Writing drivers for the Linux Crypto subsystem
|
|
|
- Gabriel Watkins
- 6 years ago
- Views:
Transcription
1 May 18, 2014
2 Marek Vasut Software engineer at DENX S.E. since 2011 Embedded and Real-Time Systems Services, Linux kernel and driver development, U-Boot development, consulting, training. Versatile Linux kernel hacker Custodian at U-Boot bootloader
3 The kernel Crypto API? Generic in-kernel transformation API Can do Cipher, Hash, Compress, RNG,... Used by: Network stack: IPsec,... Device Mapper: dm-crypt, RAID,... AF ALG and thus possibly userland Therefore, you want your drivers to be well written.
4 Today s plan Go through part of drivers/crypto/geode-aes.c Inspect how a basic transformation driver is written Point out mistakes that are easy to make in a new driver
5 Registering a transformation Lifespan of a Crypto API driver: Driver is probed Driver registers it s algs Transformations happen Driver unregisters it s algs Driver is removed
6 Example registration static int geode_aes_probe(struct pci_dev *dev, const struct pci_device_id *id) {... ret = crypto_register_alg(&geode_alg); if (ret) goto eiomap;... return 0;... eiomap: dev_err(&dev->dev, "GEODE AES initialization failed.\n"); return ret; }
7 Registration: important bits Crypto API does not track device instances Careful when probing multiple devices of the same type The probe() function doesn t need locking Static private data pointer for instances crypto register alg(struct crypto alg *alg) crypto register algs(struct crypto algs *algs, int count) crypto unregister alg(struct crypto alg *alg) crypto unregister algs(struct crypto algs *algs, int count)
8 The struct crypto alg Block cipher descriptor (telephone list): static struct crypto_alg geode_alg = {.cra_name = "aes",.cra_driver_name = "geode-aes",.cra_priority = 300,.cra_module = THIS_MODULE,.cra_blocksize = AES_BLOCK_SIZE,.cra_alignmask = 15,.cra_ctxsize.cra_init.cra_exit ---->8---- = sizeof(struct geode_aes_op), = fallback_init_cip, = fallback_exit_cip,
9 The struct crypto alg };.cra_flags = CRYPTO_ALG_TYPE_CIPHER CRYPTO_ALG_NEED_FALLBACK,.cra_u = {.cipher = {.cia_min_keysize = AES_MIN_KEY_SIZE,.cia_max_keysize = AES_MAX_KEY_SIZE,.cia_setkey = geode_setkey_cip,.cia_encrypt = geode_encrypt,.cia_decrypt = geode_decrypt } }
10 High-level view Lifespan of a Crypto API driver: Driver is probed Driver registers it s algs Transformations happen Driver unregisters it s algs Driver is removed
11 User vs. struct crypto alg WARNING: interleaved code, put your 4D glasses on: static struct crypto alg geode alg = {.cra ctxsize = sizeof(struct geode aes op), struct crypto cipher *tfm = crypto alloc cipher(alg, type, mask);.cra init = fallback init cip,.cra u.cipher = { crypto cipher setkey(tfm, key, keylen);.cia setkey = geode setkey cip, crypto cipher encrypt one(tfm, out, in);.cia encrypt = geode encrypt, } crypto free cipher(tfm);.cra exit = fallback exit cip, };
12 The transformation object Representation of transformation instance Usually encapsulated in bigger structures Contains pointers to transformation functions Contains private data for the transformation Can be accessed concurrently!
13 Setting the key static int geode_setkey_cip(struct crypto_tfm *tfm, const u8 *key, unsigned int len) { struct geode_aes_op *op = crypto_tfm_ctx(tfm); unsigned int ret; op->keylen = len; if (len == AES_KEYSIZE_128) { memcpy(op->key, key, len); return 0; } if (len!= AES_KEYSIZE_192 && len!= AES_KEYSIZE_256) { /* not supported at all */ tfm->crt_flags = CRYPTO_TFM_RES_BAD_KEY_LEN; return -EINVAL; } ---->8----
14 Setting the key recap Get TFM private data crypto tfm ctx(tfm) The key is copied into the private data Check the validity of the key size All key sizes must be handled
15 Let s encrypt a block Buffer size is always.cra blocksize in this case. static void geode_encrypt(struct crypto_tfm *tfm, u8 *out, const u8 *in) { struct geode_aes_op *op = crypto_tfm_ctx(tfm); } if (unlikely(op->keylen!= AES_KEYSIZE_128)) { crypto_cipher_encrypt_one(op->fallback.cip, out, in); return; } ---8<--->8--- actual_aes_crypt(tfm, out, in);
16 Hardware limitations Hardware can have limitations/bugs Crypto API can still use such hardware The.cra init provides means to put workaround in place: static int fallback_init_cip(struct crypto_tfm *tfm) { const char *name = crypto_tfm_alg_name(tfm); struct geode_aes_op *op = crypto_tfm_ctx(tfm); op->fallback.cip = crypto_alloc_cipher(name, 0, CRYPTO_ALG_ASYNC CRYPTO_ALG_NEED_FALLBACK); } if (IS_ERR(op->fallback.cip)) { printk(kern_err "Error allocating fallback algo %s\n", name); return PTR_ERR(op->fallback.cip); } return 0;
17 Hardware limitations static int geode_setkey_cip(struct crypto_tfm *tfm, const u8 *key, unsigned int len) ---->8---- /* The requested key size is not supported by HW, do a fallback */ op->fallback.cip->base.crt_flags &= ~CRYPTO_TFM_REQ_MASK; op->fallback.cip->base.crt_flags = (tfm->crt_flags & CRYPTO_TFM_REQ_MASK); } ret = crypto_cipher_setkey(op->fallback.cip, key, len); if (ret) { tfm->crt_flags &= ~CRYPTO_TFM_RES_MASK; tfm->crt_flags = (op->fallback.cip->base.crt_flags & CRYPTO_TFM_RES_MASK); } return ret; static void geode_encrypt(struct crypto_tfm *tfm, u8 *out, const u8 *in) { struct geode_aes_op *op = crypto_tfm_ctx(tfm); if (unlikely(op->keylen!= AES_KEYSIZE_128)) { crypto_cipher_encrypt_one(op->fallback.cip, out, in); return; }...
18 Alignment pitfalls In simple case of cipher, Crypto API realigns buffers Realigning adds overhead Use crypto * alignmask() to learn of the needs static struct crypto_alg geode_alg = {....cra_alignmask = 15,... };
19 Recap We made it through simple block cipher! static struct crypto_alg geode_alg = {.cra_name = "aes",.cra_driver_name = "geode-aes",.cra_priority = 300,.cra_module = THIS_MODULE,.cra_blocksize = AES_BLOCK_SIZE,.cra_alignmask = 15,.cra_ctxsize = sizeof(struct geode_aes_op),.cra_init = fallback_init_cip,.cra_exit = fallback_exit_cip,.cra_u.cipher = {},
20 Testing the new driver TCrypt test framework in kernel Device Mapper torture IPsec torture Userland bombing from OpenSSL
21 TCrypt Available in Linux kernel (crypto/tcrypt.c) The does it even work testsuite. Enable with CONFIG CRYPTO TEST If possible, leave enable + Easily available + Basic algo validity test Does not do stress testing
22 Device Mapper torture Available in Linux kernel (drivers/md/) Use dm-crypt for block cipher testing (aes-cbc) Use dm-crypt for hash testing (md5, crc32) Use dm-raid5 for XOR offload testing Enable with CONFIG DM CRYPT Many examples how to use cryptsetup, but look at: --hash, --cipher, --key-size + Easily available + Use for stress testing + Use to simulate real workload Produces small payloads of data
23 IPsec torture Available in Linux kernel (net/) Look for AH, ESP v4/v6 support Nice for testing hashing and AEAD Enable with CONFIG INET(6) (AH,ESP) Try setting up an IPsec tunnel and inspect a crash :-) + Easily available + Use for stress testing + Use to simulate real workload
24 What else can we do? Asynchronous tfm on large data Synchronous tfm on large data Async/Sync hashing on large data AEAD (MAC) on data Generate random numbers Compress/decompress
25 Advanced topics Here are a few keywords on the advanced side of Crypto API: Asynchronous tfm on large data Generic ScatterWalk Scatterlist alignment Callback handling Backlog queue handling Crypto request queues Async/Sync hashing on large data Harboring obscure hashing engines
26 The End Thank you for your attention! Contact: Marek Vasut Crypto ML:
Confessions of a security hardware driver maintainer
 Confessions of a security hardware driver maintainer Gilad Ben-Yossef Principal Software Engineer About me My name is Gilad Ben-Yossef. I work on upstream Linux kernel cryptography and security in genera,l
Confessions of a security hardware driver maintainer Gilad Ben-Yossef Principal Software Engineer About me My name is Gilad Ben-Yossef. I work on upstream Linux kernel cryptography and security in genera,l
Linux Kernel Cryptographic API for fun and profit
 Linux Kernel Cryptographic API for fun and profit Gilad Ben-Yossef Gilad Ben-Yossef gilad.benyossef@arm.com Twitter: @giladby About me My name is Gilad Ben-Yossef. I work on upstream Linux kernel cryptography
Linux Kernel Cryptographic API for fun and profit Gilad Ben-Yossef Gilad Ben-Yossef gilad.benyossef@arm.com Twitter: @giladby About me My name is Gilad Ben-Yossef. I work on upstream Linux kernel cryptography
POWER7+ Accelerated Encryption and Random Number Generation for Linux
 POWER7+ Accelerated Encryption and Random Number Generation for Linux Kent Yoder IBM Linux Technology Center February 22, 2013 Contents 1 Introduction 2 2 Hardware Architecture
POWER7+ Accelerated Encryption and Random Number Generation for Linux Kent Yoder IBM Linux Technology Center February 22, 2013 Contents 1 Introduction 2 2 Hardware Architecture
Using To talk with. Remote Cores. Ohad Ben-Cohen
 Virtio Using To talk with Remote Cores Ohad Ben-Cohen What? Why?? 1. simple (but allow both kernel and userland to talk with remote services) 2. performance 3. generic
Virtio Using To talk with Remote Cores Ohad Ben-Cohen What? Why?? 1. simple (but allow both kernel and userland to talk with remote services) 2. performance 3. generic
U-Boot bootloader port done right 2017 edition
 U-Boot bootloader port done right 2017 edition Marek Vašut December 1st, 2017 Marek Vasut Software engineer Versatile Linux kernel hacker Custodian at U-Boot bootloader OE-core
U-Boot bootloader port done right 2017 edition Marek Vašut December 1st, 2017 Marek Vasut Software engineer Versatile Linux kernel hacker Custodian at U-Boot bootloader OE-core
Anand Raghunathan
 ECE 695R: SYSTEM-ON-CHIP DESIGN Module 2: HW/SW Partitioning Lecture 2.26: Example: Hardware Architecture Anand Raghunathan raghunathan@purdue.edu ECE 695R: System-on-Chip Design, Fall 2014 Fall 2014,
ECE 695R: SYSTEM-ON-CHIP DESIGN Module 2: HW/SW Partitioning Lecture 2.26: Example: Hardware Architecture Anand Raghunathan raghunathan@purdue.edu ECE 695R: System-on-Chip Design, Fall 2014 Fall 2014,
Chapter 18: wolfcrypt API Reference
 Chapter 18: wolfcrypt API Reference Table of Contents March, 2016 Version 3.9.0 18.1 AES 18.2 Arc4 18.3 ASN 18.4 Blake2 18.5 Camellia 18.6 ChaCha 18.7 ChaCha20 with Poly1305 18.8 Coding 18.9 Compression
Chapter 18: wolfcrypt API Reference Table of Contents March, 2016 Version 3.9.0 18.1 AES 18.2 Arc4 18.3 ASN 18.4 Blake2 18.5 Camellia 18.6 ChaCha 18.7 ChaCha20 with Poly1305 18.8 Coding 18.9 Compression
rte_security: An update and introducing PDCP
 rte_security: An update and introducing PDCP Akhil Goyal (NXP) Hemant Agrawal (NXP) DPDK Summit Dublin- 2018 Agenda Rte_security A brief recap PDCP - Introduction Rte_security Updates for PDCP Protocol
rte_security: An update and introducing PDCP Akhil Goyal (NXP) Hemant Agrawal (NXP) DPDK Summit Dublin- 2018 Agenda Rte_security A brief recap PDCP - Introduction Rte_security Updates for PDCP Protocol
IPSec Transform Set Configuration Mode Commands
 IPSec Transform Set Configuration Mode Commands The IPSec Transform Set Configuration Mode is used to configure IPSec security parameters. There are two core protocols, the Authentication Header (AH) and
IPSec Transform Set Configuration Mode Commands The IPSec Transform Set Configuration Mode is used to configure IPSec security parameters. There are two core protocols, the Authentication Header (AH) and
Linux 2.6 CryptoAPI IPSec & FileSystems
 Linux 2.6 CryptoAPI IPSec & FileSystems Matthew G. Marsh President, Paktronix Systems LLC Chief Scientist, NEbraskaCERT Slide 1 Overview Linux 2.6 Kernel CryptoAPI What is it Why is it Who cares File System
Linux 2.6 CryptoAPI IPSec & FileSystems Matthew G. Marsh President, Paktronix Systems LLC Chief Scientist, NEbraskaCERT Slide 1 Overview Linux 2.6 Kernel CryptoAPI What is it Why is it Who cares File System
CSC369 Lecture 2. Larry Zhang
 CSC369 Lecture 2 Larry Zhang 1 Announcements Lecture slides Midterm timing issue Assignment 1 will be out soon! Start early, and ask questions. We will have bonus for groups that finish early. 2 Assignment
CSC369 Lecture 2 Larry Zhang 1 Announcements Lecture slides Midterm timing issue Assignment 1 will be out soon! Start early, and ask questions. We will have bonus for groups that finish early. 2 Assignment
Storage encryption... what about data integrity?
 Centre for Research on Cryptography and Security Storage encryption... what about data integrity? Milan Brož mbroz@redhat.com DevConf, Brno January 28, 2017 Agenda Data integrity what it is? Encryption
Centre for Research on Cryptography and Security Storage encryption... what about data integrity? Milan Brož mbroz@redhat.com DevConf, Brno January 28, 2017 Agenda Data integrity what it is? Encryption
CSC369 Lecture 2. Larry Zhang, September 21, 2015
 CSC369 Lecture 2 Larry Zhang, September 21, 2015 1 Volunteer note-taker needed by accessibility service see announcement on Piazza for details 2 Change to office hour to resolve conflict with CSC373 lecture
CSC369 Lecture 2 Larry Zhang, September 21, 2015 1 Volunteer note-taker needed by accessibility service see announcement on Piazza for details 2 Change to office hour to resolve conflict with CSC373 lecture
IPSec Transform Set Configuration Mode Commands
 IPSec Transform Set Configuration Mode Commands The IPSec Transform Set Configuration Mode is used to configure IPSec security parameters. There are two core protocols, the Authentication Header (AH) and
IPSec Transform Set Configuration Mode Commands The IPSec Transform Set Configuration Mode is used to configure IPSec security parameters. There are two core protocols, the Authentication Header (AH) and
Android Bootloader and Verified Boot
 Android Bootloader and Verified Boot Lecture 7 Security of Mobile Devices 2018 SMD Android Bootloader and Verified Boot, Lecture 7 1/38 Bootloader Recovery Verified Boot Bibliography SMD Android Bootloader
Android Bootloader and Verified Boot Lecture 7 Security of Mobile Devices 2018 SMD Android Bootloader and Verified Boot, Lecture 7 1/38 Bootloader Recovery Verified Boot Bibliography SMD Android Bootloader
Comparing TCP performance of tunneled and non-tunneled traffic using OpenVPN. Berry Hoekstra Damir Musulin OS3 Supervisor: Jan Just Keijser Nikhef
 Comparing TCP performance of tunneled and non-tunneled traffic using OpenVPN Berry Hoekstra Damir Musulin OS3 Supervisor: Jan Just Keijser Nikhef Outline Introduction Approach Research Results Conclusion
Comparing TCP performance of tunneled and non-tunneled traffic using OpenVPN Berry Hoekstra Damir Musulin OS3 Supervisor: Jan Just Keijser Nikhef Outline Introduction Approach Research Results Conclusion
VIA PadLock SDK API & Programming Guide
 VIA PadLock SDK API & Programming Guide VIA Technologies, INC. 9/1/2004 Trademarks Windows 98/Me/2000/XP are trademarks or registered trademarks of Microsoft Corporation. All other brands, product names,
VIA PadLock SDK API & Programming Guide VIA Technologies, INC. 9/1/2004 Trademarks Windows 98/Me/2000/XP are trademarks or registered trademarks of Microsoft Corporation. All other brands, product names,
Using kgdb and the kgdb Internals
 Using kgdb and the kgdb Internals Jason Wessel jason.wessel@windriver.com Tom Rini trini@kernel.crashing.org Amit S. Kale amitkale@linsyssoft.com Using kgdb and the kgdb Internals by Jason Wessel by Tom
Using kgdb and the kgdb Internals Jason Wessel jason.wessel@windriver.com Tom Rini trini@kernel.crashing.org Amit S. Kale amitkale@linsyssoft.com Using kgdb and the kgdb Internals by Jason Wessel by Tom
CSCE 715: Network Systems Security
 CSCE 715: Network Systems Security Chin-Tser Huang huangct@cse.sc.edu University of South Carolina Security in Network Layer Implementing security in application layer provides flexibility in security
CSCE 715: Network Systems Security Chin-Tser Huang huangct@cse.sc.edu University of South Carolina Security in Network Layer Implementing security in application layer provides flexibility in security
Asynchronous Events on Linux
 Asynchronous Events on Linux Frederic.Rossi@Ericsson.CA Open System Lab Systems Research June 25, 2002 Ericsson Research Canada Introduction Linux performs well as a general purpose OS but doesn t satisfy
Asynchronous Events on Linux Frederic.Rossi@Ericsson.CA Open System Lab Systems Research June 25, 2002 Ericsson Research Canada Introduction Linux performs well as a general purpose OS but doesn t satisfy
Coccinelle: Practical Program Transformation for the Linux Kernel. Julia Lawall (Inria/LIP6) June 25, 2018
 Coccinelle: Practical Program Transformation for the Linux Kernel Julia Lawall (Inria/LIP6) June 25, 2018 1 Motivation Large, critical infrastructure-software code bases Linux kernel, OpenSSL, Qemu, Firefox,
Coccinelle: Practical Program Transformation for the Linux Kernel Julia Lawall (Inria/LIP6) June 25, 2018 1 Motivation Large, critical infrastructure-software code bases Linux kernel, OpenSSL, Qemu, Firefox,
Virtual Private Networks (VPN)
 CYBR 230 Jeff Shafer University of the Pacific Virtual Private Networks (VPN) 2 Schedule This Week Mon September 4 Labor Day No class! Wed September 6 VPN Project 1 Work Fri September 8 IPv6? Project 1
CYBR 230 Jeff Shafer University of the Pacific Virtual Private Networks (VPN) 2 Schedule This Week Mon September 4 Labor Day No class! Wed September 6 VPN Project 1 Work Fri September 8 IPv6? Project 1
What is concurrency? Concurrency. What is parallelism? concurrency vs parallelism. Concurrency: (the illusion of) happening at the same time.
 What is concurrency? Concurrency Johan Montelius KTH 2017 Concurrency: (the illusion of) happening at the same time. A property of the programing model. Why would we want to do things concurrently? What
What is concurrency? Concurrency Johan Montelius KTH 2017 Concurrency: (the illusion of) happening at the same time. A property of the programing model. Why would we want to do things concurrently? What
Concurrency. Johan Montelius KTH
 Concurrency Johan Montelius KTH 2017 1 / 32 What is concurrency? 2 / 32 What is concurrency? Concurrency: (the illusion of) happening at the same time. 2 / 32 What is concurrency? Concurrency: (the illusion
Concurrency Johan Montelius KTH 2017 1 / 32 What is concurrency? 2 / 32 What is concurrency? Concurrency: (the illusion of) happening at the same time. 2 / 32 What is concurrency? Concurrency: (the illusion
ISA-L Performance Report Release Test Date: Sept 29 th 2017
 Test Date: Sept 29 th 2017 Revision History Date Revision Comment Sept 29 th, 2017 1.0 Initial document for release 2 Contents Audience and Purpose... 4 Test setup:... 4 Intel Xeon Platinum 8180 Processor
Test Date: Sept 29 th 2017 Revision History Date Revision Comment Sept 29 th, 2017 1.0 Initial document for release 2 Contents Audience and Purpose... 4 Test setup:... 4 Intel Xeon Platinum 8180 Processor
Internet Security. - IPSec, SSL/TLS, SRTP - 29th. Oct Lee, Choongho
 Internet Security - IPSec, SSL/TLS, SRTP - 29th. Oct. 2007 Lee, Choongho chlee@mmlab.snu.ac.kr Contents Introduction IPSec SSL / TLS SRTP Conclusion 2/27 Introduction (1/2) Security Goals Confidentiality
Internet Security - IPSec, SSL/TLS, SRTP - 29th. Oct. 2007 Lee, Choongho chlee@mmlab.snu.ac.kr Contents Introduction IPSec SSL / TLS SRTP Conclusion 2/27 Introduction (1/2) Security Goals Confidentiality
Cryptography and Network Security Chapter 16. Fourth Edition by William Stallings
 Cryptography and Network Security Chapter 16 Fourth Edition by William Stallings Chapter 16 IP Security If a secret piece of news is divulged by a spy before the time is ripe, he must be put to death,
Cryptography and Network Security Chapter 16 Fourth Edition by William Stallings Chapter 16 IP Security If a secret piece of news is divulged by a spy before the time is ripe, he must be put to death,
pthreads CS449 Fall 2017
 pthreads CS449 Fall 2017 POSIX Portable Operating System Interface Standard interface between OS and program UNIX-derived OSes mostly follow POSIX Linux, macos, Android, etc. Windows requires separate
pthreads CS449 Fall 2017 POSIX Portable Operating System Interface Standard interface between OS and program UNIX-derived OSes mostly follow POSIX Linux, macos, Android, etc. Windows requires separate
ADVANCED OPERATING SYSTEMS
 ADVANCED OPERATING SYSTEMS UNIT 2 FILE AND DIRECTORY I/O BY MR.PRASAD SAWANT Prof.Prasad Sawant,Assitiant Professor,Dept. Of CS PCCCS Chichwad Prof.Prasad Sawant,Assitiant Professor,Dept. Of CS PCCCS Chichwad
ADVANCED OPERATING SYSTEMS UNIT 2 FILE AND DIRECTORY I/O BY MR.PRASAD SAWANT Prof.Prasad Sawant,Assitiant Professor,Dept. Of CS PCCCS Chichwad Prof.Prasad Sawant,Assitiant Professor,Dept. Of CS PCCCS Chichwad
Software Security: Miscellaneous
 CSE 484 / CSE M 584: Computer Security and Privacy Software Security: Miscellaneous Fall 2016 Adam (Ada) Lerner lerner@cs.washington.edu Thanks to Franzi Roesner, Dan Boneh, Dieter Gollmann, Dan Halperin,
CSE 484 / CSE M 584: Computer Security and Privacy Software Security: Miscellaneous Fall 2016 Adam (Ada) Lerner lerner@cs.washington.edu Thanks to Franzi Roesner, Dan Boneh, Dieter Gollmann, Dan Halperin,
CTaoCrypt Usage Reference
 http://www.yassl.com mailto:info@yassl.com phone: +1 206 369 4800 CTaoCrypt Usage Reference CTaoCrypt is the cryptography library primarily used by CyaSSL. It is optimized for speed, small footprint, and
http://www.yassl.com mailto:info@yassl.com phone: +1 206 369 4800 CTaoCrypt Usage Reference CTaoCrypt is the cryptography library primarily used by CyaSSL. It is optimized for speed, small footprint, and
- Knowledge of basic computer architecture and organization, ECE 445
 ECE 446: Device Driver Development Fall 2014 Wednesdays 7:20-10 PM Office hours: Wednesdays 6:15-7:15 PM or by appointment, Adjunct office Engineering Building room 3707/3708 Last updated: 8/24/14 Instructor:
ECE 446: Device Driver Development Fall 2014 Wednesdays 7:20-10 PM Office hours: Wednesdays 6:15-7:15 PM or by appointment, Adjunct office Engineering Building room 3707/3708 Last updated: 8/24/14 Instructor:
CS333 Intro to Operating Systems. Jonathan Walpole
 CS333 Intro to Operating Systems Jonathan Walpole Threads & Concurrency 2 Threads Processes have the following components: - an address space - a collection of operating system state - a CPU context or
CS333 Intro to Operating Systems Jonathan Walpole Threads & Concurrency 2 Threads Processes have the following components: - an address space - a collection of operating system state - a CPU context or
Parallelizing IPsec: switching SMP to On is not even half the way
 Parallelizing IPsec: switching SMP to On is not even half the way Steffen Klassert secunet Security Networks AG Dresden June 11 2010 Table of contents Some basics about IPsec About the IPsec performance
Parallelizing IPsec: switching SMP to On is not even half the way Steffen Klassert secunet Security Networks AG Dresden June 11 2010 Table of contents Some basics about IPsec About the IPsec performance
The Case For Crypto Protocol Awareness Inside The OS Kernel
 The Case For Crypto Protocol Awareness Inside The OS Kernel Matthew Burnside Angelos D. Keromytis Department of Computer Science, Columbia University {mb,angelos}@cs.columbia.edu Abstract Separation of
The Case For Crypto Protocol Awareness Inside The OS Kernel Matthew Burnside Angelos D. Keromytis Department of Computer Science, Columbia University {mb,angelos}@cs.columbia.edu Abstract Separation of
Asymmetric Cryptography. kprv. kpub. used in digital signature
 Digital Signature logical representation: Asymmetric Cryptography plaintext plaintext kpub E kpub () kprv E kprv () ciphertext ciphertext kprv E -1 kprv () kpub E -1 kpub () used in digital envelope plaintext
Digital Signature logical representation: Asymmetric Cryptography plaintext plaintext kpub E kpub () kprv E kprv () ciphertext ciphertext kprv E -1 kprv () kpub E -1 kpub () used in digital envelope plaintext
The Case For Crypto Protocol Awareness Inside The OS Kernel
 The Case For Crypto Protocol Awareness Inside The OS Kernel Matthew Burnside Angelos D. Keromytis Department of Computer Science, Columbia University mb,angelos @cs.columbia.edu Abstract Separation of
The Case For Crypto Protocol Awareness Inside The OS Kernel Matthew Burnside Angelos D. Keromytis Department of Computer Science, Columbia University mb,angelos @cs.columbia.edu Abstract Separation of
IPSec. Slides by Vitaly Shmatikov UT Austin. slide 1
 IPSec Slides by Vitaly Shmatikov UT Austin slide 1 TCP/IP Example slide 2 IP Security Issues Eavesdropping Modification of packets in transit Identity spoofing (forged source IP addresses) Denial of service
IPSec Slides by Vitaly Shmatikov UT Austin slide 1 TCP/IP Example slide 2 IP Security Issues Eavesdropping Modification of packets in transit Identity spoofing (forged source IP addresses) Denial of service
Quiz I Solutions MASSACHUSETTS INSTITUTE OF TECHNOLOGY Fall Department of Electrical Engineering and Computer Science
 Department of Electrical Engineering and Computer Science MASSACHUSETTS INSTITUTE OF TECHNOLOGY 6.828 Fall 2012 Quiz I Solutions Mean 65 Median 66 Std. dev 17.5214 14 12 10 8 6 4 2 0 0 10 20 30 40 50 60
Department of Electrical Engineering and Computer Science MASSACHUSETTS INSTITUTE OF TECHNOLOGY 6.828 Fall 2012 Quiz I Solutions Mean 65 Median 66 Std. dev 17.5214 14 12 10 8 6 4 2 0 0 10 20 30 40 50 60
Last class: Today: Thread Background. Thread Systems
 1 Last class: Thread Background Today: Thread Systems 2 Threading Systems 3 What kind of problems would you solve with threads? Imagine you are building a web server You could allocate a pool of threads,
1 Last class: Thread Background Today: Thread Systems 2 Threading Systems 3 What kind of problems would you solve with threads? Imagine you are building a web server You could allocate a pool of threads,
How to abstract hardware acceleration device in cloud environment. Maciej Grochowski Intel DCG Ireland
 How to abstract hardware acceleration device in cloud environment Maciej Grochowski Intel DCG Ireland Outline Introduction to Hardware Accelerators Intel QuickAssist Technology (Intel QAT) as example of
How to abstract hardware acceleration device in cloud environment Maciej Grochowski Intel DCG Ireland Outline Introduction to Hardware Accelerators Intel QuickAssist Technology (Intel QAT) as example of
The Linux Kernel Cryptographic API
 Published on Linux Journal (http://www.linuxjournal.com) The Linux Kernel Cryptographic API By James Morris Created 2003-04-01 02:00 This article provides a brief overview of the new cryptographic API
Published on Linux Journal (http://www.linuxjournal.com) The Linux Kernel Cryptographic API By James Morris Created 2003-04-01 02:00 This article provides a brief overview of the new cryptographic API
Kernel Scalability. Adam Belay
 Kernel Scalability Adam Belay Motivation Modern CPUs are predominantly multicore Applications rely heavily on kernel for networking, filesystem, etc. If kernel can t scale across many
Kernel Scalability Adam Belay Motivation Modern CPUs are predominantly multicore Applications rely heavily on kernel for networking, filesystem, etc. If kernel can t scale across many
Intro to Threads. Two approaches to concurrency. Threaded multifinger: - Asynchronous I/O (lab) - Threads (today s lecture)
 Intro to Threads Two approaches to concurrency - Asynchronous I/O (lab) - Threads (today s lecture) Threaded multifinger: - Run many copies of finger simultaneously for (int i = 1; i < argc; i++) thread_create
Intro to Threads Two approaches to concurrency - Asynchronous I/O (lab) - Threads (today s lecture) Threaded multifinger: - Run many copies of finger simultaneously for (int i = 1; i < argc; i++) thread_create
Lecture 13 Page 1. Lecture 13 Page 3
 IPsec Network Security: IPsec CS 239 Computer Software March 2, 2005 Until recently, the IP protocol had no standards for how to apply security Encryption and authentication layered on top Or provided
IPsec Network Security: IPsec CS 239 Computer Software March 2, 2005 Until recently, the IP protocol had no standards for how to apply security Encryption and authentication layered on top Or provided
Introduction PCI Interface Booting PCI driver registration Other buses. Linux Device Drivers PCI Drivers
 Overview 1 2 PCI addressing 3 4 5 bus, The most common is the PCI (in the PC world), PCI - Peripheral Component Interconnect, bus consists of two components: electrical interface programming interface,
Overview 1 2 PCI addressing 3 4 5 bus, The most common is the PCI (in the PC world), PCI - Peripheral Component Interconnect, bus consists of two components: electrical interface programming interface,
Wireless Base Band Device (bbdev) Amr Mokhtar DPDK Summit Userspace - Dublin- 2017
 Wireless Base Band Device (bbdev) Amr Mokhtar DPDK Summit Userspace - Dublin- 2017 why baseband..? MAC Tx Data Downlink * Reference: 3GPP TS 36.211 & 36.212 architecture Common programing framework for
Wireless Base Band Device (bbdev) Amr Mokhtar DPDK Summit Userspace - Dublin- 2017 why baseband..? MAC Tx Data Downlink * Reference: 3GPP TS 36.211 & 36.212 architecture Common programing framework for
lib/librte_ipsec A NATIVE DPDK IPSEC LIBRARY UPDATE 2018/12 DECLAN DOHERTY, MOHAMMAD ABDUL AWAL, KONSTANTIN ANANYEV
 x lib/librte_ipsec A NATIVE DPDK IPSEC LIBRARY UPDATE 2018/12 DECLAN DOHERTY, MOHAMMAD ABDUL AWAL, KONSTANTIN ANANYEV /intro Create a DPDK native high performance library for IPsec processing. Develop
x lib/librte_ipsec A NATIVE DPDK IPSEC LIBRARY UPDATE 2018/12 DECLAN DOHERTY, MOHAMMAD ABDUL AWAL, KONSTANTIN ANANYEV /intro Create a DPDK native high performance library for IPsec processing. Develop
U-Boot bootloader port done right 2018 edition
 U-Boot bootloader port done right 2018 edition Marek Vašut February 4th, 2018 Marek Vasut Software engineer Versatile Linux kernel hacker Custodian at U-Boot bootloader OE-core
U-Boot bootloader port done right 2018 edition Marek Vašut February 4th, 2018 Marek Vasut Software engineer Versatile Linux kernel hacker Custodian at U-Boot bootloader OE-core
Linux SMR Support Status
 Linux SMR Support Status Damien Le Moal Vault Linux Storage and Filesystems Conference - 2017 March 23rd, 2017 Outline Standards and Kernel Support Status Kernel Details - What was needed Block stack File
Linux SMR Support Status Damien Le Moal Vault Linux Storage and Filesystems Conference - 2017 March 23rd, 2017 Outline Standards and Kernel Support Status Kernel Details - What was needed Block stack File
Recap: Pointers. int* int& *p &i &*&* ** * * * * IFMP 18, M. Schwerhoff
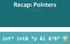 Recap: Pointers IFMP 18, M. Schwerhoff int* int& *p &i &*&* ** * * * * A 0 A 1 A 2 A 3 A 4 A 5 A 0 A 1 A 2 A 3 A 4 A 5 5 i int* p; A 0 A 1 A 2 A 3 A 4 A 5 5 i p int* p; p = &i; A 0 A 1 A 2 A 3 A 4 A 5
Recap: Pointers IFMP 18, M. Schwerhoff int* int& *p &i &*&* ** * * * * A 0 A 1 A 2 A 3 A 4 A 5 A 0 A 1 A 2 A 3 A 4 A 5 5 i int* p; A 0 A 1 A 2 A 3 A 4 A 5 5 i p int* p; p = &i; A 0 A 1 A 2 A 3 A 4 A 5
Securing Network Traffic Tunneled Over Kernel managed TCP/UDP sockets
 Securing Network Traffic Tunneled Over Kernel managed TCP/UDP sockets Sowmini Varadhan(sowmini.varadhan@oracle.com) Agenda Proceedings of NetDev 1.1: The Technical Conference on Linux Networking (February
Securing Network Traffic Tunneled Over Kernel managed TCP/UDP sockets Sowmini Varadhan(sowmini.varadhan@oracle.com) Agenda Proceedings of NetDev 1.1: The Technical Conference on Linux Networking (February
This presentation covers Gen Z Buffer operations. Buffer operations are used to move large quantities of data between components.
 This presentation covers Gen Z Buffer operations. Buffer operations are used to move large quantities of data between components. 1 2 Buffer operations are used to get data put or push up to 4 GiB of data
This presentation covers Gen Z Buffer operations. Buffer operations are used to move large quantities of data between components. 1 2 Buffer operations are used to get data put or push up to 4 GiB of data
Process. Heechul Yun. Disclaimer: some slides are adopted from the book authors slides with permission
 Process Heechul Yun Disclaimer: some slides are adopted from the book authors slides with permission 1 Recap OS services Resource (CPU, memory) allocation, filesystem, communication, protection, security,
Process Heechul Yun Disclaimer: some slides are adopted from the book authors slides with permission 1 Recap OS services Resource (CPU, memory) allocation, filesystem, communication, protection, security,
IT-Symposium OpenVMS TCP/IP 1E02. peter ranisch. pr - edv-dienstleistungen Current Versions & ECO s
 OpenVMS TCP/IP 1E02 peter ranisch pr - edv-dienstleistungen email: OpenVMS@ranisch.at 1 Current Versions & ECO s OpenVMS VAX V7.3 TCPIP V5.3 ECO 4 Mar 04 OpenVMS Alpha V7.3-2 TCPIP V5.4 ECO 7 Oct 07 OpenVMS
OpenVMS TCP/IP 1E02 peter ranisch pr - edv-dienstleistungen email: OpenVMS@ranisch.at 1 Current Versions & ECO s OpenVMS VAX V7.3 TCPIP V5.3 ECO 4 Mar 04 OpenVMS Alpha V7.3-2 TCPIP V5.4 ECO 7 Oct 07 OpenVMS
CS510 Operating System Foundations. Jonathan Walpole
 CS510 Operating System Foundations Jonathan Walpole The Process Concept 2 The Process Concept Process a program in execution Program - description of how to perform an activity instructions and static
CS510 Operating System Foundations Jonathan Walpole The Process Concept 2 The Process Concept Process a program in execution Program - description of how to perform an activity instructions and static
HLD For SMP node affinity
 HLD For SMP node affinity Introduction Current versions of Lustre rely on a single active metadata server. Metadata throughput may be a bottleneck for large sites with many thousands of nodes. System architects
HLD For SMP node affinity Introduction Current versions of Lustre rely on a single active metadata server. Metadata throughput may be a bottleneck for large sites with many thousands of nodes. System architects
SE350: Operating Systems. Lecture 3: Concurrency
 SE350: Operating Systems Lecture 3: Concurrency Main Points Thread abstraction What are threads and what is the thread abstraction? Thread life cycle What states does a thread go through? Thread Implementation
SE350: Operating Systems Lecture 3: Concurrency Main Points Thread abstraction What are threads and what is the thread abstraction? Thread life cycle What states does a thread go through? Thread Implementation
SpiNNaker Application Programming Interface (API)
 SpiNNaker Application Programming Interface (API) Version 2.0.0 10 March 2016 Application programming interface (API) Event-driven programming model The SpiNNaker API programming model is a simple, event-driven
SpiNNaker Application Programming Interface (API) Version 2.0.0 10 March 2016 Application programming interface (API) Event-driven programming model The SpiNNaker API programming model is a simple, event-driven
Disk-Level Encryption
 2011-2017 Percona, Inc. 1 / 19 Disk-Level Encryption http://www.percona.com/training/ 2011-2017 Percona, Inc. 2 / 19 Introduction Clients in the PCI, HIPPA, or PHI space Encrypted "at rest" MySQL 5.7 InnoDB
2011-2017 Percona, Inc. 1 / 19 Disk-Level Encryption http://www.percona.com/training/ 2011-2017 Percona, Inc. 2 / 19 Introduction Clients in the PCI, HIPPA, or PHI space Encrypted "at rest" MySQL 5.7 InnoDB
Cryptographic Hardware Support for the Linux Kernel
 Cryptographic Hardware Support for the Linux Kernel James Morris Red Hat Inc. Oregon Networking Summit, July 2004 Current Status Simple crypto API in the 2.6 kernel, designed primarily for IPSec and then
Cryptographic Hardware Support for the Linux Kernel James Morris Red Hat Inc. Oregon Networking Summit, July 2004 Current Status Simple crypto API in the 2.6 kernel, designed primarily for IPSec and then
OpenAMP Discussion - Linaro2018HK. Copyright 2018 Xilinx
 OpenAMP Discussion - Linaro2018HK Agenda o SPDX Short Licenses Identifier o Coding Guideline o API Standardisation o Coprocessor Image Format o OpenAMP and Container Page 2 OpenAMP License Page 3 SPDX
OpenAMP Discussion - Linaro2018HK Agenda o SPDX Short Licenses Identifier o Coding Guideline o API Standardisation o Coprocessor Image Format o OpenAMP and Container Page 2 OpenAMP License Page 3 SPDX
Processes (Intro) Yannis Smaragdakis, U. Athens
 Processes (Intro) Yannis Smaragdakis, U. Athens Process: CPU Virtualization Process = Program, instantiated has memory, code, current state What kind of memory do we have? registers + address space Let's
Processes (Intro) Yannis Smaragdakis, U. Athens Process: CPU Virtualization Process = Program, instantiated has memory, code, current state What kind of memory do we have? registers + address space Let's
CONTENTS. vii. Chapter 1 TCP/IP Overview 1. Chapter 2 Symmetric-Key Cryptography 33. Acknowledgements
 CONTENTS Preface Acknowledgements xiii xvii Chapter 1 TCP/IP Overview 1 1.1 Some History 2 1.2 TCP/IP Protocol Architecture 4 1.2.1 Data-link Layer 4 1.2.2 Network Layer 5 1.2.2.1 Internet Protocol 5 IPv4
CONTENTS Preface Acknowledgements xiii xvii Chapter 1 TCP/IP Overview 1 1.1 Some History 2 1.2 TCP/IP Protocol Architecture 4 1.2.1 Data-link Layer 4 1.2.2 Network Layer 5 1.2.2.1 Internet Protocol 5 IPv4
1 #include <linux/module.h> 2 #include <linux/sched.h> 3 #include <linux/interrupt.h> 4 #include <linux/init.h> 5 #include <linux/kernel.
 1 #include 2 #include 3 #include 4 #include 5 #include 6 #include 7 #include 8 #include
1 #include 2 #include 3 #include 4 #include 5 #include 6 #include 7 #include 8 #include
How do I perform a backup and restore from a NOKIA IP VPN 10i to another NOKIA IP VPN 10i in the event of a hardware failure?
 BACKUP AND RESTORE 1 (14) How do I perform a backup and restore from a NOKIA IP VPN 10i to another NOKIA IP VPN 10i in the event of a hardware failure? This document will demonstrate the backup process
BACKUP AND RESTORE 1 (14) How do I perform a backup and restore from a NOKIA IP VPN 10i to another NOKIA IP VPN 10i in the event of a hardware failure? This document will demonstrate the backup process
A brief introduction to C programming for Java programmers
 A brief introduction to C programming for Java programmers Sven Gestegård Robertz September 2017 There are many similarities between Java and C. The syntax in Java is basically
A brief introduction to C programming for Java programmers Sven Gestegård Robertz September 2017 There are many similarities between Java and C. The syntax in Java is basically
Operating Systems: Internals and Design Principles. Chapter 4 Threads Seventh Edition By William Stallings
 Operating Systems: Internals and Design Principles Chapter 4 Threads Seventh Edition By William Stallings Operating Systems: Internals and Design Principles The basic idea is that the several components
Operating Systems: Internals and Design Principles Chapter 4 Threads Seventh Edition By William Stallings Operating Systems: Internals and Design Principles The basic idea is that the several components
Introduction to Operating Systems. Device Drivers. John Franco. Dept. of Electrical Engineering and Computing Systems University of Cincinnati
 Introduction to Operating Systems Device Drivers John Franco Dept. of Electrical Engineering and Computing Systems University of Cincinnati Basic Computer Architecture CPU Main Memory System Bus Channel
Introduction to Operating Systems Device Drivers John Franco Dept. of Electrical Engineering and Computing Systems University of Cincinnati Basic Computer Architecture CPU Main Memory System Bus Channel
Prepared by Prof. Hui Jiang Process. Prof. Hui Jiang Dept of Electrical Engineering and Computer Science, York University
 EECS3221.3 Operating System Fundamentals No.2 Process Prof. Hui Jiang Dept of Electrical Engineering and Computer Science, York University How OS manages CPU usage? How CPU is used? Users use CPU to run
EECS3221.3 Operating System Fundamentals No.2 Process Prof. Hui Jiang Dept of Electrical Engineering and Computer Science, York University How OS manages CPU usage? How CPU is used? Users use CPU to run
Security features for UBIFS. Richard Weinberger sigma star gmbh
 Richard Weinberger sigma star gmbh /me Richard Weinberger Co-founder of sigma star gmbh Linux kernel developer and maintainer Strong focus on Linux kernel, lowlevel components, virtualization, security
Richard Weinberger sigma star gmbh /me Richard Weinberger Co-founder of sigma star gmbh Linux kernel developer and maintainer Strong focus on Linux kernel, lowlevel components, virtualization, security
IPSECv6 Peach Pit User Guide. Peach Fuzzer, LLC. v3.7.50
 IPSECv6 Peach Pit User Guide Peach Fuzzer, LLC v3.7.50 Copyright 2015 Peach Fuzzer, LLC. All rights reserved. This document may not be distributed or used for commercial purposes without the explicit consent
IPSECv6 Peach Pit User Guide Peach Fuzzer, LLC v3.7.50 Copyright 2015 Peach Fuzzer, LLC. All rights reserved. This document may not be distributed or used for commercial purposes without the explicit consent
How to Create a TINA VPN Tunnel between F- Series Firewalls
 How to Create a TINA VPN Tunnel between F- Series Firewalls As the TINA protocol offers significant advantages over IPsec, it is the main protocol that is used for VPN connections between F-Series Firewalls.
How to Create a TINA VPN Tunnel between F- Series Firewalls As the TINA protocol offers significant advantages over IPsec, it is the main protocol that is used for VPN connections between F-Series Firewalls.
Lecture 10 Midterm review
 Lecture 10 Midterm review Announcements The midterm is on Tue Feb 9 th in class 4Bring photo ID 4You may bring a single sheet of notebook sized paper 8x10 inches with notes on both sides (A4 OK) 4You may
Lecture 10 Midterm review Announcements The midterm is on Tue Feb 9 th in class 4Bring photo ID 4You may bring a single sheet of notebook sized paper 8x10 inches with notes on both sides (A4 OK) 4You may
LSN 13 Linux Concurrency Mechanisms
 LSN 13 Linux Concurrency Mechanisms ECT362 Operating Systems Department of Engineering Technology LSN 13 Creating Processes fork() system call Returns PID of the child process created The new process is
LSN 13 Linux Concurrency Mechanisms ECT362 Operating Systems Department of Engineering Technology LSN 13 Creating Processes fork() system call Returns PID of the child process created The new process is
Process. Prepared by Prof. Hui Jiang Dept. of EECS, York Univ. 1. Process in Memory (I) PROCESS. Process. How OS manages CPU usage? No.
 EECS3221.3 Operating System Fundamentals No.2 Prof. Hui Jiang Dept of Electrical Engineering and Computer Science, York University How OS manages CPU usage? How CPU is used? Users use CPU to run programs
EECS3221.3 Operating System Fundamentals No.2 Prof. Hui Jiang Dept of Electrical Engineering and Computer Science, York University How OS manages CPU usage? How CPU is used? Users use CPU to run programs
Process Concept. Minsoo Ryu. Real-Time Computing and Communications Lab. Hanyang University.
 Process Concept Minsoo Ryu Real-Time Computing and Communications Lab. Hanyang University msryu@hanyang.ac.kr Topics Covered Process Concept Definition, states, PCB Process Scheduling Scheduling queues,
Process Concept Minsoo Ryu Real-Time Computing and Communications Lab. Hanyang University msryu@hanyang.ac.kr Topics Covered Process Concept Definition, states, PCB Process Scheduling Scheduling queues,
IPv6 Protocol. Does it solve all the security problems of IPv4? Franjo Majstor EMEA Consulting Engineer Cisco Systems, Inc.
 IPv6 Protocol Does it solve all the security problems of IPv4? Franjo Majstor EMEA Consulting Engineer fmajstor@cisco.com Cisco Systems, Inc. 1 Agenda IPv6 Primer IPv6 Protocol Security Dual stack approach
IPv6 Protocol Does it solve all the security problems of IPv4? Franjo Majstor EMEA Consulting Engineer fmajstor@cisco.com Cisco Systems, Inc. 1 Agenda IPv6 Primer IPv6 Protocol Security Dual stack approach
Heap Arrays. Steven R. Bagley
 Heap Arrays Steven R. Bagley Recap Data is stored in variables Can be accessed by the variable name Or in an array, accessed by name and index a[42] = 35; Variables and arrays have a type int, char, double,
Heap Arrays Steven R. Bagley Recap Data is stored in variables Can be accessed by the variable name Or in an array, accessed by name and index a[42] = 35; Variables and arrays have a type int, char, double,
Developer manual. (Onvif Client Library) Happytimesoft Technology Co.,LTD
 Developer manual (Onvif Client Library) Happytimesoft Technology Co.,LTD Declaration All rights reserved. No part of this publication may be excerpted, reproduced, translated, annotated or edited, in any
Developer manual (Onvif Client Library) Happytimesoft Technology Co.,LTD Declaration All rights reserved. No part of this publication may be excerpted, reproduced, translated, annotated or edited, in any
Lab 9: VPNs IPSec Remote Access VPN
 Lab 9: VPNs IPSec Remote Access VPN Rich Macfarlane 2015 Aim: Details The aim of this lab is to introduce Virtual Private Network (VPN) concepts, using an IPSec remote access VPN between a remote users
Lab 9: VPNs IPSec Remote Access VPN Rich Macfarlane 2015 Aim: Details The aim of this lab is to introduce Virtual Private Network (VPN) concepts, using an IPSec remote access VPN between a remote users
Chapter 5.6 Network and Multiplayer
 Chapter 5.6 Network and Multiplayer Multiplayer Modes: Event Timing Turn-Based Easy to implement Any connection type Real-Time Difficult to implement Latency sensitive 2 Multiplayer Modes: Shared I/O Input
Chapter 5.6 Network and Multiplayer Multiplayer Modes: Event Timing Turn-Based Easy to implement Any connection type Real-Time Difficult to implement Latency sensitive 2 Multiplayer Modes: Shared I/O Input
NCP Secure Enterprise macos Client Release Notes
 Service Release: 3.20 r43098 Date: March 2019 Prerequisites Apple macos operating systems: The following Apple macos operating systems are supported with this release: macos Mojave 10.14 macos High Sierra
Service Release: 3.20 r43098 Date: March 2019 Prerequisites Apple macos operating systems: The following Apple macos operating systems are supported with this release: macos Mojave 10.14 macos High Sierra
PKCS #11 Message-Based Encryption and Decryption
 PKCS #11 Message-Based Encryption and Decryption Wan-Teh Chang , 2014-03-11 Introduction Message-based encryption refers to the process of encrypting multiple messages using the same encryption
PKCS #11 Message-Based Encryption and Decryption Wan-Teh Chang , 2014-03-11 Introduction Message-based encryption refers to the process of encrypting multiple messages using the same encryption
STUDY OF SOCKET PROGRAMMING
 STUDY OF SOCKET PROGRAMMING Sockets : An application programming interface(api) used for inter process communication. Sockets allow communication between two different processes on the same or different
STUDY OF SOCKET PROGRAMMING Sockets : An application programming interface(api) used for inter process communication. Sockets allow communication between two different processes on the same or different
NCP Secure Enterprise macos Client Release Notes
 Service Release: 3.10 r40218 Date: July 2018 Prerequisites Apple OS X operating systems: The following Apple macos operating systems are supported with this release: macos High Sierra 10.13 macos Sierra
Service Release: 3.10 r40218 Date: July 2018 Prerequisites Apple OS X operating systems: The following Apple macos operating systems are supported with this release: macos High Sierra 10.13 macos Sierra
CS G256 L07: Hash Functions May 25, 2004 MD5 SHA-1 HMAC
 CS G256 L07: Hash Functions May 25, 2004 MD5 SHA-1 HMAC Message Digests Message Digests make a fingerprint of a file. Input: 1-2 64 bytes Output: 128 or 160 * bits File digest Message Digests File digest
CS G256 L07: Hash Functions May 25, 2004 MD5 SHA-1 HMAC Message Digests Message Digests make a fingerprint of a file. Input: 1-2 64 bytes Output: 128 or 160 * bits File digest Message Digests File digest
Synchronization I. Jo, Heeseung
 Synchronization I Jo, Heeseung Today's Topics Synchronization problem Locks 2 Synchronization Threads cooperate in multithreaded programs To share resources, access shared data structures Also, to coordinate
Synchronization I Jo, Heeseung Today's Topics Synchronization problem Locks 2 Synchronization Threads cooperate in multithreaded programs To share resources, access shared data structures Also, to coordinate
Chapter 32 Security in the Internet: IPSec, SSL/TLS, PGP,
 Chapter 32 Security in the Internet: IPSec, SSL/TLS, PGP, VPN, and Firewalls 32.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 32.2 Figure 32.1 Common structure
Chapter 32 Security in the Internet: IPSec, SSL/TLS, PGP, VPN, and Firewalls 32.1 Copyright The McGraw-Hill Companies, Inc. Permission required for reproduction or display. 32.2 Figure 32.1 Common structure
Agenda Process Concept Process Scheduling Operations on Processes Interprocess Communication 3.2
 Lecture 3: Processes Agenda Process Concept Process Scheduling Operations on Processes Interprocess Communication 3.2 Process in General 3.3 Process Concept Process is an active program in execution; process
Lecture 3: Processes Agenda Process Concept Process Scheduling Operations on Processes Interprocess Communication 3.2 Process in General 3.3 Process Concept Process is an active program in execution; process
Process. Heechul Yun. Disclaimer: some slides are adopted from the book authors slides with permission 1
 Process Heechul Yun Disclaimer: some slides are adopted from the book authors slides with permission 1 Recap OS services Resource (CPU, memory) allocation, filesystem, communication, protection, security,
Process Heechul Yun Disclaimer: some slides are adopted from the book authors slides with permission 1 Recap OS services Resource (CPU, memory) allocation, filesystem, communication, protection, security,
NCP Secure Entry macos Client Release Notes
 Service Release: 3.20 r43098 Date: March 2019 Prerequisites Apple macos operating systems: The following Apple macos operating systems are supported with this release: macos Mojave 10.14 macos High Sierra
Service Release: 3.20 r43098 Date: March 2019 Prerequisites Apple macos operating systems: The following Apple macos operating systems are supported with this release: macos Mojave 10.14 macos High Sierra
FIPS Non-Proprietary Security Policy. Level 1 Validation Version 1.2
 Oracle Solaris Kernel Cryptographic Framework with SPARC T4 and T5 Software Version: 1.0 and 1.1; Hardware Version: SPARC T4 (527-1437-01) and T5 (7043165) FIPS 140-2 Non-Proprietary Security Policy Level
Oracle Solaris Kernel Cryptographic Framework with SPARC T4 and T5 Software Version: 1.0 and 1.1; Hardware Version: SPARC T4 (527-1437-01) and T5 (7043165) FIPS 140-2 Non-Proprietary Security Policy Level
Supporting Cloud Native with DPDK and containers KEITH INTEL CORPORATION
 x Supporting Cloud Native with DPDK and containers KEITH WILES @ INTEL CORPORATION Making Applications Cloud Native Friendly How can we make DPDK Cloud Native Friendly? Reduce startup resources for quicker
x Supporting Cloud Native with DPDK and containers KEITH WILES @ INTEL CORPORATION Making Applications Cloud Native Friendly How can we make DPDK Cloud Native Friendly? Reduce startup resources for quicker
Final Exam, Spring 2012 Date: May 14th, 2012
 Full Name: Final Exam, Spring 2012 Date: May 14th, 2012 Instructions: This final exam takes 1 hour and 30 minutes. Read through all the problemsandcompletetheeasy ones first. This exam is OPEN BOOK. You
Full Name: Final Exam, Spring 2012 Date: May 14th, 2012 Instructions: This final exam takes 1 hour and 30 minutes. Read through all the problemsandcompletetheeasy ones first. This exam is OPEN BOOK. You
For use by students enrolled in #71251 CSE430 Fall 2012 at Arizona State University. Do not use if not enrolled.
 Operating Systems: Internals and Design Principles Chapter 4 Threads Seventh Edition By William Stallings Operating Systems: Internals and Design Principles The basic idea is that the several components
Operating Systems: Internals and Design Principles Chapter 4 Threads Seventh Edition By William Stallings Operating Systems: Internals and Design Principles The basic idea is that the several components
OpenDataPlane: network packet journey
 OpenDataPlane: network packet journey Maxim Uvarov This presentation describes what is ODP. Touches common data types and APIs to work with network packets. Answers the question why ODP is needed and how
OpenDataPlane: network packet journey Maxim Uvarov This presentation describes what is ODP. Touches common data types and APIs to work with network packets. Answers the question why ODP is needed and how
Today s Topics. u Thread implementation. l Non-preemptive versus preemptive threads. l Kernel vs. user threads
 Today s Topics COS 318: Operating Systems Implementing Threads u Thread implementation l Non-preemptive versus preemptive threads l Kernel vs. user threads Jaswinder Pal Singh and a Fabulous Course Staff
Today s Topics COS 318: Operating Systems Implementing Threads u Thread implementation l Non-preemptive versus preemptive threads l Kernel vs. user threads Jaswinder Pal Singh and a Fabulous Course Staff
Device Drivers. CS449 Fall 2017
 Device Drivers CS449 Fall 2017 Software Layers User-level I/O so7ware & libraries Device-independent OS so7ware Device drivers Interrupt handlers User OperaEng system (kernel) Hardware Device Drivers User
Device Drivers CS449 Fall 2017 Software Layers User-level I/O so7ware & libraries Device-independent OS so7ware Device drivers Interrupt handlers User OperaEng system (kernel) Hardware Device Drivers User
OPAE Intel FPGA Linux Device Driver Architecture Guide
 OPAE Intel FPGA Linux Device Driver Architecture Guide Subscribe Send Feedback Latest document on the web: PDF HTML Contents Contents 1 OPAE Intel FPGA Linux Device Driver Architecture...3 1.1 Hardware
OPAE Intel FPGA Linux Device Driver Architecture Guide Subscribe Send Feedback Latest document on the web: PDF HTML Contents Contents 1 OPAE Intel FPGA Linux Device Driver Architecture...3 1.1 Hardware
