Data Extraction on MTK-based Android Mobile Phone Forensics
|
|
|
- Benjamin Russell
- 6 years ago
- Views:
Transcription
1 Journal of Digital Forensics, Security and Law Volume 10 Number 4 Article Data Extraction on MTK-based Android Mobile Phone Forensics Joe Kong The University of Hong Kong Follow this and additional works at: Part of the Computer Law Commons, and the Information Security Commons Recommended Citation Kong, Joe (2015) "Data Extraction on MTK-based Android Mobile Phone Forensics," Journal of Digital Forensics, Security and Law: Vol. 10 : No. 4, Article 3. DOI: Available at: This Article is brought to you for free and open access by the Journals at Scholarly Commons. It has been accepted for inclusion in Journal of Digital Forensics, Security and Law by an authorized administrator of Scholarly Commons. For more information, please contact commons@erau.edu. (c)adfsl
2 Data Extraction on MTK-Based Android Mobile Phone Forensics JDFSL V10N4 DATA EXTRACTION ON MTK-BASED ANDROID MOBILE PHONE FORENSICS Joe Kong Mphil Student in Computer Science The University of Hong Kong ABSTRACT In conducting criminal investigations it is quite common that forensic examiners need to recover evidentiary data from smartphones used by offenders. However, examiners encountered difficulties in acquiring complete memory dump from MTK Android phones, a popular brand of smartphones, due to a lack of technical knowledge on the phone architecture and that system manuals are not always available. This research will perform tests to capture data from MTK Android phone by applying selected forensic tools and compare their effectiveness by analyzing the extracted results. It is anticipated that a generic extraction tool, once identified, can be used on different brands of smartphones equipped with the same CPU chipset. Keywords: Mobile forensics, MTK Android phones, Android forensics, physical extraction, flash memory, MT6582 INTRODUCTION Smartphones are frequently used in cybercrimes or by offenders for coordinating their criminal activities as the device allows users to perform online communication and store personal or commercial information and data such as messages, s, documents, photographs, videos, GPS locations, etc. in a concentrated and portable form. Customized applications can also be downloaded and installed into smartphones to extend their functionalities. MediaTek ( MTK ) Android phones are frequently used in crime cases [1][2] because of its low selling price and high price / performance ratios of the CPU. The existing extraction tools, however, can only handle a limited number of MTK Android phones and the latest models are often not included [3]. This research attempts to explore a generic forensic tool that is applicable to these phone models and set up standard operational procedures for its implementation. The Current Problem Low and mid-range China-branded Android phones are growing popular in the Asian market. In this research paper extraction performance tests are conducted on the quadcore MT6582 processor [4], a processor chip which is used in more than 140 Android phone models [5]. Apparently live memory extraction and analysis is crucial to forensic examinations. Unlike examining a desktop or laptop computer, examiners may inadvertently modify the original device when capturing a full forensic image for data analysis as a mobile device does not have a standalone hard drive which can be shut down and disassemble from the phone without altering the data stored 2015 ADFSL Page 31
3 JDFSL V10N4 Data Extraction on MTK-Based Android Mobile Phone Forensics therein. For Android phones the extraction process is even more complicated owing to its ever-changing proprietary hardware as well as the vast variety of applications and security settings. Besides, Android versions, which users can download them from Google, are constantly updated. Thus examiners will need to carry out extensive testing and validation on the latest forensic toolkits. Extraction methodology Forensic tools used in extracting data from Android phones are largely supported by two methods: a. File System (logical) Acquisition it does not normally produce any deleted file and user s shell permission is required to run the file extraction process; and b. Physical Data Acquisition to make a bit-by-bit copy of the mobile device with maximum amount of deleted data or files recovered [3]. The process is similar to computer forensics and is widely used by forensic examiners. Either physical extraction [the boot preloader or Android Debug Bridge ( ADB ) options] or logical acquisition process (by copying from the backup mode) is able to extract data from MTK-based smartphones. As the two processes are regarded as less invasive to the physical phone when compared to the JTAG or Chip-off method, they are frequently used in forensic investigations. Besides, physical extraction has the benefit of recovering maximum amount of deleted data or files by copying bit-by-bit from physical flash memory storage [3] and its acquisition process can bypass the device s pattern locks or passcodes in many investigation cases [6]. The experiments conducted in this research are intended to identify an extraction method that suits best to MTK Android phone forensics. Objective of This Paper This paper will focus on the use of three extraction tools to capture complete memory dump of the phone under test. The competency and compatibility of these methods will be evaluated by comparing their test results. In summary the objectives set down for this project are: a. to conduct literature review pertaining to mobile forensics on MTK Android phones; b. based on the actual amount of forensic data acquired, to compare the test results on the application of forensic tools developed by different vendors and evaluate their effectiveness; and c. to identify a suitable extraction tool to cope with different brands of smartphones equipped with the same CPU chipset and review the best process for its use. Document Structure Chapter 2 provides literature review on researches conducted on Android forensics, in particular the MTK devices. Chapter 3 discusses the methodology. Chapter 4 outlines the implementation of extraction process by the three selected extraction tools. Chapter 5 compares the test results by referring to the forensic tools and methodology under test. Chapter 6 is the conclusion. It sums up the challenges to forensics conducted on MTK Android devices. It will also explore possible areas for future study in the mobile phone industry. Page ADFSL
4 Data Extraction on MTK-Based Android Mobile Phone Forensics JDFSL V10N4 PAST STUDY AND EXPERIENCE There are plenty of research studies on Android Forensics but only a few covers the realm of MTK Android Forensics. A list of the relevant works is listed here. Studies on Android Forensics In 2011 Joe Sylve introduced a tool on memory acquisition, the Droid Memory Dumper ( DMD ) [7], which captures a copy of the memory data, runs an address translation of each memory page and writes them to a TCP socket. The DMD module, however, has its restrictions: a. the ADB of the Android device has to be turned on in order for the DMD to tether data using network protocol via the virtual USB port; b. root privileges are to be executed in order to capture system data. In 2012 Ismael Valenzuela presented an enhanced module of the DMD, LiME Forensics, which is purportedly the first software to dump full contents of internal memory from an Android device [8]. The new tool requires the rooting of the device which may alter the state of the target phone and thus, casts doubt on the integrity of the evidentiary data so recovered. Lessard and Kessler (Lessard & Kessler, 2010) [9] investigated Android smartphones by acquiring a logical and physical image of the phone using dd command. They further used Cellebrite, a mobile forensic tool, to acquire the same image for comparing the two methods. In his research work, Timothy Vidas et al. (Vidas, Zhang & Christin, 2011) [10] made use of a custom recovery image to boot the device instead of loading the operating system. The recovered image can support functions like dumping the Flash Memory, allowing the execution of the su command to gain root access and adding some custom transfer binaries. The adb tool will collect data from the device and transfer them to a connecting computer via the USB port. Vijith Vijayan in his thesis, Android Forensic Capability and Evaluation of Extraction Tools [11], compared the effectiveness of logical extraction of two HTC Android phones by three mobile forensic tools. The test results however showed that a full memory dump could not be achieved. A Study on MTK Android Forensics MTK Android phones have a short product cycle as they are mostly designed for low-end to middle range products. A new phone model could have replaced the current one before analysis on its hardware specifications or system architecture is complete. Hence, there are few researches conducted on MTK forensics. After review it is found that China branded phone forensics was referred to in a research paper entitled Digital Forensic on MTK-based Shanzhai Mobile Phone with NAND Flash [12]. The authors uncovered 90% of the Shanzhai phones had been using the core processor, peripheral hardware prototype and software development platform of MTK or Spreadtrum. Nevertheless, their research confined only to extracting specific data such as locating file repository of phone books, call records, SMS and web-browsing records without obtaining a full memory dump. EXPERIMENT METHOD AND PROCEDURE Traditionally a number of forensic tools have been using the ADB as a communication interface to access the Android system via a 2015 ADFSL Page 33
5 JDFSL V10N4 Data Extraction on MTK-Based Android Mobile Phone Forensics computer installed with extraction software. In order to extract complete memory data, the Android device must be made available for super user privilege of access (also known as rooting the device ) [13] so that the examiner can make a copy of all system partitions and access files that are not originally accessible by normal users. The Android phone has to be powered up as usual and the USB Debugging mode turned on manually in the system menu of the phone. So if the mobile device is protected by power-on password or pattern lock, the extraction process cannot be executed. Alternatively the device can be put into the Download mode, a state in which the Flash Memory can be formatted and reprogrammed. The Flash Memory holds all binary information [which includes internal memory of the device, drivers, applications and other types of data in memory structure like Read Only Memory (ROM) and Non-Volatile Random Access Memory (NVRAM)] required for the device to boot up and function. With an unlocked bootloader which is commonly found in MTK Android phones, the Flash Memory can be reprogrammed in a way to establish connection of the target phone with any storage media. The above procedure is similar to computer forensics where a forensic boot disk is used to operate the cloning process for acquiring data from the target computer without affecting the original hard disk. The uniqueness of this method is that there is no need to rooting the device or enabling the USB Debugging mode before extraction, thereby resolve the difficult problem of accessing a password-protected phone. The entire process is forensically sound as it will not interfere with the internal storage of the device. In this experiment, Volcano Box has used the method of rooting the device while SP Flash Tools is an example of applying the Download mode. After making a physical copy of the mobile phone, the important task for an examiner is to identify the files that are of interest to the investigation. Message records and photos recovered will be searched to locate relevant files for the test process. The results will be analyzed to confirm the effectiveness of the methodology and the competency of the tools under test. Besides, the extracted data will be cross-referenced with the examination result conducted by the Cellebrite UFED ( Universal Forensic Extraction Device ) Touch [14]. Terminology SP Flash Tools [15] is an application that captures memory images or binary data from a mobile phone. It can erase phone data or modify codes / data and then write them back to the phone. The tool employs the boot ROM kernel library ( BROM_DLL ) and Download Agent ( DA ) program to download, read or erase files from the target phone s Flash Memory via a USB port connection. In practice, SP Flash Tools reads a length of memory from the target phone by using a scatter-file which begins at a start address and a given length. Each read back file is a continuous memory dump from the Flash Memory. Multiple blocks starting at different addresses can be read and copied into image files for storing in the forensic workstation. Volcano Box [16] supports a large number of MTK based phones including earlier feature phones to the latest Android phone models. It can capture internal information of the target phone, read / write flash, unlock user code, backup phone data and run those advanced features such as clear up the Flash Memory, repair IMEI, fix receive signals and read / write NVRAM files for MTK phones. It is in fact a tool designed for repairing, upgrading or modifying the phone system. Page ADFSL
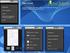
6 Data Extraction on MTK-Based Android Mobile Phone Forensics JDFSL V10N4 Cellebrite UFED is an expansive and wellknown forensic tool used in more than 60 countries. So far as the target device is on its support list, the auto-detection mechanism of the software can provide a step-by-step guide for the extraction process. For unlisted devices, UFED has also developed a generic profile to provide support. THE EXPERIMENT PROCESS The Lenovo A850 smartphone, being used for experiment, is equipped with MT6582 processor, a popular model in the MTK Android market and is installed with WhatsApp, Line and WeChat. To begin the process, a forensic workstation was set up and configured. Phone calls were made and photos taken in order to carry out the subsequent physical extraction for retrieving user s data. The Experiment on Lenovo A850 The mobile phone is running Android OS and the sequences of extraction process were as follows: Table 1. Image files extracted from Lenovo A850 a. Physical Extraction Using SP Flash Tools The phone was turned off initially. It turned on automatically when plugged into the USB port of the forensic workstation running the SP Flash Tools and started up the injected boot programs for the extraction process. A total number of 20 image files were extracted as listed in Table 1. The accumulated size of those saved files was 3,800,192KB. The phone was then turned off completely by taking out the battery. b. Physical Extraction Using Volcano Box The phone had been powered on with debugging mode enabled when plugged into the specific port of the physical Volcano Box (Picture 1). The Box was connected via USB cable to the forensic workstation running the corresponding software. The Backup EMMC option was used and one single image file with size 3,779,712KB had been extracted. The phone was then turned off completely by taking out the battery. Block Map (KB) Block Map (KB) Block Map (KB) android usrdata bootimg 6144 cache ebr1 512 ebr2 512 expdb logo 3072 mbr 512 misc 512 nvram 5120 preload preloader pro-info 3072 protect-f protect-s recovery 8192 sec_ro 6144 seccfg 128 uboot ADFSL Page 35
7 JDFSL V10N4 Data Extraction on MTK-Based Android Mobile Phone Forensics Picture 1. Cable connection using Volcano Box c. Physical Extraction Using Cellebrite UFED Touch The phone had been powered on with debugging mode enabled when plugged into the USB port of the physical Cellebrite UFED Touch. The device was connected via USB cable to the forensic workstation running the corresponding software. The Generic ADB for Chinese Android option was used and one single binary file with size 3,779,712KB had been extracted. A summary to show the memory size and files captured by the tools is shown at Table 2. EVALUATION In order to compare the test results of these three tools, the X-Ways Forensics [17], an integrated computer forensics software, was also used to mount the extracted images (for SP Flash Tools, only USR Data Image file and in the case of Volcano Box and Cellebrite, the full memory dump) from the experiment. The examination is confined to look at the user data partition of each mounted image, which purportedly contains application databases, event logs and user data for which forensic examiners are tasked to investigate information relating to criminal activities or leading to possible traces. Table 2. Test results of three extracted methods. Lenovo A850 SP Flash Tools Volcano Box Cellebrite UFED Image Size 3,800,192KB 3,779,712KB 3,779,712KB No. of Files in user partition 2,321 2,297 2,328 Page ADFSL
8 Data Extraction on MTK-Based Android Mobile Phone Forensics JDFSL V10N4 There were 20 image files recovered by SP Flash Tools. The table above shows that it has captured the largest image while the image size captured by Volcano Box and Cellebrite UFED is the same. It is noted that when the test process was conducted by Volcano Box and Cellebrite, system and application log files were created or modified whenever the phone was switched on for the extraction (this is a feature of the phone when data in memory are automatically altered once it is powered up). For instance, in the user partition, Cellebrite UFED image got 53 new files which were not found in Volcano Box and vice versa, Volcano Box had 23 new files not recovered by Cellebrite UFED image. These 76 files are system start-up event files. Besides, there are 1,173 common existing files which are different in size and they are all system log or application library files. All these files mentioned above were activated as part of the system boot up process without user s intervention. To further evaluate the results, UFED Physical Analyzer [18] was used to conduct user data carving from the acquired images (Table 3). Table 3. Comparison of data extracted among three tools Model:Lenovo A850 SP Flash Tool VolcanoBox Cellebrite UFED Analyzed Data Calender Call Log Chats Contacts Cookies Locations s Installed Applications Passwords Searched Items SMS Messages User Accounts Web Bookmarks Web History Wireless Networks Data Files Audio Images Videos ADFSL Page 37
9 JDFSL V10N4 Data Extraction on MTK-Based Android Mobile Phone Forensics Unlike single memory dump file captured by Volcano Box and Cellebrite UFED, SP Flash Tools acquired different image files according to the information on memory allocation recorded in the scatter-file. The decoding process was carried out on the USRData.img, Android.img and Preload.img files. In conclusion the three tools have produced the same result on the recovery of crucial data and files. In proving the merit of using a controlled boot program, SP Flash Tools were being used three times consecutively to acquire the USRData.img file from Lenovo A850. Having examined the mounted images using X-Ways Forensics, all the files and records extracted from these three extractions are found identical. It is fair to conclude that no file creation or modification has been made to the internal memory when the phone is booted up for data acquisition. CONCLUSION Based on the data analyzed in table 3, the three tools produce similar test results in retrieving data or files that are of interest to forensic investigations but SP Flash Tools provides more comprehensive steps for user operations and is considered to be highly adhered to the principle on digital forensics because: a. The tool can extract full range of data even if the phone is (i) password-locked; (ii) USB debugging mode is disabled; or (iii) in the absence of root access right. b. Data integrity of the mobile phone is maintained by taking control during the boot up process and suppresses the running of installed applications of the phone except relevant download agent for extraction, On the other hand, the other two forensic tools perform live extraction of data while the phone applications are running. c. The USRData.img file is acquired based on memory allocation information contained in the scatter-file. The analysis process is conducted more efficiently on the userland data when compared with the work conducted on full image dump extracted by other tools. d. The tool is open sourced and freeof-charge, i.e. incur no cost or recurrent charges on the extraction process, but its drawback lies with the lack of providing technical support on bug fixing or product development in future. e. The tool seamlessly provides an extraction method that can apply to all Android smartphones, irrespective of the phone brands or models (the upcoming models are also included), which are running on the same designated MTK based CPU chipsets. Currently, the tool supports 13 types of MTK processors in the market including the octa-core devices launched in Future Study The development in mobile forensics grows rapidly as new mobile devices with more powerful CPU and storage capacity are launching every day. Nevertheless, it is observed that forensic examiners are getting behind in exploring a competent forensic tool to extract full range of data from these devices. Efforts should be made to work out a comprehensive framework for researching applicable extraction method and evaluating mobile forensic toolkits which allows the Page ADFSL
10 Data Extraction on MTK-Based Android Mobile Phone Forensics JDFSL V10N4 extracted data, after analysis, is likely to be admissible as evidence in court proceedings. Low-end Android phones can be a useful device for offenders in view of their low price and that they can be easily disposed of either by destroying them physically or throwing them away. Past experience of forensic examinations has showed that physical extraction of data from these phones is not easy to achieve. In spite of this, considering these low-end Android phones could have used the same chips or similar form factors to cut cost, it is highly possible that a particular generic extraction tool, once identified, can be used on other CPU chipsets such as Qualcomm or the newer SnapDragon. Such extraction tool may assist in seamlessly gathering all objects and data structure from Android devices as well as bypass any hurdle created by password or encryption mechanism in an orderly manner. This will provide a good lead for conducting future study ADFSL Page 39
11 JDFSL V10N4 Data Extraction on MTK-Based Android Mobile Phone Forensics REFERENCES Kidnapping & extortion: Police ecstatic over toys to tackle cell phone crime, published in The Express Tribune, October 19, 2012, pping-extortion-police-ecstatic-over-toys-totackle-cell-phone-crime/ Investigating and analyzing the web-based contents on Chinese Shanzhai mobile phones, IEEE/SADFE 2012, 8/1/Content.pdf Det. Cynthia A. Murphy, Developing Process for Mobile Device Forensics, c/documents/mobile%20device%20forensi c%20process%20v3.0.pdf MediaTek from Wikipedia, MediaTek Top 140 quad-core MT6582 dual sim phones listed with specifications, GizChina.com, March 3, 2014, quad-core-mt6582-dual-sim-phoneslisted-specifications/ Persistent Challenges with Smartphone Forensics, Digital Forensic Investigator, February 8, 2013, 6-persistent-challenges-smartphoneforensics J. Sylve et al., Android Memory Capture and Applications for Security and Privacy, University of New Orleans Theses and Dissertations. Paper 1400, 2011, nt.cgi?article=2348&context=td Joseph T. Sylve, Android Memory Capture and Applications for Security and Privacy, University of New Orleans Theses and Dissertations, 2011, nt.cgi?article=2348&context=td Ismael Valenzuela, Acquiring volatile memory from Android based devices with LiME Forensics Part I, Ismael Valenzuela, April 23, 2012, /04/acquiring-volatile-memory-fromandroid.html Lessard J, Kessler G.C.,Android Forensics: Simplifying Cell Phone Examinations, ECU Publications Pre.2011, rticle=7480&context=ecuworks Vidas, Zhang & Christin, 2011, Toward a general collection methodology for Android devices, Vijith Vijayan, Android Forensic Capability and Evaluation of Extraction Tools, April 2012, d_forensic_capability_and_evaluation_ of_extraction_tools) Digital Forensic on MTK-based Shanzhai Mobile Phone with NAND Flash, ICDFI, Beijing, China 2012, _Mengfei_He_ICDFI2012.pdf FlashTool V Application Note, MediaTek, January 27,2009, _Application_Note.pdf UFED Touch Ultimate, Cellebrite, /brochures/ufed-touch-ultimate- ENGLISH-web.pdf Page ADFSL
12 Data Extraction on MTK-Based Android Mobile Phone Forensics JDFSL V10N4 SP Flash Tool + MediaTek MT65XX Drivers Download and Installation Guide including Bricked Devices, updated July 31, 2014, Volcano Box, X-Ways Forensics, UFED Physical Analyzer, Cellebrite, ADFSL Page 41
13 JDFSL V10N4 Data Extraction on MTK-Based Android Mobile Phone Forensics Page ADFSL
Android Forensics: Simplifying Cell Phone Examinations
 Android Forensics: Simplifying Cell Phone Examinations Jeff Lessard, Gary Kessler 2010 Presented By: Manaf Bin Yahya Outlines Introduction Mobile Forensics Physical analysis Logical analysis CelleBrite
Android Forensics: Simplifying Cell Phone Examinations Jeff Lessard, Gary Kessler 2010 Presented By: Manaf Bin Yahya Outlines Introduction Mobile Forensics Physical analysis Logical analysis CelleBrite
+ THE UFED ADVANTAGE DEVICE SUPPORT APPLICATION SUPPORT
 + + As the number of mobile devices grows, so does the volume and complexity of mobile device data. Rapid and timely deployment of the right mobile forensic tools to extract data quickly has never been
+ + As the number of mobile devices grows, so does the volume and complexity of mobile device data. Rapid and timely deployment of the right mobile forensic tools to extract data quickly has never been
Android Forensics. Presented By: Mohamed Khaled. Thanks to: Ibrahim Mosaad Mohamed Shawky
 Android Forensics Presented By: Mohamed Khaled Thanks to: Ibrahim Mosaad Mohamed Shawky Agenda Mobile Forensic Process Different Mobile Forensic Scenario Acquisition Guide Challenges of Android Forensics
Android Forensics Presented By: Mohamed Khaled Thanks to: Ibrahim Mosaad Mohamed Shawky Agenda Mobile Forensic Process Different Mobile Forensic Scenario Acquisition Guide Challenges of Android Forensics
MOBILedit Forensic Express
 MOBILedit Forensic Express All-in-one phone forensic tool from pioneers in the field MOBILedit Forensic Express is a phone and cloud extractor, data analyzer and report generator all in one solution. A
MOBILedit Forensic Express All-in-one phone forensic tool from pioneers in the field MOBILedit Forensic Express is a phone and cloud extractor, data analyzer and report generator all in one solution. A
CHALLENGES IN MOBILE FORENSICS TECHNOLOGY, METHODOLOGY, TRAINING, AND EXPENSE
 UDC 343.3/.7:340.6 Pregledni rad CHALLENGES IN MOBILE FORENSICS TECHNOLOGY, METHODOLOGY, TRAINING, AND EXPENSE American University in Bosnia & Herzegovina, BOSNIA & HERZEGOVINA, e-mail: edita.bajramovic@gmail.com
UDC 343.3/.7:340.6 Pregledni rad CHALLENGES IN MOBILE FORENSICS TECHNOLOGY, METHODOLOGY, TRAINING, AND EXPENSE American University in Bosnia & Herzegovina, BOSNIA & HERZEGOVINA, e-mail: edita.bajramovic@gmail.com
Running Head: IPHONE FORENSICS 1. iphone Forensics Jaclyn Sottilaro Monica Figueroa-Santos Antonina Spinella Saint Leo University
 Running Head: IPHONE FORENSICS 1 iphone Forensics Jaclyn Sottilaro Monica Figueroa-Santos Antonina Spinella Saint Leo University IPHONE FORENSICS 2 Abstract With an ever-growing evolution on technology,
Running Head: IPHONE FORENSICS 1 iphone Forensics Jaclyn Sottilaro Monica Figueroa-Santos Antonina Spinella Saint Leo University IPHONE FORENSICS 2 Abstract With an ever-growing evolution on technology,
Mobile Devices Villanova University Department of Computing Sciences D. Justin Price Spring 2014
 Mobile Devices Villanova University Department of Computing Sciences D. Justin Price Spring 2014 INTRODUCTION The field of computer forensics has long been centered on traditional media like hard drives.
Mobile Devices Villanova University Department of Computing Sciences D. Justin Price Spring 2014 INTRODUCTION The field of computer forensics has long been centered on traditional media like hard drives.
FORENSIC ANALYSIS OF WECHAT
 FORENSIC ANALYSIS OF WECHAT ON ANDROID SMARTPHONES Songyang Wu, Yong Zhang, Xupeng Wang, Xiong Xiong*, Lin Du Presented: Negamiye Arlene 2017 Nov 6th Content Introduction Related Works WeChat Forensics
FORENSIC ANALYSIS OF WECHAT ON ANDROID SMARTPHONES Songyang Wu, Yong Zhang, Xupeng Wang, Xiong Xiong*, Lin Du Presented: Negamiye Arlene 2017 Nov 6th Content Introduction Related Works WeChat Forensics
Forensic analysis of the android file system YAFFS2
 Edith Cowan University Research Online Australian Digital Forensics Conference Security Research Centre Conferences 2011 Forensic analysis of the android file system YAFFS2 Darren Quick University of South
Edith Cowan University Research Online Australian Digital Forensics Conference Security Research Centre Conferences 2011 Forensic analysis of the android file system YAFFS2 Darren Quick University of South
Incident Response Data Acquisition Guidelines for Investigation Purposes 1
 Incident Response Data Acquisition Guidelines for Investigation Purposes 1 1 Target Audience This document is aimed at general IT staff that may be in the position of being required to take action in response
Incident Response Data Acquisition Guidelines for Investigation Purposes 1 1 Target Audience This document is aimed at general IT staff that may be in the position of being required to take action in response
Survey on Android Forensic Tools and Methodologies
 Survey on Android Forensic Tools and Methodologies Venkateswara Rao V. CSE, UCEK, JNTUK Kakinada, India A. S. N. Chakravarthy CSE, UCEK, JNTUK Kakinada, India ABSTRACT In recent days, Android Operating
Survey on Android Forensic Tools and Methodologies Venkateswara Rao V. CSE, UCEK, JNTUK Kakinada, India A. S. N. Chakravarthy CSE, UCEK, JNTUK Kakinada, India ABSTRACT In recent days, Android Operating
Getting the best digital evidence is what matters XRY extracts more data faster, with full integrity
 Getting the best digital evidence is what matters XRY extracts more data faster, with full integrity Successful investigations rely on fast, high quality extraction of data from mobile phones. Without
Getting the best digital evidence is what matters XRY extracts more data faster, with full integrity Successful investigations rely on fast, high quality extraction of data from mobile phones. Without
Iphone 3g Factory Reset
 Iphone 3g Factory Reset Thank you very much for reading. As you may know, people have search numerous times for their chosen books like this, but end up in harmful downloads. Rather than reading a good
Iphone 3g Factory Reset Thank you very much for reading. As you may know, people have search numerous times for their chosen books like this, but end up in harmful downloads. Rather than reading a good
Intro. This program can retrieve messages, call logs, pictures, contacts, apps, calendar events, s, passwords, deleted data, and much more.
 FAQ Intro Thank you for purchasing MOBILedit Forensic Express. This tool preforms mobile phone content extractions and is used by professionals in law enforcement, military as well as the corporate and
FAQ Intro Thank you for purchasing MOBILedit Forensic Express. This tool preforms mobile phone content extractions and is used by professionals in law enforcement, military as well as the corporate and
Lamine Aouad, Tahar Kechadi, Justin Trentesaux and Nhien-An Le-Khac
 Chapter 11 AN OPEN FRAMEWORK FOR SMARTPHONE EVIDENCE ACQUISITION Lamine Aouad, Tahar Kechadi, Justin Trentesaux and Nhien-An Le-Khac Abstract The forensic processes and procedures for performing a bit-for-bit
Chapter 11 AN OPEN FRAMEWORK FOR SMARTPHONE EVIDENCE ACQUISITION Lamine Aouad, Tahar Kechadi, Justin Trentesaux and Nhien-An Le-Khac Abstract The forensic processes and procedures for performing a bit-for-bit
Getting the best digital evidence is what matters XRY extracts more data faster, with full integrity
 Getting the best digital evidence is what matters XRY extracts more data faster, with full integrity Successful investigations rely on fast, high quality extraction of data from mobile phones. Without
Getting the best digital evidence is what matters XRY extracts more data faster, with full integrity Successful investigations rely on fast, high quality extraction of data from mobile phones. Without
COMP116 Final Project. Shuyan Guo Advisor: Ming Chow
 Digital Forensics with ios Devices COMP116 Final Project Shuyan Guo Shuyan.guo@tufts.edu Advisor: Ming Chow Abstract This project focuses on ios device forensics. The study provides a general overview
Digital Forensics with ios Devices COMP116 Final Project Shuyan Guo Shuyan.guo@tufts.edu Advisor: Ming Chow Abstract This project focuses on ios device forensics. The study provides a general overview
Logical acquisition of iphone without Jail Breaking
 2018 IJSRST Volume 4 Issue 9 Print ISSN : 2395-6011 Online ISSN : 2395-602X Themed Section: Science and Technology Logical acquisition of iphone without Jail Breaking Priyank Parmar 1, Dr. Ravi Sheth 2
2018 IJSRST Volume 4 Issue 9 Print ISSN : 2395-6011 Online ISSN : 2395-602X Themed Section: Science and Technology Logical acquisition of iphone without Jail Breaking Priyank Parmar 1, Dr. Ravi Sheth 2
File Cover. Arrange your Gallery into different folder names. (Move your Camera or
 File Cover Arrange your Gallery into different folder names. (Move your Camera or Holiday Friends etc.) etc ) Download pictures into Holiday, Folder Organizer Group items according to labels and create
File Cover Arrange your Gallery into different folder names. (Move your Camera or Holiday Friends etc.) etc ) Download pictures into Holiday, Folder Organizer Group items according to labels and create
Operating System Specification Mac OS X Snow Leopard (10.6.0) or higher and Windows XP (SP3) or higher
 BlackLight is a multi-platform forensic analysis tool that allows examiners to quickly and intuitively analyze digital forensic media. BlackLight is capable of analyzing data from Mac OS X computers, ios
BlackLight is a multi-platform forensic analysis tool that allows examiners to quickly and intuitively analyze digital forensic media. BlackLight is capable of analyzing data from Mac OS X computers, ios
MPE+ Frequently Asked Questions & Troubleshooting
 MPE+ Frequently Asked Questions & Troubleshooting Version 7 (4.5.0.45078) 2011 AccessData Group, LLC Table of Contents Mobile Forensics Background Knowledge... 4 Q. What is the difference between Computer
MPE+ Frequently Asked Questions & Troubleshooting Version 7 (4.5.0.45078) 2011 AccessData Group, LLC Table of Contents Mobile Forensics Background Knowledge... 4 Q. What is the difference between Computer
Paraben s DS 7.5 Release Notes
 Paraben s DS 7.5 Release Notes Welcome to Paraben s DS Mobile Forensic Solution! DS is designed to allow investigators to acquire the data contained on mobile phones, smartphones, tablets, GPS, and PDA
Paraben s DS 7.5 Release Notes Welcome to Paraben s DS Mobile Forensic Solution! DS is designed to allow investigators to acquire the data contained on mobile phones, smartphones, tablets, GPS, and PDA
TomTom GPS Device Forensics
 TomTom GPS Device Forensics Written by Ben LeMere & Andy Sayers For more information visit GPSForensics.org blemere@gpsforensics.org asayers@gpsforensics.org Introduction: The sales of portable navigation
TomTom GPS Device Forensics Written by Ben LeMere & Andy Sayers For more information visit GPSForensics.org blemere@gpsforensics.org asayers@gpsforensics.org Introduction: The sales of portable navigation
Forensics on the Windows Platform, Part Two by Jamie Morris last updated February 11, 2003
 SecurityFocus HOME Infocus: Forensics on the Windows Platform, Part Two 2003-02-17 12:56:05-0900 SFOnline Forensics on the Windows Platform, Part Two by Jamie Morris last updated February 11, 2003 Introduction
SecurityFocus HOME Infocus: Forensics on the Windows Platform, Part Two 2003-02-17 12:56:05-0900 SFOnline Forensics on the Windows Platform, Part Two by Jamie Morris last updated February 11, 2003 Introduction
TestOut PC Pro - English 6.0.x COURSE OUTLINE. Modified
 TestOut PC Pro - English 6.0.x COURSE OUTLINE Modified 2019-01-02 TestOut PC Pro Outline - English 6.0.x Videos: 142 (17:10:32) Demonstrations: 144 (17:38:44) Simulations: 117 Fact Sheets: 189 Exams: 132
TestOut PC Pro - English 6.0.x COURSE OUTLINE Modified 2019-01-02 TestOut PC Pro Outline - English 6.0.x Videos: 142 (17:10:32) Demonstrations: 144 (17:38:44) Simulations: 117 Fact Sheets: 189 Exams: 132
Faheem, Muhammad; Le-Khac, Nhien-An; Kechadi, Tahar. Journal of Information Security, 5 :
 Provided by the author(s) and University College Dublin Library in accordance with publisher policies. Please cite the published version when available. Title Smartphone Forensic Analysis: A Case Study
Provided by the author(s) and University College Dublin Library in accordance with publisher policies. Please cite the published version when available. Title Smartphone Forensic Analysis: A Case Study
Android Forensics. Investigation, Analysis, Google Android. and Mobile Security for. Andrew Hoog. John McCash, Technical Editor SYNGRESS
 Android Forensics Investigation, Analysis, and Mobile Security for Google Android Andrew Hoog John McCash, Technical Editor AMSTERDAM BOSTON. HEIDELBERG LONDON NEW YORK OXFORD PARIS SAN DIEGO SAN FRANCISCO.
Android Forensics Investigation, Analysis, and Mobile Security for Google Android Andrew Hoog John McCash, Technical Editor AMSTERDAM BOSTON. HEIDELBERG LONDON NEW YORK OXFORD PARIS SAN DIEGO SAN FRANCISCO.
This version has been archived. Find the current version at on the Current Documents page. Archived Version. Capture of Live Systems
 Scientific Working Group on Digital Evidence Capture of Live Systems Disclaimer: As a condition to the use of this document and the information contained therein, the SWGDE requests notification by e-mail
Scientific Working Group on Digital Evidence Capture of Live Systems Disclaimer: As a condition to the use of this document and the information contained therein, the SWGDE requests notification by e-mail
Computer chip: A very small pieces of silicon or other semi-conducting material onto which integrated circuits are embedded Circuit board: A thin
 INTRODUCTION We can divide the parts that make up a computer into three broad categories or subsystem: the central processing unit (CPU), the main memory, and the input/output subsystem. The next three
INTRODUCTION We can divide the parts that make up a computer into three broad categories or subsystem: the central processing unit (CPU), the main memory, and the input/output subsystem. The next three
C HFI C HFI. EC-Council. EC-Council. Computer Hacking Forensic Investigator. Computer. Computer. Hacking Forensic INVESTIGATOR
 Page: 1 TM C HFI Computer C HFI Computer Hacking Forensic INVESTIGATOR Hacking Forensic INVESTIGATOR TM v8 v8 Page: 2 Be the leader. Deserve a place in the CHFI certified elite class. Earn cutting edge
Page: 1 TM C HFI Computer C HFI Computer Hacking Forensic INVESTIGATOR Hacking Forensic INVESTIGATOR TM v8 v8 Page: 2 Be the leader. Deserve a place in the CHFI certified elite class. Earn cutting edge
PDF LENOVO TAB 2 A7 20F
 01 July, 2018 PDF LENOVO TAB 2 A7 20F Document Filetype: PDF 459.12 KB 0 PDF LENOVO TAB 2 A7 20F Small and lightweight for easy, convenient use wherever you are The Lenovo Yoga 310-11IAP 11.6" 2 in. Tried
01 July, 2018 PDF LENOVO TAB 2 A7 20F Document Filetype: PDF 459.12 KB 0 PDF LENOVO TAB 2 A7 20F Small and lightweight for easy, convenient use wherever you are The Lenovo Yoga 310-11IAP 11.6" 2 in. Tried
A Study of User Data Integrity During Acquisition of Android Devices
 DIGITAL FORENSIC RESEARCH CONFERENCE By Namheun Son, Yunho Lee, Dohyun Kim, Joshua I. James, Sangjin Lee and Kyungho Lee Presented At The Digital Forensic Research Conference DFRWS 2013 USA Monterey, CA
DIGITAL FORENSIC RESEARCH CONFERENCE By Namheun Son, Yunho Lee, Dohyun Kim, Joshua I. James, Sangjin Lee and Kyungho Lee Presented At The Digital Forensic Research Conference DFRWS 2013 USA Monterey, CA
Digital Forensics Mobile Device Data Extraction. Crime Scene/Digital and Multimedia Division
 Mobile Device Data Extraction 12. MOBILE DEVICE DATA EXTRACTION PROCEDURE 12.1. Purpose 12.1.1. The purpose of this procedure is to extract data from mobile devices and/or removable media utilizing the
Mobile Device Data Extraction 12. MOBILE DEVICE DATA EXTRACTION PROCEDURE 12.1. Purpose 12.1.1. The purpose of this procedure is to extract data from mobile devices and/or removable media utilizing the
Course 832 EC-Council Computer Hacking Forensic Investigator (CHFI)
 Course 832 EC-Council Computer Hacking Forensic Investigator (CHFI) Duration: 5 days You Will Learn How To Understand how perimeter defenses work Scan and attack you own networks, without actually harming
Course 832 EC-Council Computer Hacking Forensic Investigator (CHFI) Duration: 5 days You Will Learn How To Understand how perimeter defenses work Scan and attack you own networks, without actually harming
Faculty of Computing,Sathyabama University, Chennai, Tamilnadu, India. Received on Accepted on
 ISSN: 0975-766X CODEN: IJPTFI Available Online through Research Article www.ijptonline.com EFFECTIVE ANDROID MOBILE ANTI-THEFT APPLICATION WITH CONTINUOUS TRACKING AND USER PROFILE RECORDING M. Ancy Rose
ISSN: 0975-766X CODEN: IJPTFI Available Online through Research Article www.ijptonline.com EFFECTIVE ANDROID MOBILE ANTI-THEFT APPLICATION WITH CONTINUOUS TRACKING AND USER PROFILE RECORDING M. Ancy Rose
Cellebrite Digital Forensics for Legal Professionals (CDFL)
 Global forensic training Course description Level Intermediate Length Two days (14 hours) Training Track Investigative The two-day Cellebrite Digital Forensics for Legal Professionals course is designed
Global forensic training Course description Level Intermediate Length Two days (14 hours) Training Track Investigative The two-day Cellebrite Digital Forensics for Legal Professionals course is designed
How To Access Iphone Backup Without Itunes Windows 7 Using
 How To Access Iphone Backup Without Itunes Windows 7 Using You can copy and save the data on your iphone, ipad, or ipod touch by backing up Read more about making backups of your device using itunes and
How To Access Iphone Backup Without Itunes Windows 7 Using You can copy and save the data on your iphone, ipad, or ipod touch by backing up Read more about making backups of your device using itunes and
AccessData Advanced Forensics
 This advanced five-day course provides the knowledge and skills necessary to install, configure and effectively use Forensic Toolkit (FTK ), FTK Imager Password Recovery Toolkit (PRTK ) and Registry Viewer.
This advanced five-day course provides the knowledge and skills necessary to install, configure and effectively use Forensic Toolkit (FTK ), FTK Imager Password Recovery Toolkit (PRTK ) and Registry Viewer.
REQUIRED TEXT: Mobile Phone Examiner Training Manual. Various articles and white papers. as assigned by instructor
 Course: CJ 4750 Small Devices Forensics Credit Hours: 3 credit hours Instructor: Joan Runs Through Office Phone: (435) 879-4420 Office Hours: TBA PREREQUISITES: CJ 2700 (CJ 3900 is highly recommended)
Course: CJ 4750 Small Devices Forensics Credit Hours: 3 credit hours Instructor: Joan Runs Through Office Phone: (435) 879-4420 Office Hours: TBA PREREQUISITES: CJ 2700 (CJ 3900 is highly recommended)
AccessData offers a broad array of training options.
 Forensics Training AccessData offers a broad array of training options. Our trainers have more than two centuries of cumulative experience in their respective fields. Take Advantage of the All Access Pass
Forensics Training AccessData offers a broad array of training options. Our trainers have more than two centuries of cumulative experience in their respective fields. Take Advantage of the All Access Pass
Forensic Analysis of Smartphones: The Android Data Extractor Lite (ADEL)
 Annual ADFSL Conference on Digital Forensics, Security and Law 2011 May 27th, 10:45 AM Forensic Analysis of Smartphones: The Android Data Extractor Lite (ADEL) Felix Freiling University of Erlangen-Nuremberg,
Annual ADFSL Conference on Digital Forensics, Security and Law 2011 May 27th, 10:45 AM Forensic Analysis of Smartphones: The Android Data Extractor Lite (ADEL) Felix Freiling University of Erlangen-Nuremberg,
Scientific Working Group on Digital Evidence
 SWGDE Best Practices for Mobile Device Evidence Collection & Preservation, The version of this document is in draft form and is being provided for comment by all interested parties for a minimum period
SWGDE Best Practices for Mobile Device Evidence Collection & Preservation, The version of this document is in draft form and is being provided for comment by all interested parties for a minimum period
Finding information on your computer
 Important Be sure to create recovery discs immediately after your computer is ready for use because there are no recovery discs provided with the computer. For instructions on how to create the recovery
Important Be sure to create recovery discs immediately after your computer is ready for use because there are no recovery discs provided with the computer. For instructions on how to create the recovery
Unlock bootloader samsung with odin
 Unlock bootloader samsung with odin Huawei Mate 20 Tidbits: Wireless Easy Projection, HiVision details, and more. When prompted by the phone, press the Volume Up key then continue to Part 2. I have tried
Unlock bootloader samsung with odin Huawei Mate 20 Tidbits: Wireless Easy Projection, HiVision details, and more. When prompted by the phone, press the Volume Up key then continue to Part 2. I have tried
AccessData Forensic Toolkit Release Notes
 AccessData Forensic Toolkit 6.2.1 Release Notes Document Date: 4/24/2017 2017 AccessData Group, Inc. All rights reserved Introduction This document lists the new features, fixed issues, and known issues
AccessData Forensic Toolkit 6.2.1 Release Notes Document Date: 4/24/2017 2017 AccessData Group, Inc. All rights reserved Introduction This document lists the new features, fixed issues, and known issues
User Operating Manual
 User Operating Manual Contents 1 Introduction... 1 1.1 Acknowledgements... 1 1.2 Safety Notice... 1 1.3 Abbreviation/term... 2 2 Brief Product Introduction... 3 2.1 Diagram for TABLET... 3 2.2 Introduction
User Operating Manual Contents 1 Introduction... 1 1.1 Acknowledgements... 1 1.2 Safety Notice... 1 1.3 Abbreviation/term... 2 2 Brief Product Introduction... 3 2.1 Diagram for TABLET... 3 2.2 Introduction
PrepAwayExam. High-efficient Exam Materials are the best high pass-rate Exam Dumps
 PrepAwayExam http://www.prepawayexam.com/ High-efficient Exam Materials are the best high pass-rate Exam Dumps Exam : 9L0-064 Title : OS X v10.8 Troubleshooting Exam Vendors : Apple Version : DEMO 1 /
PrepAwayExam http://www.prepawayexam.com/ High-efficient Exam Materials are the best high pass-rate Exam Dumps Exam : 9L0-064 Title : OS X v10.8 Troubleshooting Exam Vendors : Apple Version : DEMO 1 /
EPUB // SAMSUNG GALAXY 7500 ONLINE MANUAL DOWNLOAD
 06 January, 2019 EPUB // SAMSUNG GALAXY 7500 ONLINE MANUAL DOWNLOAD Document Filetype: PDF 165.6 KB 0 EPUB // SAMSUNG GALAXY 7500 ONLINE MANUAL DOWNLOAD Samsung GT-S7500 Galaxy Ace Plus complete Service
06 January, 2019 EPUB // SAMSUNG GALAXY 7500 ONLINE MANUAL DOWNLOAD Document Filetype: PDF 165.6 KB 0 EPUB // SAMSUNG GALAXY 7500 ONLINE MANUAL DOWNLOAD Samsung GT-S7500 Galaxy Ace Plus complete Service
ARM Security Solutions and Numonyx Authenticated Flash
 ARM Security Solutions and Numonyx Authenticated Flash How to integrate Numonyx Authenticated Flash with ARM TrustZone* for maximum system protection Introduction Through a combination of integrated hardware
ARM Security Solutions and Numonyx Authenticated Flash How to integrate Numonyx Authenticated Flash with ARM TrustZone* for maximum system protection Introduction Through a combination of integrated hardware
Contact Information. Contact Center Operating Hours. Other Contact Information. Contact Monday through Thursday Friday
 Contact Information Contact Center Operating Hours Contact Monday through Thursday Friday Phone: 1.801.796.0944 8 AM 5 PM Eastern Time 8 AM 3 PM Eastern Time Online chat: http://support.paraben.com 10
Contact Information Contact Center Operating Hours Contact Monday through Thursday Friday Phone: 1.801.796.0944 8 AM 5 PM Eastern Time 8 AM 3 PM Eastern Time Online chat: http://support.paraben.com 10
RE-ISSUE OF INVITATION FOR BIDS IN TWO BID SYSTEM FOR PROCUREMENT, INSTALLATION, MAINTENANCE AND TRAINING OF PORTABLE FORENSIC KITS AT MUMBAI.
 Request for proposal (RFP) Ref no;- Dated: 25 th September,2017 RE-ISSUE OF INVITATION FOR BIDS IN TWO BID SYSTEM FOR PROCUREMENT, INSTALLATION, MAINTENANCE AND TRAINING OF PORTABLE FORENSIC KITS AT MUMBAI.
Request for proposal (RFP) Ref no;- Dated: 25 th September,2017 RE-ISSUE OF INVITATION FOR BIDS IN TWO BID SYSTEM FOR PROCUREMENT, INSTALLATION, MAINTENANCE AND TRAINING OF PORTABLE FORENSIC KITS AT MUMBAI.
Kindle Forensics: Acquisition & Analysis
 Annual ADFSL Conference on Digital Forensics, Security and Law 2011 May 27th, 8:30 AM Kindle Forensics: Acquisition & Analysis Peter Hannay SECAU, School of Computer and Security Science, Edith Cowan University,
Annual ADFSL Conference on Digital Forensics, Security and Law 2011 May 27th, 8:30 AM Kindle Forensics: Acquisition & Analysis Peter Hannay SECAU, School of Computer and Security Science, Edith Cowan University,
FAQ s. 1. Device is frozen. Impossible to swipe finger on lock screen - Please either reboot or hard reset the device with below instructions
 FAQ s R500 1. Device is frozen. Impossible to swipe finger on lock screen - Please either reboot or hard reset the device with below instructions Reboot - Long press power button until device shuts down
FAQ s R500 1. Device is frozen. Impossible to swipe finger on lock screen - Please either reboot or hard reset the device with below instructions Reboot - Long press power button until device shuts down
1. Introduction P Package Contents 1.
 1 Contents 1. Introduction ------------------------------------------------------------------------------- P. 3-5 1.1 Package Contents 1.2 Tablet Overview 2. Using the Tablet for the first time ---------------------------------------------------
1 Contents 1. Introduction ------------------------------------------------------------------------------- P. 3-5 1.1 Package Contents 1.2 Tablet Overview 2. Using the Tablet for the first time ---------------------------------------------------
IRIS LLC Sample Interrogatories for Electronic Discovery. UNITED STATES DISTRICT COURT DISTRICT OF [Jurisdiction]
![IRIS LLC Sample Interrogatories for Electronic Discovery. UNITED STATES DISTRICT COURT DISTRICT OF [Jurisdiction] IRIS LLC Sample Interrogatories for Electronic Discovery. UNITED STATES DISTRICT COURT DISTRICT OF [Jurisdiction]](/thumbs/89/99588024.jpg) IRIS LLC Sample Interrogatories for Electronic Discovery UNITED STATES DISTRICT COURT DISTRICT OF [Jurisdiction] Court File No.: Plaintiff, INTERROGATORIES TO [Party Name v. Defendant, I. Definition. The
IRIS LLC Sample Interrogatories for Electronic Discovery UNITED STATES DISTRICT COURT DISTRICT OF [Jurisdiction] Court File No.: Plaintiff, INTERROGATORIES TO [Party Name v. Defendant, I. Definition. The
and Security Testing Shawn Valle gmail. com May 2013
 and Security Testing Shawn Valle shawnvalle @ gmail. com May 2013 Introductions 16 years in IT and security (CISSP, MCP, LCP) Co-established FFRDC s Mobile Security Practice in 2010, leading engineering
and Security Testing Shawn Valle shawnvalle @ gmail. com May 2013 Introductions 16 years in IT and security (CISSP, MCP, LCP) Co-established FFRDC s Mobile Security Practice in 2010, leading engineering
Paraben Device Seizure Version 4.3
 Paraben Device Seizure Version 4.3 E v a l u a t i o n R e p o r t July 2012 NIJ Electronic Crime Technology Center of Excellence 550 Marshall St., Suite B Phillipsburg, NJ 08865 www.ectcoe.org NIJ ECTCoE
Paraben Device Seizure Version 4.3 E v a l u a t i o n R e p o r t July 2012 NIJ Electronic Crime Technology Center of Excellence 550 Marshall St., Suite B Phillipsburg, NJ 08865 www.ectcoe.org NIJ ECTCoE
AccessData AD Lab Release Notes
 AccessData AD Lab 6.2.1 Release Notes Document Date: 4/24/2017 2017 AccessData Group, Inc. All rights reserved Introduction This document lists the new features, fixed issues, and known issues for this
AccessData AD Lab 6.2.1 Release Notes Document Date: 4/24/2017 2017 AccessData Group, Inc. All rights reserved Introduction This document lists the new features, fixed issues, and known issues for this
Learning IOS Forensics PDF
 Learning IOS Forensics PDF A practical hands-on guide to acquire and analyze ios devices with the latest forensic techniques and toolsabout This BookPerform logical, physical, and file system acquisition
Learning IOS Forensics PDF A practical hands-on guide to acquire and analyze ios devices with the latest forensic techniques and toolsabout This BookPerform logical, physical, and file system acquisition
Exploring Forensic Implications of the Fusion Drive
 Journal of Digital Forensics, Security and Law Volume 9 Number 2 Article 12 2014 Exploring Forensic Implications of the Fusion Drive Shruti Gupta Purdue University Marcus Rogers Purdue University Follow
Journal of Digital Forensics, Security and Law Volume 9 Number 2 Article 12 2014 Exploring Forensic Implications of the Fusion Drive Shruti Gupta Purdue University Marcus Rogers Purdue University Follow
Clockworkmod Won't Boot Into Recovery Droid X2
 Clockworkmod Won't Boot Into Recovery Droid X2 Entering and using recovery mode represents maybe the most common Android into recovery) is an official procedure, which means that you won't lose the stock
Clockworkmod Won't Boot Into Recovery Droid X2 Entering and using recovery mode represents maybe the most common Android into recovery) is an official procedure, which means that you won't lose the stock
9/20/2015. Cell Phone Data Retrieval and Its Legal Implications COPYRIGHT NOTICE
 Cell Phone Data Retrieval and Its Legal Implications COPYRIGHT NOTICE This presentation includes the creative works of others which are being used by permission, license or under a claim of fair use (17
Cell Phone Data Retrieval and Its Legal Implications COPYRIGHT NOTICE This presentation includes the creative works of others which are being used by permission, license or under a claim of fair use (17
central processing unit (CPU) software operating system (OS) input device output device
 central processing unit (CPU) Brain of the computer that performs instructions defined by software software Set of instructions that tells the hardware what to do. It is what guides the hardware and tells
central processing unit (CPU) Brain of the computer that performs instructions defined by software software Set of instructions that tells the hardware what to do. It is what guides the hardware and tells
Android Gingerbread Manually Update To Jelly Bean Features
 Android Gingerbread Manually Update To Jelly Bean 4.1.2 Features How to upgrade android 4.0, 4.1, 4.1.1, 4.1.2, 4.2.2 to 4.3 jellybean, 4.4, 4.4.1, 4.4.3, 4.4.4. Install latest Official Android 2.3.6 Gingerbread
Android Gingerbread Manually Update To Jelly Bean 4.1.2 Features How to upgrade android 4.0, 4.1, 4.1.1, 4.1.2, 4.2.2 to 4.3 jellybean, 4.4, 4.4.1, 4.4.3, 4.4.4. Install latest Official Android 2.3.6 Gingerbread
o Processor, disk space, and memory o Screen size and resolution o Certain testing accommodations
 Supported System Requirements for TABE Online Testing Effective October February 2019 This document describes the current system requirements for the DRC INSIGHT Online Learning System, including student-testing
Supported System Requirements for TABE Online Testing Effective October February 2019 This document describes the current system requirements for the DRC INSIGHT Online Learning System, including student-testing
Manual Android Tablet Samsung Galaxy 10.1 Note 10.1'' Wifi 3g 32gb
 Manual Android Tablet Samsung Galaxy 10.1 Note 10.1'' Wifi 3g 32gb Choose a Samsung Galaxy Note device most suited to you. The Samsung Galaxy Note 4 helps you be more productive and stay Galaxy Note (10.1,
Manual Android Tablet Samsung Galaxy 10.1 Note 10.1'' Wifi 3g 32gb Choose a Samsung Galaxy Note device most suited to you. The Samsung Galaxy Note 4 helps you be more productive and stay Galaxy Note (10.1,
Digital Cameras. An evaluation of the collection, preservation and evaluation of data collected from digital
 Ronald Prine CSC 589 - Digital Forensics New Mexico Institute of Mining and Technology October 17, 2006 Digital Cameras Executive Summary An evaluation of the collection, preservation and evaluation of
Ronald Prine CSC 589 - Digital Forensics New Mexico Institute of Mining and Technology October 17, 2006 Digital Cameras Executive Summary An evaluation of the collection, preservation and evaluation of
The following documents are included with your Sony VAIO computer.
 Documentation The following documents are included with your Sony VAIO computer. Printed Documentation Quick Start Guide Describes the process from unpacking to starting up your VAIO. Troubleshooting and
Documentation The following documents are included with your Sony VAIO computer. Printed Documentation Quick Start Guide Describes the process from unpacking to starting up your VAIO. Troubleshooting and
Vendor: CompTIA. Exam Code: Exam Name: CompTIA A+ Certification Exam (902) Version: Demo
 Vendor: CompTIA Exam Code: 220-902 Exam Name: CompTIA A+ Certification Exam (902) Version: Demo DEMO QUESTION 1 Which of the following best practices is used to fix a zero-day vulnerability on Linux? A.
Vendor: CompTIA Exam Code: 220-902 Exam Name: CompTIA A+ Certification Exam (902) Version: Demo DEMO QUESTION 1 Which of the following best practices is used to fix a zero-day vulnerability on Linux? A.
OPEN FORENSIC DEVICES
 Open Forensic Devices JDFSL V10N4 OPEN FORENSIC DEVICES Lee Tobin, Pavel Gladyshev DigitalFIRE ABSTRACT Cybercrime has been a growing concern for the past two decades. What used to be the responsibility
Open Forensic Devices JDFSL V10N4 OPEN FORENSIC DEVICES Lee Tobin, Pavel Gladyshev DigitalFIRE ABSTRACT Cybercrime has been a growing concern for the past two decades. What used to be the responsibility
Iconia One 8 B Copyright 2015 Acer. The information contained herein is subject to change without notice.
 Iconia One 8 B1-850 Copyright 2015 Acer. The information contained herein is subject to change without notice. ICONIA ONE LINEUP 1 Iconia One Android media tablet Super portable Colorful design Affordable
Iconia One 8 B1-850 Copyright 2015 Acer. The information contained herein is subject to change without notice. ICONIA ONE LINEUP 1 Iconia One Android media tablet Super portable Colorful design Affordable
Qpad X5 User Guide Hi-Target Surveying Instrument Co., Ltd. All Rights Reserved
 Qpad X5 User Guide Hi-Target Surveying Instrument Co., Ltd. All Rights Reserved Manual Revision Preface File number: Revision Date Revision Level Description 2016-06-03 1 Qpad X5 User Guide II Qpad X5
Qpad X5 User Guide Hi-Target Surveying Instrument Co., Ltd. All Rights Reserved Manual Revision Preface File number: Revision Date Revision Level Description 2016-06-03 1 Qpad X5 User Guide II Qpad X5
Running head: MOBILE FORENSICS 1
 Running head: MOBILE FORENSICS 1 Mobile Forensics Taylor Bauer, Jason Delaney, and Michael Lee COM-452-CA01 1 November 2018 MOBILE FORENSICS 2 Abstract Nowadays, many mobile devices have become a valuable
Running head: MOBILE FORENSICS 1 Mobile Forensics Taylor Bauer, Jason Delaney, and Michael Lee COM-452-CA01 1 November 2018 MOBILE FORENSICS 2 Abstract Nowadays, many mobile devices have become a valuable
COMPUTER HACKING Forensic Investigator
 COMPUTER HACKING Forensic Investigator H.H. Sheik Sultan Tower (0) Floor Corniche Street Abu Dhabi U.A.E www.ictd.ae ictd@ictd.ae Course Introduction: CHFIv8 presents a detailed methodological approach
COMPUTER HACKING Forensic Investigator H.H. Sheik Sultan Tower (0) Floor Corniche Street Abu Dhabi U.A.E www.ictd.ae ictd@ictd.ae Course Introduction: CHFIv8 presents a detailed methodological approach
BEAT 2.0 USER MANUAL
 BEAT 2.0 USER MANUAL FCC ID: 2ADLJBEAT20 The device complies with part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) This device may not cause harmful interference, and
BEAT 2.0 USER MANUAL FCC ID: 2ADLJBEAT20 The device complies with part 15 of the FCC Rules. Operation is subject to the following two conditions: (1) This device may not cause harmful interference, and
Guide to Computer Forensics and Investigations Fourth Edition. Chapter 2 Understanding Computer Investigations
 Guide to Computer Forensics and Investigations Fourth Edition Chapter 2 Understanding Computer Investigations Objectives Explain how to prepare a computer investigation Apply a systematic approach to an
Guide to Computer Forensics and Investigations Fourth Edition Chapter 2 Understanding Computer Investigations Objectives Explain how to prepare a computer investigation Apply a systematic approach to an
Matt Danner Flashback Data
 Preservation Strategies and Data Collection from a Forensic Expert's Point of View Best practices on executing preservation and administering collection protocols with emphasis on forensically sound methods
Preservation Strategies and Data Collection from a Forensic Expert's Point of View Best practices on executing preservation and administering collection protocols with emphasis on forensically sound methods
COURSE OUTLINE AND SCHEDULE: ASSIGNMENTS ARE DUE EACH MONDAY WEDNESDAY JANUARY Computing Overview
 COURSE OUTLINE AND SCHEDULE: ASSIGNMENTS ARE DUE EACH MONDAY WEDNESDAY JANUARY 22 1.0 Computing Overview 1.1 Course Introduction 1.1.1 PC Pro and A+ Certification (9:03) 1.2 Using the Simulator 1.2.1 Using
COURSE OUTLINE AND SCHEDULE: ASSIGNMENTS ARE DUE EACH MONDAY WEDNESDAY JANUARY 22 1.0 Computing Overview 1.1 Course Introduction 1.1.1 PC Pro and A+ Certification (9:03) 1.2 Using the Simulator 1.2.1 Using
Remote Device Mounting Service
 HOW TO USE REMOTE DEVICE MOUNTING SERVICES The Remote Data Mounting Services (RDMS) lets you acquire live evidence from active and remote network computers. You can gather many types of active information
HOW TO USE REMOTE DEVICE MOUNTING SERVICES The Remote Data Mounting Services (RDMS) lets you acquire live evidence from active and remote network computers. You can gather many types of active information
MOBILE DEVICE FORENSICS
 MOBILE DEVICE FORENSICS Smart phones and other handheld electronics have become an important part of our everyday lives and the ever changing technology is making these devices a major source of digital
MOBILE DEVICE FORENSICS Smart phones and other handheld electronics have become an important part of our everyday lives and the ever changing technology is making these devices a major source of digital
Iphone Factory Recovery Mode Fix Without >>>CLICK HERE<<<
 Iphone Factory Recovery Mode Fix Without Restoring 2013 Aug 30, 2013. Jason Louie Aug 28, 2013 8:49 PM Select your iphone, ipad, or ipod touch when it appears in itunes. I went into DFU mode following
Iphone Factory Recovery Mode Fix Without Restoring 2013 Aug 30, 2013. Jason Louie Aug 28, 2013 8:49 PM Select your iphone, ipad, or ipod touch when it appears in itunes. I went into DFU mode following
[FILE] WINDOWS SURFACE HARD RESET
![[FILE] WINDOWS SURFACE HARD RESET [FILE] WINDOWS SURFACE HARD RESET](/thumbs/82/85641197.jpg) 25 March, 2018 [FILE] WINDOWS SURFACE HARD RESET Document Filetype: PDF 296.76 KB 0 [FILE] WINDOWS SURFACE HARD RESET There are three ways to reset Surface. Microsoft Surface Hard Reset: Swipe in from
25 March, 2018 [FILE] WINDOWS SURFACE HARD RESET Document Filetype: PDF 296.76 KB 0 [FILE] WINDOWS SURFACE HARD RESET There are three ways to reset Surface. Microsoft Surface Hard Reset: Swipe in from
CompTIA A+ Accelerated course for & exams
 CompTIA A+ Accelerated course for 220-901 & 220-902 exams Course overview Target Audience This course is for Participants wishing to take and pass both CompTIA A+ exams (220-901 and 220-902) exam. It is
CompTIA A+ Accelerated course for 220-901 & 220-902 exams Course overview Target Audience This course is for Participants wishing to take and pass both CompTIA A+ exams (220-901 and 220-902) exam. It is
21 January, Acer Liquid E WISCBOOK // PDF \ PCGBFP2WRI. 21 January, 2018 [EPUB] ACER LIQUID E. Document Filetype: PDF 216.
![21 January, Acer Liquid E WISCBOOK // PDF \ PCGBFP2WRI. 21 January, 2018 [EPUB] ACER LIQUID E. Document Filetype: PDF 216. 21 January, Acer Liquid E WISCBOOK // PDF \ PCGBFP2WRI. 21 January, 2018 [EPUB] ACER LIQUID E. Document Filetype: PDF 216.](/thumbs/78/78772692.jpg) 21 January, 2018 [EPUB] ACER LIQUID E Document Filetype: PDF 216.04 KB 0 [EPUB] ACER LIQUID E Read reviews of the Acer Liquid M220 and shop online. Acer Liquid E3 price, specs, NDTV's Rating, Acer mobile
21 January, 2018 [EPUB] ACER LIQUID E Document Filetype: PDF 216.04 KB 0 [EPUB] ACER LIQUID E Read reviews of the Acer Liquid M220 and shop online. Acer Liquid E3 price, specs, NDTV's Rating, Acer mobile
Manual Update Android 4.3 Galaxy S4 Active S
 Manual Update Android 4.3 Galaxy S4 Active S At the time, the Samsung Galaxy S4 was running Android 4.2 Jelly Bean. Galaxy S4 has received a number of new software upgrades including Android 4.3 Jelly
Manual Update Android 4.3 Galaxy S4 Active S At the time, the Samsung Galaxy S4 was running Android 4.2 Jelly Bean. Galaxy S4 has received a number of new software upgrades including Android 4.3 Jelly
DATA DISASTER AVERTED! HOW TO BACK UP YOUR ANDROID SMARTPHONE
 DATA DISASTER AVERTED! HOW TO BACK UP YOUR ANDROID SMARTPHONE Planning ahead is the easiest way to make sure your data isn t lost to the ether, even if your phone is destroyed. Luckily, Google automatically
DATA DISASTER AVERTED! HOW TO BACK UP YOUR ANDROID SMARTPHONE Planning ahead is the easiest way to make sure your data isn t lost to the ether, even if your phone is destroyed. Luckily, Google automatically
Computer Systems. Communication (networks, radio links) Meatware (people, users don t forget them)
 Computers are useful machines, but they are generally useless by themselves. Computers are usually part of a system a computer system includes: Hardware (machines) Software (programs, applications) Communication
Computers are useful machines, but they are generally useless by themselves. Computers are usually part of a system a computer system includes: Hardware (machines) Software (programs, applications) Communication
ATV520 User Manual V1.1
 ATV520 User Manual V1.1 ATV520 Enjoy TV Box User Manual V1.0 Introduction The ATV520, also called Dual core Android TV box, is a box connected to your TV HDMI input that turn your TV to a multifunction
ATV520 User Manual V1.1 ATV520 Enjoy TV Box User Manual V1.0 Introduction The ATV520, also called Dual core Android TV box, is a box connected to your TV HDMI input that turn your TV to a multifunction
Android Forensics Concept
 Android Forensics Concept Written by Zlatko Jovanovic Widely use of personal handheld devices, opened the new area in computer forensics field, called phone, cell, or mobile forensics. In the last few
Android Forensics Concept Written by Zlatko Jovanovic Widely use of personal handheld devices, opened the new area in computer forensics field, called phone, cell, or mobile forensics. In the last few
Manual Android Jelly Bean Features Samsung Galaxy S3 Release Date
 Manual Android Jelly Bean Features Samsung Galaxy S3 Release Date The Samsung Galaxy S3 GT-I9300 variant running the Android 4.3 Jelly best-selling smartphones to date but the latest Android 4.3 Jelly
Manual Android Jelly Bean Features Samsung Galaxy S3 Release Date The Samsung Galaxy S3 GT-I9300 variant running the Android 4.3 Jelly best-selling smartphones to date but the latest Android 4.3 Jelly
SANDISK WIRELESS FLASH DRIVE MANUAL
 15 February, 2018 SANDISK WIRELESS FLASH DRIVE MANUAL Document Filetype: PDF 142.41 KB 0 SANDISK WIRELESS FLASH DRIVE MANUAL Available in multiple storage capacities, the 200GB variant of the stick is
15 February, 2018 SANDISK WIRELESS FLASH DRIVE MANUAL Document Filetype: PDF 142.41 KB 0 SANDISK WIRELESS FLASH DRIVE MANUAL Available in multiple storage capacities, the 200GB variant of the stick is
Financial CISM. Certified Information Security Manager (CISM) Download Full Version :
 Financial CISM Certified Information Security Manager (CISM) Download Full Version : http://killexams.com/pass4sure/exam-detail/cism required based on preliminary forensic investigation, but doing so as
Financial CISM Certified Information Security Manager (CISM) Download Full Version : http://killexams.com/pass4sure/exam-detail/cism required based on preliminary forensic investigation, but doing so as
Instructions For Formatting Hard Drive Windows 7 Command Prompt
 Instructions For Formatting Hard Drive Windows 7 Command Prompt How to format a hard drive in Windows Vista, 7 or 8: plus how to format hard drive drive, run the Universal USB Installer setup program,
Instructions For Formatting Hard Drive Windows 7 Command Prompt How to format a hard drive in Windows Vista, 7 or 8: plus how to format hard drive drive, run the Universal USB Installer setup program,
SSDD and SSDF Handset seizure Paraben * Seizure test SE K850, SE Xperia
 SSDD and SSDF Handset seizure Paraben * Seizure test SE K850, SE Xperia Small Scale Digital Device (SSDD) SSDD definition A Small Scale Digital Device is any of a variety of small form factor devices utilizing
SSDD and SSDF Handset seizure Paraben * Seizure test SE K850, SE Xperia Small Scale Digital Device (SSDD) SSDD definition A Small Scale Digital Device is any of a variety of small form factor devices utilizing
Vendor: ECCouncil. Exam Code: EC Exam Name: Computer Hacking Forensic Investigator Exam. Version: Demo
 Vendor: ECCouncil Exam Code: EC1-349 Exam Name: Computer Hacking Forensic Investigator Exam Version: Demo QUESTION 1 What is the First Step required in preparing a computer for forensics investigation?
Vendor: ECCouncil Exam Code: EC1-349 Exam Name: Computer Hacking Forensic Investigator Exam Version: Demo QUESTION 1 What is the First Step required in preparing a computer for forensics investigation?
Introduction to the Personal Computer
 Introduction to the Personal Computer 2.1 Describe a computer system A computer system consists of hardware and software components. Hardware is the physical equipment such as the case, storage drives,
Introduction to the Personal Computer 2.1 Describe a computer system A computer system consists of hardware and software components. Hardware is the physical equipment such as the case, storage drives,
How To Force Restore A Computer That Won Boot Up After System
 How To Force Restore A Computer That Won Boot Up After System If your computer won't start up normally, you may need to use a disk repair utility This can occur after an improper shutdown, forced restart,
How To Force Restore A Computer That Won Boot Up After System If your computer won't start up normally, you may need to use a disk repair utility This can occur after an improper shutdown, forced restart,
WYSE Academic Challenge Computer Science Test (State) 2014 Solution Set
 WYSE Academic Challenge Computer Science Test (State) 2014 Solution Set 1. Correct Answer: D Authentication involves verifying the user that will gain access to a system. The most common form of authentication
WYSE Academic Challenge Computer Science Test (State) 2014 Solution Set 1. Correct Answer: D Authentication involves verifying the user that will gain access to a system. The most common form of authentication
HUAWEI MediaPad T1 8.0 FAQ HUAWEI TECHNOLOGIES CO., LTD. Issue 01. Date 06/30
 HUAWEI MediaPad T1 8.0 FAQ Issue 01 Date 06/30 HUAWEI TECHNOLOGIES CO., LTD. 1 System and update... 1-1 1.1 Why does my HUAWEI MediaPad T1 8.0 constantly crash?... 1-1 1.2 Will data be erased if I update
HUAWEI MediaPad T1 8.0 FAQ Issue 01 Date 06/30 HUAWEI TECHNOLOGIES CO., LTD. 1 System and update... 1-1 1.1 Why does my HUAWEI MediaPad T1 8.0 constantly crash?... 1-1 1.2 Will data be erased if I update
Windows Forensics Advanced
 Windows Forensics Advanced Index: CF102 Description Windows Forensics - Advanced is the next step for forensics specialists, diving deeper into diverse processes on Windows OS serving computer investigators.
Windows Forensics Advanced Index: CF102 Description Windows Forensics - Advanced is the next step for forensics specialists, diving deeper into diverse processes on Windows OS serving computer investigators.
