ASA 8.x to 9.x Migration with FirePOWER Services
|
|
|
- Roy Wilkerson
- 5 years ago
- Views:
Transcription
1 ASA 8.x to 9.x Migration with FirePOWER Services Lab Guide Version 1.0 Another offering from team MIDAS November 17 th, 2014
2 2 Table of Contents Introduction... 3 Logical Topology... 4 Physical Topology... 5 Build Information... 6 Prerequisite knowledge... 6 Guide Overview... 7 Exercise 1: Pre-Deployment Work and Prerequisites... 8 Exercise 2: ASA Initial Steps Exercise 3: Backup ASA 5520 and Cisco s Firewall Migration Tool Exercise 4: Prepare Network for ASA 5525-X Exercise 5: Migrate to ASA 5525-X Exercise 6: FirePOWER and FireSIGHT Deployment Appendix A: Diff of startup-config.cfg and tgt_startup-config.cfg
3 3 Introduction Your integration company has been asked to migrate an existing ASA 5500 Series Firewall running ASA version 8.x code to a new ASA 5525-X running 9.x and the integrated FirePOWER Services module. This Lab will consist of deploying, licensing, and configuring an ASA 5525-X in a preexisting network. Specifics of what will be covered are as follows: Review the requirements and design. Connecting To the equipment Backup of Original ASA 5520 Use of Cisco FWM tool at for configuration conversion Short discussion on NAT and ACL changes between Pre8.3 and Transferring trustpoints from one ASA to another Installation of FirePOWER Services module Installation and Base configuration of FireSIGHT Management Center (formerly called Defense Center) Connection between FireSIGHT MC and ASA FirePOWER module. Please review the diagrams on the following pages carefully before proceeding. The following diagrams are of the intended layers two and three network design.
4 4 Logical Topology The diagram below depicts the logical L3 topology of the network.
5 5 Physical Topology The diagram below depicts the L2 network topology.
6 6 Disclaimer This Guide is intended to demonstrate one way to configure the network, to meet the specified requirements of this example. There are various ways that this can be accomplished, depending on the situation and the customer s goals/requirements. Please ensure that you consult all current official Cisco documentation before proceeding with a design or installation. This lab is primarily intended to be a learning tool, and may not necessarily follow best practice recommendation at all times, in order to convey specific information. This is not intended to be a deployment guide. It is intended for learning purposes only. Build Information As of the writing of this document, the current relevant documentation could be found on CCO at the following links: ASA Version 9.2(4) - Document Cisco Firewall Migration Services Web Service Cisco ASA FirePOWER Module Quick Start Guide Install and Upgrade Guides ASA 5500-X Series NGFW- Directory Cisco FireSIGHT Management Center Configuration Guides - Directory ASA with FirePOWER Services Partner POV or Lab License Request Roadshow ASA with FirePOWER Services: Technical Training Tech Talks: Security Deep Dives: Get Recognized Training: Security Programs and Promos FY15 Q2: The labs were constructed using the following software versions from CCO: ASA (5) ASDM 7.3(1) (Packet-tracer problem with this version of ASDM) ASA 5525x 9.2(2)4 ASDM 7.3(1) (Packet-tracer problem with this version of ASDM) FireSIGHT MC Prerequisite knowledge A solid understanding of networking, including routing and switching is assumed. Previous experience with Cisco s Adaptive Security Appliance is helpful.
7 7 Guide Overview This Guide covers the steps required to migrate firewalls from ASA Version 8.x to ASA Version 9.x software as well as configuring FirePOWER Services on the ASA as a sensor for use with the FireSIGHT Defense Center. The key focus of this document is to gain a basic understanding of how to migrate from an older ASA 5500 series firewall running ASA Version 8.x software to Cisco s Next Generation Firewall (NGFW) 5500-X series firewalls with ASA Version 9.x software, as well as the major changes, capabilities, requirements, and limitations associated with the products and the migration. FirePOWER Services deployment and configuration is also demonstrated as an advantage of the migration.
8 8 Exercise 1: Pre-Deployment Work and Prerequisites This exercise will cover the migration of an ASA 5520 to ASA 5525-X w/ FirePOWER Services and FireSIGHT Management Center. This part will also include reviewing the existing network, customer requirements per the design meeting, and the resulting decisions. Section 1.1 Review the Existing Network and Customer Requirements The goal of this section is to become familiar with the existing network and understand how the ASA 5525-X will replace the existing firewall, as well as review the highlights of the design meeting. We begin by taking a closer look at the layer one and two network diagrams.
9 9 Looking at the above diagram, we can see that at the bottom there are two servers. The left most is the existing Windows 2003 domain controller with which FireSIGHT Management Center will communicate with an installed user agent which will identify user s logon and logoff behavior. This will help identify user s traffic for the FireSIGHT Management Center. To the right, is Cisco s FireSIGHT Management Center, which manages the ASA FirePOWER Services sfr module. At the top of the diagram are both of the ASA s: the Cisco ASA 5525x that will be the target of the migration and the holder of the FirePOWER Services Module; and ASA The ASA 5520 is the firewall that is already in place. The ASA 5520 will be verified, backed up, and decommissioned. To the left of the core switch are two test User PCs. PC1 is the jump box that will be utilized to make most of the configuration changes in the lab. The bottom PC 2 is a member of the Example.com domain, and will be used for testing web access and IPS access policy. Now with this information in mind, take a look at the layer three diagram below.
10 10 If this were going into a customer s production system, there would be a three phase plan of execution. Day one would consist of backing up the existing configurations and reviewing the NAT and ACL rules. Due to the migration from ASA pre8.3 versions, there are some manual configurations that must be made after a migration. The current device s configuration would be sent in for conversion with the Firewall Migration Services (FWM) at Day two would be the change window requested where the new ASA 5525-X Next-Generation Firewall (NGFW) is positioned in the data path essentially replacing the existing ASA 5520 Firewall. There will be at least a small amount of downtime. Potentially worse side-effects of the migration are possible if Phase One is not done correctly and the ACL and NAT rules are not reviewed or recreated. At the end of day two the FirePOWER Services module should be deployed and connected with a FireSIGHT Management Center. This setup will start monitoring traffic and scanning for potential attack vectors and intrusions. Day three (Phase Three) would consist of applying a tuned Intrusion Policy through the FireSIGHT Management Center. After scanning during day two, the system should have an initial scan of the full network as well as valuable information regarding threats. Provided with this scan are resources to help towards threat mitigation. FireSIGHT Management Center and ASA with FirePOWER Services provides URL filtering, Application visibility and control (AVC), and Threat protection with NGIPS and Advanced Malware Protection (AMP). Continue to Exercise 2 to access the lab pod and begin the deployment.
11 11 Exercise 2: ASA Initial Steps Exercise 2 will cover the initial steps in accessing and using this lab platform. Section 2.1 Accessing the Lab Pod This section will cover how to access the devices in your lab through the ASTEC student portal. Begin by navigating to the internet reachable address shown below to access the lab. Make sure that any VPNs are closed and your client is not behind any proxies or tunnels for best performance and reliability. Below is the destination ASTEC VPN Service web page. In order to log into the lab, you will need a username and password. This should have been provided to you by the lab proctor.
12 12 With the username and password you received from your lab proctor, you should have also received a pod number. This pod number will correspond with your given username. For example; pod one will have a username of stu-aa, and pod two will have a username of stu-ab, and so on. Using your given username and password, log into the ASTEC Student Portal as shown below. As stated above, each username automatically selects the correct pod number. After clicking Login, the message shown below will appear. Click Continue, to accept the welcome message and access the lab portal.
13 13 Below is the resulting Lab portal page, containing six links, each of which will connect you directly to the listed device. Before beginning the Lab, open each of the items, starting with User PC1. To open each item in a new tab, click on the overlapping boxes icon to the left of each link, as shown below.
14 14 Upon clicking the icon to the left of each link, the page shown below will open, and you may receive a security warning. Click on the Continue button, to accept the warning and proceed. A second security warning will appear. Click the checked box to accept the risk and select Run.
15 15 Proceeding, accepting the security warnings a TightVNC connection will open, as can be seen below. After a moment, the TightVNC connection should connect, and PC1 should appear as seen below.
16 16 Now, open the other listed items the same way from the student portal, starting with User PC2.
17 17 Now, open the connection to the DC.
18 18 Now, open the connection to the Defense Center (which is now called FireSIGHT Management Center by Cisco).
19 19 Now, open the connection to the Web1.
20 20 Now, open the connection to the User PC3 Make certain that each of the four connections to the lab devices opens successfully, before continuing any further in the lab. If you have a problem, contact your lab proctor.
21 21 Section 2.2 Verify Connectivity to Internet and Lab Equipment This section will cover connecting to the lab equipment and creating a full configuration backup of the ASA 5520 prior to migration. Begin by returning to the PC1 connection you opened in Section 2.1. Log into PC1 under the John Doe local machine account, using the password shown below. The John Doe account is selected automatically, so all you need to do is enter the password in red below. cisco123 (All lowercase)
22 22 Once at the desktop shown below, open Google Chrome. Confirm that PC1 is able to reach the internet before continuing. Again, if you are unsuccessful, contact your lab proctor.
23 23 Close Google chrome. Now, select the OoB Console Access shortcut link from the desktop of PC1. This will launch a Firefox browser. Select your Pod Number from the drop down list. The pod number should have been assigned to you by your proctor.
24 24 Select the Content Package labeled: ASA 8.x to 9.x Migration from the drop-down menu. Click on the button labeled Access Console Map This topology diagram has clickable pictures which open up a telnet session to the device in question. The links are for the Core Switch, ASA 5520, and ASA 5525-X. We will verify the existing configurations and connectivity between devices.
25 25 Click the graphic of the Core Switch. This link connects through a terminal server to the console port of the switch. Press the Enter key on the keyboard to show the login prompt and login with the credentials listed in red: Username: Password: admin cisco123
26 26 Once you have verified that you can access and login to the Core Switch close the terminal window and end the session. Press OK to exit the telnet session Click the ASA 5520 picture in the OoB Console Access Page
27 27 Press the Enter key on the keyboard to show the ASA# prompt. The session should already be logged in, but if not type enable and please authenticate with the credentials listed in red: Username: Password: admin cisco123
28 28 Test connectivity to the Core Switch by pinging the inside interface route ping Try to ping the outside route ping Issue the show version command to verify that the current running version is 8.2(x). The show version command should show 8.2(5). show version Also take note of and/or write down the hardware MAC addresses of the interfaces used by the ASA. These will be used later on in the lab when the migration occurs to allow for communications without waiting for the ARP entries to expire.
29 29 Close the putty telnet window to the ASA 5520 and click the OK button confirm the close of the session. Finally, click on the ASA 5525-X pictured on the OoB Console Access Page
30 30 The ASA 5525-X should be running at factory default configuration and have no user password or enable password. If you are at the ciscoasa> with a > rather than # : Type enable and Press the Enter key at the password prompt. enable Issue the show version command to verify that the current running version is 9.2(2)4 show version You have reached the end of Section 2.2. You have successfully connected to all Jump boxes and the console connections to the Core Switch, Current ASA 5520, and the new ASA 5525-X. If you had any problems connecting please speak with the lab proctor and review the steps in the lab guide. Continue on to Exercise 3 Backup old ASA and Cisco s Firewall Migration Tool
31 31 Exercise 3: Backup ASA 5520 and Cisco s Firewall Migration Tool In this exercise, you will use the Firewall Migration Tool ( provided by Cisco to Migrate from the ASA 5520 running software version 8.2(x) to a usable configuration for the ASA 5525-X Next-Generation Firewall running software version 9.2(2)4. You will first backup the ASA using ASDM. You may also copy paste from console to textpad or tftp/ftp to obtain the configuration from the appliance. Due to ease of use and consistency, please follow the instructions and use ASDM for backup. After you obtain the backup configuration, you will modify a couple of lines for compatibility with the tool. (The tool requires the use of your Cisco.com Login Credentials to obtain access to the tool. You may first login to cisco.com and then navigate to the tool page as listed above.) Once the form is filled, configuration file is uploaded and the request is submitted; the process usual takes minutes to complete. Key differences between ASA s software versions of 8.2 and 8.3 changed the way NAT and ACL are configured. Due to this change, many upgraded configurations need to be manually reviewed to allow full functionality. Some of these issues will be discussed in this exercise. Documents helpful for the migration are provided below: ASA Upgrade Path Guide to reach ASA 9.2 and ASDM ASA 5500 Pre-8.3 to later Migration Resource Guide: ASA New Features Document by Version:
32 32 Section 3.1 Backup of ASA 5520 There are many ways to backup an ASA device configuration. In this lab, we will be using ASDM to retrieve the backup configuration. In this section, you will connect to the ASA 5520 that is currently passing traffic and pull its configuration. Still on PC1, Find the ASDM icon on the desktop. Launch ASDM by double-clicking on the icon.
33 33 Ensure that the Device IP Address/Name field is populated with the IP address listed in the logical configuration topology diagram near the beginning of this lab guide. For reference that IP address should be: (Notice that this IP address will no longer represent this device once migration is completed). Login with the following credentials presented in red: Username: Password: admin cisco123 Press the button OK to login You will be presented with a Java Security Warning regarding the certificate used for the connection. Press the Continue button.
34 34 Open the Tools drop-down menu. Select the Backup Configurations option from the drop-down menu.
35 35 Click the Browse Local button. Navigate to the Desktop by pressing the Desktop button on the sidebar of the selection window.
36 36 Enter the File Name: ASA5520_Backup_yyyymmdd.zip (Replace yyyy with year, mm for month, and dd for day. For example January 1, 2014 would be: ASA5520_Backup_ zip. ASA5520_Backup_yyyymmdd.zip (yyyy = year; mm = month; dd = day) Click Select File to submit. Click Backup to begin the backup process
37 37 Press Cancel to skip the step of encrypting identity certificates. (Not recommended for a production system). The backup process will now begin. Allow the backup process to complete. Review that no errors have occurred and that the progress has reached 100%.
38 38 Press the Close: button to close the window. Review the Backup Statistics Report and dismiss the window by pressing OK
39 39 Reveal the PC1 desktop by pressing desktop icon in the bottom right corner of the screen. Notice that the newly created file has appeared on the desktop. Double-click the compressed folder to show the contents of the zip file.
40 40 Navigate into the directories ASA5520_Backup_... and locate startup-config.cfg Right-click startup-config.cfg and select the option Copy. Right-click on the blue background of the desktop and select the option Paste. You have successfully completed Section 3.1 and obtained a backup of the startup configuration from the ASA Please verify that the startup-config.cfg file is located on the desktop before moving on to the next section.
41 41 Section 3.2 Modify startup-config.cfg for FWM (Firewall Migration) Tool In this section, you will change a few lines of the startup-config.cfg file in order to make it compatible with the fwm.cisco.com migration utility. This utility will throw errors if the boot system command exists in the configuration. A Still on PC1, right click the startup-config.cfg file icon. Mouse over the option Open with >. Open the file with WordPad by selecting WordPad from the option menu. If opened with Notepad, the line returns will not be present and editing will be more difficult.
42 42 The resulting opened WordPad document is shown below. Press the button labeled Find which is located on the Home ribbon. Type in boot system into the Find what: entry field. boot system
43 43 Click the button Find Next to search for the entered string. Delete the line containing the boot system configuration. The boot system command specifies an image located on the flash storage from which to boot at system startup. Due to the migration system s method of conversion, this command will cause the system to throw an error and fail. Click the Save button to save the edited configuration file. You may now close out of the WordPad text editor. Press the X button in the upper right corner of the screen.
44 44 On PC1 s Desktop, Right-Click the startup-config.cfg file icon. Move the mouse over the Send to > option from the menu.
45 45 Click the menu-item Compressed (zipped) folder to create a new zip folder on the desktop called startup-config.zip The resulting zip folder is displayed below. You have successfully complete Section 3.2 and prepared the startup-config.cfg document for use with Cisco s Firewall Migration Utility. Please Proceed onto the next section, Section 3.3.
46 46 Section 3.3 Create New Conversion Request In this section, you will submit the startup-config.cfg file for conversion utilizing the Firewall Migration Tool. The conversion takes about minutes. They will send you an to your CCO when the process is completed. NOTE: You will need to use your CCO login information. We do not collect or store personal information such as login credentials. After the lab is completed we revert the virtual machines back to their previous states. Double-click the desktop shortcut Cisco Firewall Migration Tool which opens a browser to The resulting page is shown below:
47 47 Log in to the webpage by using your CCO User ID and password. Click Log In to submit the credentials The Firewall Migration Services Platform Tool should load as shown below.
48 48 During the course of the conversion process, the site may force log off the current user account. This timeout appears to be around five minutes. If logoff happens, enter into the URL bar. Navigating backwards and forwards through the browser recent histories after a logoff simply logs the user off again. The steps are outlined in detail below. If you see the present the logout pages depicted below, follow these steps to log back into
49 49 Type into the navigation bar of the current logged off tab. Hit the Enter key to proceed back to the initial login screen using CCO credentials. Proceed to follow the login steps again to resume your work. WARNING: When logout occurs, current form data is lost. However, submitted requests continue to be processed.
50 50 Navigate to the My Conversions drop-down by click the arrow as depicted below. Click on the item Create New Conversion to start a new conversion process. The Create New Conversion form should load.
51 51 In the Description field input a description of the migration. ASA89 Migration PodX yyyymmdd (where X is the pod number) Under Source Platform for Vendor select Cisco from the drop-down menu. Under Source Platform for Product select ASA 5520 from the drop-down menu.
52 52 Under Source Platform for Software select ASA 8.2(x) from the drop-down menu. Once selected, the Target Platform > Vendor should populate as Cisco Under Target Platform for Product select ASA 5525-X from the drop-down menu.
53 53 Under Target Platform for Software select ASA 9.2(1) from the drop-down menu. Click the Browse button next to Source Configuration entry box to bring up a selection window. We use this to select the startup-config.zip created in the Section 3.2.
54 54 Once the File Upload selection window opens up, select the startup-config.zip located in the desktop folder. Click the Open button to assign the file to be uploaded for the conversion.
55 55 The Create New Conversion Form should look very similar to the one depicted below. Please check that all of the fields are inputted correctly. Conversion Description: ASA89 Migration Lab PodX yyyymmdd Source Platform Vendor: "Cisco" Product: ASA 5520 Software: ASA 8.2(x) Target Platform Vendor: "Cisco" Product: ASA 5525-X Software: ASA 9.2(1) Source Configuration: startup-config.cfg After you have verified your form, click the OK button to start the Conversion task.
56 56 A message will appear notifying you if the conversion request was created successfully processed. Continue to monitor your associated with Cisco.com account for an from fwm@cisco.com regarding a completed conversion. This section is completed. The conversion process generally takes minutes to complete. Please proceed to the next Exercise where the network is prepared for the addition of the new ASA 5525-X.
57 57 Exercise 4: Prepare Network for ASA 5525-X In this exercise, you will prepare the network for the addition of the ASA 5525-X. This will include configuring the Core Switch ports into the correct access mode and vlan, transferring and verifying the appropriate files for the ASA 5525-X deployment, and reviewing the current ASA 5520 configuration. Section 4.1 Prepare Network for ASA 5525-X This section will cover the configuration of the Core Switch s interfaces that are connected to the ASA 5525-X. If not already on User PC1, please return to User PC1 and return to the desktop. Double-click the OoB Console Access shortcut on the desktop.
58 58 This will launch a Firefox browser. Select your Pod Number from the drop down list. The pod number should have been assigned to you by your proctor. Select the Content Package labeled: ASA 8.x to 9.x Migration from the drop-down menu.
59 59 Click on the button labeled Access Console Map This topology diagram has clickable pictures which open up a telnet session to the device in question. Click the graphic of the Core Switch. This link connects through a terminal server to the console port of the switch. Press the Enter key on the keyboard to show the login prompt and login with the credentials listed in red: Username: Password: admin cisco123
60 60 Press the Enter key on the keyboard to show the login prompt and login with the credentials listed in red: Once logged into the Core Switch view the configuration for the interfaces that the ASA 5525-X is plugged into. The ASA 5525-X is physically connected to interfaces GigabitEthernet 1/0/6 and GigabitEthernet 1/0/7. As confirmed with the Physical Topology Diagram. show run interface GigabitEthernet 1/0/6 Now for G1/0/7: show run interface GigabitEthernet 1/0/7
61 61 Reference the Logical Topology diagram, also shown on the OoB webpage, and see that the interfaces should have access to vlan 50. Enter Configuration Mode on the Core-SW by entering the command below: configure terminal Configure the Gigabit Ethernet interface g1/0/6 connecting to the ASA 5525-X g0/1 inside interface to access vlan 50. interface gig1/0/6 description To ASA 5525-X g0/1 inside switchport mode access switchport access vlan 50 switchport nonegotiate spanning-tree portfast spanning-tree bpduguard enable no shutdown
62 62 Configure the Gigabit Ethernet interface g1/0/7 connecting to the ASA 5525-X mgmt 0/0 management interface to access vlan 50 as well. interface gig1/0/7 description To ASA 5525-X mgmt 0/0 switchport mode access switchport access vlan 50 switchport nonegotiate spanning-tree portfast spanning-tree bpduguard enable no shutdown end
63 63 Verify the interface configurations with the following commands: show run int g1/0/6 show run int g1/0/7 show spanning-tree vlan 50 Now that the Core Switch is configured to allow the ASA 5525-X to access the network on vlan 50, move on to the next section to put a base configuration on the ASA 5525-X.
64 64 Section 4.2 Prepare ASA 5525-X This section will cover preparing the new ASA 5525-X with an initial configuration in order to transfer files and the converted configuration prior to migration. Click on the ASA 5525-X pictured on the OoB Console Access Page to open up a telnet session to the console port of the ASA 5525-X. If presented with the prompt ciscoasa> with > rather than # : Type enable and Press the Enter key at the password prompt. (No password set) enable
65 65 Issue the dir command to see what files are on the internal flash storage of the ASA 5525-X dir We will need to transfer files to the new ASA including: anyconnect packages, backed up cryptographic keys, asdm (may or may not be on flash), the converted configuration file, etc In order to transfer the files, the ASA must have a connection to the network and be reachable from one of the jump boxes. Enter configuration mode. Upon entering configuration mode you may be prompted to enable anonymous error reporting. If prompted please respond No. conf t As this temporary configuration of the ASA 5525-X is only temporary and in place to transfer files and verify connectivity that have been previously setup, the logical configuration will use spare addresses. This configuration will be overwritten by the converted configuration from
66 66 Configure the mgmt0/0 interface to access the network with an unused address in the /24 network. interface management 0/0 ip address nameif mgmt. security-level 100 no shut end Now that the management interface is configured, attempt to ping ping Now try to ping a host in a different network like (DC) Notice that this ping did not work because there is no default route setup.
67 67 Enter configuration mode again and configure a route for the mgmt interface to connect to network /8 through the gateway conf t route mgmt Verify that the route is created by issuing the command: show route Test the connectivity by once again pinging the host Now that connectivity to the network is setup, the transferring of files can begin.
68 68 Reveal the PC1 desktop by pressing desktop icon in the bottom right corner of the screen. Double-click the shortcut to 3CDaemon located in the upper-right corner of the desktop. The resulting program window display is shown below.
69 69 Click the sidebar section button labeled FTP Server. Even though the FTP is currently running on PC1, it needs to be configured to point to the correct directory and allow anonymous access to read the files. Click the Configure FTP Server button on the sidebar. Click on the username anonymous in the left bar of the 3CDaemon Configuration window.
70 70 Click the button next to the User Directory setting to browse for the folder with the files to transfer. Select the folder ASA89 Software as it contains the anyconnect.pkg files needed for our VPN users as well as the ASDM version used in this lab. Press the OK button to confirm the directory selection
71 71 Then press the OK button to apply and configure the FTP server the 3CDaemon folder to the configured settings. A Pop-up window will appear asking if you want to save the changes made to the configuration. Press the Yes button to save the changes. Press the OK button to dismiss the Profile saved confirmation message. Now it is time to transfer files to the ASA 5525-X ensure that the 3CDaemon server is running. Take note of the listening IP address in the /24 network.
72 72 Return to the putty session of the ASA 5525-X console. If disconnected from the session, open up the OoB Console Access Page for you pod and select the ASA 5525-X again. From the console window enter the commands to transfer the asdm image from the ftp working directory to the root folder of the internal flash:/ of the ASA 5525-X. (if the ASA already has the ASDM image you may delete and re-transmit the file. It is likely that a newer update has come out since the time of writing of this lab guide. In your own deployment you should always use Cisco s best practice recommendations.) copy ftp: flash: Address of host: Source filename: asdm-731.bin Destination filename: asdm-731.bin [If a warning for over write appears press enter to confirm]
73 73 The file transfer should begin and many exclamation points will display as transferred. Now copy the files for anyconnect by issuing the commands listed below in red: copy ftp:// /anyconnect-linux k9.pkg flash: copy ftp:// /anyconnect-win k9.pkg flash: After you input each of the commands above, confirm the information in the prompts to start the transfers.
74 74 Now that ASDM and the anyconnect images are transferred to the ASA 5525-X configure the ASA to use the asdm-731.bin as the ASDM image. conf t asdm image disk0:/asdm-731.bin With the ASDM image set, ensure that the http server is enabled on the ASA and that the management network has access to the http server. This allows connection to ASDM from the PC1 desktop. http server enable http mgmt By completing this section, the inside network has been primarily made ready for migration and the ASA is accessible. It is now possible to transfer the configuration over to the ASA from the PC1. In the next section we will review the current behavior of the current ASA 5520 and expected behavior of the new ASA 5525-X.
75 75 Exercise 5: Migrate to ASA 5525-X In this exercise, the engineer tasked with the migration will obtain the converted configuration from Cisco s Firewall Migration Services utility, check for any errors or changes that need to be made, apply the configuration to the new ASA 5525-X, and verify the expected behavior. The goal of the exercise is to complete the migration from the ASA 5520 to the newer ASA 5525-X. After this exercise the ASA 5520 interfaces will be shutdown. Section 5.1 Obtain Converted Configuration from This section will cover returning to webpage at and retrieving the converted startup-config.cfg file. If you have not yet received and confirmation you may use the previously converted configuration archive on the desktop of User PC1. If not already on User PC1, please return to PC1 at this time. Back on PC1 navigate the web browser to and select the Firewall Migration Option. The current session is most likely to have expired and the user must re-authenticate. Please follow the previous instructions to log in to the website.
76 76 Click the My Conversions drop down menu on the side bar. Now click the link for My Completed Conversions to open up a list of the completed system conversion tasks.
77 77 Click on the Conversion ID corresponding with the correct conversion task. Now click on the download link on the unfolded information Press OK on the Open File prompt to save the compressed file to the Downloads folder.
78 78 Section 5.2 Review Converted Configuration and Upgrade Error Log This section will cover the review and editing of the converted configuration prior to application on the new ASA 5525-X. Press the Open Containing Folder Icon next to the downloaded file notification in Firefox. The resulting Windows Explorer.exe window is shown below.
79 79 Right click the zipped file folder starting with CSCO_ASA_5520 and select the option to Extract All Press the button labeled Extract to extract the files into a folder located within the Download folder. The Extraction will open the extracted files when completed by default. The result is shown below:
80 80 You can take a look at the README.pdf file. It contains useful reference material regarding the utility provided at It is imperative to read through the logs attached with the converted configuration. The conversion logs point out a few issues that need to be addressed. Open the logs folder. Right-click the upgrade_startup_errors.log file.
81 81 Mouse over the option Open with and click Choose default program to pull up a list of programs. Select the program WordPad. Notepad.exe does not display the line break characters correctly. In a result all of the information appears on one line. WordPad displays the line break characters correctly and will allow easier reading of the upgrade log. Follow up and open the document by click the OK button.
82 82 Read through the upgrade error log paying special attention to NAT and ACL errors. One major change during the conversion is the Real IP Migration where access lists pointing to translated addresses now will point to the Real IP address.
83 83 Errors shown in this log (line numbers relative to lines of startup-config.cfg from ASA 5520 but not exact): Line # Command Causing Error Explanation Line 3: ASA Version 8.2(5) System does not have the same version and this line will be removed and saved as the new version number when saved. (tgt_startupconfig.cfg has ASA Version 9.2(1) version number) Line 117: asdm image disk0: The system that the FWM utility uses to convert the configurations does not contain the same image name as the image used in the ASA 5520 system of our network. Warning show that it has been translated by Real IP Migration, so these access lists need to be checked and corrected manually. Line 145: access-group outside_access_in in interface outside Line 203: crypto ca trustpoint Example_TP keypair Example.com Line 249: quit (which really references: crypto ca certificate chain Example_TP certificate 9d6A2954. quit Line 279: svc image disk0:/anyconnectwin k9.pkg NT Line 281: svc image disk0:/anyconnectlinux k9.pkg See Line 279. Linux Line 283: svc enable svc cannot enable without at least one valid anyconnect image Line 305: username jdoe attributes vpn-group-policy anyvpn_gp The key pair does not exist because it must be migrated separate from the normal process of configuration backup. Again, they key pair must be installed for this to import correctly. Other mitigation factors are to regenerate keys or import the old key pair manually. Same as Line 117. The FWM utility does not contain or use same images as those used on our ASA anyconnect*.pkg assignment. When you look at the tgt_startup-config.cfg file given by it appears that the username jdoe declaration appears at the bottom of the configuration file which happens to be after the username jdoe attributes command is given. This will need to be manually fixed. NAT migration logs: The upgrade_startup_error.log document warns: The following nat command didn t have a matching global rule on interface inside and was not migrated: nat (inside) This specific error occurs because the asa allowed traffic to redirect out of the same interface that it came in on. Due to this, the case where traffic destined towards the inside and also outbound of the inside interface has no NAT configuration. However, the other global rules associated with this NAT definition have been translated as we will soon see.
84 84 Section 5.3 Edit Converted Configuration and 8.3+ NAT ACL Changes This section will go through the process of fixing the errors and warnings found in this error log and basic configuration changes of NAT and ACLs between 8.2 and This section does not have a comprehensive guide to the changes but references many basic examples. The Cisco guide to read on the changes that occurred to NAT and ACL during the 8.3 ASA version upgrade is: A basic diff of the two configurations are displayed in an appendix linked here. Please refer to the diff of the two when comparing the configurations. It may be helpful to navigate to and download the zip file to your personal computer and examine the files from there. However, the target configuration file must be deployed from PC1 and there is no outbound ftp, ssh, telnet, etc setup between PC1 and the open internet. One option may be to use a paste bin service if you wish to edit the configuration on your personal computer and then coping over to the lab environment. Notice though that this is not supported in this lab and is only to be used at your own discretion. Comparing the two results we can see that the new configuration has more Gigabit Ethernet interfaces, however the migration utility added interface GigabitEthernet1/0- interface GigabitEthernet1/5. These are interfaces that our device does not possess. Delete the Interfaces interface GigabitEthernet1/0 - interface GigabitEthernet1/5 from the target configuration and save it to a new file ASA5525_startup-config.cfg located in the FTP root of C:\Users\John Doe\Desktop\ASA89 Software\.
85 85 Delete Interfaces interface GigabitEthernet1/0- interface GigabitEthernet1/5 If we copy this configuration right now, the IP address will conflict with those currently on the ASA We will take over the IP addresses of the original ASA as we replace it with the ASA 5525-X, but for now we need to make sure that the interfaces do not turn on when the configuration is copied into the running configuration.
86 86 Ensure that all of the interfaces are shutdown in the new configuration. Although the interface IP s will not conflict with the old ASA 5520 until the interfaces turn on, the ARP cache on the routers/l3 switches will make the connections unpredictable for up to 4 hours by default. That is an unacceptable amount of downtime. Because many customers do not control their upstream (ISP) routers the problem needs to be mitigated without access to the upstream router. One solution is to use a different IP address until the old router s ARP cache expires. Another solution is to send a gratuitous ARP from the newly connected devices as to update the ARP cache. Unfortunately, the ASA does not easily send gratuitous ARPs from its outside interface. The most consistent solution is to assign the MAC addresses used by the previous ASA 5520 to the corresponding interfaces on the new ASA 5525-X. Once both device s interfaces are up, there will be inconsistent connections. Therefore, after the mac addresses are assigned to the ASA 5525-X and when it is ready to go live, we will first shutdown the interfaces of the ASA This will cause a temporary break in service. NOTE: If you have control of your upstream routers then you can issue either a clear ARP command or delete the entry manually. Recall the mac addresses learned from the ASA 5520 when first verifying or reconnect to the console and input the commands to view the mac addresses. Click the Icon for the ASA 5520 on the OoB web page.
87 87 Enter the command: show interface inside inc MAC show interface outside inc MAC show interface DMZ inc MAC Insert the commands into the configuration file to set the mac addresses to the appropriate values underneath the interface configurations for the appropriate interfaces. Make sure to match the values to the correct interfaces. mac-address XXXX.XXXX.XXXX mac-address XXXX.XXXX.XXXX mac-address XXXX.XXXX.XXXX
88 88 Connected to the ASA 5520 console: Export the certificate key pair. conf t crypto ca export Example_TP pkcs12 cisco123 (password for to encrypt key pair) Select the key pair beginning with -----BEGIN PKCS
89 89 Copy and Paste it to a notepad document. Keep this notepad open until we are ready to migrate the full configuration. This will be the final step before copying the configuration into the running configuration. Now we will mitigate the anyconnect issues encountered during the migration. Before we apply the converted configuration we need to enable the anyconnect images. Enter the following commands into the configuration file under the section webvpn below no anyconnect-essentials. anyconnect image disk0:/anyconnect-win k9.pkg 1 regex "Windows NT" anyconnect image disk0:/anyconnect-linux k9.pkg 2 regex "Linux" Now that we fixed a couple issues, upload the policy to the ASA 5525-X using the ftp services. To do this, we need to copy this file into the anonymous FTP root we configured earlier.
90 90 Press the menu button to open up the context menu where we can Save as the file. Click the Save as button to open up the save window.
91 91 Navigate to the Desktop folder by clicking Desktop from the Favorites item list. Double-click the ASA89 Software folder (which happens to be the previously configured FTP document root).
92 92 In the File name: text entry area, enter the new configuration file name: ASA5525_startup-config.cfg Then click Save Now that the configuration file is saved in the FTP root directory, open up another console session to the ASA 5525-X using the OoB web page as discussed earlier in this lab. Enter the command to copy the file from User PC1 copy ftp: flash: Address of host: Source filename: ASA5525_startup-config.cfg Destination filename: ASA5525_startup-config.cfg [If a warning for over write appears press enter to confirm]
93 93 The result is depicted below. During this section, you did a quick look and edit of the configuration prior to uploading the converted configuration file to the new ASA 5525-X. Please proceed to the next section where the new configuration is applied.
94 94 Section 5.4 Apply New Configuration to the ASA 5525-X This section will cover applying the new configuration file to the new ASA 5525-X. Then, we will examine the policies shown in ASDM as well as a few packet-tracer commands to verify the correctness of the behavior. Still in the console session to the ASA 5525-X on User PC1, erase the currently running configuration. clear configure all On the console connection to the ASA 5525-X import the key pair by issuing the command: conf t crypto ca trustpoint Example_TP enrollment self crypto ca import Example_TP pkcs12 cisco123 (password for to encrypt key pair) Paste the copied certificate by right-clicking the terminal window.
95 95 Type the word quit to stop the ASA from reading more input and complete the import of the PKCS12 key pair. quit Now that the basic issues are resolved on the system copy the transferred configuration file to the running configuration. copy flash:/asa5525_startup-config.cfg run Confirm the filename prompts
96 96 Section 5.5 Transfer Traffic Flow from ASA 5520 to ASA 5525-X This section will cover transferring the traffics flow from the older ASA 5520 to the new ASA 5525-X. Open the terminal to the ASA 5520 (you may access this through the OoB web page). Issue the commands: (WARNING this will disable access to the internet) conf t interface g0/0 shutdown interface g0/1 shutdown interface g0/2 shutdown
97 97 Return to the ASA 5525-X Console and type the following commands: conf t interface g0/0 no shutdown interface g0/1 no shutdown interface g0/2 no shutdown From the new ASA 5525-X attempt to ping the default route outside which is ping Now ping the Inside route ping
98 98 Now ping the DMZ Web1 address ping Now, set the boot system variable and copy the running config to the startup configuration. boot system disk0:/asa922-4-smp-k8.bin copy run start [enter] You have successfully applied the converted configuration and migrated the ASA 5525-X into the network.
99 99 Section 5.6 Verify Behavior This section will cover verifying the basic network behavior. On User PC1 close ASDM if still connected and reopen ASDM from the desktop icon. Find the ASDM icon on the desktop. Launch ASDM by double-clicking on the icon.
100 100 Ensure that the Device IP Address/Name field is populated with the IP address listed in the logical configuration topology diagram near the beginning of this lab guide. For reference that IP address should be: (Notice that this IP address now represents the new ASA 5525-X). Login with the following credentials presented in red: Username: Password: admin cisco123 Press the button OK to login You will be presented with a Java Security Warning regarding the certificate used for the connection. Press the Continue button.
101 101 Notice that the Device Information now reports that the ASA Version is 9.2(2)4 and Type is ASA Click on the Configuration tab on the top bar. Now click on the side bar button for Firewall.
102 102 This should bring you to the page with Access Rules. Notice that the outside interface ACLs from the migration on the previous ASA 5520 now seem to be ungrouped and somewhat incorrect. There is a mixture of access allowed to the real IP address ( ) and the translated address ( ). Edit the ACL for the outside interface allowing traffic for the protocols tcp-udp/http, tcp/https, and tcp/ssh. This will match the configuration of the previous configuration. Notice however that in this access list we are allowing tcp/ssh for the outside to dmz nat access list. This is different than the previous 8.2 configuration. The configuration was previously: object-group service DM_INLINE_SERVICE_1 service-object tcp-udp eq www service-object tcp eq https service-object tcp eq access-list dmz_nat_static extended permit tcp host eq ssh any access-list outside_access_in extended permit object-group DM_INLINE_SERVICE_1 any host static (dmz,outside) tcp access-list dmz_nat_static access-group outside_access_in in interface outside Right click the rule 1 for the outside interface and click the Edit.
103 103 Click the box with the ellipsis in it ( ) to open up the service selection menu. Type in the filer bar http and click the filter button.
104 104 Double click the tcp-udp/http predefined object to add it to the Selected Service. Do the same for tcp/ssh and tcp/https. Remove the original tcp/http as it is redundant now. The Selected Services should now look like this: Press the OK button to submit the change of selected services. Press the OK button to submit the change on the Access Rule.
105 105 Now delete the other redundant access rules applied to the same outside-access-in access list. Select outside rule 2 and click the delete button. Press delete two more times to delete the other rules in the access list. The resulting window should look similar to what is shown below:
106 106 Click the Apply Button to apply the settings on the ASA. The Preview CLI Commands window will appear. Click the Send button to send the changes to the ASA 5525-X.
107 107 Click the button labeled NAT Rules in the Firewall sidebar menu. The new NAT Rules seem to be much less clean than the original configuration, but that is due to the migration. The pre8.3 version of NAT translated the addresses after applying the access rules, now translation is done prior to those rules. The best way to have a clean configuration is to rebuild from scratch. However, the Cisco FWM migration utility focuses on making the migrated system function as similar as possible to the original system. Continue with twerking the network and making the rules cleaner, but that is beyond the scope of this migration lab. End of Exercise 5. You have successfully completed the Migration from ASA Version 8.x to ASA Version 9.x. Now we will continue exploring the benefits of Cisco s 5500-X Series Next Generation Firewalls by exploring the FirePOWER Services module.
108 108 Exercise 6: FirePOWER and FireSIGHT Deployment In this exercise, you will Section 6.1 Install FirePOWER Services on ASA 5525-X This section will cover the requirements and practice of installing the sfr module or FirePOWER Services module onto the ASA 5525-X. The ASA5525-X, as well as other NGFW with software modules, requires the SSD expansion drive in order to run the FirePOWER Services module. The SSD drive is the same as that which is required for the IPS module as well as the CX module. If not already, login to User PC1 and open a console session with the ASA 5525-X.
109 109 In order to install the FirePOWER Services module, the existing modules must be shut down and uninstalled. They should already be, but issue the commands anyway to ensure a clean installation. sw-module module sfr shutdown After the shutdown is issued, wait a few minutes until the module is responsive again. After a few minutes issue the command to uninstall the currently installed module. sw-module module sfr uninstall As mentioned before, the uninstall operation should report that it does not have a software image installed. Now that there is no image installed on the software module. Prepare the recovery image by transferring it to the system. Assuming the 3CDaemon is still running the ftp server, type the following commands to transfer the recovery image for the FirePOWER module: copy ftp: flash: Address of host: Source filename: 5525-X/asasfr-5500x-boot img Destination filename: asasfr-5500x-boot img [If a warning for over write appears press enter to confirm]
110 110 Now with the recovery image on the internal flash. Assign the recovery image to the software module and recover the system. And then boot the recovery image sw-module module sfr recover configure image disk0:/asasfr-5500x-boot img Now that the correct image is configured as the recovery image for the sfr moduel, issue the boot command to start the recovery process. sw-module module sfr recover boot Before the sfr module can have access to the network, the management interface must be brought up. It does not need any special configuration. It needs to be in the up state and the switchport should be configured to access the network. The switchport was configured in a previous section. This management interface connects to the core switch on interface g1/0/7. Configure the ASA 5525-X management 0/0 interface with the following commands: conf t (if not already in config mode) int man0/0 no shut
111 111 Now that the image is set to recover, enter into the console session with the software module by issuing the command: (The system may take a couple minutes to respond) session sfr console *NOTE: To break out of the sfr console within the console session to the ASA 5525-X, the user must use the on-screen keyboard and press the buttons CTRL + SHIFT + 6 and then X. You can also use putty s break. Login with the credentials: Username: Password: admin Admin123 Once into the sfr console run the setup to get initial connectivity. setup During the setup answer the question with these responses: hostname asasfr configure ipv4 Y DHCP N ipv4 address netmask gateway configure ipv6 N DNS address secondary DNS? N local domain name N search domain N configure NTP N Apply changes Y [Enter]
112 112 Once the setup is completed you are ready to install the sfr system software onto the software module. This image cannot be located on the local flash. We will once again utilize 3CDaemon and its ftp server. system install ftp:// /5525-x/asasfr-sys pkg After the download and unpacking finishes, the system will prompt for a acceptance of the upgrade and then reload. Press enter to reboot the sfr module and finish the FirePOWER Services module installation. Y Reboot is required to complete the upgrade. Press 'Enter' to reboot the system. [Enter] You will be disconnected from the session sfr console.
113 113 Section 6.2 Configure Core Switch Interface for FireSIGHT Management Center This section will cover the configuration of the Core Switch s interface that is connected to FireSIGHT Management Center. If not already on User PC1, please return to User PC1 and return to the desktop. Double-click the OoB Console Access shortcut on the desktop.
114 114 This will launch a Firefox browser. Select your Pod Number from the drop down list. The pod number should have been assigned to you by your proctor. Select the Content Package labeled: ASA 8.x to 9.x Migration from the drop-down menu.
115 115 Click on the button labeled Access Console Map This topology diagram has clickable pictures which open up a telnet session to the device in question. Click the graphic of the Core Switch. This link connects through a terminal server to the console port of the switch. Press the Enter key on the keyboard to show the login prompt and login with the credentials listed in red: Username: Password: admin cisco123
116 116 Press the Enter key on the keyboard to show the login prompt and login with the credentials listed in red: Once logged into the Core Switch view the configuration for the interfaces that the FireSIGHT MC is plugged into. As confirmed with the Physical Topology Diagram, the FireSIGHT MC is plugged into Gig 1/0/4. show run interface GigabitEthernet 1/0/4 Reference the Logical Topology diagram, also shown on the OoB webpage, and see that the interfaces for FireSIGHT MC should have access to vlan 20.
117 117 Enter Configuration Mode on the Core-SW by entering the command below: configure terminal Configure the Gigabit Ethernet interface g1/0/4 connecting to the ASA 5525-X g0/1 inside interface to access vlan 50. interface Gig1/0/4 description To FireSIGHT Management Center switchport mode access switchport access vlan 20 switchport nonegotiate spanning-tree portfast spanning-tree bpduguard enable no shutdown You have successfully configured the core switch for the addition for FireSIGHT Management Center.
118 118 Section 6.3 Base Configuration of FireSIGHT Management Center This section will cover the base configuration of FireSIGHT Management Center. The FireSIGHT MC virtual appliance is used in this lab and is required for management of the FirePOWER Service Module. Cisco may soon come out with an on-box management solution, but for now this system is the way that it works. To begin, open up the session with FireSIGHT that was established near the beginning of the lab. The label for the vnc connection is Defense Center because that was its name until very recently as of writing. Login to the system with the credentials: Username: Password: admin Sourcefire
119 119 Once logged in, assume the root user by issueing the command: sudo i Then enter the same password as before: Sourcefire Configure the network by issuing the command: configure-network y y n You may now close the window to the console of Defense Center also called FireSIGHT MC. Return to PC1 for the rest of configuration.
120 120 Back on PC1 open a web browser and navigate to the secure site with the IP setup in the last step of Click I Understand the Risks and then Add Exception (Chrome has a similar system)
121 121 Then click the Confirm Security Exception to save the certificate for your current browsing session. Now at the login page, login to the system with the credentials: Username: Password: admin Sourcefire On the system Install page New Password: Confirm: cisco123 cisco123 Protocol: IPv4 IPv4 Management IP: Netmask: IPv4 Default Network Gateway: Hostname: Sourcefire3D Domain: example.com Set My Clock: Via NTP from: (Skip licesnes and devices for now) Check the EULA and click Apply
122 122 This is the screen form that needs to be filled out.
123 123 You may be redirected after the settings apply. After a minute or so, the Dashboard for the FireSIGHT system loads. As is appearant, there is no data because nothing is feeding the FireSIGHT MC any data. You have successfully added a base configuration to the FireSIGHT MC.
124 124 Section 6.4 Licensing This section will cover Licensing the FireSIGHT MC. There a couple of different licenses: Protection/Control URL Filtering AMP and file analysis There are also licenses for devices or sensors on the network. ASAs with FirePOWER Services are licensed in this way and are managed through the FireSIGHT MC. They have the same license categories. To begin the licensing setup mouse over the System dropdown on the top bar. Click on Licenses to go to the license page. On the License page click the button to Add New License
125 125 The license file are located in the directory of PC1: C:\Users\John Doe\Desktop\ASA89 Software\Licenses\PodX (Where X is your Pod number) Open each file in notepad and copy the content to the License text box as shown below: Click on the Submit License button and then Return to License Page. Repeat for each license key. Note: Ensure that the pasted content does not include the header information but instead starts with: --BEGIN SourceFire Product License:
126 126 Once all 4 licenses given have been applied, the screen should look similar to this: You are now about ready to add the ASA FirePOWER Services as a sensor to the FireSIGHT system. Continue to the next section.
127 127 Section 6.5 Connect ASA with FirePOWER Services to FireSIGHT MC This section will cover connecting the ASA sfr module to the recently base configured FireSIGHT Management Center. Return to PC1 and connect to the ASA 5525-X through the OoB console web page. Issue the command to start a session with sfr module. session sfr console Once the module reboots and the system comes back up, login with the credentials: Username: Password: EULA: admin Sourcefire YES System initialization in progress. Please stand by. You must change the password for 'admin' to continue. Enter new password: cisco123 Confirm new password: cisco123 You must configure the network to continue. You must configure at least one of IPv4 or IPv6. Do you want to configure IPv4? (y/n) [y]: y Do you want to configure IPv6? (y/n) [n]: n Configure IPv4 via DHCP or manually? (dhcp/manual) [manual]: manual Enter an IPv4 address for the management interface [ ]: Enter an IPv4 netmask for the management interface [ ]: Enter the IPv4 default gateway for the management interface []: Enter a fully qualified hostname for this system [Sourcefire3D]:asasfr.example.com Enter a comma-separated list of DNS servers or 'none' []: Enter a comma-separated list of search domains or 'none' [example.net]:example.com If your networking information has changed, you will need to reconnect. For HTTP Proxy configuration, run 'configure network http-proxy' (Wait for the system to reconfigure itself.) Take a break for about 5 minutes while the system reconfigures itself. The process will take some time.
128 128 Return to the FireSIGHT Management Center webpage. Hover over the Policies option on the main top bar. Hover over the Intrusion option from the Policies top bar menu.
129 129 Click on Intrusion Policy within the Intrusion options drop down menu. Notice that there are two initial polices for this FireSIGHT MC: The Initial Inline Policy which will drop offending packets by default, and the Initial Passive Policy which will not drop offending packets.
130 130 Click on the Create Policy button to create a new Intrusion Policy to be used with our deployment. The overlay form window will appear for Create Intrusion Policy. Input the following options for the form: Name*: Description: Drop when Inline: Base Policy: Example Intrusion Policy Example s Intrusion Policy for an inline deployment [checked] Select [Connectivity Over Security] from the dropdown menu Click the button Create and Edit Policy to create the policy and start modifing options.
131 131 The policy creation will only take a brief moment. The resulting create policy is shown below:
132 132 Take note that there are 789 enabled rules, 19 of which will generate events allowing traffic through in an inline deployment and 770 rules currently setup that will block and generate events for offending traffic. We will take a look at some of the rules a bit later in this lab. Press the Commit Changes button to save this intrusion policy. Make a comment about the changes made. This time we can put into the comments: Initial Policy Creation Press the OK button to apply the change.
133 133 Once the Policy changes have been applied, the system will return the user to the Intrusion Policy screen. Notice that there are now three Intrusion Polices listed on the system. Hover over the Policies option on the main top bar. Click on the Access Control option from the Policies top bar menu.
134 134 The Access Control Policy page displays, but there are no Access Control Polices defined. Click on the New Policy button to start creating a new Access Policy. The overlay form window will appear for New Access Control Policy. Enter in the following information: Name: Description: Default Action: Example Access Control Policy Example s Access Control Policy Intrusion Prevention For reference from Page 1-11 of FireSIGHT System User Guide for 5.3.1, the Default Action of an Access Control Policy can: block all traffic from entering your network trust all traffic to enter your network without further inspection allow all traffic to enter your network, and inspect the traffic with a network discovery policy only allow all traffic to enter your network, and inspect the traffic with intrusion and network discovery policies
135 135 The form should look similar to the one shown below: Click Save to save the Access Control Policy:
136 136 Following finishing and saving the add Access Control Policy form, Example Access Control Policy screen will appear. No rules are configured for any of the rule categories, and the Default Action assigned to the Access Control Policy is defined as Intrusion Prevention: Balanced Security and Connectivity. Click the drop down menu for the Default Action section. Select the Example Intrusion Policy in order to use the Intrusion Policy that was previously created.
137 137 Select the small paper icon next to the Default Action selection dropdown to open the settings for logging. Logging must be enabled to generate connection events through the Analysis dashboard. Click the check box to choose to log events at the end of connection. Ensure that the box is checked next to Defense Center as a location to send connection events.
138 138 Finally, press the OK button to close the logging settings. As a special note: it is recommended to only choose one logging setting for connections. If chosen to log at both the beginning and end of connection, the connections will all be logged twice. The only exception is for blocked connections which are only logged at the beginning of the connection. Take a minute to verify all of the settings and look around at the other settings.
139 139 Click the Save and Apply button to save the Access Control Policy and apply it to the system and currently managed devices (there are none defined yet on this system). Click the button Apply All on the pop-up response. Accept the error message because we know that there are no devices currently being managed by the FireSIGHT MC yet.
140 140 Return to the desktop of PC1. Instead of accessing the sfr module through the ASA session sfr console command, attempt to access the device over SSH. Open the putty shortcut on the desktop (or your favorite ssh client). Once putty opens enter the IP address recently assigned to the sfr module through the configuration
141 141 Press the Open button to start the SSH session with the FirePOWER Services module. A PuTTY security alert should pop up prompting to accept the host key and trust the SSH setting. Press the YES button to accept the key and store it on the computer as trusted.
142 142 Login to the system with the credentials setup when we setup the ASA FirePOWER services module. Login with the following credentials: Username: Password: admin cisco123 Upon logging in the system, the system will show the build number and present you with a prompt.
143 143 At this point we are going to setup the connection with the FireSIGHT Management Center by first configuring the sfr module with the FireSIGHT MC address and a shared key. At the admin prompt enter the command. configure manager add cisco123 After about seconds, the system should respond back with the message that the Manger successfully configured. Return to the FireSIGHT Management Center webpage.
144 144 Hover over the Devices top bar item and click on Device Management. Click the button Add to add a device. Select the option Add Device from the drop-down menu.
145 145 An overlay form window will appear for adding a device to the FireSIGHT MC. Fill in the form with the following information Host: Registration Key cisco123 Group None Access Control Policy: Example Access Control Policy After entry the form should look similar to the one depicted below: For licensing options, check all except VPN (which cannot be selected at this time anyway).
146 146 Click Register to register the ASA 5525-X FirePOWER Services module. The system will attempt to add the device. This process will take a minute or so as it attempts to communicate with the device. Eventually the device will be added to the system and will be listed on the Device Management Page.
147 147 Glancing at the device that has been added to the system it shows that no Health policy, System Policy, or Access Control Policy have been assigned to the device. Click on the Device name (currently the IP address of the device) to enter into the management of the specific device. The Interfaces Page of the device will appear. In this page we can define Security Zones for each of the interfaces of the ASA.
148 148 Click the pencil icon adjacent to the dmz interface of the ASA. On the following overlay box, click on the drop down menu for Security Zone:. Select the new option from the drop down menu. Enter the name for the security zone to add. In this case: DMZ
149 149 Press the OK button to create the security zone. Back on the Edit Interface overlay window, click the Save button to save the chagnes. Click the pencil icon adjacent to the inside interface of the ASA. On the following overlay box, click on the drop down menu for Security Zone:. Select the new option from the drop down menu.
150 150 Enter the name for the security zone to add. In this case: inside Press the OK button to create the security zone. Back on the Edit Interface overlay window, click the Save button to save the chagnes. Click the pencil icon adjacent to the outside interface of the ASA.
151 151 On the following overlay box, click on the drop down menu for Security Zone:. Select the new option from the drop down menu. Enter the name for the security zone to add. In this case: outside Press the OK button to create the security zone.
152 152 Back on the Edit Interface overlay window, click the Save button to save the chagnes. Click Apply Changes to save the changes to the ASA5525. Click Apply to confirm applying the changes. A popup message will explain that the tasked was added to the queue. Click OK to dismiss this message.
153 153 FireSIGHT MC has some initial preparation work to do before redirecting traffic. With the ASA w/ FirePOWER device connected to and managed by the FireSIGHT MC, the basic policies need to be applied before any action on network traffic can take place. The System Policy needs to be applied to the system and managed devices. The System Policy specifies the configuration for Authentication Profiles as well as Time Synchronization between the FireSIGHT MC and the ASA sfr module as well as other FireSIGHT MC managed devices. Hover the mouse over the System heading in the top bar. Now mouse over the Local option in the expanded top bar.
154 154 Select System Policy from the Local drop down menu. This will redirect you the System Policy page. Notice that there is a Default system policy and the Initial_System_Policy Click on the green check mark box next to Initial_System_Policy 201- Select the box next to and then hit the button Apply to apply the changes.
155 155 Now mouse over the Health top bar item and select Health Policy Click on the green check box next to the Initial Health Policy to apply the policy to devices. Select the box next to and then hit the button Apply to apply the changes.
156 156 Hover over the Policies option on the main top bar. Click on the Access Control option from the Policies top bar menu. Click on the green check box next to the Example Access Control Policy, that was previously created, to apply the policy to devices.
157 157 Select the box next to and then hit the button Apply to apply the changes. Click the button Apply All on the pop-up response. Press OK to confirm the task queue message.
158 158 On User PC1 close return to ASDM. If not already connected follow the instructions below: Find the ASDM icon on the desktop. Launch ASDM by double-clicking on the icon. Ensure that the Device IP Address/Name field is populated with the IP address listed in the logical configuration topology diagram near the beginning of this lab guide. For reference that IP address should be: (Notice that this IP address now
159 159 represents the new ASA 5525-X). Login with the following credentials presented in red: Username: Password: admin cisco123 Press the button OK to login You will be presented with a Java Security Warning regarding the certificate used for the connection. Press the Continue button.
160 160 One in ASDM, enter the configuration tab of the ASA 5525-X. Navigate to the Firewall menu item on the side bar.
161 161 One in ASDM, enter the configuration tab of the ASA 5525-X. Select the option Service Policy Rules. The following screen is displayed:
162 162 Add a service policy rule by clicking the Add button. This will be a global policy that applies to all interfaces. Click Next to continue to the next page.
163 163 Enter sfr as the new traffic class: Create a new traffic class: sfr Check the box next to Source and Destination IP Address (use ACL) to use a defined ACL. Click Next to continue to the next page.
164 164 In the ACL configuration page, click the radial button to select Match. For source type any. any
165 165 For destination type any. any Click Next to continue to the next page. Click on the ASA FirePOWER Inspection tab.
166 166 Check the box labelled Enable ASA FirePOWER for this traffic flow. One the box is checked, the settings below become configurable. Ensure that the radial check box Permit traffic is selected, and that Enable Monitor Only mode is NOT checked. Click the Finish button to finish the wizard.
167 167 Notice that the policy sfr is now added to the system. Click the Apply button to apply the configuration change. Alternatively you could have used the console connection to the ASA 5525 and input: access-list sfr_redirect line 1 extended permit ip any any class-map sfr match access-list sfr_redirect policy-map global_policy class sfr sfr fail-open Send the commands to the ASA by clicking the Send button. Save the configuration to the startup-config by pressing the Save button and icon.
168 168 Ensure that you can still reach the internet by opening a web browser and navigating to cisco.com or some other website. We are now able to pass traffic through the ASA FirePOWER module. However, the FireSIGHT MC dashboard still shows little to no data collected. This is because the default Network Discovery only has Applications discovery enabled by default. The discovery of hosts and users should be collected as well.
169 169 Hover over the Policies option on the main top bar. Click on Network Discovery on the Policies top bar submenu. As can be seen, the network /0 and ::/0 (so everything ) is applied with Application Discovery. Click the Pencil icon for the network to Edit this Rule.
170 170 The overlay window pops up and shows the current Network Discovery rule. Check both the Hosts and Users checkboxes to select them for discovery. Click Save to save the Rule.
171 171 Click the Apply button to apply this configuration to the out of date device. Confrim the Network Discovery Policy application to all active devices managed by FireSIGHT MC. Click the Yes button. Click OK to dismiss the status message.
172 172 Return to the Overview Screen and see the results of your work. Thank you for taking this lab. If you have extra time and want to explore the rest of the features the useragent is downloaded and located in the downloads folder of PC1. You Have Completed the Lab!
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM
 Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM
 Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3
 Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3 From Cisco s website, here are the minimum requirements for CCP 2.7 and CCP 2.8: The following info comes from many
Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3 From Cisco s website, here are the minimum requirements for CCP 2.7 and CCP 2.8: The following info comes from many
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
Deploying Cisco ASA Firewall Features (FIREWALL) v1.0. Global Knowledge European Remote Labs Instructor Guide
 Deploying Cisco ASA Firewall Features (FIREWALL) v1.0 Global Knowledge European Remote Labs Instructor Guide Revision Draft 0.2 11/03/2011 1. Contents 1. Contents.2 2. Introduction.3 3. Remote Labs Topology,
Deploying Cisco ASA Firewall Features (FIREWALL) v1.0 Global Knowledge European Remote Labs Instructor Guide Revision Draft 0.2 11/03/2011 1. Contents 1. Contents.2 2. Introduction.3 3. Remote Labs Topology,
Easy Setup Guide. Cisco ASA with Firepower Services. You can easily set up your ASA in this step-by-step guide.
 Cisco ASA with Firepower Services Easy Setup Guide You can easily set up your ASA in this step-by-step guide. Connecting PC to ASA Installing ASDM 3 Configuring ASA 4 Using Umbrella DNS Connecting PC to
Cisco ASA with Firepower Services Easy Setup Guide You can easily set up your ASA in this step-by-step guide. Connecting PC to ASA Installing ASDM 3 Configuring ASA 4 Using Umbrella DNS Connecting PC to
VII. Corente Services SSL Client
 VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
Student Guide. Document Version: This guide documents features available in NETLAB+ VE version and later.
 Student Guide Document Version: 2018-02-15 This guide documents features available in NETLAB+ VE version 18.1.0 and later. Copyright 2018 Network Development Group, Inc. www.netdevgroup.com NETLAB Academy
Student Guide Document Version: 2018-02-15 This guide documents features available in NETLAB+ VE version 18.1.0 and later. Copyright 2018 Network Development Group, Inc. www.netdevgroup.com NETLAB Academy
GSS Administration and Troubleshooting
 CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
CHAPTER 9 GSS Administration and Troubleshooting This chapter covers the procedures necessary to properly manage and maintain your GSSM and GSS devices, including login security, software upgrades, GSSM
Configuring the SMA 500v Virtual Appliance
 Using the SMA 500v Virtual Appliance Configuring the SMA 500v Virtual Appliance Registering Your Appliance Using the 30-day Trial Version Upgrading Your Appliance Configuring the SMA 500v Virtual Appliance
Using the SMA 500v Virtual Appliance Configuring the SMA 500v Virtual Appliance Registering Your Appliance Using the 30-day Trial Version Upgrading Your Appliance Configuring the SMA 500v Virtual Appliance
Practice Labs User Guide
 Practice Labs User Guide This page is intentionally blank Contents Introduction... 3 Overview... 3 Accessing Practice Labs... 3 The Practice Labs Interface... 4 Minimum Browser Requirements... 5 The Content
Practice Labs User Guide This page is intentionally blank Contents Introduction... 3 Overview... 3 Accessing Practice Labs... 3 The Practice Labs Interface... 4 Minimum Browser Requirements... 5 The Content
Cisco NAC Appliance Agents
 10 CHAPTER This chapter presents overviews, login flow, and session termination dialogs for the following Cisco NAC Appliance access portals: Cisco NAC Agent, page 10-1 Cisco NAC Web Agent, page 10-28
10 CHAPTER This chapter presents overviews, login flow, and session termination dialogs for the following Cisco NAC Appliance access portals: Cisco NAC Agent, page 10-1 Cisco NAC Web Agent, page 10-28
NetExtender for SSL-VPN
 NetExtender for SSL-VPN Document Scope This document describes how to plan, design, implement, and manage the NetExtender feature in a SonicWALL SSL-VPN Environment. This document contains the following
NetExtender for SSL-VPN Document Scope This document describes how to plan, design, implement, and manage the NetExtender feature in a SonicWALL SSL-VPN Environment. This document contains the following
Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM
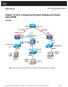 Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM Topology Note: ISR G2 devices have Gigabit Ethernet interfaces instead of Fast Ethernet interfaces. All contents are Copyright 1992
Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM Topology Note: ISR G2 devices have Gigabit Ethernet interfaces instead of Fast Ethernet interfaces. All contents are Copyright 1992
VI. Corente Services Client
 VI. Corente Services Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 II. Corente Client Configuration...
VI. Corente Services Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 II. Corente Client Configuration...
Cisco - ASA Lab Camp v9.0
 Cisco - ASA Lab Camp v9.0 Code: 0007 Lengt h: 5 days URL: View Online Based on our enhanced SASAC v1.0 and SASAA v1.2 courses, this exclusive, lab-based course, provides you with your own set of equipment
Cisco - ASA Lab Camp v9.0 Code: 0007 Lengt h: 5 days URL: View Online Based on our enhanced SASAC v1.0 and SASAA v1.2 courses, this exclusive, lab-based course, provides you with your own set of equipment
Installation and Configuration Guide
 Installation and Configuration Guide h-series 800-782-3762 www.edgewave.com 2001 2011 EdgeWave Inc. (formerly St. Bernard Software). All rights reserved. The EdgeWave logo, iprism and iguard are trademarks
Installation and Configuration Guide h-series 800-782-3762 www.edgewave.com 2001 2011 EdgeWave Inc. (formerly St. Bernard Software). All rights reserved. The EdgeWave logo, iprism and iguard are trademarks
Lab 8: Firewalls ASA Firewall Device
 Lab 8: Firewalls ASA Firewall Device 8.1 Details Aim: Rich Macfarlane 2015 The aim of this lab is to investigate a Cisco ASA Firewall Device, its default traffic flows, its stateful firewalling functionality,
Lab 8: Firewalls ASA Firewall Device 8.1 Details Aim: Rich Macfarlane 2015 The aim of this lab is to investigate a Cisco ASA Firewall Device, its default traffic flows, its stateful firewalling functionality,
Remote Access VPN. Remote Access VPN Overview. Licensing Requirements for Remote Access VPN
 Remote Access virtual private network (VPN) allows individual users to connect to your network from a remote location using a laptop or desktop computer connected to the Internet. This allows mobile workers
Remote Access virtual private network (VPN) allows individual users to connect to your network from a remote location using a laptop or desktop computer connected to the Internet. This allows mobile workers
LiveNX Upgrade Guide from v5.2.0 to v5.2.1
 LIVEACTION, INC. LiveNX Upgrade Guide from v5.2.0 to v5.2.1 UPGRADE LiveAction, Inc. 3500 Copyright WEST BAYSHORE 2016 LiveAction, ROAD Inc. All rights reserved. LiveAction, LiveNX, LiveUX, the LiveAction
LIVEACTION, INC. LiveNX Upgrade Guide from v5.2.0 to v5.2.1 UPGRADE LiveAction, Inc. 3500 Copyright WEST BAYSHORE 2016 LiveAction, ROAD Inc. All rights reserved. LiveAction, LiveNX, LiveUX, the LiveAction
UNT System Campus VPN Guide
 Contents Introduction... 3 SSL Web Portal... 4 Installing AnyConnect VPNClient... 12 Connecting AnyConnect VPN client... 16 IPSec Client Configuration... 18 Apple OS X Configuration... 21 Android Configuration...
Contents Introduction... 3 SSL Web Portal... 4 Installing AnyConnect VPNClient... 12 Connecting AnyConnect VPN client... 16 IPSec Client Configuration... 18 Apple OS X Configuration... 21 Android Configuration...
Configure the ASA for Dual Internal Networks
 Configure the ASA for Dual Internal Networks Document ID: 119195 Contributed by Dinkar Sharma, Bratin Saha, and Prashant Joshi, Cisco TAC Engineers. Aug 05, 2015 Contents Introduction Prerequisites Requirements
Configure the ASA for Dual Internal Networks Document ID: 119195 Contributed by Dinkar Sharma, Bratin Saha, and Prashant Joshi, Cisco TAC Engineers. Aug 05, 2015 Contents Introduction Prerequisites Requirements
Identity Firewall. About the Identity Firewall
 This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
This chapter describes how to configure the ASA for the. About the, on page 1 Guidelines for the, on page 7 Prerequisites for the, on page 9 Configure the, on page 10 Monitoring the, on page 16 History
DSS User Guide. End User Guide. - i -
 DSS User Guide End User Guide - i - DSS User Guide Table of Contents End User Guide... 1 Table of Contents... 2 Part 1: Getting Started... 1 How to Log in to the Web Portal... 1 How to Manage Account Settings...
DSS User Guide End User Guide - i - DSS User Guide Table of Contents End User Guide... 1 Table of Contents... 2 Part 1: Getting Started... 1 How to Log in to the Web Portal... 1 How to Manage Account Settings...
Application Note 3Com VCX Connect with SIP Trunking - Configuration Guide
 Application Note 3Com VCX Connect with SIP Trunking - Configuration Guide 28 May 2009 3Com VCX Connect Solution SIP Trunking Table of Contents 1 3COM VCX CONNECT AND INGATE... 1 1.1 SIP TRUNKING SUPPORT...
Application Note 3Com VCX Connect with SIP Trunking - Configuration Guide 28 May 2009 3Com VCX Connect Solution SIP Trunking Table of Contents 1 3COM VCX CONNECT AND INGATE... 1 1.1 SIP TRUNKING SUPPORT...
Managing Deployment. Understanding Deployment CHAPTER
 CHAPTER 8 The settings and policies you define in Security Manager must be deployed to your devices so that you can implement them in your network. The steps you take to deploy configurations to devices
CHAPTER 8 The settings and policies you define in Security Manager must be deployed to your devices so that you can implement them in your network. The steps you take to deploy configurations to devices
202 Lab Introduction Connecting to the Lab Environment
 202 Lab Introduction Connecting to the Lab Environment Objectives During this v7.1 Deployment lab, each student (from the Blue group or Green group) must verify access (and permissions) to their assigned
202 Lab Introduction Connecting to the Lab Environment Objectives During this v7.1 Deployment lab, each student (from the Blue group or Green group) must verify access (and permissions) to their assigned
Hands-On Lab. Windows Azure Virtual Machine Roles. Lab version: Last updated: 12/14/2010. Page 1
 Hands-On Lab Windows Azure Virtual Machine Roles Lab version: 2.0.0 Last updated: 12/14/2010 Page 1 CONTENTS OVERVIEW... 3 EXERCISE 1: CREATING AND DEPLOYING A VIRTUAL MACHINE ROLE IN WINDOWS AZURE...
Hands-On Lab Windows Azure Virtual Machine Roles Lab version: 2.0.0 Last updated: 12/14/2010 Page 1 CONTENTS OVERVIEW... 3 EXERCISE 1: CREATING AND DEPLOYING A VIRTUAL MACHINE ROLE IN WINDOWS AZURE...
Application Note Asterisk BE with Remote Phones - Configuration Guide
 Application Note Asterisk BE with Remote Phones - Configuration Guide 15 January 2009 Asterisk BE - Remote SIP Phones Table of Contents 1 ASTERISK BUSINESS EDITION AND INGATE... 1 1.1 REMOTE SIP PHONE
Application Note Asterisk BE with Remote Phones - Configuration Guide 15 January 2009 Asterisk BE - Remote SIP Phones Table of Contents 1 ASTERISK BUSINESS EDITION AND INGATE... 1 1.1 REMOTE SIP PHONE
Enter your Appserv username and password to sign in to the Website
 Appserv Desktop Access Logging on from a Windows 10 Device Step 1. To sign in to the Appserv Desktop Access website, either enter the following address into the Microsoft Edge browser address bar, or click
Appserv Desktop Access Logging on from a Windows 10 Device Step 1. To sign in to the Appserv Desktop Access website, either enter the following address into the Microsoft Edge browser address bar, or click
Agent and Agent Browser. Updated Friday, January 26, Autotask Corporation
 Agent and Agent Browser Updated Friday, January 26, 2018 2018 Autotask Corporation Table of Contents Table of Contents 2 The AEM Agent and Agent Browser 3 AEM Agent 5 Privacy Mode 9 Agent Browser 11 Agent
Agent and Agent Browser Updated Friday, January 26, 2018 2018 Autotask Corporation Table of Contents Table of Contents 2 The AEM Agent and Agent Browser 3 AEM Agent 5 Privacy Mode 9 Agent Browser 11 Agent
Using ASDM to manage a FirePOWER module on ASA
 Using ASDM to manage a FirePOWER module on ASA Contents Introduction Components used Prerequisites Architecture Background operation when a user connects to ASA via ASDM Step 1 The user initiates the ASDM
Using ASDM to manage a FirePOWER module on ASA Contents Introduction Components used Prerequisites Architecture Background operation when a user connects to ASA via ASDM Step 1 The user initiates the ASDM
Aspera Connect Windows XP, 2003, Vista, 2008, 7. Document Version: 1
 Aspera Connect 2.6.3 Windows XP, 2003, Vista, 2008, 7 Document Version: 1 2 Contents Contents Introduction... 3 Setting Up... 4 Upgrading from a Previous Version...4 Installation... 4 Set Up Network Environment...
Aspera Connect 2.6.3 Windows XP, 2003, Vista, 2008, 7 Document Version: 1 2 Contents Contents Introduction... 3 Setting Up... 4 Upgrading from a Previous Version...4 Installation... 4 Set Up Network Environment...
Configuring the Cisco NAM 2220 Appliance
 CHAPTER 5 This section describes how to configure the Cisco NAM 2220 appliance to establish network connectivity, configure IP parameters, and how to perform other required administrative tasks using the
CHAPTER 5 This section describes how to configure the Cisco NAM 2220 appliance to establish network connectivity, configure IP parameters, and how to perform other required administrative tasks using the
Logging. About Logging. This chapter describes how to log system messages and use them for troubleshooting.
 This chapter describes how to log system messages and use them for troubleshooting. About, page 1 Guidelines for, page 7 Configure, page 8 Monitoring the Logs, page 26 History for, page 29 About System
This chapter describes how to log system messages and use them for troubleshooting. About, page 1 Guidelines for, page 7 Configure, page 8 Monitoring the Logs, page 26 History for, page 29 About System
DOWNLOAD PDF CISCO ASA 5505 CONFIGURATION GUIDE
 Chapter 1 : Cisco ASA DMZ Configuration Example â Speak Network Solutions Cisco ASA Quick Start Guide. Step 1 Connect the power supply adaptor to the power cable.. Step 2 Connect the rectangular connector
Chapter 1 : Cisco ASA DMZ Configuration Example â Speak Network Solutions Cisco ASA Quick Start Guide. Step 1 Connect the power supply adaptor to the power cable.. Step 2 Connect the rectangular connector
Getting Started. About the ASA for Firepower How the ASA Works with the Firepower 2100
 This chapter describes how to deploy the ASA on the Firepower 2100 in your network, and how to perform initial configuration. About the ASA for Firepower 2100, page 1 Connect the Interfaces, page 4 Power
This chapter describes how to deploy the ASA on the Firepower 2100 in your network, and how to perform initial configuration. About the ASA for Firepower 2100, page 1 Connect the Interfaces, page 4 Power
LiveNX Upgrade Guide from v5.1.2 to v Windows
 LIVEACTION, INC. LiveNX Upgrade Guide from v5.1.2 to v5.1.3 - Windows UPGRADE LiveAction, Inc. 3500 Copyright WEST BAYSHORE 2016 LiveAction, ROAD Inc. All rights reserved. LiveAction, LiveNX, LiveUX, the
LIVEACTION, INC. LiveNX Upgrade Guide from v5.1.2 to v5.1.3 - Windows UPGRADE LiveAction, Inc. 3500 Copyright WEST BAYSHORE 2016 LiveAction, ROAD Inc. All rights reserved. LiveAction, LiveNX, LiveUX, the
Viewing System Status, page 404. Backing Up and Restoring a Configuration, page 416. Managing Certificates for Authentication, page 418
 This chapter describes how to maintain the configuration and firmware, reboot or reset the security appliance, manage the security license and digital certificates, and configure other features to help
This chapter describes how to maintain the configuration and firmware, reboot or reset the security appliance, manage the security license and digital certificates, and configure other features to help
Migrating from Citrix XenApp (IMA / FMA) to Parallels Remote Application Server
 Parallels Remote Application Server Migrating from Citrix XenApp (IMA / FMA) to Parallels Remote Application Server Contents 1. Introduction a. Why Should You Migrate from Citrix to Parallels RAS b. Overview
Parallels Remote Application Server Migrating from Citrix XenApp (IMA / FMA) to Parallels Remote Application Server Contents 1. Introduction a. Why Should You Migrate from Citrix to Parallels RAS b. Overview
Using Cloud VPN Service
 To begin, log in to the VMS Service Interface using your consumer credentials. In case of association with several tenants, choose a customer name from the drop-down on the left pane of the Welcome page.
To begin, log in to the VMS Service Interface using your consumer credentials. In case of association with several tenants, choose a customer name from the drop-down on the left pane of the Welcome page.
Getting Started with Soonr
 WWW.SOONR.COM Getting Started with Soonr A Quick Start Guide for New Users Soonr Inc. 12/19/2012 Revision 1.1 Copyright 2012, Soonr Inc., all rights reserved. Table of Contents 1 How Soonr Workplace Works...
WWW.SOONR.COM Getting Started with Soonr A Quick Start Guide for New Users Soonr Inc. 12/19/2012 Revision 1.1 Copyright 2012, Soonr Inc., all rights reserved. Table of Contents 1 How Soonr Workplace Works...
Cisco ASA 5500 LAB Guide
 INGRAM MICRO Cisco ASA 5500 LAB Guide Ingram Micro 4/1/2009 The following LAB Guide will provide you with the basic steps involved in performing some fundamental configurations on a Cisco ASA 5500 series
INGRAM MICRO Cisco ASA 5500 LAB Guide Ingram Micro 4/1/2009 The following LAB Guide will provide you with the basic steps involved in performing some fundamental configurations on a Cisco ASA 5500 series
CounterACT 7.0. Quick Installation Guide for a Single Virtual CounterACT Appliance
 CounterACT 7.0 Quick Installation Guide for a Single Virtual CounterACT Appliance Table of Contents Welcome to CounterACT Version 7.0... 3 Overview... 4 1. Create a Deployment Plan... 5 Decide Where to
CounterACT 7.0 Quick Installation Guide for a Single Virtual CounterACT Appliance Table of Contents Welcome to CounterACT Version 7.0... 3 Overview... 4 1. Create a Deployment Plan... 5 Decide Where to
Load Balancing VMware Workspace Portal/Identity Manager
 Load Balancing VMware Workspace Portal/Identity Manager Overview VMware Workspace Portal/Identity Manager combines applications and desktops in a single, aggregated workspace. Employees can then access
Load Balancing VMware Workspace Portal/Identity Manager Overview VMware Workspace Portal/Identity Manager combines applications and desktops in a single, aggregated workspace. Employees can then access
Contents. Introduction
 Contents Introduction Prerequisites Requirements Components Used Network Diagrams Configure Step 1. Modify Interface IP configuration on ASA Step 2. Modify DHCP pool settings on both inside and wifi interfaces
Contents Introduction Prerequisites Requirements Components Used Network Diagrams Configure Step 1. Modify Interface IP configuration on ASA Step 2. Modify DHCP pool settings on both inside and wifi interfaces
Your partner for Success. CCIE Security v5 Lab Access Guide
 Your partner for Success CCIE Security v5 Lab Access Guide Version 1.9 Author: Cloudmylab Support Contents Introduction... 4 Audience... 4 Disclaimer... 4 Legal Liability... 4 Topology... 4 Devices Used...
Your partner for Success CCIE Security v5 Lab Access Guide Version 1.9 Author: Cloudmylab Support Contents Introduction... 4 Audience... 4 Disclaimer... 4 Legal Liability... 4 Topology... 4 Devices Used...
This document describes the configuration of Secure Sockets Layer (SSL) decryption on the FirePOWER Module using ASDM (On-Box Management).
 Contents Introduction Prerequisites Requirements Components Used Background Information Outbound SSL Decryption Inbound SSL Decryption Configuration for SSL Decryption Outbound SSL decryption (Decrypt
Contents Introduction Prerequisites Requirements Components Used Background Information Outbound SSL Decryption Inbound SSL Decryption Configuration for SSL Decryption Outbound SSL decryption (Decrypt
NetBrain Technologies Inc. NetBrain Consultant Edition. Quick Start Guide
 NetBrain Technologies Inc. NetBrain Consultant Edition Quick Start Guide Content 1. Install NetBrain Workstation CE System... 3 1.1 Install and Activate NetBrain Gateway Server... 5 1.2 Install Workstation...
NetBrain Technologies Inc. NetBrain Consultant Edition Quick Start Guide Content 1. Install NetBrain Workstation CE System... 3 1.1 Install and Activate NetBrain Gateway Server... 5 1.2 Install Workstation...
Securexam Mac User Guide
 Securexam Mac User Guide Unlike previous versions, Securexam for Mac now functions much like the PC version where it integrates with PlanetSSI to retrieve a user s exams and licenses via the web and upon
Securexam Mac User Guide Unlike previous versions, Securexam for Mac now functions much like the PC version where it integrates with PlanetSSI to retrieve a user s exams and licenses via the web and upon
Deploying Citrix MetaFrame with the FirePass Controller
 Deployment Guide Deploying Citrix Presentation Server (MetaFrame) with the FirePass Controller Deploying Citrix MetaFrame with the FirePass Controller Welcome to the F5 FirePass controller Deployment Guide
Deployment Guide Deploying Citrix Presentation Server (MetaFrame) with the FirePass Controller Deploying Citrix MetaFrame with the FirePass Controller Welcome to the F5 FirePass controller Deployment Guide
Parallels Remote Application Server
 Parallels Remote Application Server Parallels Client for Mac User's Guide v16 Parallels International GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 672 20 30 www.parallels.com Copyright
Parallels Remote Application Server Parallels Client for Mac User's Guide v16 Parallels International GmbH Vordergasse 59 8200 Schaffhausen Switzerland Tel: + 41 52 672 20 30 www.parallels.com Copyright
User Manual. SSV Remote Access Gateway. Web ConfigTool
 SSV Remote Access Gateway Web ConfigTool User Manual SSV Software Systems GmbH Dünenweg 5 D-30419 Hannover Phone: +49 (0)511/40 000-0 Fax: +49 (0)511/40 000-40 E-mail: sales@ssv-embedded.de Document Revision:
SSV Remote Access Gateway Web ConfigTool User Manual SSV Software Systems GmbH Dünenweg 5 D-30419 Hannover Phone: +49 (0)511/40 000-0 Fax: +49 (0)511/40 000-40 E-mail: sales@ssv-embedded.de Document Revision:
ASACAMP - ASA Lab Camp (5316)
 ASACAMP - ASA Lab Camp (5316) Price: $4,595 Cisco Course v1.0 Cisco Security Appliance Software v8.0 Based on our enhanced FIREWALL and VPN courses, this exclusive, lab-based course is designed to provide
ASACAMP - ASA Lab Camp (5316) Price: $4,595 Cisco Course v1.0 Cisco Security Appliance Software v8.0 Based on our enhanced FIREWALL and VPN courses, this exclusive, lab-based course is designed to provide
Cisco Passguide Exam Questions & Answers
 Cisco Passguide 642-648 Exam Questions & Answers Number: 642-648 Passing Score: 800 Time Limit: 120 min File Version: 61.8 http://www.gratisexam.com/ Cisco 642-648 Exam Questions & Answers Exam Name: Deploying
Cisco Passguide 642-648 Exam Questions & Answers Number: 642-648 Passing Score: 800 Time Limit: 120 min File Version: 61.8 http://www.gratisexam.com/ Cisco 642-648 Exam Questions & Answers Exam Name: Deploying
Release Notes for Cisco ASDM Version 5.2(5)
 May 2010 This document contains release information for Cisco ASDM Version 5.2(5) on the Cisco ASA 5500. It includes the following sections: New Features, page 1 System Requirements, page 1 Upgrading ASDM,
May 2010 This document contains release information for Cisco ASDM Version 5.2(5) on the Cisco ASA 5500. It includes the following sections: New Features, page 1 System Requirements, page 1 Upgrading ASDM,
Getting Started. Access the Console for the Command-Line Interface. Access the Appliance Console
 This chapter describes how to get started with your Cisco ASA. Access the Console for the Command-Line Interface, on page 1 Configure ASDM Access, on page 9 Start ASDM, on page 15 Factory Default Configurations,
This chapter describes how to get started with your Cisco ASA. Access the Console for the Command-Line Interface, on page 1 Configure ASDM Access, on page 9 Start ASDM, on page 15 Factory Default Configurations,
Remote Support 19.1 Web Rep Console
 Remote Support 19.1 Web Rep Console 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks are the property
Remote Support 19.1 Web Rep Console 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks are the property
Amazon AppStream 2.0: SOLIDWORKS Deployment Guide
 2018 Amazon AppStream 2.0: SOLIDWORKS Deployment Guide Build an Amazon AppStream 2.0 environment to stream SOLIDWORKS to your users June 2018 https://aws.amazon.com/appstream2/ 1 Welcome This guide describes
2018 Amazon AppStream 2.0: SOLIDWORKS Deployment Guide Build an Amazon AppStream 2.0 environment to stream SOLIDWORKS to your users June 2018 https://aws.amazon.com/appstream2/ 1 Welcome This guide describes
Release Notes for the Cisco ASA Services Module, Version 8.5(x)
 Release s for the Cisco ASA Services Module, Version 8.5(x) Released: July 7, 2011 Updated: September 4, 2012 This document contains release information for the Cisco ASA Services Module (ASASM) Version
Release s for the Cisco ASA Services Module, Version 8.5(x) Released: July 7, 2011 Updated: September 4, 2012 This document contains release information for the Cisco ASA Services Module (ASASM) Version
Introduction to Change and Configuration Management
 CHAPTER 1 Introduction to Change and Configuration Management Cisco Prime Network Change and Configuration Management provides tools that allow you to manage the software and device configuration changes
CHAPTER 1 Introduction to Change and Configuration Management Cisco Prime Network Change and Configuration Management provides tools that allow you to manage the software and device configuration changes
Upgrading from TrafficShield 3.2.X to Application Security Module 9.2.3
 Upgrading from TrafficShield 3.2.X to Application Security Module 9.2.3 Introduction Preparing the 3.2.X system for the upgrade Installing the BIG-IP version 9.2.3 software Licensing the software using
Upgrading from TrafficShield 3.2.X to Application Security Module 9.2.3 Introduction Preparing the 3.2.X system for the upgrade Installing the BIG-IP version 9.2.3 software Licensing the software using
Deploying Cisco ASA Firewall Solutions (FIREWALL) v2.0. Global Knowledge European Remote Labs Instructor Guide
 Deploying Cisco ASA Firewall Solutions (FIREWALL) v2.0 Global Knowledge European Remote Labs Instructor Guide 1. Contents 1. Contents... 2 2. Introduction... 3 3. Remote Labs Topology, Connections and
Deploying Cisco ASA Firewall Solutions (FIREWALL) v2.0 Global Knowledge European Remote Labs Instructor Guide 1. Contents 1. Contents... 2 2. Introduction... 3 3. Remote Labs Topology, Connections and
SonicWALL SSL VPN 2.5 Early Field Trial
 Secure Remote Access Contents Platform Compatibility New Features Known Issues Resolved Issues Upgrading SonicWALL SSL VPN Software Procedures Related Technical Documentation Platform Compatibility The
Secure Remote Access Contents Platform Compatibility New Features Known Issues Resolved Issues Upgrading SonicWALL SSL VPN Software Procedures Related Technical Documentation Platform Compatibility The
Performing an ObserveIT Upgrade Using the Interactive Installer
 Performing an ObserveIT Upgrade Using the Interactive Installer ABOUT THIS DOCUMENT This document contains detailed procedures and instructions on how to upgrade ObserveIT by using the interactive "One
Performing an ObserveIT Upgrade Using the Interactive Installer ABOUT THIS DOCUMENT This document contains detailed procedures and instructions on how to upgrade ObserveIT by using the interactive "One
shun through sysopt radius ignore-secret Commands
 CHAPTER 30 shun through sysopt radius ignore-secret Commands 30-1 shun Chapter 30 shun To block connections from an attacking host, use the shun command in privileged EXEC mode. To disable a shun, use
CHAPTER 30 shun through sysopt radius ignore-secret Commands 30-1 shun Chapter 30 shun To block connections from an attacking host, use the shun command in privileged EXEC mode. To disable a shun, use
Table of Contents HOL-1757-MBL-6
 Table of Contents Lab Overview - - VMware AirWatch: Technology Partner Integration... 2 Lab Guidance... 3 Module 1 - F5 Integration with AirWatch (30 min)... 8 Getting Started... 9 F5 BigIP Configuration...
Table of Contents Lab Overview - - VMware AirWatch: Technology Partner Integration... 2 Lab Guidance... 3 Module 1 - F5 Integration with AirWatch (30 min)... 8 Getting Started... 9 F5 BigIP Configuration...
Cisco Secure Desktop (CSD) on IOS Configuration Example using SDM
 Cisco Secure Desktop (CSD) on IOS Configuration Example using SDM Document ID: 70791 Contents Introduction Prerequisites Requirements Components Used Network Diagram Related Products Conventions Configure
Cisco Secure Desktop (CSD) on IOS Configuration Example using SDM Document ID: 70791 Contents Introduction Prerequisites Requirements Components Used Network Diagram Related Products Conventions Configure
Upgrading an ObserveIT One-Click Installation
 Upgrading an ObserveIT One-Click Installation This document was written for ObserveIT Enterprise version 7.6.1. This document uses screenshots and procedures written for Windows Server 2012 R2 and SQL
Upgrading an ObserveIT One-Click Installation This document was written for ObserveIT Enterprise version 7.6.1. This document uses screenshots and procedures written for Windows Server 2012 R2 and SQL
Deliver and manage customer VIP POCs. The lab will be directed and provide you with step-by-step walkthroughs of key features.
 SR L15 Hands-On Lab Description Protecting Corporate Networks with Symantec Validation and ID Protection At the end of this lab, you should be able to Technically present and answer questions from your
SR L15 Hands-On Lab Description Protecting Corporate Networks with Symantec Validation and ID Protection At the end of this lab, you should be able to Technically present and answer questions from your
The VPN menu and its options are not available in the U.S. export unrestricted version of Cisco Unified Communications Manager.
 Overview, page 1 Prerequisites, page 1 Configuration Task Flow, page 1 Overview The Cisco for Cisco Unified IP Phones creates a secure VPN connection for employees who telecommute. All settings of the
Overview, page 1 Prerequisites, page 1 Configuration Task Flow, page 1 Overview The Cisco for Cisco Unified IP Phones creates a secure VPN connection for employees who telecommute. All settings of the
CLIQ Web Manager. User Manual. The global leader in door opening solutions V 6.1
 CLIQ Web Manager User Manual V 6.1 The global leader in door opening solutions Program version: 6.1 Document number: ST-003478 Date published: 2016-03-31 Language: en-gb Table of contents 1 Overview...9
CLIQ Web Manager User Manual V 6.1 The global leader in door opening solutions Program version: 6.1 Document number: ST-003478 Date published: 2016-03-31 Language: en-gb Table of contents 1 Overview...9
Aspera Connect Mac: OS X 10.6, 10.7, 10.8, Revision: Generated: 11/11/ :29
 Aspera Connect 3.5.2 Mac: OS X 10.6, 10.7, 10.8, 10.9. 10.10 Revision: 3.5.2.95905 Generated: 11/11/2014 17:29 Contents 2 Contents Introduction... 3 System Requirements... 4 Setting up Connect... 5 Part
Aspera Connect 3.5.2 Mac: OS X 10.6, 10.7, 10.8, 10.9. 10.10 Revision: 3.5.2.95905 Generated: 11/11/2014 17:29 Contents 2 Contents Introduction... 3 System Requirements... 4 Setting up Connect... 5 Part
Wireless LAN Controller Web Authentication Configuration Example
 Wireless LAN Controller Web Authentication Configuration Example Document ID: 69340 Contents Introduction Prerequisites Requirements Components Used Conventions Web Authentication Web Authentication Process
Wireless LAN Controller Web Authentication Configuration Example Document ID: 69340 Contents Introduction Prerequisites Requirements Components Used Conventions Web Authentication Web Authentication Process
Configure WSA to Upload Log Files to CTA System
 Configure WSA to Upload Log Files to CTA System Last updated: January 30, 2018 Contents Conventions Introduction Prerequisites Requirements Components Used Configure Configure the Proxy Connect to Active
Configure WSA to Upload Log Files to CTA System Last updated: January 30, 2018 Contents Conventions Introduction Prerequisites Requirements Components Used Configure Configure the Proxy Connect to Active
Deployment Guide: Routing Mode with No DMZ
 Deployment Guide: Routing Mode with No DMZ March 15, 2007 Deployment and Task Overview Description Follow the tasks in this guide to deploy the appliance as a router-firewall device on your network with
Deployment Guide: Routing Mode with No DMZ March 15, 2007 Deployment and Task Overview Description Follow the tasks in this guide to deploy the appliance as a router-firewall device on your network with
File Reputation Filtering and File Analysis
 This chapter contains the following sections: Overview of, page 1 Configuring File Reputation and Analysis Features, page 5 File Reputation and File Analysis Reporting and Tracking, page 14 Taking Action
This chapter contains the following sections: Overview of, page 1 Configuring File Reputation and Analysis Features, page 5 File Reputation and File Analysis Reporting and Tracking, page 14 Taking Action
Fundamentals of Network Security v1.1 Scope and Sequence
 Fundamentals of Network Security v1.1 Scope and Sequence Last Updated: September 9, 2003 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document
Fundamentals of Network Security v1.1 Scope and Sequence Last Updated: September 9, 2003 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document
Testing and Restoring the Nasuni Filer in a Disaster Recovery Scenario
 Testing and Restoring the Nasuni Filer in a Disaster Recovery Scenario Version 7.8 April 2017 Last modified: July 17, 2017 2017 Nasuni Corporation All Rights Reserved Document Information Testing Disaster
Testing and Restoring the Nasuni Filer in a Disaster Recovery Scenario Version 7.8 April 2017 Last modified: July 17, 2017 2017 Nasuni Corporation All Rights Reserved Document Information Testing Disaster
Nortel Network Resource Manager Fundamentals. Release: NRM 2.0 Document Revision: NN
 Release: NRM 2.0 Document Revision: 02.03 www.nortel.com NN48020-300. Release: NRM 2.0 Publication: NN48020-300 Document release date: All Rights Reserved. Printed in Canada, India, and the United States
Release: NRM 2.0 Document Revision: 02.03 www.nortel.com NN48020-300. Release: NRM 2.0 Publication: NN48020-300 Document release date: All Rights Reserved. Printed in Canada, India, and the United States
Managing NCS User Accounts
 7 CHAPTER The Administration enables you to schedule tasks, administer accounts, and configure local and external authentication and authorization. Also, set logging options, configure mail servers, and
7 CHAPTER The Administration enables you to schedule tasks, administer accounts, and configure local and external authentication and authorization. Also, set logging options, configure mail servers, and
Privileged Remote Access Failover Configuration
 Privileged Remote Access Failover Configuration 2003-2018 BeyondTrust, Inc. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust, Inc. Other trademarks are the property of
Privileged Remote Access Failover Configuration 2003-2018 BeyondTrust, Inc. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust, Inc. Other trademarks are the property of
Downloaded from: justpaste.it/i2os
 : Saved : ASA Version 9.1(2) hostname ciscoasa enable password xxx encrypted names ip local pool poolvpn 192.168.20.10-192.168.20.30 mask 255.255.255.0 interface GigabitEthernet0/0 nameif inside security-level
: Saved : ASA Version 9.1(2) hostname ciscoasa enable password xxx encrypted names ip local pool poolvpn 192.168.20.10-192.168.20.30 mask 255.255.255.0 interface GigabitEthernet0/0 nameif inside security-level
Upgrading the Server Software
 APPENDIXB This appendix describes how to upgrade or reinstall the Cisco PAM server software, desktop client software, and Gateway module firmware. Contents Upgrade Notes for Release 1.5.0, page B-2 Obtaining
APPENDIXB This appendix describes how to upgrade or reinstall the Cisco PAM server software, desktop client software, and Gateway module firmware. Contents Upgrade Notes for Release 1.5.0, page B-2 Obtaining
Platform Compatibility... 1 Known Issues... 1 Resolved Issues... 2 Deploying the SRA Virtual Appliance... 3 Related Technical Documentation...
 Secure Remote Access SonicWALL SRA 5.0.0.3 Contents Platform Compatibility... 1 Known Issues... 1 Resolved Issues... 2 Deploying the SRA Virtual Appliance... 3 Related Technical Documentation... 17 Platform
Secure Remote Access SonicWALL SRA 5.0.0.3 Contents Platform Compatibility... 1 Known Issues... 1 Resolved Issues... 2 Deploying the SRA Virtual Appliance... 3 Related Technical Documentation... 17 Platform
WhatsConfigured v3.1 User Guide
 WhatsConfigured v3.1 User Guide Contents Table of Contents Welcome to WhatsConfigured v3.1 Finding more information and updates... 1 Sending feedback... 2 Deploying WhatsConfigured STEP 1: Prepare the
WhatsConfigured v3.1 User Guide Contents Table of Contents Welcome to WhatsConfigured v3.1 Finding more information and updates... 1 Sending feedback... 2 Deploying WhatsConfigured STEP 1: Prepare the
Solution Composer. User's Guide
 Solution Composer User's Guide January 2014 www.lexmark.com Contents 2 Contents Overview...4 Understanding the basics...4 System recommendations...5 Building custom solutions...6 Getting started...6 Step
Solution Composer User's Guide January 2014 www.lexmark.com Contents 2 Contents Overview...4 Understanding the basics...4 System recommendations...5 Building custom solutions...6 Getting started...6 Step
SUREedge DR Installation Guide for Windows Hyper-V
 SUREedge DR Installation Guide for Windows Hyper-V Contents 1. Introduction... 2 1.1 SUREedge DR Deployment Scenarios... 2 1.2 Installation Overview... 3 2. Obtaining SUREedge Software and Documentation...
SUREedge DR Installation Guide for Windows Hyper-V Contents 1. Introduction... 2 1.1 SUREedge DR Deployment Scenarios... 2 1.2 Installation Overview... 3 2. Obtaining SUREedge Software and Documentation...
Sync User Guide. Powered by Axient Anchor
 Sync Powered by Axient Anchor TABLE OF CONTENTS End... Error! Bookmark not defined. Last Revised: Wednesday, October 10, 2018... Error! Bookmark not defined. Table of Contents... 2 Getting Started... 7
Sync Powered by Axient Anchor TABLE OF CONTENTS End... Error! Bookmark not defined. Last Revised: Wednesday, October 10, 2018... Error! Bookmark not defined. Table of Contents... 2 Getting Started... 7
Deployment User Guide
 Deployment User Guide Version: 010319-2 Contents STEP 1: (Windows Users Only): Determine if your PC is running the 32-bit or 64-bit version of Windows. If you are not a PC user, please proceed to step
Deployment User Guide Version: 010319-2 Contents STEP 1: (Windows Users Only): Determine if your PC is running the 32-bit or 64-bit version of Windows. If you are not a PC user, please proceed to step
WebVPN. WebVPN Security Precautions CHAPTER
 CHAPTER 28 lets users establish a secure, remote-access VPN tunnel to the security appliance using a web browser. There is no need for either a software or hardware client. provides easy access to a broad
CHAPTER 28 lets users establish a secure, remote-access VPN tunnel to the security appliance using a web browser. There is no need for either a software or hardware client. provides easy access to a broad
Appserv Internal Desktop Access Mac OS Device with Safari Browser. Enter your Appserv username and password to sign in to the Website
 Appserv Desktop Access Logging on from a Mac OS device Step 1. To sign in to the Appserv Desktop Access website, enter the following address into the Safari browser address bar. Please Note: This documentation
Appserv Desktop Access Logging on from a Mac OS device Step 1. To sign in to the Appserv Desktop Access website, enter the following address into the Safari browser address bar. Please Note: This documentation
The following topics describe how to use backup and restore features in the Firepower System:
 The following topics describe how to use backup and restore features in the Firepower System: Introduction, page 1 Limitations, page 1 Backup Files, page 2 Backing up a Firepower Management Center, page
The following topics describe how to use backup and restore features in the Firepower System: Introduction, page 1 Limitations, page 1 Backup Files, page 2 Backing up a Firepower Management Center, page
Barracuda Firewall Release Notes 6.6.X
 Please Read Before Upgrading Before installing the new firmware version, back up your configuration and read all of the release notes that apply to the versions that are more current than the version that
Please Read Before Upgrading Before installing the new firmware version, back up your configuration and read all of the release notes that apply to the versions that are more current than the version that
Avalanche Remote Control User Guide. Version 4.1
 Avalanche Remote Control User Guide Version 4.1 ii Copyright 2012 by Wavelink Corporation. All rights reserved. Wavelink Corporation 10808 South River Front Parkway, Suite 200 South Jordan, Utah 84095
Avalanche Remote Control User Guide Version 4.1 ii Copyright 2012 by Wavelink Corporation. All rights reserved. Wavelink Corporation 10808 South River Front Parkway, Suite 200 South Jordan, Utah 84095
VPN Client. VPN Client Overview. VPN Client Prerequisites. VPN Client Configuration Task Flow. Before You Begin
 Overview, page 1 Prerequisites, page 1 Configuration Task Flow, page 1 Overview The Cisco for Cisco Unified IP Phones creates a secure VPN connection for employees who telecommute. All settings of the
Overview, page 1 Prerequisites, page 1 Configuration Task Flow, page 1 Overview The Cisco for Cisco Unified IP Phones creates a secure VPN connection for employees who telecommute. All settings of the
Managing WCS User Accounts
 CHAPTER 7 This chapter describes how to configure global e-mail parameters and manage WCS user accounts. It contains these sections: Adding WCS User Accounts, page 7-1 Viewing or Editing User Information,
CHAPTER 7 This chapter describes how to configure global e-mail parameters and manage WCS user accounts. It contains these sections: Adding WCS User Accounts, page 7-1 Viewing or Editing User Information,
SonicWALL Security Appliances. SonicWALL SSL-VPN 200 Getting Started Guide
 SonicWALL Security Appliances SonicWALL SSL-VPN 200 Getting Started Guide SonicWALL SSL-VPN 200 Appliance Getting Started Guide This Getting Started Guide contains installation procedures and configuration
SonicWALL Security Appliances SonicWALL SSL-VPN 200 Getting Started Guide SonicWALL SSL-VPN 200 Appliance Getting Started Guide This Getting Started Guide contains installation procedures and configuration
Installation and Configuration Guide
 CYBERSECURITY, EVOLVED EdgeWave iprism Web Security Installation and Configuration Guide V8.0 15333 Avenue of Science, Suite 100 San Diego, CA 92128 Give us a call 1-855-881-2004 Send us an email: info@edgewave.com
CYBERSECURITY, EVOLVED EdgeWave iprism Web Security Installation and Configuration Guide V8.0 15333 Avenue of Science, Suite 100 San Diego, CA 92128 Give us a call 1-855-881-2004 Send us an email: info@edgewave.com
