IXIA VISIBILITY ARCHITECTURE Eliminating Blind spots
|
|
|
- Robyn Loreen Rodgers
- 6 years ago
- Views:
Transcription
1 IXIA VISIBILITY ARCHITECTURE Eliminating Blind spots Юлий Явич, IXIA 1
2 Enterprise Carriers/ Service Providers of the Fortune 100 of the top 50 carriers of the top 15 NEMs NEMs Customer Focused Innovation 2014 Industry-first ATI security solution 2014 Industry-first virtual tap 2014 Industry-first 400GbE test solution 2
3 IXIA SOLUTION PORTFOLIO TEST SECURITY VISIBILITY Across the Infrastructure Mobile Endpoint Network Data Center Cloud Across ALL Platforms IxNetwork/VE Multis SDN PerfectStorm BPS vepc IxLoad/VE ac, MU-MIMO 3 Flex Taps, ibypass, Virtual Taps NTO, Vision ONE, Hawkeye, xstream40, Control Tower Threat ARMOR, ATI
4 INTELLIGENT VISIBILITY 6
5 INTELLIGENT VISIBILITY - CHALLENGES How to: Get data access for tools? Network taps instead of SPAN ports? Tool 1 Tool 2 Tool N How to: Deal with limited tool ports? Scale tool capacity? Filter traffic to tools? Manage access for each tool? Clients Network Tap Switch Network Tap Switch Network Tap Server 7
6 INTELLIGENT VISIBILITY End-to-End Data Access and Distribution Taps Switch Network Packet Brokers 1G Network Operations Application Operations Taps Switch Taps Servers Aggregation Filtering Load Balancing SSL Decryption NetFlow 10G 40G Security Admin Forensics THE DATA CENTER 8
7 APPLICATIONS AND NETWORK PERFORMANCE TOOLS 9
8 SECURITY TOOLS 10
9 INTELLIGENT PACKET PROCESSING Advanced Packet Processing (AFM) Features Deduplication Header stripping Trimming Tunnel Termination Data Masking Timestamping Burst Protection NPB Adv. Packet Processing Hardware AFM All unique frames going to /8 Only the first 128 bytes of TCP Port 25 frames 13
10 ENTERPRISE INTELLIGENT APPLICATION PROCESSING Meta Data All traffic from Georgia NPB App Brokering App Filtering All voice traffic from HTC Ones Someone from remote office Skype for business monitor ATI Processor (ATIP) - Context-rich Application Visibility Application forwarding based on application, geography, and RegEx matching Real-time dashboard Rich NetFlow / IPFIX generation Device OS Browser Carrier BGP AS# Geolocation Data Masking Stateful SSL decryption 21
11 ATIP ENABLES SSL INSIGHT Passive decryption no impact on application performance Fully compatible with all other ATIP features: Rich Netflow/IPFIX Application Filtering Data Masking Geolocation Handset/workstation type Browser identification Easy setup just import server certificate & key All popular key exchange & ciphers: RSA & DH Key Exchange SHA1/521/384/256/224 MD5 3DES RC4 AES ECC (Elliptic Curve) Encryption details reported over Netflow Hardware Encryption Offload 26
12 SPY GLASS ACTIVE SSL 27
13 NTO FAMILY NTO 7300 Vision ONE 48x1/10G & 4x40G Advanced Features ATI Processor > Application layer filtering > SSL Encryption > Netflow Generation Inline Support Load Balancing GUI 1/10/40/100G Interfaces Advanced Features ATI Processor > Application layer filtering > SSL Encryption > Netflow Generation Packet Capture Load Balancing GUI 28
14 FULL DUPLEX COPPER TAP General Features > Full Duplex Mode > Passes all traffic (including errors) from all layers for comprehensive Troubleshooting > Regeneration TAP > No IP address is needed > Redundant power ensures monitoring uptime TX RX Network A TX Mon A TX Mon B Network B RX TX TP-CU3; TP-CU3-ZD 31
15 IXIA FLEXTAP - 1G/10G/40G/100G (LR & ER) > Single Mode with LC Connector - 1G (SX) > Multi Mode with LC Connector - 10G (SR) > Multi Mode with LC Connector - 40G (SR4 / Cisco Bidi/ MR4) - 100G (SR10) > Multi Mode with MTP Connector 32
16 GETTING VIRTUAL TRAFFIC TO MONITORING TOOLS 34
17 CUSTOMER CASE STUDY International Bank Customer Leading International Bank Need Massive volumes or raw application traffic to monitor Control traffic inspection costs Improve overall Incident Response Team effectiveness Results Deployed Ixia Intelligent Visibility solutions including NTO 7300 Reduced monitored traffic using advanced filters of deduplication, packet slicing, IPs, VLANs VLAN marking and Time stamping to monitoring tools Reduced planned CapEx investments 38
18 CUSTOMER CASE STUDY Large Hi-tech Company Customer Large L2/3 manufacturer Need Control traffic inspection costs Layer 7 filtering to Nectar tool Results Deployed Ixia Intelligent Visibility solution including Vision One Reduced monitored traffic using deduplication Provided Skype for business specific traffic to Nectar tool Reduced planned CapEx investments 39
19 TECHNOLOGY ECOSYSTEM Solution Overview TrafficREWIND is a unique patent pending solution that uses NetFlow metadata to regenerate the dynamics of production networks within BreakingPoint test beds 40
20 RESILIENT SECURITY 42
21 RESILIENT SECURITY Serial Deployments of Inline Security Tools is Dangerous Switch Switch Server Switch Switch Server Very complex operationally Single points of failure Administrative tension Expensive to scale 43
22 RESILIENT SECURITY A More Detailed View of a Resilient Security Framework Out of Band Sandboxing Threat Intelligence Gateway Inline Security Tool Farm Inline Security Tool Farm Network Packet Brokers (HA) Switch Bypass Switch Switch Server Switch Bypass Switch Switch Server 44 Monitored Tool Links via Heartbeat Packets
23 INLINE & MONITORING TOGETHER Inline Monitoring Inline IPS (multiple vendors) Out-of-band Monitoring Data logging 46
24 WORLD-CLASS GLOBAL SUPPORT Expert team of >100 engineers Always-on 24x7 coverage Best-in-class support tools Proven track record of superior support 49
25 WE MAKE APPLICATIONS STRONGER 50
IXVISION: VISIBILITY ARCHITECTURE Eliminating Blind spots
 IXVISION: VISIBILITY ARCHITECTURE Eliminating Blind spots Ernst Hillerkus, Regional Sales Manager Germany 2016 IXIA AN D /OR IT S AF FILIATES. ALL R IGH TS R ESERVED. 1 IXIA SOLUTIONS ARCHITECTURE IxTEST
IXVISION: VISIBILITY ARCHITECTURE Eliminating Blind spots Ernst Hillerkus, Regional Sales Manager Germany 2016 IXIA AN D /OR IT S AF FILIATES. ALL R IGH TS R ESERVED. 1 IXIA SOLUTIONS ARCHITECTURE IxTEST
Daten-Management & Sicherheit in virtualisierten Umgebungen und der Cloud. Martin Heinzelmann SR CHANNEL SE
 Daten-Management & Sicherheit in virtualisierten Umgebungen und der Cloud Martin Heinzelmann SR CHANNEL SE 1 IXIA IS NOW A PART OF KEYSIGHT TECHNOLOGIES Ixia Network Visibility Leader Turnkey Platform
Daten-Management & Sicherheit in virtualisierten Umgebungen und der Cloud Martin Heinzelmann SR CHANNEL SE 1 IXIA IS NOW A PART OF KEYSIGHT TECHNOLOGIES Ixia Network Visibility Leader Turnkey Platform
Seminar: IT Security Design der neuen Art 2016 IXIA AND/OR ITS AFFILIATES. ALL RIGHTS RESERVED.
 Seminar: IT Security Design der neuen Art 1 OUR HISTORY AND COMPETENCE Anue Systems: > Network Visibility: > Packet Brokers (NTO) > Network Testing: > Impairment Generator 2002 June 2012 1996 Oct. 2013
Seminar: IT Security Design der neuen Art 1 OUR HISTORY AND COMPETENCE Anue Systems: > Network Visibility: > Packet Brokers (NTO) > Network Testing: > Impairment Generator 2002 June 2012 1996 Oct. 2013
VISION ONE: SECURITY WITHOUT SACRIFICE
 VISION ONE: SECURITY WITHOUT SACRIFICE DATA SHEET Amplify your security without changing a cable. Vision ONE provides IT Operations the ability to deploy resources where they are needed most and secure
VISION ONE: SECURITY WITHOUT SACRIFICE DATA SHEET Amplify your security without changing a cable. Vision ONE provides IT Operations the ability to deploy resources where they are needed most and secure
VISION ONE: SECURITY WITHOUT SACRIFICE
 VISION ONE: SECURITY WITHOUT SACRIFICE DATA SHEET Amplify your security without changing a cable. Vision ONE provides IT Operations the ability to deploy resources where they are needed most and secure
VISION ONE: SECURITY WITHOUT SACRIFICE DATA SHEET Amplify your security without changing a cable. Vision ONE provides IT Operations the ability to deploy resources where they are needed most and secure
NETWORK VISIBILITY NETWORK PACKET BROKER COMPARISON TABLE KEY VISIBILITY ATTRIBUTES SYSTEM SPECIFICATIONS SYSTEM CAPACITY.
 NETWORK VISIBILITY NETWORK PACKET BROKER COMPARISON TABLE KEY VISIBILITY ATTRIBUTES Smart Drag and Drop Intuitive GUI Zero-Packet Loss Architecture Unlimited Simultaneous Advanced Features Overlapping
NETWORK VISIBILITY NETWORK PACKET BROKER COMPARISON TABLE KEY VISIBILITY ATTRIBUTES Smart Drag and Drop Intuitive GUI Zero-Packet Loss Architecture Unlimited Simultaneous Advanced Features Overlapping
NETWORK VISIBILITY NETWORK PACKET BROKER COMPARISON TABLE
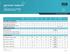 NETWORK VISIBILITY NETWORK PACKET BROKER COMPARISON TABLE Edge Edge Edge Edge Trade KEY VISIBILITY ATTRIBUTES Smart Drag and Drop Intuitive GUI Zero-Packet Loss Architecture Overlapping Filter Rules Automatically
NETWORK VISIBILITY NETWORK PACKET BROKER COMPARISON TABLE Edge Edge Edge Edge Trade KEY VISIBILITY ATTRIBUTES Smart Drag and Drop Intuitive GUI Zero-Packet Loss Architecture Overlapping Filter Rules Automatically
Ixia xstream TM 10. Aggregation, Filtering, and Load Balancing for 1GbE/10GbE Networks. Aggregation and Filtering DATA SHEET
 Ixia xstream TM 10 Aggregation, Filtering, and Load Balancing for 1GbE/10GbE Networks The Ixia xstream 10 is a network packet broker purpose-built for fail-safe inline security tools deployment and out-of-band
Ixia xstream TM 10 Aggregation, Filtering, and Load Balancing for 1GbE/10GbE Networks The Ixia xstream 10 is a network packet broker purpose-built for fail-safe inline security tools deployment and out-of-band
Rethinking Security: The Need For A Security Delivery Platform
 Rethinking Security: The Need For A Security Delivery Platform Cybercrime In Asia: A Changing Environment & Shifting Focus Asia, more vulnerable to cybercrime because of diversity and breadth of countries
Rethinking Security: The Need For A Security Delivery Platform Cybercrime In Asia: A Changing Environment & Shifting Focus Asia, more vulnerable to cybercrime because of diversity and breadth of countries
VISIBILITY INTO CLOUD COMPUTING
 VISIBILITY INTO CLOUD COMPUTING Brendan Leitch, Head of APAC Marketing 1 SECURITY AND PERFORMANCE DEPENDS ON DATA VISIBILITY Access Challenges: Get data access for tools VISIBILITY: Seeing the Traffic
VISIBILITY INTO CLOUD COMPUTING Brendan Leitch, Head of APAC Marketing 1 SECURITY AND PERFORMANCE DEPENDS ON DATA VISIBILITY Access Challenges: Get data access for tools VISIBILITY: Seeing the Traffic
SINGLEstream Link Aggregation Tap (SS-100)
 SINGLEstream Link Aggregation Tap (SS-00) Optional 3-Unit Rack Mount Datacom Systems SINGLEstream 0/00 Link Aggregation Tap provides a superior solution for 4x7 monitoring of full-duplex Ethernet links.
SINGLEstream Link Aggregation Tap (SS-00) Optional 3-Unit Rack Mount Datacom Systems SINGLEstream 0/00 Link Aggregation Tap provides a superior solution for 4x7 monitoring of full-duplex Ethernet links.
Key Benefits Ixia xstreamtm 40 Fail -safe Inline Security NPB Offers Aggregation, Filtering, and Load Balancing for 10GbE/40GbE Networks
 Ixia xstream TM 40 Fail-safe Inline Security NPB Offers Aggregation, Filtering, and Load Balancing for 10GbE/40GbE Networks The Ixia xstream 40 is a network packet broker purpose-built for fail-safe inline
Ixia xstream TM 40 Fail-safe Inline Security NPB Offers Aggregation, Filtering, and Load Balancing for 10GbE/40GbE Networks The Ixia xstream 40 is a network packet broker purpose-built for fail-safe inline
PRODUCT PORTFOLIO NETWORK MONITORING, ANALYSIS AND TROUBLESHOOTING
 2018 PRODUCT PORTFOLIO NETWORK MONITORING, ANALYSIS AND TROUBLESHOOTING FIBER TAPS COPPER TAPS NETWORK PACKET BROKERS PORTABLE TROUBLESHOOTERS IN-DEPTH PACKET ANALYSIS SOFTWARE VISIBILITY PERFORMANCE SECURITY
2018 PRODUCT PORTFOLIO NETWORK MONITORING, ANALYSIS AND TROUBLESHOOTING FIBER TAPS COPPER TAPS NETWORK PACKET BROKERS PORTABLE TROUBLESHOOTERS IN-DEPTH PACKET ANALYSIS SOFTWARE VISIBILITY PERFORMANCE SECURITY
Ref: C8-1G. The 8-Link Gigabit Copper TAP is a high density solution, providing 8 TAP links in a 1U rack space
 Data Center Copper TAPs 100% Visibility PROFITAP Copper TAPs monitor all 7 OSI layers, packets of all sizes and types, and low-level errors. Gigabit Ethernet Network TAPs Comprehensive and Flawless 10/100/1000
Data Center Copper TAPs 100% Visibility PROFITAP Copper TAPs monitor all 7 OSI layers, packets of all sizes and types, and low-level errors. Gigabit Ethernet Network TAPs Comprehensive and Flawless 10/100/1000
Cisco Nexus Data Broker
 Data Sheet Cisco Nexus Data Broker Product Overview You used to monitor traffic mainly to manage network operations. Today, when you monitor traffic you can find out instantly what is happening throughout
Data Sheet Cisco Nexus Data Broker Product Overview You used to monitor traffic mainly to manage network operations. Today, when you monitor traffic you can find out instantly what is happening throughout
Cubro Packetmaster EX48600
 Cubro Packetmaster EX48600 PRODUCT REVIEW Network Packet Broker (NPB) At a glance The Packetmaster EX48600 is a high performance network packet broker up to Layer 4 that aggregates, filters, duplicates,
Cubro Packetmaster EX48600 PRODUCT REVIEW Network Packet Broker (NPB) At a glance The Packetmaster EX48600 is a high performance network packet broker up to Layer 4 that aggregates, filters, duplicates,
The Gigamon Visibility Platform
 The Gigamon Visibility Platform See what matters. Andrea Baraldi - Sales Engineer Marco Romagnoli Sales Director 1 Safe Harbor Statement Any forward-looking indication of plans for products is preliminary
The Gigamon Visibility Platform See what matters. Andrea Baraldi - Sales Engineer Marco Romagnoli Sales Director 1 Safe Harbor Statement Any forward-looking indication of plans for products is preliminary
BIG MON CONTROLLERS BIG MON ANALYTICS NODE. Multi-Terabytes L2-GRE 1/10/25/40/100G ETHERNET SWITCH FABRIC. Optional BIG MON BIG MON SERVICE NODES
 Modern Packet Recorder: Enhancing Data Security and Privacy Compliance OVERVIEW In response to the stringent corporate governance and compliance requirements for how IT data is secured, controlled, and
Modern Packet Recorder: Enhancing Data Security and Privacy Compliance OVERVIEW In response to the stringent corporate governance and compliance requirements for how IT data is secured, controlled, and
IXIA FLEX TAP TM DATA SHEET PASSIVE NETWORK MONITORING KEY FEATURES HIGHLIGHTS
 IXIA FLEX TAP TM DATA SHEET PASSIVE NETWORK MONITORING The Ixia Flex Tap provide reliable continuous visibility of 100% of network traffic to support performance and security with no network performance
IXIA FLEX TAP TM DATA SHEET PASSIVE NETWORK MONITORING The Ixia Flex Tap provide reliable continuous visibility of 100% of network traffic to support performance and security with no network performance
Ixia xbalancer. A Purpose-Built Load Balancer for 10G Networks. The Load Balancing Solution DATA SHEET. Highlights
 Ixia xbalancer A Purpose-Built Load Balancer for 10G Networks Ixia s xbalancer is a load balancing appliance for monitoring high-speed network traffic and cost-effective way to share the increasing traffic
Ixia xbalancer A Purpose-Built Load Balancer for 10G Networks Ixia s xbalancer is a load balancing appliance for monitoring high-speed network traffic and cost-effective way to share the increasing traffic
IXIA IBYPASS HD DATA SHEET PROBLEM: INLINE TOOLS ARE A SINGLE POINT OF FAILURE IN THE NETWORK
 IXIA IBYPASS HD DATA SHEET PROBLEM: INLINE TOOLS ARE A SINGLE POINT OF FAILURE IN THE NETWORK Today s organizations are facing a triad of network concerns: the increasing volume of multiprotocol traffic
IXIA IBYPASS HD DATA SHEET PROBLEM: INLINE TOOLS ARE A SINGLE POINT OF FAILURE IN THE NETWORK Today s organizations are facing a triad of network concerns: the increasing volume of multiprotocol traffic
IXIA XSTREAM TM 40 DATA SHEET AGGREGATION, FILTERING, AND LOAD BALANCING FOR 10GBE/40GBE NETWORKS HIGHLIGHTS
 IXIA XSTREAM TM 40 DATA SHEET AGGREGATION, FILTERING, AND LOAD BALANCING FOR 10GBE/40GBE NETWORKS The need to monitor and inspect all traffic on high-volume 10GbE and 40GbE networks pressures organizations
IXIA XSTREAM TM 40 DATA SHEET AGGREGATION, FILTERING, AND LOAD BALANCING FOR 10GBE/40GBE NETWORKS The need to monitor and inspect all traffic on high-volume 10GbE and 40GbE networks pressures organizations
Product Brief GigaVUE-VM
 Product Brief GigaVUE-VM Active Visibility for Virtual Workloads With exponential growth in virtualized traffic within the data center, a primary challenge for the centralized monitoring infrastructure
Product Brief GigaVUE-VM Active Visibility for Virtual Workloads With exponential growth in virtualized traffic within the data center, a primary challenge for the centralized monitoring infrastructure
WHITE PAPER. Monitoring Converged Networks: Link Aggregation
 WHITE PAPER Monitoring Converged Networks: Link Aggregation www.ixiacom.com 915-6896-01 Rev. A, July 2014 2 Table of Contents Benefits... 4 Introduction... 4 The Net Optics Solution... 4 Easy-to-Use...
WHITE PAPER Monitoring Converged Networks: Link Aggregation www.ixiacom.com 915-6896-01 Rev. A, July 2014 2 Table of Contents Benefits... 4 Introduction... 4 The Net Optics Solution... 4 Easy-to-Use...
Features. HDX WAN optimization. QoS
 May 2013 Citrix CloudBridge Accelerates, controls and optimizes applications to all locations: datacenter, branch offices, public and private clouds and mobile users Citrix CloudBridge provides a unified
May 2013 Citrix CloudBridge Accelerates, controls and optimizes applications to all locations: datacenter, branch offices, public and private clouds and mobile users Citrix CloudBridge provides a unified
Gigamon Metadata Application for IBM QRadar Deployment Guide
 Gigamon Metadata Application for IBM QRadar Deployment Guide COPYRIGHT Copyright 2018 Gigamon. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a
Gigamon Metadata Application for IBM QRadar Deployment Guide COPYRIGHT Copyright 2018 Gigamon. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a
Automated Traffic Visibility for SDDC Solution Guide
 Automated Traffic Visibility for SDDC Solution Guide COPYRIGHT Copyright 2016 Gigamon. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
Automated Traffic Visibility for SDDC Solution Guide COPYRIGHT Copyright 2016 Gigamon. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
Use Cases Application And Service Monitoring Eliminate contention for network data. Centralize Netflow/IPFIX Generation
 X1/X2 X3/X4 X5/X6 X7/X8 X9/X10 X11/X12 X13/X14 X15/X16 X17/X18 X19/X20 X21/X22 X23/ C1 C2 C3 USB CON MGMT PTP C4 C5 STACK STACK P/S PPS(IN) C1 C2 C3 C4 C5 C6 C7 C8 X1/X2 X3/X4 X5/X6 X7/X8 X9/X10 X11/X12
X1/X2 X3/X4 X5/X6 X7/X8 X9/X10 X11/X12 X13/X14 X15/X16 X17/X18 X19/X20 X21/X22 X23/ C1 C2 C3 USB CON MGMT PTP C4 C5 STACK STACK P/S PPS(IN) C1 C2 C3 C4 C5 C6 C7 C8 X1/X2 X3/X4 X5/X6 X7/X8 X9/X10 X11/X12
Ixia Flex Tap PASSIVE NETWORK MONITORING HIGHLIGHTS KEY FEATURES. Data Sheet
 Ixia Flex Tap Data Sheet PASSIVE NETWORK MONITORING The Ixia Flex Tap provide reliable continuous visibility of 100% of network traffic to support performance and security with no network performance degradation
Ixia Flex Tap Data Sheet PASSIVE NETWORK MONITORING The Ixia Flex Tap provide reliable continuous visibility of 100% of network traffic to support performance and security with no network performance degradation
Cubro Network Security Series
 Cubro Security Series PRODUCT REVIEW Security At a glance In order to meet the demands of the operators and fastdeveloping network, Cubro delivers the network secure sockets layer analysis products --
Cubro Security Series PRODUCT REVIEW Security At a glance In order to meet the demands of the operators and fastdeveloping network, Cubro delivers the network secure sockets layer analysis products --
PRODUCT PORTFOLIO NETWORK MONITORING, ANALYSIS AND TROUBLESHOOTING
 2019 PRODUCT PORTFOLIO NETWORK MONITORING, ANALYSIS AND TROUBLESHOOTING FIBER TAPS COPPER TAPS NETWORK PACKET BROKERS PORTABLE TROUBLESHOOTERS IN-DEPTH PACKET ANALYSIS SOFTWARE VISIBILITY PERFORMANCE SECURITY
2019 PRODUCT PORTFOLIO NETWORK MONITORING, ANALYSIS AND TROUBLESHOOTING FIBER TAPS COPPER TAPS NETWORK PACKET BROKERS PORTABLE TROUBLESHOOTERS IN-DEPTH PACKET ANALYSIS SOFTWARE VISIBILITY PERFORMANCE SECURITY
Rethinking Security CLOUDSEC2016. Ian Farquhar Distinguished Sales Engineer Field Lead for the Gigamon Security Virtual Team
 Rethinking Security CLOUDSEC2016 Ian Farquhar Distinguished Sales Engineer Field Lead for the Gigamon Security Virtual Team Breaches Are The New Normal Only The Scale Surprises Us OPM will send notifications
Rethinking Security CLOUDSEC2016 Ian Farquhar Distinguished Sales Engineer Field Lead for the Gigamon Security Virtual Team Breaches Are The New Normal Only The Scale Surprises Us OPM will send notifications
2015 Product Catalog
 2015 Product Catalog Table of Contents Table of Contents 2 Decades of Experience 3 Portable Network TAPs 4 Passive TAPs 8 Modular Chassis with Management 12 Modular Chassis without Management 13 Modular
2015 Product Catalog Table of Contents Table of Contents 2 Decades of Experience 3 Portable Network TAPs 4 Passive TAPs 8 Modular Chassis with Management 12 Modular Chassis without Management 13 Modular
CloudStorm TM 100GE Application and Security Test Load Module
 CloudStorm TM 100GE Application and Security Test Load Module CLOUD-SCALE APPLICATION DELIVERY & NETWORK SECURITY TEST PLATFORM PROBLEM: AN ALL-ENCRYPTED WORLD AND INCREASING USER EXPERIENCE EXPECTATIONS
CloudStorm TM 100GE Application and Security Test Load Module CLOUD-SCALE APPLICATION DELIVERY & NETWORK SECURITY TEST PLATFORM PROBLEM: AN ALL-ENCRYPTED WORLD AND INCREASING USER EXPERIENCE EXPECTATIONS
Ixia Net Optics Flex Tap TM
 Ixia Net Optics Flex Tap TM Key Features The Ixia Net Optics Flex Tap family delivers total traffic visibility for network monitoring and security tools. Deploying these network taps on any network link
Ixia Net Optics Flex Tap TM Key Features The Ixia Net Optics Flex Tap family delivers total traffic visibility for network monitoring and security tools. Deploying these network taps on any network link
Packetron. Your path to an Intelligent Visibility Layer
 Your path to an Intelligent Visibility Layer Niagara Networks has recognized that the increase in data speed and the increase in sophistication required from network tools and applications is creating
Your path to an Intelligent Visibility Layer Niagara Networks has recognized that the increase in data speed and the increase in sophistication required from network tools and applications is creating
Brocade and Procera. Detailed Insights for OTT Application Traffic KEY BENEFITS SOLUTIONS BRIEF BUSINESS CHALLENGE
 Brocade and Procera Detailed Insights for OTT Application Traffic Brocade Packet Broker together with Procera s PacketLogic TM Deep Packet Inspection (DPI) engine is targeted towards mobile service provider
Brocade and Procera Detailed Insights for OTT Application Traffic Brocade Packet Broker together with Procera s PacketLogic TM Deep Packet Inspection (DPI) engine is targeted towards mobile service provider
ngenius 5010 Packet Flow Switch
 l DATA SHEET l ngenius 5010 Packet Flow Switch Software-Driven and Cost-Effective Performance HIGHLIGHTS 1 rackmount unit (RU) space-efficient, fixed configuration device 720Gbps throughput and non-blocking
l DATA SHEET l ngenius 5010 Packet Flow Switch Software-Driven and Cost-Effective Performance HIGHLIGHTS 1 rackmount unit (RU) space-efficient, fixed configuration device 720Gbps throughput and non-blocking
Aligning Agency Cybersecurity Practices with the Cybersecurity Framework
 POINT OF VIEW Aligning Agency Cybersecurity Practices with the Cybersecurity Framework Leveraging Gigamon to Align Cybersecurity Budgets with Desired Business Outcomes 2013-2017 Gigamon. All rights reserved.
POINT OF VIEW Aligning Agency Cybersecurity Practices with the Cybersecurity Framework Leveraging Gigamon to Align Cybersecurity Budgets with Desired Business Outcomes 2013-2017 Gigamon. All rights reserved.
Securing VMware NSX MAY 2014
 Securing VMware NSX MAY 2014 Securing VMware NSX Table of Contents Executive Summary... 2 NSX Traffic [Control, Management, and Data]... 3 NSX Manager:... 5 NSX Controllers:... 8 NSX Edge Gateway:... 9
Securing VMware NSX MAY 2014 Securing VMware NSX Table of Contents Executive Summary... 2 NSX Traffic [Control, Management, and Data]... 3 NSX Manager:... 5 NSX Controllers:... 8 NSX Edge Gateway:... 9
Cubro Sessionmaster EXA40 series
 Cubro Sessionmaster EXA40 series PRODUCT REVIEW Network Packet Broker (NPB) At a glance Definition A network packet broker (NPB) is a tool that receives data from number of network links, duplicates, aggregates
Cubro Sessionmaster EXA40 series PRODUCT REVIEW Network Packet Broker (NPB) At a glance Definition A network packet broker (NPB) is a tool that receives data from number of network links, duplicates, aggregates
SSL INSIGHT SSL ENCRYPTION CHALLENGES SSL USE EXPOSES A BLIND SPOT IN CORPORATE DEFENSES SOLUTION BRIEF UNCOVER HIDDEN THREATS IN ENCRYPTED TRAFFIC
 SOLUTION BRIEF UNCOVER HIDDEN THREATS IN ENCRYPTED TRAFFIC SSL ENCRYPTION CHALLENGES To prevent attacks, intrusions and malware, enterprises need to inspect incoming and outgoing traffic for threats. Unfortunately,
SOLUTION BRIEF UNCOVER HIDDEN THREATS IN ENCRYPTED TRAFFIC SSL ENCRYPTION CHALLENGES To prevent attacks, intrusions and malware, enterprises need to inspect incoming and outgoing traffic for threats. Unfortunately,
A10 SSL INSIGHT & SONICWALL NEXT-GEN FIREWALLS
 DEPLOYMENT GUIDE A10 SSL INSIGHT & SONICWALL NEXT-GEN FIREWALLS A10 NETWORKS SSL INSIGHT & FIREWALL LOAD BALANCING SOLUTION FOR SONICWALL SUPERMASSIVE NEXT GENERATION FIREWALLS OVERVIEW This document describes
DEPLOYMENT GUIDE A10 SSL INSIGHT & SONICWALL NEXT-GEN FIREWALLS A10 NETWORKS SSL INSIGHT & FIREWALL LOAD BALANCING SOLUTION FOR SONICWALL SUPERMASSIVE NEXT GENERATION FIREWALLS OVERVIEW This document describes
Check Point 4800 with Gigamon Inline Deployment Guide
 Check Point 4800 with Gigamon Inline Deployment Guide COPYRIGHT Copyright 2016 Gigamon. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
Check Point 4800 with Gigamon Inline Deployment Guide COPYRIGHT Copyright 2016 Gigamon. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval
User Plane Monitoring for a Mobile Network Operator (MNO)
 User Plane Monitoring for a Mobile Network Operator (MNO) Jan 2018 www.cubro.com User Plane Monitoring for a MNO The challenges Growing traffic High costs Complicated network architecture The Cubro solution
User Plane Monitoring for a Mobile Network Operator (MNO) Jan 2018 www.cubro.com User Plane Monitoring for a MNO The challenges Growing traffic High costs Complicated network architecture The Cubro solution
Brocade and Sandvine. Detailed Insights for OTT Application Traffic KEY BENEFITS SOLUTIONS BRIEF BUSINESS CHALLENGE
 Brocade and Sandvine Detailed Insights for OTT Application Traffic Brocade Packet Broker together with Sandvine s PacketLogic TM Deep Packet Inspection (DPI) engine is targeted towards mobile service provider
Brocade and Sandvine Detailed Insights for OTT Application Traffic Brocade Packet Broker together with Sandvine s PacketLogic TM Deep Packet Inspection (DPI) engine is targeted towards mobile service provider
ARIA SDS. Application
 ARIA SDS Packet Intelligence Application CSPi s ARIA SDS Packet Intelligence (PI) application enhances an organization s existing network security capabilities by enabling the monitoring of all network
ARIA SDS Packet Intelligence Application CSPi s ARIA SDS Packet Intelligence (PI) application enhances an organization s existing network security capabilities by enabling the monitoring of all network
COMMON CRITERIA CERTIFICATION REPORT
 COMMON CRITERIA CERTIFICATION REPORT Ixia NTO 7303 and Vision ONE v4.5.0.29 30 October 2017 383-4-409 1.0 Government of Canada. This document is the property of the Government of Canada. It shall not be
COMMON CRITERIA CERTIFICATION REPORT Ixia NTO 7303 and Vision ONE v4.5.0.29 30 October 2017 383-4-409 1.0 Government of Canada. This document is the property of the Government of Canada. It shall not be
DDoS Hybrid Defender. SSL Orchestrator. Comprehensive DDoS protection, tightly-integrated on-premises and cloud
 SSL Orchestrator DDoS Hybrid Defender All-in-one solution designed to deliver increased visibility into encrypted traffic Comprehensive DDoS protection, tightly-integrated on-premises and cloud Converts
SSL Orchestrator DDoS Hybrid Defender All-in-one solution designed to deliver increased visibility into encrypted traffic Comprehensive DDoS protection, tightly-integrated on-premises and cloud Converts
WHITE PAPER A10 SSL INSIGHT & FIREWALL LOAD BALANCING WITH SONICWALL NEXT-GEN FIREWALLS
 WHITE PAPER A10 SSL INSIGHT & FIREWALL LOAD BALANCING WITH SONICWALL NEXT-GEN FIREWALLS TABLE OF CONTENTS EXECUTIVE SUMMARY... 3 INTRODUCTION... 3 SOLUTION REQUIREMENTS... 3 SOLUTION COMPONENTS... 4 SOLUTION
WHITE PAPER A10 SSL INSIGHT & FIREWALL LOAD BALANCING WITH SONICWALL NEXT-GEN FIREWALLS TABLE OF CONTENTS EXECUTIVE SUMMARY... 3 INTRODUCTION... 3 SOLUTION REQUIREMENTS... 3 SOLUTION COMPONENTS... 4 SOLUTION
CHECK POINT NEXT GENERATION SECURITY GATEWAY FOR THE DATACENTER
 CHECK POINT 23500 NEXT GENERATION SECURITY GATEWAY FOR THE DATACENTER CHECK POINT 23500 NEXT GENERATION SECURITY GATEWAY Data center grade security, performance and reliability Product Benefits High performance
CHECK POINT 23500 NEXT GENERATION SECURITY GATEWAY FOR THE DATACENTER CHECK POINT 23500 NEXT GENERATION SECURITY GATEWAY Data center grade security, performance and reliability Product Benefits High performance
PRODUCT PORTFOLIO NETWORK MONITORING, ANALYSIS AND TROUBLESHOOTING
 2019 PRODUCT PORTFOLIO NETWORK MONITORING, ANALYSIS AND TROUBLESHOOTING FIBER TAPS COPPER TAPS NETWORK PACKET BROKERS PORTABLE TROUBLESHOOTERS IN-DEPTH PACKET ANALYSIS SOFTWARE VISIBILITY PERFORMANCE SECURITY
2019 PRODUCT PORTFOLIO NETWORK MONITORING, ANALYSIS AND TROUBLESHOOTING FIBER TAPS COPPER TAPS NETWORK PACKET BROKERS PORTABLE TROUBLESHOOTERS IN-DEPTH PACKET ANALYSIS SOFTWARE VISIBILITY PERFORMANCE SECURITY
Observer Probe Family
 Observer Probe Family Distributed analysis for local and remote networks Monitor and troubleshoot vital network links in real time from any location Network Instruments offers a complete line of software
Observer Probe Family Distributed analysis for local and remote networks Monitor and troubleshoot vital network links in real time from any location Network Instruments offers a complete line of software
TAP Aggregation with DANZ
 TAP Aggregation with DANZ The Missing Economics of Network Visibility Arista DANZ provides the ability to cost-effectively capture and analyze all traffic and flows in a datacenter or service provider
TAP Aggregation with DANZ The Missing Economics of Network Visibility Arista DANZ provides the ability to cost-effectively capture and analyze all traffic and flows in a datacenter or service provider
Flow-based Traffic Visibility
 Flow-based Traffic Visibility Operations, Performance, Security Pavel Minařík, Chief Technology Officer What is Flow Data? Modern method for network monitoring flow measurement Cisco standard NetFlow v5/v9,
Flow-based Traffic Visibility Operations, Performance, Security Pavel Minařík, Chief Technology Officer What is Flow Data? Modern method for network monitoring flow measurement Cisco standard NetFlow v5/v9,
Network Security Monitoring with Flow Data
 Network Security Monitoring with Flow Data IT Monitoring in Enterprises NPMD (Network Performance Monitoring & Diagnostics) SNMP basics Flow data for advanced analysis and troubleshooting Packet capture
Network Security Monitoring with Flow Data IT Monitoring in Enterprises NPMD (Network Performance Monitoring & Diagnostics) SNMP basics Flow data for advanced analysis and troubleshooting Packet capture
Man kann nur schützen was man sieht - oder Zentrales Entschlüsseln von SSL/TLS Verkehr Rethinking Security
 Man kann nur schützen was man sieht - oder Zentrales Entschlüsseln von SSL/TLS Verkehr Rethinking Security Stepan Svihla Sr. Sales Engineer Central & Eastern Europe Corporate Overview THE ESSENTIAL ELEMENT
Man kann nur schützen was man sieht - oder Zentrales Entschlüsseln von SSL/TLS Verkehr Rethinking Security Stepan Svihla Sr. Sales Engineer Central & Eastern Europe Corporate Overview THE ESSENTIAL ELEMENT
WHITE PAPER. Fail-Safe IPS Integration with Bypass Technology
 WHITE PAPER Fail-Safe IPS Integration with Bypass Technology www.ixiacom.com 915-6907-01 Rev. A, July 2014 2 Table of Contents Summary... 4 Key Features... 4 Introduction... 4 The Challenge... 5 Industry
WHITE PAPER Fail-Safe IPS Integration with Bypass Technology www.ixiacom.com 915-6907-01 Rev. A, July 2014 2 Table of Contents Summary... 4 Key Features... 4 Introduction... 4 The Challenge... 5 Industry
SOLUTION BRIEF: AN END-TO-END DATA CENTER MONITORING SOLUTION VISIT
 SOLUTION BRIEF: AN END-TO-END DATA CENTER MONITORING SOLUTION VISIT WWW.PROFITAP.COM Flowmon and Profitap s joint solution offers the most efficient end-toend monitoring platform you can get for a high-speed
SOLUTION BRIEF: AN END-TO-END DATA CENTER MONITORING SOLUTION VISIT WWW.PROFITAP.COM Flowmon and Profitap s joint solution offers the most efficient end-toend monitoring platform you can get for a high-speed
SEVONE DATA APPLIANCE FOR EUE
 Insight for the Connected World Data Appliance for EUE [ DataSheet ] SEVONE DATA APPLIANCE FOR EUE INSIGHTS FROM THE USER PERSPECTIVE. Software, applications and services running on the network infrastructure
Insight for the Connected World Data Appliance for EUE [ DataSheet ] SEVONE DATA APPLIANCE FOR EUE INSIGHTS FROM THE USER PERSPECTIVE. Software, applications and services running on the network infrastructure
Cisco ISR G2 Management Overview
 Cisco ISR G2 Management Overview Introduction The new Cisco Integrated Services Routers Generation 2 (ISR G2) Family of routers delivers the borderless network that can transform the branch office and
Cisco ISR G2 Management Overview Introduction The new Cisco Integrated Services Routers Generation 2 (ISR G2) Family of routers delivers the borderless network that can transform the branch office and
Corrigendum 3. Tender Number: 10/ dated
 (A premier Public Sector Bank) Information Technology Division Head Office, Mangalore Corrigendum 3 Tender Number: 10/2016-17 dated 07.09.2016 for Supply, Installation and Maintenance of Distributed Denial
(A premier Public Sector Bank) Information Technology Division Head Office, Mangalore Corrigendum 3 Tender Number: 10/2016-17 dated 07.09.2016 for Supply, Installation and Maintenance of Distributed Denial
Configuring SSL Security
 CHAPTER9 This chapter describes how to configure SSL on the Cisco 4700 Series Application Control Engine (ACE) appliance. This chapter contains the following sections: Overview Configuring SSL Termination
CHAPTER9 This chapter describes how to configure SSL on the Cisco 4700 Series Application Control Engine (ACE) appliance. This chapter contains the following sections: Overview Configuring SSL Termination
Cubro Packetmaster EX2 Series
 Cubro Series PRODUCT OVERVIEW Network Packet Broker (NPB) At a glance Definition The Cubro Packetmaster (Network Packet Broker) EX2 Series, based on a new designed ASIC, is a switch like device. EX2 Series
Cubro Series PRODUCT OVERVIEW Network Packet Broker (NPB) At a glance Definition The Cubro Packetmaster (Network Packet Broker) EX2 Series, based on a new designed ASIC, is a switch like device. EX2 Series
Using the Cisco ACE Application Control Engine Application Switches with the Cisco ACE XML Gateway
 Using the Cisco ACE Application Control Engine Application Switches with the Cisco ACE XML Gateway Applying Application Delivery Technology to Web Services Overview The Cisco ACE XML Gateway is the newest
Using the Cisco ACE Application Control Engine Application Switches with the Cisco ACE XML Gateway Applying Application Delivery Technology to Web Services Overview The Cisco ACE XML Gateway is the newest
ngenius 5100 Packet Flow Switch
 l DATA SHEET l ngenius 5100 Packet Flow Switch Software-Driven and Cost-Effective Performance HIGHLIGHTS 1 rackmount unit (RU), space-efficient, fixed configuration device 3.2Tbps throughput Up to 32 ports
l DATA SHEET l ngenius 5100 Packet Flow Switch Software-Driven and Cost-Effective Performance HIGHLIGHTS 1 rackmount unit (RU), space-efficient, fixed configuration device 3.2Tbps throughput Up to 32 ports
ExtremeWireless WiNG NX 9500
 DATA SHEET ExtremeWireless WiNG NX 9500 Integrated Services Platform Series for the Private Cloud FEATURES COMPLETE VISIBILITY OF THE ENTIRE DISTRIBUTED DEPLOYMENT One point of configuration; ExtremeWireless
DATA SHEET ExtremeWireless WiNG NX 9500 Integrated Services Platform Series for the Private Cloud FEATURES COMPLETE VISIBILITY OF THE ENTIRE DISTRIBUTED DEPLOYMENT One point of configuration; ExtremeWireless
2804 Hybrid Packet Broker
 2804 Hybrid Packet Broker Multi-functional Bypass Packet Broker The Niagara 2804 hybrid packet broker uniquely combines multipurpose bypass functionality with a fully featured network packet broker. The
2804 Hybrid Packet Broker Multi-functional Bypass Packet Broker The Niagara 2804 hybrid packet broker uniquely combines multipurpose bypass functionality with a fully featured network packet broker. The
Cloud, SDN and BIGIQ. Philippe Bogaerts Senior Field Systems Engineer
 Cloud, SDN and BIGIQ Philippe Bogaerts Senior Field Systems Engineer Virtual Editions TMOS/LTM 12.0 Highlights 1 NIC support Azure Marketplace Kernel Independent driver Enhanced Hypervisor support F5 Networks,
Cloud, SDN and BIGIQ Philippe Bogaerts Senior Field Systems Engineer Virtual Editions TMOS/LTM 12.0 Highlights 1 NIC support Azure Marketplace Kernel Independent driver Enhanced Hypervisor support F5 Networks,
Solution Overview Gigamon Visibility Platform for AWS
 Solution Overview Gigamon Visibility Platform for Background With the rapid evolution of the public cloud that brings instant advantages of economies of scale, elasticity and agility, IT and data center
Solution Overview Gigamon Visibility Platform for Background With the rapid evolution of the public cloud that brings instant advantages of economies of scale, elasticity and agility, IT and data center
Cisco Nexus 1000V Switch for Microsoft Hyper-V
 Q&A Cisco Nexus 1000V Switch for Microsoft Hyper-V Overview Q. What are Cisco Nexus 1000V Switches? A. Cisco Nexus 1000V Switches provide a comprehensive and extensible architectural platform for virtual
Q&A Cisco Nexus 1000V Switch for Microsoft Hyper-V Overview Q. What are Cisco Nexus 1000V Switches? A. Cisco Nexus 1000V Switches provide a comprehensive and extensible architectural platform for virtual
NX 9500 INTEGRATED SERVICES PLATFORM SERIES FOR THE PRIVATE CLOUD
 PRODUCT SPEC SHEET NX 9500 INTEGRATED SERVICES PLATFORM SERIES FOR THE PRIVATE CLOUD NX 9500 INTEGRATED SERVICES PLATFORM SERIES FOR THE PRIVATE CLOUD CENTRALIZED SERVICE DELIVERY AND MANAGEMENT PLATFORM
PRODUCT SPEC SHEET NX 9500 INTEGRATED SERVICES PLATFORM SERIES FOR THE PRIVATE CLOUD NX 9500 INTEGRATED SERVICES PLATFORM SERIES FOR THE PRIVATE CLOUD CENTRALIZED SERVICE DELIVERY AND MANAGEMENT PLATFORM
75% 64% Data Sheet GigaVUE-HC1
 CRPS 460W AC Gold USB PWR FAN PTP PPS M/S Mgnt / Con Stack/PTP G1 / G2 G3 / G4 X3/X4 X5/X6 X7/X8 X9/X10 X11/X12 PPS(IN) P/S CRPS 460W AC Gold Data Sheet 75% 64% (front) (rear) of organizations believe
CRPS 460W AC Gold USB PWR FAN PTP PPS M/S Mgnt / Con Stack/PTP G1 / G2 G3 / G4 X3/X4 X5/X6 X7/X8 X9/X10 X11/X12 PPS(IN) P/S CRPS 460W AC Gold Data Sheet 75% 64% (front) (rear) of organizations believe
Enterasys K-Series. Benefits. Product Overview. There is nothing more important than our customers. DATASHEET. Operational Efficiency.
 DATASHEET Enterasys K-Series Product Overview The Enterasys K-Series is the most cost-effective, flow-based switching solution in the industry. Providing exceptional levels of automation, visibility and
DATASHEET Enterasys K-Series Product Overview The Enterasys K-Series is the most cost-effective, flow-based switching solution in the industry. Providing exceptional levels of automation, visibility and
NetScaler for Apps and Desktops CNS-222; 5 Days; Instructor-led
 NetScaler for Apps and Desktops CNS-222; 5 Days; Instructor-led Course Description Designed for students with little or no previous NetScaler, NetScaler Gateway or Unified Gateway experience, this course
NetScaler for Apps and Desktops CNS-222; 5 Days; Instructor-led Course Description Designed for students with little or no previous NetScaler, NetScaler Gateway or Unified Gateway experience, this course
Security Overview and Cisco ACE Replacement
 Security Overview and Cisco ACE Replacement March, 2014 Florian Hartmann, Senior Systems Engineer DACH A10 Corporate Introduction Headquarters in San Jose 800+ Employees Offices in 32 countries Customers
Security Overview and Cisco ACE Replacement March, 2014 Florian Hartmann, Senior Systems Engineer DACH A10 Corporate Introduction Headquarters in San Jose 800+ Employees Offices in 32 countries Customers
HP S1500 SSL Appliance. Product overview. Key features. Data sheet
 HP S1500 SSL Appliance Data sheet Product overview The HP S1500 SSL Appliance provides hardware-accelerated Secure Sockets Layer (SSL) offloading and bridging to enable high-performance intrusion prevention
HP S1500 SSL Appliance Data sheet Product overview The HP S1500 SSL Appliance provides hardware-accelerated Secure Sockets Layer (SSL) offloading and bridging to enable high-performance intrusion prevention
Why can t I just do that with a switch? Joseph Magee Chief Security Officer Top Layer Networks
 Why can t I just do that with a switch? Joseph Magee Chief Security Officer Top Layer Networks - 1 - Introduction In the field you may come across the following question: Why can t I do what your IDS Balancer
Why can t I just do that with a switch? Joseph Magee Chief Security Officer Top Layer Networks - 1 - Introduction In the field you may come across the following question: Why can t I do what your IDS Balancer
Agile Security Solutions
 Agile Security Solutions Piotr Linke Security Engineer CISSP CISA CRISC CISM Open Source SNORT 2 Consider these guys All were smart. All had security. All were seriously compromised. 3 The Industrialization
Agile Security Solutions Piotr Linke Security Engineer CISSP CISA CRISC CISM Open Source SNORT 2 Consider these guys All were smart. All had security. All were seriously compromised. 3 The Industrialization
SuperMassive E10000 Series
 SuperMassive E10000 Series Next-Generation Firewall The Dell SonicWALL SuperMassive E10000 Series is Dell SonicWALL s Next-Generation Firewall platform designed for large networks to deliver scalability,
SuperMassive E10000 Series Next-Generation Firewall The Dell SonicWALL SuperMassive E10000 Series is Dell SonicWALL s Next-Generation Firewall platform designed for large networks to deliver scalability,
Live traffic feeds are increasingly being used by the modern enterprise to gain visibility for security and operations management
 Overview The transition from an age of systems of record to an age of systems of engagement has led to profound changes in the way information is used in an organization. These changes have now become
Overview The transition from an age of systems of record to an age of systems of engagement has led to profound changes in the way information is used in an organization. These changes have now become
Implementing Cisco Edge Network Security Solutions ( )
 Implementing Cisco Edge Network Security Solutions (300-206) Exam Description: The Implementing Cisco Edge Network Security (SENSS) (300-206) exam tests the knowledge of a network security engineer to
Implementing Cisco Edge Network Security Solutions (300-206) Exam Description: The Implementing Cisco Edge Network Security (SENSS) (300-206) exam tests the knowledge of a network security engineer to
Aggregate Interfaces and LACP
 The following topics explain aggregate interface configuration and how LACP functions on managed devices: About Aggregate Interfaces, on page 1 LAG Configuration, on page 2 Link Aggregation Control Protocol
The following topics explain aggregate interface configuration and how LACP functions on managed devices: About Aggregate Interfaces, on page 1 LAG Configuration, on page 2 Link Aggregation Control Protocol
Fidelis Network Sensor Appliances QUICK START GUIDE
 Fidelis Network Sensor Appliances Rev-H Fidelis Sensors (Direct, Internal, Web, and Mail Appliances) Based on HPE DL350-G9 and DL560-G9 Platforms 1. System Overview Fidelis Sensors are the components that
Fidelis Network Sensor Appliances Rev-H Fidelis Sensors (Direct, Internal, Web, and Mail Appliances) Based on HPE DL350-G9 and DL560-G9 Platforms 1. System Overview Fidelis Sensors are the components that
IntellaFlex XR. Network Security and Visibility Solutions. Real-time insights to help secure and protect your data
 IntellaFlex XR Network Security and Visibility Solutions Real-time insights to help secure and protect your data Enterprise-lass Network Visibility Fabric» Reduce capital equipment and operational costs»
IntellaFlex XR Network Security and Visibility Solutions Real-time insights to help secure and protect your data Enterprise-lass Network Visibility Fabric» Reduce capital equipment and operational costs»
Understanding Cisco Cybersecurity Fundamentals
 210-250 Understanding Cisco Cybersecurity Fundamentals NWExam.com SUCCESS GUIDE TO CISCO CERTIFICATION Exam Summary Syllabus Questions Table of Contents Introduction to 210-250 Exam on Understanding Cisco
210-250 Understanding Cisco Cybersecurity Fundamentals NWExam.com SUCCESS GUIDE TO CISCO CERTIFICATION Exam Summary Syllabus Questions Table of Contents Introduction to 210-250 Exam on Understanding Cisco
Brocade Virtual Traffic Manager and Parallels Remote Application Server
 White Paper Parallels Brocade Virtual Traffic Manager and Parallels Deployment Guide 01 Contents Preface...4 About This Guide...4 Audience...4 Contacting Brocade...4 Internet...4 Technical Support...4
White Paper Parallels Brocade Virtual Traffic Manager and Parallels Deployment Guide 01 Contents Preface...4 About This Guide...4 Audience...4 Contacting Brocade...4 Internet...4 Technical Support...4
SOLUTION BRIEF RSA NETWITNESS SUITE & THE CLOUD PROTECTING AGAINST THREATS IN A PERIMETER-LESS WORLD
 RSA NETWITNESS SUITE & THE CLOUD PROTECTING AGAINST THREATS IN A PERIMETER-LESS WORLD THE CLOUD MAKES THREAT HUNTING HARDER The explosion in cloud workloads is driving real, substantial business value.
RSA NETWITNESS SUITE & THE CLOUD PROTECTING AGAINST THREATS IN A PERIMETER-LESS WORLD THE CLOUD MAKES THREAT HUNTING HARDER The explosion in cloud workloads is driving real, substantial business value.
INTELLAFLEX. Packet Aggregation Switching Solutions
 INTELLAFLEX Packet Aggregation Switching Solutions APCON s scalable, high availability, network monitoring solutions increase tool efficiency for complete visibility of enterprise network traffic. Enterprise-Class
INTELLAFLEX Packet Aggregation Switching Solutions APCON s scalable, high availability, network monitoring solutions increase tool efficiency for complete visibility of enterprise network traffic. Enterprise-Class
Deep Security Integration with Sumo Logic
 A Trend Micro White Paper I May 2016 Install, Integrate and Analyze» This paper is aimed at information security and solution architects looking to integrate the Trend Micro Deep Security with Sumo Logic.
A Trend Micro White Paper I May 2016 Install, Integrate and Analyze» This paper is aimed at information security and solution architects looking to integrate the Trend Micro Deep Security with Sumo Logic.
CounterACT 7.0 Single CounterACT Appliance
 CounterACT 7.0 Single CounterACT Appliance Quick Installation Guide Table of Contents Welcome to CounterACT Version 7.0....3 Included in your CounterACT Package....3 Overview...4 1. Create a Deployment
CounterACT 7.0 Single CounterACT Appliance Quick Installation Guide Table of Contents Welcome to CounterACT Version 7.0....3 Included in your CounterACT Package....3 Overview...4 1. Create a Deployment
Use Cases Application And Service Monitoring Eliminate contention for network data. Centralize Netflow/IPFIX Generation
 X1/X2 X3/X4 X5/X6 X7/X8 X9/X10 X11/X12 X13/X14 X15/X16 X17/X18 X19/X20 X21/X22 X23/ C1 C2 C3 USB CON MGMT PTP C4 C5 STACK STACK P/S PPS(IN) C1 C2 C3 C4 C5 C6 C7 C8 X1/X2 X3/X4 X5/X6 X7/X8 X9/X10 X11/X12
X1/X2 X3/X4 X5/X6 X7/X8 X9/X10 X11/X12 X13/X14 X15/X16 X17/X18 X19/X20 X21/X22 X23/ C1 C2 C3 USB CON MGMT PTP C4 C5 STACK STACK P/S PPS(IN) C1 C2 C3 C4 C5 C6 C7 C8 X1/X2 X3/X4 X5/X6 X7/X8 X9/X10 X11/X12
Transport Level Security
 2 Transport Level Security : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 28 October 2013 css322y13s2l12, Steve/Courses/2013/s2/css322/lectures/transport.tex,
2 Transport Level Security : Security and Cryptography Sirindhorn International Institute of Technology Thammasat University Prepared by Steven Gordon on 28 October 2013 css322y13s2l12, Steve/Courses/2013/s2/css322/lectures/transport.tex,
State of Cloud Adoption. Cloud usage is over 90%, are you ready?
 State of Cloud Adoption Cloud usage is over 90%, are you ready? State of Cloud Adoption Cloud hardware, software and services are capturing 60% of IT market growth, mostly in the public cloud space Trust
State of Cloud Adoption Cloud usage is over 90%, are you ready? State of Cloud Adoption Cloud hardware, software and services are capturing 60% of IT market growth, mostly in the public cloud space Trust
SOLUTION BRIEF EXTREMEWIRELESS WiNG AZARA AZARA. WiNG RISE TO THE CHALLENGE OF PROVIDING SUPERIOR CONNECTIVITY & WLAN MANAGEMENT
 SOLUTION BRIEF WiNG AZARA RISE TO THE CHALLENGE OF PROVIDING SUPERIOR CONNECTIVITY & WLAN MANAGEMENT Freedom from the unpredictability of providing connectivity Today, mobile devices outnumber the total
SOLUTION BRIEF WiNG AZARA RISE TO THE CHALLENGE OF PROVIDING SUPERIOR CONNECTIVITY & WLAN MANAGEMENT Freedom from the unpredictability of providing connectivity Today, mobile devices outnumber the total
Cisco Data Center Network Manager 5.1
 Cisco Data Center Network Manager 5.1 Product Overview Modern data centers are becoming increasingly large and complex. New technology architectures such as cloud computing and virtualization are adding
Cisco Data Center Network Manager 5.1 Product Overview Modern data centers are becoming increasingly large and complex. New technology architectures such as cloud computing and virtualization are adding
Data-Driven DevOps: Bringing Visibility to Any Cloud, Any App, & Any Device. Erik Giesa SVP of Marketing and Business Development, ExtraHop Networks
 Data-Driven DevOps: Bringing Visibility to Any Cloud, Any App, & Any Device Erik Giesa SVP of Marketing and Business Development, ExtraHop Networks Your Monitoring Strategy Must Change How can you maintain
Data-Driven DevOps: Bringing Visibility to Any Cloud, Any App, & Any Device Erik Giesa SVP of Marketing and Business Development, ExtraHop Networks Your Monitoring Strategy Must Change How can you maintain
Validation of Cisco SCE8000
 Isocore Technical Report Validation of Cisco SCE8000 ISOCORE Internetworking Lab ISOCORE Technical Document Reference: ITD: 13039 Version (v1.3): 4/10/09 ISOCORE Internetworking Lab 1 12359 Sunrise Valley
Isocore Technical Report Validation of Cisco SCE8000 ISOCORE Internetworking Lab ISOCORE Technical Document Reference: ITD: 13039 Version (v1.3): 4/10/09 ISOCORE Internetworking Lab 1 12359 Sunrise Valley
SentinelOne Technical Brief
 SentinelOne Technical Brief SentinelOne unifies prevention, detection and response in a fundamentally new approach to endpoint protection, driven by machine learning and intelligent automation. By rethinking
SentinelOne Technical Brief SentinelOne unifies prevention, detection and response in a fundamentally new approach to endpoint protection, driven by machine learning and intelligent automation. By rethinking
VMware vcloud Networking and Security Overview
 VMware vcloud Networking and Security Overview Efficient, Agile and Extensible Software-Defined Networks and Security WHITE PAPER Overview Organizations worldwide have gained significant efficiency and
VMware vcloud Networking and Security Overview Efficient, Agile and Extensible Software-Defined Networks and Security WHITE PAPER Overview Organizations worldwide have gained significant efficiency and
