DOWNLOAD PDF CISCO ASA 5505 CONFIGURATION GUIDE
|
|
|
- Winfred Pearson
- 5 years ago
- Views:
Transcription
1 Chapter 1 : Cisco ASA DMZ Configuration Example â Speak Network Solutions Cisco ASA Quick Start Guide. Step 1 Connect the power supply adaptor to the power cable.. Step 2 Connect the rectangular connector of the power supply adaptor to the power connector on the rear panel of the ASA. Now when your router is restarted you will get this question: Pre-configure Firewall now through interactive prompts [yes]? Now we can start the configuration. The 1st thing you want to do is get into configuration mode. This means your in configuration mode. Now we will give our ASA another hostname. Privilege 15 is the highest of the privileges and gives you full control over the device. Security level for "inside" set to by default. With security levels you can always go from high to low 0 but never the other way around unless configured otherwise. This means that no one from the outside can start a session to the inside. So far for the inside VLAN. Now we will start on the outside WAN configuration. Depending on the provider you might have to do this a little bit different but I will start with a static IP address first. Security level for outside set to 0 by default. You also need to make a static route if your provider supplied you with a static IP address. This is called the default gateway. ExampleASA config interface vlan 2 ExampleASA config-if ip address dhcp setroute ExampleASA config-if nameif outside With this command you dont need to configure a default gateway since you will get this from your provider. And now to make internet work from your inside network we have to configure NAT. The interface part means that you use your interface IP address to translate to. In this case the outside interface. ExampleASA config nat inside 10 This links the inside network to the outside global. The subnet behind that states that the network You now should have an internet connection! But now you want to manage the ASA without having to walk to the server room all the time. First we start with SSH. The name for the keys will be: ExampleASA config ssh Next, we enable the ASDM graphic interface. You can do this by saving the configuration with the following command. ExampleASA config write mem Cryptochecksum: You are now finished with configuring your ASA. Next time I will go into the more detailed configuration of an ASA. Currently working as Cisco Engineer at Neon-Networking. Page 1
2 Chapter 2 : HowTo: Basic ASA configuration - racedaydvl.com Forums The Cisco ASA Firewall is the smallest model in the new Cisco series of hardware appliances. Although this model is suitable for small businesses, branch offices or even home use, its firewall security capabilities are the same as the biggest models (,, etc). Do you have a guest Wi-Fi enabled but you do not want visitors to access your internal resource? The information in this session applies to legacy Cisco ASA s i. Since ASA code version 8. We will cover the configuration for both pre You can download the entire lab setup and configuration files for FREE As part of our documentation effort, we maintain current and accurate information we provided. Documentations are routinely reviewed and updated. We ask for your address to keep you notified when the article is updated. Their security level from high to low is as following: LAN is considered the most secured network. It not only hosts internal user workstations as well as mission critical production servers. LAN users can reach other networks. However, no inbound access is allowed from any other networks unless explicitly allowed. DMZ1 hosts public facing web servers. Any one on the Internet can reach the servers on TCP port DMZ2 is designed as untrusted guest network. Its sole purpose is providing Internet access for visitors. But we do not want to open any firewall holes to our most secured network. The concept is not Cisco specific. It applies to any other business grade firewalls. By default, traffic passing from a lower to higher security level is denied. This can be overridden by an ACL applied to that lower security interface. Also the ASA, by default, will allow traffic from higher to lower security interfaces. This behavior can also be overridden with an ACL. The security levels are defined by numeric numbers between 0 and And is the most secured network. In our example we assign security levels as following: Lab topology setup In our lab, we used one host in each network to represent the characteristics of that subnet. A host is placed on the internet side for testing. Their security levels are: You do not need an ACL because all outbound traffic is traversing from higher security level inside, dmz1 and dmz2 to lower security level outside. The reason we want to give it the least preference is to avoid possible conflict with other NAT rules. The first of the two, Object NAT, is configured within the definition of a network object. This is the easiest form of NAT, but with that ease comes with a limitation in configuration granularity. For example, you cannot make translation decision based on the destination in the packet as you could with the second type of NAT, Manual NAT. Manual NAT is more robust in its granularity, but it requires that the lines be configured in the correct order in order to achieve the correct behavior. Traffic that does not match any NAT rules will traverse the firewall without any translation like NAT exemption but without explicitly configuring it, more like an implicit NAT exemption. The static and global keywords are deprecated. Next is configuring a default gateway and route all traffic to the upstream ISP. It allows icmp return traffic to pass the ASA while the Ping is initiated from inside hosts. Configure static NAT to web servers, grant Internet inbound access to web servers First we define two objects for the web server, one for its internal IP and one for its public facing IP. You can only have one set of configuration at a time. It is important to understand that these NAT rules are bi-directional in nature. As a result you can re-phrase this sentence by flipping the wording around. The result makes a lot more sense: When hosts on the outside establish a connection to Because traffic from the outside to the dmz1 network is denied by the ASA by default, users on the Internet cannot reach the web server despite the NAT configuration. We will need to configure ACLs and allow Internet inbound traffic to access the web server. In earlier versions of ASA code 8. In other words, the ACL had to permit the packet as if you were to capture that packet on the interface. This means that for 8. All other segment access is denied. The default rules can be overwritten by ACLs. In our example, we need the guests in dmz2 to be able to use the DNS servers in dmz1. We added three more lines to deny access to dmz1 and inside networks while allowing the reset of traffic to go to the Internet. What about ACLs on dmz1 and inside interfaces? We do not need any ACLs on those interfaces because the default security behavior meets our requirements. Verification and troubleshooting In this session I will demonstrate a few verification and troubleshooting techniques to quickly validate the configuration and identify the problem if any. The first technique is using ICMP ping to verify network connectivity. Obviously ping is working does Page 2
3 not conclude everything else is also working. However it is a simple tool to confirm that packet from point A can reach point B. In our example we wanted to verify that hosts in each subnet of inside, dmz1 and dmz2 have Internet access. We tried pinging the Internet host at By default, the debug messages are sent to the log buffer instead of the screen. In our case, we wanted to see the logs immediately as they popping up on the screen. Responses are being received. ICMP echo request from inside: The ASA knows exactly who requested it and who is desperately waiting for it. After testing, do remember to deactivate the debug mode because it is system resource consuming. It is an excellent tool when you do not have access to either side of the servers to generate real traffic. We first simulate web browsing traffic initiated from a host on the internet with IP The following command sates: The packet comes with source IP Implicit Rule Additional Information: Forward Flow based lookup yields rule: NAT divert to egress interface dmz1 Untranslate It is a major change since ASA code 8. Prior to code 8. Phase 3 shows the outside ACL is being verified and the traffic is allowed. The reset of the phases put the packet through various of policy checks such as QoS, policy-maps and etc. In the end, a nice summary is displayed. The input interface is outside, the output interface is dmz1 and the traffic is sent through successfully. ASA1 packet-tracer input dmz2 udp Resolve Egress Interface Result: The output interface dmz1 was identified. Phase 3 checks the ACL, and it granted traffic to go through. The reset of the phases stayed the same. In the end, the packet was sent through dmz1 interface successfully. Both packet tracer results confirmed our configuration is correct. Let try packet tracer testing on something that is not supposed to work. We wanted to see the ASA actually blocks the traffic. The web server is not configured to serve FTP traffic. ASA1 packet-tracer input outside tcp Assign security level to each ASA interface same Step 2: The default route to the Internet gateway is configured the same. The ACL permits anyone on the Internet to access the web server on port We do not want the ASA to perform Network Address Translations among internal interfaces unless the traffic is heading to the outside interface. The configuration below basically states: Same logic applies the traffic going from dmz2 to dmz1. You can download the entire lab setup and configuration files for FREE. Page 3
4 Chapter 3 : 6 Steps Cisco ASA Basic Configuration Tutorial If you have a factory default configuration, see the "ASA Default Configuration" section to check if you want to change the default interface settings according to this procedure. For more information about ASA interfaces, see the "Information About ASA Interfaces" section. This step is essential and will help the ASA Firewall understand which interface is connected to the trusted private and untrusted public network: Security level for "inside" set to by default. Security level for "outside" set to 0 by default. The ASA Firewall will automatically set the security level to for inside interfaces and 0 to outside interfaces. Traffic can flow from higher security levels to lower private to public, but not the other way around public to private unless stated by an access-lists. To change the security-level of an interface use the security-level xxx command by substituting xxx with a number from 0 to The higher the number, the higher the security level. DMZ interfaces are usually configured with a security level of In case the public interface VLAN2 is configured using the ip address dhcp setroute command, configuration of the default gateway is not required. ASA config route outside 0. ASA config ping Usually these networks can be reached via a Layer3 switch or an internal router. These additional networks are contactable via a Layer3 device with IP address ASA config route outside Network Address Translation is essential to masquerade our internal network using the single IP address our Public interface has been configured with. Network Address Translation, along with all its variations Static, Dynamic etc, is covered in great depth in our popular Network Address Translation section. We will provide both commands to cover installations with software version up to v8. The following commands apply to ASA appliances with software version up to 8. Another method of configuring NAT is with the use of access lists. With software version 8. The following commands software version 8. ASA config object network network1 ASA config-network-object nat inside,outside dynamic interface! Page 4
5 Chapter 4 : CISCO ASA GETTING STARTED MANUAL Pdf Download. The ASA adaptive security appliance supports a built-in switch. There are two kinds of ports and interfaces that you need to configure: â Physical switch portsâ The adaptive security appliance has eight Fast Ethernet switch ports that forward traffic at Layer 2, using the switching function in hardware. Type enable and then simply press enter when it prompts you for a password. So to start with lets set the hostname and the configure up the interfaces. Now unlike routers which you may be used to configuring, the ports on the back of the ASA are not actual ports like you would expect to find on the back of cisco routers. Rather than configure an IP to an interface, the ports on the back are switchports. In the above you can see: Now I mentioned security levels earlier, this is a simple way of controlling access between interfaces. Think of it like being a water drop on a steep hill. Security level 0 at the bottom. Security level at the top. Quickly make sure you can ping your default gateway, then add the route and make sure you can ping something on the internet I use googles DNS server 8. That should be all right? Surely we should be able to ping google then. How can this be though? Lets try adding in a NAT rule and seeing what happens. Try opening up a browserâ We magically get google, yet pings are failing, strange. Hint starts with Access â. But we can configure them later on, for now this guide is just about getting the ASA up and running and getting you outside access, which you are now able to do. Not so hard after all was it? In this example I will store the username and password on the device itself local. Finally http server enable enables HTTP access and http Once done, browse to the gateway of the ASA https: And there we have it, the ASA is now ready to be configured to your specificationâ. Page 5
6 Chapter 5 : *How To* Configure and get started with Cisco ASA racedaydvl.com In brief, Cisco ASA is a security device that combines firewall, antivirus, intrusion prevention, and virtual private network (VPN) capabilities. The first thing to note is that the and units have 8 ports, the has 4 ports. Any port can be configured as a WAN side port or LAN side port or another type of port failover between 2 units for example. However, only the unit can use a set of ports in switching or bridging mode â enabling you to setup 1 port for the WAN connection and 7 ports as a LAN side switch where you can connect all your equipment. For some reason Cisco decided not to include this functionality in the newer units and there is some consternation about this decision and debate as the whether they can physically include that functionality in a future software release â a lot of people will upgrade to the to gain gigabit speeds is a mbit unit only expecting it to function the same as the but will be disappointed. So for now you have to use the as a standard router with 1 port for WAN and 1 port for LAN connected to a separate switch 8 port gigabit switch is pretty cheap anyway. Although you do lose the ability to do switching you do gain in terms of licensing â the basic license for a unit does not include trunking and failover. It also limits the number of inside hosts to The units basic licensing includes unlimited inside hosts and trunking via sub-interfaces. You still have to pay extra for failover though. To connect to the router there is a separate management port usually set to IP: To connect, change your network adapters IP address to an IP within that range e. In your browser goto the address: You will need Java runtime installed on your machine in order to use ASDM and you may get problems with newer versions of Java regarding certificates. Usually you can just ignore certificate warnings but if you do get problems Java 7 release 45 is the version that works without any problems. For more details on this goto the Cisco site: Or setup a self signed certificate: Setting up the WAN interface: Most broadband connections will require you authenticate with the ISPs servers using the PPPoE protocol point-to-point protocol over ethernet: Make sure the Security Level is set to zero. Make sure the interface is enabled. You may have a different setup to mine and your ISP may use a different method of connecting you e. DHCP, in which case choose the method that is relevant to your situation. Click on the Advanced tab and check the MTU setting â the default is but you may need to change this, again depending on your ISPs setup. See here for more info: There are obviously loads of other settings here because a Cisco router can basically connect to anything if setup correctly but these should be the only changes you need to make for a standard broadband connection. Setting up the LAN interface: Make sure the security level is set to a higher number than was given for the WAN port â 50 is the default. Make sure the enable interface option is ticked. Choose a static IP and fill in the IP address and Subnet mask â this is a number on your internal network. In my case I use the IP range It is also possible to use any valid IP range as these numbers are never routed to the outside world but the convention is to use a private range specifically designated for this purpose. If you wish to block this you can do so by adding a Management Access Rule. Set the Action to Deny. Set the IP address and the Mask to Any or 0. There are two ways of adding this functionality: There should be a Default Inspection rule listed â hit Edit. Goto the Rule Actions tab. Select permit for the Action. Source will by Any. I prefer the second method as it separates the default rules from the ones you have added and keeps your rules listed under one section in the Firewall Access Rules. Setting up the DHCP server: Your next task is to setup the DHCP server which assigns addresses from your local network address range when devices try to connect. In our case I have chosen Cisco routers do not allow address reservation. This is a function on, most consumer broadband routers, that allows you to reserve a particular IP for a device from the DHCP range according to the devices MAC address. This is useful if later on you want to use port forwarding to the device â you need the IP of the device to not change over time otherwise your port forwarding and routing rules, which have been specified for a particular internal IP number, will not work. This is an essential requirement if you want to host a server behind your router â web server, minecraft server etc. When using Cisco routers you have to set the devices IP statically on the devices themselves â usually in their network adapter settings. So I have started my address range at 10 so that I can use the IPs Setting up NAT translation: In order for your devices to be able to communicate to Page 6
7 the outside world you need to setup some kind of translation to and from the external IP address and your internal IP addresses. You achieve this using a NAT rule. Destination address and service should be set to Original. Your NAT screen should look something like the image below. I have added a port forwarding NAT rule just to illustrate where the NAT rule should be positioned â it should always be at the bottom of the list otherwise your port forwarding rule would overide it. For port forwarding rules read my article here: Cisco ASA Port forwarding. Configuring NAT rules guide: But just to check here is the default Access Rules screen: At the bottom is a Global rule that denies all traffic hence IP as the service â both Inbound and Outbound. And you can then explicitly allow traffic for invidual services above this rule e. Time is a critical component for the router so you should make sure the ASA is getting the correct time from the internet. You can set the time under the Clock section. To set the ntp server goto NTP section and click Add. I prefer to use the NTP. ORG servers â unfortunately you cannnot put a host name in here, you have to use an IP. Tick the preferred box. Set the interface to Outside you can set it to an internal time server if you wish. Click OK and Apply. Going forward you should make sure you keep your router up-to-date with the latest firmware and ASDM version. And one final thing â backup your configuration using Tools, Backup Configurations. Do this now and before you do any upgrades. Chapter 6 : Cisco ASA (and, ) Basic Setup â IslandEarth For the SMB/SOHO market, Cisco's initial offering was the PIX, followed by the successful Cisco ASA The latter came to an End-of-Sale in and now the replacement low-end model is the new Cisco ASA X. Chapter 7 : ASA Factory reset - Cisco Community Cisco ASA Configuration Manual. Asa series. Cisco ASA Series Configuration Guide using ASDM Software Version, for use with Cisco ASA Chapter 8 : Sample configuration for connecting Cisco ASA devices to Azure VPN gateways Microsoft Do Now unlike routers (which you may be used to configuring), the ports on the back of the ASA are not actual ports like you would expect to find on the back of cisco routers. Instead they follow the same configuration method as the Cisco /'s etc. Chapter 9 : Cisco ASA Commands Cheat Sheet Download PDF This paper will be focusing on the Cisco ASA series adaptive security appliance (with base license) and its incorporation into a small business or Home Network. Specifically, it will look at the initial. Page 7
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM
 Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM
 Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
CHAPTER 7 ADVANCED ADMINISTRATION PC
 ii Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband ADSL Router Features... 1 Package Contents... 3 Physical Details... 4 CHAPTER 2 INSTALLATION... 6 Requirements... 6 Procedure... 6 CHAPTER 3 SETUP...
ii Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband ADSL Router Features... 1 Package Contents... 3 Physical Details... 4 CHAPTER 2 INSTALLATION... 6 Requirements... 6 Procedure... 6 CHAPTER 3 SETUP...
LevelOne FBR User s Manual. 1W, 4L 10/100 Mbps ADSL Router. Ver
 LevelOne FBR-1416 1W, 4L 10/100 Mbps ADSL Router User s Manual Ver 1.00-0510 Table of Contents CHAPTER 1 INTRODUCTION... 1 FBR-1416 Features... 1 Package Contents... 3 Physical Details... 3 CHAPTER 2
LevelOne FBR-1416 1W, 4L 10/100 Mbps ADSL Router User s Manual Ver 1.00-0510 Table of Contents CHAPTER 1 INTRODUCTION... 1 FBR-1416 Features... 1 Package Contents... 3 Physical Details... 3 CHAPTER 2
PIX/ASA: PPPoE Client Configuration Example
 PIX/ASA: PPPoE Client Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram CLI Configuration ASDM Configuration
PIX/ASA: PPPoE Client Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram CLI Configuration ASDM Configuration
SonicWALL / Toshiba General Installation Guide
 SonicWALL / Toshiba General Installation Guide SonicWALL currently maintains two operating systems for its Unified Threat Management (UTM) platform, StandardOS and EnhancedOS. When a SonicWALL is implemented
SonicWALL / Toshiba General Installation Guide SonicWALL currently maintains two operating systems for its Unified Threat Management (UTM) platform, StandardOS and EnhancedOS. When a SonicWALL is implemented
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Cisco ASA 5500 LAB Guide
 INGRAM MICRO Cisco ASA 5500 LAB Guide Ingram Micro 4/1/2009 The following LAB Guide will provide you with the basic steps involved in performing some fundamental configurations on a Cisco ASA 5500 series
INGRAM MICRO Cisco ASA 5500 LAB Guide Ingram Micro 4/1/2009 The following LAB Guide will provide you with the basic steps involved in performing some fundamental configurations on a Cisco ASA 5500 series
SonicWALL Security Appliances. SonicWALL SSL-VPN 200 Getting Started Guide
 SonicWALL Security Appliances SonicWALL SSL-VPN 200 Getting Started Guide SonicWALL SSL-VPN 200 Appliance Getting Started Guide This Getting Started Guide contains installation procedures and configuration
SonicWALL Security Appliances SonicWALL SSL-VPN 200 Getting Started Guide SonicWALL SSL-VPN 200 Appliance Getting Started Guide This Getting Started Guide contains installation procedures and configuration
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
DC-228. ADSL2+ Modem/Router. User Manual. -Annex A- Version: 1.0
 DC-228 ADSL2+ Modem/Router -Annex A- User Manual Version: 1.0 TABLE OF CONTENTS 1 PACKAGE CONTENTS...3 2 PRODUCT LAYOUT...4 3 NETWORK + SYSTEM REQUIREMENTS...6 4 DC-228 PLACEMENT...6 5 SETUP LAN, WAN...7
DC-228 ADSL2+ Modem/Router -Annex A- User Manual Version: 1.0 TABLE OF CONTENTS 1 PACKAGE CONTENTS...3 2 PRODUCT LAYOUT...4 3 NETWORK + SYSTEM REQUIREMENTS...6 4 DC-228 PLACEMENT...6 5 SETUP LAN, WAN...7
UIP1869V User Interface Guide
 UIP1869V User Interface Guide (Firmware version 0.1.8 and later) Table of Contents Opening the UIP1869V's Configuration Utility... 3 Connecting to Your Broadband Modem... 5 Setting up with DHCP... 5 Updating
UIP1869V User Interface Guide (Firmware version 0.1.8 and later) Table of Contents Opening the UIP1869V's Configuration Utility... 3 Connecting to Your Broadband Modem... 5 Setting up with DHCP... 5 Updating
CISCO EXAM QUESTIONS & ANSWERS
 CISCO 642-618 EXAM QUESTIONS & ANSWERS Number: 642-618 Passing Score: 800 Time Limit: 120 min File Version: 39.6 http://www.gratisexam.com/ CISCO 642-618 EXAM QUESTIONS & ANSWERS Exam Name: Deploying Cisco
CISCO 642-618 EXAM QUESTIONS & ANSWERS Number: 642-618 Passing Score: 800 Time Limit: 120 min File Version: 39.6 http://www.gratisexam.com/ CISCO 642-618 EXAM QUESTIONS & ANSWERS Exam Name: Deploying Cisco
Completing Interface Configuration (Transparent Mode)
 CHAPTER 9 Completing Interface Configuration (Transparent Mode) This chapter includes tasks to complete the interface configuration for all models in transparent firewall mode. This chapter includes the
CHAPTER 9 Completing Interface Configuration (Transparent Mode) This chapter includes tasks to complete the interface configuration for all models in transparent firewall mode. This chapter includes the
PIX/ASA : Port Redirection(Forwarding) with nat, global, static and access list Commands
 PIX/ASA : Port Redirection(Forwarding) with nat, global, static and access list Commands Document ID: 63872 Introduction Prerequisites Requirements Components Used Related Products Conventions Network
PIX/ASA : Port Redirection(Forwarding) with nat, global, static and access list Commands Document ID: 63872 Introduction Prerequisites Requirements Components Used Related Products Conventions Network
Access Rules. Controlling Network Access
 This chapter describes how to control network access through or to the ASA using access rules. You use access rules to control network access in both routed and transparent firewall modes. In transparent
This chapter describes how to control network access through or to the ASA using access rules. You use access rules to control network access in both routed and transparent firewall modes. In transparent
Fundamentals of Network Security v1.1 Scope and Sequence
 Fundamentals of Network Security v1.1 Scope and Sequence Last Updated: September 9, 2003 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document
Fundamentals of Network Security v1.1 Scope and Sequence Last Updated: September 9, 2003 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document
Security SSID Selection: Broadcast SSID:
 69 Security SSID Selection: Broadcast SSID: WMM: Encryption: Select the SSID that the security settings will apply to. If Disabled, then the device will not be broadcasting the SSID. Therefore it will
69 Security SSID Selection: Broadcast SSID: WMM: Encryption: Select the SSID that the security settings will apply to. If Disabled, then the device will not be broadcasting the SSID. Therefore it will
Use of the TCP/IP Protocols and the OSI Model in Packet Tracer
 Communication Networks [Netw501] Spring 2018 Tutorial 3 Packet Tracer Activity 3 Use of the TCP/IP Protocols and the OSI Model in Packet Tracer Introduction: In Packet Tracer simulation mode, detailed
Communication Networks [Netw501] Spring 2018 Tutorial 3 Packet Tracer Activity 3 Use of the TCP/IP Protocols and the OSI Model in Packet Tracer Introduction: In Packet Tracer simulation mode, detailed
Barracuda Link Balancer
 Barracuda Networks Technical Documentation Barracuda Link Balancer Administrator s Guide Version 2.3 RECLAIM YOUR NETWORK Copyright Notice Copyright 2004-2011, Barracuda Networks www.barracuda.com v2.3-111215-01-1215
Barracuda Networks Technical Documentation Barracuda Link Balancer Administrator s Guide Version 2.3 RECLAIM YOUR NETWORK Copyright Notice Copyright 2004-2011, Barracuda Networks www.barracuda.com v2.3-111215-01-1215
Configuring Interfaces (Transparent Mode)
 8 CHAPTER This chapter includes tasks to complete the interface configuration in transparent firewall mode. This chapter includes the following sections: Information About Completing Interface Configuration
8 CHAPTER This chapter includes tasks to complete the interface configuration in transparent firewall mode. This chapter includes the following sections: Information About Completing Interface Configuration
IP806GA/GB Wireless ADSL Router
 IP806GA/GB Wireless ADSL Router 802.11g/802.11b Wireless Access Point ADSL Modem NAT Router 4-Port Switching Hub User's Guide Table of Contents CHAPTER 1 INTRODUCTION... 1 Wireless ADSL Router Features...
IP806GA/GB Wireless ADSL Router 802.11g/802.11b Wireless Access Point ADSL Modem NAT Router 4-Port Switching Hub User's Guide Table of Contents CHAPTER 1 INTRODUCTION... 1 Wireless ADSL Router Features...
4-Port Broadband user manual Model
 4-Port Broadband Router user manual Model 524537 INT-524537-UM-0309-02 introduction Thank you for purchasing the INTELLINET NETWORK SOLUTIONS 4-Port Broadband Router, Model 524537. Combining a router,
4-Port Broadband Router user manual Model 524537 INT-524537-UM-0309-02 introduction Thank you for purchasing the INTELLINET NETWORK SOLUTIONS 4-Port Broadband Router, Model 524537. Combining a router,
ASA 7.x/PIX 6.x and Above: Open/Block the Ports Configuration Example
 ASA 7.x/PIX 6.x and Above: Open/Block the Ports Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram Blocking the
ASA 7.x/PIX 6.x and Above: Open/Block the Ports Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram Blocking the
PIX/ASA as a DHCP Server and Client Configuration Example
 PIX/ASA as a DHCP Server and Client Configuration Example Document ID: 70391 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure DHCP Server Configuration
PIX/ASA as a DHCP Server and Client Configuration Example Document ID: 70391 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure DHCP Server Configuration
Lab Configuring and Verifying Extended ACLs Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
CCNA Exploration Network Fundamentals
 CCNA Exploration 4.0 1. Network Fundamentals The goal of this course is to introduce you to fundamental networking concepts and technologies. These online course materials will assist you in developing
CCNA Exploration 4.0 1. Network Fundamentals The goal of this course is to introduce you to fundamental networking concepts and technologies. These online course materials will assist you in developing
Configuring Commonly Used IP ACLs
 Configuring Commonly Used IP ACLs Document ID: 26448 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration Examples Allow a Select Host to Access the Network Deny a
Configuring Commonly Used IP ACLs Document ID: 26448 Contents Introduction Prerequisites Requirements Components Used Conventions Configuration Examples Allow a Select Host to Access the Network Deny a
Lab - Troubleshooting ACL Configuration and Placement Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway HQ G0/1 192.168.1.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway HQ G0/1 192.168.1.1
ASA Access Control. Section 3
 [ 39 ] CCNP Security Firewall 642-617 Quick Reference Section 3 ASA Access Control Now that you have connectivity to the ASA and have configured basic networking settings on the ASA, you can start to look
[ 39 ] CCNP Security Firewall 642-617 Quick Reference Section 3 ASA Access Control Now that you have connectivity to the ASA and have configured basic networking settings on the ASA, you can start to look
Deploying the Barracuda Link Balancer with Cisco ASA VPN Tunnels
 Deploying the Barracuda Link Balancer with Cisco ASA VPN Tunnels This article provides a reference for deploying a Barracuda Link Balancer under the following conditions: 1. 2. In transparent (firewall-disabled)
Deploying the Barracuda Link Balancer with Cisco ASA VPN Tunnels This article provides a reference for deploying a Barracuda Link Balancer under the following conditions: 1. 2. In transparent (firewall-disabled)
UniNets CCNA Security LAB MANUAL UNiNets CCNA Cisco Certified Network Associate Security LAB MANUAL UniNets CCNA LAB MANUAL
 UNiNets CCNA Cisco Certified Network Associate Security LAB MANUAL Contents: UniNets CCNA Security LAB MANUAL Section 1 Securing Layer 2 Lab 1-1 Configuring Native VLAN on a Trunk Links Lab 1-2 Disabling
UNiNets CCNA Cisco Certified Network Associate Security LAB MANUAL Contents: UniNets CCNA Security LAB MANUAL Section 1 Securing Layer 2 Lab 1-1 Configuring Native VLAN on a Trunk Links Lab 1-2 Disabling
CCNA Semester 2 labs. Labs for chapters 2 10
 CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
LKR Port Broadband Router. User's Manual. Revision C
 LKR-604 4-Port Broadband Router User's Manual Revision C 1 Contents 1 Introduction... 4 1.1 Features... 4 1.2 Package Contents... 4 1.3 Finding Your Way Around... 5 1.3.1 Front Panel... 5 1.3.2 Rear Panel
LKR-604 4-Port Broadband Router User's Manual Revision C 1 Contents 1 Introduction... 4 1.1 Features... 4 1.2 Package Contents... 4 1.3 Finding Your Way Around... 5 1.3.1 Front Panel... 5 1.3.2 Rear Panel
Table of Contents. Cisco IPSec Tunnel through a PIX Firewall (Version 7.0) with NAT Configuration Example
 Table of Contents IPSec Tunnel through a PIX Firewall (Version 7.0) with NAT Configuration Example...1 Document ID: 63881...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2
Table of Contents IPSec Tunnel through a PIX Firewall (Version 7.0) with NAT Configuration Example...1 Document ID: 63881...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2
Troubleshooting the Security Appliance
 CHAPTER 43 This chapter describes how to troubleshoot the security appliance, and includes the following sections: Testing Your Configuration, page 43-1 Reloading the Security Appliance, page 43-6 Performing
CHAPTER 43 This chapter describes how to troubleshoot the security appliance, and includes the following sections: Testing Your Configuration, page 43-1 Reloading the Security Appliance, page 43-6 Performing
Wireless-G Router User s Guide
 Wireless-G Router User s Guide 1 Table of Contents Chapter 1: Introduction Installing Your Router System Requirements Installation Instructions Chapter 2: Preparing Your Network Preparing Your Network
Wireless-G Router User s Guide 1 Table of Contents Chapter 1: Introduction Installing Your Router System Requirements Installation Instructions Chapter 2: Preparing Your Network Preparing Your Network
ASA/PIX Security Appliance
 I N D E X A AAA, implementing, 27 28 access to ASA/PIX Security Appliance monitoring, 150 151 securing, 147 150 to websites, blocking, 153 155 access control, 30 access policies, creating for web and mail
I N D E X A AAA, implementing, 27 28 access to ASA/PIX Security Appliance monitoring, 150 151 securing, 147 150 to websites, blocking, 153 155 access control, 30 access policies, creating for web and mail
Google Cloud VPN Interop Guide
 Google Cloud VPN Interop Guide Using Cloud VPN With Cisco ASA Courtesy of Cisco Systems, Inc. Unauthorized use not permitted. Cisco is a registered trademark or trademark of Cisco Systems, Inc. and/or
Google Cloud VPN Interop Guide Using Cloud VPN With Cisco ASA Courtesy of Cisco Systems, Inc. Unauthorized use not permitted. Cisco is a registered trademark or trademark of Cisco Systems, Inc. and/or
Modular Policy Framework. Class Maps SECTION 4. Advanced Configuration
 [ 59 ] Section 4: We have now covered the basic configuration and delved into AAA services on the ASA. In this section, we cover some of the more advanced features of the ASA that break it away from a
[ 59 ] Section 4: We have now covered the basic configuration and delved into AAA services on the ASA. In this section, we cover some of the more advanced features of the ASA that break it away from a
Lab Student Lab Orientation
 Lab 1.1.1 Student Lab Orientation Objective In this lab, the students will complete the following tasks: Review the lab bundle equipment Understand the security pod topology Understand the pod naming and
Lab 1.1.1 Student Lab Orientation Objective In this lab, the students will complete the following tasks: Review the lab bundle equipment Understand the security pod topology Understand the pod naming and
Broadband Router DC-202. User's Guide
 Broadband Router DC-202 User's Guide Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband Router Features... 1 Package Contents... 3 Physical Details...3 CHAPTER 2 INSTALLATION... 5 Requirements...
Broadband Router DC-202 User's Guide Table of Contents CHAPTER 1 INTRODUCTION... 1 Broadband Router Features... 1 Package Contents... 3 Physical Details...3 CHAPTER 2 INSTALLATION... 5 Requirements...
Viewing Network Status, page 116. Configuring IPv4 or IPv6 Routing, page 116. Configuring the WAN, page 122. Configuring a VLAN, page 137
 Networking Using the Networking module to configure your Internet connection, VLAN, DMZ, zones, routing, Quality of Service (QoS), and related features. It includes the following sections: Viewing Network
Networking Using the Networking module to configure your Internet connection, VLAN, DMZ, zones, routing, Quality of Service (QoS), and related features. It includes the following sections: Viewing Network
Chapter 2 VLANs. CHAPTER 2 VLANs
 [ 52 ] Chapter 2 Beginning in Version 6.2 of the PIX firewall, there is support for subinterfaces, trunk links, and. The PIX and ASA can support 802.1q encapsulation and a number of logical interfaces
[ 52 ] Chapter 2 Beginning in Version 6.2 of the PIX firewall, there is support for subinterfaces, trunk links, and. The PIX and ASA can support 802.1q encapsulation and a number of logical interfaces
User Manual DIR-850L. Wireless AC1200 Dual Band Gigabit Router.
 User Manual DIR-850L Wireless AC1200 Dual Band Gigabit Router USER MANUAL: DIR-850L Wireless AC1200 Dual Band Gigabit Router SYSTEM REQUIREMENTS Network Requirements Web-based Configuration Utility Requirements
User Manual DIR-850L Wireless AC1200 Dual Band Gigabit Router USER MANUAL: DIR-850L Wireless AC1200 Dual Band Gigabit Router SYSTEM REQUIREMENTS Network Requirements Web-based Configuration Utility Requirements
Application Note 3Com VCX Connect with SIP Trunking - Configuration Guide
 Application Note 3Com VCX Connect with SIP Trunking - Configuration Guide 28 May 2009 3Com VCX Connect Solution SIP Trunking Table of Contents 1 3COM VCX CONNECT AND INGATE... 1 1.1 SIP TRUNKING SUPPORT...
Application Note 3Com VCX Connect with SIP Trunking - Configuration Guide 28 May 2009 3Com VCX Connect Solution SIP Trunking Table of Contents 1 3COM VCX CONNECT AND INGATE... 1 1.1 SIP TRUNKING SUPPORT...
Multihoming with BGP and NAT
 Eliminating ISP as a single point of failure www.noction.com Table of Contents Introduction 1. R-NAT Configuration 1.1 NAT Configuration 5. ISPs Routers Configuration 3 15 7 7 5.1 ISP-A Configuration 5.2
Eliminating ISP as a single point of failure www.noction.com Table of Contents Introduction 1. R-NAT Configuration 1.1 NAT Configuration 5. ISPs Routers Configuration 3 15 7 7 5.1 ISP-A Configuration 5.2
Lab 8: Firewalls ASA Firewall Device
 Lab 8: Firewalls ASA Firewall Device 8.1 Details Aim: Rich Macfarlane 2015 The aim of this lab is to investigate a Cisco ASA Firewall Device, its default traffic flows, its stateful firewalling functionality,
Lab 8: Firewalls ASA Firewall Device 8.1 Details Aim: Rich Macfarlane 2015 The aim of this lab is to investigate a Cisco ASA Firewall Device, its default traffic flows, its stateful firewalling functionality,
The Applications and Gaming Tab - Port Range Forward
 The Applications and Gaming Tab - Port Range Forward The Applications and Gaming Tab allows you to set up public services on your network, such as web servers, ftp servers, e-mail servers, or other specialized
The Applications and Gaming Tab - Port Range Forward The Applications and Gaming Tab allows you to set up public services on your network, such as web servers, ftp servers, e-mail servers, or other specialized
Application Note Asterisk BE with Remote Phones - Configuration Guide
 Application Note Asterisk BE with Remote Phones - Configuration Guide 15 January 2009 Asterisk BE - Remote SIP Phones Table of Contents 1 ASTERISK BUSINESS EDITION AND INGATE... 1 1.1 REMOTE SIP PHONE
Application Note Asterisk BE with Remote Phones - Configuration Guide 15 January 2009 Asterisk BE - Remote SIP Phones Table of Contents 1 ASTERISK BUSINESS EDITION AND INGATE... 1 1.1 REMOTE SIP PHONE
Case Study. Routing & Switching. Cisco Networking Academy Routing and Switching: Scaling Network Case Study
 Case Study Routing & Switching Cisco Networking Academy Routing and Switching: Scaling Network Case Study Overview and Objectives This case study allows students to build and configure a complex network
Case Study Routing & Switching Cisco Networking Academy Routing and Switching: Scaling Network Case Study Overview and Objectives This case study allows students to build and configure a complex network
Broadband Router. User s Manual
 Broadband Router User s Manual 1 Introduction... 4 Features... 4 Minimum Requirements... 4 Package Content... 4 Note... 4 Get to know the Broadband Router... 5 Back Panel... 5 Front Panel... 6 Setup Diagram...7
Broadband Router User s Manual 1 Introduction... 4 Features... 4 Minimum Requirements... 4 Package Content... 4 Note... 4 Get to know the Broadband Router... 5 Back Panel... 5 Front Panel... 6 Setup Diagram...7
Table of Contents. Cisco Configuring IP Access Lists
 Table of Contents Configuring IP Access Lists...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2 ACL Concepts...2 Masks...2 ACL Summarization...3 Process ACLs...4
Table of Contents Configuring IP Access Lists...1 Introduction...1 Prerequisites...2 Requirements...2 Components Used...2 Conventions...2 ACL Concepts...2 Masks...2 ACL Summarization...3 Process ACLs...4
PT Activity 8.6.1: CCNA Skills Integration Challenge Topology Diagram
 Topology Diagram All contents are Copyright 2008 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 7 Addressing Table for HQ Device Interface IP Address Subnet
Topology Diagram All contents are Copyright 2008 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 1 of 7 Addressing Table for HQ Device Interface IP Address Subnet
RX3041. User's Manual
 RX3041 User's Manual Table of Contents 1 Introduction... 2 1.1 Features and Benefits... 3 1.2 Package Contents... 3 1.3 Finding Your Way Around... 4 1.4 System Requirements... 6 1.5 Installation Instruction...
RX3041 User's Manual Table of Contents 1 Introduction... 2 1.1 Features and Benefits... 3 1.2 Package Contents... 3 1.3 Finding Your Way Around... 4 1.4 System Requirements... 6 1.5 Installation Instruction...
Lab 6: Access Lists. Device Interface IP Address Subnet Mask Gateway/Clock Rate Fa 0/ R1
 Lab 6: Access Lists Network Topology:- Device Interface IP Address Subnet Mask Gateway/Clock Rate Fa 0/0 192.168.0.1 255.255.255.0 ----- R1 Fa 0/1 192.168.10.1 255.255.255.0 ----- Se 0/0/0 10.0.0.1 255.255.255.252
Lab 6: Access Lists Network Topology:- Device Interface IP Address Subnet Mask Gateway/Clock Rate Fa 0/0 192.168.0.1 255.255.255.0 ----- R1 Fa 0/1 192.168.10.1 255.255.255.0 ----- Se 0/0/0 10.0.0.1 255.255.255.252
Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM
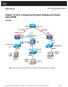 Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM Topology Note: ISR G2 devices have Gigabit Ethernet interfaces instead of Fast Ethernet interfaces. All contents are Copyright 1992
Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM Topology Note: ISR G2 devices have Gigabit Ethernet interfaces instead of Fast Ethernet interfaces. All contents are Copyright 1992
Gigaset Router / en / A31008-E105-B / cover_front_router.fm / s Be inspired
 s Be inspired Table of Contents Table of Contents Safety precautions........................... 3 The Gigaset Router........................... 3 Features and Benefits..................................................
s Be inspired Table of Contents Table of Contents Safety precautions........................... 3 The Gigaset Router........................... 3 Features and Benefits..................................................
CCNA Discovery 3 Chapter 8 Reading Organizer
 Name Date Chapter 8 Reading Organizer After completion of this chapter, you should be able to: Describe traffic filtering and explain how Access Control Lists (ACLs) can filter traffic at router interfaces.
Name Date Chapter 8 Reading Organizer After completion of this chapter, you should be able to: Describe traffic filtering and explain how Access Control Lists (ACLs) can filter traffic at router interfaces.
ASA 8.X and later: Add or Modify an Access List through the ASDM GUI Configuration Example
 ASA 8.X and later: Add or Modify an Access List through the ASDM GUI Configuration Example Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
ASA 8.X and later: Add or Modify an Access List through the ASDM GUI Configuration Example Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
Configuration Guide TL-ER5120/TL-ER6020/TL-ER REV3.0.0
 Configuration Guide TL-ER5120/TL-ER6020/TL-ER6120 1910012186 REV3.0.0 June 2017 CONTENTS About This Guide Intended Readers... 1 Conventions... 1 More Information... 1 Viewing Status Information... 2 System
Configuration Guide TL-ER5120/TL-ER6020/TL-ER6120 1910012186 REV3.0.0 June 2017 CONTENTS About This Guide Intended Readers... 1 Conventions... 1 More Information... 1 Viewing Status Information... 2 System
User Guide TL-R470T+/TL-R480T REV9.0.2
 User Guide TL-R470T+/TL-R480T+ 1910012468 REV9.0.2 September 2018 CONTENTS About This Guide Intended Readers... 1 Conventions... 1 More Information... 1 Accessing the Router Overview... 3 Web Interface
User Guide TL-R470T+/TL-R480T+ 1910012468 REV9.0.2 September 2018 CONTENTS About This Guide Intended Readers... 1 Conventions... 1 More Information... 1 Accessing the Router Overview... 3 Web Interface
Summer Webinar Series
 Summer Webinar Series Troubleshooting Traffic Flows Through Cisco ASA Firewalls Christopher Rose Sr. Client Network Engineer crose@mcnc.org Webinar Links: www.mcnc.org/cne-webinars Agenda 1. Firewall best
Summer Webinar Series Troubleshooting Traffic Flows Through Cisco ASA Firewalls Christopher Rose Sr. Client Network Engineer crose@mcnc.org Webinar Links: www.mcnc.org/cne-webinars Agenda 1. Firewall best
Advanced Security and Forensic Computing
 Advanced Security and Forensic Computing Unit 2: Network Security Elements Dr Dr Bill Buchanan, Reader, School of of Computing. >Unit 2: 2: Network Security Elements Advanced Security and Forensic Computing
Advanced Security and Forensic Computing Unit 2: Network Security Elements Dr Dr Bill Buchanan, Reader, School of of Computing. >Unit 2: 2: Network Security Elements Advanced Security and Forensic Computing
Wireless LANs (CO72047) Bill Buchanan, Reader, School of Computing.
 Bill Buchanan, Reader, School of Computing. W.Buchanan (1) Lab setup W.Buchanan (2) W.Buchanan (3) Console Server Con Cisco Aironet 1200 192.168.1.100 Port 2001 Con Cisco Aironet 1200 192.168.1.100 Port
Bill Buchanan, Reader, School of Computing. W.Buchanan (1) Lab setup W.Buchanan (2) W.Buchanan (3) Console Server Con Cisco Aironet 1200 192.168.1.100 Port 2001 Con Cisco Aironet 1200 192.168.1.100 Port
Three interface Router without NAT Cisco IOS Firewall Configuration
 Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Three interface Router without NAT Cisco IOS Firewall Configuration Document ID: 13893 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology
 Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Getting Started. Getting Started with Your Platform Model. Factory Default Configurations CHAPTER
 CHAPTER 2 This chapter describes how to access the command-line interface, configure the firewall mode, and work with the configuration. This chapter includes the following sections: with Your Platform
CHAPTER 2 This chapter describes how to access the command-line interface, configure the firewall mode, and work with the configuration. This chapter includes the following sections: with Your Platform
VPN Configuration Guide. Cisco ASA 5500 Series
 VPN Configuration Guide Cisco ASA 5500 Series 2015 equinux AG and equinux USA, Inc. All rights reserved. Under copyright law, this configuration guide may not be copied, in whole or in part, without the
VPN Configuration Guide Cisco ASA 5500 Series 2015 equinux AG and equinux USA, Inc. All rights reserved. Under copyright law, this configuration guide may not be copied, in whole or in part, without the
GSS Administration and Troubleshooting
 CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
AplombTech Smart Router Manual
 AplombTech Smart Router Manual (Version: 1.0) 1 Version & Purpose Version Manual version V 1.0 Explanation Corresponds to the initial version of device Purpose This manual describes the function features
AplombTech Smart Router Manual (Version: 1.0) 1 Version & Purpose Version Manual version V 1.0 Explanation Corresponds to the initial version of device Purpose This manual describes the function features
Troubleshooting. Testing Your Configuration CHAPTER
 82 CHAPTER This chapter describes how to troubleshoot the ASA and includes the following sections: Testing Your Configuration, page 82-1 Reloading the ASA, page 82-8 Performing Password Recovery, page
82 CHAPTER This chapter describes how to troubleshoot the ASA and includes the following sections: Testing Your Configuration, page 82-1 Reloading the ASA, page 82-8 Performing Password Recovery, page
Cisco Small Business RV320/RV325 Gigabit Dual WAN VPN Router
 ADMINISTRATION GUIDE Cisco Small Business RV320/RV325 Gigabit Dual WAN VPN Router 78-20928-02 Contents Chapter 1: Getting Started 7 Using the Getting Started Window 7 Features of the User Interface 8 Chapter
ADMINISTRATION GUIDE Cisco Small Business RV320/RV325 Gigabit Dual WAN VPN Router 78-20928-02 Contents Chapter 1: Getting Started 7 Using the Getting Started Window 7 Features of the User Interface 8 Chapter
ZyWALL 70. Internet Security Appliance. Quick Start Guide Version 3.62 December 2003
 ZyWALL 70 Internet Security Appliance Quick Start Guide Version 3.62 December 2003 Introducing the ZyWALL The ZyWALL 70 is the ideal secure gateway for all data passing between the Internet and the LAN.
ZyWALL 70 Internet Security Appliance Quick Start Guide Version 3.62 December 2003 Introducing the ZyWALL The ZyWALL 70 is the ideal secure gateway for all data passing between the Internet and the LAN.
Configuring a Palo Alto Firewall in AWS
 Configuring a Palo Alto Firewall in AWS Version 1.0 10/19/2015 GRANT CARMICHAEL, MBA, CISSP, RHCA, ITIL For contact information visit Table of Contents The Network Design... 2 Step 1 Building the AWS network...
Configuring a Palo Alto Firewall in AWS Version 1.0 10/19/2015 GRANT CARMICHAEL, MBA, CISSP, RHCA, ITIL For contact information visit Table of Contents The Network Design... 2 Step 1 Building the AWS network...
The Administration Tab - Diagnostics
 The Administration Tab - Diagnostics The diagnostic tests (Ping and Traceroute) allow you to check the connections of your network components. Ping Test. The Ping test will check the status of a connection.
The Administration Tab - Diagnostics The diagnostic tests (Ping and Traceroute) allow you to check the connections of your network components. Ping Test. The Ping test will check the status of a connection.
CCNA Security 1.0 Student Packet Tracer Manual
 1.0 Student Packet Tracer Manual This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors
1.0 Student Packet Tracer Manual This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors
exam. Number: Passing Score: 800 Time Limit: 120 min CISCO Interconnecting Cisco Networking Devices Part 1 (ICND)
 100-105.exam Number: 100-105 Passing Score: 800 Time Limit: 120 min CISCO 100-105 Interconnecting Cisco Networking Devices Part 1 (ICND) Exam A QUESTION 1 Which route source code represents the routing
100-105.exam Number: 100-105 Passing Score: 800 Time Limit: 120 min CISCO 100-105 Interconnecting Cisco Networking Devices Part 1 (ICND) Exam A QUESTION 1 Which route source code represents the routing
TestOut Routing and Switching Pro - English 6.0.x COURSE OUTLINE. Modified
 TestOut Routing and Switching Pro - English 6.0.x COURSE OUTLINE Modified 2017-07-10 TestOut Routing and Switching Pro Outline- English 6.0.x Videos: 133 (15:42:34) Demonstrations: 78 (7:22:19) Simulations:
TestOut Routing and Switching Pro - English 6.0.x COURSE OUTLINE Modified 2017-07-10 TestOut Routing and Switching Pro Outline- English 6.0.x Videos: 133 (15:42:34) Demonstrations: 78 (7:22:19) Simulations:
Managing Services Modules
 CHAPTER 58 This chapter describes how to manage the following module types: Security Services Cards (SSCs) Security Services Modules (SSMs) Security Services Processors (SSPs) Modules run advanced security
CHAPTER 58 This chapter describes how to manage the following module types: Security Services Cards (SSCs) Security Services Modules (SSMs) Security Services Processors (SSPs) Modules run advanced security
Application Note Asterisk BE with SIP Trunking - Configuration Guide
 Application Note Asterisk BE with SIP Trunking - Configuration Guide 23 January 2009 Asterisk BE SIP Trunking Table of Contents 1 ASTERISK BUSINESS EDITION AND INGATE... 1 1.1 SIP TRUNKING SUPPORT... 2
Application Note Asterisk BE with SIP Trunking - Configuration Guide 23 January 2009 Asterisk BE SIP Trunking Table of Contents 1 ASTERISK BUSINESS EDITION AND INGATE... 1 1.1 SIP TRUNKING SUPPORT... 2
ANSEL FXS / 1 PSTN. VoIP Telephone Adaptor. User Manual V1.10
 ANSEL 5518 1 FXS / 1 PSTN VoIP Telephone Adaptor User Manual V1.10 Quick Guide Step 1: Broadband (ADSL/Cable Modem) Connections for ANSEL 5518 A. Connect ANSEL 5518 WAN port to ADSL NAT Router as the following
ANSEL 5518 1 FXS / 1 PSTN VoIP Telephone Adaptor User Manual V1.10 Quick Guide Step 1: Broadband (ADSL/Cable Modem) Connections for ANSEL 5518 A. Connect ANSEL 5518 WAN port to ADSL NAT Router as the following
Dual WAN VPN Firewall VPN 3000 User s Guide. Version 1.0 Date : 1 July 2005 Please check for the latest version
 Dual WAN VPN Firewall VPN 3000 User s Guide Version 1.0 Date : 1 July 2005 Please check www.basewall.com for the latest version Basewall 2005 TABLE OF CONTENTS 1: INTRODUCTION... 4 Internet Features...
Dual WAN VPN Firewall VPN 3000 User s Guide Version 1.0 Date : 1 July 2005 Please check www.basewall.com for the latest version Basewall 2005 TABLE OF CONTENTS 1: INTRODUCTION... 4 Internet Features...
TCP/IP CONFIGURATION 3-6
 TCP/IP CONFIGURATION 3. Type IPCONFIG /RENEW and press the Enter key. Verify that your IP Address is now 192.168.2.xxx, your Subnet Mask is 255.255.255.0 and your Default Gateway is 192.168.2.1. These
TCP/IP CONFIGURATION 3. Type IPCONFIG /RENEW and press the Enter key. Verify that your IP Address is now 192.168.2.xxx, your Subnet Mask is 255.255.255.0 and your Default Gateway is 192.168.2.1. These
GajShield UTM Series uide uick Start G Q
 Quick Start Guide GajShield UTM Series Default Factory Settings Gajshield UTM is shipped with following factory default values. Web GUI Console SSH ( Serial) Console LAN Interface Us ername superuser Username
Quick Start Guide GajShield UTM Series Default Factory Settings Gajshield UTM is shipped with following factory default values. Web GUI Console SSH ( Serial) Console LAN Interface Us ername superuser Username
LevelOne WBR User s Manual. 11g Wireless ADSL VPN Router. Ver
 LevelOne WBR-3407 11g Wireless ADSL VPN Router User s Manual Ver 1.00-0510 Table of Contents CHAPTER 1 INTRODUCTION... 1 Wireless ADSL Router Features... 1 Package Contents... 5 Physical Details... 6 CHAPTER
LevelOne WBR-3407 11g Wireless ADSL VPN Router User s Manual Ver 1.00-0510 Table of Contents CHAPTER 1 INTRODUCTION... 1 Wireless ADSL Router Features... 1 Package Contents... 5 Physical Details... 6 CHAPTER
Cisco CISCO Securing Networks with ASA Advanced. Practice Test. Version
 Cisco 642-515 CISCO 642-515 Securing Networks with ASA Advanced Practice Test Version 3.1 QUESTION NO: 1 Cisco 642-515: Practice Exam Which two statements correctly describe configuring active/active failover?
Cisco 642-515 CISCO 642-515 Securing Networks with ASA Advanced Practice Test Version 3.1 QUESTION NO: 1 Cisco 642-515: Practice Exam Which two statements correctly describe configuring active/active failover?
Firewall Stateful Inspection of ICMP
 The feature categorizes Internet Control Management Protocol Version 4 (ICMPv4) messages as either malicious or benign. The firewall uses stateful inspection to trust benign ICMPv4 messages that are generated
The feature categorizes Internet Control Management Protocol Version 4 (ICMPv4) messages as either malicious or benign. The firewall uses stateful inspection to trust benign ICMPv4 messages that are generated
PrepAwayExam. High-efficient Exam Materials are the best high pass-rate Exam Dumps
 PrepAwayExam http://www.prepawayexam.com/ High-efficient Exam Materials are the best high pass-rate Exam Dumps Exam : 250-530 Title : Administration of Symantec Network Access Control 12.1 Vendors : Symantec
PrepAwayExam http://www.prepawayexam.com/ High-efficient Exam Materials are the best high pass-rate Exam Dumps Exam : 250-530 Title : Administration of Symantec Network Access Control 12.1 Vendors : Symantec
Cisco RV180 VPN Router
 Cisco RV180 VPN Router Secure, high-performance connectivity at a price you can afford. Figure 1. Cisco RV180 VPN Router (Front Panel) Highlights Affordable, high-performance Gigabit Ethernet ports allow
Cisco RV180 VPN Router Secure, high-performance connectivity at a price you can afford. Figure 1. Cisco RV180 VPN Router (Front Panel) Highlights Affordable, high-performance Gigabit Ethernet ports allow
CCNA Security PT Practice SBA
 A few things to keep in mind while completing this activity: 1. Do not use the browser Back button or close or reload any Exam windows during the exam. 2. Do not close Packet Tracer when you are done.
A few things to keep in mind while completing this activity: 1. Do not use the browser Back button or close or reload any Exam windows during the exam. 2. Do not close Packet Tracer when you are done.
ZyWALL 10W. Internet Security Gateway. Quick Start Guide Version 3.62 December 2003
 Internet Security Gateway Quick Start Guide Version 3.62 December 2003 Introducing the ZyWALL The is the ideal secure gateway for all data passing between the Internet and the LAN. By integrating NAT,
Internet Security Gateway Quick Start Guide Version 3.62 December 2003 Introducing the ZyWALL The is the ideal secure gateway for all data passing between the Internet and the LAN. By integrating NAT,
Implementing Firewall Technologies
 Implementing Firewall Technologies Network firewalls separate protected from non-protected areas preventing unauthorized users from accessing protected network resources. Technologies used: ACLs Standard,
Implementing Firewall Technologies Network firewalls separate protected from non-protected areas preventing unauthorized users from accessing protected network resources. Technologies used: ACLs Standard,
Configure the ASA for Dual Internal Networks
 Configure the ASA for Dual Internal Networks Document ID: 119195 Contributed by Dinkar Sharma, Bratin Saha, and Prashant Joshi, Cisco TAC Engineers. Aug 05, 2015 Contents Introduction Prerequisites Requirements
Configure the ASA for Dual Internal Networks Document ID: 119195 Contributed by Dinkar Sharma, Bratin Saha, and Prashant Joshi, Cisco TAC Engineers. Aug 05, 2015 Contents Introduction Prerequisites Requirements
ASACAMP - ASA Lab Camp (5316)
 ASACAMP - ASA Lab Camp (5316) Price: $4,595 Cisco Course v1.0 Cisco Security Appliance Software v8.0 Based on our enhanced FIREWALL and VPN courses, this exclusive, lab-based course is designed to provide
ASACAMP - ASA Lab Camp (5316) Price: $4,595 Cisco Course v1.0 Cisco Security Appliance Software v8.0 Based on our enhanced FIREWALL and VPN courses, this exclusive, lab-based course is designed to provide
Identity Firewall. About the Identity Firewall
 This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
Cisco Firepower Threat Defense Configuration Guide for Firepower Device Manager, Version 6.2
 Cisco Firepower Threat Defense Configuration Guide for Firepower Device Manager, Version 6.2 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Cisco Firepower Threat Defense Configuration Guide for Firepower Device Manager, Version 6.2 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Router and ACL ACL Filter traffic ACL: The Three Ps One ACL per protocol One ACL per direction One ACL per interface
 CCNA4 Chapter 5 * Router and ACL By default, a router does not have any ACLs configured and therefore does not filter traffic. Traffic that enters the router is routed according to the routing table. *
CCNA4 Chapter 5 * Router and ACL By default, a router does not have any ACLs configured and therefore does not filter traffic. Traffic that enters the router is routed according to the routing table. *
Lab Student Lab Orientation
 Lab 1.1.1 Student Lab Orientation Objective In this lab, the students will complete the following tasks: Review the lab bundle equipment Understand the security pod topology Understand the pod naming and
Lab 1.1.1 Student Lab Orientation Objective In this lab, the students will complete the following tasks: Review the lab bundle equipment Understand the security pod topology Understand the pod naming and
TEW-211BRP. Wireless AP Router. User s Manual
 TEW-211BRP Wireless AP Router User s Manual Version 1.4 - Jan 2002 CONTENTS Introduction...3 Hardware Installation...5 General Wireless AP Router System Connection...6 Wireless AP Router Default Settings
TEW-211BRP Wireless AP Router User s Manual Version 1.4 - Jan 2002 CONTENTS Introduction...3 Hardware Installation...5 General Wireless AP Router System Connection...6 Wireless AP Router Default Settings
