Contents. Introduction
|
|
|
- Brandon Potter
- 6 years ago
- Views:
Transcription
1 Contents Introduction Prerequisites Requirements Components Used Network Diagrams Configure Step 1. Modify Interface IP configuration on ASA Step 2. Modify DHCP pool settings on both inside and wifi interfaces Step 3. Specify DNS server to pass to inside and WiFI DHCP clients Step 4. Modify HTTP access configuration on the ASA for Adaptive Security Device Manager (ASDM) access: Step 5. Modify Interface IP for Access Point Management in WLAN console (interface BVI1): Step 6. Modify default-gateway on WAP Step 7. Modify the FirePOWER Module Management IP Address (Optional) If the ASA Management1/1 interface is connected to an inside switch: If the ASA is NOT connected to an inside switch: Step 8. Connect to AP GUI to enable radios and set other WAP configuration WAP CLI Configuration for a single wireless VLAN using modified IP ranges Configurations ASA Configuration Aironet WAP Configuration (without the example SSID config) FirePOWER Module Configuration (with inside switch) FirePOWER Module Configuration (without inside switch) Verify Configure DHCP with Multiple Wireless VLANs Step 1. Remove Existing DHCP configuration on Gig1/9 Step 2. Create Subinterfaces for Each VLAN on Gig1/9 Step 3. Designate a DHCP pool for each VLAN Step 4. Configure the Access Point SSIDs, save the config, and reset the module Troubleshoot Introduction This document describes how to perform initial installation and configuration of a Cisco Adaptive Security Appliance (ASA) 5506W-X device when the default IP addressing scheme needs to be modified to fit into an existing network or if multiple wireless VLANs are required. There are several configuration changes that are required when modifying the default IP addresses in order to access the wireless access point (WAP) as well as ensure that other services (such as DHCP) continue to function as expected. In addition, this document provides some CLI configuration examples for the integrated Wireless Access Point (WAP) to make it easier to complete initial configuration of the WAP. This document is intended to supplement the existing Cisco ASA X Quick Start guide available on the Cisco website.
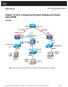
2 Prerequisites This document only applies to the initial configuration of a Cisco ASA5506W-X device that contains a wireless access point and is only intended to address the various changes needed when you modify the existing IP addressing scheme or add additional wireless VLANs. For default configuration installations, the existing ASA 5506-X Quick Start Guide must be referenced. Requirements Cisco recommends that you have knowledge of these topics: Cisco ASA 5506W-X device Client machine with a terminal emulation program such as Putty, SecureCRT, etc. Console Cable and Serial PC Terminal Adapter (DB-9 to RJ-45) Components Used The information in this document is based on these software and hardware versions: Cisco ASA 5506W-X device Client machine with a terminal emulation program such as Putty, SecureCRT, etc. Console Cable and Serial PC Terminal Adapter (DB-9 to RJ-45) ASA FirePOWER Module Integrated Cisco Aironet 702i wireless access point (Built-in WAP) The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, make sure that you understand the potential impact of any command. Network Diagrams As shown in this image, examples of the IP addressing that will be applied in two different topologies: ASA + FirePOWER with an inside switch:
3 ASA + FirePOWER without an inside switch: Configure These steps must be performed in order after you power on and boot the ASA with the console cable connected to the client. Step 1. Modify Interface IP configuration on ASA Configure the inside (GigabitEthernet 1/2) and wifi (GigabitEthernet 1/9) interfaces to have IP addresses as needed within the existing environment. In this example, inside clients are on the /24 network and WIFI clients are on the /24 network. asa(config)# interface gigabitethernet 1/2 asa(config-if)# ip address asa(config)# interface gigabitethernet 1/9 asa(config-if)# ip address Note: You will get this warning when you change the above interface IP addresses. This is expected. Interface address is not on same subnet as DHCP pool WARNING: DHCPD bindings cleared on interface 'inside', address pool removed Step 2. Modify DHCP pool settings on both inside and wifi interfaces This step is required if the ASA is to be used as the DHCP server in the environment. If another DHCP server is used to assign IP addresses to clients then DHCP should be disabled on the ASA altogether. Since you have now changed our IP addressing scheme, you need to alter the existing IP address ranges that the ASA is providing to clients. These commands will create new pools to match the new IP address range: asa(config)# dhcpd address inside asa(config)# dhcpd address wifi Also the modification of the DHCP pools will disable the previous DHCP server on the ASA, and
4 you will need to re-enable it. asa(config)# dhcpd enable inside asa(config)# dhcpd enable wifi If you do not change the interface IP addresses before making the DHCP changes then you will receive this error: asa(config)# dhcpd address inside Address range subnet or is not the same as inside interface subnet Step 3. Specify DNS server to pass to inside and WiFI DHCP clients When they assign IP addresses via DHCP, most clients also need to be assigned a DNS server by the DHCP server. These commands will configure the ASA to include the DNS server located at to all clients. You need to substitute the for either an internal DNS server or a DNS server provided by your ISP. asa(config)# dhcpd dns interface inside asa(config)# dhcpd dns interface wifi Step 4. Modify HTTP access configuration on the ASA for Adaptive Security Device Manager (ASDM) access: Since the IP addressing has been changed, HTTP access to the ASA also needs to be modified so that clients on the inside and WiFI networks can access ASDM to manage the ASA. asa(config)# no http inside asa(config)# no http wifi asa(config)# http inside asa(config)# http wifi Note: This configuration allows any client on the inside or wifi interfaces to access the ASA via ASDM. As a security best practice, you must limit the scope of addresses to trusted clients only. Step 5. Modify Interface IP for Access Point Management in WLAN console (interface BVI1): asa# session wlan console ap>enable Password: Cisco ap#configure terminal Enter configuration commands, one per line. End with CNTL/Z. ap(config)#interface BVI1 ap(config-if)#ip address Step 6. Modify default-gateway on WAP This step is required so that the WAP knows where to send all traffic that is not originated on the local subnet. This is required to provide to access the WAP GUI via HTTP from a client on the ASA inside interface.
5 ap(config)#ip default-gateway Step 7. Modify the FirePOWER Module Management IP Address (Optional) If you also plan to deploy the Cisco FirePOWER (also known as SFR) module then you also need to change its IP address in order to access it from the physical Management1/1 interface on the ASA. There are two basic deployment scenarios that determine how to configure the ASA and the SFR module: 1. A topology in which the ASA Management1/1 interface is connected to an inside switch (as per the normal quick start guide) 2. A topology where an inside switch is not present. Depending on your scenario,these are the appropriate steps: If the ASA Management1/1 interface is connected to an inside switch: You can session into the module and change it from the ASA before connecting it to an inside switch. This configuration allows you to access the SFR module via IP by placing it on the same subnet as the ASA inside interface with an IP address of Lines in bold are specific to this example and are required for establishing IP connectivity. Lines in italics will vary by environment. asa# session sfr console Opening console session with module sfr. Connected to module sfr. Escape character sequence is 'CTRL-^X'. Cisco ASA5506W v5.4.1 (build 211) Sourcefire3D login: admin Password: Sourcefire <<Output Truncated - you will see a large EULA>> Please enter 'YES' or press <ENTER> to AGREE to the EULA: YES System initialization in progress. Please stand by. You must change the password for 'admin' to continue. Enter new password: Confirm new password: You must configure the network to continue. You must configure at least one of IPv4 or IPv6. Do you want to configure IPv4? (y/n) [y]: y Do you want to configure IPv6? (y/n) [n]: n Configure IPv4 via DHCP or manually? (dhcp/manual) [manual]: Enter an IPv4 address for the management interface [ ]: Enter an IPv4 netmask for the management interface [ ]: Enter the IPv4 default gateway for the management interface []: Enter a fully qualified hostname for this system [Sourcefire3D]: Cisco_SFR Enter a comma-separated list of DNS servers or 'none' []: Enter a comma-separated list of search domains or 'none' [example.net]: example.net If your networking information has changed, you will need to reconnect. For HTTP Proxy configuration, run 'configure network http-proxy' Applying 'Default Allow All Traffic' access control policy. Note: It may take a couple minutes for the default access control policy to apply on the SFR
6 module. Once it is complete, you can escape out of the SFR module CLI and back into the ASA by pressing CTRL + SHIFT + 6 +X (CTRL ^ X) If the ASA is NOT connected to an inside switch: An inside switch may not exist in some small deployments. In this type of topology, clients would generally connect to the ASA via the WiFi interface. In this scenario, it is possible eliminate the need for an external switch and access the SFR module via a separate ASA interface by crossconnecting the Management1/1 interface to another physical ASA interface. In this example, a physical ethernet connection must exist between the ASA GigabitEthernet1/3 interface and the Management1/1 interface. Next, you configure the ASA and SFR module to be on a separate subnet and then you are able to access the SFR from both the ASA as well as clients located on the inside or wifi interfaces. ASA Interface Configuration: asa(config)# interface gigabitethernet 1/3 asa(config-if)# ip address asa(config-if)# nameif sfr INFO: Security level for "sfr" set to 0 by default. asa(config-if)# security-level 100 asa(config-if)# no shut SFR Module Configuration: asa# session sfr console Opening console session with module sfr. Connected to module sfr. Escape character sequence is 'CTRL-^X'. Cisco ASA5506W v5.4.1 (build 211) Sourcefire3D login: admin Password: Sourcefire <<Output Truncated - you will see a large EULA>> Please enter 'YES' or press <ENTER> to AGREE to the EULA: YES System initialization in progress. Please stand by. You must change the password for 'admin' to continue. Enter new password: Confirm new password: You must configure the network to continue. You must configure at least one of IPv4 or IPv6. Do you want to configure IPv4? (y/n) [y]: y Do you want to configure IPv6? (y/n) [n]: n Configure IPv4 via DHCP or manually? (dhcp/manual) [manual]: Enter an IPv4 address for the management interface [ ]: Enter an IPv4 netmask for the management interface [ ]: Enter the IPv4 default gateway for the management interface []: Enter a fully qualified hostname for this system [Sourcefire3D]: Cisco_SFR Enter a commaseparated list of DNS servers or 'none' []: Enter a comma-separated list of search domains or 'none' [example.net]: example.net If your networking information has changed, you will need to reconnect. For HTTP Proxy configuration, run 'configure network http-proxy' Applying 'Default Allow All Traffic' access control policy. Note: It may take a couple minutes for the default access control policy to apply on the SFR module. Once it is complete, you can escape out of the SFR module CLI and back into the
7 ASA by pressing CTRL + SHIFT + 6 +X (CTRL ^ X). Once the SFR configuration applies, you must be able to ping the SFR management IP address from the ASA: asa# ping Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds: Success rate is 100 percent (5/5), round-trip min/avg/max = 1/1/1 ms asa# If you cannot ping the interface successfully, verify the configuration and state of physical ethernet connections. Step 8. Connect to AP GUI to enable radios and set other WAP configuration At this point you should have connectivity to manage the WAP via the HTTP GUI as discussed in the quick start guide. You will either need to browse to the IP address of the WAP's BVI interface from a web browser of a client that is connected to the inside network on the 5506W or you can apply the example configuration and connect to the SSID of the WAP. If you do not use the CLI below, you need to plug in the ethernet cable from your client to the Gigabit1/2 interface on the ASA. If you prefer to use the CLI to configure the WAP, you can session into it from the ASA and use this example configuration. This creates an open SSID with the name of 5506W and 5506W_5Ghz so that you can use a wireless client to connect to and further manage the WAP. Note: After applying this configuration you will want to access the GUI and apply security to the SSIDs so that the wireless traffic is encrypted. WAP CLI Configuration for a single wireless VLAN using modified IP ranges dot11 ssid 5506W authentication open guest-mode dot11 ssid 5506W_5Ghz authentication open guest-mode interface Dot11Radio0 ssid 5506W interface Dot11Radio1 ssid 5506W_5Ghz interface BVI1 ip address ip default-gateway interface Dot11Radio0 no shut interface Dot11Radio1
8 no shut From this point on, you can perform the normal steps to complete the configuration of the WAP and you must be able to access it from the web browser of a client connected to the above created SSID. The default username of the access point is Cisco with a password of Cisco with a capital C. Cisco ASA 5506-X Series Quick Start Guide You need to use the IP address of instead of the as stated in the Quick Start Guide. Configurations The resulting configuration must match the output (assuming you used the example IP ranges, otherwise substitute accordingly: ASA Configuration Interfaces: Note: The lines in italics only apply if you do NOT have an inside switch: asa# sh run interface gigabitethernet 1/2 interface GigabitEthernet1/2 nameif inside security-level 100 ip address asa# sh run interface gigabitethernet 1/3 interface GigabitEthernet1/3 nameif sfr security-level 100 ip address asa# sh run interface gigabitethernet 1/9 interface GigabitEthernet1/9 nameif wifi security-level 100 ip address asa# DHCP: asa# sh run dhcpd dhcpd auto_config outside **auto-config from interface 'outside' **auto_config dns x.x.x.x x.x.x.x <-- these lines will depend on your ISP **auto_config domain isp.domain.com <-- these lines will depend on your ISP dhcpd address inside dhcpd dns interface inside dhcpd enable inside dhcpd address wifi dhcpd dns interface wifi dhcpd enable wifi asa# HTTP: asa# show run http http server enable http outside
9 http inside asa# Aironet WAP Configuration (without the example SSID config) asa# session wlan console ap>enable Password: Cisco ap#configure terminal Enter configuration commands, one per line. End with CNTL/Z. ap#show configuration include default-gateway ip default-gateway ap#show configuration include ip route ip route ap#show configuration i interface BVI ip address 10 interface BVI1 ip address FirePOWER Module Configuration (with inside switch) asa# session sfr console Opening console session with module sfr. Connected to module sfr. Escape character sequence is 'CTRL-^X'. > show network ===============[ System Information ]=============== Hostname : Cisco_SFR Domains : example.net DNS Servers : Management port : 8305 IPv4 Default route Gateway : ======================[ eth0 ]====================== State : Enabled Channels : Management & Events Mode : MDI/MDIX : Auto/MDIX MTU : 1500 MAC Address : B0:AA:77:7C:84: [ IPv4 ] Configuration : Manual Address : Netmask : Broadcast : [ IPv6 ] Configuration : Disabled ===============[ Proxy Information ]================ State : Disabled Authentication : Disabled > FirePOWER Module Configuration (without inside switch) asa# session sfr console Opening console session with module sfr. Connected to module sfr. Escape character sequence is 'CTRL-^X'. > show network ===============[ System Information ]===============
10 Hostname : Cisco_SFR Domains : example.net DNS Servers : Management port : 8305 IPv4 Default route Gateway : ======================[ eth0 ]====================== State : Enabled Channels : Management & Events Mode : MDI/MDIX : Auto/MDIX MTU : 1500 MAC Address : B0:AA:77:7C:84: [ IPv4 ] Configuration : Manual Address : Netmask : Broadcast : [ IPv6 ] Configuration : Disabled ===============[ Proxy Information ]================ State : Disabled Authentication : Disabled > Verify In order to verify that you have the proper connectivity to the WAP for completing the installation process: 1. Connect your test client to the ASA inside interface and ensure that it receives an IP address from the ASA via DHCP that is within the desired IP range. 2. Use a web browser on your client in order to navigate to and verify that the AP GUI is now accessible. 3. Ping the SFR management interface from the inside client and the ASA to verify proper connectivity. Configure DHCP with Multiple Wireless VLANs The configuration assumes that you use a single wireless VLAN. The Bridge Virtual Interface (BVI) on the Wireless AP can provide a bridge for Multiple VLANs. Because of the syntax for DHCP on the ASA, if you wish to configure the 5506W as a DHCP server for multiple VLANs, you need to create subinterfaces on the Gigabit1/9 interface and give each a name. This section guides you through the process of how to remove the default configuration and to apply the configuration necessary to set the ASA up as a DHCP server for multiple VLANs. Step 1. Remove Existing DHCP configuration on Gig1/9 First, remove the existing DHCP configuration on the Gig1/9 (wifi) interface: ciscoasa# no dhcpd address wifi ciscoasa# no dhcpd enable wifi
11 Step 2. Create Subinterfaces for Each VLAN on Gig1/9 For each VLAN that you have configured on the access point, you need to configure a subinterface of Gig1/9. In this example configuration, you add two subinterfaces: -Gig1/9.5, which will have nameif vlan5, and will correspond to VLAN 5 and subnet /24. -Gig1/9.30, which will have nameif vlan30, and will correspond to VLAN 30 and subnet /24. In practice, it is essential that the VLAN and subnet configured here match the VLAN and subnet specified on the access point. The nameif and subinterface number can be anything you choose. Please refer to the quick start guide previously mentioned for links in order to configure the access point using the web GUI. ciscoasa(config)# interface g1/9.5 ciscoasa(config-if)# vlan 5 ciscoasa(config-if)# nameif vlan5 ciscoasa(config-if)# security-level 100 ciscoasa(config-if)# ip address ciscoasa(config-if)# interface g1/9.30 ciscoasa(config-if)# vlan 30 ciscoasa(config-if)# nameif vlan30 ciscoasa(config-if)# security-level 100 ciscoasa(config-if)# ip address Step 3. Designate a DHCP pool for each VLAN Create a separate DHCP pool for each VLAN being configured. The syntax for this command requires that you list the nameif out of which the ASA will serve the pool in question. A seen in this example, which uses VLANs 5 and 30: ciscoasa(config)# dhcpd address vlan5 ciscoasa(config)# dhcpd address vlan30 ciscoasa(config)# dhcpd enable vlan5 ciscoasa(config)# dhcpd enable vlan30 Step 4. Configure the Access Point SSIDs, save the config, and reset the module Finally, the access point needs to be configured to correspond to the ASA's configuration. The GUI interface for the access point allows you to configure VLANs on the AP via the client connected to the ASA inside (Gigabit1/2) interface. However, if you prefer to use CLI to configure the AP via the ASA console session and then connect wirelessly to manage the AP, you can use this configuration as a template for creating two SSIDs on VLANs 5 and 30. This must be entered within the AP console in global configuration mode: dot11 vlan-name VLAN30 vlan 30 dot11 vlan-name VLAN5 vlan 5 dot11 ssid SSID_VLAN30 vlan 30 authentication open mbssid guest-mode dot11 ssid SSID_VLAN5 vlan 5 authentication open mbssid guest-mode
12 interface Dot11Radio0 ssid SSID_VLAN30 ssid SSID_VLAN5 mbssid interface Dot11Radio0.5 encapsulation dot1q 5 bridge-group 5 bridge-group 5 subscriber-loop-control bridge-group 5 spanning-disabled bridge-group 5 block-unknown-source no bridge-group 5 source-learning no bridge-group 5 unicast-flooding interface Dot11Radio0.30 encapsulation dot1q 30 bridge-group 30 bridge-group 30 subscriber-loop-control bridge-group 30 spanning-disabled bridge-group 30 block-unknown-source no bridge-group 30 source-learning no bridge-group 30 unicast-flooding interface Dot11Radio1 ssid SSID_VLAN30 ssid SSID_VLAN5 mbssid interface Dot11Radio1.5 encapsulation dot1q 5 bridge-group 5 bridge-group 5 subscriber-loop-control bridge-group 5 spanning-disabled bridge-group 5 block-unknown-source no bridge-group 5 source-learning no bridge-group 5 unicast-flooding interface Dot11Radio1.30 encapsulation dot1q 30 bridge-group 30 bridge-group 30 subscriber-loop-control bridge-group 30 spanning-disabled bridge-group 30 block-unknown-source no bridge-group 30 source-learning no bridge-group 30 unicast-flooding interface GigabitEthernet0.5 encapsulation dot1q 5 bridge-group 5 bridge-group 5 spanning-disabled no bridge-group 5 source-learning interface GigabitEthernet0.30 encapsulation dot1q 30 bridge-group 30 bridge-group 30 spanning-disabled no bridge-group 30 source-learning interface BVI1 ip address
13 ip default-gateway interface Dot11Radio0 no shut interface Dot11Radio1 no shutat this point, the management configuration of the ASA and AP must be complete, and the ASA acts as a DHCP server for VLANs 5 and 30. After saving the configuration using the write memory command on the AP, if you still have connectivity issues then you must reload the AP using the reload command from the CLI. However, if you receive an IP address on the newly created SSIDs then no further action is required. ap#write memory Building configuration... [OK] ap#reload Proceed with reload? [confirm] Writing out the event log to flash:/event.log... Note: You do NOT need to reload the entire ASA device. You must only reload the built-in access point. Once the AP finishes reloading, then you must have connectivity to the AP GUI from a client machine on the wifi or inside networks. It generally takes about two minutes for the AP to completely reboot. From this point on, you can apply the normal steps to complete the configuration of the WAP. Cisco ASA 5506-X Series Quick Start Guide Troubleshoot Troubleshooting ASA connectivity is outside the scope of this document since this is intended for initial configuration. Please refer to the verify and configuration sections to ensure that all steps have been properly completed.
Getting Started. Access the Console for the Command-Line Interface. Access the Appliance Console
 This chapter describes how to get started with your Cisco ASA. Access the Console for the Command-Line Interface, on page 1 Configure ASDM Access, on page 9 Start ASDM, on page 15 Factory Default Configurations,
This chapter describes how to get started with your Cisco ASA. Access the Console for the Command-Line Interface, on page 1 Configure ASDM Access, on page 9 Start ASDM, on page 15 Factory Default Configurations,
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM
 Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Wireless LAN Controller Module Configuration Examples
 Wireless LAN Controller Module Configuration Examples Document ID: 70530 Contents Introduction Prerequisites Requirements Components Used Conventions Basic Configuration Example 1 Basic Configuration with
Wireless LAN Controller Module Configuration Examples Document ID: 70530 Contents Introduction Prerequisites Requirements Components Used Conventions Basic Configuration Example 1 Basic Configuration with
ISR Wireless Configuration Example
 ISR Wireless Configuration Example Document ID: 116579 Contributed by Surendra BG, Cisco TAC Engineer. Oct 16, 2013 Contents Introduction Prerequisites Requirements Components Used Background Information
ISR Wireless Configuration Example Document ID: 116579 Contributed by Surendra BG, Cisco TAC Engineer. Oct 16, 2013 Contents Introduction Prerequisites Requirements Components Used Background Information
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM
 Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Chapter 10 Configure AnyConnect Remote Access SSL VPN Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces. 2015 Cisco and/or its affiliates. All rights
Initial Configuration for the Switch
 Options for Initial Configuration, page 1 Configuring the Switch Using the Web User Interface, page 1 Configuring the Switch Using the CLI, page 4 Configuring the Switch in the ROMMON Mode, page 12 Options
Options for Initial Configuration, page 1 Configuring the Switch Using the Web User Interface, page 1 Configuring the Switch Using the CLI, page 4 Configuring the Switch in the ROMMON Mode, page 12 Options
Configuring the Access Point/Bridge for the First Time
 CHAPTER 2 Configuring the Access Point/Bridge for the First Time This chapter describes how to configure basic settings on your access point/bridge for the first time. You can configure all the settings
CHAPTER 2 Configuring the Access Point/Bridge for the First Time This chapter describes how to configure basic settings on your access point/bridge for the first time. You can configure all the settings
Configuring a Basic Wireless LAN Connection
 This module describes how to configure a wireless LAN (WLAN) connection between a wireless device, such as a laptop computer or mobile phone, and a Cisco 800, 1800 (fixed and modular), 2800, or 3800 series
This module describes how to configure a wireless LAN (WLAN) connection between a wireless device, such as a laptop computer or mobile phone, and a Cisco 800, 1800 (fixed and modular), 2800, or 3800 series
Configuring the WMIC for the First Time
 Configuring the WMIC for the First Time This document describes how to configure basic settings on a Cisco Wireless Mobile Interface Card (WMIC) for the first time. Before You Start Before you install
Configuring the WMIC for the First Time This document describes how to configure basic settings on a Cisco Wireless Mobile Interface Card (WMIC) for the first time. Before You Start Before you install
Using the Web Graphical User Interface
 Prerequisites for Using the Web GUI, page 1 Information About Using The Web GUI, page 1 Connecting the Console Port of the Device, page 3 Logging On to the Web GUI, page 3 Enabling Web and Secure Web Modes,
Prerequisites for Using the Web GUI, page 1 Information About Using The Web GUI, page 1 Connecting the Console Port of the Device, page 3 Logging On to the Web GUI, page 3 Enabling Web and Secure Web Modes,
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces. 2016 Cisco and/or its affiliates. All
Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION Topology Objectives Implement a Layer 3 EtherChannel Implement Static Routing Implement Inter-VLAN Routing Background Cisco's switching
CCNPv7.1 SWITCH Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION Topology Objectives Implement a Layer 3 EtherChannel Implement Static Routing Implement Inter-VLAN Routing Background Cisco's switching
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM
 Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
Chapter 10 Configure Clientless Remote Access SSL VPNs Using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet Interfaces.
Configuring Cisco Mobility Express controller
 There are multiple ways one can configure a Cisco Mobility Express controller. They are as follows: 1 CLI Setup Wizard 2 Over the Air Setup Wizard 3 Network Plug and Play CLI Setup Wizard, page 1 Over-the-Air
There are multiple ways one can configure a Cisco Mobility Express controller. They are as follows: 1 CLI Setup Wizard 2 Over the Air Setup Wizard 3 Network Plug and Play CLI Setup Wizard, page 1 Over-the-Air
The following topics explain how to get started configuring Firepower Threat Defense. Table 1: Firepower Device Manager Supported Models
 The following topics explain how to get started configuring Firepower Threat Defense. Is This Guide for You?, page 1 Logging Into the System, page 2 Setting Up the System, page 6 Configuration Basics,
The following topics explain how to get started configuring Firepower Threat Defense. Is This Guide for You?, page 1 Logging Into the System, page 2 Setting Up the System, page 6 Configuration Basics,
Using the Web Graphical User Interface
 Prerequisites for Using the Web GUI, page 1 Information About Using The Web GUI, page 2 Connecting the Console Port of the Switch, page 3 Logging On to the GUI, page 4 Enabling Web and Secure Web Modes,
Prerequisites for Using the Web GUI, page 1 Information About Using The Web GUI, page 2 Connecting the Console Port of the Switch, page 3 Logging On to the GUI, page 4 Enabling Web and Secure Web Modes,
Wireless LAN Controller Web Authentication Configuration Example
 Wireless LAN Controller Web Authentication Configuration Example Document ID: 69340 Contents Introduction Prerequisites Requirements Components Used Conventions Web Authentication Web Authentication Process
Wireless LAN Controller Web Authentication Configuration Example Document ID: 69340 Contents Introduction Prerequisites Requirements Components Used Conventions Web Authentication Web Authentication Process
Using ASDM to manage a FirePOWER module on ASA
 Using ASDM to manage a FirePOWER module on ASA Contents Introduction Components used Prerequisites Architecture Background operation when a user connects to ASA via ASDM Step 1 The user initiates the ASDM
Using ASDM to manage a FirePOWER module on ASA Contents Introduction Components used Prerequisites Architecture Background operation when a user connects to ASA via ASDM Step 1 The user initiates the ASDM
Cisco Unified Communications Manager Express 7921 Push-to-talk
 Cisco Unified Communications Manager Express 7921 Push-to-talk Application Note May 13, 2008 Cisco Revision History Revision Date Author Comments 1 03/29/2007 Tony Huynh Version 1.0 Table of Contents 1
Cisco Unified Communications Manager Express 7921 Push-to-talk Application Note May 13, 2008 Cisco Revision History Revision Date Author Comments 1 03/29/2007 Tony Huynh Version 1.0 Table of Contents 1
Table of Contents. isco Configuring 802.1q Trunking Between a Catalyst 3550 and Catalyst Switches Running Integrated Cisco IOS (Nativ
 king Between a Catalyst 3550 and Catalyst Switches Running isco Configuring 802.1q Trunking Between a Catalyst 3550 and Catalyst Switches Running Integrated Cisco IOS (Nativ Table of Contents Configuring
king Between a Catalyst 3550 and Catalyst Switches Running isco Configuring 802.1q Trunking Between a Catalyst 3550 and Catalyst Switches Running Integrated Cisco IOS (Nativ Table of Contents Configuring
Configuring a Wireless LAN Connection
 CHAPTER 9 The Cisco Secure Router 520 Series routers support a secure, affordable, and easy-to-use wireless LAN solution that combines mobility and flexibility with the enterprise-class features required
CHAPTER 9 The Cisco Secure Router 520 Series routers support a secure, affordable, and easy-to-use wireless LAN solution that combines mobility and flexibility with the enterprise-class features required
Cisco Firepower Threat Defense Configuration Guide for Firepower Device Manager, Version 6.2
 Cisco Firepower Threat Defense Configuration Guide for Firepower Device Manager, Version 6.2 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Cisco Firepower Threat Defense Configuration Guide for Firepower Device Manager, Version 6.2 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com
Lab 5: Basic VLAN Configuration
 Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 172.17.99.11 255.255.255.0 N/A S2 VLAN 99 172.17.99.12 255.255.255.0 N/A S3 VLAN 99 172.17.99.13
Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 172.17.99.11 255.255.255.0 N/A S2 VLAN 99 172.17.99.12 255.255.255.0 N/A S3 VLAN 99 172.17.99.13
AOS-W 6.4. Quick Start Guide. Install the Switch. Initial Setup Using the WebUI Setup Wizard
 AOS-W 6.4 Quick Start Guide This document describes the initial setup of an Alcatel-Lucent user-centric network that consists of an Alcatel-Lucent switch and Alcatel-Lucent Access Points (APs). The installation
AOS-W 6.4 Quick Start Guide This document describes the initial setup of an Alcatel-Lucent user-centric network that consists of an Alcatel-Lucent switch and Alcatel-Lucent Access Points (APs). The installation
Lab 7.5.1: Basic Wireless Configuration
 Topology Diagram Learning Objectives Configure options in the Linksys Setup tab. Configure options in the Linksys Wireless tab. Configure options in the Linksys Administration tab. Configure options in
Topology Diagram Learning Objectives Configure options in the Linksys Setup tab. Configure options in the Linksys Wireless tab. Configure options in the Linksys Administration tab. Configure options in
Lab - Troubleshooting VLAN Configurations (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Chapter 9 Lab A: Configuring ASA Basic Settings and Firewall Using CLI
 A: Configuring ASA Basic Settings and Firewall Using CLI This lab has been updated for use on NETLAB+ Topology Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet interfaces. 2018
A: Configuring ASA Basic Settings and Firewall Using CLI This lab has been updated for use on NETLAB+ Topology Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet interfaces. 2018
PIX/ASA as a DHCP Server and Client Configuration Example
 PIX/ASA as a DHCP Server and Client Configuration Example Document ID: 70391 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure DHCP Server Configuration
PIX/ASA as a DHCP Server and Client Configuration Example Document ID: 70391 Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure DHCP Server Configuration
Getting Started. Getting Started with Your Platform Model. Factory Default Configurations CHAPTER
 CHAPTER 2 This chapter describes how to access the command-line interface, configure the firewall mode, and work with the configuration. This chapter includes the following sections: with Your Platform
CHAPTER 2 This chapter describes how to access the command-line interface, configure the firewall mode, and work with the configuration. This chapter includes the following sections: with Your Platform
To access the Startup Wizard, choose one of the following options: Wizards > Startup Wizard.
 This chapter describes the ASDM, which guides you through the initial configuration of the Cisco ASA and helps you define basic settings. Access the, on page 1 Guidelines for the, on page 1 Screens, on
This chapter describes the ASDM, which guides you through the initial configuration of the Cisco ASA and helps you define basic settings. Access the, on page 1 Guidelines for the, on page 1 Screens, on
Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION Topology Objectives Background Secure the server farm using private VLANs. Secure the staff VLAN from the student VLAN. Secure the
CCNPv7.1 SWITCH Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION Topology Objectives Background Secure the server farm using private VLANs. Secure the staff VLAN from the student VLAN. Secure the
PIX/ASA: PPPoE Client Configuration Example
 PIX/ASA: PPPoE Client Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram CLI Configuration ASDM Configuration
PIX/ASA: PPPoE Client Configuration Example Contents Introduction Prerequisites Requirements Components Used Related Products Conventions Configure Network Diagram CLI Configuration ASDM Configuration
Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3
 Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3 From Cisco s website, here are the minimum requirements for CCP 2.7 and CCP 2.8: The following info comes from many
Configuring GNS3 for CCNA Security Exam (for Windows) Software Requirements to Run GNS3 From Cisco s website, here are the minimum requirements for CCP 2.7 and CCP 2.8: The following info comes from many
cable modem dhcp proxy nat on Cisco Cable Modems
 cable modem dhcp proxy nat on Cisco Cable Modems Document ID: 12176 Contents Introduction Prerequisites Requirements Components Used Conventions Dynamic NAT Versus Static NAT Configuration Using cable
cable modem dhcp proxy nat on Cisco Cable Modems Document ID: 12176 Contents Introduction Prerequisites Requirements Components Used Conventions Dynamic NAT Versus Static NAT Configuration Using cable
Deployment of FireSIGHT Management Center on VMware ESXi
 Deployment of FireSIGHT Management Center on VMware ESXi Contents Introduction Prerequisites Components Used Configuration Deploy an OVF Template Power On and Complete Initialization Configure the Network
Deployment of FireSIGHT Management Center on VMware ESXi Contents Introduction Prerequisites Components Used Configuration Deploy an OVF Template Power On and Complete Initialization Configure the Network
Aruba Quick Start Guide
 Aruba Quick Start Guide Before you can access the Web-based Web UI tools, which is the primary configuration interface for Aruba Mobility Controllers, the switch must be configured with basic system information
Aruba Quick Start Guide Before you can access the Web-based Web UI tools, which is the primary configuration interface for Aruba Mobility Controllers, the switch must be configured with basic system information
Configuring Hybrid REAP
 13 CHAPTER This chapter describes hybrid REAP and explains how to configure this feature on controllers and access points. It contains the following sections: Information About Hybrid REAP, page 13-1,
13 CHAPTER This chapter describes hybrid REAP and explains how to configure this feature on controllers and access points. It contains the following sections: Information About Hybrid REAP, page 13-1,
Interfaces for Firepower Threat Defense
 This chapter includes Firepower Threat Defense interface configuration including Ethernet settings, EtherChannels, VLAN subinterfaces, IP addressing, and more. About Firepower Threat Defense Interfaces,
This chapter includes Firepower Threat Defense interface configuration including Ethernet settings, EtherChannels, VLAN subinterfaces, IP addressing, and more. About Firepower Threat Defense Interfaces,
Configuring DHCP for WLANs
 Finding Feature Information, page 1 Prerequisites for, page 1 Restrictions for, page 1 Information About the Dynamic Host Configuration Protocol, page 2 How to Configure DHCP for WLANs, page 4 Additional
Finding Feature Information, page 1 Prerequisites for, page 1 Restrictions for, page 1 Information About the Dynamic Host Configuration Protocol, page 2 How to Configure DHCP for WLANs, page 4 Additional
Managing Services Modules
 CHAPTER 58 This chapter describes how to manage the following module types: Security Services Cards (SSCs) Security Services Modules (SSMs) Security Services Processors (SSPs) Modules run advanced security
CHAPTER 58 This chapter describes how to manage the following module types: Security Services Cards (SSCs) Security Services Modules (SSMs) Security Services Processors (SSPs) Modules run advanced security
Lab 6-1 Configuring a WLAN Controller
 Lab 6-1 Configuring a WLAN Controller Topology Diagram Scenario In the next two labs, you will configure a wireless solution involving a router with a built-in WLAN controller, two lightweight wireless
Lab 6-1 Configuring a WLAN Controller Topology Diagram Scenario In the next two labs, you will configure a wireless solution involving a router with a built-in WLAN controller, two lightweight wireless
Cisco Wireless LAN Controller Module Feature Guide
 Cisco Wireless LAN Controller Module Feature Guide The Cisco wireless LAN (WLAN) controller module (WLCM) is designed to provide small and medium-sized businesses (SMBs) and enterprise branch office customers
Cisco Wireless LAN Controller Module Feature Guide The Cisco wireless LAN (WLAN) controller module (WLCM) is designed to provide small and medium-sized businesses (SMBs) and enterprise branch office customers
DHCP and DDNS Services
 This chapter describes how to configure the DHCP server or DHCP relay as well as dynamic DNS (DDNS) update methods. About, on page 1 Guidelines for, on page 3 Configure the DHCP Server, on page 4 Configure
This chapter describes how to configure the DHCP server or DHCP relay as well as dynamic DNS (DDNS) update methods. About, on page 1 Guidelines for, on page 3 Configure the DHCP Server, on page 4 Configure
WAP9112/9114 Quick Start Guide
 WAP9112/9114 Quick Start Guide Release 7.6 NN47252-308 Issue 02.01 March 2016 Contents Chapter 1: Introduction... 3 Chapter 2: Required Software Components... 4 Chapter 3: Installing or Upgrading Wireless
WAP9112/9114 Quick Start Guide Release 7.6 NN47252-308 Issue 02.01 March 2016 Contents Chapter 1: Introduction... 3 Chapter 2: Required Software Components... 4 Chapter 3: Installing or Upgrading Wireless
Lab - Configuring IPv6 Addresses on Network Devices
 Topology Addressing Table Device Interface IPv6 Address Prefix Length Default Gateway Objectives R1 G0/0 2001:DB8:ACAD:A::1 64 N/A G0/1 2001:DB8:ACAD:1::1 64 N/A S1 VLAN 1 2001:DB8:ACAD:1::B 64 N/A PC-A
Topology Addressing Table Device Interface IPv6 Address Prefix Length Default Gateway Objectives R1 G0/0 2001:DB8:ACAD:A::1 64 N/A G0/1 2001:DB8:ACAD:1::1 64 N/A S1 VLAN 1 2001:DB8:ACAD:1::B 64 N/A PC-A
DHCP Server RADIUS Proxy
 The Dynamic Host Configuration Protocol (DHCP) Server RADIUS Proxy is a RADIUS-based address assignment mechanism in which a DHCP server authorizes remote clients and allocates addresses based on replies
The Dynamic Host Configuration Protocol (DHCP) Server RADIUS Proxy is a RADIUS-based address assignment mechanism in which a DHCP server authorizes remote clients and allocates addresses based on replies
Console Server. Con. Cisco Aironet Port Figure 1: Aironet configuration
 Lab details At present C.6 has three Cisco Aironet 1200 access points, and three Linksys access points. The Cisco Aironets can be accessed through a console server using the console address and a specific
Lab details At present C.6 has three Cisco Aironet 1200 access points, and three Linksys access points. The Cisco Aironets can be accessed through a console server using the console address and a specific
Cisco Cloud Web Security Troubleshooting Guide
 Troubleshooting Guide Cisco Cloud Web Security Troubleshooting Guide 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 13 Contents Introduction... 3 Connectivity
Troubleshooting Guide Cisco Cloud Web Security Troubleshooting Guide 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 13 Contents Introduction... 3 Connectivity
Workgroup Bridges. Cisco WGBs. Information About Cisco Workgroup Bridges. Cisco WGBs, page 1 Third-Party WGBs and Client VMs, page 9
 Cisco WGBs, page 1 Third-Party WGBs and Client VMs, page 9 Cisco WGBs Information About Cisco A workgroup bridge (WGB) is a mode that can be configured on an autonomous IOS access point to provide wireless
Cisco WGBs, page 1 Third-Party WGBs and Client VMs, page 9 Cisco WGBs Information About Cisco A workgroup bridge (WGB) is a mode that can be configured on an autonomous IOS access point to provide wireless
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology
 Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Lab Configuring and Verifying Standard IPv4 ACLs (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
ISE Express Installation Guide. Secure Access How -To Guides Series
 ISE Express Installation Guide Secure Access How -To Guides Series Author: Jason Kunst Date: September 10, 2015 Table of Contents About this Guide... 4 How do I get support?... 4 Using this guide... 4
ISE Express Installation Guide Secure Access How -To Guides Series Author: Jason Kunst Date: September 10, 2015 Table of Contents About this Guide... 4 How do I get support?... 4 Using this guide... 4
Configuring the Eight-Port FXS RJ-21 Module
 CHAPTER 7 Configuring the Eight-Port FXS RJ-21 Module The Eight-port RJ-21 FXS Module is a high-density analog phone and fax relay interface. By providing service to analog phones and fax machines, the
CHAPTER 7 Configuring the Eight-Port FXS RJ-21 Module The Eight-port RJ-21 FXS Module is a high-density analog phone and fax relay interface. By providing service to analog phones and fax machines, the
Configuring VLANs CHAPTER
 CHAPTER 13 This chapter describes how to configure your access point/bridge to operate with the VLANs set up on your wired LAN. These sections describe how to configure your access point/bridge to support
CHAPTER 13 This chapter describes how to configure your access point/bridge to operate with the VLANs set up on your wired LAN. These sections describe how to configure your access point/bridge to support
Lab - Troubleshooting Connectivity Issues
 Lab - Troubleshooting Connectivity Issues Topology Addressing Table R1 ISP Objectives Device Interface IP Address Subnet Mask Default Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/0 10.1.1.1 255.255.255.252
Lab - Troubleshooting Connectivity Issues Topology Addressing Table R1 ISP Objectives Device Interface IP Address Subnet Mask Default Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/0 10.1.1.1 255.255.255.252
Lab Catalyst 2950T and 3550 Series Basic Setup
 Lab 1.2.9.1 Catalyst 2950T and 3550 Series Basic Setup Objective Configure a Cisco Catalyst 2950T or 3550 series Ethernet switch for the first time using the command-line interface (CLI) mode. Basic first
Lab 1.2.9.1 Catalyst 2950T and 3550 Series Basic Setup Objective Configure a Cisco Catalyst 2950T or 3550 series Ethernet switch for the first time using the command-line interface (CLI) mode. Basic first
Lab Configuring and Verifying Standard IPv4 ACLs Topology
 Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 10 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 10 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Configure the ASA for Dual Internal Networks
 Configure the ASA for Dual Internal Networks Document ID: 119195 Contributed by Dinkar Sharma, Bratin Saha, and Prashant Joshi, Cisco TAC Engineers. Aug 05, 2015 Contents Introduction Prerequisites Requirements
Configure the ASA for Dual Internal Networks Document ID: 119195 Contributed by Dinkar Sharma, Bratin Saha, and Prashant Joshi, Cisco TAC Engineers. Aug 05, 2015 Contents Introduction Prerequisites Requirements
Chapter 9 Lab A: Configuring ASA Basic Settings and Firewall Using CLI
 A: Configuring ASA Basic Settings and Firewall Using CLI Topology Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet interfaces. 2015 Cisco and/or its affiliates. All rights reserved.
A: Configuring ASA Basic Settings and Firewall Using CLI Topology Note: ISR G2 devices use GigabitEthernet interfaces instead of FastEthernet interfaces. 2015 Cisco and/or its affiliates. All rights reserved.
Lab Using the CLI to Gather Network Device Information Topology
 Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A Lo0 209.165.200.225 255.255.255.224 N/A S1 VLAN 1 192.168.1.11 255.255.255.0
Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.1.1 255.255.255.0 N/A Lo0 209.165.200.225 255.255.255.224 N/A S1 VLAN 1 192.168.1.11 255.255.255.0
Wireless Filtering and Firewalling
 Wireless Filtering and Firewalling Outline: The objective of this lab is demonstrate the principles of creating filtering rules on the wireless access point. At the start of the lab, the access point settings
Wireless Filtering and Firewalling Outline: The objective of this lab is demonstrate the principles of creating filtering rules on the wireless access point. At the start of the lab, the access point settings
Configuring Spanning Tree Protocol
 CHAPTER 7 This chapter descibes how to configure Spanning Tree Protocol (STP) on the Cisco wireless mobile interface card (WMIC). Note For complete syntax and usage information for the commands used in
CHAPTER 7 This chapter descibes how to configure Spanning Tree Protocol (STP) on the Cisco wireless mobile interface card (WMIC). Note For complete syntax and usage information for the commands used in
American Dynamics RAID Storage System iscsi Software User s Manual
 American Dynamics RAID Storage System iscsi Software User s Manual Release v2.0 April 2006 # /tmp/hello Hello, World! 3 + 4 = 7 How to Contact American Dynamics American Dynamics (800) 507-6268 or (561)
American Dynamics RAID Storage System iscsi Software User s Manual Release v2.0 April 2006 # /tmp/hello Hello, World! 3 + 4 = 7 How to Contact American Dynamics American Dynamics (800) 507-6268 or (561)
VMware ESX ESXi and vsphere. Installation Guide
 VMware ESX ESXi and vsphere Installation Guide UPDATED: 28 March 2018 Copyright Notices Copyright 2002-2018 KEMP Technologies, Inc. All rights reserved. KEMP Technologies and the KEMP Technologies logo
VMware ESX ESXi and vsphere Installation Guide UPDATED: 28 March 2018 Copyright Notices Copyright 2002-2018 KEMP Technologies, Inc. All rights reserved. KEMP Technologies and the KEMP Technologies logo
Interfaces for Firepower Threat Defense
 This chapter includes Firepower Threat Defense interface configuration including Ethernet settings, EtherChannels, VLAN subinterfaces, IP addressing, and more. About Firepower Threat Defense Interfaces,
This chapter includes Firepower Threat Defense interface configuration including Ethernet settings, EtherChannels, VLAN subinterfaces, IP addressing, and more. About Firepower Threat Defense Interfaces,
System Configuration. The following topics explain how to configure system configuration settings on Firepower Management Centers and managed devices:
 The following topics explain how to configure system configuration settings on Firepower Management Centers and managed devices: Introduction to, page 2 Appliance Information, page 5 Custom HTTPS Certificates,
The following topics explain how to configure system configuration settings on Firepower Management Centers and managed devices: Introduction to, page 2 Appliance Information, page 5 Custom HTTPS Certificates,
For more information, see "Provision APs for Mesh" on page 6 6. Connect your APs to the network. See "Install the APs" on page 6
 AOS-W 3.4.1 Quick Start Guide This document describes the initial setup of an Alcatel-Lucent user-centric network that consists of an Alcatel-Lucent switch and Alcatel-Lucent Access Points (APs). The installation
AOS-W 3.4.1 Quick Start Guide This document describes the initial setup of an Alcatel-Lucent user-centric network that consists of an Alcatel-Lucent switch and Alcatel-Lucent Access Points (APs). The installation
Securing Wireless LAN Controllers (WLCs)
 Securing Wireless LAN Controllers (WLCs) Document ID: 109669 Contents Introduction Prerequisites Requirements Components Used Conventions Traffic Handling in WLCs Controlling Traffic Controlling Management
Securing Wireless LAN Controllers (WLCs) Document ID: 109669 Contents Introduction Prerequisites Requirements Components Used Conventions Traffic Handling in WLCs Controlling Traffic Controlling Management
EAP FAST with the Internal RADIUS Server on the Autonomous Access Point Configuration Example
 EAP FAST with the Internal RADIUS Server on the Autonomous Access Point Configuration Example Document ID: 116580 Contributed by Surendra BG, Cisco TAC Engineer. Oct 10, 2013 Contents Introduction Prerequisites
EAP FAST with the Internal RADIUS Server on the Autonomous Access Point Configuration Example Document ID: 116580 Contributed by Surendra BG, Cisco TAC Engineer. Oct 10, 2013 Contents Introduction Prerequisites
Lab Configuring and Verifying Standard ACLs Topology
 Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
1 of :22
 Feedback: Help us help you Please rate this document. Excellent Good Average Fair Poor This document solved my problem. Yes No Just Browsing Suggestions to improve this document. (512 character limit)
Feedback: Help us help you Please rate this document. Excellent Good Average Fair Poor This document solved my problem. Yes No Just Browsing Suggestions to improve this document. (512 character limit)
Troubleshooting 1240AG Series Lightweight Access Points
 CHAPTER 4 Troubleshooting 1240AG Series Lightweight Access Points This chapter provides troubleshooting procedures for basic problems with the 1240AG series lightweight access point (AIR-LAP1242AG or AIR-LAP1242G).
CHAPTER 4 Troubleshooting 1240AG Series Lightweight Access Points This chapter provides troubleshooting procedures for basic problems with the 1240AG series lightweight access point (AIR-LAP1242AG or AIR-LAP1242G).
Configuring VLANs. Finding Feature Information. Prerequisites for VLANs
 Finding Feature Information, page 1 Prerequisites for VLANs, page 1 Restrictions for VLANs, page 2 Information About VLANs, page 2 How to Configure VLANs, page 7 Monitoring VLANs, page 19 Where to Go Next,
Finding Feature Information, page 1 Prerequisites for VLANs, page 1 Restrictions for VLANs, page 2 Information About VLANs, page 2 How to Configure VLANs, page 7 Monitoring VLANs, page 19 Where to Go Next,
LSI Industries AirLink Network Security. Best Practices. System Information 01/31/18. Physical Access. Software Updates. Network Encryption
 LSI Industries AirLink Network Security 01/31/18 Best Practices AirLink can provide all of its basic lighting control services without an internet connection. However, many customers will find that internet
LSI Industries AirLink Network Security 01/31/18 Best Practices AirLink can provide all of its basic lighting control services without an internet connection. However, many customers will find that internet
DHCP and DDNS Services
 This chapter describes how to configure the DHCP server or DHCP relay as well as dynamic DNS (DDNS) update methods. About, page 1 Guidelines for, page 3 Configure the DHCP Server, page 4 Configure the
This chapter describes how to configure the DHCP server or DHCP relay as well as dynamic DNS (DDNS) update methods. About, page 1 Guidelines for, page 3 Configure the DHCP Server, page 4 Configure the
Chapter 2 VLANs. CHAPTER 2 VLANs
 [ 52 ] Chapter 2 Beginning in Version 6.2 of the PIX firewall, there is support for subinterfaces, trunk links, and. The PIX and ASA can support 802.1q encapsulation and a number of logical interfaces
[ 52 ] Chapter 2 Beginning in Version 6.2 of the PIX firewall, there is support for subinterfaces, trunk links, and. The PIX and ASA can support 802.1q encapsulation and a number of logical interfaces
Lab - Troubleshooting ACL Configuration and Placement Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway HQ G0/1 192.168.1.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway HQ G0/1 192.168.1.1
LevelOne. Quick Installation Guide. WHG series Secure WLAN Controller. Introduction. Getting Started. Hardware Installation
 Introduction LevelOne WHG series Secure WLAN Controller LevelOne Secure WLAN Controller is the most advanced yet simple deployment and cost-effective wireless solution; it is an ideal security solution
Introduction LevelOne WHG series Secure WLAN Controller LevelOne Secure WLAN Controller is the most advanced yet simple deployment and cost-effective wireless solution; it is an ideal security solution
User Guide TL-R470T+/TL-R480T REV9.0.2
 User Guide TL-R470T+/TL-R480T+ 1910012468 REV9.0.2 September 2018 CONTENTS About This Guide Intended Readers... 1 Conventions... 1 More Information... 1 Accessing the Router Overview... 3 Web Interface
User Guide TL-R470T+/TL-R480T+ 1910012468 REV9.0.2 September 2018 CONTENTS About This Guide Intended Readers... 1 Conventions... 1 More Information... 1 Accessing the Router Overview... 3 Web Interface
Getting Started. About the ASA for Firepower How the ASA Works with the Firepower 2100
 This chapter describes how to deploy the ASA on the Firepower 2100 in your network, and how to perform initial configuration. About the ASA for Firepower 2100, page 1 Connect the Interfaces, page 4 Power
This chapter describes how to deploy the ASA on the Firepower 2100 in your network, and how to perform initial configuration. About the ASA for Firepower 2100, page 1 Connect the Interfaces, page 4 Power
VLANs over IP Unnumbered SubInterfaces
 The VLANs over IP Unnumbered Subinterfaces feature allows IP unnumbered interface support to be configured on Ethernet VLAN subinterfaces. This feature also provides support for DHCP on VLAN subinterfaces.
The VLANs over IP Unnumbered Subinterfaces feature allows IP unnumbered interface support to be configured on Ethernet VLAN subinterfaces. This feature also provides support for DHCP on VLAN subinterfaces.
Lab Manage AP Configuration and Image Files
 Lab 5.2.5 Manage AP Configuration and Image Files Estimated Time: 30 minutes Number of Team Members: Students will work in teams of two. Objective In this lab, the student will learn to manage configuration
Lab 5.2.5 Manage AP Configuration and Image Files Estimated Time: 30 minutes Number of Team Members: Students will work in teams of two. Objective In this lab, the student will learn to manage configuration
Lab Configure Basic AP security through GUI
 Lab 8.3.1.1 Configure Basic AP security through GUI Estimated Time: 30 minutes Number of Team Members: Students will work in teams of two. Objective In this lab, the student will learn the following objectives:
Lab 8.3.1.1 Configure Basic AP security through GUI Estimated Time: 30 minutes Number of Team Members: Students will work in teams of two. Objective In this lab, the student will learn the following objectives:
AOS-W 3.1. Quick Start Guide
 AOS-W 3.1 Quick Start Guide This document describes the initial setup of an Alcatel OmniAccess system that consists of a WLAN Switch and Alcatel Access Points (APs). The installation consists of the following
AOS-W 3.1 Quick Start Guide This document describes the initial setup of an Alcatel OmniAccess system that consists of a WLAN Switch and Alcatel Access Points (APs). The installation consists of the following
Skills Assessment Student Training
 Skills Assessment Student Training Topology Assessment Objectives Part 1: Initialize Devices (6 points, 5 minutes) Part 2: Configure Device Basic Settings (33 points, 20 minutes) Part 3: Configure Switch
Skills Assessment Student Training Topology Assessment Objectives Part 1: Initialize Devices (6 points, 5 minutes) Part 2: Configure Device Basic Settings (33 points, 20 minutes) Part 3: Configure Switch
Configure Firepower Threat Defense (FTD) Management Interface
 Configure Firepower Threat Defense (FTD) Management Interface Contents Introduction Prerequisites Requirements Components Used Background Information Configure Management Interface on ASA 5500-X Devices
Configure Firepower Threat Defense (FTD) Management Interface Contents Introduction Prerequisites Requirements Components Used Background Information Configure Management Interface on ASA 5500-X Devices
Configure the Cisco DNA Center Appliance
 Review Cisco DNA Center Configuration Wizard Parameters, page 1 Configure Cisco DNA Center Using the Wizard, page 5 Review Cisco DNA Center Configuration Wizard Parameters When Cisco DNA Center configuration
Review Cisco DNA Center Configuration Wizard Parameters, page 1 Configure Cisco DNA Center Using the Wizard, page 5 Review Cisco DNA Center Configuration Wizard Parameters When Cisco DNA Center configuration
Installing and Configuring vcloud Connector
 Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Installing and Configuring vcloud Connector vcloud Connector 2.6.0 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new
Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM
 Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM Topology Note: ISR G2 devices have Gigabit Ethernet interfaces instead of Fast Ethernet interfaces. All contents are Copyright 1992
Chapter 10 Lab B: Configuring ASA Basic Settings and Firewall Using ASDM Topology Note: ISR G2 devices have Gigabit Ethernet interfaces instead of Fast Ethernet interfaces. All contents are Copyright 1992
Lab 6-1 Configuring a WLAN Controller
 Lab 6-1 Configuring a WLAN Controller Topology Diagram Scenario Step 1 In the next two labs, you will configure a wireless solution involving a WLAN controller, two lightweight wireless access points,
Lab 6-1 Configuring a WLAN Controller Topology Diagram Scenario Step 1 In the next two labs, you will configure a wireless solution involving a WLAN controller, two lightweight wireless access points,
Lab Manage AP Configuration and Image Files
 Lab 5.2.5 Manage AP Configuration and Image Files Estimated Time: 30 minutes Number of Team Members: Students will work in teams of two. Objective In this lab, the student will learn to manage configuration
Lab 5.2.5 Manage AP Configuration and Image Files Estimated Time: 30 minutes Number of Team Members: Students will work in teams of two. Objective In this lab, the student will learn to manage configuration
CHAPTER 2 ACTIVITY
 CHAPTER 2 ACTIVITY 2.1.1.1 1. CLI stands for 2. GUI stands for 3. Write the step you used to go to CLI interface on Windows 4. The OS, normally loads from a disk drive, into RAM. 5. The portion of the
CHAPTER 2 ACTIVITY 2.1.1.1 1. CLI stands for 2. GUI stands for 3. Write the step you used to go to CLI interface on Windows 4. The OS, normally loads from a disk drive, into RAM. 5. The portion of the
Troubleshooting Lightweight Access Points
 CHAPTER 4 This chapter provides troubleshooting procedures for basic problems with the 1130AG series lightweight access point (model: AIR-LAP1131AG or AIR-LAP1131G). For the most up-to-date, detailed troubleshooting
CHAPTER 4 This chapter provides troubleshooting procedures for basic problems with the 1130AG series lightweight access point (model: AIR-LAP1131AG or AIR-LAP1131G). For the most up-to-date, detailed troubleshooting
Using the Cisco NCS Command-Line Interface
 CHAPTER 2 This chapter provides helpful tips for understanding and configuring the Cisco Prime Network Control System (NCS) from the command-line interface (CLI). The Cisco NCS can be deployed for small,
CHAPTER 2 This chapter provides helpful tips for understanding and configuring the Cisco Prime Network Control System (NCS) from the command-line interface (CLI). The Cisco NCS can be deployed for small,
CCNA Semester 2 labs. Labs for chapters 2 10
 CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
Lab - Connect to a Router for the First Time
 Introduction In this lab, you will configure basic settings on a wireless router. Recommended Equipment A computer with Windows installed An Ethernet NIC installed Wireless router Ethernet patch cable
Introduction In this lab, you will configure basic settings on a wireless router. Recommended Equipment A computer with Windows installed An Ethernet NIC installed Wireless router Ethernet patch cable
Using Cisco Workgroup Bridges
 Information About Cisco Workgroup Bridges, page 1 Restrictions for Cisco Workgroup Bridges, page 3 WGB Configuration Example, page 4 Viewing the Status of Workgroup Bridges (GUI), page 5 Viewing the Status
Information About Cisco Workgroup Bridges, page 1 Restrictions for Cisco Workgroup Bridges, page 3 WGB Configuration Example, page 4 Viewing the Status of Workgroup Bridges (GUI), page 5 Viewing the Status
Lab 6-1 Configuring a WLAN Controller
 Lab 6-1 Configuring a WLAN Controller Topology Diagram Scenario In the next two labs, you will configure a wireless solution involving a WLAN controller, two lightweight wireless access points, and a switched
Lab 6-1 Configuring a WLAN Controller Topology Diagram Scenario In the next two labs, you will configure a wireless solution involving a WLAN controller, two lightweight wireless access points, and a switched
Lab Configuring the PIX Security Appliance as a DHCP Server
 Lab 8.5.3 Configuring the PIX Security Appliance as a DHCP Server Objective Scenario Topology Estimated Time: 15 minutes Number of Team Members: Two teams with four students per team. In this lab, students
Lab 8.5.3 Configuring the PIX Security Appliance as a DHCP Server Objective Scenario Topology Estimated Time: 15 minutes Number of Team Members: Two teams with four students per team. In this lab, students
Deploying Cisco UCS Central
 This chapter includes the following sections: Obtaining the Cisco UCS Central Software from Cisco, page 1 Using the Cisco UCS Central OVA File, page 2 Using the Cisco UCS Central ISO File, page 4 Logging
This chapter includes the following sections: Obtaining the Cisco UCS Central Software from Cisco, page 1 Using the Cisco UCS Central OVA File, page 2 Using the Cisco UCS Central ISO File, page 4 Logging
