Seminar: IT Security Design der neuen Art 2016 IXIA AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED.
|
|
|
- Moris Horatio Henry
- 6 years ago
- Views:
Transcription
1 Seminar: IT Security Design der neuen Art 1
2 OUR HISTORY AND COMPETENCE Anue Systems: > Network Visibility: > Packet Brokers (NTO) > Network Testing: > Impairment Generator 2002 June Oct NetOptics: > Network Visibility: > Packet Brokers (xstream) > Inline Security (BypassTap) > Network Taps Ixia: > Founded in 1997 > Active testing of > IP networks, > Wifi > 3G/LTE 2005 July 2012 BreakingPoint: > Security testing > Attack analytics Keysight Technolgies: > April 2017 Ixia part of Keysight Technologies (ixia solutions group) 2
3 Visibility Portfolio (offline) 3
4 QUESTION How do they make sure that the millions of Dollars that has been spent are paying off in terms of: Availability: - meet SLAs Security: - Potential threats, data loss prevention, vulnerabilities Compliance: - Sarbanes-Oxley, HIPPA, PCI-DDS Performance: - End user experience, troubleshooting, root cause analysis Trends: - Capacity planning and scalability 4
5 HERE IS THE SOLUTION Step 1: Deploy Ixia TAPs Internet Deploy Ixia TAPs within your network architecture providing you full visibility S S S 5
6 TAP VERSUS SPAN TAP Full Duplex Taps (no packet loss due to aggregation) Simplest optical TAPs are safe as houses and grow with the Network from GE to 100GE Copper TAPs are fail safe even when the power is lost Available for all media types: Copper: 10M, 100M & 1G Optical: Single Mode 1G till 100G Multi Mode 1G till 100G Cisco Bidi SPAN Limited number of SPANs leads to compromise (Multiple tools cannot be used at the same time) Have to be configured and maintained (Danger working on Production Network) Load depended behavior (tend to lose packets already at lower processor load) 6
7 VIRTUAL NETWORKS Problem: East-West traffic never leaves the physical server and so it does lead again into: Hypervisor VM 1 WEB VM 2 APP VM 3 DB Security, Monitoring and Compliance Risks East-West (green arrows) Traffic NOT Seen by Network Monitoring Tools No Visibility Virtual Switch No Audit Trail No Utilization Insight 7
8 VIRTUAL TAP KVM HYPER-V Cloudlens vtap is capable of capturing and then sending inter-vm traffic of interest to the tools that are already monitoring your physical network. Plus it can perform basic filtering. ESXi vtap Service vswitch Monitoring vswitch GRE-VLAN-ERSPAN Custom Tunnel 8
9 HERE IS THE SOLUTION Step 2: Deploy Ixia Cloudlens vtap Internet S S S Ixia Cloudlens vtaps providing access to east-west traffic within the same hypervisor 9
10 PROBLEM WITH THE GRANULARITY Granularity can become very costly due to: > Every TAP requires two tool ports (A>B & B>A) > Link speed dictates tool speed and performance (very costly for 40G/100G) > Different tools are competing against the same TAP or SPAN port > If not as much tool ports as TAP or SPAN are available engineers need to change ports. (Problems with access control/rights & distance) Finally a project is dead already before it started > Tools are flooded with unnecessary data 10
11 HERE IS THE SOLUTION Step 3: Deploy Ixia Packet Broker Internet S S S Ixia Vision Packet Broker: > aggregate SPAN,& TAP & tools > filter & forward only relevant data > Providing Advanced and ATIP features > optimizing tool performance 11
12 CENTRALIZED SOLUTION 12
13 DISTRIBUTED SOLUTION WITH CLUSTERING 13
14 USE CASE VISIBILITY PER TOP OF RACK Internet Tools Farm VisionEdge Series S S Ixia VisionEdge Series Ports from 1G till 100G Filtering till L4 Single or multiple tools to be connected Tap top of rack switches with a few taps 14
15 USE CASE HIGH DENSITY LEAF-SPINE Internet Fabric Controller VisionEdge Tools Farm S S S Ixia VisionEdge Series Ports from 1G till 100G Filtering till L4 Clustering support to move network traffic to central tools Medium scale data center Multiple racks and leaf-spine topology Redundant paths to tap 15
16 VISIBILITY INTELLIGENCE STACKS NetStack(~NPB Basics) 3 Stages of Filtering Dynamic Filter Compiler Double your Ports VLAN Tagging Aggregation & Replication Load Balancing PacketStack (~AFM) Deduplication Header Stripping & Protocol Trimming Timestamping Data Masking GRE Tunneling Burst Protection AppStack (~ATIP) Application & RegEx filtering Geolocation & Tagging Real-time Dashboard NetFlow & IxFlowReg Data Masking + PCAP SecureStack Passive SSL Decryption Active SSL (Q2 2017) 16
17 PACKETSTACK (AFM) Advanced Packet Processing (AFM) Features Deduplication Header stripping Packet Trimming Data Masking Tunnel Termination Timestamping Burst Protection NPB Adv. Packet Processing Hardware AFM All unique frames going to /8 Only the first 128 bytes of TCP Port 25 frames 17
18 PACKETSTACK (AFM) 1. Assign AFM bandwidth > Network- ToolPort > Dynamic Filter 2. Configure & combine > Multiple functions at the same 18
19 APPSTACK (ATIP) Meta Data All traffic from Georgia NPB App Brokering App Filtering All voice traffic from HTC Ones Someone from S. Africa watching House of Cards on Netflix on an iphone on Vodacom s network ATI Processor (ATIP) - Context-rich Application Visibility Application forwarding based on application, geography, and RegEx matching Real-time dashboard Rich NetFlow / IPFIX generation > Device OS > Browser > Geolocation Data Masking > Dynamic (RegEx) 19
20 SECURE STACK - SPYGLASS Encrypted traffic is expected to be 75% of all traffic by the end of 2017 Challenge: It is extremely expensive to inspect encrypted traffic at volume and speed! 20
21 HIGH PERFORMANCE ACTIVE SSL INSPECTION New high-performance Application Module for Vision ONE and Vision 7300 Dedicated cryptographic processor Integrated with Inline support on NTO Both inline and passive tool support Policy-based SSL inspection URL categorization 21
22 USE CASE HIGH DENSITY WITH ADVANCED PACKET PROCESSING FOR TOOL OPTIMIZATION Internet VisionEdge Series Vision ONE/7300 Tools Farm S S S Ixia VisionEdge Series Ports from 1G till 100G Filtering till L4 Aggregating lot of ports VisionOne-ControlTower Benefits Advanced Packet Processing > De-duplication, Trimming, Stripping > L7 filtering, SSL decryption, Netflow gen. Single pane of glass UI with Ixia Fabric Controller (IFC) Medium scale data center Multiple racks and leaf-spine topology 22
23 USE CASE ULTRA SCALE WITH ADVANCED PACKET PROCESSING FOR TOOL OPTIMIZATION Internet VisionEdge Series Vision 7300 Tools Farm S S S Ixia VisionEdge Series Ports from 1G till 100G Filtering till L4 Aggregating lot of ports VisionOne-ControlTower Benefits Advanced Packet Processing (Terabits/s) > De-duplication, Trimming, Stripping > L7 filtering, SSL decryption, Netflow gen. Single pane of glass UI with Ixia Fabric Controller (IFC) Massive scale data center 100s of 10/40/100G taps required 23
24 Security Portfolio (inline) 24
25 INLINE VERSUS OUT OF BAND Out of Band Inline - Tool goes into the link - Defective tool does take the link down - Tools are: NGFW, IPS - Tool does receive only copies from the link - Defective tool does not take the link down - Tools are: APM, NPM, VoIP Analyzer, DLP, SIEM, IDS, Sandboxing - TAP: electrical or optical 10M-100G 25
26 BYPASS REGULAR OPERATION (BYPASS=OFF) Bypass Tap (1) Heartbeat packet preserves the link state towards IPS Protects against power, link, and application failure Provides flexibility for upgrades, moves, etc. 26
27 ANY ADVANTAGE BY ADDING A PACKET BROKER? Spare Unit Jumps in if any of the production units has an issue Keeps security index up (no more 100% or nothing) Load Balancing Load balance link bandwidth between one tool load balance group Cost effective solution (multiple 1G IPS are cheaper than a single 10G IPS) 27
28 AND EVEN MORE ADVANTAGES BY ADDING A PACKET BROKER Redirect packets Traffic that does not need to be inspected by the inline tools can be redirected back into the link Offload security tools from unwanted traffic Better resource management Inline SSL decryption Powerful 10Gbit/s bidirectional inline SSL decryption Offload decryption from tools (better performance and less delay at less cost) 28
29 SEAMLESS INTEGRATION OF NEW SECURITY TOOLS Phase 1 New security tools are receiving only copies of the link packets Security teams can get familiar with the behavior Phase 2 Seamless inline integration once Security teams are confided with the new tool 29
30 WHAT IF I HAVE MULTIPLE LINKS TO THE WORLD? Packet Broker does: Maintain link affinity. Packets from each link are assured to be delivered back to that link. Load balance all packets with session affinity through the individual tools in the LBG Switch to standby units in case of an issue with the production units 30
31 OK, BUT WHAT IF I HAVE INLINE AND OFFLINE SECURITY TOOLS? We are happy to help Internally tap whatever out of band tool (Sandboxing, Data Recorder, IDS) you want to the Packet Broker In this case the Packet Broker will send packet copies from the internally tapped links to the OOB tools Use Advanced Features (Deduplication, Packet Trimming, Header Stripping ) or ATIP features (Application layer filtering, SSL decryption or Netflow generation) to your advantage 31
32 BUT AN IPS DECIDES WHAT A SANDBOXING UNIT NEED TO CHECK Still not an issue Let the IPS manage filter settings of the Packet Broker programmatically through RESTful API 32
33 SINGLE POINT OF FAILURE? NOT WITH HA? Here is the solution: Use BypassVHD switches supporting High Availability (HA) and double up the Packet Broker and Tool infrastructure for 100% redundancy The advantage of a HA Bypass is that it has two links down to the Packet Broker. If one of the links fails the Bypass will switch traffic to the other Bypass. Only if both links down do not work anymore the Bypass will fail the links open 33
34 AND HERE IS THE FULL PICTURE A single ixia Packet Broker can handle inline as well as offline applications. 34
35 CloudLens 35
36 INTRODUCING CLOUDLENS Visibility across all your cloud environments - public, private, and hybrid clouds CloudLens CloudLens Private CloudLens Public Branch Office Virtual DC Private Cloud Public Cloud CloudLens vtap CloudLens vpb CloudLens vatip 36
37 VIRTUAL DATACENTER VISIBILITY Inter-VM East-West Traffic Monitoring No Blind Spots Physical End Point Tools KVM HYPER-V IPS/IDS Traffic Analysis DLP Virtual Traffic Visibility Provides Visibility into Data Center Network (Inline/ Out of Band) ESXi vswitch vtap Service Monitoring vswitch CloudLens Mgr. Netflow / Full Packets Netflow Geo-location Time Stamping Deduplication Header Stripping FireEye SPLUNK ** Scrutinizer ** NTOP Monit Probe ** (Radcom) vgsc Monitoring Host Inter-VM Traffic Monitoring Multiple Hypervisor Support (ESXi, KVM, Hyper-V, OpenStack) vswitch/router Agnostic (VSS, vds, Cisco Nexus) GRE VLAN ERSPAN Protocols Monitoring Tool Agnostic Centralized Management GRE-VLAN-ERSPAN Custom Tunnel 37
38 HOW CLOUDLENS WORKS IXIA CloudLens Public Management Layer Monitoring Tools Security Tools Performance Tools Secure Visibility Path Filtering at source Filtered Traffic securely sent from Instance to Tool 38
39 ARCHITECTURE DESIGN HYBRID CLOUD 39
40 IXIA SOLUTIONS FOR THE ARCHITECTURE DESIGN Ixia FlexTap Ixia Taps are available for all media types: Copper: 10M, 100M & 1G Optical: Single Mode & Multi Mode 1G till 100G Cisco Bidi 40
41 IXIA SOLUTIONS FOR THE ARCHITECTURE DESIGN Ixia CloudLens Inter-VM Traffic Monitoring Multiple Hypervisor Support (ESXi, KVM, VM, OpenStack) vswitch/router Agnostic (VSS, vds, Cisco Nexus) GRE-VLAN-ERSPAN Protocols 41
42 IXIA SOLUTIONS FOR THE ARCHITECTURE DESIGN Ixia CloudLens AWS Support SaaS Web-Interface where Cloud Visibility is managed Docker based component that sits within Source and Tool Instances in a customers environment Filtered traffic securely sent from Instance to Tool 42
43 IXIA SOLUTIONS FOR THE ARCHITECTURE DESIGN Ixia Packet Broker Aggregation & Filtering till Application Level Packet Processing (Trimming, Stripping, De-Duplication SSL-Decryption, Netflow Generation Web Based User Interface 43
44 SO WHAT DO I NEED FROM IXIA? Only four things: Packet Broker Bypass Tap CloudLens 44
45 IXIA FLEX TAP - 1G/10G/40G/100G (LR & ER) > Single Mode with LC Connector > Split Ratio 50/50, 60/40, 70/30, 80/20 & 90/10-1G (SX) > Multi Mode with LC Connector > 62,5 µm > Split Ratio 50/50, 60/40, 70/30, 80/20 & 90/10-1G (SX) & 10G (SR) > Multi Mode with LC Connector > 50 µm > Split Ratio 50/50, 60/40, 70/30 & 80/20-40G (SR4) > Multi Mode with MTP Connector > 50µm > Split Ratio 50/50 & 70/30-40G (Cisco Bidi) > Multi Mode > 50µm > Split Ratio 50/50-100G (SR10) > Multi Mode with MTP Connector > 50µm > Split Ratio 50:50 & 70:30-40G (MR4) > Multi Mode with LC Connector > 50 µm > Split Ratio 70/30 45
46 IXIA BYPASS SWITCH ibypass 3 ibypass 10G ibypass (4x10G) ibypass HD ibypass VHD 46
47 WHO IS WHO OF IXIA PACKET BROKER 47
48 Break 48
49 Front Line Defence Threat ARMOR 49
50 BEHIND EVERY SECURITY BREACH IS A SECURITY TEAM WITH HIGH-QUALITY TOOLS 50
51 BUT ON AVERAGE, ONLY 29% OF ALERTS RECEIVED ARE INVESTIGATED* WHY? 51 *Ponemon 2016 State of Malware Detection & Prevention
52 THE INTERNET IS FULL OF GOOD AND BAD TRAFFIC 52
53 HAMMERING YOUR COMPANY S SECURITY INFRASTRUCTURE 53
54 THE CONSTANT BARRAGE OF NETWORK PROBES AND SCANS CREATES A LOT OF NOISE AND HIDES CRITICAL EVENTS 54
55 BUT THERE IS A SOLUTION 55
56 NOW YOU CAN FILTER OUT KNOWN BAD IPs 56
57 AND COMPLETELY REMOVE UNTRUSTED COUNTRIES 57
58 MAKING YOUR SECURITY TOOLS MORE EFFICIENT 58
59 INTRODUCING 59
60 ThreatARMOR FROM IXIA ThreatARMOR is a threat intelligence gateway. Blocks known-bad IPs and eliminates untrusted countries. Reduces alert fatigue and false positives
61 HOW ThreatARMOR COMPLEMENTS YOUR SECURITY DEPLOYMENT 61
62 HOW MANY BAD IP S CAN MY SECURITY DEVICE BLOCK? Next-gen Firewalls are optimized for DPI, threat detection, web security, and user based policies. They can typically block 10,000 to 40,000 IP ranges. This enough to handle a handful of countries and some manual block rules, but not enough to handle the tens of millions of malicious, hijacked, and unregistered IP addresses without substantial performance degradation. ThreatARMOR can block over 4 billion IP s at line rate. Offloading this large-scale IP blocking to ThreatARMOR increases firewall performance by up to 75%, freeing up resources while enabling more advanced firewall features. Web Transaction Rate 4,294,967,296 EVERY IP ON THE INTERNET INDIVIDUALLY EVALUATED WITH NO PERFORMANCE HIT ATI RAP SHEETS TOP 10 BOTNET COUNTRIES NGFW+TA NGFW ,000 IP RANGES 40,000 IP RANGES TOP 5 BOTNET COUNTRIES BOGONS HIJACKED IP s ENTRY-LEVEL NGFW HIGH-END NGFW ThreatARMOR 62
63 ThreatARMOR BRINGS THREAT INTELLIGENCE TO YOUR NETWORK IXIA ATI Research Center ThreatARMOR Rap Sheets ThreatARMOR Appliance Professional-grade Threat Intelligence Clear proof for every blocked site. Set, Select and Forget. Auto-updates every 5 min. Maximum reliability
64 HOW IS ThreatARMOR DIFFERENT? HIGH PERFORMANCE HIGH RESILIENCY Purpose-built to hold every IP address on the Internet Guaranteed line-rate performance blocking full ATI Rap Sheet database Scale with no performance impact from blocking one, one thousand, or one billion IP addresses Built for maximum reliability Dual-redundant power supplies Integrated bypass NIC Field-replaceable SSD Serial console capability 64 64
65 DEPLOY ThreatARMOR IN 30 MINUTES EASY TO CONFIGURE 1. Connect power and Ethernet cables 2. Pick Report Only or Blocking Mode 3. Walk away, it updates automatically Criminal site blocking is automatic Geo-blocking is optional 65 65
66 Dashboard shows top blocked countries, recent blocked IP and reason, and top traffic Log of countries recent IP Real-time overview blocks with reason. shows countries Click on any block attempting malicious for full Rap Sheet connections, total data including local throughput and IP addresses, DNS blocked connection info, screen shots stats and checksums. Bottom allowed countries are good candidates for blocking 66
67 CASE STUDY: SECURITY INTRUSION ALERTS REDUCED BY 80% ThreatARMOR cuts intrusions and capex CASE STUDY: HyperBox CHALLENGE: With 3 million attacks on web servers daily, customer needed a cost-effective, automated defense strategy SOLUTION: ThreatARMOR RESULTS: Reduced IDS intrusion detections from 1M to 200K, saving IT significant time due to fewer alerts Deferred new capex purchases by maximizing existing IDS and firewall tools Service Provider Sector Better Visibility Better Security 67
68 ThreatARMOR - YOUR THREAT INTELLIGENCE GATEWAY BLOCK the unwanted from touching your network GET MORE out of your security team and tools ENFORCE Ixia s professional-grade Application and Threat Intelligence feed IMPROVES YOUR SECURITY PERFORMANCE FAST! 68 68
69 THANK YOU 69
70 SUMMARY Ixia Packet Broker > can be used for inline (security) or offline (visibility) applications at the same time > allows cost effective usage of any tool Ixia Bypass Switch > prevents companies from being offline due to a security tool issue Ixia Tap > Provides reliable measurement points anywhere in the data center Ixia Cloudlens > Provides packet level access in virtual environment Might be installed with a dedicated monitoring or security project but once installed it is the base for any additional tools (inline or offline) that need to be attached 73
IXIA VISIBILITY ARCHITECTURE Eliminating Blind spots
 IXIA VISIBILITY ARCHITECTURE Eliminating Blind spots Юлий Явич, IXIA 1 Enterprise Carriers/ Service Providers 74 45 15 of the Fortune 100 of the top 50 carriers of the top 15 NEMs NEMs Customer Focused
IXIA VISIBILITY ARCHITECTURE Eliminating Blind spots Юлий Явич, IXIA 1 Enterprise Carriers/ Service Providers 74 45 15 of the Fortune 100 of the top 50 carriers of the top 15 NEMs NEMs Customer Focused
Daten-Management & Sicherheit in virtualisierten Umgebungen und der Cloud. Martin Heinzelmann SR CHANNEL SE
 Daten-Management & Sicherheit in virtualisierten Umgebungen und der Cloud Martin Heinzelmann SR CHANNEL SE 1 IXIA IS NOW A PART OF KEYSIGHT TECHNOLOGIES Ixia Network Visibility Leader Turnkey Platform
Daten-Management & Sicherheit in virtualisierten Umgebungen und der Cloud Martin Heinzelmann SR CHANNEL SE 1 IXIA IS NOW A PART OF KEYSIGHT TECHNOLOGIES Ixia Network Visibility Leader Turnkey Platform
IXVISION: VISIBILITY ARCHITECTURE Eliminating Blind spots
 IXVISION: VISIBILITY ARCHITECTURE Eliminating Blind spots Ernst Hillerkus, Regional Sales Manager Germany 2016 IXIA AN D /OR IT S AF FILIATES. ALL R IGH TS R ESERVED. 1 IXIA SOLUTIONS ARCHITECTURE IxTEST
IXVISION: VISIBILITY ARCHITECTURE Eliminating Blind spots Ernst Hillerkus, Regional Sales Manager Germany 2016 IXIA AN D /OR IT S AF FILIATES. ALL R IGH TS R ESERVED. 1 IXIA SOLUTIONS ARCHITECTURE IxTEST
VISION ONE: SECURITY WITHOUT SACRIFICE
 VISION ONE: SECURITY WITHOUT SACRIFICE DATA SHEET Amplify your security without changing a cable. Vision ONE provides IT Operations the ability to deploy resources where they are needed most and secure
VISION ONE: SECURITY WITHOUT SACRIFICE DATA SHEET Amplify your security without changing a cable. Vision ONE provides IT Operations the ability to deploy resources where they are needed most and secure
Reduce Your Network's Attack Surface
 WHITE PAPER Reduce Your Network's Attack Surface Ixia's ThreatARMOR Frees Up Security Resources and Personnel The Threat Landscape When you re dealing with network security, one of the primary measurements
WHITE PAPER Reduce Your Network's Attack Surface Ixia's ThreatARMOR Frees Up Security Resources and Personnel The Threat Landscape When you re dealing with network security, one of the primary measurements
VISION ONE: SECURITY WITHOUT SACRIFICE
 VISION ONE: SECURITY WITHOUT SACRIFICE DATA SHEET Amplify your security without changing a cable. Vision ONE provides IT Operations the ability to deploy resources where they are needed most and secure
VISION ONE: SECURITY WITHOUT SACRIFICE DATA SHEET Amplify your security without changing a cable. Vision ONE provides IT Operations the ability to deploy resources where they are needed most and secure
NETWORK VISIBILITY NETWORK PACKET BROKER COMPARISON TABLE
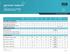 NETWORK VISIBILITY NETWORK PACKET BROKER COMPARISON TABLE Edge Edge Edge Edge Trade KEY VISIBILITY ATTRIBUTES Smart Drag and Drop Intuitive GUI Zero-Packet Loss Architecture Overlapping Filter Rules Automatically
NETWORK VISIBILITY NETWORK PACKET BROKER COMPARISON TABLE Edge Edge Edge Edge Trade KEY VISIBILITY ATTRIBUTES Smart Drag and Drop Intuitive GUI Zero-Packet Loss Architecture Overlapping Filter Rules Automatically
VISIBILITY INTO CLOUD COMPUTING
 VISIBILITY INTO CLOUD COMPUTING Brendan Leitch, Head of APAC Marketing 1 SECURITY AND PERFORMANCE DEPENDS ON DATA VISIBILITY Access Challenges: Get data access for tools VISIBILITY: Seeing the Traffic
VISIBILITY INTO CLOUD COMPUTING Brendan Leitch, Head of APAC Marketing 1 SECURITY AND PERFORMANCE DEPENDS ON DATA VISIBILITY Access Challenges: Get data access for tools VISIBILITY: Seeing the Traffic
Rethinking Security CLOUDSEC2016. Ian Farquhar Distinguished Sales Engineer Field Lead for the Gigamon Security Virtual Team
 Rethinking Security CLOUDSEC2016 Ian Farquhar Distinguished Sales Engineer Field Lead for the Gigamon Security Virtual Team Breaches Are The New Normal Only The Scale Surprises Us OPM will send notifications
Rethinking Security CLOUDSEC2016 Ian Farquhar Distinguished Sales Engineer Field Lead for the Gigamon Security Virtual Team Breaches Are The New Normal Only The Scale Surprises Us OPM will send notifications
NETWORK VISIBILITY NETWORK PACKET BROKER COMPARISON TABLE KEY VISIBILITY ATTRIBUTES SYSTEM SPECIFICATIONS SYSTEM CAPACITY.
 NETWORK VISIBILITY NETWORK PACKET BROKER COMPARISON TABLE KEY VISIBILITY ATTRIBUTES Smart Drag and Drop Intuitive GUI Zero-Packet Loss Architecture Unlimited Simultaneous Advanced Features Overlapping
NETWORK VISIBILITY NETWORK PACKET BROKER COMPARISON TABLE KEY VISIBILITY ATTRIBUTES Smart Drag and Drop Intuitive GUI Zero-Packet Loss Architecture Unlimited Simultaneous Advanced Features Overlapping
Corrigendum 3. Tender Number: 10/ dated
 (A premier Public Sector Bank) Information Technology Division Head Office, Mangalore Corrigendum 3 Tender Number: 10/2016-17 dated 07.09.2016 for Supply, Installation and Maintenance of Distributed Denial
(A premier Public Sector Bank) Information Technology Division Head Office, Mangalore Corrigendum 3 Tender Number: 10/2016-17 dated 07.09.2016 for Supply, Installation and Maintenance of Distributed Denial
Cisco Firepower NGFW. Anticipate, block, and respond to threats
 Cisco Firepower NGFW Anticipate, block, and respond to threats You have a mandate to build and secure a network that supports ongoing innovation Mobile access Social collaboration Public / private hybrid
Cisco Firepower NGFW Anticipate, block, and respond to threats You have a mandate to build and secure a network that supports ongoing innovation Mobile access Social collaboration Public / private hybrid
IXIA PHANTOM VTAP WITH TAPFLOW FILTERING
 IXIA PHANTOM VTAP WITH TAPFLOW FILTERING DATA SHEET OVERVIEW The Ixia Phantom vtap with TapFlow filtering is a software solution providing crystal-clear visibility into virtual data center network traffic.
IXIA PHANTOM VTAP WITH TAPFLOW FILTERING DATA SHEET OVERVIEW The Ixia Phantom vtap with TapFlow filtering is a software solution providing crystal-clear visibility into virtual data center network traffic.
Product Brief GigaVUE-VM
 Product Brief GigaVUE-VM Active Visibility for Virtual Workloads With exponential growth in virtualized traffic within the data center, a primary challenge for the centralized monitoring infrastructure
Product Brief GigaVUE-VM Active Visibility for Virtual Workloads With exponential growth in virtualized traffic within the data center, a primary challenge for the centralized monitoring infrastructure
Cato Cloud. Software-defined and cloud-based secure enterprise network. Solution Brief
 Cato Cloud Software-defined and cloud-based secure enterprise network Solution Brief Legacy WAN and Security Appliances are Incompatible with the Modern Enterprise Cato Networks: Software-defined and Cloud-based
Cato Cloud Software-defined and cloud-based secure enterprise network Solution Brief Legacy WAN and Security Appliances are Incompatible with the Modern Enterprise Cato Networks: Software-defined and Cloud-based
CLOUDLENS PUBLIC, PRIVATE, AND HYBRID CLOUD VISIBILITY
 CLOUDLENS PUBLIC, PRIVATE, AND HYBRID CLOUD VISIBILITY ORGANIZATIONS NEED VISIBILITY TO SECURE AND MONITOR THEIR CLOUD ENVIRONMENTS Organizations are migrating workloads to the cloud because it offers
CLOUDLENS PUBLIC, PRIVATE, AND HYBRID CLOUD VISIBILITY ORGANIZATIONS NEED VISIBILITY TO SECURE AND MONITOR THEIR CLOUD ENVIRONMENTS Organizations are migrating workloads to the cloud because it offers
Rethinking Security: The Need For A Security Delivery Platform
 Rethinking Security: The Need For A Security Delivery Platform Cybercrime In Asia: A Changing Environment & Shifting Focus Asia, more vulnerable to cybercrime because of diversity and breadth of countries
Rethinking Security: The Need For A Security Delivery Platform Cybercrime In Asia: A Changing Environment & Shifting Focus Asia, more vulnerable to cybercrime because of diversity and breadth of countries
BIG MON CONTROLLERS BIG MON ANALYTICS NODE. Multi-Terabytes L2-GRE 1/10/25/40/100G ETHERNET SWITCH FABRIC. Optional BIG MON BIG MON SERVICE NODES
 Modern Packet Recorder: Enhancing Data Security and Privacy Compliance OVERVIEW In response to the stringent corporate governance and compliance requirements for how IT data is secured, controlled, and
Modern Packet Recorder: Enhancing Data Security and Privacy Compliance OVERVIEW In response to the stringent corporate governance and compliance requirements for how IT data is secured, controlled, and
Ixia ibypass: Avoid 5 Common Security Risks in One Easy Step
 PRODUCT BRIEF Ixia ibypass: Avoid 5 Common Security Risks in One Easy Step With multi-million-dollar security breaches continuing to make headlines, businesses continue to invest in advanced security defenses
PRODUCT BRIEF Ixia ibypass: Avoid 5 Common Security Risks in One Easy Step With multi-million-dollar security breaches continuing to make headlines, businesses continue to invest in advanced security defenses
2018 Cisco and/or its affiliates. All rights reserved.
 Beyond Data Center A Journey to self-driving Data Center with Analytics, Intelligent and Assurance Mohamad Imaduddin Systems Engineer Cisco Oct 2018 App is the new Business Developer is the new Customer
Beyond Data Center A Journey to self-driving Data Center with Analytics, Intelligent and Assurance Mohamad Imaduddin Systems Engineer Cisco Oct 2018 App is the new Business Developer is the new Customer
F5 DDoS Hybrid Defender : Setup. Version
 F5 DDoS Hybrid Defender : Setup Version 13.1.0.3 Table of Contents Table of Contents Introducing DDoS Hybrid Defender... 5 Introduction to DDoS Hybrid Defender...5 DDoS deployments... 5 Example DDoS Hybrid
F5 DDoS Hybrid Defender : Setup Version 13.1.0.3 Table of Contents Table of Contents Introducing DDoS Hybrid Defender... 5 Introduction to DDoS Hybrid Defender...5 DDoS deployments... 5 Example DDoS Hybrid
Cisco Firepower NGFW. Anticipate, block, and respond to threats
 Cisco Firepower NGFW Anticipate, block, and respond to threats Digital Transformation on a Massive Scale 15B Devices Today Attack Surface 500B Devices In 2030 Threat Actors $19T Opportunity Next 10 Years
Cisco Firepower NGFW Anticipate, block, and respond to threats Digital Transformation on a Massive Scale 15B Devices Today Attack Surface 500B Devices In 2030 Threat Actors $19T Opportunity Next 10 Years
Cisco Nexus Data Broker
 Data Sheet Cisco Nexus Data Broker Product Overview You used to monitor traffic mainly to manage network operations. Today, when you monitor traffic you can find out instantly what is happening throughout
Data Sheet Cisco Nexus Data Broker Product Overview You used to monitor traffic mainly to manage network operations. Today, when you monitor traffic you can find out instantly what is happening throughout
Cato Cloud. Solution Brief. Software-defined and Cloud-based Secure Enterprise Network NETWORK + SECURITY IS SIMPLE AGAIN
 Cato Cloud Software-defined and Cloud-based Secure Enterprise Network Solution Brief NETWORK + SECURITY IS SIMPLE AGAIN Legacy WAN and Security Appliances are Incompatible with the Modern Enterprise The
Cato Cloud Software-defined and Cloud-based Secure Enterprise Network Solution Brief NETWORK + SECURITY IS SIMPLE AGAIN Legacy WAN and Security Appliances are Incompatible with the Modern Enterprise The
Deploying Intrusion Prevention Systems
 Deploying Intrusion Prevention Systems Gary Halleen Consulting Systems Engineer II Agenda Introductions Introduction to IPS Comparing Cisco IPS Solutions IPS Deployment Considerations Migration from IPS
Deploying Intrusion Prevention Systems Gary Halleen Consulting Systems Engineer II Agenda Introductions Introduction to IPS Comparing Cisco IPS Solutions IPS Deployment Considerations Migration from IPS
VeloCloud Cloud-Delivered WAN Fast. Simple. Secure. KUHN CONSULTING GmbH
 VeloCloud Cloud-Delivered WAN Fast. Simple. Secure. 1 Agenda 1. Overview and company presentation 2. Solution presentation 3. Main benefits to show to customers 4. Deployment models 2 VeloCloud Company
VeloCloud Cloud-Delivered WAN Fast. Simple. Secure. 1 Agenda 1. Overview and company presentation 2. Solution presentation 3. Main benefits to show to customers 4. Deployment models 2 VeloCloud Company
DATA SHEET AlienVault USM Anywhere Powerful Threat Detection and Incident Response for All Your Critical Infrastructure
 DATA SHEET AlienVault USM Anywhere Powerful Threat Detection and Incident Response for All Your Critical Infrastructure AlienVault USM Anywhere accelerates and centralizes threat detection, incident response,
DATA SHEET AlienVault USM Anywhere Powerful Threat Detection and Incident Response for All Your Critical Infrastructure AlienVault USM Anywhere accelerates and centralizes threat detection, incident response,
DDoS Hybrid Defender. SSL Orchestrator. Comprehensive DDoS protection, tightly-integrated on-premises and cloud
 SSL Orchestrator DDoS Hybrid Defender All-in-one solution designed to deliver increased visibility into encrypted traffic Comprehensive DDoS protection, tightly-integrated on-premises and cloud Converts
SSL Orchestrator DDoS Hybrid Defender All-in-one solution designed to deliver increased visibility into encrypted traffic Comprehensive DDoS protection, tightly-integrated on-premises and cloud Converts
Features. HDX WAN optimization. QoS
 May 2013 Citrix CloudBridge Accelerates, controls and optimizes applications to all locations: datacenter, branch offices, public and private clouds and mobile users Citrix CloudBridge provides a unified
May 2013 Citrix CloudBridge Accelerates, controls and optimizes applications to all locations: datacenter, branch offices, public and private clouds and mobile users Citrix CloudBridge provides a unified
IXIA FLEX TAP TM DATA SHEET PASSIVE NETWORK MONITORING KEY FEATURES HIGHLIGHTS
 IXIA FLEX TAP TM DATA SHEET PASSIVE NETWORK MONITORING The Ixia Flex Tap provide reliable continuous visibility of 100% of network traffic to support performance and security with no network performance
IXIA FLEX TAP TM DATA SHEET PASSIVE NETWORK MONITORING The Ixia Flex Tap provide reliable continuous visibility of 100% of network traffic to support performance and security with no network performance
Compare Security Analytics Solutions
 Compare Security Analytics Solutions Learn how Cisco Stealthwatch compares with other security analytics products. This solution scales easily, giving you visibility across the entire network. Stealthwatch
Compare Security Analytics Solutions Learn how Cisco Stealthwatch compares with other security analytics products. This solution scales easily, giving you visibility across the entire network. Stealthwatch
Cisco SAN Analytics and SAN Telemetry Streaming
 Cisco SAN Analytics and SAN Telemetry Streaming A deeper look at enterprise storage infrastructure The enterprise storage industry is going through a historic transformation. On one end, deep adoption
Cisco SAN Analytics and SAN Telemetry Streaming A deeper look at enterprise storage infrastructure The enterprise storage industry is going through a historic transformation. On one end, deep adoption
Cisco Next Generation Firewall and IPS. Dragan Novakovic Security Consulting Systems Engineer
 Cisco Next Generation Firewall and IPS Dragan Novakovic Security Consulting Systems Engineer Cisco ASA with Firepower services Cisco TALOS - Collective Security Intelligence Enabled Clustering & High Availability
Cisco Next Generation Firewall and IPS Dragan Novakovic Security Consulting Systems Engineer Cisco ASA with Firepower services Cisco TALOS - Collective Security Intelligence Enabled Clustering & High Availability
Network Virtualization Business Case
 SESSION ID: GPS2-R01 Network Virtualization Business Case Arup Deb virtual networking & security VMware NSBU adeb@vmware.com I. Data center security today Don t hate the player, hate the game - Ice T,
SESSION ID: GPS2-R01 Network Virtualization Business Case Arup Deb virtual networking & security VMware NSBU adeb@vmware.com I. Data center security today Don t hate the player, hate the game - Ice T,
A10 SSL INSIGHT & SONICWALL NEXT-GEN FIREWALLS
 DEPLOYMENT GUIDE A10 SSL INSIGHT & SONICWALL NEXT-GEN FIREWALLS A10 NETWORKS SSL INSIGHT & FIREWALL LOAD BALANCING SOLUTION FOR SONICWALL SUPERMASSIVE NEXT GENERATION FIREWALLS OVERVIEW This document describes
DEPLOYMENT GUIDE A10 SSL INSIGHT & SONICWALL NEXT-GEN FIREWALLS A10 NETWORKS SSL INSIGHT & FIREWALL LOAD BALANCING SOLUTION FOR SONICWALL SUPERMASSIVE NEXT GENERATION FIREWALLS OVERVIEW This document describes
Securing Your Amazon Web Services Virtual Networks
 Securing Your Amazon Web Services s IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up a workload,
Securing Your Amazon Web Services s IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up a workload,
PSOACI Tetration Overview. Mike Herbert
 Tetration Overview Mike Herbert Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1. Find this session in the Cisco Live Mobile App 2. Click Join the Discussion
Tetration Overview Mike Herbert Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1. Find this session in the Cisco Live Mobile App 2. Click Join the Discussion
Ixia xstream TM 10. Aggregation, Filtering, and Load Balancing for 1GbE/10GbE Networks. Aggregation and Filtering DATA SHEET
 Ixia xstream TM 10 Aggregation, Filtering, and Load Balancing for 1GbE/10GbE Networks The Ixia xstream 10 is a network packet broker purpose-built for fail-safe inline security tools deployment and out-of-band
Ixia xstream TM 10 Aggregation, Filtering, and Load Balancing for 1GbE/10GbE Networks The Ixia xstream 10 is a network packet broker purpose-built for fail-safe inline security tools deployment and out-of-band
Cisco Tetration Analytics
 Cisco Tetration Analytics Real-time application visibility and policy management using advanced analytics Yogesh Kaushik, Sr. Director Product Management PSOACI-2100 Agenda Market context Introduction:
Cisco Tetration Analytics Real-time application visibility and policy management using advanced analytics Yogesh Kaushik, Sr. Director Product Management PSOACI-2100 Agenda Market context Introduction:
WHITE PAPER A10 SSL INSIGHT & FIREWALL LOAD BALANCING WITH SONICWALL NEXT-GEN FIREWALLS
 WHITE PAPER A10 SSL INSIGHT & FIREWALL LOAD BALANCING WITH SONICWALL NEXT-GEN FIREWALLS TABLE OF CONTENTS EXECUTIVE SUMMARY... 3 INTRODUCTION... 3 SOLUTION REQUIREMENTS... 3 SOLUTION COMPONENTS... 4 SOLUTION
WHITE PAPER A10 SSL INSIGHT & FIREWALL LOAD BALANCING WITH SONICWALL NEXT-GEN FIREWALLS TABLE OF CONTENTS EXECUTIVE SUMMARY... 3 INTRODUCTION... 3 SOLUTION REQUIREMENTS... 3 SOLUTION COMPONENTS... 4 SOLUTION
Cato Cloud. Global SD-WAN with Built-in Network Security. Solution Brief. Cato Cloud Solution Brief. The Future of SD-WAN. Today.
 Cato Cloud Global SD-WAN with Built-in Network Security Solution Brief 1 Legacy WAN and Security Appliances are Incompatible with the Modern Enterprise The rise of cloud applications and mobile workforces
Cato Cloud Global SD-WAN with Built-in Network Security Solution Brief 1 Legacy WAN and Security Appliances are Incompatible with the Modern Enterprise The rise of cloud applications and mobile workforces
SECURING THE NEXT GENERATION DATA CENTER. Leslie K. Lambert Juniper Networks VP & Chief Information Security Officer July 18, 2011
 SECURING THE NEXT GENERATION DATA CENTER Leslie K. Lambert Juniper Networks VP & Chief Information Security Officer July 18, 2011 JUNIPER SECURITY LEADERSHIP Market Leadership Data Center with High-End
SECURING THE NEXT GENERATION DATA CENTER Leslie K. Lambert Juniper Networks VP & Chief Information Security Officer July 18, 2011 JUNIPER SECURITY LEADERSHIP Market Leadership Data Center with High-End
Agile Security Solutions
 Agile Security Solutions Piotr Linke Security Engineer CISSP CISA CRISC CISM Open Source SNORT 2 Consider these guys All were smart. All had security. All were seriously compromised. 3 The Industrialization
Agile Security Solutions Piotr Linke Security Engineer CISSP CISA CRISC CISM Open Source SNORT 2 Consider these guys All were smart. All had security. All were seriously compromised. 3 The Industrialization
Securing Your Microsoft Azure Virtual Networks
 Securing Your Microsoft Azure Virtual Networks IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up
Securing Your Microsoft Azure Virtual Networks IPS security for public cloud deployments It s no surprise that public cloud infrastructure has experienced fast adoption. It is quick and easy to spin up
Design and Deployment of SourceFire NGIPS and NGFWL
 Design and Deployment of SourceFire NGIPS and NGFWL BRKSEC - 2024 Marcel Skjald Consulting Systems Engineer Enterprise / Security Architect Abstract Overview of Session This technical session covers the
Design and Deployment of SourceFire NGIPS and NGFWL BRKSEC - 2024 Marcel Skjald Consulting Systems Engineer Enterprise / Security Architect Abstract Overview of Session This technical session covers the
SEVONE DATA APPLIANCE FOR EUE
 Insight for the Connected World Data Appliance for EUE [ DataSheet ] SEVONE DATA APPLIANCE FOR EUE INSIGHTS FROM THE USER PERSPECTIVE. Software, applications and services running on the network infrastructure
Insight for the Connected World Data Appliance for EUE [ DataSheet ] SEVONE DATA APPLIANCE FOR EUE INSIGHTS FROM THE USER PERSPECTIVE. Software, applications and services running on the network infrastructure
SEVONE END USER EXPERIENCE
 Insight for the Connected World End User Experience [ DataSheet ] SEVONE END USER EXPERIENCE INSIGHTS FROM THE USER PERSPECTIVE. Software, applications and services running on the network infrastructure
Insight for the Connected World End User Experience [ DataSheet ] SEVONE END USER EXPERIENCE INSIGHTS FROM THE USER PERSPECTIVE. Software, applications and services running on the network infrastructure
Ixia Flex Tap PASSIVE NETWORK MONITORING HIGHLIGHTS KEY FEATURES. Data Sheet
 Ixia Flex Tap Data Sheet PASSIVE NETWORK MONITORING The Ixia Flex Tap provide reliable continuous visibility of 100% of network traffic to support performance and security with no network performance degradation
Ixia Flex Tap Data Sheet PASSIVE NETWORK MONITORING The Ixia Flex Tap provide reliable continuous visibility of 100% of network traffic to support performance and security with no network performance degradation
WEBSCALE CONVERGED APPLICATION DELIVERY PLATFORM
 SECURITY ANALYTICS WEBSCALE CONVERGED APPLICATION DELIVERY PLATFORM BLAZING PERFORMANCE, HIGH AVAILABILITY AND ROBUST SECURITY FOR YOUR CRITICAL WEB APPLICATIONS OVERVIEW Webscale is a converged multi-cloud
SECURITY ANALYTICS WEBSCALE CONVERGED APPLICATION DELIVERY PLATFORM BLAZING PERFORMANCE, HIGH AVAILABILITY AND ROBUST SECURITY FOR YOUR CRITICAL WEB APPLICATIONS OVERVIEW Webscale is a converged multi-cloud
CloudStorm TM 100GE Application and Security Test Load Module
 CloudStorm TM 100GE Application and Security Test Load Module CLOUD-SCALE APPLICATION DELIVERY & NETWORK SECURITY TEST PLATFORM PROBLEM: AN ALL-ENCRYPTED WORLD AND INCREASING USER EXPERIENCE EXPECTATIONS
CloudStorm TM 100GE Application and Security Test Load Module CLOUD-SCALE APPLICATION DELIVERY & NETWORK SECURITY TEST PLATFORM PROBLEM: AN ALL-ENCRYPTED WORLD AND INCREASING USER EXPERIENCE EXPECTATIONS
ARIA SDS. Application
 ARIA SDS Packet Intelligence Application CSPi s ARIA SDS Packet Intelligence (PI) application enhances an organization s existing network security capabilities by enabling the monitoring of all network
ARIA SDS Packet Intelligence Application CSPi s ARIA SDS Packet Intelligence (PI) application enhances an organization s existing network security capabilities by enabling the monitoring of all network
The Next Generation Security Platform. Domenico Stranieri Pre- Sales Engineer Palo Alto Networks EMEA Italy
 The Next Generation Security Platform Domenico Stranieri Pre- Sales Engineer Palo Alto Networks EMEA Italy The Next Generation Enterprise Security Platform Core Value Proposition An Enterprise Security
The Next Generation Security Platform Domenico Stranieri Pre- Sales Engineer Palo Alto Networks EMEA Italy The Next Generation Enterprise Security Platform Core Value Proposition An Enterprise Security
SINGLEstream Link Aggregation Tap (SS-100)
 SINGLEstream Link Aggregation Tap (SS-00) Optional 3-Unit Rack Mount Datacom Systems SINGLEstream 0/00 Link Aggregation Tap provides a superior solution for 4x7 monitoring of full-duplex Ethernet links.
SINGLEstream Link Aggregation Tap (SS-00) Optional 3-Unit Rack Mount Datacom Systems SINGLEstream 0/00 Link Aggregation Tap provides a superior solution for 4x7 monitoring of full-duplex Ethernet links.
Subscriber Data Correlation
 Subscriber Data Correlation Application of Cisco Stealthwatch to Service Provider mobility environment Introduction With the prevalence of smart mobile devices and the increase of application usage, Service
Subscriber Data Correlation Application of Cisco Stealthwatch to Service Provider mobility environment Introduction With the prevalence of smart mobile devices and the increase of application usage, Service
Ixia Net Optics Flex Tap TM
 Ixia Net Optics Flex Tap TM Key Features The Ixia Net Optics Flex Tap family delivers total traffic visibility for network monitoring and security tools. Deploying these network taps on any network link
Ixia Net Optics Flex Tap TM Key Features The Ixia Net Optics Flex Tap family delivers total traffic visibility for network monitoring and security tools. Deploying these network taps on any network link
A10 HARMONY CONTROLLER
 DATA SHEET A10 HARMONY CONTROLLER AGILE MANAGEMENT, AUTOMATION, ANALYTICS FOR MULTI-CLOUD ENVIRONMENTS PLATFORMS A10 Harmony Controller provides centralized agile management, automation and analytics for
DATA SHEET A10 HARMONY CONTROLLER AGILE MANAGEMENT, AUTOMATION, ANALYTICS FOR MULTI-CLOUD ENVIRONMENTS PLATFORMS A10 Harmony Controller provides centralized agile management, automation and analytics for
NSG100 Nebula Cloud Managed Security Gateway
 Managed Security Gateway The Zyxel Nebula Cloud Managed Security Gateway is built with remote management and ironclad security for organizations with growing numbers of distributed sites. With the extensive
Managed Security Gateway The Zyxel Nebula Cloud Managed Security Gateway is built with remote management and ironclad security for organizations with growing numbers of distributed sites. With the extensive
SONICWALL GLOBAL MANAGEMENT SYSTEM
 SONICWALL GLOBAL MANAGEMENT SYSTEM Comprehensive security management, monitoring, reporting and analytics A winning security management strategy demands deep understanding of the security environment to
SONICWALL GLOBAL MANAGEMENT SYSTEM Comprehensive security management, monitoring, reporting and analytics A winning security management strategy demands deep understanding of the security environment to
Automate Application Deployment with F5 Local Traffic Manager and Cisco Application Centric Infrastructure
 Automate Application Deployment with F5 Local Traffic Manager and Cisco Application Centric Infrastructure White Paper 2016 Cisco F5 Networks. All rights reserved. Page 1 Contents What You Will Learn...
Automate Application Deployment with F5 Local Traffic Manager and Cisco Application Centric Infrastructure White Paper 2016 Cisco F5 Networks. All rights reserved. Page 1 Contents What You Will Learn...
Big Tap Monitoring Fabric Pervasive Network Visibility at Ultra Low Cost Release Version 4.1.0
 Big Tap Monitoring Fabric Pervasive Network Visibility at Ultra Low Cost Release Version 4.1.0 Big Tap Monitoring Fabric enables monitoring of network traffic of an organization s entire network and selectively
Big Tap Monitoring Fabric Pervasive Network Visibility at Ultra Low Cost Release Version 4.1.0 Big Tap Monitoring Fabric enables monitoring of network traffic of an organization s entire network and selectively
SYMANTEC DATA CENTER SECURITY
 SYMANTEC DATA CENTER SECURITY SYMANTEC UNIFIED SECURITY STRATEGY Users Cyber Security Services Monitoring, Incident Response, Simulation, Adversary Threat Intelligence Data Threat Protection Information
SYMANTEC DATA CENTER SECURITY SYMANTEC UNIFIED SECURITY STRATEGY Users Cyber Security Services Monitoring, Incident Response, Simulation, Adversary Threat Intelligence Data Threat Protection Information
Cyber Security at large scale
 Cyber Security & Data Summit June 18 Cyber Security at large scale www.telesoft-technologies.com copyright 2017 by Telesoft Technologies. All rights reserved. Agenda Telesoft Introduction Large scale Challenges
Cyber Security & Data Summit June 18 Cyber Security at large scale www.telesoft-technologies.com copyright 2017 by Telesoft Technologies. All rights reserved. Agenda Telesoft Introduction Large scale Challenges
McAfee Network Security Platform
 McAfee Network Security Platform 9.2 (Quick Tour) McAfee Network Security Platform [formerly McAfee IntruShield ] is a combination of network appliances and software that accurately detects and prevents
McAfee Network Security Platform 9.2 (Quick Tour) McAfee Network Security Platform [formerly McAfee IntruShield ] is a combination of network appliances and software that accurately detects and prevents
Application Performance Troubleshooting
 KNOW YOUR NETWORK DATA SHEET Application Performance Troubleshooting From Flows to Conversations Overview In order to guarantee the performance of business applications, enterprise IT organizations need
KNOW YOUR NETWORK DATA SHEET Application Performance Troubleshooting From Flows to Conversations Overview In order to guarantee the performance of business applications, enterprise IT organizations need
The threat landscape is constantly
 A PLATFORM-INDEPENDENT APPROACH TO SECURE MICRO-SEGMENTATION Use Case Analysis The threat landscape is constantly evolving. Data centers running business-critical workloads need proactive security solutions
A PLATFORM-INDEPENDENT APPROACH TO SECURE MICRO-SEGMENTATION Use Case Analysis The threat landscape is constantly evolving. Data centers running business-critical workloads need proactive security solutions
Sichere Applikations- dienste
 Sichere Applikations- dienste Innovate, Expand, Deliver Manny Rivelo Für SaaS und traditionelle Service-Modelle EVP, Strategic Solutions Carsten Langerbein Field Systems Engineer c.langerbein@f5.com Es
Sichere Applikations- dienste Innovate, Expand, Deliver Manny Rivelo Für SaaS und traditionelle Service-Modelle EVP, Strategic Solutions Carsten Langerbein Field Systems Engineer c.langerbein@f5.com Es
Next Generation Hybrid Network Visibility Solution
 Next Generation Hybrid Network Visibility Solution Series 4000 Platform APCON s Series 4000 platform is designed to grow and accommodate unprecedented levels of bandwidth and enable network visibility
Next Generation Hybrid Network Visibility Solution Series 4000 Platform APCON s Series 4000 platform is designed to grow and accommodate unprecedented levels of bandwidth and enable network visibility
Seceon s Open Threat Management software
 Seceon s Open Threat Management software Seceon s Open Threat Management software (OTM), is a cyber-security advanced threat management platform that visualizes, detects, and eliminates threats in real
Seceon s Open Threat Management software Seceon s Open Threat Management software (OTM), is a cyber-security advanced threat management platform that visualizes, detects, and eliminates threats in real
SteelConnect. The Future of Networking is here. It s Application- Defined for the Cloud Era. SD-WAN Cloud Networks Branch LAN/WLAN
 Data Sheet SteelConnect The Future of Networking is here. It s Application- Defined for the Cloud Era. SD-WAN Cloud Networks Branch LAN/WLAN The Business Challenge Delivery of applications is becoming
Data Sheet SteelConnect The Future of Networking is here. It s Application- Defined for the Cloud Era. SD-WAN Cloud Networks Branch LAN/WLAN The Business Challenge Delivery of applications is becoming
Cloud, SDN and BIGIQ. Philippe Bogaerts Senior Field Systems Engineer
 Cloud, SDN and BIGIQ Philippe Bogaerts Senior Field Systems Engineer Virtual Editions TMOS/LTM 12.0 Highlights 1 NIC support Azure Marketplace Kernel Independent driver Enhanced Hypervisor support F5 Networks,
Cloud, SDN and BIGIQ Philippe Bogaerts Senior Field Systems Engineer Virtual Editions TMOS/LTM 12.0 Highlights 1 NIC support Azure Marketplace Kernel Independent driver Enhanced Hypervisor support F5 Networks,
IXIA IBYPASS HD DATA SHEET PROBLEM: INLINE TOOLS ARE A SINGLE POINT OF FAILURE IN THE NETWORK
 IXIA IBYPASS HD DATA SHEET PROBLEM: INLINE TOOLS ARE A SINGLE POINT OF FAILURE IN THE NETWORK Today s organizations are facing a triad of network concerns: the increasing volume of multiprotocol traffic
IXIA IBYPASS HD DATA SHEET PROBLEM: INLINE TOOLS ARE A SINGLE POINT OF FAILURE IN THE NETWORK Today s organizations are facing a triad of network concerns: the increasing volume of multiprotocol traffic
The Gigamon Visibility Platform
 The Gigamon Visibility Platform See what matters. Andrea Baraldi - Sales Engineer Marco Romagnoli Sales Director 1 Safe Harbor Statement Any forward-looking indication of plans for products is preliminary
The Gigamon Visibility Platform See what matters. Andrea Baraldi - Sales Engineer Marco Romagnoli Sales Director 1 Safe Harbor Statement Any forward-looking indication of plans for products is preliminary
NSG50/100/200 Nebula Cloud Managed Security Gateway
 NSG50/100/200 Managed The Zyxel Managed is built with remote management and ironclad security for organizations with growing numbers of distributed sites. With the extensive suite of security features
NSG50/100/200 Managed The Zyxel Managed is built with remote management and ironclad security for organizations with growing numbers of distributed sites. With the extensive suite of security features
Beyond Blind Defense: Gaining Insights from Proactive App Sec
 Beyond Blind Defense: Gaining Insights from Proactive App Sec Speaker Rami Essaid CEO Distil Networks Blind Defense Means Trusting Half Your Web Traffic 46% of Web Traffic is Bots Source: Distil Networks
Beyond Blind Defense: Gaining Insights from Proactive App Sec Speaker Rami Essaid CEO Distil Networks Blind Defense Means Trusting Half Your Web Traffic 46% of Web Traffic is Bots Source: Distil Networks
SIEM Solutions from McAfee
 SIEM Solutions from McAfee Monitor. Prioritize. Investigate. Respond. Today s security information and event management (SIEM) solutions need to be able to identify and defend against attacks within an
SIEM Solutions from McAfee Monitor. Prioritize. Investigate. Respond. Today s security information and event management (SIEM) solutions need to be able to identify and defend against attacks within an
WIND RIVER TITANIUM CLOUD FOR TELECOMMUNICATIONS
 WIND RIVER TITANIUM CLOUD FOR TELECOMMUNICATIONS Carrier networks are undergoing their biggest transformation since the beginning of the Internet. The ability to get to market quickly and to respond to
WIND RIVER TITANIUM CLOUD FOR TELECOMMUNICATIONS Carrier networks are undergoing their biggest transformation since the beginning of the Internet. The ability to get to market quickly and to respond to
BUILDING A NEXT-GENERATION FIREWALL
 How to Add Network Intelligence, Security, and Speed While Getting to Market Faster INNOVATORS START HERE. EXECUTIVE SUMMARY Your clients are on the front line of cyberspace and they need your help. Faced
How to Add Network Intelligence, Security, and Speed While Getting to Market Faster INNOVATORS START HERE. EXECUTIVE SUMMARY Your clients are on the front line of cyberspace and they need your help. Faced
Data Center Security. Fuat KILIÇ Consulting Systems
 Data Center Security Fuat KILIÇ Consulting Systems Engineer @Security Data Center Evolution WHERE ARE YOU NOW? WHERE DO YOU WANT TO BE? Traditional Data Center Virtualized Data Center (VDC) Virtualized
Data Center Security Fuat KILIÇ Consulting Systems Engineer @Security Data Center Evolution WHERE ARE YOU NOW? WHERE DO YOU WANT TO BE? Traditional Data Center Virtualized Data Center (VDC) Virtualized
Trends and challenges Managing the performance of a large-scale network was challenging enough when the infrastructure was fairly static. Now, with Ci
 Solution Overview SevOne SDN Monitoring Solution 2.0: Automate the Operational Insight of Cisco ACI Based Infrastructure What if you could automate the operational insight of your Cisco Application Centric
Solution Overview SevOne SDN Monitoring Solution 2.0: Automate the Operational Insight of Cisco ACI Based Infrastructure What if you could automate the operational insight of your Cisco Application Centric
Copyright 2011 Trend Micro Inc.
 Copyright 2011 Trend Micro Inc. 2008Q1 2008Q2 2008Q3 2008Q4 2009Q1 2009Q2 2009Q3 2009Q4 2010Q1 2010Q2 2010Q3 2010Q4 2011Q1 2011Q2 2011Q3 2011Q4 M'JPY Cloud Security revenue Q to Q Growth DeepSecurity/Hosted/CPVM/IDF
Copyright 2011 Trend Micro Inc. 2008Q1 2008Q2 2008Q3 2008Q4 2009Q1 2009Q2 2009Q3 2009Q4 2010Q1 2010Q2 2010Q3 2010Q4 2011Q1 2011Q2 2011Q3 2011Q4 M'JPY Cloud Security revenue Q to Q Growth DeepSecurity/Hosted/CPVM/IDF
Hardening the Education. with NGFW. Narongveth Yutithammanurak Business Development Manager 23 Feb 2012
 Hardening the Education IT Environment with NGFW Narongveth Yutithammanurak Business Development Manager 23 Feb 2012 Technology Trends Security Performance Bandwidth Efficiency Manageability Page 2 What
Hardening the Education IT Environment with NGFW Narongveth Yutithammanurak Business Development Manager 23 Feb 2012 Technology Trends Security Performance Bandwidth Efficiency Manageability Page 2 What
Exploring Cloud Security, Operational Visibility & Elastic Datacenters. Kiran Mohandas Consulting Engineer
 Exploring Cloud Security, Operational Visibility & Elastic Datacenters Kiran Mohandas Consulting Engineer The Ideal Goal of Network Access Policies People (Developers, Net Ops, CISO, ) V I S I O N Provide
Exploring Cloud Security, Operational Visibility & Elastic Datacenters Kiran Mohandas Consulting Engineer The Ideal Goal of Network Access Policies People (Developers, Net Ops, CISO, ) V I S I O N Provide
VMworld disclaimer This presentation may contain product features that are currently under development. This overview of new technology represents no
 LHC3296BUS OVH: Shields Up! Building a True Security Barrier in the Cloud Chris Romano, Principal Systems Engineer #VMworld #LHC3296BUS VMworld disclaimer This presentation may contain product features
LHC3296BUS OVH: Shields Up! Building a True Security Barrier in the Cloud Chris Romano, Principal Systems Engineer #VMworld #LHC3296BUS VMworld disclaimer This presentation may contain product features
CISCO NETWORKS BORDERLESS Cisco Systems, Inc. All rights reserved. 1
 CISCO BORDERLESS NETWORKS 2009 Cisco Systems, Inc. All rights reserved. 1 Creating New Business Models The Key Change: Putting the Interaction Where the Customer Is Customer Experience/ Innovation Productivity/
CISCO BORDERLESS NETWORKS 2009 Cisco Systems, Inc. All rights reserved. 1 Creating New Business Models The Key Change: Putting the Interaction Where the Customer Is Customer Experience/ Innovation Productivity/
Enhanced Threat Detection, Investigation, and Response
 Enhanced Threat Detection, Investigation, and Response What s new in Cisco Stealthwatch Enterprise Release 6.10.2 Cisco Stealthwatch Enterprise is a comprehensive visibility and security analytics solution
Enhanced Threat Detection, Investigation, and Response What s new in Cisco Stealthwatch Enterprise Release 6.10.2 Cisco Stealthwatch Enterprise is a comprehensive visibility and security analytics solution
Version 1.24 Installation Guide for On-Premise Uila Deployment Hyper-V
 Version 1.24 Installation Guide for On-Premise Uila Deployment Hyper-V Table of Contents Introduction... 2 Scope and Purpose... 2 Architecture Overview... 2 Virtual Architecture... 2 Getting Started...
Version 1.24 Installation Guide for On-Premise Uila Deployment Hyper-V Table of Contents Introduction... 2 Scope and Purpose... 2 Architecture Overview... 2 Virtual Architecture... 2 Getting Started...
Cisco Stealthwatch Improves Threat Defense with Network Visibility and Security Analytics
 Solution Overview Cisco Stealthwatch Improves Threat Defense with Network Visibility and Security Analytics BENEFITS Gain visibility across all network conversations, including east-west and north-south
Solution Overview Cisco Stealthwatch Improves Threat Defense with Network Visibility and Security Analytics BENEFITS Gain visibility across all network conversations, including east-west and north-south
Cisco HyperFlex and the F5 BIG-IP Platform Accelerate Infrastructure and Application Deployments
 OVERVIEW + Cisco and the F5 BIG-IP Platform Accelerate Infrastructure and Application Deployments KEY BENEFITS Quickly create private clouds Tested with industry-leading BIG-IP ADC platform Easily scale
OVERVIEW + Cisco and the F5 BIG-IP Platform Accelerate Infrastructure and Application Deployments KEY BENEFITS Quickly create private clouds Tested with industry-leading BIG-IP ADC platform Easily scale
JURUMANI MERAKI CLOUD MANAGED SECURITY & SD-WAN
 JURUMANI CLOUD MANAGED SECURITY & SD-WAN SECURITY BY DESIGN OVERVIEW Cisco Meraki MX Security Appliances are ideal for organizations considering a Unified Threat Managment (UTM) solution, for distributed
JURUMANI CLOUD MANAGED SECURITY & SD-WAN SECURITY BY DESIGN OVERVIEW Cisco Meraki MX Security Appliances are ideal for organizations considering a Unified Threat Managment (UTM) solution, for distributed
McAfee Network Security Platform 9.2
 McAfee Network Security Platform 9.2 (9.2.7.22-9.2.7.20 Manager-Virtual IPS Release Notes) Contents About this release New features Enhancements Resolved issues Installation instructions Known issues Product
McAfee Network Security Platform 9.2 (9.2.7.22-9.2.7.20 Manager-Virtual IPS Release Notes) Contents About this release New features Enhancements Resolved issues Installation instructions Known issues Product
FlowMagic-3200 Next Generation Scale Out and Scale Up Traffic Visibility, Archiving and Data Mining Appliance
 HARDWARE DATASHEET FlowMagic-3200 Next Generation Scale Out and Scale Up Traffic Visibility, Archiving and Data Mining Appliance FlowMagic Product Family Overview As networks, applications and services
HARDWARE DATASHEET FlowMagic-3200 Next Generation Scale Out and Scale Up Traffic Visibility, Archiving and Data Mining Appliance FlowMagic Product Family Overview As networks, applications and services
Cloud-Managed Security for Distributed Networks with Cisco Meraki MX
 Cloud-Managed Security for Distributed Networks with Cisco Meraki MX Joe Aronow, Product Architect Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1. Find this
Cloud-Managed Security for Distributed Networks with Cisco Meraki MX Joe Aronow, Product Architect Cisco Spark How Questions? Use Cisco Spark to communicate with the speaker after the session 1. Find this
SOLUTION BRIEF: AN END-TO-END DATA CENTER MONITORING SOLUTION VISIT
 SOLUTION BRIEF: AN END-TO-END DATA CENTER MONITORING SOLUTION VISIT WWW.PROFITAP.COM Flowmon and Profitap s joint solution offers the most efficient end-toend monitoring platform you can get for a high-speed
SOLUTION BRIEF: AN END-TO-END DATA CENTER MONITORING SOLUTION VISIT WWW.PROFITAP.COM Flowmon and Profitap s joint solution offers the most efficient end-toend monitoring platform you can get for a high-speed
What s next for your data center? Power Your Evolution with Physical and Virtual ADCs. Jeppe Koefoed Wim Zandee Field sales, Nordics
 What s next for your data center? Power Your Evolution with Physical and Virtual ADCs. Jeppe Koefoed Wim Zandee Field sales, Nordics Vision: Everything as a service Speed Scalability Speed to Market
What s next for your data center? Power Your Evolution with Physical and Virtual ADCs. Jeppe Koefoed Wim Zandee Field sales, Nordics Vision: Everything as a service Speed Scalability Speed to Market
Business Strategy Theatre
 Business Strategy Theatre Security posture in the age of mobile, social and new threats Steve Pao, GM Security Business 01 May 2014 In the midst of chaos, there is also opportunity. - Sun-Tzu Security:
Business Strategy Theatre Security posture in the age of mobile, social and new threats Steve Pao, GM Security Business 01 May 2014 In the midst of chaos, there is also opportunity. - Sun-Tzu Security:
WITH ACTIVEWATCH EXPERT BACKED, DETECTION AND THREAT RESPONSE BENEFITS HOW THREAT MANAGER WORKS SOLUTION OVERVIEW:
 SOLUTION OVERVIEW: ALERT LOGIC THREAT MANAGER WITH ACTIVEWATCH EXPERT BACKED, DETECTION AND THREAT RESPONSE Protecting your business assets and sensitive data requires regular vulnerability assessment,
SOLUTION OVERVIEW: ALERT LOGIC THREAT MANAGER WITH ACTIVEWATCH EXPERT BACKED, DETECTION AND THREAT RESPONSE Protecting your business assets and sensitive data requires regular vulnerability assessment,
Data Sheet GigaSECURE Cloud
 Data Sheet GigaSECURE Cloud Intelligent network traffic visibility that enables enterprises to extend their security posture to Microsoft The rapid evolution of Infrastructure-as-a-Service (IaaS) brings
Data Sheet GigaSECURE Cloud Intelligent network traffic visibility that enables enterprises to extend their security posture to Microsoft The rapid evolution of Infrastructure-as-a-Service (IaaS) brings
SOLUTION BRIEF EXTREMEWIRELESS WiNG AZARA AZARA. WiNG RISE TO THE CHALLENGE OF PROVIDING SUPERIOR CONNECTIVITY & WLAN MANAGEMENT
 SOLUTION BRIEF WiNG AZARA RISE TO THE CHALLENGE OF PROVIDING SUPERIOR CONNECTIVITY & WLAN MANAGEMENT Freedom from the unpredictability of providing connectivity Today, mobile devices outnumber the total
SOLUTION BRIEF WiNG AZARA RISE TO THE CHALLENGE OF PROVIDING SUPERIOR CONNECTIVITY & WLAN MANAGEMENT Freedom from the unpredictability of providing connectivity Today, mobile devices outnumber the total
SSL INSIGHT SSL ENCRYPTION CHALLENGES SSL USE EXPOSES A BLIND SPOT IN CORPORATE DEFENSES SOLUTION BRIEF UNCOVER HIDDEN THREATS IN ENCRYPTED TRAFFIC
 SOLUTION BRIEF UNCOVER HIDDEN THREATS IN ENCRYPTED TRAFFIC SSL ENCRYPTION CHALLENGES To prevent attacks, intrusions and malware, enterprises need to inspect incoming and outgoing traffic for threats. Unfortunately,
SOLUTION BRIEF UNCOVER HIDDEN THREATS IN ENCRYPTED TRAFFIC SSL ENCRYPTION CHALLENGES To prevent attacks, intrusions and malware, enterprises need to inspect incoming and outgoing traffic for threats. Unfortunately,
SD-WAN Deployment Guide (CVD)
 SD-WAN Deployment Guide (CVD) All Cisco Meraki security appliances are equipped with SD-WAN capabilities that enable administrators to maximize network resiliency and bandwidth efficiency. This guide introduces
SD-WAN Deployment Guide (CVD) All Cisco Meraki security appliances are equipped with SD-WAN capabilities that enable administrators to maximize network resiliency and bandwidth efficiency. This guide introduces
