Using BiDiBLAH: Very concise getting started guide.
|
|
|
- Adam Fletcher
- 5 years ago
- Views:
Transcription
1 Using BiDiBLAH: Very concise getting started guide. 1
2 Tables of contents Using BiDiBLAH... 3 Install procedure:... 3 Installing the raw socket driver:... 3 Install and/or configure your firewall... 5 Configure BiDiBLAH to your liking... 7 Notes on using Forward Notes on Reverse Notes on using the portscanner Notes on the design of BiDiBLAH
3 Using BiDiBLAH Install procedure: You need to have the.net framework installed. The install shield should assist you if you don t have it installed yet. If you plan to make use of BiDiBLAH s vulnerability scans you must install a Nessus server and/or have a valid username and password on the Nessus server. Nessus can be found at If you plan to make of the MetaSploit functionality you need to install Metasploit (>=2.4) locally on your machine the default install should be good. Metasploit can be found at BiDiBLAH uses Microsoft s Office (Word) 2003 for reporting. If you want to use BiDiBLAH to write reports you should have Office 2003 installed. Because of differences in the Office automation libraries in.net Office 2002 is not supported sorry. The crippleware version of BiDiBLAH is limited as follows: o It will exit after 7 minutes of usage this should be more than enough time to see how things work, but not enough time for script kiddies to cause real damage o The saving and loading (of data) has been disabled After the install shield has exited please following these procedures: Installing the raw socket driver: Because Microsoft decided to disable the use of raw socket for writing in XP service pack 2, BiDiBLAH uses a raw socket driver and drops down to Ethernet layer. You must thus install this driver as it is used for the asynchronous portscanner/banner grabber. Do the following: Go to the control panel, open Network connections and right click on the Local Area Connection you wish to use. Go to properties: 3
4 Go to Internet Protocol (TCP/IP) and click on Install: Choose Protocol and click on Have disk. Navigate to the ndisprot.inf file and select it (it is in the driver directory from the program base): 4
5 You will see that the driver is not signed: NB: After the driver is installed YOU NEED TO REBOOT for the install to complete. Install and/or configure your firewall BiDiBLAH sends SYN packet when doing the portscan and the banner grabber. This happens outside of the normal TCP/IP stack. The stack thus does not know about these packets. Because of this you need to do two things: 1. Disable XP s internal firewall 2. Make sure your stack does not send RST packets You can do this in two easy steps. First we need to disable the internal XP firewall. This is easy. Go to your control panel -> Windows Firewalls -> Off: 5
6 Next we need to block RST packets. You can do this on your upstream firewall but in most cases it is just easier to do it locally. Download the Windows version of the famous BSD based firewall ipfw called WIPFW (it s free, and works very nicely, a breeze to install, really powerful and way small to download). You can get WIPFW from: You should download wipfw-stable. Once you have unzipped it run the file install.cmd: After this everything happen from the command line. You can now use wipfw as you would use ipfw under Unix. You need to only add one rule to deny RST packets. This is done with this following rule: 6
7 wipfw add 5 deny TCP from any to any tcpflags rst You add this rule at the command prompt. You do something like this (assuming that wipfw was extracted in c:\tools) : On a network level we are now ready to go. Make sure that, when you are using the portscanner or the banner grabber inside of BiDiBLAH, your firewall is always configured as described above. Else BiDiBLAH WON T WORK. Configure BiDiBLAH to your liking Now open BiDiBLAH. Click on the SETUP tab: 7
8 In order to use BiDiBLAH properly you need to configure it go to the SETUP tab: At the Subdomain tab: Enter your Google API key (You can get a key at api.google.com) The Google depth (in multiples of 10) sets how many queries should be returned The Google keywords are words that BidiBLAH use to combine with queries At Forwards tab: Select where your BFDNS files are. The application will look for any file that ends with a.bfdns extension and add its content to the list of names that will be used for brute force. The test depth sets how deep within each file the application will test before assuming a naming scheme If you want to test all the entries you can check the override checkbox At Portscan tab: Enter the source IP where QAlive will send packets from. If this is not your IP address, packets will be spoofed from the address that you selected. This could be useful when you are running a tcpdump somewhere else Enter your source mac address you can get it doing an ipconfig /all in a DOS window. If you wish to spoof your mac address (why??) you may do it here. 8
9 Enter the destination mac address. Because we haven t implemented ARP you need to set this up manually. Most of the time it isn t a big deal though you will probably be scanning machines on the other side of your default gateway. That makes the destination mac address that of your default gateway. You can get this easily by looking at your ARP table. Do an arp a in a DOS window. If you are scanning locally sorry (or you can hook a router between you and your local net. We will implement ARP in a next release if there s demand for it). Load the port list file this is a single text file containing the ranges of ports you wish to see as a drop down list (in QAlive). At Nessus tab: Select the Nessus server (IP or DNS name), Nessus username and password Select where the application should find the PLG files (Nessus plugin selection file). This will appear in the plugin set drop down list in the Nessus section. At MetaSploit tab: Enter the location of Metasploit framework s web interface Enter the location of your local MSF home this is used when configuring your exploits If your exploits are already configured you can save the config strings in file and load it You should also load the MetaSploit 2 Nessus text file. This matches Nessus plugins to MetaSploit exploits The PERL interpreter used for Metasploit needs to be set You can test your Metasploit setup by clicking load exploits in the MetaSploit tab you should see a list of exploits. Double clicking on the exploit brings up the exploit configuration screen. When you are done configuring: Click on the SAVE button in the Config Load/Save section next time you start BiDiBLAH you can now just click on the blue LOAD button and you don t have to go through the whole mission again. Loading and saving configurations: Choose the Load Config tab to load a sample configuration file located in c:\bidiblah\config (if you chose defaults). The location of the BFDNS files, a default set of ports in the portlist file as well as the IP2C DB should be configured correctly. If you installed the application in a different location you need to configure these manually. At any stage you can save the configuration (and load it later again) Saving/Loading your data (DISABLED IN CRIPPLED VERSION) At any stage you can go to the SETUP tab and hit the Save button in the Data Load/Save combo. This will save the contents of all the forms the Load button will load it back into the forms. 9
10 Keep in mind that it will ADD the entries to all the forms. That s why there s a CLEAR ALL button this will clear all entries from all forms. Notes on using Forward The last entry on a line tells you what type of entry it is: FL: normal forward lookup from brute force GFL: Google forward lookup means we got the name from a Google search ZT: from a zone transfer NS: this is a name server for the domain MX: this is a mail server for the domain ZTCN: alias found in a zone transfer ZTMX: alias for an MX record found in zone transfer 10
11 Notes on Reverse Matched entries (reverse DNS entries that match the filter) get a RL at the end that s for Reverse Listing. Unmatched entries get RLNM (Reverse Listing Non- Matched). You will see that hostnames are also collected. This is done in order to create custom host list (possibly as a custom.bfdns file). The idea here is that organization might re-use host names between domains. Matched additional domains are populated by trying to figure out the domain of a reverse DNS entry where the entry matches the filter, but the domain is not found as an input domain (neither in domains or sub domains). 11
12 Notes on using the portscanner 1. YOU NEED TO DISABLE ANY HOST BASED FIREWALL. 2. Keep in mind that this process is not kind on NAT devices (it works fine but I am glad I don t need to keep state of the stuff going out). For the same reasons your admin might not be pleased when running this behind a stateful firewall. I am using it with NAT and a stateful firewall (and tunneling) and it works fine but I guess it hurts. 3. Click on the Import app button this imports the netblocks from the netblock section you may add or delete blocks here. 4. Click on Bind driver this binds the driver 5. Click on the Adaptor drop down list. Select the interface you want to use to send the packets. This might be interesting when you have multiple interfaces. 6. Select a port list from the Ports drop down. If a port file was not found in the configuration a default list of ports will be shown. 7. Hit Start. 8. You can adjust the delay on the fly (at SETUP tab > portscanner tab) I have used it down to 6ms between packets. To know if you are losing responses, do a ping in another window you can ping anything at the other end of your connection but it makes sense to ping something as close as possible to your target. As soon as you see packet loss on the ping you know you might be losing responses. 9. When the scan is done the driver will unbind this ensures that you don t forget to unbind it when using the banner scanner. 12
13 Notes on the design of BiDiBLAH 1. BiDiBLAH was built for users that understand what it is that they want to do. It was built to be as flexible as possible with a power user in mind. It was not build to be a point and click tool. If it does not work for you then you probably should not be using it in the first place. 2. As far as possible forms are text boxes these boxes are hot in other words you can make a change in the text box and it will be carried over the other parts in the application. It also means you can copy, cut and paste from these forms to reports or other applications. The exception in the filters in the reverse scan once you started the scan you cannot change the values (well you can change it but it s not going to affect the results). Keep in mind that this method limits us to do sanity checks of the text you enter. 3. The application is database-less. Information is stored in the forms itself. While this could be a pitfall in the long run it means that one can very easily make changes on the fly to the data. 4. On just about every tab you will see two buttons Import (App) and Import (file). You can either get data for the section from the previous section, or you can import it from a file. When importing from file every item is on a separate line. 5. You will also see preserve checkboxes just about everywhere. If you check this data that s in the form won t be deleted when you import new data (nice for adding stuff). 6. Almost all text based forms has two small buttons a red clr and a white s/u. The clr clears the form it does not wait for confirmation. The s/u button performs the same as an UNIX sort uniq on the text in the form nice if you suspect that duplicate entries crept in. 13
Assessment. automation: Deux ex Machina. Rube Goldberg Machine? 2005 LAS VEGAS
 Assessment automation: Deux ex Machina Rube Goldberg Machine? 2005 LAS VEGAS Before we begin.you can find all of this at: http://www.sensepost.com/research/bidiblah As promised at Amsterdam E-Or release!
Assessment automation: Deux ex Machina Rube Goldberg Machine? 2005 LAS VEGAS Before we begin.you can find all of this at: http://www.sensepost.com/research/bidiblah As promised at Amsterdam E-Or release!
SensePost. Automation - Deus ex Machina or Rube Goldberg Machine?
 SensePost Roelof Temmingh is the Technical Director of SensePost where his primary function is that of external penetration specialist. Roelof is internationally recognized for his skills in the assessment
SensePost Roelof Temmingh is the Technical Director of SensePost where his primary function is that of external penetration specialist. Roelof is internationally recognized for his skills in the assessment
MAC Address Filtering Setup (3G18Wn)
 MAC Address Filtering Setup (3G18Wn) MAC Address Filtering MAC address filtering refers to the process of allowing (or denying) access to your wireless network based on the hardware address of the device
MAC Address Filtering Setup (3G18Wn) MAC Address Filtering MAC address filtering refers to the process of allowing (or denying) access to your wireless network based on the hardware address of the device
CCNA 1 Chapter 2 v5.0 Exam Answers %
 CCNA 1 Chapter 2 v5.0 Exam Answers 2015 100% 1. Which two features are characteristics of flash memory? (Choose two.) Flash provides nonvolatile storage. Flash receives a copy of the IOS from RAM when
CCNA 1 Chapter 2 v5.0 Exam Answers 2015 100% 1. Which two features are characteristics of flash memory? (Choose two.) Flash provides nonvolatile storage. Flash receives a copy of the IOS from RAM when
Nmap & Metasploit. Chun-Jen (James) Chung. Arizona State University
 Nmap & Metasploit Chun-Jen (James) Chung Nmap recap Nmap uses raw IP packets in novel ways to determine what hosts are available on the network What services (application name and version) those hosts
Nmap & Metasploit Chun-Jen (James) Chung Nmap recap Nmap uses raw IP packets in novel ways to determine what hosts are available on the network What services (application name and version) those hosts
Figure 1-1. When we finish Part 2, our server will be ready to have workstations join the domain and start sharing files. Now here we go!
 1 of 18 9/6/2008 4:05 AM Configuring Windows Server 2003 for a Small Business Network, Part 2 Written by Cortex Wednesday, 16 August 2006 Welcome to Part 2 of the "Configuring Windows Server 2003 for a
1 of 18 9/6/2008 4:05 AM Configuring Windows Server 2003 for a Small Business Network, Part 2 Written by Cortex Wednesday, 16 August 2006 Welcome to Part 2 of the "Configuring Windows Server 2003 for a
CCNA 1 Chapter 2 v5.0 Exam Answers 2013
 CCNA 1 Chapter 2 v5.0 Exam Answers 2013 1. Refer to the exhibit. A switch was configured as shown. A ping to the default gateway was issued, but the ping was not successful. Other switches in the same
CCNA 1 Chapter 2 v5.0 Exam Answers 2013 1. Refer to the exhibit. A switch was configured as shown. A ping to the default gateway was issued, but the ping was not successful. Other switches in the same
Install & Configure Windows 10, Visual Studio, & MySQL Dr. Tom Hicks Trinity University
 Install & Configure Windows 10, Visual Studio, & MySQL Dr. Tom Hicks Trinity University Windows 10 Install 1] Push the Next Button. 2] Push the Install Now Button. Windows-Database-Server-Installation-1.docx
Install & Configure Windows 10, Visual Studio, & MySQL Dr. Tom Hicks Trinity University Windows 10 Install 1] Push the Next Button. 2] Push the Install Now Button. Windows-Database-Server-Installation-1.docx
Lesson 12 Lab Key Lab Exercises
 Lab 1 Doing a Ping Test Lesson 12 Lab Key Lab Exercises The purpose of this lab is to familiarize the student with running a ping test. This lab will also help the student correctly interpret the results
Lab 1 Doing a Ping Test Lesson 12 Lab Key Lab Exercises The purpose of this lab is to familiarize the student with running a ping test. This lab will also help the student correctly interpret the results
AWS Remote Access VPC Bundle
 AWS Remote Access VPC Bundle Deployment Guide Last updated: April 11, 2017 Aviatrix Systems, Inc. 411 High Street Palo Alto CA 94301 USA http://www.aviatrix.com Tel: +1 844.262.3100 Page 1 of 12 TABLE
AWS Remote Access VPC Bundle Deployment Guide Last updated: April 11, 2017 Aviatrix Systems, Inc. 411 High Street Palo Alto CA 94301 USA http://www.aviatrix.com Tel: +1 844.262.3100 Page 1 of 12 TABLE
How to Set-up Your DVR/NVR on a Network
 How to Set-up Your DVR/NVR on a Network Ok, you wanna view your cameras over the Internet, but you don't know how? So, you opened this guide and now you're looking at it and you're like "What!?" There's
How to Set-up Your DVR/NVR on a Network Ok, you wanna view your cameras over the Internet, but you don't know how? So, you opened this guide and now you're looking at it and you're like "What!?" There's
Test - Accredited Configuration Engineer (ACE) Exam - PAN-OS 6.0 Version
 Test - Accredited Configuration Engineer (ACE) Exam - PAN-OS 6.0 Version ACE Exam Question 1 of 50. Traffic going to a public IP address is being translated by your Palo Alto Networks firewall to your
Test - Accredited Configuration Engineer (ACE) Exam - PAN-OS 6.0 Version ACE Exam Question 1 of 50. Traffic going to a public IP address is being translated by your Palo Alto Networks firewall to your
Installing the L-Series Library Admin and Personality Module on the L180 and L700 Series Libraries
 Installing the L-Series Library Admin and Personality Module on the L180 and L700 Series Libraries The following instructions describe the installation procedures for installing the L-Series Library Admin
Installing the L-Series Library Admin and Personality Module on the L180 and L700 Series Libraries The following instructions describe the installation procedures for installing the L-Series Library Admin
Sam Spade 1.14 Open Source Security Tool by Steve Atkins
 CS 413 Spring 2005 Max Konovalov Sam Spade 1.14 Open Source Security Tool by Steve Atkins University of Alaska Anchorage Department of Mathematical Sciences This paper describes Sam Spade 1.14 open source
CS 413 Spring 2005 Max Konovalov Sam Spade 1.14 Open Source Security Tool by Steve Atkins University of Alaska Anchorage Department of Mathematical Sciences This paper describes Sam Spade 1.14 open source
How to Configure Mobile VPN for Forcepoint NGFW TECHNICAL DOCUMENT
 How to Configure Mobile VPN for Forcepoint NGFW TECHNICAL DOCUMENT Table of Contents TABLE OF CONTENTS 1 BACKGROUND 2 WINDOWS SERVER CONFIGURATION STEPS 2 CONFIGURING USER AUTHENTICATION 3 ACTIVE DIRECTORY
How to Configure Mobile VPN for Forcepoint NGFW TECHNICAL DOCUMENT Table of Contents TABLE OF CONTENTS 1 BACKGROUND 2 WINDOWS SERVER CONFIGURATION STEPS 2 CONFIGURING USER AUTHENTICATION 3 ACTIVE DIRECTORY
HOME AUTOMATION, INC. Model 93A00-1. Serial Server. User s Manual
 HOME AUTOMATION, INC. Model 93A00-1 Serial Server User s Manual Document Number 93I00-1 Rev. A December, 2009 Introduction The 93A00-1 is a RS232/RS485 to TCP/IP converter integrated with a robust system
HOME AUTOMATION, INC. Model 93A00-1 Serial Server User s Manual Document Number 93I00-1 Rev. A December, 2009 Introduction The 93A00-1 is a RS232/RS485 to TCP/IP converter integrated with a robust system
6.1. Getting Started Guide
 6.1 Getting Started Guide Netmon Getting Started Guide 2 Contents Contents... 2 Appliance Installation... 3 IP Address Assignment (Optional)... 3 Logging In For the First Time... 5 Initial Setup... 6 License
6.1 Getting Started Guide Netmon Getting Started Guide 2 Contents Contents... 2 Appliance Installation... 3 IP Address Assignment (Optional)... 3 Logging In For the First Time... 5 Initial Setup... 6 License
Configuring RentalPoint Web Services
 Table of Contents 1. What is RentalPoint Web Services? 2 2. How to Configure Your Server 2 2.1 Download and Install.NET Framework 4.5.1 2 2.2 Download and Install IIS 2 2.3 Download and Install RPWS Files
Table of Contents 1. What is RentalPoint Web Services? 2 2. How to Configure Your Server 2 2.1 Download and Install.NET Framework 4.5.1 2 2.2 Download and Install IIS 2 2.3 Download and Install RPWS Files
Lab - Observing DNS Resolution
 Objectives Part 1: Observe the DNS Conversion of a URL to an IP Address Part 2: Observe DNS Lookup Using the Nslookup Command on a Web Site Part 3: Observe DNS Lookup Using the Nslookup Command on Mail
Objectives Part 1: Observe the DNS Conversion of a URL to an IP Address Part 2: Observe DNS Lookup Using the Nslookup Command on a Web Site Part 3: Observe DNS Lookup Using the Nslookup Command on Mail
Setting Up Windows 2K VPN Connection Through The Symantec Raptor Firewall Firewall
 Setting Up Windows 2K VPN Connection Through The Symantec Raptor Firewall Firewall By: Loc Huynh Date: 24 March 2003 Table of Contents 1.0 Foreword...2 2.0 Setting VPN on VPN Server...2 3.0 Setting Symantec
Setting Up Windows 2K VPN Connection Through The Symantec Raptor Firewall Firewall By: Loc Huynh Date: 24 March 2003 Table of Contents 1.0 Foreword...2 2.0 Setting VPN on VPN Server...2 3.0 Setting Symantec
UKNova s Getting Connectable Guide
 UKNova s Getting Connectable Guide Version 1.2 2010/03/22 1. WHAT IS "BEING CONNECTABLE" AND WHY DO I NEED IT? Being connectable means being able to give back to others it is the fundamental principle
UKNova s Getting Connectable Guide Version 1.2 2010/03/22 1. WHAT IS "BEING CONNECTABLE" AND WHY DO I NEED IT? Being connectable means being able to give back to others it is the fundamental principle
If you have a computer enabled with Intel Active Management Technology
 Chapter13 Intel Active Management Technology in Small and Medium-sized Business I do not fear computers. I fear the lack of them. Isaac Asimov (1920 1992) If you have a computer enabled with Intel Active
Chapter13 Intel Active Management Technology in Small and Medium-sized Business I do not fear computers. I fear the lack of them. Isaac Asimov (1920 1992) If you have a computer enabled with Intel Active
Loadbalancer.org Virtual Appliance quick start guide v6.3
 Loadbalancer.org Virtual Appliance quick start guide v6.3 What are your objectives?...2 What is the difference between a one-arm and a two-arm configuration?...2 What are the different load balancing methods
Loadbalancer.org Virtual Appliance quick start guide v6.3 What are your objectives?...2 What is the difference between a one-arm and a two-arm configuration?...2 What are the different load balancing methods
Broadband Router DC 202
 Broadband Router DC 202 Full Manual Table of Contents DC-202 xdsl/cable Broadband router REQUIREMENTS...4 INTRODUCTION...4 DC-202 Features...4 Internet Access Features...4 Advanced Internet Functions...5
Broadband Router DC 202 Full Manual Table of Contents DC-202 xdsl/cable Broadband router REQUIREMENTS...4 INTRODUCTION...4 DC-202 Features...4 Internet Access Features...4 Advanced Internet Functions...5
Date : June 16, 2011 Version : 1
 EaseGate Guide Date : June 16, 2011 Version : 1 EaseGate Guide Copyright 2010-2011 PATRONSOFT LIMITED All rights reserved. Every effort has been made to ensure the accuracy of this guide. PATRONSOFT LIMITED
EaseGate Guide Date : June 16, 2011 Version : 1 EaseGate Guide Copyright 2010-2011 PATRONSOFT LIMITED All rights reserved. Every effort has been made to ensure the accuracy of this guide. PATRONSOFT LIMITED
2. The next screen will tell you to press the lighted Cisco logo on the Router. After you have pressed the logo, click the Next button to continue.
 2. The next screen will tell you to press the lighted Cisco logo on the Router. After you have pressed the logo, click the Next button to continue. To exit the Wireless Setup Wizard, click the Exit button.
2. The next screen will tell you to press the lighted Cisco logo on the Router. After you have pressed the logo, click the Next button to continue. To exit the Wireless Setup Wizard, click the Exit button.
Networks Lab Pod Diagram
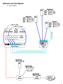 (Console cable) Networks Lab Pod Diagram (x = pod number) 190.111.50.x 190.111.x.254 PodxLinux Addr: 190.111.x.3 Mask: 255.255.255.0 GW: 190.111.x.254 DNS: 190.111.x.1 PodxServer Addr: 190.111.x.1 Mask:
(Console cable) Networks Lab Pod Diagram (x = pod number) 190.111.50.x 190.111.x.254 PodxLinux Addr: 190.111.x.3 Mask: 255.255.255.0 GW: 190.111.x.254 DNS: 190.111.x.1 PodxServer Addr: 190.111.x.1 Mask:
GSS Administration and Troubleshooting
 CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
A Practical (and Personal) Perspective on IPv6 for Servers. Geoff Huston June 2011
 A Practical (and Personal) Perspective on IPv6 for Servers Geoff Huston June 2011 Lets look at... Why we need IPv6 The differences between IPv4 and IPv6 Some practical hints for Dual Stack Services Why?
A Practical (and Personal) Perspective on IPv6 for Servers Geoff Huston June 2011 Lets look at... Why we need IPv6 The differences between IPv4 and IPv6 Some practical hints for Dual Stack Services Why?
Assignment 2 TCP/IP Vulnerabilities
 LEIC/MEIC - IST Alameda LEIC/MEIC/MERC IST Taguspark DEASegInf Network and Computer Security 2012/2013 Assignment 2 TCP/IP Vulnerabilities Goals Gather information about the machines in the network. Explore
LEIC/MEIC - IST Alameda LEIC/MEIC/MERC IST Taguspark DEASegInf Network and Computer Security 2012/2013 Assignment 2 TCP/IP Vulnerabilities Goals Gather information about the machines in the network. Explore
Lab - Using Wireshark to Examine a UDP DNS Capture
 Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
agility17dns Release latest Jun 15, 2017
 agility17dns d ocsdocumentation Release latest Jun 15, 2017 Contents 1 Lab Access 1 2 Network Topology 3 3 GSLB 5 3.1 Initial Setup............................................... 5 3.2 Logging..................................................
agility17dns d ocsdocumentation Release latest Jun 15, 2017 Contents 1 Lab Access 1 2 Network Topology 3 3 GSLB 5 3.1 Initial Setup............................................... 5 3.2 Logging..................................................
SP PRO Communications Internet Connectivity
 SP PRO Communications Internet Connectivity Introduction Being able to remotely communicate with a SP PRO installation can provide many advantages. These include the ability to monitor system performance,
SP PRO Communications Internet Connectivity Introduction Being able to remotely communicate with a SP PRO installation can provide many advantages. These include the ability to monitor system performance,
Static routing KTHNOC/SUNET. January 18, 2004
 Static routing KTHNOC/SUNET January 18, 2004 The goal with this lab is to introduce you to configuring a Cisco router and your workstation. You will also learn how to set up the router for static routing.
Static routing KTHNOC/SUNET January 18, 2004 The goal with this lab is to introduce you to configuring a Cisco router and your workstation. You will also learn how to set up the router for static routing.
Implementing DVN. directpacket Product Guide
 Implementing DVN directpacket Product Guide directpacket Research www.directpacket.com 2 1 DVN and the IPC Community The Secure Dedicated Versatile Network (DVN) Server is a hardened internet facing device
Implementing DVN directpacket Product Guide directpacket Research www.directpacket.com 2 1 DVN and the IPC Community The Secure Dedicated Versatile Network (DVN) Server is a hardened internet facing device
SonicWALL / Toshiba General Installation Guide
 SonicWALL / Toshiba General Installation Guide SonicWALL currently maintains two operating systems for its Unified Threat Management (UTM) platform, StandardOS and EnhancedOS. When a SonicWALL is implemented
SonicWALL / Toshiba General Installation Guide SonicWALL currently maintains two operating systems for its Unified Threat Management (UTM) platform, StandardOS and EnhancedOS. When a SonicWALL is implemented
ISA 674 Understanding Firewalls & NATs
 ISA 674 Understanding & NATs Angelos Stavrou September 12, 2012 Types of Types of Schematic of a Firewall Conceptual Pieces Packet UDP Packet Dynamic Packet Application Gateways Circuit Relays Personal
ISA 674 Understanding & NATs Angelos Stavrou September 12, 2012 Types of Types of Schematic of a Firewall Conceptual Pieces Packet UDP Packet Dynamic Packet Application Gateways Circuit Relays Personal
PreLab for CS356 Lab NIL (Lam) (To be submitted when you come for the lab)
 PreLab for CS356 Lab NIL (Lam) (To be submitted when you come for the lab) Name: UT EID: 1. Differentiate between Routers, Switches, and Hubs. 2. Explain subnet masks. 3. For this lab, where is subnet
PreLab for CS356 Lab NIL (Lam) (To be submitted when you come for the lab) Name: UT EID: 1. Differentiate between Routers, Switches, and Hubs. 2. Explain subnet masks. 3. For this lab, where is subnet
Endian Proxy / Firewall
 Endian Proxy / Firewall Created October 27, 2006 by Bruce A. Westbrook Revisions: Introduction This document describes the step by step process of installing and configuring the Endian Firewall, Community
Endian Proxy / Firewall Created October 27, 2006 by Bruce A. Westbrook Revisions: Introduction This document describes the step by step process of installing and configuring the Endian Firewall, Community
Step-by-Step Configuration
 Step-by-Step Configuration Kerio Technologies C 2001-2004 Kerio Technologies. All Rights Reserved. Printing Date: April 25, 2004 This guide provides detailed description on configuration of the local network
Step-by-Step Configuration Kerio Technologies C 2001-2004 Kerio Technologies. All Rights Reserved. Printing Date: April 25, 2004 This guide provides detailed description on configuration of the local network
CS 356 Lab #1: Basic LAN Setup & Packet capture/analysis using Ethereal
 CS 356 Lab #1: Basic LAN Setup & Packet capture/analysis using Ethereal Tasks: Time: 2:00 hrs (Task 1-6 should take 45 min; the rest of the time is for Ethereal) 1 - Verify that TCP/IP is installed on
CS 356 Lab #1: Basic LAN Setup & Packet capture/analysis using Ethereal Tasks: Time: 2:00 hrs (Task 1-6 should take 45 min; the rest of the time is for Ethereal) 1 - Verify that TCP/IP is installed on
FW- 525B Quick Start Guide
 FW- 525B Quick Start Guide 2013 Rubicon Communications, LP Contents Introduction... 3 Plugging everything in... 3 Description of Port Indicators... 3 Initial Configuration... 4 Logging into the web interface...
FW- 525B Quick Start Guide 2013 Rubicon Communications, LP Contents Introduction... 3 Plugging everything in... 3 Description of Port Indicators... 3 Initial Configuration... 4 Logging into the web interface...
CHAPTER 7 ADVANCED ADMINISTRATION PC
 ii Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband ADSL Router Features... 1 Package Contents... 3 Physical Details... 4 CHAPTER 2 INSTALLATION... 6 Requirements... 6 Procedure... 6 CHAPTER 3 SETUP...
ii Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband ADSL Router Features... 1 Package Contents... 3 Physical Details... 4 CHAPTER 2 INSTALLATION... 6 Requirements... 6 Procedure... 6 CHAPTER 3 SETUP...
Configuring DDoS Prevention
 CHAPTER 10 This chapter describes how to configure a GSS to prevent Distributed Denial of Service (DDoS) attacks. It contains the following major sections: Logging in to the CLI and Enabling Privileged
CHAPTER 10 This chapter describes how to configure a GSS to prevent Distributed Denial of Service (DDoS) attacks. It contains the following major sections: Logging in to the CLI and Enabling Privileged
Port Forwarding Setup (NB7)
 Port Forwarding Setup (NB7) Port Forwarding Port forwarding enables programs or devices running on your LAN to communicate with the internet as if they were directly connected. This is most commonly used
Port Forwarding Setup (NB7) Port Forwarding Port forwarding enables programs or devices running on your LAN to communicate with the internet as if they were directly connected. This is most commonly used
SOA Software API Gateway Appliance 6.3 Administration Guide
 SOA Software API Gateway Appliance 6.3 Administration Guide Trademarks SOA Software and the SOA Software logo are either trademarks or registered trademarks of SOA Software, Inc. Other product names, logos,
SOA Software API Gateway Appliance 6.3 Administration Guide Trademarks SOA Software and the SOA Software logo are either trademarks or registered trademarks of SOA Software, Inc. Other product names, logos,
Configuring a Palo Alto Firewall in AWS
 Configuring a Palo Alto Firewall in AWS Version 1.0 10/19/2015 GRANT CARMICHAEL, MBA, CISSP, RHCA, ITIL For contact information visit Table of Contents The Network Design... 2 Step 1 Building the AWS network...
Configuring a Palo Alto Firewall in AWS Version 1.0 10/19/2015 GRANT CARMICHAEL, MBA, CISSP, RHCA, ITIL For contact information visit Table of Contents The Network Design... 2 Step 1 Building the AWS network...
Firewalls. Types of Firewalls. Schematic of a Firewall. Conceptual Pieces Packet Filters Stateless Packet Filtering. UDP Filtering.
 Network Security - ISA 656 & NATs Angelos Stavrou Types of Schematic of a Conceptual Pieces Packet UDP Types of Packet Dynamic Packet Application Gateways Circuit Relays Personal /or Distributed Many firewalls
Network Security - ISA 656 & NATs Angelos Stavrou Types of Schematic of a Conceptual Pieces Packet UDP Types of Packet Dynamic Packet Application Gateways Circuit Relays Personal /or Distributed Many firewalls
Internet Load Balancing Guide. Peplink Balance Series. Peplink Balance. Internet Load Balancing Solution Guide
 Peplink Balance Internet Load Balancing Solution Guide http://www.peplink.com Copyright 2010 Peplink Internet Load Balancing Instant Improvement to Your Network Introduction Introduction Understanding
Peplink Balance Internet Load Balancing Solution Guide http://www.peplink.com Copyright 2010 Peplink Internet Load Balancing Instant Improvement to Your Network Introduction Introduction Understanding
Windows Help document Part A
 Compiled by: Todd Johnstone Before starting these steps, open a Word document, save it in documents in a folder called computing problems and use that document to capture items that show as bad as you
Compiled by: Todd Johnstone Before starting these steps, open a Word document, save it in documents in a folder called computing problems and use that document to capture items that show as bad as you
Link Gateway Initial Configuration Manual
 Link Gateway Initial Configuration Manual Copyright 2016 NetLinkz. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
Link Gateway Initial Configuration Manual Copyright 2016 NetLinkz. All Rights Reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated
Wireless Setup Instructions
 Wireless Setup Instructions THESE INSTRUCTIONS ARE VERY IMPORTANT TO SECURE YOUR WIRELESS NETWORK The purpose of this procedure is to "lock" your router so other users can not access your network without
Wireless Setup Instructions THESE INSTRUCTIONS ARE VERY IMPORTANT TO SECURE YOUR WIRELESS NETWORK The purpose of this procedure is to "lock" your router so other users can not access your network without
Packet: Data can be broken into distinct pieces or packets and then reassembled after delivery. Computers on the Internet communicate via packets.
 Broadband Setup from A to Z Print out all the info below and get to work...have fun!! A word of caution! It is very important that you SECURE your wireless network using WEP or WPA encryption (password).
Broadband Setup from A to Z Print out all the info below and get to work...have fun!! A word of caution! It is very important that you SECURE your wireless network using WEP or WPA encryption (password).
Computer Security and Privacy
 CSE P 590 / CSE M 590 (Spring 2010) Computer Security and Privacy Tadayoshi Kohno Thanks to Dan Boneh, Dieter Gollmann, John Manferdelli, John Mitchell, Vitaly Shmatikov, Bennet Yee, and many others for
CSE P 590 / CSE M 590 (Spring 2010) Computer Security and Privacy Tadayoshi Kohno Thanks to Dan Boneh, Dieter Gollmann, John Manferdelli, John Mitchell, Vitaly Shmatikov, Bennet Yee, and many others for
NetBrain OE System Quick Start Guide
 NetBrain Technologies Inc. NetBrain OE System Quick Start Guide For Operator Edition Administrators Table of Contents 1. Install NetBrain OE System... 3 1.1 Install Gateway Server... 4 1.2 Install Network
NetBrain Technologies Inc. NetBrain OE System Quick Start Guide For Operator Edition Administrators Table of Contents 1. Install NetBrain OE System... 3 1.1 Install Gateway Server... 4 1.2 Install Network
Security Concerns With Tunneling draft-ietf-v6ops-tunnel-security-concerns-00
 Security Concerns With Tunneling draft-ietf-v6ops-tunnel-security-concerns-00 Dave Thaler Suresh Krishnan Jim Hoagland IETF 72 1 Status Formerly draft-ietf-v6ops-teredo-securityconcerns-02.txt Most points
Security Concerns With Tunneling draft-ietf-v6ops-tunnel-security-concerns-00 Dave Thaler Suresh Krishnan Jim Hoagland IETF 72 1 Status Formerly draft-ietf-v6ops-teredo-securityconcerns-02.txt Most points
TCP/IP Diagnostic Utilities on Windows 2008 Server
 TCP/IP Diagnostic Utilities on Windows 2008 Server June 20, 2012 Copyright 2012 by World Class CAD, LLC. All Rights Reserved. TCP/IP Utilities In this lesson, we will learn about how to use the TCP/IP
TCP/IP Diagnostic Utilities on Windows 2008 Server June 20, 2012 Copyright 2012 by World Class CAD, LLC. All Rights Reserved. TCP/IP Utilities In this lesson, we will learn about how to use the TCP/IP
An Introduction to Google Calendar
 An Introduction to Google Calendar Google Calendar is a Google App that is a great resource to use to manage your everyday tasks and activities. It integrates with your Gmail and other Google Apps so you
An Introduction to Google Calendar Google Calendar is a Google App that is a great resource to use to manage your everyday tasks and activities. It integrates with your Gmail and other Google Apps so you
TexSaw Penetration Te st in g
 TexSaw Penetration Te st in g What is penetration testing? The process of breaking something or using something for an unintended used case for the purpose of bettering the system or application. This
TexSaw Penetration Te st in g What is penetration testing? The process of breaking something or using something for an unintended used case for the purpose of bettering the system or application. This
Hackveda Training - Ethical Hacking, Networking & Security
 Hackveda Training - Ethical Hacking, Networking & Security Day1: Hacking windows 7 / 8 system and security Part1 a.) Windows Login Password Bypass manually without CD / DVD b.) Windows Login Password Bypass
Hackveda Training - Ethical Hacking, Networking & Security Day1: Hacking windows 7 / 8 system and security Part1 a.) Windows Login Password Bypass manually without CD / DVD b.) Windows Login Password Bypass
RX3041. User's Manual
 RX3041 User's Manual Table of Contents 1 Introduction... 2 1.1 Features and Benefits... 3 1.2 Package Contents... 3 1.3 Finding Your Way Around... 4 1.4 System Requirements... 6 1.5 Installation Instruction...
RX3041 User's Manual Table of Contents 1 Introduction... 2 1.1 Features and Benefits... 3 1.2 Package Contents... 3 1.3 Finding Your Way Around... 4 1.4 System Requirements... 6 1.5 Installation Instruction...
Upgrading from TrafficShield 3.2.X to Application Security Module 9.2.3
 Upgrading from TrafficShield 3.2.X to Application Security Module 9.2.3 Introduction Preparing the 3.2.X system for the upgrade Installing the BIG-IP version 9.2.3 software Licensing the software using
Upgrading from TrafficShield 3.2.X to Application Security Module 9.2.3 Introduction Preparing the 3.2.X system for the upgrade Installing the BIG-IP version 9.2.3 software Licensing the software using
6. 3. Media Sharing Access the USB disk. 5. Click OK. Tips:
 Chapter 6 USB Application 5. Click OK. Tips: The router can share 32 volumes at most. You can click not need to share. on the page to detach the corresponding volume you do 6. 3. Media Sharing The feature
Chapter 6 USB Application 5. Click OK. Tips: The router can share 32 volumes at most. You can click not need to share. on the page to detach the corresponding volume you do 6. 3. Media Sharing The feature
Configuration Guide. For Managing EAPs via EAP Controller
 Guide For Managing EAPs via EAP Controller 1910012313 REV1.0.0 December 2017 CONTENTS 1 Overview... 1 2 Configuration... 2 2.1 Managing EAPs in the Same Subnet... 2 2.2 Managing EAPs in Different Subnets...
Guide For Managing EAPs via EAP Controller 1910012313 REV1.0.0 December 2017 CONTENTS 1 Overview... 1 2 Configuration... 2 2.1 Managing EAPs in the Same Subnet... 2 2.2 Managing EAPs in Different Subnets...
INBOUND AND OUTBOUND NAT
 INBOUND AND OUTBOUND NAT Network Address Translation Course # 2011 1 Overview! Network Address Translation (NAT)! Aliases! Static Address Mappings! Inbound Tunnels! Advanced Tunnel Option SYN Cookies Authentication
INBOUND AND OUTBOUND NAT Network Address Translation Course # 2011 1 Overview! Network Address Translation (NAT)! Aliases! Static Address Mappings! Inbound Tunnels! Advanced Tunnel Option SYN Cookies Authentication
DOWNLOAD PDF CISCO ASA 5505 CONFIGURATION GUIDE
 Chapter 1 : Cisco ASA DMZ Configuration Example â Speak Network Solutions Cisco ASA Quick Start Guide. Step 1 Connect the power supply adaptor to the power cable.. Step 2 Connect the rectangular connector
Chapter 1 : Cisco ASA DMZ Configuration Example â Speak Network Solutions Cisco ASA Quick Start Guide. Step 1 Connect the power supply adaptor to the power cable.. Step 2 Connect the rectangular connector
Detecting Specific Threats
 The following topics explain how to use preprocessors in a network analysis policy to detect specific threats: Introduction to Specific Threat Detection, page 1 Back Orifice Detection, page 1 Portscan
The following topics explain how to use preprocessors in a network analysis policy to detect specific threats: Introduction to Specific Threat Detection, page 1 Back Orifice Detection, page 1 Portscan
CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists
 CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists Name: In this lab you will learn: PartA Cisco 2600 Router Configuration Static Routing PartB 20 min Dynamic
CS 326e Lab 2, Edmondson-Yurkanan, Spring 2004 Router Configuration, Routing and Access Lists Name: In this lab you will learn: PartA Cisco 2600 Router Configuration Static Routing PartB 20 min Dynamic
SAGEMCOM 5355 GATEWAY
 SAGEMCOM F@ST 5355 GATEWAY Disclaimer This is not an official document. I am not employed by Telstra nor am I an IT person. I wrote this document because setting up my gateway was a hassle due to the lack
SAGEMCOM F@ST 5355 GATEWAY Disclaimer This is not an official document. I am not employed by Telstra nor am I an IT person. I wrote this document because setting up my gateway was a hassle due to the lack
Comodo One Software Version 3.8
 rat Comodo One Software Version 3.8 Dome Cloud Firewall Quick Start Guide Guide Version 1.1.061118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo Dome Cloud Firewall Quick Start This
rat Comodo One Software Version 3.8 Dome Cloud Firewall Quick Start Guide Guide Version 1.1.061118 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo Dome Cloud Firewall Quick Start This
Access Switch VLAN Y Y.1 /24
 Topology: Fa 0/1 VNC Server Fa 0/0 Port B Access Router Trunk VLAN X Access Switch VLAN Y Backbone Router 141.85.Y.1 /24 28.0.0.42 OSPF X.0.0.0/8 Port A 27.45.67.89 Work Station DHCP Server The Goal: Connect
Topology: Fa 0/1 VNC Server Fa 0/0 Port B Access Router Trunk VLAN X Access Switch VLAN Y Backbone Router 141.85.Y.1 /24 28.0.0.42 OSPF X.0.0.0/8 Port A 27.45.67.89 Work Station DHCP Server The Goal: Connect
Basics of executing a penetration test
 Basics of executing a penetration test 25.04.2013, WrUT BAITSE guest lecture Bernhards Blumbergs, CERT.LV Outline Reconnaissance and footprinting Scanning and enumeration System exploitation Outline Reconnaisance
Basics of executing a penetration test 25.04.2013, WrUT BAITSE guest lecture Bernhards Blumbergs, CERT.LV Outline Reconnaissance and footprinting Scanning and enumeration System exploitation Outline Reconnaisance
LevelOne FBR User s Manual. 1W, 4L 10/100 Mbps ADSL Router. Ver
 LevelOne FBR-1416 1W, 4L 10/100 Mbps ADSL Router User s Manual Ver 1.00-0510 Table of Contents CHAPTER 1 INTRODUCTION... 1 FBR-1416 Features... 1 Package Contents... 3 Physical Details... 3 CHAPTER 2
LevelOne FBR-1416 1W, 4L 10/100 Mbps ADSL Router User s Manual Ver 1.00-0510 Table of Contents CHAPTER 1 INTRODUCTION... 1 FBR-1416 Features... 1 Package Contents... 3 Physical Details... 3 CHAPTER 2
NETWORK LAB 2 Configuring Switch Desktop
 Configuring Switch 1. Select the switch tab and then add a switch from the list of switches we have to the workspace, we will choose (2950-24) switch. 2. Add a number of PCs next to the switch in order
Configuring Switch 1. Select the switch tab and then add a switch from the list of switches we have to the workspace, we will choose (2950-24) switch. 2. Add a number of PCs next to the switch in order
ELEC5616 COMPUTER & NETWORK SECURITY
 ELEC5616 COMPUTER & NETWORK SECURITY Lecture 17: Network Protocols I IP The Internet Protocol (IP) is a stateless protocol that is used to send packets from one machine to another using 32- bit addresses
ELEC5616 COMPUTER & NETWORK SECURITY Lecture 17: Network Protocols I IP The Internet Protocol (IP) is a stateless protocol that is used to send packets from one machine to another using 32- bit addresses
AppWizard Installation/Upgrade Guide (v.4.00)
 AppWizard Installation/Upgrade Guide (v.4.00) Last Updated: 15 September 2010 1 Introduction This manual is intended for the installation or upgrade of AppWizard 5.00. Please ensure that all steps are
AppWizard Installation/Upgrade Guide (v.4.00) Last Updated: 15 September 2010 1 Introduction This manual is intended for the installation or upgrade of AppWizard 5.00. Please ensure that all steps are
Table of contents. Digifobpro User Instructions - WiFi Module Page - 2
 Table of contents WiFi Module - What is it? 3 Configure WiFi on your digifobpro 4 Server Settings 5-7 Connecting digifobpro to your PC 8 Functions menu in digiconnect 9 Configuring WiFi using digiconnect
Table of contents WiFi Module - What is it? 3 Configure WiFi on your digifobpro 4 Server Settings 5-7 Connecting digifobpro to your PC 8 Functions menu in digiconnect 9 Configuring WiFi using digiconnect
CSC 574 Computer and Network Security. TCP/IP Security
 CSC 574 Computer and Network Security TCP/IP Security Alexandros Kapravelos kapravelos@ncsu.edu (Derived from slides by Will Enck and Micah Sherr) Network Stack, yet again Application Transport Network
CSC 574 Computer and Network Security TCP/IP Security Alexandros Kapravelos kapravelos@ncsu.edu (Derived from slides by Will Enck and Micah Sherr) Network Stack, yet again Application Transport Network
SelfMon VirtualKeypad Configuration Guide
 SelfMon VirtualKeypad Configuration Guide Typical System Configuration TCP Port 10001 Port Forward to Internal Panel IP Address Panel with Internal IP Address Internal Wifi Connection Internal IP Address
SelfMon VirtualKeypad Configuration Guide Typical System Configuration TCP Port 10001 Port Forward to Internal Panel IP Address Panel with Internal IP Address Internal Wifi Connection Internal IP Address
Computer Security II Lab Network Security
 Computer Security II Lab Network Security Setup Boot lab machine into Windows. In Windows Explorer, navigate to \\evs2\compga02\ and download the three Virtual Machines clientvm1819.zip, servervm1819.zip
Computer Security II Lab Network Security Setup Boot lab machine into Windows. In Windows Explorer, navigate to \\evs2\compga02\ and download the three Virtual Machines clientvm1819.zip, servervm1819.zip
Networking Basics Sharing a network printer
 Networking Basics Sharing a network printer To check for proper installation: Go to Start > Printers and Faxes. The printer icon will appear at right, indicating proper installation. You have completed
Networking Basics Sharing a network printer To check for proper installation: Go to Start > Printers and Faxes. The printer icon will appear at right, indicating proper installation. You have completed
8.9.2 Lab: Configure an Ethernet NIC to use DHCP in Windows Vista
 8.9.2 Lab: Configure an Ethernet NIC to use DHCP in Windows Vista Introduction If Vista is not available in your classroom, you may complete this lab by viewing the figures in this document. Print and
8.9.2 Lab: Configure an Ethernet NIC to use DHCP in Windows Vista Introduction If Vista is not available in your classroom, you may complete this lab by viewing the figures in this document. Print and
M1 Z Wave Gateway Setup Guide
 M1 Z Wave Gateway Setup Guide Introduction Revision 1.1 This setup guide will guide you through the steps on setting up the Ness M1 Z Wave Gateway. Hardware Required M1XEP (Ethernet Module) with M1XEP
M1 Z Wave Gateway Setup Guide Introduction Revision 1.1 This setup guide will guide you through the steps on setting up the Ness M1 Z Wave Gateway. Hardware Required M1XEP (Ethernet Module) with M1XEP
Lab - Using Wireshark to Examine a UDP DNS Capture
 Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Topology Objectives Part 1: Record a PC s IP Configuration Information Part 2: Use Wireshark to Capture DNS Queries and Responses Part 3: Analyze Captured DNS or UDP Packets Background / Scenario If you
Lab 8: Introduction to Pen Testing (HPING)
 Lab 8: Introduction to Pen Testing (HPING) Aim: To provide a foundation in understanding of email with a focus on hping to provide security assessments and in understanding the trails of evidence produced.
Lab 8: Introduction to Pen Testing (HPING) Aim: To provide a foundation in understanding of email with a focus on hping to provide security assessments and in understanding the trails of evidence produced.
DC-228. ADSL2+ Modem/Router. User Manual. -Annex A- Version: 1.0
 DC-228 ADSL2+ Modem/Router -Annex A- User Manual Version: 1.0 TABLE OF CONTENTS 1 PACKAGE CONTENTS...3 2 PRODUCT LAYOUT...4 3 NETWORK + SYSTEM REQUIREMENTS...6 4 DC-228 PLACEMENT...6 5 SETUP LAN, WAN...7
DC-228 ADSL2+ Modem/Router -Annex A- User Manual Version: 1.0 TABLE OF CONTENTS 1 PACKAGE CONTENTS...3 2 PRODUCT LAYOUT...4 3 NETWORK + SYSTEM REQUIREMENTS...6 4 DC-228 PLACEMENT...6 5 SETUP LAN, WAN...7
AirCruiser G Wireless Router GN-BR01G
 AirCruiser G Wireless Router GN-BR01G User s Guide i Contents Chapter 1 Introduction... 1 Overview...1 Features...1 Package Contents...2 AirCruiser G Wireless Router Rear Panel...2 AirCruiser G Wireless
AirCruiser G Wireless Router GN-BR01G User s Guide i Contents Chapter 1 Introduction... 1 Overview...1 Features...1 Package Contents...2 AirCruiser G Wireless Router Rear Panel...2 AirCruiser G Wireless
MikroTik lifehacking. Daniel Starnowski
 MikroTik lifehacking Daniel Starnowski About me Daniel Starnowski MikroTik user since 2008 MikroTik trainer since 2011 daniel@startik.net What is lifehacking MikroTik lifehacking MikroTik live hacking
MikroTik lifehacking Daniel Starnowski About me Daniel Starnowski MikroTik user since 2008 MikroTik trainer since 2011 daniel@startik.net What is lifehacking MikroTik lifehacking MikroTik live hacking
XBox Setup.
 XBox Setup (NB604) XBox Setup There are two ways of allowing your XBox to communicate with the internet. One is through port forwarding and the other is through the DMZ feature. Port forwarding will enable
XBox Setup (NB604) XBox Setup There are two ways of allowing your XBox to communicate with the internet. One is through port forwarding and the other is through the DMZ feature. Port forwarding will enable
History Page. Barracuda NextGen Firewall F
 The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
The Firewall > History page is very useful for troubleshooting. It provides information for all traffic that has passed through the Barracuda NG Firewall. It also provides messages that state why traffic
Configuring OpenVPN on pfsense
 Configuring OpenVPN on pfsense Configuring OpenVPN on pfsense Posted by Glenn on Dec 29, 2013 in Networking 0 comments In this article I will go through the configuration of OpenVPN on the pfsense platform.
Configuring OpenVPN on pfsense Configuring OpenVPN on pfsense Posted by Glenn on Dec 29, 2013 in Networking 0 comments In this article I will go through the configuration of OpenVPN on the pfsense platform.
Openvpn Client Do Not Change Default Gateway
 Openvpn Client Do Not Change Default Gateway I currently have a router using OpenVPN in client mode to connect to a host Is it possible to make OpenVPN the default gateway for everyone connected So what
Openvpn Client Do Not Change Default Gateway I currently have a router using OpenVPN in client mode to connect to a host Is it possible to make OpenVPN the default gateway for everyone connected So what
REMOTE ACCESS DDNS CONFIGURATION MANUAL
 REMOTE ACCESS DDNS CONFIGURATION MANUAL NVR IP Series 1 www.mezory.com INTRODUCTION TO REMOTE ACCESS As the World sinks into one global village, reliable connectivity is one of the most demanding facilities
REMOTE ACCESS DDNS CONFIGURATION MANUAL NVR IP Series 1 www.mezory.com INTRODUCTION TO REMOTE ACCESS As the World sinks into one global village, reliable connectivity is one of the most demanding facilities
Computer Network Vulnerabilities
 Computer Network Vulnerabilities Objectives Explain how routers are used to protect networks Describe firewall technology Describe intrusion detection systems Describe honeypots Routers Routers are like
Computer Network Vulnerabilities Objectives Explain how routers are used to protect networks Describe firewall technology Describe intrusion detection systems Describe honeypots Routers Routers are like
ch02 True/False Indicate whether the statement is true or false.
 ch02 True/False Indicate whether the statement is true or false. 1. No matter what medium connects computers on a network copper wires, fiber-optic cables, or a wireless setup the same protocol must be
ch02 True/False Indicate whether the statement is true or false. 1. No matter what medium connects computers on a network copper wires, fiber-optic cables, or a wireless setup the same protocol must be
Wireless-G Router User s Guide
 Wireless-G Router User s Guide 1 Table of Contents Chapter 1: Introduction Installing Your Router System Requirements Installation Instructions Chapter 2: Preparing Your Network Preparing Your Network
Wireless-G Router User s Guide 1 Table of Contents Chapter 1: Introduction Installing Your Router System Requirements Installation Instructions Chapter 2: Preparing Your Network Preparing Your Network
Sucuri Webinar Q&A HOW TO IDENTIFY AND FIX A HACKED WORDPRESS WEBSITE. Ben Martin - Remediation Team Lead
 Sucuri Webinar Q&A HOW TO IDENTIFY AND FIX A HACKED WORDPRESS WEBSITE. Ben Martin - Remediation Team Lead 1 Question #1: What is the benefit to spammers for using someone elses UA code and is there a way
Sucuri Webinar Q&A HOW TO IDENTIFY AND FIX A HACKED WORDPRESS WEBSITE. Ben Martin - Remediation Team Lead 1 Question #1: What is the benefit to spammers for using someone elses UA code and is there a way
F5 WANJet 200. Quick Start Guide. Quick Start Overview
 F5 WANJet 200 Quick Start Guide Quick Start Overview Following is a high level overview of the steps required to successfully install and configure your F5 WANJet 200 appliance. For detailed instructions
F5 WANJet 200 Quick Start Guide Quick Start Overview Following is a high level overview of the steps required to successfully install and configure your F5 WANJet 200 appliance. For detailed instructions
4-Port Router. Share your broadband Internet connection. E Wired. Ethernet. Ethernet. User Manual. F5D5231-4_uk
 4-Port Router Share your broadband Internet connection User Manual E Wired Ethernet Ethernet 10/100 Mbps F5D5231-4_uk Table of Contents 1 Introduction............................................. 1 Benefits
4-Port Router Share your broadband Internet connection User Manual E Wired Ethernet Ethernet 10/100 Mbps F5D5231-4_uk Table of Contents 1 Introduction............................................. 1 Benefits
UPDATING SOCRATES Version Build May 2018
 UPDATING SOCRATES Version 3.5.8.7 Build 10124 May 2018 10124 Update ALL USERS... 1 MAC USERS... 1 When to run the update... 1 XP USERS... 1 How often to update... 1 Registering to access the client section
UPDATING SOCRATES Version 3.5.8.7 Build 10124 May 2018 10124 Update ALL USERS... 1 MAC USERS... 1 When to run the update... 1 XP USERS... 1 How often to update... 1 Registering to access the client section
