Stepping Stone to Car Hacking
|
|
|
- Deirdre Bradley
- 5 years ago
- Views:
Transcription
1 Stepping Stone to ar Hacking The Realistic Threat Model Movie
2 Liran Zwickel - Security researcher Who We Are nigmatos - Automotive yber Security Yannay Livneh - Security researcher Alex Fok TO
3 Agenda History State of the Art New Attack Vectors Applied Hacking
4 Legal Aspects of Automotive yber Research Digital Millennium opyright Act (DMA) - by President linton in 1998, generally prohibits modifying copyrighted software Section 1201 of the DMA effectively prohibits the reverse engineering of computer software for security research purposes, even if the researcher has purchased the software and owns the device October of 2015, the.s. opyright Office signed into law a new series of exemptions to the DMA that allow good-faith security research in a controlled environment designed to avoid any harm to individuals or to the public Due to a one-year delay in implementation, the DMA exemptions did not legally take effect until October 2016.
5 Automotive yber hallenges The number of known incidents is low pdates Distribution xpensive Long life cycle => low computation power Physical access protection is poor Lack of standardization
6 Attack Vectors SW pdates Vendror(S) loud Repair Shops Physical Intrusion Infotainment Wi-Fi\BT Telematics V2X ommunication TPMS OBD
7 ATOMOTIV YBR SRITY HALLNG omplete control through cellular. hrysler had to recall 1.4 M vehicles (2015) Ability to lock and unlock car as well as access to personal data through WiFi (2016) Autopilot & multiple car systems hacked through WiFi (2016) onnected onnected and Intelligent onnected and Super Intelligent
8 nhackable ars nhackable ars 1.1B 1.2B Hackable ars 65M Really?
9 Dumb is the New Smart s
10 AN Bus Automotive Networks Queen Selected Security challenges Lack of device authentication Lack of content authentication Who sent this message?
11 The Architecture VI OM loud Internet The Internet OBD
12 Vector Attacks Analysis - Yannay
13 nhackable
14 ar Hacking Objectives ontrol critical functions Sabotage Private information theft OM deception
15 The Architecture OM loud Internet The Internet O B D
16 The Architecture OM loud Internet The Internet O B D
17 Trust Model
18 Potential Attack Surfaces Internet Rogue ars
19 The Internets
20 Internet to loud Looks Promising Most objectives achieved Full scale OM loud Internet The Internet
21 Feasible IoT Old Machines Distributed Objectives: 1 hop away Internet to Repair Shop
22 Repair Shop to VI asy By design Badly Secured All objectives achieved O B D
23 Rogue ar
24 ar to VI asy, asy, asy All objectives achieved an it scale? O B D
25 Plan for Scale Rogue car attacks VI VI attacks car ar attacks another VI??? Profit
26 Weird Bonus Vectors
27 Trusted Input Direct Access VI to loud OM loud Internet The Internet
28 ar to loud O B D OM loud Internet The Internet
29 cosystem Research 101 OM loud web research VI embedded research ar AN and and stuff
30 Applied Hacking - Liran
31 Quick review VI (Diagnostic Device)
32 Quick review VI (Diagnostic Device)?
33 AN BS (OR: I have access to the car. Now what?)
34 AN? What is AN? Developed by Bosch in 1983 Standardized in 1993 by The ISO (International Organization for Standardization) Fast (p to 1Mbps) heap Reliable Yo! an you turn on the head lights? Yup. I m on it
35 AN? What is AN?
36 AN? What is AN?
37 AN Message Field name Length (bits) Purpose Start-of-frame 1 Denotes the start of frame transmission Identifier (green) 11 A (unique) identifier which also represents the message priority Remote transmission request (RTR) (blue) 1 Must be dominant (0) for data frames and recessive (1) for remote request frames (see Remote Frame, below) Identifier extension bit (ID) 1 Must be dominant (0) for base frame format with 11-bit identifiers Reserved bit (r0) 1 Reserved bit. Must be dominant (0), but accepted as either dominant or recessive. Data length code (DL) (yellow) 4 Number of bytes of data (0 8 bytes) [a] Data field (red) 0 64 (0-8 bytes) Data to be transmitted (length in bytes dictated by DL field) R 15 yclic redundancy check R delimiter 1 Must be recessive (1) AK slot 1 Transmitter sends recessive (1) and any receiver can assert a dominant (0) AK delimiter 1 Must be recessive (1) nd-of-frame (OF) 7 Must be recessive (1)
38 AN Message 123 # # fd 3e 3f 23 ff ff ff ff Dice nigmatos Research Software
39 AN Message Types Sensor Messages Rain Sensor Gear Mode Speed Seatbelt Sensor Its not raining Its not raining Its not raining Its raining! Actuators Turn on Washers Move Side Mirrors OK! Turn on those washers! onfigurations Lock doors in high speeds Disable the rain sensor!
40 Possible Attacks Actuators onfigurations - Starting the ngine - Disable Parking Sensor - Pressing the Breaks - Turning on Indicators - Pressing the Gas - Disable Reverse amera - Disabling ar Alerts (oil, water, etc) - Folding Side Mirrors - Starting Washers - Automatic Door Locking at High Speeds - Wasting all Washer Fluid (muhaha!) - etc - Automatic Breaks (according to motion sensor) - Infotainment Voltage Time After Switch-off - Automatic Washers Not good enough VI (Diagnostic Device) - nable Video in Motion - etc
41 onnecting To The AN Bus - OBD On-board diagnostics (OBD) is an automotive term referring to a vehicle's self-diagnostic and reporting capability. OBD Messages: - ngine RPM (0x) - Vehicle speed (0xD) - Throttle position (0x11) - ngine run time (0x7F)
42 DS Protocol nified Diagnostic Services (DS) is a diagnostic communication protocol in the electronic control unit () specific communication - Reset - Read DT Information - lear Diagnostic Information - Firmware pgrade
43 DS Firmware pgrade Diagnostic Session ontrol(0x2) Diagnostic Session ontrol(ak) Security Access Request Diagnostic Device Security Access hallenge (3d,1f,29,41) Security Access Response (1d,2f,9d,a1) Security Access Granted Bla bla Bla bla Bla bla Bla bla
44 DS Firmware pgrade Request Download Request Download(AK) Diagnostic Device Transfer Data Transfer Data Transfer Data Transfer xit Transfer xit(ak)
45 VI Version 1 VI Version 1 alculating (using a decoding function that is located on the device) Access Request hallenge Response
46 VI Version 2 Hey, give me the decode function for this specific decode function VI Version 2 alculating (using a decoding function received from the cloud) Access Request hallenge Response
47 Summary VI (Diagnostic Device)
48 Summary VI (Diagnostic Device)
49 Summary - Alex
50 The Architecture Internet OM loud The Internets O B D O B D n Server V2X
51 What Next? Further Vendors Research Solutions Short term bandage (Security Review, hardening) Long term implement vehicle security solutions ooperation, cooperation, cooperation
52 Questions @yannayli
53 Thank You
PENETRATION TESTING OF AUTOMOTIVE DEVICES. Dr. Ákos Csilling Robert Bosch Kft., Budapest HUSTEF 15/11/2017
 PENETRATION TESTING OF AUTOMOTIVE DEVICES Dr. Ákos Csilling Robert Bosch Kft., Budapest HUSTEF 15/11/2017 Imagine your dream car 2 Image: 2017 ESCRYPT. Exemplary attack demonstration only. This is NOT
PENETRATION TESTING OF AUTOMOTIVE DEVICES Dr. Ákos Csilling Robert Bosch Kft., Budapest HUSTEF 15/11/2017 Imagine your dream car 2 Image: 2017 ESCRYPT. Exemplary attack demonstration only. This is NOT
The House Intelligent Switch Control Network based On CAN bus
 The House Intelligent Switch Control Network based On CAN bus A.S.Jagadish Department Electronics and Telecommunication Engineering, Bharath University Abstract The Embedded Technology is now in its prime
The House Intelligent Switch Control Network based On CAN bus A.S.Jagadish Department Electronics and Telecommunication Engineering, Bharath University Abstract The Embedded Technology is now in its prime
MIGRATING TO CAN FD. Tony Adamson. Marketing Director CAN / LIN / FlexRay
 MIGRATING TO CAN FD Tony Adamson Marketing Director CAN / LIN / FlexRay Agenda WHO ARE WE CAR NETWORKS UNDER TRANSFORMATION SPEED SRITY OUR MISSION AND STRATEGY 2 2 FEBRUARY 16, 2016 VECTOR CAN FD SYMPOSIUM
MIGRATING TO CAN FD Tony Adamson Marketing Director CAN / LIN / FlexRay Agenda WHO ARE WE CAR NETWORKS UNDER TRANSFORMATION SPEED SRITY OUR MISSION AND STRATEGY 2 2 FEBRUARY 16, 2016 VECTOR CAN FD SYMPOSIUM
Sicherheitsaspekte für Flashing Over The Air in Fahrzeugen. Axel Freiwald 1/2017
 Sicherheitsaspekte für Flashing Over The Air in Fahrzeugen Axel Freiwald 1/2017 All OEMs Will Implement Software OTA As Soon As Possible IHS Study Motivation: Save on recalls caused by software bugs Evolution
Sicherheitsaspekte für Flashing Over The Air in Fahrzeugen Axel Freiwald 1/2017 All OEMs Will Implement Software OTA As Soon As Possible IHS Study Motivation: Save on recalls caused by software bugs Evolution
How to Hack Your Mini Cooper: Reverse Engineering CAN Messages on Passenger Automobiles
 How to Hack Your Mini Cooper: Reverse Engineering CAN Messages on Passenger Automobiles Jason Staggs Who is this guy? Jason Staggs Graduate Research Assistant Institute for Information Security (isec)
How to Hack Your Mini Cooper: Reverse Engineering CAN Messages on Passenger Automobiles Jason Staggs Who is this guy? Jason Staggs Graduate Research Assistant Institute for Information Security (isec)
Automotive Anomaly Monitors and Threat Analysis in the Cloud
 Automotive Anomaly Monitors and Threat Analysis in the Cloud Dr. André Weimerskirch Vector Automotive Cyber Security Symposium October 12, 2017 Cybersecurity Components Secure Internal & External Communications
Automotive Anomaly Monitors and Threat Analysis in the Cloud Dr. André Weimerskirch Vector Automotive Cyber Security Symposium October 12, 2017 Cybersecurity Components Secure Internal & External Communications
Development of Intrusion Detection System for vehicle CAN bus cyber security
 Development of Intrusion Detection System for vehicle CAN bus cyber security Anastasia Cornelio, Elisa Bragaglia, Cosimo Senni, Walter Nesci Technology Innovation - SSEC 14 Workshop Automotive SPIN Italia
Development of Intrusion Detection System for vehicle CAN bus cyber security Anastasia Cornelio, Elisa Bragaglia, Cosimo Senni, Walter Nesci Technology Innovation - SSEC 14 Workshop Automotive SPIN Italia
Preventing Cyber Attacks on Aftermarket Connectivity Solutions Zach Blumenstein, BD Director Argus Cyber Security
 Preventing Cyber Attacks on Aftermarket Connectivity Solutions Zach Blumenstein, BD Director Argus Cyber Security In less than a year, 100s of millions connected cars Aftermarket connectivity most prevalent
Preventing Cyber Attacks on Aftermarket Connectivity Solutions Zach Blumenstein, BD Director Argus Cyber Security In less than a year, 100s of millions connected cars Aftermarket connectivity most prevalent
Cybersecurity Challenges for Connected and Automated Vehicles. Robert W. Heller, Ph.D. Program Director R&D, Southwest Research Institute
 Cybersecurity Challenges for Connected and Automated Vehicles Robert W. Heller, Ph.D. Program Director R&D, Southwest Research Institute Cars are becoming complex (and CAV is only part of it) 1965: No
Cybersecurity Challenges for Connected and Automated Vehicles Robert W. Heller, Ph.D. Program Director R&D, Southwest Research Institute Cars are becoming complex (and CAV is only part of it) 1965: No
Controller area network
 Controller area network From Wikipedia, the free encyclopedia (Redirected from Controller area network) Controller area network (CAN or CAN-bus) is a vehicle bus standard designed to allow microcontrollers
Controller area network From Wikipedia, the free encyclopedia (Redirected from Controller area network) Controller area network (CAN or CAN-bus) is a vehicle bus standard designed to allow microcontrollers
Workshop on In Vehicle Network using CAN By
 Workshop on In Vehicle Network using CAN By Modern CAR Modern CAR INTRODUCTION 1. Controller Area Network (CAN) was initially created by German automotive system supplier Robert Bosch in the mid-1980s.
Workshop on In Vehicle Network using CAN By Modern CAR Modern CAR INTRODUCTION 1. Controller Area Network (CAN) was initially created by German automotive system supplier Robert Bosch in the mid-1980s.
Connect Vehicles: A Security Throwback
 Connect Vehicles: A Security Throwback Chris Valasek (@nudehaberdasher) Director of Vehicle Security Research Introduction Hello Chris Valasek Director of Vehicle Security Research IPS Dev -> Windows RE
Connect Vehicles: A Security Throwback Chris Valasek (@nudehaberdasher) Director of Vehicle Security Research Introduction Hello Chris Valasek Director of Vehicle Security Research IPS Dev -> Windows RE
Experimental Security Analysis of a Modern Automobile
 Experimental Security Analysis of a Modern Automobile Matthias Lange TU Berlin June 29th, 2010 Matthias Lange (TU Berlin) Experimental Security Analysis of a Modern Automobile June 29th, 2010 1 / 16 Paper
Experimental Security Analysis of a Modern Automobile Matthias Lange TU Berlin June 29th, 2010 Matthias Lange (TU Berlin) Experimental Security Analysis of a Modern Automobile June 29th, 2010 1 / 16 Paper
Diagnostic Trends 2017 An Overview
 Diagnostic Trends 2017 An Overview Vector India Conference, 2017-07-18+19 V1.0 2017-07-14 Agenda 1. DoIP 2. Remote Diagnostics 3. Cyber Security 4. Summary 2/29 DoIP Why DoIP? Why another diagnostic network?
Diagnostic Trends 2017 An Overview Vector India Conference, 2017-07-18+19 V1.0 2017-07-14 Agenda 1. DoIP 2. Remote Diagnostics 3. Cyber Security 4. Summary 2/29 DoIP Why DoIP? Why another diagnostic network?
Conquering Complexity: Addressing Security Challenges of the Connected Vehicle
 Conquering Complexity: Addressing Security Challenges of the Connected Vehicle October 3, 2018 Securely Connecting People, Applications, and Devices Ted Shorter Chief Technology Officer CSS Ted.Shorter@css-security.com
Conquering Complexity: Addressing Security Challenges of the Connected Vehicle October 3, 2018 Securely Connecting People, Applications, and Devices Ted Shorter Chief Technology Officer CSS Ted.Shorter@css-security.com
Automotive Attack Surfaces. UCSD and University of Washington
 Automotive Attack Surfaces UCSD and University of Washington Current Automotive Environment Modern cars are run by tens of ECUs comprising millions of lines of code ECUs are well connected over internal
Automotive Attack Surfaces UCSD and University of Washington Current Automotive Environment Modern cars are run by tens of ECUs comprising millions of lines of code ECUs are well connected over internal
Applied Automotive Engineering: Brian Herrold and Timothy Cleary May 16 th Pennsylvania State University
 Applied Automotive Engineering: Brian Herrold and Timothy leary May 16 th 2014 Pennsylvania State University Overview of This Module Introduction Vehicle Networking In-Vehicle Serial Data ommunication
Applied Automotive Engineering: Brian Herrold and Timothy leary May 16 th 2014 Pennsylvania State University Overview of This Module Introduction Vehicle Networking In-Vehicle Serial Data ommunication
Examining future priorities for cyber security management
 Examining future priorities for cyber security management Cybersecurity Focus Day Insurance Telematics 16 Andrew Miller Chief Technical Officer Thatcham Research Owned by the major UK Motor Insurers with
Examining future priorities for cyber security management Cybersecurity Focus Day Insurance Telematics 16 Andrew Miller Chief Technical Officer Thatcham Research Owned by the major UK Motor Insurers with
A Beginner s Guide to Controller Area Network Bus Access in Modern Vehicles
 Kennesaw State University From the SelectedWorks of Kevin McFall November 15, 2016 A Beginner s Guide to Controller Area Network Bus Access in Modern Vehicles Kevin McFall, Kennesaw State University T.
Kennesaw State University From the SelectedWorks of Kevin McFall November 15, 2016 A Beginner s Guide to Controller Area Network Bus Access in Modern Vehicles Kevin McFall, Kennesaw State University T.
Future Implications for the Vehicle When Considering the Internet of Things (IoT)
 Future Implications for the Vehicle When Considering the Internet of Things (IoT) FTF-AUT-F0082 Richard Soja Automotive MCU Systems Engineer A P R. 2 0 1 4 TM External Use Agenda Overview of Existing Automotive
Future Implications for the Vehicle When Considering the Internet of Things (IoT) FTF-AUT-F0082 Richard Soja Automotive MCU Systems Engineer A P R. 2 0 1 4 TM External Use Agenda Overview of Existing Automotive
Cyber Security and Vehicle Diagnostics. Mark Zachos DG Technologies
 Cyber Security and Vehicle Diagnostics Mark Zachos DG Technologies SAE INTERNATIONAL SAE J3061 Cybersecurity Guidebook for Cyber-Physical Automotive Systems Published January 2016; drive to a risk-based,
Cyber Security and Vehicle Diagnostics Mark Zachos DG Technologies SAE INTERNATIONAL SAE J3061 Cybersecurity Guidebook for Cyber-Physical Automotive Systems Published January 2016; drive to a risk-based,
SECURITY OF VEHICLE TELEMATICS SYSTEMS. Daniel Xiapu Luo Department of Computing The Hong Kong Polytechnic University
 SECURITY OF VEHICLE TELEMATICS SYSTEMS Daniel Xiapu Luo Department of Computing The Hong Kong Polytechnic University 1 2 3 TELEMATICS 4 TELEMATICS 5 OBD-II On-Board Diagnostic Perform emissions related
SECURITY OF VEHICLE TELEMATICS SYSTEMS Daniel Xiapu Luo Department of Computing The Hong Kong Polytechnic University 1 2 3 TELEMATICS 4 TELEMATICS 5 OBD-II On-Board Diagnostic Perform emissions related
CONTROLLER AREA NETWORK AS THE SECURITY OF THE VEHICLES
 INTERNATIONAL JOURNAL OF COMPUTER ENGINEERING & TECHNOLOGY (IJCET) Proceedings of the International Conference on Emerging Trends in Engineering and Management (ICETEM14) ISSN 0976 6367(Print) ISSN 0976
INTERNATIONAL JOURNAL OF COMPUTER ENGINEERING & TECHNOLOGY (IJCET) Proceedings of the International Conference on Emerging Trends in Engineering and Management (ICETEM14) ISSN 0976 6367(Print) ISSN 0976
AX200. Installation Guide
 Axxess Identification Ltd 27-28 Shrivenham Hundred Business Park, Watchfield, Swindon, Wiltshire SN6 8TZ United Kingdom Tel: +44 (0)1793 784002 Fax: +44 (0)1793 784005 Email: info@axxessid.com May 2008
Axxess Identification Ltd 27-28 Shrivenham Hundred Business Park, Watchfield, Swindon, Wiltshire SN6 8TZ United Kingdom Tel: +44 (0)1793 784002 Fax: +44 (0)1793 784005 Email: info@axxessid.com May 2008
WeVe: When Smart Wearables Meet Intelligent Vehicles
 WeVe: When Smart Wearables Meet Intelligent Vehicles Jiajia Liu School of Cyber Engineering, Xidian University, Xi an, China Smart wearables and intelligent vehicles constitute indispensable parts of Internet
WeVe: When Smart Wearables Meet Intelligent Vehicles Jiajia Liu School of Cyber Engineering, Xidian University, Xi an, China Smart wearables and intelligent vehicles constitute indispensable parts of Internet
IS CAR HACKING OVER? AUTOSAR SECURE ONBOARD COMMUNICATION
 SESSION ID: SBX3-W1 IS CAR HACKING OVER? AUTOSAR SECURE ONBOARD COMMUNICATION Jeffrey Quesnelle Director of Software Development Intrepid Control Systems @IntrepidControl Introduction Spent 15 years working
SESSION ID: SBX3-W1 IS CAR HACKING OVER? AUTOSAR SECURE ONBOARD COMMUNICATION Jeffrey Quesnelle Director of Software Development Intrepid Control Systems @IntrepidControl Introduction Spent 15 years working
OBD-II Diagnostic In this guide you will learn how to use our new feature OBD-II Diagnostic. And, specifically, how to set it up and use it in repair.
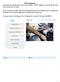 OBD-II Diagnostic In this guide you will learn how to use our new feature OBD-II Diagnostic. And, specifically, how to set it up and use it in repair. Keep in mind that the whole range of functionality
OBD-II Diagnostic In this guide you will learn how to use our new feature OBD-II Diagnostic. And, specifically, how to set it up and use it in repair. Keep in mind that the whole range of functionality
UNECE WP29/TFCS Regulation standards on threats analysis (cybersecurity) and OTA (software update)
 UNECE WP29/TFCS Regulation standards on threats analysis (cybersecurity) and OTA (software update) Koji NAKAO, NICT, Japan (Expert of UNECE WP29/TFCS) General Flow of works in WP29/TFCS and OTA Data protection
UNECE WP29/TFCS Regulation standards on threats analysis (cybersecurity) and OTA (software update) Koji NAKAO, NICT, Japan (Expert of UNECE WP29/TFCS) General Flow of works in WP29/TFCS and OTA Data protection
SGS CYBER SECURITY GROWTH OPPORTUNITIES
 SGS CYBER SECURITY GROWTH OPPORTUNITIES Eric Krzyzosiak GENERAL MANAGER DIGITAL Jeffrey Mc Donald Executive Vice President CERTIFICATION & BUSINESS ENHANCEMENT Eric Lee WIRELESS & CONSUMER RETAIL CYBER
SGS CYBER SECURITY GROWTH OPPORTUNITIES Eric Krzyzosiak GENERAL MANAGER DIGITAL Jeffrey Mc Donald Executive Vice President CERTIFICATION & BUSINESS ENHANCEMENT Eric Lee WIRELESS & CONSUMER RETAIL CYBER
13W-AutoSPIN Automotive Cybersecurity
 13W-AutoSPIN Automotive Cybersecurity Challenges and opportunities Alessandro Farsaci (CNH industrial) Cosimo Senni (Magneti Marelli) Milan, Italy November 12th, 2015 Agenda Automotive Cybersecurity Overview
13W-AutoSPIN Automotive Cybersecurity Challenges and opportunities Alessandro Farsaci (CNH industrial) Cosimo Senni (Magneti Marelli) Milan, Italy November 12th, 2015 Agenda Automotive Cybersecurity Overview
Communication in Automotive Networks Illustrated with an Example of Vehicle Stability Program: Part I - Control Area Network
 DOI 10.7603/s40707-013-0013-8 Communication in Automotive Networks Illustrated with an Example of Vehicle Stability Program: Part I - Control Area Network Grzejszczyk Elżbieta, Ph.D.eng. Docent, Electrical
DOI 10.7603/s40707-013-0013-8 Communication in Automotive Networks Illustrated with an Example of Vehicle Stability Program: Part I - Control Area Network Grzejszczyk Elżbieta, Ph.D.eng. Docent, Electrical
Automotive Cyber Security
 Automotive Cyber Security Rajeev Shorey (Ph.D.) Principal Scientist TCS Innovation Labs Cincinnati, USA & Bangalore, India Copyright 2013 Tata Consultancy Services Limited Connected Vehicles Chennai, 18
Automotive Cyber Security Rajeev Shorey (Ph.D.) Principal Scientist TCS Innovation Labs Cincinnati, USA & Bangalore, India Copyright 2013 Tata Consultancy Services Limited Connected Vehicles Chennai, 18
Agenda. About TRL. What is the issue? Security Analysis. Consequences of a Cyber attack. Concluding remarks. Page 2
 Security Insert the Vulnerabilities title of your of the presentation Connected here Car Presented Presented by by Peter Name Vermaat Here Principal Job Title ITS - Date Consultant 24/06/2015 Agenda 1
Security Insert the Vulnerabilities title of your of the presentation Connected here Car Presented Presented by by Peter Name Vermaat Here Principal Job Title ITS - Date Consultant 24/06/2015 Agenda 1
Lecture 2. Basics of networking in automotive systems: Network. topologies, communication principles and standardised protocols
 Lecture 2. Basics of networking in automotive systems: Network topologies, communication principles and standardised protocols Objectives Introduce basic concepts used in building networks for automotive
Lecture 2. Basics of networking in automotive systems: Network topologies, communication principles and standardised protocols Objectives Introduce basic concepts used in building networks for automotive
Securing the future of mobility
 Kaspersky Transportation System Security AVL Software and Functions Securing the future of mobility www.kaspersky.com #truecybersecurity Securing the future of mobility Connected car benefits The need
Kaspersky Transportation System Security AVL Software and Functions Securing the future of mobility www.kaspersky.com #truecybersecurity Securing the future of mobility Connected car benefits The need
The modern car has 100 million lines of code and over half of new vehicles will be connected by 2020.
 Automotive The modern car has 100 million lines of code and over half of new vehicles will be connected by 2020. Cars are becoming increasingly connected through a range of wireless networks The increased
Automotive The modern car has 100 million lines of code and over half of new vehicles will be connected by 2020. Cars are becoming increasingly connected through a range of wireless networks The increased
NC1701 ENHANCED VEHICLE COMMUNICATIONS CONTROLLER
 NC1701 ENHANCED VEHICLE COMMUNICATIONS CONTROLLER Nebula Systems has created the first dedicated controller for use in Telematics embedded systems, enabling companies in the Connected Car space to access
NC1701 ENHANCED VEHICLE COMMUNICATIONS CONTROLLER Nebula Systems has created the first dedicated controller for use in Telematics embedded systems, enabling companies in the Connected Car space to access
Connected Cars as the next great consumer electronics device
 Connected Cars as the next great consumer electronics device Sanjay Khatri Head of Platform Product Marketing Cisco Jasper 1992 2016 Cisco Systems, Inc. All rights reserved. Connected Cars: The next great
Connected Cars as the next great consumer electronics device Sanjay Khatri Head of Platform Product Marketing Cisco Jasper 1992 2016 Cisco Systems, Inc. All rights reserved. Connected Cars: The next great
Secure Ethernet Communication for Autonomous Driving. Jared Combs June 2016
 Secure Ethernet Communication for Autonomous Driving Jared Combs June 2016 Agenda Motivation for Security The Multi-Level Security Architecture Proposal Level 1: Restrict access to the network Level 2:
Secure Ethernet Communication for Autonomous Driving Jared Combs June 2016 Agenda Motivation for Security The Multi-Level Security Architecture Proposal Level 1: Restrict access to the network Level 2:
Embedded EtherNet/IP Option Card for DriveLogix 5730 Controllers
 Installation Instructions Embedded EtherNet/IP Option ard for DriveLogix 5730 ontrollers!!! TTENTION: To avoid an electric shock hazard, verify that the voltage on the bus capacitors has discharged before
Installation Instructions Embedded EtherNet/IP Option ard for DriveLogix 5730 ontrollers!!! TTENTION: To avoid an electric shock hazard, verify that the voltage on the bus capacitors has discharged before
Security Analysis of modern Automobile
 Security Analysis of modern Automobile Dixit Verma Department of Electrical & Computer Engineering Missouri University of Science and Technology dv6cb@mst.edu 20 Apr 2017 Outline Introduction Attack Surfaces
Security Analysis of modern Automobile Dixit Verma Department of Electrical & Computer Engineering Missouri University of Science and Technology dv6cb@mst.edu 20 Apr 2017 Outline Introduction Attack Surfaces
VIDA RELEASE NEWS ABOUT THIS DOCUMENT RELEASE: VIDA 2014C INFORMATION TO INDEPENDENT OPERATORS
 RELEASE: VIDA 2014C INFORMATION TO INDEPENDENT OPERATORS ABOUT THIS DOCUMENT... 1 INSTALLATION... 2 COMMUNICATION TOOL... 4 NEW CAR MODELS & INFORMATION... 4 START TAB... 4 VEHICLE PROFILE TAB... 5 INFORMATION
RELEASE: VIDA 2014C INFORMATION TO INDEPENDENT OPERATORS ABOUT THIS DOCUMENT... 1 INSTALLATION... 2 COMMUNICATION TOOL... 4 NEW CAR MODELS & INFORMATION... 4 START TAB... 4 VEHICLE PROFILE TAB... 5 INFORMATION
Communication Networks for the Next-Generation Vehicles
 Communication Networks for the, Ph.D. Electrical and Computer Engg. Dept. Wayne State University Detroit MI 48202 (313) 577-3855, smahmud@eng.wayne.edu January 13, 2005 4 th Annual Winter Workshop U.S.
Communication Networks for the, Ph.D. Electrical and Computer Engg. Dept. Wayne State University Detroit MI 48202 (313) 577-3855, smahmud@eng.wayne.edu January 13, 2005 4 th Annual Winter Workshop U.S.
Connected Car Solutions Based on IoT
 FEATURED ARTICLES Autonomous Driving Technology for Connected Cars Connected Car Solutions Based on IoT With the aim of achieving a prosperous society in which people and vehicles exist in harmony, the
FEATURED ARTICLES Autonomous Driving Technology for Connected Cars Connected Car Solutions Based on IoT With the aim of achieving a prosperous society in which people and vehicles exist in harmony, the
Countermeasures against Cyber-attacks
 Countermeasures against Cyber-attacks Case of the Automotive Industry Agenda Automotive Basics ECU, domains, CAN Automotive Security Motivation, trends Hardware and Software Security EVITA, SHE, HSM Secure
Countermeasures against Cyber-attacks Case of the Automotive Industry Agenda Automotive Basics ECU, domains, CAN Automotive Security Motivation, trends Hardware and Software Security EVITA, SHE, HSM Secure
Diesel Particulate Filter DPF Service Regeneration Table 1: Service Regeneration Successful Table 2: Service Regeneration Unsuccessful
 Service Information 2007 Chevrolet Silverado - 4WD [1GCHK23657F529413] Sierra, Silverado VIN C/K Service Manual Engine Engine Controls and Fuel - 6.6L LMM Diagnostic Information and Procedures Document
Service Information 2007 Chevrolet Silverado - 4WD [1GCHK23657F529413] Sierra, Silverado VIN C/K Service Manual Engine Engine Controls and Fuel - 6.6L LMM Diagnostic Information and Procedures Document
CAN bus and NMEA2000 1
 NMEA2000 relation to CAN and how Warwick Control can help Richard McLaughlin B.Sc., M.Sc., CEng Dr Chris Quigley Warwick Control NMEA Conference 2016, Naples, Florida CAN bus and NMEA2000 1 Company Profile
NMEA2000 relation to CAN and how Warwick Control can help Richard McLaughlin B.Sc., M.Sc., CEng Dr Chris Quigley Warwick Control NMEA Conference 2016, Naples, Florida CAN bus and NMEA2000 1 Company Profile
Linux in the connected car platform
 Linux in the connected car platform Background Long time desktop Linux user Designed several capes for the BeagleBone Black Currently an Embedded engineer for Dialexa What is a connected car anyway? A
Linux in the connected car platform Background Long time desktop Linux user Designed several capes for the BeagleBone Black Currently an Embedded engineer for Dialexa What is a connected car anyway? A
Application. Diagnosing the dashboard by the CANcheck software. Introduction
 Diagnosing the dashboard by the CANcheck software Introduction In recent years, vehicle electronics technology improved and advances day by day. A great of advanced electronic technology has been applied
Diagnosing the dashboard by the CANcheck software Introduction In recent years, vehicle electronics technology improved and advances day by day. A great of advanced electronic technology has been applied
IT-Security Challenges in the Internet of Things. Christian Graffer Product Manager Endian
 IT-Security Challenges in the Internet of Things Christian Graffer Product Manager Endian Who is Endian? Founded in 2003 at Bolzano, Italy, by a team of experienced network specialists and Linux enthusiasts
IT-Security Challenges in the Internet of Things Christian Graffer Product Manager Endian Who is Endian? Founded in 2003 at Bolzano, Italy, by a team of experienced network specialists and Linux enthusiasts
Automotive Cybersecurity: Why is it so Difficult? Steven W. Dellenback, Ph.D. Vice President R&D Intelligent Systems Division
 Automotive Cybersecurity: Why is it so Difficult? Steven W. Dellenback, Ph.D. Vice President R&D Intelligent Systems Division Cybersecurity is not one Entry Point Four Major Aspects of Cybersecurity How
Automotive Cybersecurity: Why is it so Difficult? Steven W. Dellenback, Ph.D. Vice President R&D Intelligent Systems Division Cybersecurity is not one Entry Point Four Major Aspects of Cybersecurity How
Security Concerns in Automotive Systems. James Martin
 Security Concerns in Automotive Systems James Martin Main Questions 1. What sort of security vulnerabilities do modern cars face today? 2. To what extent are external attacks possible and practical? Background
Security Concerns in Automotive Systems James Martin Main Questions 1. What sort of security vulnerabilities do modern cars face today? 2. To what extent are external attacks possible and practical? Background
WHITE PAPER. Decoupling Hardware from Software in the Next Generation of Connected Vehicles AUTOMOTIVE CONNECTIVITY
 WHITE PAPER Decoupling Hardware from Software in the Next Generation of Connected Vehicles AUTOMOTIVE CONNECTIVITY Contents DEMOCRATIZING VEHICLE SOFTWARE 3 UNDERSTANDING THE TRUE DEPTH & POTENTIAL OF
WHITE PAPER Decoupling Hardware from Software in the Next Generation of Connected Vehicles AUTOMOTIVE CONNECTIVITY Contents DEMOCRATIZING VEHICLE SOFTWARE 3 UNDERSTANDING THE TRUE DEPTH & POTENTIAL OF
M2MD Communications Gateway: fast, secure, efficient
 Solution Brief M2MD Communications Gateway: fast, secure, efficient G+D Mobile Security and M2MD enable automakers to improve user experience through fast, secure and efficient cellular automotive connectivity.
Solution Brief M2MD Communications Gateway: fast, secure, efficient G+D Mobile Security and M2MD enable automakers to improve user experience through fast, secure and efficient cellular automotive connectivity.
in London (United Kingdom) Sponsored by Motorola Semiconductor National Semiconductor Philips Semiconductors Organized by
 2 nd international CAN Conference icc 995 in London (United Kingdom) Sponsored by Motorola Semiconductor National Semiconductor Philips Semiconductors Organized by CAN in Automation (CiA) international
2 nd international CAN Conference icc 995 in London (United Kingdom) Sponsored by Motorola Semiconductor National Semiconductor Philips Semiconductors Organized by CAN in Automation (CiA) international
Autorama, Connecting Your Car to
 Autorama, Connecting Your Car to the Internet of Tomorrow Nicholas Sargologos, Senior Marketing Manager, Digital Networking Freescale Semiconductor Overview Automotive OEMs need a secure, managed process
Autorama, Connecting Your Car to the Internet of Tomorrow Nicholas Sargologos, Senior Marketing Manager, Digital Networking Freescale Semiconductor Overview Automotive OEMs need a secure, managed process
Autologic Technical Specifications JAGUAR
 Autologic Technical Specifications JAGUAR 1. JAGUAR PRODUCT DESCRIPTION The Autologic diagnostic tool for Jaguar vehicles is without doubt the most comprehensive tool to be made available to independent
Autologic Technical Specifications JAGUAR 1. JAGUAR PRODUCT DESCRIPTION The Autologic diagnostic tool for Jaguar vehicles is without doubt the most comprehensive tool to be made available to independent
from SCADA to IoT Cyber Security Bogdan Matache - Romania 2015
 from SCADA to IoT Cyber Security Bogdan Matache - Romania 2015 About ME, Bogdan Matache Cyber Security Specialist Military Technical Academy SCADA Security Specialist InfoSec Institute Auditor ISO 27001
from SCADA to IoT Cyber Security Bogdan Matache - Romania 2015 About ME, Bogdan Matache Cyber Security Specialist Military Technical Academy SCADA Security Specialist InfoSec Institute Auditor ISO 27001
EXPLOITING CLOUD SYNCHRONIZATION TO HACK IOTS
 SESSION ID: SBX1-R1 EXPLOITING CLOUD SYNCHRONIZATION TO HACK IOTS Alex Jay Balan Chief Security Researcher Bitdefender @jaymzu 2 IoT = hardware + OS + app (+ Cloud) wu-ftpd IIS5.0 RDP Joomla app 3 EDIMAX
SESSION ID: SBX1-R1 EXPLOITING CLOUD SYNCHRONIZATION TO HACK IOTS Alex Jay Balan Chief Security Researcher Bitdefender @jaymzu 2 IoT = hardware + OS + app (+ Cloud) wu-ftpd IIS5.0 RDP Joomla app 3 EDIMAX
The Future of Mobility
 The Future of Mobility Christoph Wagner The best way to predict the future is to design it. Buckminster Fuller The Future of Mobility Automated Connected Electrified Secured smooth traffic Early warning
The Future of Mobility Christoph Wagner The best way to predict the future is to design it. Buckminster Fuller The Future of Mobility Automated Connected Electrified Secured smooth traffic Early warning
Securing the Connected Car. Eystein Stenberg Product Manager Mender.io
 Securing the Connected Car Eystein Stenberg Product Manager Mender.io The software defined car Electronics Telematics Infotainment Connected Assisted driving Autonomous Hardware enabled Software enabled
Securing the Connected Car Eystein Stenberg Product Manager Mender.io The software defined car Electronics Telematics Infotainment Connected Assisted driving Autonomous Hardware enabled Software enabled
FlexRay and Automotive Networking Future
 FlexRay and Automotive Networking Future Chris Quigley Warwick Control Technologies Presentation Overview High Speed and High Integrity Networking Why FlexRay? CAN Problems Time Triggered Network Principles
FlexRay and Automotive Networking Future Chris Quigley Warwick Control Technologies Presentation Overview High Speed and High Integrity Networking Why FlexRay? CAN Problems Time Triggered Network Principles
Support cloud-based integration
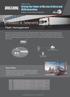 M2M series Driving the Future of Mission-Critical and M2M Innovation Support cloud-based integration M2 M Transport & Telematics Fleet Management We provide a total monitoring solution with On-Board Diagnostics
M2M series Driving the Future of Mission-Critical and M2M Innovation Support cloud-based integration M2 M Transport & Telematics Fleet Management We provide a total monitoring solution with On-Board Diagnostics
Options for collision shops to perform scan services independently
 Scan Tool and Services Overview for Pre-and Post-scanning Overview: Pre-and Post-scanning solutions available today for collision diagnostics vary widely for applications and capabilities. Some tools or
Scan Tool and Services Overview for Pre-and Post-scanning Overview: Pre-and Post-scanning solutions available today for collision diagnostics vary widely for applications and capabilities. Some tools or
Controller Area Network (CAN)
 Controller Area Network (CAN) EECS 461, Fall 2008 J. A. Cook J. S. Freudenberg 1 Introduction Up until now, we ve considered our embedded control system to be self-contained: an algorithm implemented in
Controller Area Network (CAN) EECS 461, Fall 2008 J. A. Cook J. S. Freudenberg 1 Introduction Up until now, we ve considered our embedded control system to be self-contained: an algorithm implemented in
Development Progress and OEM Perspective of C-V2X in China
 Development Progress and OEM Perspective of C-V2X in China Dr. Xiang Dang (ABM) Deputy General Manager Research& Advanced Technology Department SAIC MOTOR 1 C-V2X Development Progress in China 2 OEM s
Development Progress and OEM Perspective of C-V2X in China Dr. Xiang Dang (ABM) Deputy General Manager Research& Advanced Technology Department SAIC MOTOR 1 C-V2X Development Progress in China 2 OEM s
Christoph Schmittner, Zhendong Ma, Paul Smith
 FMVEA for Safety and Security Analysis of Intelligent and Cooperative Vehicles 1st International workshop on the Integration of Safety and Security Engineering (ISSE 14) Christoph Schmittner, Zhendong
FMVEA for Safety and Security Analysis of Intelligent and Cooperative Vehicles 1st International workshop on the Integration of Safety and Security Engineering (ISSE 14) Christoph Schmittner, Zhendong
Micronet SmartHub. Platform Datasheet. The Next Generation Rugged On-Board Computing Platform. Preliminary February, 2019.
 Micronet SmartHub Platform Datasheet The Next Generation Rugged On-Board Computing Platform March 2018 Preliminary February, 2019 Disclaimer: Micronet reserves the right to change product specifications
Micronet SmartHub Platform Datasheet The Next Generation Rugged On-Board Computing Platform March 2018 Preliminary February, 2019 Disclaimer: Micronet reserves the right to change product specifications
Second Encoder Option Card for PowerFlex 700S Drives with Phase II Control
 Installation Instructions Second Encoder Option ard for PowerFlex 700S Drives with Phase II ontrol!!! TTENTION: To avoid an electric shock hazard, verify that the voltage on the bus capacitors has discharged
Installation Instructions Second Encoder Option ard for PowerFlex 700S Drives with Phase II ontrol!!! TTENTION: To avoid an electric shock hazard, verify that the voltage on the bus capacitors has discharged
4G and 5G Cellular Technologies Enable Intelligent Transportation Use Cases
 4G and 5G Cellular Technologies Enable Intelligent Transportation Use Cases Martti Mustajärvi martti.mustajarvi@nokia.com Nokia Innovation Steering Principal Technologist 1 Nokia 2016 1 Our mission is
4G and 5G Cellular Technologies Enable Intelligent Transportation Use Cases Martti Mustajärvi martti.mustajarvi@nokia.com Nokia Innovation Steering Principal Technologist 1 Nokia 2016 1 Our mission is
Introduction to Controller Area Network (CAN)
 Introduction to Controller Area Network (CAN) 2003 Microchip Technology Incorporated. All Rights Reserved. Introduction to Controller Area Network (CAN) 1 Topics CAN Protocol Overview What is CAN? CAN
Introduction to Controller Area Network (CAN) 2003 Microchip Technology Incorporated. All Rights Reserved. Introduction to Controller Area Network (CAN) 1 Topics CAN Protocol Overview What is CAN? CAN
CONTROLLER AREA NETWORK (CAN) DEEP PACKET INSPECTION. Görkem Batmaz, Systems Engineer Ildikó Pete, Systems Engineer 28 th March, 2018
 CONTROLLER AREA NETWORK (CAN) DEEP PACKET INSPECTION Görkem Batmaz, Systems Engineer Ildikó Pete, Systems Engineer 28 th March, 2018 Car Hacking Immediately my accelerator stopped working. As I frantically
CONTROLLER AREA NETWORK (CAN) DEEP PACKET INSPECTION Görkem Batmaz, Systems Engineer Ildikó Pete, Systems Engineer 28 th March, 2018 Car Hacking Immediately my accelerator stopped working. As I frantically
RIOT and CAN. Vincent Dupont. RIOT Summit September 25-26, OTA keys. Vincent Dupont (OTA keys) RIOT and CAN RIOT Summit / 34
 RIOT and CAN Vincent Dupont OTA keys RIOT Summit September 25-26, 2017 Vincent Dupont (OTA keys) RIOT and CAN RIOT Summit 2017 1 / 34 Who am I? What is OTA keys? Me: Embedded software engineer: 6 years,
RIOT and CAN Vincent Dupont OTA keys RIOT Summit September 25-26, 2017 Vincent Dupont (OTA keys) RIOT and CAN RIOT Summit 2017 1 / 34 Who am I? What is OTA keys? Me: Embedded software engineer: 6 years,
M2MD Communications Gateway: fast, secure and efficient
 Solution Brief M2MD Communications Gateway: fast, secure and efficient Key Benefits G+D Mobile Security and M2MD enable automakers to improve user experience through fast, secure and efficient cellular
Solution Brief M2MD Communications Gateway: fast, secure and efficient Key Benefits G+D Mobile Security and M2MD enable automakers to improve user experience through fast, secure and efficient cellular
GPS+CAMTM. User Manual VS55020
 VS55020 GPS+CAMTM User Manual Congratulations on purchasing the Vision System. This innovative product integrates the functions of a front view car video recorder, a rear view monitoring system, and GPS
VS55020 GPS+CAMTM User Manual Congratulations on purchasing the Vision System. This innovative product integrates the functions of a front view car video recorder, a rear view monitoring system, and GPS
Building Digital Key Solution for Automotive
 Building Digital Key Solution for Automotive Content Overview Use Cases Unlocking Use Cases Key Provisioning Use Cases Key Sharing Use Cases Key Properties High Level Architecture and Related Standards
Building Digital Key Solution for Automotive Content Overview Use Cases Unlocking Use Cases Key Provisioning Use Cases Key Sharing Use Cases Key Properties High Level Architecture and Related Standards
Implementation and validation of SAE J1850 (VPW) protocol solution for diagnosis application
 Implementation and validation of SAE J1850 (VPW) protocol solution for diagnosis application Pallavi Pandurang Jadhav 1, Prof. S.N.Kore 2 1Department Of Electronics Engineering, Walchand College Of Engineering,
Implementation and validation of SAE J1850 (VPW) protocol solution for diagnosis application Pallavi Pandurang Jadhav 1, Prof. S.N.Kore 2 1Department Of Electronics Engineering, Walchand College Of Engineering,
OBD Auto Doctor. User Manual for ios (iphone and ipad) Copyright 2018 Creosys Ltd
 OBD Auto Doctor User Manual for ios (iphone and ipad) Copyright 2018 Creosys Ltd User Manual for ios (iphone and ipad) 1. Introduction 1.1 Platform and Hardware Requirements 1.2 Supported Adapters 1.3
OBD Auto Doctor User Manual for ios (iphone and ipad) Copyright 2018 Creosys Ltd User Manual for ios (iphone and ipad) 1. Introduction 1.1 Platform and Hardware Requirements 1.2 Supported Adapters 1.3
Security of Embedded Hardware Systems Insight into Attacks and Protection of IoT Devices
 Security of Embedded Hardware Systems Insight into Attacks and Protection of IoT Devices Dr. Johann Heyszl, Head of Hardware Security Department Fraunhofer-Institute for Applied and Integrated Security
Security of Embedded Hardware Systems Insight into Attacks and Protection of IoT Devices Dr. Johann Heyszl, Head of Hardware Security Department Fraunhofer-Institute for Applied and Integrated Security
Connected vehicle cloud Commercial presentation
 Connected vehicle cloud 17.1 Commercial presentation 2017.07.01 The evolution of the automotive industry 2017 2020 2025 2030 A vehicle can generate 1 GB of data per second By 2020 automakers could make
Connected vehicle cloud 17.1 Commercial presentation 2017.07.01 The evolution of the automotive industry 2017 2020 2025 2030 A vehicle can generate 1 GB of data per second By 2020 automakers could make
MASP Chapter on Safety and Security
 MASP Chapter on Safety and Security Daniel Watzenig Graz, Austria https://artemis.eu MASP Chapter on Safety & Security Daniel Watzenig daniel.watzenig@v2c2.at Francois Tuot francois.tuot@gemalto.com Antonio
MASP Chapter on Safety and Security Daniel Watzenig Graz, Austria https://artemis.eu MASP Chapter on Safety & Security Daniel Watzenig daniel.watzenig@v2c2.at Francois Tuot francois.tuot@gemalto.com Antonio
Security Challenges with ITS : A law enforcement view
 Security Challenges with ITS : A law enforcement view Central Observatory for Intelligent Transportation Systems FRENCH MINISTRY OF INTERIOR GENDARMERIE NATIONALE Colonel Franck MARESCAL franck.marescal@gendarmerie.interieur.gouv.fr
Security Challenges with ITS : A law enforcement view Central Observatory for Intelligent Transportation Systems FRENCH MINISTRY OF INTERIOR GENDARMERIE NATIONALE Colonel Franck MARESCAL franck.marescal@gendarmerie.interieur.gouv.fr
Securing the Connected Car. Eystein Stenberg CTO Mender.io
 Securing the Connected Car Eystein Stenberg CTO Mender.io The software defined car Electronics Telematics Infotainment Connected Assisted driving Autonomous Hardware enabled Software enabled Software defined
Securing the Connected Car Eystein Stenberg CTO Mender.io The software defined car Electronics Telematics Infotainment Connected Assisted driving Autonomous Hardware enabled Software enabled Software defined
Connected Car. Start Guide. Device by
 Connected Car Start Guide Device by Keep your family safe Receive real-time vehicle diagnostics Track the location of your car Stay connected with Wi-Fi LTE capable device Step 1 Check vehicle compatibility
Connected Car Start Guide Device by Keep your family safe Receive real-time vehicle diagnostics Track the location of your car Stay connected with Wi-Fi LTE capable device Step 1 Check vehicle compatibility
v.logic Intelligent Solution Interface V4-CCC
 v.logic Intelligent Solution Interface For the E-series BMW and Mini with navigation system or radio and 6.5 or 8.8 monitor with 10pin BMW LVDS connector Product features Plug and play media-controller
v.logic Intelligent Solution Interface For the E-series BMW and Mini with navigation system or radio and 6.5 or 8.8 monitor with 10pin BMW LVDS connector Product features Plug and play media-controller
Giancarlo Vasta, Magneti Marelli, Lucia Lo Bello, University of Catania,
 An innovative traffic management scheme for deterministic/eventbased communications in automotive applications with a focus on Automated Driving Applications Giancarlo Vasta, Magneti Marelli, giancarlo.vasta@magnetimarelli.com
An innovative traffic management scheme for deterministic/eventbased communications in automotive applications with a focus on Automated Driving Applications Giancarlo Vasta, Magneti Marelli, giancarlo.vasta@magnetimarelli.com
Automotive Gateway: A Key Component to Securing the Connected Car
 Automotive : A Key Component to Securing the Connected Car Introduction Building vehicles with gateways electronic devices that enable secure and reliable communications among a vehicle s electronic systems
Automotive : A Key Component to Securing the Connected Car Introduction Building vehicles with gateways electronic devices that enable secure and reliable communications among a vehicle s electronic systems
Chevrolet/GMC 8 MyLink Navigation Interface i05
 2013-2015 Chevrolet/GMC 8 MyLink Navigation Interface i05 S1C016A-Y03E And 2016-2018 Chevrolet/GMC 8 MyLink Navigation Interface i06 S1C016A-Y10E / S1C016A-Y13E Installation and User Manual Disclaimer
2013-2015 Chevrolet/GMC 8 MyLink Navigation Interface i05 S1C016A-Y03E And 2016-2018 Chevrolet/GMC 8 MyLink Navigation Interface i06 S1C016A-Y10E / S1C016A-Y13E Installation and User Manual Disclaimer
Release Date: September 4, 2014
 MV1DU User s Guide Release Date: September 4, 2014 Use of the MV1DU Diagnostic System requires an active license agreement or MV-1 Dealer Agreement. For information on obtaining a license, please email
MV1DU User s Guide Release Date: September 4, 2014 Use of the MV1DU Diagnostic System requires an active license agreement or MV-1 Dealer Agreement. For information on obtaining a license, please email
Restech. User Security AVOIDING LOSS GAINING CONFIDENCE IN THE FACE OF TODAY S THREATS
 Restech User Security AVOIDING LOSS GAINING CONFIDENCE IN THE FACE OF TODAY S THREATS Your presenter: Vince Gremillion, CISSP 30+ years technical and customer service experience Founder/Co-Owner RESTECH
Restech User Security AVOIDING LOSS GAINING CONFIDENCE IN THE FACE OF TODAY S THREATS Your presenter: Vince Gremillion, CISSP 30+ years technical and customer service experience Founder/Co-Owner RESTECH
Course Introduction. Purpose. Objectives. Content. Learning Time
 Course Introduction Purpose This training course provides an overview of Message Frames and hardware issues of the Controller Area Network (CAN) technology used to build networked, multiprocessor embedded
Course Introduction Purpose This training course provides an overview of Message Frames and hardware issues of the Controller Area Network (CAN) technology used to build networked, multiprocessor embedded
Functional Safety and Cyber-Security Experiences and Trends
 Functional Safety and Cyber-Security Experiences and Trends Dr. Christof Ebert, Vector Consulting Services V1.0 2017-12-11 Welcome Vector Consulting Services Experts for product development, product strategy
Functional Safety and Cyber-Security Experiences and Trends Dr. Christof Ebert, Vector Consulting Services V1.0 2017-12-11 Welcome Vector Consulting Services Experts for product development, product strategy
IoT as Enabling Technology for Smart Cities Panel PANEL IEEE RTSI
 IoT as Enabling Technology for Smart Cities Panel PANEL SESSION @ IEEE RTSI Torino, September 17, 2015, 8.30-10.00 Giuliana Gangemi, STMicroelectronics, giuliana.gangemi@st.com IoT Ecosystem 2 Sensors
IoT as Enabling Technology for Smart Cities Panel PANEL SESSION @ IEEE RTSI Torino, September 17, 2015, 8.30-10.00 Giuliana Gangemi, STMicroelectronics, giuliana.gangemi@st.com IoT Ecosystem 2 Sensors
WardsAuto Interiors Conference Creating the Ultimate User Experience
 Bitte decken Sie die schraffierte Fläche mit einem Bild ab. Please cover the shaded area with a picture. (24,4 x 11,0 cm) WardsAuto Interiors Conference Creating the Ultimate User Experience Scott Beutler,
Bitte decken Sie die schraffierte Fläche mit einem Bild ab. Please cover the shaded area with a picture. (24,4 x 11,0 cm) WardsAuto Interiors Conference Creating the Ultimate User Experience Scott Beutler,
Quick Start Guide Pre-and Post Scanning
 Quick Start Guide Pre-and Post Scanning Emerging Technologies Tools Subcommittee Chuck Olsen AirPro Diagnostics Table of Contents Pg- 1) Getting Started, Pre and Post Repair Scanning Pg- 4) Research &
Quick Start Guide Pre-and Post Scanning Emerging Technologies Tools Subcommittee Chuck Olsen AirPro Diagnostics Table of Contents Pg- 1) Getting Started, Pre and Post Repair Scanning Pg- 4) Research &
The Internet of Things. Steven M. Bellovin November 24,
 The Internet of Things Steven M. Bellovin November 24, 2014 1 What is the Internet of Things? Non-computing devices...... with CPUs... and connectivity (Without connectivity, it s a simple embedded system)
The Internet of Things Steven M. Bellovin November 24, 2014 1 What is the Internet of Things? Non-computing devices...... with CPUs... and connectivity (Without connectivity, it s a simple embedded system)
SHP-DH520. Samsung SDS Door Lock
 SHP-DH520 Samsung SDS Door Lock User and Reference Guide Ver1.0.0 Product Specifications Item Exterior Unit Size Interior Unit Voltage Emergency Power Source Battery Life Support Card Standard Spec. 77.4mm(W)
SHP-DH520 Samsung SDS Door Lock User and Reference Guide Ver1.0.0 Product Specifications Item Exterior Unit Size Interior Unit Voltage Emergency Power Source Battery Life Support Card Standard Spec. 77.4mm(W)
Abrites Diagnostics for Peugeot/Citroën User Manual
 Abrites Diagnostics for Peugeot/Citroën User Manual Version: 1.7 www.abrites.com Manual verion: 1.7 1 List of Revisions Date Chapter Description Revision 19.Oct.2010 ALL First version of the document.
Abrites Diagnostics for Peugeot/Citroën User Manual Version: 1.7 www.abrites.com Manual verion: 1.7 1 List of Revisions Date Chapter Description Revision 19.Oct.2010 ALL First version of the document.
Voertuigconstructeurs en data economie
 Voertuigconstructeurs en data economie STUDIEDAG VERKEERSVEILIGHEID VLAAMS HUIS VOOR DE VERKEERSVEILIGHEID DEPT MOW VLAAMS PARLEMENT, BRUSSEL 11 DECEMBER 2017 Saturday, 30 December 2017 AGENDA 1. Context
Voertuigconstructeurs en data economie STUDIEDAG VERKEERSVEILIGHEID VLAAMS HUIS VOOR DE VERKEERSVEILIGHEID DEPT MOW VLAAMS PARLEMENT, BRUSSEL 11 DECEMBER 2017 Saturday, 30 December 2017 AGENDA 1. Context
Features: Contents: If you are missing any of the above components please contact Racepak at
 -------------------------------------------------------------------------------------------- 250-DS-UDX -------------------------------------------------------------------------------------------- Features:
-------------------------------------------------------------------------------------------- 250-DS-UDX -------------------------------------------------------------------------------------------- Features:
