IBM Proventia Network Multi-Function Security - MX0804 and MX1004
|
|
|
- Erick Thompson
- 5 years ago
- Views:
Transcription
1 One appliance, six security features designed to preemptively stop Internet threats IBM Proventia Network Multi-Function Security - MX0804 and one is safe Single layered security such as a firewall or antivirus protection is no longer enough. Security threats have become more sophisticated in their approaches to attacking businesses. The severity of a security breach can be disastrous, if not fatal to an organization. Mid-market organizations, as well asremote and branch offices, face th e same types of Internet threats that larger enterprise-level networks face. The IBM Proventia Network Multi- Function Security (MFS) MX0804 and appliances from IBM Internet Security Systems (ISS) provide comprehensive security designed to preemptively stop Internet threats before they penetrate the network and disrupt business operations. Big security in a small form factor The complexity of the modern networklandscape requires businesses to adopt a multilayered approach to security. Proventia Network MFS incorporates six security technologies onto a single appliance. The Proventia Network MFS product family combines an industry-leading Intrusion Prevention System (IPS) with Stateful firewall, signature and behavioral Antivirus, virtual private network (VPN) capabilities, content filtering and anti-spam. By joining these six security modules, Proventia Network MFS provides all the security content needed to support enterpriselevel networks on a single appliance, while retaining an affordable price for midmarket organizations and business locations. Proventia Network MFS MX0804 and are ideal for midmarket businesses, branch offices and smaller retail locations. Since these technologies are consolidated onto a single device, organizations benefit from an industrial-strength security technology that does not require a host of in-house security experts to monitor and manage, or possibly jeopardize network performance. Flexible and scalable By default, the Proventia Network MFS product family provides comprehensive security the moment the appliance is attached to the network. For organizations with limited nformation technology (IT) expertise, the default settings on the Proventia Network MFS provide the security coverage needed to secure the network from attack.
2 Module Intrusion prevention Protection Delivered More than 1,800 CVEs* and hundreds more preemptive protection algorithms on by default Antivirus Sophos provides more than 340,000 virus signatures for known viruses and behavioural detection of unknown viruses Anti-spam Web filtering 95 percent of spam blocked More than 9 Billion URLs categorized to the filter list For businesses with IT expertise, Proventia Network MFS MX0804 and can be customized to seamlessly integrate into even the most advanced network environments. Businesses can choose which security modules to utilize, create policies that allow/deny specific Internet traffic, and build groups within the network to establish permission to access certain information. To help reduce the amount of individual hands on time required, a single policy can be applied across multiple devices, thereby allowing you to manage groups of devices rather than each device seperately. Meeting compliance requirements Business compliance and industry regulations can also add a level of complexity to network security, as well as increase cost and drain IT resources in an often already-strained department. Proventia Network MFS MX0804 and are designed to protect organizations against security threats, safeguard critical data and help meet security requirements for regulation such as Sarbanes-Oxley (SOX), the Health Insurance Portability and Accountability Act (HIPAA) and the payment Card Industry (PCI) Data Security Standard (the Proventia Network MFS family helps to achieve Proventia Network MFS can also help organizations manage the security posture of multiple locations from a single site. The security architecture can even be standardized through the use of such features as locally resolved variables. For organizations with more than ten locations, or for those looking 10 out of the 12 security standards defined by the PCI Data Security Standard) without increasing the budget or draining IT resources. In fact, the Proventia Network MFS product family can help reduce IT resource requirements, allowing organizations to focus on revenue-generating activities. for advanced reporting features and management capabilities, Proventia Features and benefits at a glance Network MFS, combined with the IBM Performance-based protection offers Proventia Management SiteProtector system, can provide a complete set of central management features that help save time and reduce complexity. the industry s leading performancebased service level agreements (SLAs) with a cash-back payment when managed by IBM ISS. All-in-one protection helps eliminate the need to acquire, install and manage multiple solutions from different vendors by offering all six security modules for one low price. Easy to manage allows organizations the option to plug and play the device or customize the security features to meet their needs. Easy to update supplies prompt updates via IBM X-Press Update product enhancements, to help protect businesses against the newest security threats by updating without manual intervention or system downtime. Virtual patch protection helps provide pre-emptive protection that is designed to put organizations in control over ad-hoc and emergency patching by shielding vulnerabilities at the network level. IBM Internet Security Systems X-Force research and development team security intelligence provides easily accessible event details, including full descriptions with recommended actions and responses Intuitive reporting transforms raw data into informative and intuitive reports to aid decision making. Streamlined compliance helps achieve compliance with security protocols in such industry regulations such as HIPAA, SOX and the PCI Data Security Standard.
3 Specifications MX0804 Hardware specifications Form factor Interfaces (10/100/1000) Weight Dimensions (W x H x D) Enclosure Serial ports UPS support AC power Operating Emissions/Product Safety/Certifications Redundant power supply Redundant disk array Operating system (OS) Meantime between failure (MTBF) Network Features Network Address Translation (NAT) Masquerading/port address translation Reverse NAT Traffic-based access control Dynamic Host Configuration Protocol (DHCP) Point-to-Point Protocol over Ethernet (PPoE) Layer 2 mode Open Shortest Path First (OSPF) Desktop Four 10/100/ kg (2.6 lbs) 250 x 39 x 177 mm 9.8 x 1.5 x 6.9 inches Desktop One HZ full range 0-40 Celsius Fahrenheit 5-85 C/104 F U.S.: FCC CFR47 Part 15 Class A Europe: CISPR 22 Class A; CE Mark of Conformity Japan: VCCI-A Korea: Korean Requirement Class A Australia/New Zealand: ACA C-Tick UL st Edition Underwriters Laboratory, Safety Information CAN/CSA st Edition EN :2001 European rm IEC st Edition, International Electrotechnical Commission, Safety Information rdic deviations to IEC st Edition Proprietary 30,000 hours (3.4 years) IP, Port, protocol Client and Server Desktop Four 10/100/1000 Mbps 1.2 kg (2.6 lbs) 250 x 39 x 177 mm 9.8 x 1.5 x 6.9 inches Desktop One HZ full range 0-40 Celsius Fahrenheit 5-85 C/104 F U.S.: FCC CFR47 Part 15 Class B Europe: CISPR 22 Class B; CE Mark of Conformity Japan: VCCI-B Korea: Korean Requirement Class B Australia/New Zealand: ACA C-Tick UL st Edition Underwriters Laboratory, Safety Information CAN/CSA st Edition EN :2001 European rm IEC st Edition, International Electrotechnical Commission, Safety Information rdic deviations to IEC st Edition Proprietary 30,000 hours (3.4 years) IP, Port, protocol Client and Server
4 Quality of Service (QoS) RIP VPN features ** Internet Protocol Security (IPSec) with Internet Key Exchange (IKE) Layer Two Tunneling Protocol support (L2TP) Encryption algorithms Authentication algorithms Perfect forward secrecy (Diffie-Hellman) IPSec NAT traversal Public Key Infrastructure (PKI) support Interoperability with major VPN vendors (IPSec) Microsoft Windows XP client wizard SSL VPN features Modes of Access Authentication Mechanisms Client Security Checks User / Group Access Control VPN Tunnels Protected Maximum Concurrent Users Web Filtering URL blocking Rate of URL database updates Number of URL categories Image analysis Text Analysis User-configurable include/exclude lists Spyware analysis Anti-spam Spam-detection rate False-positive rate Subject-line tagging Automatic spam deletion Spam sample database Supports mail protocols Simple Mail Transfer protocol (SMTP) and Post Office Protocol 3 (POP3) MX0804 Traffic Prioritization, Bandwidth Enforcement, Bandwidth Guarantees Version 1, Version 2 DES, 3DES, AES MD5, SHA-1 Groups 1, 2, 5 Included Web, Web and TCP, Full Install Active Directory, LDAP, RADIUS, X509 IPS, Antivirus, SPAM, URL Filtering 10 More than 9 Billion URLs categorized More than 300,000 updated URLs daily 62+ Greater than 95% 0.01% (1 in 10,000) More than 200,000 Traffic Prioritization, Bandwidth Enforcement, Bandwidth Guarantees Version 1, Version 2 DES, 3DES, AES MD5, SHA-1 Groups 1, 2, 5 Included Web, Web and TCP, Full Install Active Directory, LDAP, RADIUS, X509 IPS, Antivirus, SPAM, URL Filtering 10 More than 9 Billion URLs categorized More than 300,000 updated URLs daily 62+ Greater than 95% 0.01% (1 in 10,000) More than 200,000
5 MX0804 Intrusion Prevention System (IPS)/ IntrusionDetection System (IDS Number of protocols and filetypes inspected Number of attack detection algorithms Blocking Number of blocked CVEs out-of-the-box Other preemptive decodes blocked out-of-the-box Web application protection Data Loss Prevention capabilities Drop offending packet Reset connection Block connection Block worm Block Trojan Block intruder Neuter attack Block future traffic Performance Maximum recommended users*** Stateful throughput speed (firewall only) Full inspection speed firewall, IPS and Web filtering Full inspection speed IPS, Web filtering and antivirus (mail only) Full inspection speed IPS, Web filtering and antivirus (mail, FTP, Web) Maximum connections per second Maximum concurrent sessions More than 200 More than 2,500 More than 1,800 More than 400 Detects/Blocks: SSNs, CC numbers and addresses in normal data stream and can inspect Microsoft Office document attachments Mbps 15 Mbps 2,000 50,000 More than 200 More than 2,500 More than 1,800 More than 400 Detects/Blocks: SSNs, CC numbers and addresses in normal data stream and can inspect Microsoft Office document attachments Mbps 34 Mbps 3,000 50,000
6 MX0804 VPN Performance VPN capacity or maximum recommended tunnels (site-to-site/remote) Maximum VPN 3DES encryption speed Maximum VPN AES encryption speed**** Maximum VPN 3DES encryption speed with hardware acceleration**** Maximum VPN AES encryption speed with hardware acceleration**** (with both antivirus and anti-spam) Maximum number of 1KB messages throughput per hour Maximum number of 1KB messages with 500KB attachments throughput per hour Logging / notification Event logging Simple Network Management Protocol (SNMP) High-availability Active / passive VPN user authentication Internal database RADIUS (external) database LDAP support RSA SecureID (external) database Xauth over RADIUS for IPSec VPN IP/MAC address binding Management Centralized management Local management Multiple administrators and user levels External administrator database Multilanguage support Secure shell (SSH) access 15 Mbps 30 Mbps N/A N/A Through RADIUS Through RADIUS Management (with SiteProtector system) Web-based (with SiteProtector system) (with SiteProtector system) English, Japanese SSH 25 Mbps 50 Mbps N/A N/A 1, Through RADIUS Through RADIUS Management (with SiteProtector system) Web-based (with SiteProtector system) (with SiteProtector system) English, Japanese SSH
7 MX0804 Customer support Hours available Standard Hours available Premium Number of support incidents Number of designated callers Additional designated callers Additional languages Customer portal Customer knowledgebase Warranty Advanced hardware replacement Third Party Certifications 24x7x365 24x7x365 Unlimited From two to five Optional Optional One year + contract SCP (Service, Capability &Performance) Standard NSS Labs ICSA VPNC (Virtual Private Network Consortium) 24x7x365 24x7x365 Unlimited From two to five Optional Optional One year + contract SCP (Service, Capability &Performance) Standard NSS Labs ICSA VPNC (Virtual Private Network Consortium) * Common Vulnerabilities and Exposures (CVE) as recorded on **Free VPN client available using Windows XP L2TP VPN client or by purchasing a separate VPN client. *** Capacity ratings based on nodes represent general guidelines about the size of the network that should be placed behind a particular Proventia NetworkMulti-Function appliance model. Proventia Network MFS MX0804L, L, MX3006L, MX4006L, MX5008L & MX5110L models are limited to a maximum VPN performance of 44 Mbps. ****The Proventia Network MFS MX0804W, W, MX3006W, MX4006W, MX5008W & MX5110W models only contain the DES Encryption Algorithm to meet Russian Federation encryption requirements.
8 About IBM ISS IBM ISS is the trusted security expert to global enterprises and world governments, providing products and services that protect against Internet threats. An established world leader in security since 1994, IBM ISS delivers proven cost efficiencies and reduces regulatory and business risk across the enterprise. IBM ISS products and services are based on the proactive security intelligence conducted by the X-Force team a world authority in vulnerability and threat research. For more information about Proventia Network MFS MX0804 or, please contact your IBM representative or IBM Business Partner. You may also call or visit ibm.com/ services/us/iss. Copyright IBM Corporation 2009 IBM Global Services Route 100 Somers, NY U.S.A. Produced in the United States of America All Rights Reserved. IBM and the IBM logo are trademarks or registered trademarks of International Business Machines Corporation in the United States, other countries, or both. Proventia, SiteProtector and X-Force are trademarks or registered trademarks of Internet Security Systems, Inc., in the United States, other countries, or both. Internet Security Systems, Inc., is a wholly-owned subsidiary of International Business Machines Corporation. Microsoft and Windows are trademarks of Microsoft Corporation in the United States, other countries, or both. Other company, product and service names may be trademarks or service marks of others. References in this publication to IBM products or services do not imply that IBM intends to make them available in all countries in which IBM operates. * Money-back payment (for Managed Protection Services - Premium Level only): If IBM Internet Security Systems fails to meet the Security Incidents Prevention Guarantee, client shall be paid US$50,000 for each instance this guarantee has not been met. Please see IBM Internet Security Systems SLAs for more details. The customer is responsible for ensuring compliance with legal requirements. It is the customer s sole responsibility to obtain advice of competent legal counsel as to the identification and interpretation of any relevant laws and regulatory requirements that may affect the customer s business and any actions the reader may have to take to comply with such laws. IBM does not provide legal advice or represent or warrant that its services or products will ensure that the customer is in compliance with any law or regulation. SED03088-USEN-00
IBM Proventia Network Multi-Function Security MX0804 and MX1004
 One appliance, six security features designed to preemptively stop Internet threats IBM Proventia Network Multi-Function Security MX0804 and one is safe Single layered security such as a firewall or antivirus
One appliance, six security features designed to preemptively stop Internet threats IBM Proventia Network Multi-Function Security MX0804 and one is safe Single layered security such as a firewall or antivirus
IBM Proventia Network Multi-Function Security MX1004
 Delivering comprehensive protection from a single device IBM Proventia Network Multi-Function Security MX1004 Comprehensive, affordable network protection for any size business The IBM Proventia Network
Delivering comprehensive protection from a single device IBM Proventia Network Multi-Function Security MX1004 Comprehensive, affordable network protection for any size business The IBM Proventia Network
IBM Proventia Network Multi-Function Security MX1004
 Delivering comprehensive protection from a single device IBM Proventia Network Multi-Function Security MX1004 Comprehensive, affordable network protection for any size business The IBM Proventia Network
Delivering comprehensive protection from a single device IBM Proventia Network Multi-Function Security MX1004 Comprehensive, affordable network protection for any size business The IBM Proventia Network
IBM Global Technology Services Provide around-the-clock expertise and protect against Internet threats.
 IBM Global Technology Services Provide around-the-clock expertise and protect against Internet threats. Enhancing cost to serve and pricing maturity Keeping up with quickly evolving ` Internet threats
IBM Global Technology Services Provide around-the-clock expertise and protect against Internet threats. Enhancing cost to serve and pricing maturity Keeping up with quickly evolving ` Internet threats
IBM Proventia Network Multi-Function Security offers security protection at a low cost in a single device
 IBM United States Announcement 608-005, dated January 15, 2008 IBM Proventia Network Multi-Function Security offers security protection at a low cost in a single device Description...2 Installation...6
IBM United States Announcement 608-005, dated January 15, 2008 IBM Proventia Network Multi-Function Security offers security protection at a low cost in a single device Description...2 Installation...6
IBM Internet Security Systems October Market Intelligence Brief
 IBM Internet Security Systems October 2007 Market Intelligence Brief Page 1 Contents 1 All About AIX : Security for IBM AIX 1 AIX Adoption Rates 2 Security Benefits within AIX 3 Benefits of RealSecure
IBM Internet Security Systems October 2007 Market Intelligence Brief Page 1 Contents 1 All About AIX : Security for IBM AIX 1 AIX Adoption Rates 2 Security Benefits within AIX 3 Benefits of RealSecure
IBM Proventia Network Anomaly Detection System
 Providing enterprise network visibility and internal network protection IBM Proventia Network Anomaly Detection System Enhanced network intelligence and security for enterprise networks IBM Proventia Network
Providing enterprise network visibility and internal network protection IBM Proventia Network Anomaly Detection System Enhanced network intelligence and security for enterprise networks IBM Proventia Network
IBM Proventia Network Enterprise Scanner
 Protecting corporate data with preemptive risk identification IBM Proventia Network Enterprise Scanner Identifying risk and prioritizing protection IBM Proventia Network Enterprise Scanner * (Enterprise
Protecting corporate data with preemptive risk identification IBM Proventia Network Enterprise Scanner Identifying risk and prioritizing protection IBM Proventia Network Enterprise Scanner * (Enterprise
NSG100 Nebula Cloud Managed Security Gateway
 Managed Security Gateway The Zyxel Nebula Cloud Managed Security Gateway is built with remote management and ironclad security for organizations with growing numbers of distributed sites. With the extensive
Managed Security Gateway The Zyxel Nebula Cloud Managed Security Gateway is built with remote management and ironclad security for organizations with growing numbers of distributed sites. With the extensive
NSG50/100/200 Nebula Cloud Managed Security Gateway
 NSG50/100/200 Managed The Zyxel Managed is built with remote management and ironclad security for organizations with growing numbers of distributed sites. With the extensive suite of security features
NSG50/100/200 Managed The Zyxel Managed is built with remote management and ironclad security for organizations with growing numbers of distributed sites. With the extensive suite of security features
Gigabit SSL VPN Security Router
 As Internet becomes essential for business, the crucial solution to prevent your Internet connection from failure is to have more than one connection. PLANET is the ideal to help the SMBs increase the
As Internet becomes essential for business, the crucial solution to prevent your Internet connection from failure is to have more than one connection. PLANET is the ideal to help the SMBs increase the
IBM Internet Security Systems Proventia Management SiteProtector
 Supporting compliance and mitigating risk through centralized management of enterprise security devices IBM Internet Security Systems Proventia Management SiteProtector Highlights Reduces the costs and
Supporting compliance and mitigating risk through centralized management of enterprise security devices IBM Internet Security Systems Proventia Management SiteProtector Highlights Reduces the costs and
NSG50/100/200 Nebula Cloud Managed Security Gateway
 NSG50/100/200 The Zyxel is built with remote management and ironclad security for organizations with multiple distributed sites. With an extensive suite of security features including ICSAcertified firewall,
NSG50/100/200 The Zyxel is built with remote management and ironclad security for organizations with multiple distributed sites. With an extensive suite of security features including ICSAcertified firewall,
Alcatel OmniAccess 200 Series
 Alcatel OmniAccess Alcatel OmniAccess 200 Series Security Appliance The corporate enterprise s most valued asset is mission critical data whether it is accessed by only a few or many thousands of employees.
Alcatel OmniAccess Alcatel OmniAccess 200 Series Security Appliance The corporate enterprise s most valued asset is mission critical data whether it is accessed by only a few or many thousands of employees.
The SonicWALL SSL-VPN Series
 The SSL-VPN Series SSL-V PN Simple, Affordable, Secure and Clientless Remote Access Seamless integration behind virtually any firewall Clientless connectivity Unrestricted concurrent user tunnels NetExtender
The SSL-VPN Series SSL-V PN Simple, Affordable, Secure and Clientless Remote Access Seamless integration behind virtually any firewall Clientless connectivity Unrestricted concurrent user tunnels NetExtender
Future-ready security for small and mid-size enterprises
 First line of defense for your network Quick Heal Terminator (UTM) (Unified Threat Management Solution) Data Sheet Future-ready security for small and mid-size enterprises Quick Heal Terminator is a high-performance,
First line of defense for your network Quick Heal Terminator (UTM) (Unified Threat Management Solution) Data Sheet Future-ready security for small and mid-size enterprises Quick Heal Terminator is a high-performance,
Cisco SR 520-T1 Secure Router
 Secure, High-Bandwidth Connectivity for Your Small Business Part of the Cisco Small Business Pro Series Connections -- between employees, customers, partners, and suppliers -- are essential to the success
Secure, High-Bandwidth Connectivity for Your Small Business Part of the Cisco Small Business Pro Series Connections -- between employees, customers, partners, and suppliers -- are essential to the success
Next-Generation Firewall Series Datasheet
 RUIJIE NETWORKS COMPANY LIMITED www.ruijienetworks.com Ruijie 1600 Next-Generation Firewall Series Datasheet Ruijie 1600 Firewall Series is a collection of nextgeneration firewall offering security, routing
RUIJIE NETWORKS COMPANY LIMITED www.ruijienetworks.com Ruijie 1600 Next-Generation Firewall Series Datasheet Ruijie 1600 Firewall Series is a collection of nextgeneration firewall offering security, routing
Cisco ASA 5500 Series IPS Solution
 Cisco ASA 5500 Series IPS Product Overview As mobile devices and Web 2.0 applications proliferate, it becomes harder to secure corporate perimeters. Traditional firewall and intrusion prevention system
Cisco ASA 5500 Series IPS Product Overview As mobile devices and Web 2.0 applications proliferate, it becomes harder to secure corporate perimeters. Traditional firewall and intrusion prevention system
IBM Europe, Middle East, and Africa Services Announcement ZS , dated October 6, 2009
 Services Announcement ZS09-0202, dated October 6, 2009 Security software for IBM Proventia Endpoint Secure Control, IBM ISS Data Security Services endpoint system protection - Digital Guardian software
Services Announcement ZS09-0202, dated October 6, 2009 Security software for IBM Proventia Endpoint Secure Control, IBM ISS Data Security Services endpoint system protection - Digital Guardian software
IBM Security Services Overview
 Services Overview Massimo Nardone Senior Lead IT Security Architect Global Technology Services, IBM Internet Security Systems massimo.nardone@fi.ibm.com THE VEHICLE THE SKILL THE SOLUTION Today s Business
Services Overview Massimo Nardone Senior Lead IT Security Architect Global Technology Services, IBM Internet Security Systems massimo.nardone@fi.ibm.com THE VEHICLE THE SKILL THE SOLUTION Today s Business
Establish and Maintain Secure Cardholder Data with IBM Payment Card Industry Solutions
 Providing stronger ssecurity practices that enable PCI Compliance and protect cardholder data. Establish and Maintain Secure Cardholder Data with IBM Payment Card Industry Solutions Highlights Pre-assessment
Providing stronger ssecurity practices that enable PCI Compliance and protect cardholder data. Establish and Maintain Secure Cardholder Data with IBM Payment Card Industry Solutions Highlights Pre-assessment
UNIFIED THREAT MANAGEMENT SOLUTIONS AND NEXT-GENERATION FIREWALLS NETWORK SECURITY NETWORK SECURITY I ENDPOINT SECURITY I DATA SECURITY
 UNIFIED THREAT MANAGEMENT SOLUTIONS AND NEXT-GENERATION FIREWALLS NETWORK SECURITY NETWORK SECURITY I ENDPOINT SECURITY I DATA SECURITY OUR MISSION Provide cybersecurity and data protection for organizations,
UNIFIED THREAT MANAGEMENT SOLUTIONS AND NEXT-GENERATION FIREWALLS NETWORK SECURITY NETWORK SECURITY I ENDPOINT SECURITY I DATA SECURITY OUR MISSION Provide cybersecurity and data protection for organizations,
NETWORK SECURITY STORMSHIELD. Unified Threat Management Solutions and Next- Generation Firewalls
 NETWORK SECURITY STORMSHIELD NETWORK SECURITY Unified Threat Management Solutions and Next- Generation Firewalls Our Mission Make the digital world a sustainable and trustworthy environment while ensuring
NETWORK SECURITY STORMSHIELD NETWORK SECURITY Unified Threat Management Solutions and Next- Generation Firewalls Our Mission Make the digital world a sustainable and trustworthy environment while ensuring
Symantec Network Security 7100 Series
 Symantec Network Security 7100 Series Proactive intrusion prevention device protects against known and unknown attacks to secure critical networks transition can be accomplished transparent to any network
Symantec Network Security 7100 Series Proactive intrusion prevention device protects against known and unknown attacks to secure critical networks transition can be accomplished transparent to any network
Training UNIFIED SECURITY. Signature based packet analysis
 Training UNIFIED SECURITY Signature based packet analysis At the core of its scanning technology, Kerio Control integrates a packet analyzer based on Snort. Snort is an open source IDS/IPS system that
Training UNIFIED SECURITY Signature based packet analysis At the core of its scanning technology, Kerio Control integrates a packet analyzer based on Snort. Snort is an open source IDS/IPS system that
IBM Tivoli Directory Server
 Build a powerful, security-rich data foundation for enterprise identity management IBM Tivoli Directory Server Highlights Support hundreds of millions of entries by leveraging advanced reliability and
Build a powerful, security-rich data foundation for enterprise identity management IBM Tivoli Directory Server Highlights Support hundreds of millions of entries by leveraging advanced reliability and
Cloud-based data backup: a buyer s guide
 IBM Global Technology Services IBM SmartCloud IBM Managed Backupi Cloud-based data backup: a buyer s guide How to choose a third-party provider to develop, implement and manage your data backup solution
IBM Global Technology Services IBM SmartCloud IBM Managed Backupi Cloud-based data backup: a buyer s guide How to choose a third-party provider to develop, implement and manage your data backup solution
Cisco RV180 VPN Router
 Cisco RV180 VPN Router Secure, high-performance connectivity at a price you can afford. Figure 1. Cisco RV180 VPN Router (Front Panel) Highlights Affordable, high-performance Gigabit Ethernet ports allow
Cisco RV180 VPN Router Secure, high-performance connectivity at a price you can afford. Figure 1. Cisco RV180 VPN Router (Front Panel) Highlights Affordable, high-performance Gigabit Ethernet ports allow
PASS4TEST. IT Certification Guaranteed, The Easy Way! We offer free update service for one year
 PASS4TEST IT Certification Guaranteed, The Easy Way! \ http://www.pass4test.com We offer free update service for one year Exam : 642-504 Title : Securing Networks with Cisco Routers and Switches Vendors
PASS4TEST IT Certification Guaranteed, The Easy Way! \ http://www.pass4test.com We offer free update service for one year Exam : 642-504 Title : Securing Networks with Cisco Routers and Switches Vendors
Corente Cloud Services Exchange
 Corente Cloud Services Exchange Oracle s Corente Cloud Services Exchange (Corente CSX) is a cloud-based service that enables distributed enterprises to deliver trusted IPSec VPN connectivity services to
Corente Cloud Services Exchange Oracle s Corente Cloud Services Exchange (Corente CSX) is a cloud-based service that enables distributed enterprises to deliver trusted IPSec VPN connectivity services to
Security with Passion. Endian UTM Virtual Appliance
 Security with Passion Endian UTM Virtual Appliance Endian UTM Virtual Appliance Endian UTM Virtual Appliance: Secure and Protect your Virtual Infrastructure Whether you are securing your internal virtual
Security with Passion Endian UTM Virtual Appliance Endian UTM Virtual Appliance Endian UTM Virtual Appliance: Secure and Protect your Virtual Infrastructure Whether you are securing your internal virtual
The SonicWALL PRO Series
 The SonicWALL PRO Series NETWORK SECURITY Dynamic Multi-function Network Security Appliances Powerful re-assembly free deep packet inspection engine Real-time gateway anti-virus, anti-spyware, anti-spam
The SonicWALL PRO Series NETWORK SECURITY Dynamic Multi-function Network Security Appliances Powerful re-assembly free deep packet inspection engine Real-time gateway anti-virus, anti-spyware, anti-spam
McAfee Network Security Platform
 McAfee Network Security Platform A uniquely intelligent approach to network security McAfee Network Security Platform is a uniquely intelligent security solution that discovers and blocks sophisticated
McAfee Network Security Platform A uniquely intelligent approach to network security McAfee Network Security Platform is a uniquely intelligent security solution that discovers and blocks sophisticated
Features. HDX WAN optimization. QoS
 May 2013 Citrix CloudBridge Accelerates, controls and optimizes applications to all locations: datacenter, branch offices, public and private clouds and mobile users Citrix CloudBridge provides a unified
May 2013 Citrix CloudBridge Accelerates, controls and optimizes applications to all locations: datacenter, branch offices, public and private clouds and mobile users Citrix CloudBridge provides a unified
IronPort C100 for Small and Medium Businesses
 I R O N P O R T E M A I L S E C U R I T Y A P P L I A N C E S S I M P L E I N S TA L L AT I O N, E A S Y M A N A G E M E N T, A N D P O W E R F U L P R O T E C T I O N F O R Y O U R E M A I L I N F R A
I R O N P O R T E M A I L S E C U R I T Y A P P L I A N C E S S I M P L E I N S TA L L AT I O N, E A S Y M A N A G E M E N T, A N D P O W E R F U L P R O T E C T I O N F O R Y O U R E M A I L I N F R A
Addendum to RFP SSL/IT/RFP-004/ dated 28-March-2017
 Addendum to RFP SSL/IT/RFP-00/0- dated -March-0 Revised RFP Submission date: th April 0, 00 Hours RFP is now open for all SBI empanelled and non-empanelled bidders. Additional Requirement: Bidders are
Addendum to RFP SSL/IT/RFP-00/0- dated -March-0 Revised RFP Submission date: th April 0, 00 Hours RFP is now open for all SBI empanelled and non-empanelled bidders. Additional Requirement: Bidders are
University of Pittsburgh Security Assessment Questionnaire (v1.7)
 Technology Help Desk 412 624-HELP [4357] technology.pitt.edu University of Pittsburgh Security Assessment Questionnaire (v1.7) Directions and Instructions for completing this assessment The answers provided
Technology Help Desk 412 624-HELP [4357] technology.pitt.edu University of Pittsburgh Security Assessment Questionnaire (v1.7) Directions and Instructions for completing this assessment The answers provided
SteelGate Overview. Manage perimeter security and network traffic to ensure operational efficiency, and optimal Quality of Service (QoS)
 Internet Communications Made Safe SteelGate Overview SteelGate Overview SteelGate is a high-performance VPN firewall appliance that Prevent Eliminate threats & attacks at the perimeter Stop unauthorized
Internet Communications Made Safe SteelGate Overview SteelGate Overview SteelGate is a high-performance VPN firewall appliance that Prevent Eliminate threats & attacks at the perimeter Stop unauthorized
McAfee Network Security Platform
 McAfee Network Security Platform A uniquely intelligent approach to network security McAfee Network Security Platform is a uniquely intelligent security solution that discovers and blocks sophisticated
McAfee Network Security Platform A uniquely intelligent approach to network security McAfee Network Security Platform is a uniquely intelligent security solution that discovers and blocks sophisticated
Meraki MX Family Cloud Managed Security Appliances
 DATASHEET Meraki MX Family Cloud Managed Security Appliances Overview The Meraki MX is a complete next generation firewall and branch gateway solution, designed to make distributed networks fast, secure,
DATASHEET Meraki MX Family Cloud Managed Security Appliances Overview The Meraki MX is a complete next generation firewall and branch gateway solution, designed to make distributed networks fast, secure,
GLOBALPROTECT. Key Usage Scenarios and Benefits. Remote Access VPN Provides secure access to internal and cloud-based business applications
 GLOBALPROTECT Prevent Breaches and Secure the Mobile Workforce GlobalProtect extends the protection of Palo Alto Networks Next-Generation Security Platform to the members of your mobile workforce, no matter
GLOBALPROTECT Prevent Breaches and Secure the Mobile Workforce GlobalProtect extends the protection of Palo Alto Networks Next-Generation Security Platform to the members of your mobile workforce, no matter
Easy To Install. Easy To Manage. Always Up-To-Date.
 WATCHGUARD FIREBOX SYSTEM Easy To Install. Easy To Manage. Always Up-To-Date. Overview The WatchGuard Firebox System is a comprehensive firewall and VPN security solution that reduces the time and resources
WATCHGUARD FIREBOX SYSTEM Easy To Install. Easy To Manage. Always Up-To-Date. Overview The WatchGuard Firebox System is a comprehensive firewall and VPN security solution that reduces the time and resources
QUICKSTART GUIDE FOR BRANCH SRX SERIES SERVICES GATEWAYS
 APPLICATION NOTE QUICKSTART GUIDE FOR BRANCH SRX SERIES SERVICES GATEWAYS Configuring Basic Security and Connectivity on Branch SRX Series Services Gateways Copyright 2009, Juniper Networks, Inc. Table
APPLICATION NOTE QUICKSTART GUIDE FOR BRANCH SRX SERIES SERVICES GATEWAYS Configuring Basic Security and Connectivity on Branch SRX Series Services Gateways Copyright 2009, Juniper Networks, Inc. Table
Internet Scanner 7.0 Service Pack 2 Frequently Asked Questions
 Frequently Asked Questions Internet Scanner 7.0 Service Pack 2 Frequently Asked Questions April 2005 6303 Barfield Road Atlanta, GA 30328 Tel: 404.236.2600 Fax: 404.236.2626 Internet Security Systems (ISS)
Frequently Asked Questions Internet Scanner 7.0 Service Pack 2 Frequently Asked Questions April 2005 6303 Barfield Road Atlanta, GA 30328 Tel: 404.236.2600 Fax: 404.236.2626 Internet Security Systems (ISS)
Seqrite TERMINATOR (UTM) Unified Threat Management Solution.
 Unified Threat Management Solution TERMINATOR Introduction Seqrite TERMINATOR is a high-performance, easy-to-use Unified Threat Management solution for small and mid-size enterprises. It is a robust solution
Unified Threat Management Solution TERMINATOR Introduction Seqrite TERMINATOR is a high-performance, easy-to-use Unified Threat Management solution for small and mid-size enterprises. It is a robust solution
VPN Routers DSR-150/250/500/1000AC. Product Highlights. Features. Overview. Comprehensive Management Capabilities. Web Authentication Capabilities
 Product Highlights Comprehensive Management Solution Advanced features such as WAN failover, load balancing, and integrated firewall help make this a reliable, secure, and flexible way to manage your network.
Product Highlights Comprehensive Management Solution Advanced features such as WAN failover, load balancing, and integrated firewall help make this a reliable, secure, and flexible way to manage your network.
NSG50/100 Nebula Cloud Managed Security Gateway
 /100 The Zyxel is built with remote management and ironclad security for organizations with growing numbers of distributed sites. With the extensive suite of security features that includes ICSAcertified
/100 The Zyxel is built with remote management and ironclad security for organizations with growing numbers of distributed sites. With the extensive suite of security features that includes ICSAcertified
Security Assessment Checklist
 Security Assessment Checklist Westcon Security Checklist - Instructions The first step to protecting your business includes a careful and complete assessment of your security posture. Our Security Assessment
Security Assessment Checklist Westcon Security Checklist - Instructions The first step to protecting your business includes a careful and complete assessment of your security posture. Our Security Assessment
Configuring VPN from Proventia M Series Appliance to NetScreen Systems
 Configuring VPN from Proventia M Series Appliance to NetScreen Systems January 13, 2004 Overview This document describes how to configure a VPN tunnel from a Proventia M series appliance to NetScreen 208
Configuring VPN from Proventia M Series Appliance to NetScreen Systems January 13, 2004 Overview This document describes how to configure a VPN tunnel from a Proventia M series appliance to NetScreen 208
Unified Services Routers
 Product Highlights Comprehensive Management Solution Active-Active WAN port features such as auto WAN failover and load balancing, ICSA-certified firewall, and D-Link Green Technology make this a reliable,
Product Highlights Comprehensive Management Solution Active-Active WAN port features such as auto WAN failover and load balancing, ICSA-certified firewall, and D-Link Green Technology make this a reliable,
Meraki MX Family Cloud Managed Security Appliances
 DATASHEET Meraki MX Family Cloud Managed Security Appliances Overview The Meraki MX is a complete next generation firewall and branch gateway solution, designed to make distributed networks fast, secure,
DATASHEET Meraki MX Family Cloud Managed Security Appliances Overview The Meraki MX is a complete next generation firewall and branch gateway solution, designed to make distributed networks fast, secure,
Syllabus: The syllabus is broadly structured as follows:
 Syllabus: The syllabus is broadly structured as follows: SR. NO. TOPICS SUBTOPICS 1 Foundations of Network Security Principles of Network Security Network Security Terminologies Network Security and Data
Syllabus: The syllabus is broadly structured as follows: SR. NO. TOPICS SUBTOPICS 1 Foundations of Network Security Principles of Network Security Network Security Terminologies Network Security and Data
NetDefend Firewall UTM Services
 NetDefend Firewall UTM Services Unified Threat Management D-Link NetDefend UTM firewalls (DFL-260/860/1660/2560/2560G) integrate an Intrusion Prevention System (IPS), gateway AntiVirus (AV), and Web Content
NetDefend Firewall UTM Services Unified Threat Management D-Link NetDefend UTM firewalls (DFL-260/860/1660/2560/2560G) integrate an Intrusion Prevention System (IPS), gateway AntiVirus (AV), and Web Content
Systrome Next Gen Firewalls
 N E T K S Systrome Next Gen Firewalls Systrome s Next Generation Firewalls provides comprehensive security protection from layer 2 to layer 7 for the mobile Internet era. The new next generation security
N E T K S Systrome Next Gen Firewalls Systrome s Next Generation Firewalls provides comprehensive security protection from layer 2 to layer 7 for the mobile Internet era. The new next generation security
All-in one security for large and medium-sized businesses.
 All-in one security for large and medium-sized businesses www.entensys.com sales@entensys.com Overview UserGate UTM provides firewall, intrusion detection, anti-malware, spam and content filtering, and
All-in one security for large and medium-sized businesses www.entensys.com sales@entensys.com Overview UserGate UTM provides firewall, intrusion detection, anti-malware, spam and content filtering, and
Cisco NAC Network Module for Integrated Services Routers
 Cisco NAC Network Module for Integrated Services Routers The Cisco NAC Network Module for Integrated Services Routers (NME-NAC-K9) brings the feature-rich Cisco NAC Appliance Server capabilities to Cisco
Cisco NAC Network Module for Integrated Services Routers The Cisco NAC Network Module for Integrated Services Routers (NME-NAC-K9) brings the feature-rich Cisco NAC Appliance Server capabilities to Cisco
Configuring VPN from Proventia M Series Appliance to Proventia M Series Appliance
 Configuring VPN from Proventia M Series Appliance to Proventia M Series Appliance January 13, 2004 Overview Introduction This document describes how to configure a VPN tunnel from one Proventia M series
Configuring VPN from Proventia M Series Appliance to Proventia M Series Appliance January 13, 2004 Overview Introduction This document describes how to configure a VPN tunnel from one Proventia M series
Appliance Comparison Chart
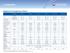 Appliance Comparison Chart Edge 0 70 570 070 070 070 Models Edge X, Edge W, Edge X ADSL, Edge W ADSL 6 7 76 57 576 07 076 07 076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65, R70 R65, R70
Appliance Comparison Chart Edge 0 70 570 070 070 070 Models Edge X, Edge W, Edge X ADSL, Edge W ADSL 6 7 76 57 576 07 076 07 076 07 076 Software Edition Embedded NGX R65, R70 R65, R70 R65, R70 R65, R70
HP Instant Support Enterprise Edition (ISEE) Security overview
 HP Instant Support Enterprise Edition (ISEE) Security overview Advanced Configuration A.03.50 Mike Brandon Interex 03 / 30, 2004 2003 Hewlett-Packard Development Company, L.P. The information contained
HP Instant Support Enterprise Edition (ISEE) Security overview Advanced Configuration A.03.50 Mike Brandon Interex 03 / 30, 2004 2003 Hewlett-Packard Development Company, L.P. The information contained
The case for cloud-based data backup
 IBM Global Technology Services IBM SmartCloud IBM Managed Backupi The case for cloud-based data backup IBM SmartCloud Managed Backup offers significant improvement over traditional data backup methods
IBM Global Technology Services IBM SmartCloud IBM Managed Backupi The case for cloud-based data backup IBM SmartCloud Managed Backup offers significant improvement over traditional data backup methods
Product Brief Nortel Switched Firewall 6000 Series
 Product Brief Nortel Switched Firewall 6000 Series Accelerated VPN-Firewall High-performance stateful firewall appliance for perimeter deployment Dual component switch-based appliance for highcapacity,
Product Brief Nortel Switched Firewall 6000 Series Accelerated VPN-Firewall High-performance stateful firewall appliance for perimeter deployment Dual component switch-based appliance for highcapacity,
etrust Antivirus Release 7.1
 D A T A S H E E T etrust Antivirus Release 7.1 etrust Antivirus provides superior protection from the perimeter to the PDA against today s most prevalent security threat viruses. It eliminates virus infections,
D A T A S H E E T etrust Antivirus Release 7.1 etrust Antivirus provides superior protection from the perimeter to the PDA against today s most prevalent security threat viruses. It eliminates virus infections,
AIR-WLC K9 Datasheet. Overview. Check its price: Click Here. Quick Specs
 AIR-WLC4402-12-K9 Datasheet Check its price: Click Here Overview Cisco 4400 Series Wireless LAN Controller provides systemwide wireless LAN functions for medium to large-sized facilities. By automating
AIR-WLC4402-12-K9 Datasheet Check its price: Click Here Overview Cisco 4400 Series Wireless LAN Controller provides systemwide wireless LAN functions for medium to large-sized facilities. By automating
Cisco SA 500 Series Security Appliances
 Cisco SA 500 Series Security Appliances An All-in-One Security Solution to Secure Your Small Business The Cisco SA 500 Series Security Appliances, part of the Cisco Small Business Pro Series, are comprehensive
Cisco SA 500 Series Security Appliances An All-in-One Security Solution to Secure Your Small Business The Cisco SA 500 Series Security Appliances, part of the Cisco Small Business Pro Series, are comprehensive
Endian Hotspot main features
 Endian Hotspot main features Service Customization Freely configurable home page after successful login Completely customizable welcome page and printed user information through a user friendly visual
Endian Hotspot main features Service Customization Freely configurable home page after successful login Completely customizable welcome page and printed user information through a user friendly visual
Cisco Network Admission Control (NAC) Solution
 Data Sheet Cisco Network Admission Control (NAC) Solution New: Updated to include the Cisco Secure Network Server (SNS) Cisco Network Admission Control (NAC) solutions allow you to authenticate wired,
Data Sheet Cisco Network Admission Control (NAC) Solution New: Updated to include the Cisco Secure Network Server (SNS) Cisco Network Admission Control (NAC) solutions allow you to authenticate wired,
IBM Security Network Protection Solutions
 Systems IBM Security IBM Security Network Protection Solutions Pre-emptive protection to keep you Ahead of the Threat Tanmay Shah Product Lead Network Protection Appliances IBM Security Systems 1 IBM Security
Systems IBM Security IBM Security Network Protection Solutions Pre-emptive protection to keep you Ahead of the Threat Tanmay Shah Product Lead Network Protection Appliances IBM Security Systems 1 IBM Security
NetDefend UTM Firewall Series
 NetDefend UTM Firewall Series Integrated Firewall/VPN Powerful Firewall Engine Virtual Private Network (VPN) Security Granular Bandwidth Management 802.1Q VLAN Tagging and Port-Based VLAN D-Link End-to-End
NetDefend UTM Firewall Series Integrated Firewall/VPN Powerful Firewall Engine Virtual Private Network (VPN) Security Granular Bandwidth Management 802.1Q VLAN Tagging and Port-Based VLAN D-Link End-to-End
Cisco VPN Internal Service Module for Cisco ISR G2
 Data Sheet Cisco VPN Internal Service Module for Cisco ISR G2 Compact Versatile High-Performance VPN Module The Cisco VPN Internal Service Module (VPN ISM) is a module for the Cisco Integrated Services
Data Sheet Cisco VPN Internal Service Module for Cisco ISR G2 Compact Versatile High-Performance VPN Module The Cisco VPN Internal Service Module (VPN ISM) is a module for the Cisco Integrated Services
CoreMax Consulting s Cyber Security Roadmap
 CoreMax Consulting s Cyber Security Roadmap What is a Cyber Security Roadmap? The CoreMax consulting cyber security unit has created a simple process to access the unique needs of each client and allows
CoreMax Consulting s Cyber Security Roadmap What is a Cyber Security Roadmap? The CoreMax consulting cyber security unit has created a simple process to access the unique needs of each client and allows
Meraki Z-Series Cloud Managed Teleworker Gateway
 Datasheet Z Series Meraki Z-Series Cloud Managed Teleworker Gateway Fast, Reliable Connectivity for the Modern Teleworker The Cisco Meraki Z-Series teleworker gateway is an enterprise class firewall, VPN
Datasheet Z Series Meraki Z-Series Cloud Managed Teleworker Gateway Fast, Reliable Connectivity for the Modern Teleworker The Cisco Meraki Z-Series teleworker gateway is an enterprise class firewall, VPN
Exam: : VPN/Security. Ver :
 Exam: Title : VPN/Security Ver : 03.20.04 QUESTION 1 A customer needs to connect smaller branch office locations to its central site and desires a more which solution should you recommend? A. V3PN solution
Exam: Title : VPN/Security Ver : 03.20.04 QUESTION 1 A customer needs to connect smaller branch office locations to its central site and desires a more which solution should you recommend? A. V3PN solution
IronPort X1000 Security System
 I r o n P o r t E M A I L S E C U R I T Y A P P L I A N C E S T H E U LT I M AT E E M A I L S E C U R I T Y S Y S T E M F O R T H E W O R L D S M O S T D E M A N D I N G N E T W O R K S. IronPort X1000
I r o n P o r t E M A I L S E C U R I T Y A P P L I A N C E S T H E U LT I M AT E E M A I L S E C U R I T Y S Y S T E M F O R T H E W O R L D S M O S T D E M A N D I N G N E T W O R K S. IronPort X1000
Datasheet Fujitsu ETERNUS DX60 S2 Disk Storage System
 Datasheet Fujitsu ETERNUS DX60 S2 Disk Storage System The Economy Storage ETERNUS DX S2 DISK STORAGE SYSTEMS Fujitsu s second generation of ETERNUS DX disk storage systems, ETERNUS DX S2, are The Flexible
Datasheet Fujitsu ETERNUS DX60 S2 Disk Storage System The Economy Storage ETERNUS DX S2 DISK STORAGE SYSTEMS Fujitsu s second generation of ETERNUS DX disk storage systems, ETERNUS DX S2, are The Flexible
Data Sheet FUJITSU Storage ETERNUS DX200F All-Flash-Array
 Data Sheet FUJITSU Storage ETERNUS DX200F All-Flash-Array Data Sheet FUJITSU Storage ETERNUS DX200F All-Flash-Array Superior performance at reasonable cost ETERNUS DX - Business-centric Storage ETERNUS
Data Sheet FUJITSU Storage ETERNUS DX200F All-Flash-Array Data Sheet FUJITSU Storage ETERNUS DX200F All-Flash-Array Superior performance at reasonable cost ETERNUS DX - Business-centric Storage ETERNUS
Cisco ASA 5500 Series IPS Edition for the Enterprise
 Cisco ASA 5500 Series IPS Edition for the Enterprise Attacks on critical information assets and infrastructure can seriously degrade an organization s ability to do business. The most effective risk mitigation
Cisco ASA 5500 Series IPS Edition for the Enterprise Attacks on critical information assets and infrastructure can seriously degrade an organization s ability to do business. The most effective risk mitigation
CRYPTTECH. Cost-effective log management for security and forensic analysis, ensuring compliance with mandates and storage regulations
 Cost-effective log management for security and forensic analysis, ensuring compliance with mandates and storage regulations Integration with Numerous Type of Devices Flexible Architectural Configuration
Cost-effective log management for security and forensic analysis, ensuring compliance with mandates and storage regulations Integration with Numerous Type of Devices Flexible Architectural Configuration
CCISO Blueprint v1. EC-Council
 CCISO Blueprint v1 EC-Council Categories Topics Covered Weightage 1. Governance (Policy, Legal, & Compliance) & Risk Management 1.1 Define, implement, manage and maintain an information security governance
CCISO Blueprint v1 EC-Council Categories Topics Covered Weightage 1. Governance (Policy, Legal, & Compliance) & Risk Management 1.1 Define, implement, manage and maintain an information security governance
TRACKVIA SECURITY OVERVIEW
 TRACKVIA SECURITY OVERVIEW TrackVia s customers rely on our service for many mission-critical applications, as well as for applications that have various compliance and regulatory obligations. At all times
TRACKVIA SECURITY OVERVIEW TrackVia s customers rely on our service for many mission-critical applications, as well as for applications that have various compliance and regulatory obligations. At all times
Security Terminology Related to a SOC
 Security Terminology Related to a SOC Cybersecurity literacy is crucial for practicing proper security hygiene. As business leaders develop fluency in the language of information security (infosec), they
Security Terminology Related to a SOC Cybersecurity literacy is crucial for practicing proper security hygiene. As business leaders develop fluency in the language of information security (infosec), they
Hillstone IPSec VPN Solution
 1. Introduction With the explosion of Internet, more and more companies move their network infrastructure from private lease line to internet. Internet provides a significant cost advantage over private
1. Introduction With the explosion of Internet, more and more companies move their network infrastructure from private lease line to internet. Internet provides a significant cost advantage over private
Data Sheet FUJITSU ETERNUS DX60 S3 Disk Storage System
 Data Sheet FUJITSU ETERNUS DX60 S3 Disk Storage System Data Sheet FUJITSU ETERNUS DX60 S3 Disk Storage System The Economy Storage System for SMBs ETERNUS DX Storage Combining leading performance architecture
Data Sheet FUJITSU ETERNUS DX60 S3 Disk Storage System Data Sheet FUJITSU ETERNUS DX60 S3 Disk Storage System The Economy Storage System for SMBs ETERNUS DX Storage Combining leading performance architecture
EC-Council Certified Network Defender (CND) Duration: 5 Days Method: Instructor-Led
 EC-Council Certified Network Defender (CND) Duration: 5 Days Method: Instructor-Led Certification: Certified Network Defender Exam: 312-38 Course Description This course is a vendor-neutral, hands-on,
EC-Council Certified Network Defender (CND) Duration: 5 Days Method: Instructor-Led Certification: Certified Network Defender Exam: 312-38 Course Description This course is a vendor-neutral, hands-on,
Cisco RV260 VPN Routers
 Data Sheet Cisco RV260 VPN Routers The Cisco Small Business RV260, RV260P, and RV260W VPN routers are highperformance models combining business-class features with performance, security, reliability, and
Data Sheet Cisco RV260 VPN Routers The Cisco Small Business RV260, RV260P, and RV260W VPN routers are highperformance models combining business-class features with performance, security, reliability, and
Cisco Security Solutions for Systems Engineers (SSSE) Practice Test. Version
 Cisco 642-566 642-566 Security Solutions for Systems Engineers (SSSE) Practice Test Version 3.10 QUESTION NO: 1 You are the network consultant from Your company. Please point out two requirements call
Cisco 642-566 642-566 Security Solutions for Systems Engineers (SSSE) Practice Test Version 3.10 QUESTION NO: 1 You are the network consultant from Your company. Please point out two requirements call
IBM PowerSC. Designed for Enterprise Security & Compliance in Cloud and Virtualised environments. Highlights
 IBM PowerSC Designed for Enterprise Security & Compliance in Cloud and Virtualised environments Highlights Simplify management and measurement for security & compliance Quickly view security compliance
IBM PowerSC Designed for Enterprise Security & Compliance in Cloud and Virtualised environments Highlights Simplify management and measurement for security & compliance Quickly view security compliance
Preemptive security products and services
 IBM Global Technology Services Preemptive security products and services Providing protection ahead of the threat GL_11192_ISS Green A4 brochure_01.indd 1 26/08/09 8:39 AM Today, security threats to your
IBM Global Technology Services Preemptive security products and services Providing protection ahead of the threat GL_11192_ISS Green A4 brochure_01.indd 1 26/08/09 8:39 AM Today, security threats to your
IBM System p5 550 and 550Q Express servers
 The right solutions for consolidating multiple applications on a single system IBM System p5 550 and 550Q Express servers Highlights Up to 8-core scalability using Quad-Core Module technology Point, click
The right solutions for consolidating multiple applications on a single system IBM System p5 550 and 550Q Express servers Highlights Up to 8-core scalability using Quad-Core Module technology Point, click
Data Sheet Fujitsu ETERNUS DX500 S3 Disk Storage System
 Data Sheet Fujitsu ETERNUS DX500 S3 Disk Storage System Leading storage performance, automated quality of service ETERNUS DX - Business-centric Storage ETERNUS DX500 S3 Combining leading performance architecture
Data Sheet Fujitsu ETERNUS DX500 S3 Disk Storage System Leading storage performance, automated quality of service ETERNUS DX - Business-centric Storage ETERNUS DX500 S3 Combining leading performance architecture
Cisco ACE30 Application Control Engine Module
 Data Sheet Cisco ACE30 Application Control Engine Module Product Overview The Cisco ACE30 Application Control Engine Module (Figure 1) belongs to the Cisco ACE family of application switches, which deliver
Data Sheet Cisco ACE30 Application Control Engine Module Product Overview The Cisco ACE30 Application Control Engine Module (Figure 1) belongs to the Cisco ACE family of application switches, which deliver
Security Quick Sales Guide
 Security Quick Sales Guide Security Quick Finder Product/Segment Model 200 ~ 500 PC Users USG 2000 75 ~ 200 PC Users USG 1000 50 ~ 75 PC Users USG 300 Unified Security Gateway 25 ~ 50 PC Users USG 200
Security Quick Sales Guide Security Quick Finder Product/Segment Model 200 ~ 500 PC Users USG 2000 75 ~ 200 PC Users USG 1000 50 ~ 75 PC Users USG 300 Unified Security Gateway 25 ~ 50 PC Users USG 200
Security with Passion Secure your Business with Endian UTM
 Security with Passion Endian UTM Security Gateways Secure your Business with Endian UTM Unlimited : No user licensing limitations for all functionality (VPN included) Fully Loaded: Every product has all
Security with Passion Endian UTM Security Gateways Secure your Business with Endian UTM Unlimited : No user licensing limitations for all functionality (VPN included) Fully Loaded: Every product has all
VeloCloud SD-WAN Subscription
 Enterprise/Premium Subscription Datasheet VeloCloud SD-WAN Subscription VeloCloud Cloud Delivered SD-WAN assures enterprise and cloud application performance over Internet and hybrid WAN while simplifying
Enterprise/Premium Subscription Datasheet VeloCloud SD-WAN Subscription VeloCloud Cloud Delivered SD-WAN assures enterprise and cloud application performance over Internet and hybrid WAN while simplifying
IBM SmartCloud Notes Security
 IBM Software White Paper September 2014 IBM SmartCloud Notes Security 2 IBM SmartCloud Notes Security Contents 3 Introduction 3 Service Access 4 People, Processes, and Compliance 5 Service Security IBM
IBM Software White Paper September 2014 IBM SmartCloud Notes Security 2 IBM SmartCloud Notes Security Contents 3 Introduction 3 Service Access 4 People, Processes, and Compliance 5 Service Security IBM
PineApp Mail Secure SOLUTION OVERVIEW. David Feldman, CEO
 PineApp Mail Secure SOLUTION OVERVIEW David Feldman, CEO PineApp Mail Secure INTRODUCTION ABOUT CYBONET CORE EXPERIENCE PRODUCT LINES FACTS & FIGURES Leader Product Company Servicing Multiple Vertical
PineApp Mail Secure SOLUTION OVERVIEW David Feldman, CEO PineApp Mail Secure INTRODUCTION ABOUT CYBONET CORE EXPERIENCE PRODUCT LINES FACTS & FIGURES Leader Product Company Servicing Multiple Vertical
Data Sheet Fujitsu ETERNUS DX200 S3 Disk Storage System
 Data Sheet Fujitsu ETERNUS DX200 S3 Disk Storage System The all-in-one storage system for SMBs or subsidiaries ETERNUS DX - Business-centric Storage ETERNUS DX200 S3 Combining leading performance architecture
Data Sheet Fujitsu ETERNUS DX200 S3 Disk Storage System The all-in-one storage system for SMBs or subsidiaries ETERNUS DX - Business-centric Storage ETERNUS DX200 S3 Combining leading performance architecture
Next-Generation Firewall Series Datasheet
 RUIJIE NETWORKS COMPANY LIMITED www.ruijienetworks.com Ruijie 1600 Next-Generation Firewall Series Datasheet Ruijie 1600 Firewall Series is a collection of nextgeneration firewall offering security, routing
RUIJIE NETWORKS COMPANY LIMITED www.ruijienetworks.com Ruijie 1600 Next-Generation Firewall Series Datasheet Ruijie 1600 Firewall Series is a collection of nextgeneration firewall offering security, routing
Data Security and Privacy Principles IBM Cloud Services
 Data Security and Privacy Principles IBM Cloud Services 2 Data Security and Privacy Principles: IBM Cloud Services Contents 2 Overview 2 Governance 3 Security Policies 3 Access, Intervention, Transfer
Data Security and Privacy Principles IBM Cloud Services 2 Data Security and Privacy Principles: IBM Cloud Services Contents 2 Overview 2 Governance 3 Security Policies 3 Access, Intervention, Transfer
Symantec Protection Suite Add-On for Hosted Security
 Symantec Protection Suite Add-On for Hosted Email Security Overview Malware and spam pose enormous risk to the health and viability of IT networks. Cyber criminal attacks are focused on stealing money
Symantec Protection Suite Add-On for Hosted Email Security Overview Malware and spam pose enormous risk to the health and viability of IT networks. Cyber criminal attacks are focused on stealing money
