalogix Essentials for Office Creating a Backup
 Metalogix Essentials for Office 365 2.1 2018 Quest Software Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished
Metalogix Essentials for Office 365 2.1 2018 Quest Software Inc. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished
FPS BYOD Wireless Network
 FPS BYOD Wireless Network This document will help users connect their personally owned wireless devices to Framingham Public Schools BYOD wireless network. Visitors: If you have a visitor with a personal
FPS BYOD Wireless Network This document will help users connect their personally owned wireless devices to Framingham Public Schools BYOD wireless network. Visitors: If you have a visitor with a personal
External Data Connector for SharePoint
 External Data Connector for SharePoint Last Updated: July 2017 Copyright 2014-2017 Vyapin Software Systems Private Limited. All rights reserved. This document is being furnished by Vyapin Software Systems
External Data Connector for SharePoint Last Updated: July 2017 Copyright 2014-2017 Vyapin Software Systems Private Limited. All rights reserved. This document is being furnished by Vyapin Software Systems
Upgrading to Sage ACT! 2013 from ACT! 3.x, 4.x, 5.x (2000), or 6.x (2004)
 Upgrading to Sage ACT! 2013 from ACT! 3.x, 4.x, 5.x (2000), or 6.x (2004) Copyright 2012 Sage Software, Inc. All Rights Reserved. Sage, the Sage logos, ACT!, and the Sage product and service names mentioned
Upgrading to Sage ACT! 2013 from ACT! 3.x, 4.x, 5.x (2000), or 6.x (2004) Copyright 2012 Sage Software, Inc. All Rights Reserved. Sage, the Sage logos, ACT!, and the Sage product and service names mentioned
Upgrade Guide. NovaBACKUP xsp NovaStor. All Rights Reserved.
 Upgrade Guide NovaBACKUP xsp 17 2015 NovaStor. All Rights Reserved. NovaBACKUP Upgrade Information... 3 Intended Audience... 3 Upgrade Paths... 3 License Keys... 3 NovaBACKUP xsp Modules... 3 Preparing
Upgrade Guide NovaBACKUP xsp 17 2015 NovaStor. All Rights Reserved. NovaBACKUP Upgrade Information... 3 Intended Audience... 3 Upgrade Paths... 3 License Keys... 3 NovaBACKUP xsp Modules... 3 Preparing
Zebra Link-OS Printer Profile Manager Enterprise
 Zebra Link-OS Printer Profile Manager Enterprise User Guide P1094865-001 Copyright 2017 ZIH Corp. and/or its affiliates. All rights reserved. ZEBRA and the stylized Zebra head are trademarks of ZIH Corp.,
Zebra Link-OS Printer Profile Manager Enterprise User Guide P1094865-001 Copyright 2017 ZIH Corp. and/or its affiliates. All rights reserved. ZEBRA and the stylized Zebra head are trademarks of ZIH Corp.,
Copyright NeoAccel Inc. SSL VPN-Plus TM. NeoAccel Management Console: Network Extension version 2.3
 Copyright 2005-2009. NeoAccel Inc. SSL VPN-Plus TM NeoAccel Management Console: Network Extension version 2.3 NeoAccel makes no warranty of any kind with regard to this manual, including, but not limited
Copyright 2005-2009. NeoAccel Inc. SSL VPN-Plus TM NeoAccel Management Console: Network Extension version 2.3 NeoAccel makes no warranty of any kind with regard to this manual, including, but not limited
Wireless Data Privacy Configuration Guide. HP ProCurve Secure Access 700wl Series.
 Wireless Data Privacy Configuration Guide HP ProCurve Secure Access 700wl Series www.hp.com/go/hpprocurve HP PROCURVE SECURE ACCESS 700WL SERIES WIRELESS DATA PRIVACY CONFIGURATION GUIDE Copyright 2003
Wireless Data Privacy Configuration Guide HP ProCurve Secure Access 700wl Series www.hp.com/go/hpprocurve HP PROCURVE SECURE ACCESS 700WL SERIES WIRELESS DATA PRIVACY CONFIGURATION GUIDE Copyright 2003
Outlook Web Access. Implementation Guide. (Version 5.4) Copyright 2012 Deepnet Security Limited
 Implementation Guide (Version 5.4) Copyright 2012 Deepnet Security Limited Copyright 2012, Deepnet Security. All Rights Reserved. Page 1 Trademarks Deepnet Unified Authentication, MobileID, QuickID, PocketID,
Implementation Guide (Version 5.4) Copyright 2012 Deepnet Security Limited Copyright 2012, Deepnet Security. All Rights Reserved. Page 1 Trademarks Deepnet Unified Authentication, MobileID, QuickID, PocketID,
One Identity Starling Two-Factor Desktop Login 1.0. Administration Guide
 One Identity Starling Two-Factor Desktop Login 1.0 Administration Guide Copyright 2018 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software
One Identity Starling Two-Factor Desktop Login 1.0 Administration Guide Copyright 2018 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software
One Identity Safeguard for Privileged Sessions 5.9. Remote Desktop Protocol Scenarios
 One Identity Safeguard for Privileged Sessions 5.9 Remote Desktop Protocol Scenarios Copyright 2018 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright.
One Identity Safeguard for Privileged Sessions 5.9 Remote Desktop Protocol Scenarios Copyright 2018 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright.
Nimsoft Service Desk. Single Sign-On Configuration Guide. [assign the version number for your book]
![Nimsoft Service Desk. Single Sign-On Configuration Guide. [assign the version number for your book] Nimsoft Service Desk. Single Sign-On Configuration Guide. [assign the version number for your book]](/thumbs/80/81218109.jpg) Nimsoft Service Desk Single Sign-On Configuration Guide [assign the version number for your book] Legal Notices Copyright 2012, CA. All rights reserved. Warranty The material contained in this document
Nimsoft Service Desk Single Sign-On Configuration Guide [assign the version number for your book] Legal Notices Copyright 2012, CA. All rights reserved. Warranty The material contained in this document
Agilent Genomic Workbench 6.0
 Agilent Genomic Workbench 6.0 Standard Edition Installation Guide Notices Agilent Technologies, Inc. 2010 No part of this manual may be reproduced in any form or by any means (including electronic storage
Agilent Genomic Workbench 6.0 Standard Edition Installation Guide Notices Agilent Technologies, Inc. 2010 No part of this manual may be reproduced in any form or by any means (including electronic storage
INFORMATION SYSTEMS SERVICE NETWORKS AND TELECOMMUNICATIONS SECTOR
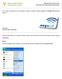 INFORMATION SYSTEMS SERVICE NETWORKS AND TELECOMMUNICATIONS SECTOR User Guide: Connecting to the University of Cyprus wireless network ucywifi for Windows XP operating systems ΥΠΣ ΕΔ/55 Last review date:
INFORMATION SYSTEMS SERVICE NETWORKS AND TELECOMMUNICATIONS SECTOR User Guide: Connecting to the University of Cyprus wireless network ucywifi for Windows XP operating systems ΥΠΣ ΕΔ/55 Last review date:
